A Feasible Region-Based Evaluation Method for the Renewable Energy Hosting Capacity with Frequency Security Constraints
Abstract
1. Introduction
- The evaluation process incorporates frequency security constraints, including the frequency change rate, steady-state frequency deviation, frequency standby, and frequency nadir point. The polynomial chaos expansion (PCE) theory is employed to address the challenging frequency nadir constraint by integrating the step-response integral. This technique fulfils the intricate demands of power systems.
- An evaluation model is constructed to accurately quantify the promotional effect of various flexible resources, such as demand response (DR), energy storage, thermal storage, Combined Heat and Power units (CHP), and Power-to-Gas units (P2G), on the hosting capacity of renewable energy.
- Using progressive vertex enumeration, a safe area is formed for the viable output of renewable energy. This is achieved while ensuring that the security restrictions for power grid operation are met. The construction takes into account the coupling correlation characteristics of the renewable energy units. This guarantees that the system can accommodate renewable energy in a manner that is safer, more adaptable, and more dependable.
2. Analytical Method for Characterizing System Dynamic Frequency Constraints
2.1. Maximum RoCoF Constraints
2.2. Steady-State Frequency Deviation Constraints
2.3. Constructing Frequency Nadir Constraints Based on Polynomial Chaos Expansion
3. Evaluation Model for Renewable Energy Hosting Capacity with Frequency Security Constraints Considering Multiple Types of Flexible Resources
3.1. Objective Function
3.2. Constraints
3.2.1. Flexible Resource Operation Constraints
- Constraints of DR
- 2.
- Constraints of CHP and thermal storage systems
- 3.
- Constraints of energy storage systems
- 4.
- Constraints of P2G
- 5.
- Constraints of thermal power units
3.2.2. Other Operation Constraints
- 6.
- Renewable energy output constraints
- 7.
- Branch flow constraints
- 8.
- Total power balance constraint
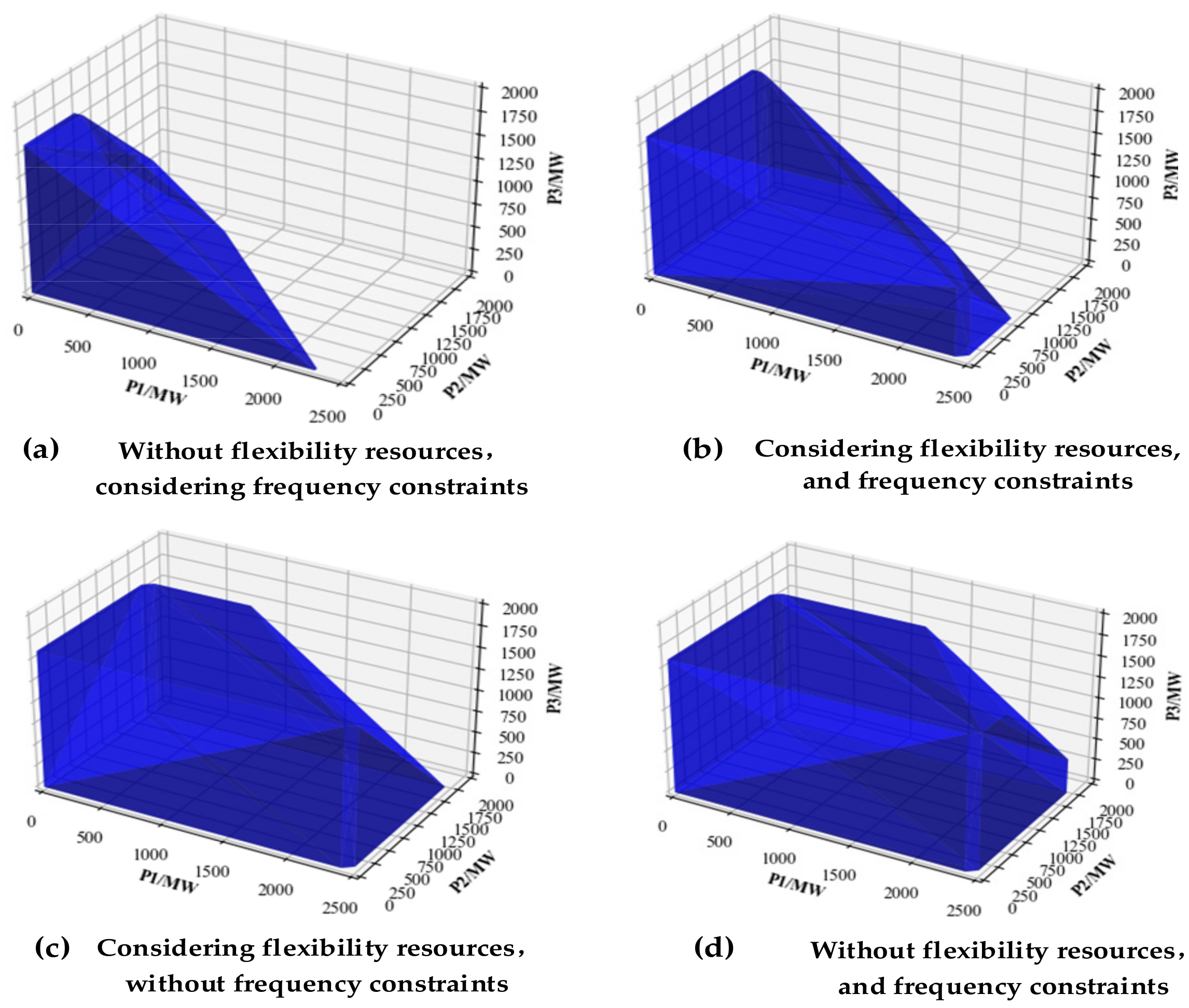
4. The Feasible Region of the Renewable Energy Hosting Capacity
4.1. Definition of Feasible Region of Renewable Energy Hosting Capacity
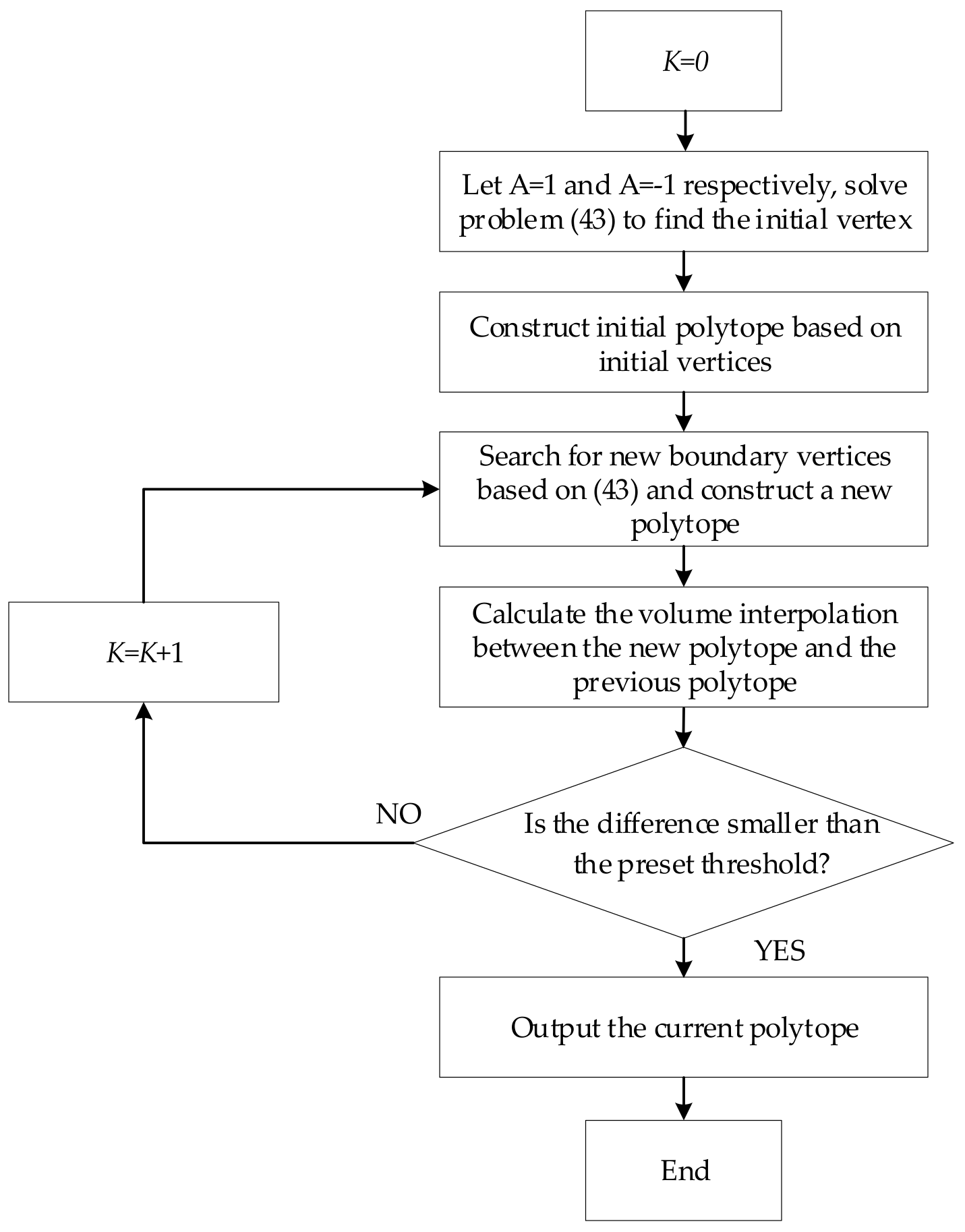
4.2. The Progressive Vertex Enumeration Method to Determine the Feasible Region of the Renewable Energy Hosting Capacity
- Constructing an initial polytope
- 2.
- Updating the polytope iteratively
- 3.
- Iterative convergence criterion
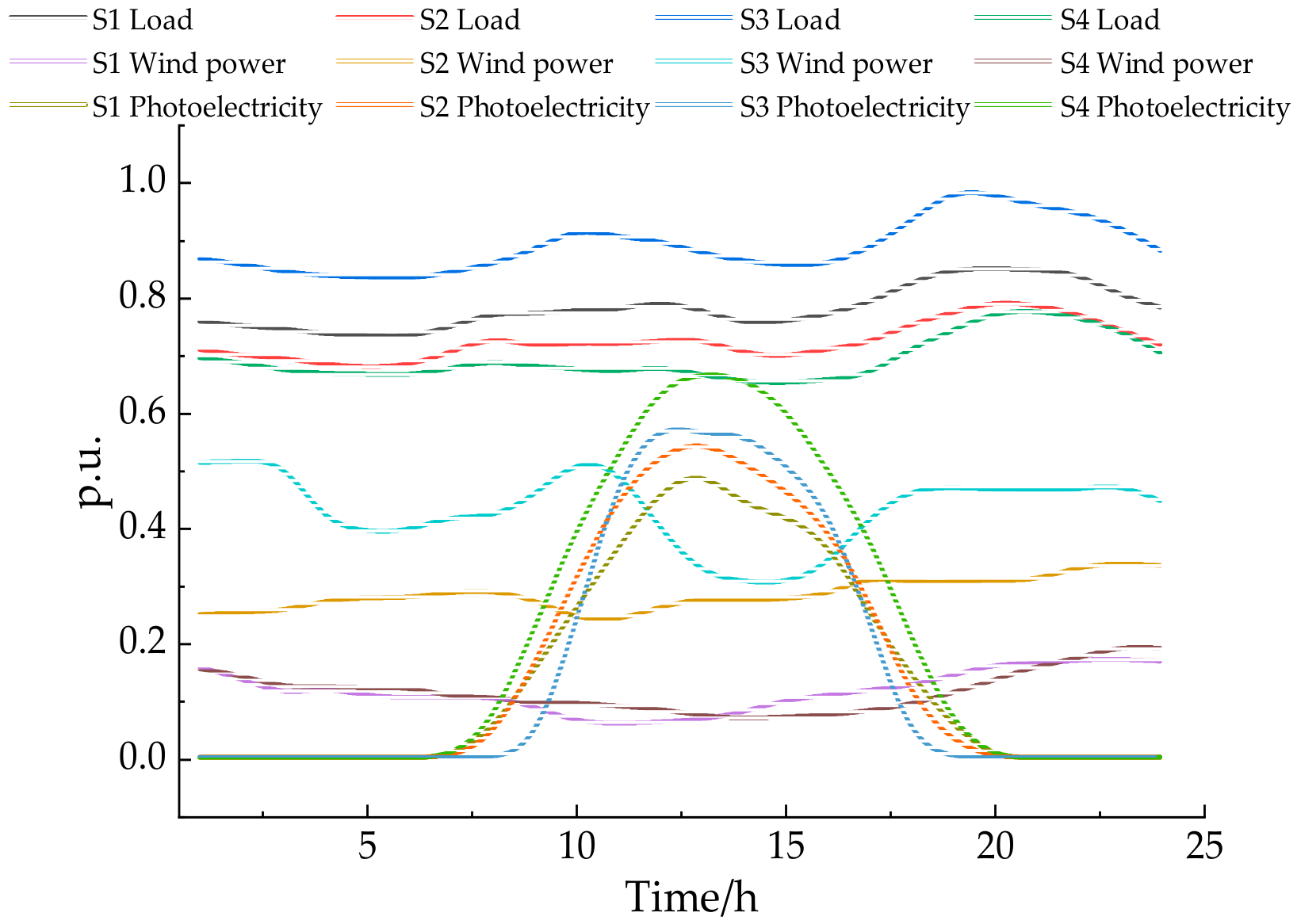
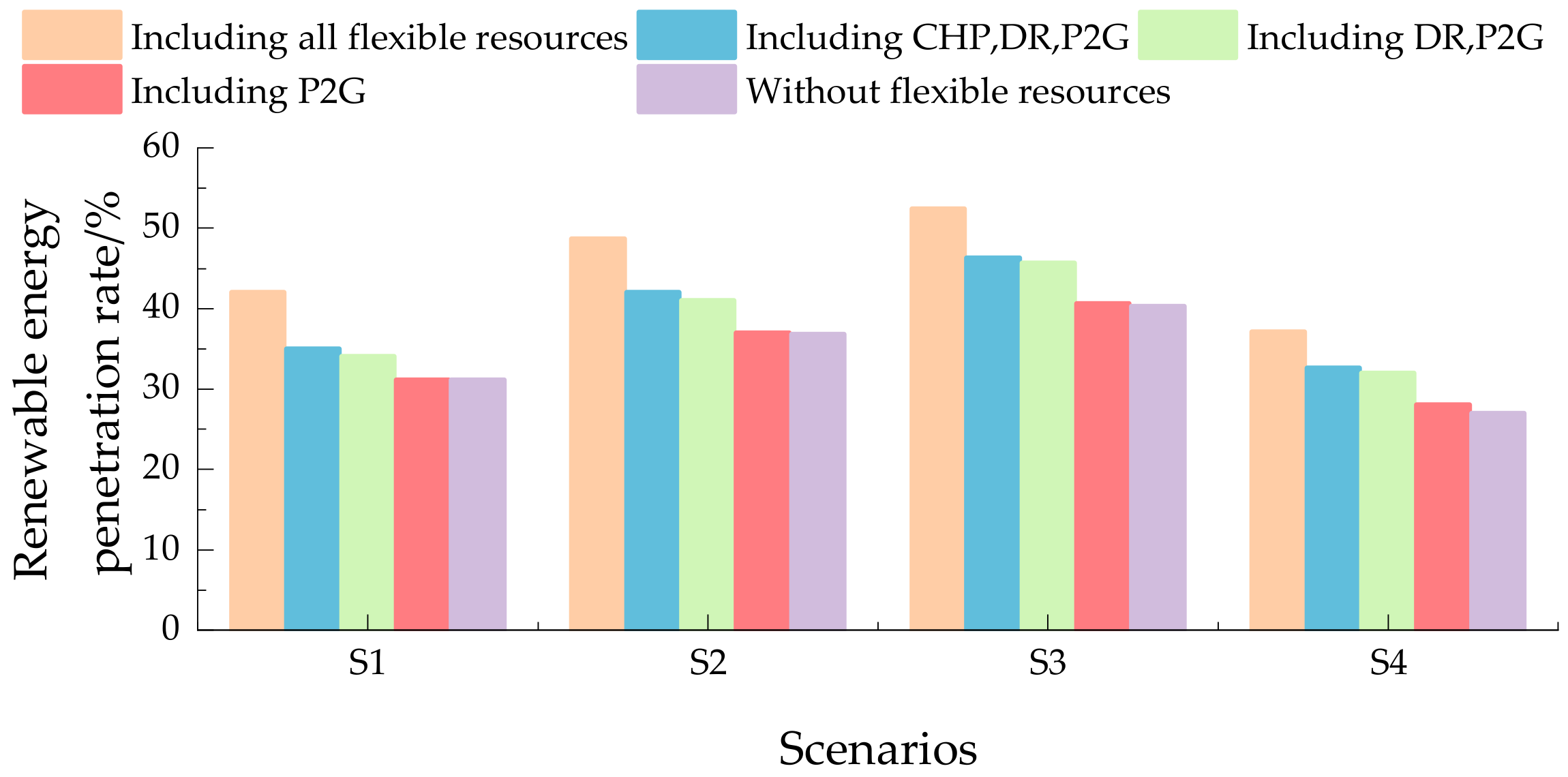
5. Case Study
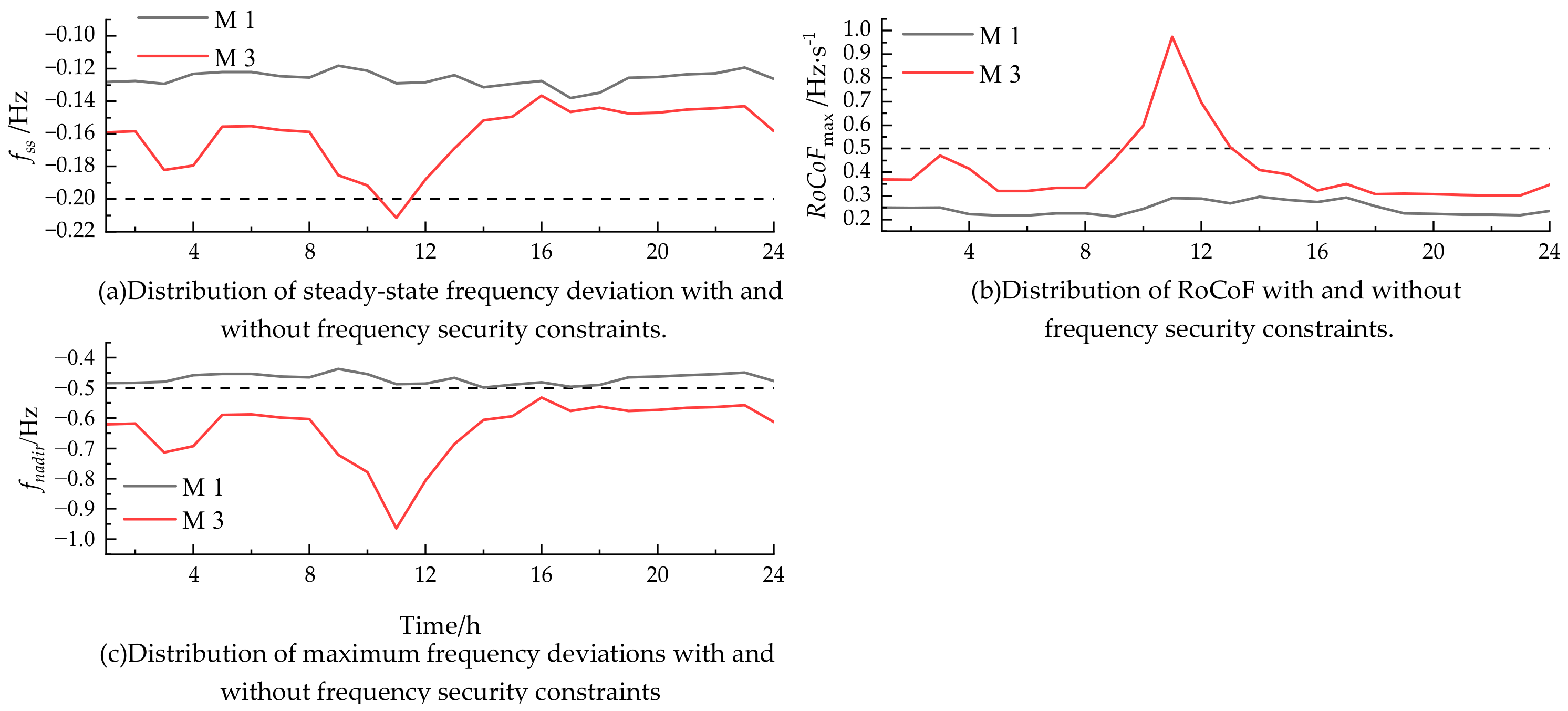
- M 1: The flexibility resources and frequency security constraints are taken into account.
- M 2: Only frequency security constraints are considered [17].
- M 3: Only flexible resources are considered [27].
- M 4: Neither flexibility resources nor frequency security constraints are considered [13].
6. Conclusions
- Utilizing a PCE fitting strategy significantly boosts the solving efficiency of the models incorporating a nadir point frequency constraint. A comparative analysis of four case studies reveals that our model outperforms traditional methods by providing a more precise evaluation of the renewable energy hosting capacity, considering both frequency security constraints and flexible resource models. The incorporation of these factors allows for a comprehensive evaluation that existing methods often overlook, leading to a more realistic estimation of grid capabilities.
- As renewable energy penetration grows, so does the risk of the system frequency exceeding safe deviation limits. Our model underscores the critical need to account for frequency security constraints when evaluating the renewable energy hosting capacity. By addressing these constraints, our approach prevents potential issues, such as the overestimation of the hosting capacity observed in methodologies that neglect frequency safety considerations. This clear identification of the frequency constraints ensures a thorough and safe evaluation.
- The progressive vertex enumeration approach properly counts and visualizes the renewable energy hosting capacity of a power grid, reflecting the coupling features of renewable energy. The interdependence of the output from renewable energy units throughout each period is explained, and the capacity of the distribution network to host renewable energy is graphically monitored.
Author Contributions
Funding
Conflicts of Interest
References
- Cevallos-Sierra, J.; Ramos-Martin, J. Spatial assessment of the potential of renewable energy: The case of Ecuador. Renew. Sustain. Energy Rev. 2018, 81, 1154–1165. [Google Scholar] [CrossRef]
- Fan, J.L.; Wang, J.X.; Hu, J.W.; Wang, Y.; Zhang, X. Optimization of China’s provincial renewable energy installation plan for the 13th five-year plan based on renewable portfolio standards. Appl. Energy 2019, 254, 113757. [Google Scholar] [CrossRef]
- Zargar, R.H.M.; Moghaddam, M.H.Y. Development of a Markov-Chain-Based Solar Generation Model for Smart Microgrid Energy Management System. IEEE Trans. Sustain. Energy 2020, 11, 736–745. [Google Scholar] [CrossRef]
- Dubey, A.; Santoso, S. On Estimation and Sensitivity Analysis of Distribution Circuit’s Photovoltaic Hosting Capacity. IEEE Trans. Power Syst. 2017, 32, 2779–2789. [Google Scholar] [CrossRef]
- Zhao, Z.; Xue, Y.; Liu, Z.; Zheng, W.; Duan, S.; Yu, L. A novel estimation method for maximum PV hosting capacity in radial distribution networks using bus voltage and electrical distance. Electr. Power Syst. Res. 2023, 224, 109791. [Google Scholar] [CrossRef]
- Dong, X.; Kang, C.; Ding, Y.; Wang, C. Estimating the wind power integration threshold considering electro-thermal coupling of overhead transmission lines. IEEE Trans. Power Syst. 2019, 34, 3349–3358. [Google Scholar] [CrossRef]
- Ding, T.; Kou, Y.; Yang, Y.; Zhang, Y.; Yan, H.; Blaabjerg, F. Evaluating maximum photovoltaic integration in district distribution systems considering optimal inverter dispatch and cloud shading conditions. IET Renew. Power Gener 2016, 11, 165–172. [Google Scholar] [CrossRef]
- Ding, K.; Chen, B.; Qin, J. Evaluation Method of Consumption Ability of New Large Scale Energy Clusters Connected to Weak Grids. Electr. Power Constr. 2023, 44, 86–94. [Google Scholar]
- Zhu, J.; Shi, K.; Li, Q.; Yu, R.Y.; Xia, J.R.; Yuan, Y. Time Series Production Simulation and Renewable Energy Accommodation Capacity Evaluation Considering Transmission Network Power Flow Constraints. Grid Technol. 2022, 46, 1947–1955. [Google Scholar]
- Yifan, L.; Xinyan, F.; Bo, W.; Zhenhua, C. Risk Assessment of New Energy Consumption Capacity Considering Node Vulnerability. Grid Technol. 2020, 44, 4479–4486. [Google Scholar]
- Wu, H.; Yuan, Y.; Zhu, J.; Qian, K.; Xu, Y. Potential Assessment of Spatial Correlation to Improve Maximum Distributed PV Hosting Capacity of Distribution Networks. J. Mod. Power Syst. Clean Energy 2021, 9, 800–810. [Google Scholar] [CrossRef]
- Wang, S.; Chen, S.; Ge, L.; Wu, L. Distributed Generation Hosting Capacity Evaluation for Distribution Systems Considering the Robust Optimal Operation of OLTC and SVC. IEEE Trans. Sustain. Energy 2016, 7, 1111–1123. [Google Scholar] [CrossRef]
- Ayres, H.; Freitas, W.; De Almeida, M.; Da Silva, L. Method for determining the maximum allowable penetration level of distributed generation without steady-state voltage violations. IET Gener. Transm. Distrib. 2010, 4, 495–508. [Google Scholar] [CrossRef]
- Meibom, P.; Barth, R.; Hasche, B.; Brand, H.; Weber, C.; O’malley, M. Stochastic optimization model to study the operational impacts of high wind penetrations in Ireland. IEEE Trans. Power Syst. 2011, 26, 1367–1379. [Google Scholar] [CrossRef]
- Cardozo, C.; Capely, L.; Dessante, P. Frequency constrained unit commitment. Energy Syst. 2017, 8, 31–56. [Google Scholar] [CrossRef]
- Pérez-Illanes, F.; Álvarez-Miranda, E.; Rahmann, C.; Campos-Valdés, C. Robust unit commitment including frequency stability constraints. Energies 2016, 9, 957. [Google Scholar] [CrossRef]
- Abiari, H.; Daemi, T.; Saeid, S.A. Frequency-constrained unit commitment under uncertain PFR of energy storage systems. J. Energy Storage 2023, 73, 108848. [Google Scholar] [CrossRef]
- Liu, L.; Li, W.; Ba, Y.; Shen, J.; Jin, C.; Wen, K. An analytical model for frequency nadir prediction following a major disturbance. IEEE Trans. Power Syst. 2020, 35, 2527–2536. [Google Scholar] [CrossRef]
- Egido, I.; Fernandez-Bernal, F.; Centeno, P.; Rouco, L. Maximum frequency deviation calculation in small, isolated power systems. IEEE Trans. Power Syst. 2009, 24, 1731–1738. [Google Scholar] [CrossRef]
- Zhang, Y.; Guo, Q.; Zhou, Y.; Sun, H. Frequency-constrained unit commitment for power systems with high renewable energy penetration. Int. J. Electr. Power Energy Syst. 2023, 153, 109274. [Google Scholar] [CrossRef]
- Paturet, M.; Markovic, U.; Delikaraoglou, S.; Vrettos, E.; Aristidou, P.; Hug, G. Stochastic unit commitment in low-inertia grids. IEEE Trans. Power Syst. 2020, 35, 3448–3458. [Google Scholar] [CrossRef]
- Ahmadi, H.; Ghasemi, H. Security-constrained unit commitment with linearized system frequency limit constraints. IEEE Trans. Power Syst. 2014, 29, 1536–1545. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhou, M.; Wu, Z.; Liu, S.; Guo, Z.; Li, G. A frequency security constrained scheduling approach considering wind farm providing frequency support and reserve. IEEE Trans. Sustain. Energy 2022, 13, 1086–1100. [Google Scholar] [CrossRef]
- Nguyen, N.; Bera, A.; Mitra, J. Energy storage to improve reliability of wind integrated systems under frequency security constraint. IEEE Trans. Ind. Appl. 2018, 54, 4039–4047. [Google Scholar] [CrossRef]
- Lu, X.; Li, K.; Xu, H.; Wang, F.; Zhou, Z.; Zhang, Y. Fundamentals and business model for resource aggregator of demand response in electricity markets. Energy 2020, 204, 117885. [Google Scholar] [CrossRef]
- Tang, W.; Li, Z.; Yu, Z.; Qian, T.; Lian, X.; Chen, X. Cost-optimal operation and recovery method for power distribution systems considering multiple flexible resources and logistics restrictions. Sustain. Energy Technol. Assess. 2022, 49, 101761. [Google Scholar] [CrossRef]
- Yu, S.; Zhou, S.; Qin, J. Layout optimization of China’s power transmission lines for renewable power integration considering flexible resources and grid stability. Int. J. Electr. Power Energy Syst. 2022, 135, 107507. [Google Scholar] [CrossRef]
- Hungerford, Z.; Bruce, A.; MacGill, I. The value of flexible load in power systems with high renewable energy penetration. Energy 2019, 188, 115960. [Google Scholar] [CrossRef]
- Rahimi, M.; Ardakani, F.J.; Olatujoye, O. Improving flexible optimal scheduling of virtual power plants considering dynamic line rating and flexible supply and demand. Int. J. Electr. Power Energy Syst. 2023, 150, 109099. [Google Scholar] [CrossRef]
- Wang, T.; Miao, S.; Yao, F.; Liu, Z.; Zhang, S. Day-ahead and Intra-day Joint Dispatch Strategy of High Proportion Wind Power System Considering Dynamic Frequency Response Constraints. Proc. CSEE 2023, 45, 1–19. [Google Scholar]
- Shen, D.; Wu, H.; Liang, H.; Qiu, Y.; Xie, H.; Gan, D. Accurate Polynomial Approximation of Bifurcation Hypersurfaces in Parameter Space for Small Signal Stability Region Considering Wind Generation. IEEE Trans. Power Syst. 2022, 37, 4512–4524. [Google Scholar] [CrossRef]
- Migliorati, G.; Nobile,, F.; von Schwerin, E.; Tempone, R. Approximation of quantities of interest in stochastic PDEs by the random discrete L2 projection on polynomial spaces. SIAM J. Sci. Comput. 2013, 3, A1440–A1460. [Google Scholar]
- Pan, C.; Hu, B.; Shao, C.; Xu, L.; Xie, K.; Wang, Y.; Anvari-Moghaddam, A. Reliability-Constrained Economic Dispatch with Analytical Formulation of Operational Risk Evaluation. IEEE Trans. Power Syst. 2024, 39, 4422–4436. [Google Scholar] [CrossRef]
- Zhang, D.; Zhao, J.; Dai, W.; Wang, C.; Jian, J.; Shi, B.; Wu, T. A feasible region evaluation method of renewable energy accommodation capacity. Energy Rep. 2021, 7, 1513–1520. [Google Scholar] [CrossRef]
- Dai, W.; Liu, Z.; Goh, H.H.; Luo, C.; Shi, B.; Xia, W. A constraint equivalent model of heat network for combined heat and power systems cooperation considering uncertainties. Electr. Power Syst. Res. 2023, 222, 109504. [Google Scholar] [CrossRef]
- Zhang, T.; Wang, J.; Wang, H.; Ruiyang, J.; Li, G.; Zhou, M. On the Coordination of Transmission-Distribution Grids: A Dynamic Feasible Region Method. IEEE Trans. Power Syst. 2023, 38, 1857–1868. [Google Scholar] [CrossRef]
- Sun, B.; Dai, W.; Zhang, D.; Goh, H.H.; Zhao, J.; Shi, B.; Wu, T. An Effective Spinning Reserve Allocation Method Considering Operational Reliability with Multi-Uncertainties. IEEE Trans. Power Syst. 2024, 39, 1568–1581. [Google Scholar] [CrossRef]
- Ardakani, A.J.; Bouffard, F. Identification of Umbrella Constraints in DC-Based Security-Constrained Optimal Power Flow. IEEE Trans. Power Syst. 2013, 28, 3924–3934. [Google Scholar] [CrossRef]




| S1 | S2 | S3 | S4 | ||
|---|---|---|---|---|---|
| Renewable energy penetration rate (%) | Without frequency security constraints | 52 | 60 | 67.7 | 45.7 |
| Considering frequency security constraints | 42 | 48.7 | 52.4 | 37.1 |
| S1 | S2 | S3 | S4 | ||
|---|---|---|---|---|---|
| Renewable energy penetration rate/% | Without frequency security constraints | 56.07 | 55.03 | 63.41 | 52.72 |
| Consider frequency security constraints | 51.94 | 45.47 | 55.36 | 45.78 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Z.; Zhao, H.; Ran, Q.; Wang, Y.; Yu, J.; Liu, H.; Duan, H. A Feasible Region-Based Evaluation Method for the Renewable Energy Hosting Capacity with Frequency Security Constraints. Energies 2024, 17, 3317. https://doi.org/10.3390/en17133317
Zhang Z, Zhao H, Ran Q, Wang Y, Yu J, Liu H, Duan H. A Feasible Region-Based Evaluation Method for the Renewable Energy Hosting Capacity with Frequency Security Constraints. Energies. 2024; 17(13):3317. https://doi.org/10.3390/en17133317
Chicago/Turabian StyleZhang, Zhi, Haibo Zhao, Qingyue Ran, Yao Wang, Juan Yu, Hongli Liu, and Hui Duan. 2024. "A Feasible Region-Based Evaluation Method for the Renewable Energy Hosting Capacity with Frequency Security Constraints" Energies 17, no. 13: 3317. https://doi.org/10.3390/en17133317
APA StyleZhang, Z., Zhao, H., Ran, Q., Wang, Y., Yu, J., Liu, H., & Duan, H. (2024). A Feasible Region-Based Evaluation Method for the Renewable Energy Hosting Capacity with Frequency Security Constraints. Energies, 17(13), 3317. https://doi.org/10.3390/en17133317





