Abstract
Wireless Sensor Networks (WSNs) are among the most emerging technologies, thanks to their great capabilities and their ever growing range of applications. However, the lifetime of WSNs is extremely restricted due to the delimited energy capacity of their sensor nodes. This is why energy conservation is considered as the most important research concern for WSNs. Radio communication is the utmost energy consuming function in a WSN. Thus, energy efficient routing is necessitated to save energy and thus prolong the lifetime of WSNs. For this reason, numerous protocols for energy efficient routing in WSNs have been proposed. This article offers an analytical and up to date survey on the protocols of this kind. The classic and modern protocols presented are categorized, depending on i) how the network is structured, ii) how data are exchanged, iii) whether location information is or not used, and iv) whether Quality of Service (QoS) or multiple paths are or not supported. In each distinct category, protocols are both described and compared in terms of specific performance metrics, while their advantages and disadvantages are discussed. Finally, the study findings are discussed, concluding remarks are drawn, and open research issues are indicated.
1. Introduction
A Wireless Sensor Network (WSN) is a set of wirelessly interconnected multifunctional devices, called sensor nodes, or just nodes, that are placed in an area of interest with at least one sink node, called base station (BS) [1]. The BS can both apply centralized control over the network it belongs to and communicate with the network end user(s) or/and other wireless or wired networks (Figure 1).
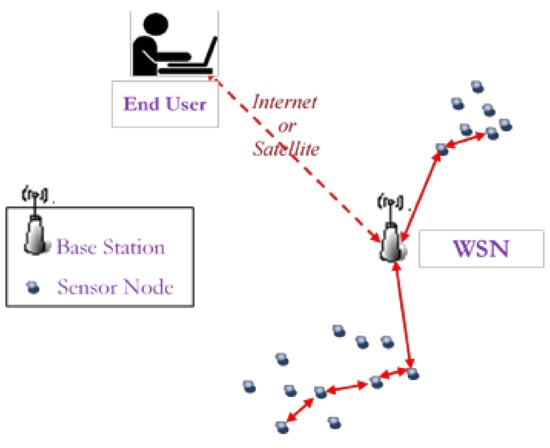
Figure 1.
An overview of a typical Wireless Sensor Network (WSN) architecture.
A typical sensor node is an electronic device, which, as shown in Figure 2, consists of a processing unit, a communication module, a single or many sensing elements, and a power unit. It may also contain optional equipment such as a mobility module or/and a position tracking module [1,2]. A sensor node uses its sensing elements to gather data related to its ambient conditions. In addition, a sensor node uses its processing unit to handle the data it collects, and its communication module to wirelessly exchange data with other sensor nodes and the BS. The power unit is typically a battery. The position tracking module monitors the current location of the sensor node. Finally, the mobility unit provides transportability.
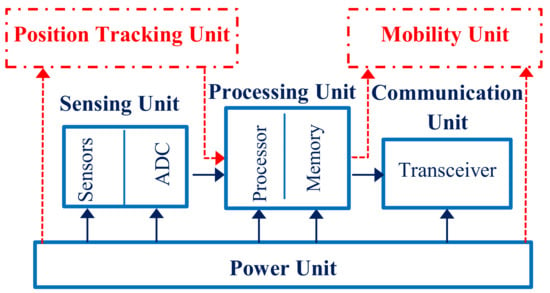
Figure 2.
The architecture of a typical sensor node.
In a WSN, the operation of both sensor nodes and the BS(s) is regulated by the so-called protocol stack. As shown in Figure 3, the protocol stack consists of five layers: the physical, the data link, the network, the transport, and the application layer [1].
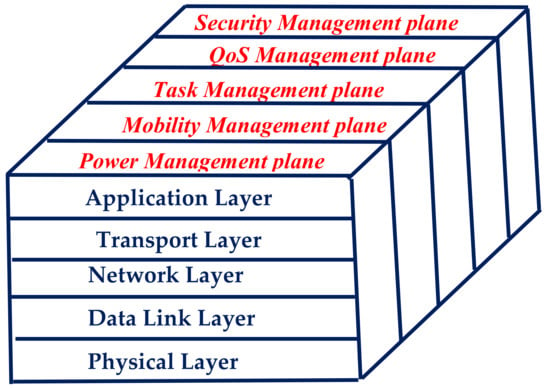
Figure 3.
Overview of the WSN protocol stack.
Specifically, the physical layer performs modulation, transmission, and reception tasks such as the selection of communication frequency, the generation of carrier frequency, the detection and modulation of signals, and the encryption of data. The data link layer deals with data frame detection, data stream multiplexing, medium access and error control in order to achieve consistent point-to-point, and point-to-multipoint connections. The network layer performs the routing of the data delivered by the transport layer. The transport layer is in charge of the retainment of the data flow. The application layer is the layer that adapts its content in order to suit the characteristics of each specific application. In addition, the protocol stack includes five management planes that intend to optimize the operation of a WSN in terms of corresponding performance metrics. They namely are: the power, the mobility, the task, the quality of service (QoS), and the security management planes [3].
Specifically, the power management plane is responsible for diminishing energy consumption. The mobility management plane is responsible for maintaining data routes even when there are movements of nodes. The task management plane is responsible for the assignment of various tasks, such as sensing, routing, and data aggregation, to the sensor nodes. The QoS management plane deals with fault tolerance, error control, and performance optimization according to particular QoS metrics. Security management plane records and regulates the network performance in terms of security [4].
A WSN may contain one or more BSs along with some hundreds or even thousands of sensor nodes. The combined use of such a quantity of nodes enables the concurrent acquisition of data related with the ambient conditions at wide areas of interest. This makes WSNs be ideal for the accomplishment of an ever increasing range of tasks such as fire detection, energy management, biomedical applications, environmental and habitat monitoring, surveillance and reconnaissance, home automation, object tracking, traffic control, inventory control, agriculture, machine failure diagnosis, and various military applications [5,6,7,8,9,10,11].
On the other hand, despite the numerous benefits that WSNs offer, there are serious problems that obstruct their operation, such as the presence of congestion, connectivity loss, vulnerable security, deteriorated QoS, and insufficient coverage [12,13,14,15,16,17]. However, it is commonly accepted that, the most important, by far, weakness of WSNs is the extremely limited lifetime of their sensor nodes, due to their strict energy constraints. This is due to the fact that the batteries that typically supply the energy to the sensor nodes are usually impractical to be either replaced or recharged because sensor nodes are usually located at difficult to reach places. The limited energy sufficiency of sensor nodes is the main cause for the termination of their operation and thus the gradual elimination of the overall lifetime of WSNs. Therefore, the accomplishment of energy saving is an issue of crucial importance for the effective operation of WSNs [18]. This is why energy inefficiencies that exist at each one of the five layers of the protocol stack of sensor nodes have to be eliminated. Actually, a sensor node consumes its energy primarily during its wireless communications and only partially during sensing and data processing [19]. For this reason, there are numerous research efforts that pursue energy conservation at the network layer of the protocol stack through the attainment of energy efficient route setup and consistent data communication among the sensor nodes themselves and the BS.
Consequently, the main goal of routing protocols in WSNs is to preserve the energy of sensor nodes, in order to keep them workable for as much time as possible, and thus prolong the network lifetime and retain network connectivity. In addition, given that neighboring sensor nodes may produce similar sensing data, routing protocols in a WSN need to identify and eliminate the redundant information. Furthermore, in WSNs, the most of data flow is directed from many sources to one single sink, while IP based organization is not forthrightly applied and sensor nodes have limited storage and processing capacity. On the other hand, routing protocols proposed for wired networks do not examine issues like the aforementioned. Instead, their primary concern is the achievement of high Quality of Service (QoS). Hence, they are considered to be unsuitable for WSNs.
For all aforementioned reasons, numerous protocols for energy efficient routing especially in WSNs have been proposed during the last two decades. Many of them are collectively presented in relevant surveys [20,21,22,23,24,25,26,27]. For taxonomy purposes, the use of specific categories has been suggested in order to classify protocols. This work both adopts and extends the classification proposed in [22,23], as shown in Figure 4. According to this, protocols are classified into four categories depending on (i) how the network is structured, (ii) how data are exchanged, (iii) whether location information is used or not, and (iv) whether Quality of Service (QoS) or multiple paths are supported or not.
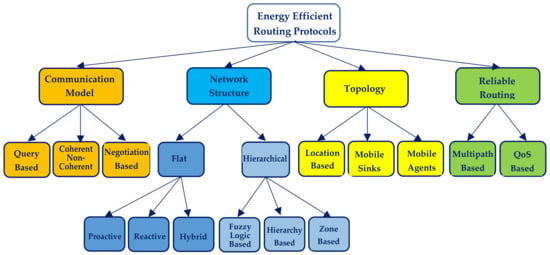
Figure 4.
The classification of Energy Efficient Routing Protocols as adopted in this research work.
The intention of this article is to provide a collective presentation of characteristic protocols that belong to each one of these categories, both classic and modern ones, highlight their main features, make a comparative study on their advantages and disadvantages, provide a discussion on general and specific considerations raised, and denote future research issues. Compared to previous similar reviews, the work presented in this article, provides not only an up-to-date but also a more exhaustive survey of energy efficient routing protocols. In addition, it both extends the existing taxonomies and considers more performance criteria for the comparative study of the protocols studied. In accordance with this perspective, the rest of this article is organized as follows. In Section 2, protocols classified according to Communication Model are presented. In Section 3, protocols classified according to Network Structure are described. Section 4 refers to protocols classified according to Topology. Section 5 analyzes Reliable Routing protocols. In Section 6, main findings in this survey are discussed and concluding remarks are extracted. Finally, Section 7 identifies open research issues.
2. Communication Model
Protocols of this category communication takes place from neighbor to neighbor, usually via single-hop routing. These data-centric protocols can convey more data for a certain quantity of energy. However, data delivery is not guaranteed. Protocols of this kind are classified into three subcategories depending on the method used in order to exchange data, which namely are: Query based, Coherent/Non-coherent, and Negotiation based.
2.1. Query Based
Protocols of this subcategory use queries in order to route data. Whenever a node needs new data, it propagates a message (query) to ask for these data from the node that has them. Next, the node which owns the data requested sends them to the node that has applied the query. In what follows in this section, six typical examples of query based energy efficient routing protocols are described.
Directed Diffusion (DD) [28] is a protocol that uses a naming scheme for data packets. It saves energy by diffusing data through the nodes and preventing unnecessary operations to run.DD uses a list of attribute-value pairs, with which it defines interests as object name, transmission, or geographic location. Interests are broadcasted from the BS to its neighbors and can be cached for later use. Interest caching includes gradients. Gradient is a reply link, from the neighbor sent the interest, which is described by data flow, duration, and expiring time generated from received interests. The nodes can do in-network data aggregation that is modeled as a minimum Steiner tree. Combining interests and gradients, multiple paths are generated between the BS and nodes, with one path been chosen using reinforcement. To achieve this, the BS resends the initial interest from the selected path, in smaller intervals, resulting in reinforcement of the source node to send data more frequently. When a route failure occurs, DD tries to create a new or an alternative path by reinitiating reinforcement to search for new paths with lower casting ratios. The main advantages of DD are that node addressing mechanisms are not needed and there is no need for global knowledge of network topology. In addition, high energy efficiency is achieved. On the other hand, its query-driven model is not applicable to all WSNs. In addition, DD is not suitable for environment monitoring. Moreover, depending on the application, the naming scheme should be defined beforehand.
COUGAR [29] is a protocol that perceives the network as a distributed database system. It uses declarative queries to replace the network layer functions of query processing, as the selection of relevant nodes and utilizes in network data aggregation to save energy. To replace the network layer functions, it imports an additional layer, called query layer, between network and application layer. In COUGAR’s architecture, nodes select a leader node for data aggregation and transmission to the BS. Then, the BS generates a query plan, which also describes leader selection for the query, with information about in network computation and data flow for incoming queries and sends them to relevant nodes. The main advantage of COUGAR is that it provides energy efficiency even with huge number of active nodes. However, more overhead is added by the extra layer usage. Moreover, data computation in the network needs synchronization.
ACtive QUery forwardIng in sensoR nEtworks (ACQUIRE) [30] uses a data centric mechanism for query sending and perceives the network as a distributed database, as COUGAR, which can divide complex queries in many sub-queries. The BS transmits a query, which is forwarded from every node that receives it. Upon query forwarding, nodes use their pre-cached information to reply to the query partially, updating pre-cached information from neighbor nodes, when needed, within a d hops distance. After the query is resolved, it can be sent back to the BS either from the reverse path or the shortest path. ACQUIRE provides efficient queries with proper setting of look-ahead parameter d. The traffic behaves like flooding when look-ahead parameter d is equal to network size but when the parameter is significant small queries have to travel more. ACQUIRE provides efficient querying when responses are collected from many nodes. However, if the look-ahead parameter is too small, query travels more hops.
Energy aware routing [31] is a data centric routing protocol that constantly uses non optimal paths to maximize network lifetime. To pick one of these paths, it uses a probability function that depends on energy consumption of each path. This approach takes into consideration network lifetime as the only metric attribute. Instead of using the minimum energy path, it uses multiple routes with a certain probability to maximize network lifetime. The operation of the routing protocol has three phases:
- (i)
- Setup phase: Localized flooding is performed to find all paths from source to destination, calculate corresponding energy costs and create routing tables.
- (ii)
- Data Communication phase: Based on the energy costs calculated, routing paths are chosen probabilistically and data are sent from source to destination.
- (iii)
- Routing maintenance phase: With the intermittent use of localized flooding, routing paths are kept alive.
Energy aware routing protocol compared to DD provides greater energy efficiency. However, a single path use removes path failure tolerance. In addition, compared to DD, more complex routing paths are formed due to the storage of location information and the addressing mechanism.
Gradient Based Routing (GBR) [32] is a variant of Directed Diffusion. It combines the number of hops with interests and creates link heights and gradients to improve data communication. When an interest is diffused through the network, the number of hops is stored. Every node can find out the minimum number of hops to the BS, called node’s height. A link’s gradient is the difference of height between two neighbor nodes. A packet is transmitted through a link with a high gradient. The algorithm uniformly balances traffic over the network, which helps to balance nodes’ load and prolong network lifetime, using techniques as data aggregation and traffic spread, as nodes act as relays for multiple paths. It uses three data spreading techniques:
- (i)
- Stochastic design: the sender node picks one link in random in case there are two or more hops with the same gradient.
- (ii)
- Energy based design: when a node has energy below a specified threshold, it increases its height to discourage other neighbors to transmit data.
- (iii)
- Flow based design: flows from nodes that are part of other flows are prevented.
Compared to DD, GBR has lower communication energy consumption. In addition, GBR provides great load balancing. However, increased overhead is produced.
In [33], two schemes called Constrained Anisotropic Diffusion Routing (CADR) and Information Driven Sensor Querying (IDSQ) are introduced. In order to maximize information gain while maintaining latency and bandwidth at minimum, nodes are queried and data are routed by activating sensor nodes close to a specific event and data routes are dynamically adjusted. In this way, compared to Directed Diffusion, greater energy efficiency is provided. In addition, queries reach neighbors first. On the other hand, the combination of the processes creates overhead. In CADR, nodes evaluate objectives of information/cost and route packets based on local information/cost gradient and requirements of the end user. To model the information utility measure, standard estimation theory is used. In IDSQ, there is no defined routing of queries and information between nodes and the BS, but the way to select the optimal order of nodes for maximum incremental information gain is provided. Thus, IDSQ acts as an auxiliary optimization process.
A synopsis of the characteristics of Query based routing protocols is shown in Table 1.

Table 1.
Synopsis of communication model protocols belonging to query based subcategory.
2.2. Coherent/Non-Coherent
In this subcategory, nodes process collected data in the node level before they route them. In Coherent protocols, a node applies minimum processing only on the data it captures. On the other hand, in non-coherent routing protocols, nodes preprocess data they capture and send them to nodes, called aggregators, which further process them. In what follows in this section, two typical examples of this subcategory are described. A synopsis of their features is shown in Table 2.

Table 2.
Synopsis of communication model protocols of the Coherent/Non-Coherent subcategory.
Single Winner Algorithm (SWE) [34] elects an aggregator node, called Central Node (CN), to perform complex computations, depending on energy reservoirs and computational power. There are various message broadcasts before a CN can be elected. The first message is an announcement of nomination of each node and, when another node receives the message, it compares those candidates with itself. This comparison creates a second message broadcast, with the result of the comparison being sent again for another comparison, until a CN is elected. During the message broadcasts, better candidates create a minimum hop spanning tree, routed at the winning candidates, covering eventually the entire network. In SWE, great scalability is achieved. In addition, a minimum hop spanning tree is used. On the other hand, high energy consumption takes place when electing a CN. In addition, there is high overhead in CN.
Multiple Winner Algorithm (MWE) [34] is an extension of SWE to prevent extra energy and computational overhead when multiple sources send data to CN. In MWE, each node keeps records of best candidate nodes and a set of minimum energy paths to each source. Thus, both energy and overhead are saved. Then, SWE is used to elect the best candidate for CN to aggregate data. Thus, energy consumption is reduced and a set of minimum energy routes to each source is found. However, long delays are caused and the scalability achieved is limited.
2.3. Negotiation Based
In this subcategory routing protocols, a source node exchanges data with their destination after negotiating. These protocols name data based on a naming scheme and use these names to advertise, negotiate and eventually reduce redundant data at destination. In what follows in this section, SPIN family protocols, which are typical examples of this negotiation based energy efficient routing, protocols are described.
Sensor Protocols for Information via Negotiation (SPIN) [35] is a protocol that names the data using high level descriptors or meta-data. Before data transmission takes place, meta-data are exchanged among nodes via an advertisement mechanism. The meta-data format is no standard, but it depends on the application. Every node upon receiving new data advertises packets to its neighbors with advertisement messages (ADV). Interested neighbors, who do not have the data, send a request message (REQ). Then, sending nodes send the actual data (DATA) to interested nodes. This negotiation of meta-data not only solves the classic problems of Flooding, but also is more energy efficient. In addition, metadata negotiation reduces in half redundant data and changes in topology are localized. However, data delivery to destination is not guaranteed. This is because sensor nodes located between source and destination may not be interested. Furthermore, SPIN protocol is not appropriate for applications that require constant data delivery, such as intruder detection.
SPIN Point to Point (SPIN-PP) [36] is a variant of SPIN for communication between only two nodes that use the same 3-way handshake SPIN algorithm. When new data are available at a node, it sends ADV messages. Interested nodes send an REQ message back to the source, in order to show their interest for these new data. Then, the source replies with a DATA message containing the data. This algorithm is executed between two nodes, without any interference. In addition, as it happens in SPIN too, SPIN-PP does not take into consideration energy constrains. In SPINN-PP protocol, set-up simplicity is offered, and implosion is avoided. However, needless energy consumption takes place while data delivery is not guaranteed.
SPIN-Energy Conservation (SPIN-EC) [36] protocol uses the same algorithm of SPIN-PP but adds a heuristic of energy conservation. To take into consideration energy constraints, SPIN-EC uses an energy threshold. Nodes, whose residual energy is below this threshold, can receive ADV or REQ messages, but they will not send REQ messages if they are interested or will not handle DATA messages. SPIN-EC considers energy constraints and properly adapts its operation. However, nodes even below the low energy threshold keep consuming energy because they are still able to receive ADV and REQ messages.
SPIN for Broadcast Networks (SPIN-BC) [36] is another variation of SPIN protocol that uses one to many communications. The source sends the ADV message to all nodes in its range and interested nodes wait for a predetermined time before they send an REQ message. In case they receive an REQ message from another interested node, they cancel their REQ message to limit unnecessary requests. The source, in the case that it receives the REQ message, broadcasts the DATA message once, regardless of the number of REQ messages. SPIN-BC uses cheap one to many communications. It also achieves good scalability and generally performs better than SPIN-PP. However, there is a waiting time before sending the REQ message.
SPIN with ReLiability (SPIN-RL) [36] utilizes the SPIN-BC algorithm with an ADV message tracking mechanism and a limit of data transmission at sources. The ADV messages contain information of the source while receiving nodes store them for later use. An interested node sends an REQ message and, in the case that it does not receive the DATA, it resends the REQ message. The source node then waits for a specific time before it broadcasts the DATA again to the interested nodes. Generally, SPIN-RL is a more reliable protocol than SPIN-BC. Furthermore, SPIN-RL provides remarkable loss tolerance and good scalability. Yet, processing tasks performed increase overhead.
A synoptic overview of the characteristics of the aforementioned negotiation based routing protocols belonging to the Communication Model category is presented in Table 3.

Table 3.
Synopsis of Communication Model protocols of the Negotiation based subcategory.
3. Network Structure
Protocols belonging to the network structure scheme are classified in two subcategories according to whether the nodes are treated as equals or whether they are members of a hierarchy. These subcategories are: Flat and Hierarchical protocols as described below.
3.1. Flat
In Flat subcategory, nodes are considered to be equal entities with unique global addresses. Protocols of this type can be further classified into three different operational categories which namely are: proactive protocols, reactive protocols, and hybrid protocols.
3.1.1. Proactive
The proactive protocols are constantly active waiting to sense anything with the result of a quicker response and a greater energy consumption. In what follows in this section, two typical examples of proactive flat energy efficient routing protocols are described.
Wireless Routing Protocol (WRP) [37] is a table based protocol which uses the distributed Bellman–Ford algorithm. WRP maintains more accurate information and an up-to-date view of the network with the use of a set of tables. These tables are:
- -
- Distance Table (DT),
- -
- Routing Table (RT),
- -
- Link Cost Table (LCT),
- -
- Message Retransmission List (MRL).
The DT contains the distance of neighbor nodes while the RT contains the routes to them. Furthermore, LCT contains the transmission energy cost of the links and MRL contains a sequence number of the update messages, a retransmission counter, an acknowledgement-required flag vector, with every neighbor being one entry and a list of updates sent in the update message. Update messages are used by mobile nodes to inform each other of link changes. An update message, which contains the updates in a list, is transmitted among neighboring nodes. Another list that contains responses indicating which mobile nodes should acknowledge the updates. When a loss of a link occurs between two nodes, they transmit to their neighbors, update messages. Then, the neighbors change the entries of their DT and check for new paths among other nodes. These new paths are transmitted back to the original nodes, which in turn update their tables.
In WRP, faster route convergence during a link failure event is achieved. In addition, few table updates are needed. Additionally, minimized looping situations are caused. On the other hand, large memory and great processing power are required. At the same time, scalability provided is limited.
Topology Dissemination Based on Reverse-Path Forwarding Protocol (TBRPF) [38] compares previous and current network states and broadcasts the difference between them, which is a smaller routing message that can be sent more frequently. Similarly, TBRPF protocol creates spanning trees from source to destination, by calculating minimum-hop paths used to broadcast, in the reverse direction, link-state updates. After minimum-hop path calculation, every source creates a broadcast tree. Every node has a topology table that includes all link states, a list of neighboring nodes and a parent, a list of children, and a sequence number of most recent link state updates. New topology information is used to modify the spanning tree. The broadcast of a link-state update that originates at a source is accepted by another node, if it is received from the parent of the source and has a larger sequence number than the corresponding link-state entry in the topology table of the parent. Then, the topology table is updated and forwarded to all children of the node.
In TBRPF protocol, multiple paths to destination are obtainable. Another advantage of TBRPF is that less frequent updates are needed. On the other hand, the waste of both bandwidth and packet is produced because of loop-freedom.
A synoptic overview of the characteristics of the aforementioned proactive flat routing protocols belonging to Network Structure category is presented in Table 4.

Table 4.
Synopsis of Network Structure Protocols belonging to the Flat Proactive subcategory.
3.1.2. Reactive
The reactive flat protocols are actuated after an event has occurred leading in energy conservation, but also a slower response. In this subsection, five typical examples of protocols of this type are described.
Temporarily Ordered Routing Algorithm (TORA) [39] implements link reversal concept. Every node has an attribute called height, which is its location from the BS, with tall nodes being distant nodes and short being closer to the destination. When a link established the destination node compares its own height i with its neighbor height j, then the link is marked either upstream or downstream if j is greater than i or vice versa, respectively. The data packets flow through the downstream direction from distant nodes to closer to the BS nodes. In order for this algorithm to be energy efficient, control messages should be limited in a small area of nodes close to the event. The use of TORA reduces both energy consumption and communication overhead. Nevertheless, no incorporation of multicast in basic operation is achieved.
In Flooding [40], nodes broadcast data packets to all of their neighbors except the sender of the message, until the packet is received by its destination or the maximum number of hops is reached. Although Flooding does not require a routing algorithm to exist, in most cases, the destination will get its packet. In addition, it is resource blind because it generates network overhead with similar sensed data and it does not consider the energy reserves of nodes. It is easy to implement and requires no knowledge of network topology. On the other hand, neighbor nodes sensing the same region send similar data packets to the same neighbor node and high energy consumption without energy awareness is caused.
Gossiping [41] is another simple networking technique that solves the implosion problem of flooding and routes data without the need of a routing algorithm. During its operation, a source node picks a random neighbor node to send a data packet. Then, the receiver node picks another random neighbor to forward the packet and so on, until the destination receives the data. In Gossiping, implosion is avoided. On the other hand, delays in propagation of data are caused.
Rumor Routing (RR) [42] is an alternative of Directed Diffusion, operating between event flooding and query flooding. RR prevents flooding by creating agents whenever a node observes an event. These agents are broadcasted through the network creating paths to the event. When a query is created, it travels on random routes until it meets an agent, discovering the route to the event. If a query is unable to find any agent, the algorithm can either resubmit it or flood it.
RR is tunable to different application requirements and is able to maintain only one route from source to destination. In addition, less energy is consumed during event flooding and tolerance of node failures is achieved. However, RR performs worse as events get more. In addition, overhead is caused by adjusting used parameters.
E-TORA [43] is a variation of TORA with energy awareness. Instead of using only the shorter path nodes, it considers their energy level and prevents frequent use of low energy nodes, resulting in better network lifetime than TORA. Whenever a node needs new data, it broadcasts a query message and sets its route-required flag; receiving nodes operate as follows:
- (i)
- In case the receiving node has unset route-required flag and not any downstream links, the query packets are re-broadcasted and its route-required flag is set.
- (ii)
- In case the receiving node has set route-required flag and not any downstream links, the query packets are discarded.
In E-TORA, network lifetime is extended and node power level awareness is offered. On the other hand, multicast communication is not considered.
The main features of reactive flat energy efficient routing protocols are synoptically presented in Table 5.

Table 5.
Synopsis of Network Structure Protocols belonging to the Flat Reactive subcategory.
3.1.3. Hybrid
These protocols combine the benefits of proactive and reactive routing protocols. They use a proactive routing scheme locally to respond quickly and inter-locally, reactive routing scheme to respond more efficiently with lower energy consumption. In what follows in this section, two typical examples of hybrid flat energy efficient routing protocols are described.
Zone Routing Protocol (ZRP) [44] combines the advantages of proactive and reactive protocols. ZRP divides the network into zones and uses two schemes for routing, one for in-zone nodes, and one for nodes outside of it. These two schemes are:
- (i)
- Inter-zone routing: nodes inform their neighbors periodically, broadcasting notices when a link-state changes, resulting in nodes knowing a path to any other inter-zone node.
- (ii)
- Outside zone routing: nodes send route request (RREQ) to zone border nodes. Border nodes check in the zone node table, if they find a match to the request, they send a route reply (RREP), else they send a request to another border node until they find a route. Multiple routing paths are discovered with minimum number of query messages. On the other hand, simultaneous querying of nodes is not possible. In ZRP, only a small amount of routing information is required and less routing traffic is caused. However, excessive delays are caused.
Adaptive Threshold Energy Efficient cross layer based Routing (ATEER) [45] is a clustering protocol for heterogeneous WSNs that combines the properties of reactive and proactive network subcategories. ATEER operation consists of two models:
- (i)
- Network model: a model that focuses on cluster head selection and cluster formation.
- (ii)
- Radio energy model: a model used to calculate transmission energy consumption, reception, and data accumulation.
ATEER classifies sensor nodes into three modes, super-advanced, advanced and normal, depending on their residual energy level. Utilizing the energy classification, a cluster head can be elected by using a probability derived from the division of the network’s mean energy to the residual energy of candidate nodes. If the result is less than 1, then this node has a higher probability to be elected as a cluster head. In addition, cluster head and cluster nodes are connected via single-hop communication. In ATEER, increased network lifetime is achieved by utilizing node’s energy classification. In addition, redundant data are reduced. On the other hand, energy consumption is caused due to the periodic data sending of node’s residual energy information. Moreover, there is a lack of GPS navigation.
The main features of the aforementioned hybrid flat energy efficient routing protocols are synoptically presented in Table 6.

Table 6.
Synopsis of Network Structure Protocols belonging to the Flat Hybrid subcategory.
3.2. Hierarchical
In Hierarchical subcategory, a WSN is divided in clusters with an elected cluster head for each one. Cluster heads are used for high level communication with the BS, while cluster nodes monitor the environment and exchange data between neighboring nodes and cluster head. They are further divided into three subcategories depending on how they route data or how they divide the network area. These subcategories are Hierarchy based, Zone based, and Fuzzy logic based.
3.2.1. Hierarchy Based
Routing protocols of this kind create clusters with cluster heads and cluster nodes routing data through two levels of communication, a low level one for cluster nodes to cluster heads and a high level for cluster heads to BS. A core design attribute of hierarchical protocols is scalability. Within a single tier network when node number increases, the BS overloads resulting in communication latency and inadequate event tracking. The single BS design has scalability limitations for a greater set of nodes that cover a wider area of interest due to the fact that nodes are not capable of long distance transmission. Cluster’s formation criteria usually are nodes’ energy reservoir and proximity to cluster head. Actually, hierarchy based hierarchical protocols constitute the most popular subcategory of energy efficient routing protocols. In what follows in this section, 59 typical examples of this type are described.
Low Energy Adaptive Clustering Hierarchy (LEACH) [46] is one of the first hierarchical clustering protocols. It creates clusters of nodes based on signal strength and use cluster heads to aggregate, compress, and transmit packets to the BS. The optimal cluster head number is estimated around 5% of total nodes, while all of the processes as data fusion and data aggregation are performed locally in the clusters. During LEACH operation, cluster heads change randomly to balance remaining energy and network lifetime. In the cluster formation process, nodes compare signal strength of their neighbor cluster heads and join the one with the strongest signal. When a node becomes a cluster head, it cannot become once again for P rounds. In order for a node n to become a cluster head, this node picks a random number between 0 and 1 and calculates the threshold T by using (1):
where P is the desired cluster head percentage, G stands for the set of nodes, and r represents the number of the round selected by the cluster head. Then, the specific node becomes cluster head for this round if the number is below this threshold.
In LEACH, transmissions are reduced, resulting in reduced energy loss. In addition, global network knowledge is not required. However, as it uses single hop routing, it is not suggested for sensor networks deployed in large areas. In addition, dynamic clustering creates overhead that may shrink gain in energy consumption.
Low-Energy adaptive Clustering Hierarchy-Centralized (LEACH-C) [47] is a variation of LEACH that forms clusters using the BS. During clustering, nodes transmit to the BS energy level and location information. The BS divides the network into a fixed number of clusters and their cluster heads, based on the energy needed during data transmission from cluster nodes to their cluster heads. In LEACH-C, more energy efficient clusters for data transmission are produced. In addition, the optimal number of cluster heads is predetermined. On the other hand, overhead is produced to the BS.
Quadrature-LEACH (Q-LEACH) [48] is a clustering protocol for homogeneous WSNs, based on LEACH, which divides the network into four equal, parts based on location information and uses an innovative method for cluster head election. For cluster head election in Q-LEACH, every sensor node chooses a random number between 0 and 1, while in every sector there is a threshold between 0 and 1. In the case that the random number of a sensor node is less than the threshold of the network part, which has been set, then the node becomes the cluster head, and broadcasts it to the network. Normal nodes select their cluster head within their own sector based on the Received Signal Strength Indicator (RSSI) of the broadcasting and communicate with it using their assigned TDMA slot. In Q-LEACH, cluster head election does not consume energy and improved network lifetime is achieved. However, the energy holes of the network may be increased.
Universal-LEACH (U-LEACH) [49] is a clustering routing protocol that combines Improved LEACH operation and the chain formation of PEGASIS. U-LEACH elects cluster heads by taking into consideration node residual energy and forms clusters based on their position on an x-axis. After clustering, it uses the chain formation process of PEGASIS to construct a chain starting from the distant cluster heads within every cluster and ending at the BS. Cluster heads transmit their data to the master cluster head, which aggregates data and forwards them to the BS. In U-LEACH, greater network lifetime is achieved due to the reduction of the energy consumption. On the other hand, the distance between master cluster head and the BS are not taken into consideration.
Hybrid-LEACH (H-LEACH) [50] is a protocol used to face the problems of LEACH and HEED protocols, such as energy holes and the inability to elect cluster heads based on different energy levels. To deal with these issues, it blocks low energy nodes to be elected as cluster heads. H-LEACH takes into account the maximum energy of a node, its remaining energy, the energy required for data transmission, and the probability of energy usage, and implements a threshold value. The nodes below the threshold are considered dead. Furthermore, to evaluate the routing paths, it uses the distance between transmitter and receiver. Finally, cluster heads transmit data to the BS by utilizing TDMA. By using H-LEACH, the network lifetime is extended. On the other hand, the number of unused nodes which are below the threshold is high.
Three-Layer LEACH protocol (TL-LEACH) [51] is another clustering protocol for WSNs, based on LEACH, which reduces the number of nodes that communicate directly to the BS with a similar cluster head election as in LEACH.
The network is divided into three layers as follows:
- (i)
- Layer 0 sensor nodes.
- (ii)
- Layer 1 cluster heads elected from Layer 0 nodes.
- (iii)
- Layer 2 cluster heads elected from Layer 1 cluster heads.
Layer 0 nodes sense the environment and send their packets to layer 1 cluster heads; data packets are forwarded there to layer 2 cluster heads and eventually to the BS. In every round, nodes elect themselves randomly as layer 1 cluster heads, while layer 2 cluster heads are elected based on the residual energy of layer 1 cluster heads. Furthermore, in the next rounds, cluster heads are changed randomly, while information from layer 1 cluster heads are fused in layer 2 cluster heads to be sent to the BS later. With the use of TL-LEACH, the number of sensor nodes communicating with the BS is low and the network lifetime is prolonged. On the other hand, the three-layer scheme used creates overhead.
Enhanced Heterogeneous LEACH (EHE-LEACH) [52] is an enhanced version of LEACH for heterogeneous WSNs. EHE-LEACH combines the BS to node direct communication and the BS to cluster communication, based on a fixed distance threshold value. In EHE-LEACH nodes located close to the BS, i.e., those whose distance from the BS is below the distance threshold value, do not form clusters and communicate directly with the BS while the others operate within a cluster with an elected cluster head each. In order to reduce energy consumption, there are nodes with two energy levels, normal and advanced, with advanced nodes having higher energy reservoir than normal ones. Furthermore, for improved energy efficiency and network stability, EHE-LEACH gives higher probability during cluster head election to advanced nodes rather than normal ones. On the other hand, non-clustered nodes do not implement a sleeping schedule, thus consuming more energy.
Improved-LEACH (I-LEACH) [53] is another modification of the LEACH protocol that improves the processes of cluster head selection and cluster formation. I-LEACH, during cluster head election, implements a threshold and takes into account three parameters which namely are:
- (i)
- Number of Neighbors.
- (ii)
- Residual Energy.
- (iii)
- Ratio of the average distance of nodes from the BS and the distance between each individual node.
In order for a node to be elected as a cluster head, it needs to have a high number of neighbors, greater residual energy than the average nodes of the network, and be close to the BS. The result of the above three parameters is a number ranging from 0 to 1. In case the number is under the threshold, the node can be elected as cluster head. During cluster formation, a selection priority is used, based on the distance between cluster head and BS, to reduce energy consumption during packet transmission of remote cluster heads. Moreover, to improve the network’s performance, the BS is located in a remote point of the sensor node covered area. The use of I-LEACH assures network stability and reduces energy consumption. However, there is lack of a data aggregation mechanism.
LEACH-Expected Residual Energy (LEACH-ERE) [54] is another clustering protocol for homogeneous WSNs, based on LEACH. It introduces the Expected Residual Energy (ERE) value and can be suitable for WSNs having the BS far away from the node deployment field. The ERE value is the predicted remaining energy in case the node is elected as a cluster head. In LEACH-ERE, cluster head election happens at the end of each round using a random number generation function between 0 and 1 and a predefined threshold, which is the percentage of the tentative nodes. Cluster nodes with bigger generated numbers of the threshold become cluster heads and calculate the chance, utilizing a fuzzy inference system, with inputs the residual energy and the ERE value. A bigger chance results in a higher possibility to be elected as a cluster head.
LEACH-ERE achieves stable performance. On the other hand, it provides no consideration of distance to the BS, resulting in early death of faraway nodes.
The Three Level Hierarchical Clustering LEACH Protocol (TLHCLP) [55] is another clustering protocol based on LEACH, for homogeneous WSNs that sets a radius around BS, to include some nodes within it and exclude the others. TLHCLP tries to distribute cluster heads evenly and divides the network into three layers:
- (i)
- Layer 1, which includes nodes collecting data and sends them to layer 2.
- (ii)
- Layer 2, which includes the cluster heads that gather data from layer’s 1 nodes.
- (iii)
- Layer 3, which includes nodes and cluster heads inside the radius of the BS.
During data transmission, only cluster heads within the radius of the base station are allowed to send data to it directly, the cluster heads outside the radius forward data to the cluster heads within the radius. The use of TLHCLP extends network lifetime. However, data redundancy is high close to the BS.
Dominating Set based modified LEACH using Ant Colony Optimization for data gathering (LEACH-DS-ACO) [56] is an improvement of THLCLP used to overcome the problem of redundancy of TLHCLP. It combines a Dominating Set algorithm (DS) for cluster formation and Ant Colony Optimization (ACO) to shorten transmission distance within a cluster, in order to reduce the chain lengths of it. LEACH-DS-ACO extends network lifetime. On the other hand, mobility is not supported.
Power Efficient Gathering Sensor Information System (PEGASIS) [57] is an improvement of LEACH protocol, which, instead of creating clusters, it creates chains of nodes. The main characteristic of a chain is that every node transmits data only to the two nearby neighbor nodes and only one sensor node can be selected to communicate with BS. Collected data are transferred from node to node being aggregated and finally transmitted to the BS. PEGASIS provides higher energy efficiency than LEACH. In addition, less broadcasts use data aggregation. On the other hand, large delay is caused for distant nodes. In addition, redundant data are transmitted. Moreover, single leader mechanism may cause congestion.
Hierarchical PEGASIS [58] is an extension of PEGASIS that tries to reduce the delay that occurs from packets during transmission to the BS and offers a solution to data collection problem taking into account the metric Energy x Delay. Simultaneous packet transmission used to reduce delay and suggests two approaches to prevent collisions and signal interference among sensor nodes. The first approach is called CDMA and incorporates signal coding while the second approach spatially separated nodes only can transmit packets simultaneous. The protocol with CDMA nodes can construct chains with a tree like hierarchy, in which a selected node in a specific level transmits data to a node in the higher level of the hierarchy. This method ensures parallel data transmission and reduces delay. On the other hand, the protocol without CDMA creates a three-level node hierarchy that reduces interference problems with carefully scheduled simultaneous broadcasts. However, significant overhead is caused.
Multi-Hop PEGASIS (MH-PEGASIS) [59] is an improved version of PEGASIS, which utilizes inter-cluster communication and multi-hop routing to reduce energy consumption during data transmission of distant cluster heads to the BS. In MH PEGASIS, every round consists of two phases the initialization and the data transmission phases. During the initialization phase, an inter cluster communication happens where every node communicates with its neighbors. Receiving nodes aggregate data with their own and transmit them until the cluster head receives them. During the transmission phase, cluster heads forward their data to upper level cluster heads until they reach the BS. In MH PEGASIS, the energy consumption of distant cluster heads is reduced and the network lifetime is extended. On the other hand, load balancing issues are caused.
Enhanced PEGASIS [60] is an improved version of PEGASIS protocol, which reduces redundant data during transmission. To achieve this, the BS divides the network into levels depending on how strong the receiving signal of a node is. To determine optimum number of levels, enhanced PEGASIS takes into account various parameters such as network’s density, the BS location, number of nodes, and application requirements. As performed in the original PEGASIS, within the level area, chain construction begins from the farthest nodes utilizing a greedy algorithm. Cluster heads collect data from nodes within the same level and forward them to the lower level until they reach the BS while higher level nodes are the most distant ones. In Enhanced PEGASIS, redundant data are reduced. However, delay is high in distant nodes.
Threshold sensitive Energy Efficient sensor Network (TEEN) [61] is one of the most popular hierarchical protocols. It has been designed for time critical applications, where the network operates in reactive mode, responsiveness is very important. TEEN’s architecture is based on hierarchical clustering with a use of a Data-Centric mechanism. Distant nodes form first level clusters, while nearby nodes form second level clusters until a route to the BS is formed. After cluster formation process, two thresholds for sensed characteristics, which namely are Soft Threshold (ST) and Hard Threshold (HT), are broadcasted to cluster nodes from cluster heads. HT is the minimum value of a sensed parameter that a node needs to sense in order to activate its antenna and transmit it to a cluster head. In addition, it allows nodes to transmit only when the characteristic is in the range of the interest reducing significantly the number of broadcasts. Furthermore, it transmits data only when the value of this characteristic changes by an amount equal or greater than ST from the previous sensed value. Consequently, the use of ST reduces further the number of transmissions in the case that there is little or no change in the value of the sensed parameter. Both hard and soft thresholds can be adjusted in order to control the number of packet transmissions. TEEN provides higher energy efficiency than LEACH and LEACH-C and reduces the number of broadcasts. However, both overhead and complexity are high during multiple level cluster creation. Furthermore, periodic communication is not possible due to the reactive nature of the protocol.
AdaPtive ΤΕΕΝ (APTEEN) [62] is the extension of ΤΕΕΝ that aims both in capturing data collections and reacting in time critical events. When the BS has formed clusters, cluster heads broadcast, to every cluster node within their cluster, attributes, threshold values, and transmission schedule. Then, cluster heads perform data aggregation, before they forward data to the BS, to save energy. APTEEN follows the same architecture of TEEN but supports three different query types:
- (i)
- Historical query, used to analyze past data values.
- (ii)
- One-time query, used to take snapshot view of network.
- (iii)
- Persistent query, used to monitor an event for a period of time.
In APTEEN, energy dissemination is less than that in TEEN. However, APTEEN is more complex than TEEN and has longer delay times.
Virtual Grid Architecture (VGA) [63] is a protocol that utilizes a multi-level data aggregation and procession during data routing, in order to improve network lifetime and energy efficiency. VGA’s routing consists of two phases:
- (i)
- Clustering aggregated data phase: divided in stationary clusters, the cluster head nodes, called Local Aggregators perform data aggregation. Master Aggregators, a part of Local Aggregator nodes, perform global or inter-cluster aggregation.
- (ii)
- Routing aggregated data phase: in order to achieve an optimal and efficient solution, it uses heuristics, such as correlation of sensing information, in overlapping groups of Local Aggregator nodes.
In VGA, energy efficiency is high, but the non-deterministic polynomial time problem of optimal selection of local aggregators as master aggregators exists.
In Two-Tier Data Dissemination (TTDD) [64], protocol sinks are able to move dynamically, while sensor nodes are static and location aware. Event data are created from a source node, which is the node closer to the event. The source builds a virtual grid, with itself as the first crossing point and transmits a message, with greedy geographical forwarding, at four different adjacent crossing points. The message stops when it reaches a node close to the crossing point and transmission ends when the boundaries of the network are reached. TTDD can be used for multiple mobile sinks in an area with static nodes. On the other hand, a virtual grid structure has to be built by each source node.
Base-Station Controlled Dynamic Clustering Protocol (BCDCP) [65] forms balanced clusters in terms of energy level and number of cluster nodes. Nodes transmit energy level information to the BS, which is a high energy node that calculates the average energy level. The BS selects nodes with energy level above the average level as cluster heads and forms clusters with similar number of cluster nodes. Furthermore, data transmission to the BS is achieved through a cluster head to cluster head routing. In BCDCP, cluster head overload is avoided and uniform placement of cluster heads is achieved. However, there is decreased performance gain for a small field area.
Equalized Cluster Head Election Routing Protocol (ECHERP) [66] is a hierarchical routing protocol that uses the Gaussian elimination algorithm for the cluster head selection. In the initialization phase of ECHERP, the BS uses an advertisement TDMA schedule in order to get information regarding the location and the energy conservation of each individual network node. Next, the BS uses the Gaussian Elimination algorithm to compute, by considering all possible node combinations, the energy outflow that every single node will have if it becomes a cluster head at the very next round. In this way, the combination of cluster heads that minimizes the overall energy consumption is both discovered and selected. Gaussian elimination is executed in two phases. During the first phase, the rank of the linear system built, which represents the energy spent, is reduced by using the forward elimination technique. In the second phase, the solution of this system built is found by using the back-substitution technique. Next, the base station notifies the IDs of the newly elected cluster heads and it transmits them to the network for the cluster nodes to join the clusters. Finally, each cluster head uses a TDMA schedule in order to collect data from the nodes that belong to its cluster and then sends aggregated information to the BS either directly (if possible) or via upper level cluster heads. ECHERP achieves high energy efficiency, good scalability, and better overall performance compared to LEACH, PEGASIS, and BCDCP. On the other hand, metrics related to QoS and time constraints are not considered.
Multi-hop virtual Multiple Input Multiple Output (MIMO) [67] is a protocol that uses multiple nodes to collect and transmit event data with multiple hops to a remote BS. The network is divided in clusters where cluster heads communicate only with in-cluster nodes, which use Space-Time Block Code (STBC) for data encoding and transmission. Due to the short range of the intra-cluster communication, it assumes the use of an Additive White Gaussian Noise Channel with squared power path loss. MIMO achieves good energy saving, but may perform below optimal performance.
Hierarchical Power Aware Routing (HPAR) [68] protocol takes into consideration both the transmission power and the minimum battery power of nodes in routing paths. Specifically, first neighboring nodes are grouped in formations called zones and then it applies a maximum battery life policy. This policy uses an approximation algorithm called max-min ZPmin. At first, this algorithm discovers the least power consumption path. Then, it finds another path that maximizes the minimum battery energy. Finally, by taking into consideration both outcomes, the optimal routing path is discovered. In HPAR, both the transmission power and the minimum battery power are considered. In addition, the use of zones supports scalability. On the other hand, high overhead is caused.
Sleep/Wake Scheduling [69] is a hierarchical protocol that divides the network into clusters that consist of a cluster head and cluster nodes and implements two radio modes, sleep, and wake. During Sleep/Wake Scheduling operation, a node can put its radio module into sleep mode, when there is no traffic in the network and into wake mode, when a node transmits or receives a packet. The key point is that it synchronizes sender and receiver, so that they can be put to sleep or wake mode at the same time with accurate synchronization, while random errors can occur due to system’s non-deterministic factors. In addition, a cluster head can be also a cluster node resulting in a complex multi-level structure that supports multiple paths. With Sleep/Wake Scheduling, energy saving is achieved with sleep mode and congestion awareness is accomplished. However, the algorithm complexity causes overhead.
Grid Based Data Dissemination (GBDD) [70] is a protocol in which the BS expresses an interest in data communication, and constructs a grid of squared cells. The sides of the cell have of a size a, containing a node. The size a is determined by two radio ranges that every node is capable of high power range (RH) and low power range (RL). The BS uses its geographical coordinates (x, y) as the starting point of grid cell formation and sets itself as the crossing point of the grid. In GBDD, continuous data delivery from source to the BS is achieved. Another advantage of GBDD is that only the BS constructs the grid. A disadvantage of GBDD is that, at high speeds, more energy is consumed.
Extending Lifetime of Cluster Head (ELCH) [71] protocol uses an election scheme, where cluster nodes vote their cluster heads and multi-hop routing between cluster head and the BS communication.
ELCH operation consists of two phases:
- (i)
- Election phase. The neighboring nodes form clusters and elect a cluster head using a voting scheme.
- (ii)
- Network preparation phase. The cluster consists of neighboring nodes and one cluster head. Afterwards, cluster head uses the TDMA mechanism to transmit the time slot of every cluster node and maintains a maximum power table each round for every node. Then, data communication begins, data flow from cluster nodes directly to cluster head while each cluster head communicates with each other and the BS using multi-hop routing.
In ELCH, energy consumption is kept low and thus the network life is prolonged. However, in the case that the number of cluster nodes exceeds a specific amount, network operation faces a negative effect.
Novel Hierarchical Routing Protocol Algorithm (NHRPA) [72] performs only one initialization node process during sensor node network deployment. NHRPA mainly uses loop, judgment, and assignment operations to deal with nodes and considers node distribution density, nodes residual energy, and node to the BS distance to adopt a suitable routing technology. The use of NHRPA achieves balanced energy consumption and can adopt suitable routing technology. However, packet latency is caused.
Scaling Hierarchical Power Efficient Routing (SHPER) [73] is a hierarchical energy efficient protocol which aims to extend the network lifetime as much as possible by both using the optimal routing paths and keeping alive the weakest network nodes. The operation of SHPER consists of two phases:
- (i)
- Initialization phase: In this phase, the BS transmits a TDMA schedule and requests of the nodes to advertise themselves. Then, the nodes transmit their advertisements and their in-between distances are identified. After that, the BS elects a predefined number of high and low level cluster heads, based on their residual energy, then it broadcasts new cluster head IDs and threshold values. High level cluster head is closer to the BS and communicates with it via single-hop routing, while low level cluster heads are the distant ones and need to route data to the BS via the high level cluster heads.
- (ii)
- Steady state phase: Each cluster head defines the most energy efficient path to route its messages to the BS by taking into account both the residual energy of sensor nodes and the energy cost of data transmission. Thus, weak nodes are preserved. Nodes transmit sensed data if their sensed value is above the hard threshold and changed from their previous value by the soft threshold.
SHPER attains high energy efficiency because it both achieves even energy depletion of nodes and performs routing via the most energy efficient paths. In addition, due to its hierarchical architecture, it attains high scalability. When the energy reserves of nodes are unequal and the BS is far away from the network field, the use of SHPER protocol becomes even more beneficial. However, mobility is not considered.
Power Efficient Multimedia Routing (PEMuR) [74] is based on SHPER protocol and combines hierarchical energy efficient routing and video packet scheduling models. It is ideal for video communication over Wireless Multimedia Sensor Networks aiming at both energy savings and high QoS. The operation of PEMuR consists of two phases, which namely are the initialization and the steady state phase. During the initialization phase, the nodes become members of the upper and lower level clusters which are created by the BS. The cluster heads inform the BS the energy status of all of their cluster members. During the steady state, the nodes having the highest residual energy in each cluster are elected to be the new cluster heads. Additionally, the soft, hard, and energy thresholds are defined. Nodes are supposed to transmit whenever their residual energy is below the energy threshold or the values of sensed parameters meet conditions related with hard and soft thresholds. Messages are routed from the cluster heads to the BS via direct communication in case they are upper level cluster heads or via intermediate upper level cluster heads if they are lower level. In both cases, energy efficient routing is achieved, by taking into consideration both the energy conserves of the nodes and the energy cost of data transmission.
Moreover, PEMuR protocol proposes an analytical model that can accurately predict for every packet the effect that its loss has on the resulting distortion of decoded video. Thus, PEMuR can successfully cope with limited available channel bandwidth by selectively dropping less significant packets prior to their transmission. PEMuR achieves great energy efficiency and good scalability along with high preservation of QoS in multimedia content transmission. However, there is lack of mobility considerations.
Novel Energy Aware Hierarchical Cluster based (NEAHC) protocol [75] is a hierarchical protocol designed to limit the unbalanced energy consumption of the sensor nodes of multi-hop protocols. In a multi-hop network, data travel from the cluster head to the BS, while energy consumption depends on the distance and the number of hops, between the sending and the receiving node. Nodes close to the BS need to relay more data than the distant nodes and consume more energy. Before cluster head election, NEAHC chooses one cluster head, depending on its residual energy and a lower number of switches between sleep and active modes, in order to balance energy consumption. The great advantage of NEAHC is that energy holes are less likely to occur. On the other hand, cluster head selection increases the network energy consumption In addition, nodes in sleep-mode may cause network disconnections.
Hierarchical Energy-Balancing Multipath (HEBM) [76] is a hierarchical routing protocol with an adaptive clustering scheme, for homogeneous WSNs and a static base station with unlimited energy reservoir and communication power. It calculates the best cluster size balance, resulting in a minimum energy network topology. HEBM operates in time intervals or rounds, which consist of six phases. Before it calculates cluster sizes and considering network’s density and size, it separates the nodes into clusters. By utilizing cluster range and the minimum energy path to cluster head, the levels of the network are formed. HEBM algorithm ensures a fairly distributed network because cluster head election considers network residual energy and distance from neighbor nodes. In this way, load balancing is achieved. Moreover, less message delays occur. On the other hand, extra overhead from collecting network data and calculating cluster size is caused. In addition, mobility is not supported.
Energy Efficiency Semi-StatiC routing algorithm (EESSC) [77] is a hierarchical protocol based on an improved HAC (Hierarchical Agglomerative Clustering) approach. EESSC operation consists of four steps:
- (i)
- The BS sends a message to all nodes of the network to activate them,
- (ii)
- Utilizing the HAC method sensor nodes form clusters and the LNC (List of Nodes in Cluster).
- (iii)
- Sensor nodes begin to operate while the cluster head within a cluster would be rotated according to LNC.
- (iv)
- In case every node within a cluster has low energy, disabling it to operate as a cluster head, the network will perform a re-clustering.
The use of EESSC achieves energy saving and solves the problem of energy holes. On the other hand, the distance between a node and a cluster head is not considered.
Distributed Energy Efficient Clustering (DEEC) [78] is a hierarchical routing protocol for heterogeneous WSNs following the operation principles of LEACH protocol. In DEEC during the cluster head election process, the nodes calculate an election probability, which derives from the ratio between their residual energy and the network’s average energy. Furthermore, the number of rounds that the nodes will perform as a cluster head, defined as rotating epoch, is calculated from the initial and residual energy. Therefore, higher initial and residual energy nodes are more probable to be elected as cluster heads. By using DEEC, energy efficient performance is achieved in multi-level heterogeneous networks with more than two energy levels. In addition, the global knowledge of the network energy is not required. However, DEEC is not suitable for time critical applications.
Hybrid Energy Efficient Routing (HEER) [79] is reactive routing protocol that combines the operations of TEEN and DEEC protocols. The cluster head election process is based on DEEC along with the threshold mechanism of TEEN. During the election phase of HEER protocol, nodes elect themselves as cluster heads by using the node’s initial and residual energies as in the DEEC protocol with higher energy nodes becoming more often cluster heads. After the cluster head election process, the cluster head sends to its members the threshold values HT and ST, in a similar way as in TEEN protocol, resulting in a smaller number of data transmissions. In this way, the network lifetime is prolonged. Additionally, HEER can be applied in time critical applications, operating in both heterogeneous and homogeneous networks. Its disadvantage is that it lacks data aggregation at the sink node and causes data flooding.
Improved Inter-Cluster Data Aggregation HEER (IICDAHEER) [80] is an improved version of HEER, which adds inter-cluster data aggregation and additive and divisible functions to minimize packet number. Cluster head election and the values of HT and ST are the same as in the HEER protocol. Additive function combines different data packets generated from the nodes while the divisible function is used when the generated data packets, of the inter-cluster nodes, are the same. In this way, IICDAHEER prolongs even higher energy efficiency. However, the protocol considers the BS to be located at the center of the area.
Hierarchical Energy Efficient Reliable Transport Protocol (HEERTP) [81] is a hierarchical cluster based protocol, which reduces energy consumption during redundant data transport over a WSN and cluster head election. To address these problems, HEERTP protocol divides the network in clusters and elect cluster heads, which are responsible for collecting cluster’s data and handle redundancy by aggregating redundant data. Furthermore, receiver nodes utilize a data table, which is updated in case they receive useful data and timeouts, which, when they occur, receiver nodes check for redundant data. In order to further improve energy savings, a cluster head is elected by its residual energy and position, without spending communication energy. HEERTP protocol can also elect a cluster head by electing a Root cluster head (RCH), which is a node close to the BS that analyzes data it receives from the other cluster heads. In HEERTP, both energy consumption during cluster head election and redundant data are reduced. However, useful data may not be sent to the BS.
Energy-Aware for cluster based sensor networks [82] protocol suggests a different hierarchical approach, a three-tier architecture, in which clusters are formed before network operation. This algorithm deploys less energy constrained cluster heads that are assumed to know nodes location. These cluster heads, also called gateways, set up multi hop routes and maintain node states. Nodes use a TDMA based MAC for data transfer to getaway nodes, which are only allowed to communicate with the BS. Every node can operate in active or low-power modes. Sensing and processing circuits can be turned on and off independently resulting in four operating modes:
- (i)
- Sense only
- (ii)
- Relay only
- (iii)
- Sense-Relay
- (iv)
- Inactive
In Sense only mode, the node searches the environment and generates data in a constant rate. In Relay only mode, sensing circuits are shut down and only relaying circuits operate and transmit data to and from other nodes. In Sense-Relay mode, a node senses and transmits message from other nodes. Finally, if a node is in Inactive mode, sense and relay circuits are turned off. Using a cost function to calculate link cost, a minimum cost path can be found. The gateway node will monitor available energy levels of every node that is active in one operating mode. The rerouting process is triggered by an application related event that requires a different set of nodes that monitor the environment or battery level of active nodes. The protocols achieve high energy efficiency. However, many gateways may be required to ensure high coverage.
The authors of Self-organizing protocol [83] developed a taxonomy of sensor applications and proposed an architecture to build sensor applications. This protocol supports heterogeneous sensor nodes that can be either mobile or stationary, can sense the environment, and relay data to a set of nodes, called routers, which are static and the backbone of communication. Router nodes relay data from sensor nodes to more powerful sink nodes. In order to tolerate faults, self-organizing protocol uses a Local Markov Loop (LML) algorithm in data transmission which picks a random path in the spanning tree of a graph. There are four phases in the self-organizing algorithm:
- (i)
- Discovery phase: Every node discovers neighbor nodes.
- (ii)
- Organization phase: Groups that are formed and merged forming a hierarchy where every node has an address based on its hierarchy position. Then, size O (logN) routing tables are created and, after that, broadcast trees that span all nodes are constructed.
- (iii)
- Maintenance phase: In this phase, routing tables and node energy levels are being created. LML is used to maintain broadcast trees.
- (iv)
- Self-organization phase: If an error of partial or whole node groups, re-organizations are performed.
In Self-organizing protocol low maintenance of routing table is required. In addition, hierarchical routing maintenance is strictly balanced. Moreover, less energy consumption than SPIN occurs when broadcasting messages. Furthermore, the use of LML in relaying trees can tolerate faults. On the other hand, not on demand organization phase results in extra overhead. In addition, organization phase is performed again if many network disruptions take place during hierarchy forming, thus resulting in extra overhead.
Distributed Hierarchical Agglomerative Clustering (DHAC) [84] is a hierarchical protocol, which suggests that a node needs only to know its next hop neighbor to build clusters. During cluster formation in DHAC, nodes initially obtain input data set and build a resemblance matrix. During this process, nodes elect themselves as cluster heads and exchange information via HELLO messages with their neighbors. Then, the DHAC algorithm is executed and each cluster head establishes its local resemblance matrix to find the minimum coefficient, then every cluster determines its minimum cluster head. After that, it cuts the hierarchical tree if the predefined upper limit size of clusters is reached. Next, DHAC controls the minimum cluster size, which can be used as a lower limit size by using the procedure Merge Clusters. Finally, cluster heads with lower id between two nodes that join the cluster on the first step are chosen. This procedure does not require additional processing. DHAC and then uses the sequence of nodes merging into clusters following the schedule while every cluster node gets an assigned role and starts to communicate in turns with cluster head. By using DHAC, network lifetime is prolonged. However, the performance worsens when network traffic gets high.
Hybrid Energy Efficient Distributed (HEED) protocol [85] is a clustering protocol in which cluster head election is based mostly on residual energy and other parameters as distance from neighbors or number of neighbors. In HEED, cluster formation function is triggered in given intervals for cluster head election and uncovered nodes, those without a cluster head, which can elect themselves as one. Furthermore, HEED parameters such as minimum selection probability, which is a probability for a node to be elected as a cluster head and network operation interval, which informs the user about how frequent cluster head election process happens can be tuned easily for better optimization in case of the requirements of an application such as network’s density. The low communication cost and the good scalability are the main advantages of HEED. On the other hand, different energy levels are not considered.
Stable Election Protocol (SEP) [86] is a hierarchical routing protocol for heterogeneous WSNs with two energy-leveled nodes, normal and advanced, which increases the stable period during the clustering hierarchy process. SEP is a dynamic protocol in terms that there is a random deployment of the two energy leveled nodes.
In addition, during the cluster head election, the nodes elect themselves as cluster heads, depending on their initial energy in respect to the energy of other nodes without any requirement of global knowledge of residual energy during each cluster head election round. SEP achieves network lifetime prolongation. In addition, global knowledge of residual energy during the round of cluster head election is not required. Its disadvantage is that the cluster heads are elected based only on their initial energy level.
Enhanced-Stable Election Protocol (E-SEP) [87] is an improved version of the SEP algorithm for heterogeneous WSNs. To maintain a more uniform energy consumption, among the nodes, it uses a clustering algorithmic approach with a three-tier node configuration. E-SEP uses Constant Bit Rate (CBR), a common traffic pattern used in clustering for heterogeneous networks. During the clustering process, the three-tier heterogeneous nodes elect themselves as cluster heads depending on their residual energy, resulting in uniform energy distribution between the nodes. E-SEP attains both increased network lifetime and improved resource sharing. Its disadvantage is the uncontrolled number of associated cluster nodes within each cluster results in load imbalances.
Energy Aware Distributed Clustering (EADC) [88] is a cluster based routing protocol for non-uniform node distribution WSNs, which combines an energy-aware clustering algorithm and a cluster based routing algorithm and can operate with heterogeneous nodes. During the setup phase, the nodes are divided into equal clusters. EADC balances the energy consumption of the cluster heads by modifying the intra-cluster and inter-cluster consumption with the use of a cluster based inter-cluster routing algorithm. Each cluster head picks another cluster head as its next hop, based on its residual energy and the number of its cluster nodes. The non-uniform node distribution causes imbalanced energy consumption, which EADC implements an increased forwarding task of cluster heads in sporadic areas to solve it. EADC elongates network lifetime. The Relay node is elected based on residual energy and number of cluster nodes only.
Improved Energy Aware Distributed Clustering (I-EADC) [89] is an improved version of the EADC protocol that solves the energy imbalance in non-uniform node distribution. During clustering, the network area is divided into equal clusters and cluster heads are elected according to their residual energy. Relay nodes are cluster heads, elected based on their energy estimate, to transfer data from the other cluster heads to the BS. Cluster nodes transmit packets to their cluster heads using single-hop and cluster heads send their data to the BS via direct communication or via relay nodes. I-EADC extends network lifetime and is applicable in both uniform and non-uniform distributions. However, in this protocol, there is a lack of energy balancing in inter-cluster communication.
Chain Based Cluster Cooperative Protocol (CBCCP) [90] is a clustering protocol suitable for real-time applications that divides the network into clusters, elects cluster heads as well as Cluster COrdinators (CCOs), and performs a multi-hop packet transmission from the clusters to the BS through the CCOs. During the clustering process, the number of clusters is derived from the SEP algorithm. Initially, cluster heads, used to aggregate cluster’s data, are elected randomly as in LEACH protocol, but, in the next rounds, cluster head election is based on a predefined energy level threshold. When the residual energy of a cluster head drops below the threshold value, the cluster head election process begins again. During data transmission, CBCCP reduces energy consumption with the use of CCOs to transmit data packets to the next clusters until they reach the BS. Within every cluster, there are multiple CCOs depending on the number of the nearby clusters, each transmitting data to one of them. CCOs follow the same election process as the cluster heads. In CBCCP protocol, not only is the clustering process simple, but also load balancing is achieved and long delays are avoided. However, energy balancing problems for inter-cluster communication are not taken into consideration.
Well Balanced TEEN (WB-TEEN) [91] is an improved version of TEEN that balances the size of the formed clusters. During the cluster formation process, every cluster head informs the other nodes with a packet including an identifier; then, every node sends a request packet with a strong signal to join the cluster. Cluster head picks those with the strongest one and, in case there are two nodes with the same signal strength, the cluster head picks one randomly. Furthermore, to limit the cluster size, every cluster head has a degree, to determine if the cluster head has reached its limit. In case the number of the cluster nodes is below the degree, then it can accept another node or, on the other hand, the node is rejected. The degree is calculated from (2):
where NN is the total number of the network nodes and is the number of the cluster heads.
By using WB-TEEN, the network lifetime is extended. However, far away nodes die too early.
In order to overcome the early death of faraway nodes, the authors in [91] also introduce Well Balanced TEEN with Multi-hop intra cluster communication (WBM-TEEN), which is WB-TEEN with multi hop routing within the clusters, overcoming path failures. Furthermore, WBM-TEEN is capable of data aggregation to further improve the performance.
In WBM-TEEN, energy consumption is reduced. Additionally, increased reliability is attained. On the other hand, single-hop routing is used in inter-cluster transmission.
Heuristic Algorithm for Clustering Hierarchy (HACH) [92] is another clustering protocol that achieves energy efficient operation by electing evenly distributed cluster heads and utilizes sleep scheduling. HACH’s operation focuses on two main ingredients: cluster head election and sleep scheduling. The SSIN (Stochastic Selection of Sleep Nodes) sleep scheduling that is used in HACH protocol deposits low energy nodes in sleep mode without affecting network’s coverage. The distance from one another is calculated in order to evaluate network coverage ability and the nodes with more residual energy are chosen as cluster heads.
In HACH protocol, the procedure of sleep scheduling prolongs network lifetime, even when different levels of heterogeneity are present. On the other hand, cluster heads may have to transmit over long distances, thus increasing their energy consumption.
Threshold Sensitive Stable Election Protocol (TSEP) [93] is a protocol that combines TEEN and SEP protocols to provide an operation with three energy leveled nodes and adjusting between energy efficiency, accuracy, and low response time. When TSEP elects a cluster head, it uses three different probabilities assigned to each energy level of the nodes. In the start of every round, the cluster head broadcasts Hard and Soft Thresholds (HT, ST), as well as Report Time (RT) and Attributes (A). RT expresses the period of time, within which reports are sent from every node while A represents the physical parameters.
TSEP protocol is suitable for applications that require continuous data transmission and provides both good energy efficiency and network stability. On the other hand, there is no awareness in the cases that thresholds are not reached.
Double-phase Cluster- head Election Scheme (DCE) [94] is a clustering protocol that implements an extra phase during the cluster head election:
- (i)
- In the first phase, a tentative cluster head is chosen randomly with the use of a probability function that considers relative initial and residual energy levels.
- (ii)
- In the new second phase, the non-elected nodes determine their minimum communication tentative cluster and compare their own remaining energy with that of the tentative cluster nodes, then the tentative cluster nodes are replaced accordingly in case the non-elected nodes have more residual energy.
This set of phases ensures a distributed energy consumption, resulting in longer stability periods than other clustering protocols. During the procedure of cluster head random election, the network is enabled instantly, without delay, resulting in a more stable network. Additionally, the network is always active, and does not waste time for cluster head election. However, in every round, DCE may change up to two times cluster head selection, thus increasing the energy consumption of the network.
Best Selection Double Cluster Head (BSDCH) [95] is a clustering protocol that divides the network field in equal regions and form chains with the nodes. Cluster heads are divided into main and secondary ones. A main cluster head sends data to the BS while a secondary cluster head receives data from the main and forwards them to the BS. BSDCH elects as cluster head the node having the minimum value of the factor F that is found by using (3):
where is the weighting coefficient of energy, is the initial energy of the node, represents the current energy of node i, denotes the distance of each node to the cluster center, and is the weighting coefficient of distance to the center, where . Similarly, the node with the most energy and the least distance to main cluster head and the best location to BS is selected as secondary cluster head. Secondary cluster head selection is based on the value of Fi factor:
where is the distance of each node to the BS, where χ is the weighting coefficient of distance to the base station where .
During initialization, the BS forms hierarchy clusters, configures the number of the levels, assigning each one with an ID, by taking into account distribution density, the BS location and number of nodes. Every node calculates its distance from the BS by the signal strength of the signal it receives from the BS. When clustering process is completed, the algorithm builds chains of nodes within each level; therefore, nodes of a chain have the same ID.
Although BSDCH is based on PEGASIS, it can send data to the BS more efficiently since it uses fewer hops. Thus, not only network lifetime is prolonged, but also high communication data rates are attained. On the other hand, extra overhead is added during cluster head election. Moreover, overlaps are observed.
Back-off based Distributed Clustering Protocol (BDCP) [96] is a clustering protocol in which every node has a back off timer and consists of cluster head election phase and cluster formation phase. During cluster head election, each node starts its timer, which considers a maximum time allocation for the election process and a ratio of its residual energy divided by its initial maximum energy. When the timer countdown finishes, node i is elected as a cluster head for the next round and broadcasts an announcement to its neighbors. Then, the nodes received the announcement switch off their timers and store the announcement with the information of the candidate cluster head. During cluster formation, a node joins a cluster according to its own distance from the cluster head and cluster head’s residual energy, in the case that it receives more than one cluster head announcement messages, it.
In BDCP protocol, energy consumption is reduced and increased throughput is achieved. On the other hand, single-hop routing restricts the network scalability. Furthermore, increased overhead is produced.
Multi hop-Back-off based Distributed Clustering Protocol (M-BDCP) [96] is a variant of BDCP protocol, which uses multi-hop routing. M-BDCP differs from the initial BDCP in the use of multi-hop routing to transmit data to the BS, the rest of the protocol operation is the same. Furthermore, in order to find the optimum path, the BS broadcasts a route discovery message to every node within the network.
In M-BDCP, multi-hop routing improves the network scalability. Moreover, both energy efficiency and throughput are high. On the other hand, overhead produced is considerably high.
Instantaneous Clustering Protocol (ICP) [97] is a parallel clustering protocol aiming to solve time and energy consumption during cluster head election. ICP forms clusters with the single-hop scheme in a parallel manner that results in reducing the duration time of clustering the whole network to a duration time of organizing one cluster. Instead of using the voting election scheme, cluster heads are determined locally with the use of a combination of a pre-assigned probability and node’s current state. For as long as the sensor nodes are connected to each other, clustering duration time and transmission load are kept to a minimum, which results in less wasted time for cluster head selection and more energy conservation of nodes.
By using ICP, energy efficiency achieved is good. In addition, both time and energy are saved during cluster head selection. However, data reliability is not taken into account.
Multi-Level Route-aware Clustering (MLRC) [98] is a routing protocol which combines a multi-criterion clustering algorithm and a route establishment algorithm. It uses this combination in order to construct an optimal routing tree to reduce packet transmission cost and the number of control packets. The clustering algorithm sets the requirements for candidate cluster heads, such as residual energy and distance from the BS, reducing energy consumption across large distances and balances energy among cluster heads. The route establishment algorithm is used to gather information and specifications of the route to construct a routing tree, with the BS being its root. During this stage, first level cluster heads, those closer to the BS, specify their next hop cluster heads in the tree and so on, with cluster nodes being the leaves of this tree. The routing tree allows nodes to receive information about optimal routes for the destination reducing communication between them. By using MLRC, network lifetime is elongated and the transmission cost between sensor nodes is minimized. However, there is lack of flexibility.
Efficient Data GathEring (EDGE) [99] is a protocol with a tree based topology rooted at the BS. To initialize the tree construction procedure, the BS sends a Child ReQuest packet (CRQ). The nodes that receive CRQ are candidates to elect as parents while the others wait for a short period of time. After that, they collect a number of candidate parent nodes and pick one based on the best defined metric. When a new node is introduced in the network, it sends a Parent ReQuest (PRQ) packet to inform its own neighbors for its existence. Data packets flow from children nodes to parent nodes and eventually to the BS.
By using EDGE protocol, energy saving is achieved, flooding is avoided, and scalability is attained. On the other hand, the traffic overhead that is produced around the BS is particularly high.
Cluster Tree Power Aware (CTPA) [100] is a routing protocol that uses a splitting algorithm during clustering setup and the minimum spanning tree comparative analysis of energy efficient routing protocols for the WSN algorithm. During the process of cluster formation, the BS divides the network in two sub-clusters and further in smaller clusters until it meets the desired number of them. In the first round, the BS elects a node as cluster head in each cluster, the one closer to the center of it, while nodes outside the cluster elect their own cluster heads taking into account the power of received broadcast messages. After the first round is over, the procedure of cluster head election is executed by the sensor nodes. Via the Minimum Spanning Tree, the BS collects data from the cluster heads, while all nodes are able to aggregate data when the packets are transmitted to the cluster heads. In addition, cluster heads use a buffering mechanism to store latest queries and results or to check if the queries exist. In the case they do not, the queries are then forwarded to the rest of the nodes.
CTPA protocol reduces energy consumption. On the other hand, the buffering mechanism used in CTPA protocol may cause overhead.
General Self Organized Tree Based (GSTEB) [101] is a protocol for periodic sensing of environment that aims to increase the network lifetime by using TDMA and Frequency Hopping Spread Spectrum (FHSS) mechanisms. In GSTEB, every node has an energy factor, for which is its residual energy is divided by an adjustable minimum energy value. After energy factor calculation, nodes transmit their factors to their neighbors via the TDMA mechanism and store these factors in a table. During every round, a root node, which is elected based on its residual energy, collects, aggregates, and transmits packets to the BS and broadcasts information, related with its energy and location, to the network. In addition, GSTEB uses a parent–children node scheme where nodes select their parent nodes, based on the energy factor and send them data packets to store them. Then, parent nodes change their roles to children nodes to send their data in the respective time slot. In the case that a node is about to die, it must broadcast a corresponding message to inform the other nodes by using TDMA scheduling. Nodes that receive the announcement update their table. Finally, GSTEB balances the energy consumption by using the self-organizing mechanism to change topology.
So, by using GSTEB, network lifetime is extended, collisions are avoided, and energy balance is attained. Yet, overhead is caused due to the large number of control packets, and scalability is limited.
Unequal Multi-hop Balanced Immune Clustering (UMBIC) [102] is a protocol that is particularly suitable for large scale monitoring. It combines the Multi-Objective Immune Algorithm (MOIA) and the Unequal Clustering Mechanism (UCM) in order to overcome the hot spot problem and improve network lifetime of WSNs with different densities. UMBIC uses an MOIA mechanism to elect cluster heads based on residual energy and build a routing tree among them to reduce the communication cost of data and control packets as well as to keep network connectivity. Moreover, the cluster head closer to the BS is elected as a Vice Cluster Head (VCH), which acts as backup in the case that another cluster head fails. Otherwise, it performs as a simple cluster node. To further reduce energy consumption, UMBIC protocol makes use of MOIA when the energy reservoirs of the cluster heads are above an energy threshold. Likewise, during the clustering process, UMBIC protocol uses the UCM to create unequal clusters depending on their distance from the BS and their residual energy in order to configure the intra-cluster and inter-cluster energy consumption. To evaluate the results of UMBIC protocol, the Balanced Extent of Energy Dissipation (BEED) metric is used. Specifically, BEED measures the ability of the protocol to balance the energy dissipation.
By using UMBIC protocol, network lifetime is prolonged. Additionally, extended stability is achieved and great scalability is accomplished. On the other hand, there is lack of fast and simple convergence.
The main features of the aforementioned hierarchy based hierarchical energy efficient routing protocols are synoptically presented in Table 7.

Table 7.
Synopsis of Hierarchical Protocols belonging to Hierarchy based subcategory.
3.2.2. Zone Based
In this subcategory, the network area is divided into zones. A zone, depending on the operation of each protocol, can operate either as a cluster with cluster head election or as a direct communication zone without cluster heads. Furthermore, each zone could be assigned a particular energy level of nodes depending of the routing algorithm or include relay nodes that transmit data from sub cluster heads to the base station. In what follows in this section, four typical examples of zone based energy efficient routing protocols are described.
Distributed Regional Energy Efficient Multi-hop-Maximum Energy (DREEM-ME) [103] is a routing protocol for homogeneous WSNs that uses a fixed number of cluster heads in each round and ensures that these cluster heads have the maximum energy. DREEM-ME separates the network into concentric circles, forming four equal sectors that divide the area in regions, excluding the first, which is in the center of the area containing the base station. Each region elects cluster heads and utilizes multi-hop communication between the other regions with the exception of region one, which uses direct communication to communicate with the base station. Furthermore, DREEM-ME reduces packet loss, during bad wireless link status, with the implementation of the Random Uniformed Distribution Model mechanism.
Thus, by using DREEM-ME, not only is energy saving achieved, but also a lower number of packets are dropped. Additionally, extended stability period is attained. On the other hand, energy depletion is not balanced. In addition, scalability is limited.
Regional Energy Efficient Cluster Heads based on Maximum Energy (REECH-ME) [104] is a clustering protocol that divides the network in nine regions with the first positioned in the center of the network, being the largest one containing the base station. The regions have a predefined number of nodes distributed randomly, while the first one has twice the number of nodes. Every region acts as a cluster including the cluster head election process, which is based on maximum residual energy. Furthermore, packets are transmitted from each region’s cluster head to the base station excluding region one, in which nodes use direct transmission to transmit their data. In order to reduce packet loss, REECH-ME utilizes the Uniform Random Distribution Model.
REECH-ME is considered to be suitable for monitoring applications. It provides improved stability period, prolonged network lifetime, and balanced energy consumption. On the other hand, its architecture is based on the use of strict settlements which limit the scalability provided.
Zone-Stable Election Protocol (Z-SEP) [105] is a clustering routing protocol for heterogeneous WSNs that combines nodes with two energy levels and a double communication scheme, as some nodes can communicate directly to the base station while others form clusters and transmit their data to the base station using the SEP algorithm.
Z-SEP divides the network into three zones:
- (i)
- Head Zone 0, which includes the base station and normal energy nodes.
- (ii)
- Head Zone 1, which includes randomly deployed advanced nodes.
- (iii)
- Head Zone 2 that includes randomly deployed advanced nodes as Head Zone 1.
During data transmission, nodes in Head zone 0 transmit packets directly to the base station while nodes in Head Zones 1 and 2, which are more dense than Head zone 0, transmit their data through an elected cluster head using an SEP algorithm.
With ZSEP, energy consumption is decreased, high throughput is achieved, and stability period is increased. Yet, the suggested network infrastructure may not be realistic. Also, overhead is added.
Zone based Stable cluster head Election Protocol -Enhanced (ZSEP-E) [106] is a clustering protocol created to face the problems of Z-SEP and SEP–E. It divides the network in three zones and utilizes three energy leveled nodes: normal, intermediate and advanced. ZSEP-E forms hierarchical clusters within the zones. Zones 1 and 3 include homogeneous advanced nodes distributed evenly, while zone 2 includes the base station, which is located in the center with the other two types of nodes normal and intermediate. During cluster head election process, in zone 2, intermediate nodes are only elected as cluster heads, while, in the other two zones, advanced nodes are elected.
ZSEP-E extends network lifetime and achieves even distribution of advanced nodes. On the other hand, non-random deployment of nodes is used and the structural considerations made may be unfeasible in real case scenarios.
A synopsis of the characteristics of the zone based subcategory hierarchical protocols is presented in Table 8.

Table 8.
Synopsis of Hierarchical Protocols belonging to the Zone based subcategory.
3.2.3. Fuzzy Logic Based
During the operation of these protocols, the core functions of the network as data routing, cluster head election, the hotspot problem or network balancing, are executed with the assistance of fuzzy logic, which enables the network to combine and evaluate diverse parameters while operating efficiently. In what follows in this section, eight typical examples of fuzzy logic based energy efficient routing protocols are described.
Fuzzy Logic-Based Energy Efficient Packet Loss Preventive Routing Protocol (FEEPRP) [107] is an energy aware packet loss preventive routing protocol, which aims to save energy and, at the same time, control congestion, avoid malicious nodes, and prevent data losses. FEEPRP uses a fuzzy control mechanism that monitors the past records of residual energy, packets dropped at each node, and hop count to decide which route to select for sending messages. Each time, a different route is selected according to the output given by the fuzzy logic mechanism. The residual energy of each route is considered as one of the inputs in the fuzzy control to assure energy conservation as well. Energy conservation is enhanced more by letting nodes sleep when idle. The throughput achieved is high. However, processing overhead is notable. In addition, mobility of nodes is not supported.
Distributed load balancing Unequal Clustering in wireless sensor networks using Fuzzy approach (DUCF) [108] is a clustering protocol, which balances the energy consumed by nodes and reduces the energy consumed by cluster heads. One common problem DUCF faces, called hotspot, is that the cluster heads closer to the base station have to send their data and relay data from distant cluster heads, due to its multi-hop routing, resulting in increased consumption. To solve this, it utilizes a fuzzy approach achieving better network balance. In addition, to achieve energy balance, more consuming cluster heads, should meet the energy requirements within an area with a low number of nodes, closer to neighbor nodes and the base station. Therefore, during cluster head election, DUCF takes into account three parameters, which namely are: (a) the residual energy, (b) node degree, and (c) distance to the base station. By using DUCF, not only is network lifetime prolonged, but also the hotspot problem is solved. However, Coverage redundancy is not supported.
Energy-Aware Unequal Clustering with Fuzzy approach (EAUCF) [109] is a clustering energy balance protocol which utilizes Fuzzy logic in order to solve the hotspot problem, a common issue of cluster heads in close proximity to the base station. Before EAUCF elects a cluster head, it considers two Fuzzy input variables and uses a “competition radius”. The first Fuzzy input is the residual energy of the candidate cluster head while the second one is the distance between cluster head and base station. Sensor nodes which have more residual energy and are closer to the base station are more probable to become the next cluster head. In EAUCF, high energy nodes are more probable to be elected as cluster heads and network lifetime is extended. On the other hand, there is a lack of parameters for selection of data packets to be broadcasted. In addition, mobility of nodes is not supported.
Energy-aware distributed dynamic Clustering Protocol in wireless sensor networks using Fuzzy logic (ECPF) [110] is a dynamic clustering protocol that utilizes fuzzy logic to divide the network in unequal clusters.
ECPF operates in rounds with each one of them consisting of two phases:
- (i)
- Setup phase, which forms network clusters and elects cluster heads and
- (ii)
- Steady State phase that uses TDMA frames, where in each frame a node sends data to its cluster head and at the end of it the cluster head aggregates data collected and sends the outcome to the base station.
In addition, cluster heads store their residual energy information in their memory at the end of every round, to reduce communication between nodes. In the case that the residual energy of a cluster head is below a threshold, this cluster head informs the base station with a small data packet in the current TDMA and the base station in its turn, informs the nodes to perform from the beginning both clustering and cluster head election. With the use of ECPF, both network lifetime is extended and scalability is attained. On the other hand, coverage preservation causes high energy consumption.
Multi-Objective Fuzzy Clustering Algorithm for wireless sensor networks (MOFKA) [111] is an energy-balancing clustering protocol that utilizes fuzzy logic to address the hotspot problem but is also an independent distribution method for the wireless sensor network.
MOFKA calculates cluster head competition radius and takes into account three parameters:
- (i)
- Distance to the base station,
- (ii)
- Node’s residual energy, and
- (iii)
- Density of the cluster.
Also, fuzzy logic is used to overcome the uncertainties that may occur during WSN operation. With the use of MOFKA, higher energy efficiency is achieved comparatively with other fuzzy logic based protocols. In addition, scalability is attained. Moreover, mobility of nodes without increasing energy consumption is supported. On the other hand, performance declines in dense networks.
SEP based on Fuzzy Logic (SEPFL) [112] protocol is an improved version of the SEP protocol, which utilizes fuzzy logic control during cluster head election. During the setup time, the base station collects information about the nodes and then utilizes fuzzy logic to further operate. It uses three fuzzy parameters, battery level, distance and density to assign a value to every node representing its probability to be elected as a cluster head. After that, the protocol calculates two threshold values, one for normal nodes and one for advanced and stores them. Then, SEPFL considers these two values for each node in order to elect cluster heads.
By using SEPFL, network lifetime is extended and great stability is attained. Nevertheless, overhead is caused due to the complexity of the algorithm.
Fuzzy Logic-TEEN (FL-TEEN) [113] is a version of TEEN that implements the fuzzy inference system during the cluster head election process. The fuzzy inference system utilizes three parameters:
- (i)
- Battery level, which is the residual energy of the nod.
- (ii)
- Factor of node density, which shows the number of neighbor nodes or in case of a cluster head it is an indirect indicator of the amount of collected data.
- (iii)
- Data frequency, which is the data satisfied by the two thresholds of the previous rounds and indicates the quantity of data collected from the corresponding area.
At the start of each round, nodes gather the values of these three parameters of themselves. Routing takes place by considering these values.
With the use of FL-TEEN, network lifetime is prolonged and, comparatively to TEEN, the election of cluster heads is more sophisticated. In addition, FL-TEEN improves network stability and uniformity of energy However, FL-TEEN needs more variables to consider in order to achieve better cluster head elections.
Hybrid Hierarchical Clustering Approach (HHCA) [114] is a protocol that utilizes a three-layer approach and the centralized Fuzzy C-Mean (FCM) approach. HHCA forms grids that include clusters and separates the network into three layers:
- (i)
- Layer three is the base station,
- (ii)
- Layer two is the Grid Heads (GH),
- (iii)
- Layer one is the cluster heads, and
- (iv)
- Layer zero is the Sensor Nodes (SNs).
Data packets are transmitted from the SNs, in layer zero, to the upper layers until they reach the base station. In order to form grids and to elect GHs, in every round, nodes send their residual energy and position information to the base station, which performs the FCM algorithm. Then, a distributed LEACH approach with energy considerations is performed to form clusters and to elect cluster heads.
With HHCA, great energy balancing improved credibility is attained. On the other hand, reliability issues take place.
A synopsis of the characteristics of the aforementioned zone based hierarchical routing protocols is presented in Table 9.

Table 9.
Synopsis of Hierarchical Protocols belonging to a Fuzzy Logic based subcategory.
4. Topology
Routing protocols of this category are classified into four subcategories depending on whether they use their location information, tree topology, mobile sinks, or mobile agents to route data. These subcategories namely are: Location based, Mobile Agent based, and Mobile Sink based.
4.1. Location Based
In most WSN protocols, location information of nodes is needed to calculate the distance between two nodes and to estimate energy consumption. Sensor networks are spatially deployed on a region and as there is no addressing scheme such as the IP addresses, location information can be utilized to route data efficiently. In protocols of Topology subcategory, nodes know their own neighbor positions as well as message sources that are assumed to be informed about the position of the destination information. In what follows in this section, seventeen typical examples of location based energy efficient routing protocols are described.
Geographic and Energy Aware Routing (GEAR) [115] uses two heuristics for packet routing, energy aware, and geographically informed neighbor selection. GEAR localizes interests of the Directed Diffusion protocol in a target region instead of sending them in the entire network. GEAR operation consists of two phases:
- (i)
- Packet forwarding towards a target region: When a node receives a packet, it forwards it to the neighbor closer to target region. In case there is no close neighbor to the target region, there is a hole in the network and sending node forwards the packet to a node with the minimum cost.
- (ii)
- Packet forwarding within target region: If the packet reaches the targeted region, it can be diffused in it with the use of either restrictive flooding or recursive geographic flooding.
GEAR both reduces and balances energy consumption. However, periodic table exchanges cause increased overhead.
Graph EMbedding for routing (GEM) [116] protocol uses virtual coordinates and two processes, Virtual Polar Coordinate Space (VPCS) and Virtual Polar Coordinate Routing (VPCR) to route data. VPCS process creates a spanning tree, which has a root node and an assigned angle range to every node. Parent nodes split this angle range to children nodes in their sub-trees. The parent nodes of a sub-tree are aware of the center of mass and average position of all nodes within their sub-tree. In the VPCR process, GEM defines points out of a node’s level and angle and routes data from any node to any point within VPCS. With the use of GEM, messages are efficiently routed. In addition, void and obstacle tolerance are attained. Another advantage of GEM is that it scales greatly with size and density. On the other hand, low level nodes are overloaded.
Implicit Geographic Forwarding (IGF) [117] is a state free protocol, without state tables of nearby nodes. Instead, it utilizes lazy binding and location address semantics. With the use of two metrics, Increased Distance Towards Destination (IDTD) and Energy Remaining (ER), a node can choose next hop of a packet in real time. A property useful for networks with migrating nodes or real-time shifts in topology. By using IGF, state information cost is eliminated and fault tolerance is attained. In addition, end to end latency is reduced. On the other hand, IGF depends on the up to date local neighbor tables.
Scalable Energy–efficient Location Aided Routing (SELAR) [118] protocol applies to static networks and considers two parameters, location, and energy consumption. At first, the base station floods its location to neighbor nodes and then those nodes flood their location to their neighbors with a reference to the base station included. Then, only energy information needs to be exchanged. To ensure energy savings, control packets travel one hop and data packets travel from within a zone to the base station. This zone is defined by the area of source node’s range and an angle a in the direction of the base station. Source node defines a min and a max value for angle a, starting from min and progresses to max with steps. If there is no neighboring node in the zone, it uses gossiping to forward the message. The advantage of SELAR is that energy dissipation not only is deceased, but also it takes place in a uniform way. The disadvantage of SELAR is that it does not work well with mobile nodes.
Greedy Distributed Spanning Tree Routing (GDSTR) [119] algorithm uses hull trees, which is a different kind of spanning tree, where every node stores all the locations of its descendant nodes in the tree, in a convex hull. The hull trees are constructed from aggregating convex hull information, which is used to avoid non-productive paths. In addition, they are able to traverse a significantly reduced sub-tree, which consists of nodes with convex hulls containing the destination point. GDSTR handles local dead ends differently than other geographic routing algorithms by switching to routing on a spanning tree until greedy forwarding can make progress again. Each node maintains a summary of the area covered by the sub-tree below each of its tree neighbors, to choose a direction on the tree that will probably make progress towards the destination. GDSTR is simple and easy to implement and understand. In addition, compared to other geographic face routing protocols, it has lower path and hop stretch. However, in GDSTR, a local dead end problem occurs.
Minimum Energy Relay Routing (MERR) [120] is a protocol based on the concept that the energy consumption of a path from the source to the base station depends on the distance between the pairs of the nodes in this particular path. In MERR, a characteristic distance is defined. A node searches its descendant nodes within its maximum range and picks the node closer to the characteristic distance or, in case every descending node’s distance is greater than the characteristic, it picks its direct descending node. When the selection has been done, the sending node reduces antenna’s power level to the minimum required to reach only the selected node.
MERR achieves both reduction and uniformity of energy consumption. Its disadvantage is that energy is wasted when nodes are close.
In On-demand Geographic Forwarding (OGF) [121], when a node needs to send a packet, it searches its forwarding table. Depending on the search results, the following cases can be the outcome of this search:
- (i)
- Case one: it finds the desired information and sends the packet.
- (ii)
- Case two: receiving node has a special code in its entry, called passive, which allows the sender node to transmit packets only to passive nodes, resulting in the sender node going directly into void handling.
- (iii)
- Case three: no receiving node entries in forwarding table with the result of sender node starting a contention to find its next hop node. If a sender cannot find a destination node, it turns into void handling mode.
After successful packet delivery, sender node updates the forwarding table, inserting an entry for the established connection. OGF accomplishes both high energy conservation and good scalability. Also, void handling is provided. Yet, it depends on the up to date local neighbor tables.
Partial-partition Avoiding Geographic Routing-Mobile (PAGER-M) [122] protocol introduces a function of cost for every node, which depends on the distance between nodes and base station. This function tries to estimate a route close to the Euclidean length of the shortest route of a node to the base station. In PAGER-M, nodes use Greedy forward to transmit packets to the base station, which may sometimes fail at a node with distant neighbors from a base station. In that case, the packet is transmitted according to the rule of High to Low cost. By using PAGER-M, energy consumption is kept low and low overhead of routing is managed. However, PAGER-M is a stateless location based routing protocol.
Hybrid Geographic Routing (HGR) [123] protocol uses a combination of direction and distance criteria for its routing needs. In HGR, every node defines a priority for its next hop Qi, which can take many forms for proper use of its distance and direction routing criteria. This priority becomes greater as the projected progress of node i gets larger and as a deviation angle between the line that connects z with i and the line that connects z with j gets smaller.
By using HGR, both notable energy savings and a high delivery ratio are achieved. Additionally, reduction of the end to end delay is possible, but not guaranteed.
Minimum Energy Communication Network (MECN) [124] sets up and maintains a minimum energy network for wireless sensor nodes using low power GPS. Although this protocol is used for mobile networks too, it is best suited to WSNs without mobility. It assumes a master site as the information the base station has in sensor networks. MECN identifies a relay region for each node consisting of sensor nodes in a surrounding area where data transmission via those is more efficient that direct communication. Furthermore, MECN manages to find a subnet with a lower number of nodes that will need less energy to transmit between two specific nodes. With this method, it finds global minimum energy paths without the need to consider all the nodes of the entire network. This is achieved with the use of a localized search for every node considering its relay region. MECN has two phases:
- (i)
- First phase: The construction of a sparse graph begins by taking positions of a two-dimensional plane, consisting of the enclosures of each transmit node in the graph. This construction process needs local computations in nodes and the graph contains globally energy efficient links.
- (ii)
- Second phase: It finds the optimal links within the enclosure graph and uses the distributed Bellman–Ford shortest path algorithm with the cost metric of power consumption. In case of mobile nodes, the position is tracked using GPS.
MECN achieves energy saving and fault tolerance. However, link maintenance consumes energy and adds overhead.
Small MECN (SMECN) [125] is an extension of MECN which considers obstacles between two nodes while the network is still assumed to be fully connected as in MECN. SMECN constructs a subnet like the one in MECN, which is smaller in terms of number of edges and uses the minimum energy property. According to this property for any pair of nodes in a graph associated with the sensor network, there is a path, named minimum energy-efficient path, that has the smallest cost regarding energy consumption over all possible paths between this pair of nodes.
SMECN saves more energy than MECN. Moreover, both link maintenance cost and number of hops are reduced. Nevertheless, additional overhead is caused.
Geographic Adaptive Fidelity (GAF) [126] is a routing protocol primarily designed for mobile Ad Hoc networks but can be applied to WSNs too. It constructs a virtual grid with points that are associated with the GPS location of nodes. Nodes that are associated with the same point have equivalent energy cost for routing packets. Using this grid, unnecessary nodes can be turned off keeping the level of routing fidelity intact and increasing the network lifetime. GAF defines the following three states:
- (i)
- Discovery state: to determine neighbor nodes in the grid.
- (ii)
- Active state: reflecting participation in routing.
- (iii)
- Sleep state: when radio circuits are turned off.
Node states and the related parameters are application dependent. GAF can handle mobility nodes with every sensor node estimating the time it leaves the grid, sending this information to its neighbors. Sleeping nodes, to keep routing fidelity, can adjust sleeping times and wake up before the leaving time of active nodes expire.
In this way, considerable energy efficiency is attained. Additionally, GAF supports both mobility and non-mobility nodes and keeps the network connected by keeping a representative node, in a region of virtual grid, active. On the other hand, nodes neither aggregate nor merge data.
Power Aware Scheduling and Clustering algorithm (PASC) [127] is a clustering protocol for homogeneous large scale WSNs with multi-hop routing that combines neighbor nodes in clusters or zones to reduce similar data sensed from neighboring regions and keeps only the cluster heads active by turning some sensor nodes off. During initialization, all nodes are homogeneous with a unique ID and Global Positioning System (GPS) location information, while the network is divided into zones. Then, during cluster head election, which is repeated in every round, nodes wait for a random time to receive messages and, in case they do not, they send a message to their neighbors requesting to be elected as cluster heads. This message contains their zone number and location information. After that, nodes that receive the request compare them with their own information and discard it, if it contains a number of a different zone or else they send a response with their residual energy. Candidate cluster heads wait for a predefined time (T) to gather all messages and are elected as cluster heads. To prevent increased energy consumption during data transmission, the multi-hop routes are optimized, while cluster heads choose the node with the highest residual energy for their next hop. In this way, reduction of energy consumption is achieved. The disadvantage of PASC is that nodes closer to the base station die earlier.
PASC-Ant Colony Optimization (PASC-ACO) [128] is an improved version of PASC protocol that forms clusters with the same mechanism as in PASC and utilizes the Ant Colony Optimization (ACO) algorithm, to route data to the base station, through the optimal path, during packet transmission.
The use of PASC-ACO prolongs network lifetime and achieves higher efficiency in dense network areas. On the other hand, the use of GPS increases energy consumption.
PASC-Adaptive Redeployment (PASC-AR) [129] is another improved version of PASC protocol, which supports the same clustering mechanism that is used in PASC combined with Adaptive Redeployment (AR). During data transmission, the redundant mobile nodes are moved via AR in a sequential pattern from dense to sparse zones, in order to prevent nodes to sense similar areas.
By using PASC-AR, network lifetime is prolonged and energy holes are covered. However, the use of mobility increases energy consumption.
Dynamic Energy Efficient Latency Improving Protocol (DEELIP) [130] is a protocol that utilizes Distance Metric (DM) to measure nodes distance and divides the network in parent-child hops in order to reduce transmission delay. DEELIP does not form conventional clusters. Instead, every node has parent and children nodes, in the next and the previous hops, respectively. During data transmission, the DM is used to measure the actual air distance for the next hop nodes instead of counting hops, while parent nodes are selected based on their least distance to the sending nodes. The base station broadcasts only once a packet containing its location information, so that receiving nodes can compare their distance from it. The use of DEELIP extends network lifetime, and achieves both low latency and improved stability. Yet, nodes are considered to be static during data gathering.
Distance Routing Effect Algorithm for Mobility (DREAM) [131] is protocol with mobile nodes that maintain a location table for every node in the network. Every node transmits its location frequently to nearby nodes and less frequently to faraway nodes in order to save resources. When a node needs to transmit a data packet to a faraway node, it first sends the packet to a nearby node which is located at the direction of destination node. Next, the receiving node forwards the message to a nearby node which is located at the direction of the destination. This procedure is repeated until destination node receives the packet.
By using DREAM, efficient transmission of data packets is achieved and the end to end delay is kept small. The disadvantage of DREAM is that there is waste of network bandwidth due to node location transmission.
A synopsis of the main characteristics of the aforementioned topology protocols belonging to the location based subcategory is presented in Table 10.

Table 10.
Synopsis of Topology Protocols belonging to Location based subcategory.
4.2. Mobile Agent Based
The main characteristic of this subcategory is the Mobile Agent, which is a program that migrates from node to node and performs tasks autonomously, based on environmental conditions. In what follows in this section, two typical examples of mobile agent based energy efficient routing protocols are described.
Multi-agent based Itinerary Planning (MIP) [132] protocol is used when a single agent based itinerary planning protocol is not sufficient as in a network of large scale. MIP defines an impact factor for every node and distributes it to every sensor node in the network. Then, the source with the greatest impact factor is selected. The main advantage of MIP is that lower energy consumption is achieved with small number of sources. Its disadvantage is that high delay is caused.
Itinerary Energy Minimum for First source selection (IEMF) [133] initially picks an arbitrary source sensor node v as a tentative S (1) leaving the rest of sources in a set V − {v}. The v is set as the starting point, while the rest of the sources in the set will have their itineraries evaluated by visiting in sequence, everyone in the set, until all routes, starting from the base station to sources, are obtained. Finally, the route with the minimum cost of energy is selected. The Itinerary Energy Minimum Algorithm or IEMA adds a route optimization apart from S (1) selection. IEMF achieves not only great energy efficiency, but also high delivery ratio. However, the scalability of IEMF is limited.
A synopsis of the characteristics of the aforementioned topology routing protocols belonging to mobile agent subcategory is presented in Table 11.

Table 11.
Synopsis of Topology Protocols belonging to Mobile Agent subcategory.
4.3. Mobile Sink Based
In this subcategory, the sink or the base station can move with the assistance of a robotic platform within the network, through the deployed nodes, in specific paths or patterns to collect data from them. In what follows in this section, two typical examples of this kind of protocols are described.
Mobile Sink based adaptive Immune Energy-Efficient clustering Protocol (MSIEEP) [134] utilizes a mobile the base station to solve the energy hole problem, to improve security, and to reduce the packet drop rate. MSIEEP uses the Adaptive Immune Algorithm (AIA) to determine the position of the mobile the base station based on three predefined paths and to calculate the optimal number of cluster heads. The first moving pattern is a rectangular amid four regions, while the second is a rectangular among eight regions and the third pattern is a straight line crossing four regions. In addition, MSIEEP allocates uniformly the cluster heads in the network and each one informs its cluster nodes of their TDMA schedule for intra-cluster communications. During inter-cluster communication, they use a unique CDMA schedule to avoid neighbor cluster interference. MSIEEP not only extends network lifetime, but also achieves low drop packet ratio and increased stability period. However, predefined routing paths limit its applications.
Multi-hop HEER-Sink Mobility (MHEER-SM) [135] is an upgraded version of HEER algorithm, which combines three operations, a fixed number of clusters, multi-hop routing for distant cluster heads, and a mechanically driven sink. MHEER-SM separates the network area in sub-areas with equal numbers of nodes that operate as clusters, performs the HEER’s cluster head election process, and efficiently monitors all the areas. Furthermore, to reduce energy consumption of the distant cluster heads, MHEER-SM utilizes multi-hop routing, by forwarding data packets to nearby cluster heads until the base station gets the data. Although packets may get lost, MHEER-SM uses a Uniform Random Distribution Model to calculate dropped packets. Finally, the base station can move in a fixed start-stop pattern to collect data from static nodes directly. MHEER-SM reduces communication cost and extends network lifetime. On the other hand, nodes are deployed in a fixed way.
A synopsis of the characteristics of the aforementioned topology routing protocols belonging to mobile sink subcategory is presented in Table 12.

Table 12.
Synopsis of Topology Protocols belonging to Mobile Sink subcategory.
5. Reliable Routing
According to the Reliable Routing scheme, protocols are classified in two subcategories, depending on whether they support QoS or whether they avoid redundant data and tolerate path failures with the use of multiple paths. These subcategories are QoS based and Multipath based.
5.1. QoS Based
In most WSN protocols, location information of nodes is needed to calculate the distance between two nodes and to estimate energy consumption. Sensor networks are spatially deployed on a region and, as there is no addressing scheme such as the IP addresses, location information can be utilized to route data efficiently. In protocols of Topology subcategory, nodes that know their own neighbor positions as well as message sources are assumed to be informed about the position of the destination information. In what follows in this section, seventeen typical examples of location based energy efficient routing protocols are described. In the QoS based subcategory, protocols try to balance network’s energy consumption, data quality, and end to end delay using certain QoS metrics as delay, energy, response time, etc. In what follows in this section, eighteen typical examples of QoS based energy efficient routing protocols are described.
Stateless Protocol for rEal-timE communication (SPEED) [136] is a QoS routing protocol for WSNs that provide low end to end delays, demands from every node to maintain neighbor node information, and using a geographic forwarding to find paths. It achieves a certain speed for every packet in the network so each application is able to estimate a packet’s end to end delay by dividing the distance to the base station to the speed of the packet and provides congestion avoidance for congested networks. The routing module of SPEED is called Stateless Geographic Non deterministic Forwarding (SNFG) and works along with another four modules in the network layer. In addition, it maintains a desired delivery speed across the network while it includes a two-tier adaption for diverting traffic at network layer and locally regulating packets sent to the MAC layer. SPEED uses the following components:
- (i)
- An Applications Programming Interface (API)
- (ii)
- A delay estimation scheme
- (iii)
- A scheme for neighbor beacon exchange
- (iv)
- A Nondeterministic Geographic Forwarding (NGF) algorithm
- (v)
- Last mile processing
- (vi)
- Backpressure Rerouting
- (vii)
- A Neighborhood Feedback Loop (NFL)
- (viii)
- Load balancing is achieved with the SNGF mechanism scattering the packets in a large transmission region
In SPEED, total transmission power is less due to the simplicity of routing and the uniformity of traffic distribution. In addition, SPEED performs better in terms of end to end delay and miss ratio. Its weakness is that there is no energy consumption metric.
Multi path and Multi SPEED (MMSPEED) [137] can achieve high QoS in both Timeliness and Reliability domains. In the timeliness domain it guarantees multiple speed options for packet delivery while, in the reliability domain, it performs probabilistic multipath forwarding for various requirements. MMSPEED does not need to be aware of network geographic information, but, with the use of localized geographic packet forwarding and dynamic compensation, it can counterbalance any local decision inaccuracies in the routing path. MMSPEED offers both energy efficiency and scalability. However, when the load is high, MMSPEDD is unable to meet end to end delay requirements.
Multimedia Geographic Routing (MGR) [138] is a protocol for multimedia applications introduced to exploit Mobile Multimedia Nodes (MMN) in an architecture called Mobile Multimedia Sensor Network (MMSN). MGR tries to guarantee the delay with high priority and, after that, it continuously minimizes energy consumption to magnify network lifetime. In order to select the best next hop location of a selected node, it divides the distance of the selected node to the base station, with ideal hop counts from selected node to the base station and calculates the desired hop distance to pick the next hop. MGR saves up to 30% more energy compared to classical geographic routing. In addition, in most cases, there is guaranteed small delay. However, the delay guaranteeing is the top priority goal.
Energy Aware QoS routing [139] is a protocol where real-time traffic is generated from imaging nodes. A minimum cost energy efficient path meeting a certain end to end delay during the connection is found. The function of link cost captures various communication parameters as energy reservoir, transmission energy, and error rate. To support simultaneously best effort and real-time traffic, the protocol employs a class based queuing model, which allows for sharing services for real-time and non-real-time traffic. Initially defined by the gateway, a starting value of bandwidth ratio r represents the limit of dedicated bandwidth to the real-time and non-real-time traffic on a specific link in case of congestion. Adjusting r value does not reduce normal data throughput. This protocol finds a list of minimum cost paths using an extended version of Dijkstra’s algorithm and picks the path from the list that meets the required end to end delay. Energy Aware QoS routing is good in terms of both QoS and energy. Its disadvantage is that r value is initially defined to be the same for all nodes, thus not providing flexibility for different links.
The Maximum lifetime energy routing [140] algorithm suggests a solution which is based on a network flow approach, which maximizes network operation time by defining the link cost as a function of remaining energy and required transmission energy of a node using that link. The routing problem of sensor networks can be also solved by calculating traffic distribution that maximizes feasible operating network time. To find the best link metric for the maximization problem, two algorithms have been proposed that are different in the definition of link cost and the nodes’ residual energy. Using the shortest path Belmann–Ford algorithm for the link costs, the minimum cost routes to the destination are found. The residual energy in a minimum cost link path is largest among all the other paths. These algorithms are compared to Minimum Transmitted Energy (MTE) algorithm, which uses for the link cost. Specifically, on average, greater operation time than in MTE is achieved. However, computational overhead is considerable.
In [141], the so-called Maximum Lifetime Data Gathering problem is studied. It is the problem of finding how to both collect the data from all of the network nodes and transmit them to the base station, in order to have the network lifetime maximized. In order to solve this problem, the authors in [141] propose the Maximum Lifetime Data Aggregation (MLDA) algorithm, which takes into account data aggregation while it sets up maximum lifetime routes. A variation of the algorithm has been proposed for the applications for which data aggregation cannot be applied as video node broadcasts. This algorithm is called Maximum Lifetime Data Routing (MLDR) and is modeled as a network flow problem that takes into account node energy constraints. Both MLDA and MLDR are compared with hierarchical-PEGASIS in terms of system operating time. They are both significantly better than Hierarchical-PEGASIS in terms of performance. In terms of network lifetime, the performance of MLDA is better than that of other protocols. On the other hand, delay of data packet transmission is significantly greater in MLDA than in Hierarchical-PEGASIS. In addition, MLDA requires more computational power for large sensor networks.
Minimum Cost Bandwidth-Constrained Routing (MCBCR) [142] protocol, which is a simple, scalable, and efficient protocol, solves the minimum cost routing problem of WSNs. The most proper paths for routing data from nodes to the base station are found. In addition, the routing cost is minimized, without the load on each wireless link, exceeding its capacity. The polynomial-time minimum cost flow algorithm achieves high scalability. By using MCBCR, both long network lifetime and high scalability are achieved. However, high computational overhead is produced.
Energy Efficient Structure-free Data Aggregation and Delivery (ESDAD) [143] is an energy efficient and structure free protocol that aggregates redundant data. ESDAD divides the network area into several sub-regions each with a unique reliability requirement. In every sub-region, there is one or more sender nodes, depending on the sub-region data traffic that collects and sends data to the other sender nodes. Applying the reliability requirement scheme, ESDAD, can choose the number of sender nodes per sub-region, achieving energy saving and decreasing message delays. ESDAD performs better than the traditional structure-free protocols regarding energy efficiency and reliability. Additionally, the miss ratio is minimized. However, mobility is not considered.
Voronoi Neighbor Based Energy Efficient Event Detection (VNBEEED) [144] proposes an interpolation method to minimize in-network traffic which is particularly high in dense networks due to redundant sensed data of neighboring nodes. VNBEEED models a WSN as a Markov Random Field (MRF) and applies local inference at every intermediate node to identify the shortest path with minimum energy consumption. In order to do so, VNBEEED uses messages of two types, i.e., data messages and sleep messages. In addition, it induces random delays into nodes of the same level that sensed an event, so only a subset of them will transmit the data message to the base station via the shortest path and a sleep message to their neighbors that sensed the data, so they will enter sleep mode. Thus, great energy saving is made. On the other hand, important messages may not reach the base station.
Efficient Dynamic Authentication and Key management (EDAK) [145] is an efficient dynamic authentication and key distribution protocol for heterogeneous WSNs, designed to safely transfer data packets between the base station and sensor nodes. EDAK combines energy efficiency and data protection and a dynamic key generator for new data. In addition, to identify the valid sensor node, it applies the authentication mechanism DMK (Dynamic Matrix Key). The use of this method results in no need for exchanging keys, which achieves energy efficient operation and faster communication, with reduced complexity and overhead. However, energy holes still exist.
The Stable and Predictive Energy-aware Coverage Scheduling (SPEC) [146] is a protocol, which utilizes a one-way scheduling strategy, a wake-up strategy and reduces unnecessary repetitive eligibility executions among the nodes. This scheduling aim to remove the risk of network isolation by allowing some sensor nodes within a cluster to be in sleep mode. According to this strategy, nodes operate in four different states:
- (i)
- Discovery, where nodes exchange messages to discover their neighbors,
- (ii)
- Active, where nodes sense the environment and communicate with their neighbors,
- (iii)
- Sleep, where they are switched off waiting to be activated, and
- (iv)
- Exhausted, where nodes have consumed their energy reservoirs.
After the discovery phase, nodes have discovered their neighborhood and SPEC knows which nodes should be switched in and out of sleep mode within the clusters. Once this is determined, clusters elect a cluster head and SPEC continues to employ it as the cluster head until it depletes its energy reserves. As soon as a cluster head is dead, another sensor node in close proximity to the exhausted one, which was previously in sleep mode, will then become the new cluster head in the next round. As long as the sensor nodes exchange data among them, no energy is wasted because of either switching between states or the process of new cluster head election. Based on its aforesaid operation, SPEC keeps energy consumption amid state changes low. In addition, it offers reduced computation energy loss. However, network is broken up when a cluster head dies.
Sleep-awake Energy Efficient Distributed (SEED) [147] is a protocol for heterogeneous networks. SEED reduces redundant data to the base station and separates the network into three energy regions, depending on their distance from the base station to distribute energy evenly. These regions are:
- (i)
- A region close to the base station with normal energy nodes,
- (ii)
- A region next to the first with advanced energy nodes,
- (iii)
- A region far away from the base station with super energy nodes.
After every region is separated, it is then divided into clusters while nodes of the same application within a cluster form a sub-cluster. SEED limits the node’s communication by enabling only one sensor node to transmit data to the base station, while the others remain in sleep mode for energy conservation. In addition, cluster heads do not send data to the cluster heads of other regions, but rather send them directly to the base station avoiding both hotspot problems and energy holes near the base station. In addition, the cluster head election’s main criterion is the remaining energy of a node. SEED attains high energy efficiency and great data redundancy. However, the nodes in sleep mode may disrupt the network. In addition, the scalability provided is not high.
Energy Efficient Routing Protocol (EERP) [148] is a protocol that combines an optimal aggregated cost function with the A* algorithm to maximize the lifetime of a WSN. In order to find the optimal path with minimum hop count, EERP takes into account the following three network attributes:
- (i)
- Node’s residual energy, in order to have a metric of WSN’s lifetime,
- (ii)
- Packet Reception Rate (PRR), which is the ratio of the base station received data packets to total sent packets,
- (iii)
- Free buffer, which helps the network calculate the traffic load nodes can handle.
These parameters are vital at the start of each round, where the base station receives and analyzes all these parameters in order to find the optimal path. When a node has new data to send, the base station chooses which sensor nodes will receive and forward the packet. EERP provides both optimal path calculation in each round and increased network lifetime. On the other hand, energy consumption when data collection rises is increased. Moreover, it has a lack of scalability.
Energy Efficient Cross-layer Protocol (EECP) [149] is a routing protocol that interacts with the Physical, MAC, and network layer. To ensure data efficient transmission, packets are routed through nodes with high energy closer to the base station, and it utilizes sleep time for energy efficient performance.
EECP saves energy by utilizing five parameters:
- (i)
- Sleep time maximization of nodes out of the routing path
- (ii)
- Tries to use different routing path each time
- (iii)
- Avoids to wake up the nodes before the time that they are needed to
- (iv)
- Reduces collisions
- (v)
- Prevents energy consumption from idle listening and overhearing
Using EECP offers reduced collisions, prolonged network life, and good load balancing. However, the nodes being in sleep mode may deteriorate the network performance. In addition, during next hop selection, EECP may pick the same node from a previous hop.
Cluster Chain Weight Metrics (CCWM) [150] is a QoS based routing protocol, which achieves energy efficiency by avoiding long distances between cluster heads and cluster nodes as well as dense areas. To elect a cluster head, CCWM takes into account parameters such as path loss factor, residual energy, and node degree. Another novelty is the cluster heads supporting only a specific number of nodes, resulting in efficient operation of MAC layer. Furthermore, the protocol tries to position the cluster head in the middle of the cluster, to avoid long distances between cluster nodes and, by utilizing a cost propagation model, it achieves a good link between cluster heads and cluster nodes that saves more energy. However, the cluster head election procedure creates overhead.
Balanced Energy Efficient Network Integrated Super Heterogeneous (BEENISH) [151] is a clustering protocol for heterogeneous WSNs that reduces energy consumption, increases stability, and prolongs network lifetime. To perform efficiently, BEENISH selects a cluster head based on residual energy by taking into account the energy reservoirs of the nodes in the network. In addition, BEENISH introduces a four-level energy scheme to classify the residual energy of nodes. These four energy levels are: normal, advance, super, and ultra-super. Nodes in the ultra-super energy level are elected as cluster heads more often than those in the super energy level. Super energy level nodes are elected as cluster head more often than advanced, etc. By employing this strategy, the network’s energy balance is achieved and energy consumption is reduced due to less communication taking place between the nodes during cluster head election. On the other hand, the distance between nodes is not considered.
Energy Consumption Rate based Stable Election Protocol (ECRSEP) [152] is another clustering protocol, which utilizes the so-called Energy Consumption Rate (ECR) for cluster head election. During every round, ECRSEP elects nodes as cluster heads in case they have low ECR. After the end of a round, in the next one, ECRSEP uses the previous ECRs to select a cluster head and elects again those with the lowest ones. Therefore, sensor nodes, which have been elected as cluster heads in the previous round, will not be chosen, due to their high ECR, compared to non-cluster head nodes. The formula for calculating ECR is:
where symbolizes the initial energy, stands for the residual energy of each node and denotes the current round. ECRSEP reduces communication energy consumption and provides energy balanced networks. However, it suffers from a problem with energy holes.
Sequential Assignment Routing (SAR) [153] uses a concept of QoS in its routing decisions for the first time in routing protocols. It decides the routing depending on three factors:
- (i)
- Energy resources
- (ii)
- QoS on each path
- (iii)
- Priority level of each packet
It is a table driven multi path-approach. With the use of trees, multiple paths from the base station to nodes are formed. These trees are rooted to single-hop neighbor nodes of the base station by considering the above three factors. Each path is selected by considering energy resources and QoS on the route. In case of failure, recovery can occur on each route, with enforced consistency of routing table between upstream and downstream nodes. Failures occurring locally trigger a procedure of path restoration.
SAR provides more energy efficiency from Minimum-Energy Metric algorithm. In addition, multiple routes from nodes to the base station are maintained and every packet’s priority is considered. However, there is a large maintenance cost of tables and states in every node when the number of nodes is large.
Reliable Routing Distributed Learning Automaton (RRDLA) [154] is a QoS routing protocol that introduces Distributed Learning Automaton (DLA) model to find the smallest number of nodes needed to preserve desired QoS requirements. RRDLA algorithm consists of four phases:
- (i)
- Initial, where the network initializes its operation and forms DLA,
- (ii)
- Learning, where a small number of nodes with high Packet Delivery Ratio (PDR) are selected,
- (iii)
- Transmitting, where the selected nodes transmit their data via the reliable links established,
- (iv)
- Retransmitting, where the undelivered data packets are sent towards the base station.
RRDLA achieves data routing via the paths that minimize the end-to-end delay and energy consumption while maximizing the PDR. However, overhead is caused.
A synopsis of the characteristics of the aforementioned QoS based energy efficient routing protocols is presented in Table 13.

Table 13.
Synopsis of Reliable Routing protocols belonging to QoS based subcategory.
5.2. Multipath Based
Multipath based protocols are able to use many different paths, being able that way to tolerate route failures, perform load balancing, and lower end-to-end delay. In what follows in this section, twelve typical examples of multipath based energy efficient routing protocols are described.
In Routing On-demand Acyclic Multipath (ROAM) [155], every router node maintains three tables: a distance table, a routing table, and a link-cost table. Distance table is a matrix that contains the distance between two neighbors at a router, routing table at a router is a column vector that contains: for every destination, the feasible distance, the distance to the destination node, the reported distance, the query origin flag, the timestamp, and the successor. The link-cost table contains the costs of the links to each known neighbor. To maintain routes and loop freedom, it uses a concept called feasible distance. In addition, it detects network partitions by requiring nodes to send update messages to neighbors whenever there is a change in distance to a certain destination. When a router needs to send a data packet to a destination with no entry in its routing table, it starts a diffused search that propagates from the source on a hop by hop basis, until it finds a router with an entry for the requested destination. Then, the router with the entry sends a reply message with the distance of the destination node. In the case that there is no route to destination all nodes in the same connected component determine that the destination is unreachable and prevent the routers from unnecessary search packets. By using ROAM, network lifetime is extended. In addition, unreachable destination informing is produced. Moreover, unnecessary packets are prevented. However, periodic updates need to be sent.
Label based Multipath Routing (LMR) [156] protocol broadcasts a control message across the entire network to find an alternative path. During this procedure, whenever a message passes through a path, the path is assigned a label with information used for segmented backup path search in case a disjoint path is not achievable. This protocol uses only localized information, with one flooding, to find disjoint paths or segments, protecting this way, the working path. When a node, reinforces one of their link to form the working path, it transmits a label message to its neighbors. Reinforcement and label messages have an integer value that is increased by 1 when a working node broadcasts a new label message. Nodes on the working path remember the value of their own labels. Label messages are forwarded to the source along all the paths from which the data messages pass through, in order to make the label messages from nodes close to the base station go as far as possible, so that the disjoint paths can be found. When they receive two or more label messages, nodes transmit the one with smaller label value or in case the values are equal, it transmits the first one recorded. In addition, the working nodes do not forward label messages from other nodes. Each node keeps track of all the labels it has seen along with the associated neighbors the labels coming from. By using LMR, energy consumption is decreased. Overhead of routing and delay to setup a backup route with label information are reduced too. However, overhead is caused due to various types of messages.
GRAdient Broadcast (GRAB) [157] protocol uses advertisement packets (ADV) that include link cost, in order to send reliable packets to the destination. ADV packets contain broadcast costs of sender node, saved in a cost field for later use. The receiving node adds a link cost between sender node and itself, to the cost in the received ADV message and compares calculated and sender costs. The receiving node’s cost will be set as the smaller of these two costs and then it will send an ADV packet containing it. In addition, a sender node can adjust data delivery’s robustness by controlling bandwidth depending of the credits contained in the data message. GRAB is both energy efficient and robust. In addition, it does not depend on individual nodes to deliver data. However, overhead due to redundant data may be caused.
Hierarchy based Multipath Routing Protocol (HMRP) [158] uses two characteristics within the operation of each node, a layer construction packet that is broadcasted initially one time and a table with Candidates Information called CIT. During packet transmission, sender nodes need to know only the parent sensor node that will receive the packet. HMRP supports mechanisms as data aggregation in every node except leaf nodes, multiple candidate paths to forward data through them and can be used with multiple base stations. By using HMRP, extension of network lifetime using data aggregation and energy balanced routing is achieved. In addition, great scalability with low overhead among nodes is attained. Moreover, simplicity is attained with a small number of operations and maintained states in every node. However, only one broadcast of the layer construction packet is used.
Cluster based Multi-Path Routing (CBMPR) [159] protocol combines cluster based and multi-path routing to route data efficiently. To reduce routing control overhead and improve network scalability, it uses a cluster network to find multiple paths that provides independent paths. CBMPR sets cluster heads and cluster nodes that send regular HELLO messages. Then, cluster nodes add their IP address while cluster heads add these IP addresses in their HELLO messages and keep track of all IP addresses of their cluster nodes and neighbor cluster heads in their routing tables. As a multipath protocol, it sets up multiple paths that can be classified as optimal path, shortest path and so on according to three parameters, i.e., hop number (h), accumulated delay (d), and bandwidth (b), which are included in the path messages received by the source. Its operation consists of the following steps:
- (i)
- At first, it calculates the path weight value based on (6):
- (ii)
- The second step is the utilization of a coding technique called M for N diversity (provided that at minimum N blocks will get to the destination it reconstructs the original X bit information packet) to solve the network’s inherent unreliability by adding extra information overhead to every packet, which is fragmented into smaller blocks.
- (iii)
- Finally, the blocks are distributed over available paths according to path’s weight value. A large path weight value means more blocks distributed via this path. To minimize packet drop rate, achieve load balancing, and improve end to end delay, the data load is sent via multiple paths.
In CBMPR, the simple cluster level hop by hop routing is used. In addition, less interference exists compared to multipath routing. Yet, errors and increased overhead in packet reassembly exist.
Directional Geographical Routing (DGR) [160] protocol offers a solution to the real-time video streaming problem in a constrained network, in terms of bandwidth and energy, with scattered Video Nodes (VN) as well as the combination of Forward Error Correction (FEC) coding. In DGR, a VN sends an aggregated packet of data and FEC packets of the video frame to direct neighbor nodes. Receiving nodes read aggregated packet’s identifiers and sequence numbers and set their payload in the aggregated packet. Finally, receiving nodes unicast the packets via relative individual routes to the base station. In DGR, low delays, extended network lifetime and high video quality are attained. However, DGR mainly focuses at video data transmission.
Directional Control Fusion (DCF) [161] is a protocol that combines load balancing and data fusion mechanisms. With the use of multipath fusion factor, DCF can compromise multipath converging and multipath expanding to meet various criteria of each application. In every round, a source is elected as a reference based on energy and distance criteria. Then, all source nodes start a timer called Reference Source Selection timer (RSS timer) and set a random value on one of the criteria. A source with a small value of RSS Timer is more eligible as the reference source of this round. After that, DCF monitors the timers and sets the next reference source the one with the first expired timer, which in turn sends an announcement message, with its location, to its neighbors. Then, receiving sources cancel their timer and the reference source constructs the reference route while the rest of the sources send the control packets. In DCF, multipath-converging and multipath-expanding trade-offs are combined. However, one source node per round is selected as the reference source.
Routing Protocol for Low power and Lossy networks (RPL) [162] is an IPv6 protocol, which contains an ingredient called Destination Oriented DAG (DODAG) that is rooted on a single root node with no outgoing edge. This DODAG formation starts at the root and spreads gradually to cover the whole network. Each router in the converged state of the wireless network has identified a set of parents, on the path towards the DODAG root node as its preferred parent. Every router emits DODAG Information Object (DIO) messages with the use of link local multicasting that indicates its respective Rank in the DODAG. After it has received a number of DIO messages, the router will calculate its rank. In case the rank is greater than the rank of its parents, it starts to emit DIO messages. The root can increase a sequence number in the DIO messages to trigger “global recalculation” of DODAG. RPL also provides an information dissemination mechanism over a dynamically formed network topology. This dissemination enables a minimal configuration in the nodes, enabling them to operate mostly autonomous. The minimum in router state requirements to run RPL is the following:
- (i)
- The DODAG root identifier
- (ii)
- The address and rank of the parents
- (iii)
- The shared DODAG root configuration parameters
- (iv)
- The maximum rank, which has been advertised by the Wireless Sensor Network router
In RPL, low energy consumption is achieved. However, only unicast traffic is supported.
Scalable Solution to Minimum Cost-Forwarding (SSMCF) [163] is a solution to the problem of delivery to the base station of minimum cost messages, from any given source, along the minimum-cost path in a simple, large, and scalable network. A cost function is used to capture delay, throughput, and energy consumption from every node to the base station. There are two phases during SSMCF:
- (i)
- First phase: Is the setup phase in which the cost value has been set for every node. The cost is diffused from the base station through the network. After that, each node sets the value cost by adding the cost from the node it received and the link cost. This cost setup is not done through the flooding mechanism, but, instead, a back-off algorithm is used to limit the number of messages exchanged. Packet forwarding has a preset delay time to allow messages with minimum cost to arrive. After that, it uses only one cost message to find the optimal cost from node to base station. The next hop states are unnecessary after the cost fields are set, ensuring scalability.
- (ii)
- During the second phase, source transmits data to its neighbor nodes. Each node in turn adds the transmission cost of them, from the base station to the cost of the packet and checks the remaining cost in it. If the remaining cost is not sufficient to send it to the base station, the packet is dropped; otherwise, it forwards the packet to its neighbors.
The design adopted has three goals:
- (i)
- Optimality: Achieve least cost forwarding
- (ii)
- Simplicity: Reduce performed operations to the minimum number and the states that participate in data forwarding.
- (iii)
- Scalability: Scale to large size network, as unconstrained scale is an inherent feature of sensor network.
In SSMCF, with the use of back-off based algorithm and proper set up back-off timer, the medium number of advertisement messages can be reduced. In addition, SSMCF scales up to large network sizes. However, it requires constant time and space complexities at each node. In addition, to achieve optimal forwarding, it needs to have the minimum number of advertisement messages.
Fast Adaptive, and Energy efficient Multi path-multi channel (FAEM) [164] utilizes the basketball NET topology that pre-assigns every node with a multi-parent-multi-child connection table along with a different receiving channel per node from their respective neighbor nodes removing transmission interference. FAEM protocol divides operational time in duty cycles with every cycle containing two phases, a scheduling and a forwarding one:
- (i)
- The first phase is called Distributed iterative scheduling phase. It schedules the three activities that a node can perform in the network, which are sleep, download to children nodes, and upload to parent nodes.
- (ii)
- The second one goes by the name of Slot based packet forwarding phase. It divides transmission time in a fixed number of frames that each contains a fixed number of slots. Every slot lasts enough for only one data packet transmission between two nodes.
In FAEM, low energy consumption is achieved with sleep mode. In addition, collision-free data transmission is attained. In addition, interference prevention is attained. However, network is unable to connect mobile parent-children nodes.
Energy Aware Routing (ERA) [165] is an improved version of the BDCP protocol that combines the clustering operation of BDCP and a multi-hop routing called Directed Virtual Backbone (DVB) to transmit data to the base station. When the protocol starts the clustering process, the base station constructs DVB and divides the cluster heads in levels, according to their distance from the base station. The base station is set in the level 0 as the parent node of level 1 cluster heads, the cluster heads of level 1 are the parent nodes of cluster heads in level 2 and so on. In addition, it is possible for a cluster head to have multiple parent nodes resulting in multiple paths to the base station. The use of ERA extends network lifetime. Yet, DVB does not provide optimum routing performance.
A synopsis of the characteristics of the aforementioned multipath based energy efficient routing protocols is presented in Table 14.

Table 14.
Synopsis of Reliable Routing protocols belonging to Multipath based subcategory.
6. Conclusions
This research work provided a survey on both classic and modern protocols, which have been proposed for the achievement of energy efficient routing in WSNs. Generally, the protocols presented were classified, according to their main structural or operational features, into four main categories which namely are: Communication Model, Network Structure, Topology, and Reliable Routing. Various representative examples of the aforementioned categories of protocols were studied and their pros and cons were highlighted. Their common characteristic is that they all pursue energy conservation by performing energy efficient routing. On the other hand, this study made evident that there are many differences in their structure and operation that were stated.
Specifically, protocols belonging to Communication Model category were further classified as Query based, Coherent or Non Coherent, and Negotiation based. Query based protocols use queries in order to enable the transmission of data from nodes that possess data to nodes that request these data. Their operation supports dynamic network topologies and multiple route replies. On the other hand, query based protocols are not appropriate for applications that require continuous data delivery such as environmental monitoring, since they route data after receiving queries and not in a constant rate. Coherent based protocols support minimum processing only of the data a node captures, while, in non-Coherent based routing protocols, nodes preprocess data they capture and send them to other nodes, called aggregators, which further process them. Coherent based protocols are not suitable for applications that require low end-to-end delay and high scalability, while non-Coherent based can be utilized for applications that require a large number of nodes. Negotiation based protocols use negotiation schemes in order to support communication among network nodes, in which data exchanged are named in order to reduce redundant information at destination nodes. In this way, both point-to-point and broadcast communication is indeed energy efficient. However, the successful delivery of data is not guaranteed. Therefore, negotiation based protocols should not be utilized for applications that require reliable data packet delivery such as intruder detection, due to the fact that some nodes might not be interested to obtain new data, thus obstructing critical information of reaching its destination.
Energy efficient routing protocols of Network Structure category were classified as either Flat or Hierarchical. Flat protocols treat all network nodes as equal entities. They perform well in networks with few sensor nodes, but they have extremely low scalability. Thus, they can be effective only in small scale applications as machine fault diagnosis. On the other hand, in Hierarchical protocols, network nodes are treated according to the place they hold within the hierarchical structure of the network. In this way, data aggregation is enabled, the communication overhead is reduced, and great scalability is achieved. Thus, hierarchical protocols are suitable for applications that require large scale WSNs with heavy load and wide coverage area.
Energy efficient routing protocols belonging to Topology category use position related information in order to route data. They were further classified into three subcategories which namely are: Location based, Mobile Sink based, and Mobile Agent based. In Location based protocols, every network node is aware of the positions of both its neighbors and the destination node during data routing. Thus, the most energy efficient routing paths are identified, and no flood is caused. They can be used in applications that utilize location information of a specific node, as a free parking space in a parking lot facility. Mobile agent based routing protocols use a mobile agent, which is a processing function that travels among the network nodes in order to collect their data. In mobile sink protocols, the data sinks or base stations themselves are able to travel within the network field, by using movable platforms, in specific paths or patterns to gather data from the nodes deployed. Military operations, such as battlefield surveillance, are typical applications where protocols of this kind are suitable to be used in.
Energy efficient routing protocols of Reliable Routing category protocols were classified into two corresponding subcategories depending on whether they pursue QoS metrics or perform routing via multiple paths. Specifically, QoS based protocols take into consideration not only the energy consumption, but also other metrics such as end to end delay and data quality. Operations which involve the transmission of multimedia data are typical examples of applications of such protocols. Multipath based protocols route data from nodes to sinks via various paths, in order to perform load balancing, overcome route failures, and decrease end-to-end delay. Their main weakness is that they involve high processing and communication overhead.
7. Open Research Issues
WSNs are considered to be among the most emerging scientific domains and have an ever growing range of applications. However, the operation of WSNs is harshly obstructed due to both the specific limitations of their sensor nodes and the inherent problems of wireless communications in overall. It is generally adopted that, among all the factors that have detrimental effect, the energy constraints of sensor nodes constitute the real Achilles’ heel of WSNs.
Given that energy depletion in sensor nodes is mainly performed during their communication, numerous research efforts focus on the attainment of energy efficiency in data routing. The comparative investigation of such works was the aim of the survey presented in this article. Of course, energy conservation in communication can be even greater by applying additional measures.
For instance, it is true that a great part of the data sensed by the sensor nodes in WSNs are redundant. Hence, passing out redundant data decreases the volume of data transmitted along with the energy expenditure and the latency associated. This is why there is need for novel data aggregation schemes [166,167,168]. Likewise, the use of compression and restoration schemes provides substantial reduction of communication load [169,170,171].
Likewise, whenever a sensor node becomes inactive, because of either the depletion of its energy residues or a malfunction, the communication cost for the remaining active nodes is increased. Thus, the preservation of network connectivity is very important for the execution of the routing process and the extension of network lifetime. This is the aim of relative protocols proposed [172,173].
At the same time, the attainment of the maximum possible coverage of the network field for a given number of sensor nodes is anticipated. For these reasons, methodologies that pursue coverage maximization in two dimensions [174,175], three dimensions [176], or in conjunction with connectivity preservation are proposed [177,178,179].
In addition, the presence of congestion not only obstructs the transmission of data, but it also causes packet losses and consequently necessitates packet retransmissions that deplete the energy reserves of sensor nodes. Congestion avoidance [180,181,182,183] and congestion control [184,185,186] methods are used to prevent the occurrence of upcoming congestion and eradicate existent congestion, respectively.
In addition, QoS provision in terms of general performance metrics such as reliable and timely delivery of data or other application specified features obliges the development of such schemes [187,188,189,190].
Moreover, wireless communications are susceptible to numerous types of potential attacks. Specifically, confidentiality, authentication, integrity, availability, and freshness are the main security considerations for WSNs. In order to cope with such issues, the development of security schemes that are specialized for WSNs is necessitated [191,192,193,194].
Of course, the achievement of energy efficiency along with other performance metrics is not an easy task because of the contradictory conditions that must be met. For this reason, multi-objective optimization algorithms have been proposed which aim to optimize the operation of WSNs by pursuing the simultaneous accomplishment of multiple criteria [195,196,197].
In addition, WSNs, by their nature, are dynamic environments in terms of both their structure and their operation. Therefore, the use of Machine Learning (ML) is an excellent alternative for the development of energy efficient routing protocols in WSNs because it provides the ability of self-learning from the experience gathered and thus self-adapt to the modifications occurring [198,199,200].
Likewise, Artificial Intelligence methods, such as Fuzzy Logic, Genetic Algorithm, Ant Colony Optimization, Particle Swarm Optimization, and Artificial Immune Algorithm are a very promising in supporting the development of energy efficient routing protocols in WSNs [201,202].
Another issue that is worth mentioning is that the vast majority of research works focuses on homogeneous WSNs, meaning that all the sensor nodes are presumed to incorporate identical operational and structural characteristics. This assumption simplifies considerably the research needed for the study of the relevant research issues, but it may lead to unrealistic results because in real-life scenarios heterogeneous WSNs are too common to ignore [27]. In order to cope with this issue, novel research works are proposed [203,204,205].
Likewise, in most of the routing protocols that are proposed for WSNs, there is lack of mobility considerations. However, mobile wireless sensor networks (MWSNs), thanks to their enhanced capabilities, outperform traditional WSNs in terms of various performance metrics and thus are involved in more and more applications. On the other hand, routing in a mobile network by default is particularly complex and thus initiates notable research issues. For these reasons, a lot of research interest in energy efficient routing is expected to be attracted by MWSNs [206,207,208].
Almost 75% of the surface of planet Earth is covered by water. This fact, by itself, is adequate to highlight the importance of Underwater Wireless Sensor Networks (UWSNs). However, conventional mediums used in terrestrial communications are not able to support underwater communications because they are associated with high attenuation, long propagation delay, and limited transmission capacity. For these reasons, novel research works are required to handle with issues of such type [209,210,211].
Last but not least, the authors of this research work believe that WSNs will keep on being in the center of scientific interest and hope that this survey will be helpful for scientists that devote their research efforts to this very challenging domain.
Author Contributions
Conceptualization, D.K. and C.N.; methodology, D.K. and C.N.; formal analysis, D.K., and C.N.; investigation, D.K., C.N., and G.V.; resources, D.K., C.N., and G.V.; writing—original draft preparation, D.K., C.N., and G.V.; writing—review and editing, D.K. and C.N.; visualization, D.K. and C.N.; supervision, D.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless Sensor Networks: A Survey. Comput. Netw. 2002, 38, 399–422. [Google Scholar] [CrossRef]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Wang, Q.; Balasingham, I. Wireless Sensor Networks-an Introduction. In Wireless Sensor Networks: Application-Centric Design; InTechOpen: London, UK, 2010; pp. 1–14. [Google Scholar]
- Fahmy, H.M. Protocol Stack of WSNs. In Wireless Sensor Networks; Springer: Singapore, 2016; pp. 55–68. [Google Scholar]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of Wireless Sensor Networks: An Up-to-Date Survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef]
- Arampatzis, T.; Lygeros, J.; Manesis, S. A Survey of Applications of Wireless Sensors and Wireless Sensor Networks. In Proceedings of the 2005 IEEE International Symposium on Mediterrean Conference on Control and Automation Intelligent Control, Limassol, Cyprus, 27–29 June 2005; Volume 200, pp. 719–724. [Google Scholar]
- Hussian, R.; Sharma, S.; Sharma, V.; Sharma, S. WSN applications: Automated intelligent traffic control system using sensors. Int. J. Soft Comput. Eng. 2013, 3, 77–81. [Google Scholar]
- Nikolidakis, S.A.; Kandris, D.; Vergados, D.D.; Douligeris, C. Energy efficient automated control of irrigation in agriculture by using wireless sensor networks. Comput. Electron. Agric. 2015, 113, 154–163. [Google Scholar] [CrossRef]
- Abreu, C.; Mendes, P. Wireless Sensor Networks for Biomedical Applications. In Proceedings of the 2013 IEEE 3rd Portuguese Meeting in Bioengineering (ENBENG), Braga, Portugal, 20–23 February 2013; pp. 1–4. [Google Scholar]
- Pantazis, N.A.; Nikolidakis, S.A.; Kandris, D.; Vergados, D.D. An Automated System for Integrated Service Management in Emergency Situations. In Proceedings of the 2011 15th Panhellenic Conference on Informatics, Kastoria, Greece, 30 September–2 October 2011; pp. 154–157. [Google Scholar]
- Đurišić, M.P.; Tafa, Z.; Dimić, G.; Milutinović, V. A Survey of Military Applications of Wireless Sensor Networks. In Proceedings of the 2012 Mediterranean Conference on Embedded Computing (MECO), Bar, Montenegro, 19–21 June 2012; pp. 196–199. [Google Scholar]
- Tripathi, A.; Gupta, H.P.; Dutta, T.; Mishra, R.; Shukla, K.K.; Jit, S. Coverage and Connectivity in WSNs: A Survey, Research Issues and Challenges. IEEE Access 2018, 6, 26971–26992. [Google Scholar] [CrossRef]
- Zhu, C.; Zheng, C.; Shu, L.; Han, G. A survey on coverage and connectivity issues in wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 619–632. [Google Scholar] [CrossRef]
- Ploumis, S.E.; Sgora, A.; Kandris, D.; Vergados, D.D. Congestion Avoidance in Wireless Sensor Networks: A Survey. In Proceedings of the 2012 IEEE Panhellenic Conference on Informatics (PCI 2012), Piraeus, Greece, 5–7 October 2012; pp. 234–239. [Google Scholar]
- Kavitha, T.; Sridharan, D. Security vulnerabilities in wireless sensor networks: A survey. J. Inf. Assur. Secur. 2010, 5, 31–44. [Google Scholar]
- Uthra, R.A.; Raja, S.V. QoS routing in wireless sensor networks—A survey. ACM Comput. Surv. 2012, 45, 9. [Google Scholar] [CrossRef]
- Kandris, D.; Tsagkaropoulos, M.; Politis, I.; Tzes, A.; Kotsopoulos, S. A Hybrid Scheme for Video Transmission over Wireless Multimedia Sensor Networks. In Proceedings of the IEEE 17th Mediterranean Conference on Control and Automation, Thessaloniki, Greece, 24–26 June 2009; pp. 964–969. [Google Scholar]
- Pantazis, N.; Kandris, D. Power Control Schemes in Wireless Sensor Networks. WSEAS Trans. Commun. 2005, 4, 1100–1107. [Google Scholar]
- Kandris, D.; Tsioumas, P.; Tzes, A.; Pantazis, N.; Vergados, D.D. Hierarchical Energy Efficient Routing in Wireless Sensor Networks. In Proceedings of the 16th IEEE Mediterranean Conference on Control and Automation (MED’08), Ajaccio, France, 25–27 June 2008; pp. 1856–1861. [Google Scholar]
- Akkaya, K.; Younis, M. A Survey on Routing Protocols for Wireless Sensor Networks. Ad Hoc Netw. 2005, 3, 325–349. [Google Scholar] [CrossRef]
- Al-Karaki, A.; Kamal, A.E. Routing Techniques in Wireless Sensor networks: A Survey. Secur. Netw. 2004, 11, 6–28. [Google Scholar]
- Pantazis, N.A.; Nikolidakis, S.A.; Vergados, D.D. Energy-Efficient Routing Protocols in Wireless Sensor Networks: A Survey. IEEE Commun. Surv. Tutor. 2013, 15, 551–591. [Google Scholar] [CrossRef]
- Warrier, M.M.; Kumar, A. Energy Efficient Routing in Wireless Sensor Networks: A Survey. In Proceedings of the 2016 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 23–25 March 2016; pp. 1987–1992. [Google Scholar]
- Cirstea, C. Energy Efficient Routing Protocols for Wireless Sensor Networks: A Survey. In Proceedings of the 2011 IEEE 17th International Symposium for Design and Technology in Electronic Packaging (SIITME), Timisoara, Romania, 20–23 October 2011; pp. 277–282. [Google Scholar]
- Mohamed, R.E.; Saleh, A.I.; Abdelrazzak, M.; Samra, A.S. Survey on wireless sensor network applications and energy efficient routing protocols. Wirel. Pers. Commun. 2018, 101, 1019–1055. [Google Scholar] [CrossRef]
- Mundada, M.R.; Kiran, S.; Khobanna, S.; Varsha, R.N.; George, S.A. A study on energy efficient routing protocols in wireless sensor networks. Int. J. Distrib. Parallel Syst. 2012, 3, 311–330. [Google Scholar] [CrossRef]
- Jingjing, Y.; Mengchu, Z.; Zhijun, D. Recent advances in energy-efficient routing protocols for wireless sensor networks: A review. IEEE Access 2016, 4, 5673–5686. [Google Scholar]
- Intanagonwiwat, C.; Govindan, R.; Estrin, D. Directed Diffusion: A Scalable and Robust Communication Paradigm for Sensor Networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 56–67. [Google Scholar]
- Yao, Y.; Gehrke, J. The cougar approach to In-network query processing in sensor networks. ACM Sigmod Record 2002, 31, 9–18. [Google Scholar] [CrossRef]
- Sadagopan, N.; Krishnamachari, B.; Helmy, A. Active Query Forwarding in Sensor Networks (ACQUIRE). Ad Hoc Netw. 2005, 3, 91–113. [Google Scholar] [CrossRef]
- Shah, R.C.; Rabaey, J.M. Energy aware routing for low energy ad hoc sensor networks. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Orlando, FL, USA, 17–21 March 2002. [Google Scholar]
- Schurgers, C.; Srivastava, M.B. Energy Efficient Routing in Wireless Sensor Networks. In Proceedings of the MILCOM Proceedings on Communications for Network-Centric Operations: Creating the Information Force, McLean, VA, USA, 28–31 October 2001. [Google Scholar]
- Chu, M.; Haussecker, H.; Zhao, F. Scalable information driven sensor querying and routing for ad hoc heterogeneous sensor networks. Int. J. High Perform. Comput. Appl. 2002, 16, 293–313. [Google Scholar] [CrossRef]
- Gao, J.L. Energy Efficient Routing for Wireless Sensor Networks. Ph.D. Thesis, University of California, Los Angeles, CA, USA, 2000. [Google Scholar]
- Heinzelman, W.R.; Kulik, J.; Balakrishnan, H. Adaptive protocols for Information Dissemination in Wireless Sensor Networks. In Proceedings of the 5th Annual ACM/IEEE International Conference on Mobile Computing and Networking (MobiCom99), Seattle, WA, USA, 15–20 August 1999. [Google Scholar]
- De Morais Cordeiro, C.; Agrawal, D.P. Ad Hoc and Sensor Networks: Theory and Applications; World Scientific: Singapore, 2006. [Google Scholar]
- Murthy, S.; Garcia-Luna-Aceves, J.J. An Efficient Routing Protocol for Wireless Networks. Mob. Netw. Appl. 1996, 1, 183–197. [Google Scholar] [CrossRef]
- Ogier, R.; Templin, F.; Lewis, M. Topology Dissemination Based on Reverse-Path Forwarding (TBRPF); RFC 3684; ISOC: Reston, USA, 2004. [Google Scholar]
- Park, V.D.; Corson, M.S. A Highly Adaptive Distributed Routing Algorithm for Mobile Wireless Networks. In Proceedings of the INFOCOM’97, Kobe, Japan, 7–12 April 1997; pp. 1405–1413. [Google Scholar]
- Lim, H.; Kim, C. Flooding in Wireless Ad Hoc Networks. Comput. Commun. 2001, 24, 353–363. [Google Scholar] [CrossRef]
- Hedetniemi, S.M.; Hedetniemi, S.T.; Liestman, A.L. A Survey of Gossiping and Broadcasting in Communication Networks. Networks 1998, 18, 319–349. [Google Scholar] [CrossRef]
- Braginsky, D.; Estrin, D. Rumor Routing Algorithm for Sensor Networks. In Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications, Atlanta, GA, USA, 28 September 2002; p. 2231. [Google Scholar]
- Yu, F.; Li, Y.; Fang, F.; Chen, Q. A New TORA Based Energy Aware Routing Protocol in Mobile Ad Hoc Networks. In Proceedings of the 2007 3rd IEEE/IFIP international conference in central Asia on Internet, Tashkent, Uzbekistan, 26–28 September 2007; pp. 1–4. [Google Scholar]
- Haas, Z.J. A New Routing Protocol for the Reconfigurable Wireless Networks. In Proceedings of the ICUPC 97—6th International Conference on Universal Personal Communications, San Diego, CA, USA, 12–16 October 1997; Volume 2, pp. 562–566. [Google Scholar]
- Singh, R.; Verma, A.K. Energy efficient cross layer based adaptive threshold routing protocol for WSN. AEU Int. J. Electron. Commun. 2017, 72, 166–173. [Google Scholar] [CrossRef]
- Handy, M.J.; Haase, M.; Timmermann, D. Low Energy Adaptive Clustering Hierarchy with Deterministic Cluster-Head Selection. In Proceedings of the 4th International Workshop on Mobile and Wireless Communications Network 2002, Stockholm, Sweden, 9–11 September 2002; Volume 1, pp. 368–372. [Google Scholar]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An Application-Specific Protocol Architecture for Wireless Microsensor Networks. IEEE Trans. Wirel. Commun. 2002, 1, 60–70. [Google Scholar] [CrossRef]
- Manzoor, B.; Javaid, N.; Rehman, O.; Akbar, M.; Nadeem, Q.; Iqbal, A.; Ishfaq, M. Q-LEACH: A New Routing Protocol for WSNs. Procedia Comput. Sci. 2013, 19, 926–931. [Google Scholar] [CrossRef]
- Kumar, N.; Bhutani, P.; Mishra, P. U-LEACH: A Novel Routing Protocol for Heterogeneous Wireless Sensor Networks. In Proceedings of the 2012 International Conference on Communication, Information & Computing Technology (ICCICT), Mumbai, India, 19–20 October 2012. [Google Scholar]
- Razaque, A.; Mudigulam, S.; Gavini, K.; Amsaad, F.; Abdulgader, M.; Krishna, G.S. H-LEACH: Hybrid-Low Energy Adaptive Clustering Hierarchy for Wireless Sensor Networks. In Proceedings of the 2016 IEEE Long Island Systems, Applications and Technology Conference (LISAT), Farmingdale, NY, USA, 29 April 2016. [Google Scholar]
- Zhixiang, D.; Bensheng, Q. Three-Layered Routing Protocol for WSN Based on LEACH Algorithm. In Proceedings of the IET Conference Wireless, Mobile & Sensor Networks, Shanghai, China, 12–14 December 2007; pp. 72–75. [Google Scholar]
- Tyagi, S.; Gupta, S.K.; Tanwar, S.; Kumar, N. EHE-LEACH: Enhanced Heterogeneous LEACH Protocol for Lifetime Enhancement of Wireless SNs. In Proceedings of the 2013 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Mysore, India, 22–25 August 2013. [Google Scholar]
- Beiranvand, Z.; Patooghy, A.; Fazeli, M. I-LEACH: An Efficient Routing Algorithm to Improve Performance & to Reduce Energy Consumption in Wireless Sensor Networks. In Proceedings of the 5th Conference on Information and Knowledge Technology, Shiraz, Iran, 28–30 May 2013. [Google Scholar]
- Lee, J.S.; Cheng, W.L. Fuzzy-Logic based Clustering Approach for Wireless Sensor Networks Using Energy Predication. IEEE Sens. J. 2012, 12, 2891–2897. [Google Scholar] [CrossRef]
- Taneja, H.; Bhalla, P. An Improved Version of LEACH: Three Levels Hierarchical Clustering LEACH Protocol (TLHCLP) for Homogeneous WSN. Int. J. Adv. Res. Comput. Commun. Eng. 2013, 2, 3610–3615. [Google Scholar]
- Ghosh, S.; Mondal, S.; Biswas, U. A Dominating Set Based Modified LEACH Using Ant Colony Optimization for Data Gathering in WSN 2016. In Proceedings of the 2016 2nd International Conference on Advances in Electrical, Electronics, Information, Communication and Bio-Informatics (AEEICB), Chennai, India, 27–28 February 2016. [Google Scholar]
- Lindsey, S.; Raghavendra, C.S. PEGASIS: Power Efficient Gathering in Sensor Information Systems. In Proceedings of the IEEE Aerospace Conference, Big Sky, MT, USA, 9–16 March 2002. [Google Scholar]
- Lindsay, S.; Raghavendra, C.S.; Sivalingam, K.M. Data Gathering in Sensor Networks Using the Energy* Delay Metric. In Proceedings of the IPDPS Workshop on Issues in Wireless Networks and Mobile Computing, San Francisco, CA, USA, 23–27 April 2001. [Google Scholar]
- Aliouat, Z.; Aliouat, M. Efficient Management of Energy Budget for PEGASIS Routing Protocol. In Proceedings of the 2012 6th International Conference on Sciences of Electronics, Technologies of Information and Telecommunications (SETIT), Sousse, Tunisia, 21–24 March 2012. [Google Scholar]
- Jung, S.M.; Han, Y.J.; Chung, T.M. The Concentric Clustering Scheme for Efficient Energy Consumption in the PEGASIS. In Proceedings of the 9th International Conference on Advanced Communication Technology, Kobe, Japan, 12–14 February 2007. [Google Scholar]
- Manjeshwar, A.; Agrawal, D.P. Teen: A Routing Protocol for Enhanced Efficiency in Wireless Sensor Networks. In Proceedings of the 15th International Parallel and Distributed Processing Symposium (IPDPS’01) Workshops, San Francisco, CA, USA, 23–27 April 2001. [Google Scholar]
- Manjeshwar, A.; Agrawal, D.P. APTEEN: A Hybrid Protocol for Efficient Routing and Comprehensive Information Retrieval in Wireless Sensor Networks. In Proceedings of the International Parallel and Distributed Processing Symposium, Auderdale, FL, USA, 15–19 April 2002; pp. 195–202. [Google Scholar]
- Al-Karaki, J.N.; Ul-Mustafa, R.; Kamal, A.E. Data Aggregation in Wireless Sensor Networks Exact and Approximate Algorithms. In Proceedings of the IEEE Workshop High Performance Switching and Routing 2004, Phoenix, AZ, USA, 19–21 April 2004; pp. 241–245. [Google Scholar]
- Luo, H.; Ye, F.; Cheng, J.; Lu, S.; Zhang, L. TTDD: Two-Tier Data Dissemination in Large-Scale Wireless Sensor Networks. Wirel. Netw. 2005, 11, 161–175. [Google Scholar] [CrossRef]
- Muruganathan, S.D.; Ma, D.C.; Bhasin, R.I.; Fapojuwo, A.O. A Centralized Energy-Efficient Routing Protocol for Wireless Sensor Networks. IEEE Commun. Mag. 2005, 43, 8–13. [Google Scholar] [CrossRef]
- Nikolidakis, S.A.; Kandris, D.; Vergados, D.D.; Douligeris, C. Energy Efficient Routing in Wireless Sensor Networks Through Balanced Clustering. Algorithms 2013, 6, 29–42. [Google Scholar] [CrossRef]
- Yuan, Y.; He, Z.; Chen, M. Virtual MIMO based Cross-layer Design for Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2006, 55, 856–864. [Google Scholar] [CrossRef]
- Li, Q.; Aslam, J.; Rus, D. Hierarchical Power-aware Routing in Sensor Networks. In Proceedings of the DIMACS Workshop on Pervasive Networking, Piscataway, NJ, USA, 21 May 2001; pp. 25–27. [Google Scholar]
- Wu, Y.; Fahmy, S.; Shroff, N.B. Energy Efficient Sleep/Wake Scheduling for Multi-Hop Sensor Networks: Non-Convexity and Approximation Algorithm. In Proceedings of the 26th Annual IEEE Conference on Computer Communications (INFOCOM 2007), Anchorage, AK, USA, 6–12 May 2007; pp. 1568–1576. [Google Scholar]
- Sharma, T.P.; Joshi, R.C.; Misra, M. GBDD: Grid Based Data Dissemination in Wireless Sensor Networks. In Proceedings of the 16th International Conference on Advanced Computing and Communications (ADCOM 2008), Chennai, India, 14–17 December 2008; pp. 234–240. [Google Scholar]
- Lotf, J.J.; Bonab, M.N.; Khorsandi, S. A Novel Cluster based Routing Protocol with Extending Lifetime for Wireless Sensor Networks. In Proceedings of the 2008 5th IFIP International Conference on Wireless and Optical Communications Networks (WOCN’08), Surabaya, Indonesia, 5–7 May 2008; pp. 1–5. [Google Scholar]
- Cheng, H.B.; Geng, Y.; Hu, S.J. NHRPA: A Novel Hierarchical Routing Protocol Algorithm for Wireless Sensor Networks. J. China Univ. Posts Telecommun. 2008, 15, 75–81. [Google Scholar] [CrossRef]
- Kandris, D.; Tsioumas, P.; Tzes, A.; Nikolakopoulos, G.; Vergados, D.D. Power Conservation Through Energy Efficient Routing in Wireless Sensor Networks. Sensors 2009, 9, 7320–7342. [Google Scholar] [CrossRef] [PubMed]
- Kandris, D.; Tsagkaropoulos, M.; Politis, I.; Tzes, A.; Kotsopoulos, S. Energy efficient and perceived QoS aware video routing over Wireless Multimedia Sensor Networks. Ad Hoc Netw. 2011, 9, 591–607. [Google Scholar] [CrossRef]
- Ke, W.; Yangrui, O.; Hong, J.; Heli, Z.; Xi, L. Energy aware hierarchical cluster based routing protocol for WSNs. J. China Univ. Posts Telecommun. 2016, 23, 46–52. [Google Scholar] [CrossRef]
- Gherbi, C.; Aliouat, Z.; Benmohammed, M. An adaptive clustering approach to dynamic load balancing and energy efficiency in wireless sensor networks. Energy 2016, 114, 647–662. [Google Scholar] [CrossRef]
- Du, T.; Qu, S.; Liu, F.; Wang, Q. An energy efficiency semi-static routing algorithm for WSNs based on HAC clustering method. Inf. Fusion 2015, 21, 18–29. [Google Scholar] [CrossRef]
- Qing, L.; Zhu, Q.; Wang, M. Design of a distributed energy-efficient clustering algorithm for heterogeneous wireless sensor networks. Comput. Commun. 2006, 29, 2230–2237. [Google Scholar] [CrossRef]
- Yi, D.; Yang, H. HEER-A delay-aware and energy-efficient routing protocol for wireless sensor networks. Comput. Netw. 2016, 104, 155–173. [Google Scholar] [CrossRef]
- Sharma, S.; Rani, M. Improved Inter-Cluster Data Aggregation HEER protocol. Int. J. Comput. Sci. Mob. Comput. 2014, 3, 1111–1118. [Google Scholar]
- Mohanty, P.; Kabat, M.R. A Hierarchical Energy Efficient Reliable Transport Protocol for Wireless Sensor Networks. Ain Shams Eng. J. 2014, 5, 1141–1155. [Google Scholar] [CrossRef]
- Younis, M.; Youssef, M.; Arisha, K. Energy-Aware Routing in Cluster Based Sensor Networks. In Proceedings of the 10th IEEE/ACM International Symposium on Modeling, Analysis and Simulation of Computer and Telecommunication Systems (MASCOTS2002), Fort Worth, TX, USA, 11–16 October 2002. [Google Scholar]
- Subramanian, L.; Katz, R.H. An architecture for building self-configurable systems. In Proceedings of the IEEE/ACM Workshop on Mobile Ad Hoc Networking and Computing, Boston, MA, USA, 11 August 2000. [Google Scholar]
- Lung, C.H.; Zhou, C. Using Hierarchical Agglomerative Clustering in Wireless Sensor Networks: An Energy-efficient and Flexible Approach. Ad Hoc Netw. 2010, 8, 328–344. [Google Scholar] [CrossRef]
- Younis, O.; Fahmy, S. HEED: A Hybrid, Energy-Efficient, Distributed Clustering Approach for Ad hoc Sensor Networks. IEEE Trans. Mob. Comput. 2004, 3, 366–379. [Google Scholar] [CrossRef]
- Smaragdakis, G.; Matta, I.; Bestavros, A. SEP: A Stable Election Protocol for Clustered Heterogeneous Wireless Sensor Networks. In Proceedings of the 2nd IEEE International Workshop on Sensor and Actor Network Protocols and Applications, Boston, MA, USA, 22 August 2004; pp. 1–11. [Google Scholar]
- Aderohunmu, F.A.; Deng, J.D. An Enhanced Stabel Election Protocol (SEP) for Clustered Heterogeneous WSN; Discussion Paper Series, No. 2009/07; Department of Information Science, University of Ontago: Dunedin, New Zealand, 2010; ISSN 1177-455X. [Google Scholar]
- Yu, J.; Qi, Y.; Wang, G.; Gu, X. A cluster based routing protocol for wireless sensor networks with non-uniform node distribution. AEU Int. J. Electron. Commun. 2012, 66, 54–61. [Google Scholar] [CrossRef]
- Gupta, V.; Pandey, R. An Improved Energy Aware Distributed Clustering Protocol for Wireless Sensor Networks. Int. J. Comput. Netw. Inf. Secur. 2016, 8, 29. [Google Scholar] [CrossRef]
- Rani, S.; Malhotra, J.; Talwar, R. Energy efficient chain based cooperative routing protocol for WSN. Appl. Soft Comput. 2014, 35, 386–397. [Google Scholar] [CrossRef]
- Aliouat, Z.; Harous, S. An Efficient Clustering Protocol Increasing Wireless Sensor Networks Life Time. In Proceedings of the 2012 International Conference on Innovations in Information Technology (IIT), Al-Ain, UAE, 18–20 March 2012. [Google Scholar]
- Oladimeji, M.O.; Turkey, M.; Dudley, S. HACH: Heuristic Algorithm for Clustering Hierarchy protocol in wireless sensor networks. Appl. Soft Comput. 2017, 55, 452–461. [Google Scholar] [CrossRef]
- Kashaf, A.; Javaid, N.; Khan, Z.A.; Khan, I.A. TSEP: Threshold-sensitive Stable Election Protocol for WSNs. In Proceedings of the 2012 10th International Conference on Frontiers of Information Technology, Islamabad, Pakistan, 17–19 December 2012. [Google Scholar]
- Han, R.; Yang, W.; Wang, Y.; You, K. DCE: A Distributed Energy-Efficient Clustering Protocol for Wireless Sensor Network Based on Double-Phase Cluster-Head Election. Sensors 2017, 17, 998. [Google Scholar] [CrossRef]
- Noori, M.; Khoshtarash, A. BSDCH: New Chain Routing Protocol with Best Selection Double Cluster Head. Wirel. Sen. Netw. 2012, 5, 27987. [Google Scholar]
- Amgoth, T.; Jana, P.K. BDCP: A Back off Based Distributed Clustering Protocol for Wireless Sensor Networks. In Proceedings of the 2013 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Mysore, India, 22–25 August 2013. [Google Scholar]
- Kong, L.; Xiang, Q.; Liu, X.; Liu, X.Y.; Gao, X.; Chen, G.; Wu, M.Y. ICP: Instantaneous clustering protocol for wireless sensor networks. Comput. Netw. 2016, 101, 144–157. [Google Scholar] [CrossRef]
- Sabet, M.; Naji, H. An energy efficient multi-level route-aware clustering algorithm for wireless sensor networks: A self-organized approach. Comput. Electr. Eng. 2016, 56, 399–417. [Google Scholar] [CrossRef]
- Thepvilojanapong, N.; Tobe, Y.; Sezaki, K. On the Construction of Efficient Data Gathering Tree in Wireless Sensor Networks. In Proceedings of the 2005 IEEE International Symposium on Circuits and Systems, Kobe, Japan, 23–26 May 2005. [Google Scholar]
- Mishra, S.; Sahoo, S.; Thakkar, H.; Chakrabarty, A. Cluster Tree Power Aware Routing Protocol for WSN (CTPA). IJTEL 2012, 1, 10–13. [Google Scholar]
- Han, Z.; Wu, J.; Zhang, J.; Liu, L.; Tian, K. A General Self-Organization Tree-Based Energy-Balance Routing Protocol for Wireless Sensor Network. In Proceedings of the 2012 18th IEEE-NPSS Real Time Conference, Berkeley, CA, USA, 9–15 June 2012; pp. 1–6. [Google Scholar]
- Li, C.; Ye, M.; Chen, G.; Wu, J. An Energy-Efficient Unequal Clustering Mechanism for Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Mobile Adhoc and Sensor Systems Conference, Washington, DC, USA, 7–10 November 2005. [Google Scholar]
- Amjad, N.; Javaid, N.; Haider, A.; Awan, A.A.; Rahman, M. DREEM-ME: Distributed Regional Energy Efficient Multi-hop Routing Protocol based on Maximum Energy in WSNs. In Proceedings of the 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications, Compiegne, France, 28–30 October 2003. [Google Scholar]
- Amjad, N.; Javaid, N.; Haider, A.; Awan, A.A.; Rahman, M. REECHME: Regional Energy Efficient Cluster Heads based on Maximum Energy Routing Protocol for WSNs. In Proceedings of the 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications, Compiegne, France, 28–30 October 2003. [Google Scholar]
- Faisal, S.; Javaid, N.; Javaid, A.; Khan, M.A.; Bouk, S.H.; Khan, Z.A. Z-SEP: Zonal-stable election protocol for wireless sensor networks. arXiv 2013, arXiv:1303.5364. [Google Scholar]
- Mary, S.A.; Gnanadurai, J.B. A Zone-Based Clustering Protocol for wireless Sensor Networks. In Proceedings of the 9th International Conference on Computer Engineering and Applications, Toronto, ON, Canada, 13–14 July 2019; pp. 151–161. [Google Scholar]
- Misra, S.; Roy, S.; Obaidat, M.S.; Mohanta, D. A Fuzzy Logic-Based Energy Efficient Packet Loss Preventive Routing Protocol. In Proceedings of the 2009 International Symposium on Performance Evaluation of Computer & Telecommunication Systems, Istanbul, Turkey, 13–16 July 2009; Volume 41, pp. 185–192. [Google Scholar]
- Baranidharan, B.; Santhi, B. DUCF: Distributed load balancing Unequal Clustering in wireless sensor networks using Fuzzy approach. Appl. Soft Comput. 2016, 40, 495–506. [Google Scholar] [CrossRef]
- Bagci, H.; Yazici, A. An energy aware fuzzy approach to unequal clustering in wireless sensor networks. Appl. Soft Comput. 2013, 13, 1741–1749. [Google Scholar] [CrossRef]
- Taheri, H.; Neamatollahi, P.; Younis, O.M.; Naghibzadeh, S.; Yaghmaee, M.H. An energy-aware distributed clustering protocol in wireless sensor networks using fuzzy logic. Ad Hoc Netw. 2012, 10, 1469–1481. [Google Scholar] [CrossRef]
- Sert, S.A.; Bagci, H.; Yazici, A. MOFCA: Multi-objective fuzzy clustering algorithm for wireless sensor networks. Appl. Soft Comput. 2015, 30, 151–165. [Google Scholar] [CrossRef]
- Tamandani, Y.K.; Bokhari, M.U. SEPFL routing protocol based on fuzzy logic control to extend the lifetime and throughput of the wireless sensor network. Wirel. Netw. 2016, 22, 647–653. [Google Scholar] [CrossRef]
- Jung, K.; Lee, J.Y.; Jeong, H.Y. Improving adaptive cluster head selection of teen protocol using fuzzy logic for WMSN. Multimed. Tools Appl. 2016, 76, 18175–18190. [Google Scholar] [CrossRef]
- Lee, J.S.; Kao, T.Y. An Improved Three Layer Low-Energy Adaptive Clustering Hierarchy for Wireless Sensor Networks. IEEE Internet Things J. 2012, 3, 951–958. [Google Scholar] [CrossRef]
- Yu, Y.; Govindan, R.; Estrin, D. Geographical and Energy Aware Routing: A Recursive Data Dissemination Protocol for Wireless Sensor Networks; Technical Report; UCLA Computer Science Department: Los Angeles, CA, USA, 2001; pp. 1–11. [Google Scholar]
- Newsome, J.; Song, D. GEM: Graph EMbedding for Routing and Data-Centric Storage in Sensor Networks without Geographic Information. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems, Los Angeles, CA, USA, 5–7 November 2003; pp. 76–88. [Google Scholar]
- Blum, B.; He, T.; Son, S.; Stankovic, J. IGF: A State-Free Robust Communication Protocol for Wireless Sensor Networks; Technical Report CS-2003-11; Department of Computer Science, University of Virginia: Charlottesville, VA, USA, 2003. [Google Scholar]
- Lukachan, G.; Labrador, M.A. SELAR: Scalable Energy-Efficient Location Aided Routing Protocol for Wireless Sensor Networks. In Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks, Tampa, FL, USA, 16–18 November 2004; pp. 694–695. [Google Scholar]
- Leong, B.; Liskov, B.; Morris, R.T. Geographic Routing Without Planarization. In Proceedings of the 3rd Conference on Networked Systems Design and Implementation, San Jose, CA, USA, 8–10 May 2006; Volume 3, pp. 25–39. [Google Scholar]
- Zimmerling, M.; Dargie, W.; Reason, J.M. Reason, Energy-Efficient Routing in Linear Wireless Sensor Networks. In Proceedings of the 4th IEEE Internatonal Conference on Mobile Adhoc and Sensor Systems (MASS 2007), Pisa, Italy, 8–11 October 2007; pp. 1–3. [Google Scholar]
- Chen, D.; Varshney, P. On-demand Geographic Forwarding for Data Delivery in Wireless Sensor Networks. Comput. Commun. 2007, 30, 2954–2967. [Google Scholar] [CrossRef]
- Zou, L.; Lu, M.; Xiong, Z. PAGER-M: A Novel Location based Routing Protocol for Mobile Sensor Networks. In Proceedings of the 2007 ACM SIGMOD International Conference on Management of Data, Beijing, China, 12–14 June 2007; pp. 1182–1185. [Google Scholar]
- Chen, M.; Leung, V.C.; Mao, S.; Xiao, Y.; Chlamtac, I. Hybrid Geographical Routing for Flexible Energy-Delay Trade-Offs. IEEE Trans. Veh. Technol. 2009, 58, 4976–4988. [Google Scholar] [CrossRef]
- Rodoplu, V.; Meng, T.H. Minimum energy mobile wireless networks. IEEE J. Sel. Areas Commun. 1999, 17, 1333–1344. [Google Scholar] [CrossRef]
- Li, L.; Halpern, J.Y. Minimum Energy Mobile Wireless Networks Revisited. In Proceedings of the IEEE International Conference on Communications (ICC), Helsinki, Finland, 11–14 June 2001. [Google Scholar]
- Xu, Y.; Heidemann, J.; Estrin, D. Geography-Informed Energy Conservation for Ad Hoc Routing. In Proceedings of the 7th Annual ACM/IEEE International Conference on Mobile Computing and Networking (MobiCom), Rome, Italy, 16–21 July 2001. [Google Scholar]
- Boucetta, C.; Idoudi, H.; Saidane, L.A. PASC: Power Aware Scheduled Clustering in Wireless Sensor Networks. In Proceedings of the 2014 11th International Symposium on Wireless Communications Systems (ISWCS), Barcelona, Spain, 26–29 August 2014. [Google Scholar]
- Boucetta, C.; Idoudi, H.; Saidane, L.A. Ant Colony Optimization Based Hierarchical Data Dissemination in WSN. In Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015. [Google Scholar]
- Boucetta, C.; Idoudi, H.; Saidane, L.A. Adaptive Scheduling with Fault Tolerance for Wireless Sensor Networks. In Proceedings of the 2015 IEEE 81st Vehicular Technology Conference (VTC Spring), Glasgow, Scotland, 11–14 May 2015. [Google Scholar]
- Chaudhary, D.D.; Waghmare, L.M. Energy Efficiency and Latency Improving Protocol for Wireless Sensor Networks. In Proceedings of the 2013 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Mysore, India, 22–25 August 2013. [Google Scholar]
- Basagni, S.; Chlamtac, I.; Syrotiuk, V.R.; Woodward, B.A. A Distance Routing Effect Algorithm for Mobility (DREAM). In Proceedings of the 4th annual ACM/IEEE international conference on Mobile computing and networking, Dallas, TX, USA, 25–30 October 1998; pp. 67–84. [Google Scholar]
- Chen, M.; Gonzalez, S.; Zhang, Y.; Leung, V.C. Multi-agent Itinerary Planning in Wireless Sensor Networks. Comput. Sci. 2009, 22, 584–597. [Google Scholar]
- Chen, M.; Yang, L.T.; Kwon, T.; Zhou, L.; Jo, M. Itinerary Planning for Energy-efficient Agent Communication in Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2011, 60, 1–8. [Google Scholar]
- Abo-Zahhad, M.; Ahmed, S.M.; Sabor, N.; Sasaki, S. Mobile Sink based Adaptive Immune Energy Efficient Clustering Protocol for Improving the Lifetime and Stability Period of Wireless Sensor Networks. IEEE Sen. J. 2015, 15, 4576–4586. [Google Scholar] [CrossRef]
- Akbar, M.; Javaid, N.; Khan, Z.A.; Qasim, U.; Alghamdi, T.A.; Mohammad, S.N.; Ahmed, S.H.; Khan, M.I.; Bouk, S.H. Towards Network Lifetime Maximization: Sink Mobility Aware Multihop Scalable Hybrid Energy Efficient Protocols for Terrestrial WSNs. Int. J. Distrib. Sen. Netw. 2015, 11, 908495. [Google Scholar] [CrossRef]
- He, T.; Stankovic, J.A.; Lu, C.; Abdelzaher, T. SPEED: A Stateless Protocol for Real-Time Communication in Sensor Networks. In Proceedings of the 23rd International Conference on Distributed Computing Systems, Providence, RI, USA, 19–22 May 2003; pp. 46–55. [Google Scholar]
- Felemban, E.; Lee, C.G.; Ekici, E. MMSPEED: Multipath Multi-SPEED Protocol for QoS Guarantee of Reliability and Timeliness in Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2006, 5, 738–754. [Google Scholar] [CrossRef]
- Chen, M.; Lai, C.F.; Wang, H. Mobile Multimedia Sensor Networks: Architecture and Routing. In Proceedings of the Mobility Management in the Networks of the Future World, Shanghai, China, 10 April 2011; pp. 409–412. [Google Scholar]
- Akkaya, K.; Younis, M. An Energy-Aware QoS Routing Protocol for Wireless Sensor Networks. In Proceedings of the IEEE Workshop on Mobile and Wireless Networks (MWN 2003), Providence, RI, USA, 19–22 May 2003. [Google Scholar]
- Chang, J.H.; Tassiulas, L. Maximum Lifetime Routing in Wireless Sensor Networks. IEEE/ACM Trans. Netw. 2004, 12, 609–619. [Google Scholar] [CrossRef]
- Kalpakis, K.; Dasgupta, K.; Namjoshi, P. Maximum Lifetime Data Gathering and Aggregation in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Networking (NETWORKS 2002), Atlanta, GA, USA, 26–29 August 2002. [Google Scholar]
- Patel, M.; Chandrasekaran, R.; Venkatesan, S. Efficient Minimum-Cost Bandwidth-Constrained Routing in Wireless Sensor Networks. In Proceedings of the International Conference on Wireless Networks, Las Vegas, NV, USA, 21–24 June 2004; pp. 447–453. [Google Scholar]
- Mohanty, P.; Kabat, M.R. Energy efficient structure-free data aggregation and delivery in WSN. Egypt. Inf. J. 2016, 17, 273–284. [Google Scholar] [CrossRef]
- Singh, V.K.; Verma, R.; Kumar, M. Voronoi Neighbor Based Energy Efficient Event Detection in Wireless Sensor Networks. AEU Int. J. Electron. Commun. 2017, 82, 358–367. [Google Scholar] [CrossRef]
- Athmani, S.; Bilami, A.; Boubiche, D.E. EDAK: An Efficient Dynamic Authentication and Key Management Mechanism for heterogeneous WSNs. Future Gener. Comput. Syst. 2019, 92, 789–799. [Google Scholar] [CrossRef]
- Chenait, M.; Zebbane, B.; Benzaid, C.; Badache, N. Energy-Efficient Coverage Protocol Based on Stable and Predictive Scheduling in Wireless Sensor Networks. Comput. Netw. 2017, 127, 1–2. [Google Scholar] [CrossRef]
- Ahmed, G.; Zou, J.; Fareed, M.M.; Zeeshan, M. Sleep-awake energy efficient distributed clustering algorithm for wireless sensor networks. Comput. Electr. Eng. 2016, 56, 385–398. [Google Scholar] [CrossRef]
- Ghaffari, A. An Energy Efficient Routing Protocol for Wireless Sensor Networks using A-star Algorithm. J. Appl. Res. Technol. 2014, 12, 815–822. [Google Scholar] [CrossRef]
- Semchedine, F.; Oukachbi, W.; Zaichi, N.; Bouallouche-Medjkoune, L. EECP: A New Cross-layer Protocol for Routing in Wireless Sensor Networks. Procedia Comput. Sci. 2015, 73, 336–341. [Google Scholar] [CrossRef]
- Mahajan, S.; Malhotra, J.; Sharma, S. An energy balanced QoS based cluster head selection strategy for WSN. Egypt. Inf. J. 2014, 15, 189–199. [Google Scholar] [CrossRef]
- Qureshi, T.N.; Javaid, N.; Khan, A.H.; Iqbal, A.; Akhtar, E.; Ishfaq, M. BEENISH: Balanced Energy Efficient Network Integrated Super Heterogeneous Protocol for Wireless Sensor Networks. Procedia Comput. Sci. 2013, 19, 920–925. [Google Scholar] [CrossRef]
- Rehman, O.; Javaid, N.; Manzoor, B.; Hafeez, A.; Iqbal, A.; Ishfaq, M. Energy consumption rate based stable election protocol (ECRSEP) for WSNs. Procedia Comput. Sci. 2013, 19, 932–937. [Google Scholar] [CrossRef][Green Version]
- Sohrabi, K.; Gao, J.; Ailawadhi, V.; Pottie, G.J. Protocols for Self- Organization of a Wireless Sensor Network. IEEE Pers. Commun. 1999, 7, 16–27. [Google Scholar] [CrossRef]
- Mostafaei, H. Energy-Efficient Algorithm for Reliable Routing of Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2019, 66, 5567–5575. [Google Scholar] [CrossRef]
- Raju, J.; Garcia-Luna-Aceves, J.J. A New Approach to on-Demand Loop-free Multipath Routing. In Proceedings of the 8th International Conference on Computer Communications and Networks, Boston, MA, USA, 11–13 October 1999; pp. 522–527. [Google Scholar]
- Hou, X.; Tipper, D.; Kabara, J. Label based Multipath Routing (LMR) in Wireless Sensor Networks. In Proceedings of the 6th International Symposium on Advanced Radio Technologies (ISART), Boulder, CO, USA, 2–4 March 2004; pp. 113–118. [Google Scholar]
- Ye, F.; Zhong, G.; Lu, S.; Zhang, L. Gradient Broadcast: A Robust Data Delivery Protocol for Large Scale Sensor Networks. Wirel. Netw. 2005, 11, 285–298. [Google Scholar] [CrossRef]
- Wang, Y.; Tsai, C.H.; Mao, H. HMRP: Hierarchy based Multipath Routing Protocol for Wireless Sensor Networks. Sci. Eng. 2006, 9, 255–264. [Google Scholar]
- Zhang, J.; Jeong, C.K.; Lee, G.Y.; Kim, H.J. Cluster based Multi-Path Routing Algorithm for Multi-hop Wireless Network. Future Gener. Commun. Netw. 2007, 1, 67–75. [Google Scholar]
- Chen, M.; Leung, V.C.; Mao, S.; Yuan, Y. Directional Geographical Routing for Real-Time Video Communications in Wireless Sensor Networks. Comput. Commun. 2007, 30, 1–16. [Google Scholar] [CrossRef]
- Chen, M.; Leung, V.C.; Mao, S. Directional Controlled Fusion in Wireless Sensor Networks. Mob. Netw. Appl. 2009, 14, 220–229. [Google Scholar] [CrossRef]
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.W.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R.K. RPL: IPv6 Routing Protocol for Low power and Lossy Networks; RFC 6550; IETF: Fremont, CA, USA, 2012. [Google Scholar]
- Ye, F.; Chen, A.; Lu, S.; Zhang, L. A Scalable Solution to Minimum Cost Forwarding in Large Scale Sensor Networks. In Proceedings of the 10th International Conference on Computer Communications and Networks, Scottsdale, AZ, USA, 15–17 October 2001; pp. 304–309. [Google Scholar]
- Tan, C.K.; Liew, S.Y.; Goh, H.G.; Andonovic, I. A Fast, Adaptive, and Energy-Efficient Multi-Path Multi-Channel Data Collection Protocol for Wireless Sensor Networks. In Proceedings of the 2017 International Conference on Recent Advances in Signal Processing, Telecommunications and Computing, Danag, Vietnam, 9–11 January 2017. [Google Scholar]
- Amgoth, T.; Jana, P.K. Energy-aware routing algorithm for wireless sensor networks. Comput. Electr. Eng. 2015, 41, 357–367. [Google Scholar] [CrossRef]
- Dhand, G.; Tyagi, S.S. Data aggregation techniques in WSN: Survey. Procedia Comput. Sci. 2016, 92, 378–384. [Google Scholar] [CrossRef]
- Pushpalatha, S.; Shivaprakasha, K.S. Energy-Efficient Communication Using Data Aggregation and Data Compression Techniques in Wireless Sensor Networks: A Survey. In Advances in Communication, Signal Processing, VLSI, and Embedded Systems; Springer: Singapore, 2020; pp. 161–179. [Google Scholar]
- Roy, N.R.; Chandra, P. Analysis of Data Aggregation Techniques in WSN. In International Conference on Innovative Computing and Communications; Springer: Singapore, 2020; pp. 571–581. [Google Scholar]
- Nikolakopoulos, G.; Kandris, D.; Tzes, A. Adaptive compression of slowly varying images transmitted over wireless sensor networks. Sensors 2010, 10, 7170–7191. [Google Scholar] [CrossRef]
- Nikolakopoulos, G.; Stavrou, P.; Tsitsipis, D.; Kandris, D.; Tzes, A.; Theocharis, T. A dual scheme for compression and restoration of sequentially transmitted images over Wireless Sensor Networks. Ad Hoc Netw. 2013, 11, 410–426. [Google Scholar] [CrossRef]
- Uthayakumar, J.; Elhoseny, M.; Shankar, K. Highly Reliable and Low-Complexity Image Compression Scheme Using Neighborhood Correlation Sequence Algorithm in WSN. IEEE Trans. Reliab. 2020, 1–26. [Google Scholar] [CrossRef]
- Dagdeviren, O.; Akram, V.K. The Effect of Random Node Distribution and Transmission Ranges on Connectivity Robustness in Wireless Sensor Networks. In Proceedings of the 2019 International Symposium on Networks, Computers and Communications (ISNCC), Istanbul, Turkey, 18–20 June 2019; pp. 1–5. [Google Scholar]
- Swetha, K.; Lahari, V.; Manikrisha, G.V.; Sai, K.B. A Survey on Placement of Sensor Nodes in Deployment of Wireless Sensor Networks. In Proceedings of the 2019 International Conference on Intelligent Sustainable Systems (ICISS), Palladam, India, 21–22 February 2019; pp. 132–139. [Google Scholar]
- Das, S.; Debbarma, M.K. A Survey on Coverage Problems in Wireless Sensor Network Based on Monitored Region. In Advances in Data and Information Sciences; Springer: Singapore, 2019; pp. 349–359. [Google Scholar]
- Elhabyan, R.; Shi, W.; St-Hilaire, M. Coverage protocols for wireless sensor networks: Review and future directions. J. Commun. Netw. 2019, 21, 45–60. [Google Scholar] [CrossRef]
- Han, F.; Liu, X.; Mohamed, I.I.; Ghazali, K.H.; Zhao, Y. A Survey on Deployment and Coverage Strategies in Three-Dimensional Wireless Sensor Networks. In Proceedings of the 2019 8th International Conference on Software and Computer Applications, Penang, Malaysia, 19–21 February 2019; pp. 544–549. [Google Scholar]
- Farsi, M.; Elhosseini, M.A.; Badawy, M.; Ali, H.A.; Eldin, H.Z. Deployment techniques in wireless sensor networks, coverage and connectivity: A survey. IEEE Access 2019, 7, 28940–28954. [Google Scholar] [CrossRef]
- Senouci, M.R.; Mellouk, A. A robust uncertainty-aware cluster-based deployment approach for WSNs: Coverage, connectivity, and lifespan. J. Netw. Comput. Appl. 2019, 146, 102414. [Google Scholar] [CrossRef]
- Harizan, S.; Kuila, P. Coverage and connectivity aware energy efficient scheduling in target based wireless sensor networks: An improved genetic algorithm based approach. Wirel. Netw. 2019, 25, 1995–2011. [Google Scholar] [CrossRef]
- Kandris, D.; Vergados, D.J.; Vergados, D.D.; Tzes, A. A Routing Scheme for Congestion Avoidance in Wireless Sensor Networks. In Proceedings of the 6th Annual IEEE Conference on Automation Science and Engineering (CASE 2010), Toronto, ON, Canada, 21–24 August 2010; pp. 21–24. [Google Scholar]
- Kandris, D.; Tselikis, G.; Anastasiadis, E.; Panaousis, E.; Dagiuklas, T. COALA: A protocol for the avoidance and alleviation of congestion in wireless sensor networks. Sensors 2017, 17, 2502. [Google Scholar] [CrossRef]
- Kazmi, H.S.; Javaid, N.; Awais, M.; Tahir, M.; Shim, S.O.; Zikria, Y.B. Congestion avoidance and fault detection in WSNs using data science techniques. Trans. Emerg. Telecommun. Technol. 2019. [Google Scholar] [CrossRef]
- Gholipour, M.; Haghighat, A.T.; Meybodi, M.R. Congestion avoidance in cognitive wireless sensor networks using TOPSIS and response surface methodology. Telecommun. Syst. 2018, 67, 519–537. [Google Scholar] [CrossRef]
- Ghaffari, A. Congestion control mechanisms in wireless sensor networks: A survey. J. Netw. Comput. Appl. 2015, 52, 101–115. [Google Scholar] [CrossRef]
- Jan, M.A.; Jan, S.R.; Alam, M.; Akhunzada, A.; Rahman, I.U. A comprehensive analysis of congestion control protocols in wireless sensor networks. Mob. Netw. Appl. 2018, 23, 456–468. [Google Scholar] [CrossRef]
- Bohloulzadeh, A.; Rajaei, M. A Survey on Congestion Control Protocols in Wireless Sensor Networks. Int. J. Wirel. Inf. Netw. 2020, 1–20. [Google Scholar] [CrossRef]
- Venugopal, K.R.; Kumaraswamy, M. An Introduction to QoS in Wireless Sensor Networks. In QoS Routing Algorithms for Wireless Sensor Networks; Springer: Singapore, 2020; pp. 1–21. [Google Scholar]
- Li, S.; Kim, J.G.; Han, D.H.; Lee, K.S. A survey of energy-efficient communication protocols with QoS guarantees in wireless multimedia sensor networks. Sensors 2019, 19, 199. [Google Scholar] [CrossRef] [PubMed]
- Alhazmi Abrar, S.; Alzahrani Asma, S.; Alqahtani Ohood, N. Survey: Application-Aware Quality of Service Provisions in Wireless Sensor Networks. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–7. [Google Scholar]
- Yahiaoui, S.; Omar, M.; Bouabdallah, A.; Natalizio, E.; Challal, Y. An energy efficient and QoS aware routing protocol for wireless sensor and actuator networks. AEU Int. J. Electron. Commun. 2018, 83, 193–203. [Google Scholar] [CrossRef]
- Rani, A.; Kumar, S. A Survey of Security in Wireless Sensor Networks. In Proceedings of the 2017 3rd International Conference on Computational Intelligence & Communication Technology (CICT), Ghaziabad, India, 9–10 February 2017; pp. 1–5. [Google Scholar]
- Tomić, I.; McCann, J.A. A survey of potential security issues in existing wireless sensor network protocols. IEEE Internet Things J. 2017, 4, 1910–1923. [Google Scholar] [CrossRef]
- Xie, H.; Yan, Z.; Yao, Z.; Atiquzzaman, M. Data collection for security measurement in wireless sensor networks: A survey. IEEE Internet Things J. 2018, 6, 2205–2224. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, S.; Agrawal, R. An Analysis and Comparison of Security Protocols on Wireless Sensor Networks (WSN). In Design Frameworks for Wireless Networks; Springer: Singapore, 2020; pp. 3–21. [Google Scholar]
- Ibrahem, M.S.; Nazri, M.Z.; Othman, Z. Wireless Sensor Networks: An Overview of Multi-Objective Optimization Problems. J. Adv. Res. Dyn. Control Syst. 2018, 10, 1569–1588. [Google Scholar]
- Fei, Z.; Li, B.; Yang, S.; Xing, C.; Chen, H.; Hanzo, L. A survey of multi-objective optimization in wireless sensor networks: Metrics, algorithms, and open problems. IEEE Commun. Surv. Tutor. 2016, 19, 550–586. [Google Scholar] [CrossRef]
- Kandris, D.; Alexandridis, A.; Dagiuklas, T.; Panaousis, E.; Vergados, D.D. Multiobjective Optimization Algorithms for Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2020, in press. [Google Scholar]
- Kumar, D.P.; Amgoth, T.; Annavarapu, C.S. Machine learning algorithms for wireless sensor networks: A survey. Inf. Fusion 2019, 49, 1–25. [Google Scholar] [CrossRef]
- Lata, S.; Mehfuz, S. Machine Learning based Energy Efficient Wireless Sensor Network. In Proceedings of the 2019 International Conference on Power Electronics, Control and Automation (ICPECA), New Delhi, India, 16–17 November 2019; pp. 1–5. [Google Scholar]
- Zantalis, F.; Koulouras, G.; Karabetsos, S.; Kandris, D. A review of machine learning and IoT in smart transportation. Future Internet 2019, 11, 94. [Google Scholar] [CrossRef]
- Thangaramya, K.; Kulothungan, K.; Logambigai, R.; Selvi, M.; Ganapathy, S.; Kannan, A. Energy aware cluster and neuro-fuzzy based routing algorithm for wireless sensor networks in IoT. Comput. Netw. 2019, 151, 211–223. [Google Scholar] [CrossRef]
- Sabor, N.; Abo-Zahhad, M. A Comprehensive Survey of Intelligent-Based Hierarchical Routing Protocols for Wireless Sensor Networks. In Nature Inspired Computing for Wireless Sensor Networks; Springer: Singapore, 2020; pp. 197–257. [Google Scholar]
- Zhang, Y.; Zhang, X.; Ning, S.; Gao, J.; Liu, Y. Energy-efficient multilevel heterogeneous routing protocol for wireless sensor networks. IEEE Access 2019, 7, 55873–55884. [Google Scholar] [CrossRef]
- Verma, S.; Sood, N.; Sharma, A.K. A novelistic approach for energy efficient routing using single and multiple data sinks in heterogeneous wireless sensor network. Peer Peer Netw. Appl. 2019, 12, 1110–1136. [Google Scholar] [CrossRef]
- Zhao, X.; Ren, S.; Quan, H.; Gao, Q. Routing Protocol for Heterogeneous Wireless Sensor Networks Based on a Modified Grey Wolf Optimizer. Sensors 2020, 20, 820. [Google Scholar] [CrossRef]
- Yue, Y.-G.; He, P. A comprehensive survey on the reliability of mobile wireless sensor networks: Taxonomy, challenges, and future directions. Inf. Fusion 2018, 44, 188–204. [Google Scholar] [CrossRef]
- Sabor, N.; Sasaki, S.; Abo-Zahhad, M.; Ahmed, S.M. A comprehensive survey on hierarchical-based routing protocols for mobile wireless sensor networks: Review, taxonomy, and future directions. Wirel. Commun. Mob. Comput. 2017, 2017, 2818542. [Google Scholar] [CrossRef]
- Manikanthan, S.V.; Padmapriya, T. An efficient cluster head selection and routing in mobile WSN. Int. J. Interact. Mob. Technol. 2019, 13, 56–70. [Google Scholar]
- Gandhi Swati, A.; Sonavane, S.S. A Review on Routing Protocols and Deployment Challenges Concerning Underwater Wireless Sensor Network. TEST Eng. Manag. 2020, 82, 9020–9026. [Google Scholar]
- Jouhari, M.; Ibrahimi, K.; Tembine, H.; Ben-Othman, J. Underwater wireless sensor networks: A survey on enabling technologies, localization protocols, and internet of underwater things. IEEE Access 2019, 7, 96879–96899. [Google Scholar] [CrossRef]
- Haque, K.F.; Kabir, K.H.; Abdelgawad, A. Advancement of Routing Protocols and Applications of Underwater Wireless Sensor Network (UWSN): A Survey. Preprints 2020. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).