Investigating the Influence of Special On–Off Attacks on Challenge-Based Collaborative Intrusion Detection Networks †
Abstract
:1. Introduction
- We first describe the high-level architecture of a typical challenge-based CIDN with the adopted assumptions and then investigate the influence of the SOOA, which can behave normally to one IDS node while responding maliciously to another node. In this case, trust computation in the third node may be affected, as it may receive the opposite judgement from its partner nodes.
- To investigate the attack performance, we have performed two experiments under a simulated and a real CIDN environment. Our results demonstrate that the SOOA has the potential to greatly affect the trust computation of IDS nodes; that is, some malicious nodes can keep their reputation without timely detection. Finally, we discuss some countermeasures and solutions.
2. Related Work
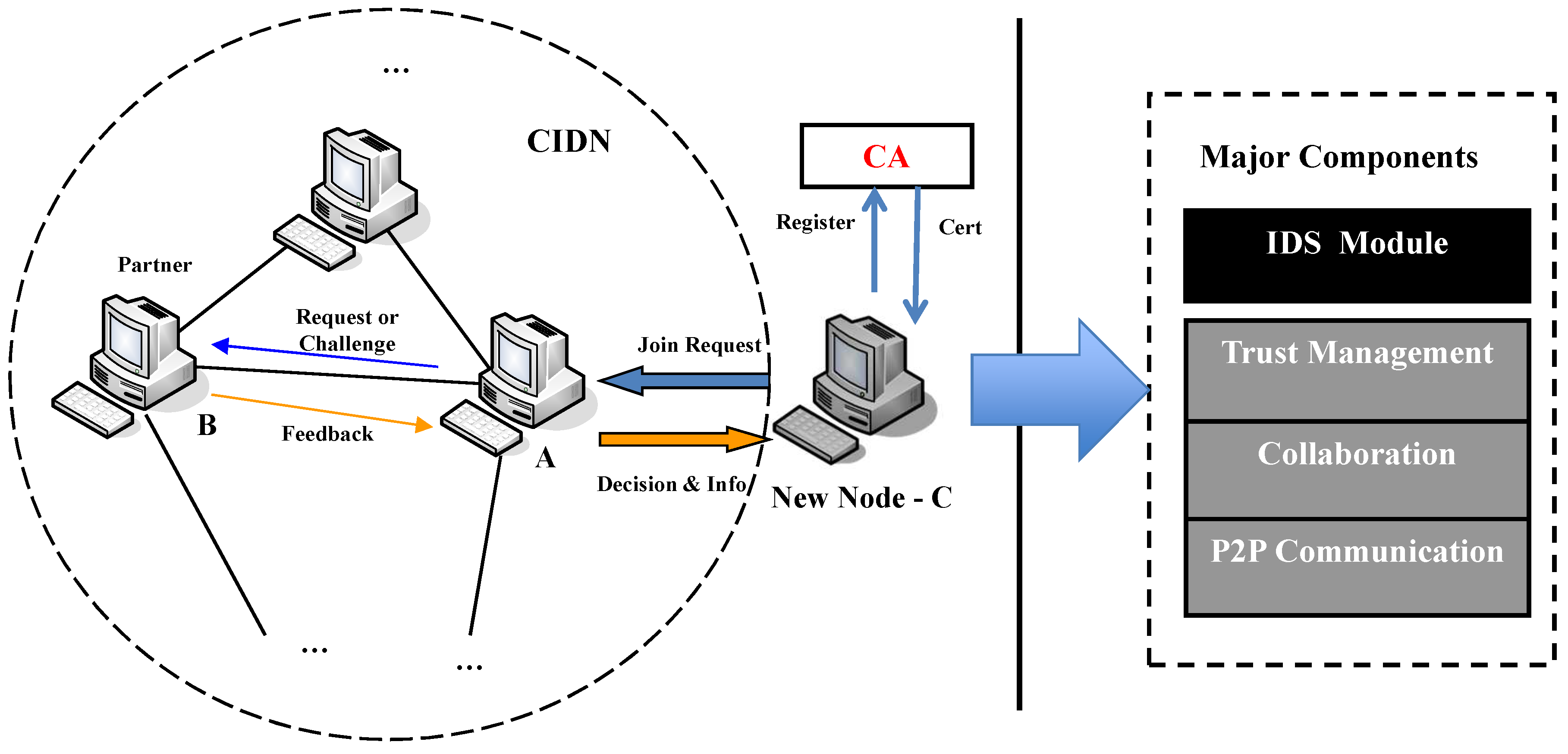
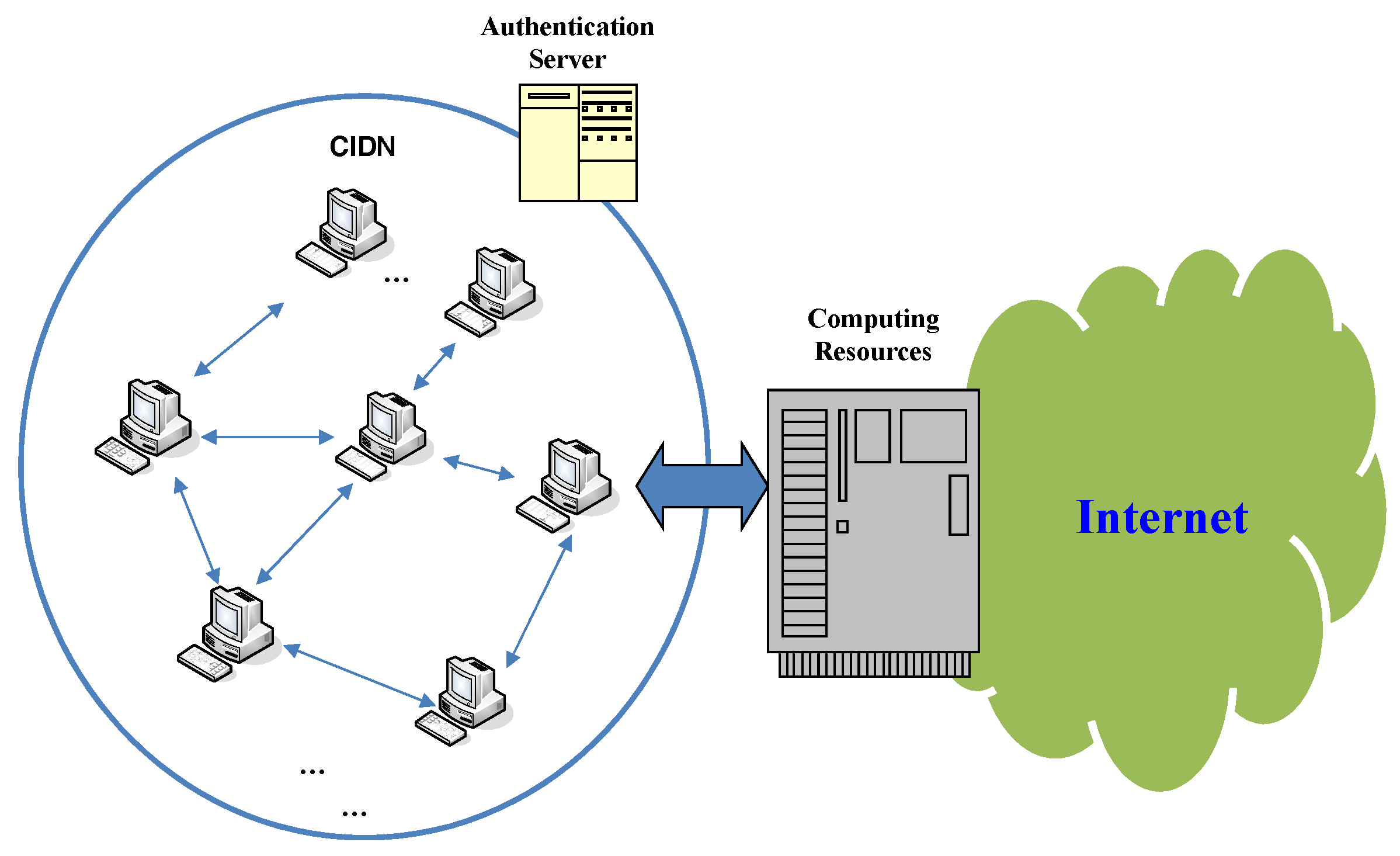
3. Challenge-Based CIDNs
3.1. Background
- Challenges. This type of message contains several IDS alarms requesting the target node to rank the severity. For instance, a testing node can send a challenge periodically to one or several tested nodes and then obtain their answers. Because the testing node extracts IDS alarms from its own database, it can know the alarm severity in advance. Accordingly, it can evaluate the tested nodes’ trustworthiness by identifying the deviation between the expected and the received feedback. For the satisfaction mapping, we refer to Section 5.
- Normal requests. This type of message is sent by a detector to collect data for alarm aggregation. In a CIDN, if a node starts to aggregate alarms, it can send a normal request to other IDS nodes. Then, other trusted nodes can give alarm information on the basis of their own experience. Intuitively, alarm aggregation is a very important step to improve the detection accuracy of a separate intrusion detector. It is worth noting that the alarm aggregation process only considers the information from trusted nodes.
- Trust management component. To measure the reputation of IDS nodes, this component is responsible for comparing the expected answer with the received feedback. As mentioned above, each IDS node can request for the alarm severity through sending either normal requests or challenges. In order to protect challenges, Fung et al. [5] assumed that challenges should be delivered randomly, associated with timing, making them hard to be identified from a normal request.
- Collaboration component. The goal of this component is to handle CIDN messages, that is, to help a node measure the reputation of others by sending normal requests or challenges. For example, this component can return the answers when an IDS node receives a CIDN message. In Figure 1, node B would return its feedback according to its own experience, if node A delivers a request or a challenge.
- P2P communication. This component aims to help maintain connections with other nodes, that is, by configuring the network initialization, address management and node-to-node communication. The trust of the P2P communication is assumed to be trusted.
- Sybil attack. This kind of attack describes the situation in which a node tries to create many fake identities [25]. These fake identities can be utilized to gain a larger impact on alarm aggregation in a CIDN node. The challenge mechanism mitigates this attack through requesting each IDS node to register via a trusted CA and obtain a unique proof identity.
- Newcomer (re-entry) attack. This type of attack indicates the situation in which a node tries to re-enter the network as a newcomer, aiming to erase its bad history. The challenge mechanism avoids this attack by allocating a low reputation level to all new joined nodes.
- Betrayal attack. This kind of attack indicates the situation in which a trusted node turns out to be an untruthful node unexpectedly. The challenge mechanism mitigates this attack by employing a strategy: that is, a high reputation level can only be achieved after a long time-period of interaction with consistent good behavior, whereas the reputation can be quickly degraded by detecting only a few bad actions. To realize this strategy, a forgetting factor can be used to give more weight to recent behavioral events.
3.2. Assumption Analysis
- First assumption. Challenges should be sent randomly to ensure they are hard to be identified from normal messages.
- Second assumption. Malicious nodes always behave untruthfully to other nodes, that is, by sending untruthful answers to the received messages.
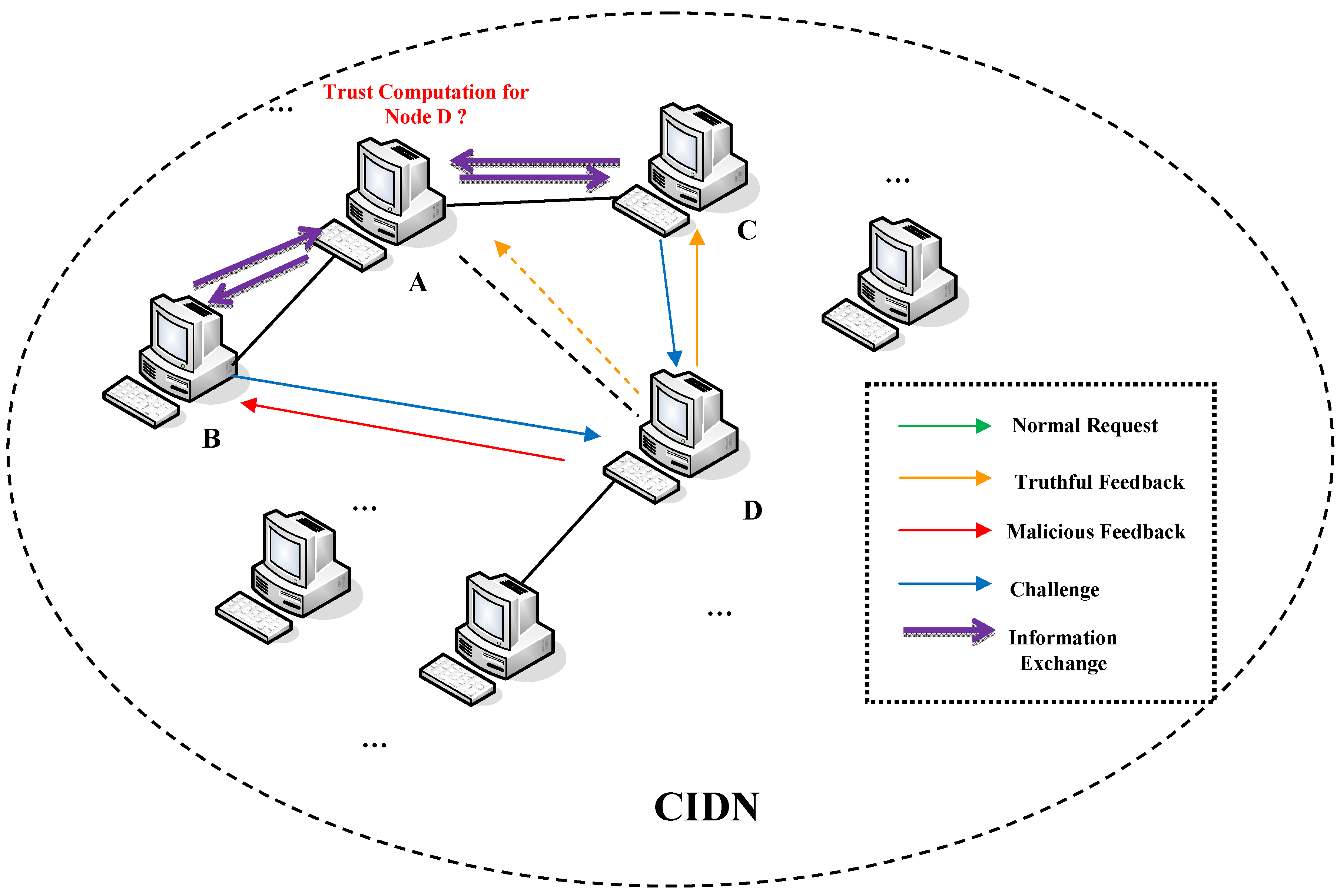
4. SOOA: Special On–Off Attack
- Scenario 1: node is not a partner node of node . In this scenario, node D chooses to send a truthful response to node C while sending untruthful (or malicious) answers to node B. Figure 2 shows that node A can communicate and collect data with/from its partner nodes; thus, node A may receive different (or opposite) reports on node D. This scenario often occurs for a hierarchical network structure, for which a central server needs to collect information and judge the trustworthiness of each node.
- Scenario 2: node is a partner node of node . In this scenario, node D can respond truthfully to node A if they are partner nodes. In CIDNs, node A can judge the trustworthiness of node D through both its own trust computation and the judgement from other nodes, for example, nodes B and C. In this case, node D can perform the same as in Scenario 1 to affect the decision, such as by alarm aggregation of node A.
5. Evaluation
5.1. CIDN Settings
5.2. Simulation Experiment
- Scenario 1. In this condition, node A had six partner nodes in its list without node D. In this case, node D behaved normally to some partner nodes of node A, while it behaved untruthfully to the remaining partner nodes.
- Scenario 2. In this scenario, node A had seven partner nodes including node D, which could send truthful answers to several partner nodes of node A, while sending untruthful (or malicious) answers to the rest of the partner nodes.
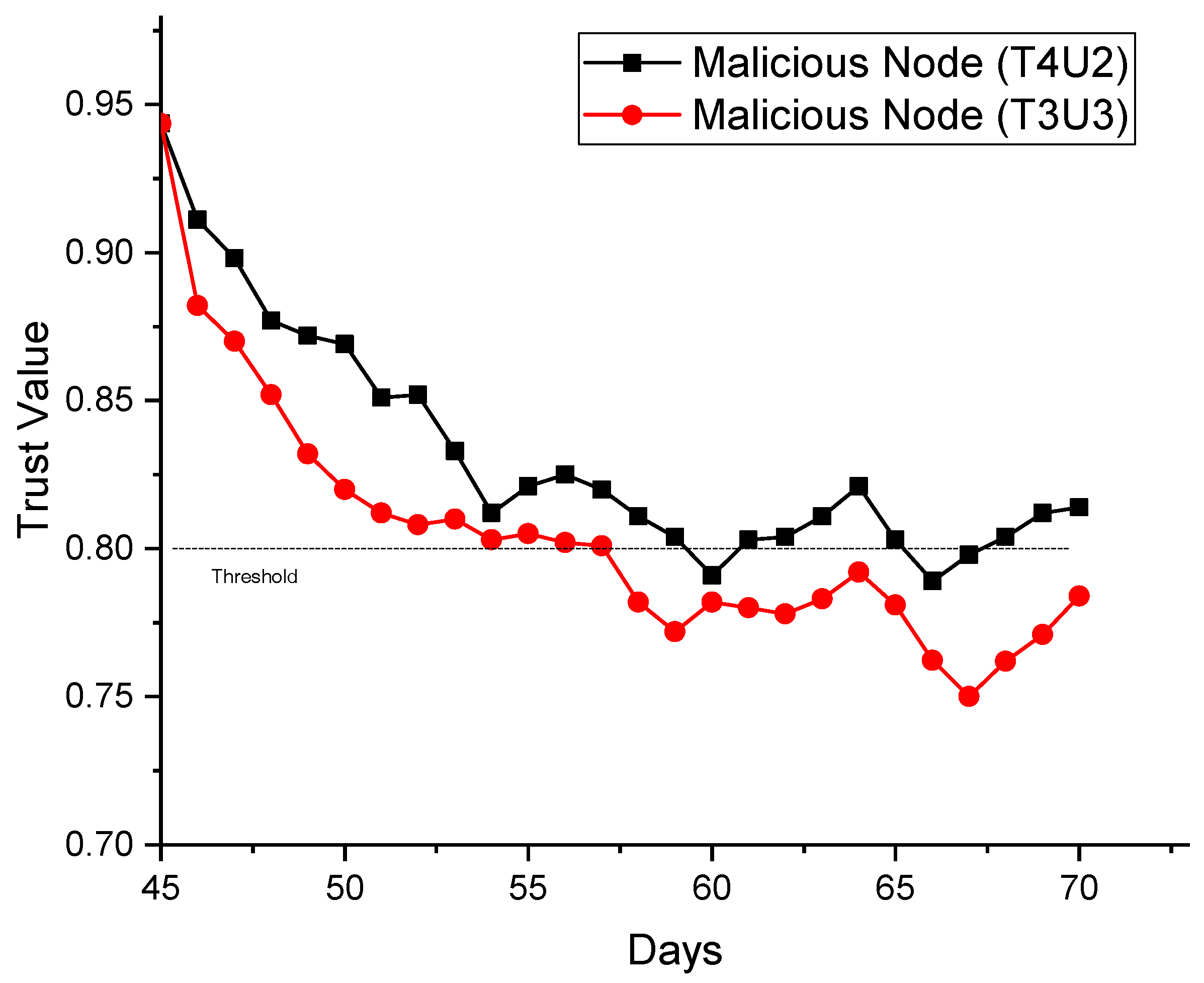
- T4U2. Under this condition, it was found that the trust value of the malicious node (node D) could gradually decrease below the threshold after nearly 15 days, while the trust value could return above the threshold over a period of time. This was because up to four partner nodes reported a “benign” status for node D. Supposing node A was a central server in a CIDN, node D could still make an impact on its judgement as long as its trust value was higher than the threshold of 0.8.
- T3U3. In this condition, node D could behave untruthfully to three partner nodes of node A. It was identified that the trust value of node D could keep decreasing at most cases and fall below the threshold after 15 days without going up to the threshold again. Intuitively, the detection accuracy was better than for the first condition, as one more node would report a “malicious” status for node D.
- T4U2. In this condition, the trust value of node D computed by node A could gradually decrease closer to the threshold during the first 10 days, because two partner nodes could report malicious actions of node D to node A. Afterwards, the trust value was maintained in the range from 0.81 to 0.82 in most cases, as four partner nodes reported that node D was normal. As the trust value was higher than the threshold of 0.8, node D could still make an influence on node A and its alarm aggregation.
- T3U3. In this condition, node D sent truthful feedback to three partner nodes of node A but sent malicious feedback to the other three partner nodes. It was found that the trust value of node D computed by node A could keep decreasing during the first 15 days, whereupon it was maintained around the threshold. As node D always sent truthful feedback to node A, its trust value crossed below and above the threshold.
5.3. Evaluation in a Real Environment
- Scenario 1. In this scenario, it was found that the trust value of the malicious node could decrease much faster under T3U3 than T4U2. More specifically, the trust value under T4U2 could deviate around the threshold, while decreasing nearly directly under T3U3. The observations are in-line with the results obtained in the simulated environment. While we identified that the trust value of the malicious node decreased faster in a real network environment under T3U3, an attacker should make a better strategy to launch the SOOA, that is, behave normally to more than half the nodes.
- Scenario 2. Figure 7 shows that the trust value of the malicious node under T3U3 could maintain a downtrend for the first 10 days but would deviate around the threshold later; that is, it was above the threshold for a total of 10 days. Under T4U2, it was found that the trust value of the malicious node would not decrease below the threshold. Similarly, the observations are in-line with the results obtained in the simulated evaluation.
5.4. Discussion
- The impact of partner nodes’ selection. In this work, we assume that each partner has the same impact on the decision in the target node. Thus, there is no need to consider how to select a partner node for the SOOA. However, if we consider that the target node may give different weights to its partner nodes, then there is a need to identify which type of partner node can be attacked. This is an interesting topic for our future work.
- A variety of combinations. In this work, we only evaluated two combinations, namely, T3U3 and T4U2, under two scenarios. The obtained results have demonstrated the influence of the SOOA on the robustness of the challenge mechanisms. In future work, it will be an interesting topic to investigate the trend of trust values in other combinations, for example, T4U3 and T5U5.
- Emphasizing the impact of malicious actions. In CIDNs, if a node wishes to evaluate a node’s trustworthiness, it has to collect information from other trusted nodes. Our attack allows malicious nodes to behave maliciously, without a timely detection. One potential solution is to punish more for malicious actions, if detected by a node, for example, by building a trust computation by means of IS, which can give greater weight to expert nodes.
- Employing additional measurements. In challenge-based CIDNs, the trustworthiness of a node is mainly determined by challenges, but the challenges have to be sent over a period of time, rendering the network vulnerable to advanced attacks. To enhance the robustness of CIDNs, additional measures should be considered to evaluate the trustworthiness of a node, for example, packet-level trust [11].
6. Conclusions
Author Contributions
Conflicts of Interest
Abbreviations
| IDS | Intrusion detection system |
| CIDN | Collaborative intrusion detection network |
| SOOA | Special on–off attack |
| IS | Intrusion sensitivity |
| PMFA | Passive message fingerprint attack |
References
- Scarfone, K.; Mell, P. Guide to Intrusion Detection and Prevention Systems (IDPS); NIST Special Publication: Gaithersburg, MD, USA, 2007; pp. 800–894. [Google Scholar]
- Gong, F. Next Generation Intrusion Detection Systems (IDS); McAfee Network Security Technologies Group: Santa Clara, CA, USA, 2003. [Google Scholar]
- Duma, C.; Karresand, M.; Shahmehri, N.; Caronni, G. A Trust-Aware, P2P-Based Overlay for Intrusion Detection. In Proceedings of the 17th International Workshop on Database and Expert Systems Applications, Krakow, Poland, 4–8 September 2006; pp. 692–697. [Google Scholar]
- Wu, Y.-S.; Foo, B.; Mei, Y.; Bagchi, S. Collaborative Intrusion Detection System (CIDS): A Framework for Accurate and Efficient IDS. In Proceedings of the 2003 Annual Computer Security Applications Conference (ACSAC), Las Vegas, NV, USA, 8–12 December 2003; pp. 234–244. [Google Scholar]
- Fung, C.J.; Boutaba, R. Design and management of collaborative intrusion detection networks. In Proceedings of the 2013 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ghent, Belgium, 27–31 May 2013; pp. 955–961. [Google Scholar]
- Fung, C.J.; Baysal, O.; Zhang, J.; Aib, I.; Boutaba, R. Trust Management for Host-Based Collaborative Intrusion Detection. In DSOM 2008, Lecture Notes in Computer Science (LNCS) 5273; De Turck, F., Kellerer, W., Kormentzas, G., Eds.; Springer: Berlin, Germany, 2008; pp. 109–122. [Google Scholar]
- Fung, C.J.; Zhang, J.; Aib, I.; Boutaba, R. Robust and scalable trust management for collaborative intrusion detection. In Proceedings of the 11th IFIP/IEEE International Conference on Symposium on Integrated Network Management (IM), Long Island, NY, USA, 1–5 June 2009; pp. 33–40. [Google Scholar]
- Li, W.; Meng, Y.; Kwok, L.-F.; Ip, H.H.S. PMFA: Toward Passive Message Fingerprint Attacks on Challenge-based Collaborative Intrusion Detection Networks. In Proceedings of the 10th International Conference on Network and System Security (NSS), Taipei, Taiwan, 28–30 September 2016; pp. 433–449. [Google Scholar]
- Meng, M.; Luo, X.; Li, W.; Li, Y. Design and Evaluation of Advanced Collusion Attacks on Collaborative Intrusion Detection Networks in Practice. In Proceedings of the 15th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Tianjin, China, 23–26 August 2016; pp. 1061–1068. [Google Scholar]
- Li, W.; Meng, Y.; Kwok, L.-F. SOOA: Exploring Special On-Off Attacks on Challenge-Based Collaborative Intrusion Detection Networks. In Proceedings of the 12th International Conference on Green, Pervasive, and Cloud Computing (GPC), Cetara, Italy, 11–14 May 2017; pp. 402–415. [Google Scholar]
- Meng, Y.; Li, W.; Xiang, Y.; Choo, K.-K.R. A Bayesian Inference-based Detection Mechanism to Defend Medical Smartphone Networks against Insider Attacks. J. Netw. Comput. Appl. 2017, 78, 162–169. [Google Scholar] [CrossRef]
- Donovan, S.; Feamster, N. Alternative trust sources: Reducing DNSSEC signature verification operations with TLS. In Proceedings of the 2015 ACM Conference on Special Interest Group on Data Communication (SIGCOMM), London, UK, 17–21 August 2015; pp. 353–354. [Google Scholar]
- Kolias, C.; Kolias, V.; Kambourakis, G. TermID: A distributed swarm intelligence-based approach for wireless intrusion detection. Int. J. Inf. Secur. 2017, 16, 401–416. [Google Scholar] [CrossRef]
- Meng, Y.; Li, W.; Kwok, L.-F. Evaluation of detecting malicious nodes using Bayesian model in wireless intrusion detection. In Proceedings of the 7th International Conference on Network and System Security (NSS), Helsinki, Finland, 21–23 August 2013; Lecture Notes in Computer Science 7873. Springer: Berlin, Germany, 2013; pp. 40–53. [Google Scholar]
- Meng, W.; Au, M.H. Towards statistical trust computation for medical smartphone networks based on behavioral profiling. In Proceedings of the 11th IFIP WG 11.11 International Conference on Trust Management (IFIPTM), Gothenburg, Sweden, 12–16 June 2017; pp. 152–159. [Google Scholar]
- Meng, W.; Li, W.; Wang, Y.; Au, M.H. Detecting malicious nodes in medical smartphone networks through euclidean distance-based behavioral profiling. In Proceedings of the 9th International Symposium on Cyberspace Safety and Security (CSS), Xi’an, China, 23–25 October 2017; pp. 163–175. [Google Scholar]
- Meng, W.; Li, W.; Su, C.; Zhou, J.; Lu, R. Enhancing Trust Management for Wireless Intrusion Detection via Traffic Sampling in the Era of Big Data. IEEE Access 2017. [Google Scholar] [CrossRef]
- Ramos, A.; Lazar, M.; Filho, R.H.; Rodrigues, J.J.P.C. A security metric for the evaluation of collaborative intrusion detection systems in wireless sensor networks. In Proceedings of the IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017. [Google Scholar]
- Li, W.; Meng, Y.; Kwok, L.-F.; Ip, H.H.S. Developing Advanced Fingerprint Attacks on Challenge-based Collaborative Intrusion Detection Networks. Clust. Comput. 2017, 1–12. [Google Scholar] [CrossRef]
- Li, W.; Meng, Y.; Kwok, L.-F. Enhancing Trust Evaluation Using Intrusion Sensitivity in Collaborative Intrusion Detection Networks: Feasibility and Challenges. In Proceedings of the 9th International Conference on Computational Intelligence and Security (CIS), Leshan, China, 14–15 December 2013; pp. 518–522. [Google Scholar]
- Li, W.; Meng, W.; Kwok, L.-F. Design of intrusion sensitivity-based trust management model for collaborative intrusion detection networks. In Trust Management VIII, IFIP AICT; Zhou, J., Gal-Oz, N., Zhang, J., Gudes, E., Eds.; Springer: Heidelberg, Germany, 2014; Volume 430, pp. 61–76. [Google Scholar]
- Li, W.; Meng, Y.; Kwok, L.-F.; Ip, H.H.S. Enhancing Collaborative Intrusion Detection Networks Against Insider Attacks Using Supervised Intrusion Sensitivity-Based Trust Management Model. J. Netw. Comput. Appl. 2017, 77, 135–145. [Google Scholar] [CrossRef]
- Li, W.; Meng, W. Enhancing collaborative intrusion detection networks using intrusion sensitivity in detecting pollution attacks. Inf. Comput. Secur. 2016, 24, 265–276. [Google Scholar] [CrossRef]
- Cho, J.-H.; Chan, K.; Adali, S. A Survey on Trust Modeling. ACM Comput. Surv. 2015, 48. [Google Scholar] [CrossRef]
- Douceur, J. The sybil attack. In IPTPS 2002. LNCS; Druschel, P., Kaashoek, M.F., Rowstron, A., Eds.; Springer: Heidelberg, Germany, 2002; Volume 2429. [Google Scholar]
- Perrone, L.P.; Nelson, S.C. A Study of On-Off Attack Models for Wireless Ad Hoc Networks. In Proceedings of the 2006 Workshop on Operator-Assisted Community Networks, Berlin, Germany, 18–19 September 2006; pp. 1–10. [Google Scholar]
- Snort: An Open Source Network Intrusion Prevention and Detection System (IDS/IPS). Homepage. Available online: http://www.snort.org/ (accessed on 8 January 2018).


| Parameters | Value | Description |
|---|---|---|
| 0.9 | Forgetting factor | |
| 10/day | Low request frequency | |
| 20/day | High request frequency | |
| r | 0.8 | Trust threshold |
| 0.5 | Trust value for newcomers | |
| m | 10 | Lower limit of received feedback |
| d | 0.3 | Severity of punishment |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, W.; Meng, W.; Kwok, L.F. Investigating the Influence of Special On–Off Attacks on Challenge-Based Collaborative Intrusion Detection Networks. Future Internet 2018, 10, 6. https://doi.org/10.3390/fi10010006
Li W, Meng W, Kwok LF. Investigating the Influence of Special On–Off Attacks on Challenge-Based Collaborative Intrusion Detection Networks. Future Internet. 2018; 10(1):6. https://doi.org/10.3390/fi10010006
Chicago/Turabian StyleLi, Wenjuan, Weizhi Meng, and Lam For Kwok. 2018. "Investigating the Influence of Special On–Off Attacks on Challenge-Based Collaborative Intrusion Detection Networks" Future Internet 10, no. 1: 6. https://doi.org/10.3390/fi10010006
APA StyleLi, W., Meng, W., & Kwok, L. F. (2018). Investigating the Influence of Special On–Off Attacks on Challenge-Based Collaborative Intrusion Detection Networks. Future Internet, 10(1), 6. https://doi.org/10.3390/fi10010006







