Abstract
Recently, Creignou et al. (Theory Comput. Syst. 2017), introduced the class DelayFPT into parameterised complexity theory in order to capture the notion of efficiently solvable parameterised enumeration problems. In this paper, we propose a framework for parameterised ordered enumeration and will show how to obtain enumeration algorithms running with an FPT delay in the context of general modification problems. We study these problems considering two different orders of solutions, namely, lexicographic order and order by size. Furthermore, we present two generic algorithmic strategies. The first one is based on the well-known principle of self-reducibility and is used in the context of lexicographic order. The second one shows that the existence of a neighbourhood structure among the solutions implies the existence of an algorithm running with FPT delay which outputs all solutions ordered non-decreasingly by their size.
1. Introduction
Given a computational problem one often is interested in generating all solutions. For instance, one wants to list all answers to a query to a database [1] or is interested in all hits that a web search engine produces [2]. Even in bioinformatics [3] or computational linguistics [4] such enumeration problems play a crucial role. In this setting, one is more interested in the delay between output solutions rather than in the overall runtime of such algorithms. Here, a uniform stream of solutions is highly desired. Johnson et al. [5] explain in their seminal paper that the notion of the complexity class , which consists of problems whose delay is bounded by a polynomial in the input length, is very important.
A view on studied enumeration problems fuels the observation that often a specific order in the output solutions is very central: Many applications benefit from printing “cheap” solutions first. Moreover, enumerating all solutions in non-decreasing order allows to determine not only the smallest solution, but also the kth-smallest one. Such a generating algorithm allows finding the smallest solution obeying further constraints (at each generation step one verifies which constraints match). Unfortunately, this technique cannot guarantee efficient enumeration because a long prefix of candidates may not satisfy them. Yet, this technique is very versatile due to its applicability to any additional decidable constraint [6]. Now, we want to exemplify this observation.
Creignou and Hébrard [7] studied, within the well-known Schaefer framework for Boolean constraint satisfaction problems [8], which classes of propositional CNF formulas enumerating all satisfying solutions is possible in . They showed that for the classes of Horn, anti-Horn, affine or bijunctive formulas, such an algorithm exists. However, for any other class of formulas, having a algorithm implies . Interestingly, their proof builds on the self-reducibility of the propositional satisfiability problem. By the approach of a flashlight search, that is, trying first an assignment 0 and then 1, they observed that their enumeration algorithm obeys lexicographic order.
Later, Creignou et al. [9] studied enumerating satisfying assignments for propositional formulas in non-decreasing weight. Surprisingly, now, efficiently enumerating is only possible for Horn formulas and width-2 affine formulas (that is, affine formulas with at most two literals per clause). To achieve their result, the authors exploited priority queues to ensure enumeration in order (as was observed already by Johnson et al. [5]).
While parameterised enumeration had already been considered before (see, e.g., the works of Fernau, Damaschke and Fomin et al. [10,11,12]), the notion of fixed-parameter tractable delay was novel, leading to the complexity class [13]. Intuitively, the “polynomial time” in the definition of here is substituted by a fixed-parameter runtime-bound of the form , where n denotes the input length, k is the input parameter and f is a computable function. This introduces the notion of efficiency in the context of the parameterised world, that is, fixed-parameter tractability (), to the enumeration framework. Creignou et al. [13] investigated a wealth of problems from propositional logic and developed enumeration algorithms based on self-reducibility and on the technique of kernelisation. Particularly, the membership of an enumeration problem in can be characterised by a specificly tailored form of kernelisability, very much as in the context of usual decision problems.
As this area of parameterised enumeration is rather young and has received less attention, we want to further support this topic with this paper. Here, we study ordered enumeration in the context of parameterised complexity. First, we introduce arbitrary orders to the parameterised enumeration framework. Then we consider the special context of graph modification problems where we are interested in ordered enumeration for the two mostly studied orders, namely by lexicographic and by non-decreasing size (where the size is the number of modifications that have to be made). We use two algorithmic strategies, depending on the respective order as follows. Based on the principle of self-reducibility we obtain (and polynomial-space) enumeration algorithms for lexicographic order, as soon as the decision problem is efficiently solvable. Secondly, we present a enumeration algorithm for order by size as soon as a certain -computable neighbourhood function on the solutions set exists (see Theorem 1). Notice that the presented algorithms do not enumerate the set of minimal solutions but the set of solutions of bounded size. Extending to such solutions from minimal ones in the enumeration process is not generally trivial. To cope with the order, we use a priority queue that may require exponential space in the input length (as there exist potentially that many solutions).
Eventually, we show that the observed principles and algorithmic strategies can be applied to general modification problems as well. For instance, a general modification problem could allow to flip bits of a string. It is a rather rare situation that a general algorithmic scheme is developed. Usually algorithms are devised on a very individual basis. We prove a wide scope of applicability of our method by presenting new delay ordered enumeration algorithms for a large variety of problems, such as cluster editing [14], triangulation [15], triangle deletion [16], closest-string [17] and backdoor sets [18]. Furthermore, there already exists work which adopts the introduced framework of Creignou et al. [13] in the area of conjunctive query enumeration [19], triangle enumeration [20], combinatorial optimisation [21], abstract argumentation [22] and global constraints [23].
2. Preliminaries
We start by defining parameterised enumeration problems with a specific ordering and their corresponding enumeration algorithms. Most definitions in this section transfer those of Johnson et al. and Schmidt [5,24] from the context of enumeration and those of Creignou et al. [13] from the context of parameterised enumeration to the context of parameterised ordered enumeration.
The studied orderings of enumeration problems in this paper are quasi-orders which will be defined in the following.
Definition 1
(Quasi-Order). Let R be a set and ⪯ a binary relation on R. Then ⪯ is a preorder (or quasi-order) if we have for all elements :
- and
- if and then .
We will write whenever is not true.
Now, we proceed by introducing parameterised enumeration problems with ordering. Intuitively, the corresponding enumeration algorithm for such problems has to obey the given ordering, that is, it has to produce solutions without violating that ordering.
Definition 2.
A parameterised enumeration problem with ordering is a quadruple such that the following holds:
- I is the set of instances.
- is the parameterisation function; κ is required to be polynomial time computable.
- is a function such that for all , is a finite set, the set of solutions of x. Further we write .
- ⪯ is a quasi-order on .
Notice that this order on all solutions is only a short way of simultaneously giving an order for each instance. Furthermore, we will write an index E letter, e.g., , , to denote that we are talking about an instance set, parameterisation function, etc., of a given enumeration problem E. In the next step, we fix the notion of enumeration algorithms in our setting.
Definition 3
(Enumeration Algorithm). Let be a parameterised enumeration problem with ordering. Then an algorithm is an enumeration algorithm for E if the following holds:
- For every , terminates after a finite number of steps.
- For every , outputs exactly the elements of without duplicates.
- For every and , if and then outputs solution y before solution z.
Before we define complexity classes for parameterised enumeration, we need the notion of delay for enumeration algorithms.
Definition 4
(Delay). Let be a parameterised enumeration problem with ordering and be an enumeration algorithm for E. Let be an instance. The ith delay of is the elapsed runtime with respect to of between outputting the ith and th solution in . The 0th delay is the precomputation time which is the elapsed runtime with respect to of from the start of the computation to the first output statement. Analogously, the nth delay, for , is the postcomputation time, which is the elapsed runtime with respect to of after the last output statement until terminates. Then, the delay of is the maximum over all of the ith delay of .
Now we are able to define two different complexity classes for parameterised enumeration following the notion of Creignou et al. [13].
Definition 5.
Let be a parameterised enumeration problem. We say that E is enumerable if there exists an enumeration algorithm , a computable function and a polynomial p such that for every , outputs all solutions of in time .
An enumeration algorithm is a algorithm if there exists a computable function and a polynomial p such that for every , outputs all solutions of with delay of at most .
The class consists of all parameterised enumeration problems that admit a -enumeration algorithm.
Some of our enumeration algorithms will make use of priority queues to enumerate all solutions in the correct order and to avoid duplicates. We will follow the approach of Johnson et al. [5]. For an instance x of a parameterised enumeration problem whose sizes of solutions are polynomially bounded in ; we use a priority queue Q to store a subset of of cardinality potentially exponential in . The insert operation of Q requires time. The extract minimum operation requires time, too. It is important, however, that the computation of the order between two elements takes at most time. As pointed out by Johnson et al., the required queue can be implemented with the help of standard balanced tree schemes [25].
2.1. Graph Modification Problems
Graph modification problems have been studied for a long time in computational complexity theory [26]. Already in the monograph by Garey and Johnson [27], among the graph-theoretic problems considered, many fall into this problem class. To the best of our knowledge, graph modification problems were studied in the context of parameterised complexity for the first time in [28].
In this paper, we consider only undirected graphs. Let denote the set of all undirected graphs. A graph property is a set of graphs. Given a graph property and an undirected graph G, we write if the graph G obeys the property , that is, .
Definition 6
(Graph Operations). A graph operation for G is either of the following:
- removing a vertex: A function such that is the graph obtained by removing the vertex v from G (if v is present; otherwise is the identity) and deleting all incident edges to v,
- adding/removing an edge: A function such that , is the graph obtained by adding/removing the edge to G if u and v are present in G; otherwise both functions are the identity
Two operations are dependent if
- and (o removes the vertex v and removes an edge incident to v) or
- and (o removes the edge and adds the same edge again).
A set of operations is consistent if it does not contain two dependent operations. Given such a consistent set of operations S, the graph obtained from G by applying the operations in S on G is denoted by .
Now, we turn towards the definition of solutions and will define minimality in terms of being inclusion-minimal.
Definition 7
(Solutions). Given a graph property , a graph G, and a set of operations O, we say that S is a solution for with respect to if the following three properties hold:
- 1.
- is a consistent set of operations,
- 2.
- and
- 3.
- .
A solution S is minimal if there is no solution such that .
Cai [28] was interested in the following parameterised graph modification decision problem with respect to a given graph property :
| Problem: | |
| Input: | , G undirected graph, , O set of operations on G. |
| Parameter: | The integer k. |
| Question: | Does there exist a solution for with respect to ? |
Some of the most important examples of graph modification problems are presented now. A chord in a graph is an edge between two vertices of a cycle C in G which is not part of C. A given graph is triangular (or chordal) if each of its induced cycles of four or more nodes has a chord. The problem triangulation then asks, given an undirected graph G and , whether there exists a set of at most k edges such that adding this set of edges to G makes it triangular. Yannakakis showed that this problem is complete [15]. Kaplan et al. [29] and independently Cai [28] have shown that the parameterised problem is in . For this problem, a solution is a set of edges which have to be added to the graph to make the graph triangular. Observe that, in this special case of the modification problem, the underlying property , “to be triangular”, does not have a finite forbidden set characterisation (since cycles of any length are problematic). Nevertheless, we will see later, that one can efficiently enumerate all minimal solutions as well.
A cluster is a graph such that all its connected components are cliques. In order to transform (or modify) a graph G we allow here only two kinds of operations: Adding or removing an edge. Cluster-Edition asks, given a graph G and a parameter k, whether there exists a consistent set of operations of cardinality at most k such that is cluster. It was shown by Shamir et al., that the problem is complete [14].
The problem Triangle-Deletion asks whether a given graph can be transformed into a triangle-free graph by deletion of at most k vertices. Yannakakis has shown that the problem is complete [16].
Analogous problems can be defined for many other classes of graphs, e.g., line graphs, claw-free graphs, Helly circular-arc graphs, etc., see [30].
Now, we turn towards the main focus of the paper. Here, we are interested in corresponding enumeration problems with ordering. In particular, we will focus on two well-known preorders, lexicographic ordering and ordering by size. Since our solutions are subsets of an ordered set of operations, they can be encoded as binary strings in which the ith bit from right indicates whether the ith operation is in the subset. We define the lexicographic ordering of solutions as the lexicographic ordering of these strings. Then, the size of a solution simply is its cardinality.
| Problem: | Enum- |
| Input: | , G undirected graph, , O ordered set of operations on G. |
| Parameter: | The integer k. |
| Output: | All solutions of with respect to in lexicographic order. |
| Problem: | Enum- |
| Input: | , G undirected graph, , O set of operations on G. |
| Parameter: | The integer k. |
| Output: | All solutions of with respect to in non-decreasing size. |
If the context is clear, we omit the subscript for the graph modification problem and simply write . Furthermore, we write for the function associating solutions to a given instance, and also for the set of all solutions of .
3. Enumeration of Graph Modification Problems with Ordering
In this section, we study the two previously introduced parameterised enumeration problems with ordering (lexicographic and size ordering).
3.1. Lexicographic Ordering
We first prove that, for any graph property , if the decision problem is in then there is an efficient enumeration algorithm for Enum-.
Lemma 1.
Let be a graph modification problem. If is in thenEnum-with polynomial space.
Proof.
Algorithm 1 enumerates all solutions of an instance of a given modification problem by the method of self-reducibility (it is an extension of the flash light search of Creignou and Hébrard [7]). The algorithm uses a function ExistsSol that tests if the instance of the modification problem has a solution. By the assumption of the lemma, so this function runs in FPT time. We use calls to this function to avoid exploration of branches of the recursion tree that do not lead to any output. Moreover, we ensure that the solutions using have to be consistent. This consistency check runs in polynomial time for graph operations. The rest yields a search tree of depth at most k. From this it follows that, for any instance of length n, the time beween the output of any two solutions is bounded by for some polynomial p and a computable function f. □
| Algorithm 1: Enumerate all solutions of in lexicographic order |
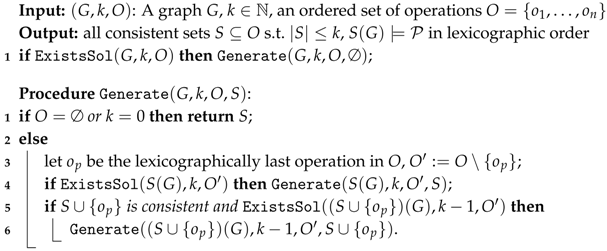 |
Corollary 1.
Enum-Triangulationlex ∈ DelayFPT with polynomial space.
Proof.
Kaplan et al. [29] and Cai [28] showed that Triangulation ∈ FPT. Now, by applying Lemma 1, we get the result. □
Cai [28] identified a class of graph properties whose associated modification problems belong to . Let us introduce some terminology.
Definition 8.
Given two graphs and , we write if H is an induced subgraph of G, i.e., and . Let be a set of graphs and be a graph property. We say that is a forbidden set characterisation of if for any graph G it holds that: iff for all
Among the problems presented in the previous section (see page 5), Triangle-Deletion and Cluster-Editing have a finite forbidden set characterisation, namely by triangles and paths of length two. In contrast to that, Triangulation has a forbidden set characterisation which is infinite, since cycles of arbitrary length are problematic. Actually, for properties having a finite forbidden set characterisation, the corresponding modification problem is fixed-parameter tractable. Together with Lemma 1, this provides a positive result in terms of enumeration.
Proposition 1
([28]). If a property has a finite forbidden set characterisation then is in .
Corollary 2.
For any graph modification problem, if has a finite forbidden set characterisation thenEnum-with polynomial space.
Proof.
This result follows by combining Proposition 1 with Lemma 1. □
3.2. Size Ordering
A common strategy in the enumeration context consists of defining a notion of a neighbourhood that allows to compute a new solution from a previous one with small amounts of computation time (see, e.g., the work of Avis and Fukuda [31]). We introduce the notion of a neighbourhood function, which, roughly speaking, generates some initial solutions from which all solutions can be produced. A priority queue then takes care of the ordering and avoids duplicates, which may require exponential space. For the graph modification problems of interest, we show that if the inclusion-minimal solutions can be generated in , then such a neighbourhood function exists, accordingly providing a -enumeration algorithm. In the following, (the “seed”) is a technical symbol that will be used to generate the initial solutions.
Definition 9.
Let be a graph modification problem. A neighbourhood function for is a (partial) function such that the following holds:
- 1.
- For all and , is defined.
- 2.
- For all , if , and is an arbitrary set of solutions otherwise.
- 3.
- For all and , if then .
- 4.
- For all and all , there exists and such that (i) , (ii) for and (iii) .
Furthermore, we say that is computable, when is computable in time for any and .
As a result, a neighbourhood function for a problem is a function that in a first phase computes from scratch an initial set of solutions (see Definition 9(2)). In many of our applications below, will be the set of all minimal solutions for x. In a second phase these solutions are iteratively extended (see condition (3)), where condition (4) guarantees that we do not miss any solution, as we will see in the next theorem.
Theorem 1.
Let be a graph modification problem. If admits a neighbourhood function that is -computable, thenEnum-.
Proof.
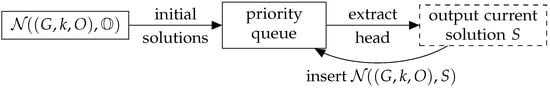
Algorithm 2 outputs all solutions in time. By the definition of the priority queue (recall in particular that insertion of an element is done only if the element is not yet present in the queue) and by the fact that all elements of are of bigger size than S by Definition 9(3), it is easily seen that the solutions are output in the right order and that no solution is output twice.
Besides, no solution is omitted. Indeed, given and associated with S by Definition 9(4), we prove by induction that each is inserted in Q during the run of the algorithm:
- :
- This proceeds from line 2 of the algorithm.
- :
- The solution is inserted in Q by induction hypothesis and hence all elements of , including , are inserted in Q (line 5 of Algorithm 2). Consequently, each is inserted in Q and then output during the run. In particular, this is true for .
Finally, we claim that Algorithm 2 (see Figure 1 for a graphical representation) runs in time. Indeed, the delay between the output of two consecutive solutions is bounded by the time required to compute a neighbourhood of the form or and to insert all its elements in the priority queue. This is in due to the assumption on being computable and as there is only a single extraction and many insertion operations in the queue. □

Figure 1.
Structure of Algorithm 2.
| Algorithm 2: algorithm for Enum- |
 |
A natural way to provide a neighbourhood function for a graph modification problem is to consider the inclusion minimal solutions of . Let us denote by Min- the problem of enumerating all inclusion minimal solutions of .
Theorem 2.
Let be a graph modification problem. IfMin-is enumerable thenEnum-.
Proof.
Let be an algorithm for Min-. Because of Theorem 1, it is sufficient to build an -neighbourhood function for . For an instance of and for , we define as the result of Algorithm 3.
| Algorithm 3: Procedure for computing |
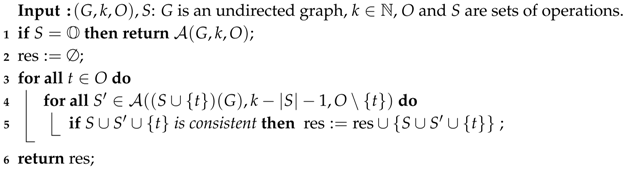 |
Accordingly, the function clearly fulfils Conditions 2 and 3 of Definition 9. We prove by induction that it also satisfies Condition 4 (that is, each solution T of size k comes with a sequence such that and for each i). If T is a minimal solution for , then and the expected sequence reduces to . Otherwise, there exists an and a non-empty set of transformations, say , such that and there is no solution for G between S and . This entails that is a minimal solution for and, as a consequence, (see lines 4–5 of Algorithm 3). The conclusion follows from the induction hypothesis that guarantees the existence of solutions such that , and . The expected sequence for T is nothing but . To conclude, it remains to show that Algorithm 3 is . This follows from the fact that is an algorithm (Lines 1 and 4 of Algorithm 3). □
Corollary 3.
Enum-Triangulationsize.
Proof.
All inclusion-minimal k-triangulations can be output in time for a given graph G and as shown by Kaplan et al. [29] (Theorem 2.4). This immediately yields the expected result via Theorem 2. □
Corollary 4.
For any property that has a finite forbidden set characterisation, the problemEnum-is in .
Proof.
The algorithm developed by Cai [28] for the decision problem is based on a bounded search tree, whose exhaustive examination provides all size minimal solutions in . Theorem 2 yields the conclusion. □
Corollary 5.
Enum-Cluster-Editingsize andEnum-Triangulation-Deletionsizeare in .
Proof.
Both problems have a finite forbidden set characterisation. For the cluster editing problem, paths of length two are the forbidden pattern, and, regarding Enum-Triangle-Deletionsize, the forbidden patterns are triangles. The result then follows from Corollary 4. □
4. Generalisation to Modification Problems
In this section, we will show how the algorithmic strategy that has been defined and formalised in the context of graph modification can be of use for many other problems, coming from various combinatorial frameworks.
Definition 10
(General Operations). Let be a language defined over an alphabet and let be an input. A set of operations is an infinite set of operations on instances of Q. We say that an operation ω is valid with respect to an instance , if . We write for the set of possible (valid) operations on an instance x.
Two operations are dependent with respect to an instance if
- or (intuitively, ω and cancel out)
- or . (intuitively, the order of ω and does not matter)
A set of operations is consistent with respect to x if it does not contain two dependent operations. Similarly, we say that an operation ω is consistent with a set S if and only if is consistent.
For instance, the set could contain operations that add edges or, in another case, flip bits. How exactly is defined highly depends on the corresponding language Q.
Example 1.
Let be the language of all undirected graphs encoded by adjacency matrices. Then is the set of all graph operations in the sense of Definition 6: Removing vertices or edges, adding edges. Note that contains all operations of the kind
for all . Furthermore, let be a concrete input graph. As a result, then is the restriction of Ω to those such that encode vertices in G.
Similarly to how it was defined in Section 2.1, a property is just a set. In the following context, it is a subset of a considered language Q. Intuitively, in the concept of graph modification problems, one may think of Q as . Then a graph property is just a subset of .
Definition 11
(General Solutions). Let be a language defined over an alphabet, be a finite set of operations on and be a property. We say that S is a solution (of x) if S is a consistent set of operations and . Furthermore, we denote by the set of all solutions for every instance . In addition, is the set of solutions for every instance .
Example 2.
Continuing the previous example, if the property is “to be a cluster” then a consistent solution S to a given graph is a sequence of removing vertices, adding and deleting of edges where
- there is no edge added or deleted such that vertex i or j is removed,
- there is no edge added and removed and
- .
Similarly, adding edge together with removing vertex i or j or removing edge is an inconsistent set of operations.
Now we want to define the corresponding decision and enumeration tasks. On that account, let be a property, be a parametrised problem with and be a set of operations.
| Parameter: | —parameterised modification problem w.r.t. a property over |
| Input: | , , set of operations. |
| Parameter: | The integer k. |
| Question: | Is there a solution and ? |
| Parameter: | Enum-Min-—parameterised minimum enumeration modification problem w.r.t. a property over |
| Input: | , , set of operations. |
| Parameter: | The integer k. |
| Output: | All minimal (w.r.t. some order) solutions with . |
The enumeration modification problem where we want to output all possible sets of transformations on a given instance x (and not only the minimum ones) then is Enum-.
In the following, we show how the notion of neighbourhood functions can be generalised as well. This will in turn yield generalisations of the results for graph modification problems afterwards.
Definition 12.
Let Σ be an alphabet, be a property and be a parameterised modification problem over Σ. A neighbourhood function for is a (partial) function such that the following holds:
- 1.
- For all and , is defined.
- 2.
- For all , if , and is an arbitrary set of solutions otherwise.
- 3.
- For all and , if then .
- 4.
- For all and all , there exists and such that (i) , (ii) for and (iii) .
Furthermore, we say that is computable when is computable in time for any and .
As already announced before, we are able to state generalised versions of Theorems 1 and 2 which can be proven in a similar way. However, one has to replace the graph modification problems by general modification problems.
Corollary 6.
Let be a property, be a parameterised modification problem and Ω be a set of operations such that is finite for all . If admits a neighbourhood function that is computable then Enum- using
- polynomial space for lexicographic order and
- exponential space for size order.
Corollary 7.
Let be a property, be a parameterised modification problem and Ω be a set of operations such that is finite for all . If Enum-Min- is enumerable and the consistency of solutions can be checked in then Enum- and using
- polynomial space for lexicographic order and
- exponential space for size order.
4.1. Closest String
In the following, we consider a central complete problem in coding theory [32]. Given a set of binary strings I, we want to find a string s with maximum Hamming distance for a , where is the Hamming distance between two strings.
Definition 13
(Bit-Flip operation). Given a string with and a set , denotes the string obtained from w by flipping the bits indicated by S, more formally , where if and otherwise.
The corresponding parametrised version is the following.
| Problem: | Closest-String |
| Input: | A sequence of k strings over each of given length and an integer . |
| Parameter: | The integer d. |
| Question: | Does there exist such that for all ? |
Proposition 2
([17]). Closest-String is in .
Moreover, an exhaustive examination of a bounded search tree constructed from the idea of Gramm et al. [17] (Figure 1), allows to produce all minimal solutions of this problem in . Accordingly, we get the following result for the corresponding enumeration problems.
Theorem 3.
- Enum-Closest-Stringlexwith polynomial space.
- Enum-Closest-Stringlexwith exponential space.
Proof.
is just the set of operations which flip the ith bit of a string for every . By combining Proposition 2 with Corollary 7 we get the desired result. □
4.2. Backdoors
In this section, we will consider the concept of backdoors. Let be a class of propositional formulas. Intuitively, a backdoor is a set of variables of a given propositional formula with the following property. Applying assignments over these variables to the formula always yields a formula in the class . Of course, one aims for formula classes for which satisfiability can be decided efficiently. Informally speaking, with the parameter backdoor size of a formula one tries to describe a distance to tractability. This definition was first introduced by Golmes, Williams and Selman [18] to model short distances to efficient subclasses. Until today, backdoors gained copious attention in many different areas: abduction [33], answer set programming [34,35], argumentation [36], default logic [37], temporal logic [38], planning [39] and constraint satisfaction [40,41].
Consider a formula in conjunctive normal form. Denote by for a partial truth assignment the result of removing all clauses from which contain a literal ℓ with and removing literals ℓ with from the remaining clauses.
Definition 14.
Let be a class of CNF formulas and ϕ be a CNF formula. A set of variables of ϕ is a strong backdoor set of ϕ if for all truth assignments we have that .
Definition 15
([42,43]). Let be a class of CNF formulas and ϕ be a CNF formula. A set of variables of ϕ is a -deletion backdoor set of ϕ if is in , where denotes the formula obtained from ϕ by deleting in ϕ all occurrences of variables from V.
Definition 16
(Weak Backdoor Sets). Let be a class of CNF formulas and ϕ be a propositional CNF formula. A set of variables from ϕ is a weak backdoor set of ϕ if there exists an assignment such that and is satisfiable.
Now let us consider the following enumeration problem.
| Problem: | Enum-Weak-BackDoorSet |
| Input: | A formula in CNF, . |
| Parameter: | The integer k. |
| Output: | The set of all weak backdoor sets of of size at most k. |
Similarly, define Enum-Strong-BackDoorSet for the set of all strong backdoor sets of of size at most k. Observe that the backdoor set problems can be seen as modification problems where solutions are sequences of variable assignments. The target property then simply is the class of CNF formulas .
Notice that Creignou et al. [13](Theorem 4), have studied enumeration for exact strong HORNbackdoor sets and provided an algorithm running in , where denotes the set of all Horn formulas, that is, CNF formulas whose clauses contain at most one positive literal.
Definition 17
(Base Class [44]). The class is a base class if it can be recognised in (that is, ), the satisfiability of its formulas is in and the class is closed under isomorphisms w.r.t. variable names. We say that is clause defined if for every CNF formula ϕ we have: if and only if for all clauses C from ϕ.
Proposition 3
([44](Proposition 2)). For every clause-defined base class , the detection of weak backdoor sets is in for input formulas in 3-CNF.
In their proof, Gaspers and Szeider [44] describe how utilising a bounded search tree allows one to solve the detection of weak backdoors in time. Interesting to note, this technique results in obtaining all minimal solutions in time. This observation results in the following theorem.
Theorem 4.
For every clause-defined base class and input formula in 3-CNF
- Enum-Weak--Backdoorslexwith polynomial space and
- Enum-Weak--Backdoorssizewith exponential space.
Proof.
The set of operations contains functions that replace a specific variable by a truth value . A solution encodes the chosen backdoor set together with the required assignment. Proposition 3 yields Enum-Min-Weak--Backdoorslex, resp., Enum-Min-Weak--Backdoorssize being enumerable. As the consistency check for solutions is in polynomial time, applying Corollary 7 completes the proof. □
In the following result, we will examine the parametrised enumeration complexity of the task to enumerate all strong -backdoor sets of a given 3-CNF formula for some clause-defined base class . Crucially, every strong backdoor set has to contain at least one variable from a clause that is not in C which relates to “hitting all bad clauses” like in the definition of deletion backdoors (see Definition 15).
Theorem 5.
For every clause-defined base class and input formula in 3-CNF:
- Enum-Strong--Backdoorslexwith polynomial space and
- Enum-Strong--Backdoorssizewith exponential space.
Proof.
We show that for every clause-defined base class and input formula in 3-CNF, the problem Min-Strong--Backdoors is enumerable. Indeed, we only need to branch on the variables from a clause and remove the corresponding literals over the considered variable from . The size of the branching tree is at most . As for base classes the satisfiability test is in , this yields an algorithm. The neighbourhood function for is defined to be the set of the pairwise unions of all minimal strong backdoors of together with for all variables . If , then the operations are As application of the functions happens only with respect to the backdoor size k, which is the parameter, the formula size increases by an exponential factor in the parameter only. This yields the preconditions for Corollary 7. □
4.3. Weighted Satisfiability Problems
Finally, we consider satisfiability questions for formulas in the Schaefer framework [8]. A constraint language is a finite set of relations. A formula , is a conjunction of constraints using only relations from and, consequently, is a quantifier-free first order formula.
As opposed to the approach of Creignou et al. [13], who examined maximum satisfiability, we now focus on the problem MinOnes-SAT defined below.
If are two (partial) assignments over some set of variables X and Y, then is true, if for all and .
Definition 18
(Minimality). Given a propositional formula ϕ and an assignment θ over the variables in ϕ with , we say that θ is minimal if there does not exist an assignment and . The size of θ is the number of variables it sets to true.
Formally, the problem of interest is defined with respect to any fixed constraint language :
| Problem: | Min-MinOnes-SATsize |
| Input: | , a formula , . |
| Parameter: | The integer k. |
| Output: | Generate all inclusion-minimal satisfying assignments of with by non-decreasing size. |
Similarly, the problem Enum-MinOnes-SAT asks for all satisfying assignments of with . In this context, the operations in are functions that replace the variable with index by true.
Theorem 6.
For all constraint languages Γ, we have: Min-MinOnes-SATsize is enumerable and Enum-MinOnes-SATsize with exponential space.
Proof.
For the first claim we can simply compute the minimal assignments by a straightforward branching algorithm: Initially, begin with the all 0-assignment, then consider all unsatisfied clauses in turn and flip one of the occurring variables to true. The second claim follows by a direct application of Corollary 7. □
5. Conclusions
We presented delay ordered enumeration algorithms for a large variety of problems, such as cluster editing, chordal completion, closest-string and weak and strong backdoors. An important point of our paper is that we propose a general strategy for efficient enumeration. This is rather rare in the literature, where algorithms are usually devised individually for specific problems. In particular, our scheme yields algorithms for all graph modification problems that are characterised by a finite set of forbidden patterns.
Initially, we focussed on graph-theoretic problems. Afterwards, the generic approach we presented covered problems which are not only of a graph-theoretic nature. Here, we defined general modification problems detached from graphs and constructed generic enumeration algorithms for arising problems in the world of strings, numbers, formulas, constraints, etc.
As an observation, we would like to mention that the algorithms presented in this paper require exponential space due to the inherent use of the priority queues to achieve ordered enumeration. An interesting question, continuing the research of Meier [45], is whether there is a method which requires less space but uses a comparable delay between the output of solutions and still obeys the underlying order on solutions.
Author Contributions
Conceptualization, N.C., R.K., A.M., J.-S.M., F.O. and H.V.; Funding acquisition, N.C., A.M. and H.V.; Methodology, N.C., R.K., A.M., J.-S.M., F.O. and H.V.; Supervision, N.C., A.M. and H.V.; Writing—original draft, N.C., R.K., A.M., F.O. and H.V.; Writing—review and editing, N.C., R.K., A.M., F.O. and H.V.
Funding
This research was funded by Deutsche Forschungsgemeinschaft (ME 4279/1-2) and the French Agence Nationale de la Recherche (AGGREG project reference ANR-14-CE25-0017).
Acknowledgments
We thank the anonymous reviewers for their valuable feedback.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Durand, A.; Schweikardt, N.; Segoufin, L. Enumerating answers to first-order queries over databases of low degree. In Proceedings of the 33rd ACM SIGMOD-SIGACT-SIGART Symposium on Principles of Database Systems, PODS’14, Snowbird, UT, USA, 22–27 June 2014; Hull, R., Grohe, M., Eds.; pp. 121–131. [Google Scholar] [CrossRef]
- Fogaras, D.; Rácz, B. A Scalable Randomized Method to Compute Link-Based Similarity Rank on the Web Graph. In Proceedings of the Current Trends in Database Technology—EDBT 2004 Workshops, EDBT 2004 Workshops PhD, DataX, PIM, P2P&DB, and ClustWeb, Heraklion, Crete, Greece, 14–18 March 2004; Revised Selected Papers. Lindner, W., Mesiti, M., Türker, C., Tzitzikas, Y., Vakali, A., Eds.; Lecture Notes in Computer Science. Springer: Berlin, Germany, 2004; Volume 3268, pp. 557–567. [Google Scholar] [CrossRef]
- Acuña, V.; Milreu, P.V.; Cottret, L.; Marchetti-Spaccamela, A.; Stougie, L.; Sagot, M. Algorithms and complexity of enumerating minimal precursor sets in genome-wide metabolic networks. Bioinformatics 2012, 28, 2474–2483. [Google Scholar] [CrossRef] [PubMed]
- Dill, K.A.; Lucas, A.; Hockenmaier, J.; Huang, L.; Chiang, D.; Joshi, A.K. Computational linguistics: A new tool for exploring biopolymer structures and statistical mechanics. Polymer 2007, 48, 4289–4300. [Google Scholar] [CrossRef]
- Johnson, D.S.; Papadimitriou, C.H.; Yannakakis, M. On Generating All Maximal Independent Sets. Inf. Process. Lett. 1988, 27, 119–123. [Google Scholar] [CrossRef]
- Sörensen, K.; Janssens, G.K. An algorithm to generate all spanning trees of a graph in order of increasing cost. Pesqui. Oper. 2005, 25, 219–229. [Google Scholar] [CrossRef]
- Creignou, N.; Hébrard, J.J. On generating all solutions of generalized satisfiability problems. Theor. Informatics Appl. 1997, 31, 499–511. [Google Scholar] [CrossRef]
- Schaefer, T.J. The Complexity of Satisfiability Problems. In Proceedings of the 10th Annual ACM Symposium on Theory of Computing, San Diego, CA, USA, 1–3 May 1978; Lipton, R.J., Burkhard, W.A., Savitch, W.J., Friedman, E.P., Aho, A.V., Eds.; pp. 216–226. [Google Scholar] [CrossRef]
- Creignou, N.; Olive, F.; Schmidt, J. Enumerating All Solutions of a Boolean CSP by Non-decreasing Weight. In Proceedings of the 14th International Conference on Theory and Applications of Satisfiability Testing, SAT 2011, Ann Arbor, MI, USA, 19–22 June 2011; Lecture Notes in Computer Science. Springer: Berlin, Germany, 2011; Volume 6695, pp. 120–133. [Google Scholar]
- Fernau, H. On Parameterized Enumeration. In Computing and Combinatorics; Springer: Berlin, Germany, 2002. [Google Scholar]
- Damaschke, P. Parameterized enumeration, transversals, and imperfect phylogeny reconstruction. Theor. Comput. Sci. 2006, 351, 337–350. [Google Scholar] [CrossRef]
- Fomin, F.V.; Saurabh, S.; Villanger, Y. A Polynomial Kernel for Proper Interval Vertex Deletion. SIAM J. Discret. Math. 2013, 27, 1964–1976. [Google Scholar] [CrossRef]
- Creignou, N.; Meier, A.; Müller, J.; Schmidt, J.; Vollmer, H. Paradigms for Parameterized Enumeration. Theory Comput. Syst. 2017, 60, 737–758. [Google Scholar] [CrossRef]
- Shamir, R.; Sharan, R.; Tsur, D. Cluster graph modification problems. Discret. Appl. Math. 2004, 114, 173–182. [Google Scholar] [CrossRef]
- Yannakakis, M. Computing the minimum fill-in is NP complete. SIAM J. Algebr. Discret. Methods 1981, 2, 77–79. [Google Scholar] [CrossRef]
- Yannakakis, M. Node- and edge-deletion NP complete problems. In Proceedings of the 10th Annual ACM Symposium on Theory of Computing, San Diego, CA, USA, 1–3 May 1978; pp. 253–264. [Google Scholar]
- Gramm, J.; Niedermeier, R.; Rossmanith, P. Fixed-Parameter Algorithms for CLOSEST STRING and Related Problems. Algorithmica 2003, 37, 25–42. [Google Scholar] [CrossRef]
- Williams, R.; Gomes, C.P.; Selman, B. Backdoors To Typical Case Complexity. In Proceedings of the IJCAI-03, Eighteenth International Joint Conference on Artificial Intelligence, Acapulco, Mexico, 9–15 August 2003; pp. 1173–1178. [Google Scholar]
- Kröll, M.; Pichler, R.; Skritek, S. On the Complexity of Enumerating the Answers to Well-designed Pattern Trees. In Proceedings of the 19th International Conference on Database Theory (ICDT 2016), Bordeaux, France, 15–18 March 2016; Martens, W., Zeume, T., Eds.; Leibniz International Proceedings in Informatics (LIPIcs). Schloss Dagstuhl–Leibniz-Zentrum fuer Informatik: Wadern, Germany, 2016; Volume 48, pp. 22:1–22:18. [Google Scholar] [CrossRef]
- Bentert, M.; Fluschnik, T.; Nichterlein, A.; Niedermeier, R. Parameterized aspects of triangle enumeration. J. Comput. Syst. Sci. 2019, 103, 61–77. [Google Scholar] [CrossRef]
- Bökler, F.; Ehrgott, M.; Morris, C.; Mutzel, P. Output-sensitive complexity of multiobjective combinatorial optimization. J. Multi-Criteria Decis. Anal. 2017, 24, 25–36. [Google Scholar] [CrossRef]
- Kröll, M.; Pichler, R.; Woltran, S. On the Complexity of Enumerating the Extensions of Abstract Argumentation Frameworks. In Proceedings of the 26th International Joint Conference on Artificial Intelligence, IJCAI 17, Melbourne, Australia, 19–25 August 2017; AAAI Press: Palo Alto, CA, USA, 2017; pp. 1145–1152. [Google Scholar]
- Carbonnel, C.; Hebrard, E. On the Kernelization of Global Constraints. In Proceedings of the 26th International Joint Conference on Artificial Intelligence, IJCAI 2017, Melbourne, Australia, CA, USA, 2017, 19–25 August 2017; AAAI Press: Palo Alto, CA, USA, 2017; pp. 578–584. [Google Scholar] [CrossRef]
- Schmidt, J. Enumeration: Algorithms and Complexity. Master’s Thesis, Leibniz Universität Hannover, Hanover, Germany, 2009. [Google Scholar]
- Hirai, Y.; Yamamoto, K. Balancing weight-balanced trees. J. Funct. Program. 2011, 21, 287–307. [Google Scholar] [CrossRef][Green Version]
- Bodlaender, H.L.; Heggernes, P.; Lokshtanov, D. Graph Modification Problems (Dagstuhl Seminar 14071). Dagstuhl Rep. 2014, 4, 38–59. [Google Scholar] [CrossRef]
- Garey, M.R.; Johnson, D.S. Computers and Intractability; A Guide to the Theory of NP-Completeness; W. H. Freeman & Co.: New York, NY, USA, 1990. [Google Scholar]
- Cai, L. Fixed-parameter tractability of graph modification problems for hereditary properties. Inf. Process. Lett. 1996, 58, 171–176. [Google Scholar] [CrossRef]
- Kaplan, H.; Shamir, R.; Tarjan, R.E. Tractability of parameterized completion problems on chordal, strongly chordal, and proper interval graphs. SIAM J. Comput. 1999, 28, 1906–1922. [Google Scholar] [CrossRef]
- Brandtstädt, A.; Le, V.B.; Spinrad, J.P. Graph Classes: A Survey; Monographs on Discrete Applied Mathematics; SIAM: Philadelphia, PA, USA, 1988. [Google Scholar]
- Avis, D.; Fukuda, K. Reverse search for enumeration. Discret. Appl. Math. 1996, 65, 21–46. [Google Scholar] [CrossRef]
- Frances, M.; Litman, A. On covering problems of codes. Theory Comput. Syst. 1997, 30, 113–119. [Google Scholar] [CrossRef]
- Pfandler, A.; Rümmele, S.; Szeider, S. Backdoors to Abduction. In Proceedings of the 23rd International Joint Conference on Artificial Intelligence, IJCAI 13, Beijing, China, 3–9 August 2013; Rossi, F., Ed.; pp. 1046–1052. [Google Scholar]
- Fichte, J.K.; Szeider, S. Backdoors to tractable answer set programming. Artif. Intell. 2015, 220, 64–103. [Google Scholar] [CrossRef]
- Fichte, J.K.; Szeider, S. Backdoors to Normality for Disjunctive Logic Programs. ACM Trans. Comput. Log. 2015, 17, 7:1–7:23. [Google Scholar] [CrossRef]
- Dvořák, W.; Ordyniak, S.; Szeider, S. Augmenting tractable fragments of abstract argumentation. Artif. Intell. 2012, 186, 157–173. [Google Scholar] [CrossRef]
- Fichte, J.K.; Meier, A.; Schindler, I. Strong Backdoors for Default Logic. In Proceedings of the 19th International Conference on Theory and Applications of Satisfiability Testing—SAT 2016, Bordeaux, France, 5–8 July 2016; pp. 45–59. [Google Scholar] [CrossRef]
- Meier, A.; Ordyniak, S.; Ramanujan, M.S.; Schindler, I. Backdoors for Linear Temporal Logic. Algorithmica 2019, 81, 476–496. [Google Scholar] [CrossRef] [PubMed]
- Kronegger, M.; Ordyniak, S.; Pfandler, A. Backdoors to planning. Artif. Intell. 2019, 269, 49–75. [Google Scholar] [CrossRef]
- Ganian, R.; Ramanujan, M.S.; Szeider, S. Combining Treewidth and Backdoors for CSP. In Proceedings of the 34th Symposium on Theoretical Aspects of Computer Science, STACS 2017, Hannover, Germany, 8–11 March 2017; Leibniz International Proceedings in Informatics (LIPIcs). Vollmer, H., Vallée, B., Eds.; Schloss Dagstuhl—Leibniz-Zentrum fuer Informatik: Wadern, Germany, 2017; Volume 66, pp. 36:1–36:17. [Google Scholar] [CrossRef]
- Gaspers, S.; Misra, N.; Ordyniak, S.; Szeider, S.; Zivny, S. Backdoors into heterogeneous classes of SAT and CSP. J. Comput. Syst. Sci. 2017, 85, 38–56. [Google Scholar] [CrossRef]
- Nishimura, N.; Ragde, P.; Szeider, S. Solving #SAT using vertex covers. Acta Inform. 2007, 44, 509–523. [Google Scholar] [CrossRef]
- Szeider, S. Matched Formulas and Backdoor Sets. J. Satisf. Boolean Model. Comput. 2009, 6, 1–12. [Google Scholar]
- Gaspers, S.; Szeider, S. Backdoors to Satisfaction. In The Multivariate Algorithmic Revolution and Beyond; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7370, pp. 287–317. [Google Scholar] [CrossRef]
- Meier, A. Enumeration in Incremental FPT-Time. arXiv 2018, arXiv:1804.07799. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).