Research and Prospect of Defense for Integrated Energy Cyber–Physical Systems Against Deliberate Attacks
Abstract
1. Introduction
2. Methodology
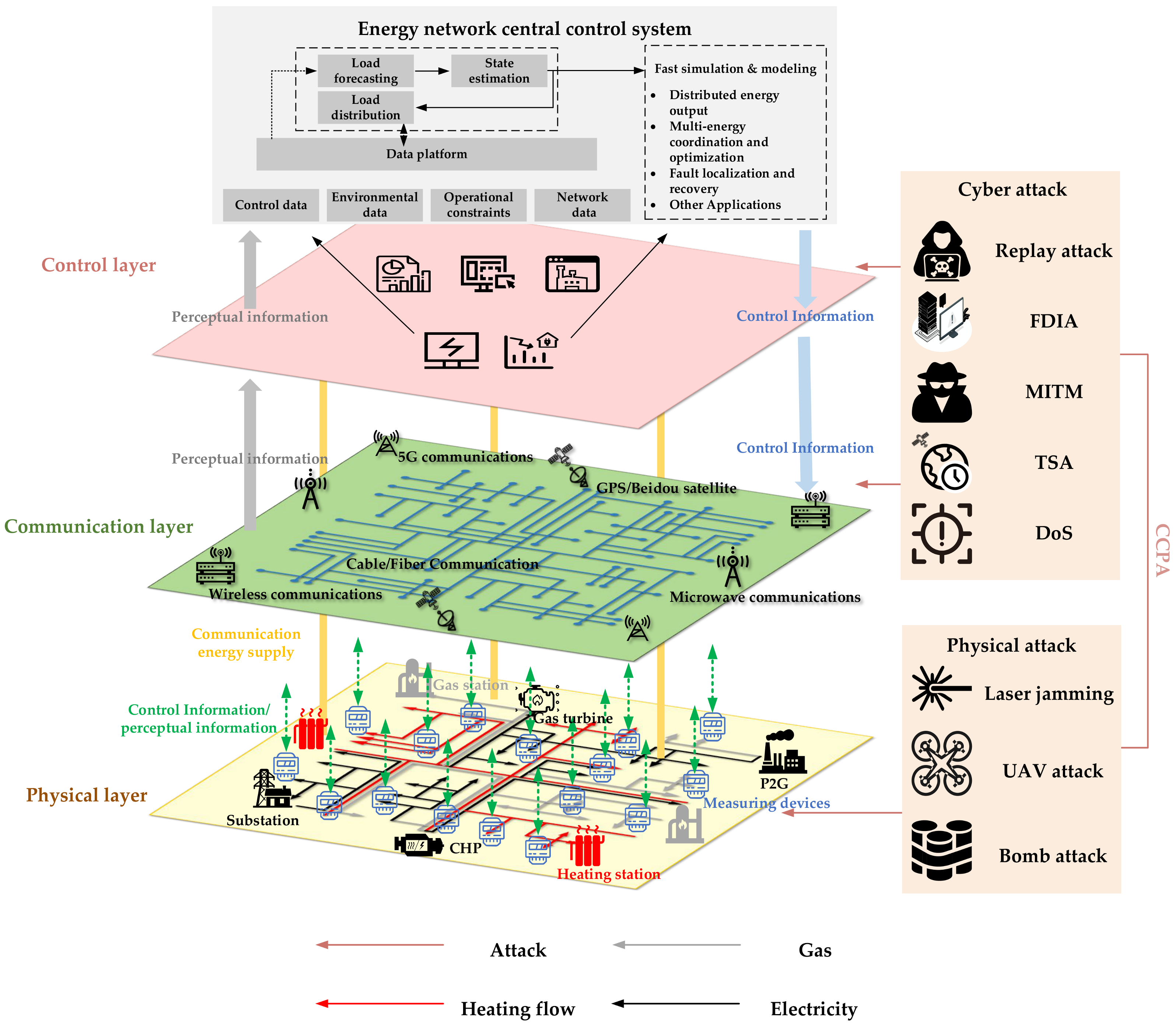
3. Deliberate Attacks on IECPS
3.1. Cyberattacks
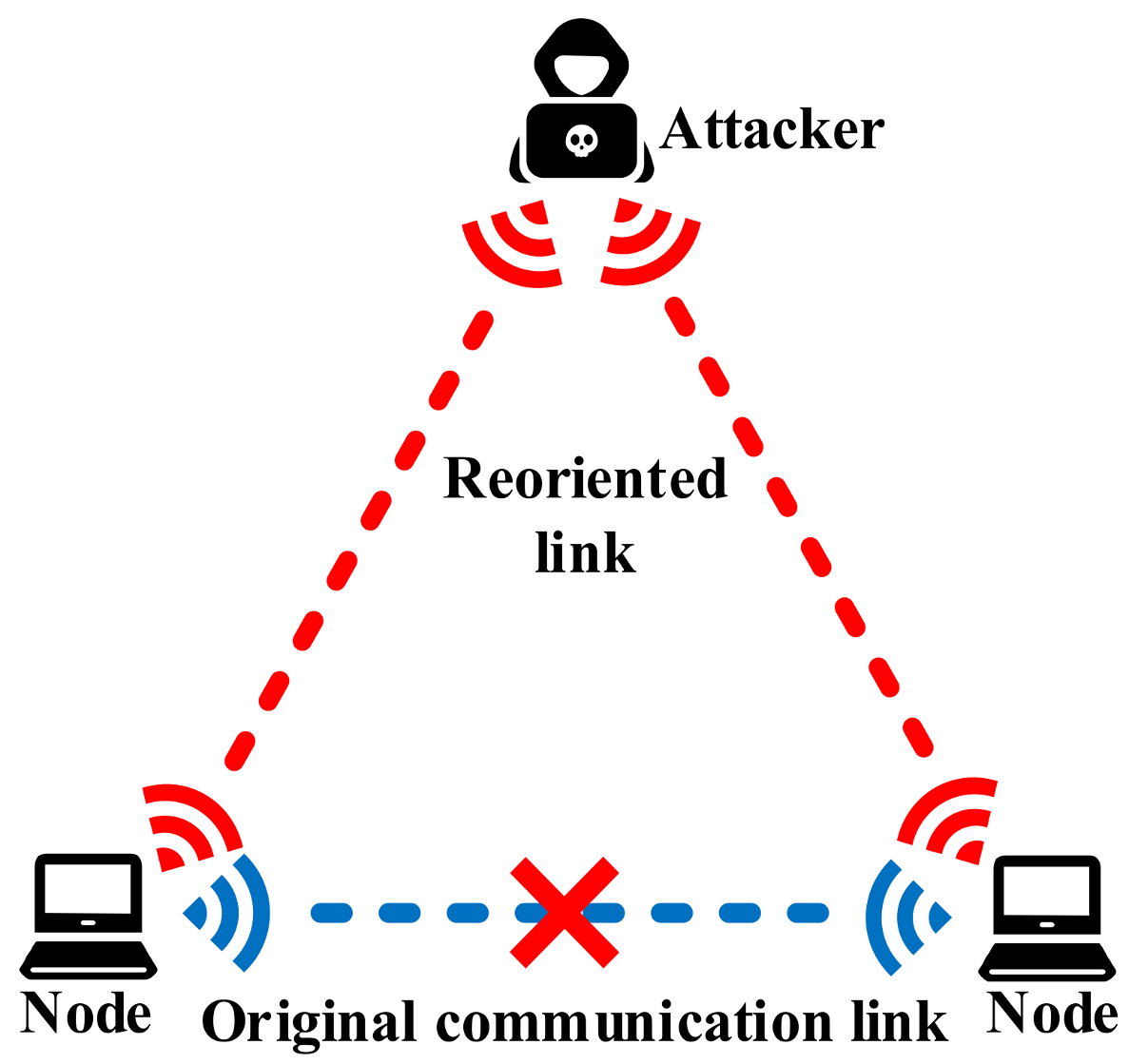
3.1.1. Replay Attacks
3.1.2. Man-in-the-Middle Attacks
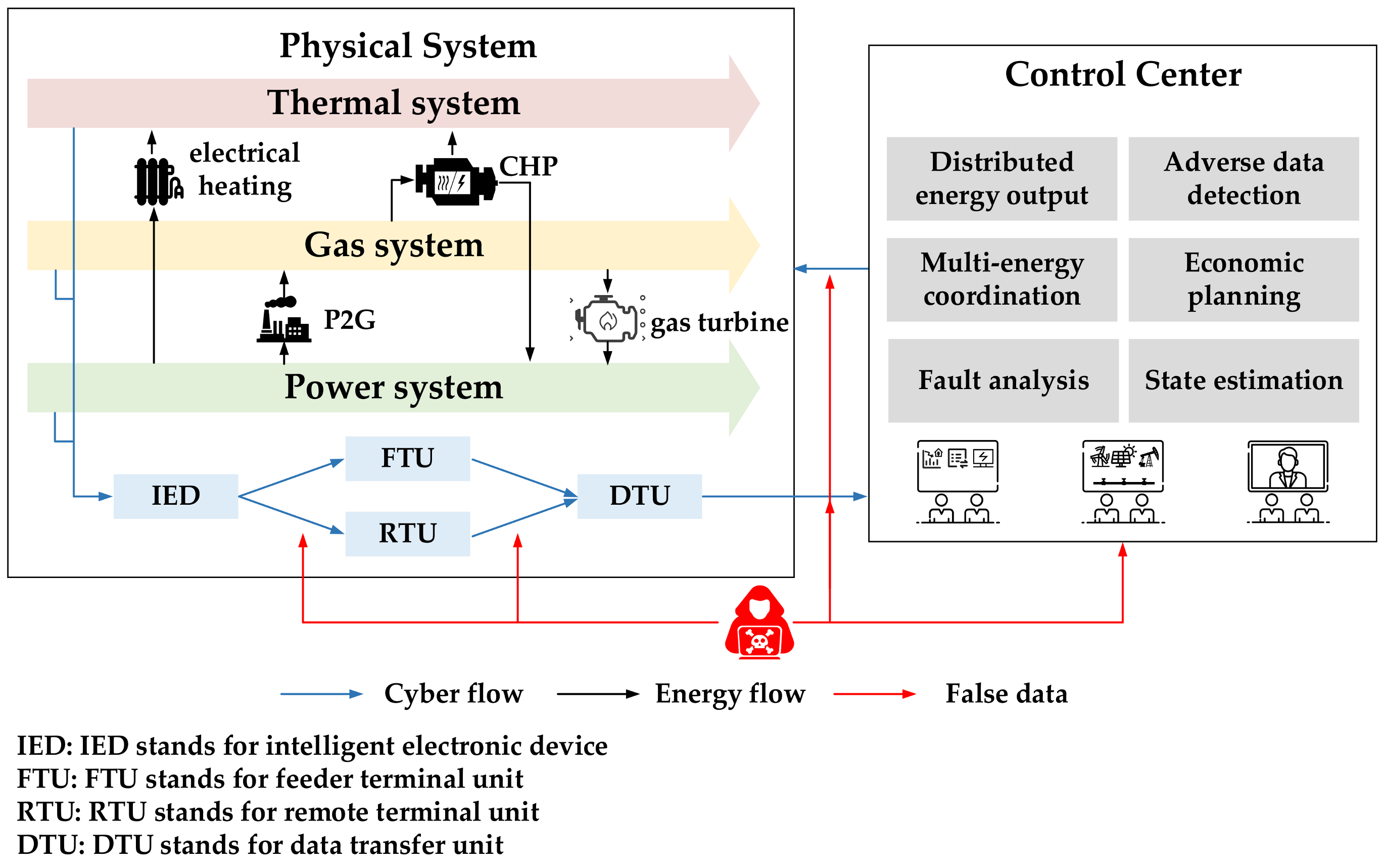
3.1.3. False Data Injection Attacks
- General FDIA model
- Load redistribution attackmodel
- False topology attackmodel
- (1)
- The topology tampering part involves an attacker trying to fake the disconnection of a transformer branch by tampering with the transformer protection action information, thereby disconnecting the circuit breakers at both ends:where and , respectively, indicate the protection action state of the transformer branch before and after the attack; and , respectively, indicate the state of the front–end circuit breaker of the transformer before and after the attack, with a value of 0 indicating that the circuit breaker is closed and a value of 1 indicating that the circuit breaker is open; and , respectively, indicate the state of the back–end circuit breaker of the transformer before and after the attack, with a value of 0 indicating that the circuit breaker is closed and a value of 1 indicating that the circuit breaker is open.
- (2)
- In the power tampering part, the attack vectors need to be designed to ensure the data matching, i.e., the attack vectors need to be made to ensure that the power remains balanced before and after the attack:where is the false data of injected branch volume measurement; is the transfer factor matrix of the lines before and after the attack; is the node–load correlation matrix of the lines before and after the attack; is the node power measurement matrix of the lines before and after the attack; is the set of lines to be attacked; and is the set of system lines.
3.1.4. Time Synchronization Attacks
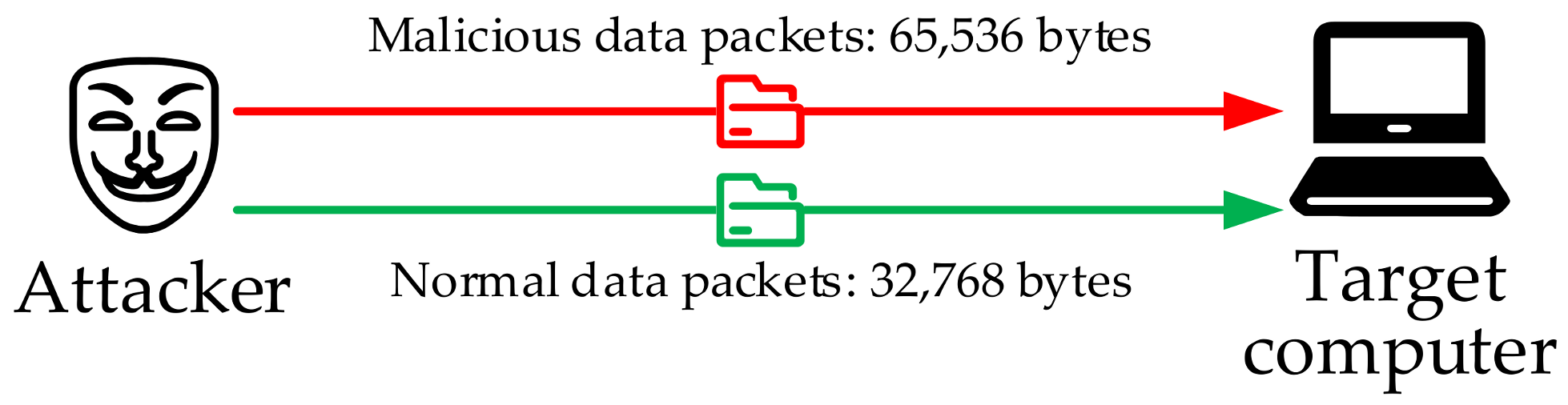
3.1.5. DoS Attacks
3.1.6. Coordinated Cyberattacks
3.2. Physical Attacks
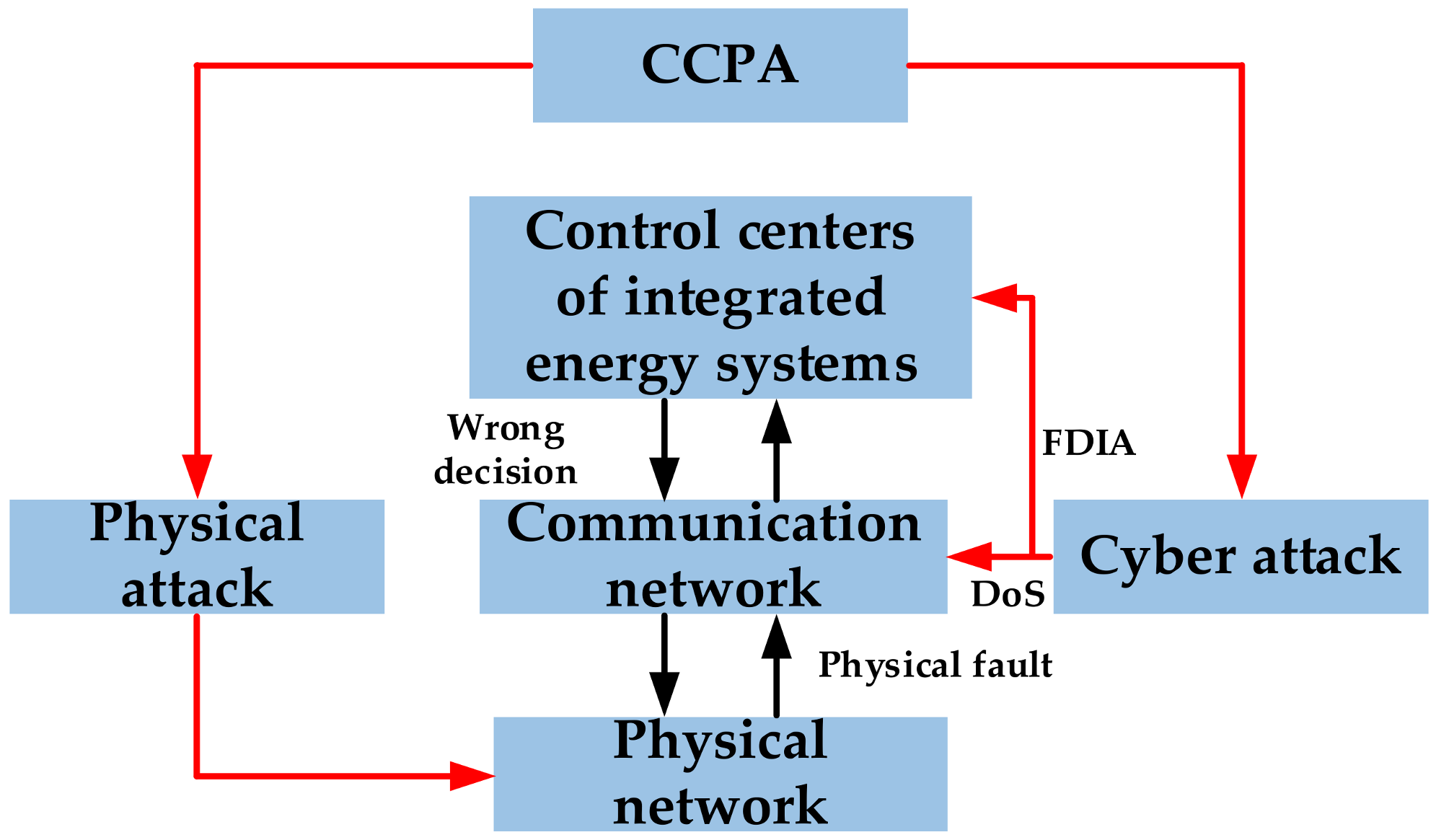
3.3. Coordinated Cyber–Physical Attacks
3.3.1. A Coordinated Strategy for Prioritizing Physical Attacks
3.3.2. A Coordinated Strategy for Prioritizing Cyberattacks
4. Defense Strategies Against Deliberate Attacks on IECPS
4.1. Preemptive Prevention
4.1.1. Redundant Equipment Planning
4.1.2. Cross-System Coupling Planning
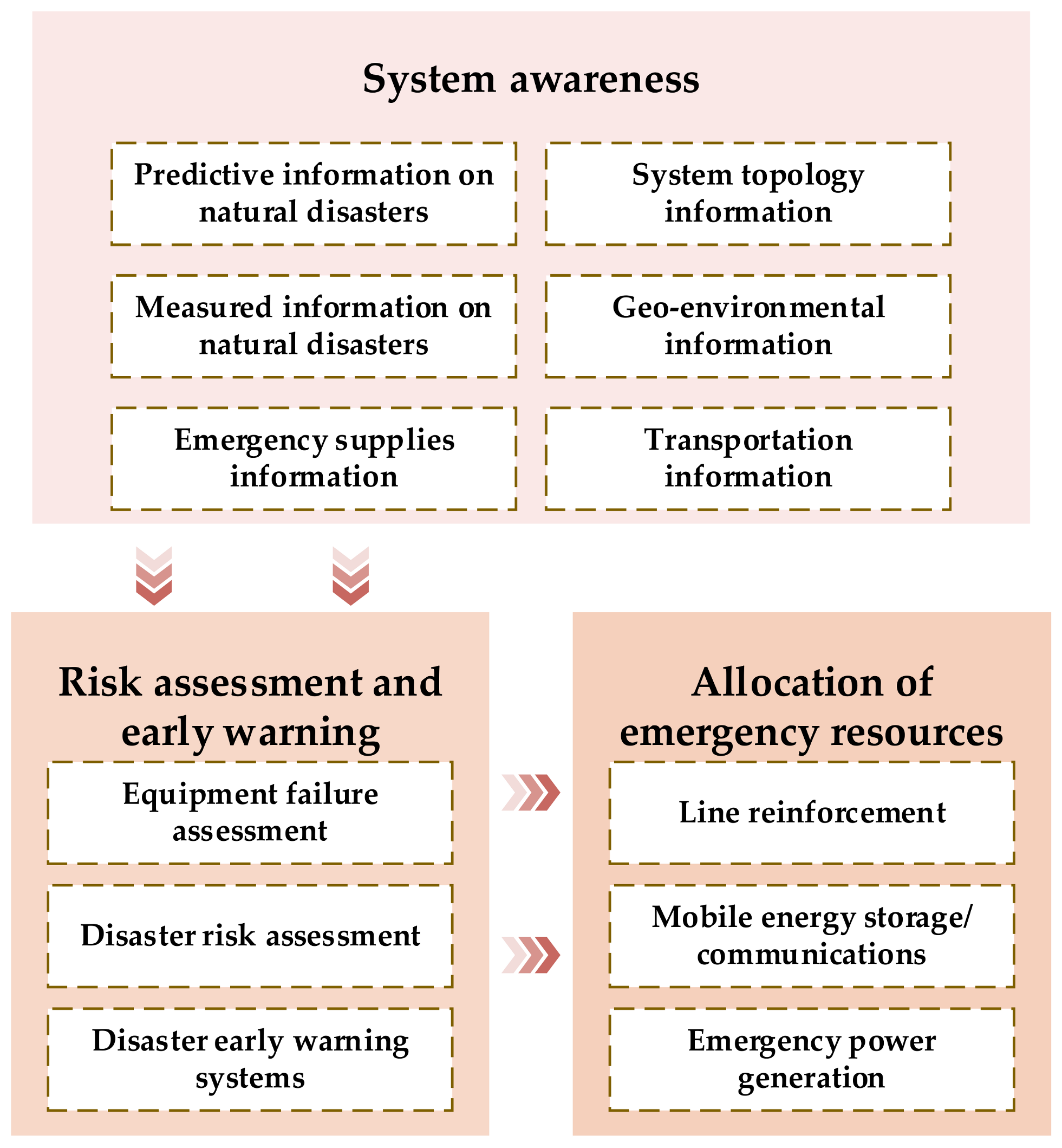
4.1.3. Emergency Defense Resource Planning
4.2. Process Response
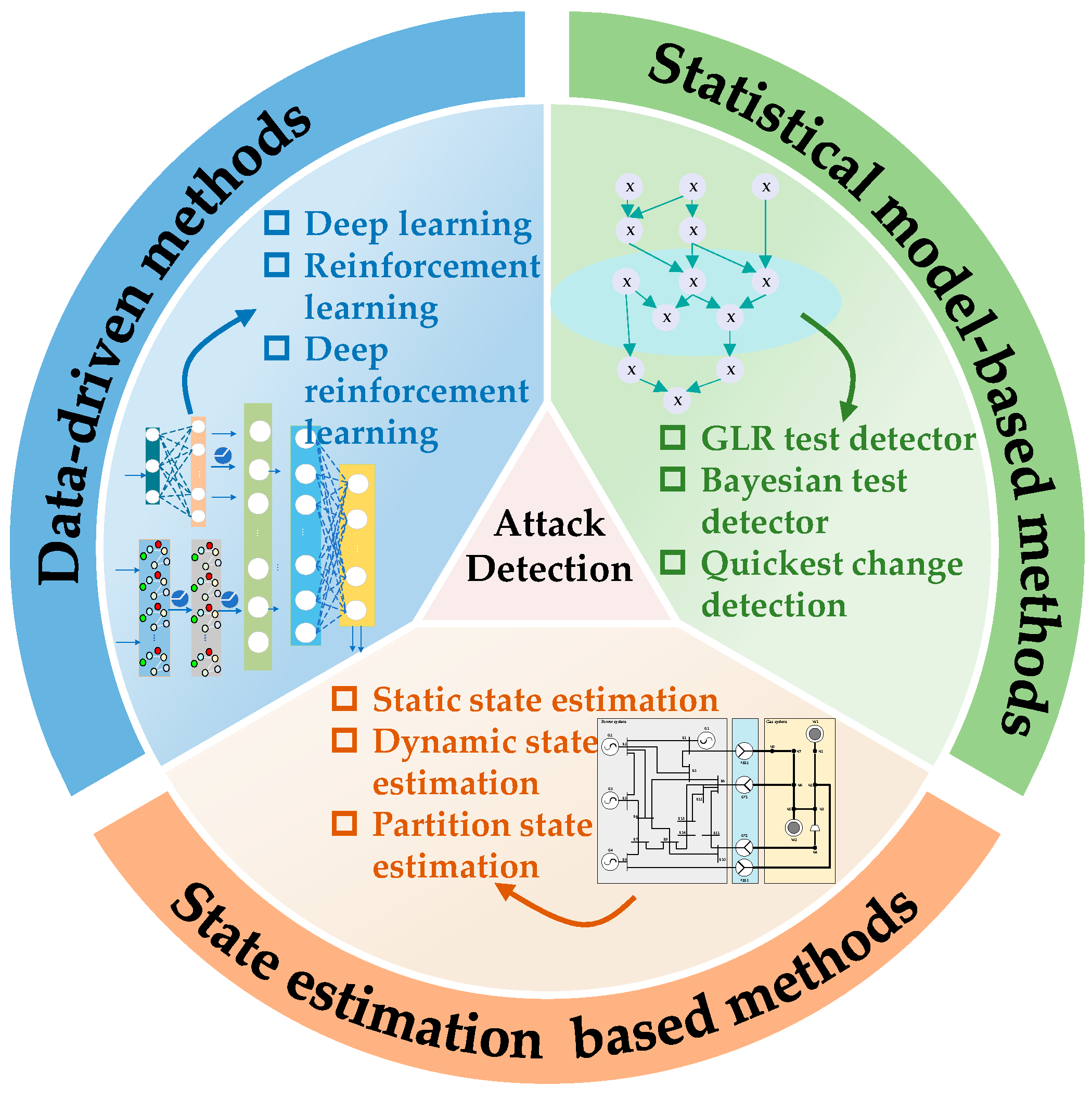
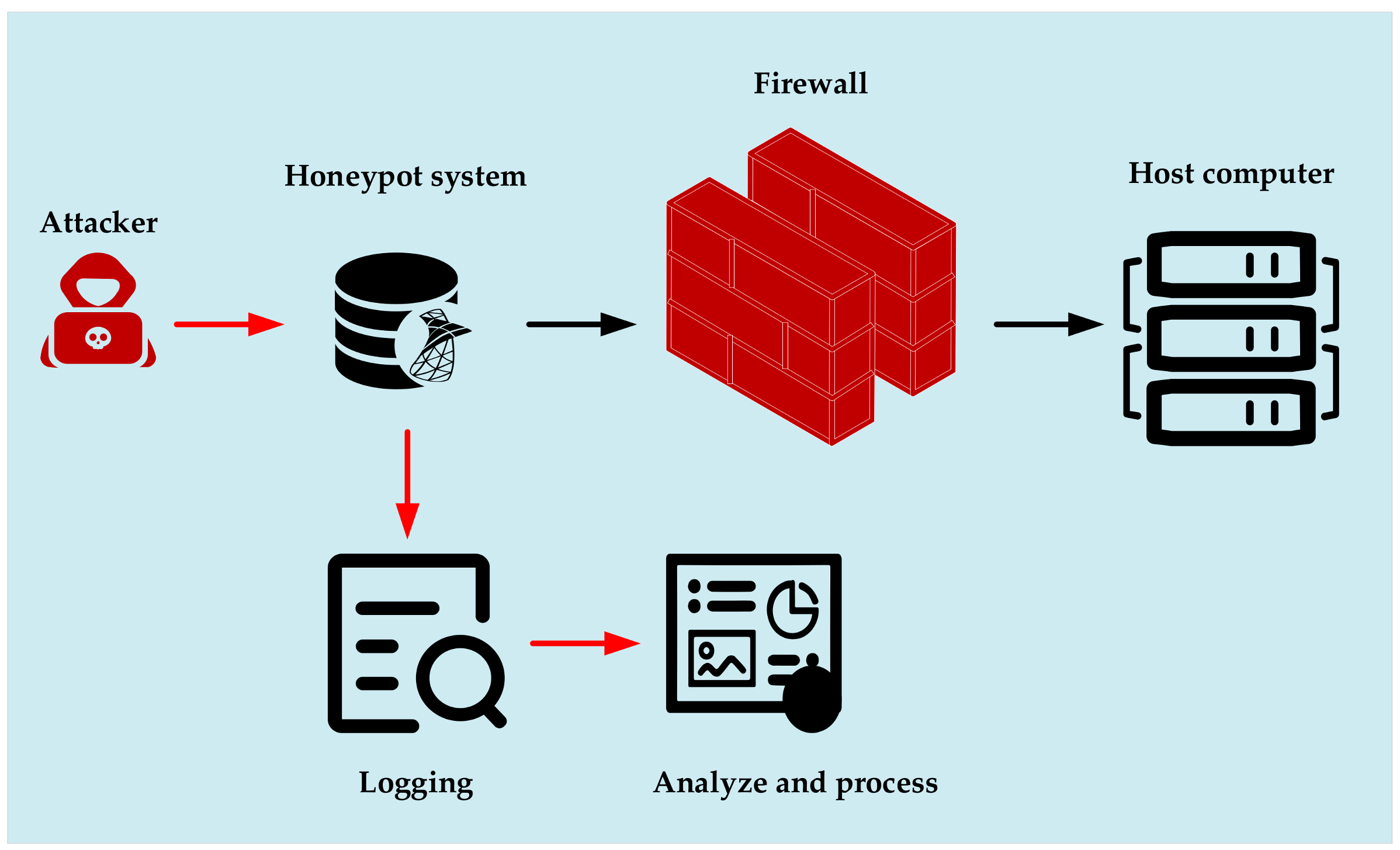
4.2.1. Deliberate Attack Detection
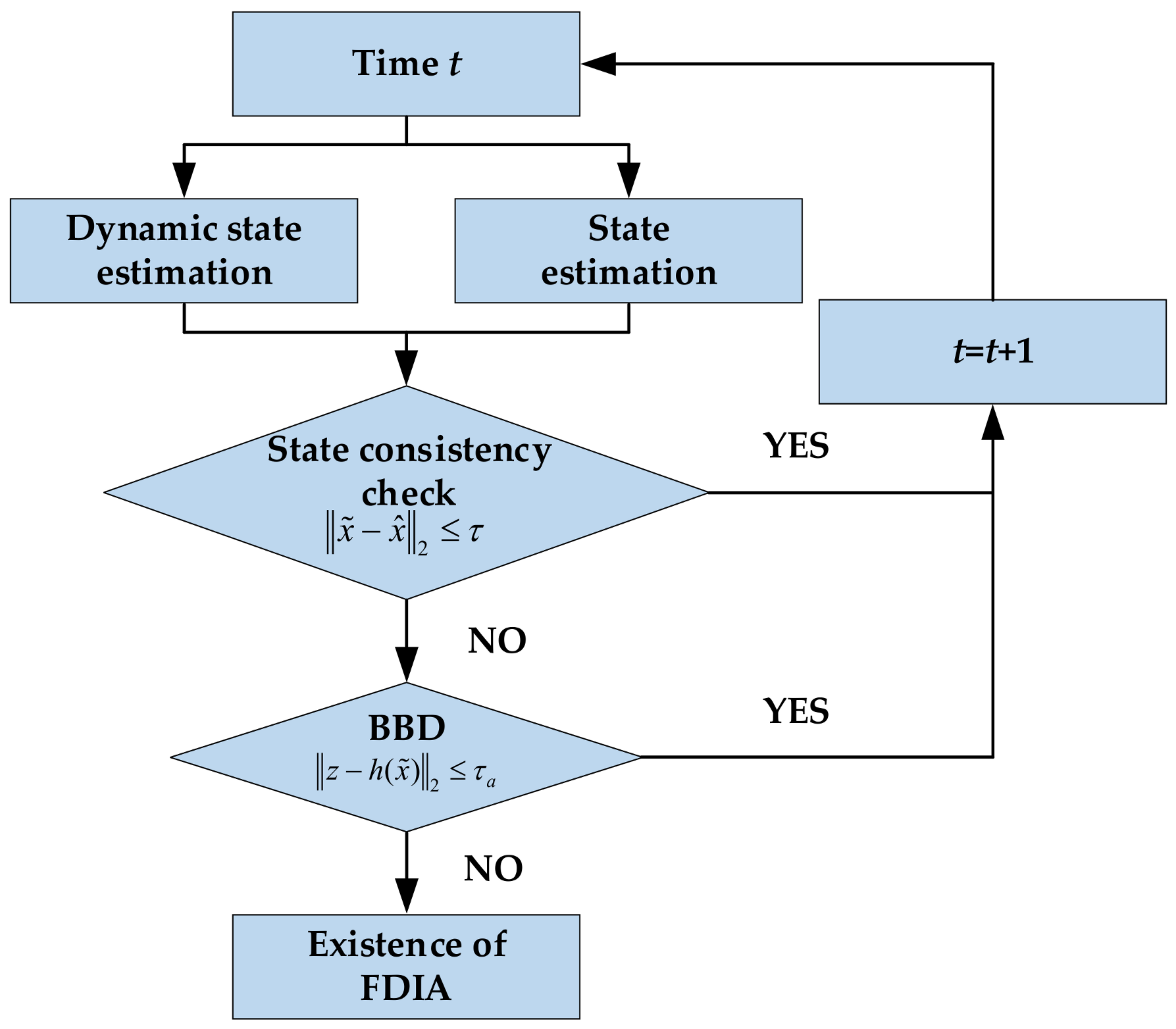
- State estimation-based detection methods
- Statistical model-based detection methods
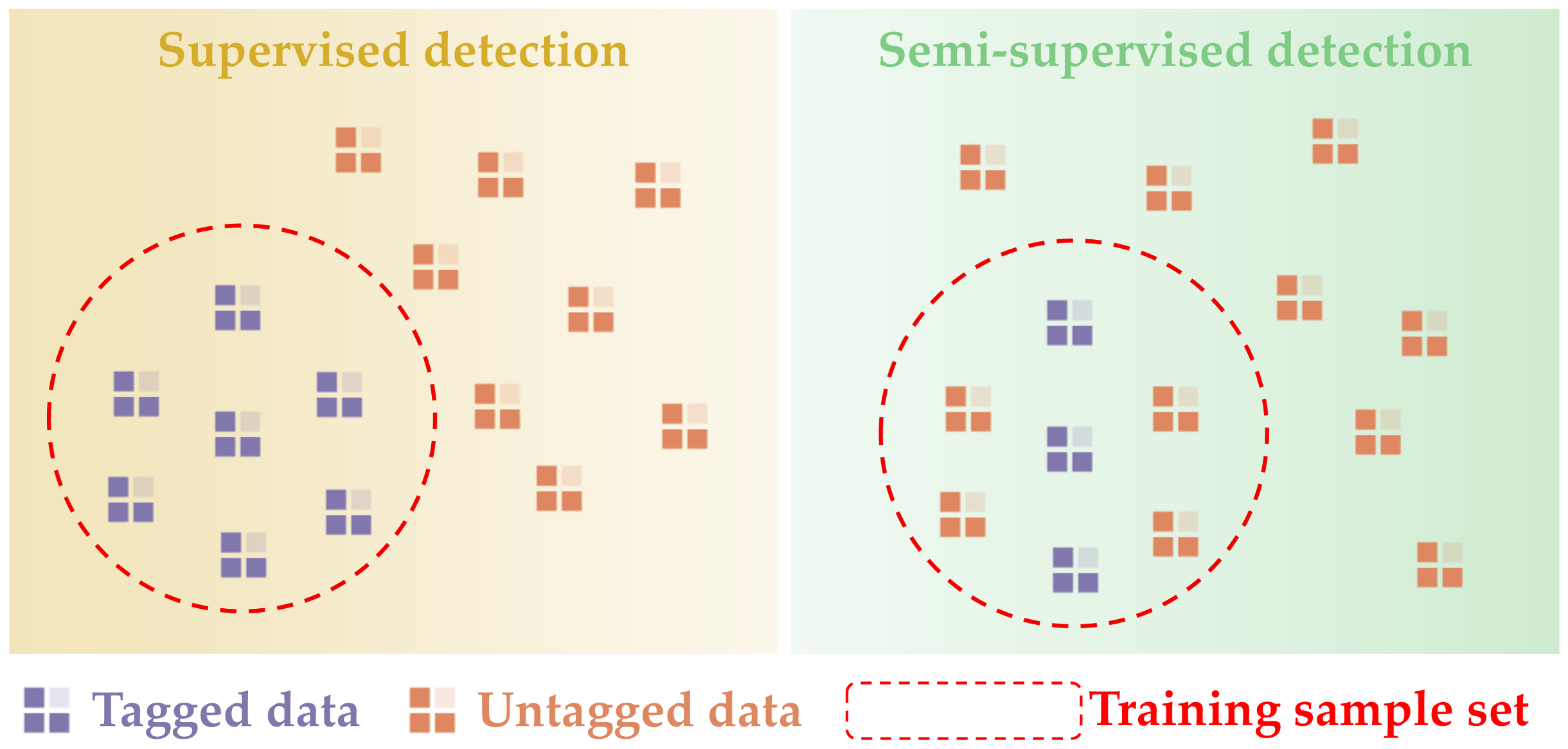
- Data-driven detection methods
4.2.2. System Fault Isolation
4.2.3. Multi-Source Coordinated Dispatch
4.3. Post–Event Recovery and Summarizing
4.3.1. Incident Assessment and Reconstruction
4.3.2. Attack Traceability and Analysis
4.3.3. Defense Evaluation and Enhancement
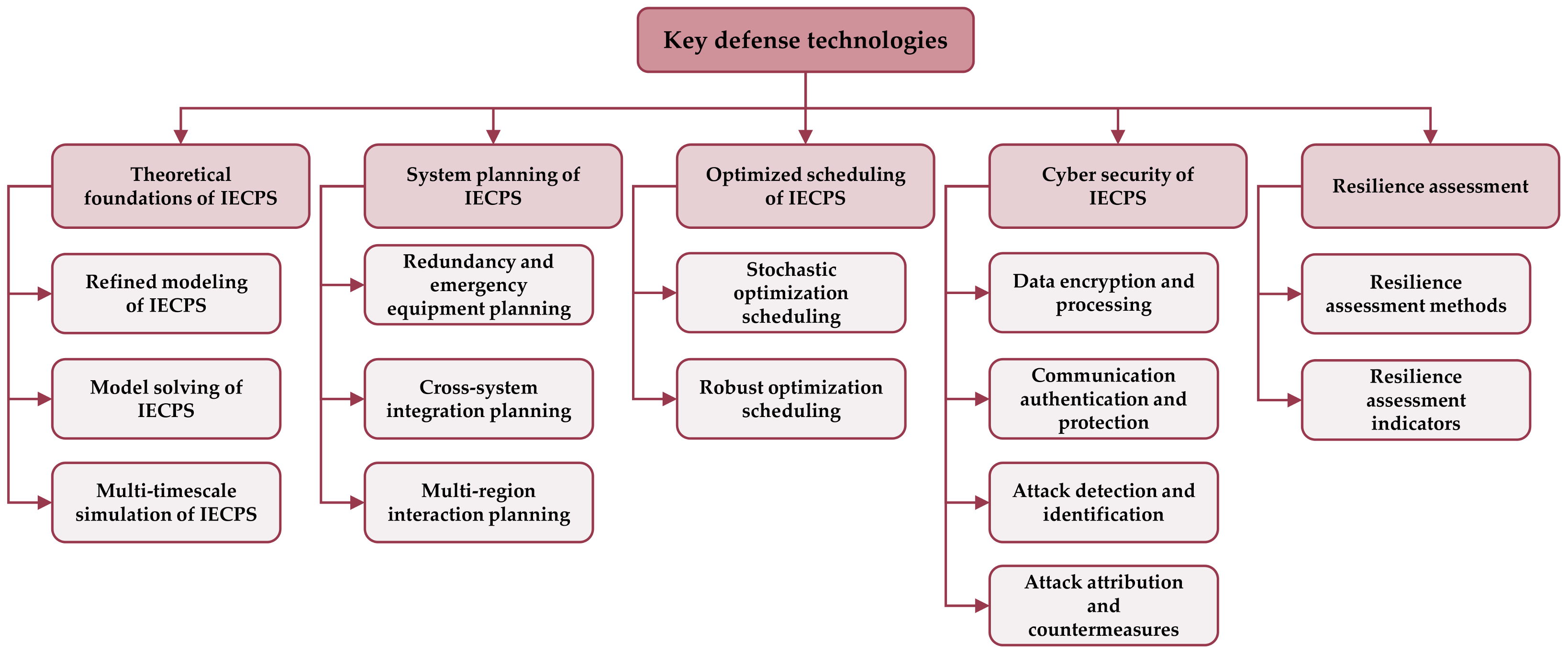
5. Key Technologies Supporting Deliberate Attack Defense for IECPS
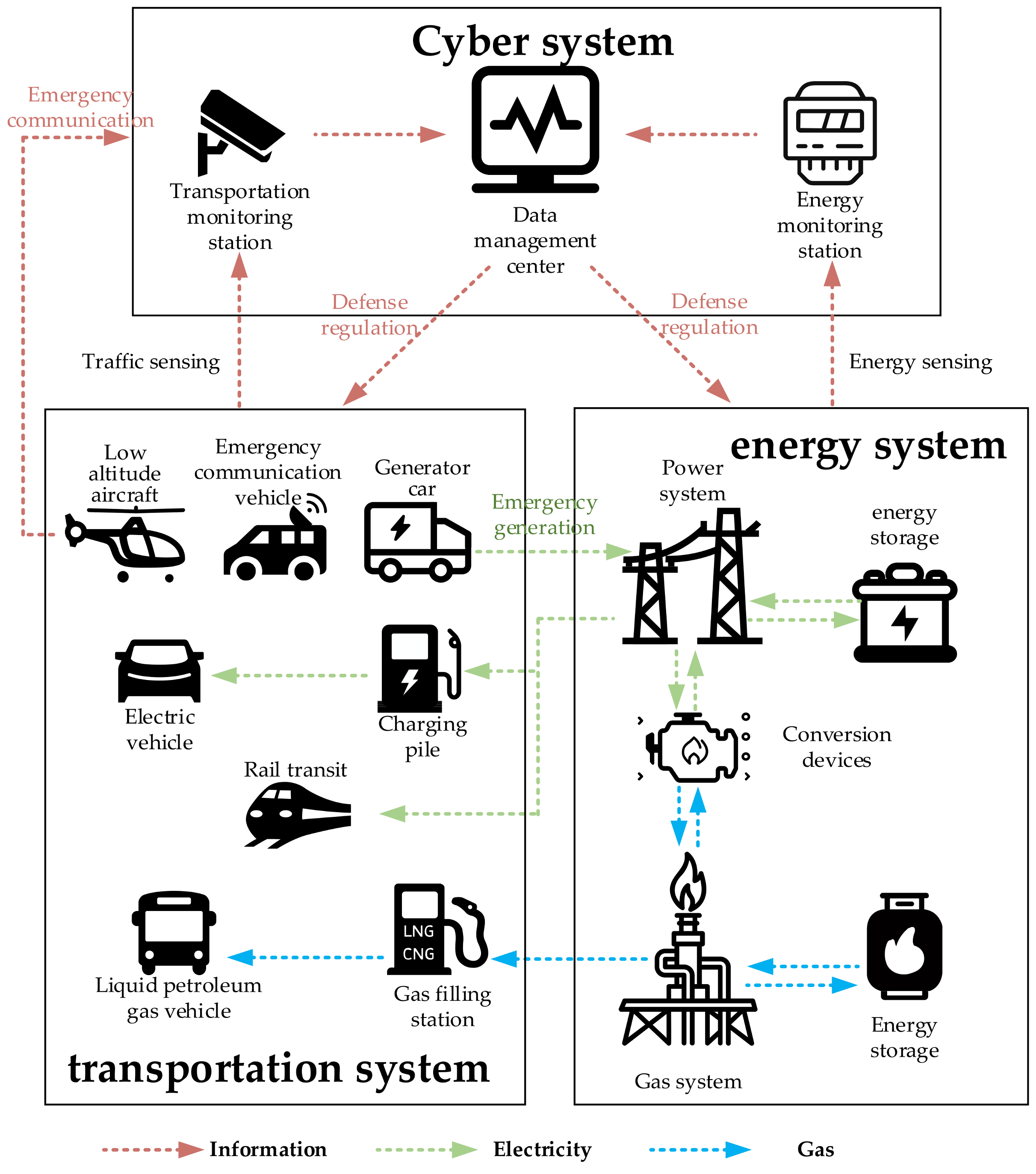
5.1. Theoretical Foundations of IECPS
5.1.1. Refined Modeling of IECPS
5.1.2. Model Solving of IECPS
- Analytic methods
- Heuristic algorithms
- Machine learning methods
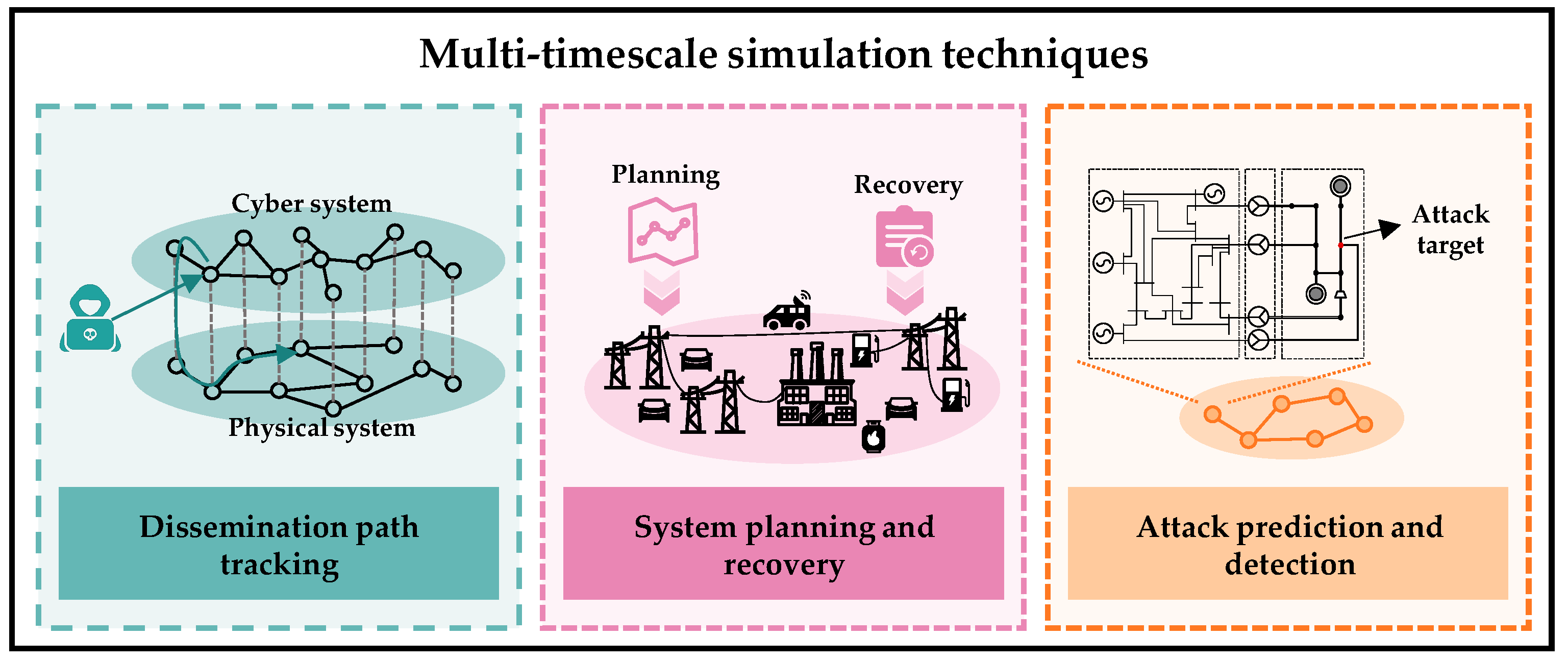
5.1.3. Multi-Timescale Simulation of IECPS
5.2. System Planning of IECPS
5.2.1. Redundancy and Emergency Equipment Planning
5.2.2. Cross-System Integration in Planning
5.2.3. Multi-Region Interaction on Planning
5.3. Optimized Scheduling of IECPS
5.3.1. Stochastic Optimization Scheduling
5.3.2. Robust Optimization Scheduling
5.4. Cyber Security of IECPS
5.4.1. Data Encryption and Processing
5.4.2. Communication Authentication and Protection
5.4.3. Attack Detection and Identification
5.4.4. Attack Attribution and Countermeasures
5.5. System Defense Assessment Technology
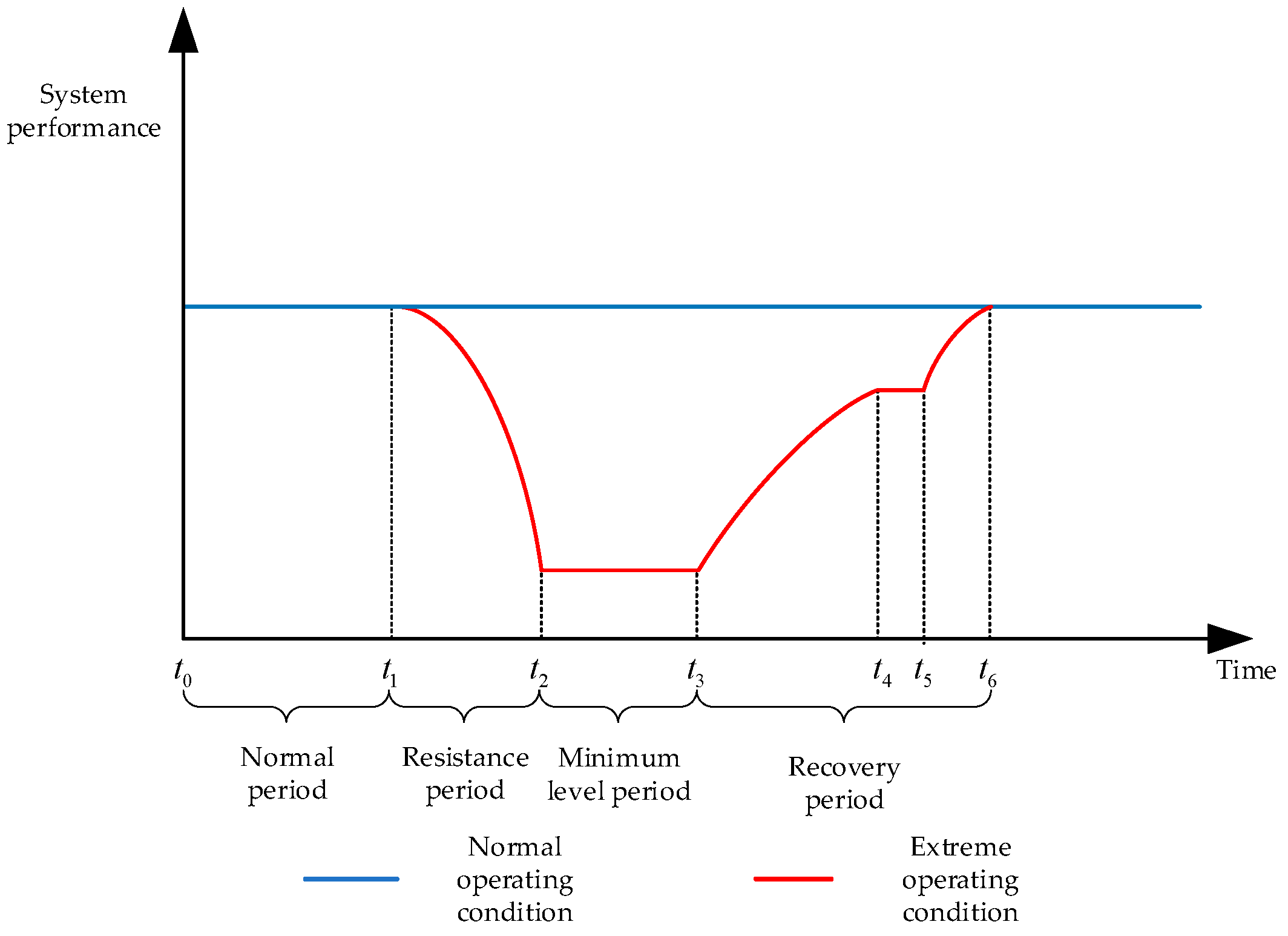
5.5.1. Resilience Assessment Methods
5.5.2. Resilience Assessment Indicators
6. Issues and Challenges in the Defense Against Deliberate Attacks on IECPS
6.1. Complexity of Modeling and Solving
6.2. Difficulties in Attack Detection and Early Warning
6.3. Obstacles in Defense Evaluation and Improvement
7. Conclusions
- Advanced attack strategies. The development of more threatening attack strategies can clarify system weaknesses and vulnerabilities, and help update and iterate the defense strategy. Nowadays, in addition to collaborating to develop based on several existing typical attack types, we should focus on the development of advanced cyberattack strategies against AI technology, which is applied in large numbers. Moreover, further research on multi-stage attack strategies that match real-world attack logic is needed, as this area of research is currently relatively weak.
- Efficient data processing. Combining traditional modeling methods with machine learning technology, we can develop a modeling method that combines both solution speed and solution accuracy to achieve high-precision digital reconstruction of IECPS. At the same time, the agility of system perception is improved with the help of big data technology to create IECPS with fast response capability and strong adaptability.
- Reliable privacy protection. In recent years, advanced persistent threat organizations and various cyber ransom syndicates have been targeting IECPS, and it is essential to strengthen the protection of data and information to prevent privacy leakage. The superior performance of quantum technology in data encryption and data transmission is expected to resist the intrusion of advanced persistent threat organizations and ransom groups into IECPS.
- Advanced system planning. At present, IECPS are still under gradual construction, but the development of various types of technology is very rapid. Only with advanced strategic planning can we avoid the problem of equipment compatibility that cannot be achieved during the construction of the subsequent security system. Whether to incorporate transportation into the energy system planning, as well as how to ensure the safety of the entire system after the incorporation of transportation into energy planning is topics that need to be explored.
- Reasonable emergency response mechanism. We should face the demand of users for rapid restoration of energy supply under malicious attacks, study the system reconfiguration and load restoration strategy of multi-energy synergy, and study the new technology of system restoration with the participation of resources, such as flex-direct, micro-grid, and energy storage. We should consider the emergency response mechanism in extreme situations, such as unsound pipeline networks and unavailable facilities, and improve the ability of IECPS to cope with malicious attacks.
- Scientific assessment system. The establishment of a scientific assessment system is the key to ensuring the rational formulation of system defense strategies. A multi-stage, multi-dimensional assessment system is not only conducive to accurately assessing the loss of the system but also can reflect whether the defense strategy is good or bad.
- Advanced equipment development. While information-based and intelligent equipment provides easy access to malicious attacks, it is undeniable that this advanced equipment maximizes the chances of stopping attacks. The development of more secure monitoring equipment can significantly reduce the probability of system attacks, while the development of equipment such as energy storage, electric vehicles, and emergency response devices provides regulating resources to mitigate the impact of attacks.
- Stabilized energy markets. The energy market serves as the foundation for the existence and operation of IECPS. Disruptions in the energy market will inevitably introduce uncertainties into the operation of IECPS, and attackers can potentially destabilize its safe and stable functioning by manipulating the market. Conversely, the energy market also possesses regulatory characteristics akin to those of the transportation system. Therefore, it is crucial to establish appropriate regulatory and operational frameworks to ensure that energy markets have a positive and stabilizing impact on energy systems.
- Practical energy projects. Future research also relies on a program of actual engineering projects. Each country should vigorously support the construction of relevant pilot projects to provide financial support for the construction of the safety system of IECPS, to provide research cases and accumulate technical experience. The combination of theoretical research and theoretical application will be accelerated by means of engineering applications.
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| IECPS | integrated energy cyber–physical system |
| CCPA | coordinated cyber–physical attack |
| APT | advanced persistent threat |
| GPS | global positioning system |
| RA | replay attack |
| MITM | man-in-the-middle attack |
| FDIA | false data injection attack |
| TSA | time synchronization attack |
| DoS | denial of service attack |
| CCA | coordinated cyberattack |
| AGC | automatic generation control |
| IED | intelligent electronic device |
| FTU | feeder terminal unit |
| RTU | remote terminal unit |
| DTU | data transfer unit |
| AC | alternating current |
| LR | load redistribution attack |
| DC | direct current |
| PMU | phasor measurement unit |
| DDoS | distribution denial of service |
| EV | electric vehicle |
| AI | artificial intelligence |
| BDD | bad data detection |
| KF | Kalman filter |
| MTD | moving target defense |
| GLR | generalized likelihood ratio |
| QCD | quickest change detection |
| CUSUM | cumulative sum test |
| G2V | grid-to-vehicle |
| V2G | vehicle-to-grid |
| V2B | vehicle-to-building |
| IoT | internet of things |
| IP | internet protocol address |
| HTTP | hypertext transfer protocol |
| IDS | intrusion detection system |
References
- Yang, J.; Zhang, N.; Wang, Y.; Kang, C. Multi-energy system towards renewable energy accommodation: Review and prospect. Autom. Electr. Power Syst. 2018, 42, 11–24. [Google Scholar]
- Zhang, W.; Zhang, C.; Li, J.; Zhu, L.; Cao, S.; Huang, W. Multi-resource collaborative service restoration of a distribution network with decentralized hierarchical droop control. Prot. Control Mod. Power Syst. 2024, 9, 19–37. [Google Scholar] [CrossRef]
- Lin, Y.; Luo, H.; Chen, Y.; Yang, Q.; Zhou, J.; Chen, X. Enhancing participation of widespread distributed energy storage systems in frequency regulation through partitioning–based control. Prot. Control Mod. Power Syst. 2025, 10, 76–89. [Google Scholar] [CrossRef]
- Lin, J. Risk Assessment of Cyber-Attacks in Integrated Energy System. Master’s Thesis, Guangxi University, Nanning, China, 2021. [Google Scholar]
- Zhang, G.; Zhong, H.; Tan, Z.; Cheng, T.; Xia, Q.; Kang, C. Texas electric power crisis of 2021 warns of a new blackout mechanism. CSEE J. Power Energy Syst. 2022, 8, 1–9. [Google Scholar]
- Xin, B.; Li, M.; He, J.; He, J.; Sun, W. Research on security defense system of new power system. Proc. CSEE 2023, 43, 5723–5732. [Google Scholar]
- Tang, Y.; Wang, Q.; Ni, M.; Liang, Y. Analysis of cyber attacks in cyber physical power system. Autom. Electr. Power Syst. 2016, 40, 148–151. [Google Scholar]
- Zang, T.; Wang, Z.; Wei, X.; Zhou, Y.; Wu, J.; Zhou, B. Current status and perspective of vulnerability assessment of cyber-physical power systems based on complex network theory. Energies 2023, 16, 6509. [Google Scholar] [CrossRef]
- Jang, K.B.; Baek, C.H.; Woo, T.H. Analysis of cyber nuclear terrorism by DTrack consequences in the civilian nuclear power plant. J. Nucl. Sci. Technol. 2022, 59, 207–215. [Google Scholar] [CrossRef]
- Ransomware Operators Demand $14 Million from Power Company. Available online: https://www.securityweek.com/ransomware-operators-demand-14-million-power-company/ (accessed on 16 February 2025).
- Energy Company EDP Confirms Cyberattack, Ragnar Locker Ransomware Blamed. Available online: https://www.zdnet.com/article/edp-energy-confirms-cyberattack-ragnar-locker-ransomware-blamed/ (accessed on 16 February 2025).
- America’s Largest Oil Pipeline Hit by Cyberattack—Multiple States Declared in State of Emergency. Available online: https://www.bbc.com/zhongwen/simp/world-57054720 (accessed on 16 February 2025).
- Industroyer2: Industroyer Reloaded. Available online: https://www.welivesecurity.com/2022/04/12/industroyer2-industroyer-reloaded/ (accessed on 16 February 2025).
- Cyber Incident Victim: Acea. Available online: https://www.csidb.net/csidb/incidents/39d3dade-5940-4110-8c1e-50a6c66528be/ (accessed on 17 February 2025).
- Tang, Y.; Chen, Q.; Li, M.; Wang, Q.; Ni, M.; Liang, Y. Overview on cyber-attacks against cyber physical power system. Autom. Electr. Power Syst. 2016, 40, 59–69. [Google Scholar]
- Tian, E.; Peng, C. Memory-based event-triggering H∞ load frequency control for power systems under deception attacks. IEEE Trans. Cybern. 2020, 50, 4610–4618. [Google Scholar] [CrossRef]
- Tadepalli, P.S.; Pullaguram, D. Distributed control microgrids: Cyber-attack models, impacts and remedial strategies. IEEE Trans. Signal Inf. Process. Netw. 2022, 8, 1008–1023. [Google Scholar] [CrossRef]
- Ahmed, C.M.; Palleti, V.R.; Mishra, V.K. A practical physical watermarking approach to detect replay attacks in a CPS. J. Process Control 2022, 116, 136–146. [Google Scholar] [CrossRef]
- Deb Roy, S.; Sharma, A.; Chakrabarti, S.; Debbarma, S. Securing power system data in motion by timestamped digital text watermarking. IEEE Trans. Smart Grid 2024, 15, 4974–4985. [Google Scholar] [CrossRef]
- Narang, J.K.; Bag, B. Deep learning-based integrated attack detection framework to protect distance relays against cyberattacks. Electr. Power Syst. Res. 2024, 231, 110346. [Google Scholar] [CrossRef]
- Raoof, A.; Lung, H.; Matrawy, A. Securing RPL using network coding: The chained secure mode (CSM). IEEE Internet Things J. 2022, 9, 4888–4898. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, C.; Zhang, S.; Liu, Y.; Huang, C.; Du, Y. A Tri-level programming-based frequency regulation market equilibrium under cyber attacks. Prot. Control Mod. Power Syst. 2023, 8, 55. [Google Scholar] [CrossRef]
- Cheng, G.; Lin, Y.; Zhao, J.; Yan, J. A highly discriminative detector against false data injection attacks in AC state estimation. IEEE Trans. Smart Grid 2022, 13, 2318–2330. [Google Scholar] [CrossRef]
- Jena, P.K.; Ghosh, S.; Koley, E.; Manohar, M. An ensemble classifier based scheme for detection of false data attacks aiming at disruption of electricity market operation. J. Netw. Syst. Manag. 2021, 29, 43. [Google Scholar] [CrossRef]
- Konstantinou, C.; Maniatakos, M. A case study on implementing false data injection attacks against nonlinear state estimation. In Proceedings of the 2nd ACM Workshop on Cyber–Physical Systems Security and Privacy, Vienna, Austria, 28 October 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 81–92. [Google Scholar]
- Zhang, Z.; Huang, S.; Liu, F.; Mei, S. Pattern analysis of topological attacks in cyber-physical power systems considering cascading outages. IEEE Access 2020, 8, 134257–134267. [Google Scholar] [CrossRef]
- Yang, H.; He, X.; Wang, Z.; Qiu, R.C.; Ai, Q. Blind false data injection attacks against state estimation based on matrix reconstruction. IEEE Trans. Smart Grid 2022, 13, 3174–3187. [Google Scholar] [CrossRef]
- Li, X.; Wang, Y.; Lu, Z. Graph-based detection for false data injection attacks in power grid. Energy 2023, 263, 125865. [Google Scholar] [CrossRef]
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A survey on the detection algorithms for false data injection attacks in smart grids. IEEE Trans. Smart Grid 2020, 11, 2218–2234. [Google Scholar] [CrossRef]
- Tan, R.; Nguyen, H.H.; Foo, E.Y.S.; Dong, X.; Yau, D.K.Y.; Kalbarczyk, Z.; Iyer, R.K.; Gooi, H.B. Optimal false data injection attack against automatic generation control in power grids. In Proceedings of the 2016 ACM/IEEE 7th International Conference on Cyber-Physical Systems (ICCPS), Vienna, Austria, 11–14 April 2016; pp. 1–10. [Google Scholar]
- Musleh, A.S.; Chen, G.; Dong, Z.Y.; Wang, C.; Chen, S. Attack detection in automatic generation control systems using LSTM-based stacked autoencoders. IEEE Trans. Ind. Inform. 2023, 19, 153–165. [Google Scholar] [CrossRef]
- Ghiasi, M.; Niknam, T.; Wang, Z.; Mehrandezh, M.; Dehghani, M.; Ghadimi, N. A Comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future. Electr. Power Syst. Res. 2023, 215, 108975. [Google Scholar] [CrossRef]
- Kumar, M.; Prasad, S.; Ansari, M.R.; Mohapatra, B. Resonance attacks detection and mitigation control scheme on frequency regulation in multi-area smart grid. Int. J. Control 2023, 96, 2212–2229. [Google Scholar] [CrossRef]
- Yuan, Y.; Li, Z.; Ren, K. Modeling load redistribution attacks in power systems. IEEE Trans. Smart Grid 2011, 2, 382–390. [Google Scholar] [CrossRef]
- Liu, X.; Bao, Z.; Lu, D.; Li, Z. Modeling of local false data injection attacks with reduced network information. IEEE Trans. Smart Grid 2015, 6, 1686–1696. [Google Scholar] [CrossRef]
- Yuan, Y.; Li, Z.; Ren, K. Quantitative analysis of load redistribution attacks in power systems. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1731–1738. [Google Scholar] [CrossRef]
- Ruan, J.; Yang, C.; Wang, Q.; Wang, S.; Liang, G.; Zhao, J.; Qiu, J. Assessment of spatiotemporally coordinated cyberattacks on renewable energy forecasting in smart energy system. Appl. Energy 2023, 347, 121470. [Google Scholar] [CrossRef]
- Ruan, J.; Wang, Q.; Chen, S.; Lyu, H.; Liang, G.; Zhao, J.; Dong, Z.Y. On vulnerability of renewable energy forecasting: Adversarial learning attacks. IEEE Trans. Ind. Inform. 2024, 20, 3650–3663. [Google Scholar] [CrossRef]
- Chen, F.; Shi, J.; Liu, H.; Wang, R.; Zhao, M.; Liu, D. Reliability evaluation of power generation and transmission system considering load redistribution attack and defense of vulnerable line. Autom. Electr. Power Syst. 2022, 46, 65–72. [Google Scholar]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. A framework for cyber-topology attacks: Line-switching and new attack scenarios. IEEE Trans. Smart Grid 2019, 10, 1704–1712. [Google Scholar] [CrossRef]
- Wang, S.; Ding, Z.; Wu, J.; Qiu, A. False data injection attack scheme of electricity market based on topology tampering. Electr. Power Autom. Equip. 2021, 41, 147–152. [Google Scholar]
- Liu, X.; Li, Z.; Liu, X.; Li, Z. Masking transmission line outages via false data injection attacks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1592–1602. [Google Scholar] [CrossRef]
- He, Z.; Gao, S.; Wei, X.; Zang, T.; Lei, J. Research on offensive and defensive game model of false topology attack based on collaborative tampering with branch and protection. Power Syst. Technol. 2022, 46, 4346–4355. [Google Scholar]
- Liang, G.; Weller, S.R.; Luo, F.; Zhao, J.; Dong, Z.Y. Generalized FDIA-based cyber topology attack with application to the australian electricity market trading mechanism. IEEE Trans. Smart Grid 2018, 9, 3820–3829. [Google Scholar] [CrossRef]
- Zhang, Z.; Gong, S.; Dimitrovski, A.D.; Li, H. Time synchronization attack in smart grid: Impact and analysis. IEEE Trans. Smart Grid 2013, 4, 87–98. [Google Scholar] [CrossRef]
- Shereen, E.; Delcourt, M.; Barreto, S.; Dán, G.; Le Boudec, J.-Y.; Paolone, M. Feasibility of time–synchronization attacks against PMU-based state estimation. IEEE Trans. Instrum. Meas. 2020, 69, 3412–3427. [Google Scholar] [CrossRef]
- Wang, Q.; Li, M.; Tang, Y.; Ni, M. A review on research of cyber-attacks and defense in cyber physical power systems part one modelling and evaluation. Autom. Electr. Power Syst. 2019, 43, 9–21. [Google Scholar]
- Li, Y.; Huang, R.; Ma, L. Hierarchical-attention-based defense method for load frequency control system against DoS attack. IEEE Internet Things J. 2021, 8, 15522–15530. [Google Scholar] [CrossRef]
- Zhang, X.; Liu, X.; Ding, T.; Wang, P. On resilience and distributed fixed-time control of mtdc systems under dos attacks. IEEE Trans. Autom. Sci. Eng. 2023, 20, 2569–2580. [Google Scholar] [CrossRef]
- Zhang, Y.; Xie, X.; Fu, W.; Chen, X.; Hu, S.; Zhang, L.; Xia, Y. An optimal combining attack strategy against economic dispatch of integrated energy system. IEEE Trans. Circuits Syst. II Express Briefs 2023, 70, 246–250. [Google Scholar] [CrossRef]
- Mohan, A.M.; Meskin, N.; Mehrjerdi, H. A comprehensive review of the cyber-attacks and cyber-security on load frequency control of power systems. Energies 2020, 13, 3860. [Google Scholar] [CrossRef]
- Demir, K.; Nayyer, F.; Suri, N. MPTCP-H: A DDoS attack resilient transport protocol to secure wide area measurement systems. Int. J. Crit. Infrastruct. Prot. 2019, 25, 84–101. [Google Scholar] [CrossRef]
- Kim, Y.; Hakak, S.; Ghorbani, A. Detecting distributed denial-of-service (DDoS) attacks that generate false authentications on electric vehicle (EV) charging infrastructure. Comput. Secur. 2024, 144, 103989. [Google Scholar] [CrossRef]
- Tawfiq, M. Modeling Time-Varying Wide-Scale Distributed Denial of Service Attacks on Electric Vehicle Charging Stations. Ain Shams Eng. J. 2024, 15, 102860. [Google Scholar]
- Yan, B.; Yao, P.; Yang, T.; Zhou, B.; Yang, Q. Game-theoretical model for dynamic defense resource allocation in cyber-physical power systems under distributed denial of service attacks. J. Mod. Power Syst. Clean Energy 2024, 12, 41–51. [Google Scholar] [CrossRef]
- Tawfiq, A.; Abdulaziz, A. A comprehensive survey of cyberattacks on EVs: Research domains, attacks, defensive mechanisms, and verification methods. Def. Technol. 2024, 42, 31–58. [Google Scholar]
- Feng, Y.; Huang, R.; Zhao, W.; Yin, P.; Li, Y. A survey on coordinated attacks against cyber–physical power systems: Attack, detection, and defense methods. Electr. Power Syst. Res. 2025, 241, 111286. [Google Scholar] [CrossRef]
- Xiahou, K.; Xu, X.; Huang, D.; Du, W.; Li, M. Sliding-Mode Perturbation Observer-Based Delay-Independent Active Mitigation for AGC systems against false data injection and random time-delay attacks. IEEE Trans. Ind. Cyber-Phys. Syst. 2024, 2, 446–458. [Google Scholar] [CrossRef]
- Zadsar, M.; Abazari, A.; Ameli, A.; Yan, J.; Ghafouri, M. Prevention and detection of coordinated false data injection attacks on integrated power and gas systems. IEEE Trans. Power Syst. 2023, 38, 4252–4268. [Google Scholar] [CrossRef]
- Zhou, B.; Ming, X.; Zang, T.; Zhang, Y.; Chen, Y.; Zhao, W. Loss assessment and vulnerability analysis of an integrated electricity natural gas system under load redistribution attack. Adv. Eng. Sci. 2023, 55, 3–13. [Google Scholar]
- Gu, W.; Ding, S.; Lu, S.; Zhao, P.; Zou, D.; Qiu, Y.; Yu, R.; Sheng, L. Coordinated heat and power cyber-attacks with time window matching strategy. IEEE Trans. Smart Grid 2023, 14, 2747–2761. [Google Scholar] [CrossRef]
- Zhang, H.; Chen, Z.; Yu, C.; Yue, D.; Xie, X.; Hancke, G.P. Event-trigger-based resilient distributed energy management against FDI and DoS attack of cyber-physical system of smart grid. IEEE Trans. Syst. Man Cybern. Syst. 2024, 54, 3220–3230. [Google Scholar] [CrossRef]
- Maiti, S.; Balabhaskara, A.; Adhikary, S.; Koley, I.; Dey, S. Targeted attack synthesis for smart grid vulnerability analysis. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 2576–2590. [Google Scholar]
- Xia, Y.; Xu, Y.; Mondal, S.; Gupta, A.K. A transfer learning-based method for cyber-attack tolerance in distributed control of microgrids. IEEE Trans. Smart Grid 2024, 15, 1258–1270. [Google Scholar] [CrossRef]
- Li, H.; Lu, R.; Zhou, L.; Yang, B.; Shen, X. An efficient merkle-tree-based authentication scheme for smart grid. IEEE Syst. J. 2014, 8, 655–663. [Google Scholar] [CrossRef]
- Kim, J.; Tong, L. On topology attack of a smart grid: Undetectable attacks and countermeasures. IEEE J. Sel. Areas Commun. 2013, 31, 1294–1305. [Google Scholar] [CrossRef]
- Yang, T.; Xu, Z.; Zhao, J.; Zhai, F. Review on research of attack and defense methods for digitalized new power system. Autom. Electr. Power Syst. 2024, 48, 112–126. [Google Scholar]
- Cao, P.; Ji, Y.; Ding, M.; Ni, L.; Ma, Y.; Jin, L. Research on the impact of graphite fiber attached insulator. In Proceedings of the 2022 IEEE 5th International Electrical and Energy Conference (CIEEC), Nangjing, China, 27–29 May 2022; pp. 1704–1709. [Google Scholar]
- Wu, Y.; Chen, Z.; Dang, J.; Chen, Y.; Zhao, X.; Zha, L. Allocation of defensive and restorative resources in electric power system against consecutive multi-target attacks. Reliab. Eng. Syst. Saf. 2022, 219, 108199. [Google Scholar] [CrossRef]
- Karabiber, A. Detecting and pricing nontechnical losses by using utility power meters in electricity distribution grids. J. Electr. Eng. Technol. 2019, 14, 1933–1942. [Google Scholar] [CrossRef]
- Li, P.; Fu, J.; Xie, K.; Hu, B.; Wang, Y.; Shao, C.; Sun, Y.; Huang, W. A Defense planning model for a power system against coordinated cyber–physical attack. Prot. Control Mod. Power Syst. 2024, 9, 84–95. [Google Scholar] [CrossRef]
- Tian, J.; Wang, B.; Li, T.; Shang, F.; Cao, K. Coordinated cyber-physical attacks considering dos attacks in power systems. Int. J. Robust Nonlinear Control 2020, 30, 4345–4358. [Google Scholar] [CrossRef]
- Zhang, Z.; Deng, R.; Tian, Y.; Cheng, P.; Ma, J. SPMA: Stealthy physics–manipulated attack and countermeasures in cyber-physical smart grid. IEEE Trans. Inf. Forensics Secur. 2023, 18, 581–596. [Google Scholar] [CrossRef]
- Li, S.; Shi, L. A tri-level optimization strategy incorporating wind power against coordinated cyber-physical attacks. IET Gener. Transm. Distrib. 2023, 17, 2228–2248. [Google Scholar] [CrossRef]
- Xiang, Y.; Wang, L.; Liu, N. Coordinated attacks on electric power systems in a cyber-physical environment. Electr. Power Syst. Res. 2017, 149, 156–168. [Google Scholar] [CrossRef]
- Ren, H.; Jiang, Z.; Wu, Q.; Li, Q.; Lv, H. Optimal planning of an economic and resilient district integrated energy system considering renewable energy uncertainty and demand response under natural disasters. Energy 2023, 277, 127644. [Google Scholar] [CrossRef]
- Ren, H.; Zhang, Y.; Wu, Q.; Li, Q. Research review on planning and operation dispatch of integrated energy system for resilience enhancement. Autom. Electr. Power Syst. 2024, 1–16. [Google Scholar]
- Adefarati, T.; Bansal, R.C. Reliability assessment of distribution system with the integration of renewable distributed generation. Appl. Energy 2017, 185, 158–171. [Google Scholar] [CrossRef]
- Gharehveran, S.S.; Ghassemzadeh, S.; Rostami, N. Two-stage resilience-constrained planning of coupled multi–energy microgrids in the presence of battery energy storages. Sustain. Cities Soc. 2022, 83, 103952. [Google Scholar] [CrossRef]
- Wang, J.-J.; Fu, C.; Yang, K.; Zhang, X.-T.; Shi, G.; Zhai, J. Reliability and availability analysis of redundant bchp (building cooling, heating and power system. Energy 2013, 61, 531–540. [Google Scholar] [CrossRef]
- Nazemi, M.; Moeini-Aghtaie, M.; Fotuhi-Firuzabad, M.; Dehghanian, P. Energy storage planning for enhanced resilience of power distribution networks against earthquakes. IEEE Trans. Sustain. Energy 2020, 11, 795–806. [Google Scholar] [CrossRef]
- Abdulrazzaq Oraibi, W.; Mohammadi-Ivatloo, B.; Hosseini, S.H.; Abapour, M. Multi microgrid framework for resilience enhancement considering mobile energy storage systems and parking lots. Appl. Sci. 2023, 13, 1285. [Google Scholar] [CrossRef]
- Lei, S.; Wang, J.; Chen, C.; Hou, Y. Mobile emergency generator pre-positioning and real-time allocation for resilient response to natural disasters. IEEE Trans. Smart Grid 2018, 9, 2030–2041. [Google Scholar] [CrossRef]
- Flôr, V.B.B.; Filho, M.B.D.C.; Souza, J.C.S.; Vergara, P.P. Critical data visualization to enhance protection schemes for state estimation. IEEE Trans. Smart Grid 2023, 14, 1249–1261. [Google Scholar] [CrossRef]
- He, X.; Tu, C.; Yu, L. Measurements processing method of distribution network state estimation and anti false data injection attack strategy. High Volt. Eng. 2021, 47, 2342–2349. [Google Scholar]
- Huang, C.; Hong, M.; Fu, S.; Deng, S. Distributed state estimation of active distribution network considering false data injection attack. Electr. Power Eng. Technol. 2022, 41, 22–31. [Google Scholar]
- Shafie, A.E.; Chihaoui, H.; Hamila, R.; Al-Dhahir, N.; Gastli, A.; Ben-Brahim, L. Impact of passive and active security attacks on MIMO smart grid communications. IEEE Syst. J. 2019, 13, 2873–2876. [Google Scholar] [CrossRef]
- Derhab, A.; Guerroumi, M.; Belaoued, M.; Cheikhrouhou, O. BMC-SDN: Blockchain-based multicontroller architecture for secure software-defined networks. Wirel. Commun. Mob. Comput. 2021, 2021, 9984666. [Google Scholar] [CrossRef]
- Yang, W.; Wan, Y.; He, J.; Cao, Y. Security vulnerabilities and countermeasures for time synchronization in TSCH networks. Wirel. Commun. Mob. Comput. 2018, 2018, 1954121. [Google Scholar] [CrossRef]
- Cao, P.; Liu, M. PMU placement method based on improved integer programming method combined with zero injection buses. Power Syst. Prot. Control 2021, 49, 143–150. [Google Scholar]
- Zhou, S.; Liu, X.; Xiong, Z.; Wang, X.; Jiang, C.; Zhang, S. Line Hardening and energy storage system configuration strategies for resilience enhancement of a hybrid AC-DC distribution system. J. Shanghai Jiaotong Univ. 2021, 55, 1619. [Google Scholar]
- Zhang, H.; Ma, S.; Chen, X.; Gong, X.; Wei, K. Distribution network energy storage planning ensuring uninterrupted power supply for critical loads. Power Syst. Technol. 2021, 45, 259–268. [Google Scholar]
- Said, D.; Elloumi, M.; Khoukhi, L. Cyber-attack on P2P energy transaction between connected electric vehicles: A false data injection detection based machine learning model. IEEE Access 2022, 10, 63640–63647. [Google Scholar] [CrossRef]
- Jafari, M.; Kavousi-Fard, A.; Sheikh, M.; Jin, T.; Karimi, M. A copula-based secured intelligent dynamic-static energy community transportation system for smart cities. Sustain. Cities Soc. 2024, 107, 105432. [Google Scholar] [CrossRef]
- Xu, T.; Shao, C.; Shahidehpour, M.; Wang, X. Coordinated planning strategies of power systems and energy transportation networks for resilience enhancement. IEEE Trans. Sustain. Energy 2023, 14, 1217–1229. [Google Scholar] [CrossRef]
- 14th Five-Year Plan for Energy in Lin-Gang Special Area. Available online: https://en.lingang.gov.cn/html/website/lg/English/about/14th/Industrial%20Development/1668586084997582850.html (accessed on 20 January 2025).
- Huang, G.; Li, G.; Xiao, Y.; Bie, Z.; Sun, S. Optimal Placement for Integrated Electricity and Gas Energy System Considering Natural Disasters and Man-made Attacks. Power Syst. Technol. 2021, 45, 959–970. [Google Scholar]
- Kumar, R.; Mishra, S.K.; Mohanta, D.K. An integrated development environment based situational awareness for operational reliability evaluation in wind energy systems incorporating uncertainties. Electr. Power Syst. Res. 2024, 233, 110467. [Google Scholar] [CrossRef]
- Lv, X.; Yang, X.; An, L.; Lin, Z. Multi-fault repair and recovery strategy for local energy internet integrated with trans-portation network. Electr. Power Autom. Equip. 2020, 40, 32–39. [Google Scholar]
- Zhang, H.; Liu, Y. Comprehensive assessment of extreme ice disaster affecting power system operation available. Proc. CSEE 2011, 31, 52–58. [Google Scholar]
- Hu, X.; Zhang, H.; Ma, D.; Wang, R. Situation awareness method using spectral analysis of random matrix for integrated energy system. ISA Trans. 2020, 99, 240–251. [Google Scholar] [CrossRef]
- Liu, Y.; Hazarika, H.; Kanaya, H.; Takiguchi, O.; Murai, M.; Hidayat, M.N.; Kochi, Y. Design and deployment of an iot-based landslide early warning system. In Proceedings of the 2022 International Conference and Utility Exhibition on Energy, Environment and Climate Change (ICUE), Pattaya, Thailand, 26–28 October 2022; pp. 1–7. [Google Scholar]
- Zhu, J.; Dai, C.; Yang, H.; Shan, Y.; Ren, J.; Liu, Y.; Li, J.; Chen, W.; Liang, J.; Ling, S. Intellisense bio-ionotronics battery for early warning of geological seepage. ACS Sens. 2023, 8, 2731–2739. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Ding, Z.; Xie, S. Construction of experimental platform for resilience enhancement of energy-transport-information integrated systems. Exp. Technol. Manag. 2023, 40, 7–13. [Google Scholar]
- Wu, Y.; Xue, Y.; Xie, Y.; Wang, H.; Duan, R.; Huang, W. Space-time impact of typhoon and rainstorm on power grid fault probability. Autom. Electr. Power Syst. 2016, 40, 20–29+83. [Google Scholar]
- Du, S.; Guo, C.; Yu, X.; Zhao, F.; Xin, H.; Fang, Y. Review and prospect of resilient distribution network under typhoon disaster. Electr. Power Autom. Equip. 2022, 42, 176–186+209. [Google Scholar]
- Shahgholian, G.; Moradian, M.; Fathollahi, A. Droop Control Strategy in inverter-based microgrids: A brief review on analysis and application in islanded mode of operation. IET Renew. Power Gener. 2025, 19, e13186. [Google Scholar] [CrossRef]
- Najafi Tari, A.; Sepasian, M.S.; Tourandaz Kenari, M. Resilience assessment and improvement of distribution networks against extreme weather events. Int. J. Electr. Power Energy Syst. 2021, 125, 106414. [Google Scholar] [CrossRef]
- Chen, B.; Wu, Q.H.; Li, M.; Xiahou, K. Detection of false data injection attacks on power systems using graph edge-conditioned convolutional networks. Prot. Control Mod. Power Syst. 2023, 8, 16. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A.N.; Tari, Z. A taxonomy of cyber defence strategies against false data attacks in smart grids. ACM Comput. Surv. 2023, 55, 331:1–331:37. [Google Scholar] [CrossRef]
- Liu, T.; Gu, Y.; Wang, D.; Gui, Y.; Guan, X. A novel method to detect bad data injection attack in smart grid. In Proceedings of the 2013 Proceedings IEEE INFOCOM 2013, Turin, Italy, 14–19 April 2013; pp. 3423–3428. [Google Scholar]
- Zhao, J.; Gómez-Expósito, A.; Netto, M.; Mili, L.; Abur, A.; Terzija, V.; Kamwa, I.; Pal, B.; Singh, A.K.; Qi, J.; et al. Power system dynamic state estimation: Motivations, definitions, methodologies, and future work. IEEE Trans. Power Syst. 2019, 34, 3188–3198. [Google Scholar] [CrossRef]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using kalman filter. IEEE Trans. Control Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- He, Y.; Zhou, C.; Zheng, N.; Zhang, W.; Xie, Y. Detection method against false data injection attack based on extended kalman filter. Electric Power 2017, 50, 35–40. [Google Scholar]
- He, D.; Xu, C.; Lou, X. Data attack detection of connected vehicle systems based on adaptive kalman filtering. J. Zhejiang Univ. Technol. 2021, 49, 178–185. [Google Scholar]
- Liu, X.; Chang, P.; Sun, Q. Grid false data injection attacks detection based on xgboost and unscented kalman filter adaptive hybrid prediction. Proc. CSEE 2021, 41, 5462–5476. [Google Scholar]
- Chen, B.; Li, H.; Li, B. Application research on pseudo measurement modeling and AUKF in FDIAs identification of distribution network. Power Syst. Technol. 2019, 43, 3226–3236. [Google Scholar]
- Liu, C.; Wu, J.; Long, C.; Kundur, D. Reactance perturbation for detecting and identifying FDI attacks in power system state estimation. IEEE J. Sel. Top. Signal Process. 2018, 12, 763–776. [Google Scholar] [CrossRef]
- Zhang, Z.; Deng, R.; Yau, D.K.Y.; Cheng, P.; Chen, J. Analysis of moving target defense against false data injection attacks on power grid. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2320–2335. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, B.; Liu, X.; Pahwa, A.; Wu, H. Voltage stability constrained moving target defense against net load redistribution attacks. IEEE Trans. Smart Grid 2022, 13, 3748–3759. [Google Scholar] [CrossRef]
- Lakshminarayana, S.; Belmega, E.V.; Poor, H.V. Moving-target defense against cyber-physical attacks in power grids via game theory. IEEE Trans. Smart Grid 2021, 12, 5244–5257. [Google Scholar] [CrossRef]
- Kosut, O.; Jia, L.; Thomas, R.; Tong, L. Malicious data attacks on the smart grid. IEEE Trans. Smart Grid 2011, 2, 645–658. [Google Scholar] [CrossRef]
- Wei, S.; Xu, J.; Wu, Z.; Hu, Q.; Yu, X. A false data injection attack detection strategy for unbalanced distribution networks state estimation. IEEE Trans. Smart Grid 2023, 14, 3992–4006. [Google Scholar] [CrossRef]
- Tang, B.; Yan, J.; Kay, S.; He, H. Detection of false data injection attacks in smart grid under colored gaussian noise. In Proceedings of the 2016 IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA, 17–19 October 2016; pp. 172–179. [Google Scholar]
- Liu, X.; Guan, Y.; Kim, S.W. Bayesian test for detecting false data injection in wireless relay networks. IEEE Commun. Lett. 2018, 22, 380–383. [Google Scholar] [CrossRef]
- Mangalwedekar, S.; Bansode, P.; Kazi, F.; Singh, N. A bayesian game-theoretic defense strategy for false data injection attacks in smart grid. In Proceedings of the 2017 14th IEEE India Council International Conference (INDICON), Roorkee, India, 15–17 December 2017; pp. 1–6. [Google Scholar]
- Khan, M.A.; Nasralla, M.M.; Umar, M.M.; Khan, S.; Choudhury, N. An efficient multilevel probabilistic model for abnormal traffic detection in wireless sensor networks. Sensors 2022, 22, 410. [Google Scholar] [CrossRef] [PubMed]
- Chen, L.; Li, S.; Wang, X. Quickest fault detection in photovoltaic systems. IEEE Trans. Smart Grid 2018, 9, 1835–1847. [Google Scholar] [CrossRef]
- Rovatsos, G.; Jiang, X.; Domínguez-García, A.D.; Veeravalli, V.V. Statistical power system line outage detection under transient dynamics. IEEE Trans. Signal Process. 2017, 65, 2787–2797. [Google Scholar] [CrossRef]
- Huang, Y.; Li, H.; Campbell, K.; Zhu, H. Defending false data injection attack on smart grid network using adaptive CUSUM test. In Proceedings of the 2011 45th Annual Conference on Information Sciences and Systems, Baltimore, MD, USA, 23–25 March 2011; pp. 1–6. [Google Scholar]
- Li, S.; Yılmaz, Y.; Wang, X. Quickest detection of false data injection attack in wide-area smart grids. IEEE Trans. on Smart Grid 2015, 6, 2725–2735. [Google Scholar] [CrossRef]
- Nath, S.; Akingeneye, I.; Wu, J.; Han, Z. Quickest detection of false data injection attacks in smart grid with dynamic models. IEEE J. Emerg. Sel. Top. Power Electron. 2022, 10, 1292–1302. [Google Scholar] [CrossRef]
- Hussain, S.; Hussain, S.M.S.; Hemmati, M.; Iqbal, A.; Alammari, R.; Zanero, S.; Ragaini, E.; Gruosso, G. A novel hybrid cybersecurity scheme against false data injection attacks in automated power systems. Prot. Control Mod. Power Syst. 2023, 8, 37. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Yarman Vural, F.T.; Kulkarni, S.R.; Vincent Poor, H. Smarter security in the smart grid. In Proceedings of the 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm), Tainan, Taiwan, 5–8 November 2012; pp. 312–317. [Google Scholar]
- Yang, Z.; Liu, H.; Bi, T.; Yang, Q. PMU bad data detection method based on long short-term memory network. Power Syst. Prot. Control 2020, 48, 1–9. [Google Scholar]
- He, Y.; Mendis, G.J.; Wei, J. Real-time detection of false data injection attacks in smart grid: A deep learning-based intelligent mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. [Google Scholar] [CrossRef]
- Yu, J.; Hou, Y.; Li, V. Online false data injection attack detection with wavelet transform and deep neural networks. IEEE Trans. Industr. Inform. 2018, 14, 3271–3280. [Google Scholar] [CrossRef]
- Hu, C.; Yan, J.; Wang, C. Advanced cyber-physical attack classification with extreme gradient boosting for smart transmission grids. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019. [Google Scholar]
- Zhang, B.; Liu, X.; Yu, Z.; Wang, W.; Jin, Q.; Li, W. Review on artificial intelligence-based network attack detection in power systems. High Volt. Eng. 2022, 48, 4413–4426. [Google Scholar]
- Khalid, H.M.; Peng, J.C.-H. A bayesian algorithm to enhance the resilience of WAMS applications against cyber attacks. IEEE Trans. Smart Grid 2016, 7, 2026–2037. [Google Scholar] [CrossRef]
- Wang, X. Research on Malicious Data Attacks and Recognition in Energy Internet. Master’s Thesis, North China Electric Power University, Beijing, China, 2023. [Google Scholar]
- Qi, R.; Rasband, C.; Zheng, J.; Longoria, R. Detecting cyber attacks in smart grids using semi-supervised anomaly detection and deep representation learning. Information 2021, 12, 328. [Google Scholar] [CrossRef]
- Wang, P.; Govindarasu, M.; Ashok, A.; Sridhar, S.; McKinnon, D. Data-driven anomaly detection for power system generation control. In Proceedings of the 2017 IEEE International Conference on Data Mining Workshops (ICDMW), New Orleans, LA, USA, 18–21 November 2017; pp. 1082–1089. [Google Scholar]
- Zhang, Y.; Wang, J.; Chen, B. Detecting false data injection attacks in smart grids: A semi-supervised deep learning approach. IEEE Trans. Smart Grid 2021, 12, 623–634. [Google Scholar] [CrossRef]
- Mohammadpourfard, M.; Sami, A.; Seifi, A.R. A statistical unsupervised method against false data injection attacks: A visualization-based approach. Expert Syst. Appl. 2017, 84, 242–261. [Google Scholar] [CrossRef]
- Zhang, Y.; Yan, J. Domain-adversarial transfer learning for robust intrusion detection in the smart grid. In Proceedings of the 2019 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Beijing, China, 21–23 October 2019; pp. 1–6. [Google Scholar]
- Konstantinou, C.; Maniatakos, M. A data-based detection method against false data injection attacks. IEEE Des. Test 2020, 37, 67–74. [Google Scholar] [CrossRef]
- Zhao, Y.; Li, Z.; Ju, P.; Wang, C. Resilience of power system with integrated energy in context of low-carbon energy transition: Review and prospects. Electr. Power Autom. Equip. 2021, 41, 13–23+47. [Google Scholar]
- Hategekimana, P.; Ferre, A.J.; Bernuz, J.M.R.; Ntagwirumugara, E. Fault detecting and isolating schemes in a low-voltage DC microgrid network from a remote village. Energies 2022, 15, 4460. [Google Scholar] [CrossRef]
- Zhang, G.; Tong, X.; Hong, Q.; Lu, X.; Booth, C.D. A novel fault isolation scheme in power system with dynamic topology using wide-area information. IEEE Trans. Ind. Inform. 2022, 18, 2399–2410. [Google Scholar] [CrossRef]
- Esfahani, A.G.; Fani, B.; Delshad, M.; Saghafi, H. A three-stage multi-agent-based peer-to-peer method for fault isolation of high distributed generation penetrated distribution networks. IET Renew. Power Gener. 2023, 17, 1255–1266. [Google Scholar] [CrossRef]
- Lv, W.; Zheng, T.; Yang, Y.; Li, R.; Sun, S. Novel fault isolation scheme under protection failure in MVDC distribution networks without DC circuit breakers. Int. J. Electr. Power Energy Syst. 2023, 148, 108901. [Google Scholar] [CrossRef]
- Peng, K.; Zhang, C.; Xu, B.; Chen, Y.; Cheng, J.; Zhao, X. Key issues of fault analysis on distribution system with high-density distributed generations. Autom. Electr. Power Syst. 2017, 41, 184–192. [Google Scholar]
- Chen, Y.; Wen, J.; Chen, T.; Ojas, P. Bayesian networks for whole building level fault diagnosis and isolation. In Proceedings of the 2018 5th International High Performance Buildings Conference, Purdue, West Lafayette, IN, USA, 9–12 July 2018; pp. 1–10. [Google Scholar]
- Chen, Y.; Wen, J.; Pradhan, O.; Lo, L.J.; Wu, T. Using discrete bayesian networks for diagnosing and isolating cross-level faults in HVAC systems. Appl. Energy 2022, 327, 120050. [Google Scholar] [CrossRef]
- Wang, Z.; Wang, L.; Tan, Y.; Yuan, J.; Li, X. Fault diagnosis using fused reference model and bayesian network for building energy systems. J. Build. Eng. 2021, 34, 101957. [Google Scholar] [CrossRef]
- Kiluk, S. Algorithmic acquisition of diagnostic patterns in district heating billing system. Appl. Energy 2012, 91, 146–155. [Google Scholar] [CrossRef]
- Månsson, S.; Kallioniemi, P.O.J.; Sernhed, K.; Thern, M. A machine learning approach to fault detection in district heating substations. Energy Procedia 2018, 149, 226–235. [Google Scholar] [CrossRef]
- Li, M.; Deng, W.; Xiahou, K.; Ji, T.; Wu, Q. A data-driven method for fault detection and isolation of the integrated energy-based district heating system. IEEE Access 2020, 8, 23787–23801. [Google Scholar] [CrossRef]
- Huang, J.; Ghalamsiah, N.; Patharkar, A.; Pradhan, O.; Chu, M.; Wu, T.; Wen, J.; O’Neill, Z.; Selcuk Candan, K. An entropy-based causality framework for cross-level faults diagnosis and isolation in building HVAC systems. Energy Build. 2024, 317, 114378. [Google Scholar] [CrossRef]
- Dong, G.; He, C.; Liu, X.; Nan, L.; Liu, T.; Zhang, Y. Coordinated recovery method of post-disaster distribution network cyber-physical system considering network reconstruction and emergency resources. Electr. Power Autom. Equip. 2024, 44, 106–113. [Google Scholar]
- Szott, M.; Wermiński, S.; Jarnut, M.; Kaniewski, J.; Benysek, G. Battery energy storage system for emergency supply and improved reliability of power networks. Energies 2021, 14, 720. [Google Scholar] [CrossRef]
- Zhou, B.; Wu, J.; Zang, T.; Cai, Y.; Sun, B.; Qiu, Y. Emergency dispatch approach for power systems with hybrid energy considering thermal power unit ramping. Energies 2023, 16, 4213. [Google Scholar] [CrossRef]
- Hou, H.; Tang, J.; Zhang, Z.; Wu, X.; Wei, R.; Wang, L.; He, H. Stochastic pre-disaster planning and post-disaster restoration to enhance distribution system resilience during typhoons. Energy Convers. Econ. 2023, 4, 346–363. [Google Scholar] [CrossRef]
- Malek, A.F.; Mokhlis, H.; Mansor, N.N.; Jamian, J.J.; Wang, L.; Muhammad, M.A. Power distribution system outage management using improved resilience metrics for smart grid applications. Energies 2023, 16, 3953. [Google Scholar] [CrossRef]
- Bustamante, R.; Mosqueda, G.; Kim, M. Enhanced seismic protection system for an emergency diesel generator unit. Energies 2022, 15, 1728. [Google Scholar] [CrossRef]
- Zhou, D. China’s energy emergency management system and capacity building. Jiang-Huai Trib. 2020, 27–32. [Google Scholar] [CrossRef]
- Ge, H.; Li, J.; Liu, H.; Cao, Y.; Yang, Z.; Yan, J. Assessing and boosting the resilience of a distribution system under extreme weather. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019. [Google Scholar]
- Ameli, H.; Qadrdan, M.; Strbac, G. Value of gas network infrastructure flexibility in supporting cost effective operation of power systems. Appl. Energy 2017, 202, 571–580. [Google Scholar] [CrossRef]
- Bao, Z.; Ye, Y.; Wu, L. Multi-timescale coordinated schedule of interdependent electricity-natural gas systems considering electricity grid steady-state and gas network dynamics. Int. J. Electr. Power Energy Syst. 2020, 118, 105763. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhou, K.; Yang, S. A post-disaster load supply restoration model for urban integrated energy systems based on multi-energy coordination. Energy 2024, 303, 132008. [Google Scholar] [CrossRef]
- Wang, T.; Wang, Y.; Yu, H.; Tang, Y.; Gu, W.; Lu, Y.; Han, J. Resilience resources scheduling for new distribution system with high proportions of renewables. Renew. Energy Resour. 2022, 40, 1249–1256. [Google Scholar]
- Wang, J.; Ge, H.; Yang, Y.; Pan, Z.; Liu, Y.; Zhao, H. Collaborative service restoration with network reconfiguration for resilience enhancement in integrated electric and heating systems. Electronics 2023, 12, 3792. [Google Scholar] [CrossRef]
- Wang, Z.; Ding, T.; Jia, W.; Huang, C.; Mu, C.; Qu, M.; Shahidehpour, M.; Yang, Y.; Blaabjerg, F.; Li, L.; et al. Multi-stage stochastic programming for resilient integrated electricity and natural gas distribution systems against typhoon natural disaster attacks. Renew. Sustain. Energy Rev. 2022, 159, 111784. [Google Scholar] [CrossRef]
- Jia, L.; Pannala, S.; Kandaperumal, G.; Srivastava, A. Coordinating energy resources in an islanded microgrid for economic and resilient operation. IEEE Trans. Ind. Appl. 2022, 58, 3054–3063. [Google Scholar] [CrossRef]
- Brown, M.A.; Soni, A. Expert perceptions of enhancing grid resilience with electric vehicles in the united states. Energy Res. Soc. Sci. 2019, 57, 101241. [Google Scholar] [CrossRef]
- Wei, J.; Gao, X.; Cheng, P.; Fu, W.; Zeng, H. Coordinated post-disaster recovery and assessment method for integrated electricity-gas-transportation system. IEEE Access 2023, 11, 11685–11699. [Google Scholar] [CrossRef]
- Zhao, P.; Li, S.; Hu, P.J.-H.; Cao, Z.; Gu, C.; Xie, D.; Zeng, D.D. Coordinated cyber security enhancement for grid-transportation systems with social engagement. IEEE Trans. Emerg. Top. Comput. Intell. 2022, 8, 3199–3213. [Google Scholar] [CrossRef]
- Zang, T.; Liu, Y.; Wang, S.; Xiao, Y.; Wang, Z.; Zhou, B. Multi-period maintenance and restoration collaborative strategy for cyber physical distribution system considering fault propagation effect. Electr. Power Autom. Equip. 2024, 44, 247–256. [Google Scholar]
- Pang, K.; Wang, Y.; Wen, F.; Wang, C.; Zhao, J.; Liu, Y. Cyber-physical collaborative restoration strategy for power transmission system with communication failures. Autom. Electr. Power Syst. 2021, 45, 58–67. [Google Scholar]
- Ti, B.; Zhang, C.; Liu, J.; Wu, Z.; Huang, Z. Cyber-physical collaborative restoration strategy for power transmission system considering maintenance scheduling. CSEE J. Power Energy Syst. 2024, 10, 1331–1341. [Google Scholar]
- Liu, Y.; Feng, H.; Hatziargyriou, N.D. Multi-stage collaborative resilient enhancement strategy for coupling faults in distribution cyber physical systems. Appl. Energy 2023, 348, 121560. [Google Scholar] [CrossRef]
- Liu, X.; Ding, L.; Zhen, T.; Wu, J.; Li, Y. Analysis of cyber attack traceback techniques from the perspective of network forensics. J. Softw. 2021, 32, 194–217. [Google Scholar]
- Nizam, S.A.S.; Ibrahim, Z.-A.; Rahim, F.A.; Fadzil, H.S.; Abdullah, H.I.M.; Mustaffa, M.Z. Forensic analysis on false data injection attack on IoT environment. Int. J. Adv. Comput. Sci. Appl. IJACSA 2021, 12, 265–271. [Google Scholar] [CrossRef]
- Dosiek, L. Extracting electrical network frequency from digital recordings using frequency demodulation. IEEE Signal Process. Lett. 2015, 22, 691–695. [Google Scholar] [CrossRef]
- Berjawi, A.E.H.; Walker, S.L.; Patsios, C.; Hosseini, S.H.R. An evaluation framework for future integrated energy systems: A whole energy systems approach. Renew. Sustain. Energy Rev. 2021, 145, 111163. [Google Scholar] [CrossRef]
- Huang, X. A data-driven WSN security threat analysis model based on cognitive computing. J. Sens. 2022, 2022, 5013905. [Google Scholar] [CrossRef]
- Ma, H.; Wang, Y.; He, M. Collaborative optimization scheduling of resilience and economic oriented islanded integrated energy system under low carbon transition. Sustainability 2023, 15, 15663. [Google Scholar] [CrossRef]
- De La Torre Parra, G.; Rad, P.; Choo, K.-K.R. Implementation of deep packet inspection in smart grids and industrial internet of things: Challenges and opportunities. J. Netw. Comput. Appl. 2019, 135, 32–46. [Google Scholar] [CrossRef]
- Cui, Y.; Zhang, H.; Zhong, W. Day-ahead scheduling considering participation of price-based demand response and CSP plant in wind power accommodation. Power Syst. Technol. 2020, 44, 183–191. [Google Scholar]
- Dong, Y.; Wang, Q.; Cao, J. Identification of false data injection attacks in power grid based on oversampling and cascade machine learning. Autom. Electr. Power Syst. 2023, 47, 179–188. [Google Scholar]
- Correa-posada, C.; Sánchez-martín, P. Integrated power and natural gas model for energy adequacy in short-term operation. IEEE Trans. Power Syst. 2015, 30, 3347–3355. [Google Scholar] [CrossRef]
- Anand, H.; Narang, N.; Dhillon, J. Multi-objective combined heat and power unit commitment using particle swarm optimization. Energy 2019, 172, 794–807. [Google Scholar] [CrossRef]
- Zhou, S.; Hu, Z.; Gu, W. Combined heat and power system intelligent economic dispatch: A deep reinforcement learning approach. Int. J. Electr. Power Energy Syst. 2020, 120, 106016. [Google Scholar] [CrossRef]
- Qu, K.; Zhang, X.; Yu, T. Knowledge transfer based Q-learning algorithm for optimal dispatch of multi-energy system. Autom. Electr. Power Syst. 2017, 41, 18–25. [Google Scholar]
- Liu, F.; Bie, Z.; Wang, X. Day-ahead dispatch of integrated electricity and natural gas system considering reserve scheduling and renewable uncertainties. IEEE Trans. Sustain. Energy 2019, 10, 646–658. [Google Scholar] [CrossRef]
- Zhang, B.; Hu, W.; Cao, D. Deep reinforcement learning-based approach for optimizing energy conversion in integrated electrical and heating system with renewable energy. Energy Convers. Manag. 2019, 202, 112199. [Google Scholar] [CrossRef]
- Ye, Y.; Qiu, D.; Wu, X. Model-free real-time autonomous control for a residential multi-energy system using deep reinforcement learning. IEEE Trans. Smart Grid 2020, 11, 3068–3082. [Google Scholar] [CrossRef]
- Chen, H.; Kou, Y.; Zhou, L. Collaborative optimal dispatching mode and mechanism of watershed-type wind-solar-water multi-energy complementary bases for clean energy absorption. Electr. Power Autom. Equip. 2019, 39, 61–70. [Google Scholar]
- Li, J.; Zhu, M.; Lu, Y.; Huang, Y.; Wu, T. Review on optimal scheduling of integrated energy systems. Power Syst. Technol. 2021, 45, 2256–2272. [Google Scholar]
- Zeng, Q.; Fang, J.; Chen, Z.; Conejo, A.J. A two-stage stochastic programming approach for operating multi-energy systems. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–6. [Google Scholar]
- Guo, Z.; Li, G.; Zhou, M.; Feng, W. Two-stage robust optimal scheduling of regional integrated energy system considering network constraints and uncertainties in source and load. Power Syst. Technol. 2019, 43, 3090–3100. [Google Scholar]
- Alabdulwahab, A.; Abusorrah, A.; Zhang, X.; Shahidehpour, M. Coordination of interdependent natural gas and electricity infrastructures for firming the variability of wind energy in stochastic day-ahead scheduling. IEEE Trans. Sustain. Energy 2015, 6, 606–615. [Google Scholar] [CrossRef]
- Qadrdan, M.; Wu, J.; Jenkins, N.; Ekanayake, J. Operating strategies for a GB integrated gas and electricity network considering the uncertainty in wind power forecasts. IEEE Trans. Sustain. Energy 2014, 5, 128–138. [Google Scholar] [CrossRef]
- Li, Y.; Liu, W.; Shahidehpour, M.; Wen, F.; Wang, K.; Huang, Y. Optimal operation strategy for integrated natural gas generating unit and power-to-gas conversion facilities. IEEE Trans. Sustain. Energy 2018, 9, 1870–1879. [Google Scholar] [CrossRef]
- Wu, G.; Liu, J.; Xiang, Y.; Sheng, X.; Ma, Y. Day-ahead optimal scheduling of integrated electricity and natural gas system with medium- and long-term electricity contract decomposition and wind power uncertainties. Electr. Power Autom. Equip. 2019, 39, 246–253. [Google Scholar]
- Wang, C.; Gao, R.; Wei, W.; Shafie-khah, M.; Bi, T.; Catalão, J.P.S. Risk-based distributionally robust optimal gas-power flow with wasserstein distance. IEEE Trans. Power Syst. 2019, 34, 2190–2204. [Google Scholar] [CrossRef]
- Mitridati, L.; Pinson, P. Optimal coupling of heat and electricity systems: A stochastic hierarchical approach. In Proceedings of the 2016 International Conference on Probabilistic Methods Applied to Power Systems (PMAPS), Beijing, China, 16–20 October 2016; pp. 1–6. [Google Scholar]
- Good, N.; Karangelos, E.; Navarro, A.; Mancarella, P. Optimization Under Uncertainty of Thermal Storage-Based Flexible Demand Response With Quantification of Residential Users’ Discomfort. IEEE Trans. Smart Grid 2015, 6, 2333–2342. [Google Scholar] [CrossRef]
- Shui, Y.; Liu, J.; Gao, H.; Huang, S.; Jiang, Z. A distributionally robust coordinated dispatch model for integrated electricity and heating systems considering uncertainty of wind power. Proc. CSEE 2018, 38, 7235–7247+7450. [Google Scholar]
- Noor, M.; Jolan, R. A systematic review of ultra-lightweight encryption algorithms. Int. J. Nonlinear Anal. Appl. 2022, 13, 3825–3851. [Google Scholar]
- Zhu, L.; Peng, L.; Han, H.; Bao, X.; Gang, W.; Hou, Z.; Xu, M. Research on the Security of Unified Communications System’s Applications in the Power System. In Proceedings of the 2015 5th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Changsha, China, 26–29 November 2015; pp. 2475–2479. [Google Scholar]
- Sun, W.; Sun, H.; He, J.; Tu, J.; Zhang, G. Review of power system resilience assessment techniques for severe natural disasters. Power Syst. Technol. 2024, 48, 129–139. [Google Scholar]
- Quan, M.; Chen, Y. Analysis of evaluation system & mode of overseas resilient city. Hous. Sci. 2019, 39, 1–6. [Google Scholar]
- Chen, X.; Fan, Y.; Gong, X. Study on comprehensive evaluation index system for disaster prevention of urban ice-resistant secure power grid. Power Syst. Technol. 2019, 43, 3808–3815. [Google Scholar]
- Wang, J.; Yao, J.; Liu, Z.; Ouyang, J.; Xiong, X. Fault statistical analysis and probability distribution fitting for a power distribution network in adverse weather conditions. Power Syst. Prot. Control 2022, 50, 143–153. [Google Scholar]
- Li, Y.; Wang, Z.; Zhao, Q. Distributed fault section location for ADN based on bayesian complete analytic model and multi-factor dimension reduction. Power Syst. Technol. 2021, 45, 3917–3925. [Google Scholar]
- Li, X.; Sun, T.; Hou, K.; Jiang, T.; Chen, H.; Li, G.; Jia, H. Evaluating resilience of island integrated energy systems with earthquake. Proc. CSEE 2020, 40, 5476–5493. [Google Scholar]
- Zhang, H.; Wang, P.; Yao, S.; Liu, X.; Zhao, T. Resilience assessment of interdependent energy systems under hurricanes. IEEE Trans. Power Syst. 2020, 35, 3682–3694. [Google Scholar] [CrossRef]
- Peng, H.; Hu, L.; Tan, M.; Li, J.; Su, Y. Decision-making method for electricity-gas region integrated energy system security correction based on deep reinforcement learning. Power Syst. Technol. 2024, 48, 1019–1029. [Google Scholar]
- Chen, L.; Deng, X.; Chen, H.; Shi, J. Review of the assessment and improvement of power system resilience. Power Syst. Prot. Control 2022, 50, 11–22. [Google Scholar]
- Zhao, Q.; Du, Y.; Zhang, T. Resilience index system and comprehensive assessment method for distribution network considering multi-energy coordination. Inter. Journal Elect. Power Energy Syst. 2021, 133, 107211. [Google Scholar] [CrossRef]
- Bajpai, P.; Chanda, S.; Srivastava, A. A novel metric to quantify and enable resilient distribution system using graph theory and Choquet integral. IEEE Trans. Smart Grid 2018, 9, 2918–2929. [Google Scholar] [CrossRef]
- Peng, H.; Li, C.; Liu, J.; Su, Y.; Tan, M. Resilience assessment of electricity-gas regional integrated energy system based on heterogeneous interdependent network. Power Syst. Technol. 2021, 45, 2811–2820. [Google Scholar]
- Wang, H.; Hou, K.; Liu, X.; Yu, X.; Jia, H.; Du, J. Resilience enhancement method for electricity-gas interconnection system based on global sensitivity analysis. Autom. Electr. Power Syst. 2023, 47, 59–67. [Google Scholar]
- Nan, C.; Sansavini, G. A quantitative method for assessing resilience of interdependent infrastructures. Reliab. Eng. Syst. Safe. 2017, 157, 35–53. [Google Scholar] [CrossRef]
- Bie, C.; Lin, C.; Li, G.; Qiu, A. Development and prospect of resilient power system in the context of energy transition. Proc. CSEE 2020, 40, 2735–2745. [Google Scholar]
- Huang, W.; Wu, J.; Guo, Z. Power grid resilience assessment and differentiated planning against typhoon disasters. Autom. Electr. Power Syst. 2023, 47, 84–91. [Google Scholar]
- Huang, Y. Resilience Assessment and Improvement Strategy Analysis of Multi-Agent and Decentralized Decisionmaking Energy Interconnection System. Master’s Thesis, North China Electric Power University, Beijing, China, 2022. [Google Scholar]
- Cui, H.; Xue, T.; Wang, Q.; Tang, Y. The Poisoning Attack and Detection Shemes for AI Algorithms in Power Systems. Power Syst. Technol. 2024, 48, 5024–5033. [Google Scholar]
- Zhou, B.; Cai, Y.; Zang, T.; Wu, J.; Li, X.; Dong, S. Reliability optimization method for gas-electric integrated energy systems considering cyber-physical interactions. Energies 2023, 16, 5187. [Google Scholar] [CrossRef]
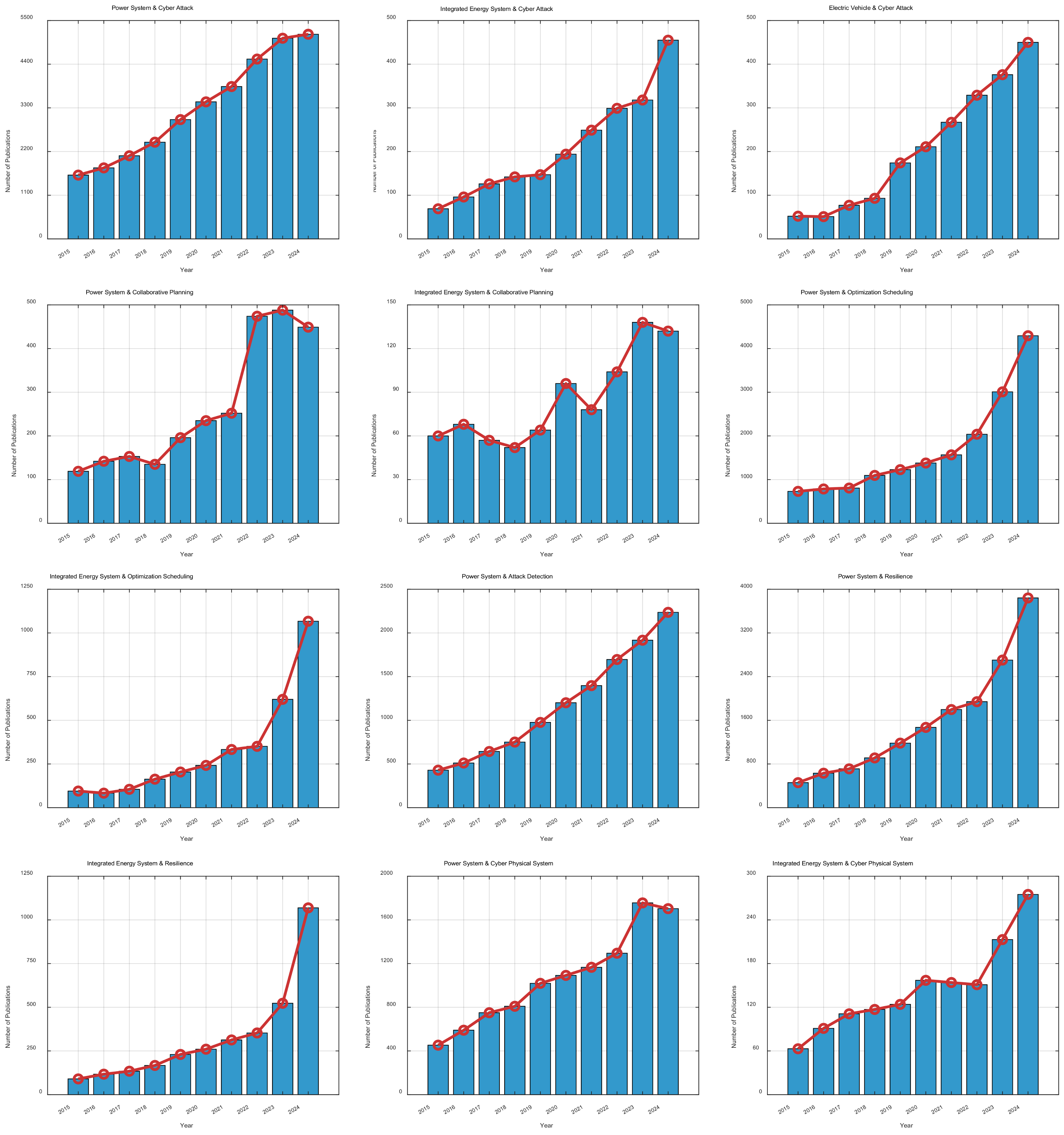



| Year | Target of Attack | Attack Method | Result | Ref. |
|---|---|---|---|---|
| 2015 | Electricity Company of Ukraine | Blank Energy malware | A major power outage that lasted several hours | [7] |
| 2020 | Light S.A. Electricity Company, Brazil | Sodinokibi ransomware | Extortion of USD 14 million. | [10] |
| 2020 | EDP Energy, Portugal | Ragnar Locker ransomware | Extortion of USD 10.9 million | [11] |
| 2021 | Colonial Pipeline, USA | - | All pipelines stopped and some services shut down | [12] |
| 2022 | High voltage substations in Ukraine | Industroyer2 malware | Stopped before causing an actual accident | [13] |
| 2023 | Acea, Italy | Black Basta ransomware | Web service crash | [14] |
| Type | Target | Ref. |
|---|---|---|
| General FDIA | State estimator | [23] |
| Energy market | [24] | |
| RTU | [25] | |
| AGC | [26,27,28,29,30,31,32,33] | |
| Load redistribution attack | Power system | [34,35,36] |
| Weather forecast system | [37,38] | |
| Integrated energy system | [39] | |
| False topology attack | DC power flow model | [40,41,42] |
| AC power flow model | [43,44] |
| Attack Targets | Modeling Methods | Cyberattack | Ref. | ||||||
|---|---|---|---|---|---|---|---|---|---|
| RA | MITM | FDIA | TSA | DoS | Time Delay Attack | Soft Intrusion | |||
| AGC | Optimization model | √ | √ | [58] | |||||
| Integrated power and gas system | √ | [59] | |||||||
| Integrated power and gas system | √ | [60] | |||||||
| Integrated heat and electric system | √ | [61] | |||||||
| Power system | √ | √ | [62] | ||||||
| AGC | Deep reinforcement learning | √ | √ | [63] | |||||
| Microgrid | Deep neural network | √ | √ | [64] | |||||
| Power system | Attack graph model | √ | √ | [65] | |||||
| Power system | Heuristic algorithm | √ | √ | [66] | |||||
| System | Methods | Multi-Stage Model | Data Driven | Ref. | |
|---|---|---|---|---|---|
| Stochastic Optimization | Robust Optimization | ||||
| Electric–Heat–Gas Integrated System | √ | √ | [201] | ||
| √ | √ | [202] | |||
| Integrated power and gas system | √ | √ | [203,204] | ||
| √ | [205] | ||||
| √ | [206] | ||||
| √ | √ | [207] | |||
| Integrated heat and electric system | √ | √ | [208,209] | ||
| √ | √ | √ | [210] | ||
| Indicator Categories | Indicators | Evaluation Object | Ref. |
|---|---|---|---|
| System structure-based indicators | Node degree, node betweenness, weighted node degree of betweenness, connectivity | Power system | [222] |
| Distribution line strength | Distribution network | [223] | |
| Number of common branches, number of switch operations, path redundancy ratio, equipment availability | Power system | [224] | |
| Component redundancy | Integrated energy system | [225] | |
| System performance-based indicators | Load loss expectation | Integrated energy system | [219] |
| Load recovery rate | Power System | [226] | |
| Performance curve integral area | Power system | [227] | |
| Maximum loss of important loads, load recovery rate | Power system | [228] | |
| Load loss duration | Integrated energy system | [229] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zang, T.; Tong, X.; Li, C.; Gong, Y.; Su, R.; Zhou, B. Research and Prospect of Defense for Integrated Energy Cyber–Physical Systems Against Deliberate Attacks. Energies 2025, 18, 1479. https://doi.org/10.3390/en18061479
Zang T, Tong X, Li C, Gong Y, Su R, Zhou B. Research and Prospect of Defense for Integrated Energy Cyber–Physical Systems Against Deliberate Attacks. Energies. 2025; 18(6):1479. https://doi.org/10.3390/en18061479
Chicago/Turabian StyleZang, Tianlei, Xiaoning Tong, Chuangzhi Li, Yahui Gong, Rui Su, and Buxiang Zhou. 2025. "Research and Prospect of Defense for Integrated Energy Cyber–Physical Systems Against Deliberate Attacks" Energies 18, no. 6: 1479. https://doi.org/10.3390/en18061479
APA StyleZang, T., Tong, X., Li, C., Gong, Y., Su, R., & Zhou, B. (2025). Research and Prospect of Defense for Integrated Energy Cyber–Physical Systems Against Deliberate Attacks. Energies, 18(6), 1479. https://doi.org/10.3390/en18061479







