Data-Driven Machine Learning Methods for Nontechnical Losses of Electrical Energy Detection: A State-of-the-Art Review
Abstract
:1. Introduction
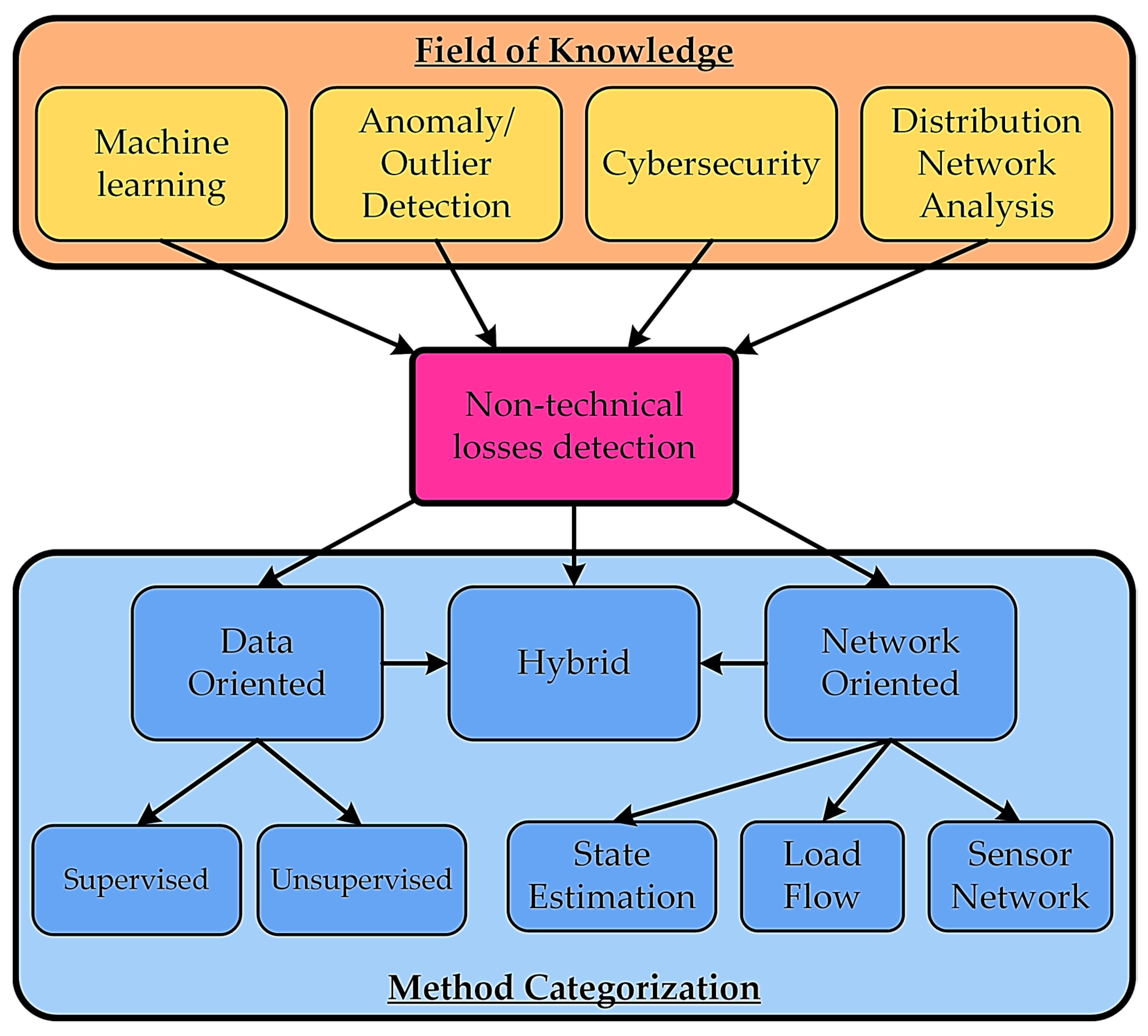
2. Methods of Identification and Assessment of Nontechnical Losses of Electrical Energy
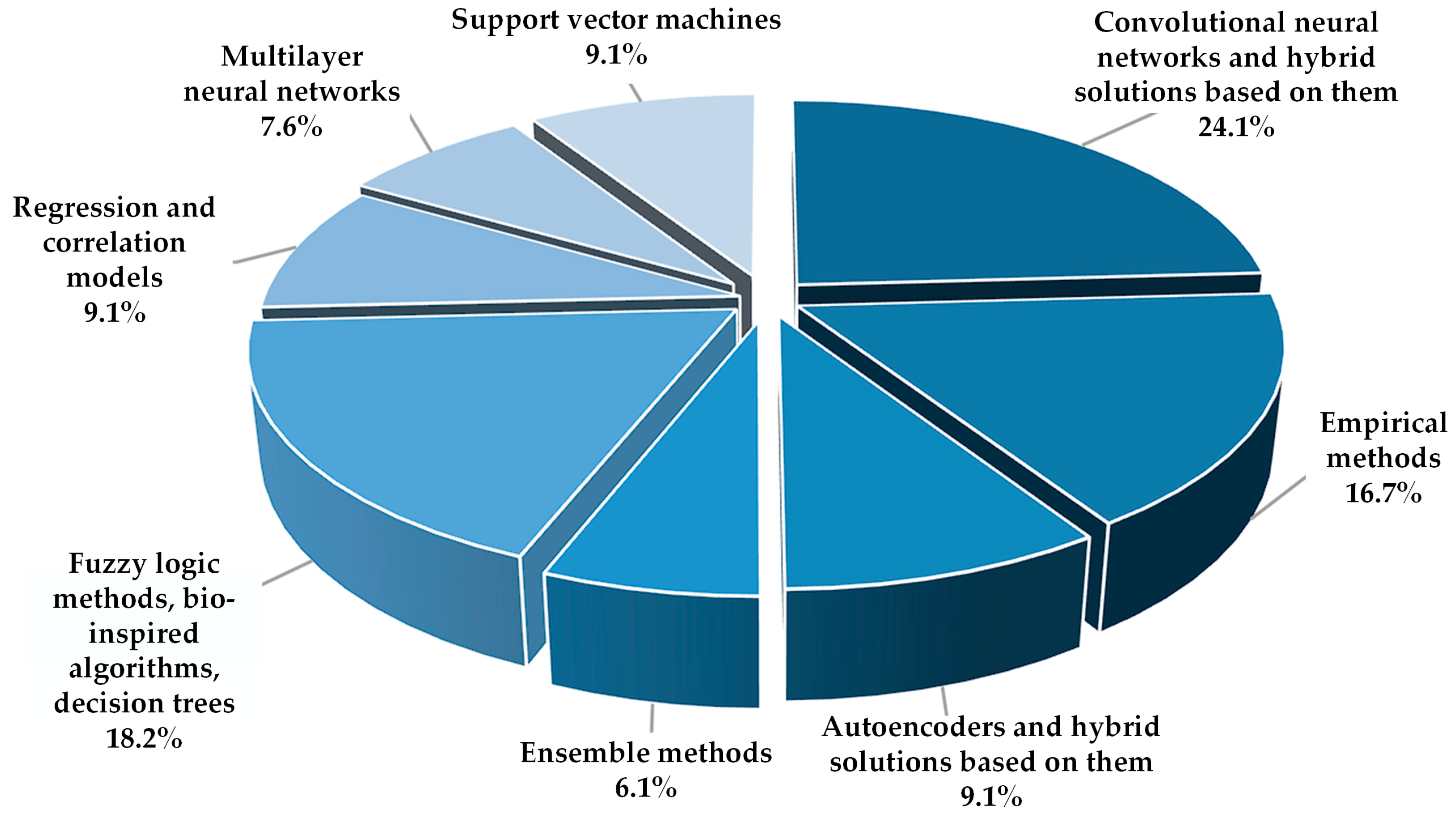
3. Analysis of the Methods Used to Identify NTLEE
3.1. Comparison of the Sensitivity of the Main Models and Methods
3.2. Comparison of Learning and Recognition Times
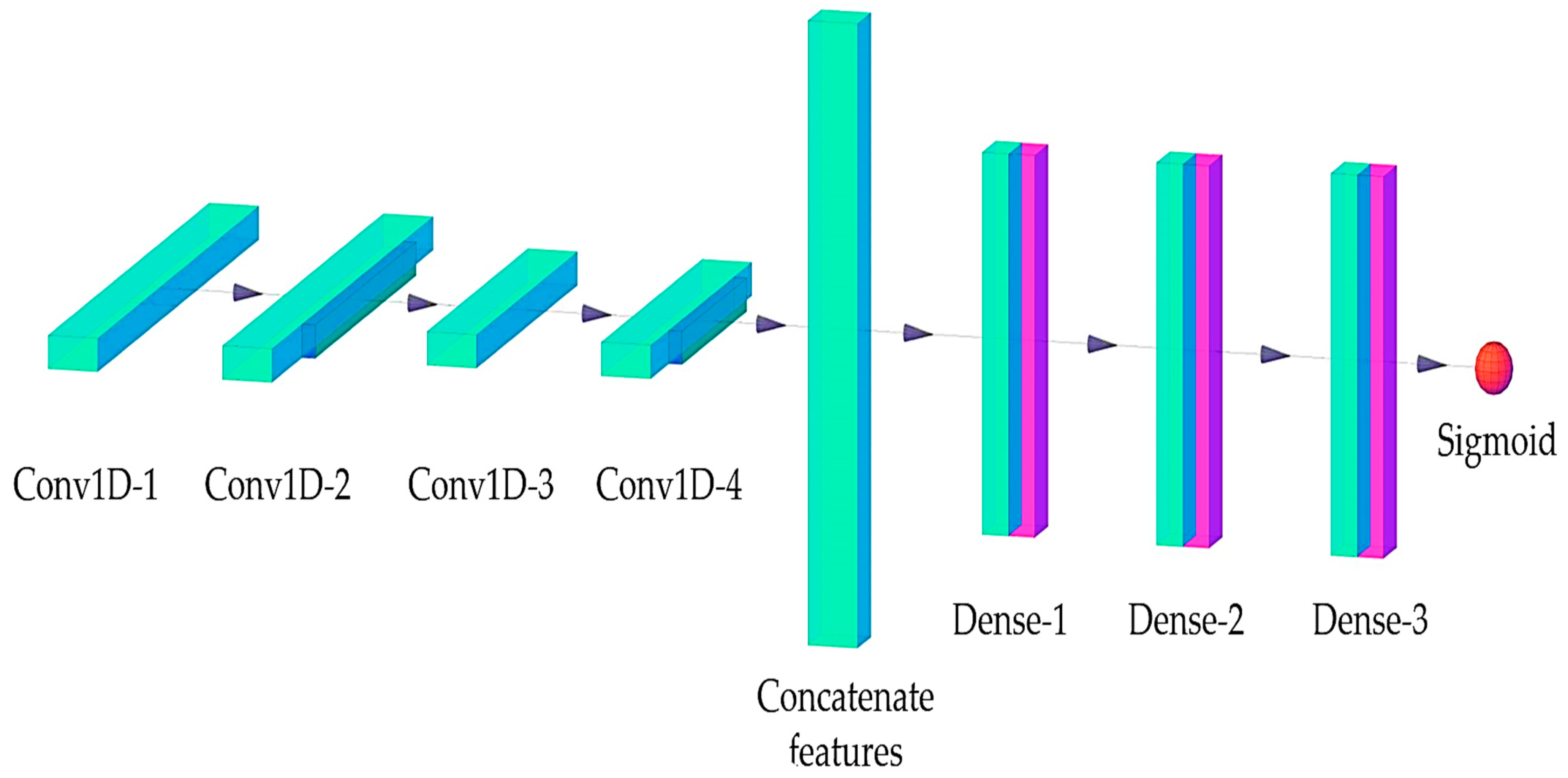
3.3. The Main Hyperparameters of ANN
3.4. Source Data, Metric, Depth of Retrospective, and Sampling Rate
3.5. Types and Features of Measurement Information Sources
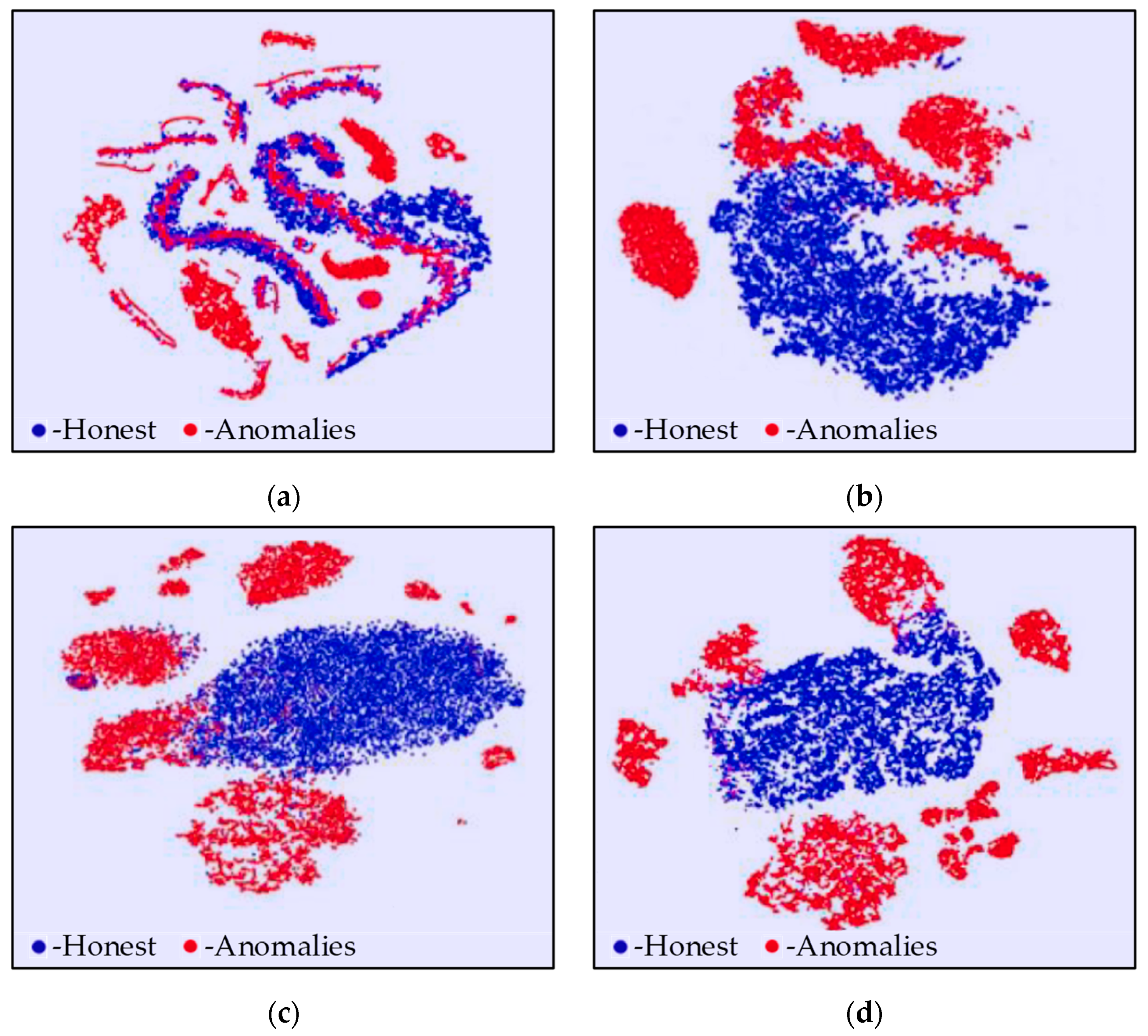
3.6. The Effect of Additional Data on the Sensitivity of the Algorithm
3.7. The Problem of Balanced Source Data
- Weight coefficients: The task of the weighting coefficients is to equalize the data and create a balance by multiplying by the value of the weighting coefficient, which is equal to the inverse of the percentage of data.
- RUS: This technique reduces the number of measurements without theft of electrical energy to the number of measurements with theft of electrical energy.
- ROS: This technique acts like RUS, but instead of reducing the number of measurements without theft, it, on the contrary, increases the number of measurements with theft of electrical energy.
- RUS-ROS: A compromise solution between RUS and ROS, the essence of which is to simultaneously reduce the number of measurements without theft of electrical energy and increase the number of measurements with theft of electrical energy until equal proportions are achieved.
- K-medoids, K-means: In this technique, clustering of the initial data to centroids/medoids is performed, taking them as new points. In fact, there is a decrease in the number of measurements without theft of electrical energy.
- Tomek links: If a measurement without theft of electrical energy is located next to a measurement in which there is theft of electrical energy, then the measurement without theft is deleted.
- SMOTE: Additionally, new points with thefts of electric energy are synthesized next to the original points where the theft data is present.
- ADASYN: A kind of SMOTE with the number of synthesized points proportional to the weighting factor of the number of points with electrical energy theft.
- CBOS: When using this technique, additional points with NTLEE are synthesized near the measured points with NTLEE, but the number of points is modeled in proportion to their distance to the cluster centroid.
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Emerging Markets Smart Grid: Outlook 2021. Available online: https://www.giiresearch.com/report/ng987743-emerging-markets-smart-grid-outlook.html (accessed on 7 August 2023).
- Find the Leak: How Network Companies Reduce Energy Losses. Available online: https://www.kommersant.ru/doc/5140335 (accessed on 7 August 2023). (In Russian).
- Tyumen Power Engineers Reduced Commercial Electricity Losses by 37 Million Rubles. Available online: https://rg.ru/2022/08/09/reg-urfo/tiumenskie-energetiki-snizili-kommercheskie-poteri-elektroenergii-na-37-mln-rublej.html (accessed on 7 August 2023). (In Russian).
- In 2022, Rosseti-Siberia Reduced Commercial Electricity Losses by 42%. Available online: http://energo-news.ru/archives/171689 (accessed on 7 August 2023). (In Russian).
- Meter Tampering: The Major Cause of Non-Technical Losses. Available online: https://clouglobal.com/meter-tampering-the-major-cause-of-non-technical-losses/ (accessed on 7 August 2023).
- Yan, Z.; Wen, H. Performance analysis of electricity theft detection for the Smart Grid: An Overview. IEEE Trans. Instrum. Meas. 2022, 71, 1–28. [Google Scholar] [CrossRef]
- Savian, F.S.; Siluk, J.C.M.; Garlet, T.B.; do Nascimento, F.M.; Pinheiro, J.; Vale, Z. Non-technical losses: A systematic contemporary article review. Renew. Sustain. Energy Rev. 2021, 147, 111205. [Google Scholar] [CrossRef]
- Messinis, G.M.; Hatziargyriou, N.D. Review of non-technical loss detection methods. Electr. Power Syst. Res. 2018, 158, 250–266. [Google Scholar] [CrossRef]
- Antmann, P. Reducing Technical and Non-Technical Losses in the Power Sector. In Background Paper for the World Bank Group Energy Sector Strategy; World Bank Press: Washington, DC, USA, 2009; p. 92639. [Google Scholar]
- Mail.ru Group Helped Rosseti Center to Reduce Commercial Electricity Losses with the Help of AI. Available online: https://www.cnews.ru/news/line/2021-03-17_mailru_group_pomogla_rosseti (accessed on 7 August 2023). (In Russian).
- Search for Commercial Losses in Electrical Networks with Analytics. Available online: https://energytool.mts.ru/commercial_losses (accessed on 7 August 2023). (In Russian).
- Best Fraud Detection Software and Tools in 2023. Available online: https://seon.io/resources/comparisons/fraud-detection-and-prevention-software-tools/ (accessed on 7 August 2023). (In Russian).
- Pazderin, A.V.; Bartolomey, P.I.; Pazderin, A. A Model of energy cost distribution for participants of energy exchange in electric networks. Energetik 2022, 4, 35–40. (In Russian) [Google Scholar]
- Pazderin, A.V.; Egorov, A.O.; Kochneva, E.S.; Samoylenko, V.O. The use of methodological approaches of the theory of state estimation for the calculation and reliability of electric energy flows in networks. Electricity 2014, 10, 12–21. (In Russian) [Google Scholar]
- Fragkioudaki, A.; Cruz-Romero, P.; Gomez-Exposito, A.; Arcos-Vargas, A.; Cruz, P.; Biscarri, J. Detection of Non-technical Losses in Smart Distribution Networks: A Review. In Trends in Practical Applications of Scalable Multi-Agent Systems, the PAAMS Collection; AISC: Chicago, IL, USA, 2016; pp. 43–54. [Google Scholar]
- Ahmed, M.; Khan, A.; Ahmed, M.; Tahir, M.; Jeon, G.; Fortino, G.; Piccialli, F. Energy Theft Detection in Smart Grids: Taxonomy, Comparative Analysis, Challenges, and Future Research Directions. IEEE/CAA J. Autom. Sin. 2022, 9, 578–600. [Google Scholar] [CrossRef]
- Shilin, A.A.; Saprykina, D.A. Analysis of Sources of commercial Losses in the Power System. Energy Resour. Sav. Ind. Transp. 2019, 27, 2. (In Russian) [Google Scholar]
- Kosolapov, A.M.; Frantasov, D.N.; Kudryashova, Y.V. Improving the Accuracy of the Analysis of Commercial Electricity Losses. 2014. No. 1. pp. 86–91. Available online: http://repo.ssau.ru/bitstream/Perspektivnye-informacionnye-tehnologii/Povyshenie-tochnosti-informacionnyh-sistem-rascheta-poter-elektroenergii-59424/1/pit_2013_itt_6.pdf (accessed on 7 August 2023). (In Russian).
- Omorov, T.T. To the problem of identification of technical and commercial losses of electricity as part of the AIIS KUE. Account. Electr. 2018, 5, 56–60. (In Russian) [Google Scholar]
- Venkateswarlu, S. Controller Design for Detection of Various Power Thefts. In Proceedings of the 2021 Innovations in Power and Advanced Computing Technologies, Kuala Lumpur, Malaysia, 27–29 November 2021. [Google Scholar]
- Lydia, M.; Kumar, G.E.P.; Levron, Y. Detection of Electricity Theft based on Compressed Sensing. In Proceedings of the 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS), Coimbatore, India, 15–16 March 2019. [Google Scholar]
- Zhukov, M.V.; Zelensky, E.G.; Kononov, Y.G. Localization of Commercial Electricity Losses in 6–10 kV Networks by Methods of State Assessment; Bulletin of the North Caucasus Federal University: Stavropol, Russia, 2013. (In Russian) [Google Scholar]
- Pulz, J.; Almeida, C.F.M. An alternative approach for regulatory evaluation of non-technical losses in Brazil. In Proceedings of the CIRED 2021 the 26th International Conference and Exhibition on Electricity Distribution, Online, 20–23 September 2021; Institution of Engineering and Technology: London, UK, 2021. [Google Scholar]
- Aryanezhad, M. A novel approach to detection and prevention of electricity pilferage over power distribution network. Int. J. Electr. Power Energy Syst. 2019, 111, 191–200. [Google Scholar] [CrossRef]
- Vieira, V.G.; Bernardon, D.P.; Heinke, M.; Figueiredo, M.; Evaldt, M.; Uberti, V.; Abaide, A.; Chiara, L.; Silva, J. A Methodology to Identify Non-technical losses on rural grids using artificial neural networks and deep learning. In Proceedings of the CIRED 2021 the 26th International Conference and Exhibition on Electricity Distribution, Online, 20–23 September 2021; Institution of Engineering and Technology: London, UK, 2021. [Google Scholar]
- Firoozi, H.; Rajabi Mashhadi, H. Non-technical loss detection in limited-data low-voltage distribution feeders. Int. J. Electr. Power Energy Syst. 2022, 135, 107523. [Google Scholar] [CrossRef]
- Pereira, J.; Saraiva, F. A Comparative Analysis of Unbalanced Data Handling Techniques for Machine Learning Algorithms to Electricity Theft Detection. In Proceedings of the 2020 IEEE Congress on Evolutionary Computation (CEC), Glasgow, UK, 19–24 July 2020. [Google Scholar]
- Coma-Puig, B.; Carmona, J. Non-technical losses detection in energy consumption focusing on energy recovery and explainability. Mach. Learn. 2022, 111, 487–517. [Google Scholar] [CrossRef]
- Madrigal, M.; Rico, J.J.; Uzcategui, L. Estimation of Non-Technical Energy Losses in Electrical Distribution Systems. IEEE Lat. Am. Trans. 2017, 15, 1447–1452. [Google Scholar] [CrossRef]
- Olivares-Rojas, J.C.; Reyes-Archundiaa, E.; Rodriíguez-Mayab, N.E.; Gutiérrez-Gnecchia, J.A.; Molina-Morenoa, I.; Cerda-Jacoboc, J. Machine Learning Model for the Detection of Electric Energy Fraud using an Edge-Fog Computing Architecture. In Proceedings of the 2020 IEEE International Conference on Engineering Veracruz, Boca del Rio, Mexico, 26–29 October 2020. [Google Scholar]
- Yip, S.-C.; Wong, K.S.; Hew, W.-P.; Gan, M.-T.; Phan, R.C.-W.; Tan, S.-W. Detection of energy theft and defective smart meters in smart grids using linear regression. Int. J. Electr. Power Energy Syst. 2017, 91, 230–240. [Google Scholar] [CrossRef]
- de Oliveira Ventura, L.; Melo, J.D.; Padilha-Feltrin, A.; Fern, J.P.; Fernandez-Gutierrez, J.P.; Sanchez Zuleta, C.C.; Piedrahita Escobar, C.C. A new way for comparing solutions to non-technical electricity losses in South America. Util. Policy 2020, 67, 101113. [Google Scholar] [CrossRef]
- Jamil, F. On the electricity shortage, price and electricity theft nexus. Energy Policy 2013, 54, 267–272. [Google Scholar] [CrossRef]
- Jamil, F. Electricity theft among residential consumers in Rawalpindi and Islamabad. Energy Policy 2018, 123, 147–154. [Google Scholar] [CrossRef]
- Kang, L.; Shang, Y.; Zhang, M.X.; Liao, L.Y. Research on monitoring technology of power stealing behavior in bitcoin mining based on analyzing electric energy data. Energy Rep. 2022, 8, 1183–1189. [Google Scholar] [CrossRef]
- Liua, S.; Liangc, Y.; Wangc, J.; Jianga, T.; Suna, W.; Ruia, Y. Identification of stealing electricity based on big data analysis. Energy Rep. 2020, 6, 731–738. [Google Scholar] [CrossRef]
- Lewis, F.B. Costly ‘Throw-Ups’: Electricity Theft and Power Disruptions. Electr. J. 2015, 28, 118–135. [Google Scholar] [CrossRef]
- Yang, Y.; Song, R.; Xue, Y.; Zhang, P.; Xu, Y.; Kang, J.; Zhao, H. A Detection Method for Group Fixed Ratio Electricity Thieves Based on Correlation Analysis of Non-Technical Loss. IEEE Access 2022, 10, 5608–5619. [Google Scholar] [CrossRef]
- Reuter, S.; Winter, J.; Iséni, S.; Schmidt-Bleker, A.; Dünnbier, M.; Masur, K.; Wende, K.; Weltmann, K.-D. Electricity Theft Pinpointing Through Correlation Analysis of Master and Individual Meter Readings. IEEE Trans. Smart Grid 2020, 11, 3031–3042. [Google Scholar]
- Fan, T. Research on automatic user identification system of leaked electricity based on Data Mining Technology. Energy Rep. 2021, 7, 1092–1100. [Google Scholar] [CrossRef]
- Singhal, D.; Ahuja, L.; Seth, A. Anomaly Detection in Smart Meters: Analytical Study. In Proceedings of the 2022 2nd International Conference on Power Electronics & IoT Applications in Renewable Energy and Its Control (PARC), Mathura, India, 21–22 January 2022. [Google Scholar]
- Otuoze, A.O.; Mustafa, M.W.; Abdulrahman, A.T.; Mohammed, O.O.; Salisu, S. Penalization of electricity thefts in smart utility networks by a cost estimation-based forced corrective measure. Energy Policy 2020, 143, 111553. [Google Scholar] [CrossRef]
- Khan, I.U.; Javaid, N.; Taylor, C.J.; Ma, X. Data Driven Analysis for Electricity Theft Attack-Resilient Power Grid. IEEE Trans. Power Syst. 2022, 38, 537–548. [Google Scholar] [CrossRef]
- Bian, J.; Wang, L.; Scherer, R.; Woźniak, M.; Zhang, P.; Wei, W. Abnormal Detection of Electricity Consumption of User Based on Particle Swarm Optimization and Long Short-Term Memory with the Attention Mechanism. IEEE Access 2021, 9, 47252–47265. [Google Scholar] [CrossRef]
- Dong, L.; Li, Q.; Wu, K.; Fei, K.; Liu, C.; Wang, N.; Yang, J.; Li, Y. Nontechnical Loss Detection of Electricity based on Neural Architecture Search in Distribution Power Networks. In Proceedings of the 2020 International Conference on Smart Grid and Clean Energy Technologies (ICSGCE), Kuching, Malaysia, 18–21 May 2020. [Google Scholar]
- Shang, Y. Prediction method of electricity stealing behavior based on multi-dimensional features and BP neural network. Energy Rep. 2022, 8, 523–531. [Google Scholar] [CrossRef]
- Bakre, S.; Shiralkar, A.; Shelar, S.V.; Ingle, S. Artificial Neural Network Based Electricity Theft Detection. In Proceedings of the 2022 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 9–11 March 2022. [Google Scholar]
- de Souzaa, M.A.; Pereiraa, J.L.R.; Alvesa, G.d.O.; de Oliveiraa, B.C.; Meloa, I.D.; Garciab, P.A.N. Detection and identification of energy theft in advanced metering infrastructures. Electr. Power Syst. Res. 2020, 182, 106258. [Google Scholar] [CrossRef]
- Yakubu, O.; Babu, C.N.; Adjei, O. Electricity theft: Analysis of the underlying contributory factors in Ghana. Energy Policy 2018, 123, 611–618. [Google Scholar] [CrossRef]
- Wong, J.C.Y.; Blankenship, B.; Urpelainen, J.; Ganesan, K.; Bharadwaj, K.; Balani, K. Perceptions and acceptability of electricity theft: Towards better public service provision. World Dev. 2021, 140, 105301. [Google Scholar] [CrossRef]
- Naqvi, I.; Poorthuis, A.; Govind, A. Urban governance and electricity losses: An exploration of spatial unevenness in Karachi, Pakistan. Energy Res. Soc. Sci. 2021, 79, 102166. [Google Scholar] [CrossRef]
- Winther, T. Electricity theft as a relational issue: A comparative look at Zanzibar, Tanzania, and the Sunderban Islands, India. Energy Sustain. Dev. 2012, 16, 111–119. [Google Scholar] [CrossRef]
- Arkorful, V.E. Unravelling electricity theft whistleblowing antecedents using the theory of planned behavior and norm activation model. Energy Policy 2022, 160, 112680. [Google Scholar] [CrossRef]
- Singh, D.K.; Kediya, S.; Mahajan, R.; Asthana, P.K. Study of non-technical factors responsible for power losses at MSEB. In Proceedings of the 2021 International Conference on Computational Intelligence and Computing Applications (ICCICA), Nagpur, India, 26–27 November 2021. [Google Scholar]
- Razavi, R.; Fleury, M. Socio-economic predictors of electricity theft in developing countries: An Indian case study. Energy Sustain. Dev. 2019, 49, 1–10. [Google Scholar] [CrossRef]
- Never, B. Social norms, trust and control of power theft in Uganda: Does bulk metering work for MSEs. Energy Policy 2015, 82, 197–206. [Google Scholar] [CrossRef]
- Adongo, C.A.; Taale, F.; Bukari, S.; Suleman, S.; Amadu, I. Electricity theft whistleblowing feasibility in commercial accommodation facilities. Energy Policy 2021, 155, 112347. [Google Scholar] [CrossRef]
- Sharma, T.; Pandey, K.K.; Punia, D.K.; Rao, J. Of pilferers and poachers: Combating electricity theft in India. Energy Res. Soc. Sci. 2016, 11, 40–52. [Google Scholar] [CrossRef]
- Gaur, V.; Gupta, E. The determinants of electricity theft: An empirical analysis of Indian states. Energy Policy 2016, 93, 127–136. [Google Scholar] [CrossRef]
- Yurtseven, Ç. The causes of electricity theft: An econometric analysis of the case of Turkey. Util. Policy 2015, 37, 70–78. [Google Scholar] [CrossRef]
- Mendiola, J.E.; Pedrasa, M.A.A. Detection of Pilferage in an AMI-Enabled Low-Voltage Network Using Energy Reading Anomalies. In Proceedings of the 2019 International Conference on Smart Grid Synchronized Measurements and Analytics (SGSMA), College Station, TX, USA, 21–23 May 2019. [Google Scholar]
- Omidvar Tehrani, S.; Shahrestani, A.; Yaghmaee, M.H. Online electricity theft detection framework for large-scale smart grid data. Electr. Power Syst. Res. 2022, 208, 107895. [Google Scholar] [CrossRef]
- Zhang, M. Research on comprehensive diagnosis model of anti-stealing electricity based on big data technology. Energy Rep. 2022, 8, 916–925. [Google Scholar] [CrossRef]
- Xue, L.; Cheng, L.; Li, Y.; Mao, Y. Quantum Machine Learning for Electricity Theft Detection: An Initial Investigation. In Proceedings of the 2021 IEEE International Conferences on Internet of Things (iThings) and IEEE Green Computing & Communications (GreenCom) and IEEE Cyber, Physical & Social Computing (CPSCom) and IEEE Smart Data (SmartData) and IEEE Congress on Cybermatics (Cybermatics), Melbourne, Australia, 6–8 December 2021. [Google Scholar]
- Long, H.; Chen, C.; Gu, W.; Xie, J.; Wang, Z.; Li, G. A Data-Driven Combined Algorithm for Abnormal Power Loss Detection in the Distribution Network. IEEE Access 2020, 8, 24675–24686. [Google Scholar] [CrossRef]
- Buzau, M.M.; Tejedor-Aguilera, J.; Cruz-Romero, P.; Gómez-Expósito, A. Detection of Non-Technical Losses Using Smart Meter Data and Supervised Learning. IEEE Trans. Smart Grids 2019, 10, 2661–2670. [Google Scholar] [CrossRef]
- Haq, E.U.; Huang, J.; Xu, H.; Li, K.; Ahmad, F. A hybrid approach based on deep learning and support vector machine for the detection of electricity theft in power grids. Energy Rep. 2021, 7, 349–356. [Google Scholar] [CrossRef]
- Depuru, S.S.S.R.; Wang, L.; Devabhaktuni, V.; Green, R.C. High-performance computing for detection of electricity theft. Int. J. Electr. Power Energy Syst. 2013, 47, 21–30. [Google Scholar] [CrossRef]
- Ahmad, T.; Chen, H.; Wang, J.; Guo, Y. Review of various modeling techniques for the detection of electricity theft in smart grid environment. Renew. Sustain. Energy Rev. 2018, 82, 2916–2933. [Google Scholar] [CrossRef]
- Kong, X.; Zhao, X.; Liu, C.; Li, Q.; Dong, D.L.; Li, Y. Electricity theft detection in low-voltage stations based on similarity measure and DT-KSVM. Int. J. Electr. Power Energy Syst. 2021, 125, 106544. [Google Scholar] [CrossRef]
- Messinis, G.M.; Rigas, A.E.; Hatziargyriou, N.D. A Hybrid Method for Non-Technical Loss Detection in Smart Distribution Grids. IEEE Trans. Smart Grids 2019, 10, 6080–6091. [Google Scholar] [CrossRef]
- Engelbrecht, J.; Hancke, G.P.; Osifeko, M.O. Design and Implementation of an Electrical Tamper Detection System. In Proceedings of the IECON 2019—45th Annual Conference of the IEEE Industrial Electronics Society, Lisbon, Portugal, 14–17 October 2019. [Google Scholar]
- Massaferro, P.; Martino, J.M.D.; Fernandez, A. Fraud Detection on Power Grids While Transitioning to Smart Meters by Leveraging Multi-Resolution Consumption Data. IEEE Trans. Smart Grids 2022, 13, 2381–2389. [Google Scholar] [CrossRef]
- Esmael, A.A.; da Silva, H.H.; Ji, T.; da Silva Torres, R. Non-Technical Loss Detection in Power Grid Using Information Retrieval Approaches: A Comparative Study. IEEE Access 2021, 9, 40635–40648. [Google Scholar] [CrossRef]
- Arif, A.; Alghamdi, T.A.; Khan, Z.A.; Javaid, N. Towards Efficient Energy Utilization Using Big Data Analytics in Smart Cities for Electricity Theft Detection. Big Data Res. 2022, 27, 100285. [Google Scholar] [CrossRef]
- Javaid, N.; Gul, H.; Baig, S.; Shehzad, F.; Xia, C.; Guan, L.; Sultana, T. Using GANCNN and ERNET for Detection of Non-Technical Losses to Secure Smart Grids. IEEE Access 2021, 9, 98679–98700. [Google Scholar] [CrossRef]
- Lee, J.; Sun, Y.G.; Sim, I.; Kim, S.H.; Kim, D.I.; Kim, J.Y. Non-Technical Loss Detection Using Deep Reinforcement Learning for Feature Cost Efficiency and Imbalanced Dataset. IEEE Access 2022, 10, 27084–27095. [Google Scholar] [CrossRef]
- Fei, K.; Li, Q.; Zhu, C. Non-technical losses detection using missing values’ pattern and neural architecture search. Int. J. Electr. Power Energy Syst. 2022, 134, 107410. [Google Scholar] [CrossRef]
- Pereira, J.; Saraiva, F. Convolutional neural network applied to detect electricity theft: A comparative study on unbalanced data handling techniques. Int. J. Electr. Power Energy Syst. 2021, 131, 107085. [Google Scholar] [CrossRef]
- Yang, J.; Fei, K.; Ren, F.; Li, Q.; Li, J.; Duan, Y.; Dong, L. Non-technical Loss Detection using Missing Values’ Pattern. In Proceedings of the 2020 International Conference on Smart Grid and Clean Energy Technologies (ICSGCE), Kuching, Malaysia, 4–7 October 2020. [Google Scholar]
- Fei, K.; Li, Q.; Zhu, C.; Dong, M.; Li, Y. Electricity frauds detection in Low-voltage networks with contrastive predictive coding. Int. J. Electr. Power Energy Syst. 2022, 137, 107715. [Google Scholar] [CrossRef]
- Niu, Z.; Zhang, G. A Data-Driven Method for Electricity Theft Detection Combing ConvGRU and K-means Clustering. In Proceedings of the 2021 IEEE 5th Conference on Energy Internet and Energy System Integration (EI2), Taiyuan, China, 22–24 October 2021. [Google Scholar]
- Ayub, N.; Aurangzeb, K.; Awais, M.; Ali, U. Electricity Theft Detection Using CNN-GRU and Manta Ray Foraging Optimization Algorithm. In Proceedings of the 2020 IEEE 23rd International Multitopic Conference (INMIC), Bahawalpur, Pakistan, 5–7 November 2020. [Google Scholar]
- Hasan, M.N.; Toma, R.N.; Nahid, A.; Islam, M.M.M. Electricity Theft Detection in Smart Grid Systems: A CNN-LSTM Based Approach. Energies 2019, 12, 3310. [Google Scholar] [CrossRef]
- Javaid, N.; Jan, N.; Javed, M.U. An adaptive synthesis to handle imbalanced big data with deep siamese network for electricity theft detection in smart grids. J. Parallel Distrib. Comput. 2021, 153, 44–52. [Google Scholar] [CrossRef]
- Li, S.; Han, Y.; Yao, X.; Yingchen, S.; Wang, J.; Zhao, Q. Electricity Theft Detection in Power Grids with Deep Learning and Random Forests. J. Electr. Comput. Eng. 2019, 20, 1–12. [Google Scholar] [CrossRef]
- Lepolesa, L.J.; Achari, S.; Cheng, L. Electricity Theft Detection in Smart Grids Based on Deep Neural Network. IEEE Access 2022, 10, 39638–39655. [Google Scholar] [CrossRef]
- Buzau, M.M.; Tejedor-Aguilera, J.; Cruz-Romero, P.; Gómez-Expósito, A. Hybrid Deep Neural Networks for Detection of Non-Technical Losses in Electricity Smart Meters. IEEE Trans. Power Syst. 2020, 35, 1254–1263. [Google Scholar] [CrossRef]
- Mujeeb, S.; Javaid, N.; Ahmed, A.; Gulfam, S.M.; Qasim, U.; Shafiq, M.; Choi, J.-G. Electricity Theft Detection with Automatic Labeling and Enhanced RUSBoost Classification Using Differential Evolution and Jaya Algorithm. IEEE Access 2021, 9, 128521–128539. [Google Scholar] [CrossRef]
- Li, J.; Liao, W.; Yang, R.; Chen, Z. A Data Augmentation Method for Distributed Photovoltaic Electricity Theft Using Wasserstein Generative Adversarial Network. In Proceedings of the 2021 IEEE 5th Conference on Energy Internet and Energy System Integration (EI2), Taiyuan, China, 22–24 October 2021. [Google Scholar]
- Aslam, Z.; Ahmed, F.; Almogren, A.; Shafiq, M.; Zuair, M.; Javaid, N. An Attention Guided Semi-Supervised Learning Mechanism to Detect Electricity Frauds in the Distribution Systems. IEEE Access 2020, 8, 221767–221782. [Google Scholar] [CrossRef]
- Huang, Y.; Xu, Q. Electricity theft detection based on stacked sparse denoising autoencoder. Int. J. Electr. Power Energy Syst. 2021, 125, 106448. [Google Scholar] [CrossRef]
- Takiddin, A.; Ismail, M.; Zafar, U.; Serpedin, E. Deep Autoencoder-Based Anomaly Detection of Electricity Theft Cyberattacks in Smart Grids. IEEE Syst. J. 2022, 16, 4106–4117. [Google Scholar] [CrossRef]
- Ayub, N.; Aurangzeb, K.; Awais, M.; Ali, U. Energy theft detection in an edge data center using threshold-based abnormality detector. Int. J. Electr. Power Energy Syst. 2020, 121, 106162. [Google Scholar]
- Shehzad, F.; Javaid, N.; Aslam, S.; Javed, M.U. Electricity theft detection using big data and genetic algorithm in electric power systems. Electr. Power Syst. Res. 2022, 209, 107975. [Google Scholar] [CrossRef]
- Ullah, A.; Javaid, N.; Asif, M.; Javed, M.U.; Yahaya, A.S. AlexNet, AdaBoost and Artificial Bee Colony Based Hybrid Model for Electricity Theft Detection in Smart Grids. IEEE Access 2022, 10, 18681–18694. [Google Scholar] [CrossRef]
- Gunturi, S.K.; Sarkar, D. Ensemble machine learning models for the detection of energy theft. Electr. Power Syst. Res. 2021, 192, 106904. [Google Scholar] [CrossRef]
- Sharma, R.; Joshi, A.M.; Sahu, C.; Sharma, G.; Akindeji, K.T.; Sharma, S. Semi Supervised Cyber Attack Detection System for Smart Grid. In Proceedings of the 2022 30th Southern African Universities Power Engineering Conference (SAUPEC), Durban, South Africa, 25–27 January 2022. [Google Scholar]
- Alharbi, M.; Alghumayjan, S.; Alsaleh, M.; Shah, D.; Alabdulkareem, A. Electricity Non-Technical Loss Detection: Enhanced Cost-Driven Approach Utilizing Synthetic Control. In Proceedings of the 2021 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference, Washington, DC, USA, 16–18 February 2021. [Google Scholar]
- Massaferro, P.; Marichal, H.; Di Martino, M.; Santomauro, F.; Kosut, J.P.; Fernandez, A. Improving electricity non-technical losses detection including neighborhood information. In Proceedings of the 2018 IEEE Power & Energy Society General Meeting (PESGM), Portland, OR, USA, 5–9 August 2018. [Google Scholar]
- Muzumdar, A.; Modi, C.; Vyjayanthi, C. Designing a blockchain-enabled privacy-preserving energy theft detection system for smart grid neighborhood area network. Electr. Power Syst. Res. 2022, 207, 107884. [Google Scholar] [CrossRef]
- Viegas, J.L.; Esteves, P.R.; Melício, R.; Mendes, V.M.F.; Vieira, S.M. Solutions for detection of non-technical losses in the electricity grid: A review. Renew. Sustain. Energy Rev. 2017, 80, 1256–1268. [Google Scholar] [CrossRef]
- UMass Dataset. Available online: https://traces.cs.umass.edu/index.php/Smart/Smart (accessed on 10 October 2023).
- SGCC Dataset. Available online: https://github.com/henryRDlab/ElectricityTheftDetection (accessed on 10 October 2023).
- Irish Smart Energy Trial (ISET) Dataset. Available online: https://www.ucd.ie/issda/data/commissionforenergyregulationcer/ (accessed on 10 October 2023).
- Household Electric Power Consumption. Available online: https://www.kaggle.com/datasets/uciml/electric-power-consumption-data-set?resource=download (accessed on 10 October 2023).
- Electric Load Diagrams Dataset. Available online: https://archive.ics.uci.edu/ml/datasets/ElectricityLoadDiagrams20112014 (accessed on 10 October 2023).
- Load Profiles for TMY3 Location Dataset. Available online: https://data.openei.org/submissions/153 (accessed on 10 October 2023).
- Low Carbon London Smart Meter Trial Dataset. Available online: https://data.london.gov.uk/dataset/smartmeter-energy-use-data-in-london-households (accessed on 10 October 2023).
- Open Energy Information. Available online: https://openei.org/wiki/Data (accessed on 10 October 2023).
- Pecan Street Dataset. Available online: https://www.pecanstreet.org/work/energy/ (accessed on 10 October 2023).
- AEA Dataset. Available online: https://www.aeaweb.org/journals/data/data-code-policy (accessed on 10 October 2023).
- PRECON Dataset. Available online: https://web.lums.edu.pk/~eig/precon.html (accessed on 10 October 2023).
- Nadeem, A.; Arshad, N. PRECON: Pakistan Residential Electricity Consumption Dataset. In Proceedings of the 2019 the Tenth ACM International Conference on Future Energy Systems, New York, NY, USA, 25–28 June 2019. [Google Scholar]

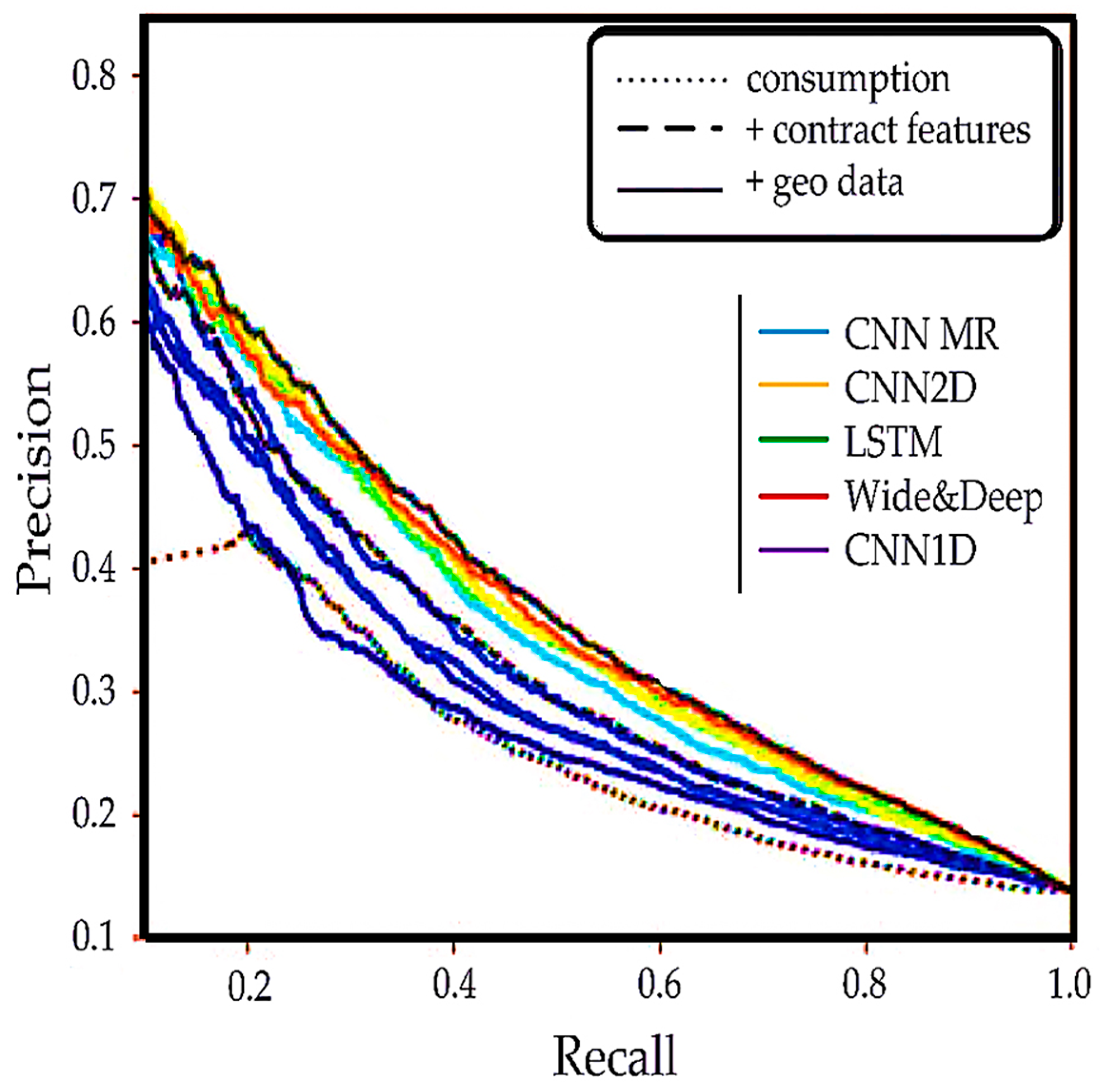
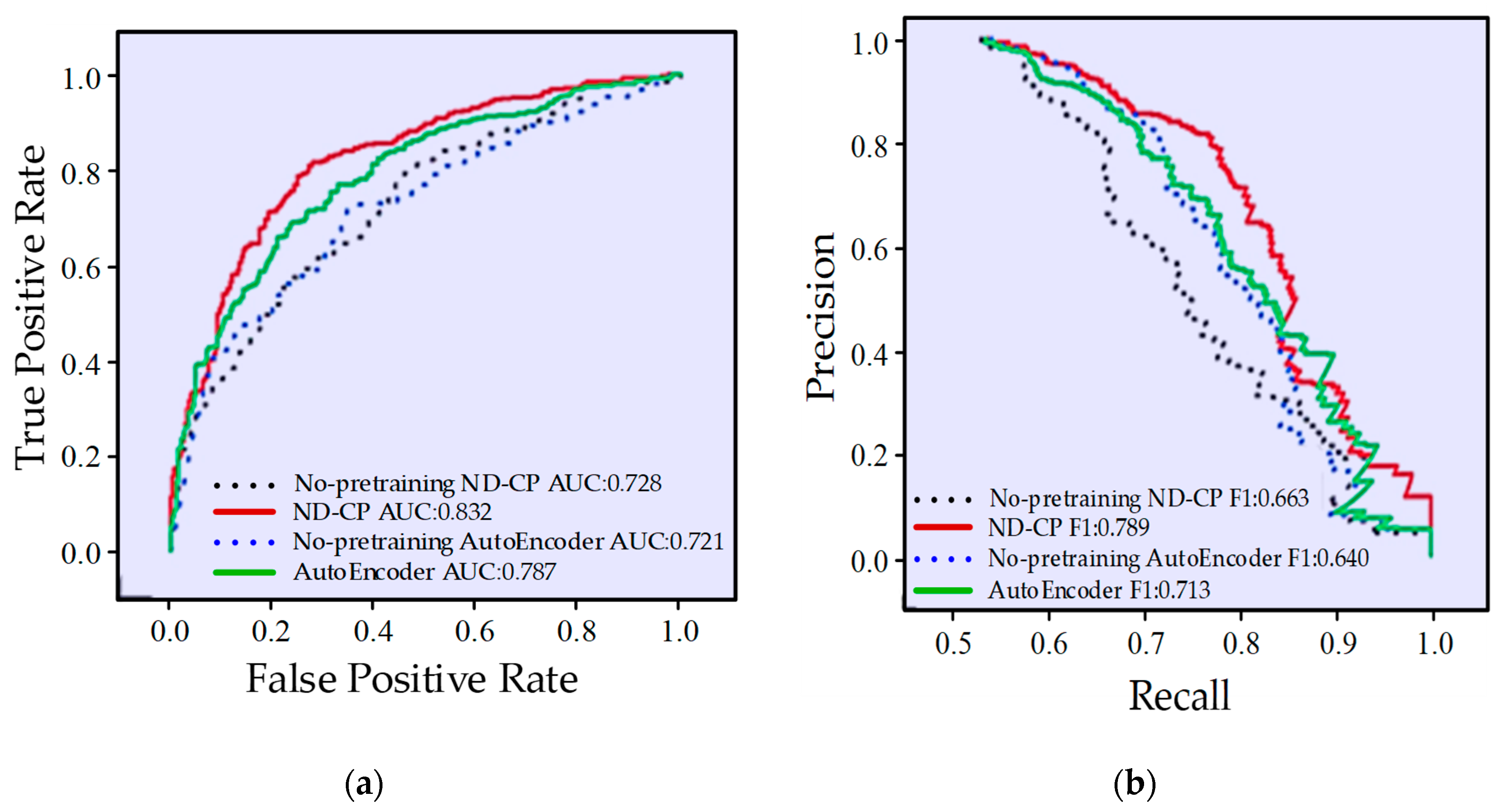
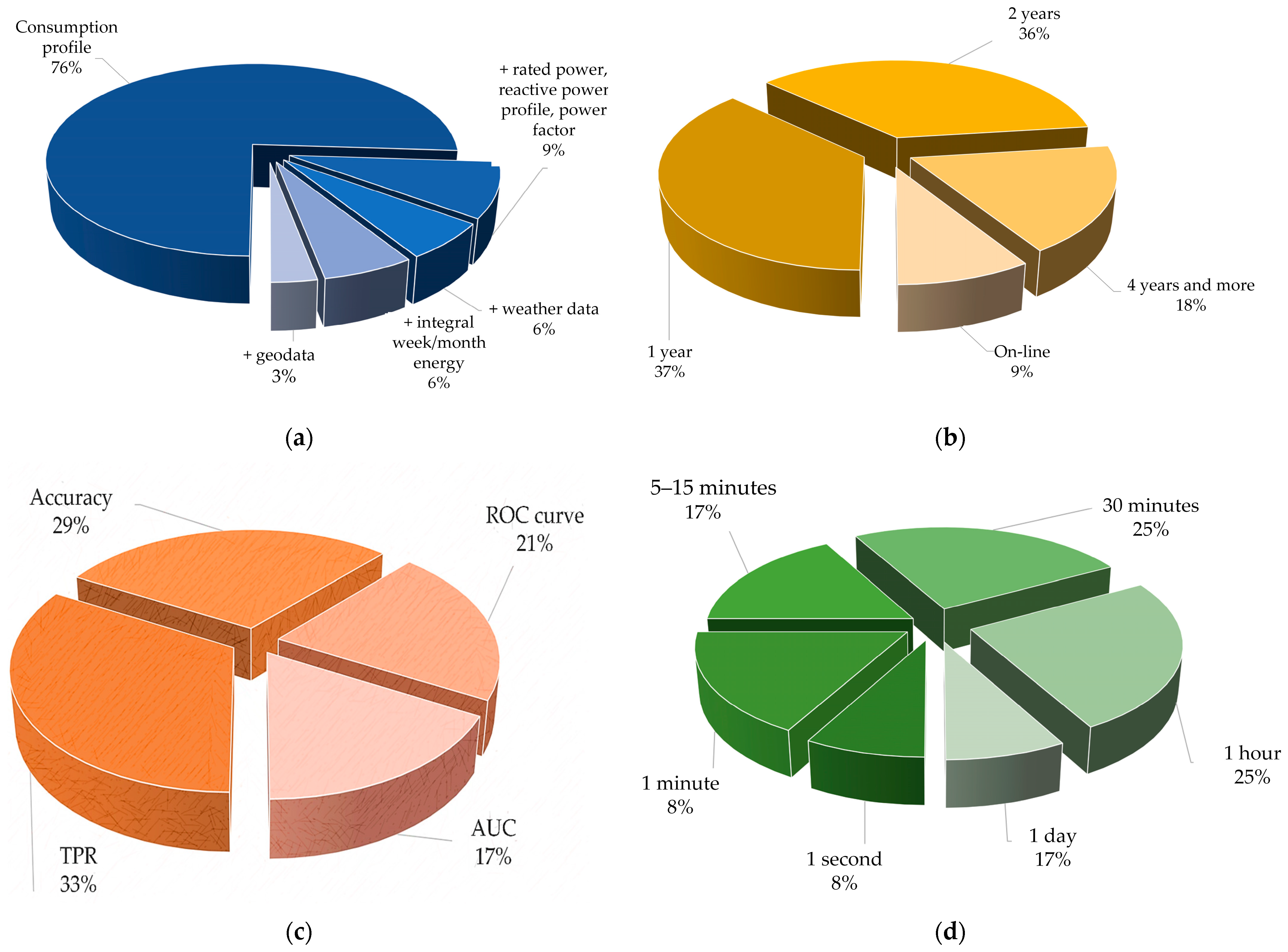

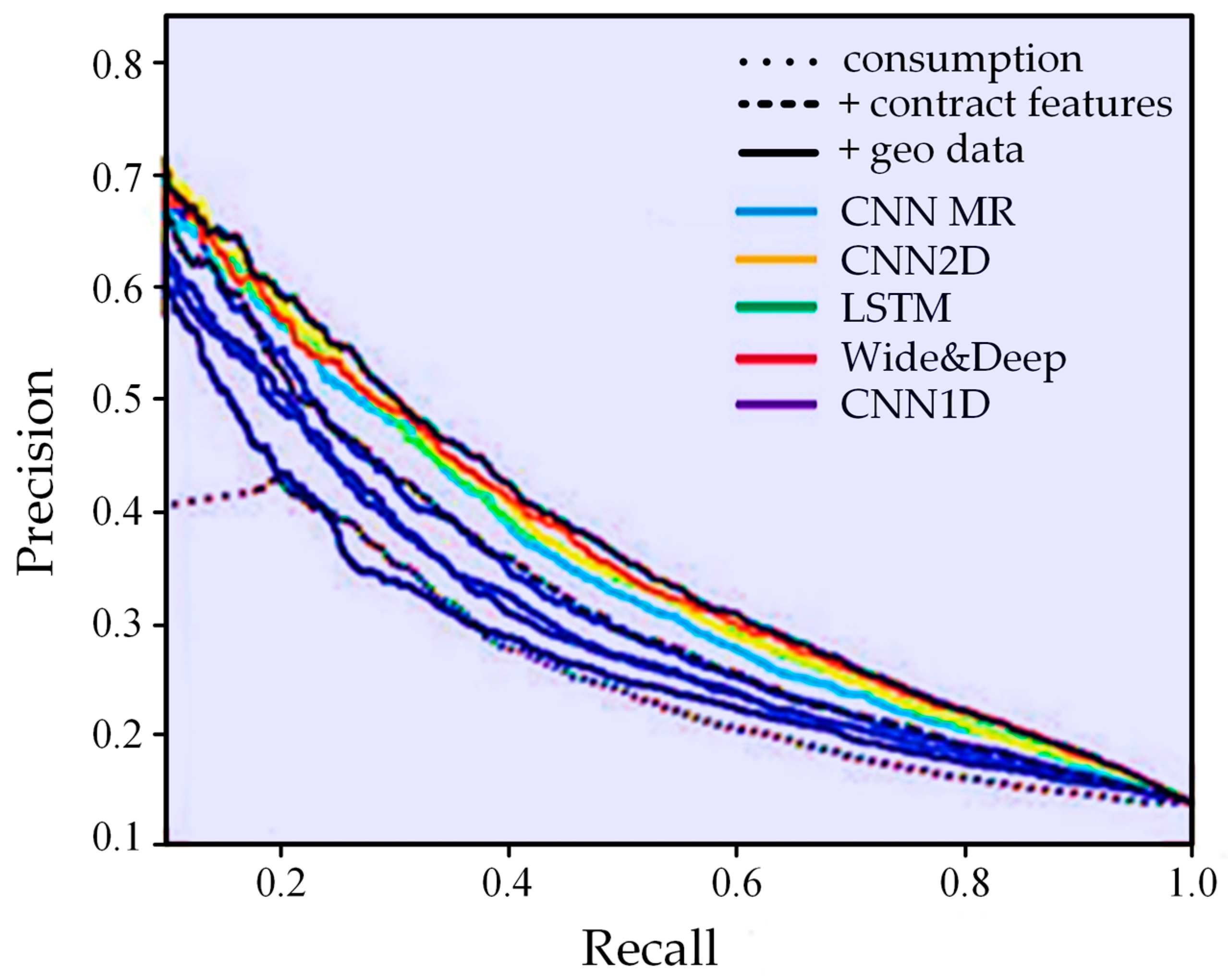
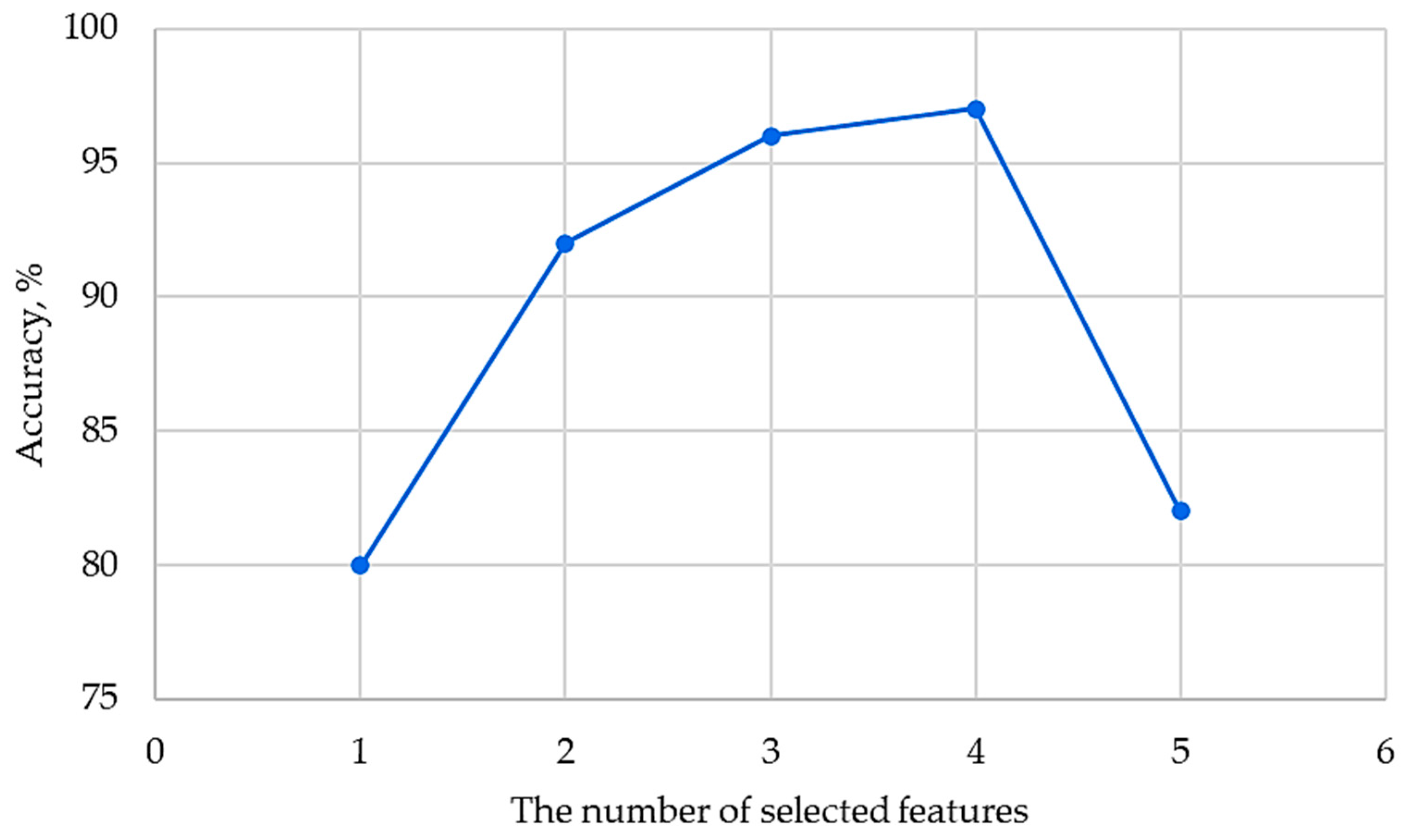
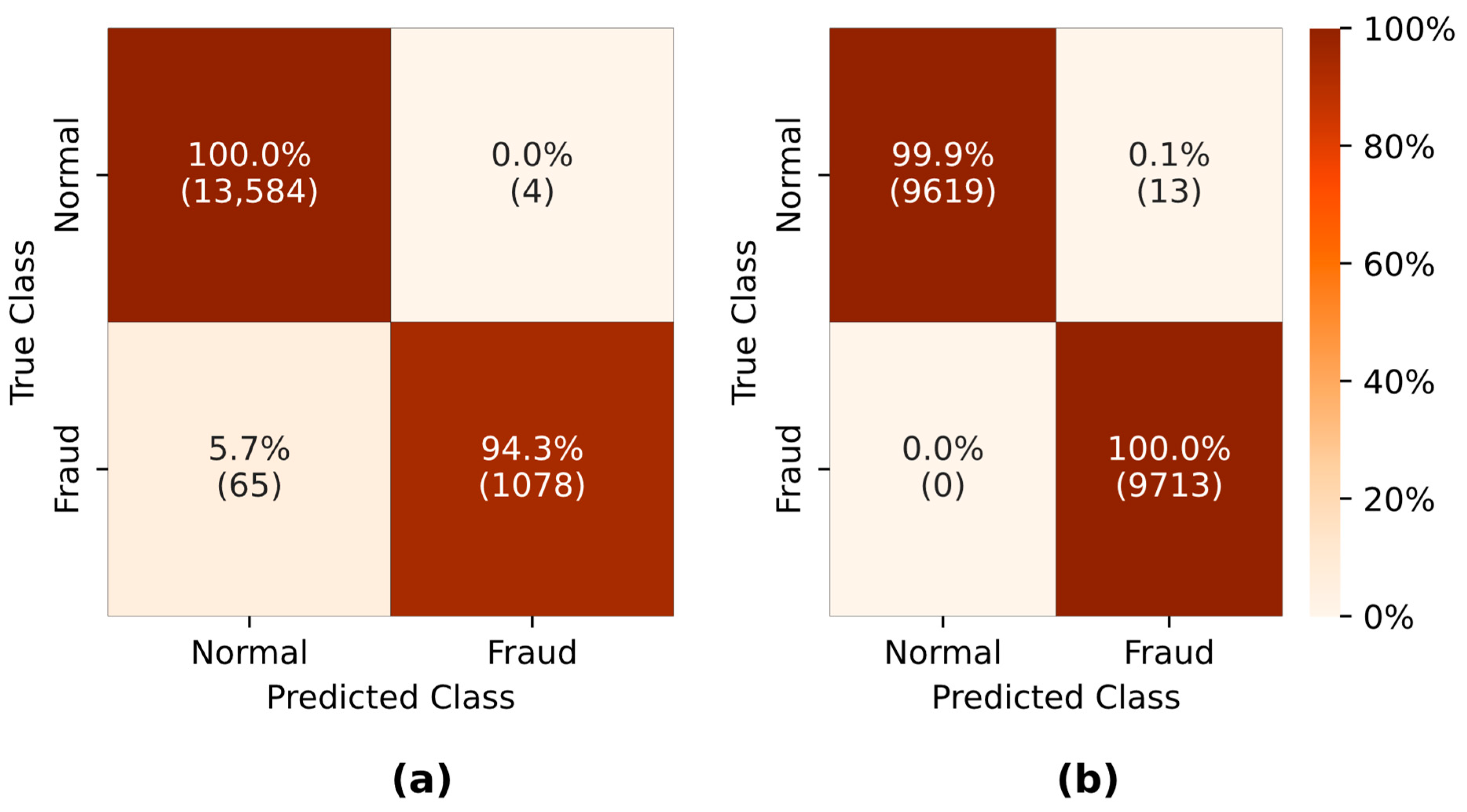
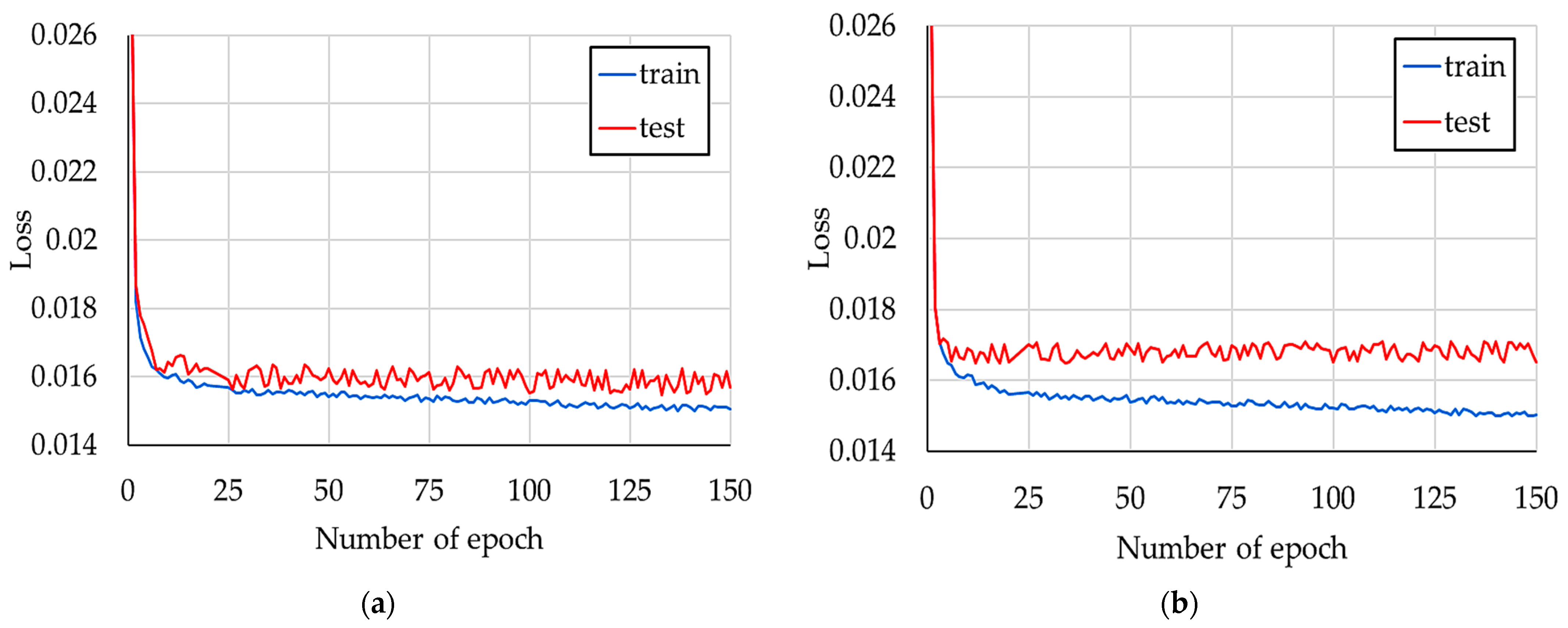
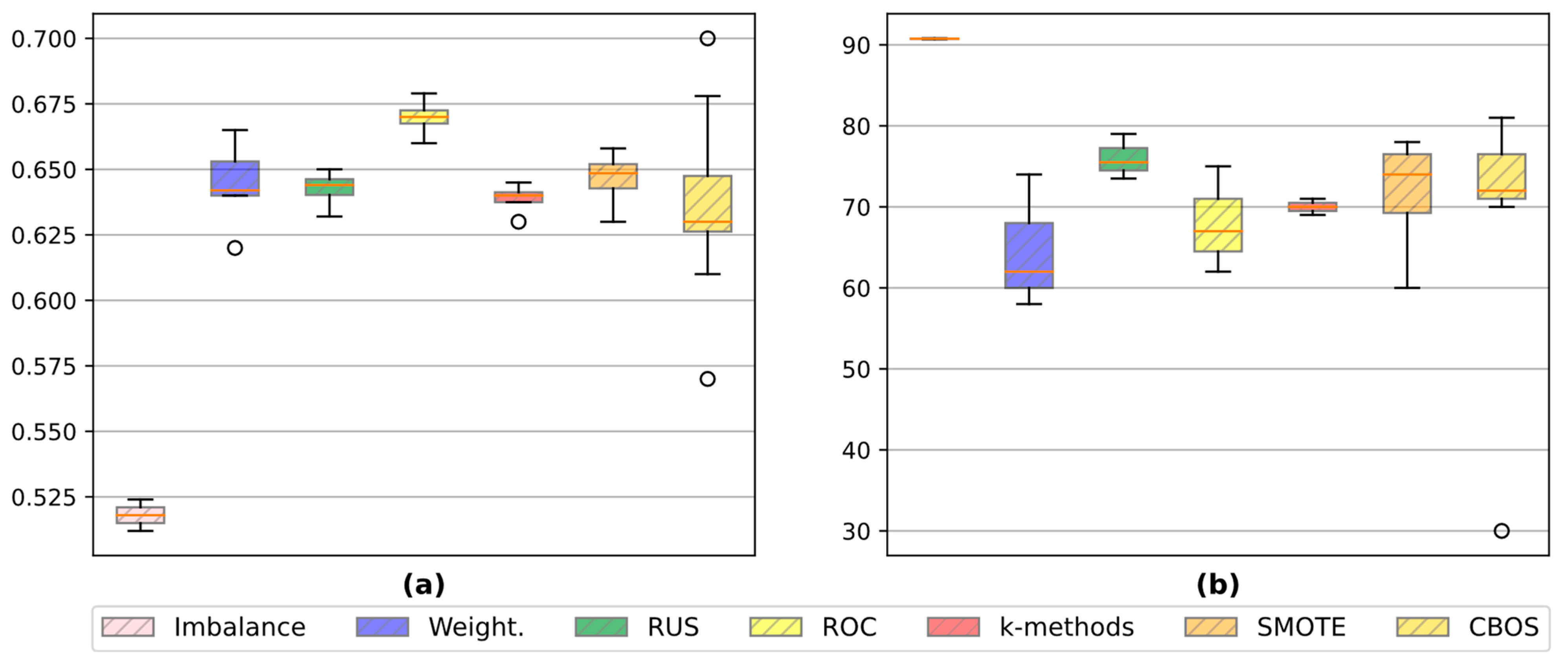
| Ref. | Method/Algorithm | Time Step | Data Source | Additional Data Used | Metrics Used | Efficiency | Comments |
|---|---|---|---|---|---|---|---|
| [26] | Fuzzy logic: c-means algorithm, maximum likelihood criterion | 1 h | Synthetic (33-bus distribution system) | Topology, types of consumers | - | The error of load estimation in 80% of feeders was obtained less than 6% | The article, in addition to identifying power imbalances associated with non-commercial losses, focused on the optimal placement of accounting tools. |
| [27] | Logistic regression, random forest, support vector machine, artificial neural network with various balancing techniques | 1 day | State Grid Corporation of China (SGCC) dataset | - | ROC curve F1 score accuracy | Accuracy: from 49 to 92% depending upon method and balancing technique used | The article was primarily devoted to comparing different methods of classifying consumers with unbalanced data. |
| [28] | Gradient boosting, logistic regression | 1 month | Anonymous dataset, containing Spanish house and apartment energy profiles for two regions | Visit-related customer features, sociological features (average annual income, etc.), contractual information | - | - | The paper proposed a regression model to identify the sources of nontechnical losses. |
| [30] | Decision tree regression, linear regression, sequential neural network, multilayer perceptron regression | 15 min | Energy consumption from three smart meters over a 2-year horizon (time step—15 min) | - | MAPE | MAPE: from 11 to 27 % depending on method and size of database | In the article, several machine learning methods were tested and compared on real data. It was shown how the accuracy of the assessment of involvement in theft varies depending on the dataset for training. |
| [31] | Linear regression-based algorithms | 30 min | Synthetic: real SEAI consisting of half-hourly energy usage reports for over 5000 Irish residential and commercial premises. Energy fraud was simulated. | - | Own indexes: anomaly and detection coefficients | - | A methodology for determining and managing accounts in the smart grid network was proposed. Consumer attention was drawn to the presence of anomalies and detection coefficients. |
| [35] | Pearson correlation algorithm | 5 min | Sample consisted of real data but was very small (only 16 users) | - | - | Accuracy: 62.5% | The work aimed at identifying mining farms involved in the theft of electrical energy based on the correlation between subscriber consumption and network losses. |
| [36] | Outlier detection | - | Real voltage data consisting of 320 high-voltage consumers’ energy and voltage profiles | - | - | - | Theft of electrical energy was determined based on the difference in voltage profiles: the greater the discrepancy, the more likely it is that the deviant was involved in the theft. |
| [38] | Fuzzy logic algorithm based on covariance analysis and optimization | 15 min | State Grid Corporation of China (SGCC) dataset. Energy fraud was simulated. | - | AUC, ROC curve | AUC: 0.998 | The method is based on the following observation: the correlation between the graph of total nontechnical losses and the graph of the consumer is maximal if he is involved in these losses. At the same time, only fixed-ratio electrical energy thieves were considered. Then, the optimization method identified consumers who best explained the presence of NTL. |
| [39] | Correlation analysis | 5 min | “Smart” dataset UMass (114 single-family apartments, western Massachusetts) | - | MAP@K | MAP@K: from 0.60 to 0.86 depending on fraction of thief consumers | Similar to the article above, consumers involved in theft were identified based on the correlation between their consumption schedule and the curve of nontechnical losses in the network area. |
| [43] | Artificial neural network with balancing approach + simulated annealing for hyperparameter configuration | 1 h | State Grid Corporation of China (SGCC) dataset (3615 dishonest and 38,757 fair consumers) | - | TPR, FNR, FPR, TNR, AUC | AUC: 0.987 | The paper described a complete framework for identifying unscrupulous consumers, including data preprocessing, data resampling and balancing, optimal hyperparameters using simulated annealing, ANN classifier. |
| [44] | Long short-term memory with the attention mechanism + particle swarm optimizer | 1 h | Public dataset of the University of Massachusetts | Hourly temperature, humidity, body temperature | RMSE, MAE, MAPE, AE, M, PR, FPR | MAPE: 0.087 MAE: 0.152 RMSE: 0.186 | The paper presented a model for identifying unscrupulous consumers based on LSTM with attention mechanism while particle swarm algorithm was used in order to choose optimal neural network settings. Results were compared with CNN-LSTM, LSTM, gated recurrent unit (GRU), SVM, RF, and LR. |
| [45] | Artificial neural network + Bayesian optimization | 1 h | State Grid Corporation of China (SGCC) dataset | - | TPR, FNR, FPR, TNR, AUC, MAP@N, F1-score | F1 score: 0.582 AUC: 0.919 | The paper proposed a framework for identifying sources of commercial losses. Its basis was a neural network while a Bayesian optimizer was used to optimize hyperparameters and network architecture. |
| [48] | Multilayer perceptron artificial neural network (MP-ANN) with self-organizing mapping (SOM) | 3 h | Synthetic dataset based on IEEE70 test distribution network | - | FPR, detection rate (DR), highest difference (HD) | DR: 93.4% FPR: 1.9% HD: 91.5% | The paper proposed to identify unscrupulous consumers in two stages: at the first stage, they were classified using SOM in the form of a daily load schedule for characteristic groups, at the second—with the help of MP-ANN trained into separate groups—unscrupulous EE consumers were identified. |
| [60] | Anomaly coefficient method | 1 h | Original synthetic dataset (five consumers) | - | - | - | The paper proposed a method for calculating anomaly coefficients for consumers, according to which unscrupulous subscribers could be prioritized. To evaluate these coefficients, a system of linear equations was solved based on measurements of individual consumer counters and a balancing counter. |
| [63] | Correlation analysis algorithm | 1 h | Original synthetic dataset (50 consumers) | Current and voltage daily profiles, type of meter placement | - | - | Unscrupulous consumers were identified based on the correlation between technical losses in the network and the profile of consumers’ electrical energy, taking into account the installation location of the meter and the possibility of theft. |
| [65] | k-means, support vector machine (SVM), risk assessment | 1 h | Real data from Tianjin Electric Power Company (460 feeders) | Grid topology | - | - | A three-stage algorithm for identifying sources of commercial losses: feeders with an abnormal loss profile (clustering and SVM) were determined, the time points at which abnormal losses were observed (according to statistics) were determined, the source of such losses in the network was based on steady-state simulation. |
| [66] | Extreme gradient-boosted trees | 6 h | Real energy recordings over 10 years | Alarm signals from meters, reactive power, voltage and current magnitudes, GIS, contract conditions, meter location | ROC curve, TPR, FPR, precision, AUC | AUC: from 0.76 to 0.91 depending on input data types | The main value of the work is an experiment to train a classifier model on a large sample of real measurements of data and other information about consumers. In particular, it was shown that taking into account additional factors and data makes it possible to increase the accuracy of the model. |
| [67] | Convolutional neural network, support vector machine | 1 day | Real energy recordings over 1 year containing energy profiles of 26,530 consumers | - | TNR, TPR, ROC curve, F1 score, precision, recall | All metrics: greater than 85% | The paper proposed a consumer classifier model based on a convolutional neural network and SVM. The first one was used to reduce the dimension of the problem state space and identify the main features (specific features). The values obtained at the output were processed using an SVM to classify consumers into honest and unscrupulous. |
| [70] | Decision tree combined k-nearest neighbor, support vector machine | 30 min | Real Irish Smart Energy Trial energy consumption dataset (theft data were generated using Wasserstein generative adversarial networks) | A number of energy curve characteristics (daily maximum load, load rate, coefficient of variation, etc.) | Accuracy, AUC | Accuracy: 95.6% | The paper proposed a model combining decision tree, k-nearest neighbor algorithm, and support vector machine. The influence of the number of factors taken into account on the accuracy of classification was also investigated. |
| [71] | Support vector machine, voltage sensitivity analysis | 30 min | Real Irish Smart Energy Trial energy consumption dataset (theft data were generated) | Topology, voltage measurements | DR, accuracy, AUC | Accuracy: (1) 91.2 (2) 99.4 (3) 99.4 AUC: (1) 93.7 (2) 99.9 (3) 99.9 | The study described three approaches to identifying sources of losses: based on SVM (1), based on the results of stress sensitivity analysis (2), and also as a solution to the optimization problem of distribution of losses between nodes (3). For the last two cases, voltage measurements were required. |
| [77] | Deep reinforcement learning, convolutional neural network | 30 min | Real Irish Smart Energy Trial energy consumption dataset (theft data were generated) | - | TPR, FPR, FOR, F1-score, Precision | F1 score: from 90.16 to 99.89 depending on balancing method | The paper described how consumer classification can be implemented using the reinforcement learning method. A convolutional network was used to increase the sensitivity of the framework when analyzing time series of consumption. |
| [80] | Convolutional neural network, k-means | 1 h | State Grid Corporation of China (SGCC) dataset | - | TPR, FPR, AUC, FOR, F1 score, precision | AUC: 0.92 F1 score: 0.60 | In addition to the scheme of joint use of CNN and k-means, a new factor was introduced in the article—location information of missing values. |
| [83] | Convolutional neural network with gated recurrent unit + manta ray foraging optimizer for tuning | 1 day | State Grid Corporation of China (SGCC) dataset | - | Accuracy, precision, recall, F1 score | Accuracy: 91.10% AUC: 0.91 Recall: 93% Precision: 91.11% F1 score: 89% | The paper showed that the use of a metaheuristic approach, for example, manta ray foraging optimizer, for setting up a neural network makes it possible to increase the sensitivity of the network when identifying unscrupulous electrical energy consumers. |
| [84] | Convolutional neural network, long short-term memory | 1 h | State Grid Corporation of China (SGCC) dataset | Accuracy, precision, recall | Accuracy: 89% Precision: 0.90 Recall: 0.87 | In many ways similar to [86]. | |
| [85] | Deep Siamese network, long short-term memory, convolutional neural network | 1 h | State Grid Corporation of China (SGCC) dataset | - | Accuracy, precision, recall, F1 score, specificity, AUC, MAP@N | AUC: 0.934 Accuracy: 0.953 | The paper proposed a model that allows users to search for unscrupulous consumers. The model involved data processing in four stages: preprocessing of electrical energy profiles, feature extraction with convolutional neural network, analysis of sequential time series, and classification of consumers. |
| [86] | Convolutional neural network, random forest classifier | 1 h | Electric Ireland and Sustainable Energy Authority of Ireland dataset (5000 residential households and business). Thefts were generated synthetically. | - | Precision, recall, F1 score, AUC, accuracy | AUC: 0.99 | The paper showed a framework in which CNN was used to identify essential features of consumption profiles, and RF was used to classify consumers, according to these characteristics, into conscientious and unscrupulous. |
| [87] | Deep neural network | 1 h | State Grid Corporation of China (SGCC) dataset (3615 dishonest and 38,757 fair consumers) | - | AUC, accuracy, TPR, FPR, F1 score, MCC, PPV | AUC: 97% Accuracy: 91.8% | The study showed the prospects of using a deep learning network to identify sources of losses. The experiment demonstrated that such a multilayer neural network can provide classification accuracy higher than solutions combining autoencoders, convolutional networks, etc. |
| [89] | Component analysis, sparse autoencoder + differential evolution and JAYA methods for classification | 1 h | State Grid Corporation of China (SGCC) dataset (3615 dishonest and 38,757 fair consumers), UMass (114 single-family apartments, western Massachusetts) | - | Accuracy, AUC, F1 score, specificity, recall, precision | Accuracy: from 0.956 to 0.993 AUC: from 0.833 to 0.957 depending on dataset and metaheuristic classifier | The paper proposed an algorithm for identifying unscrupulous consumers based on component analysis, an autoencoder, as well as classifiers based on differential evolution and JAYA techniques (DE-RUSBoost and JAYA-RUSBoost, respectively). The developed solution was compared with other classification methods. |
| [91] | Denoising autoencoder and attention-guided triple GAN | 1 h | State Grid Corporation of China (SGCC) dataset (3615 dishonest and 38757 fair consumers) | - | Accuracy, AUC, F1 score, MCC, recall, precision | Precision: 0.987 AUC: 0.952 | The paper proposed a combination of autoencoder and attention guided triple GAN, which made it possible to identify significant features from the input data and identify sources of commercial losses. |
| [92] | Stack autoencoder | 1 h | Real energy profiles dataset for 1201 consumers from Fujian, China | - | DR, FPR, ROC curve, AUC | DR: 95% FPR: 7% | The paper proposed and investigated a noise-resistant autoencoder model. In addition, the optimal attack vector was obtained in the work, which allows users to assess the vulnerability of the developed model, to determine the limiting case in which the autoencoder does not react to the source of commercial losses. |
| [93] | Autoencoder with long short-term memory-based sequence to sequence structure | 30 min | Real Irish Smart Energy Trial energy consumption dataset (theft data were generated) | - | DR, FA, accuracy, AUC, ACC, F1 score, SP, PR | AUC: 90 Accuracy: 94.5 | The authors of the article proposed the structure of an autoencoder that also includes LSTM blocks. The effectiveness of various variants of the structure for detecting standard types of theft was investigated. |
| [96] | AlexNet and AdaBoost algorithms + artificial bee colony for hyperparameter tuning | 1 h | State Grid Corporation of China (SGCC) dataset (3615 dishonest and 38,757 fair consumers) | - | AUC, REC, PRE, F1 score, MCC, TPR, FPR | Precision: from 0.55 to 0.86 depending on balancing method | The article suggested a combination of existing methods to improve the results of the classification of consumers. The influence of data balance on classification results was investigated and three approaches were compared: no balancing, near miss, and synthetic minority oversampling techniques. |
| [97] | Ensemble machine learning | 30 min | Real energy profiles over 1 year. Thefts were simulated using predefined patterns | - | ROC curve, AUC, precision | Precision: form 0.88 to 0.99 depending on ensemble model and number of users considered | The work verified the effectiveness of ensemble machine learning models to identify unscrupulous consumers according to the daily load schedule. The accuracy of the classifier was investigated depending on the number of consumers under consideration. |
| [99] | XGBoost, random forest, Bayesian dropout neural network, support vector machine, linear regression, k-nearest neighbors | 1 month | Real database of 10,000 actual energy profiles clients over 1 year | - | ROC curve, precision, recall, AUPR (original authors’ metric) | Precision: 75% | The article proposed a method combining SVM and RF to identify new instances of unfair consumption. At the same time, the paper introduced a target cost function to determine consumers whose verification is economically feasible. |
| [100] | Random forest classifier | 1 month | Real database of 6029 clients from Montevideo city | Maximum power, days passed since the last inspection, contract conditions | AUC, accuracy, precision, recall, F1 score | Accuracy: 0.643 AUC: 0.646 Depending on set of metrics used | The paper presented an analysis of the impact of taking into account additional factors on the results of consumer classification. The results confirmed the expediency of taking into account many factors during classification. |
| Metric | Full Name | Formula |
|---|---|---|
| Rec, Sen, TPR | Recall, sensitivity, true positive rate | |
| FPR | False positive rate | |
| Spe, TNR | Specificity, true negative rate | |
| Pre | Precision | |
| Acc | Accuracy | |
| ROC curve | Receiver operating characteristic | - |
| AU-ROC | Area under ROC | |
| PR-curve | Precision recall curve | - |
| AU-PR | Area under PR | |
| Rec, Sen, TPR | Recall, sensitivity, true positive rate | |
| FPR | False positive rate | |
| Spe, TNR | Specificity, true negative rate |
| Consumer Data | Recognized as Measurements that Do Not Contain NTLEE | Recognized as Measurements Containing NTLEE |
|---|---|---|
| Without NTLEE | True negative (TN) | False positive (FP) |
| With NTLEE | False negative (FN) | True positive (TP) |
| № | Type ANN | Training Time, s | Recognition Time, s |
|---|---|---|---|
| 1 | Convolutional neural network with recurrent neural network (CNN + GRU) | 1611.10 | 2.49 |
| 2 | Autoencoder (AE) | 303.42 | 2.37 |
| 3 | Deconvolutional neural network (DNN) | 42.04 | 2.35 |
| 4 | Convolutional neural network (CNN) | 38.81 | 2.13 |
| № | Parameter | Comparison within a Group of Points of Time of a Single Consumer | Within a Group of Consumer Points for a Single Point of Time | |
|---|---|---|---|---|
| 1 | Multidimensionality | Two-dimensional—Intervals 1 h and more often | One-dimensional—Daily, monthly intervals | One-dimensional—Any interval |
| 2 | Dimension of the input layer | Number of days (31, no more than 90) × Number of measurements per day | Sampling depth × Number of measurements per day (1)) | Number of consumers × Number of measurements per day |
| 3 | Number of convolutional layers | 4–6 | 2–4 | 6+ |
| 4 | Dimension of the filter core | 3 × 3, 5 × 5 | 3 × 1–5 × 1 | 51 × 1–251 × 1 |
| 5 | Number of channels | 32–128 (fixed or layer-by-layer growth) | 32–128 (fixed or layer-by-layer growth) | 5–20 (growth by layers) |
| 6 | Number of subdiscretization layers | 1–2 times less convolutional layers | 1–2 times less convolutional layers | = number of convolutional layers |
| 7 | Number of normalization layers | 1 or = number of convolutional layers | 1 or = number of convolutional layers | not used or 1 |
| 8 | Normalization bucket size | 30–50 | 30–50 | minimum |
| 9 | Step | 1, in subdiscretization layers 2–3 | 1, in subdiscretization layers 2 | 1, in subdiscretization layers 2 |
| 10 | Learning rate | variable 10−5–10−2 | variable 10−5–10−2 | variable 10−5–10−2 |
| 11 | Percentage of excluded neurons | 0.3 | 0 | 0–0.3 |
| 12 | Number of fully connected layers | 3–5 | 3 | 1–3 |
| 13 | Number of neurons in a fully connected layer | 32–128 | 32–128 | 6+ |
| 14 | Number of training epochs | 100–300 to 500 | 100 | 50 |
| 15 | Activation function | ReLU, LeakyReLU | ReLU, Sigmoid (last layer) | Sigmoid, ReLU |
| 16 | Learning algorithm | SGD | Adam, SGD | SGD, Adam |
| № | Parameter | Autoencoder (AE, SAE, DAE, VAE, etc.) | Managed Recurrent Blocks | Long-Term-Short-Term Memory Networks | Direct Distribution Networks (Multilayer Perceptrons) |
|---|---|---|---|---|---|
| 1 | Application | Time series analysis | Memory elements | NON-time series analysis for NTLEE | |
| 2 | Number of layers | 3, rarely 5 | 1–2 | 4 | |
| 3 | Number of neurons | 256-128-64-128-256 400-300-200-100-200-300-400 | 50–100 | 64–512 | |
| 4 | Learning rate | variable 10−4–10−1 | variable 10−4–10−1 | variable 10−5–10−2 | |
| 5 | Percentage of excluded neurons | 0.2–0.4 | 0.3–0.4 | 0–0.4 | 5–20 (growth by layers) |
| 6 | Number of training epochs | 30–60 | 20–30 | 50 | =number of convolutional layers |
| 7 | Activation function | ReLU | Tanh | Sigmoid, ReLU | not used or 1 |
| 8 | Learning algorithm | SGD | Adam, SGD | Adam | SGD, Adam |
| № | Dataset Name | Number of Consumers | Time Horizon | Discreteness |
|---|---|---|---|---|
| 1 | UMass Smart dataset [103] | Over 400 anonymous houses | Over 2 years | 1 min |
| 2 | SGCC dataset [104] | 42,372 users | Over 2 years | Day 1 |
| 3 | Irish Smart Energy Trial (ISET) dataset [105] | Over 5000 household, industrial and small-motor consumers | 535 days | 30 min |
| 4 | Individual household electric power consumption dataset [106] | 1 house | About 4 years old | 1 min |
| 5 | Electricity Load Diagrams dataset [107] | 370 consumers | About 4 years old | 15 min |
| 6 | Load Profiles for TMY3 Locations dataset [108] | More than 16 types of small-engine and household buildings at three locations in the USA | 1 year | 1 h |
| 7 | Low Carbon London Smart meter trials dataset [109] | 5567 households | Over 2 years | 30 min |
| 8 | Open Energy Information (OpenEI) [110] | 936 household consumers | 1 year | 60 min |
| 9 | Pecan Street dataset [111] | More than 1000 consumers | In real time | |
| 10 | AER dataset [112] | 25 households | 2 year | 30 min |
| 11 | PRECON [113,114] | 40 domestic households | 1 year | 1 s |
| № | Measurements | Recognized as Measurements, Not Containing NTLEE | Recognized as Measurements Containing NTLEE |
|---|---|---|---|
| 1 | Without balancing | 44 min | 12.58 s |
| 2 | Weight coefficients | 46.5 min | 15.85 s |
| 3 | RUS | 13 min | 9.13 s |
| 4 | ROS | 60 min | 13.52 s |
| 5 | K-medoids | 27 min | 11.66 s |
| 6 | SMOTE | 8 h and 12.5 min | 4 min and 12.71 s |
| 7 | CBOS | 8 h and 2 min | 30.59 s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pazderin, A.; Kamalov, F.; Gubin, P.Y.; Safaraliev, M.; Samoylenko, V.; Mukhlynin, N.; Odinaev, I.; Zicmane, I. Data-Driven Machine Learning Methods for Nontechnical Losses of Electrical Energy Detection: A State-of-the-Art Review. Energies 2023, 16, 7460. https://doi.org/10.3390/en16217460
Pazderin A, Kamalov F, Gubin PY, Safaraliev M, Samoylenko V, Mukhlynin N, Odinaev I, Zicmane I. Data-Driven Machine Learning Methods for Nontechnical Losses of Electrical Energy Detection: A State-of-the-Art Review. Energies. 2023; 16(21):7460. https://doi.org/10.3390/en16217460
Chicago/Turabian StylePazderin, Andrey, Firuz Kamalov, Pavel Y. Gubin, Murodbek Safaraliev, Vladislav Samoylenko, Nikita Mukhlynin, Ismoil Odinaev, and Inga Zicmane. 2023. "Data-Driven Machine Learning Methods for Nontechnical Losses of Electrical Energy Detection: A State-of-the-Art Review" Energies 16, no. 21: 7460. https://doi.org/10.3390/en16217460
APA StylePazderin, A., Kamalov, F., Gubin, P. Y., Safaraliev, M., Samoylenko, V., Mukhlynin, N., Odinaev, I., & Zicmane, I. (2023). Data-Driven Machine Learning Methods for Nontechnical Losses of Electrical Energy Detection: A State-of-the-Art Review. Energies, 16(21), 7460. https://doi.org/10.3390/en16217460









