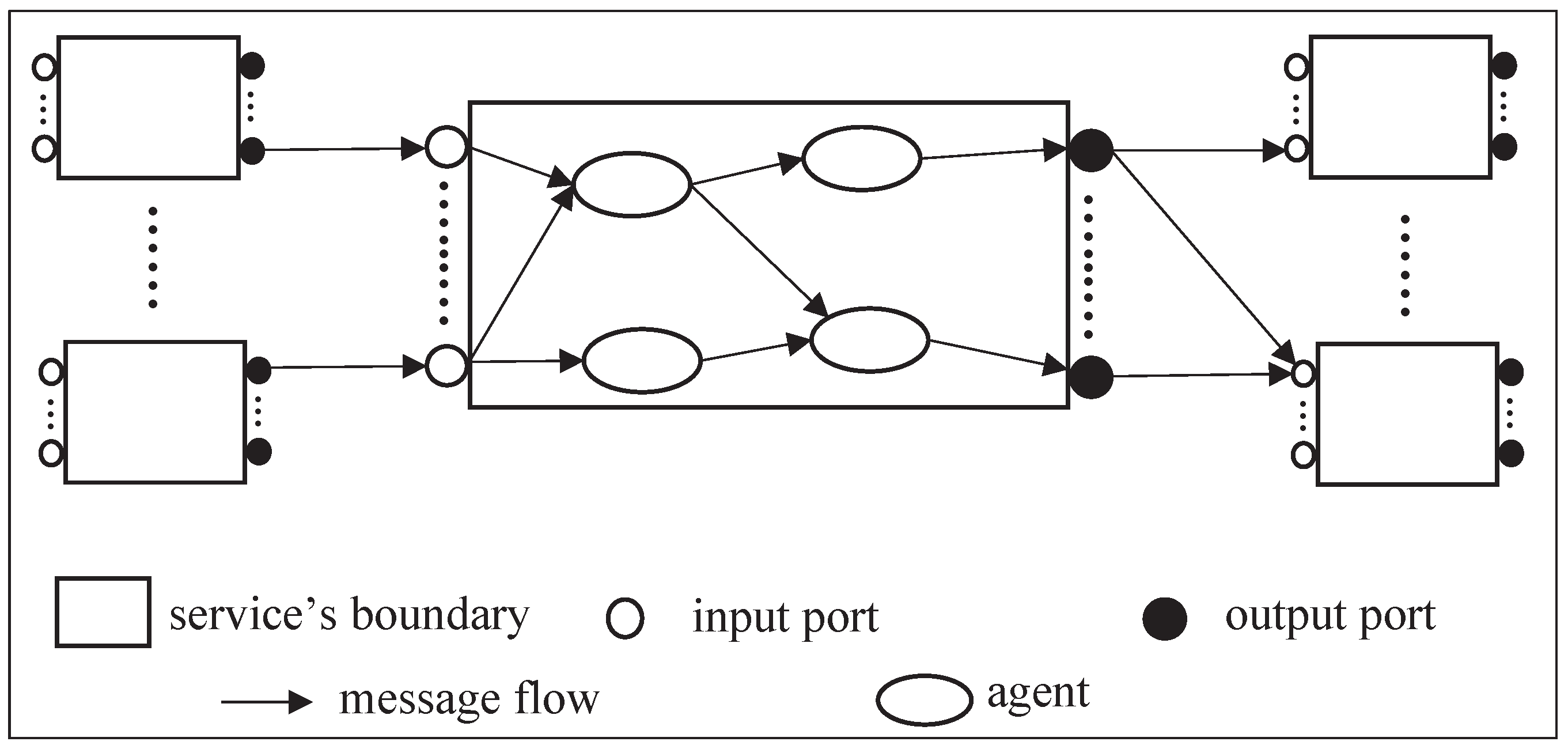
In this section, we study some important properties and propositions of IoT services. We also present a proximity model to represent an appropriate notion of proximity for IoT services. Developing such a model requires more than simply representing geographic locations and specifications of sensors and actuators. Particularly, proximity may be geographical or logical, and is often dependent on the context. For example, consider a camera capable of capturing high-quality images in good lighting, but limited in its range and resolution in dark or foggy conditions. In this paper, we address these challenges by representing a sufficiently rich and context-sensitive notion of proximity.
5.1. Properties and Propositions
The necessary and sufficient condition for serving an IoT service request is stated in Axiom 2, as follows:
Axiom 2: Serving a service request. A service request set to can be served by a set of contributors if and only if each member of can be served by a subset of .
The necessary and sufficient condition for serving a client tuple is stated in Axiom 3, as follows:
Axiom 3: Serving a client tuple. A client tuple can be served by a set of contributors if and only if has the sensing capabilities to serve the requirements of , and can be accommodated in ’s sensing schedules.
There are two types of deadlines set by the directory service in each contributor’s request to serve : (i) the offer response’s deadline by which a contributor has to respond to the directory service’s request; and (ii) the offer acceptance’s deadline by which the directory service has to accept the contributor’s response to its request.
The following axiom describes the conditional contributor commitment to contribute in serving the service request:
Axiom 4: Conditional contributor commitment. A contributor conditionally commits to serving its part, , if it indicates its capability to serve to the directory service, and can be accommodated in c’s sensing schedule, with the condition that the directory service accepts the assignment of to c by a deadline .
We assume that the directory service guarantees to send a confirmation message to the contributor service before the deadline if the directory service has accepted c’s offer.
The following axiom describes the unconditional contributor commitment to contribute in serving the service request:
Axiom 5: Unconditional contributor commitment. A contributor c’s conditional commitment to serve becomes unconditional when the server accepts c’s offer by the deadline .
Theorem 1. If the directory service accepts a request ρ, it is served.
Proof. According to Axiom 1, if a request is accepted in the system, there must be at least one set which can be served by the directory service, and the service can schedule the processing time required to serve . According to Axioms 2 and 5, if can be served by the directory service, the directory service must have received unconditional offers from a set of contributors to participate in serving . To obtain an unconditional commitment from a contributor , according to Axiom 4, c must have checked its sensing schedule and temporarily reserved a time slot for serving its part in . c would have sent an offer to the server by the deadline, and this offer would have been accepted by the server by c’s deadline. The directory service would have sent a confirmation message to c. Then, c would have, finally, sent a message to the directory service conforming that c has scheduled its part in for execution. If all members in have sent a confirmation message to the directory service, this means each member must have scheduled its part, , for execution. In other words, has unconditionally committed to collectively serve a set of client tuples which covers all members in . Therefore, has a commitment to be served by both a set of contributors and the directory service. This means that a request is served if the directory service accepts it, which proves Theorem 1. □
There are two types of delay set by the client in this request, which tell the directory service about the following requirements: (i) the freshness of the sensed data; and (ii) the time ranges of receiving service updates from the server.
The following definition describes the compatible delay tolerance of the sensing requests served by a single contributor service.
Definition 5 (Compatible delay tolerance)
. The delay tolerances of multiple sensing requests, which are parts of contributor tuples, are compatible if the hosting contributor can opportunistically merge these requests to form one sensing group so that one optimal sampling instance would satisfy them all.
Axiom 6: Tolerant sensor sampling. If multiple sensing requests have compatible delay tolerances at a contributor c, then c can opportunistically merge these requests to form one sensing group so that one optimal sampling instance would satisfy all of them.
Axiom 6 serves as the foundation for our ShareSens approach [
20]. It is used when the optimized sensing option has been selected. ShareSens assumes that requests pick from a limited number of sampling rates available, selected both to increase opportunity for sharing sampled data as well as to enhance the performance of the scheduling mechanism, which implicitly encourages selecting a delay tolerance when submitting a sensing request. The quality of service determines the cost/price of the service in our pricing model. ShareSens provides two options of quality of service for serving a sensing request when dealing with tolerant sensor sampling: (i) the same time lag delays all samples; or (ii) samples are provided within a range, but there is no promise to have an equal time distance between them.
Definition 6 (Contributor service ability)
. A contributor c indicates its ability to serve its part in , , if c has the sensing capabilities to serve the requirements of , and the sensing requests in can be served using a mix of the following options:
- 1.
Some sensing requests in can join some of the sensing groups already being served at c if the sensing schedule of those groups is not altered after the arrival of the incoming requests;
- 2.
Some sensing requests in can be merged with some of the sensing groups already being served at c if they have compatible delay tolerances with those groups so that the existing sensing schedule at c is altered in order to accommodate the incoming requests;
- 3.
Some sensing requests in are separately scheduled in a new sensing group.
Choosing between the above options depends on the complexity of the reasoning process for accommodating the incoming requests. If the reasoning cost of option 2 is high, then it may be more efficient to use option number 3 directly. In other words, there should be a balance between cost effectiveness and the expected benefits. Therefore, optimizing the schedule has to be weighed against the benefits of the optimal schedule, which may depend on the duration of the sensing request.
Axiom 7: Opportunistic merging of sampling requests. An incoming sensing request can partially or completely share the same sampling stream with a sensing group already being served at a contributor c if and only if it has a delay tolerance which is compatible with that group.
Definition 7 (Client tuple)
. A client tuple ζ represents a single timed service feed, which is formally represented as:where Y denotes an expression that is evaluated by the server to obtain the sensing task (i.e., the sensing parameters) which is carried out by the contributors. s represents the client service, is the delivery time, and is the maximum time delay between the sensing time and the delivery time. If the sensed data is a result of aggregating multiple sensing feeds, then becomes the maximum time delay between the oldest feed and the delivery time of the aggregate. Contributor tuples are created using a function
as follows:
where
denotes the set of all contributor tuples which are sufficient to serve
,
is the set of contributors who collectively participate in serving
,
is a single contributor tuple generated from a contributor
, and
k is the size of the
set.
A contributor tuple
is represented as follows:
where
s denotes a contributing service’s unique name (i.e., actor name),
represents the sensing instructions,
is the sensing time,
is the maximum time delay between the sensing time and sending data to the service coordinator, and
represents the sensing data. Note that
is empty before filling the sensing data by the contributor service.
The following transition rule shows the process of assigning the sensing tasks represented in the contributor tuples
to
:
where
is a directory service;
is a set of contributing services which will participate in serving
,
is the set of the contributor tuples (i.e., sensing tasks);
is a set of actor messages where each
is a message sent to
, where
; and
such that
is
’s sensing assignment.
On receiving its assigned set of contributor tuples
, a contributor
c adds them to its schedule, as follows:
where
is a schedule message,
is the contributor tuples assigned to contributor
c, and
is the contributor’s state.
Each contributor
c senses/executes the tuples that have a sensing time equals to
t. After the sensing computation in
is executed,
d is filled in with the sensing data, and a serve-next message is sent to the contributor itself in order to serve the next message or sensing task. The contributor then sends the sensed data
d to the server when
, as described by the following transition rule:
where
is a contributing service,
is a consuming service,
,
, and
is a data contribution message.
On receiving a contribution message
, the server actor proceeds to aggregate the message and update the request’s state, as follows:
where
is a contribution message, where
is the current state of the request
.
If the aggregation condition is met and
, the server notifies a service update to the client:
where
,
is the current state of the request
, and
is the new state of the request.
If the aggregation condition is not met, the server updates the request’s state:
Theorem 2. If there is a delay which can be tolerated to a group of sensing requests at a contributor c, one sampling instance is carried out for all of them.
Proof. According to Axiom 6, if the delay in sampling can be tolerated to a group of sampling requests at a contributor c, c can adjust their sampling rates within a predefined delay so that they all can share the same sampling instance. In this case, there must be a set of contributors that have conditionally committed to collectively serve a set of client tuples , which is a superset of . According to Axiom 3, if a contributor conditionally commits to serve its part , this means c has indicated its ability to serve to the server, and can be accommodated in c’s sensing schedule.
□
5.2. Fine-Grained Resource Model for IoT Services
Our model assumes that IoT services are owned by their initiator. This capability can also inform the pricing of using services. The directory service can set the price of creating a new service, and the initiator service can charge the cost of using its services.
Property 1. For an accepted request ρ, the time delay to send any aggregated update θ in ξ to a client σ does not exceed the max-delay of the client tuple, , specified by σ.
Proof. For the same client tuple , the max delay of the contributor tuples mean it is limited by the oldest tuple in the aggregate. This is assuming that the sensed data in any contributor tuple , including the oldest feed, must be collected and sent to the server no later than , where is the maximum time delay between the sensing time and sending data to the server. Therefore, is sent to no later than . This proves the property. □
Property 2. There are no wasted contributions in the system.
Proof. Assume that a request is accepted in the system. According to Axiom 1, if a request is accepted in the system, there must be at least one set that can be served by the server. According to Axioms 2 and 5, there must be a set of contributors which have unconditionally committed to serve a set of client tuples, , which is exactly equal to the set so that each and every member in is a member in . Therefore, there are no wasted contributions in the system. This proves the property. □
A contributor context sampling is a process of obtaining a contributor context by the mobile device. To quantitatively describe the consumption of resources, particularly the energy consumed by sensors involved in the sampling, in the proposed IoT system, we adopt the following energy model. Each of the sampling methods supported by the mobile device is associated with a resource cost
required for its invocation for context sampling and is determined by the following function:
A total cost of the IoT system functioning is determined by costs of the individual contributor context samplings and is represented as the sum of their individual costs:
Given a service list, the goal of the IoT system is to define the function that maximizes the number of IoT services that are hosted at the contributor’s device, and minimizes the total cost of consumed resources.
We use a sliding-window concept to aggregate the most recently collected sensor data from contributors as input to the aggregation function. We collect a series of sensor feeds from different contributors at the same time, denoted as
. Each service consumes
computational resource units from each contributor during data acquisition. The total computation cost can be expressed by:
We define
to denote the communication cost of unit data, and the total communication cost can be expressed by:
where
is the size of the sensing data.
We consider three types of overhead costs in the IoT system: context sampling, computation, and communication. The total cost within a long time period
can be calculated by:
Our objective is to calculate the amount of resources a service uses.
We represent the availability of each resource (e.g., sensor sampling, CPU cycles, network utilization, etc.) in a system of services by a resource term , where:
denotes the located type of the specified resource. It contains both the type of the resource r and the relative location (locality) of the resource . The locality could be relative or absolute based on the type of the service. Note that the location where the resource is residing is dynamic, as we deal with mobile resources.
represents the rate of availability of the resource, in quantity or time. For example, if the specified resource is a contributor’s sensor, then this parameter represents the sampling rate of that sensor which is the time between any two consecutive context samplings. The higher its value, the more frequent the context is sampled. In addition, this parameter adjusts the required accuracy when sampling the context. The higher its value, the more precise the sampled context is.
is the time interval during which the resource exists, where
For example, consider that a GPS sensor at a contributor is sampled at rate 10 Hz and available at a time interval , and can be represented as .
As each resource term is associated with a time interval
, relationships between time intervals must be defined before we can discuss the operations on resource terms. We use interval algebra to formalize relations between two time intervals, as shown in
Figure 3.
If two resource terms in a resource set have the same located types and overlapping time intervals, they can be combined as follows:
where for any interval for which they overlap, their rates are added, and for remaining intervals, they are represented separately in the set, and ∖ is a relative complement operation.
Resource requirements of service requests: A service request consumes resources at every step of its execution. We represent request’s computations in terms of the resources they consume. Request’s computations in our model can be divided into three categories: sensing computation at a contributor device, CPU processing at the server side, and network utilization.
We represent the resource requirements for a contributor tuple
as follows:
where
is a function which takes a contributor tuple
as a parameter and returns a set of resource amounts representing the required resources for serving that tuple,
s is the earliest start time of executing
(i.e., sensing time),
d is the deadline by which the sensing task must be completed, and
q is the quantity of resource required. For example:
Consider a function
f, which, when a resource set
E and the resource requirement of a contributor tuple
are provided as parameters, returns a Boolean value true or false, indicating whether or not the contributor tuple can be served given the available set of resources:
where
gives the union of all resources in
which exist in the interval
. For each member
r in
R,
f searches in the set of available resources
E for the amount of resources required to service
r.
Axiom 8: Single contributor tuple accommodation. A contributor tuple can be accommodated by a system if, by time s, the system satisfies the resource requirement , i.e., , where E is the available resources of the system.
Axiom 9: Sequential contributor tuples accommodation. A system with resources E can accommodate a sequential contributor tuples, represented in a single client tuple , if the system can satisfy the simple resource requirements for each contributor tuple in .
We represent the requirements of a set of contributor tuples in
sequentially, as follows:
where
.
A concurrent computation consists multiple actors (e.g., contributors). Resource requirements of a concurrent computation
can be satisfied by satisfying resource requirements of the individual actors, as follows:
where
represents computations carried out by actor
.