Cyber Security Threat Modeling for Supply Chain Organizational Environments
Abstract
:1. Introduction
2. Related Work
2.1. CSC Security Environment
2.2. Threat Modeling
3. Threat Modeling for Supply Chain Contexts
3.1. The Need for Cyber Supply Chain Threat Modeling
- Evolution of the cyber supply chain threat landscape;
- Integration of supply chain stakeholders on the cyber threat model;
- Inability to determine cascading threat impacts on inbound and outbound supply chains;
- Evolving threat landscapes affecting the supply chain organisation context
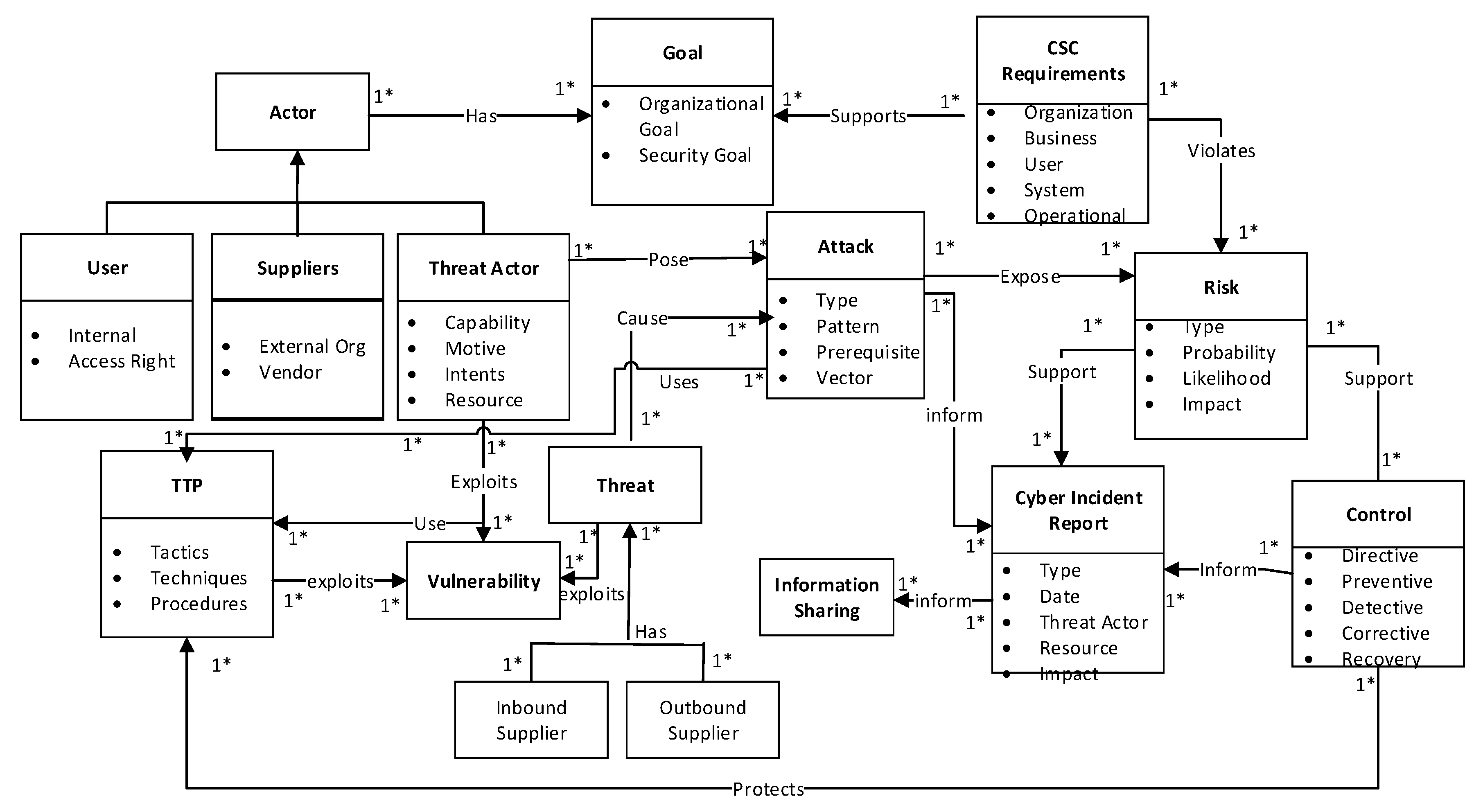
3.2. Conceptual View
- Tactics describe how threat actors operate during the various attack campaigns. This includes how the adversary carries out reconnaissance for initial intelligence gathering, how the information is gathered, and how the initial compromises were conducted. For instance, tactics may be to send a spear phishing email to a group on the supply chain.
- Techniques are the strategies used by the adversary to facilitate the initial compromises such as tools, skills, and capabilities deployed. This includes how the adversary establishes control, maneuvers within the supply chain system infrastructures, and exfiltrates data, as well as how to obfuscate through the system. The adversary conceals the email contents in such a way that is not obvious to detect.
- Procedures are the set of tactics and techniques put together to perform an attack. Procedures may vary depending on the threat actor goal, purpose, and nature of the attack. A procedure includes carrying out reconnaissance on the victim’s systems to identify vulnerable spots, gather information, access rights, and control mechanisms to determine what could be exploited.
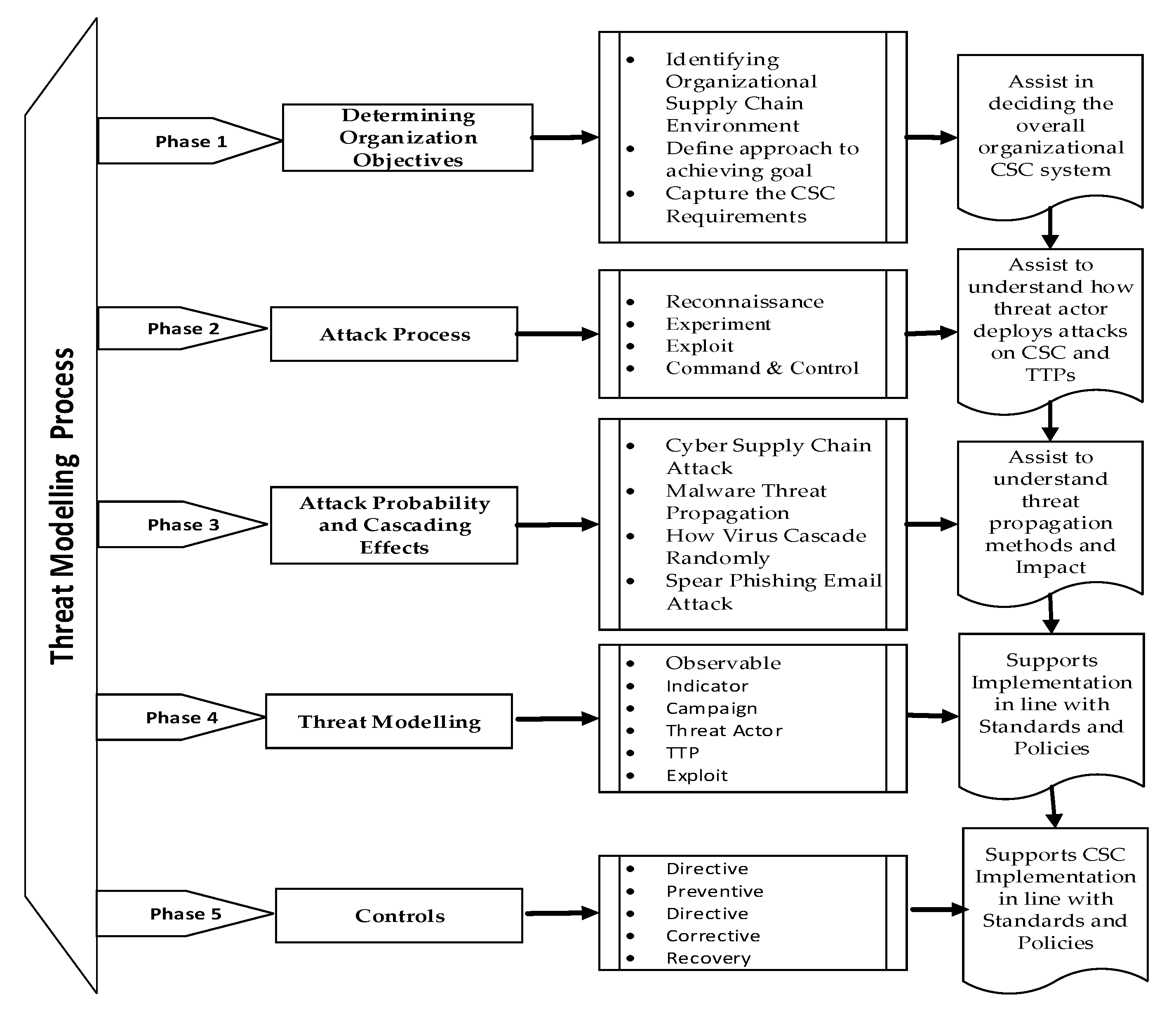
3.3. Threat Modeling Process
- Activity 1: Identifying the organizational supply chain environmentThis activity identifies CSC systems and the external organization, suppliers, distributors, and third party vendors on the inbound and outbound supply chains. The purpose is to identify the vendor’s software, hardware, and network design process and policies. This informs strategic management whether the organizational goals are achievable, repeatable, and measurable.
- Activity 2. Define the approach to achieving the goalThis activity identifies necessary actions required to achieve the organizational goals. The organizational goal is to provide safe and reliable service to consumers, while the security goal is to ensure that the supply chain system is secure, reliable, for the overall to achieve business continuity and information assurance.
- Activity 3. Capture the CSC requirementsThis activity involves capturing the overall CSC requirement on the inbound and outbound supply chains to ensure the security goal and constraints. The requirements ensure proper integration and interfacing with vendors. Here, the systems development life cycle (SDLC) concepts are used to capture the requirements.
- What infrastructure is the organization using: topology, IPs, software, or configurations;
- Profile of the organization, business applications, third party vendors, and other organizations;
- Is the supply chain a corporate and public network system (e.g., virtual private network VPN);
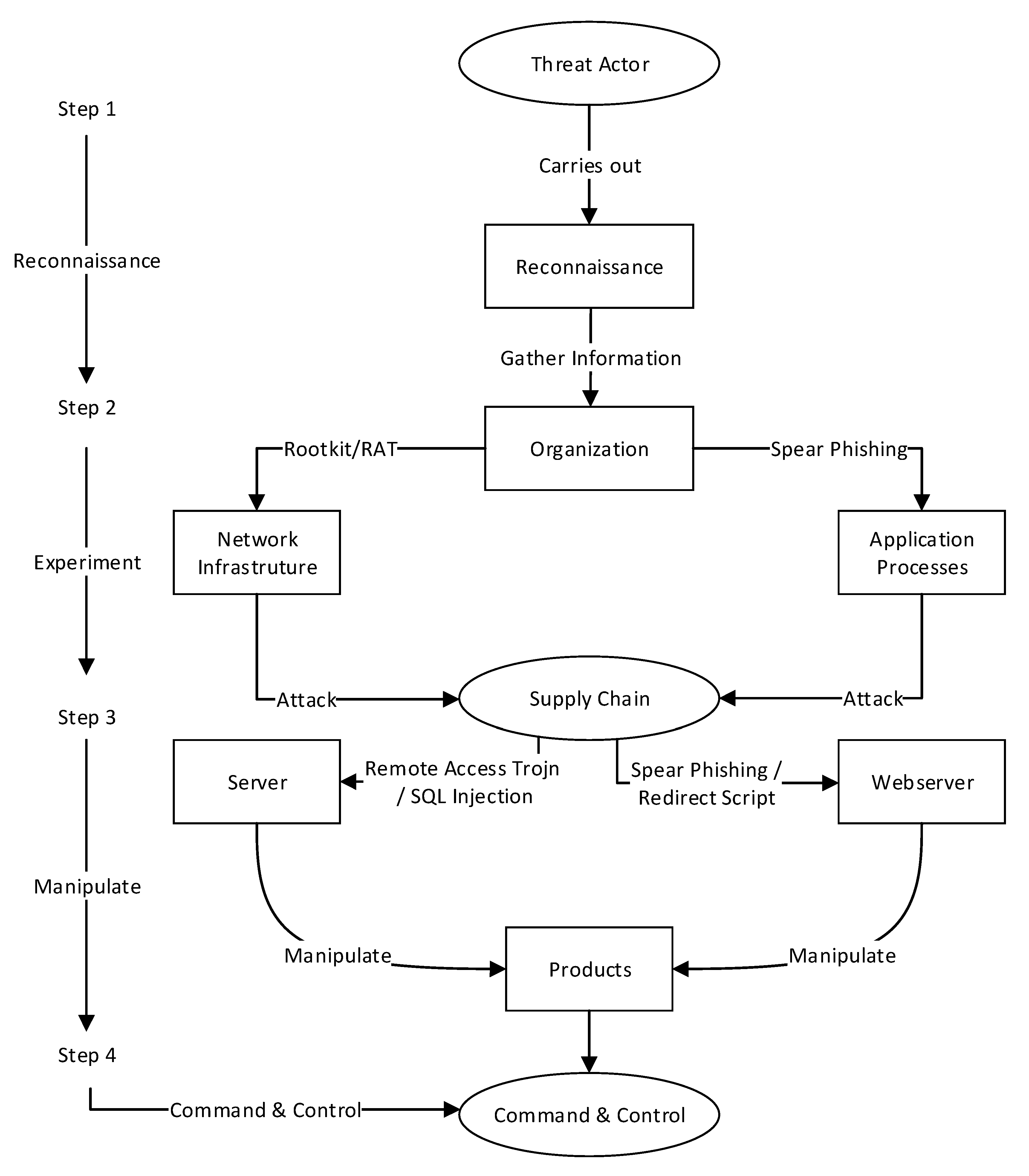
- What type of attack can be initiated (e.g., malware, redirect script, injection, and phishing)? For instance, the adversary could use passive attack tools such as Nmap or Kali Linux.
- The adversary creates an executable malware remotely;
- The adversary inserts a remote access Trojan (RAT), and the malware is installed and executed when a user downloads or opens it through a spear phishing email.
- Penetration: We assumed that the threat actor could penetrate the vulnerable spots on the inbound and outbound chain in all the scenarios.
- Manipulation: This stage is where the threat actor gains access into the supply chain system and can manipulate data. Threat actor motives and intents were determined by the manipulation.
- Severity of attack: The severity of an attack is determined by the extent to which a threat has propagated to the supply chain system. The severity of the attack and the cascading effect are used to determine the the required controls to mitigate the attacks. We categorized the attacks as low, medium, or high in all the scenarios we considered, as there were penetrations available to the threat actor that corresponded to the level of propagation on the targeted supply chain system.
| Algorithm 1 Cascading Effect Algorithm |
| Input: Propagation Attack Scenarios Output: Penetration Effects Initialization
|
| Pseudocode |
Start,
|
- Directive controls are more strategic, where risks are identified and assigned to specific inbound and outbound supply chain requirements.
- Preventive controls are policies implemented on associated risk probabilities that are intended to preclude actions violating policy or increasing third party risk. This includes supply chain risk assessments and audits.
- Detective controls use attack indicators to identify practices, processes, and tools that identify and possibly react to security violations. These include firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS) configurations.
- Corrective controls involve measures such as courses of actions and CSC risk management designed to react to detections of an incident in order to reduce or eliminate the opportunity for the unwanted event to recur.
- Recovery controls are mechanisms put in place to restore a system to its original state once an incident has occurred and resulted in compromising integrity or availability. These include countermeasures, backups, segmentation, and incidence response strategy.
4. Evaluation
4.1. Data Gathering
4.2. Running Example of a Case Study
4.3. Smart Grid Electric Power Infrastructure
4.3.1. Application Infrastructures and Core Business Systems
4.3.2. Electric Power Distribution Challenges
4.3.3. The ECG Supply Chain Organizational Environment
4.4. Study Goal
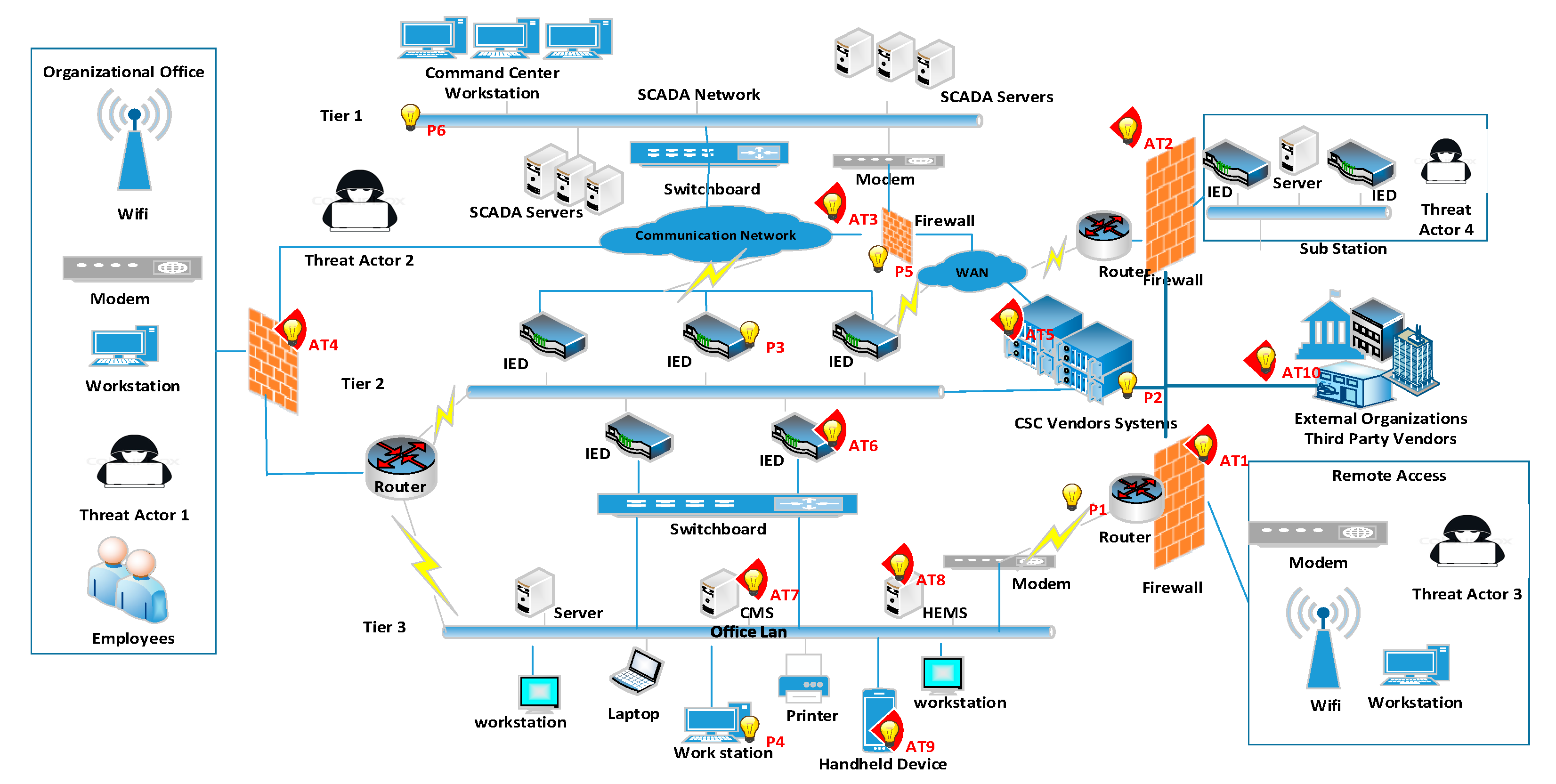
4.5. The Process
- Tier 1: smart grid integrates with SCADA system servers and uses a switchboard to establish WAN communication with the IED units.
- Tier 2: uses IEDs to connect with AMI and demand response applications.
- Tier 3: uses LAN to integrate with the CMS and uses the IED to communicate.
- Penetration (P) to represent how the adversary attacks the system (P1–P6);
- Attack (AT) to represent the devices that were under attack (AT1–AT10);
- Steps (ST) to represent the steps the threat actor followed to attack (ST1–ST4).
- P1. Threat actor penetrates the system from a remote source through the firewall refer Step 1.
- P2. Threat actor gains remote access through Vendor Systems refer Step 2.
- P3. Threat actor exploits the IED that supports the communication systems refer Step 3.
- P4. Threat actor manipulates the workstations, server, and handheld devices refer Step 4.
- P5. Threat actor penetrates the command center firewall refer Step 4.
- P6. Threat actor gains access into the command center and takes controls of the SCADA servers, manipulating, exfiltrating, and obfuscating.
- AT1. The internal threat actor uses social engineering, ID theft, and administrative privileges to gain access through the LAN firewall to manipulate the system refer Step 4.
- AT1–AT4. Indicates that the firewall devices affected are under cyber attack.
- AT5. CSC vendor systems are under attack.
- AT6. IEDs are under attacks.
- AT7. CMS server is under attack.
- (HEMS) server is under attack.
- AT9. Handheld devices are under attack.
- A10. Vendor devices are under attack.
Bayesian Probability Theorem
- Penetration manipulation (160) and cascading (210);
- No cascading manipulation (236) and cascading (523).
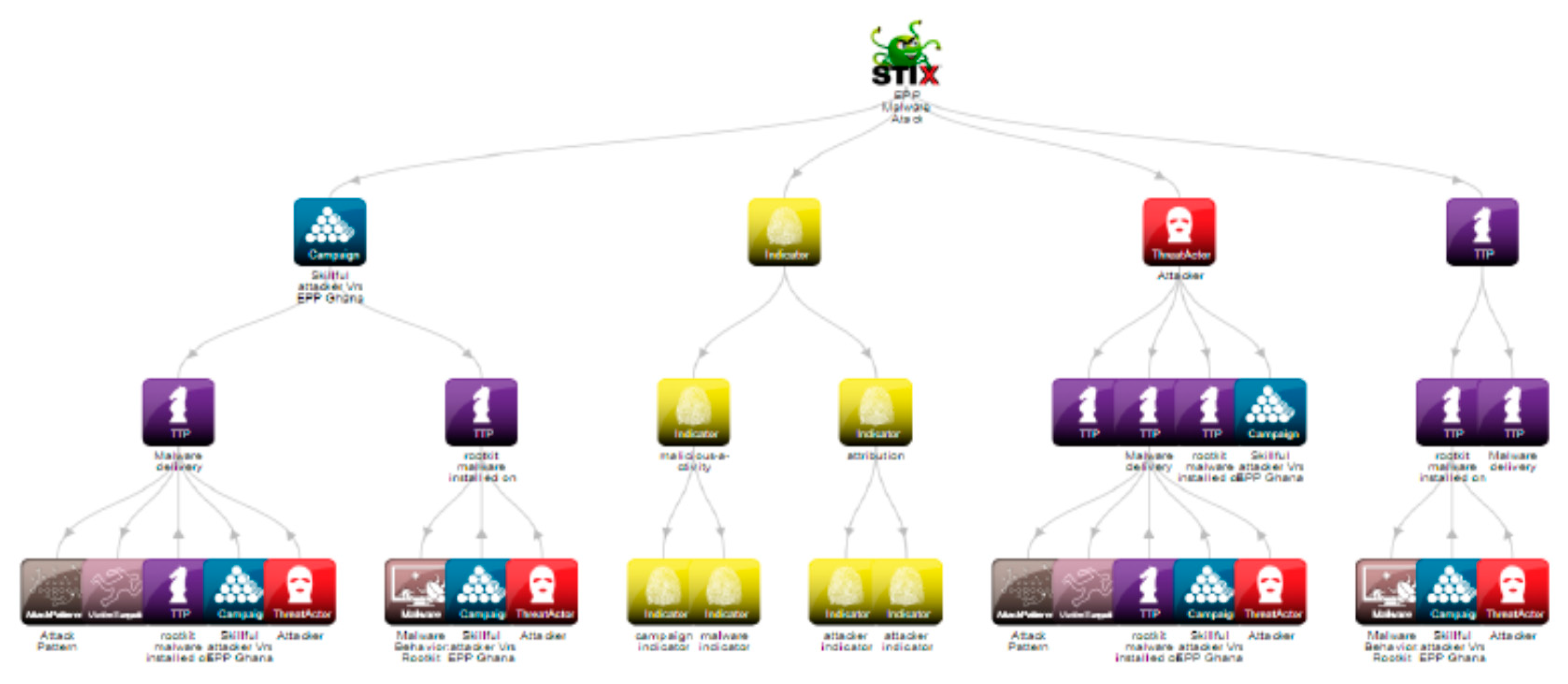
4.6. Modeling Attack using STIXviz Tool
4.7. Cyber Supply Chain Controls
5. Discussions
5.1. Threat Actor Motivation and Intent
5.2. Attack on the Cyber Physical Components
5.3. Threat Modeling and Analyses
- What attacks have occurred before (malware, SQL injection, session hijacking, XSS);
- How did they occur (causes of action and intrusion sets);
- Who are the threat actors (internal and external staff, adversaries, and threat actors);
- What are the likely occurrences (risk assessments, indicators);
- How can they be detected (penetration tests, vulnerability assessments, threat modeling);
- How can they be recognized (threat intelligence models);
- How can they be mitigated (risk management, controls, policies, regular updates, insurance, and awareness).
5.4. STIX Model
5.5. Comparing Results with Other Works
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Boyens, J.; Pauslen, C.; Moorthy, R.; Bartol, N. Supply Chain Risk Management Practices for Federal Information Systems and Organizations. NIST Comput. Sec. 2015, 800, 1. [Google Scholar] [CrossRef]
- Yu, E. Modeling Strategic Relationship for Process Reengineering. Ph.D. Thesis, Department of Computer Science, University of Toronto, Toronto, ON, Canada, 1995. [Google Scholar]
- Humayed, A.; Lin, J.; Li, F.; Luo, Bo. Cyber-Physical Systems Security—A Survey. Available online: http://ieeexplore.ieee.org/document/7924372/ (accessed on 10 October 2018).
- Woods, B.; Bochman, A. Supply Chain in the Software Era; Atlantic Council: Washington, DC, USA, 2018. [Google Scholar]
- Zetter, K. Inside the Cunning, Unprecedented Hack of Ukraine’s Power Grid. Available online: https://www.wired.com/2016/03/inside-cunning-unprecedented-hackukraines-power-grid/ (accessed on 18 September 2018).
- MITRE. Threat Based Defense. Understanding an Attackers Tactics and Techniques Is Key to Successful Cyber Defense. Available online: https://www.mitre.org/capabilities/cybersecurity/threat-based-defense (accessed on 10 October 2018).
- Phillips, C.; Swiler, L.P. A Graph-based System for Network-vulnerability Analysis. In Proceedings of the 1998 Workshop on New Security Paradigms, Charlottesville, VA, USA, 22–26 September 1998; Association for Computing Machinery (ACM): New York, NY, USA, 1998. [Google Scholar]
- BSIMM. Attack Models with BSIMM Framework. Available online: https://www.bsimm.com/framework/intelligence/attack-models/ (accessed on 20 September 2016).
- CIS Controls. Basic Organizational Foundational; Ver. 7; Center for Internet Security: East Green Bush, NY, USA, 2018. [Google Scholar]
- STIX: Assets Affected in an Incident. Available online: http://stixproject.github.io/documentation/idioms/affected-assets/ (accessed on 5 May 2018).
- Idaho National Laboratories. Cyber Threat and Vulnerability Analysis of the U.S. Electric Sector. Mission Support Centre Analysis. 2016. Available online: https://energy.gov/epsa/downloads/cyber-threat-and-vulnerability-analysis-us-electric-sector (accessed on 25 Febuary 2019).
- Common Weakness Enumeration (CWE). Common Weakness Enumeration. Supply Chain Risk Management and Due Diligence. Available online: https://cwe.mitre.org/data/index.html (accessed on 10 October 2018).
- Wang, W.; Lu, Z. Cyber Security in Smart Grid: Survey and Challenges. 2012. Available online: https://research.ece.ncsu.edu/netwis/papers/12WL-COMNET.pdf (accessed on 15 November 2013).
- Sun, C.; Hahn, A.; Liu, C. Cyber Security of a Power Grid: State of the Art. Electr. Power Energy Syst. 2018, 99, 45–56. [Google Scholar] [CrossRef]
- CAPEC-437: Supply Chain. Common Attack Pattern Enumeration and Classification: Domain of Attack. Available online: https://capec.mitre.org/data/definitions/437.html MITRE (accessed on 10 October 2018).
- Open Web Application Security Project (OWASP). The Ten Most Critical Application Security Risks. Creative Commons Attribution-Share Alike 4.0 International License. 2017. Available online: https://owasp.org (accessed on 10 September 2018).
- Kure, H.I.; Islam, S.; Razzaque, M.A. An Integrated Cyber Security Risk Management Approach for a Cyber-Physical System. Appl. Sci. 2018, 8, 898. [Google Scholar] [CrossRef]
- Caltagirone, S.; Pendergast, A.; Christopher, B. The Diamond Model of Intrusion Analysis; Center for Cyber Intelligence Analysis and Threat Research Hanover Md.: 2013. Available online: http://www.activeresponse.org/wp-content/uploads/2013/07/diamond.pdf (accessed on 20 September 2018).
- Gai, K.; Qiu, M.; Ming, Z.; Zhao, H.; Qiu, L. Spoofing-Jamming Attack Strategy Using Optimal Power Distributions in Wireless Smart Grid Networks. IEEE Trans. Smart Grid 2017, 8, 2431–2439. [Google Scholar] [CrossRef]
- Gai, K.; Qui, M. Blend Arithmetic Operations on Tensor-Based Fully Homomorphic Encryption Over Real Numbers. IEEE Trans. Ind. Inf. 2018, 14, 3590–3598. [Google Scholar] [CrossRef]
- Gai, K.; Choo, K.R.; Qiu, M.; Zhu, L. Privacy-Preserving Content-Oriented Wireless Communication in Internet-of-Things. IEEE Internet Things J. 2018, 5, 3059–3067. [Google Scholar] [CrossRef]
- Schneier, B. Attacks Trees. Dr. Dodds J. 1999, 24, 21–29. [Google Scholar]
- Mouratidis, H.; Kalloniatis, C.; Islam, S.; Huget, M.; Gritzalis, S. Aligning Security and Privacy to Support the Development of Secure Information Systems. J. UCS 2012, 18, 1608–1672. [Google Scholar]
- US-Cert. Building Security in Software & Supply Chain Assurance. Available online: https://www.us-cert.gov/bsi/articles/knowledge/attack-patterns (accessed on 20 September 2018).
- Conway, E.; Luu, N.; Shaffer, E. Best Practices in Cyber Supply Chain Risk Management; Cisco: San Jose, CA, USA, 2017; Available online: https://www.cisco.com/c/dam/en_us/about/doing_business/trust-center/docs/cyber-supply-chain-risk-management.pdf (accessed on 20 September 2018).
- Boyens, J. Integrating Cybersecurity into Supply Chain Risk Management; RSA; Moscone Center: San Francisco, CA, USA, 2016. [Google Scholar]
- Wallace, M. Mitigating Cyber Risks in IT Supply Chain; The Global Business Law Review; 2016. Cleveland-Marshal College of Law. Library. Cleveland State University. Available online: https://engagedscholarship.csuohio.edu/gblr/vol6/iss1/2 (accessed on 10 September 2018).
- Brown, D.A. Best Practices in Cyber Supply Chain Risk Management; Intel; 2017. Available online: https://www.nist.gov/document-18221. (accessed on 20 October 2018).
- NIST SP 800-53, Rev. 3, Recommended Security Controls for Federal Information Systems. 2017. Available online: https://csrc.nist.gov/CSRC/media/Publications/sp/800-53/rev-5/draft/documents/sp800-53r5-draft-controls-markup.pdf (accessed on 17 September 2018).
- NIST 800-150. Guide to Cyber Threat Information Sharing. Available online: http://dx.doi.org/10.6028/NIST.SP.800-150. (accessed on 11 October 2018).
- Barnum, S. Standardizing Cyber Threat Intelligence Information with the Structured Threat Information eXpression (STIX); V1.1, Revision 1; 2014. Available online: https://www.mitre.org/sites/default/files/publications/stix.pdf (accessed on 11 October 2018).
- Mell, P.; Scarfone, K.; Romanosky, S. A Complete Guide to the Common Vulnerability Scoring System; Ver. 2.0; 2007. Available online: https://ws680.nist.gov/publication/get_pdf.cfm?pub_id=51198. (accessed on 11 October 2018).
- Brewer, R. Your PhD Thesis: How to Plan, Draft, Revise and Edit Your Thesis; Studymates Limited: Abergele, UK, 2017; ISBN 978-1-84285-079-1. [Google Scholar]
- Electricity Company of Ghana. ECG. Available online: http://ecgonline.info/ (accessed on 10 September 2018).
- IEC Standard. IEC 61850: Communication Networks and Systems in Substations; IEC: Geneva, Switzerland, 2004. [Google Scholar]
- National Institute of Standards and Technology (NIST). Framework and Road Map for Smart Grid Interoperability Standards; Release 3.0; NIST: Gaithersburg, MD, USA, 2014.
| Network Infrastructure | Application Systems | People/User | Controls |
|---|---|---|---|
| Smart Grid Architecture | Content Management System/CRM | Staff | Security/Audit |
| Mesh Topology | HEMS | Suppliers | Best Practices & Guidelines |
| SCADA Systems | Mobile Devices/Advanced Metering Integration | Vendors | ISO 27001-2 ISMS |
| UHF Radio | Prepaid | Distributors | |
| Sub Station | Postpaid System | Policies |
| Concepts | Properties | Descriptions |
|---|---|---|
| Goal | Organizational goal | Distribute electric power to customers |
| Generate utility bills, | ||
| Receive payments | ||
| Provide vendors remote access to CSC Secure systems | ||
| Security goal | ||
| Actors | Users | Employees: internal and external |
| Suppliers | Suppliers | |
| Distributors | ||
| Threat actor | A person, user account, or processes that can be identified by the intent, motives, and capabilities of an attacker | |
| Requirements | Organizational requirement, | Specify high level organizational environment overall and integrate with the security constraints to achieve the organizational goal |
| user categories, ID, stakeholders, description, acceptance criteria | ||
| Supply Chain System | Inbound | Organizations |
| Financial institutions | ||
| Third party vendors | ||
| Individual consumers | ||
| Services providers | ||
| Outbound | ||
| Organizations | ||
| Stakeholders | ||
| Power transmission company | ||
| Sub-stations | ||
| Vulnerability | Router, firewall, wifi Remote services: remote login, remote command execution | CSC Source and destination, Timestamp, |
| Dynamic, host configuration protocol, (DHCP) server logs | Domain name, | |
| TCP/UDP port number, media, | ||
| MAC address | ||
| IP Address | ||
| Attack | Attack goal | Compromise system of: |
| Attack pattern | Malware, spyware, injection | |
| Attack prerequisites | Information on vulnerabilities | |
| Attack vectors | Mechanisms to deploy attack | |
| TTPs | Tactic, Technique, & Procedure | |
| Threat | Indicators | Determines vulnerabilities, flaws, and loopholes that can be exploited by a threat actor or a threat agent |
| Specific observable patterns | ||
| SCS threat activities | ||
| Adversary behaviors | ||
| Risky events | ||
| State of an incident |
| Attack Vector Type | CSC System Target | Position | Steps | |
|---|---|---|---|---|
| Penetrating | External | CSC WAN/firewall | P1 | ST1 |
| CSC vendor remote access | P2 | ST2 | ||
| IED-supported communication | P3 | ST3 | ||
| Workstation, CMS, HEMS | P4 | ST4 | ||
| Command center firewall | P5 | ST4 | ||
| Internal | Organizational LAN firewall | AT4 | ||
| Command center SCADA | P6 | ST4 | ||
| Attacking | Devices under cyber attack | Firewall | AT1–AT4 | |
| CSC vendors | AT5 | |||
| IEDs | AT6 | |||
| CMS | AT7 | |||
| HEMS | AT8 | |||
| Handheld devices | AT9 | |||
| Vendor devices | AT 10 | |||
| Scenario | Vulnerable Spots | Penetration | Manipulation% | Probability | Threat Indicators |
|---|---|---|---|---|---|
| 1 | Firewall | Y | 70 | High | Wrong Firewall |
| 2 | IDS/IPS | Y | 60 | High | Configuration |
| 3 | Vendor | Y | 80 | High | Audit |
| 4 | Network | Y | 40 | Medium | Sub-netting |
| 5 | IP | Y | 55 | Medium | Segmentation |
| 6 | Database | Y | 75 | High | Sanitizations |
| 7 | Software | Y | 75 | High | Reprogram |
| 8 | Website | Y | 90 | High | SSL/TLS |
| No | Control | Principle | Critical | Security Purpose | Implement | Activity |
|---|---|---|---|---|---|---|
| 1 | Inventory and Control of Hardware Assets | Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access. | Network, laptops, (BYOD) might be out of synch with security updates or might already be compromised. | Attackers can take advantage of hardware installed but not configured and patched with security updates until later. | Utilize active discovery tool to identify devices connected to network and update the hardware asset inventory. | Maintain up-to-date inventory of stored assets or process information and hardware, whether connected to network or not. |
| 2 | Inventory and Control of Software Assets | Manage CSC network so that only authorized software is installed. Unauthorized software is found and prevented from installation or execution. | Attackers scan targets sites with vulnerable software that can be remotely exploited and distribute hostile web pages or to third-party sites. | Managing and control of all software plays a critical role in planning, backup, incident response, and recovery. | Utilize inventory tools throughout to automate the documentation of all software on business systems. | Utilize application whitelisting technology on all assets to ensure that only authorized software executes. |
| 3 | Continuous Vulnerability Management | Continuously assess and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attacks. | Understanding and managing vulnerabilities must become a continuous activity, requiring significant time, attention, and resources. | Threat actors try to exploit vulnerabilities and attack victim’s systems before the organization becomes aware. Due to lack of CSC risk assessment. | Organizations that do not scan for vulnerabilities and proactively address discovered flaws face a significant likelihood of having their computer systems compromised. | Utilize an up-to-date compliant vulnerability scanning tool to automatically scan all systems to identify potential vulnerabilities, Deploy automated security updates. |
| 4 | Controlled use of Admin Privileges | Not changing hard-coded password default. Impacts on the processes and tools used to track, control, and prevent the correct use, assignment, and configuration of administrative privileges. | Misuse of admin privileges is a primary method for attacks to spread inside a target system. | A privileged user can open a malicious email attachment or website hosting exploited browsers. Second guessing password for an administrative user. | Change default hard-coded password. Ensure all users with administrative account access use a dedicated or secondary account for elevated activities. | Configure systems to issue a log entry and alert when an account is added to or removed from any group assigned administrative privileges. |
| 5 | Secure Configuration for Hardware and Software on Mobile Device Laptop and Servers | Implement and manage (track, report, correct) security configuration of assets by using configuration management and change control process. | Developing configuration settings with good security properties is complex. It requires system analysis. | Implement regular security updates on configuration. Ensure vulnerabilities are reported and update to support new operational requirements. | Maintain documented, standard security configuration standards for all authorized operating systems and software. | Utilize Security Content Automation Protocol compliant configuration monitoring system. Verify security configuration. Catalog approved exceptions and alerts in the event of unauthorized changes |
| 6 | Maintenance, Monitoring, and Analysis of Audit Logs | Collect and analyze audit logs of events that could help detect, or recover from an attack. | Deficiencies in loggings and analysis allow attacker to hide location and activities. | Keep logging records for audit and compliance purposes. Attackers hide their trails nowadays. | Ensure that local logging has been enabled on all systems and networking devices. | Ensure that appropriate logs are being aggregated to a central log management system for analysis and review. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yeboah-Ofori, A.; Islam, S. Cyber Security Threat Modeling for Supply Chain Organizational Environments. Future Internet 2019, 11, 63. https://doi.org/10.3390/fi11030063
Yeboah-Ofori A, Islam S. Cyber Security Threat Modeling for Supply Chain Organizational Environments. Future Internet. 2019; 11(3):63. https://doi.org/10.3390/fi11030063
Chicago/Turabian StyleYeboah-Ofori, Abel, and Shareeful Islam. 2019. "Cyber Security Threat Modeling for Supply Chain Organizational Environments" Future Internet 11, no. 3: 63. https://doi.org/10.3390/fi11030063
APA StyleYeboah-Ofori, A., & Islam, S. (2019). Cyber Security Threat Modeling for Supply Chain Organizational Environments. Future Internet, 11(3), 63. https://doi.org/10.3390/fi11030063






