Artificial Intelligence and Algorithmic Approaches of Health Security Systems: A Review
Abstract
1. Introduction
2. Overview of Health Security Systems
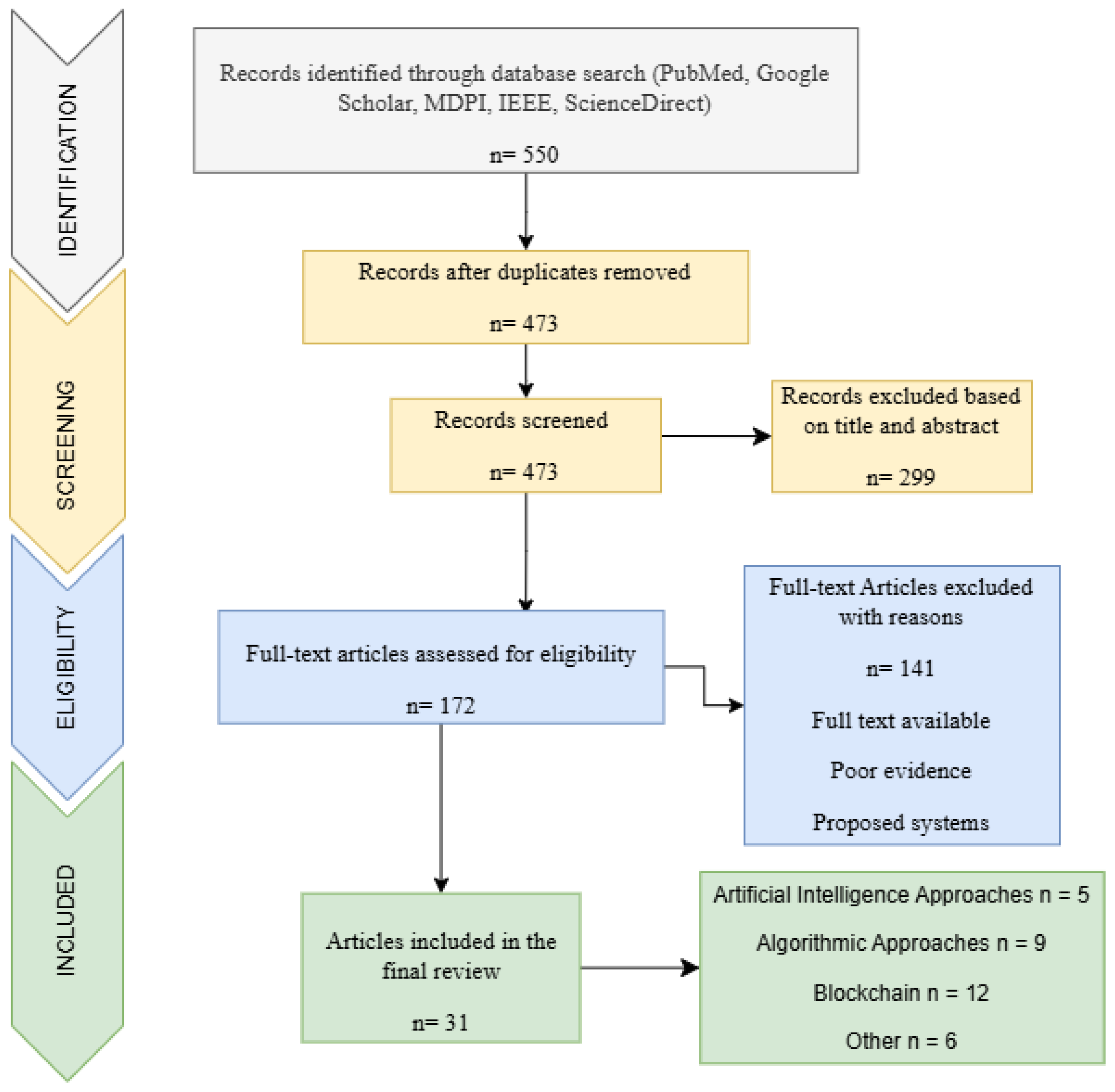
3. Materials and Methods
Inclusion and Exclusion Criteria
- Publications from 2018 to 2024.
- Studies explored healthcare system security using proven technologies, including artificial intelligence (AI), blockchain, Internet of Things (IoT), or other algorithmic and innovative data protection methods.
- Articles that demonstrated practical applications of these technologies, with experimental validation conducted under controlled test conditions.
- Studies that addressed security issues, whether related to network security or software security.
- Studies focus solely on non-healthcare applications.
- Articles lacking sufficient documentation or relying exclusively on theoretical models without experimental evaluation or practical evidence.
- Case studies or reports in which the proposed system was not tested under controlled conditions, such as simulated cyber threats.
4. Results
4.1. Security Systems Based on Blockchain Approaches
Challenges and Risks of Blockchain
4.2. Attack Types and Mitigation Strategies
- Man-in-the-middle (Middleman Attack): The attacker interferes with the communication between two parties, trying to obtain or alter information. The security of key agreement and authentication protocols is verified through the AVISPA tool [26].
- DoS (Denial of Service): Attackers flood the medical server with numerous requests, overwhelming its resources and substantially slowing down or crashing the system, which compromises the availability of medical services [31].
- Blackhole Attack: In this attack, a malicious node interferes with the flow of data by redirecting it to a blank spot and preventing proper transmission in the network [29].
- Selective Forwarding Attack: During this attack, selected data packets—often of a sensitive nature—are dropped by sensors, disrupting the information flow [29].
- Sybil Attack: A malicious node pretends to be multiple different nodes, illegally gaining access to the network and causing a security risk [29].
- Hello Flood Attack: An attack where a node sends fake Hello packets, disrupting the communication flow and confusing data transmission [29].
- Privacy Leakage: This involves the loss of sensitive data, mainly due to inadequate protection measures [15].
- Tampering (Data Tampering): Malicious users tamper with medical records, affecting the reliability of the data [15].
- Forgery: Malicious attempts to create fake medical data or transactions for fraudulent purposes [15].
- Single Point of Failure: In traditional systems, there is a central point of vulnerability that can cause total system failure [15].
- Data tampering attacks: Attackers focus on data tampering. The blockchain ensures integrity by preventing tampering [26].
- Forgery attacks: Attempts to create false data. ECC and mobile agents offer protection [26].
- Privacy violation attacks: Revealing personal data. Anonymous authentication protects the personal data of patients and professionals [26].
- Data breach: Unauthorized individuals gain access to sensitive information through attacks such as hacking or phishing, causing damage to personal and financial data [34].
- DDoS (Distributed Denial of Service): Coordinated attacks by multiple compromised devices, or a botnet, flood a system with excessive traffic, rendering it inoperative and denying service to legitimate users. This widespread disruption critically affects the availability of medical services [39].
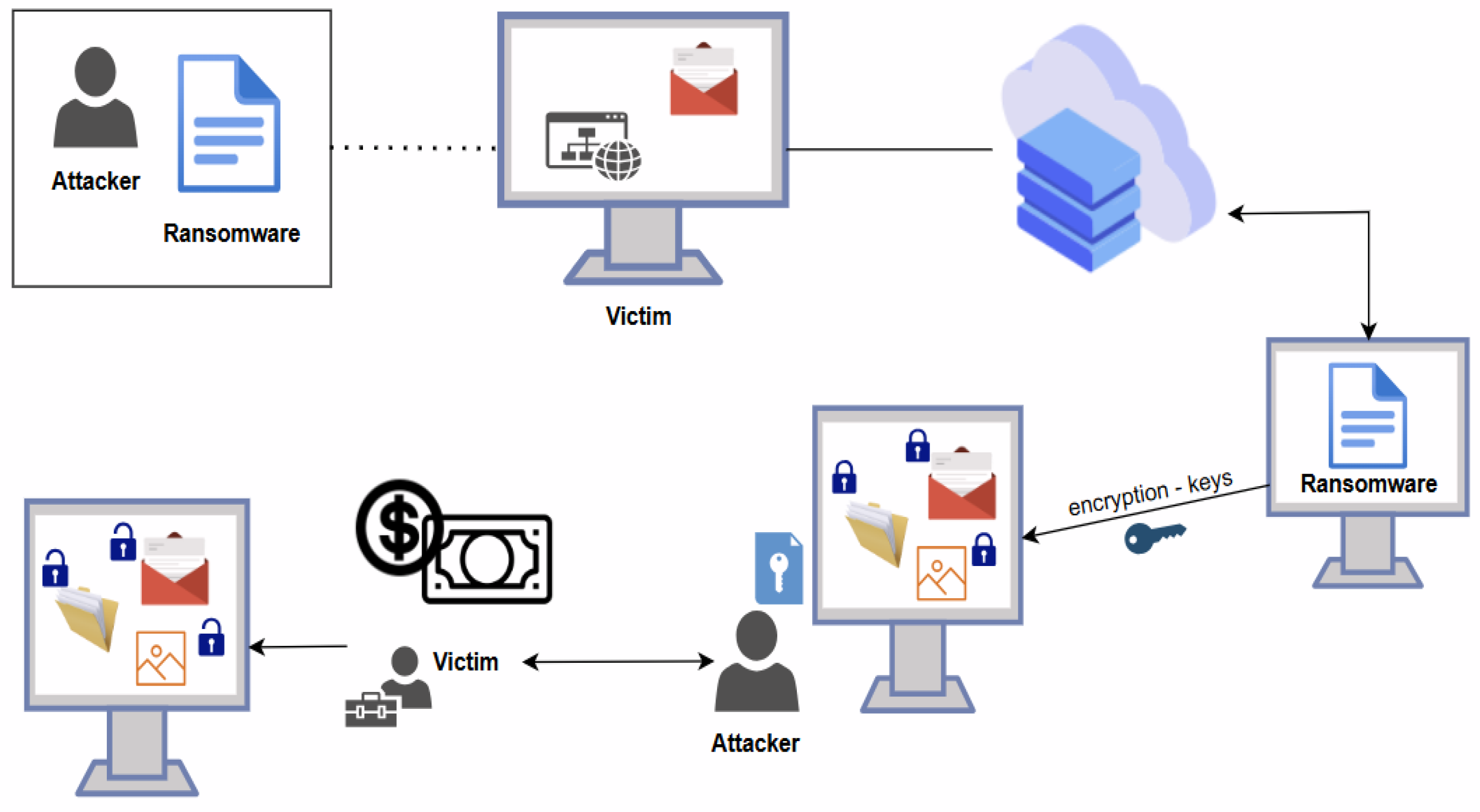
- Ransomware: A type of malware that encrypts a victim’s files, demanding a ransom payment for the decryption key. This malware exploits the critical nature of personal and business data, forcing victims to pay to regain access. Ransomware attacks can severely disrupt operations and result in substantial financial and data losses, underlining the importance of robust cybersecurity measures to protect sensitive information [40].
4.3. Ransomware
5. Discussion and Conclusions
6. Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Almalawi, A.; Khan, A.I.; Alsolami, F.; Abushark, Y.B.; Alfakeeh, A.S. Managing Security of Healthcare Data for a Modern Healthcare System. Sensors 2023, 23, 3612. [Google Scholar] [CrossRef] [PubMed]
- Javaid, M.; Haleem, A.; Singh, R.P.; Suman, R. Towards Insighting Cybersecurity for Healthcare Domains: A Comprehensive Review of Recent Practices and Trends. Cyber Secur. Appl. 2023, 1, 100016. [Google Scholar] [CrossRef]
- Lee, I. Analyzing Web Descriptions of Cybersecurity Breaches in the Healthcare Provider Sector: A Content Analytics Research Method. Comput. Secur. 2023, 129, 103185. [Google Scholar] [CrossRef]
- Mariettou, S.; Koutsojannis, C.; Triantafillou, V. Security Systems in Greek Health Care Institutions: A Scoping Review Towards an Effective Benchmarking Approach. In Proceedings of the International Conferences e-Society 2024 and Mobile Learning, Porto, Portugal, 9–11 March 2024; pp. 53–60. [Google Scholar]
- Coutinho, B.; Ferreira, J.; Yevseyeva, I.; Basto-Fernandes, V. Integrated Cybersecurity Methodology and Supporting Tools for Healthcare Operational Information Systems. Comput. Secur. 2023, 129, 103189. [Google Scholar] [CrossRef]
- Angraal, S.; Krumholz, H.M.; Schulz, W.L. Blockchain Technology. Circ. Cardiovasc. Qual. Outcomes 2017, 10, e003800. [Google Scholar] [CrossRef] [PubMed]
- Azzaoui, A.E.; Chen, H.; Kim, S.H.; Pan, Y.; Park, J.H. Blockchain-Based Distributed Information Hiding Framework for Data Privacy Preserving in Medical Supply Chain Systems. Sensors 2022, 22, 1371. [Google Scholar] [CrossRef]
- Riplinger, L.; Piera-Jiménez, J.; Dooling, J.P. Patient Identification Techniques—Approaches, Implications, and Findings. Yearb. Med. Inform. 2020, 29, 81–86. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Sangaiah, A.K.; Li, X.; Wu, F. An Enhanced Three Factor Based Authentication Protocol Using Wireless Medical Sensor Networks for Healthcare Monitoring. J. Ambient Intell. Humaniz. Comput. 2018, 15, 1165–1186. [Google Scholar] [CrossRef]
- Intrusion Detection System for Healthcare Systems Using Medical and Network Data: A Comparison Study. Available online: https://ieeexplore.ieee.org/document/9109651 (accessed on 3 September 2024).
- Kanagala, P. Effective Cyber Security System to Secure Optical Data Based on Deep Learning Approach for Healthcare Application. Optik 2022, 272, 170315. [Google Scholar] [CrossRef]
- Sardar, A.; Umer, S.; Rout, R.K.; Wang, S.-H.; Tanveer, M. A Secure Face Recognition for IoT-Enabled Healthcare System. ACM Trans. Sens. Netw. 2022, 19, 1–23. [Google Scholar] [CrossRef]
- Natarajan, R.; Lokesh, G.H.; Flammini, F.; Premkumar, A.; Venkatesan, V.K.; Gupta, S.K. A Novel Framework on Security and Energy Enhancement Based on Internet of Medical Things for Healthcare 5.0. Infrastructures 2023, 8, 22. [Google Scholar] [CrossRef]
- Ravi, V. Deep Learning-Based Network Intrusion Detection in Smart Healthcare Enterprise Systems. Multimed. Tools Appl. 2023, 83, 39097–39115. [Google Scholar] [CrossRef]
- Tariq, N.; Qamar, A.; Asim, M.; Khan, F.A. Blockchain and Smart Healthcare Security: A Survey. Procedia Comput. Sci. 2020, 175, 615–620. [Google Scholar] [CrossRef]
- Puri, V.; Kataria, A.; Sharma, V. Artificial Intelligence-powered Decentralized Framework for Internet of Things in Healthcare 4.0. Trans. Emerg. Telecommun. Technol. 2021, 35, e4245. [Google Scholar] [CrossRef]
- Abid, A.; Cheikhrouhou, S.; Kallel, S.; Tari, Z.; Jmaiel, M. A Smart Contract-Based Access Control Framework for Smart Healthcare Systems. Comput. J. 2022, 67, 407–422. [Google Scholar] [CrossRef]
- Sharma, P.; Namasudra, S.; Crespo, R.G.; Parra-Fuente, J.; Trivedi, M.C. EHDHE: Enhancing Security of Healthcare Documents in IoT-Enabled Digital Healthcare Ecosystems Using Blockchain. Inf. Sci. 2023, 629, 703–718. [Google Scholar] [CrossRef]
- Selvarajan, S.; Mouratidis, H. A Quantum Trust and Consultative Transaction-Based Blockchain Cybersecurity Model for Healthcare Systems. Sci. Rep. 2023, 13, 7107. [Google Scholar] [CrossRef]
- Rani, S.; Chauhan, M.; Kataria, A.; Khang, A. IoT Equipped Intelligent Distributed Framework for Smart Healthcare Systems. In Studies in Big Data; Springer: Berlin/Heidelberg, Germany, 2023; pp. 97–114. [Google Scholar]
- Akinola, O.; Akinola, A.; Oyekan, B.; Oyerinde, O.; Adebiyi, H.F.; Sulaimon, B. Blockchain-Enabled Security Solutions for Medical Device Integrity and Provenance in Cloud Environments. Int. J. Sci. Res. Mod. Technol. 2024, 3, 123–135. [Google Scholar] [CrossRef]
- Mohammed, M.A.; Lakhan, A.; Zebari, D.A.; Ghani, M.K.A.; Marhoon, H.A.; Abdulkareem, K.H.; Nedoma, J.; Martinek, R. Securing Healthcare Data in Industrial Cyber-Physical Systems Using Combining Deep Learning and Blockchain Technology. Eng. Appl. Artif. Intell. 2024, 129, 107612. [Google Scholar] [CrossRef]
- An AOI-Aware Data Transmission Algorithm in Blockchain-Based Intelligent Healthcare Systems. Available online: https://ieeexplore.ieee.org/document/10433851 (accessed on 3 September 2024).
- Wu, C.; Tang, Y.M.; Kuo, W.T.; Yip, H.T.; Chau, K.Y. Healthcare 5.0: A Secure and Distributed Network for System Informatics in Medical Surgery. Int. J. Med. Inform. 2024, 186, 105415. [Google Scholar] [CrossRef]
- Mallick, S.R.; Lenka, R.K.; Tripathy, P.K.; Rao, D.C.; Sharma, S.; Ray, N.K. A Lightweight, Secure, and Scalable Blockchain-Fog-IoMT Healthcare Framework with IPFS Data Storage for Healthcare 4.0. SN Comput. Sci. 2024, 5, 198. [Google Scholar] [CrossRef]
- Idrissi, H.; Palmieri, P. Agent-Based Blockchain Model for Robust Authentication and Authorization in IoT-Based Healthcare Systems. J. Supercomput. 2023, 80, 6622–6660. [Google Scholar] [CrossRef]
- Chakraborty, C.; Nagarajan, S.M.; Devarajan, G.G.; Ramana, T.V.; Mohanty, R. Intelligent AI-Based Healthcare Cyber Security System Using Multi-Source Transfer Learning Method. ACM Trans. Sens. Netw. 2023. [Google Scholar] [CrossRef]
- Banu, S.A.; Al-Alawi, A.I.; Padmaa, M.; Priya, P.S.; Thanikaiselvan, V.; Amirtharajan, R. Healthcare with Datacare—A Triangular DNA Security. Multimed. Tools Appl. 2023, 83, 21153–21170. [Google Scholar] [CrossRef]
- Jabeen, T.; Jabeen, I.; Ashraf, H.; Jhanjhi, N.Z.; Yassine, A.; Hossain, M.S. An Intelligent Healthcare System Using IoT in Wireless Sensor Network. Sensors 2023, 23, 5055. [Google Scholar] [CrossRef]
- Anand, A.; Bedi, J.; Aggarwal, A.; Khan, M.A.; Rida, I. Authenticating and Securing Healthcare Records: A Deep Learning-Based Zero Watermarking Approach. Image Vis. Comput. 2024, 145, 104975. [Google Scholar] [CrossRef]
- Aldosary, A.; Tanveer, M. PAAF-SHS: PUF and Authenticated Encryption Based Authentication Framework for the IoT-Enabled Smart Healthcare System. Internet Things 2024, 26, 101159. [Google Scholar] [CrossRef]
- Gopalakrishnan, N.R.; Kumar, N.R.M.S. Cloud Security System for ECG Transmission and Monitoring Based on Chaotic Logistic Maps. J. Adv. Res. Appl. Sci. Eng. Technol. 2024, 39, 1–18. [Google Scholar] [CrossRef]
- Wenhua, Z.; Hasan, M.K.; Jailani, N.B.; Islam, S.; Safie, N.; Albarakati, H.M.; Aljohani, A.; Khan, M.A. A Lightweight Security Model for Ensuring Patient Privacy and Confidentiality in Telehealth Applications. Comput. Hum. Behav. 2024, 153, 108134. [Google Scholar] [CrossRef]
- Pichandi, K.V.; Janarthanan, V.; Annamalai, T.; Arumugam, M. Enhancing Healthcare in the Digital Era: A Secure e-Health System for Heart Disease Prediction and Cloud Security. Expert Syst. Appl. 2024, 255, 124479. [Google Scholar] [CrossRef]
- Saini, K.K.; Kaur, D.; Kumar, D.; Kumar, B. An Efficient Three-Factor Authentication Protocol for Wireless Healthcare Sensor Networks. Multimed. Tools Appl. 2024, 83, 63699–63721. [Google Scholar] [CrossRef]
- Nadhan, A.S.; Jacob, I.J. Enhancing Healthcare Security in the Digital Era: Safeguarding Medical Images with Lightweight Cryptographic Techniques in IoT Healthcare Applications. Biomed. Signal Process. Control 2024, 88, 105511. [Google Scholar] [CrossRef]
- Clemente-Lopez, D.; De Jesus Rangel-Magdaleno, J.; Muñoz-Pacheco, J.M. A Lightweight Chaos-Based Encryption Scheme for IoT Healthcare Systems. Internet Things 2023, 25, 101032. [Google Scholar] [CrossRef]
- Abuasal, S.; Alsarayra, K.; Alyabroodie, Z. Designing a Standard-Based Approach for Security of Healthcare Systems. J. Stat. Appl. Probab. 2024, 13, 419–434. [Google Scholar] [CrossRef]
- Snehi, M.; Bhandari, A. Vulnerability Retrospection of Security Solutions for Software-Defined Cyber–Physical System against DDoS and IoT-DDoS Attacks. Comput. Sci. Rev. 2021, 40, 100371. [Google Scholar] [CrossRef]
- Ali, A. Ransomware: A Research and a Personal Case Study of Dealing with This Nasty Malware. Available online: https://www.informingscience.org/Publications/3707 (accessed on 3 October 2024).
- Patyal, M.; Sampalli, S.; Qiang, Y.; Rahman, M. Multi-Layered Defense Architecture against Ransomware. Int. J. Bus. Cyber Secur. 2017, 1, 2. [Google Scholar]
- Qartah, A.A. Evolving Ransomware Attacks on Healthcare Providers. Master’s Thesis, Utica College, Utica, NY, USA, 2020. [Google Scholar] [CrossRef]
- Treadwell, G.W. Preventing Employee Frauds in Small Businesses with Low-Cost Methods. J. Bus. Account. 2021, 14, 3–15. [Google Scholar]
| Author(s) | Security System | Synopsis | Mitigated Attacks | Evidence Type |
|---|---|---|---|---|
| [1] | LRO-S encryption method | It combines lion and remora optimization with serpent encryption to secure medical data, offering enhanced protection against cyber-attacks and privacy breaches, with improved encryption/decryption time and performance compared to existing methods. | Privacy Breaches, Unauthorized Access | Cryptographic, Algorithmic, Mathematical |
| [9] | WMSNs (Wireless Medical Sensor Networks) | It operates using three-factor authentication to securely verify remote users in WMSN environments. Additionally, it has been validated using Burrows–Abadi–Needham (BAN) logic and the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool. | Unauthorized Access, Offline Password Guessing Attacks | Simulation |
| [10] | IDS (Intrusion Detection System) | The proposed IDS is designed to detect network intrusions while minimizing the load on resource-constrained sensors, enhancing security without overburdening limited-capacity devices. | Man-in-the-middle | Empirical |
| [11] | Μodified deep learning approach based on Cyber–Physical Systems (CPS) | The system uses deep learning and CPS for the secure processing of IoT data, protecting against DoS and DDoS attacks, with 98.2% accuracy and improved performance compared to existing models such as LSTM and CNN. | DoS (Denial of Service), DDoS (Distributed Denial of Service) | Algorithmic, Performance |
| [12] | BioCryptosystem | It enhances the security of biometric data by using FaceHashing with BioCrypto-Circuit and BioCrypto-Protection techniques, offering robust protection against external attacks and misuse. | Unauthorized Access | Empirical, Algorithmic |
| [13] | Energy-Efficient Routing Protocol (ECC-EERP) | This protocol enhances security and energy efficiency in Internet of Medical Things (IoMT) applications by employing elliptic curve cryptography for secure data transmission while minimizing energy consumption and communication overload. | Empirical, Algorithmic | |
| [14] | N-IDS (Network-Intrusion Detection System) | This system detects intrusions and attacks in a smart healthcare system using a deep learning approach that combines CNN (Convolutional Neural Networks) and LSTM (Long Short-Term Memory) to extract optimal features from network data and detect attacks with high | Empirical, Algorithmic | |
| [15,16,17,18,19,20,21,22,23,24,25,26] | Blockchain | Modern security systems enhance medical data privacy, integrity, and access control in healthcare, enabling secure management of patient records, IoT (Internet of Things) devices, and remote healthcare systems. | Man-in-the-middle, DDoS (Distributed Denial of Service), Single Point of Failure, Data Tampering, Unauthorized Access, Tampering Attacks, Data Breach, Counterfeit Product Attacks | Survey, Algorithmic, Statistical, Cryptographic |
| [27] | QP-CNN (Quantum Photonic Convolutional Neural Network) | The QP-CNN enhances the security of AI-based healthcare systems by utilizing quantum photonic computation for the encryption and protection of patient data during transmission and storage. The study demonstrates its effectiveness through simulations, achieving high accuracy and various performance metrics. | DoS (Denial of Service), Stolen Device, Untraceability/Anonymity, Replay, Man-in-the-Middle, Impersonation, Temporary Secret Leakage Attack | Empirical |
| [27] | CMTL (Centralized Multi-Source Transfer Learning) | The “EoT-TL Healthcare” system combines edge computing, Internet of Things, blockchain, and cloud technologies for cyberattack detection and data security optimization in healthcare, with high performance evaluated using three datasets. | DoS (Denial of Service), DDoS (Distributed Denial of Service), Malware, Injection, Man-in-the-Middle | Empirical, Mathematical, Algorithmic |
| [28] | Cryptosystem with SHA-256 and Hyper Chaotic Multi Attractors Chen System | It uses DNA encoding, SHA-256, and HCMACS for secure medical image encryption, protecting statistical, differential, and brute-force attacks, while ensuring the confidentiality, integrity, and availability of data. | Statistical, Differential, Chosen-Plaintext | Algorithmic, Simulation, Cryptographic |
| [29] | Encryption technique | It uses genetic encryption for the secure transmission of health data via wireless sensors while incorporating an authentication process for user verification and preventing malicious attacks. | Blackhole, Selective Forwarding, Sybil, Hello Flood | Algorithmic, Simulation |
| [30] | Zero-watermarking | Uses deep learning and specialized image processing techniques to secretly embed a distinguishing mark in medical images. This prevents unauthorized access or distribution, ensuring the protection and integrity of healthcare records. | Signal Interference, Spatial Manipulation, Communication Protocol Vulnerabilities | Algorithmic, Simulation, Cryptographic |
| [31] | PAAF-SHS (Physical Unclonable Authentication Function-Smart Healthcare Systems) | The PAAF-SHS provides secure encrypted communication between users and medical servers using mutual authentication and PUF technology. | Stolen Device, DoS (Denial of Service), Replay Attack, Man-in-the-Middle, Phishing, Impersonation, Key Compromise, Insider Threats | Algorithmic, Simulation, Cryptographic |
| [32] | CLM-based ECG Encryption System | The system utilizes the Chaotic Logistic Map (CLM) and fingerprint data to encrypt ECG signals, thereby ensuring secure transmission over the internet. | Noise-based attacks, Hacking attacks | Mathematical, Algorithmic |
| [33] | Encryption Framework for Secure Telehealth and Electronic Health Records (EHR) | The system utilizes ECG signals and a lightweight encryption algorithm to securely transmit electronic health records (EHR) in telehealth applications, ensuring enhanced data privacy, confidentiality, and access control. | - | Algorithmic, Simulation, Cryptographic |
| [34] | IEDF (Intelligent Encryption and Decryption Framework) | It combines the Advanced Encryption Standard (AES), Data Encryption Standard (DES), Rivest–Shamir–Adleman (RSA), and Modified Blowfish (MBF) algorithms for cloud data security, using Automatic Sequence Cryptography (ASC) for efficient and secure data block encryption. | Data Breaches | Algorithmic, Simulation |
| [35] | WSNs (Wireless Healthcare Sensor Networks) | This protocol enhances the security of wireless sensor networks used in healthcare by implementing a three-factor authentication strategy that incorporates user identity, password, and biometric data. It ensures robust mutual authentication and protects against various potential attacks. Formally verified using the ProVerif tool. | User Impersonation, Offline Password Guessing Attack, Insider Attack, Device Stolen, GWN Bypassing Attack, DoS (Denial of service), | Algorithmic, Simulation |
| [36] | Image Encryption Framework | The Deep Learning-Based Image Encryption Framework employs ResNet-50 to secure medical images through encryption and decryption, effectively addressing cyber threats and ensuring the confidentiality and integrity of sensitive patient data. | Unauthorized Access, Data Breaches, DoS (Denial of Service), Impersonation Attacks, Replay Attacks | Algorithmic, Simulation, Cryptographic |
| [37] | Chaos-Based Lightweight Encryption Scheme | Its 4-scroll chaotic attractor securely encrypts health data, particularly from wearable devices. It ensures confidentiality and integrity while maintaining real-time processing. The method has demonstrated strong resistance to known and chosen plaintext attacks, supported by a large key space and adequate throughput. | Unauthorized Access, Data Breaches, Known-Plaintext, Chosen-Plaintext Attacks | Algorithmic, Simulation, Cryptographic |
| [38] | Standard-Based Approach | It utilizes standards such as COSMIC ISO/IEC 19761 to design a secure healthcare system architecture. This method combines system and software security requirements, employing features like access control, data encryption, and auditability to mitigate vulnerabilities and protect against unauthorized access. | Unauthorized Access, Data Breaches, Ransomware, Tampering, Data Corruption | Simulation |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mariettou, S.; Koutsojannis, C.; Triantafillou, V. Artificial Intelligence and Algorithmic Approaches of Health Security Systems: A Review. Algorithms 2025, 18, 59. https://doi.org/10.3390/a18020059
Mariettou S, Koutsojannis C, Triantafillou V. Artificial Intelligence and Algorithmic Approaches of Health Security Systems: A Review. Algorithms. 2025; 18(2):59. https://doi.org/10.3390/a18020059
Chicago/Turabian StyleMariettou, Savina, Constantinos Koutsojannis, and Vassilios Triantafillou. 2025. "Artificial Intelligence and Algorithmic Approaches of Health Security Systems: A Review" Algorithms 18, no. 2: 59. https://doi.org/10.3390/a18020059
APA StyleMariettou, S., Koutsojannis, C., & Triantafillou, V. (2025). Artificial Intelligence and Algorithmic Approaches of Health Security Systems: A Review. Algorithms, 18(2), 59. https://doi.org/10.3390/a18020059







