Autonomous Scheduling for Reliable Transmissions in Industrial Wireless Sensor Networks
Abstract
1. Introduction
- Auto-Sched enhances the reliability of data transmissions. To do so, it provides dedicated slots for autonomous transmission and retransmission scheduling. Each node autonomously computes its transmission and reception time slot scheduling based on hop counts to the gateway, its unique identifier (MAC address or a unique node ID [14]), the current link quality and the worst-case link quality constraints in the network. For uplink schedules, our methodology to ensure allocating collision-free time slots is to create parallel pipeline-like communication schedules for all nodes, where each pipeline in the scheduling table starts from the slot allocated to the source node and ends at the slot allocated to the gateway. Similarly, for downlink schedules, parallel downward pipeline-like communication schedules are constructed, starting from the slot allocated to the gateway and ending at the slot allocated to the corresponding destination actuator node. Our performance analysis in Section 5 demonstrates that Auto-Sched significantly enhances the packet delivery ratio (PDR) and mitigates end-to-end delays across varying network sizes and packet generation intervals, compared with widely adopted techniques in [13,15,17].
- Auto-Sched enhances robustness against network changes. We propose a simple algorithm that enables a node aimed at changing the parent (due to link or node failures) or joining the network, delivering its request to intermediate nodes through the new path to the gateway within, at most, two slotframes. To do so, Auto-Sched allocates a time slot for each individual node in the network, to receive collision-free join or parent change requests. Once the request is passed through the intermediate nodes, the time and frequency scheduling are computed autonomously by Auto-Sched, enhancing resiliency against faults and minimizing packet drops. This means that, a multi-path or multicast approach is no longer needed to overcome node or link failure issues. This feature of Auto-Sched enables each node to flawlessly change parent and construct new routes in the event of link or node failure, with minimal influence on communications and computations. Our analysis shows superior performance in reducing delay and packet drop compared with approaches in [13,15].
2. Related Works
Discussions
3. Preliminaries
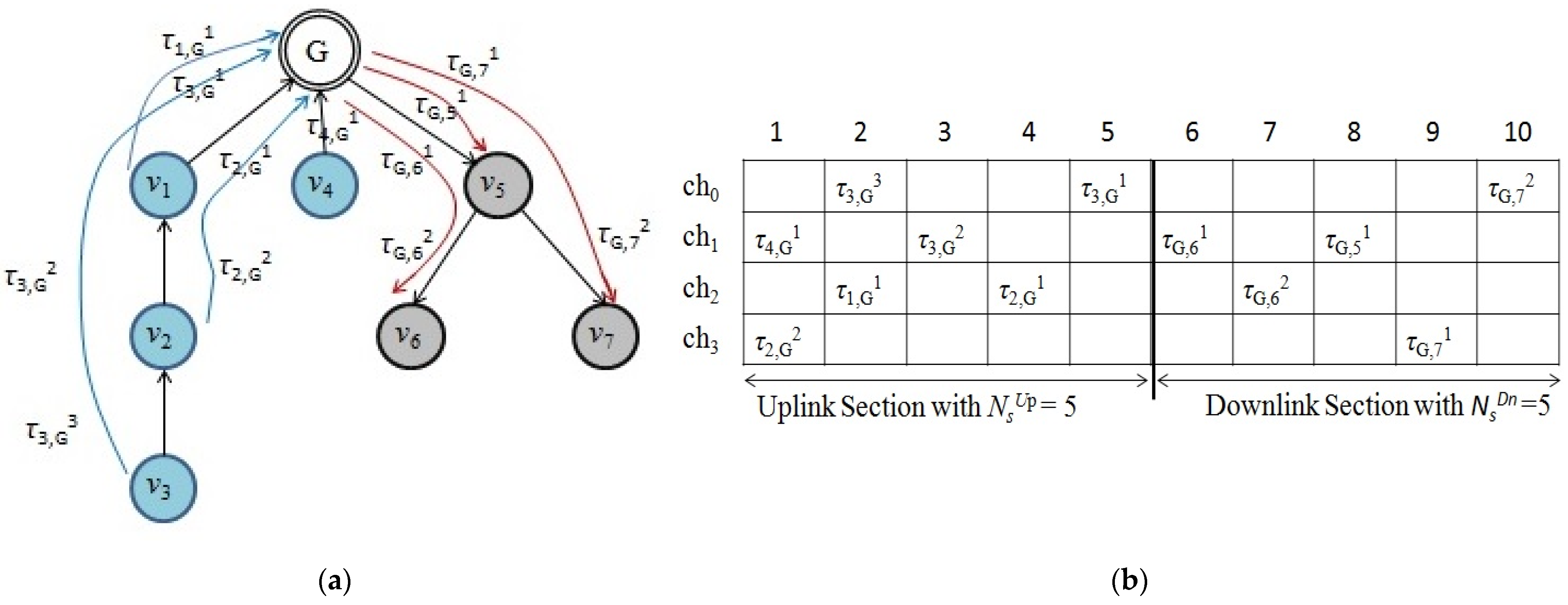
3.1. System Model and Notations
3.2. Overview of RPL DODAG Construction
3.3. Problem Definition
4. Autonomous Scheduling for Control Systems
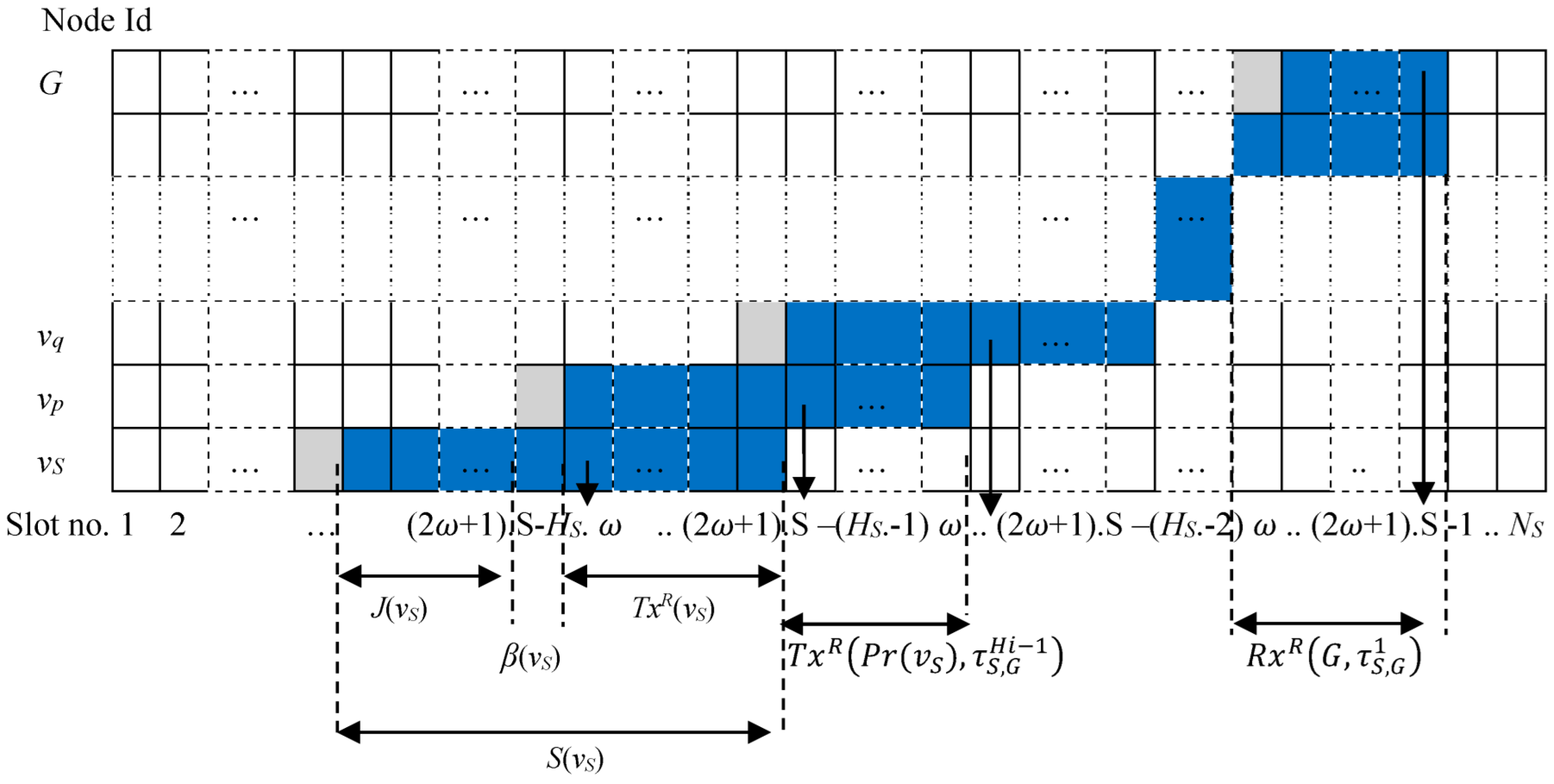
4.1. Autonomous and Reliable Time Slot Allocation for Uplink Traffic
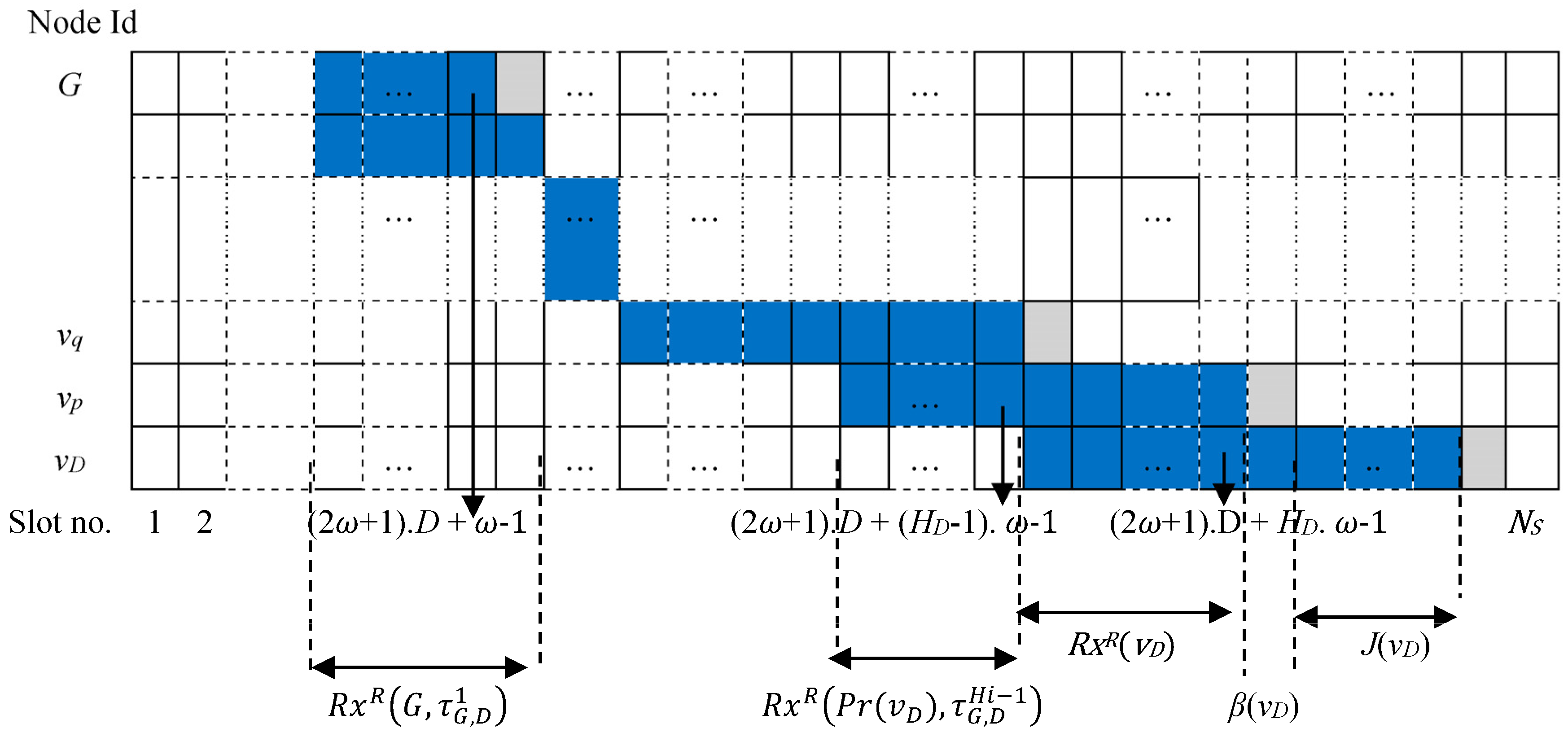
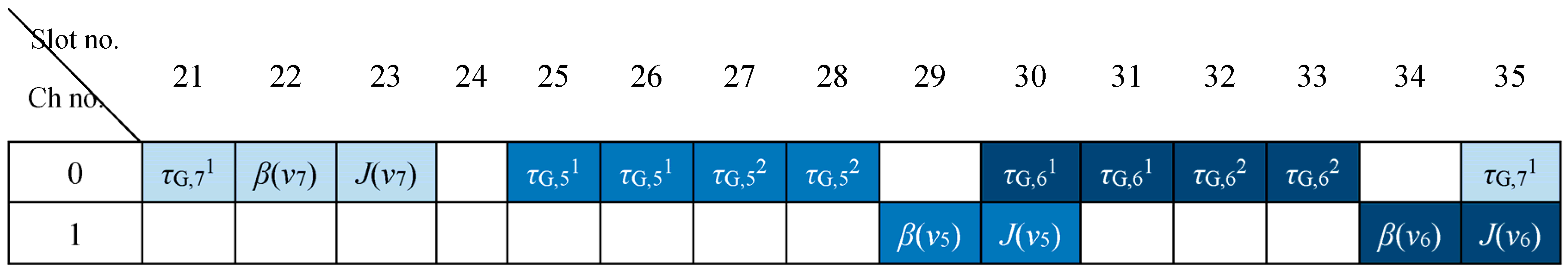
4.2. Autonomous and Reliable Time Slot Allocation for Downlink Traffic
4.3. Schedule Re-Construction after Link/Node Failure in Auto-Sched
| Algorithm 1: Auto-SchedU Schedule Reconstruction (NB(vi)) |
| 1: If (parent node failure), then |
| 1.1: Find the best parent vj ∈ NB(vi). |
| 1.2: Send DAO to J(vj). |
| 2: End If |
| 3: If(received DAO in J(vi)) |
| 3.1: Delay the current packet to next slotframe. |
| 3.2: Send the DAO within Auto-SchedU data slot to gateway, instead. |
| 3.3: Construct the new schedule for the new child, by Equations (11), (12), (15) and (16). |
| 4: End If. |
| 5: If(received DAO in Auto-SchedU data slot) |
| 5.1: Send the DAO within Auto-SchedU data slot to gateway. |
| 5.2: Construct the new schedule for the new child, by Equations (13)–(16). |
| 6: End If. |
| Algorithm 2: Auto-SchedD Schedule Re-Construction (NB(vi)) |
| 1: If (no packet received after a time out), then |
| 1.1: Find the best parent vj. |
| 1.2: Send DAO to J(vj). |
| 2: End If |
| 3: If(received DAO in J(vi)) |
| 3.1: Forward the DAO within J(P(vi)). |
| 3.2: Construct the new schedule for the new child, by Equations (27)–(30). |
| 4: End If. |
5. Experimental Results
5.1. Simulation Parameters
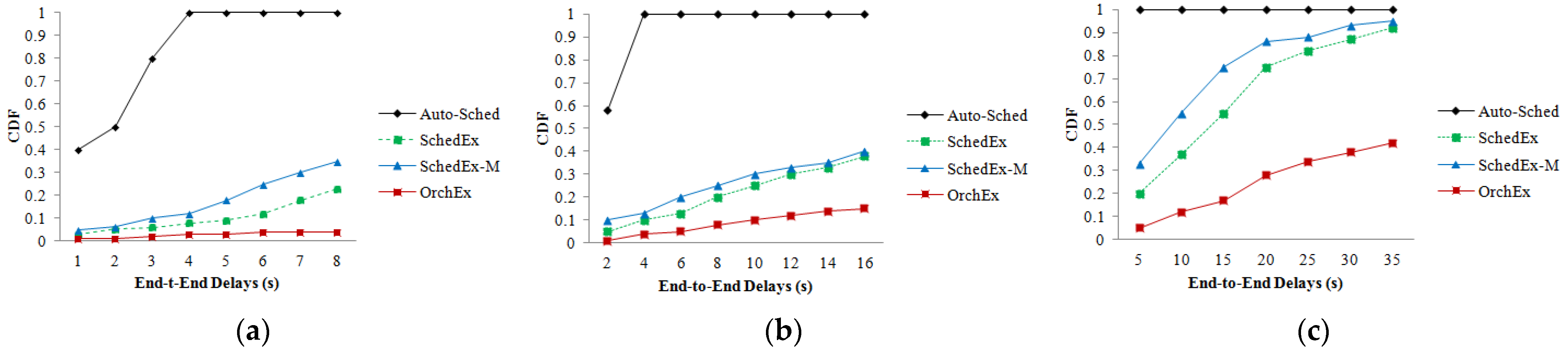
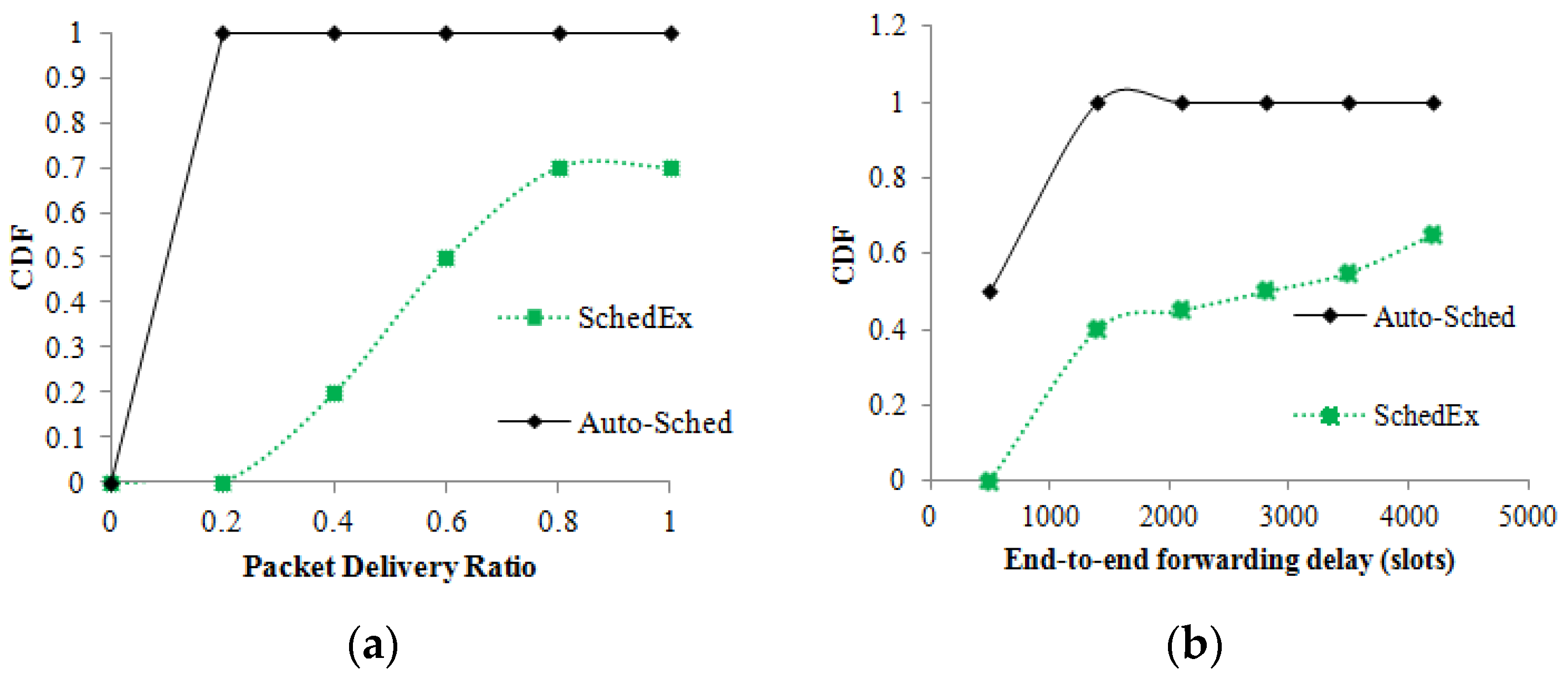
5.2. Performance under Interference
5.3. Performance under Node Failure
5.4. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Willig, A. Recent and emerging topics in wireless industrial communications: A selection. IEEE Trans. Ind. Informat. 2008, 4, 102–124. [Google Scholar] [CrossRef]
- Miorandi, D.; Uhlemann, E.; Vitturi, S.; Willig, A. Guest editorial: Special section on wireless technologies in factory and industrial automation, Part I. IEEE Trans. Ind. Informat. 2008, 3, 95–98. [Google Scholar] [CrossRef]
- Salvadori, F.; Gehrke, C.S.; de Oliveira, A.C.; de Campos, M.; Sausen, P.S. Smart grid infrastructure using a hybrid network architecture. IEEE Tran. Smart Grid 2013, 4, 1630–1639. [Google Scholar] [CrossRef]
- Ghayvat, H.; Liu, J.; Mukhopadhyay, S.C.; Gui, X. Wellness sensor networks: A proposal and implementation for smart home for assisted living sign in or purchase. IEEE Sens. J. 2015, 15, 7341–7348. [Google Scholar] [CrossRef]
- IETF 6TiSCH Working Group. Available online: https://datatracker.ietf.org/wg/6tisch/ (accessed on 25 August 2023).
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.W.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R.K. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. Available online: https://tools.ietf.org/html/rfc6550 (accessed on 25 August 2023).
- Gnawali, O.; Levis, P. The Minimum Rank with Hysteresis Objective Function. IETF 2012, RFC 6719. Available online: https://tools.ietf.org/html/rfc6719 (accessed on 25 August 2023).
- IEEE 802.15.4e; IEEE Standard for Local and Metropolitan Area Networks–Part 15.4: Low-Rate Wireless Personal Area Networks (LRWPANs) Amendment 1: MAC Sublayer. IEEE 802.15.4e Task Group: Piscataway, NJ, USA, 2012.
- Jung, J.; Kim, D.; Hong, J.; Kang, J.; Yi, Y. Parameterized slot scheduling for adaptive and autonomous TSCH networks. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018. [Google Scholar]
- Yan, M.; Lam, K.-Y.; Han, S.; Chan, E.; Chen, Q.; Fan, P.; Chen, D.; Nixon, M. Hypergraph-based data link layer scheduling for reliable packet delivery in wireless sensing and control networks with end-to-end delay constraints. Inf. Sci. 2014, 278, 34–55. [Google Scholar] [CrossRef]
- Hashimoto, M.; Wakamiya, N.; Murata, M.; Kawamoto, Y.; Fukui, K. End-to-end reliability- and delay-aware scheduling with slot sharing for wireless sensor networks. In Proceedings of the International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 5–10 January 2016. [Google Scholar]
- Yang, D.; Xu, Y.; Wang, H.; Zheng, T.; Zhang, H.; Zhang, H.; Gidlund, M. Assignment of segmented slots enabling reliable real-time transmission in industrial wireless sensor networks. IEEE Trans. Indust. Elec. 2015, 62, 3966–3977. [Google Scholar] [CrossRef]
- Shi, J.; Sha, M.; Yang, Z. Distributed graph routing and scheduling for industrial wireless sensor-actuator networks. IEEE/ACM Trans. Netw. 2019, 27, 1669–1682. [Google Scholar] [CrossRef]
- Duquennoy, S.; Al Nahas, B.; Landsiedel, O.; Watteyne, T. Orchestra: Robust mesh networks through autonomously scheduled TSCH. In Proceedings of the 13th ACM in Embedded Networked Sensor Systems, Seoul, Republic of Korea, 1–4 November 2015. [Google Scholar]
- Oh, S.; Hwang, K.; Kim, K.H.; Kim, K. Escalator: An autonomous scheduling scheme for convergecast in TSCH. J. Sens. 2018, 18, 1209. [Google Scholar] [CrossRef] [PubMed]
- Kim, S.; Kim, H.; Kim, C. ALICE: Autonomous link-based cell scheduling for TSCH. In Proceedings of the 18th ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Montreal, QC, Canada, 16–18 April 2019. [Google Scholar]
- Deac, D.; Teshoma, E.; Van Glabeek, R.; Doborota, V.; Breaken, A.; Steenhaut, K. Traffic aware scheduler for time-slotted channel-hopping-based IPv6 wireless sensor networks. J. Sens. 2022, 22, 6397. [Google Scholar] [CrossRef] [PubMed]
- Osman, M.; Nabki, F. OSCAR: An optimized scheduling cell allocation algorithm for convergecast in IEEE 802.15.4e TSCH networks. J. Sens. 2021, 21, 2493. [Google Scholar] [CrossRef] [PubMed]
- Zhang, T.; Gong, T.; Han, S.; Deng, Q.; Hu, X.S. Fully Distributed Packet Scheduling Framework for Handling Disturbances in Lossy Real-Time Wireless Networks. IEEE Trans. Mob. Comput. 2021, 20, 502–518. [Google Scholar] [CrossRef]
- Elsts, A.; Kim, S.; Kim, H.S.; Kim, C. An emprical survey of autonomous scheduling methods for TSCH. IEEE Access 2020, 8, 67147–67165. [Google Scholar] [CrossRef]
- Levis, P.; Patel, N.; Culler, D.; Shenker, S. Trickle: A selfregulating algorithm for code propagation and maintenance in wireless sensor networks. In Proceedings of the 1st USENIX/ACM Symposium on Networked Systems Design and Implementation, San Francisco, CA, USA, 29–31 March 2004. [Google Scholar]
- Vall, E.O.A.; Blough, D.; Ferri, B.H.; Rilley, G. Distributed global ID assignment for wireless sensor networks. Ad Hoc Netw. 2009, 7, 1194–1216. [Google Scholar] [CrossRef][Green Version]
- Vallati, C.; Brienza, S.; Anastasi, G.; Das, S.K. Improving network formation in 6TiSCH networks. IEEE Ttrans. Mob. Comput. 2019, 18, 98–110. [Google Scholar] [CrossRef]
- Osterlind, F.; Dunkels, A.; Eriksson, J.; Finne, N.; Voigt, T. Cross-level sensor network simulation with COOJA. In Proceedings of the 31st IEEE Conference on Local Computer Networks, Tampa, FL, USA, 14–16 November 2006. [Google Scholar]
- Zurawski, R. Networked embedded systems: An overview. In Networked Embedded Systems; Zurawski, R., Ed.; CRC Press: Boca Raton, FL, USA, 2009; Chapter 1; pp. 1.11–1.16. [Google Scholar]


| Scheduler | Strong Points | Limitations |
|---|---|---|
| Orchestra Receiver-based [14] | Simplicity, Low bandwidth, Low Energy consumption | Collision, hidden node, congestion and packet drop issues. |
| Orchestra Sender-based [14] | Delay, congestion and packet drop issues. | |
| OrchEx [17] | Simplicity, Improved collision and packet drop issues compared to Orchestra Receiver-based. | Collision, delay, congestion and packet drop issues persists in intermediate nodes that do not constitute the child nodes of gateway. |
| OSCAR [18] | Simplicity, Lower bandwidth and energy consumption compared to Orchestra Receiver-based. | Fixed amount of time slots are allocated to each node. Thus, for unreliable links or for high traffic loads, it may define insufficient resource allocation, while for high link qualities or for low traffic load, it may define unnecessary resource allocation. |
| ALICE [16] | Improved collision and packet drop issues compared to Orchestra. Supports both downlink and uplink traffic. | A single time slot is allocated to each communication link. Thus, it can result in insufficient resource allocation. |
| SchedEx [13] | Improves collision and packet drop issues compared to Orchestra Sender-based. Higher reliability in routing layer. | Fixed bandwidth is allocated to each node, which cannot be adopted to low or higher link quality constraints. Not usable with RPL standard. |
| Escalator [15] | Sufficient amount of bandwidth is granted to each node to deliver all buffered packets to the gateway within a single slotframe. | The resource allocation does not deal with links reliability, and an ideal link quality is assumed. No support for downlink traffic. |
| Symbol | Meaning | Symbol | Meaning |
|---|---|---|---|
| S(vS) | Set of time slots allocated to the source sensor node S, to transmit τS,G1, to receive join requests and to broadcast EBs. | RxR (vp, τS,G k) | The set of time slots allocated to intermediate node vp for receiving packet τS, due to the worst-case link quality. |
| TxR (vS) | The subset of time slots in S(vS) reserved for re-transmitting τS,G1 to pr(vS), in the worst-case link quality. | Rx(vp, τS,G k) | The subset of time slots in RxR(vp, τS,G k) allocated to intermediate node vp for receiving packet τS, due to the current actual link quality. |
| Tx (vS) | The subset of time slots in TxR (vS) used for re-transmitting τS,G1 to pr(vS), due to the current link quality. | FdR (vp, τS,G k) | The set of time slots allocated to intermediate node vp for forwarding packet τS, due to the worst-case link quality. |
| J(vS) | The subset of time slots in S(vS) that are utilized to receive join requests such as DAO and DIS. | Fd (vp, τS,G k) | The subset of time slots in FdR (vp, τS,G k) allocated to intermediate node vp for forwarding the packet τS, due to the current actual link quality. |
| B(vS) | A time slot in S(vS) that is utilized to broadcast EB control packets. | Ch_Tx(vi) | The channel offset allocated to each node vi to transmit the buffered packets. |
| Ch_Rx(vi) | The channel offset allocated to each node vi to receive the data packets from child nodes. |
| Symbol | Meaning | Symbol | Meaning |
|---|---|---|---|
| RxR(vD) | The set of time slots reserved for receiving the control packet generated by gateway and destined for destination actuator vD, in the worst-case link quality. | RxR(vp, τS,G k) | The set of time slots allocated to intermediate node vp for receiving packet τS, due to worst-case link quality. |
| Rx(vD) | The subset of time slots in RxR(vD), used for receiving the control packet generated by the gateway and destined for vD, due to current actual link quality. | Rx(vp, τS,G k) | The subset of time slots in RxR(vp, τS,G k) allocated to intermediate node vp for receiving packet τS, due to current actual link quality. |
| J(vD) | The set of time slots that node vD utilizes for receiving join requests such as DAO and DIS. | FdR (vp, τS,G k) | The set of time slots allocated to intermediate node vp for forwarding the packet τS, due to the worst-case link quality. |
| B(vD) | A time slot that that node vD utilizes to broadcast EB control packets. | Fd (vp, τS,G k) | The subset of time slots in FdR (vp, τS,G k) allocated to intermediate node vp for forwarding the packet τS, due to the current actual link quality. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Darbandi, A.; Kim, M.-K. Autonomous Scheduling for Reliable Transmissions in Industrial Wireless Sensor Networks. Energies 2023, 16, 7039. https://doi.org/10.3390/en16207039
Darbandi A, Kim M-K. Autonomous Scheduling for Reliable Transmissions in Industrial Wireless Sensor Networks. Energies. 2023; 16(20):7039. https://doi.org/10.3390/en16207039
Chicago/Turabian StyleDarbandi, Armaghan, and Myung-Kyun Kim. 2023. "Autonomous Scheduling for Reliable Transmissions in Industrial Wireless Sensor Networks" Energies 16, no. 20: 7039. https://doi.org/10.3390/en16207039
APA StyleDarbandi, A., & Kim, M.-K. (2023). Autonomous Scheduling for Reliable Transmissions in Industrial Wireless Sensor Networks. Energies, 16(20), 7039. https://doi.org/10.3390/en16207039









