Authentication-Based Secure Data Dissemination Protocol and Framework for 5G-Enabled VANET
Abstract
1. Introduction
- An interactive framework for various levels in IoV Architecture is presented;
- Secure message authentication protocol is designed for 5G-enabled vehicular networks;
- Performance evaluation is conducted and a comparison with other protocols is performed.
2. Related Work
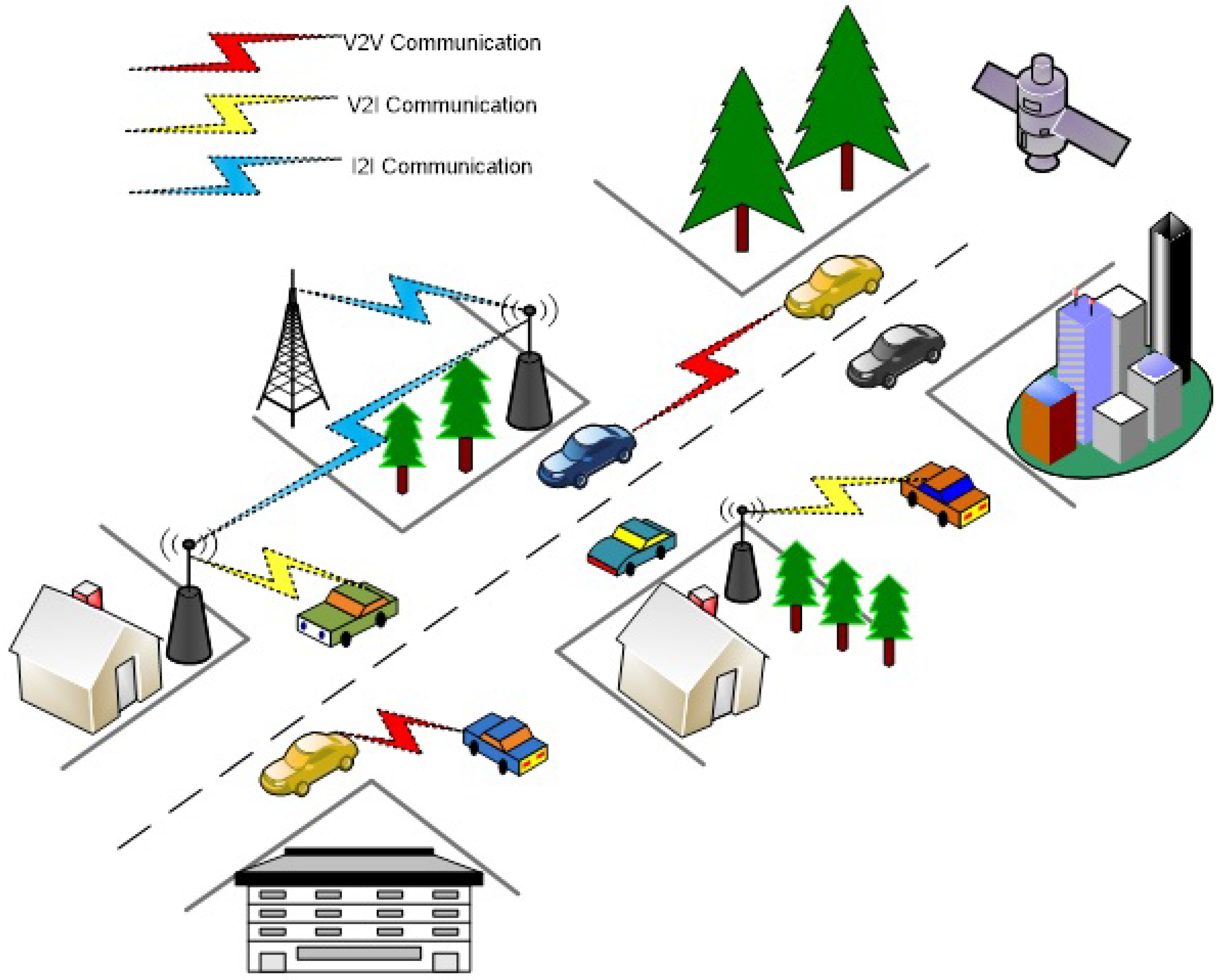
3. Interactive Model and Architecture of IoV
3.1. Interactive Model
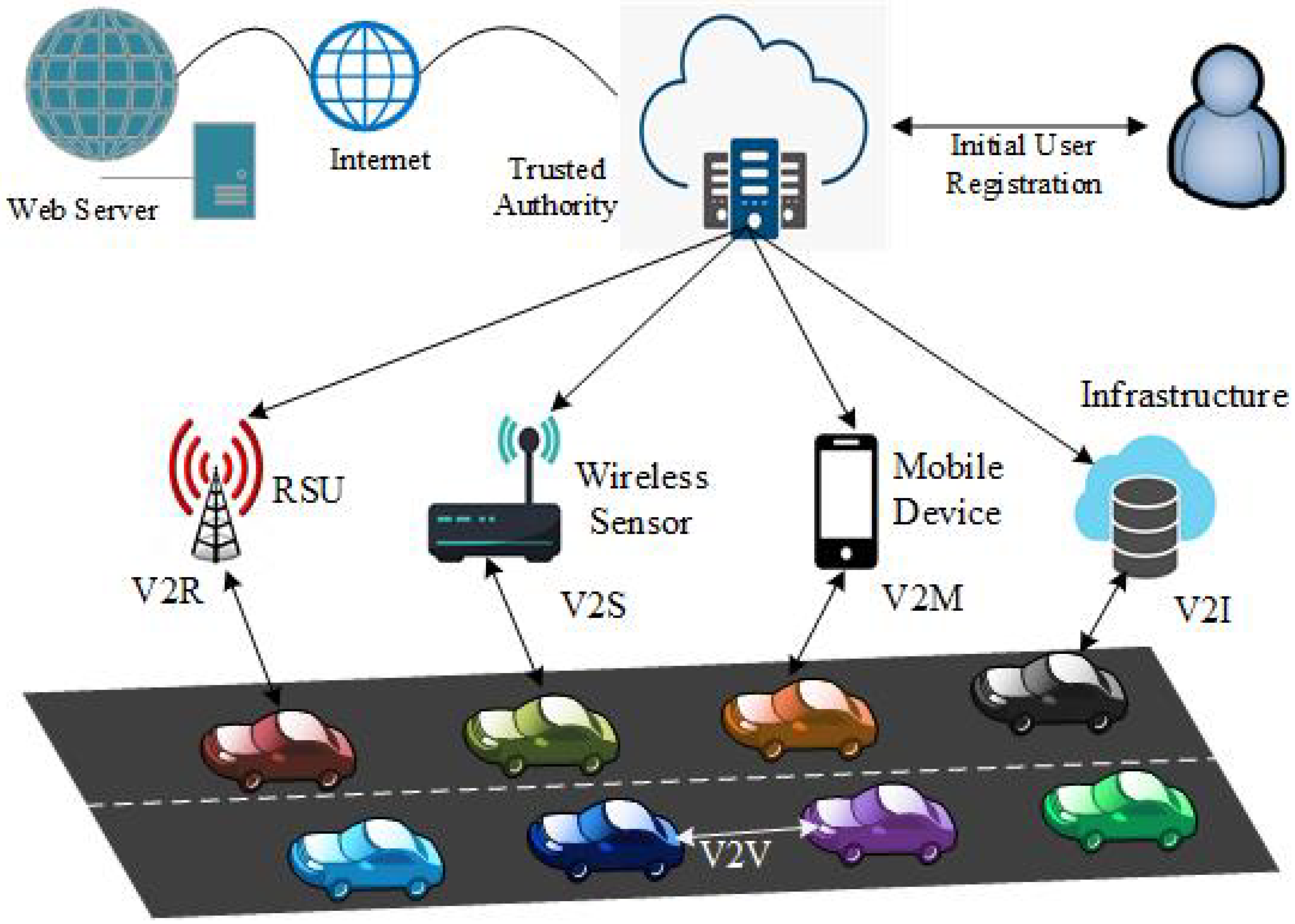
3.2. IoV Architecture
3.2.1. Application Layer
3.2.2. Control Layer
3.2.3. Cognition Layer
3.2.4. Communication Layer
3.2.5. Sensing Layer
4. System Model for A-MAC
4.1. Initiation Level
4.2. Assessment Level
4.3. Validation Level
4.3.1. Elementary Validation
4.3.2. Message Validation
5. Performance Evaluation
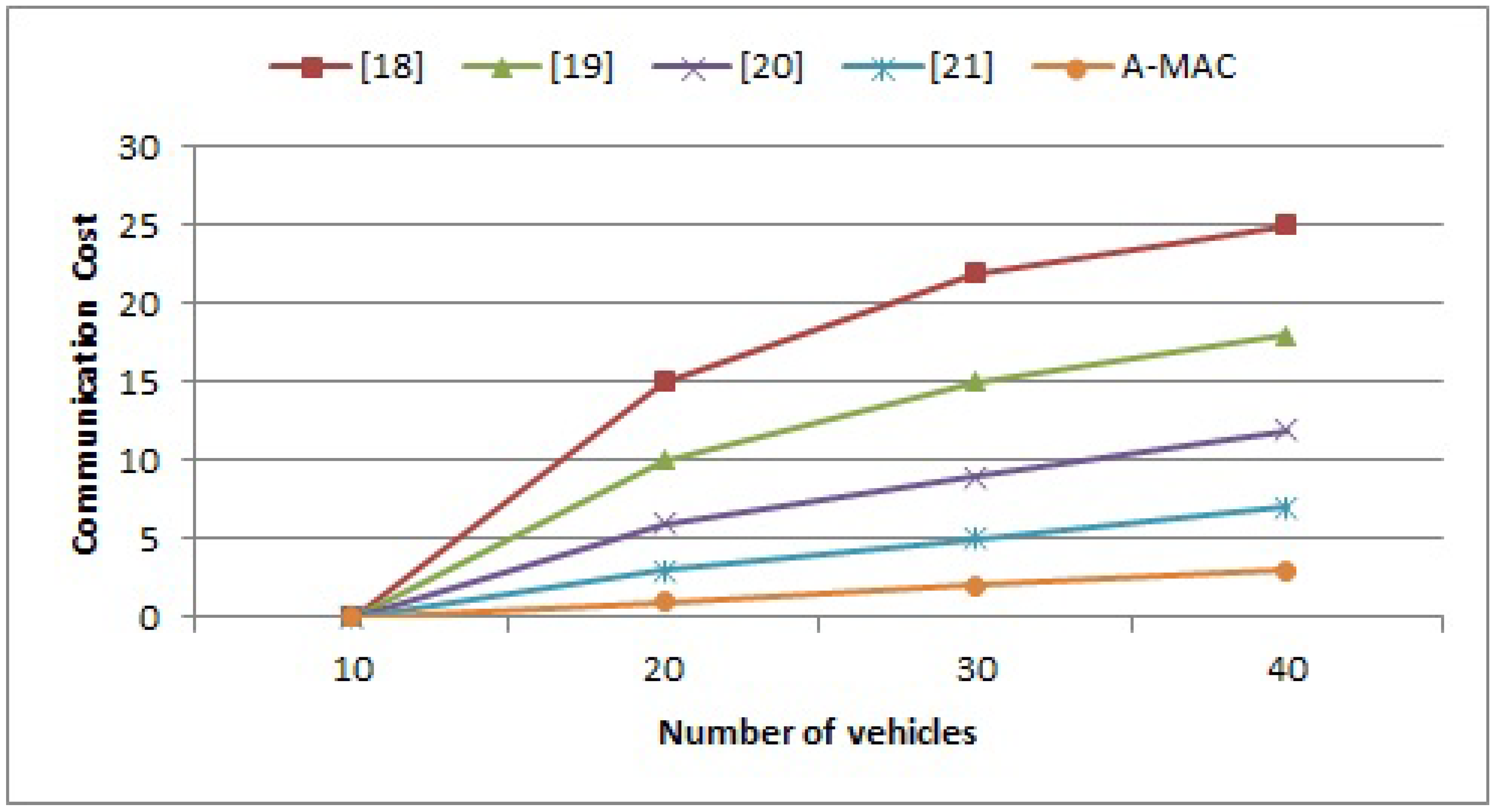
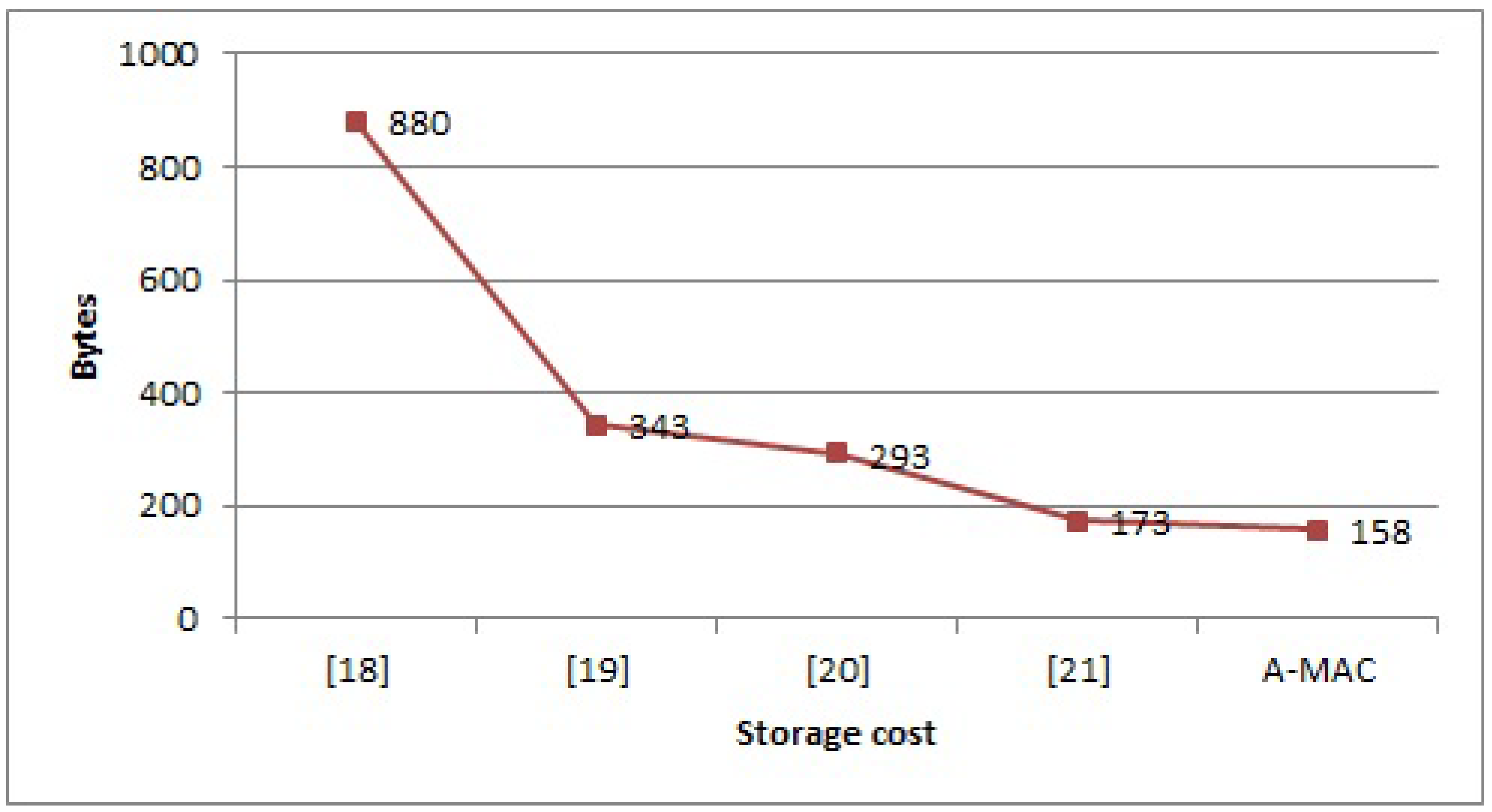
5.1. Communication and Storage Costs
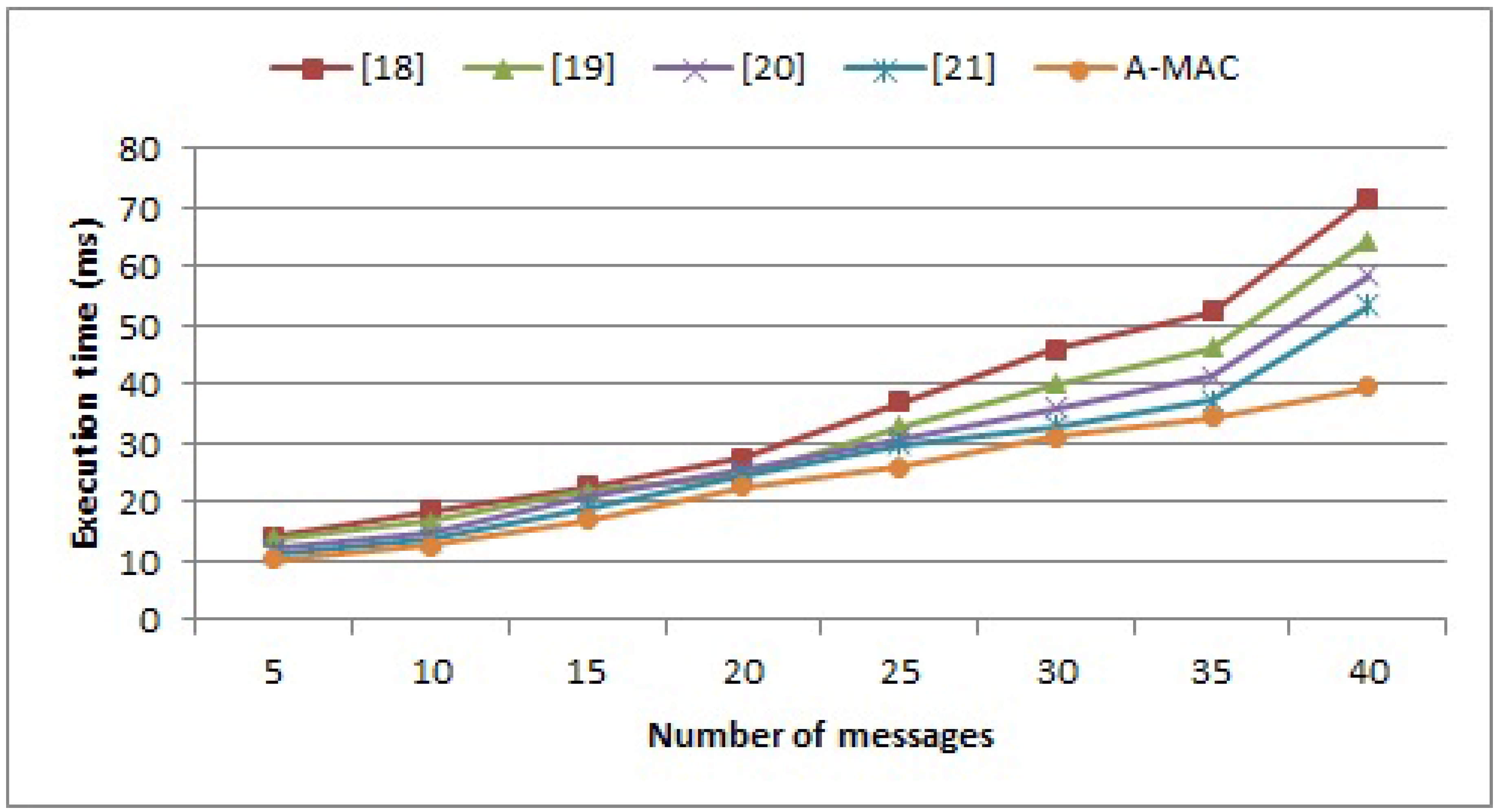
5.2. Execution Time
5.3. RSU’s Overhead
5.4. Discussion and Comparative Summary
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| ADAS | Advanced Driver Assistance System |
| D2D | Device-To-Device |
| DAS | Data Acquisition System |
| DSRC | Dedicated Short-Range Communication |
| ITS | Intelligent Transportation Systems |
| IoT | Internet of Things |
| IoV | Internet of Vehicles |
| MAC | Media Access Control |
| MD5 | Message-Digest algorithm 5 |
| OBU | On-Board Unit |
| QoS | Quality of Service |
| RSU | Roadside Unit |
| RSA | Rivest–Shamir–Adleman |
| SSL | Secure Sockets Layer |
| TA | Trust authority |
| TCP | Transmission Control Protocol |
| TLS | Transport Layer Security |
| V2M | Vehicle-to-Mobile station |
| V2P | Vehicle-to-Personal devices |
| V2R | Vehicle-to-Roadside unit |
| V2S | Vehicle-to-Sensors |
| V2V | Vehicle-to-Vehicle |
| V2X | Vehicle-to-Anything |
| VANET | Vehicular Ad hoc Network |
References
- Ang, L.; Seng, K.P.; Ijemaru, G.K.; Zungeru, A.M. Deployment of IoV for Smart Cities: Applications, Architecture, and Challenges. IEEE Access 2019, 7, 6473–6492. [Google Scholar] [CrossRef]
- Limbasiya, T.; Das, D. IoVCom: Reliable Comprehensive Communication System for Internet of Vehicles. IEEE Trans. Dependable Sec. Comput. 2019. [Google Scholar] [CrossRef]
- Gupta, N.; Prakash, A.; Tripathi, R. Medium access control protocols for safety applications in Vehicular Ad-Hoc Network: A classification and comprehensive survey. Veh. Commun. 2015, 2, 223–237. [Google Scholar] [CrossRef]
- Kenney, J.B. Dedicated Short-Range Communications (DSRC) Standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Al-Sultan, S.; Al-Doori, M.M.; Al-Bayatti, A.H.; Zedan, H. A comprehensive survey on vehicular Ad Hoc network. J. Netw. Comput. Appl. 2014, 37, 380–392. [Google Scholar] [CrossRef]
- Lee, S.; Park, J.; Gerla, M.; Lu, S. Secure Incentives for Commercial Ad Dissemination in Vehicular Networks. IEEE Trans. Veh. Technol. 2012, 61, 2715–2728. [Google Scholar] [CrossRef]
- Yong, X.; Libing, W.; Yubo, Z.; Luyao, Y. Anonymous Mutual Authentication and Key Agreement Protocol in Multi-Server Architecture for VANETs. J. Comput. Res. Dev. 2016, 53. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An Efficient Message-Authentication Scheme Based on Edge Computing for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2018, 20, 1621–1632. [Google Scholar] [CrossRef]
- Cheng, J.; Cheng, J.; Zhou, M.; Liu, F.; Gao, S.; Liu, C. Routing in Internet of Vehicles: A Review. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2339–2352. [Google Scholar] [CrossRef]
- Zhang, L.; Ding, G.; Wu, Q.; Zou, Y.; Han, Z.; Wang, J. Byzantine Attack and Defense in Cognitive Radio Networks: A Survey. IEEE Commun. Surv. Tutor. 2015, 17, 1342–1363. [Google Scholar] [CrossRef]
- Zhong, H.; Huang, B.; Cui, J.; Xu, Y.; Liu, L. Conditional Privacy-Preserving Authentication Using Registration List in Vehicular Ad Hoc Networks. IEEE Access 2018, 6, 2241–2250. [Google Scholar] [CrossRef]
- Zhang, C.; Lu, R.; Lin, X.; Ho, P.; Shen, X. An Efficient Identity-Based Batch Verification Scheme for Vehicular Sensor Networks. In Proceedings of the IEEE INFOCOM 2008-The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 246–250. [Google Scholar] [CrossRef]
- Bazzi, A.; Cecchini, G.; Menarini, M.; Masini, B.M.; Zanella, A. Survey and Perspectives of Vehicular Wi-Fi versus Sidelink Cellular-V2X in the 5G Era. Future Internet 2019, 11, 122. [Google Scholar] [CrossRef]
- Cavalcanti, E.R.; de Souza, J.A.R.; Spohn, M.A.; de Morais Gomes, R.C.; da Costa, A.F.B.F. VANETs’ Research over the Past Decade: Overview, Credibility, and Trends. SIGCOMM Comput. Commun. Rev. 2018, 48, 31–39. [Google Scholar] [CrossRef]
- Chen, M.; Tian, Y.; Fortino, G.; Zhang, J.; Humar, I. Cognitive Internet of Vehicles. Comput. Commun. 2018, 120, 58–70. [Google Scholar] [CrossRef]
- Wan, J.; Zhang, D.; Zhao, S.; Yang, L.T.; Lloret, J. Context-aware vehicular cyber-physical systems with cloud support: Architecture, challenges, and solutions. IEEE Commun. Mag. 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Altameem, A.; Prasad, M.; Lin, C.; Liu, X. Internet of Vehicles: Motivation, Layered Architecture, Network Model, Challenges, and Future Aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]
- Li, J.; Lu, H.; Guizani, M. ACPN: A Novel Authentication Framework with Conditional Privacy-Preservation and Non-Repudiation for VANETs. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 938–948. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensic Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Wang, F.; Xu, Y.; Zhang, H.; Zhang, Y.; Zhu, L. 2FLIP: A Two-Factor Lightweight Privacy-Preserving Authentication Scheme for VANET. IEEE Trans. Veh. Technol. 2016, 65, 896–911. [Google Scholar] [CrossRef]
- Zhang, L.; Hu, C.; Wu, Q.; Domingo-Ferrer, J.; Qin, B. Privacy-Preserving Vehicular Communication Authentication with Hierarchical Aggregation and Fast Response. IEEE Trans. Comput. 2016, 65, 2562–2574. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Kannan, A.; Jegatha Deborah, L. Dual Authentication and Key Management Techniques for Secure Data Transmission in Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1015–1028. [Google Scholar] [CrossRef]
- Malik, A.; Pandey, B. Security Analysis of Discrete Event Based Threat Driven Authentication Approach in VANET Using Petri Nets. Int. J. Netw. Secur. 2018, 20, 601–608. [Google Scholar] [CrossRef]
- Ora, P.; Pal, P.R. Data security and integrity in cloud computing based on RSA partial homomorphic and MD5 cryptography. In Proceedings of the 2015 International Conference on Computer, Communication and Control (IC4), Indore, India, 10–12 September 2015. [Google Scholar] [CrossRef]
- Cao, D.; Yang, B. Design and implementation for MD5-based data integrity checking system. In Proceedings of the 2nd IEEE International Conference on Information Management and Engineering, Chengdu, China, 16–18 April 2010; pp. 608–611. [Google Scholar] [CrossRef]
- Chawdhury, M.D.A.; Habib, A.H.M.A. Security enhancement of MD5 hashed passwords by using the unused bits of TCP header. In Proceedings of the 2008 11th International Conference on Computer and Information Technology, Khulna, Bangladesh, 24–27 December 2008; pp. 714–717. [Google Scholar] [CrossRef]
- Liu, J.; Li, Q.; Cao, H.; Sun, R.; Du, X.; Guizani, M. MDBV: Monitoring Data Batch Verification for Survivability of Internet of Vehicles. IEEE Access 2018, 6, 50974–50983. [Google Scholar] [CrossRef]
- Yang, F.; Wang, S.; Li, J.; Liu, Z.; Sun, Q. An overview of Internet of Vehicles. China Commun. 2014, 11, 1–15. [Google Scholar] [CrossRef]
- Salameh, N.; Challita, G.; Mousset, S.; Bensrhair, A.; Ramaswamy, S. Collaborative positioning and embedded multi-sensors fusion cooperation in advanced driver assistance system. Transp. Res. Part C Emerg. Technol. 2013, 29, 197–213. [Google Scholar] [CrossRef]
- Gupta, N.; Prakash, A.; Tripathi, R. Clustering based cognitive MAC protocol for channel allocation to prioritize safety message dissemination in vehicular ad-hoc network. Veh. Commun. 2016, 5, 44–54. [Google Scholar] [CrossRef]
- Temel, S.; Vuran, M.C.; Faller, R.K. A Primer on Vehicle-to-Barrier Communications: Effects of Roadside Barriers, Encroachment, and Vehicle Braking. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016. [Google Scholar] [CrossRef]
- Gao, S.; Lim, A.; Bevly, D. An empirical study of DSRC V2V performance in truck platooning scenarios. Digit. Commun. Netw. 2016, 2, 233–244. [Google Scholar] [CrossRef]
- Xie, Y.; Su, X.; He, Y.; Chen, X.; Cai, G.; Xu, B.; Ye, W. STM32-based vehicle data acquisition system for Internet-of-Vehicles. In Proceedings of the IEEE/ACIS 16th International Conference on Computer and Information Science (ICIS), Wuhan, China, 24–26 May 2017; pp. 895–898. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Chang, G. Efficient Privacy-Preserving Dual Authentication and Key Agreement Scheme for Secure V2V Communications in an IoV Paradigm. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Fortino, G.; Russo, W.; Savaglio, C.; Viroli, M.; Zhou, M. Modeling Opportunistic IoT Services in Open IoT Ecosystems. Available online: http://ceur-ws.org/Vol-1867/w16.pdf (accessed on 26 February 2020).
- Cugola, G.; Margara, A. Processing Flows of Information: From Data Stream to Complex Event Processing. ACM Comput. Surv. 2012, 44. [Google Scholar] [CrossRef]
- Tan, H.; Ma, M.; Labiod, H.; Boudguiga, A.; Zhang, J.; Chong, P.H.J. A Secure and Authenticated Key Management Protocol (SA-KMP) for Vehicular Networks. IEEE Trans. Veh. Technol. 2016, 65, 9570–9584. [Google Scholar] [CrossRef]
- Vladyko, A.; Khakimov, A.; Muthanna, A.; Ateya, A.A.; Koucheryavy, A. Distributed Edge Computing to Assist Ultra-Low-Latency VANET Applications. Future Internet 2019, 11, 128. [Google Scholar] [CrossRef]
- Arena, F.; Pau, G. An Overview of Vehicular Communications. Future Internet 2019, 11, 27. [Google Scholar] [CrossRef]
- Libed, J.M.; Sison, A.M.; Medina, R.P. Improved MD5 through the Extension of 1024 Message Input Block. In Proceedings of the 2018 International Conference on Machine Learning and Machine Intelligence, Hanoi, Vietnam, 28–30 September 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 18–23. [Google Scholar] [CrossRef]
- Vasudev, H.; Das, D. A Lightweight Authentication Protocol for V2V Communication in VANETs. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence Computing, Advanced Trusted Computing, Scalable Computing Communications, Cloud Big Data Computing, Internet of People and Smart City Innovation, Guangzhou, China, 8–12 October 2018; pp. 1237–1242. [Google Scholar] [CrossRef]
- MathWorks MATLAB. Version 8.5 (R2015a). Available online: https://www.mathworks.com/help/matlab/release-notes-R2015a.html (accessed on 26 February 2020).
- Ren, C.; Zhang, W.; Qin, L.; Sun, B. Queue Spillover Management in a Connected Vehicle Environment. Future Internet 2018, 10, 79. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Molinaro, A.; Harri, J.; Rothenberg, C.E.; Vinel, A. Enhancing the 3GPP V2X Architecture with Information-Centric Networking. Future Internet 2019, 11, 199. [Google Scholar] [CrossRef]
- Liu, Q.; Ma, Y.; Alhussein, M.; Zhang, Y.; Peng, L. Green data center with IoT sensing and cloud-assisted smart temperature control system. Comput. Netw. 2016, 101, 104–112. [Google Scholar] [CrossRef]



| Scheme | Overhead | Source Auth. | Modification | Privacy | Loc. Track | ID Disclosure | Traceability |
|---|---|---|---|---|---|---|---|
| [8] | High | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ |
| [18] | High | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| [19] | Low | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| [20] | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| [21] | Low | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| [22] | Low | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| [23] | High | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ |
| [24] | Medium | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ |
| [25] | Medium | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Notations | Description |
|---|---|
| Any vehicle x in the network | |
| TA | Trust Authority |
| ID of TA | |
| ID of any vehicle x | |
| Private key of unit TA | |
| h(.) | Hash function |
| ⊕ | XOR operator |
| ‖ | Connection symbol |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gupta, N.; Manaswini, R.; Saikrishna, B.; Silva, F.; Teles, A. Authentication-Based Secure Data Dissemination Protocol and Framework for 5G-Enabled VANET. Future Internet 2020, 12, 63. https://doi.org/10.3390/fi12040063
Gupta N, Manaswini R, Saikrishna B, Silva F, Teles A. Authentication-Based Secure Data Dissemination Protocol and Framework for 5G-Enabled VANET. Future Internet. 2020; 12(4):63. https://doi.org/10.3390/fi12040063
Chicago/Turabian StyleGupta, Nishu, Ravikanti Manaswini, Bongaram Saikrishna, Francisco Silva, and Ariel Teles. 2020. "Authentication-Based Secure Data Dissemination Protocol and Framework for 5G-Enabled VANET" Future Internet 12, no. 4: 63. https://doi.org/10.3390/fi12040063
APA StyleGupta, N., Manaswini, R., Saikrishna, B., Silva, F., & Teles, A. (2020). Authentication-Based Secure Data Dissemination Protocol and Framework for 5G-Enabled VANET. Future Internet, 12(4), 63. https://doi.org/10.3390/fi12040063







