Influence Maximization with Priority in Online Social Networks
Abstract
1. Introduction
- We propose the Influence Maximization with Priority () problem that considers priority constraint in Influence Maximization () problem. It means we expand the by adding a constraint to influence on a given set of users. aims to find the seed set S with size k so that total influence of priority users is at least a given threshold and still maintain the influence of cascade maximized.
- We propose two approximation algorithms, and , for the problem. algorithm provides an approximation ratio of , where is an output of the algorithm. In addition, is a randomized approximation algorithm providing an approximation ratio of with probability at least , where are input parameters and t is an output of algorithm.
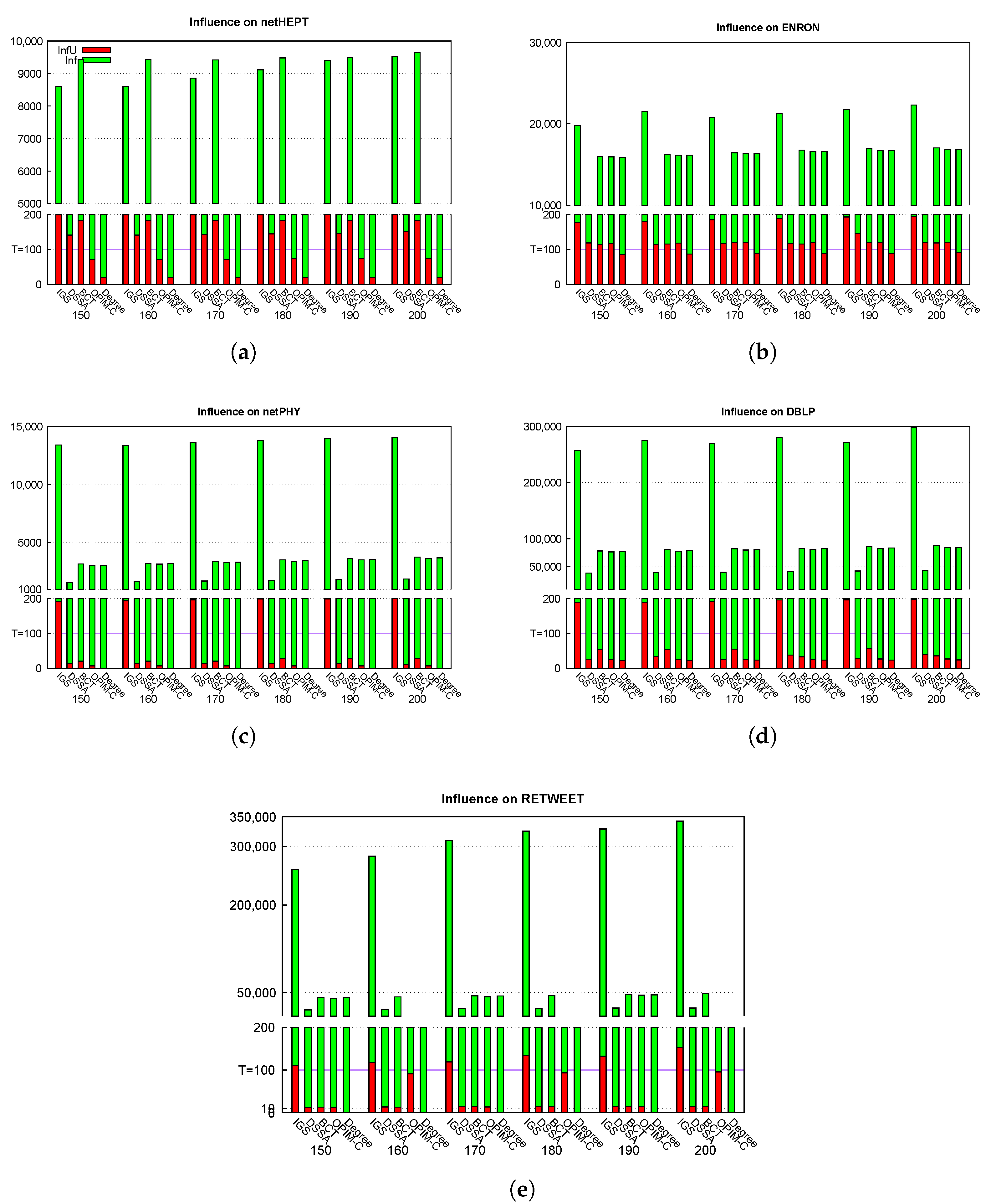
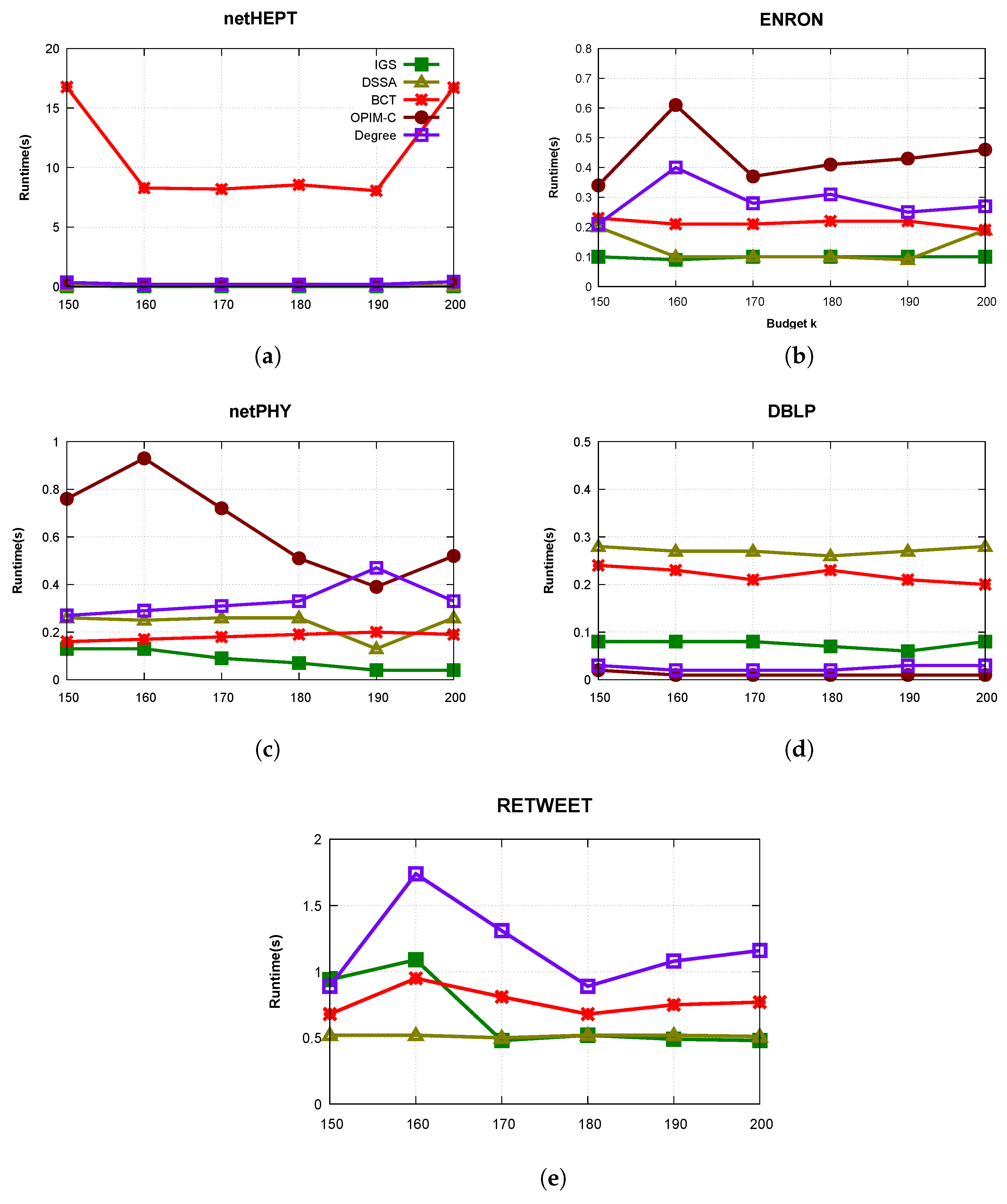
- We conduct extensive experiments on various real networks such as netHEPT, netPHY, Email-Enron, DBLP, and Twitter ReTweet. The results indicate that our algorithm, , often outperforms state-of-the-art algorithms in terms of influence, running time and memory used. In particular, provides the solution which ensures that the influence on the priority set is approximately from twice to 10 times greater than its threshold T while still maintains influence spread approximations as in algorithms. Further, we also demonstrate that is faster and uses lower memory than the others in a lot of cases. On the whole, although has to care about how influences to a target given users, still gives considerable fast runtime, low memory used and high maximized influence on all nodes such as state-of-the-art algorithms such as DSSA, BCT, OPIM-C. It proves that has been very well designed.
2. Model and Problem Definition
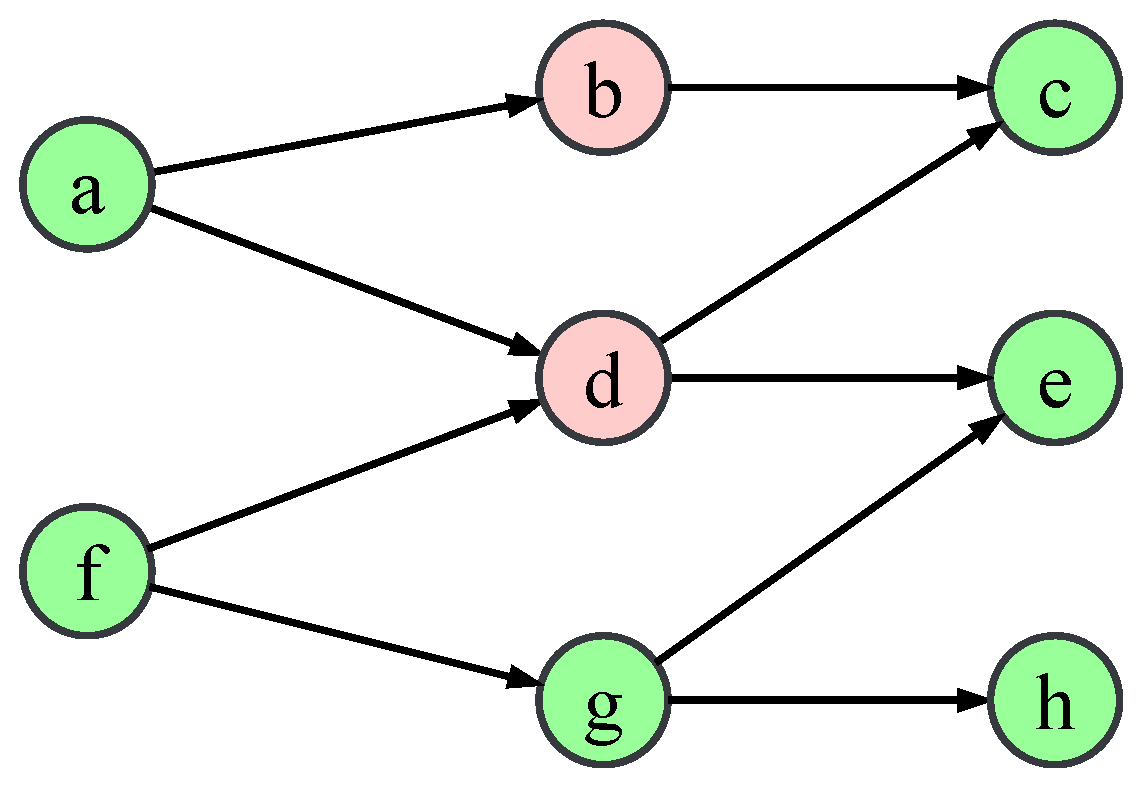
2.1. Graph Notation and Independent Cascade Model
- At step , all nodes in S is activated.
- At step , for an activated node u in previous steps, it has a single chance to activate each inactive neighbour v with the successful probability . An activated node remains till the end of the diffusion process.
- The propagation process ends when no more node is activated.
2.2. Problem Definition
3. Integrated Greedy Algorithm
| Algorithm 1: Integrated Greedy () algorithm |
 |
4. Sampling Algorithm with Provable Guarantees
4.1. Estimator of Influence Functions
- 1.
- Picking a source node u with probability .
- 2.
- Generating a sample graph g from G, and returning as nodes which can be reached from u in g.
| Algorithm 2: Generating RR sample under model |
 |
- 1.
- Picking a source node with probability .
- 2.
- Generating a sample graph g from G, and returning as nodes which can be reached from u in g.
4.2. Algorithm Description and Theoretical Analysis
| Algorithm 3: Integrated Greedy -based Sampling () algorithm |
 |
- Case 1:
- If , then .
- Case 2:
- If , (40) becomes:
- Case 1:
- If the algorithm stops with the condition , apply (26) with set and , we have:From (27), we have:Apply an union probability that the events (54) and (57) happen with the probability at most . Assume that they do not happen, we have:Hence, in this case the algorithm satisfies approximation guarantee with probability at least .
- Case 2:
- If the algorithm stops at any iterator . At this iterator, the condition in line 19 is satisfied, apply Lemma 5 and Lemma 6, the following thing happens with the probability at least :
5. Experiments
5.1. Experimental Settings
5.2. Experimental Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Kempe, D.; Kleinberg, J.M.; Tardos, É. Maximizing the spread of influence through a social network. In Proceedings of the Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–27 August 2003; pp. 137–146. [Google Scholar] [CrossRef]
- Nguyen, H.T.; Thai, M.T.; Dinh, T.N. A Billion-Scale Approximation Algorithm for Maximizing Benefit in Viral Marketing. IEEE/ACM Trans. Netw. 2017, 25, 2419–2429. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, D.; Tan, K. Real-time Targeted Influence Maximization for Online Advertisements. PVLDB 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Pham, C.V.; Thai, M.T.; Duong, H.V.; Bui, B.Q.; Hoang, H.X. Maximizing misinformation restriction within time and budget constraints. J. Comb. Optim. 2018, 35, 1202–1240. [Google Scholar] [CrossRef]
- Tong, G.A.; Wu, W.; Guo, L.; Li, D.; Liu, C.; Liu, B.; Du, D. An efficient randomized algorithm for rumor blocking in online social networks. In Proceedings of the 2017 IEEE Conference on Computer Communications, INFOCOM 2017, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Budak, C.; Agrawal, D.; El Abbadi, A. Limiting the spread of misinformation in social networks. In Proceedings of the 20th International Conference on World Wide Web, WWW 2011, Hyderabad, India, 28 March–1 April 2011; pp. 665–674. [Google Scholar] [CrossRef]
- Nguyen, H.T.; Cano, A.; Tam, V.; Dinh, T.N. Blocking Self-avoiding Walks Stops Cyber-epidemics: A Scalable GPU-based Approach. IEEE Trans. Knowl. Data Eng. 2020, 32, 1263–1275. [Google Scholar] [CrossRef]
- Nguyen, N.P.; Yan, G.; Thai, M.T. Analysis of misinformation containment in online social networks. Comput. Netw. 2013, 57, 2133–2146. [Google Scholar] [CrossRef]
- Zhang, H.; Alim, M.A.; Li, X.; Thai, M.T.; Nguyen, H.T. Misinformation in Online Social Networks: Detect Them All with a Limited Budget. ACM Trans. Inf. Syst. 2016, 34, 18:1–18:24. [Google Scholar] [CrossRef]
- Zhang, H.; Kuhnle, A.; Zhang, H.; Thai, M.T. Detecting misinformation in online social networks before it is too late. In Proceedings of the 2016 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, ASONAM 2016, San Francisco, CA, USA, 18–21 August 2016; pp. 541–548. [Google Scholar] [CrossRef]
- Ye, M.; Liu, X.; Lee, W. Exploring social influence for recommendation: A generative model approach. In Proceedings of the 35th International ACM SIGIR conference on research and development in Information Retrieval, SIGIR ’12, Portland, OR, USA, 12–16 August 2012; pp. 671–680. [Google Scholar] [CrossRef]
- Chen, W.; Collins, A.; Cummings, R.; Ke, T.; Liu, Z.; Rincón, D.; Sun, X.; Wang, Y.; Wei, W.; Yuan, Y. Influence Maximization in Social Networks When Negative Opinions May Emerge and Propagate. In Proceedings of the Eleventh SIAM International Conference on Data Mining, SDM 2011, Mesa, AZ, USA, 28–30 April 2011; pp. 379–390. [Google Scholar] [CrossRef]
- Borodin, A.; Filmus, Y.; Oren, J. Threshold Models for Competitive Influence in Social Networks. In Proceedings of the Internet and Network Economics—6th International Workshop, WINE 2010, Stanford, CA, USA, 13–17 December 2010; pp. 539–550. [Google Scholar] [CrossRef]
- Tang, Y.; Shi, Y.; Xiao, X. Influence Maximization in Near-Linear Time: A Martingale Approach. In Proceedings of the 2015 ACM SIGMOD International Conference on Management of Data, Melbourne, Victoria, Australia, 31 May–4 June 2015; pp. 1539–1554. [Google Scholar] [CrossRef]
- Nguyen, H.T.; Thai, M.T.; Dinh, T.N. Stop-and-Stare: Optimal Sampling Algorithms for Viral Marketing in Billion-scale Networks. In Proceedings of the 2016 International Conference on Management of Data, SIGMOD Conference 2016, San Francisco, CA, USA, 26 June–1 July 2016; pp. 695–710. [Google Scholar] [CrossRef]
- Chen, W.; Yuan, Y.; Zhang, L. Scalable Influence Maximization in Social Networks under the Linear Threshold Model. In Proceedings of the ICDM 2010, The 10th IEEE International Conference on Data Mining, Sydney, Australia, 14–17 December 2010; pp. 88–97. [Google Scholar] [CrossRef]
- Chen, S.; Fan, J.; Li, G.; Feng, J.; Tan, K.; Tang, J. Online Topic-Aware Influence Maximization. PVLDB 2015, 8, 666–677. [Google Scholar] [CrossRef]
- Aslay, Ç.; Barbieri, N.; Bonchi, F.; Baeza-Yates, R.A. Online Topic-aware Influence Maximization Queries. In Proceedings of the 17th International Conference on Extending Database Technology, EDBT 2014, Athens, Greece, 24–28 March 2014; pp. 295–306. [Google Scholar] [CrossRef]
- Pham, C.V.; Duong, H.V.; Hoang, H.X.; Thai, M.T. Competitive Influence Maximization within Time and Budget Constraints in Online Social Networks: An Algorithmic Approach. Appl. Sci. 2019, 9, 2274. [Google Scholar] [CrossRef]
- Tang, Y.; Xiao, X.; Shi, Y. Influence maximization: Near-optimal time complexity meets practical efficiency. In Proceedings of the International Conference on Management of Data, SIGMOD 2014, Snowbird, UT, USA, 22–27 June 2014; pp. 75–86. [Google Scholar] [CrossRef]
- Domingos, P.M.; Richardson, M. Mining the network value of customers. In Proceedings of the seventh ACM SIGKDD international conference on Knowledge discovery and data mining, San Francisco, CA, USA, 26–29 August 2001; pp. 57–66. [Google Scholar]
- Leskovec, J.; Krause, A.; Guestrin, C.; Faloutsos, C.; VanBriesen, J.M.; Glance, N.S. Cost-effective outbreak detection in networks. In Proceedings of the 13th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, San Jose, CA, USA, 12–15 August 2007; pp. 420–429. [Google Scholar] [CrossRef]
- Tang, J.; Tang, X.; Xiao, X.; Yuan, J. Online Processing Algorithms for Influence Maximization. In Proceedings of the 2018 International Conference on Management of Data (SIGMOD’ 18), Houston, TX, USA, 10–15 June 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 991–1005. [Google Scholar] [CrossRef]
- Nguyen, H.; Zheng, R. On Budgeted Influence Maximization in Social Networks. IEEE J. Sel. Areas Commun. 2013, 31, 1084–1094. [Google Scholar] [CrossRef]
- Pham, C.V.; Duong, H.V.; Thai, M.T. Importance Sample-Based Approximation Algorithm for Cost-Aware Targeted Viral Marketing. In Proceedings of the Computational Data and Social Networks—8th International Conference, CSoNet 2019, Ho Chi Minh City, Vietnam, 18–20 November 2019; pp. 120–132. [Google Scholar] [CrossRef]
- Li, X.; Smith, J.D.; Dinh, T.N.; Thai, M.T. TipTop: (Almost) Exact Solutions for Influence Maximization in Billion-Scale Networks. IEEE/ACM Trans. Netw. 2019, 27, 649–661. [Google Scholar] [CrossRef]
- Barbieri, N.; Bonchi, F.; Manco, G. Topic-aware social influence propagation models. Knowl. Inf. Syst. 2013, 37, 555–584. [Google Scholar] [CrossRef]
- Li, G.; Chen, S.; Feng, J.; Tan, K.-L.; Li, W.-S. Efficient Location-Aware Influence Maximization. In Proceedings of the 34th IEEE International Conference on Data Engineering, ICDE 2018, Paris, France, 16–19 April 2018; pp. 1569–1572. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, Y.; Zhang, W.; Lin, X. Efficient Distance-Aware Influence Maximization in Geo-Social Networks. IEEE Trans. Knowl. Data Eng. 2017, 29, 599–612. [Google Scholar] [CrossRef]
- Bharathi, S.; Kempe, D.; Salek, M. Competitive Influence Maximization in Social Networks. In Proceedings of the Internet and Network Economics, Third International Workshop, WINE 2007, San Diego, CA, USA, 12–14 December 2007; pp. 306–311. [Google Scholar] [CrossRef]
- Liu, W.; Yue, K.; Wu, H.; Li, J.; Liu, D.; Tang, D. Containment of competitive influence spread in social networks. Knowl.-Based Syst. 2016, 109, 266–275. [Google Scholar] [CrossRef]
- He, X.; Song, G.; Chen, W.; Jiang, Q. Influence Blocking Maximization in Social Networks under the Competitive Linear Threshold Model. In Proceedings of the Twelfth SIAM International Conference on Data Mining, Anaheim, CA, USA, 26–28 April 2012; pp. 463–474. [Google Scholar] [CrossRef]
- Lu, W.; Bonchi, F.; Goyal, A.; Lakshmanan, L.V.S. The bang for the buck: Fair competitive viral marketing from the host perspective. In Proceedings of the 19th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, KDD 2013, Chicago, IL, USA, 11–14 August 2013; pp. 928–936. [Google Scholar] [CrossRef]
- Chen, W.; Lakshmanan, L.V.S.; Castillo, C. Information and Influence Propagation in Social Networks; Synthesis Lectures on Data Management; Morgan & Claypool Publishers: San Rafael, CA, USA, 2013. [Google Scholar] [CrossRef]
- Bozorgi, A.; Samet, S.; Kwisthout, J.; Wareham, T. Community-based influence maximization in social networks under a competitive linear threshold model. Knowl.-Based Syst. 2017, 134, 149–158. [Google Scholar] [CrossRef]
- Tsang, A.; Wilder, B.; Rice, E.; Tambe, M.; Zick, Y. Group-Fairness in Influence Maximization. In Proceedings of the Twenty-Eighth International Joint Conference on Artificial Intelligence, IJCAI 2019, Macao, China, 10–16 August 2019; pp. 5997–6005. [Google Scholar] [CrossRef]
- Farnadi, G.; Babaki, B.; Gendreau, M. A Unifying Framework for Fairness-Aware Influence Maximization. In Proceedings of the Companion of The 2020 Web Conference 2020, Taipei, Taiwan, 20–24 April 2020; pp. 714–722. [Google Scholar] [CrossRef]
- Stoica, A.; Han, J.X.; Chaintreau, A. Seeding Network Influence in Biased Networks and the Benefits of Diversity. In Proceedings of the WWW ’20: The Web Conference 2020, Taipei, Taiwan, 20–24 April 2020; pp. 2089–2098. [Google Scholar] [CrossRef]
- Nguyen, L.N.; Zhou, K.; Thai, M.T. Influence Maximization at Community Level: A New Challenge with Non-submodularity. In Proceedings of the 39th IEEE International Conference on Distributed Computing Systems, ICDCS 2019, Dallas, TX, USA, 7–10 July 2019; pp. 327–337. [Google Scholar] [CrossRef]
- Borgs, C.; Brautbar, M.; Chayes, J.T.; Lucier, B. Maximizing Social Influence in Nearly Optimal Time. In Proceedings of the Twenty-Fifth Annual ACM-SIAM Symposium on Discrete Algorithms, SODA 2014, Portland, OR, USA, 5–7 January 2014; pp. 946–957. [Google Scholar] [CrossRef]
- Chung, F.R.K.; Lu, L. Survey: Concentration Inequalities and Martingale Inequalities: A Survey. Internet Math. 2006, 3, 79–127. [Google Scholar] [CrossRef]
- Rossi, R.A.; Ahmed, N.K. The Network Data Repository with Interactive Graph Analytics and Visualization; AAAI: Palo Alto, CA, USA, 2015. [Google Scholar]
| Database | #Nodes | #Edges | Types | Avg. Degree |
|---|---|---|---|---|
| netHEPT [15] | 15 K | 59 K | directed | 4.1 |
| ENRON [15] | 37 K | 184 K | directed | 5 |
| netPHY [15] | 37 K | 181 K | directed | 13.4 |
| DBLP [15] | 655 K | 2 M | directed | 6.1 |
| TWITTER RETWEET [42] | 1 M | 2 M | directed | 4 |
| Dataset | |||||||
|---|---|---|---|---|---|---|---|
| T | NetHept | Enron | netPHY | DBLP | RETWEET | ||
| 100 | 5666.16 | 14,267.40 | 1865.92 | 54,033.50 | 17,307.70 | ||
| 1482.04 | 1075.77 | 1192.84 | 1271.62 | 511.08 | |||
| 200 | 5581.34 | 14,162.20 | 1805.26 | 53,553.90 | 18,581.50 | ||
| 1478.93 | 1079.74 | 1175.32 | 1267.52 | 491.35 | |||
| 300 | 5645.40 | 14,284.80 | 1773.33 | 53,240.50 | 19,459.10 | ||
| 1476.08 | 1074.30 | 1153.32 | 1264.79 | 492.39 | |||
| 400 | 5640.21 | 14,196.50 | 1688.53 | 52,918.80 | 18,832.20 | ||
| 1468.48 | 1075.68 | 1125.69 | 1260.31 | 490.46 | |||
| 500 | 5039.45 | 14,245.50 | 1593.66 | 52,130.90 | 228,801.00 | ||
| 1238.54 | 1079.28 | 1104.20 | 1252.70 | 994.40 | |||
| DSSA | 4098.63 | 9960.35 | 3230.27 | 58,197.7 | 38,253.7 | ||
| 1093.7 | 857.608 | 174.479 | 474.635 | 168.087 | |||
| BCT | 11,088.10 | 19,901.70 | 6675.95 | 117,197.00 | 77,316.90 | ||
| 1280.54 | 1701.60 | 386.49 | 474.635 | 159.77 | |||
| OPIM-C | 3779.09 | 19,326.3 | 6262.5 | 112,334 | 72,026.1 | ||
| 600.93 | 894.18 | 194.04 | 459.801 | 173.41 | |||
| Degree | 3824.44 | 19,349.10 | 6345.86 | 114,249 | 73,936 | ||
| 292.82 | 779.84 | 164 | 260.94 | 22.77 | |||
| Dataset | Algorithm | Budget k | |||||
|---|---|---|---|---|---|---|---|
| 150 | 160 | 170 | 180 | 190 | 200 | ||
| NetHEPT | IGS | 9.90 | 9.90 | 9.90 | 9.89 | 9.89 | 9.95 |
| DSSA | 22.84 | 22.84 | 22.84 | 22.84 | 22.84 | 22.84 | |
| BCT | 1023.79 | 1017.52 | 1021.60 | 1012.21 | 1020.18 | 1020.74 | |
| OPIM-C | 47.76 | 47.91 | 48.03 | 48.11 | 48.30 | 48.46 | |
| Degree | 49.14 | 49.18 | 49.48 | 49.68 | 49.86 | 50.13 | |
| ENRON | IGS | 16.82 | 16.79 | 16.81 | 16.81 | 16.82 | 16.82 |
| DSSA | 30.48 | 28.07 | 28.07 | 28.07 | 28.07 | 30.48 | |
| BCT | 30.35 | 30.35 | 30.39 | 30.39 | 30.39 | 30.39 | |
| OPIM-C | 27.16 | 27.20 | 42.00 | 27.22 | 27.25 | 27.30 | |
| Degree | 27.98 | 28.08 | 43.77 | 28.19 | 28.27 | 28.41 | |
| NetPHY | IGS | 15.18 | 15.18 | 15.18 | 15.18 | 15.18 | 15.04 |
| DSSA | 52.12 | 52.12 | 52.12 | 52.12 | 38.50 | 52.14 | |
| BCT | 34.82 | 34.82 | 34.82 | 34.82 | 34.82 | 34.80 | |
| OPIM-C | 87.88 | 88.39 | 88.92 | 89.31 | 90.26 | 90.51 | |
| Degree | 92.26 | 92.71 | 93.33 | 93.88 | 94.68 | 94.98 | |
| DBLP | IGS | 138.66 | 138.66 | 138.66 | 138.66 | 138.66 | 138.66 |
| DSSA | 152.90 | 152.87 | 152.87 | 152.91 | 152.91 | 152.83 | |
| BCT | 162.88 | 162.87 | 162.87 | 162.88 | 162.88 | 162.89 | |
| OPIM-C | 475.05 | 373.72 | 373.78 | 373.95 | 477.18 | 477.51 | |
| Degree | 500.87 | 395.00 | 394.26 | 395.35 | 504.52 | 505.26 | |
| RETWEET | IGS | 214.67 | 214.67 | 214.67 | 214.67 | 214.67 | 214.67 |
| DSSA | 253.14 | 253.14 | 253.14 | 253.14 | 253.14 | 253.14 | |
| BCT | 282.50 | 282.50 | 282.50 | 282.47 | 282.50 | 282.48 | |
| OPIM-C | 877.31 | 874.20 | 722.91 | 876.99 | 886.78 | 877.80 | |
| Degree | 918.53 | 916.23 | 756.93 | 920.00 | 930.33 | 921.95 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pham, C.V.; Ha, D.K.T.; Vu, Q.C.; Su, A.N.; Hoang, H.X. Influence Maximization with Priority in Online Social Networks. Algorithms 2020, 13, 183. https://doi.org/10.3390/a13080183
Pham CV, Ha DKT, Vu QC, Su AN, Hoang HX. Influence Maximization with Priority in Online Social Networks. Algorithms. 2020; 13(8):183. https://doi.org/10.3390/a13080183
Chicago/Turabian StylePham, Canh V., Dung K. T. Ha, Quang C. Vu, Anh N. Su, and Huan X. Hoang. 2020. "Influence Maximization with Priority in Online Social Networks" Algorithms 13, no. 8: 183. https://doi.org/10.3390/a13080183
APA StylePham, C. V., Ha, D. K. T., Vu, Q. C., Su, A. N., & Hoang, H. X. (2020). Influence Maximization with Priority in Online Social Networks. Algorithms, 13(8), 183. https://doi.org/10.3390/a13080183




