Abstract
Gamification, the use of game design elements in applications that are not games, has been developed to provide attractive environments and maintain user interest in several domains. In domains such as education, marketing and health, where gamification techniques are applied, user engagement in applications has increased. In these applications the protection of users’ privacy is an important aspect to consider, due to the applications obtaining a record of the personal information of their users. Thus, the purpose of this paper is to identify if applications where gamification is applied do respect users’ privacy. For the accomplishment of this aim, two main steps have been implemented. Since the main principle of gamification is the existence of game elements, the first step was to identify the set of game elements recorded in the literature that are commonly applied in various applications. Afterwards, an examination of the relationship between these elements and privacy requirements was implemented in order to identify which elements conflict with the privacy requirements leading to potential privacy violations and which elements do not. Α conceptual model according to the results of this examination was designed, which presents how elements conflict with requirements. Based on the results, there are indeed game elements which can lead to privacy violations. The results of this work provide valuable guidance to software developers, especially during the design stages of gamified applications since it helps them to consider the protection of users’ privacy in parallel from the early stages of the application development onwards.
1. Introduction
During the last few years, the use of Information and Communication Technologies (ICTs) has become more common. ICTs with different graphics, activities, requirements, and concepts have been designed for a variety of sectors. They are based on several methods or techniques according to each case, such as Virtual Reality (VR), a computer-generated simulation of a real-life environment, which makes the user feel like they are within the simulation [1]. Another example is Augmented Reality (AR) which is implemented in mobile applications and through it, items of real environments are presented in the digital world of the application [2].
After the second half of 2010, a new method, named gamification, has been introduced in ICTs, aiming to encourage users to use different types of technologies. Gamification is a method which has been implemented in several sectors, supporting user engagement and providing benefits, such as an increase of user activities, social interaction, quality and productivity of actions [3]. As the use of this method increased over the past few years [4], several attempts to define gamification have been carried out, but a standard definition has not yet been provided [5]. The most cited definition was published by Deterding et al. in 2011, who stated that “gamification is the use of game design elements in non-game contexts” [5].
Gamified applications aim to increase users’ motivation and awareness towards the use of ICTs, and the quality and quantity of the given activities’ output [3]. ICTs that use gamification consist of game design elements, thereby providing “gameful” environments and experiences for the users. Game design elements should be meaningful to the user and result in a positive change in the user’s mind in order to achieve user engagement. Such elements include the profiles, leaderboards and points [3,4].
According to the literature, research has been conducted combining gamification with other sectors. Useful implementations of this method have been noticed in the marketing domain, which aims to increase sales and to drum up interest in their products by providing appropriate gamified applications [6,7]. Equally important is the use of these applications in the health domain as users can be educated to protect themselves in a more entertaining way and without being afraid of their health problems [8,9,10,11]. Their daily interactions with these applications helps them to not forget the advice from their doctors and their prescriptions as well. In addition, another sector where gamification has been used is the education sector, which enables users to be educated in a more educational and effective way so that student interest is maintained [12,13,14].
Additionally, gamified services have been recorded in relation to tourism [15,16,17] and culture [18,19,20] offering benefits depending on the sector. The use of gamification in the aforementioned sectors is just as important as it is in software engineering. Pedreira et al. [21] in 2014, conducted a systematic mapping of gamification in software engineering by analysing several attempts in order to characterise the state of the art of this field and to identify gaps and opportunities for further research. In addition to this study, in 2018 a similar mapping was conducted by Alhammad et al. [22] regarding gamification in software engineering education, aiming to identify the works of this area. To a lesser extent, attempts to associate this method with security have been implemented with the purpose of highlighting the crucial role of security in applications and the benefits of this method in educating users regarding security issues [23,24,25].
While secure gamified services are important, the protection of users’ privacy while using them is necessary as well. As the personal information of users is stored and users’ actions are monitored, the development of services which respect users’ privacy is needed. This work concerns the examination of the relationship between gamification and privacy. Recent research efforts try to relate gamification with privacy concerns [26,27,28]. Although there are studies [29,30,31] that report the importance of privacy in gamified applications, a more detail analysis of the relationship between these two topics has not yet been recorded. Most of the studies only highlight the importance of privacy, mentioning that privacy has to be considered during the development of a gamified service in order to ensure that users will be protected [32]. Stanculescu et al. [33] mention that the protection of privacy in gamified services may increase user engagement because users will come to trust the service. Similarly, de Sa et al. [34] report that if gamified services provide privacy settings and are informed regarding the use of their information, then the trust between users and services will be increased. A more comprehensive combination of gamification and privacy has been conducted by Crowley et al. [35] who mention the case of face recognition from users’ images combining with the location and time data. As they report, this technique conflicts with privacy as users’ information can be compromised. Regarding the same privacy issue, Scherr et al. [36] suggest a technique which protect users’ faces. Specifically, they mention that the use of an animated emoji based on users’ various expressions would support privacy protection, as users’ characteristics will not be recorded.
The increasing use of ICTs magnifies the need to protect user’s privacy, as while using these applications, the personal information and activities of users are recorded without informing the users [31]. In addition, although game elements provide benefits to users and increase the use of services, it has not been investigated thus far whether they have vulnerabilities which may harm privacy [37]. As an example, several gamified applications require connecting with the user’s location, leading the applications to record his movements [19]. According to this example, the users’ privacy may be harmed. Thus, the consideration of privacy as a part of a system’s development process is important to prevent the violation of users’ privacy.
Therefore, the aim of this paper is the development of a conceptual model which represents the relationship between privacy and gamification. This is used in order to identify how user’s privacy can be violated while using gamified applications and which aspects should be considered during their development. For the accomplishment of this work, several steps have been implemented. According to Deterding et al. [5] the main principle of gamification is the game elements, as by implementing them, applications are being characterised as gamified. Thus, first it was necessary to conduct research in order to record the use of gamification in several domains and to identify which elements are used to gamify a service.
Afterwards, and in order to relate game elements with privacy concerns, a second round of research was conducted to identify how privacy can be considered during software development. According to the results, several research articles define privacy requirements as the main principle to be considered in order to ensure the protection of users’ privacy in services [38,39]. Additionally, they mention that their introduction can be accomplished by using corresponding methodologies, with a variety of these methodologies being suggested to software developers [40,41,42,43,44].
Based on the fact that game elements are the key concepts for designing gamified applications [4,5] and in parallel, privacy requirements should be considered during the development of services [38,39,40,41,42,43,44], it is interesting to study their relationship in order to identify if the concept and use of game elements lead to privacy violations through the unsuccessful completion of specific privacy requirements. Hence, a conceptual model was developed to examine the relationship between these two principles, aiming to identify whether elements conflict with privacy requirements and if so, which ones. Through this examination, software developers will be able to consider privacy during the development of a gamified service and to check which privacy requirements have to be analysed in connection to each game element.
The rest of the paper is organised as follows. In Section 2 the results of this work are described. In Section 2.1 the game elements mentioned in the literature are presented and their concepts are described. Section 2.2 includes the second part of this work, which concerns the identification of privacy requirements and the key role in designing privacy-aware information systems as they are recorded in the respective literature. In Section 2.3, the relationship of game elements with respective privacy requirements is described in detail and the conceptual model which represents this relationship is presented. In Section 3 a discussion of the results is presented. The methodology which has been followed for the summarisation of game elements is included in Section 4. Finally, Section 5 concludes the paper.
2. Results
2.1. Game Elements
According to the definition of gamification [5], services can be gamified using game elements. Implementing such elements and interesting activities in ICTs through a more attractive environment is implemented, resulting the increase of users’ engagement, curiosity, quality and productivity of actions [3,4]. The first step of this work was to conduct research in order to examine the variety of game elements and their use. During the research, it was found out that studies regarding gamification do not include the same game elements, but instead report several elements, depending on their contexts or research area. For instance, You-kai Chou [8] presents examples of gamified applications in the healthcare domain, mentioning the game element “challenges” in contrast to B. Merino de Paz [45] which describes other elements, like avatars. In addition, the “leaderboards” seem to be a considerably reported element by various studies [3,46], nevertheless, there are studies [8,12,45] that do not discuss it.
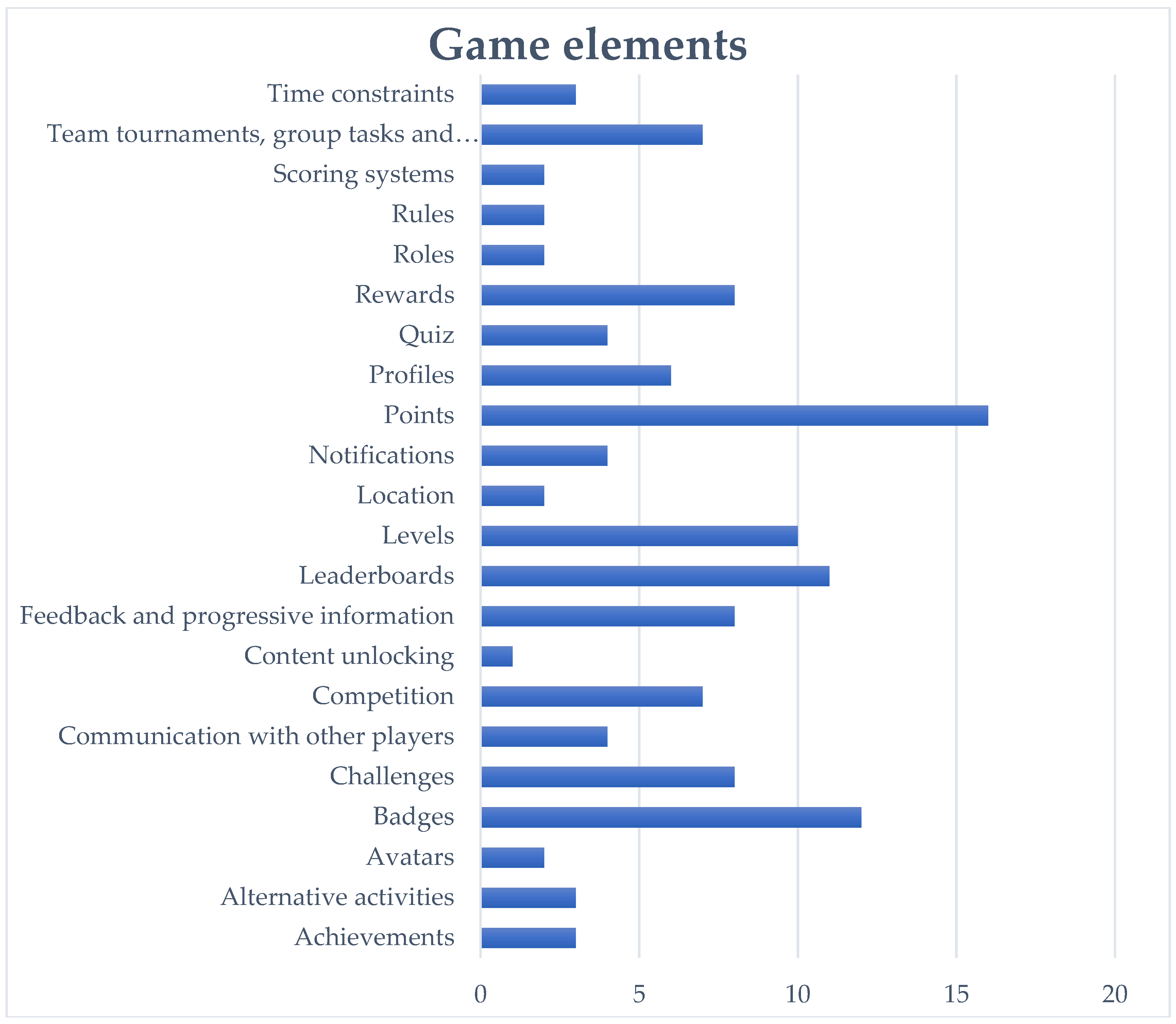
In Figure 1, the variety of the game elements is presented according to the reviewed works. Some of them are described in many studies, while others are not frequently mentioned. The game elements badges, challenges, leaderboards, levels and points are the most cited in the literature, in contrast to other elements, such as content unlocking, rules and time constraints. In addition, the elements scoring systems and roles seems to be mentioned by the same amount of studies. Furthermore, the elements rewards, profiles, feedback and progressive information are found in a variety of publications.
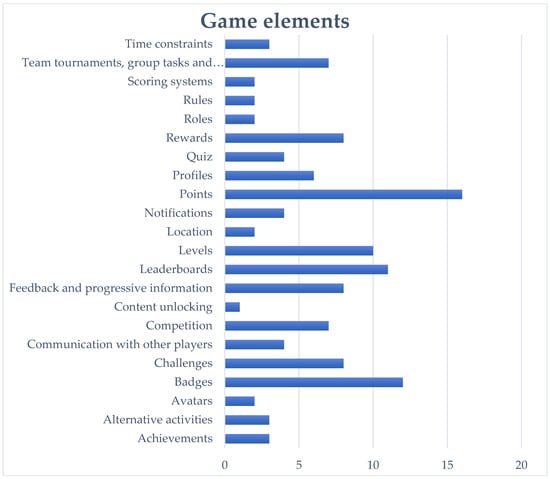
Figure 1.
Game elements and number of works mentioned.
Based on their description, some elements are more important relative to others, e.g., it is necessary to select points or to pass levels in order to receive rewards and badges. According to the results, most of the studies include several combinations of game elements, as their aim can be accomplished by matching their contexts. In Table 1, the elements which were mentioned in the literature are presented, assigned to the studies in which they are recorded.
Game design elements should be meaningful to the user and result in positive change in the user’s mind in order to achieve user engagement. Such elements are the profiles [8,13,45,46,47], where users can represent themselves with avatars [45,48]—figures or icons of a particular person—and select their own role [46,49] in the offered alternative activities [8,46,49]. Feedback and progressive information tasks [3,12,13,45,46,47,48,50] might be provided in order for the user to be informed of his actions, status and achievements [12,48,51]; moreover, some tasks with time constraints [6,46,49], and challenges [3,6,8,46,47,48,50,52] intrigue users during the interaction with the applications, as they can challenge other users in a competition [6,13,45,47,48,49,53]. In addition, game elements include scoring systems [6,46] and leaderboards [3,6,13,46,47,48,49,50,53,54], where users’ results are compared, team tournaments [8,13,45,46,47,48,49], where users have to complete group tasks [8,13,45,46,47,48,49] and to collaborate [8,13,45,46,47,48,49] in order to get badges [3,6,12,45,46,48,49,50,53,55,56,57,58] and rewards [3,6,8,13,47,49,51,52].
Additionally, the element rules [45,49] might seem deterring, although there are some examples of gamified applications which include it. This contradiction is based on the fact that in gamified technologies the element rule is not used as a restriction which deters users from using them but instead might be a condition to achieve some goals. Such goals might be the collection of points [3,8,12,13,45,46,47,48,49,50,51,52,53,55,56,58] in order to pass or to unlock [48] several levels [3,6,12,13,45,46,47,48,49,55] and this might be accomplished by answering for example a quiz [8,13,45,49]. Other gamified applications record the location [45,56] of a user, as their context is based on maps. Notifications [8,45,46,47], communication [6,12,45,46] parts between users can be used to create a “gameful” environment, as well.

Table 1.
Game elements considered by each study.
Table 1.
Game elements considered by each study.
| Game Elements | Studies |
|---|---|
| Achievements | [12,48,49] |
| Alternative activities | [8,46,49] |
| Avatars | [45,48] |
| Badges | [3,6,12,45,46,48,49,50,53,55,56,57,58] |
| Challenges | [3,6,8,46,47,48,50,52] |
| Communication with other players | [6,12,45,46] |
| Competition | [6,13,45,47,48,49,53] |
| Content unlocking | [48] |
| Feedback and progressive information | [3,12,13,45,46,47,48,50] |
| Leaderboards | [3,6,13,46,47,48,49,50,53,54,55] |
| Levels | [3,6,12,13,45,46,47,48,49,55] |
| Location | [45,56] |
| Notifications | [8,45,46,47] |
| Points | [3,8,12,13,45,46,47,48,49,50,51,52,53,55,56,58] |
| Profiles | [8,13,45,46,47] |
| Quiz | [8,13,45,49] |
| Rewards | [3,6,8,13,47,49,51,52] |
| Roles | [46,49] |
| Rules | [45,49] |
| Scoring systems | [6,46] |
| Team tournaments, group tasks and collaboration | [8,13,45,46,47,48,49] |
| Time constraints | [6,40,46] |
2.2. Privacy Requirements
As was reported above, some research [31] has been conducted on the privacy field in relation to gamification, resulting of the existence of a crucial gap. Due to this fact, the next step of this work is the conduction of research in the privacy domain to record how it can be considered during the development of services to ensure the protection of users’ privacy. The results of this step will support the examination of the relationship between gamification and privacy in order to identify if this method respects privacy issues and how they can be combined, while designing services.
As most of users’ information is digitalised, privacy is an important aspect to be considered during the development of ICTs for the protection of users’ personal information [54,55,56]. According to the literature, privacy can be protected by analysing and eliciting privacy requirements from the early stages of a software lifecycle until the late design phases [29,30,31,32,33,34,35,36,37,38,39]. In addition, several methods have been suggested to software developers for the accomplishment of this task [40,41,42,43,44].
According to several studies on privacy, the requirements of this domain are the anonymity—the ability of a subject to be unidentifiable to other subjects—pseudonimity—a subjects uses pseudonymous and not real names in order to ensure his anonymity—unlinkability—when a third party cannot link the relationship between subjects, actions, messages—undetectability—when the existence of a component cannot be detected by a third party—unobservability – the ability to hide the actions between subjects [38,39,40,41,42,43,44].
By considering all these privacy requirements during the development of a software, users’ privacy can be protected. In this work the aim is to identify if gamification respect privacy requirements by examining the relationship between game elements and the respective requirements and to provide a conceptual model that represents this examination in order software developers to be able to consider privacy during the development of a gamified service and to identify which privacy requirements have to be analysed in connection to each game element.
2.3. Game Elements/Privacy Requirements
As in gamified applications the performed activities and the employees/users who perform them can be monitored privacy can be violated. The main issues that need to be considered during the development of gamified applications and for which the users should be informed about are the kind of stored data, the time and place that data will be stored and the persons who have access to the users’ data [29,30,31].
According to gamification the key concepts is the introduction of game elements in services to be gamified. Similarly, in the privacy domain it is important to develop software with privacy requirements in mind. As a consequence, the examination of the relationship between these two parameters is important in order to identify if game elements respect privacy requirements.
To achieve all of this, all summarised elements of the Table 1 was examined in connection with the identified privacy requirements, based on the context and use of each one. Through this examination, it was identified that there are game elements such as badges, rewards, time constraints whose meaning and use do not violate privacy, as if the rewards are not connected to a person, his identity cannot be revealed. By contrast, elements such as leaderboards, profiles and competition may harm privacy due to the record of user’s personal information and the fact that users’ identity can be linked with their actions.
Some applications used to have the creation of a profile as a mandatory condition in order to interact with them. A minority of others can be used without this requirement. As the creation of a profile can be completed, usually, by connecting through a social account such as Facebook or by using an email account, obtaining a record of users’ personal data is inevitable. Even if the creation of a profile is necessary for the accomplishment of several tasks offered by an application, it automatically means that the protection of privacy is a difficult task. Starting from the game element “avatar”, which concerns an icon with the face of a person, the identity of a user can be revealed. Thus, either the anonymity or pseudonimity of a user can be compromised and therefore, a third-party can link and detect the identity with the user’s actions and observe them. The case of a “challenge” with other players and specifically, if a user has a profile, creates a a risk for the anonymity of users, as they can recognise easily their opponents’ identity and information. Consequently, the actions of the user can be linked with his identity.
The elements “communication” or “competition” with other players clearly harm the privacy of a user and their privacy requirements, due to their context. Regardless of the existence of a profile, users’ traits can be compromised by their communication. The only difference between these two elements is that a competition users’ privacy can be harmed only if the user has a profile, so that her identity is known. Even if she uses a pseudonymous identity, a third-party can recognise her using other information, such as her email address or social media account.
The element “leaderboards” can violate the anonymity of a user in case of a profile as the results of the competition are public, so that they can be linked to the name of each user. In that case the identity and the actions of the user cannot be unlinked. The same risk concerns the case of a pseudonymous identity, as it is connected to the users account, so his identity can be recognised. The “location” element is very risky due to the connection with users’ real locations. The actions of a user can be recorded and monitored, so privacy cannot be protected and this element conflicts with all privacy requirements.
Most of applications use “notifications” in order to notify users regarding the next or pending actions. In that case there is a connection with users’ account as the actions are recorded and the person who completes them can be compromised. As such, this element is a risk for all their privacy requirements.
The next element according to the table is the “profile”. With this element, users’ data are recorded and stored and consequently, so that the identity of the user can be identified regardless of whether they have a pseudonymous identity or not and can be connected with his actions. Afterwards, the conflict between the element “quiz” and the requirements depends on the type of the quiz. In the case that the user has a profile his anonymity is in risk, the pseudonymous identity can be disclosed and the answers can be linked with the person. Depending on the type of questions the same requirements can be harmed, e.g., if the questions concern user information and habits. The “role” of a person can be disclosed if the user has a profile as his identity can be linked with his actions which afterwards can be detected and observed. In conclusion, if the user “collaborates” with others, then the actions and his identity can be compromised, due to the existence of a profile which prevents his privacy from being protected. Table 2 represents the aforementioned analysis by matching the game elements with the privacy requirements.

Table 2.
Matching Game elements with Privacy Requirements.
The above identification shows that the game elements conflict with privacy requirements. Both are considered during the design phase of a service by software developers. The results presented in Table 2 should be considered by developers in order to ensure that user privacy can be protected. In order for developers to understand how each element conflicts with the privacy requirements, a conceptual model according to the findings of this work has been designed.
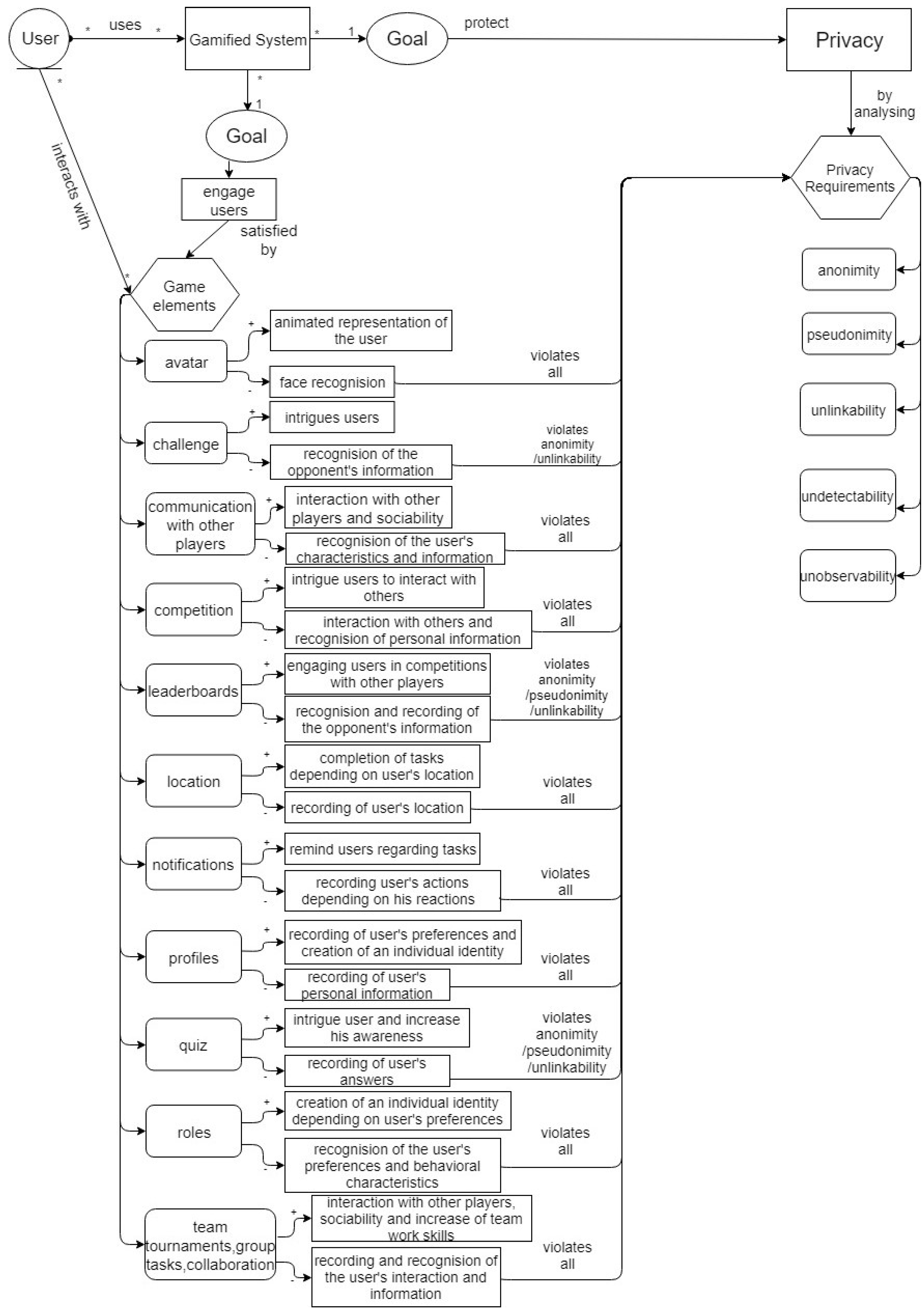
Specifically, according to Figure 2, many gamified systems are used by several users. While designing gamified systems, software developers should achieve two main goals. First, as the aim of gamification is to engage users, game elements are needed to be used for the satisfaction of this purpose. Through the interaction between users and game elements, a more interesting service can be provided, resulting in the increase of its use. In parallel, a gamified system should be designed, while considering the protection of user privacy. This goal can be satisfied by analysing privacy requirements.
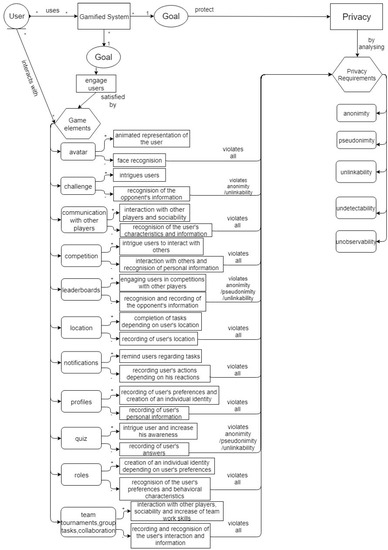
Figure 2.
The interrelation of game elements and privacy requirements.
The main purpose of this model is to present how each element conflicts with the privacy requirements. To achieve it, the advantages and the disadvantages of the elements are presented and afterwards, each disadvantage has been assigned to the privacy requirements. According to this analysis, software developers will be able to understand how the elements violate privacy requirements. The game element avatar consists of an animated representation of the user which creates a more entertaining way to create his identity. At the same time, in order to create this animated character, the technique face recognition is needed. This fact means that user’s face is recorded, resulting in the violation of either his anonymity or his pseudonimity and accordingly, all privacy requirements are violated. The game element “challenge” on the one side intrigues users, as it supports the interactions between them, but it means that their information can be recognised. Thus, this disadvantage results in the violation of anonymity and unlinkability.
In addition, interactions between users and the increase of their sociability can be achieved by the communication platforms or competitions. Accordingly, this element violates all requirements, as users’ characteristics and information regarding their identity can be revealed. A result after several competitions is the record of users’ results and statuses in leaderboards, but this record violates the anonymity or pseudonimity of users and the unlinkability between their identities and their actions. A crucial violation is the record of users’ location, as some gamified services requires the connection of user locations to complete tasks. This element violates all privacy requirements, as the status, location and information of users can be recorded and monitored. Another element which violates all the privacy requirements is the notifications. On one hand, this technique reminds users of several tasks, but it also means that their reactions are recorded and monitored. Accordingly, the creation of a profile provides an individual identity, but users’ personal information can be recorded. Thus, all privacy requirements are violated. Similarly, by the creation of a role, an individual identity can be created depending on users’ preferences, but these preferences and the behavioural characteristics of users can be recognised. Another element which intrigues users is the provision of quizes. The benefit of this element is the increase of users’ awareness, but it requires the recording of users’ answers. Thus, either anonymity or pseudonimity can be violated and users’ information can be linked to the identity of users. The last element, according to the model consists of the group tasks between users. As with the elements of competition and communication, the collaboration between users increases their sociability and team work skills, but their information and actions can be recorded and recognised. As a result, all privacy requirements can be harmed.
3. Discussion
According to the results of this research, gamification is an important method that can be used due to the increase of users’ engagement and can be implemented in the service of sectors such as health, marketing, tourism, software engineering, education, culture and security [6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25]. The game elements, the main principle of gamification, have been applied in various domains, indicating the benefits of this method. The aim of gamified applications in marketing and tourism is to increase companies’ sales and to engage people to visit tourist destinations, accordingly. On the other side, the implementation of this method in education, culture and health is designed to educate users depending on the context of each application. For instance, there are gamified services in health, where users are trained to not forget their prescriptions and daily exercises. This type of application is educational, maintaining users’ interest and in parallel, supporting actions regarding the protection of their health. In addition, according to the literature, this method has been studied in relation to software engineering, highlighting that the incorporation of game mechanics and elements is a more attractive task for s/w developers while designing gamified services. Furthermore, the combination of gamification with the security domain aims to increase user awareness regarding their protection by indicating threats while using technologies. As the use of ICTs has been increased, such services are important for users. In all these studies several game elements were mentioned. The first step of this work was the conducting of research to record the mentioned game elements in the literature. It was noticed that game elements cannot be used individually but exists only by several combinations, e.g., a user can pass levels by collecting points and in leaderboards the results are recorded based on the progress of each user.
As ICTs are used by people and their information is recorded, it is important not only to provide novel services but also to consider privacy issues during their development. According to the literature, privacy can be protected by introducing, eliciting and analysing privacy requirements during the design of systems [38,39,40,41,42,43,44]. It was noticed that, though there are works which study the relation between gamification, software engineering and security, there is an important gap in the literature regarding the combination of gamification and privacy, where the need to identify the relationship between them is discerned. Specifically, with the regulation “General Data Protection Regulation (GDPR)” the protection of users’ personal data has a mandatory aspect which needs to be considered while developing technologies. By developing gamified services which protect users’ privacy, users will feel comfortable and they will trust these services.
As mentioned, a detailed examination of the relationship between game elements and privacy requirements has not been provided and it has not been investigated whether the benefits that game elements provide may conflict with privacy. In this work, this relationship is examined by combining the game elements and privacy requirements, as both are used by gamification and privacy accordingly, during the design of systems. The examination was based on the concept and use of game elements and on the other side on the aim of privacy requirements. By this approach, the purpose was to explore if the use of game design elements respect privacy requirements or conflict with them. For instance, the game element of “location” conflicts with all privacy requirements, as by using this element, the location of users can be recorded and monitored. Consequently, it violates users’ privacy, as his actions, statement and identity can be recognised. Another example involves the element “leaderboards”, where users’ results for several activities are presented in comparison to others. Thus, the identity of a user is connected with his progress, so that, a third party can be informed about users’ actions. In this case, users’ privacy is not protected as well. Based on this approach of identification, all the elements were examined in relation to requirements. Certainly, according to the results, there are game elements, such as points, levels whose concepts do not violate privacy, as a number—in case of points—or a level does not betray by itself the connection to an identity.
As mentioned, a such examination has not yet been recorded in the literature. As game elements and privacy requirements are implemented while designing systems, a representation of the relationship between them based on the results of the above examination is needed. Thus, a conceptual model was designed to highlight how the game elements conflict with privacy requirements and which aspects should be considered while designing such services. Although game elements provide benefits to users and increase the use of these services, in parallel they may violate privacy. This model will support developers while designing gamified systems, as it provides a set of concepts that can be used, allowing them to make design choices. They will be able to identify which techniques have to be implemented in order to avoid several vulnerabilities which may harm users’ privacy.
It is clear that the protection of privacy is a complicated task, as the existence of some game elements require actions which conflict with privacy requirements. This fact has to be considered by software developers of gamified applications during the development of a service from the early stages of the design phase.
4. Materials and Methods
As was reported, it was important to explore how gamification is implemented in several sectors. A number of studies which concern gamification were collected and examined to identify the use of this method by several sectors. According to the definition of this method [5], game elements are used to gamify services. By studying several implementations of gamification, it was noticed that different game elements are used, depending on the case, the concept and the aim of each service. As a consequence, the first step was to conduct research in order to record all the game elements mentioned in the literature and to comprehend their use and context.
As in all services where user information and actions are monitored, it was crucial to identify if the relationship between gamification and privacy has been recorded. Thus, one of the above-mentioned sectors was privacy. Despite the importance of privacy protection, according to the results, a crucial gap has been identified regarding privacy in gamified applications. Thus, the second step of this work was to conduct a research on privacy domain in order to explore how privacy can be protected during the design of services. A variety of studies mention that privacy requirements are the principles which should be considered by software developers for the development of privacy-aware systems [38,39,40,41,42,43,44]. Further to the above results and as long as the privacy requirements and the importance has been comprehended, the next step was to examine the relationship between them and the game elements. The aim of this work was to examine the relationship between game elements and privacy requirements, the cores of gamification and privacy, respectively, in order, afterwards, to identify the impact of gamification, and specifically, of the game elements to privacy requirements and if gamification respects privacy. To carry out these review steps, we followed the recommendations in reference [59].
Data Sources and Search Strategy
A literature review of works, written in English and indexed in Google Scholar, Scopus, IEEExplore, ACM Digital Library, Springer Database and Google for examples of gamified applications, was conducted to explore game elements. This research was conducted during November 2018 and the search was applied to the titles, abstracts and keywords of journal, workshop and conference papers in order to ensure that their contexts were appropriate for the purpose of this work. The search strategy is outlined in Table 3.

Table 3.
Summary of the search strategy.
While gamification is defined as the services which use game elements to be gamified, the main selected search terms were: “Gamification” and “Game elements”. By searching first only with the use of these two terms, several studies concerning gamification were identified in combination with other sectors. Thus, the Boolean AND was employed to link these terms to “Education”, “Marketing”, “Health”, “Tourism”, “Culture”, “Security” and “Privacy” in order to identify implementations of gamification or game elements in these sectors.
After searching regarding gamification, as it was reported, the second level of search concerned privacy. As it was noticed that a variety of studies mentioned the importance of privacy requirements for the design of services, the search was limited to identifying what are the privacy requirements and how they can be considered by software developers. Thus, the main terms were: “Privacy” and “Privacy Requirements”, using the Boolean AND to link them. A number of publications were recorded and furthermore, some of them concerned methods which used to analyse and elicit privacy requirements for the design of privacy-aware systems.
Due to the large number of results returned by a general search and in order to keep the search within reasonable bounds, the number of the results was limited by selecting publications according to the inclusion and exclusion criteria. The selection strategy is summarised in Table 4. First, academic, journal, conference papers and sites with examples of gamified application were needed to identify the combination of gamification with the above-mentioned sectors. Furthermore, papers dealing with game elements were selected to record their variety, as they showed the ways of gamifying services. Next, studies which describe the privacy requirements and their introduction into systems were selected. The publication date for the studies of gamification was defined as being since 2008, as according to the literature most of the studies were published after 2010. Thus, it was preferable to limit the publication period to the last ten years. In order for the comprehension of this research to be effective, the studies had to be written in English.

Table 4.
Summary of the selection strategy.
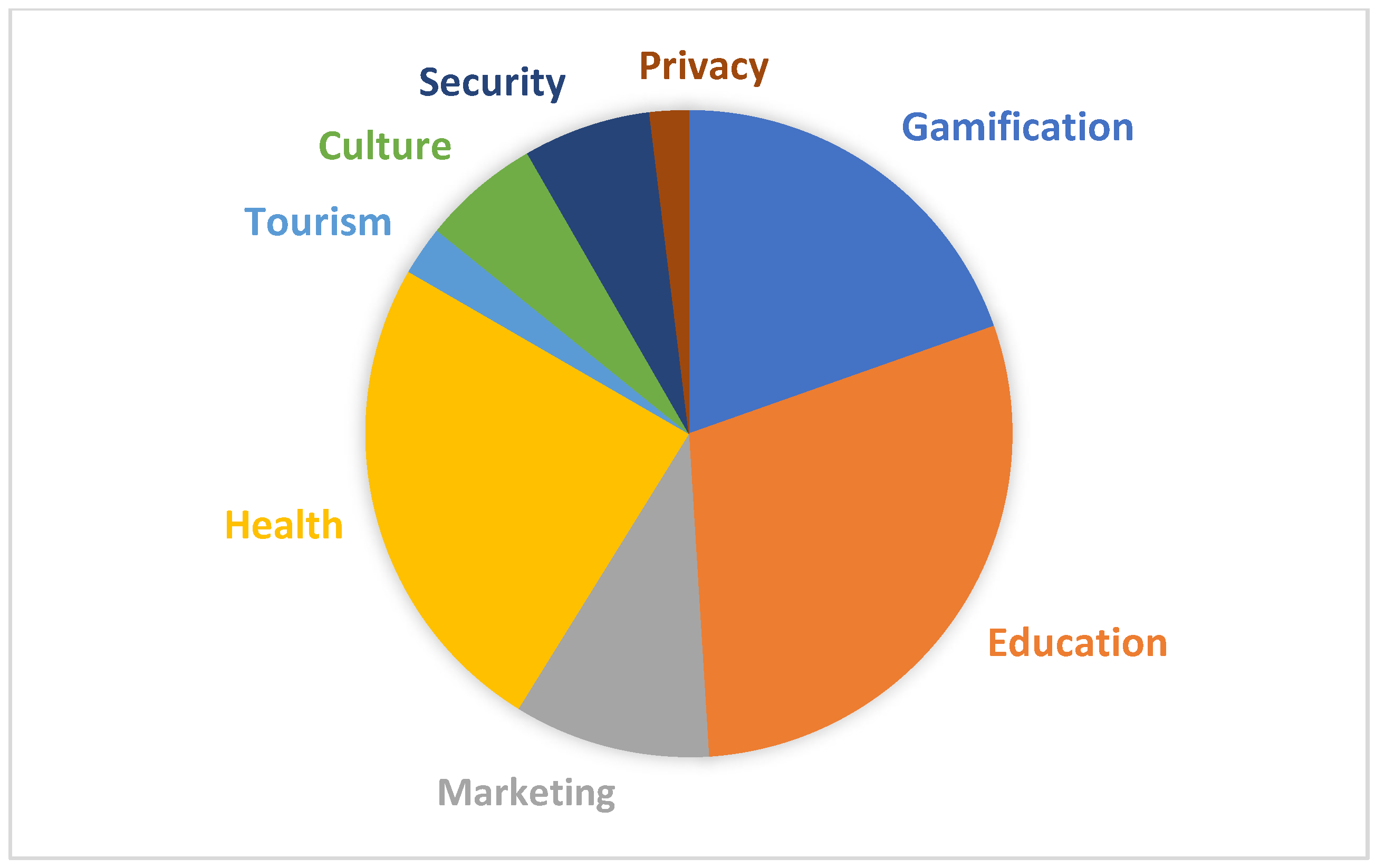
In the first stage, 300 studies were retrieved by the database search process using the terms “Gamification” and “Game elements”. The number was decreased after studying the titles, keywords and abstracts, as many results concerned studies of games and not the method of gamification. In addition, the selection was based on the above-mentioned criteria. As mentioned above, the term “Gamification” was combined with other terms. By combining the terms “Gamification” and “Education” 400 studies were retrieved. Next, 250 studies regarding gamification and health were retrieved and fewer than 100 studies were obtained by a search for gamification and marketing. In addition, 60 studies were retrieved regarding culture and security, while the fewest studies concerned tourism and privacy. According to the titles, keywords and abstracts of all these studies, many of them did not mention gamification or were duplicated, so these studies were not selected. The results of the search process regarding the amount of each search combination are presented in Figure 3. According to this figure most of the figures concerned the method of gamification and its combination with education, marketing and health, while fewer number of studies were retrieved for the tourism, culture, security and privacy sectors.
Figure 3.
Results of search process.
On that note, studies which do not mention game elements were excluded, as the aim was to record the elements used to gamify an application. Studies whose full-text was not accessible were not used, as this fact would complicate the accomplishment of this work. Finally, papers available only in the form of abstracts or PowerPoint presentation were not preferred, due to the fact that they do not present in detail the results and the flow of each research.
5. Conclusions
This study yielded some interesting findings. First, the method of gamification is described, citing details regarding its definition, implementation, principles and benefits. The implementation of gamification in services supports user engagement, and consequently, the use of such services can be increased. The increased use of gamified services means that the protection of users’ information has to be protected. In order to satisfy this purpose, the consideration of users’ privacy protection while designing services is important. Although a variety of implementations of this method in several sectors has been recorded, a gap between gamification and privacy was noticed, which is crucial as the introduction of privacy in services is an important aspect to be considered during system development.
Specifically, the increase of several services raises several risks and concerns regarding the protection of user privacy, as their personal information is recorded, monitored and their identity can be connected with their actions. Due to this fact and the recorded gap, the aim of this research was to identify if gamification impacts privacy. According to the literature in the privacy domain, privacy can be protected by analysing and eliciting specific privacy requirements during system design. Thus, in the second phase of this work the record of privacy requirements was implemented in order to comprehend their concept and role during system development.
As the aforementioned steps have been completed, the development of the conceptual model which represents the relationship between the game elements and the privacy requirements is the main contribution of this work. This approach was based on the fact that both are used during the design of services and include the main principles of gamification and privacy domain, accordingly. Thus, a conceptual model by which software developers will be able to consider privacy during the development of a gamified service and to identify which privacy requirements have to be analysed in connection to each game element, is needed. The elements were examined concerning their impact on privacy requirements and the examination was based on the concept of each element and requirement. According to the results of this approach, the majority of the game elements conflict with privacy requirements and their use may be harmful for users’ privacy. The benefits of the game elements can be at the same time disadvantages for users’ privacy. For example, the recognition of users’ faces may provide an animated character, but users’ characteristics are recorded, so their anonymity is violated. Thus, software developers should consider this fact and the impact of each element, while developing a gamified service in order to ensure that the privacy of users will be protected. Several techniques which provide a gamified environment and in parallel, respect privacy issues should be used. Consequently, the trust between users and gamified applications will be increased, as they will provide an environment which protect users’ information.
Author Contributions
A.-G.M. contributed on the investigation of game elements and writing of original draft. A.K. contributed in the analysis and visualization of the work. C.K. contributed in the conceptualization of the idea as well as in supervision and writing-review and editing and S.G. contributed in the supervision and writing-review and editing of the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Seth, A.; Vance, J.M.; Oliver, J.H. Virtual reality for assembly methods prototyping: A review. Virtual Real. 2011, 15, 5–20. [Google Scholar] [CrossRef]
- Azum, A.R. A Survey of Augmented Reality. Mass. Inst. Technol. 1997, 6, 355–385. [Google Scholar] [CrossRef]
- Hamari, J.; Koivisto, J.; Sarsa, H. Does Gamification Work?—A Literature Review of Empirical Studies on Gamification. In Proceedings of the 2014 47th Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 6–9 January 2014; pp. 3025–3034. [Google Scholar] [CrossRef]
- Mora, A.; Riera, D.; Gonzalez, C.; Arnedo-Moreno, J. A Literature Review of Gamification Design Frameworks. In Proceedings of the 2015 7th International Conference on Games and Virtual Worlds for Serious Applications (VS-Games), Skövde, Sweden, 16–18 September 2015; pp. 1–8. [Google Scholar] [CrossRef]
- Deterding, S.; Dixon, D.; Khaled, R.; Nacke, L. From game design elements to gamefulness: Defining “gamification”. In Proceedings of the 15th International Academic MindTrek Conference: Envisioning Future Media Environments, Tampere, Finland, 28–30 September 2011; p. 7. [Google Scholar]
- Lucassen, G.; Jansen, S. Gamification in Consumer Marketing—Future or Fallacy? Procedia Soc. Behav. Sci. 2014, 148, 194–202. [Google Scholar] [CrossRef]
- Huotari, K.; Hamari, J. Defining gamification: A service marketing perspective. In Proceeding of the 16th International Academic MindTrek Conference (MindTrek ’12), Tampere, Finland, 3–5 October 2012; p. 17. [Google Scholar] [CrossRef]
- Yu-kai Chou: Gamification & Behavioral Design-Healthcare. Available online: https://yukaichou.com/gamification-examples/top-ten-gamification-healthcare-games/ (accessed on 12 December 2018).
- King, D.; Greaves, F.; Exeter, C.; Darzi, A. Gamification: Influencing health behaviours with games. J. R. Soc. Med. 2013, 106, 76–78. [Google Scholar] [CrossRef] [PubMed]
- Cafazzo, J.A.; Casselman, M.; Hamming, N.; Katzman, D.K.; Palmert, M.R. Design of an mHealth App for the Self-management of Adolescent Type 1 Diabetes: A Pilot Study. J. Med. Internet Res. 2012, 14, e70. [Google Scholar] [CrossRef] [PubMed]
- Nevin, C.R.; Westfall, O.A.; Rodriguez, M.J.; Dempsey, D.M.; Cherrington, A.; Roy, B.; Patel, M.; Willig, J.H. Gamification as a tool for enhancing graduate medical education. Postgrad. Med. J. 2014, 90, 685–693. [Google Scholar] [CrossRef] [PubMed]
- Gåsland, M.M. Game Mechanic Based E-Learning—A Case Study. Master’s Thesis, Norwegian University of Science and Technology, Trondheim, Norway, June 2011. [Google Scholar]
- Yu-kai Chou: Gamification & Behavioral Design-Education. Available online: https://yukaichou.com/gamification-examples/top-10-education-gamification-examples/ (accessed on 12 December 2018).
- Huang, W.H.-Y.; Soman, D. A Practitioner’s Guide to Gamification of Education; University of Toronto: Toronto, ON, Canada, December 2013. [Google Scholar]
- Xu, F.; Weber, J.; Buhalis, D. Gamification in Tourism. In Information and Communication Technologies in Tourism 2014; Xiang, Z., Tussyadiah, I., Eds.; Springer International Publishing: Cham, Switzerland, 2013; pp. 525–537. [Google Scholar]
- Mehrbod, A.; Mehrbod, N.; Grilo, A.; Vasconcelos, C.; Silva, J.L. Gamification in supported geocaching tours. In Proceedings of the 2017 International Conference on Engineering, Technology and Innovation (ICE/ITMC), Funchal, Portugal, 27–29 June 2017; pp. 1419–1423. [Google Scholar] [CrossRef]
- Sever, N.S.; Sever, G.N.; Kuhzady, S. The Evaluation of Potentials of Gamification in Tourism Marketing Communication. Int. J. Acad. Res. Bus. Soc. Sci. 2015, 5, 188–202. [Google Scholar] [CrossRef]
- Almaliki, M.; Jiang, N.; Ali, R.; Dalpiaz, F. Gamified Culture-Aware Feedback Acquisition. In Proceedings of the 2014 IEEE/ACM 7th International Conference on Utility and Cloud Computing, London, UK, 8–11 December 2014; pp. 624–625. [Google Scholar] [CrossRef]
- Döpker, A.; Brockmann, T.; Stieglitz, S. Use Cases for Gamification in Virtual Museums. In Proceedings of the 2015 Virtual Reality International Conference, Laval, France, 8–10 April 2015; p. 14. [Google Scholar]
- Heryadi, Y.; Robbany, A.Z.; Sudarma, H. User experience evaluation of virtual reality-based cultural gamification using GameFlow approach. In Proceedings of the 2016 1st International Conference on Game, Game Art, and Gamification (ICGGAG), Jakarta, Indonesia, 19–21 December 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Pedreira, O.; García, F.; Brisaboa, N.; Piattini, M. Gamification in software engineering—A systematic mapping. Inf. Softw. Technol. 2015, 57, 157–168. [Google Scholar] [CrossRef]
- Alhammad, M.M.; Moreno, A.M. Gamification in software engineering education: A systematic mapping. J. Syst. Softw. 2018, 141, 131–150. [Google Scholar] [CrossRef]
- Yonemura, K.; Komura, R.; Sato, J.; Hoga, T.; Takeichi, Y.; Chida, E. Effect of security education using KIPS and gamification theory at KOSEN. In Proceedings of the 2018 IEEE Symposium on Computer Applications & Industrial Electronics (ISCAIE), Penang, Malaysia, 28–29 April 2018; pp. 255–258. [Google Scholar] [CrossRef]
- Yonemura, K.; Yajima, K.; Komura, R.; Sato, J.; Takeichi, Y. Practical security education on operational technology using gamification method. In Proceedings of the 2017 7th IEEE International Conference on Control System, Computing and Engineering (ICCSCE), Penang, Malaysia, 24–26 November 2017; pp. 284–288. [Google Scholar] [CrossRef]
- Yonemura, K.; Sato, J.; Takeichi, Y.; Komura, R.; Yajima, K. Security Education Using Gamification Theory. In Proceedings of the 2018 International Conference on Engineering, Applied Sciences, and Technology (ICEAST), Phuket, Thailand, 4–7 July 2018; pp. 1–4. [Google Scholar] [CrossRef]
- He, Q.; Ant, A.I. A Framework for Modeling Privacy Requirements in Role Engineering. In Proceedings of the 2003 Requirements Engineering: Foundation for Software Quality (REFSQ) Workshop, Klagenfurt/Velden, Austria, 16–17 June 2003; pp. 137–146. [Google Scholar]
- Miyazaki, S.; Mead, N.; Zhan, J. Computer-Aided Privacy Requirements Elicitation Technique. In Proceedings of the 2008 IEEE Asia-Pacific Services Computing Conference, Yilan, Taiwan, 9–12 December 2008; pp. 367–372. [Google Scholar] [CrossRef]
- Rottondi, C.; Verticale, G. Enabling privacy in a gaming framework for smart electricity and water grids. In Proceedings of the 2016 International Workshop on Cyber-physical Systems for Smart Water Networks (CySWater), Vienna, Austria, 11 April 2016; pp. 25–30. [Google Scholar] [CrossRef]
- Shahri, A.; Hosseini, M.; Phalp, K.; Taylor, J.; Ali, R. Towards a Code of Ethics for Gamification at Enterprise. In The Practice of Enterprise Modeling; Frank, U., Loucopoulos, P., Pastor, Ó., Petrounias, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 197, pp. 235–245. [Google Scholar]
- Herzig, P.; Ameling, M.; Schill, A. A Generic Platform for Enterprise Gamification. In Proceedings of the 2012 Joint Working IEEE/IFIP Conference on Software Architecture and European Conference on Software Architecture, Helsinki, Finland, 20–24 August 2012; pp. 219–223. [Google Scholar] [CrossRef]
- Thiebes, S.; Lins, S.; Basten, D. Gamifying Information Systems—A Synthesis of Gamification Mechanics and Dynamics. In Proceedings of the 2014 Conference on European Conference on Information Systems, Helsinki, Finland, 9–11 June 2014. [Google Scholar]
- Helf, C.; Zwickl, P.; Hlavacs, H.; Reichl, P. mHealth Stakeholder Integration: A gamification-based Framework-approach towards behavioural change. In Proceedings of the 13th International Conference on Advances in Mobile Computing and Multimedia (MoMM 2015), Brussels, Belgium, 11–13 December 2015; pp. 268–274. [Google Scholar] [CrossRef]
- Stanculescu, L.C.; Bozzon, A.; Sips, R.-J.; Houben, G. Work and Play: An Experiment in Enterprise Gamification. In Proceedings of the 19th ACM Conference on Computer-Supported Cooperative Work & Social Computing (CSCW ’16), San Francisco, CA, USA, 27 February–2 March 2016; pp. 345–357. [Google Scholar] [CrossRef]
- De Sá, M.; Shamma, D.A.; Churchill, E.F. Live mobile collaboration for video production: Design, guidelines, and requirements. Pers. Ubiquitous Comput. 2014, 18, 693–707. [Google Scholar] [CrossRef]
- Crowley, D.N.; Breslin, J.G.; Corcoran, P.; Young, K. Gamification of citizen sensing through mobile social reporting. In Proceedings of the 2012 IEEE International Games Innovation Conference, Rochester, NY, USA, 7–9 September 2012; pp. 1–5. [Google Scholar] [CrossRef]
- Scherr, S.A.; Elberzhager, F.; Holl, K. Acceptance testing of mobile applications: Automated emotion tracking for large user groups. In Proceedings of the 5th International Conference on Mobile Software Engineering and Systems (MOBILESoft ’18), Gothenburg, Sweden, 27–28 May 2018; pp. 247–251. [Google Scholar] [CrossRef]
- Thiel, S.-K. A Review of Introducing Game Elements to e-Participation. In Proceedings of the 2016 Conference for E-Democracy and Open Government (CeDEM), Krems, Austria, 18–20 May 2016; pp. 3–9. [Google Scholar]
- Pattakou, A.; Mavroeidi, A.-G.; Diamantopoulou, V.; Kalloniatis, C.; Gritzalis, S. Towards the Design of Usable Privacy by Design Methodologies. In Proceedings of the 2018 IEEE 5th International Workshop on Evolving Security & Privacy Requirements Engineering (ESPRE), Banff, AB, Canada, 20–21 August 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Pattakou, A.; Kalloniatis, C.; Gritzalis, S. Security and Privacy Requirements Engineering Methods for Traditional and Cloud-Based Systems: A Review. In Proceedings of the Eighth International Conference on Cloud Computing, GRIDs and Virtualization, Athens, Greece, 19–23 February 2017. [Google Scholar]
- Islam, S.; Mouratidis, H.; Kalloniatis, C.; Hudic, A.; Zechner, L. Model Based Process to Support Security and Privacy Requirements Engineering. Int. J. Secur. Softw. Eng. 2012, 3, 1–22. [Google Scholar] [CrossRef]
- Liu, L.; Yu, E.; Mylopoulos, J. Security and privacy requirements analysis within a social setting. In Proceedings of the 11th IEEE International Requirements Engineering Conference, Monterey Bay, CA, USA, 12 September 2003; pp. 151–161. [Google Scholar] [CrossRef]
- Jensen, C.; Tullio, J.; Potts, C.; Mynatt, E.D. STRAP: A Structured Analysis Framework for Privacy; Georgia Institute of Technology: Atlanta, GA, USA, 2005. [Google Scholar]
- Deng, M.; Wuyts, K.; Scandariato, R.; Preneel, B.; Joosen, W. A privacy threat analysis framework: Supporting the elicitation and fulfillment of privacy requirements. Requir. Eng. 2011, 16, 3–32. [Google Scholar] [CrossRef]
- Kalloniatis, C.; Belsis, P.; Gritzalis, S. A soft computing approach for privacy requirements engineering: The PriS framework. Appl. Soft Comput. 2011, 11, 4341–4348. [Google Scholar] [CrossRef]
- De Paz, B.M. Gamification: A Tool to Improve Sustainability Efforts. Ph.D. Thesis, University of Manchester, Manchester, UK, 2013. [Google Scholar]
- Seaborn, K.; Fels, D.I. Gamification in theory and action: A survey. Int. J. Hum. Comput. Stud. 2015, 74, 14–31. [Google Scholar] [CrossRef]
- Yu-kai Chou: Gamification & Behavioral Design-Marketing. Available online: http://yukaichou.com/gamification-examples/top-10-marketing-gamification-cases-remember/ (accessed on 12 December 2018).
- Werbach, K.; Hunter, D. For the Win: How Game Thinking Can Revolutionize Your Business; Wharton Digital Press: Philadelphia, PA, USA, 2012. [Google Scholar]
- Morford, Z.H.; Witts, B.N.; Killingsworth, K.J.; Alavosius, M.P. Gamification: The Intersection between Behavior Analysis and Game Design Technologies. Behav. Anal. 2014, 37, 25–40. [Google Scholar] [CrossRef] [PubMed]
- Morschheuser, B.; Hassan, L.; Werder, K.; Hamari, J. How to design gamification? A method for engineering gamified software. Inf. Softw. Technol. 2018, 95, 219–237. [Google Scholar] [CrossRef]
- Ahtinen, A.; Mattila, E.; Välkkynen, P.; Kaipainen, K.; Vanhala, T.; Ermes, M.; Sairanen, E.; Myllymäki, T.; Lappalainen, R. Mobile Mental Wellness Training for Stress Management: Feasibility and Design Implications Based on a One-Month Field Stud. JMIR mHealth uHealth 2013, 1, e11. [Google Scholar] [CrossRef] [PubMed]
- Bista, S.K.; Nepal, S.; Paris, C. Engagement and Cooperation in Social Networks: Do Benefits and Rewards Help? In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; pp. 1405–1410. [Google Scholar] [CrossRef]
- Chen, Y.; Pu, P. HealthyTogether: Exploring social incentives for mobile fitness applications. In Proceedings of the Second International Symposium of Chinese CHI (Chinese CHI ’14), Toronto, ON, Canada, 26–27 April 2014; pp. 25–34. [Google Scholar] [CrossRef]
- Amo, L.; Liao, C.R.; Rao, H.R.; Walker, G. Effects of Leaderboards in Games on Consumer Engagement. In Proceedings of the 2018 ACM SIGMIS Conference on Computers and People Research (SIGMIS-CPR’18), Buffalo-Niagara Falls, NY, USA, 18–20 June 2018; pp. 58–59. [Google Scholar] [CrossRef]
- Cheong, C.; Cheong, F.; Filippou, J. Quick Quiz: A Gamified Approach for Enhancing Learning. In Proceedings of the Pacific Asia Conference on Information Systems (PACIS 2013), Jeju Island, Korea, 18–22 June 2013; pp. 1–14. [Google Scholar]
- Cramer, H.; Rost, M.; Holmquist, L.E. Performing a check-in: Emerging practices, norms and “conflicts” in location-sharing using foursquare. In Proceedings of the 13th International Conference on Human Computer Interaction with Mobile Devices and Services (MobileHCI ’11), Stockholm, Sweden, 30 August–2 September 2011; p. 57. [Google Scholar] [CrossRef]
- Denny, P. The effect of virtual achievements on student engagement. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI ’13), Paris, France, 27 April–2 May 2013; p. 763. [Google Scholar] [CrossRef]
- McDaniel, R.; Lindgren, R.; Friskics, J. Using badges for shaping interactions in online learning environments. In Proceedings of the 2012 IEEE International Professional Communication Conference, Orlando, FL, USA, 8–10 October 2012; pp. 1–4. [Google Scholar] [CrossRef]
- Kitchenham, B.A.; Budgen, D.; Pearl Brereton, O. Using mapping studies as the basis for further research—A participant-observer case study. Inf. Softw. Technol. 2011, 53, 638–651. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).