A Cross-Layer Optimization QoS Scheme in Wireless Multimedia Sensor Networks
Abstract
1. Introduction
- Considering the characteristics of wireless sensor networks, distance coefficients are introduced into the Lyapunov function to increase network lifetime while maintaining QoS performances.
- To unify the dimension, different types of queues are normalized in the Lyapunov optimization framework.
- A DQS scheme and delay coefficients are utilized to adaptively allocate scheduling priorities to packets belonging to different services.
2. Network Model and Design of Queues
2.1. Network Model
2.2. Virtual Queue at The Transport Layer
2.3. Data Queue at The Network Layer
2.4. Design of Energy Queue
3. Problem Formation and Dynamic Algorithm
3.1. Design Throughput Utility Optimization Problem
3.2. Design Dynamic Algorithm via Lyapunov Optimization
| Algorithm 1 (Distributed gradient projection power control algorithm) [49]: |
| There are s links in link set , which are . In each time slot, the optimal transmission power of node n is gained through multiple iterations of . denotes the ttth iteration of . represents other links, except for (n, n′), in the network. is updated as follows: |
| Algorithm 2 (Block coordinate descent power control algorithm) [41]: |
| There are s links in link set , which are . There are multiple iterations in a time slot. In each iteration, the optimal transmission powers of links in are calculated in turn. The optimization process in each iteration is as follows:
……
|
4. Simulation
4.1. Simulation Setup
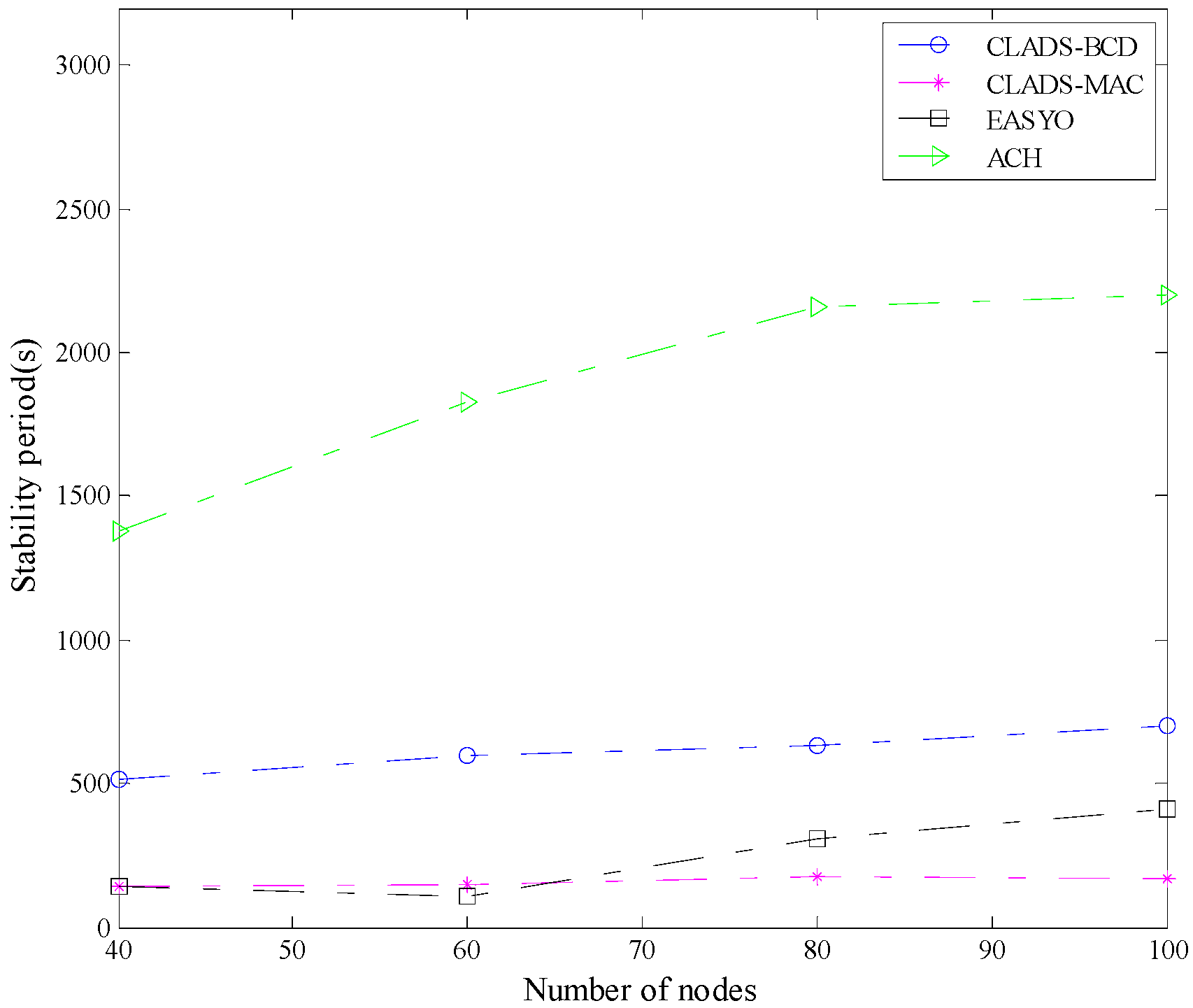
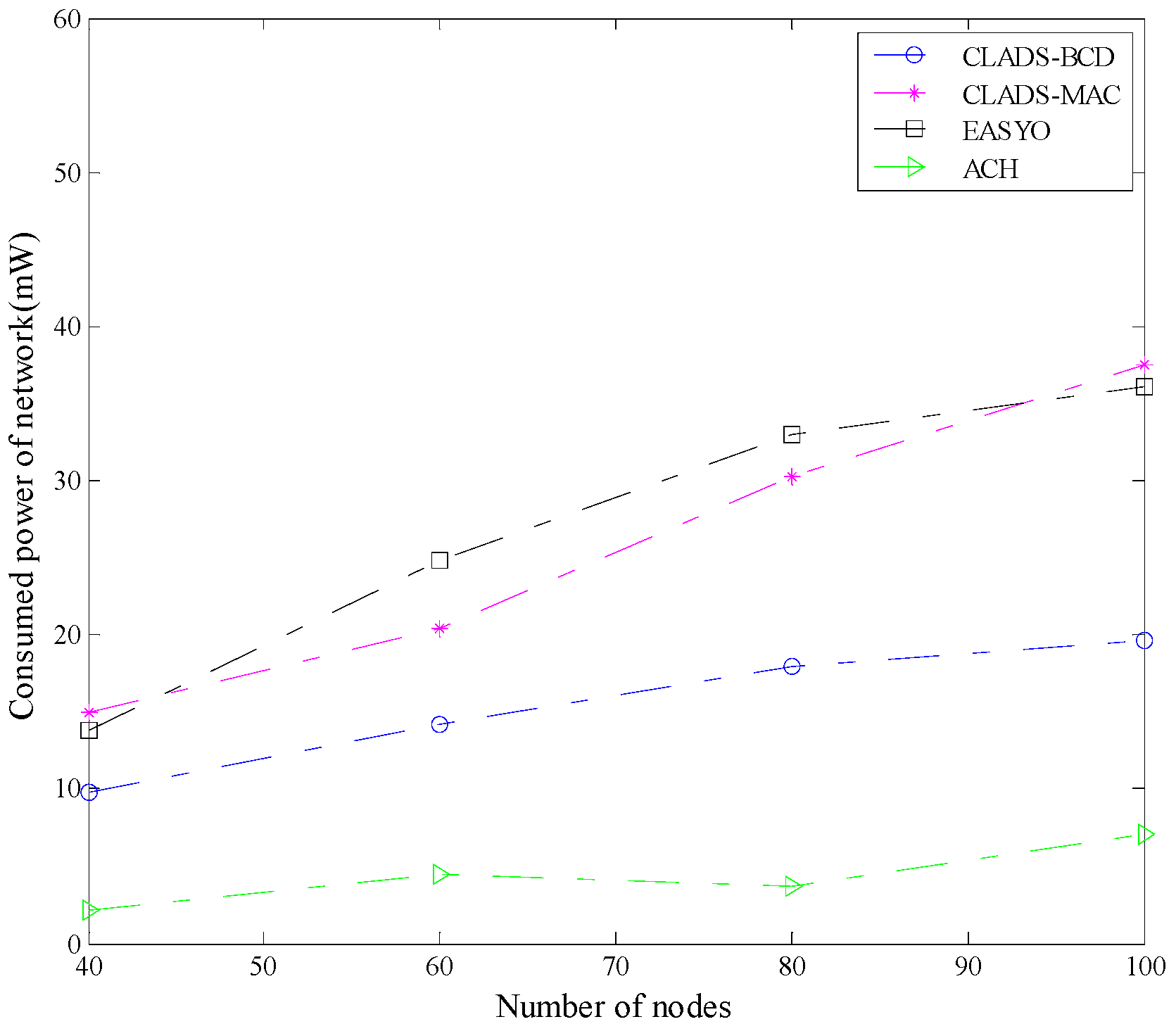
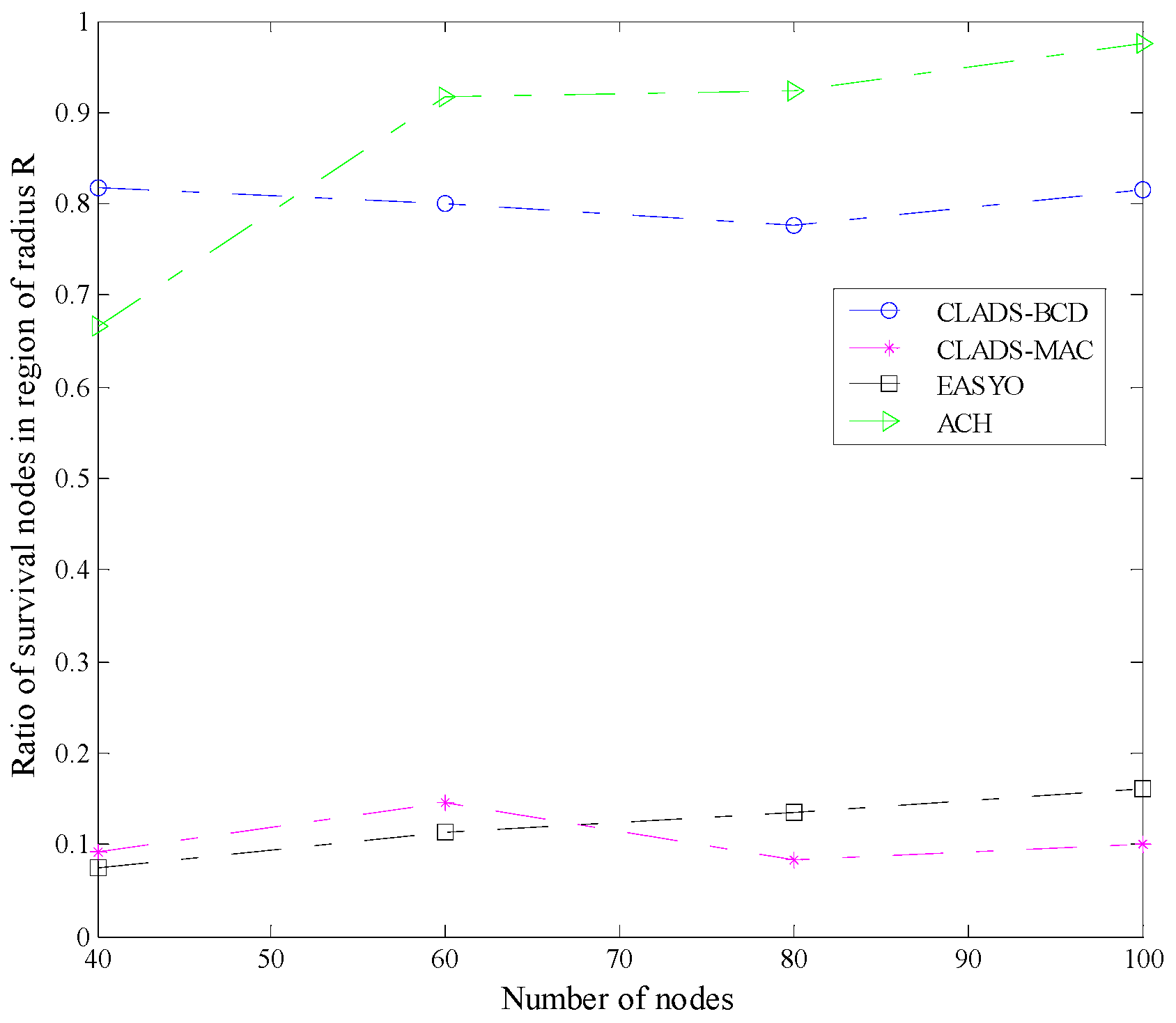
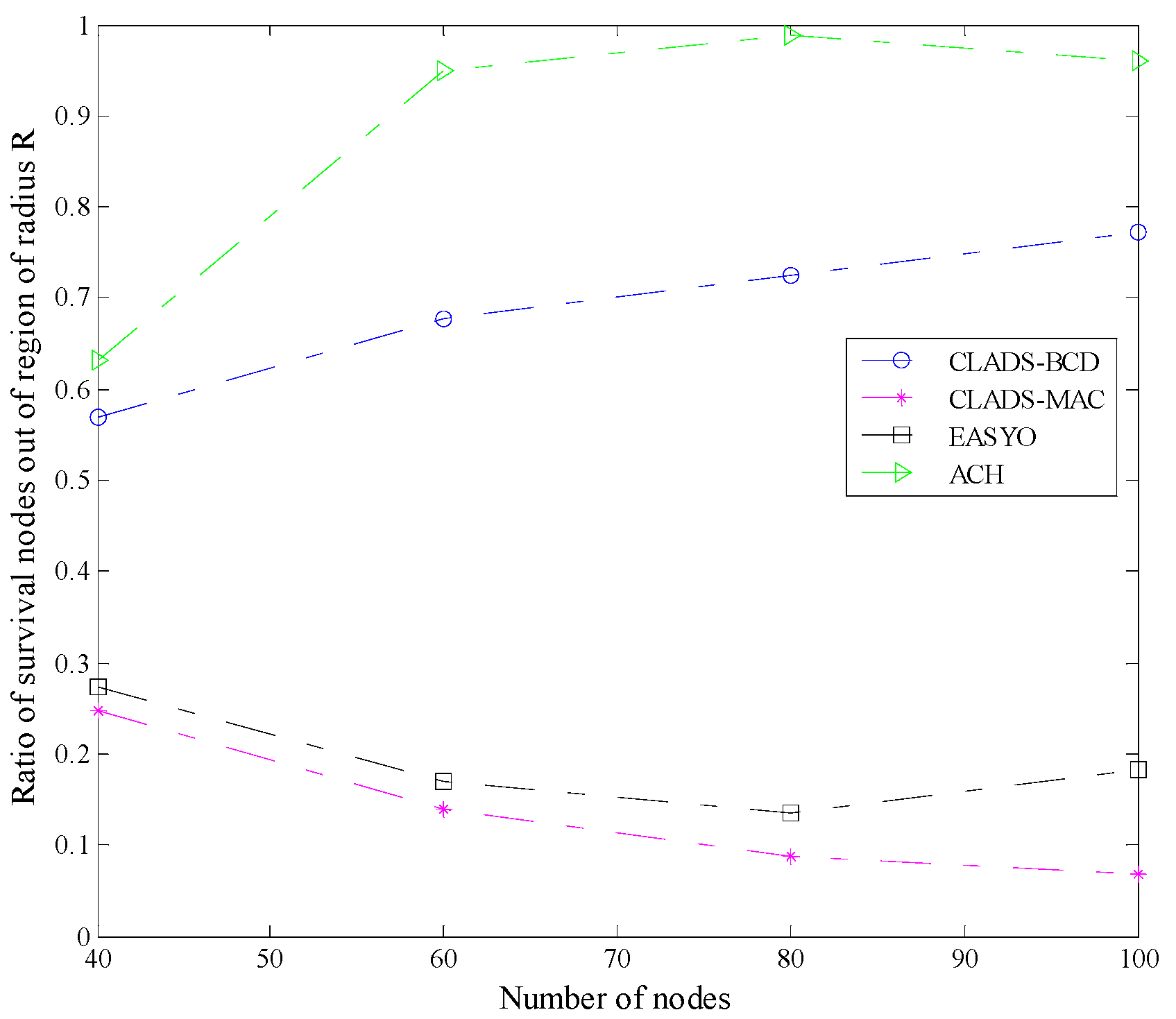
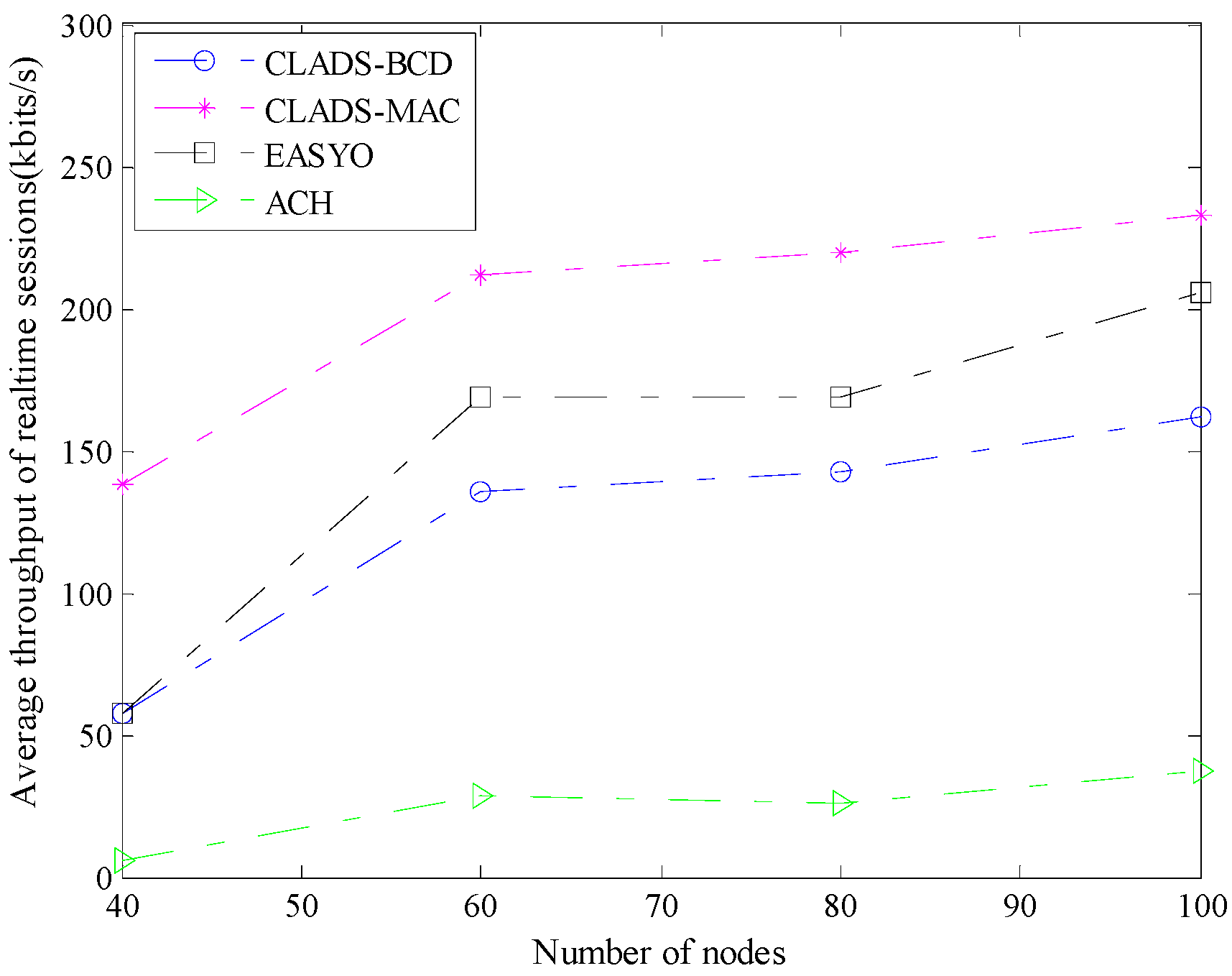
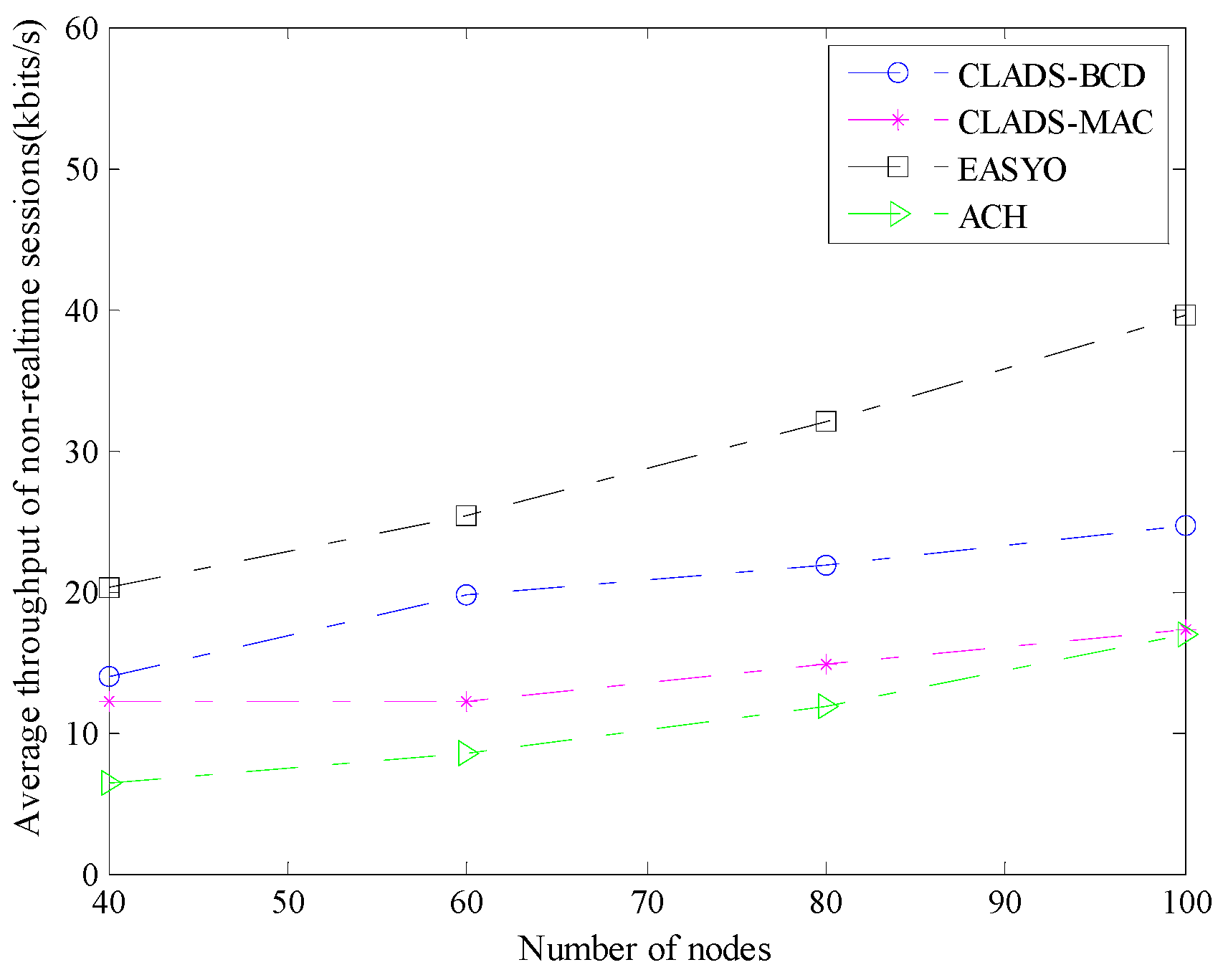
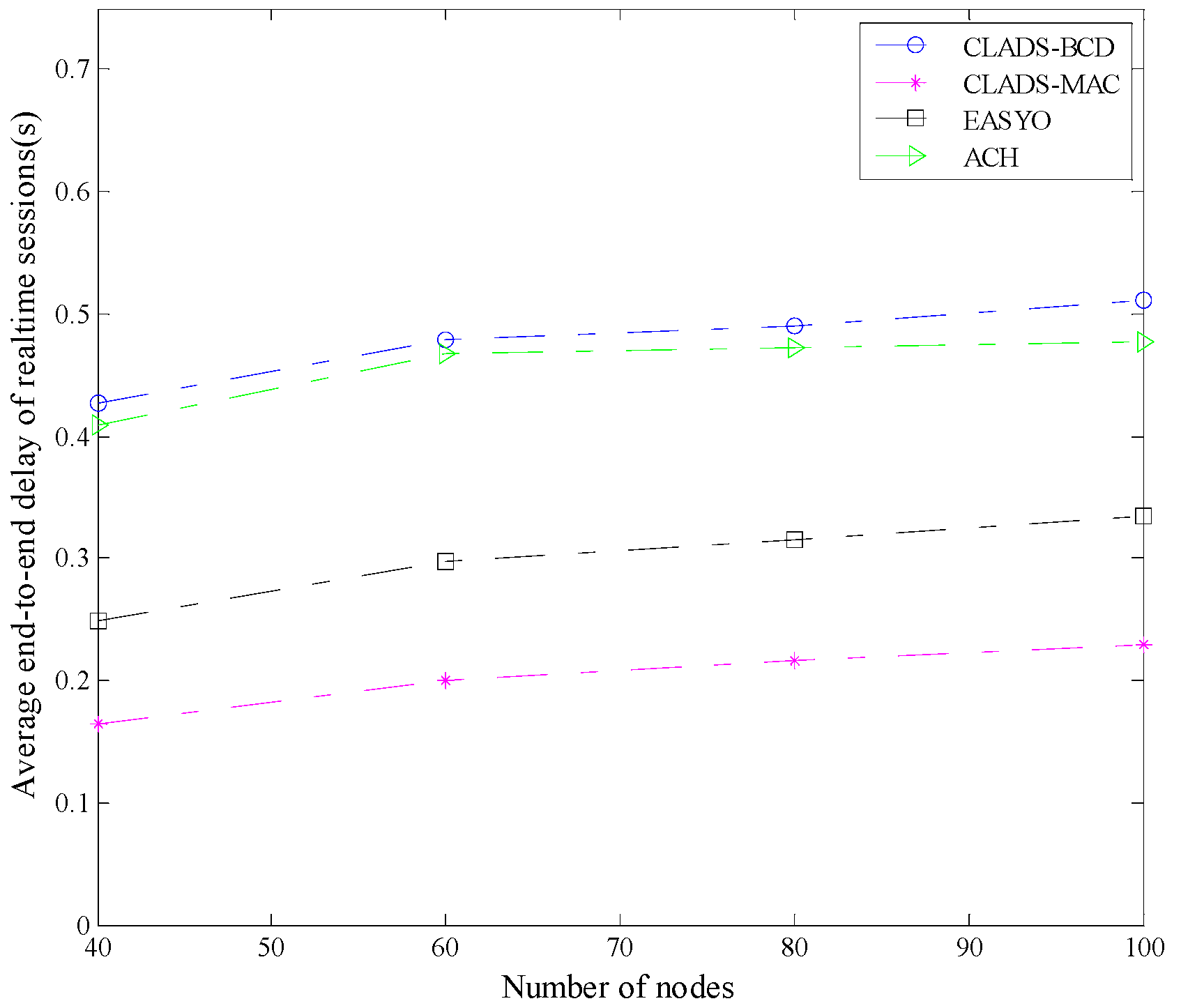
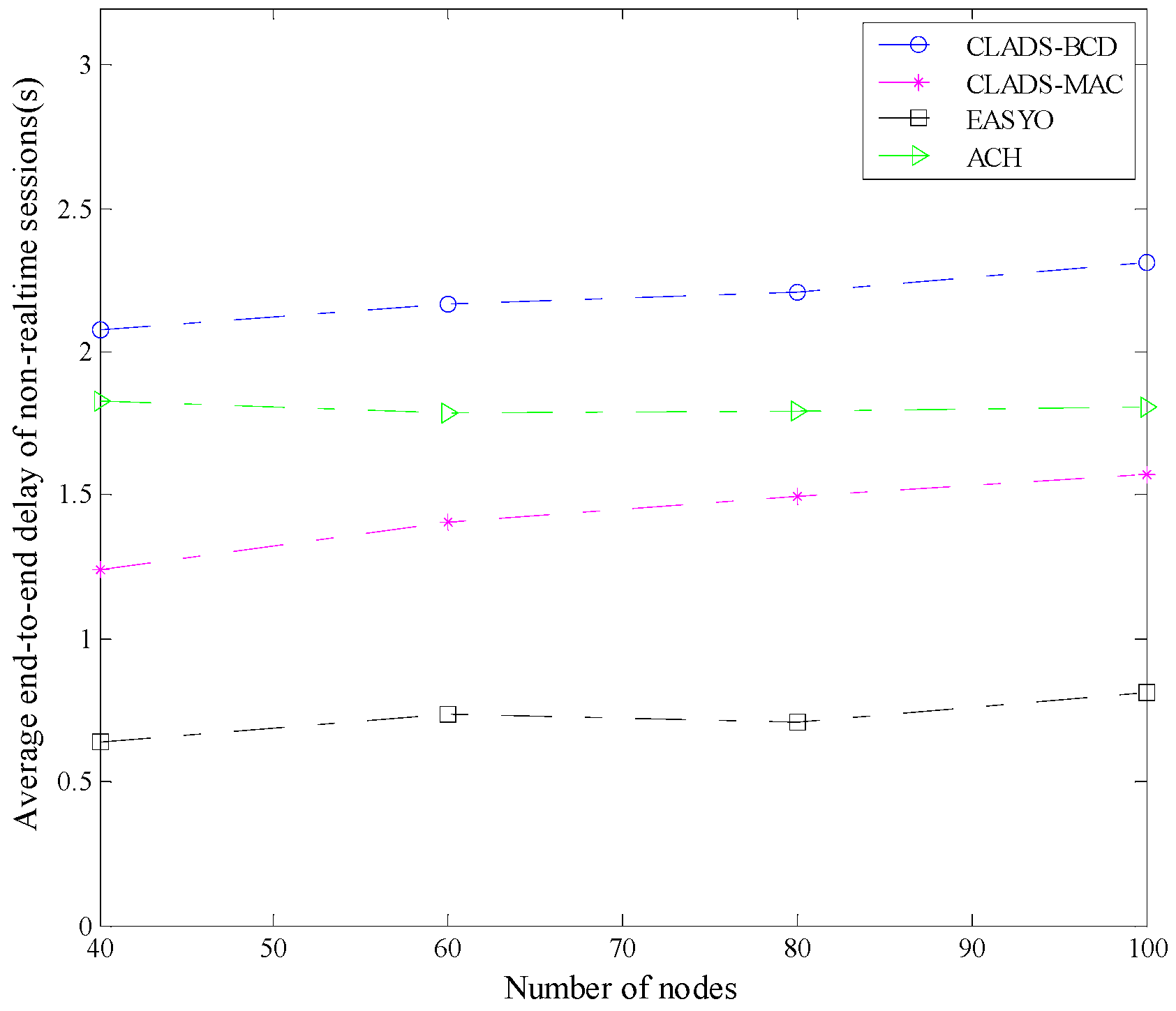
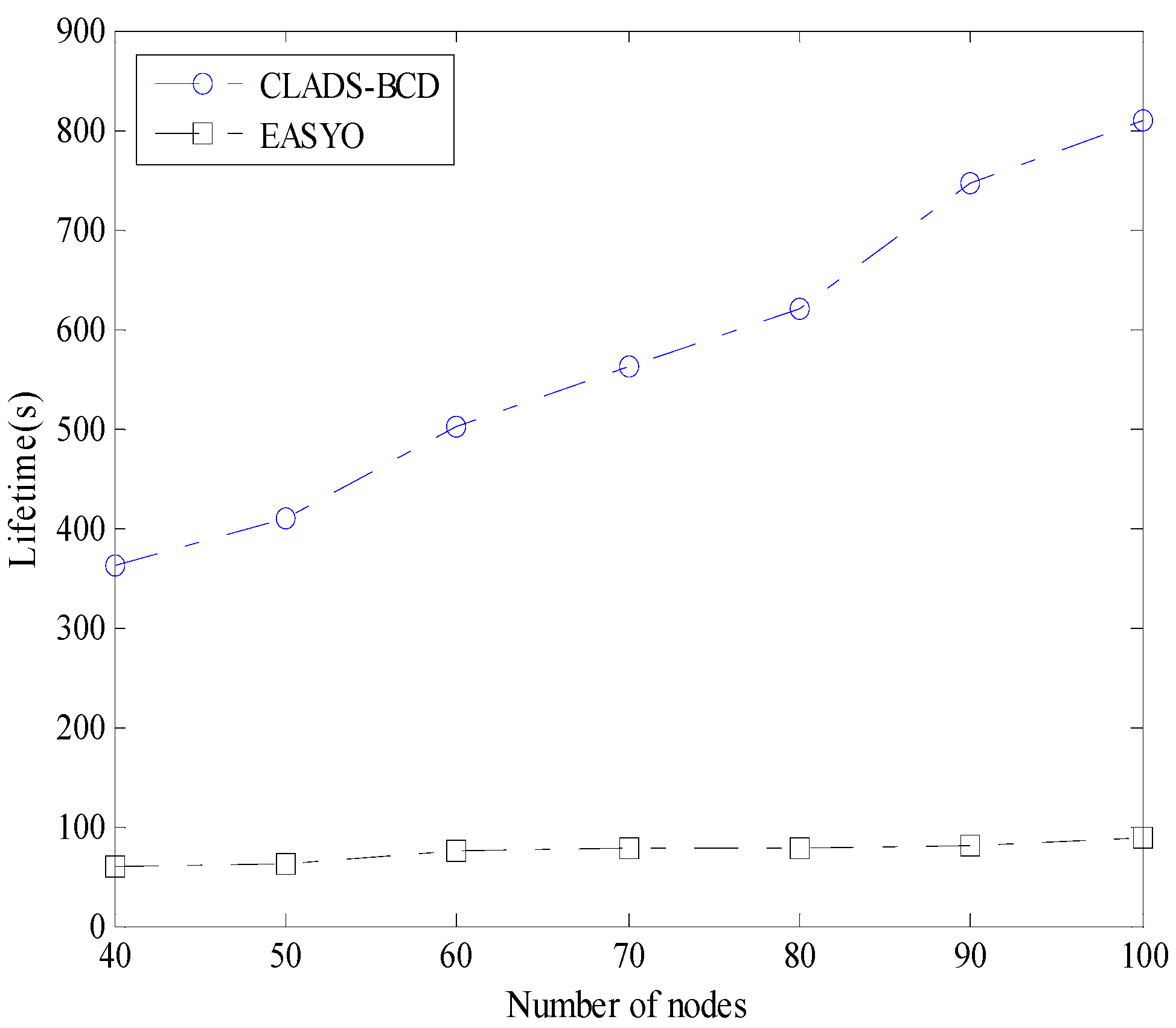
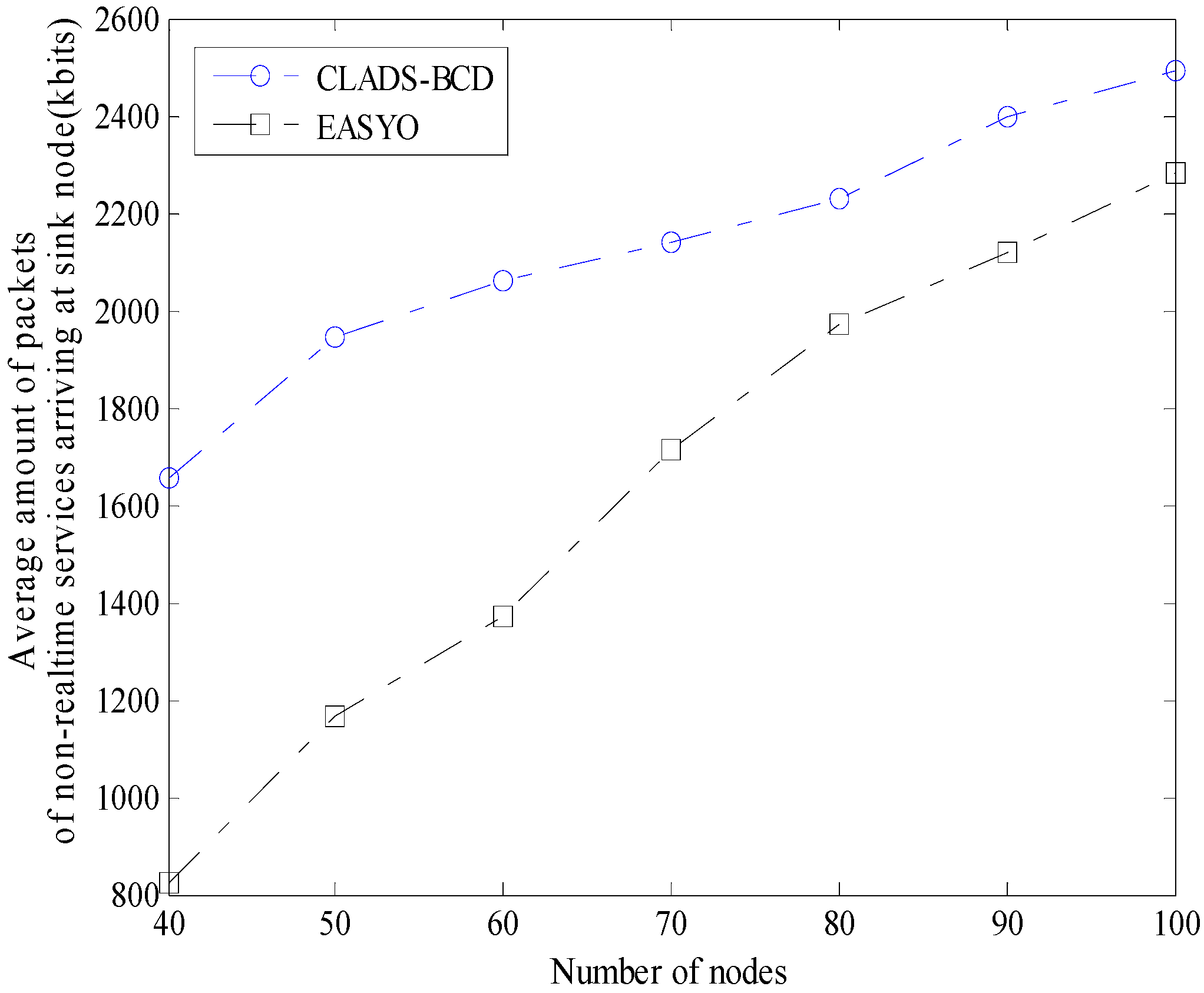
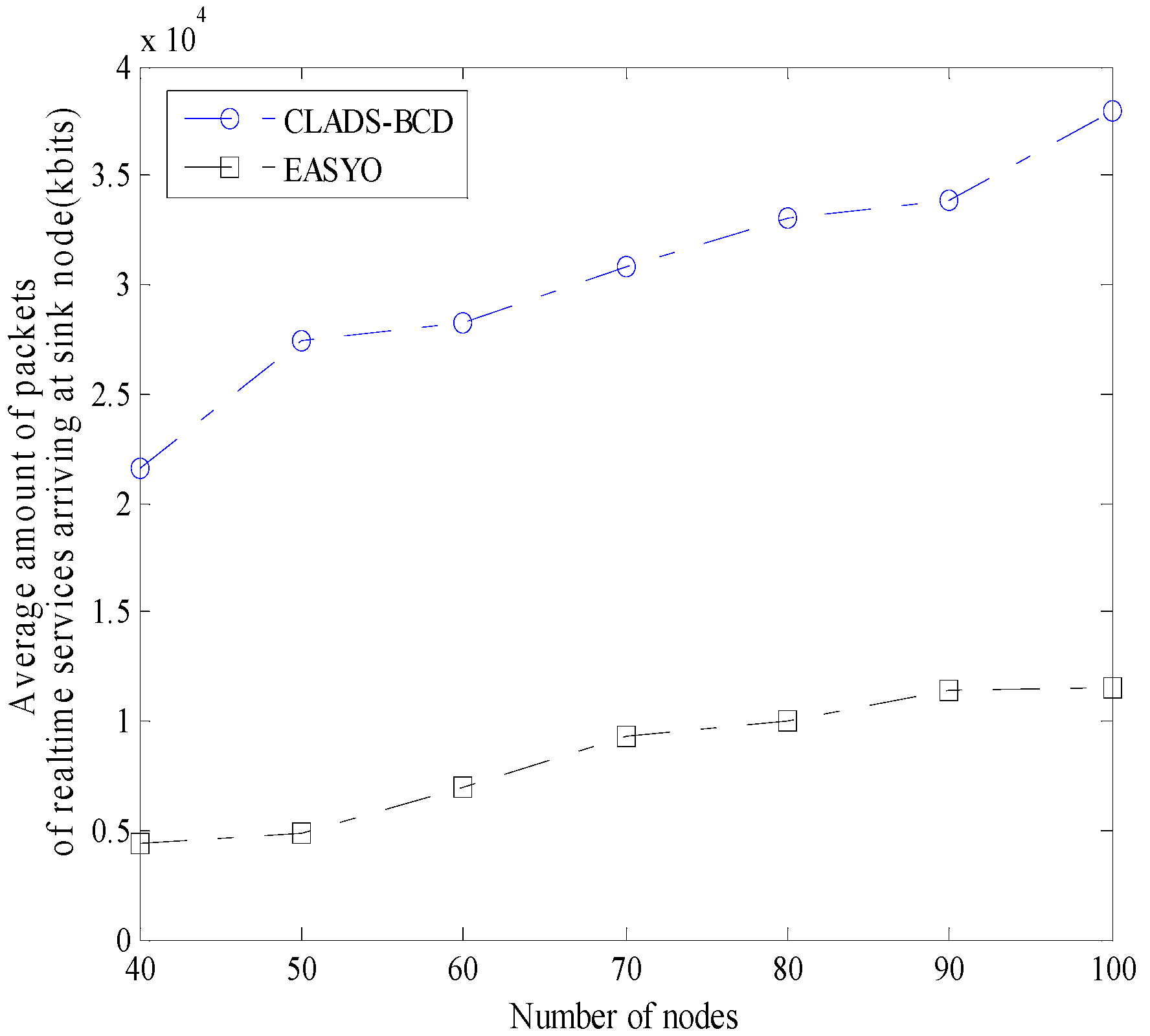
4.2. Comparison of Performance
5. Conclusions
Funding
Conflicts of Interest
References
- Akyildiz, I.F.; Melodia, T.; Chowdhury, K.R. A survey on wireless multimedia sensor networks. Int. J. Comput. Telecommun. Netw. 2007, 51, 921–960. [Google Scholar] [CrossRef]
- Muhammad, F.M.; Syed, H.A.; Siraj, M.; Song, H.B.; Danda, B.R. Multimedia streaming in information-centric networking: A survey and future perspectives. Comput. Netw. 2017, 125, 103–121. [Google Scholar]
- Yao, Y.C.; Wen, J.H.; Weng, C.E. The performance evaluation of IEEE 802.11e for QoS support in wireless LANs. Wirel. Pers. Commun. 2013, 69, 413–425. [Google Scholar] [CrossRef]
- Mu’Azu, A.A.; Tang, L.J.; Hasbullah, H.; Lawal, I.A.; Shah, P.A. Real-time massage differentiation with priority data service flows in VANET. In Proceedings of the International Conference on Computer and Information Sciences, Kuala Lumpur, Malaysia, 3–5 June 2014. [Google Scholar] [CrossRef]
- Qin, Y.; Li, L.; Zhong, X.X.; Yang, Y.Y. A cross-layer QoS design with energy and traffic balance aware for different types of traffic in MANETs. Wirel. Pers. Commun. 2015, 85, 1429–1449. [Google Scholar] [CrossRef]
- Wu, K.D.; Liao, W.J. On service differentiation for multimedia traffic in multi-hop wireless networks. IEEE Trans. Wirel. Commun. 2009, 8, 2464–2472. [Google Scholar] [CrossRef]
- Liu, C.Y.; Fu, B.; Huang, H.J. Delay minimization and priority scheduling in wireless mesh networks. Wirel. Netw. 2014, 20, 1955–1965. [Google Scholar] [CrossRef]
- Brahmia, M.E.A.; Abouaissa, A.; Lorenz, P. Adaptive scheduling mechanism for IPTV over WIMAX IEEE 802.16j networks. Int. J. Commun. Syst. 2014, 27, 1009–1019. [Google Scholar] [CrossRef]
- Mezouary, R.E.; Loutfi, A.; Koutbi, M.E. A cross-layer architecture for service differentiation in wireless sensor networks with multiple sinks. In Proceedings of the International Conference on Multimedia Computing and Systems, Marrakech, Morocco, 14–16 April 2014; pp. 843–848. [Google Scholar]
- Yuan, D.; Song, M.; Teng, Y.; Ma, D.; Wang, X.J.; Lu, G.F. QoE-oriented resource allocation for multiuser-multiservice femtocell networks. China Commun. 2015, 12, 27–41. [Google Scholar] [CrossRef]
- Reis, A.B.; Chakareski, J.; Kassler, A.; Sargento, S. Quality of experience optimized scheduling in multi-service wireless mesh networks. In Proceedings of the International Conference on Image Processing, HongKong, China, 26–29 September 2010; pp. 3233–3236. [Google Scholar]
- Lari, A.R.; Akbari, B. Network adaptive multipath video delivery over wireless multimedia sensor networks based on packet and path priority scheduling. In Proceedings of the International Conference on Broadband, Wireless Computing Communication and Applications, Fukuoka, Japan, 4–6 November 2010; pp. 351–356. [Google Scholar]
- Djenouri, D.; Balasingham, I. Traffic differentiation based modular QoS localized routing for wireless sensor networks. IEEE Trans. Mob. Comput. 2011, 10, 797–809. [Google Scholar] [CrossRef]
- Sahin, D.; Gungor, V.C.; Kocak, T.; Tuna, G. Quality-of-service differentiation in single-path and multi-path routing for wireless sensor network-based smart grid applications. Ad Hoc Netw. 2014, 22, 43–60. [Google Scholar] [CrossRef]
- Shah, G.A.; Gungor, V.C.; Akan, O.B. A cross-layer QoS-aware communication framework in cognitive radio sensor networks for smart grid applications. IEEE Trans. Ind. Inform. 2013, 9, 1477–1485. [Google Scholar] [CrossRef]
- Zhou, A.F.; Liu, M.; Li, Z.C.; Dutkiewicz, E. Cross-layer design for proportional delay differentiation and network utility maximization in multi-hop wireless networks. IEEE Trans. Wirel. Commun. 2012, 11, 1446–1455. [Google Scholar] [CrossRef]
- Vo, N.S.; Duong, T.Q.; Zepernick, H.J.; Fiedler, M. A cross-layer optimized scheme and its application in mobile multimedia networks with QoS provision. IEEE Syst. J. 2016, 10, 817–830. [Google Scholar] [CrossRef]
- Jiang, S. Granular differentiated queueing services for QoS: Structure and cost model. Acm Sigcomm Comput. Commun. Rev. 2005, 35, 13–22. [Google Scholar] [CrossRef]
- Teng, X.; Jiang, S.; Wei, G.; Liu, G. A cross-layer implementation of differentiated queueing service (DQS) for wireless mesh networks. In Proceedings of the the 67th IEEE Vehicular Technology Conference, Singapore, 11–14 May 2008; pp. 2233–2237. [Google Scholar]
- Tang, L.; Jiang, S.M.; Ao, X. Improved differentiated queueing service based on event QoS parameters for wireless sensor networks. In Proceedings of the IEEE 12th International Conference on Communication Technology, Nanjing, China, 11–14 November 2010; pp. 1327–1331. [Google Scholar]
- Mammu, A.S.K.; Sharma, A.; Hemandezjayo, U.; Sainz, N. A novel cluster-based energy efficient routing in wireless sensor networks. In Proceedings of the IEEE 27th International Conference on Advanced Information Networking and Applications, Barcelona, Spain, 25–28 March 2013; pp. 41–47. [Google Scholar]
- Smaragdakis, G.; Matta, I.; Bestavros, A. SEP: A Stable Election Protocol for Clustered Heterogeneous Wireless Sensor Networks. In Proceedings of the 2nd International Workshop on Sensor and Actor Network Protocols and Applications (SANPA), Boston, MA, USA, 2004. [Google Scholar]
- Tyagi, S.; Tanwar, S.; Gupta, S.K.; Kumar, N.; Rodrigues, J.J.P.C. A lifetime extended multi-levels heterogeneous routing protocol for wireless sensor networks. Telecommun. Syst. 2015, 59, 43–62. [Google Scholar] [CrossRef]
- Ahmad, A.; Javaid, N.; Khan, Z.A.; Qasim, U.; Alghamdi, T.A. (ACH)2: Routing scheme to maximize lifetime and throughput of wireless sensor networks. IEEE Sens. J. 2014, 14, 3516–3532. [Google Scholar] [CrossRef]
- Wu, D.P.; He, J.; Wang, H.G.; Wang, C.G.; Wang, R.Y. A hierarchical packet forwarding mechanism for energy harvesting wireless sensor networks. IEEE Commun. Mag. 2015, 53, 92–98. [Google Scholar] [CrossRef]
- Han, R.; Yang, W.; Wang, Y.; You, K. DCE: A distributed energy-efficient clustering protocol for wireless sensor networks based on double-phase cluster-head election. Sensors 2017, 17, 998. [Google Scholar] [CrossRef] [PubMed]
- Peyman, N.; Saeid, A.; Mahmoud, N.; Younis, O. Hierarchical clustering-task scheduling policy in cluster-based wireless sensor networks. IEEE Trans. Ind. Inform. 2018, 14, 1876–1886. [Google Scholar]
- Prince, R.; Pragya, D. Optimized and load balanced clustering for wireless sensor networks to increase the lifetime of WSN using MADM approaches. Wirel. Netw. 2018, 1–37. [Google Scholar] [CrossRef]
- Solares, J.; Sboui, L.; Rezki, Z.; Alouini, M. Power minimization of a wireless sensor node under different rate constraints. IEEE Trans. Signal Process. 2016, 64, 3458–3469. [Google Scholar] [CrossRef]
- Liao, S.B.; Zhang, Q.F. A multiutility framework with application for studying tradeoff between utility and lifetime in wireless sensor networks. IEEE Trans. Veh. Technol. 2015, 64, 4701–4711. [Google Scholar] [CrossRef]
- Yetgin, H.; Cheung, K.T.K.; Hajjar, M.E.; Hanzo, L. Cross-layer network lifetime maximization in interference-limited WSNs. IEEE Trans. Veh. Technol. 2014, 64, 3795–3803. [Google Scholar] [CrossRef]
- Kurt, S.; Yildiz, H.U.; Yigit, M.; Tavli, B.; Gungor, V.C. Packet size optimization in wireless sensor networks for smart grid applications. IEEE Trans. Ind. Electron. 2016, 64, 2392–2401. [Google Scholar] [CrossRef]
- Luo, J.; Iyer, A.; Rosenberg, C. Throughput-lifetime tradeoffs in multihop wireless networks under an SINR-based interference model. IEEE Trans. Mob. Comput. 2010, 10, 419–433. [Google Scholar] [CrossRef]
- Lee, J.H.; Moon, I. Modeling and optimization of energy efficient routing in wireless sensor networks. Appl. Math. Modeling 2014, 38, 2280–2289. [Google Scholar] [CrossRef]
- Lu, T.; Liu, G.H.; Chang, S. Energy-efficient data sensing and routing in unreliable energy-harvesting wireless sensor network. Wirel. Netw. 2018, 24, 611–625. [Google Scholar] [CrossRef]
- Fabian, C.; Andre, R.; Marc, S.; Nubia, V. An exact approach to extend network lifetime in a general class of wireless sensor networks. Inf. Sci. 2017, 433–434, 274–291. [Google Scholar] [CrossRef]
- Shalli, R.; Syed, H.A.; Rajneesh, T.; Jyoteesh, M.; Song, H.B. IoMT: A reliable cross layer protocol for Internet of multimedia Things. IEEE Internet Things J. 2017, 4, 832–839. [Google Scholar]
- Jiao, Z.Z.; Tian, R.; Zhang, B.X.; Li, C. A gradient-assisted energy-efficient backpressure scheduling algorithm for wireless sensor networks. Int. J. Distrib. Netw. 2015, 2015. [Google Scholar] [CrossRef]
- Song, Y.; Zhang, C.; Fang, Y.G. Minimum energy scheduling in multi-hop wireless networks with retransmissions. IEEE Trans. Wirel. Commun. 2010, 9, 348–355. [Google Scholar] [CrossRef]
- Liu, Z.; Yang, X.Y.; Zhao, P.; Yu, W. On energy-balanced backpressure routing mechanisms for stochastic energy harvesting wireless sensor networks. Int. J. Distrib. Sens. Netw. 2016, 12. [Google Scholar] [CrossRef]
- Xu, W.Q.; Zhang, Y.S.; Shi, Q.J.; Wang, X.D. Energy management and cross layer optimization for wireless sensor network powered by heterogeneous energy sources. IEEE Trans. Wirel. Commun. 2015, 14, 2814–2826. [Google Scholar] [CrossRef]
- Miguel, C.F.; Carles, A.H.; Javier, M.; Alejandro, R. Stochastic routing and scheduling policies for energy harvesting communication networks. IEEE Trans. Signal Process. 2018, 66, 3363–3376. [Google Scholar]
- Qiu, T.; Qiao, R.X.; Wu, Q.D.P. EABS: An event-aware backpressure scheduling scheme for emergency Internet of Things. IEEE Trans. Mob. Comput. 2018, 17, 72–84. [Google Scholar] [CrossRef]
- Georgiadis, L.; Neely, M.J.; Tasiulas, L. Resource allocation and cross-layer control in wireless networks. Found. Trends Netw. 2006, 1, 1–144. [Google Scholar] [CrossRef]
- Neely, M.J. Optimizing Time Average. In Stochastic Network Optimization with Application to Communication and Queueing Systems; Morgan & Claypool Publishers: San Rafael, CA, USA, 2010; pp. 45–48. ISBN 9781608454563. [Google Scholar]
- Jin, J.; Sridharan, A.; Krishnamachari, B.; Palaniswami, M. Handling inelastic traffic in wireless sensor networks. IEEE J. Sel. Areas Commun. 2010, 28, 1105–1115. [Google Scholar] [CrossRef]
- Julian, D.; Chiang, M.; O’Neill, D.; Boyd, S. Qos and fairness constrained convex optimization of resource allocation for wireless cellular and ad hoc networks. In Proceedings of the INFOCOM, 21th Annual Joint Conference of the IEEE Computer and Communications Societies, New York, NY, USA, 23–27 June 2002; pp. 477–486. [Google Scholar]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004; pp. 67–112. ISBN 0521833787. [Google Scholar]
- Cohen, M.; Azaiza, F. Balancing transport and physical layers in wireless ad hoc networks: Jointly optimal congestion control and power control. IEEE J. Sel. Areas Commun. 2006, 23, 104–116. [Google Scholar]
- Lin, X.J.; Shroff, N.B. The impact of imperfect scheduling on cross-layer congestion control in wireless networks. IEEE/Acm Trans. Netw. 2006, 14, 302–315. [Google Scholar]
- Fan, S.; Zhao, H.L. Delay-based cross-layer QoS scheme for video streaming in wireless ad hoc networks. China Commun. 2018, 15, 215–234. [Google Scholar] [CrossRef]
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, S. A Cross-Layer Optimization QoS Scheme in Wireless Multimedia Sensor Networks. Algorithms 2019, 12, 68. https://doi.org/10.3390/a12040068
Fan S. A Cross-Layer Optimization QoS Scheme in Wireless Multimedia Sensor Networks. Algorithms. 2019; 12(4):68. https://doi.org/10.3390/a12040068
Chicago/Turabian StyleFan, Shu. 2019. "A Cross-Layer Optimization QoS Scheme in Wireless Multimedia Sensor Networks" Algorithms 12, no. 4: 68. https://doi.org/10.3390/a12040068
APA StyleFan, S. (2019). A Cross-Layer Optimization QoS Scheme in Wireless Multimedia Sensor Networks. Algorithms, 12(4), 68. https://doi.org/10.3390/a12040068



