A New Lightweight Watchdog-Based Algorithm for Detecting Sybil Nodes in Mobile WSNs
Abstract
:1. Introduction
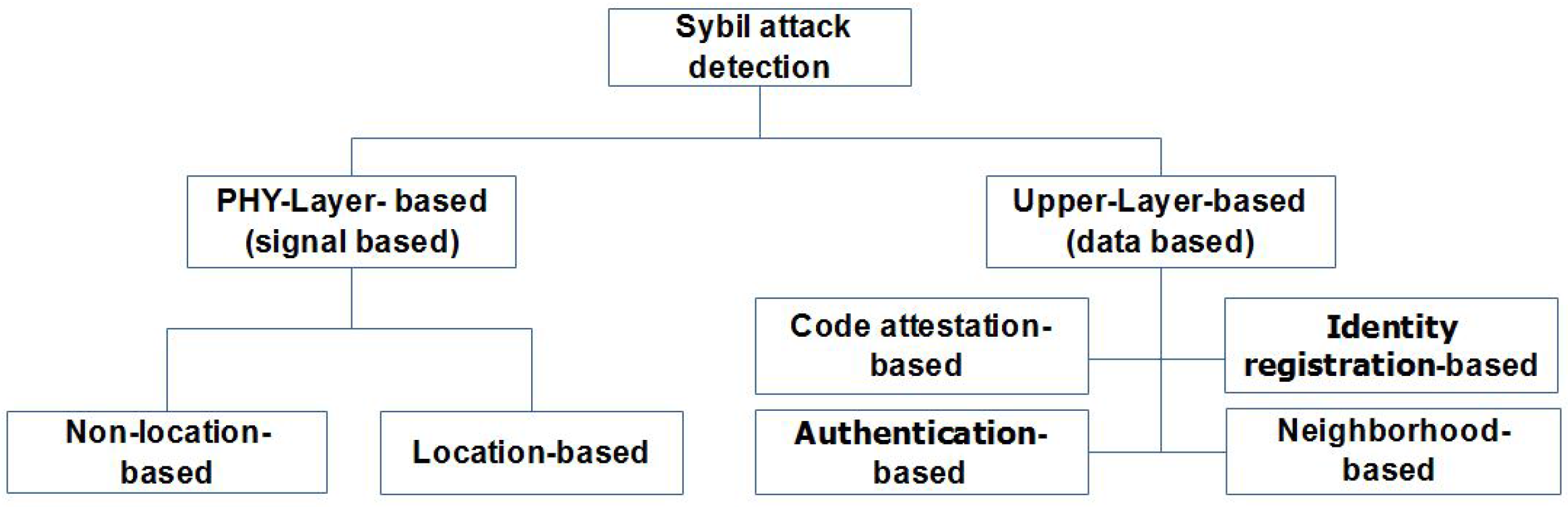
2. Related Works
3. Problem Statement and Attack Model Assumptions
4. Proposed Algorithm
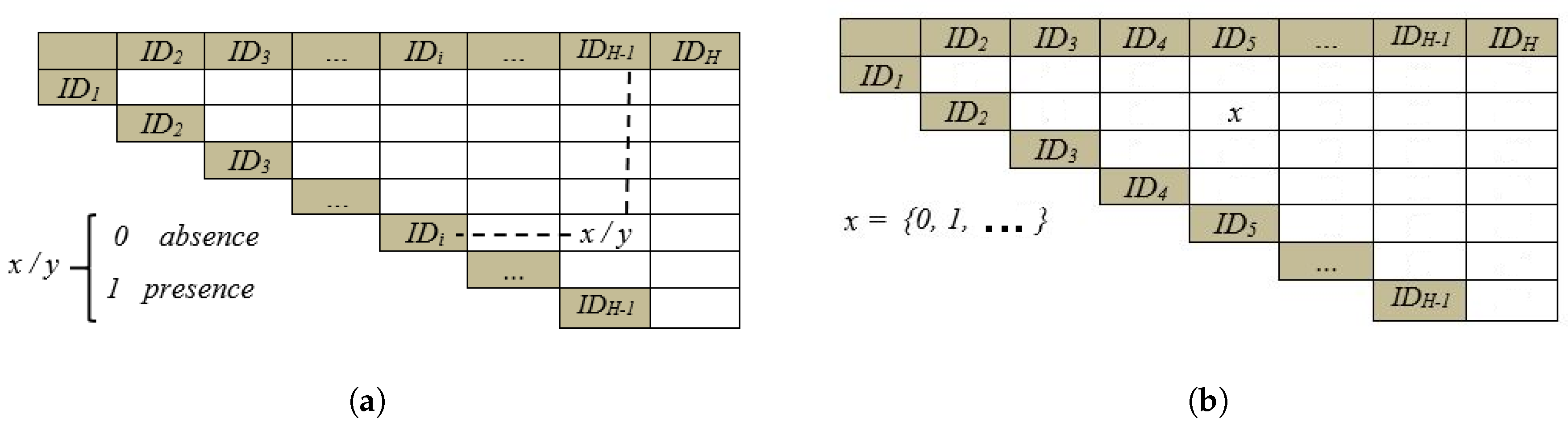
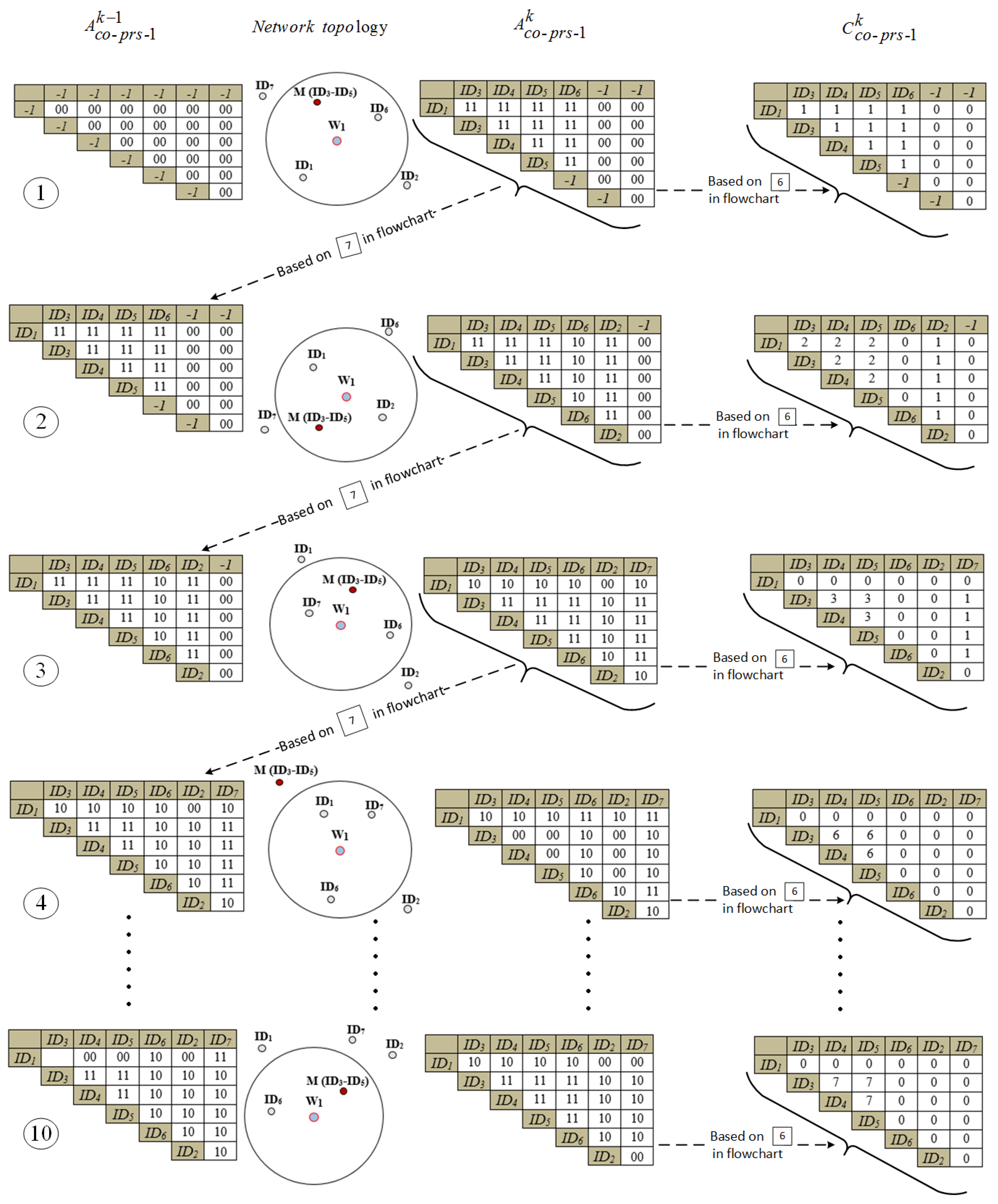
- : This is an upper-triangle matrix which contains the co-presence status of all node pairs at time index k. The elements of are in the form of where 0 and 1 represent absence and presence respectively (Figure 2a). In Figure 2, H refers to the total number of Sybil and normal-node IDs which is equal to:where , , and S equals the number of Sybil IDs per malicious node.
- : This matrix which is structurally similar to (upper-triangle ) scores the co-presence of each node pair at time index k (Figure 2b) and is updated according to , and the co-presence state diagram model.
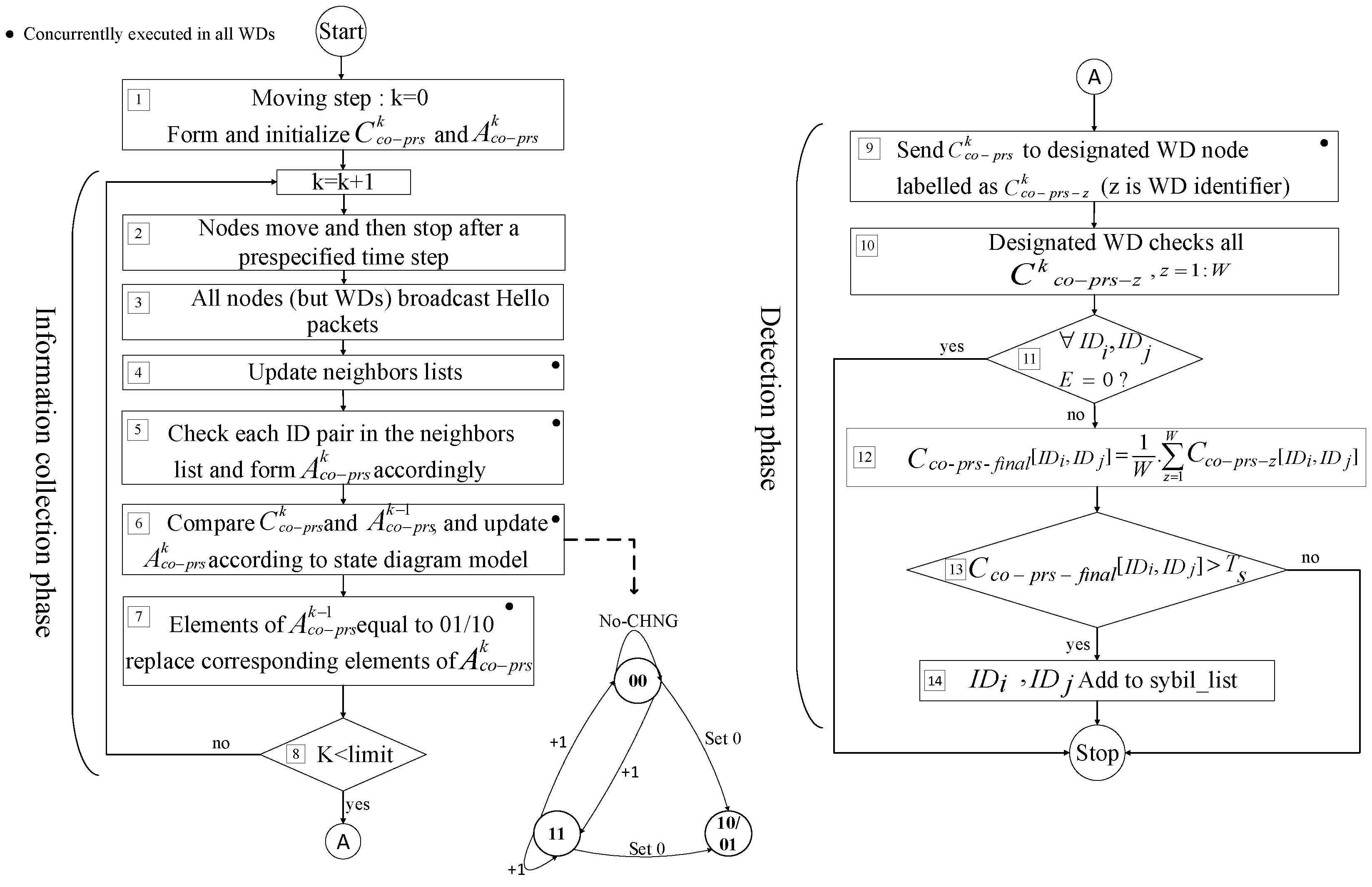
- Co-presence state diagram model: This diagram shows how a transition between co-presence states of ID pairs updates the elements of the matrix (Figure 3).
- Initialization phaseStep I (): Each WD constitutes of matrices and and fills the former with 00s corresponding to the general co-absence status.
- Information collection phaseStep II (,,): Hello Packets are broadcasted by normal and malicious nodes at fixed time intervals (movement steps). Following each movement, all WD nodes update their neighbors lists by overhearing these Hello Packets.Step III (): Each WD forms the new based on its current neighbors list as follows. Two-digit binary numbers 00, 11, and correspond to co-absence, co-presence, and alternate-presence statuses respectively. Specifically, if , the content of element (, ) of matrix is set to 00. On the other hand, if , this content is set to 11. Finally, if and (or vice versa), the content of the corresponding element of is set to 10. These values also represent the states in the co-presence state diagram model.Step IV (): By comparing the contents of the corresponding elements of and , the content of the corresponding element of is updated according to the transitions in the state diagram. For instance, when and , according to the state diagram, must be increased.Step V (,): In this step, is updated so that the elements of which are equal to replace the corresponding elements of (trap states are preserved).Steps II to V are repeated for a predetermined number of times representing the network’s lifetime.
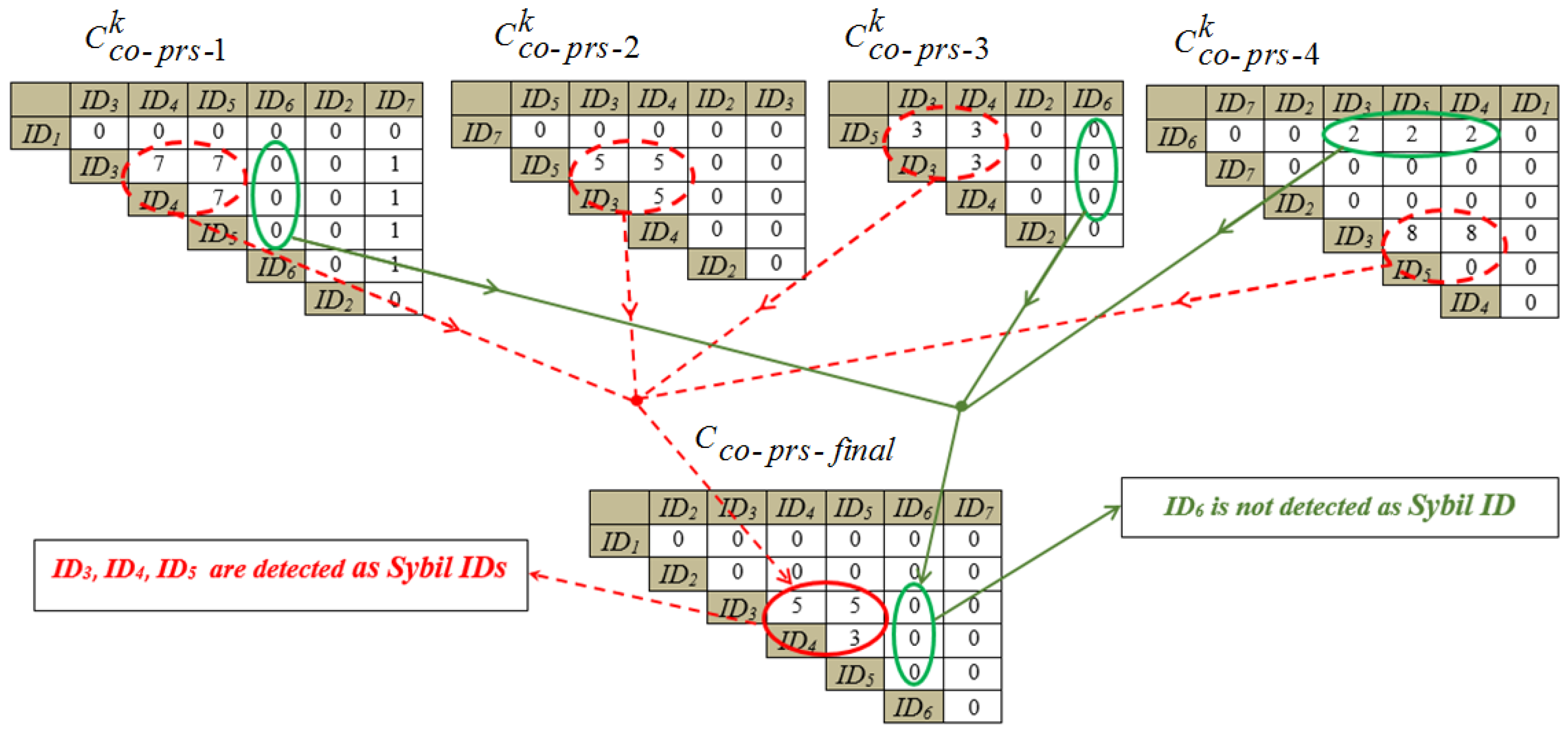
- Detection phaseStep VI (,,,): All WDs send their co-presence information (labeled as ) to a designated WD node . The designated WD then checks the elements of for each WD and creates a matrix according to:whereinandStep VII (,): The designated WD examines the elements of against a predetermined Sybil threshold, . If is greater than , and are added to its internally maintained Sybil list. is a representation of how often on average two non-sybil IDs are expected to co-appear in one WD’s neighborhood. can be specified by trial and error to generate satisfactory true and false detection results. The designated WD finally broadcasts the Sybil list to other WDs to act upon.Notes :
- -
- There are rare circumstances where the proposed algorithm falsely detects normal nodes as Sybil IDs (false negative). In particular, this happens when a malicious node and a normal node simultaneously move in and out of a WD’s neighborhood and because the proposed algorithm operates based on co-appearance detection .
- -
- While the detection phase is implemented in the designated WD node, it is no different from other WDs. If the designated WD fails, provisions could be put in place (as a future work) to replace it with another WD. Thus, the algorithm can be thought of as being somewhat protected from the single-point-of-failure problem.
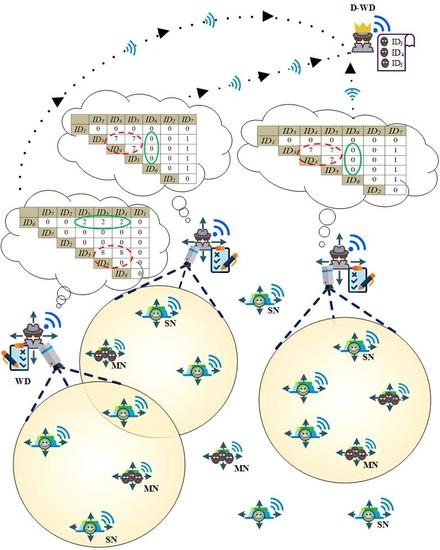
- Information collection phase: Figure 5 shows the information collection phase of the algorithm illustrating how it proceeds step-by-step as is implemented in . The same procedure is repeated in not shown here for the sake of brevity.In each row (corresponding to a specific time step), the left most column illustrates the former IDs-co-presence status of the network shown by matrix . The second column from the left illustrates the network topology after applying one-step movement.Similarly, the third column from the left shows the current (post-movement) IDs-co-presence status of the network presented by matrix . By comparing and , the scoring matrix is updated according to the state diagram of Figure 3, as shown in the forth column. This algorithm proceeds in the following row (corresponding to the next time step) starting with a generated from in the preceding row and manipulated by in the flowchart of Figure 4. This phase is terminated by reaching the simulation step limit which is equal to 10 in this example.
- Detection phase: The designated WD receives the matrices from the other three WDs. Then the designated WD uses the received information, and its own matrix to form the matrix according to Equation (2). Finally, each element of the matrix is compared against the Sybil threshold, , to detect and announce the Sybil IDs as illustrated in Figure 6.
5. Simulation Results and Performance Evaluation
5.1. Measures of performance
- True Detection Rate (): the percentage of Sybil nodes detected by a detection algorithm.
- False Detection Rate (): the percentage of normal nodes detected as Sybil nodes erroneously.
- Memory overhead: the amount of memory consumption for algorithm implementation.
- Communicational overhead: the amount of extra algorithm-specific control-information required for algorithm implementation.
- Computational load: the number of computational operations needed for implementing an algorithm.
5.2. Simulation Setup
5.3. Simulation Results
5.3.1. Evaluation
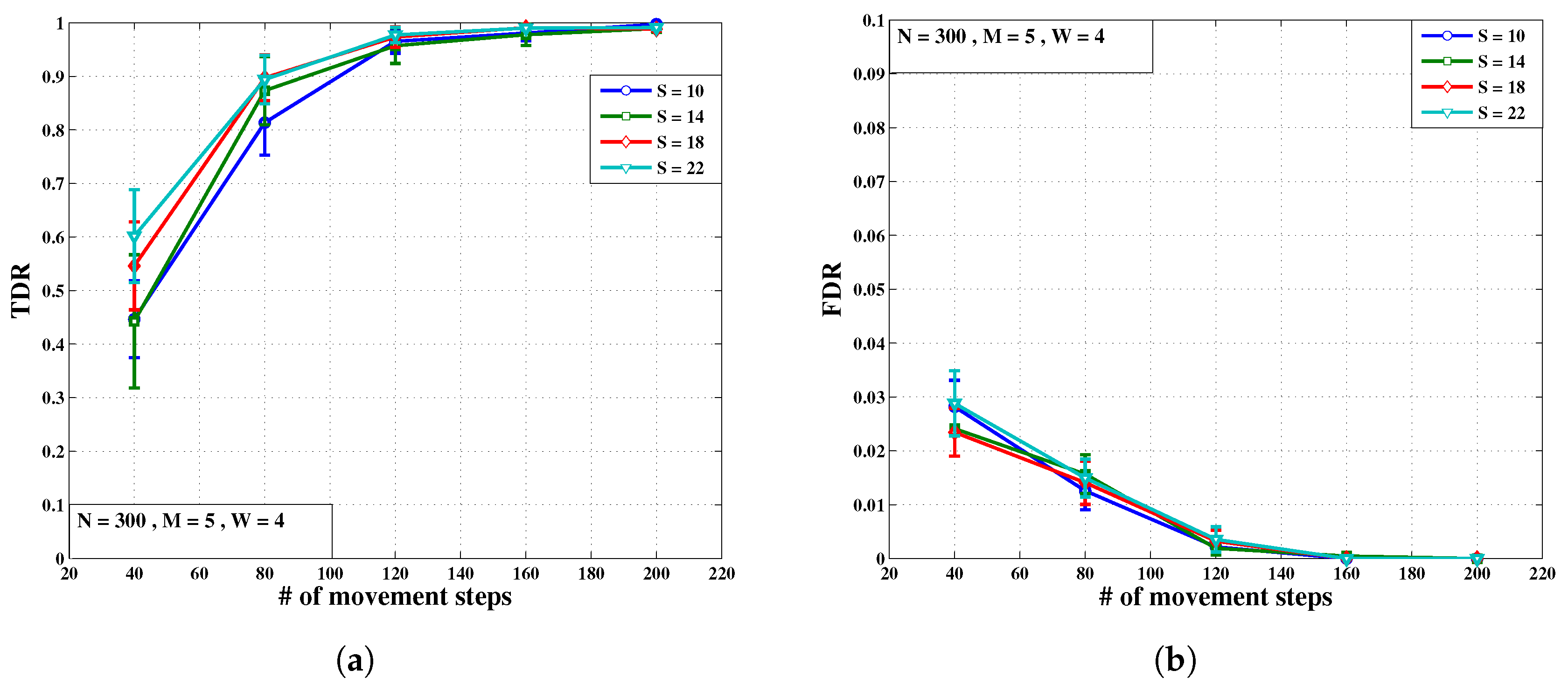
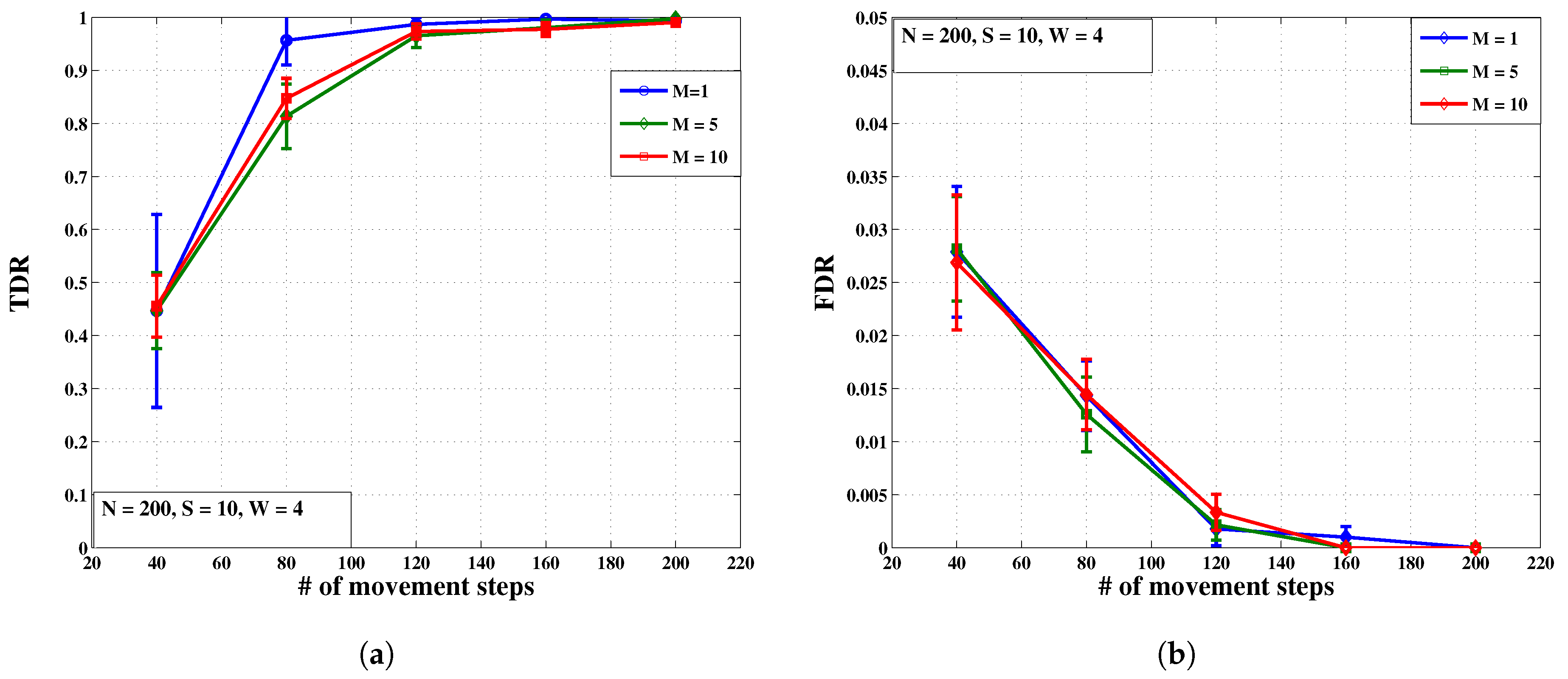
- Test 1: This test is designed to evaluate the new algorithm’s TDR and FDR against the number of movement steps for different number of Sybil IDs as a parameter varying from 8 to 20. The value of the remaining parameters are fixed as they appear in Table 1.Figure 7a shows that TDR increases as time goes by. This is completely expected since more information is collected in longer periods of time. After 120 movement steps, for any number of Sybil IDs, good detection rates of at least are achieved.Similarly, we expect FDR to improve by collecting more information over time towards higher movement steps. As Figure 7b illustrates, regardless of the number of Sybil IDs, FDR sufficiently nears zero at movement steps close to 160.
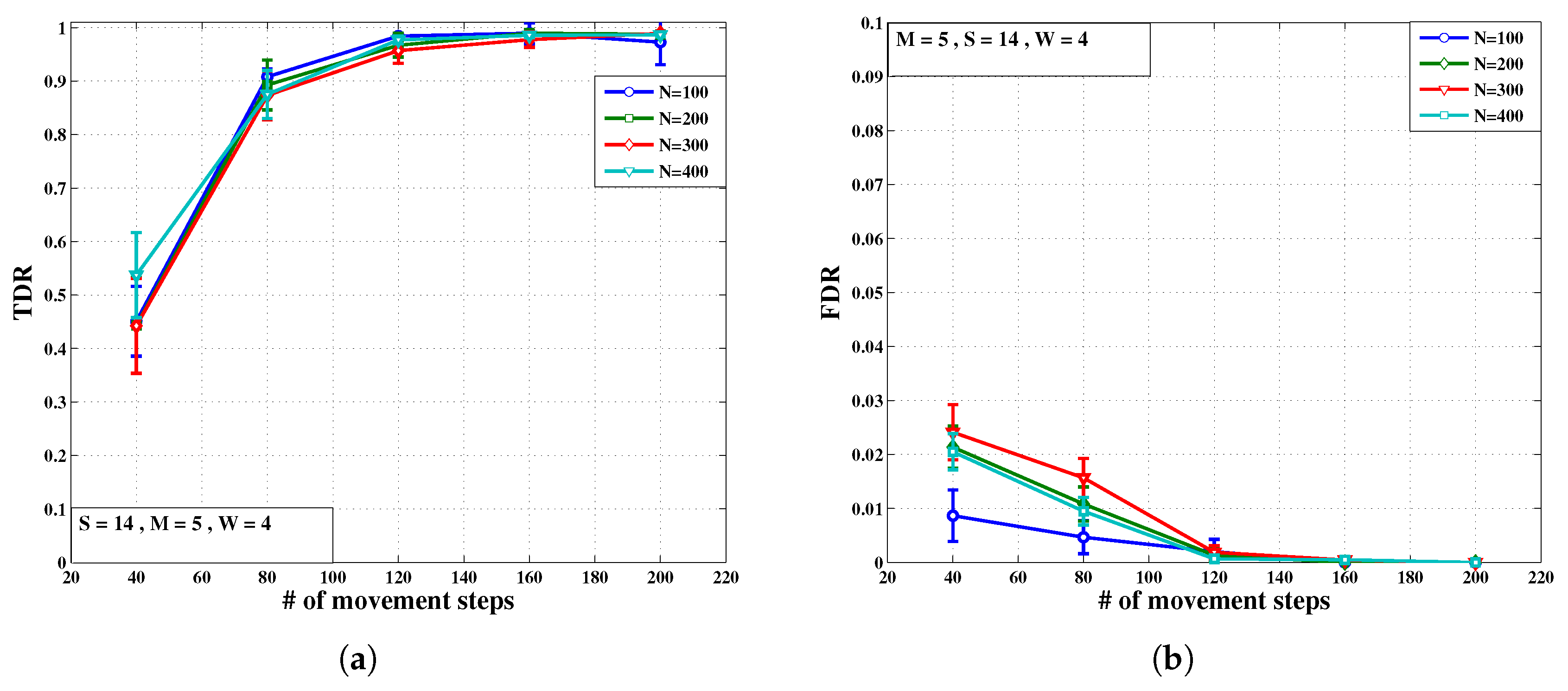
- Test 2: In this test, TDR and FDR have been evaluated against the number of movement steps for different number of normal nodes varying from 100 to 400 (The values of the remaining parameters are fixed as they appear in Table 1).As shown in Figure 8a and very consistent with the results of Figure 7a, good TDR results are obtained after 120 number of movement steps, no matter what the number of normal nodes is Similar to what we observed in Figure 7b of Test 1, Figure 8b shows that FDR decreases with increasing movement steps until reaching almost zero at movement steps close to 200.
- Test 3: Through this test it is illustrated how TDR and FDR are affected by varying the number of malicious nodes from 1 to 10. The fixed parameters are and ( for the values of other parameters refer to Table 1).In Figure 9a,b, almost perfect TDRs and FDRs are achieved for all number of malicious nodes from movement steps greater than or equal to 120 on.
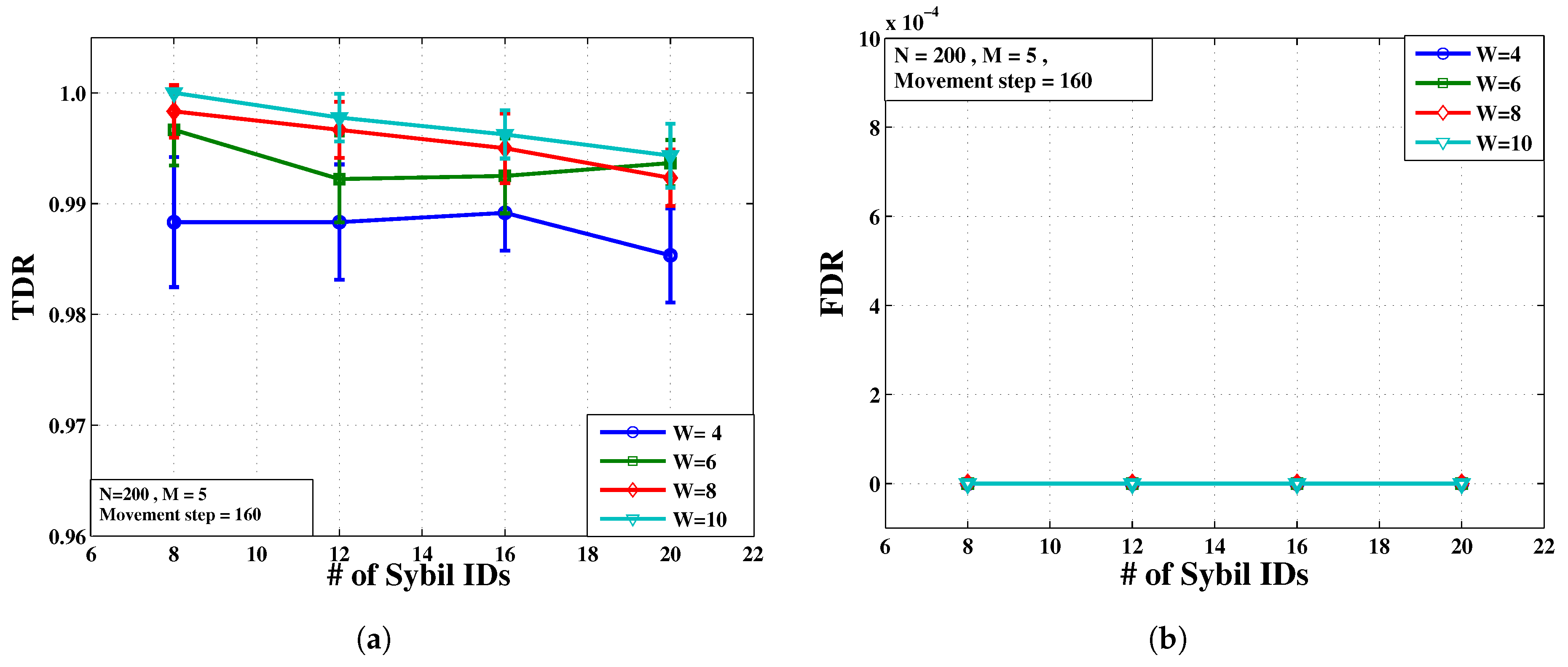
- Test 4: Values of TDR and FDR against the number of Sybil IDs for different number of watchdog nodes is the subject of this test. The results correspond to movement step equal to 160 where the system has already reached its steady state. As before, the other fixed parameters are as they appear in Table 1.
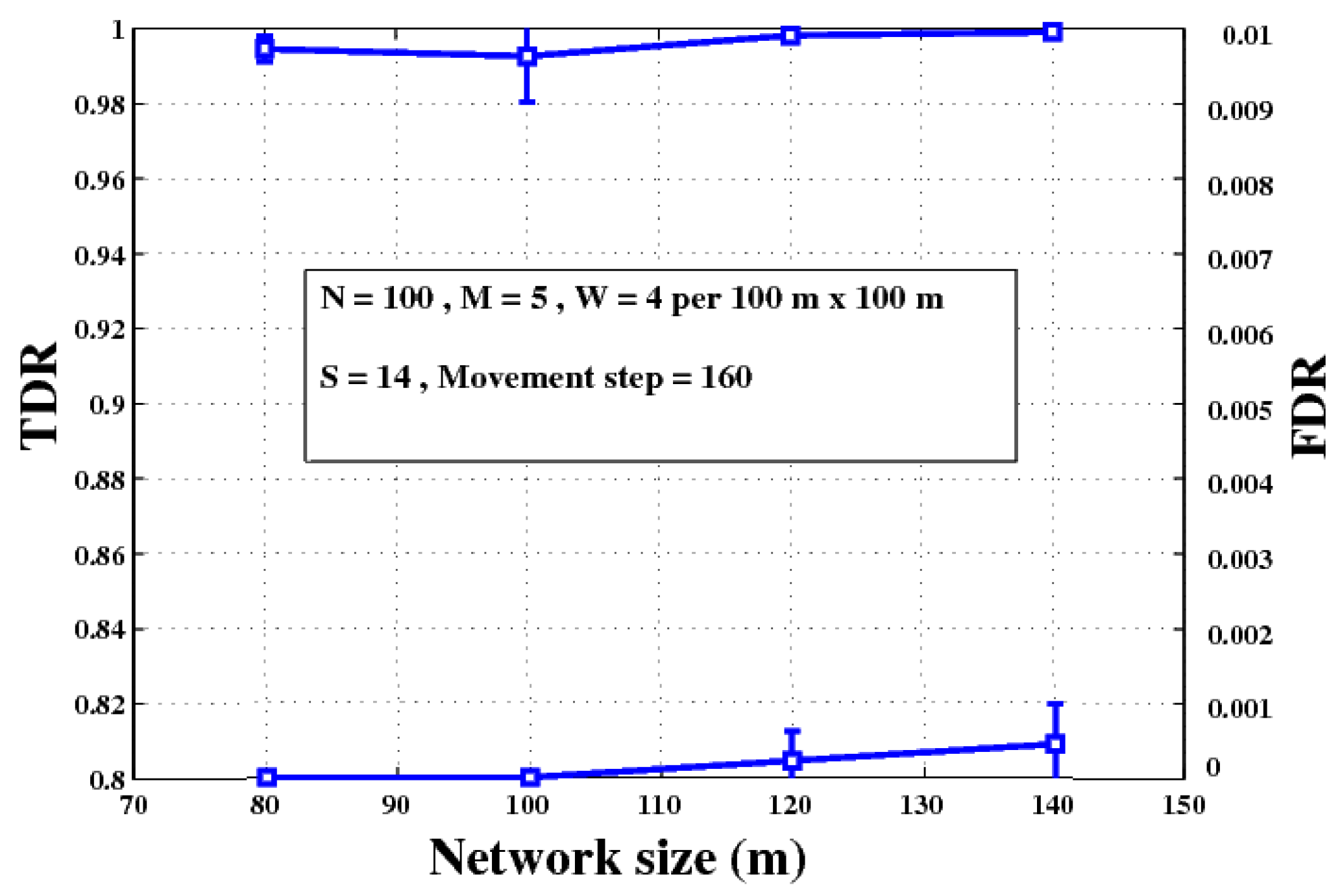
- Test 5: In this test, the effect of scalability on the TDR/FDR performance of the proposed algorithm is verified (Figure 11). To make it a fair comparison, all node populations (normal, malicious, and watchdog) grow proportionally with the network area. The value of population parameters and the snapshot instance (Movement step) are mentioned in the figure. The maximum network size adopted is constrained by the limitations of J-SIM. The other fixed parameters are as they appear in Table 1.The TDR/FDR results of Figure 11 show very insignificant variations with respect to the network size. This is somewhat expected since in wireless networks it is the routing that is mostly susceptible to scalability which is not a concern herein.
- Comparing Figure 7 and Figure 8, the convergence rates of TDR and FDR are more sensitive to the number of Sybil IDs per malicious node and the number of normal nodes respectively, before reaching their steady states. This is expected because of the very definition of TDR and FDR in Section 5.1.
- Somewhat related to the previous observation, Figure 7a and Figure 9a show that increasing the total number of Sybil IDs by increasing S and M have opposite impacts on TDR. In fact, increasing S makes the Sybil pattern more noticeable and in favor of TDR. As illustrated by Figure 7b and Figure 9b increasing the total number of Sybil IDs does not have much effect on FDR.
- The results in Figure 10a suggest that, in steady state, there is a turning point of WD population above which not much TDR gain is achieved.
5.3.2. Comparison
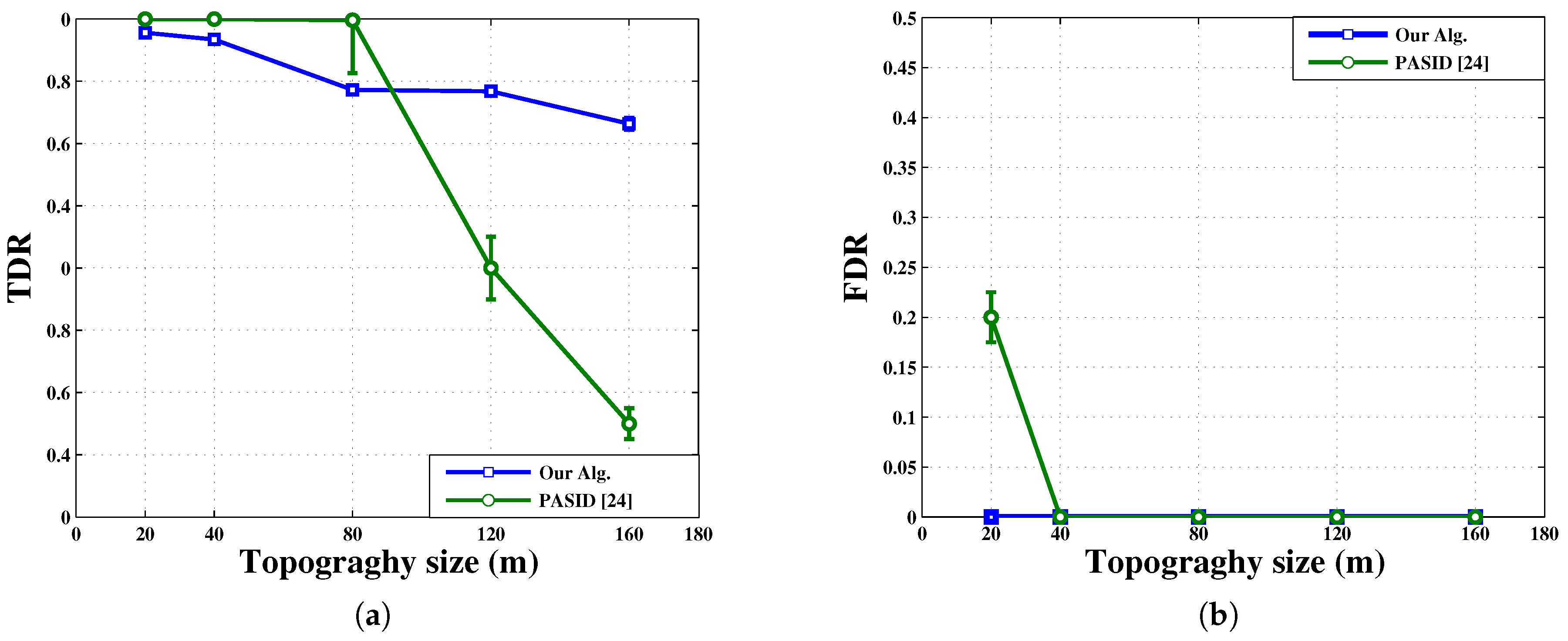
- Comparison 1: To compare our algorithm with PASID, we have to set the simulation parameters as per [24]. Therefore, in this part, we assume , , , and the results are calculated at . Figure 12 illustrates TDR and FDR for PASID and our algorithm against the network size (herein called topography size as in [24]). To be consistent with results in [24], each point of the new proposed algorithm’s results is an average over 240 combinations of , and , and where the latter corresponds to the best case result reported in [24]. The results of PASID are extracted from [24]. The new algorithm performs better than PASID in terms of FDR for all network sizes. In terms of TDR, the new algorithm has a significant edge over PASID in large networks while slightly under-performing it in smaller ones.
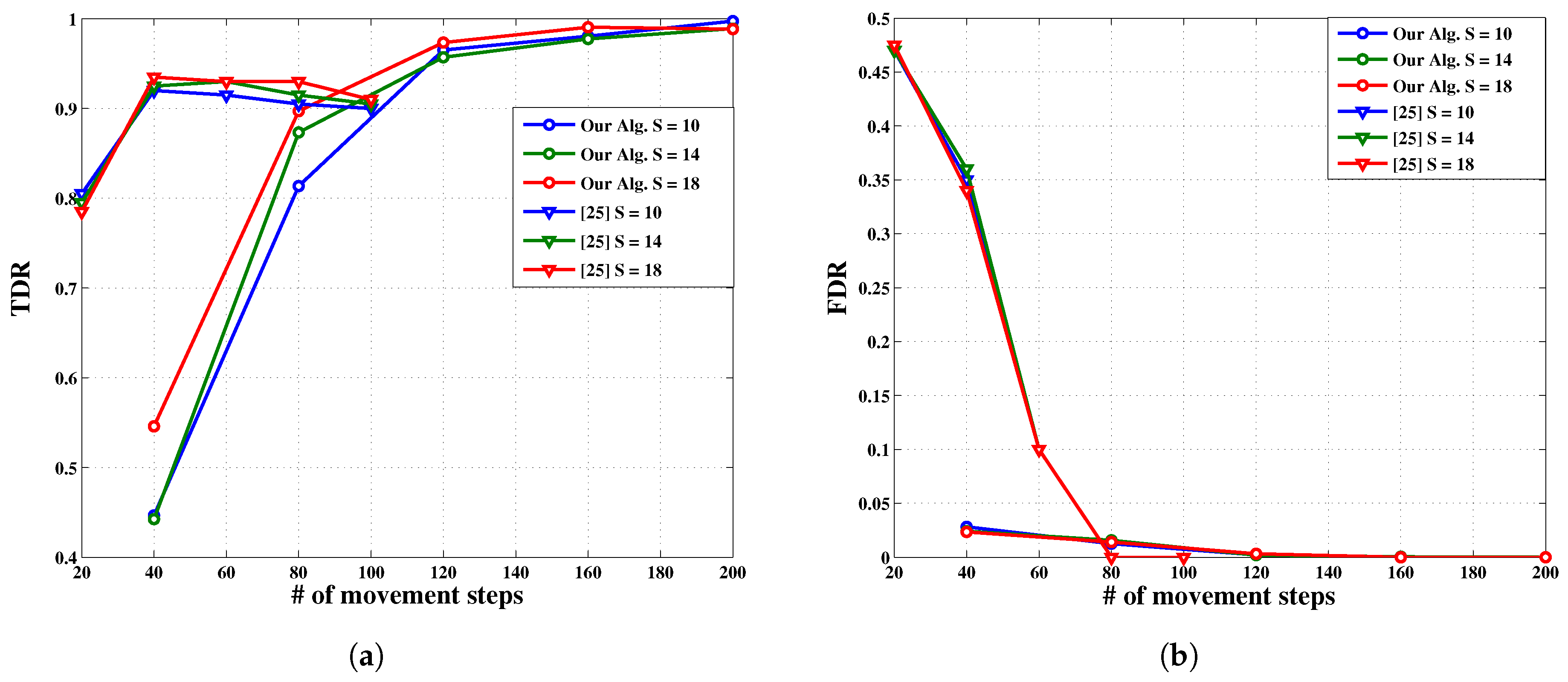
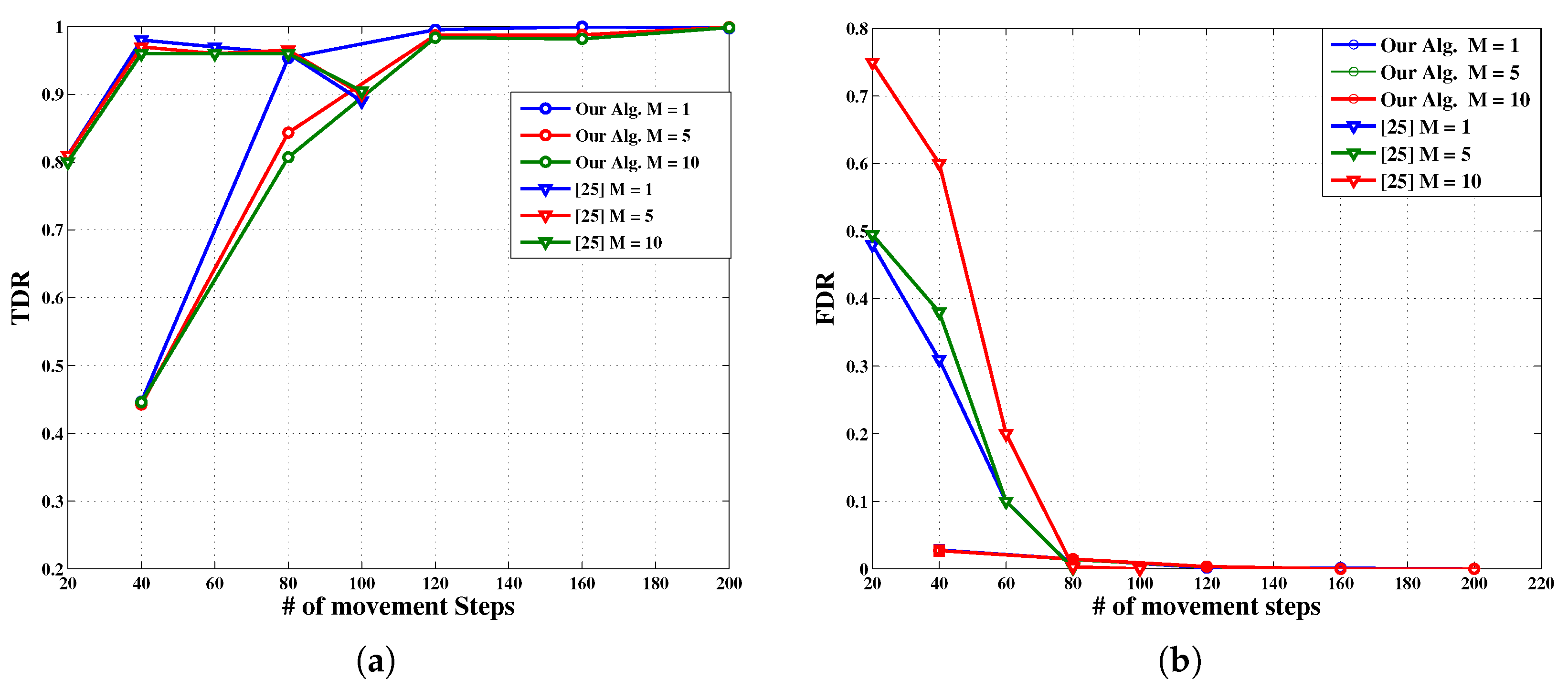
- Comparison 2: In this test we compare our algorithm with another relevant algorithm in [25]. Our algorithm uses a somewhat similar information collection strategy as in [25] while using a completely different detection rule. To make our results comparable, we adopt the same values for our simulation parameters as those in [25].
- Regarding TDR, although the detection process is slightly late in picking up due to its conservative approach (Equation (2) in step V) to somewhat compensate for erroneous receptions , it performs reliably and asymptotically better.
6. Conclusions
Author Contributions
Conflicts of Interest
Abbreviations
| WSN | Wireless Sensor Network |
| TDR | True Detection Rate |
| FDR | False Detection Rate |
| PHY | Physical |
| RSSI | Received Signal Strength Indicator |
| TDoA | Time Difference of Arrival |
| AoA | Angle of Arrival |
| IoT | Internet of Things |
| MANET | Mobile Ad hoc Network |
| PASID | Passive Ad hoc Sybil Identity Detection |
| UWB | Ultra-Wide Band |
| USAS | Unpredictable Software-based Solution |
| WD | Watchdog Node |
| SN | Sensor Node |
| MN | Malicious Node |
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayircl, E. A survey on sensor networks. IEEE Commun. Mag. 2002, 40, 102–114. [Google Scholar] [CrossRef]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Sagduyu, Y.E.X.; Berry, R.A.; Ephremides, A. Jamming Games in Wireless Networks with Incomplete Information. IEEE Commun. Mag. 2011, 49, 112–118. [Google Scholar] [CrossRef]
- Tsiropoulou, E.E.; Baras, J.S.; Papavassiliou, S.; Qu, G. On the Mitigation of Interference Imposed by Intruders in Passive RFID Networks. In Proceedings of the 7th International Conference GameSec, New York, NY, USA, 2–4 November 2016. [Google Scholar]
- Chen, X.; Makki, K.; Yen, K.; Niki, P. Sensor Network Security: A Survey. IEEE Commun. Surv. Tutor. 2009, 11, 5–73. [Google Scholar] [CrossRef]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The Sybil Attack in Sensor Networks: Analysis & Defenses. In Proceedings of the Third International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 26–27 April 2004. [Google Scholar]
- Bettstetter, C.; Resta, G.; Santi, P. The Node Distribution of the Random Waypoint Mobility Model for Wireless Ad Hoc Networks. IEEE Trans. Mob. Comput. 2003, 2, 257–269. [Google Scholar] [CrossRef]
- Ssu, K.F.; Wang, W.T.; Chang, W.C. Detecting Sybil attacks in wireless sensor networks using neighboring information. Comput Netw. 2009, 53, 3042–3056. [Google Scholar] [CrossRef]
- Seshadri, A.; Perrig, A.; Doorn, L.; Khosla, P. SWAtt: Software-based attestation for embedded devices. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 12 May 2004. [Google Scholar]
- Seshadri, A.; Perrig, A.; Doorn, V.; Khosla, P. SCUBA: Secure Code Update By Attestation in Sensor Networks. In Proceedings of the 5th ACM Workshop on Wireless Security, Los Angeles, CA, USA, 29 September 2006. [Google Scholar]
- Jin, X.; Putthapipat, P.; Pan, D.; Pissinou, N.; Kami Makki, S. Unpredictable Software-based Attestation Solution for Node Compromise Detection in Mobile WSN. In Proceedings of the Workshop on Advances in Communications and Networks, Miami, FL, USA, 6–10 December 2010. [Google Scholar]
- Borisov, N. Computational puzzles as Sybil defense. In Proceedings of the IEEE international Conference on Peer-to-Peer Computing (P2P), Cambridge, UK, 6–8 September 2006. [Google Scholar]
- Zhang, Q.; Wang, P.; Reeves, D.; Ning, P. Defending against Sybil attacks in sensor networks. In Proceedings of the 25th IEEE International Conference Distributed Computing Systems Workshops, Columbus, OH, USA, 6–10 June 2005. [Google Scholar]
- Sharmila, S.; Umamaheswari, G. Node ID based detection of Sybil attack in mobile wireless sensor network. Int. J. Electron. 2012, 100, 1441–1454. [Google Scholar] [CrossRef]
- Marti, S.; Giuli, T.J.; Lai, K.; Baker, M. migration watchdog Mitigating Routing Misbehavior in Mobile Ad Hoc Networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000. [Google Scholar]
- Sun, B.; Osborne, L.; Yang, X.; Guizani, S. Intrusion detection techniques in mobile ad hoc and wireless sensor networks. IEEE Wirel. Commun. 2013, 14, 56–63. [Google Scholar] [CrossRef]
- Douceur, J.R.; Druschel, P.; Kaashoek, M.F.; Rowstron, A. The Sybil attack. In Proceedings of the International Workshop on Peer-to-Peer Systems, Cambridge, MA, USA, 7–8 March 2002. [Google Scholar]
- Abbas, S.; Merabti, M.; Llewellyn-Jones, D.; Kifayat, K. Lightweight Sybil Attack Detection in MANETs. IEEE Syst. J. 2013, 7, 236–248. [Google Scholar] [CrossRef]
- Demirbas, M.; Song, Y. An RSSI-based scheme for Sybil attack detection in wireless networks. In Proceedings of the International Symposium on World of Wireless Mobile and Multimedia Networks, Washington, DC, USA, 26 June 2006. [Google Scholar]
- Wen, M.; Li, H.; Zheng, Y.-F. TDOA-based Sybil attack detection scheme for wireless sensor. J. Shanghai Univ. 2008, 12, 66–70. [Google Scholar] [CrossRef]
- Sarigiannidis, P.; Karapistoli, E.; Economides, A.A. Detecting Sybil Attacks in Wireless Sensor Networks using UWB Ranging-based Information. Expert Syst. Appl. 2015, 42, 7560–7572. [Google Scholar] [CrossRef]
- Li, F.; Mitial, P.; Cocsar, M.; Borisov, N. SybilControl: Practical Sybil defense with computational puzzles. In Proceedings of the 19th ACM Conference on Computer and Communications Security, Raleigh, NC, USA, 16–18 October 2012. [Google Scholar]
- Tangpong, A.; Kesidis, G.; Hsu, H.; Hurson, A. Robust Sybil Detection for MANETs. In Proceedings of the International Conference on Computer Communications and Networks (ICCCN), San Francisco, CA, USA, 3–6 August 2009. [Google Scholar]
- Piro, C.; Shields, C.; Neil Levine, B. Detecting the Sybil Attack in Mobile Ad hoc Networks. In Proceedings of the Secure-comm and Workshops, Baltimore, MD, USA, 28 August–1 September 2006. [Google Scholar]
- Jamshidi, M.; Zangeneh, E.; Esnaashari, M.; Meybodi, M. A lightweight algorithm for detecting mobile Sybil nodes in mobile wireless sensor networks. Comput. Electr. Eng. 2016, 40, 1–13. [Google Scholar] [CrossRef]
- Sobeih, A.; Hou, J.C.; Kung, L.; Ning, L.; Zhang, H.; Chen, W.; Tyan, H.; Lim, W. J-Sim: A simulation and emulation environment for wireless sensor networks. IEEE Wirel. Commun. 2006, 13, 104–119. [Google Scholar] [CrossRef]

| Parameter | Value/Fixed | Value/Variable |
|---|---|---|
| No. of normal nodes, N | 300 | |
| No. of watchdog nodes, W | 4 | |
| No. of Sybil IDs/malicious node, S | 14 | |
| No. of malicious nodes, M | 5 | |
| Max speed of nodes | 5 m/s | - |
| Topology size | 100 m × 100 m | - |
| Wireless radio range | 10 m | - |
| Simulation time step | 50 ms | - |
| Sybil threshold, | 1 | - |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almas Shehni, R.; Faez, K.; Eshghi, F.; Kelarestaghi, M. A New Lightweight Watchdog-Based Algorithm for Detecting Sybil Nodes in Mobile WSNs. Future Internet 2018, 10, 1. https://doi.org/10.3390/fi10010001
Almas Shehni R, Faez K, Eshghi F, Kelarestaghi M. A New Lightweight Watchdog-Based Algorithm for Detecting Sybil Nodes in Mobile WSNs. Future Internet. 2018; 10(1):1. https://doi.org/10.3390/fi10010001
Chicago/Turabian StyleAlmas Shehni, Rezvan, Karim Faez, Farshad Eshghi, and Manoochehr Kelarestaghi. 2018. "A New Lightweight Watchdog-Based Algorithm for Detecting Sybil Nodes in Mobile WSNs" Future Internet 10, no. 1: 1. https://doi.org/10.3390/fi10010001
APA StyleAlmas Shehni, R., Faez, K., Eshghi, F., & Kelarestaghi, M. (2018). A New Lightweight Watchdog-Based Algorithm for Detecting Sybil Nodes in Mobile WSNs. Future Internet, 10(1), 1. https://doi.org/10.3390/fi10010001