Identity-as-a-Service: An Adaptive Security Infrastructure and Privacy-Preserving User Identity for the Cloud Environment
Abstract
1. Introduction
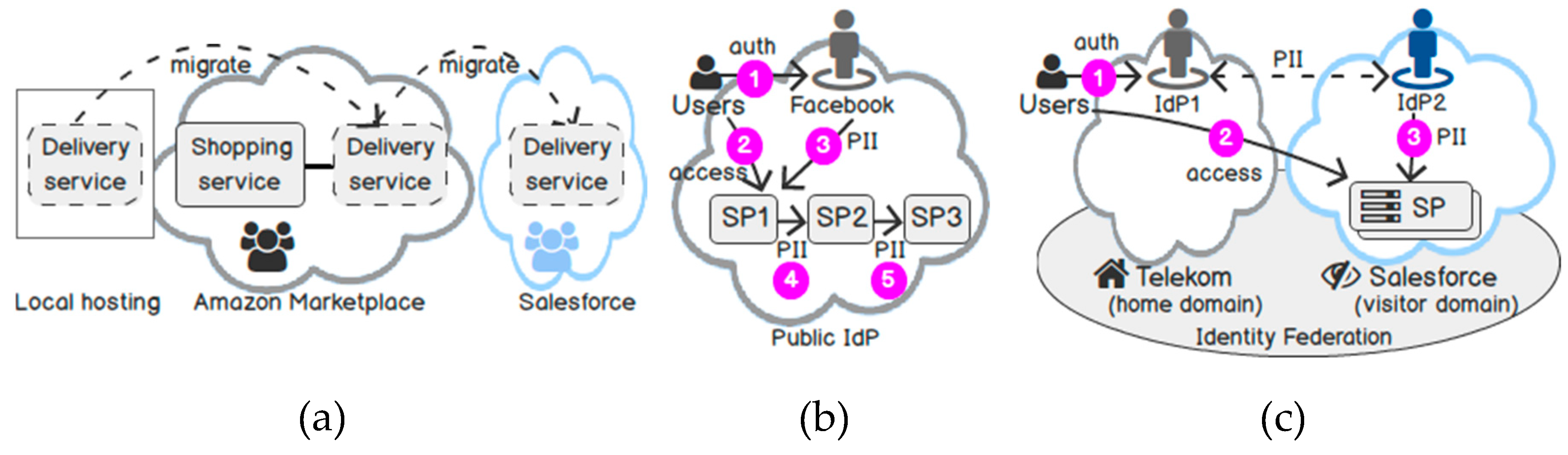
2. The Need for Identity-as-a-Service
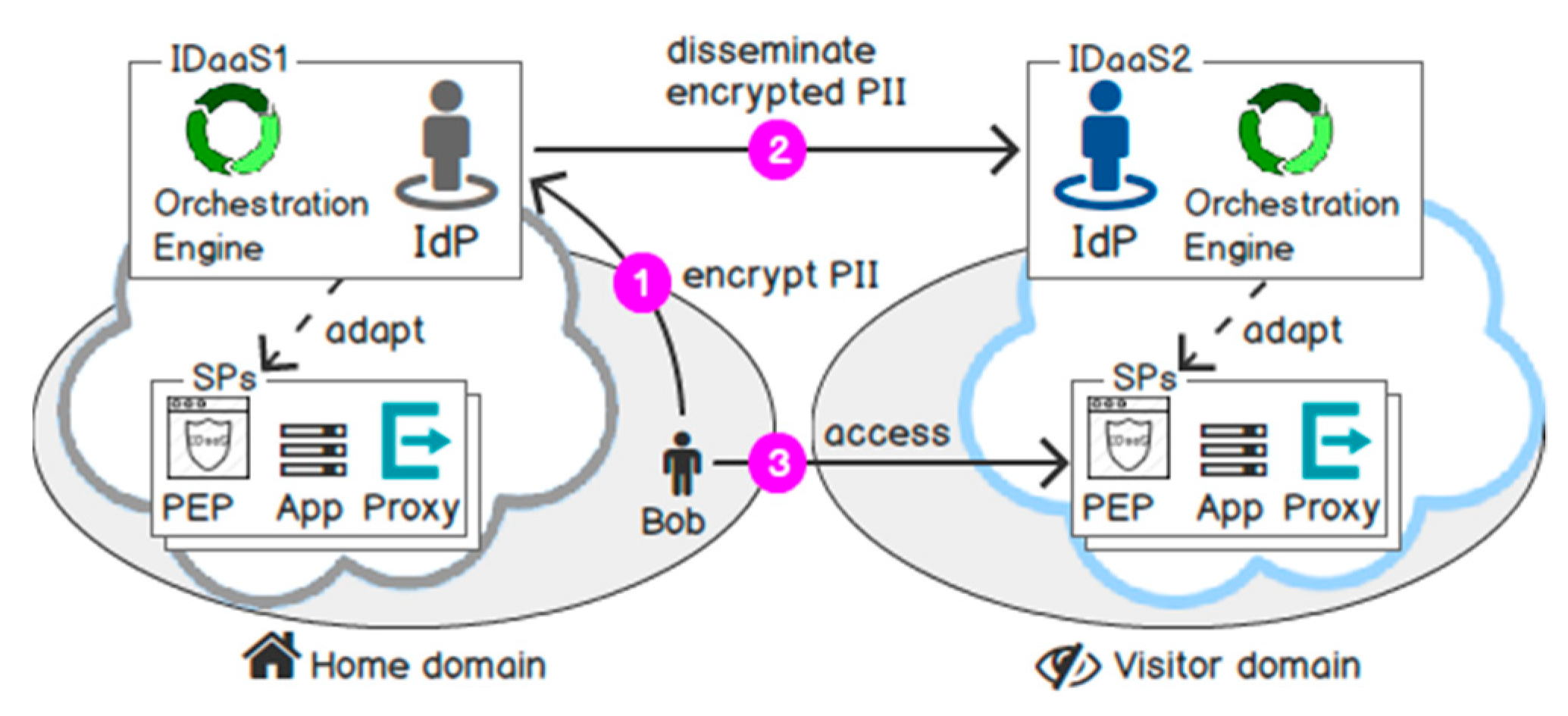
- Trust adaptation: In [33], we proposed to separate the security infrastructure from the application business logic as a new virtualization layer. In particular, we move the trust and protection relationship as well as the identity propagation between application components out of the application implementation and model them as a security topology. The topology describes the AAI components, their relationships with the application components in a platform-independent modelling language. Using the topology, IDaaS can adapt the security infrastructure, establishes a dynamic trust relationship between cloud services on demand, and evaluates any changes in the runtime environment to conform to the model.
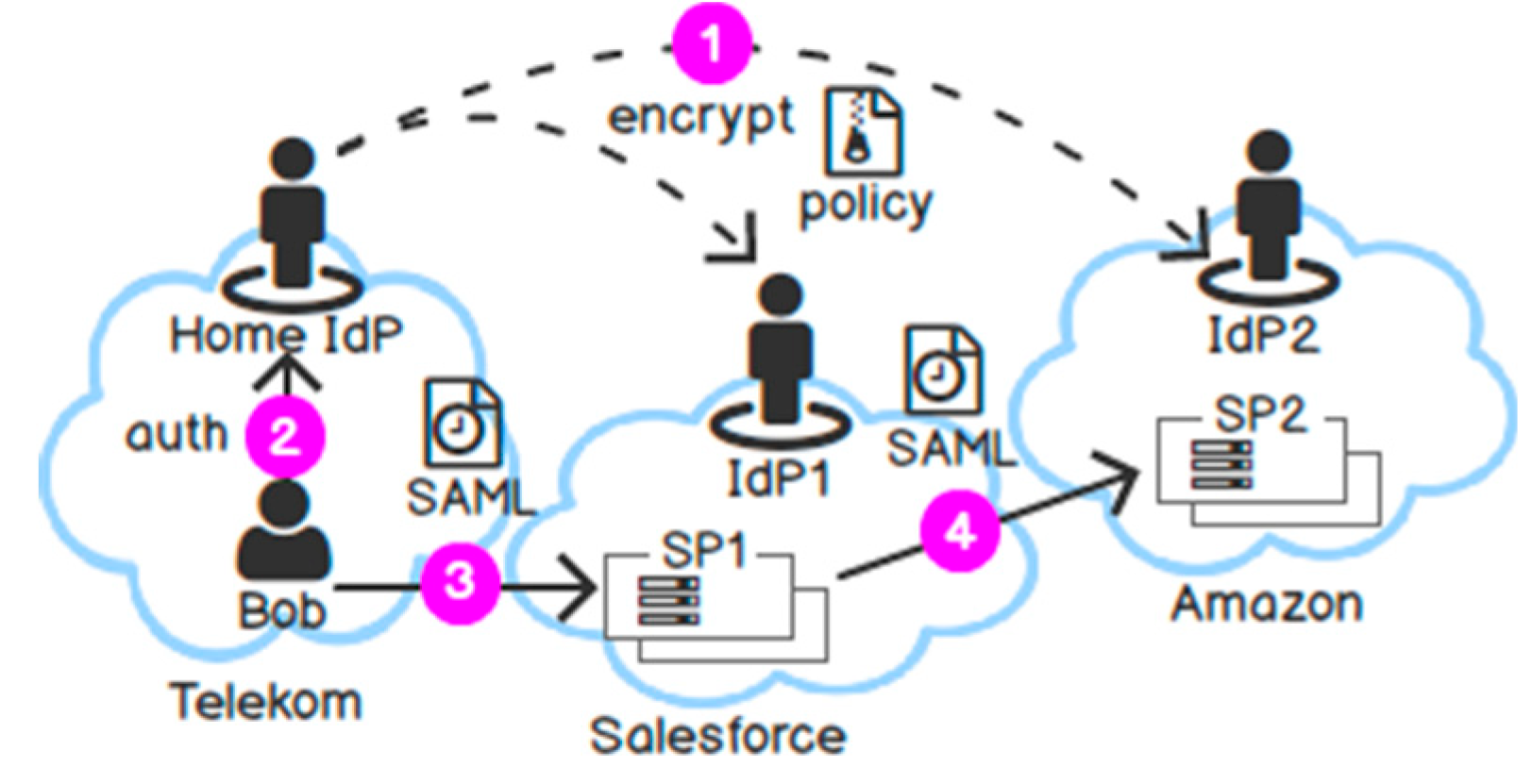
- Purpose-based Encryption: In [34], we proposed a broader solution to solve the privacy issues above: We protect PII over an intended channel (i.e., a frontend service), as well as an unintended channel (i.e., a backend service is completely transparent to the user), and against an untrusted host. We also notice that absolute protection does not exist. Thus, we seek an efficient solution that is compliant with the law, in particular, the General Data Protection Regulation (GDPR) [35]. As a result, we proposed a new approach to Purpose-based Encryption (PBE). To the best of our knowledge, our work is the first approach to combine Purpose-based Access Control and Attribute-based Encryption (ABE) to protect the confidentiality of disseminated data with multi-authorities support. Briefly, a user Bob encrypts his PII with a disclosure policy based on three main factors: “domains”, “time”, and “purposes”. Then, IDaaS disseminates Bob’s encrypted PII in various domains. Only services hosted in specific domains (e.g., Facebook, Salesforce) can decrypt the ciphertext within a given period (e.g., 14 days), if and only if the access purposes of the service (e.g., marketing, purchase) satisfy the intended purposes that Bob specifies before. Our PBE is efficient: First, our solution involves the least user interaction to prevent identity theft via the human link. Second, the implementation can be easily adapted to existing IDM systems, and the performance is fast.
3. Related Work and Discussions
3.1. Authentication and Authorisation Infrastructure
3.2. Privacy-Preserving User Identity
4. Architecture Design Overview
4.1. Design Principles for Trust Adaptation
4.2. Design Principles of Purpose-Based Encryption
5. Trust Adaptation
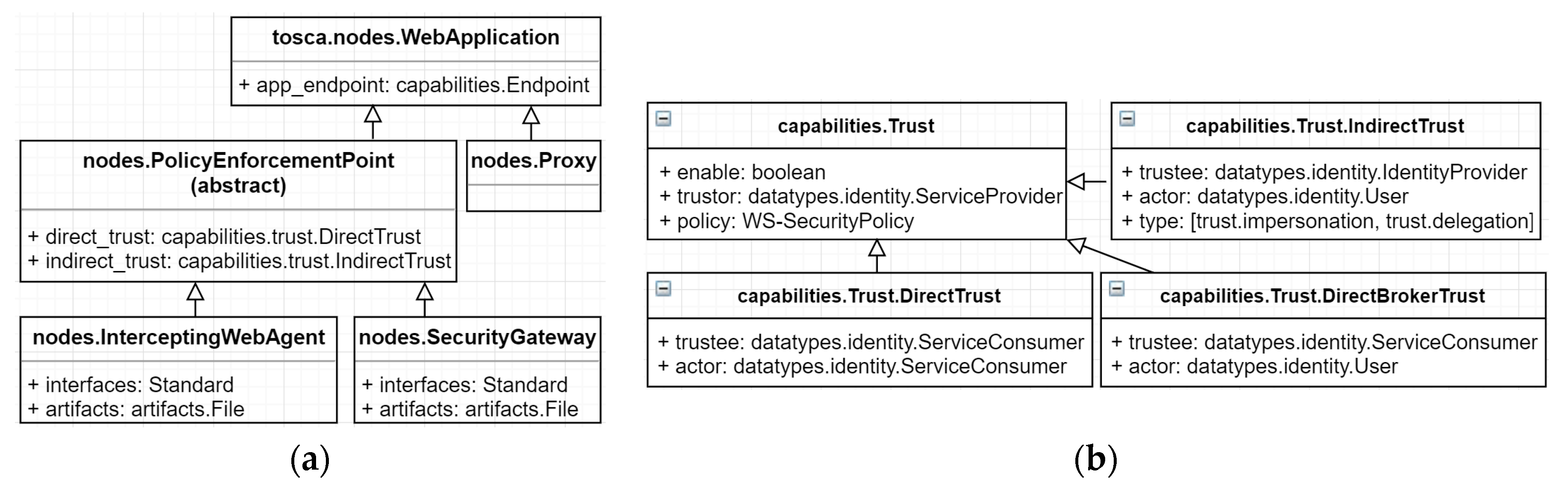
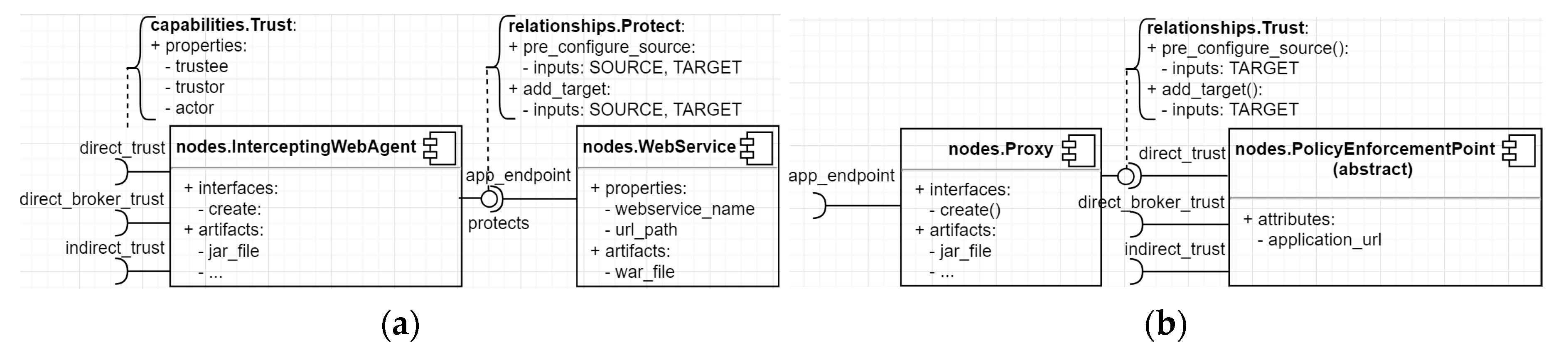
5.1. Topology Modelling
5.1.1. Node Types
5.1.2. Capabilities Types
- DirectTrust: An SP (trustor) trusts a service consumer (trustee) directly. When using this trust model, the service consumer indicates the SP to execute further using the service consumer’s identity itself (actor). This trust model may generate a security policy that builds a mutual trust relationship between Web services such as the “SSL transport binding” [57].
- DirectBrokerTrust: An SP (trustor) trusts a service consumer (trustee) to generate a self-signed identity for a user. The service consumer indicates the SP to execute further using the user identity (actor). This trust model may generate a security policy that builds a mutual trust relationship between Web services and transmits a self-signed user identity such as the “SAML assertion Sender Vouches over SSL” [57].
- IndirectTrust: An SP (trustor) trusts an IdP (trustee) for issuing a user identity. The service consumer may act on behalf of a user (i.e., identity impersonation) or act as the user (i.e., identity delegation) to request a user identity from the IdP. The consumer indicates the SP to execute further using the user identity (actor). This trust model may generate a security policy that establishes trust with an unknown Web service and transmits a user identity such as the “Symmetric binding with supporting token” [57].
5.1.3. Relationship Types
5.2. Experimental Results
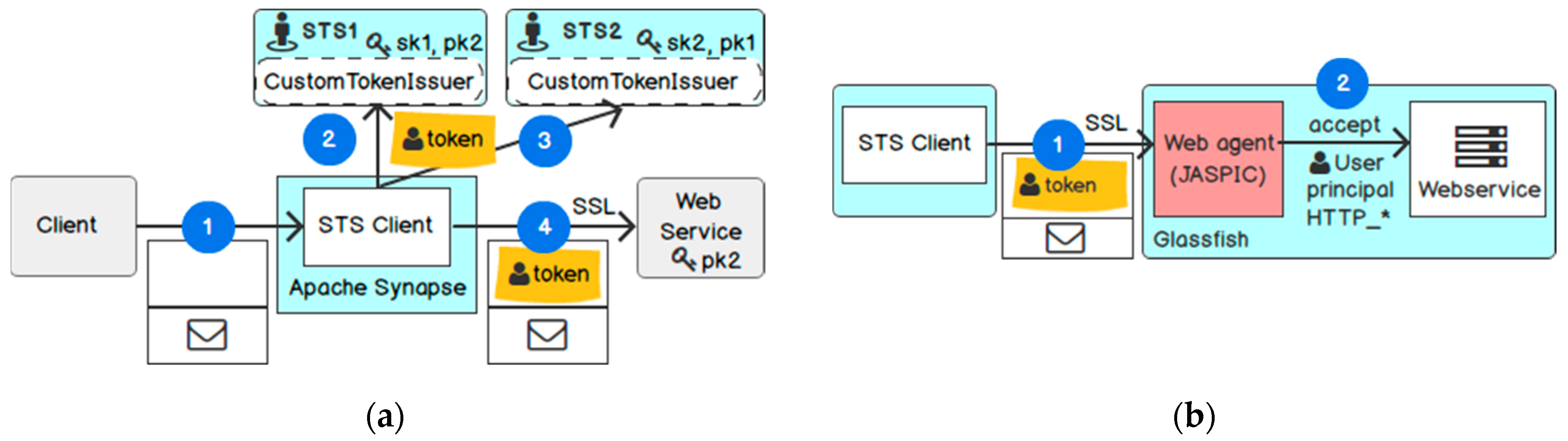
5.2.1. Test Environment
5.2.2. Migration Workflow
5.3. Implementation
5.4. Evaluation
6. Purpose-Based Encryption
6.1. Multi-Authority ABE Scheme
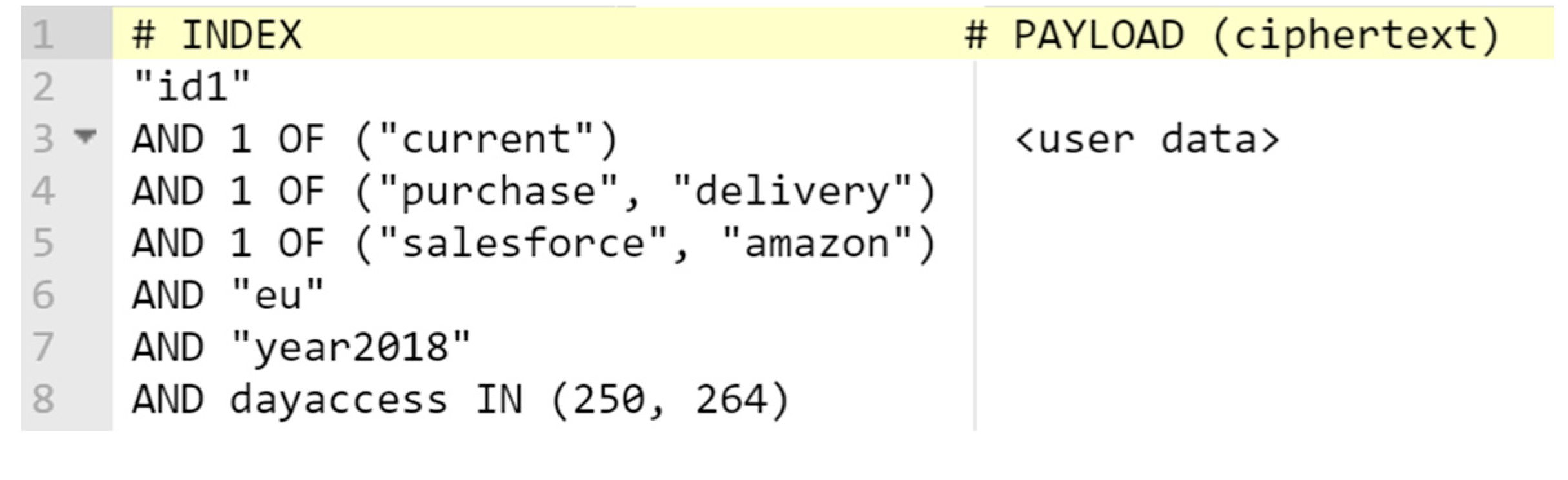
6.2. PII Encryption
6.3. The Life Cycle of PII in Federated Security Domains
6.4. Experimental Results
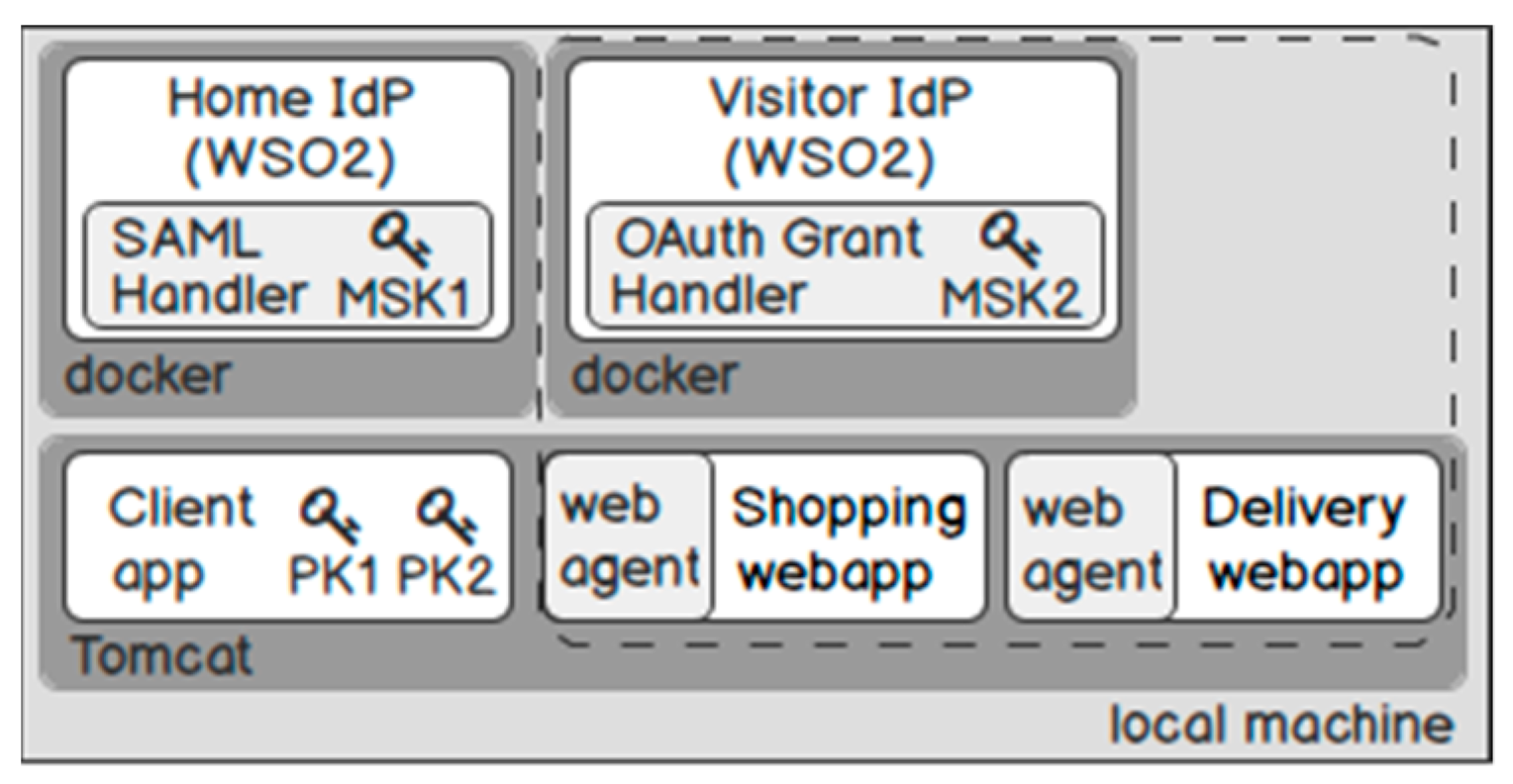
6.4.1. Test Environment
6.4.2. The Lifecycle of PII under Test
6.5. Implementation
6.6. Evaluation
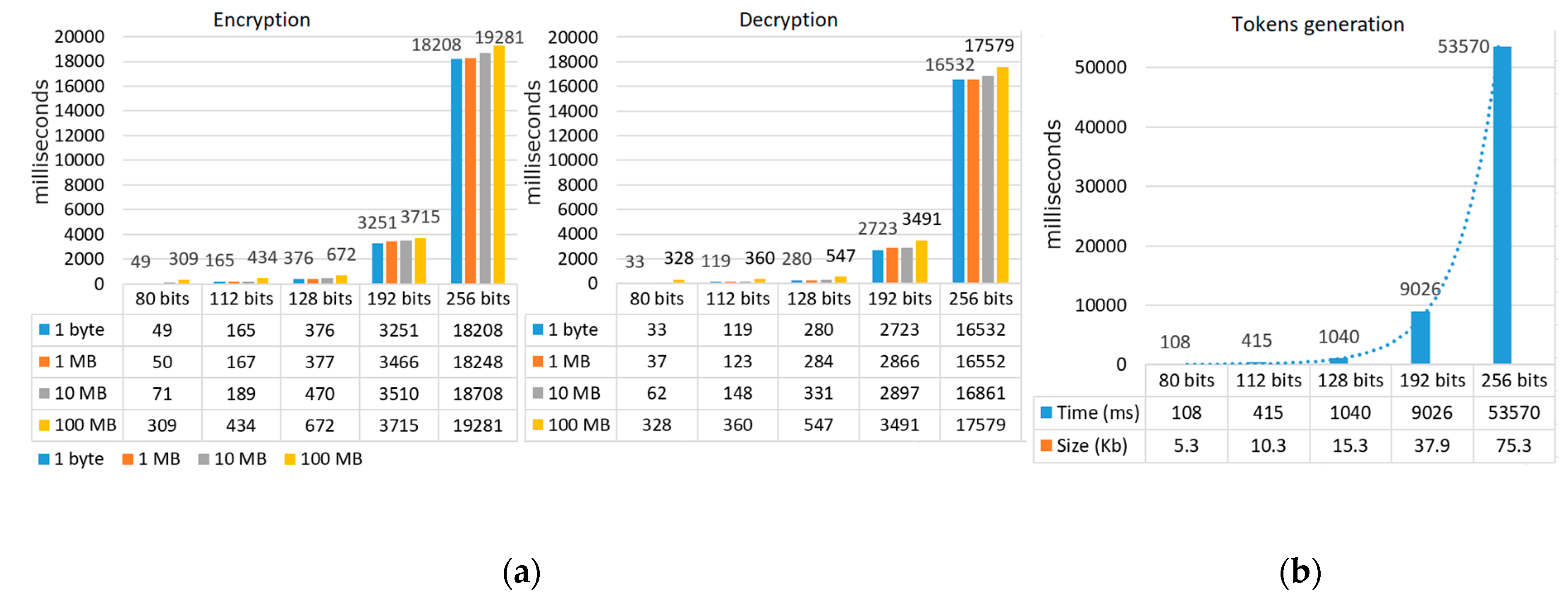
6.6.1. Performance
- Security levels: The ABE scheme computes bilinear pairing operations. The National Institute for Standards and Technology (NIST) has recommended the sizes for secure settings of parings and their validity period [77]. Our implementation also follows these key size settings of NIST for both AES and ABE.
- Key attributes: The decryption of the ABE scheme has (2l + 1) pairing operations for l key attributes, and the pairing is an expensive operation. By using the segment tree [74], we can reduce any numerical ranges of size N by a set of size log2(N) key attributes. Also, we present the access time policy in a “day” unit, which takes at most 10 key attributes. The “day” unit is not as precise as “millisecond”. However, most examples of data retention in the P3P [2] are in days, so we think the “day” unit is reasonable.
6.6.2. Benefits and Limitations
- Identity propagation between intermediaries: Each intermediate service in the call chain (e.g., the shopping and delivery service) uses the SAML response to perform a purpose authorisation request without the user interaction. Therefore, we prevent identity theft in case of users mistakenly decide, which attributes to disclose to a service. According to GDPR, the data controller is accountable for transferring PII to the data processor. That is, the data controller must determine the purposes of PII processing. In other words, when a cloud service registers on a cloud provider, it must provide its business information to the cloud provider such as the access purpose of the service. The IdP use this information to authorise a purpose request.
- Honest-but-curious IdP or SP: Here, we assume that SPs receive the SAML response and the tokens and try to learn more information about PII. First, the home IdP issues the SAML response with its private key. Therefore, SPs cannot modify the SAML response to request the visitor IdP for more capabilities than they are allowed. Second, SPs cannot combine different tokens from different transactions or users to gain more capabilities (i.e., the decryption simply fails if they do so). On the other hand, the visitor IdP can only issue a purpose token for an SP but does not have the time token to decrypt PII. However, our concept cannot prevent the collusion attacks between the visitor IdP and the SPs. Here, we assume that adversaries cannot control both systems at the same time.
- Dishonest IdP or SP: A dishonest entity is an entity that does not follow the protocol. For example, an IdP authorises a wrong purpose (with more capabilities) to an SP or an SP forwards its purpose token to another service. In such cases, an honest entity can prove that the other side has violated the protocol and the dishonest entity must pay for the penalty (according to GDPR, an entity may pay a penalty up to 20 million Euro). In the Facebook incident, Facebook would prove that it did not authorise Cambridge Analytica for the purpose “analysis”, so the dishonest application, which forwarded the user data, would pay for the penalty.
- Insider attack on an IdP: PII is encrypted on the IdP. Therefore, an administrator of one IdP does not have enough tokens to decrypt it. However, our approach cannot prevent the collusion attacks between the home and visitor IdP. Here, we assume that adversaries cannot control both IdPs at the same time.
- Malicious host: A malicious host may change the execution of plaintext code to bypass the disclosure policies and access data. In our case, if the host running the shopping (or delivery service) changes the cryptographic computation in anyways, the decryption simply fails.
7. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AAI | Authentication and Authorisation Infrastructure |
| ABE | Attribute-based Encryption |
| AES | Advanced Encryption Standard |
| B2B | Business-to-Business |
| DOB | Date Of Birth |
| GDPR | General Data Protection Regulation |
| IDaaS | Identity-as-a-Service |
| IDM | Identity Management |
| IdP | Identity Provider |
| LSSS | Linear Secret Sharing Scheme |
| P3P | Platform for Privacy Preferences Project |
| PAT | Purpose Access Token |
| PBE | Purpose-based Encryption |
| PDP | Policy Decision Point |
| PEP | Policy Enforcement Point |
| PII | Personal Identifiable Information |
| SaaS | Software-as-a-Service |
| SP | Service Provider |
| TAT | Time Access Token |
| TOSCA | Topology and Orchestration Specification for Cloud Applications |
References
- ITU-T. NGN Identity Management Framework, Recommendation Y.2720. Available online: https://www.itu.int/rec/T-REC-Y.2720/ (accessed on 21 October 2009).
- Rigo, W.; Matthias, S. The Platform for Privacy Preferences 1.1 (P3P1.1) Specification. Available online: http://www.w3.org/TR/P3P11/ (accessed on 13 November 2006).
- Chadwick, D. Federated Identity Management. In Foundations of Security Analysis and Design V SE - 3; Aldini, A., Barthe, G., Gorrieri, R., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5705, pp. 96–120. [Google Scholar] [CrossRef]
- Bücker, A.; Werner, F.; Hinton, H.; Hippenstiel, H.P.; Hollin, M.; Neucom, R.; Weeden, S.; Westman, J.; Buecker, A.; Filip, W.; et al. Federated Identity Management and Web Services Security with IBM Tivoli Security Solutions; IBM Redbooks: Indianapolis, IN, USA, 2005. [Google Scholar]
- Cantor, S.; Kemp, J.; Maler, E. Assertions and Protocols for the OASIS Security Assertion Markup Language (SAML) V2.0. Available online: http://docs.oasis-open.org/security/saml/v2.0/ (accessed on 15 March 2005).
- Kaler, C.; Mcintosh, M.; Goodner, M.; Nadalin, A. Web Services Federation Language (WS-Federation) Version 1.2. Available online: http://docs.oasis-open.org/wsfed/federation/v1.2/ws-federation.html (accessed on 22 May 2009).
- Delessy, N.; Fernandez, E.B.; Larrondo-Petrie, M.M. A Pattern Language for Identity Management. In Proceedings of the 2007 International Multi-Conference on Computing in the Global Information Technology (ICCGI’07), Guadeloupe City, Guadeloupe, 4–9 March 2007; p. 31. [Google Scholar] [CrossRef]
- Vo, T.H.; Fuhrmann, W.F.; Fischer-Hellmann, K.P. Identity-as-a-Service (IDaaS): A Missing Gap for Moving Enterprise Applications in Inter-Cloud. In Proceedings of the Eleventh International Network Conference, INC 2016, Frankfurt, Germany, 19–21 July 2016; pp. 121–126. [Google Scholar]
- Cadwalladr, C.; Graham-Harrison, E. Revealed: 50 million Facebook Profiles Harvested for Cambridge Analytica in Major Data Breach. Available online: https://www.theguardian.com/news/2018/mar/17/cambridge-analytica-facebook-influence-us-election (accessed on 17 March 2018).
- Laurent, M.; Bouzefrane, S. Digital Identity Management; ISTE Press Ltd.: London, UK, 2015. [Google Scholar]
- BBC News. Singapore Personal Data Hack Hits 1.5 m, Health Authority Says. Available online: https://www.bbc.com/news/world-asia-44900507 (accessed on 20 July 2018).
- Schläger, C.; Sojer, M.; Muschall, B.; Pernul, G. Attribute-Based Authentication and Authorisation Infrastructures for E-Commerce Providers. In Proceedings of the 7th International Conference on E-Commerce and Web Technologies, Krakow, Poland, 5–7 September 2006; Volume 4082, pp. 132–141. [Google Scholar] [CrossRef]
- Andrikopoulos, V.; Binz, T.; Leymann, F.; Strauch, S. How to Adapt Applications for the Cloud Environment. Computing 2012, 95, 493–535. [Google Scholar] [CrossRef]
- Bellendorf, J.; Mann, Z. Cloud Topology and Orchestration Using TOSCA: A Systematic Literature Review. In Proceedings of the 7th IFIP WG 2.14 European Conference, ESOCC 2018, Como, Italy, 12–14 September 2018; pp. 207–215. [Google Scholar] [CrossRef]
- Cai, Z.; Zhao, L.; Wang, X.; Yang, X.; Qin, J.; Yin, K. A Pattern-Based Code Transformation Approach for Cloud Application Migration. In Proceedings of the 2015 IEEE 8th International Conference on Cloud Computing (CLOUD), New York, NY, USA, 27 June–2 July 2015; pp. 33–40. [Google Scholar]
- Frey, S.; Hasselbring, W.; Schnoor, B. Automatic Conformance Checking for Migrating Software Systems to Cloud Infrastructures and Platforms. J. Softw. Evol. Process 2013, 25, 1089–1115. [Google Scholar] [CrossRef]
- Menychtas, A.; Santzaridou, C.; Kousiouris, G.; Varvarigou, T.; Orue-Echevarria, L.; Alonso, J.; Gorronogoitia, J.; Bruneliere, H.; Strauss, O.; Senkova, T.; et al. ARTIST Methodology and Framework: A Novel Approach for the Migration of Legacy Software on the Cloud. In Proceedings of the 2013 15th International Symposium on Symbolic and Numeric Algorithms for Scientific Computing (SYNASC), Timisoara, Romania, 23–26 September 2013; pp. 424–431. [Google Scholar]
- Kritikos, K.; Massonet, P. Security-Based Adaptation of Multi-Cloud Applications. In Data Privacy Management, and Security Assurance; Garcia-Alfaro, J., Navarro-Arribas, G., Aldini, A., Martinelli, F., Suri, N., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 47–64. [Google Scholar]
- Lizar, M.; Turner, D. Consent Receipt Specification v.1.1.0. Available online: https://kantarainitiative.org/file-downloads/consent-receipt-specification-v1-1-0/ (accessed on 20 February 2018).
- Chaum, D. Security without Identification: Transaction Systems to Make Big Brother Obsolete. Commun. ACM 1985, 28, 1030–1044. [Google Scholar] [CrossRef]
- Camenisch, J.; Lysyanskaya, A. An Efficient System for Non-Transferable Anonymous Credentials with Optional Anonymity Revocation. In Advances in Cryptology—EUROCRYPT 2001; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 93–118. [Google Scholar] [CrossRef]
- Camenisch, J.; Van Herreweghen, E. Design and Implementation of the Idemix Anonymous Credential System. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002. [Google Scholar] [CrossRef]
- Bendiab, K.; Kolokotronis, N.; Shiaeles, S.N.; Boucherkha, B. WiP: A Novel Blockchain-Based Trust Model for Cloud Identity Management. In Proceedings of the 16th IEEE International Conference on Dependable, Autonomic and Secure Computing (DASC 2018), Athens, Greece, 12–15 August 2018; pp. 724–729. [Google Scholar]
- Mikula, T.; Jacobsen, R.H. Identity and Access Management with Blockchain in Electronic Healthcare Records. In Proceedings of the 2018 21st Euromicro Conference on Digital System Design (DSD), Prague, Czech Republic, 29–31 August 2018; pp. 699–706. [Google Scholar]
- Bhargav-Spantzel, A.; Squicciarini, A.C.; Xue, R.; Bertino, E. Practical Identity Theft Prevention Using Aggregated Proof of Knowledge; CERIAS Tech Report 2006-26; Purdue University: West Lafayette, IN, USA, 2006. [Google Scholar]
- Bertino, E.; Lafayette, W.; Paci, F.; Ferrini, R. Privacy-Preserving Digital Identity Management for Cloud Computing. Identity 2009, 32, 1–7. [Google Scholar]
- Guo, N.; Gao, T.; Zhang, B.; Fernando, R.; Bertino, E. Aggregated Privacy-Preserving Identity Verification for Composite Web Services. In Proceedings of the 2011 IEEE International Conference on Web Services, Washington, DC, USA, 4–9 July 2011; pp. 692–693. [Google Scholar]
- Chow, S.S.M.; He, Y.-J.; Hui, L.C.K.; Yiu, S.M. SPICE—Simple Privacy-Preserving Identity-Management for Cloud Environment. In Applied Cryptography and Network Security; Bao, F., Samarati, P., Zhou, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 526–543. [Google Scholar] [CrossRef]
- Malina, L.; Hajny, J.; Dzurenda, P.; Zeman, V. Privacy-Preserving Security Solution for Cloud Services. J. Appl. Res. Technol. 2015, 13, 20–31. [Google Scholar] [CrossRef]
- Identity in the Cloud Use Cases Version 1.0. Available online: http://docs.oasis-open.org/id-cloud/IDCloud-usecases/v1.0/cn01/IDCloud-usecases-v1.0-cn01.html (accessed on 14 May 2019).
- Cameron, K. The Laws of Identity. Available online: http://www.identityblog.com/?p=352/#lawsofiden_topic3 (accessed on 13 May 2005).
- Landau, S.; Moore, T. Economic Tussles in Federated Identity Management. First Monday 2012, 17. [Google Scholar] [CrossRef]
- Vo, T.H.; Fuhrmann, W.; Fischer-Hellmann, K.P. How to Adapt Authentication and Authorization Infrastructure of Applications for the Cloud. In Proceedings of the 2017 IEEE 5th International Conference on Future Internet of Things and Cloud (FiCloud), Prague, Czech Republic, 21–23 August 2017; pp. 54–61. [Google Scholar] [CrossRef]
- Vo, T.H.; Fuhrmann, W.; Fischer-Hellmann, K.P. Privacy-Preserving User Identity in Identity-as-a-Service. In Proceedings of the 21st Conference on Innovation in Clouds, Internet and Networks, ICIN 2018, Paris, France, 20–22 February 2018; pp. 1–8. [Google Scholar] [CrossRef]
- General Data Protection Regulation, Final Version, Official Journal of the European Union. Available online: https://eur-lex.europa.eu (accessed on 4 May 2016).
- Onelogin. Developing with Web Access Management (WAM). Available online: https://developers.onelogin.com/wam (accessed on 17 October 2016).
- Ping Identity. Available online: https://pingidentity.com (accessed on 10 December 2016).
- Almorsy, M.; Grundy, J.; Ibrahim, A.S. TOSSMA: A Tenant-Oriented SaaS Security Management Architecture. In Proceedings of the 2012 IEEE 5th International Conference on Cloud Computing (CLOUD), Honolulu, HI, USA, 24–29 June 2012; pp. 981–988. [Google Scholar] [CrossRef]
- Steel, C. Core Security Patterns: Best Practices and Strategies for J2EE, Web Services, and Identity Management; Prentice Hall: Upper Saddle River, NJ, USA, 2005. [Google Scholar]
- Vedamuthu, A.S.; Orchard, D.; Hirsch, F.; Hondo, M.; Yendluri, P.; Boubez, T.; Yalçinalp, Ü. Web Services Policy 1.5. Available online: https://www.w3.org/TR/ws-policy/ (accessed on 4 September 2007).
- Lawrence, K.; Kaler, C. WS-SecurityPolicy 1.2. Available online: http://docs.oasis-open.org/ws-sx/ws-securitypolicy/200702/ws-securitypolicy-1.2-spec-os.pdf (accessed on 25 April 2012).
- Membrey, P.; Chan, K.C.C.; Ngo, C.; Demchenko, Y.; De Laat, C. Trusted Virtual Infrastructure Bootstrapping for on Demand Services. In Proceedings of the 2012 Seventh International Conference on Availability, Reliability and Security, ARES 2012, Prague, Czech Republic, 20–24 August 2012; pp. 350–357. [Google Scholar]
- Lang, U. OpenPMF SCaaS: Authorization as a Service for Cloud & SOA Applications. In Proceedings of the 2010 IEEE Second International Conference on Cloud Computing Technology and Science, Indianapolis, IN, USA, 30 November–3 December 2010; pp. 634–643. [Google Scholar] [CrossRef]
- Cimato, S.; Damiani, E.; Zavatarelli, F.; Menicocci, R. Towards the Certification of Cloud Services. In Proceedings of the 2013 IEEE Ninth World Congress on Services, Santa Clara, CA, USA, 28 June–3 July 2013; pp. 92–97. [Google Scholar] [CrossRef]
- Chadwick, D.W.; Fatema, K. A Privacy Preserving Authorisation System for the Cloud. J. Comput. Syst. Sci. 2012, 78, 1359–1373. [Google Scholar] [CrossRef]
- Mont, M.C.; Pearson, S.; Bramhall, P. Towards Accountable Management of Identity and Privacy: Sticky Policies and Enforceable Tracing Services. In Proceedings of the 14th International Workshop on Database and Expert Systems Applications, Prague, Czech Republic, 1–5 September 2003. [Google Scholar]
- Beiter, M.; Mont, M.C.; Chen, L.; Pearson, S. End-to-End Policy Based Encryption Techniques for Multi-Party Data Management. Comput. Stand. Interfaces 2014, 36, 689–703. [Google Scholar] [CrossRef]
- Ben Othmane, L. Active Bundles for Protecting Confidentiality of Sensitive Data Throughout Their Lifecycle; Western Michigan University: Kalamazoo, MI, USA, 2010. [Google Scholar]
- Kiernan, J. Hippocratic Databases. In Proceedings of the 28th International Conference on Very Large Data Bases, Hong Kong, China, 20–24 August 2002; pp. 143–154. [Google Scholar]
- Byun, J.-W.; Bertino, E.; Li, N. Purpose Based Access Control of Complex Data for Privacy Protection. In Proceedings of the Tenth ACM symposium on Access Control Models and Technologies, SACMAT ’05, Stockholm, Sweden, 1–3 June 2005; pp. 102–110. [Google Scholar]
- Yang, N.; Barringer, H. A Purpose-Based Access Control Model. Inf. Assur. 2007, 1, 51–58. [Google Scholar]
- Ni, Q.; Bertino, E.; Lobo, J.; Brodie, C.; Karat, C.-M.; Karat, J.; Trombeta, A. Privacy-Aware Role-Based Access Control. ACM Trans. Inf. Syst. Secur. 2010, 13, 1–31. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-Based Encryption from the Weil Pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef]
- Sander, T.; Tschudin, C.F. Protecting Mobile Agents Against Malicious Hosts. In Mobile Agents and Security; Springer: London, UK, 1998; pp. 44–60. [Google Scholar]
- Rouselakis, Y.; Waters, B. Efficient Statically-Secure Large-Universe Multi-Authority Attribute-Based Encryption. In Financial Cryptography and Data Security, Proceedings of the 19th International Conference, FC 2015, San Juan, Puerto Rico, 26-30 January 2015, Revised Selected Papers; Böhme, R., Okamoto, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 315–332. [Google Scholar] [CrossRef]
- Rutkowski, M.; Boutier, L. TOSCA Simple Profile in YAML Version 1.1, OASIA Standard. Available online: http://docs.oasis-open.org/tosca/TOSCA-Simple-Profile-YAML/v1.1/TOSCA-Simple-Profile-YAML-v1.1.html (accessed on 31 January 2018).
- Levinson, R.L.; Gullotta, T.; Chang, S.; Raepple, M. WS-SecurityPolicy Examples Version 1.0. Available online: http://docs.oasis-open.org/ws-sx/security-policy/examples/ws-sp-usecases-examples.html (accessed on 4 November 2010).
- OpenStack. Available online: https://www.openstack.org/ (accessed on 19 March 2018).
- AmazonWS. Available online: https://aws.amazon.com/ (accessed on 19 March 2018).
- Gnaniah, S. WSO2 Identity Server Documentation. Available online: http://docs.wso2.com/ (accessed on 19 March 2018).
- Alien4Cloud Version 1.4. Available online: https://alien4cloud.github.io/ (accessed on 19 March 2018).
- Cloud-Init Documentation. Available online: http://cloudinit.readthedocs.io (accessed on 17 May 2018).
- Cloudify Documenation. Available online: https://docs.cloudify.co/ (accessed on 20 May 2016).
- Apache Synapse Enterprise Service Bus (ESB). Available online: http://synapse.apache.org/ (accessed on 19 April 2018).
- Cantor, S. SAML V2.0 Condition for Delegation Restriction. Available online: http://docs.oasis-open.org/security/saml/Post2.0/sstc-saml-delegation-cs-01.html (accessed on 31 August 2016).
- Gonidis, F.; Paraskakis, I.; Kourtesis, D. Addressing the Challenge of Application Portability in Cloud Platforms. In Proceedings of the 7th South East European Doctoral Student Conference (DSC 2012), Thessaloniki, Greece, 24–25 September 2012; pp. 565–576. [Google Scholar]
- Microsoft. Windows Identity Foundation. Available online: https://msdn.microsoft.com/en-us/library/ee748484.aspx (accessed on 26 October 2016).
- Bertocci, V. Programming Windows Identity Foundation; Microsoft Press: Redmond, WA, USA, 2011. [Google Scholar]
- Leymann, F.; Rutkowski, M.; Hohl, A. Topology and Orchestration Specification for Cloud Applications - Primer Version 1.0, OASIS Committee Note Draft 01. Available online: http://docs.oasis-open.org/tosca/tosca-primer/v1.0/tosca-primer-v1.0.html (accessed on 31 January 2013).
- eXtensible Access Control Markup Language (XACML) Version 3.0. Available online: http://docs.oasis-open.org/xacml/3.0/xacml-3.0-core-spec-os-en.html (accessed on 22 January 2013).
- Campbell, B.; Mortimore, C.; Jones, M. Security Assertion Markup Language (SAML) 2.0 Profile for OAuth 2.0 Client Authentication and Authorization Grants. Available online: https://tools.ietf.org/html/rfc7522 (accessed on 31 May 2015).
- De Caro, A.; Iovino, V. JPBC: Java Pairing Based Cryptography. In Proceedings of the 16th IEEE Symposium on Computers and Communications, ISCC 2011, Kerkyra, Corfu, Greece, 28 June–1 July 2011; pp. 850–855. [Google Scholar]
- Lynn, B. On the Implementation of Pairing-Based Cryptosystems; Stanford University: Stanford, CA, USA, 2007. [Google Scholar]
- Attrapadung, N.; Hanaoka, G.; Ogawa, K.; Ohtake, G.; Watanabe, H.; Yamada, S. Attribute-Based Encryption for Range Attributes. In Security and Cryptography for Networks, Proceedings of the 10th International Conference, SCN 2016, Amalfi, Italy, 31 August–2 September 2016; Zikas, V., De Prisco, R., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 42–61. [Google Scholar]
- Lewko, A.; Waters, B. Decentralizing Attribute-Based Encryption. In Advances in Cryptology, Proceedings of the EUROCRYPT 2011: 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, Estonia, 15–19 May 2011; Paterson, K.G., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 568–588. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. AES Proposal: Rijndael. 1999. Available online: http://www.cryptosoft.de/docs/Rijndael.pdf (accessed on 19 March 2017).
- Barker, E. Recommendation for Key Management—Part 1: General. In NIST Spec. Publ. 800-57; National Institute of Standards and Technology: Gaithersburg, MA, USA, 2016; pp. 1–142. Available online: http:10.6028/NIST.SP.800-57pt3r1 (accessed on 1 January 2017).
- Barreto, P.S.L.M. Pairing-Friendly Elliptic Curves of Prime Order. In Selected Areas in Cryptography; Preneel, B., Tavares, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 319–331. [Google Scholar]
- Galbraith, S.D.; Paterson, K.G.; Smart, N.P. Pairings for Cryptographers. Discret. Appl. Math. 2008, 156, 3113–3121. [Google Scholar] [CrossRef]







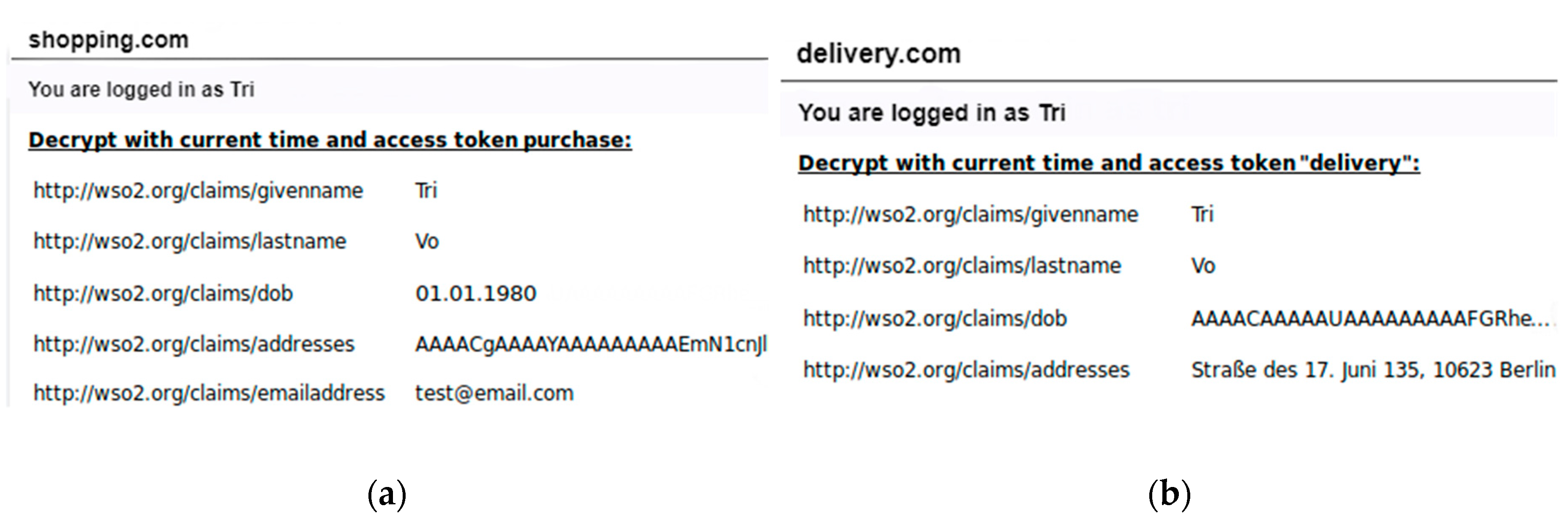
| Attribute Name | Attribute Value | Purpose | PPurpose | Domain | Country Name | Lifetime (days) |
|---|---|---|---|---|---|---|
| Last name | Tri | current, contact | purchase, delivery | salesforce, amazon | eu | 30 |
| DOB | 01.01.1980 | current | purchase, government | salesforce, amazon | eu | 30 |
| Addresses | Berlin… | contact | delivery | salesforce | eu | 14 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vo, T.H.; Fuhrmann, W.; Fischer-Hellmann, K.-P.; Furnell, S. Identity-as-a-Service: An Adaptive Security Infrastructure and Privacy-Preserving User Identity for the Cloud Environment. Future Internet 2019, 11, 116. https://doi.org/10.3390/fi11050116
Vo TH, Fuhrmann W, Fischer-Hellmann K-P, Furnell S. Identity-as-a-Service: An Adaptive Security Infrastructure and Privacy-Preserving User Identity for the Cloud Environment. Future Internet. 2019; 11(5):116. https://doi.org/10.3390/fi11050116
Chicago/Turabian StyleVo, Tri Hoang, Woldemar Fuhrmann, Klaus-Peter Fischer-Hellmann, and Steven Furnell. 2019. "Identity-as-a-Service: An Adaptive Security Infrastructure and Privacy-Preserving User Identity for the Cloud Environment" Future Internet 11, no. 5: 116. https://doi.org/10.3390/fi11050116
APA StyleVo, T. H., Fuhrmann, W., Fischer-Hellmann, K.-P., & Furnell, S. (2019). Identity-as-a-Service: An Adaptive Security Infrastructure and Privacy-Preserving User Identity for the Cloud Environment. Future Internet, 11(5), 116. https://doi.org/10.3390/fi11050116





