Adaptive Authentication Protocol Based on Zero-Knowledge Proof
Abstract
:1. Introduction
- Roadside Units (RSU);
- On Board Unit (OBU);
- Certificate Authority (CA);
- Service Provider (SP).
- The protocol should have high cryptographic strength without the use of symmetric and asymmetric ciphers, with minimal time spent on its execution;
- The protocol should ensure the confidentiality of the vehicle’s route;
- The protocol should have a mechanism that allows the vehicle’s owner to change the level of confidentiality depending on the intensity of traffic.
Our Impact
- Based on the properties described above, an authentication protocol has been developed that can adapt its characteristics to the intensity of traffic on the road. Its basis is a zero-knowledge authentication protocol (ZKAP), which will ensure the high confidentiality of the route and anonymity of the vehicle owner. At the same time, this protocol spent minimal time on vehicle identification compared to other ZKAPs, which allows us to increase the volume of traffic and transmit useful information between OBUs and RSUs.
- A mechanism has been developed that allows the owner of the vehicle to change the parameters of the authentication protocol. If the traffic intensity on the road is low, then the OBU uses a maximal level of confidentiality. The vehicle’s owner reduces the level of confidentiality to a minimal value if the amount of network traffic between OBUs and RSUs increases in response to greater traffic intensity on the road. Since there is no exchange of useful information during OBU and RSU authentication, a reduction in the level of confidentiality reduces the time needed to determine the status of the vehicle. This will lead to an increase in the amount of transmitted useful information.
2. Analysis of Authentication Protocols Used to Ensure Confidentiality in VANET
3. Zero-Knowledge Authentication Protocols: Advantages and Disadvantages
4. ZKAP Using Session Keys
5. Development of a Scheme for Adapting the Authentication Protocol to the Road Traffic Intensity
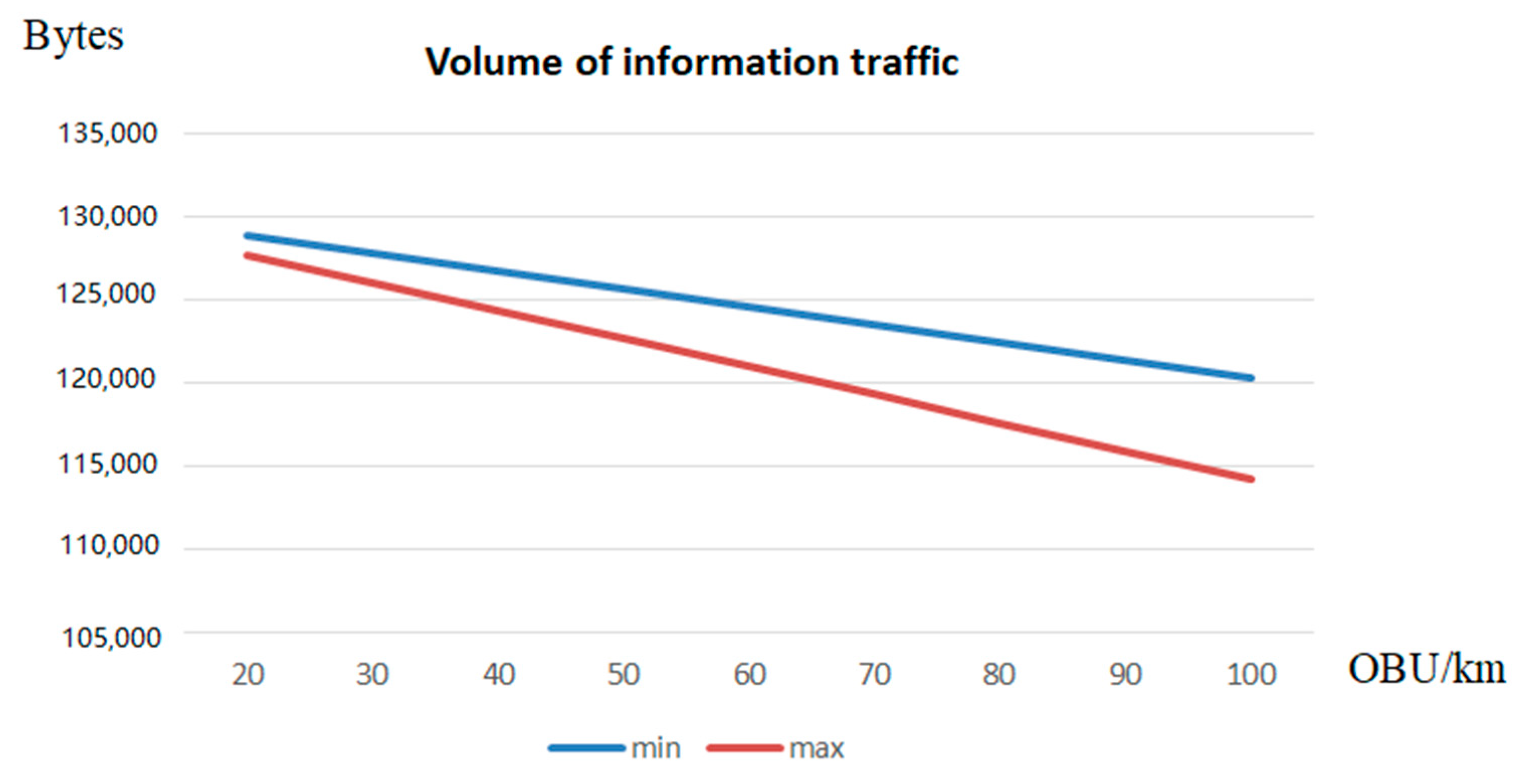
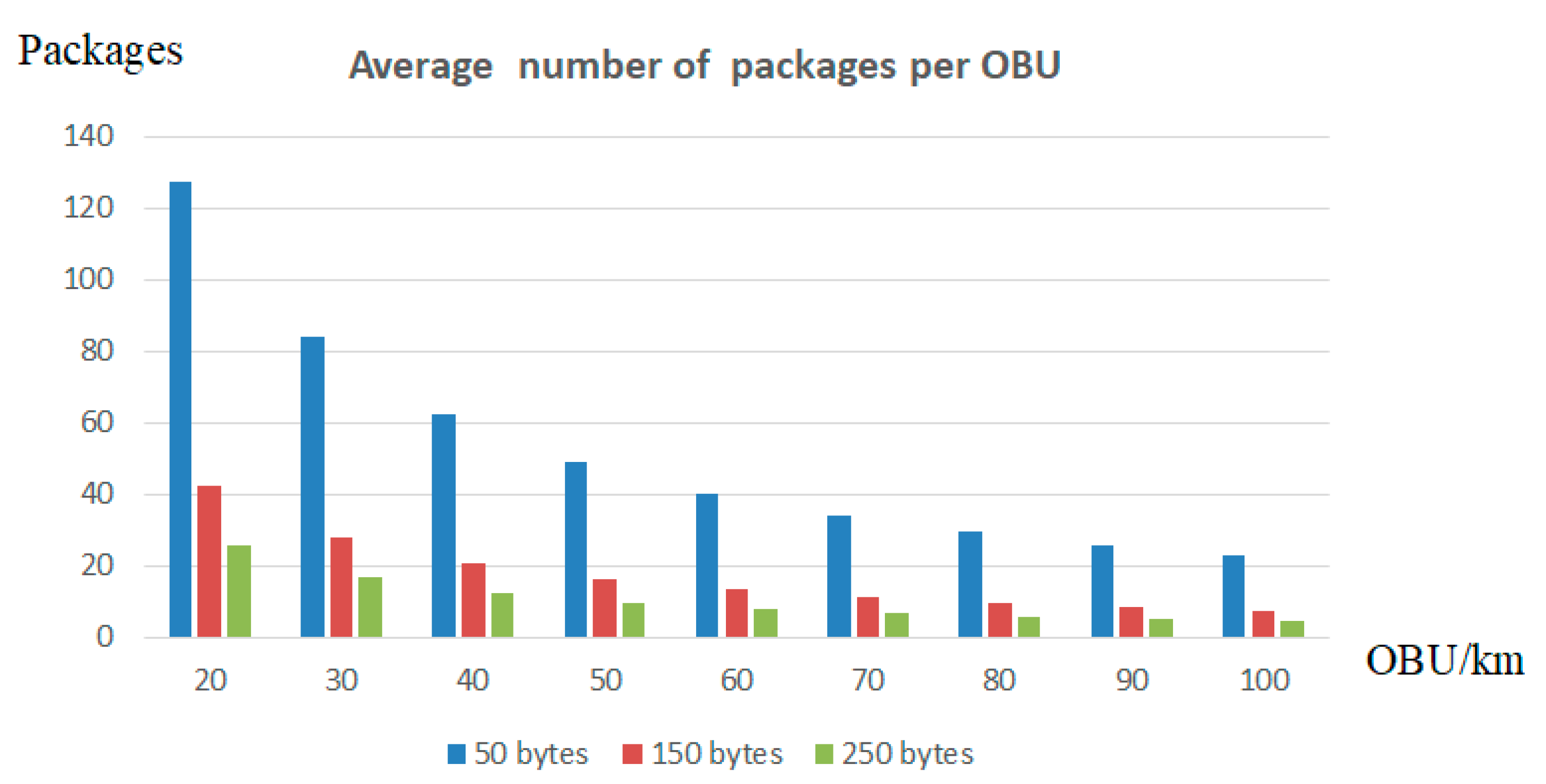
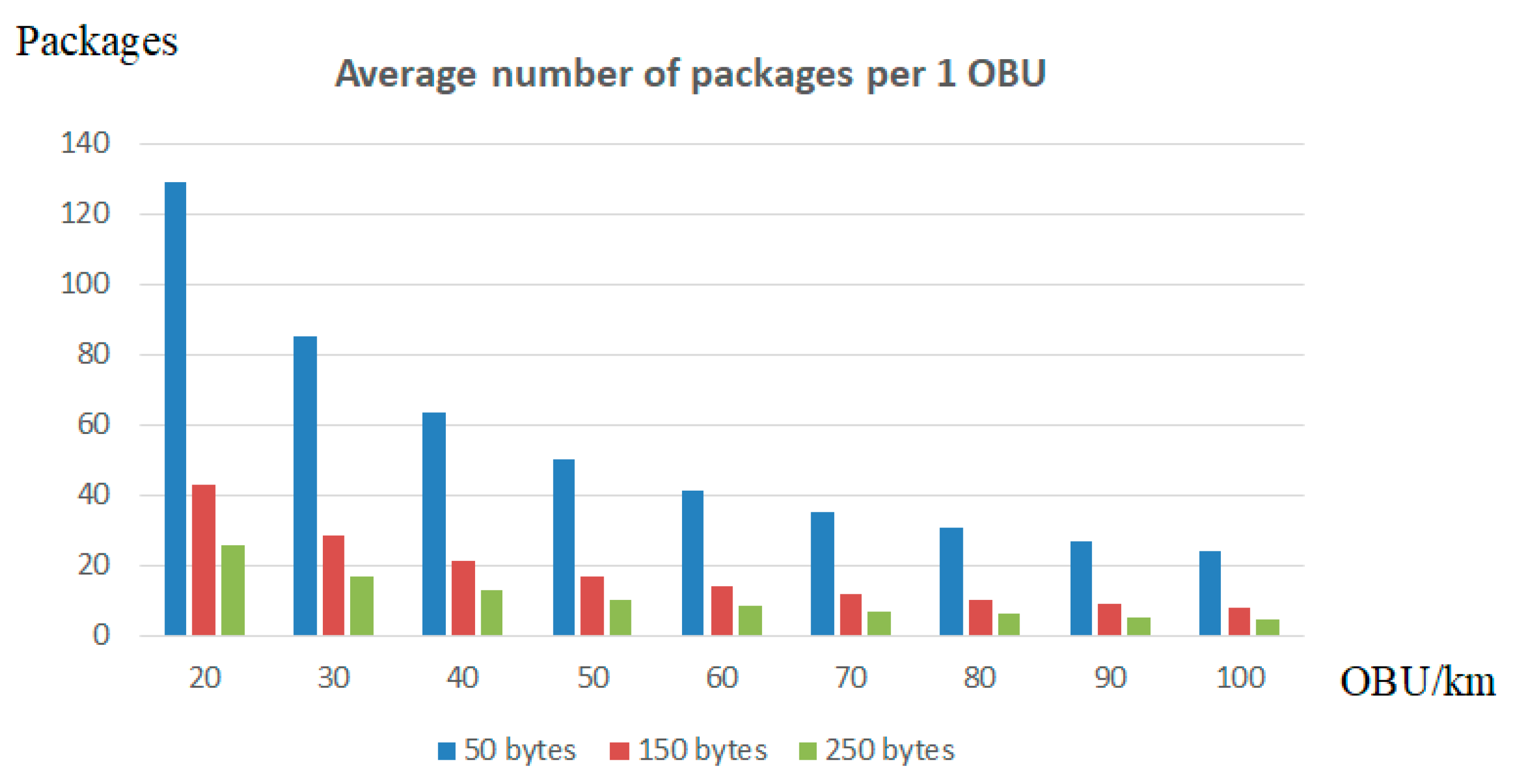
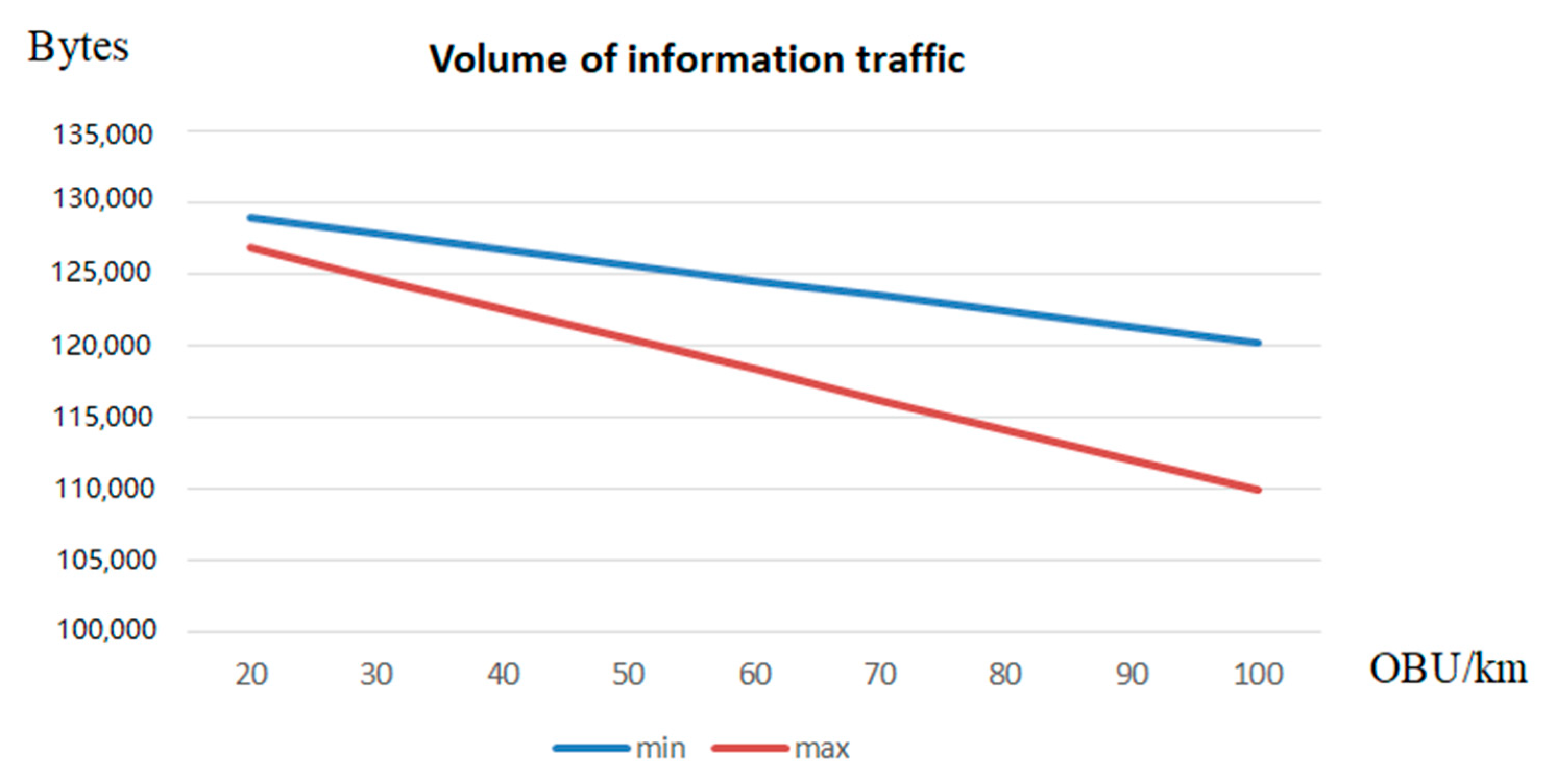
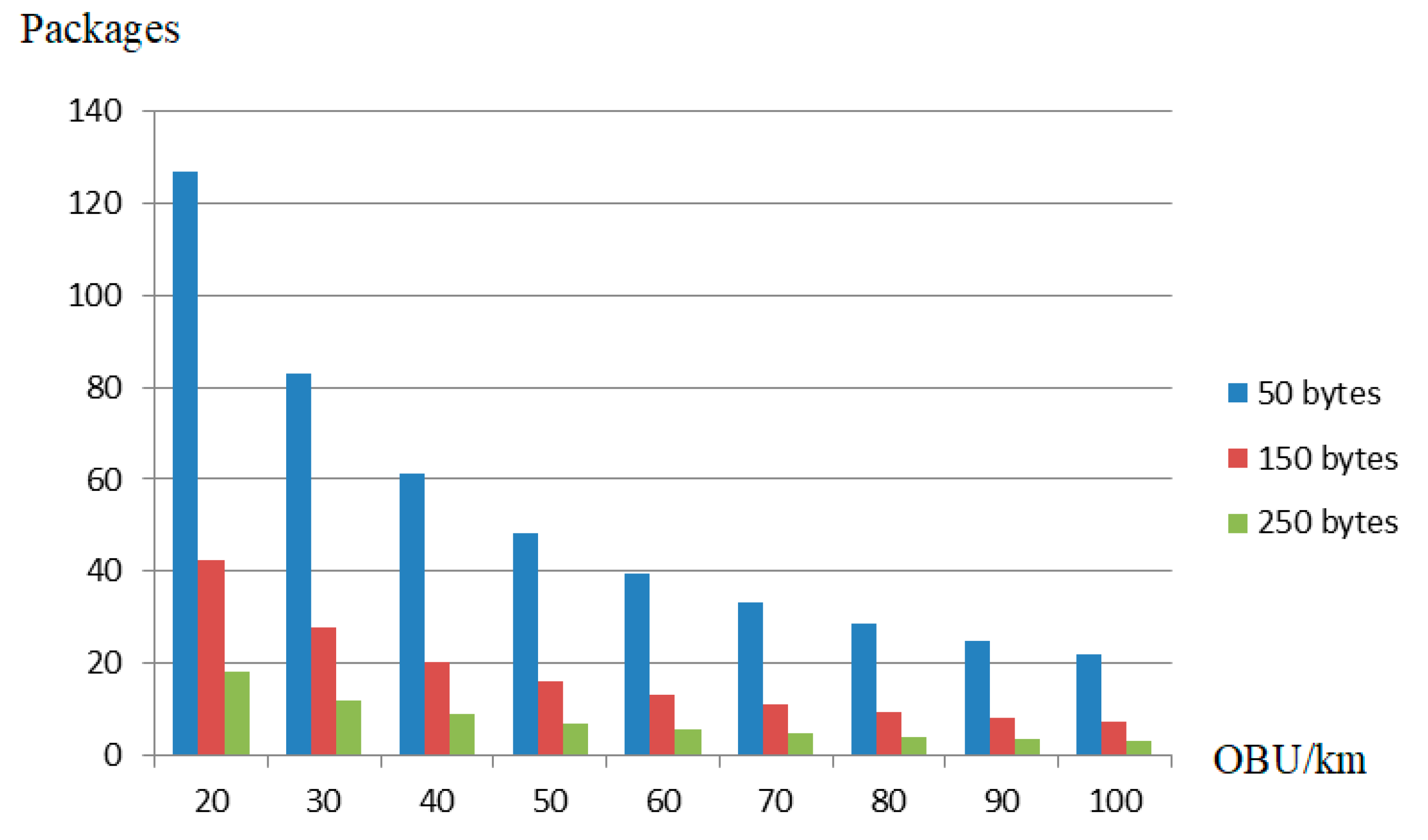
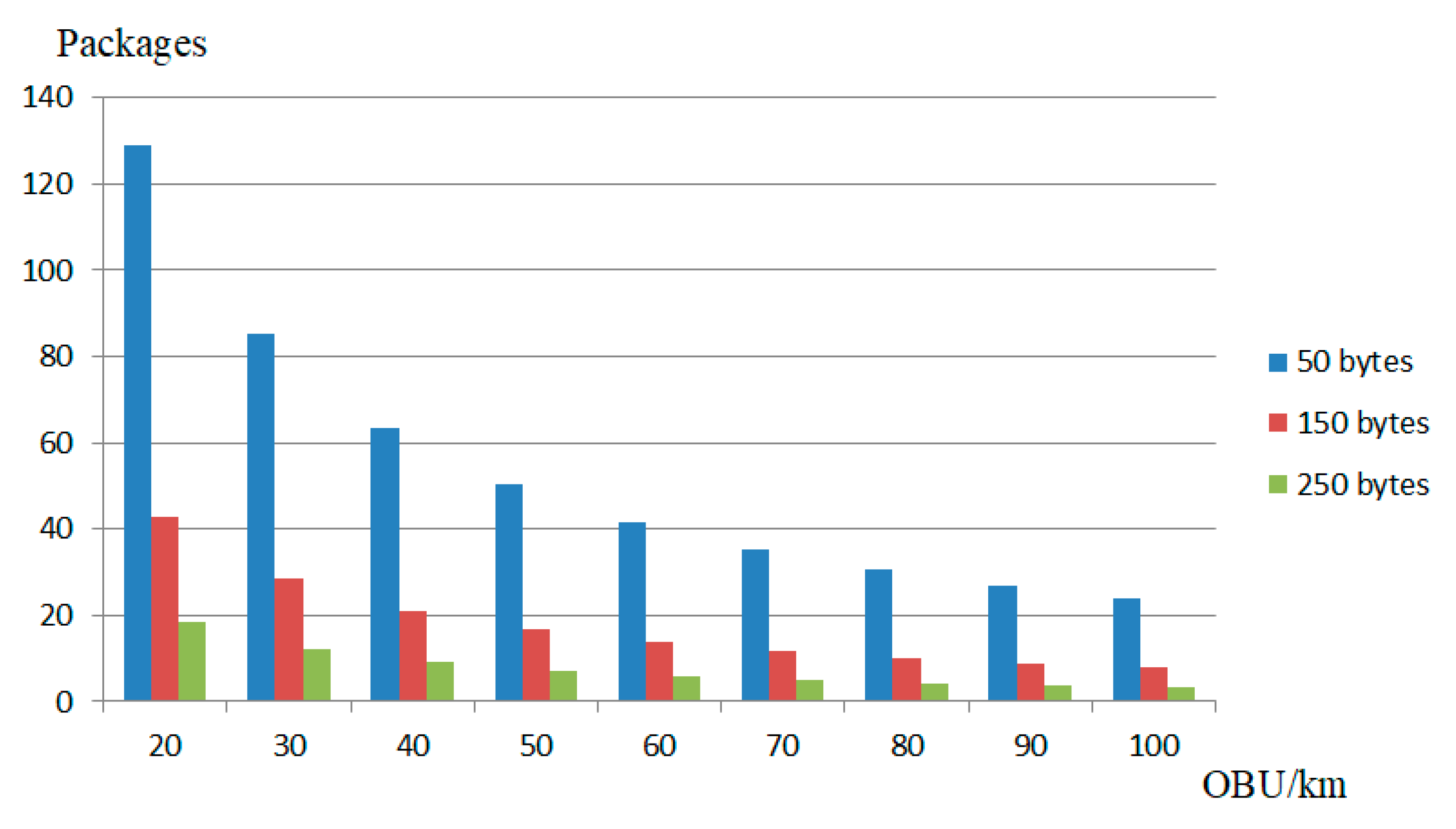
6. Analysis of the Results of the Conducted Research
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- OneWeb. Available online: https://oneweb.net/ (accessed on 25 October 2021).
- Henri, Y. The OneWeb Satellite System. In Handbook of Small Satellites; Springer: Cham, Switzerland, 2020; pp. 1–10. [Google Scholar]
- Debiao, H.; Sherali, Z. An Analysis of RFID Authentication Schemes for Internet of Things in Healthcare Environment Using Elliptic Curve Cryptography. IEEE Internet Things J. 2014, 2, 72–83. [Google Scholar]
- Liu, Z.; Zhang, W.; Wu, C. A Lightweight Code-Based Authentication Protocol for RFID Systems. In Proceedings of the International Conference Applications and Techniques Information Security, Beijing, China, 4–6 November 2015; Volume 557, pp. 114–128. [Google Scholar]
- Srinivas, J.; Ashok, K.D.; Athanasios, V.V. Designing Secure Lightweight Blockchain-Enabled RFID-Based Authentication Protocol for Supply Chains in 5G Mobile Edge Computing Environment. IEEE Trans. Ind. Inform. 2020, 16, 7081–7093. [Google Scholar]
- Michail, S.; Ming, T.O.; Ravivarma, V.S.; Junya, N.; Ren, O.; Jing, H.K. Ultralightweight Mutual Authentication RFID Protocol for Blockchain Enabled Supply Chains. IEEE Access. 2019, 7, 7273–7285. [Google Scholar]
- Xiong, C. Secured System Architecture for the Internet of Things Using a Two Factor Authentication Protocol; University of Ottawa: Ottawa, ON, Canada, 2020; p. 144. [Google Scholar]
- Kang, J.; Park, G.; Park, J.H. Design of secure authentication scheme between devices based on zero-knowledge proofs in home automation service environments. J. Supercomput. 2016, 72, 4319–4336. [Google Scholar] [CrossRef]
- Soewito, B.; Marcellinus, Y. IoT security system with modified Zero Knowledge Proof algorithm for authentication. Egypt. Inform. J. 2021, 22, 269–276. [Google Scholar] [CrossRef]
- Elhoseny, M.; Shankar, K. Energy Efficient Optimal Routing for Communication in VANETs via Clustering Model. Emerg. Technol. Connect. Internet Veh. Intell. Transp. Syst. Netw. 2019, 242, 1–14. [Google Scholar]
- Hamdi, M.M.; Audah, L.; Abduljabbar, S.; Hamid, A. A Review of Applications, Characteristics and Challenges in Vehicular Ad Hoc Networks (VANETs). In Proceedings of the 2020 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 26–28 June 2020; pp. 1–7. [Google Scholar]
- Zeadally, S.; Hunt, R.; Chen, Y.-S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J. A Comprehensive Survey on VANET Security Services in Traffic Management System. Wirel. Commun. Mob. Comput. 2019, 2019, 23. [Google Scholar] [CrossRef] [Green Version]
- Arif, M.; Wang, G.; Geman, O.; Balas, V.E.; Tao, P.; Brezulianu, A.; Chen, J. SDN-based VANETs, Security Attacks, Applications, and Challenges. Appl. Sci. 2020, 10, 3217. [Google Scholar] [CrossRef]
- Sundareswaran, V.; Aravindhar, J. A Secured Data Transmission in VANET using Dual Group Keys and Frequent Data Identification. Taga J. 2017, 14, 2042–2051. [Google Scholar]
- Kang, J.; Elmehdwi, Y.; Lin, D. SLIM: Secure and Lightweight Identity Management in VANETs with Minimum Infrastructure Reliance. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Singapore, 8–10 August 2018; Volume 238, pp. 823–837. [Google Scholar]
- Daeinabi, A.; Rahbar, A.G. Detection of malicious vehicles (DMV) through monitoring in Vehicular Ad-Hoc Networks. Multimed. Tools Appl. 2013, 66, 325–338. [Google Scholar] [CrossRef]
- Hegde, N.; Manvi, S.S. MFZKAP: Multi Factor Zero Knowledge Proof Authentication for Secure Service in Vehicular Cloud Computing. In Proceedings of the 2019 Second International Conference on Advanced Computational and Communication Paradigms (ICACCP), Gangtok, India, 25–28 February 2019; pp. 1–6. [Google Scholar]
- Whaiduzzaman, M.; Sookhak, M.; Gani, A.; Buyya, R. A survey on vehicular cloud computing. J. Netw. Comput. Appl. 2014, 40, 325–344. [Google Scholar] [CrossRef]
- Chen, Y.; Sion, R. On securing untrusted clouds with cryptography. In Proceedings of the 9th Annual ACM Workshop on Privacy in the Electronic Society, New York, NY, USA, 4 October 2010; Volume 23, p. 109114. [Google Scholar]
- Alizadeh, M.; Abolfazli, S.; Zamani, M.; Baharun, S.; Sakurai, K. Authentication in mobile cloud computing: A survey. J. Netw. Comput. Appl. 2016, 61, 59–80. [Google Scholar] [CrossRef]
- Li, H.; Dai, Y.; Tian, L.; Yang, H. Identity-Based Authentication for Cloud Computing. In Proceedings of the IEEE International Conference on Cloud Computing, Bangalore, India, 21–25 September 2009; Volume 5931, pp. 157–166. [Google Scholar]
- Lipton, B. Zero-Knowledge Proof and Authentication Protocols. In Proceedings of the IEEE Conference on Computer Communications, Phoenix, AZ, USA, 10–15 April 2016; pp. 1903–1911. [Google Scholar]
- Liu, X.; Yang, Y.; Xu, E.; Jia, Z. An Authentication Scheme in VANETs Based on Group Signature. In Proceedings of the International Conference on Intelligent Computing, Mukalla, Yemen, 15–16 December 2019; Volume 11643, pp. 346–355. [Google Scholar]
- Yue, X.; Chen, B.; Wang, X.; Duan, Y.; Gao, M.; He, Y. An Efficient and Secure Anonymous Authentication Scheme for VANETs Based on the Framework of Group Signatures. IEEE Access 2018, 6, 62584–62600. [Google Scholar] [CrossRef]
- Hao, Y.; Cheng, Y.; Ren, K. Distributed Key Management with Protection Against RSU Compromise in Group Signature Based VANETs. In Proceedings of the IEEE Conference and Exhibition on Global Telecommunications (GLOBECOM), New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–5. [Google Scholar]
- Rasheed, A.A.; Mahapatra, R.N.; Hamza-Lup, F.G. Adaptive Group-Based Zero Knowledge Proof-Authentication Protocol in Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2019, 21, 867–881. [Google Scholar] [CrossRef]
- Al-Mutiri, R.; Al-Rodhaan, M.; Tian, Y. Improving vehicular authentication in VANET using cryptography. Int. J. Commun. Netw. Inf. Secur. 2018, 10, 248–255. [Google Scholar]
- Alaya, B.; Sellami, L. Clustering method and symmetric/asymmetric cryptography scheme adapted to securing urban VANET networks. J. Inf. Secur. Appl. 2021, 58, 102779. [Google Scholar] [CrossRef]
- Pandi, V.; Maria, A.; Victor, C.; Jegatha, D.; Balamurugan, B. Computationally efficient privacy preserving authentication and key distribution techniques for vehicular ad hoc networks. Clust. Comput. 2017, 20, 2439–2450. [Google Scholar]
- Jinhui, L.; Yong, Y.; Jianwei, J.; Shijia, W.; Peiru, F.; Houzhen, W.; Huanguo, Z. Lattice-based double-authentication-preventing ring signature for security and privacy in vehicular Ad-Hoc networks. Tsinghua Sci. Technol. 2019, 24, 575–584. [Google Scholar]
- Pravin, M.; Vijay, K.Y.; Shekhar, V.; Sridhar, V. Efficient Lattice-Based Ring Signature for Message Authentication in VANETs. IEEE Syst. J. 2020, 14, 5463–5474. [Google Scholar]
- Liquan, C.; Tianyang, T.; Kunliang, Y.; Mengnan, Z.; Yingchao, W. V-LDAA: A New Lattice-Based Direct Anonymous Attestation Scheme for VANETs System. Secur. Commun. Netw. 2021, 2021, 867–881. [Google Scholar] [CrossRef]
- Stallings, W. Cryptography and Network Security: Principles and Practice, 6th ed.; Pearson: New York, NY, USA, 2013. [Google Scholar]
- Schneier, B. Applied Cryptography—Protocols, Algorithms, and Source Code in C, 2nd ed.; John Wiley & Sons: New York, NY, USA, 1996. [Google Scholar]
- Kahate, A. Cryptography and Network Security; Tata McGraw-Hill Education: New York, NY, USA, 2013. [Google Scholar]
- Dousti, M.S.; Jalili, R. An efficient statistical zero-knowledge authentication protocol for smart cards. Int. J. Comput. Math. 2015, 93, 453–481. [Google Scholar] [CrossRef]
- Kumari, S.; Chaudhry, S.A.; Wu, F.; Li, X. An improved smart card based authentication scheme for session initiation protocol. Peer-Peer Netw. Appl. 2017, 10, 92–105. [Google Scholar] [CrossRef]
- Walshe, M.; Epiphaniou, G.; Al-Khateeb, H.; Hammoudeh, M.; Katos, V.; Dehghantanha, A. Non-interactive zero knowledge proofs for the authentication of IoT devices in reduced connectivity environments. Ad Hoc Netw. 2019, 95, 101988. [Google Scholar] [CrossRef]
- Assidi, H.; Ayebie, E.B.; Souidi, E.M. Two Mutual Authentication Protocols Based on Zero-Knowledge Proofs for RFID Systems. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Korea, 28–30 November 2018; Volume 10779, pp. 267–283. [Google Scholar]
- Doss, R.; Trujillo-Rasua, R.; Piramuthu, S. Secure attribute-based search in RFID-based inventory control systems. Decis. Support Syst. 2020, 132, 113270. [Google Scholar] [CrossRef]
- Dixit, M.K. A Secure Way of Cloud Supported user Identification for Internet of Things using Feige–Fiat–Shamir Identification Scheme. J. Web Dev. Web Des. 2021, 6, 24–30. [Google Scholar]
- Al-Adhami, A.H.; Ambroze, M.; Stengel, I.; Tomlinson, M. An Effencient Improvement of RFID Authentication Protocol Using Hash Function ZKP. In Proceedings of the 2019 2nd Scientific Conference of Computer Sciences (SCCS), Baghdad, Iraq, 27–28 March 2019; pp. 87–92. [Google Scholar]
- Zhang, C.; Lin, X.; Lu, R.; Ho, P.-H. RAISE: An Efficient RSU-Aided Message Authentication Scheme in Vehicular Communication Networks. In Proceedings of the 2008 IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 1451–1457. [Google Scholar]
- Dodis, Y.; Yampolskiy, A. A Verifiable Random Function with Short Proofs and Keys. Int. Workshop Public Key Cryptogr. 2005, 3386, 416–431. [Google Scholar]
- Secure Password Check. Available online: https://password.kaspersky.com (accessed on 17 October 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chistousov, N.K.; Kalmykov, I.A.; Dukhovnyj, D.V.; Kalmykov, M.I.; Olenev, A.A. Adaptive Authentication Protocol Based on Zero-Knowledge Proof. Algorithms 2022, 15, 50. https://doi.org/10.3390/a15020050
Chistousov NK, Kalmykov IA, Dukhovnyj DV, Kalmykov MI, Olenev AA. Adaptive Authentication Protocol Based on Zero-Knowledge Proof. Algorithms. 2022; 15(2):50. https://doi.org/10.3390/a15020050
Chicago/Turabian StyleChistousov, Nikita Konstantinovich, Igor Anatolyevich Kalmykov, Daniil Vyacheslavovich Dukhovnyj, Maksim Igorevich Kalmykov, and Aleksandr Anatolyevich Olenev. 2022. "Adaptive Authentication Protocol Based on Zero-Knowledge Proof" Algorithms 15, no. 2: 50. https://doi.org/10.3390/a15020050
APA StyleChistousov, N. K., Kalmykov, I. A., Dukhovnyj, D. V., Kalmykov, M. I., & Olenev, A. A. (2022). Adaptive Authentication Protocol Based on Zero-Knowledge Proof. Algorithms, 15(2), 50. https://doi.org/10.3390/a15020050






