Recommending Links to Control Elections via Social Influence
Abstract
1. Introduction
Original Contribution
2. Related Work
3. Preliminaries
The Influence Maximization Problem
4. Problem Statement
5. Approximation Result
6. Improving the Running Time
| Algorithm 1:Greedy |
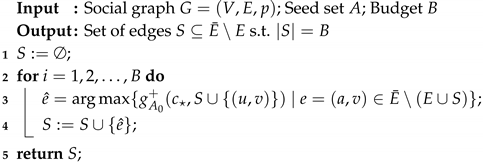 |
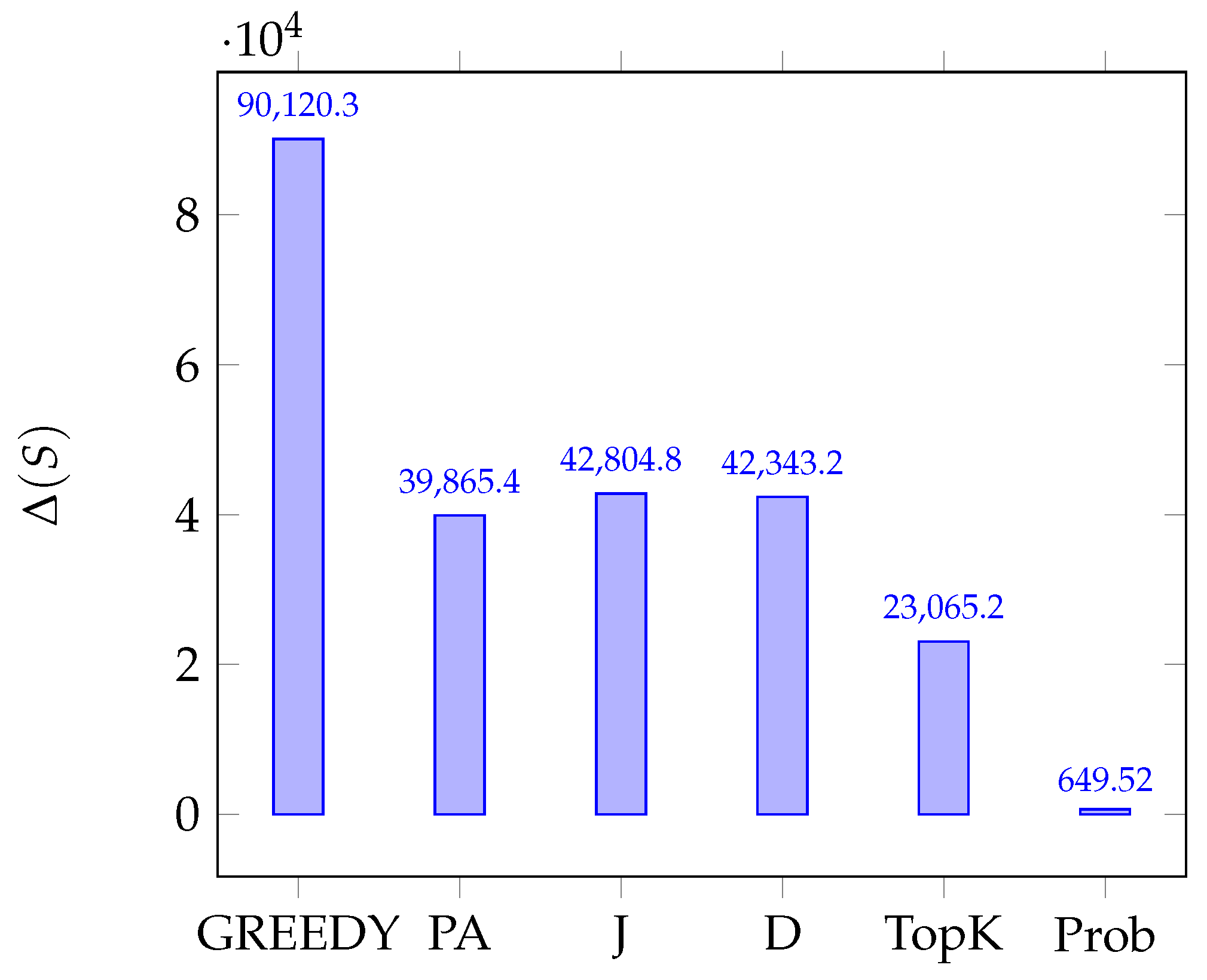
7. Experimental Study
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bond, R.M.; Fariss, C.J.; Jones, J.J.; Kramer, A.D.I.; Marlow, C.; Settle, J.E.; Fowler, J.H. A 61-million-person experiment in social influence and political mobilization. Nature 2012, 489, 295. [Google Scholar] [CrossRef] [PubMed]
- Ferrara, E. Disinformation and social bot operations in the run up to the 2017 French presidential election. First Monday 2017, 22. [Google Scholar] [CrossRef]
- Kreiss, D. Seizing the moment: The presidential campaigns’ use of Twitter during the 2012 electoral cycle. New Media Soc. 2016, 18, 1473–1490. [Google Scholar] [CrossRef]
- Stier, S.; Bleier, A.; Lietz, H.; Strohmaier, M. Election Campaigning on Social Media: Politicians, Audiences, and the Mediation of Political Communication on Facebook and Twitter. Political Commun. 2018, 35, 50–74. [Google Scholar] [CrossRef]
- Allcott, H.; Gentzkow, M. Social Media and Fake News in the 2016 Election; Working Paper 23089; National Bureau of Economic Research: Cambridge, MA, USA, 2017. [Google Scholar] [CrossRef]
- Faliszewski, P.; Rothe, J.; Moulin, H. Control and Bribery in Voting. In Handbook of Computational Social Choice; Cambridge University Press: Cambridge, UK, 2016; pp. 146–168. [Google Scholar] [CrossRef]
- Wilder, B.; Vorobeychik, Y. Controlling Elections through Social Influence. In Proceedings of the AAMAS 2018 17th International Conference on Autonomous Agents and MultiAgent Systems, Stockholm, Sweden, 10–15 July 2018; pp. 265–273. [Google Scholar]
- Kempe, D.; Kleinberg, J.M.; Tardos, É. Maximizing the Spread of Influence through a Social Network. Theory Comput. 2015, 11, 105–147. [Google Scholar] [CrossRef]
- Corò, F.; Cruciani, E.; D’Angelo, G.; Ponziani, S. Vote For Me!: Election Control via Social Influence in Arbitrary Scoring Rule Voting Systems. In Proceedings of the 18th International Conference on Autonomous Agents and MultiAgent Systems AAMAS ’19, Montrea, QC, Canada, 13–17 May 2019; pp. 1895–1897. [Google Scholar]
- Corò, F.; Cruciani, E.; D’Angelo, G.; Ponziani, S. Exploiting Social Influence to Control Elections Based on Scoring Rules. In Proceedings of the Twenty-Eighth International Joint Conference on Artificial Intelligence, IJCAI, Macao, China, 10–16 August 2019; pp. 201–207. [Google Scholar] [CrossRef]
- Faliszewski, P.; Gonen, R.; Koutecký, M.; Talmon, N. Opinion Diffusion and Campaigning on Society Graphs. In Proceedings of the Twenty-Seventh International Joint Conference on Artificial Intelligence, IJCAI-18. International Joint Conferences on Artificial Intelligence Organization, Stockholm, Germany, 13–19 July 2018; pp. 219–225. [Google Scholar] [CrossRef]
- Bredereck, R.; Elkind, E. Manipulating Opinion Diffusion in Social Networks. In Proceedings of the 26th International Joint Conference on Artificial Intelligence, Melbourne, Australia, 19–25 August 2017; pp. 894–900. [Google Scholar]
- D’Angelo, G.; Severini, L.; Velaj, Y. Recommending links through influence maximization. Theor. Comput. Sci. 2019, 764, 30–41. [Google Scholar] [CrossRef]
- D’Angelo, G.; Severini, L.; Velaj, Y. Selecting Nodes and Buying Links to Maximize the Information Diffusion in a Network. In Proceedings of the 42nd International Symposium on Mathematical Foundations of Computer Science, Aalborg, Denmark, 21–25 August 2017; pp. 75:1–75:14. [Google Scholar] [CrossRef]
- Sheldon, D.; Dilkina, B.; Elmachtoub, A.N.; Finseth, R.; Sabharwal, A.; Conrad, J.; Gomes, C.; Shmoys, D.; Allen, W.; Amundsen, O.; et al. Maximizing the spread of cascades using network design. In Proceedings of the Twenty-Sixth Conference on Uncertainty in Artificial Intelligence, Catalina Island, CA, USA, 8–11 July 2010. [Google Scholar]
- Amelkin, V.; Singh, A.K. Fighting Opinion Control in Social Networks via Link Recommendation. In Proceedings of the 25th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, Anchorage, AK, USA, 4–8 August 2019. [Google Scholar]
- Zhang, Y.; Adiga, A.; Vullikanti, A.; Prakash, B.A. Controlling propagation at group scale on networks. In Proceedings of the 2015 IEEE International Conference on Data Mining (ICDM), Atlantic City, NJ, USA, 14–17 November 2015. [Google Scholar]
- Crescenzi, P.; D’angelo, G.; Severini, L.; Velaj, Y. Greedily improving our own closeness centrality in a network. ACM Trans. Knowl. Discov. Data 2016, 11, 9. [Google Scholar] [CrossRef]
- Parotsidis, N.; Pitoura, E.; Tsaparas, P. Centrality-aware link recommendations. In Proceedings of the Ninth ACM International Conference on Web Search and Data Mining, San Francisco, CA, USA, 22–25 February 2016. [Google Scholar]
- Papagelis, M. Refining social graph connectivity via shortcut edge addition. ACM Trans. Knowl. Discov. Data 2015, 10, 12. [Google Scholar] [CrossRef]
- Kempe, D.; Kleinberg, J.M.; Tardos, É. Maximizing the spread of influence through a social network. In Proceedings of the Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–27 August 2003; pp. 137–146. [Google Scholar] [CrossRef]
- Chen, W.; Wang, C.; Wang, Y. Scalable influence maximization for prevalent viral marketing in large-scale social networks. In Proceedings of the 16th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 25–28 July 2010; pp. 1029–1038. [Google Scholar] [CrossRef]
- Nemhauser, G.L.; Wolsey, L.A.; Fisher, M.L. An analysis of approximations for maximizing submodular set functions-I. Math. Program. 1978, 14, 265–294. [Google Scholar] [CrossRef]
- Aboueimehrizi, M.; Corò, F.; Cruciani, E.; D’Angelo, G. Election Control with Voters’ Uncertainty: Hardness and Approximation Results. arXiv 2019, arXiv:1905.04694. [Google Scholar]
- Corò, F.; D’Angelo, G.; Velaj, Y. Recommending Links to Maximize the Influence in Social Networks. In Proceedings of the Twenty-Eighth International Joint Conference on Artificial Intelligence, IJCAI, Macao, China, 10–16 August 2019; pp. 2195–2201. [Google Scholar] [CrossRef]
- Cohen, E.; Delling, D.; Pajor, T.; Werneck, R.F. Sketch-based Influence Maximization and Computation: Scaling Up with Guarantees. In Proceedings of the 23rd ACM International Conference on Conference on Information and Knowledge Management, Shanghai, China, 3–7 November 2014. [Google Scholar]
- Kunegis, J. KONECT-The Koblenz Network Collection. In Proceedings of the International World Wide Web Conferen, Rio de Janeiro, Brazi, 13–17 May 2013. [Google Scholar]
- Arnetminer. Available online: http://arnetminer.org (accessed on 15 January 2015).
- Leskovec, J.; Krevl, A. SNAP Datasets: Stanford Large Network Dataset Collection. 2014. Available online: http://snap.stanford.edu/data (accessed on 28 September 2019).
- Bollobás, B.; Borgs, C.; Chayes, J.; Riordan, O. Directed scale-free graphs. In Proceedings of the Fourteenth Annual ACM-SIAM Symposium on Discrete Algorithms, Baltimore, MD, USA, 12–14 January 2003. [Google Scholar]
- Newman, M.E. Clustering and preferential attachment in growing networks. Phys. Rev. E 2001, 64, 025102. [Google Scholar] [CrossRef] [PubMed]
- Jaccard, P. Étude comparative de la distribution florale dans une portion des Alpes et des Jura. Bull. Soc. Vaudoise Sci. Nat. 1901, 37, 547–579. [Google Scholar]
- Boldi, P.; Vigna, S. Axioms for centrality. Internet Math. 2014, 10, 222–262. [Google Scholar] [CrossRef]
| Name | ||
|---|---|---|
| Software Engineering (SE) | 3141 | 14,787 |
| Theoretical CS (TCS) | 4172 | 14,272 |
| High-Performance Comp. (HPC) | 4869 | 35,036 |
| Wiki-Vote (Wiki) | 7115 | 103,689 |
| Computer Graphic (CGM) | 8336 | 41,925 |
| Computer Networks (CN) | 9420 | 53,003 |
| Artificial Intelligence (AI) | 27,617 | 268,460 |
| Slashdot (Sl) | 51,083 | 130,370 |
| Epinions (Epi) | 75,879 | 508,837 |
| Slashdot-Zoo (Sl-z) | 79,116 | 515,397 |
| 465,017 | 834,797 |
| SE | 6.65 | 330.88 | 4878.01% | 0.70 | 23.03 | 106.79 | 363.76% | 0.83 | −26.31 | 13.02 | 149.48% | 1.12 |
| TCS | −57.61 | 305.47 | 630.22% | 0.95 | −15.87 | 74.41 | 568.99% | 1.13 | −22.23 | 34.05 | 253.16% | 1.44 |
| HPC | −32.31 | 470.10 | 1554.99% | 1.16 | −33.41 | 96.28 | 388.15% | 1.26 | −14.80 | 37.35 | 352.35% | 1.87 |
| Wiki | −32.39 | 680.64 | 2201.34% | 3.68 | −28.80 | 140.87 | 589.14% | 4.03 | −27.41 | 49.01 | 278.80% | 5.80 |
| CN | −38.08 | 1144.90 | 3106.47% | 3.15 | −57.77 | 243.39 | 521.32% | 3.61 | 12.83 | 122.41 | 854.42% | 5.04 |
| CGM | −0.54 | 846.73 | 157 × % | 2.43 | −52.16 | 157.97 | 402.87% | 2.57 | −10.08 | 92.88 | 1021.20% | 4.02 |
| AI | 221.07 | 3394.04 | 1435.27% | 14.03 | 7.24 | 816.50 | 11,179.65% | 14.62 | 10.78 | 362.16 | 3259.92% | 21.22 |
| Sl | 150.59 | 2958.49 | 1864.54% | 41.33 | −16.43 | 750.20 | 4664.81% | 48.02 | 54.87 | 493.46 | 799.25% | 57.78 |
| Sl-z | 523.65 | 11,613.94 | 2117.86% | 70.36 | 130.74 | 2941.96 | 2150.17% | 81.61 | 12.48 | 1115.27 | 8837.80% | 118.94 |
| Epi | 365.45 | 5700.39 | 1459.81% | 80.61 | 47.68 | 1465.61 | 2974.00% | 98.97 | 16.76 | 691.97 | 4027.51% | 123.17 |
| 1665.35 | 363 × | 109 × % | 717.66 | −238.7 | 90 × | 190 × % | 790.26 | 166.5 | 37,739 | 113 × % | 746.86 | |
| G | Greedy | Pref. Attachment | Jaccard | ||||||
|---|---|---|---|---|---|---|---|---|---|
| 2 | 5 | 10 | 2 | 5 | 10 | 2 | 5 | 10 | |
| SE | 4878.01 | 363.76 | 149.48 | 895.00 | 62.25 | 25.25 | 757.50 | 42.97 | 24.79 |
| TCS | 630.22 | 568.99 | 253.16 | 154.79 | 136.00 | 51.79 | 110.12 | 90.67 | 23.43 |
| HPC | 1554.99 | 388.15 | 352.35 | 47.22 | 10.22 | 14.33 | 174.83 | 42.98 | 40.19 |
| Wiki | 2201.34 | 589.14 | 278.80 | 959.02 | 266.30 | 125.44 | 240.12 | 67.07 | 38.78 |
| CN | 3106.47 | 521.32 | 854.42 | 565.63 | 92.67 | 181.23 | 249.39 | 37.84 | 84.84 |
| CGM | 157 × | 402.87 | 1021.20 | 18 × | 48.84 | 107.16 | 21 × | 58.00 | 115.80 |
| AI | 1435.27 | 12 × | 3259.92 | 58.13 | 468.75 | 135.80 | 95.40 | 715.93 | 228.99 |
| Sl | 1864.54 | 4664.81 | 799.25 | 302.27 | 680.22 | 91.69 | 292.41 | 673.30 | 87.54 |
| Sl-z | 2117.86 | 2150.17 | 8837.80 | 758.46 | 760.91 | 3495.03 | 159.30 | 172.30 | 776.79 |
| Epi | 1459.81 | 2974.00 | 4027.51 | 371.26 | 707.52 | 905.31 | 222.93 | 447.97 | 541.20 |
| 109 × | 190 × | 113 × | 10,423.88 | 16,858.20 | 11,472.56 | 9824.01 | 18,093.83 | 12,013.41 | |
| G | Degree | TopK | Prob | ||||||
|---|---|---|---|---|---|---|---|---|---|
| 2 | 5 | 10 | 2 | 5 | 10 | 2 | 5 | 10 | |
| SE | 1005.18 | 69.08 | 27.94 | 1852.49 | 135.54 | 54.45 | 1408.16 | 110.77 | 44.69 |
| TCS | 171.96 | 155.64 | 57.31 | 150.14 | 144.49 | 48.14 | 257.26 | 196.71 | 67.87 |
| HPC | 49.80 | 10.48 | 14.92 | 232.46 | 57.06 | 46.01 | 402.95 | 91.87 | 92.15 |
| Wiki | 1322.04 | 359.21 | 173.85 | 1336.46 | 370.66 | 180.50 | 304.50 | 65.13 | 36.57 |
| CN | 1058.30 | 165.02 | 349.46 | 1082.34 | 187.46 | 351.23 | 661.83 | 108.42 | 163.51 |
| CGM | 27 × | 73.03 | 158.09 | 18 × | 47.00 | 119.36 | 44 × | 118.67 | 280.47 |
| AI | 84.67 | 677.83 | 197.02 | 264.10 | 2067.03 | 625.05 | 349.74 | 2612.15 | 795.94 |
| Sl | 306.53 | 697.86 | 93.54 | 336.11 | 757.73 | 102.47 | 569.15 | 1266.83 | 169.13 |
| Sl-z | 778.30 | 778.93 | 3587.66 | 585.11 | 643.20 | 2946.73 | 366.46 | 365.02 | 1770.74 |
| Epi | 255.76 | 488.91 | 625.85 | 275.55 | 525.05 | 673.50 | 372.59 | 713.16 | 887.83 |
| 8609.83 | 17,899.79 | 11,862.66 | 8497.19 | 9795.90 | 7198.48 | 208.64 | −373.04 | 247.40 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Corò, F.; D’Angelo, G.; Velaj, Y. Recommending Links to Control Elections via Social Influence. Algorithms 2019, 12, 207. https://doi.org/10.3390/a12100207
Corò F, D’Angelo G, Velaj Y. Recommending Links to Control Elections via Social Influence. Algorithms. 2019; 12(10):207. https://doi.org/10.3390/a12100207
Chicago/Turabian StyleCorò, Federico, Gianlorenzo D’Angelo, and Yllka Velaj. 2019. "Recommending Links to Control Elections via Social Influence" Algorithms 12, no. 10: 207. https://doi.org/10.3390/a12100207
APA StyleCorò, F., D’Angelo, G., & Velaj, Y. (2019). Recommending Links to Control Elections via Social Influence. Algorithms, 12(10), 207. https://doi.org/10.3390/a12100207






