1. Introduction
The low-voltage distribution platform area composed of transformers, storing the energy produced by wind generators and solar, loads, and other new energy sources is not only the core part of the power distribution network but also a part of the new integrated energy system (IES) [
1]. The performance of a station area, where high-voltage power is converted to low-voltage power using a transformer and distributed to end-users, has a direct impact on the stability and safety of electricity consumption. Therefore, safety analysis is a key factor that must be emphasized in the planning and operation of low-voltage power stations. Traditionally, a single transformer and a single supply circuit were used to supply power to a station area, which resulted in a fragile grid structure. To solve this problem, most of the current interconnections are made to improve the reliability of the power supply by cutting peaks and filling valleys with each other. However, this interconnection method also increases the risk of system operation [
2].
The stable operation of the system cannot be guaranteed without safety. Although there are mature safety analysis methods for a single low-voltage substation system, the safety analysis of LVDSs, as a key component of the integrated energy system, is more complex. It is not only necessary to ensure the safe operation of a single LVDS, but also to consider the security challenges that may be brought about by the interaction of different LVDSs. At present, the safety analysis of low-voltage distribution substations mainly adopts the point-by-point method [
3], which has obvious limitations in practice, such as the need to carry out time-consuming multi-energy flow calculations before each safety calibration, which cannot meet the needs of real-time online safety analysis. At the same time, the method is also unable to provide the complete operating range and safety boundaries of LVDS platforms, thus failing to provide dispatchers and market participants with key information such as comprehensive assessment and adjustable margins on work point safety. Therefore, research on the safety of LVDSs is still in its infancy, and there is an urgent need to develop more efficient and comprehensive safety analysis methods to achieve a unified analysis of substation safety from a comprehensive perspective [
4].
The safety domain approach demonstrates significant advantages over the point-by-point approach in the safety analysis of integrated energy systems [
5]: first, it significantly improves the efficiency of online safety analysis by pre-completing complex processes such as energy flow calculation in the offline stage, making real-time assessment possible; second, the safety domain approach can determine the safety margin of the system by measuring the distance between the working point and the safety boundary, providing a quantitative safety index for the system operation provides a quantitative safety index [
6]; finally, this method can provide comprehensive safety information of the system, which helps to realize the comprehensive perception of the system posture and take proactive preventive and control measures, thus enhancing the system’s ability to cope with potential risks [
4].
Inspired by the Electric Power System Security Domain (EPS-SR), researchers have begun to explore the integrated energy system (IES) security region (IES-SR). Among them, Ref. [
7] focuses on the N-1 safety criterion for IESs; Ref. [
8] introduced the concept of IES-SR and the corresponding modeling framework for the first time, and subsequent studies further developed and improved on this basis; Ref. [
9] proposed a robust security region (RSR) for an electric–gas IES. Ref. [
10] explores the dual time-scale characterization of IESs and establishes conditions that allow for the decomposition of IESs into fast and slow subsystems, to facilitate the construction of their accurate steady-state safety zones. Ref. [
11] proposes a novel and robust computational scheme to compute the steady-state safety zones of IESs, and demonstrates the elimination of the estimation errors of existing methods. Ref. [
12] proposes a new approach to the RIES optimal control problem that minimizes the control cost and the amount of adjustment while maximizing the safety and efficiency. Meanwhile, there is an equivalent hyperplane method proposed in [
13] to solve the SSR model. These studies provide multiple perspectives for the understanding of IES-SR and promote the theoretical development and practical applications in this field. Ref. [
14] proposes the IES-SR pragmatic security boundary model with a downscaling observation method. Ref. [
15] performs a bottleneck analysis based on the pragmatic security boundary model for secure IES-SR operation. Ref. [
16] proposes a secure domain model for IES-SRs with renewable energy sources and optimal control of the operating points.
IES-SR research has progressed, but challenges remain. Most of the existing IES-SR models are based on nonlinear energy flow equations for heterogeneous energy systems, leading to diverse and complex solution methods [
17]. These models are especially computationally demanding when dealing with high-dimensional IES-SR problems. A lot of resources will be consumed if the efficiency of solving the models is not emphasized. Therefore, it is imperative to improve the efficiency of IES-SR model solving. Therefore, in this paper, a LVDS-SR modeling method based on the high-dimensional safety domain definition method is proposed with the LVDS system as the research object. The general mathematical model, edge points, and safety boundaries of the station area system are solved accurately to obtain the safety domain model.
The rest of this paper is organized as follows.
Section 1 summarizes the problems and state-of-the-art approaches of existing safety domain modeling methods.
Section 2 defines the concepts related to the safety domain of a low-voltage distribution substation station.
Section 3 establishes a mathematical model of the bench area that contains the circuit part and the air circuit part.
Section 4 solves the safety domain of the LV distribution substation area using the high-dimensional safety domain definition method proposed in this paper.
Section 5 performs an arithmetic example analysis to validate the method proposed in this paper.
Section 6 summarizes the paper.
The main contributions of this paper are as follows:
- 1.
Definition of concepts: This paper defines the concepts of safe working points, security boundaries, and security regions. These concepts provide a theoretical basis for subsequent analysis and modeling.
- 2.
The solution results are more accurate: In this paper, the general mathematical model, edge points, and security boundaries of the table system are solved exactly.
- 3.
Advanced modeling methods are proposed: This paper presents a security domain (LVDS-SR) modeling method based on a high-dimensional security domain definition. The method can obtain a more accurate model and more efficient solution compared to the traditional modeling method.
2. Definition of LVDS-SR Related Concepts
2.1. Definition of Safe Working Points
The operating point is the specific set of values corresponding to the operating parameters of each electrical component of a power system in a particular operating state. It represents the safety of the system in a particular state [
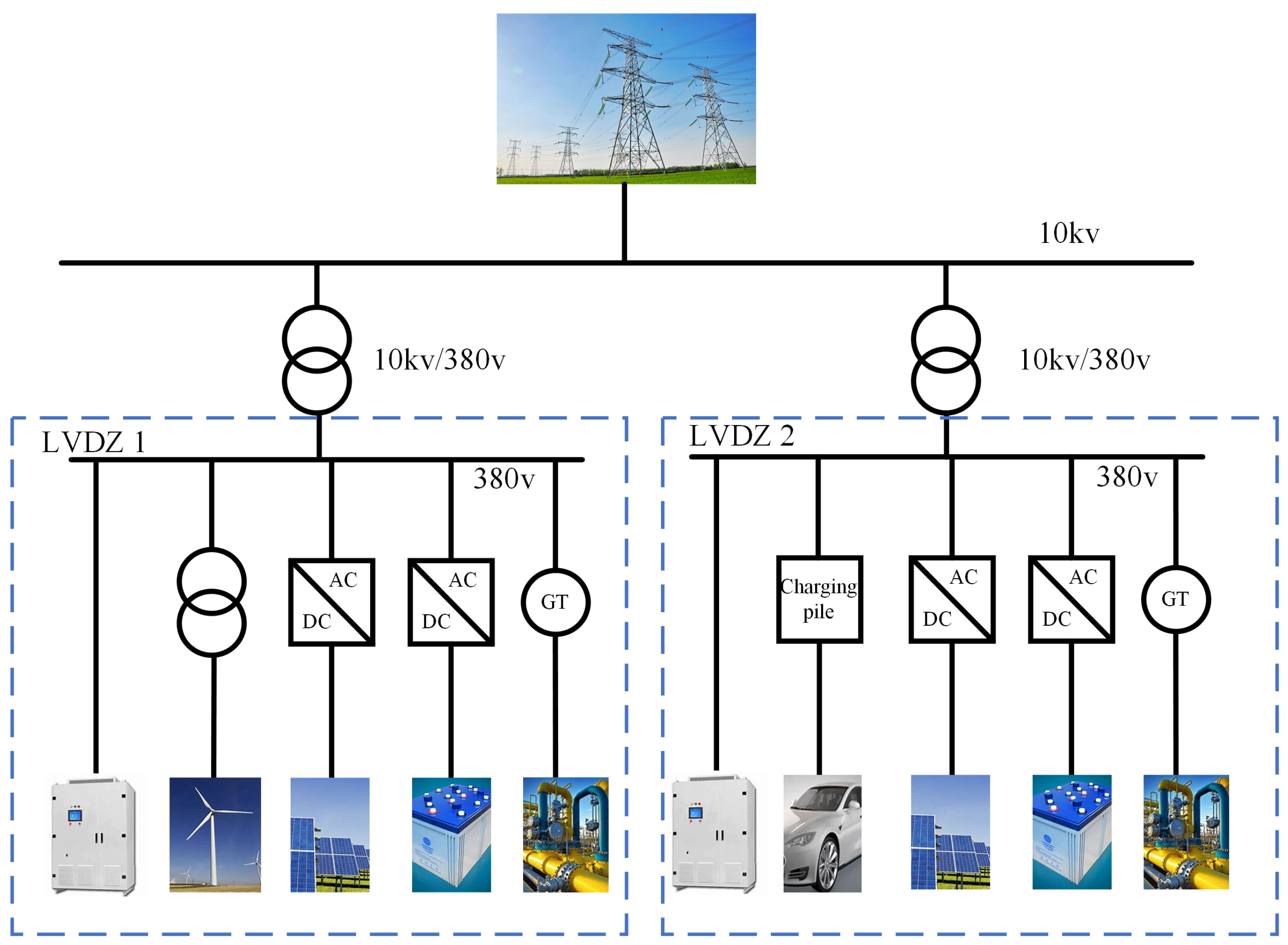
18]. In a low-voltage distribution substation systems, loads represent energy demands. The power supply acts as the supply side and is responsible for meeting these demands. In this way, the system can guarantee safe operation. The operating point of the system is defined by key variables such as load, which are the basis for assessing the safety of the system. The structure of a low-voltage distribution substation station is shown in
Figure 1. There are several types of energy sources included in modern bench systems, for example, wind energy, photovoltaic energy, natural gas, and energy storage.
There are two types of energy sources in the station: electricity and natural gas. In this paper, the liaison between the two is established through coupled units: the natural gas compressor serves as an electrical load, which is supplied with driving power by the electrical system part, and the gas turbine (GT) serves as a natural gas load, which receives the input flow from the natural gas network [
19]. Therefore, in this paper, the operating point is denoted as
where
is the nodal power of the power type load;
is the flow rate of natural gas;
i,
j is the number of nodes;
is the power consumed by the compressor;
is the flow rate of natural gas consumed by the gas generator at node
j.
2.2. Definition of Security
The LVDS studied in this paper can be considered part of an integrated energy system. Therefore, we define the safety of the low-voltage distribution substation (LVDS) as follows: the system is considered to be safe under a particular work point if all state quantities at that work point meet the constraints of operation. Such a work point is called a safe work point and is symbolized by . On the contrary, if there exists any state quantity that does not satisfy the operational constraints, the work point is considered unsafe. In short, whether a work point is safe or not depends on whether all of its state quantities meet the established operational constraints.
2.3. Definition of Security Region
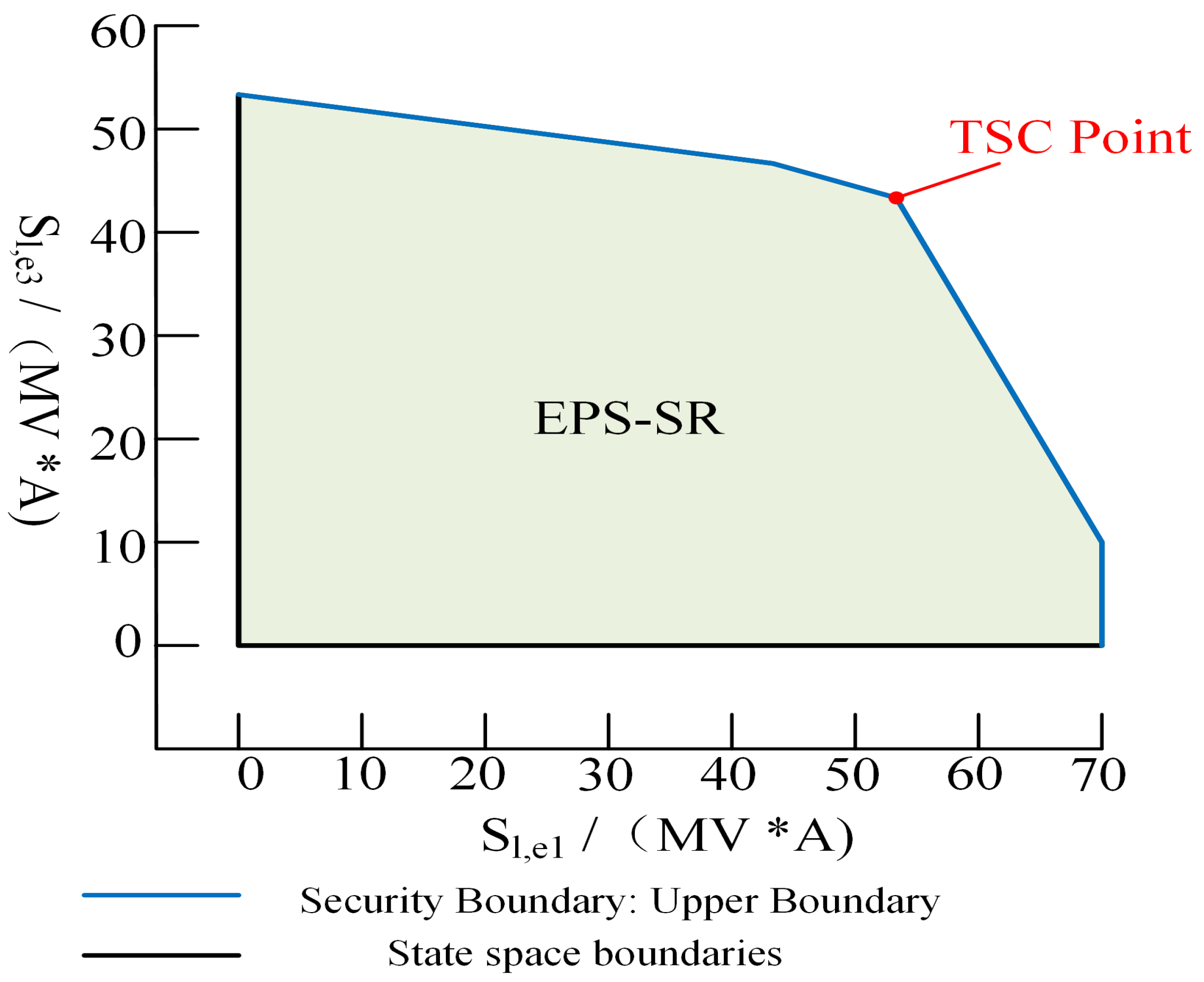
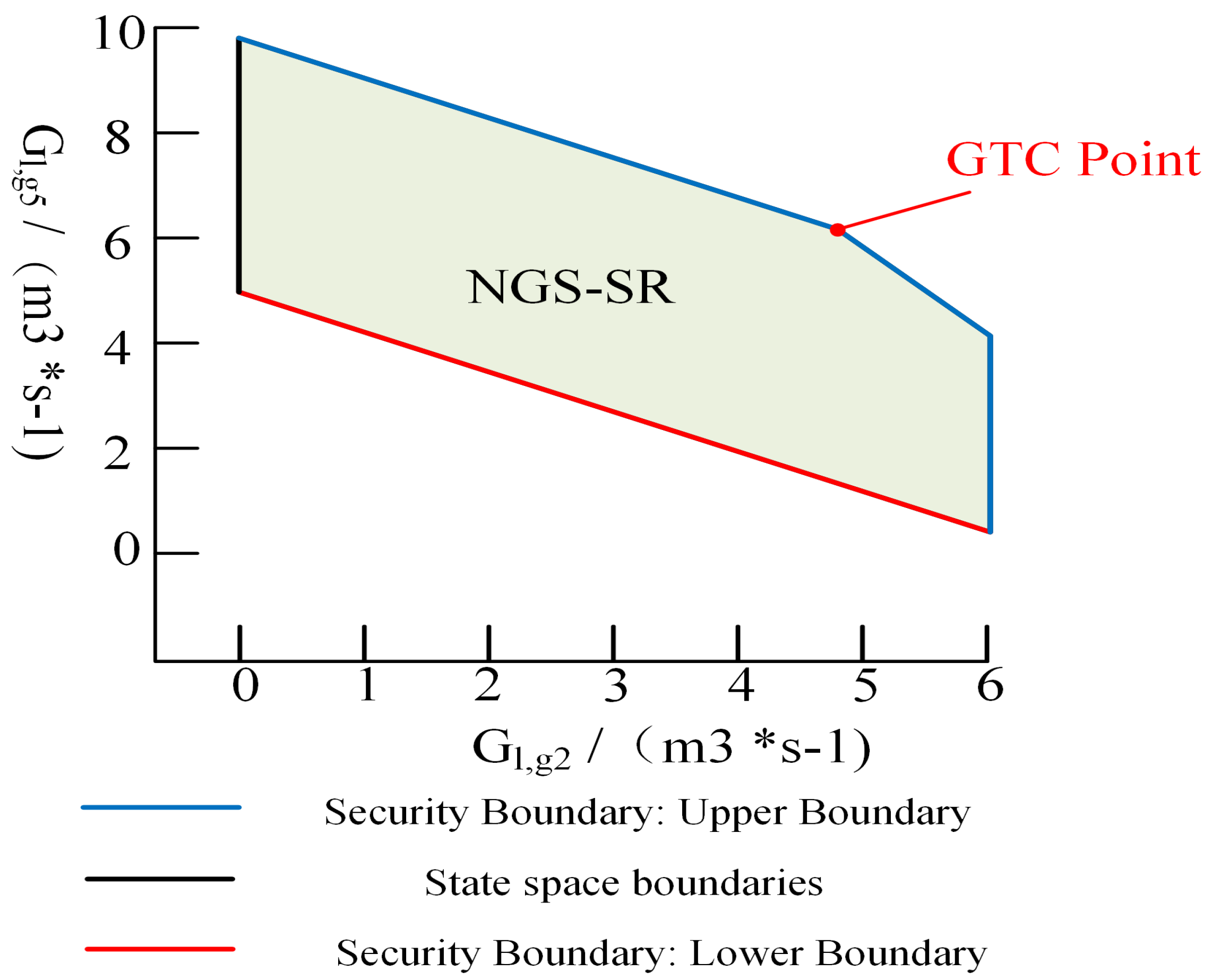
LVDS-SR is defined as the set of all safe operating points during LVDS running, denoted by . The LVDS-SR is a closed region in the state space and consists of the EPS-SR and the NGS-SR. The safe boundary of the LVDS is defined as the set consisting of all critical points in the LVDS-SR, denoted by . In this paper, total supply capability (TSC) and gas transmission capability (GTC) are used to measure the maximum supply potential of the LVDS during safe operation. The TSC and GTC points correspond to the operating states when the LVDS power supply and gas delivery are maximized, and they are the efficient working points in the LVDS-SR. Whether the work points are located in the safety domain is the key criterion to judge their safety. If the work point is located within the security domain, then the system is in a safe operating state. Conversely, if the work point is not within the security domain, then the system is at a security risk.
The specific location of work points within the safety domain also indicates the amount of safety margin. Using the security domain, grid operators can visually assess the current level of security of the system, clearly identifying how much system security margin is available in all directions, which enables them to make quick and accurate decisions about preventive measures or responses to emergencies. With this intuitive display of security status, dispatchers can manage the grid more effectively to ensure the reliability and security of the power supply.
4. Security Region Solving
4.1. Difficulties and Solution Ideas
The difficulty of solving the security domain increases with the high dimensionality of the LVDS work points since the LVDS-SR of the IES presents itself as a complex hyperpolyhedral shape in the high-dimensional state space. This leads to two main problems:
One is that it is difficult to directly observe and completely represent the security boundary of the LVDS-SR in high-dimensional space, and in particular, it is difficult to determine the cutoff point of the boundary curvature change, which is crucial for the accurate fitting of the boundary.
Secondly, with an increase in the dimension of the security domain, the number of work points to be verified increases dramatically, and it will be extremely time-consuming to continue to use the traditional multi-energy flow computation method to verify the security of each work point.
In this paper, the solutions to the above difficulties are as follows:
- (1)
Difficulty 1: This paper proposes a method for fitting security boundary expressions applicable to high-dimensional state-space security domains. The method can automate the determination of the partition point by measuring the distance between the boundary point and the hyperplane. In addition, the fitting method does not need to obtain the partition where the security boundary undergoes curvature change by observation.
- (2)
Difficulty 2: In this paper, a mathematical model is used to compute multiple energy flows instead of the complex energy flow equations in heterogeneous energy systems. This approach saves computational resources by reducing the need for repeated iterative solving of nonlinear equations.
4.2. Specific Steps of the Solution Method
Based on the above method, we obtain complete security domain results for high-dimensional LVDS-SRs. These results include security boundary points and security boundary expressions obtained by fitting. The specific process is as follows: firstly, mathematical model solving is carried out to obtain the complete state quantities of the working points, which is the basis of boundary point solving; secondly, boundary point solving is carried out to find the working points that satisfy the critical security; finally, the security boundary expression is obtained through the fitting of the security boundary.
4.2.1. Mathematical Model Solution
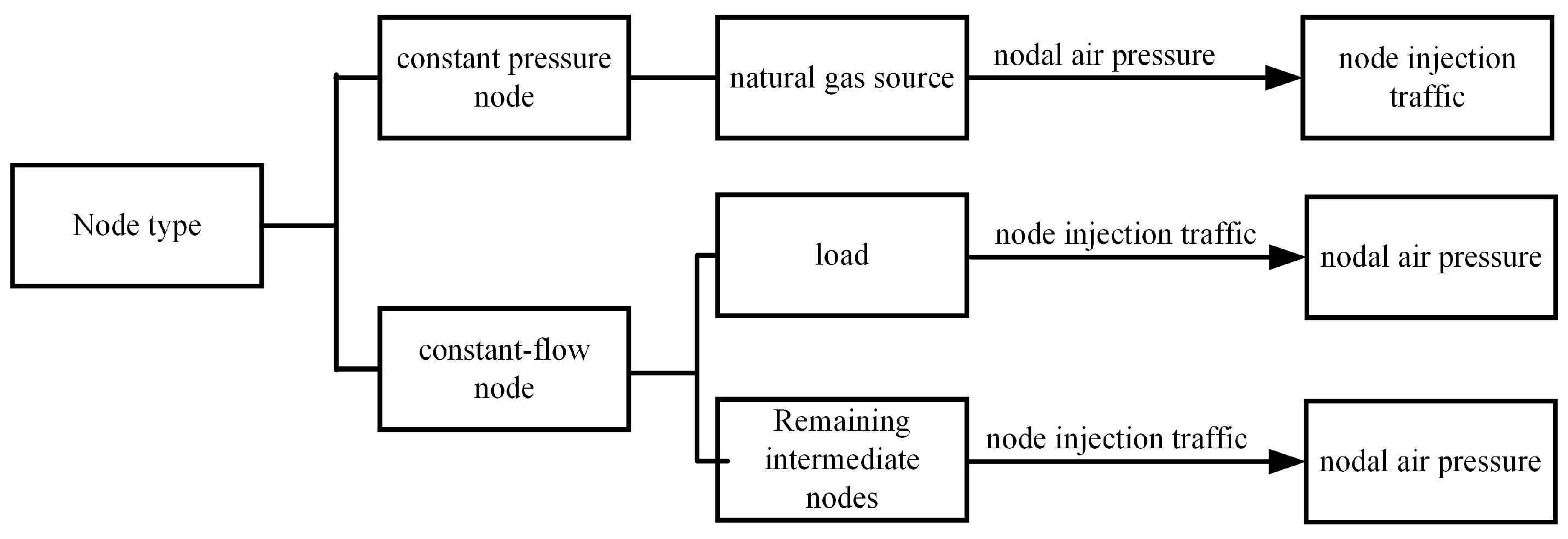
The nodes of the natural gas part can be divided into constant-pressure nodes and constant-flow nodes, as shown in
Figure 2. Next, the mathematical model of Equation (
9) is rearranged by node type to obtain
where
is the nodal air pressure at a constant-pressure node and
is the injected flow rate.
is the nodal air pressure at a constant-flow node and
is the injected flow rate.
,
,
and
are obtained by rearranging the generalized nodal conductivity matrix
for natural gas systems. The purpose of this rearrangement is to divide the matrix into different sub-matrices based on the type of nodes.
Finally,
and
can be solved from Equation (
12) as follows:
Mathematical model of the coupling part.
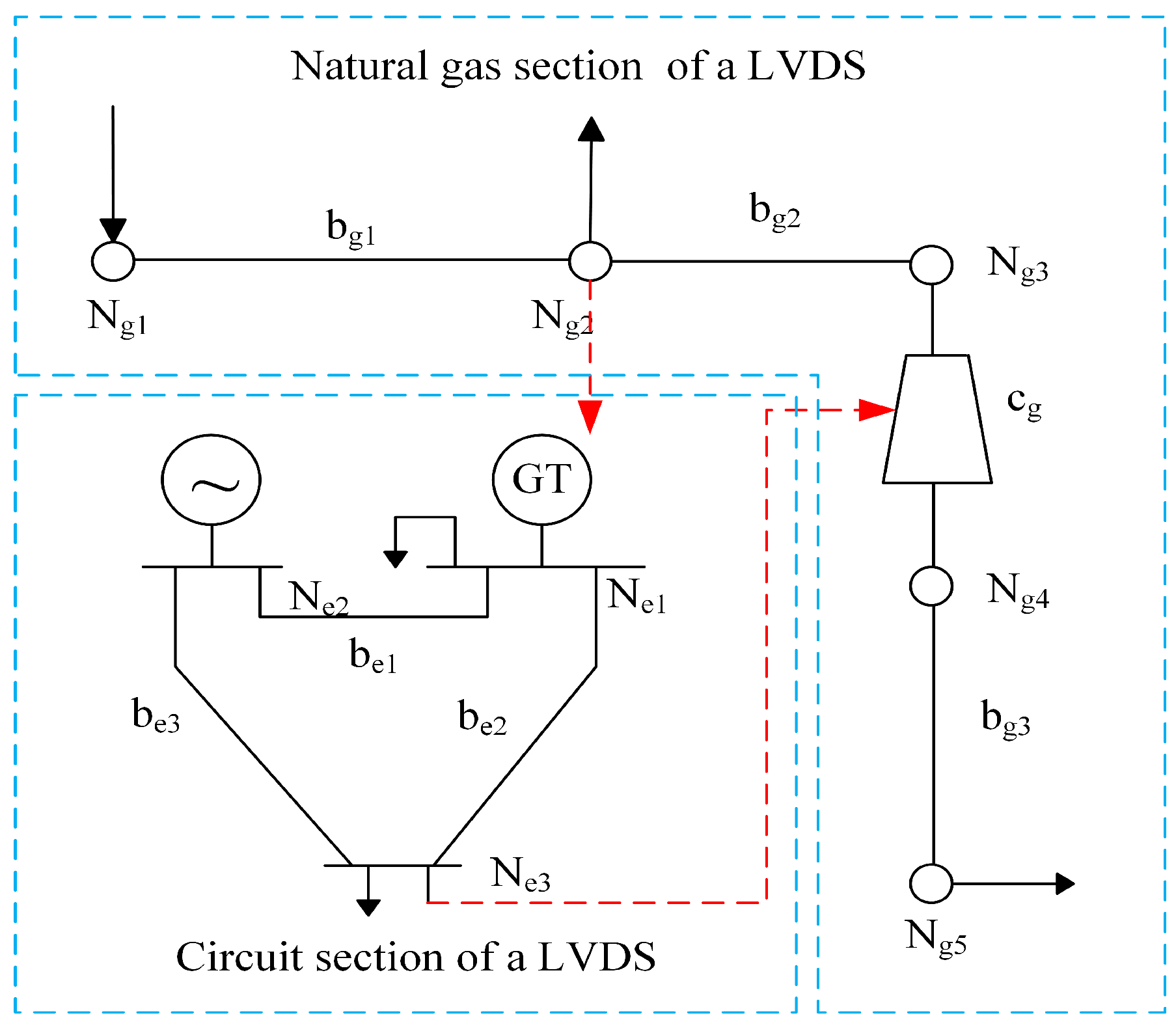
First, based on the energy flow relationship, the nodes where the coupling units in the LVDS are located are categorized as shown in
Figure 3.
Subsequently, the natural gas mathematical model is solved based on the node division of the coupling unit in the natural gas network in order to obtain detailed state information on the natural gas system.
Finally, based on the coupled unit constraint equations in (14), the required state quantities of the coupled unit are calculated to solve the power system mathematical model, thus realizing the transfer of energy parameters between different energy systems.
4.2.2. Boundary Point Solving
There is a gas-path-based NGS-SR solving method proposed in [
4], which uses the bisection method to solve for the boundary points by iteratively correcting the working points to the boundary points. In this paper, the method is used to solve LVDS-SR boundary points. When solving, any element of the working point is selected for correction, and the rest of the elements are sampled at equal intervals; at the same time, in order to facilitate the subsequent fitting of the security boundary, it is necessary to ensure that the number of boundary points obtained is not less than the number of security domain dimensions.
4.2.3. Safety Boundary Fitting
The LVDS-SR is a closed region in N-dimensional state space. When N > 3, the reduced-dimensional view of the domain and the corresponding boundary expression are often obtained by 2D/3D observation, but the reduced dimensionality can only reflect the local information of the LVDS-SR. The boundary points are N-dimensional, reflecting the LVDS-SR’s global information, but the boundary points are discrete in the state space, and the relative expressions are not easy to use. For this reason, this paper proposes a fitting method that can solve the security boundary expression of a high-dimensional LVDS-SR.
Analogous to the power system [
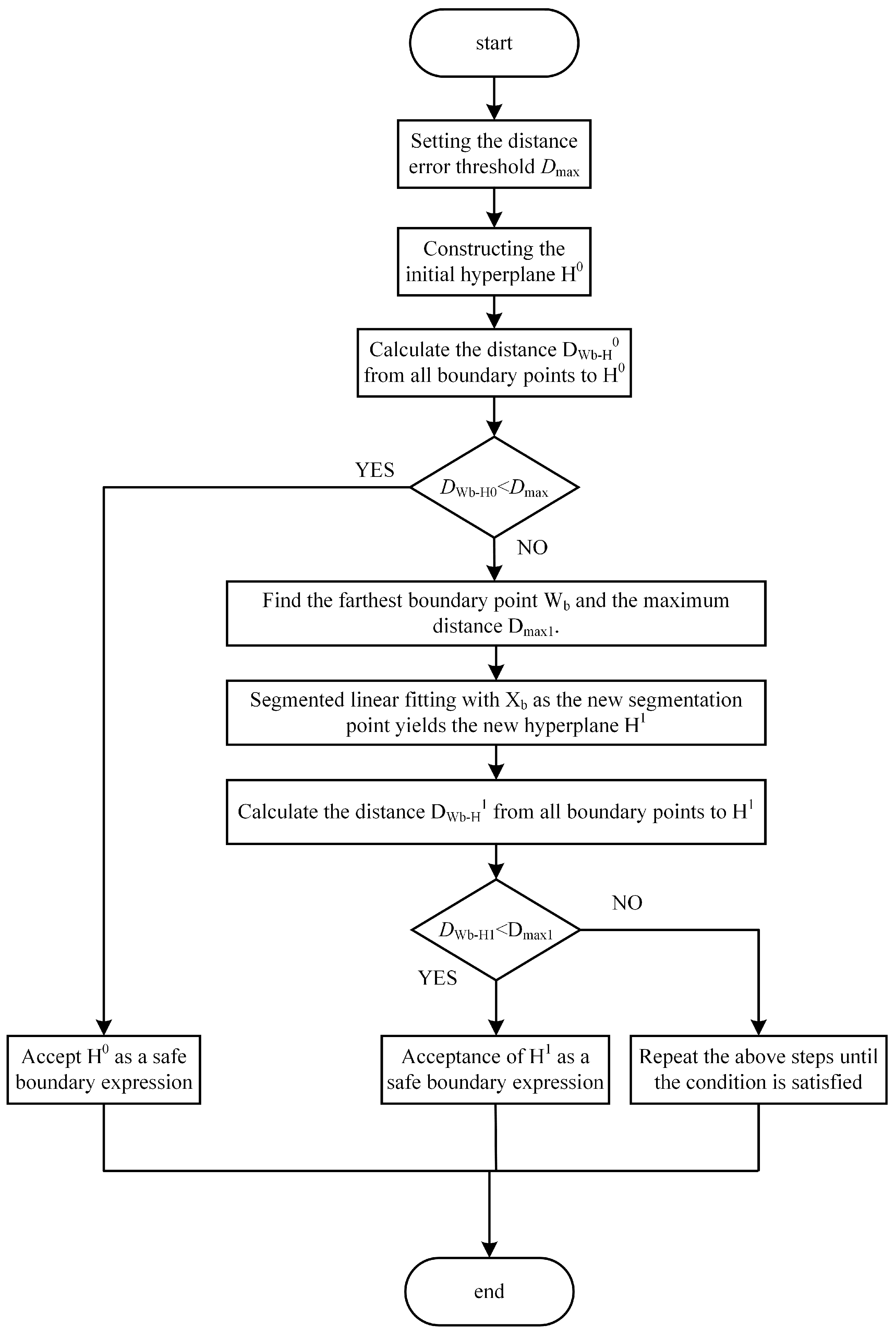
22], a set of hyperplanes are used to inscribe the security boundary of the LVDS-SR, and a segmented linearization method is used to fit the hyperplanes. It is difficult to find suitable segment points between hyperplanes in high-dimensional space. This is because it is difficult to directly observe the segmentation where the boundary undergoes a large curvature change in the high-dimensional space. It calculates the distance from the boundary points to the hyperplane to achieve the automatic solution of the segmentation points. The program algorithm is specified in
Figure 4:
The specific fitting steps are as follows:
- (1)
Set the threshold of distance error . represents the upper limit of the distance from all boundary points to the fitted hyperplane during the fitting process. It represents the fitting accuracy of hyperplanes and the end conditions of piecewise fitting.
- (2)
Construct the initial hyperplane. First, in order to improve the fitting efficiency, the number of fitting iterations should be minimized on the basis of ensuring accuracy. Therefore, for the initial hyperplane fitted for the first time, N linearly irrelevant boundary points with the largest possible coverage domain range are selected for fitting. The initial hyperplane equations are as follows:
where
is the initial hyperplane equation;
,
are the fitting coefficients of
, which can be calculated from the boundary points selected in the fitting;
is the variable of
corresponding to the work point element; and N is the dimension of the LVDS-SR.
Next, the distance from each boundary point to
is calculated. For the boundary point
, the distance
from
to
is
where
is the vector of
;
is the 2-parameter of
. Finally, record the boundary point
with the farthest distance to
among all boundary points; the corresponding distance is recorded as
, and judge whether
satisfies the fitting accuracy: if
, then the accuracy is satisfied, and
is the final boundary expression; otherwise, take
as a segmentation point, and group the boundary points selected when fitting
for segmentation fitting.
- (3)
Segmented linear fitting. The steps in the kth segmented fitting are as follows. First, for the selected boundary points, if the linear irrelevance condition is satisfied, hyperplanes of the form shown in (15) are fitted into hyperplanes by grouping, and a total of M hyperplane equations are obtained.
Next, the distance from the boundary point Wb to each hyperplane is calculated according to (16), and the smallest value is taken:
where
is the minimum distance from
to all hyperplanes;
is the distance from
to hyperplane
.
Finally, calculate of all boundary points, take the maximum value of it, denoted as , and the corresponding boundary point is denoted as . Judge whether the kth segmented fitting meets the fitting accuracy: if , then it meets the accuracy, and all the distances from the boundary points to the hyperplane are within the error range, so that we can obtain the final safety boundary, and the safety boundary-fitting process is ended; otherwise, take as the segmentation point, group the boundary points selected in the kth segmentation fitting, obtain N new hyperplanes, and continue the k+1th segmentation fitting. It should be noted that for the N-dimensional security domain, the uniqueness of the hyperplane fitting result is guaranteed by the fact that N linearly independent boundary points are selected for each of its hyperplane fittings.