Smart Contract Vulnerability Detection Model Based on Siamese Network (SCVSN): A Case Study of Reentrancy Vulnerability
Abstract
1. Introduction
- Applying the natural language processing side to smart contract processing, and proposing a smart contract embedding method that reduces the impact of irrelevant content on smart contract vulnerability detection.
- This is the first model that applies the Siamese network to smart contract vulnerability detection at the source code level. SCVSN improves the accuracy of smart contract vulnerability detection and reduces the false positive rate of smart contract vulnerability detection by calculating the similarities. To ensure that the number of positive and negative sample pairs is balanced during training, we also propose a classification algorithm for positive and negative sample pairs.
- The SCVSN model proposed in this paper is demonstrated to have excellent performance in smart contract vulnerability detection tasks through extensive experiments on the existing smart contract dataset, and the SCVSN model is compared with the deep learning-based smart contract vulnerability detection methods proposed in previous studies.
2. Related Work
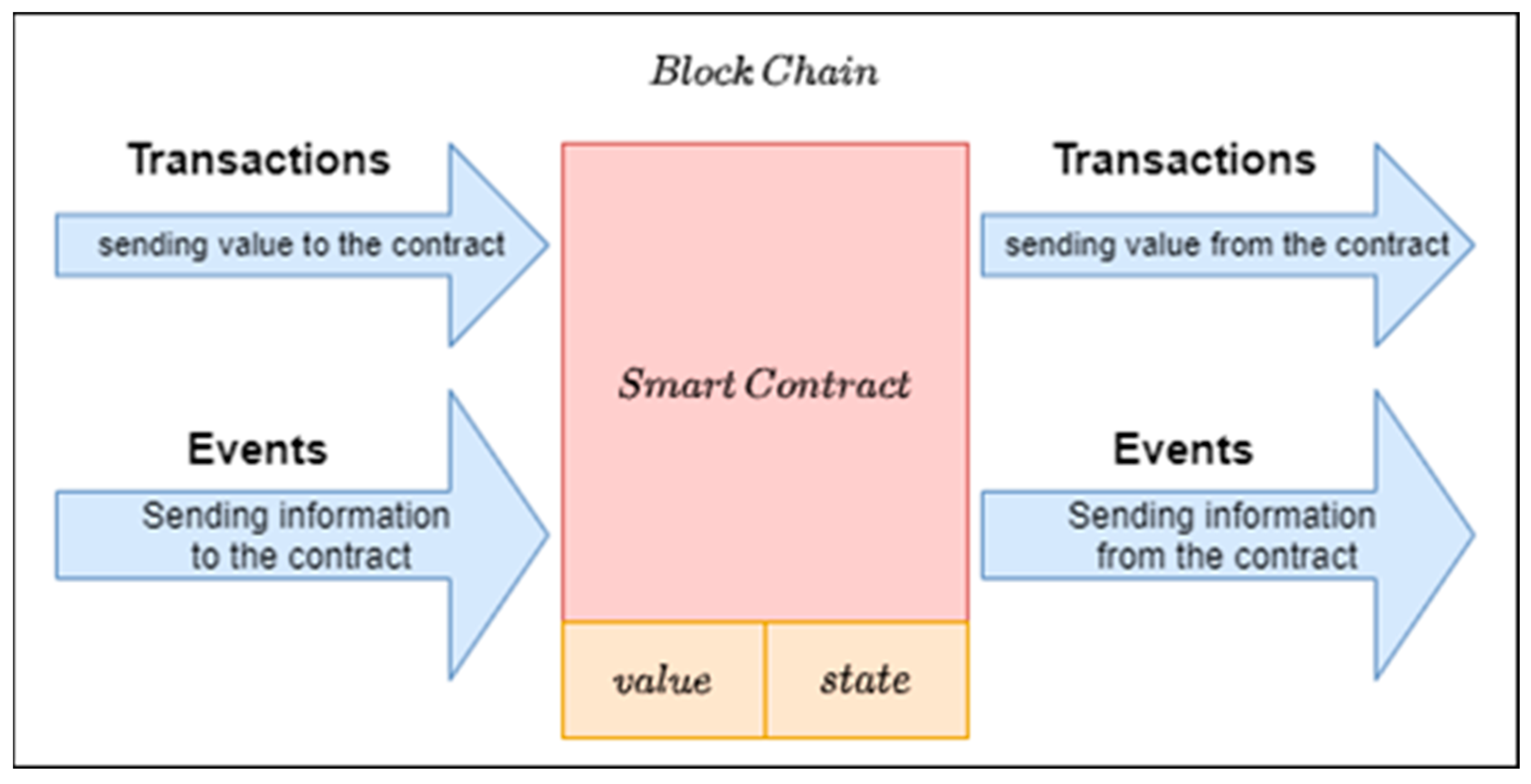
2.1. BlockChain and Power Systems
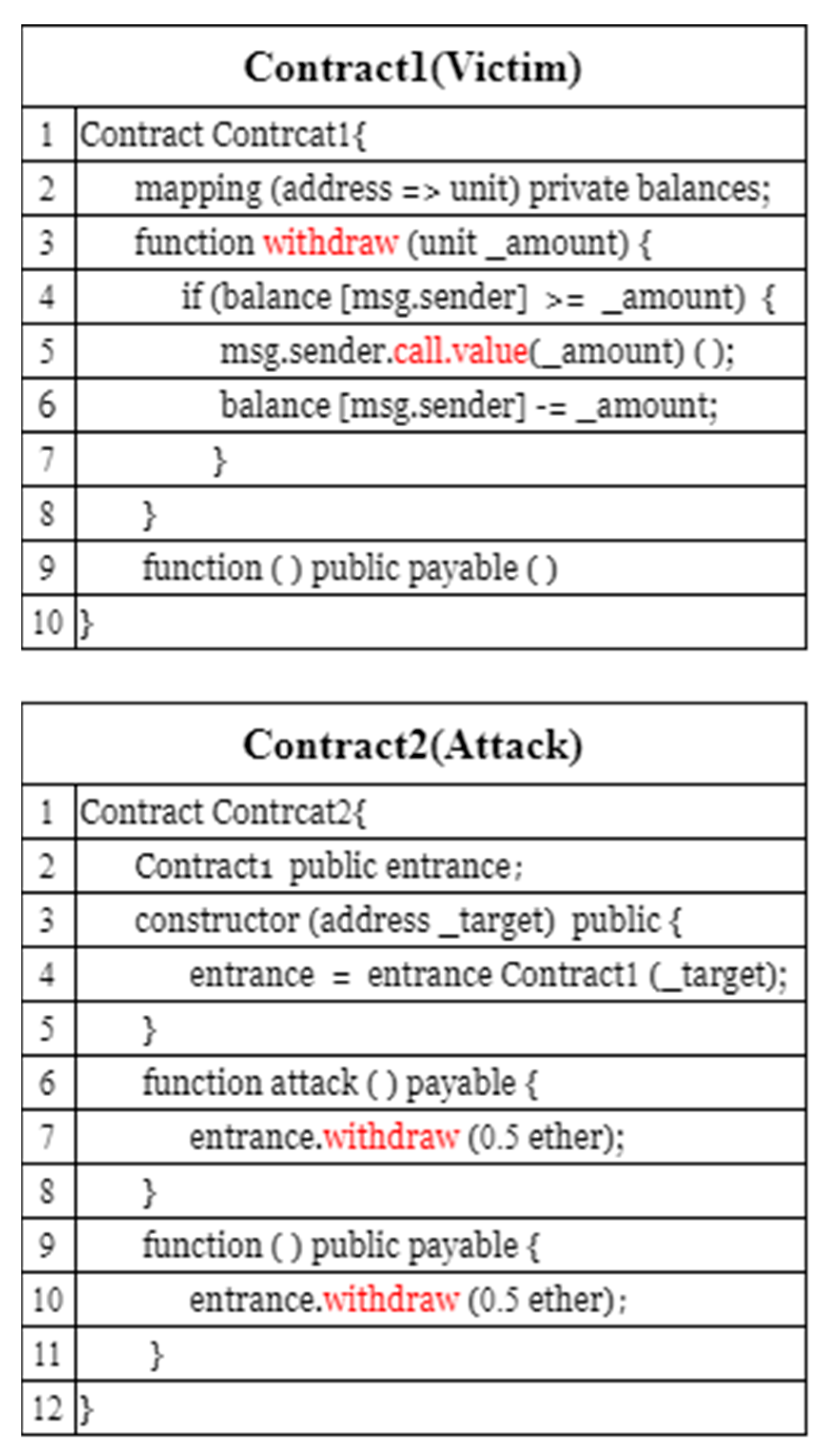
2.2. Smart Contract Vulnerability Detection
2.3. Siamese Network
2.4. Research Motivation
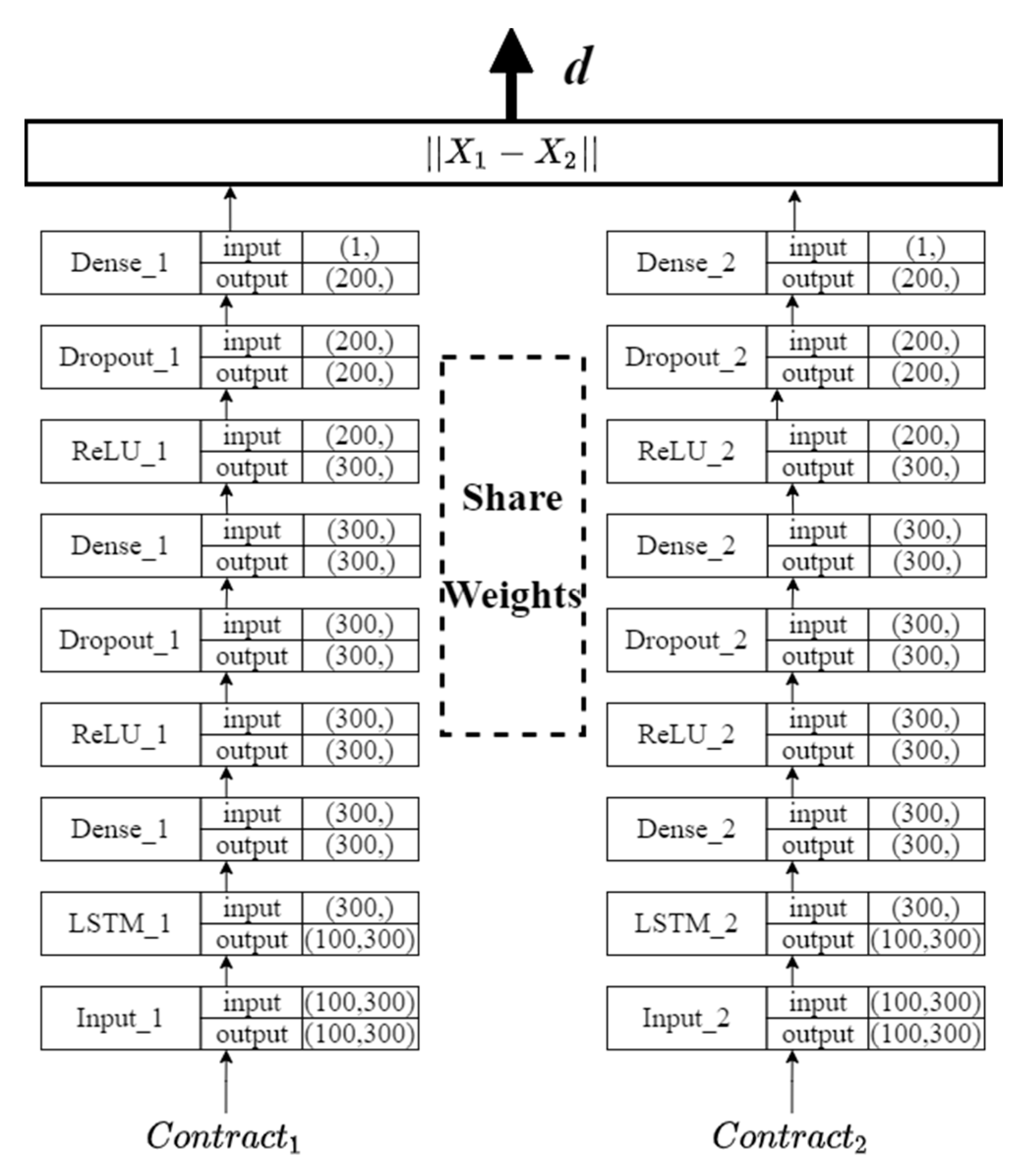
3. Siamese Network Structure in SCVSN Model
3.1. Siamese Network Structure in SCVSN Model
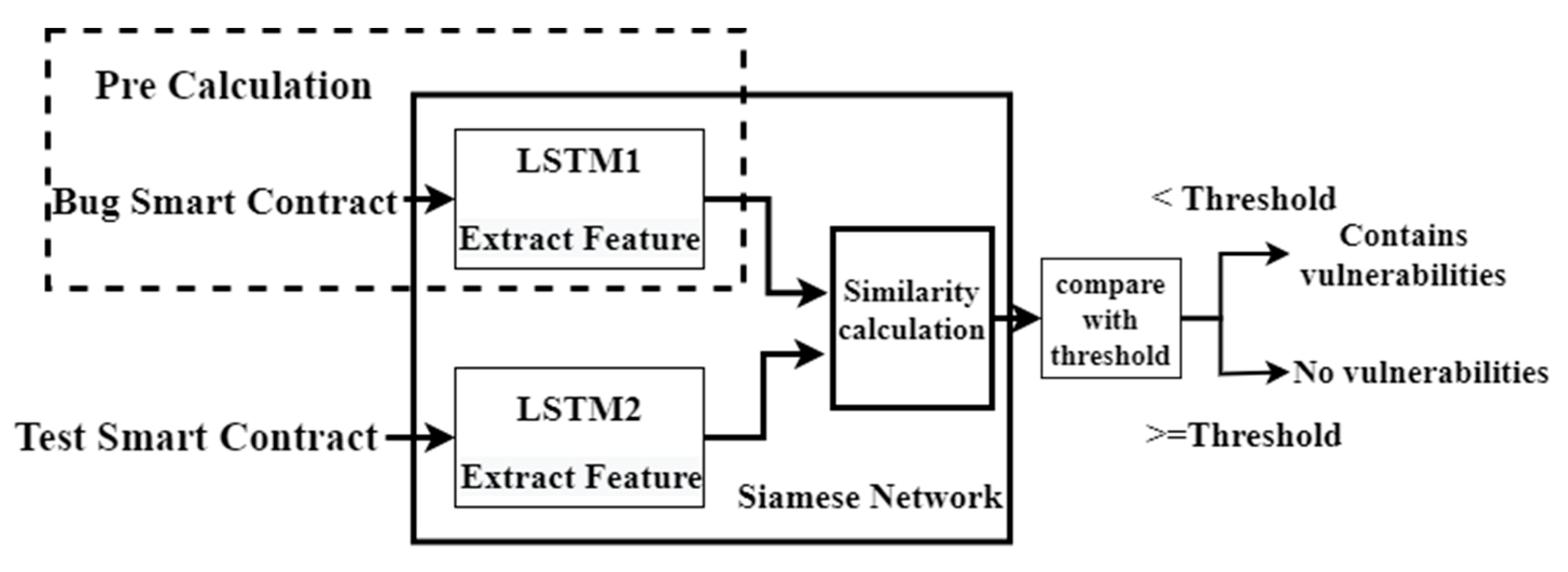
3.2. The Core Idea of SCVSN Model
- How to implement smart contract vulnerability detection via SCVSN model.
- How to train SCVSN model to improve their feature extraction capabilities.
- How to reduce rate of false positives.
| Algorithm 1. Positive and negative sample classification |
| Input: |
| : bug smart contract dataset; |
| : source smart contact dataset; |
| : label of ; : label of ; Output: Pairs: dataset of sample pairs consisting of positive and negative samples in a specific order |
| Pairs_label: label of the dataset |
| 1: int = 0; |
| 2: int = 0; |
| 3: for = 0;<.length;++ do |
| 4: for = 0;<.length;++ do |
| 5: Pairs.append(, ) |
| 6: if == then |
| 7: Pairs_label. append (1) |
| 8: else |
| 9: Pairs_label. append (0) |
| 10: end if |
| 11: end for |
| 12: end for |
| 13: return Pairs, Pairs_label; |
| Algorithm 2. training process of the SCVSN model |
| Input: |
| Pairs: The positive and negative sample pairs constructed by Algorithm 1; |
| Pairs_label: The labels corresponding to the positive and negative sample pairs; |
| 1: for ( |
| 2: = word2vec ( |
| 3: = word2vec ( |
| 4: =() |
| 5: =() |
| 6: d = |
| 7: if label = 0 then |
| 8: if d > m then |
| 9: continue |
| 10: else |
| 11: = Equation (7) |
| 12: end if |
| 13: else |
| 14: = Equation (8) |
| 15: end if |
| 16: Compute gradient: ▽ |
| 17: Update model: = |
| 18: end for |
4. Experiment
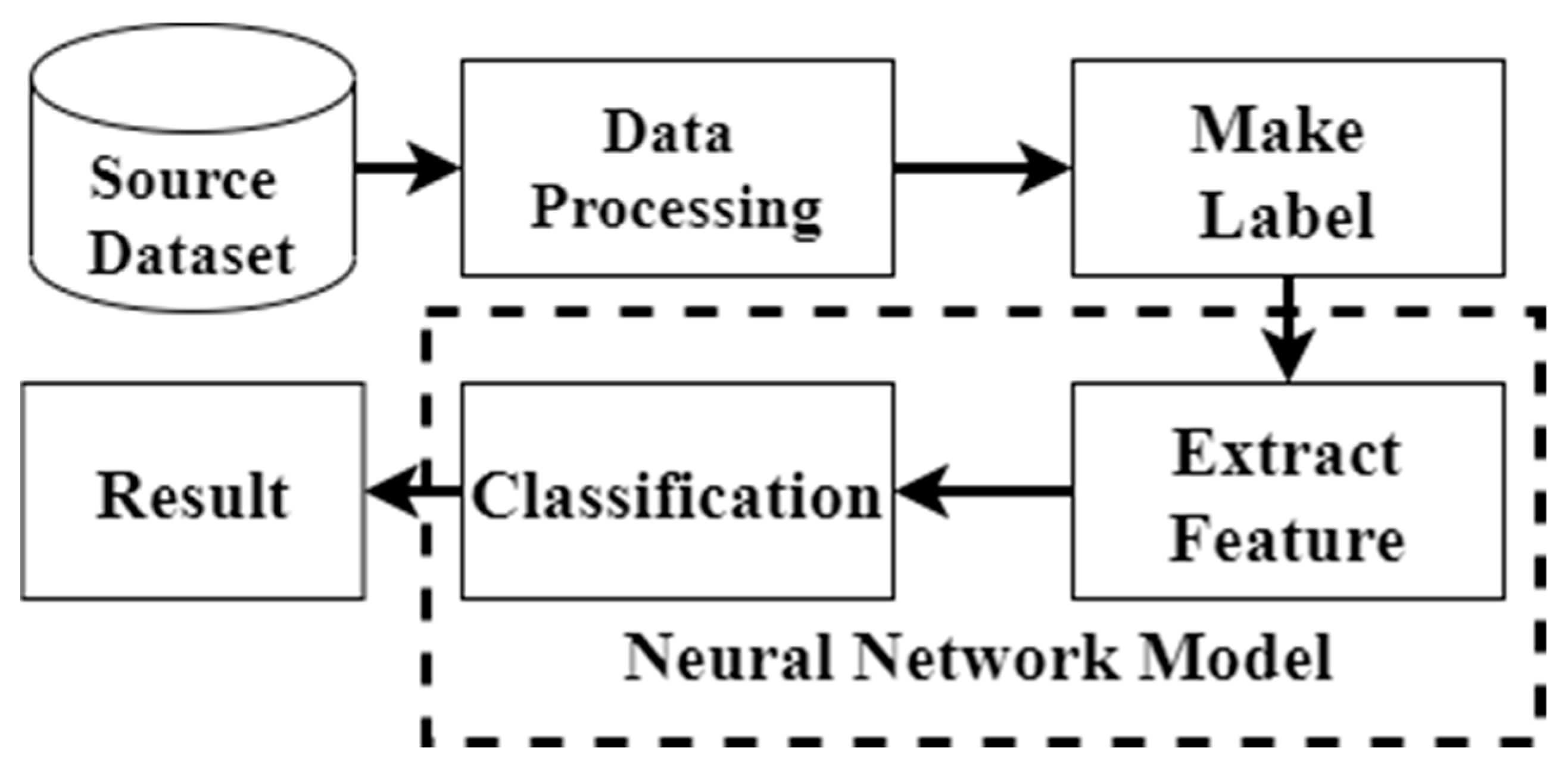
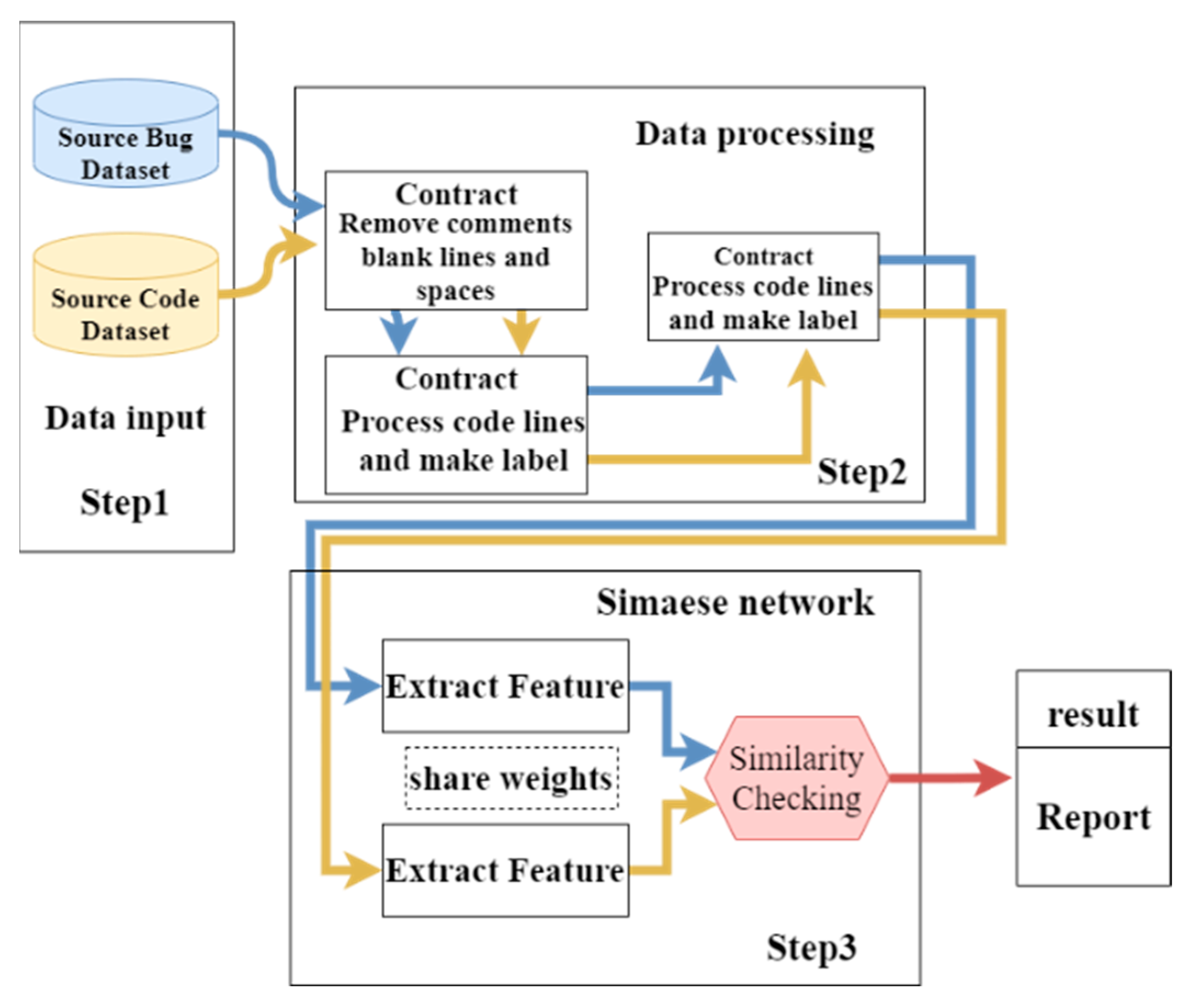
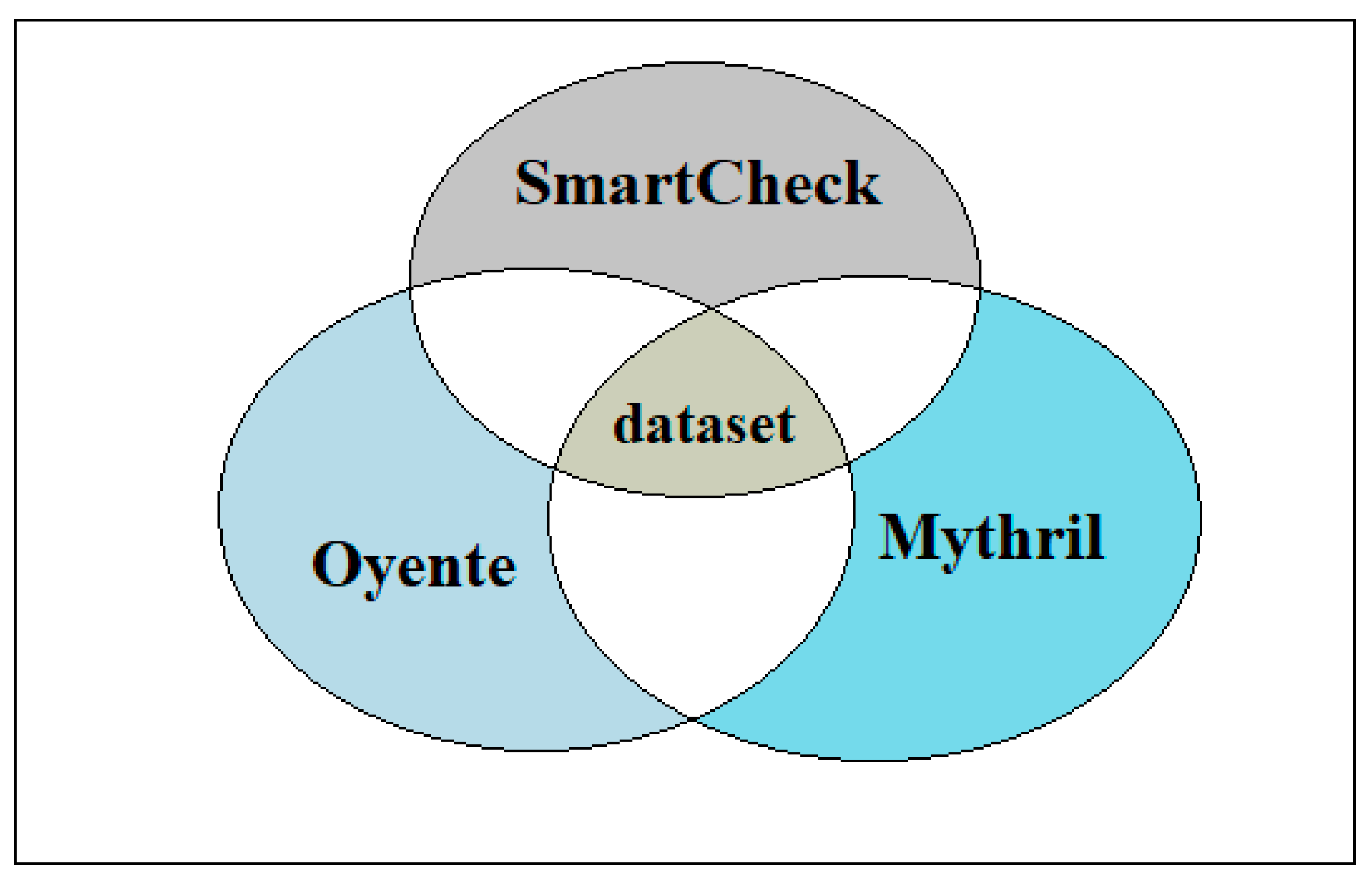
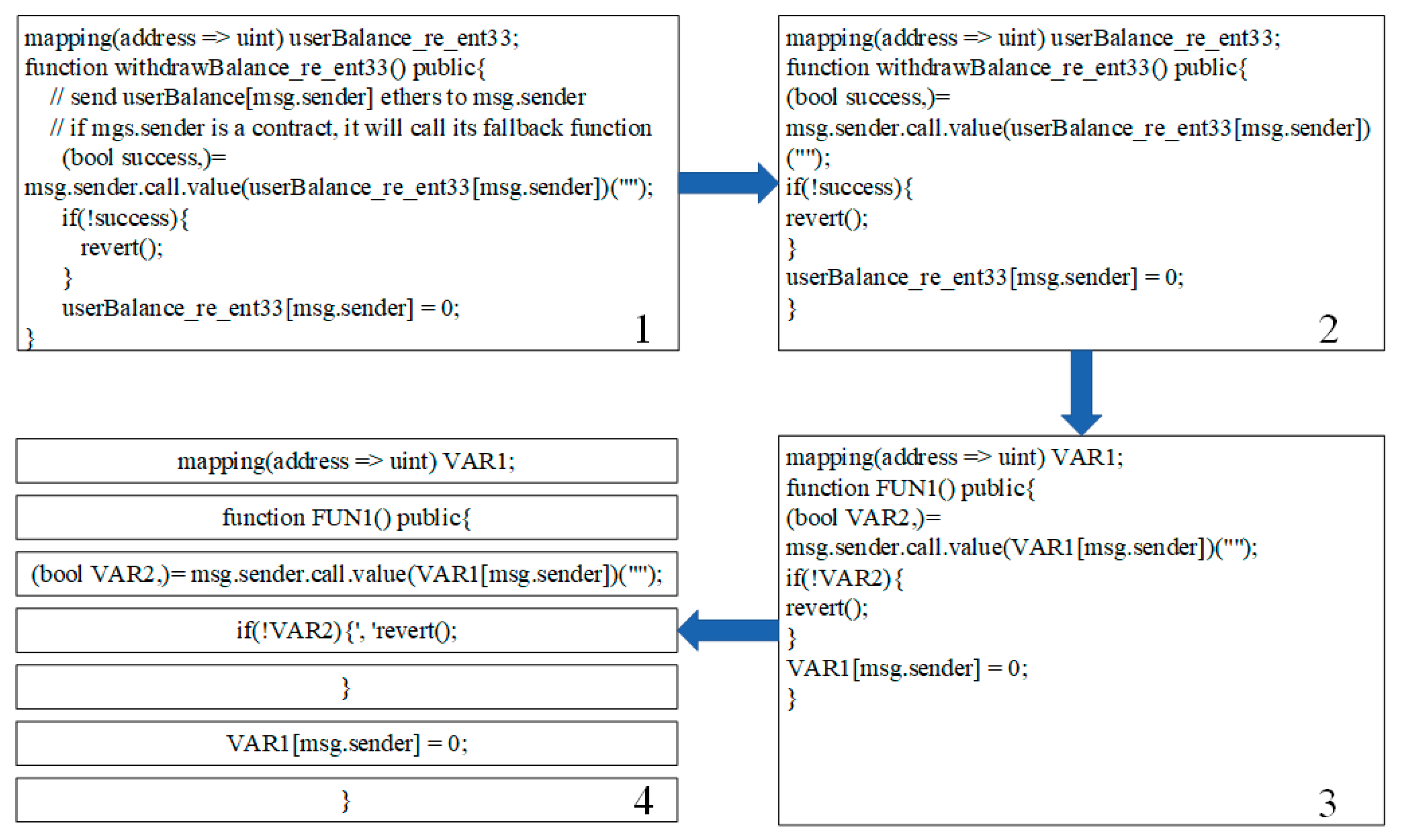
4.1. Dataset Processing
4.2. Experimental Procedure
4.3. Experimental Performance Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Giancaspro, M. Is a ‘smart contract’ really a smart idea? Insights from a legal perspective. Comput. Law Secur. Rev. 2017, 33, 825–835. [Google Scholar] [CrossRef]
- Khan, S.N.; Loukil, F.; Ghedira-Guegan, C.; Benkhelifa, E.; Bani-Hani, A. Blockchain smart contracts: Applications, challenges, and future trends. Peer Peer Netw. Appl. 2021, 14, 2901–2925. [Google Scholar] [CrossRef] [PubMed]
- Ghiasi, M.; Wang, Z.; Mehrandezh, M.; Jalilian, S.; Ghadimi, N. Evolution of smart grids towards the Internet of energy: Concept and essential components for deep decarbonisation. IET Smart Grid 2022, 1–17. [Google Scholar] [CrossRef]
- Oliva, G.A.; Hassan, A.E.; Jiang, Z.M. An exploratory study of smart contracts in the Ethereum blockchain platform. Empir. Softw. Eng. 2020, 25, 1864–1904. [Google Scholar] [CrossRef]
- Samreen, N.F.; Alalfi, M.H. Reentrancy vulnerability identification in ethereum smart contracts. In Proceedings of the 2020 IEEE 3rd International Workshop on Blockchain Oriented Software Engineering, London, ON, Canada, 18 February 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar]
- Ghiasi, M.; Niknam, T.; Wang, Z.; Mehrandezh, M.; Dehghani, M.; Ghadimi, N. A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future. Electr. Power Syst. Res. 2023, 215, 108975. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L. DeepCoin: A Novel Deep Learning and Blockchain-Based Energy Exchange Framework for Smart Grids. IEEE Trans. Eng. Manag. 2020, 67, 1285–1297. [Google Scholar] [CrossRef]
- Dehghani, M.; Niknam, T.; Ghiasi, M.; Bayati, N.; Savaghebi, M. Cyber-Attack Detection in DC Microgrids Based on Deep Machine Learning and Wavelet Singular Values Approach. Electronics 2021, 10, 1914. [Google Scholar] [CrossRef]
- Ghiasi, M.; Dehghani, M.; Niknam, T.; Kavousi-Fard, A.; Siano, P.; Alhelou, H.H. Cyber-Attack Detection and Cyber-Security Enhancement in Smart DC-Microgrid Based on Blockchain Technology and Hilbert Huang Transform. IEEE Access 2021, 9, 29429–29440. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Luo, F.; Zhao, J.; Dong, Z.Y. Distributed Blockchain-Based Data Protection Framework for Modern Power Systems Against Cyber Attacks. IEEE Trans. Smart Grid 2019, 10, 3162–3173. [Google Scholar] [CrossRef]
- Yu, X.; Zhao, H.; Hou, B.; Ying, Z.; Wu, B. DeeSCVHunter A Deep Learning-Based Framework for Smart Contract Vulnerability Detection. In Proceedings of the 2021 International Joint Conference on Neural Networks (IJCNN), Shenzhen, China, 18–22 July 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar]
- Wu, H.; Zhang, Z.; Wang, S.; Lei, Y.; Lin, B.; Qin, Y.; Zhang, H.; Mao, X. Peculiar: Smart Contract Vulnerability Detection Based on Crucial Data Flow Graph and Pre-training Techniques. In Proceedings of the 2021 IEEE 32nd International Symposium on Software Reliability Engineering (ISSRE), Wuhan, China, 25–28 October 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar]
- Mi, F.; Wang, Z.; Zhao, C.; Guo, J.; Ahmed, F.; Khan, L. VSCL: Automating Vulnerability Detection in Smart Contracts with Deep Learning. In Proceedings of the 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Sydney, Australia, 3–6 May 2021; IEEE: Piscataway, NJ, USA. [Google Scholar]
- Qian, P.; Liu, Z.; He, Q.; Zimmermann, R.; Wang, X. Towards Automated Reentrancy Detection for Smart Contracts Based on Sequential Models. IEEE Access 2020, 8, 19685–19695. [Google Scholar] [CrossRef]
- Xing, C.; Chen, Z.; Chen, L.; Guo, X.; Zheng, Z.; Li, J. A new scheme of vulnerability analysis in smart contract with machine learning. Wirel. Netw. 2020, 1–10. [Google Scholar] [CrossRef]
- Zhuang, Y.; Liu, Z.; Qian, P.; Liu, Q.; Wang, X.; He, Q. Smart Contract Vulnerability Detection using Graph Neural Network. In Proceedings of the Twenty-Ninth International Joint Conference on Artificial Intelligence (IJCAI-20), Yokohama, Japan, 11–17 July 2020; pp. 3283–3290. [Google Scholar]
- Bromley, J.; Bentz, J.W.; Bottou, L.; Guyon, I.; Lecun, Y.; Moore, C.; Säckinger, E.; Shah, R. Signature verification using a “Siamese” time delay neural network. In Advances in Neural Information Processing Systems; Series in Machine Perception and Artificial Intelligence; World Scientific: Singapore, 1994; pp. 25–44. ISBN 1793-0839. [Google Scholar]
- Amin-Naji, M.; Mahdavinataj, H.; Aghagolzadeh, A. Alzheimer’s disease diagnosis from structural MRI using Siamese convolutional neural network. In Proceedings of the 2019 4th International Conference on Pattern Recognition and Image Analysis (IPRIA), Tehran, Iran, 6–7 March 2019; IEEE: Piscataway, NJ, USA, 2019. [Google Scholar]
- Li, Z.; Song, P. Audio similarity detection algorithm based on Siamese LSTM network. In Proceedings of the 2021 6th International Conference on Intelligent Computing and Signal Processing (ICSP), Xi’an, China, 9–11 April 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar]
- Wu, Y.; Wang, W. Code Similarity Detection Based on Siamese Network. In Proceedings of the 2021 IEEE International Conference on Information Communication and Software Engineering (ICICSE), Chengdu, China, 19–21 March 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar]
- Wang, Q.; Wang, Z.; Sun, Y.; Zhang, X.; Li, W.; Ge, Y.; Huang, X.; Liu, Y.; Chen, Y. SCCNN: A Diagnosis Method for Hepatocellular Carcinoma and Intrahepatic Cholangiocarcinoma Based on Siamese Cross Contrast Neural Network. IEEE Access 2020, 8, 85271–85283. [Google Scholar] [CrossRef]
- Tang, E.; Wang, Y.; Liu, Y. Siamese Network with Channel-wise Attention and Multi-scale Fusion for Robust Object Tracking. In Proceedings of the 2020 39th Chinese Control Conference (CCC), Shenyang, China, 27–29 July 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar]
- Shen, J.; Tang, X.; Dong, X.; Shao, L. Visual Object Tracking by Hierarchical Attention Siamese Network. IEEE Trans. Cybern. 2020, 50, 3068–3080. [Google Scholar] [CrossRef] [PubMed]
- Karevan, Z.; Suykens, J.A.K. Transductive LSTM for time-series prediction: An application to weather forecasting. Neural Netw. 2020, 125, 1–9. [Google Scholar] [CrossRef] [PubMed]
- Ghaleb, A.; Pattabiraman, K. How effective are smart contract analysis tools? Evaluating smart contract static analysis tools using bug injection. In Proceedings of the 29th ACM SIGSOFT International Symposium on Software Testing and Analysis (ISSTA ‘20), Online, 18–22 July 2020; Khurshid, S., Păsăreanu, C.S., Eds.; ACM: New York, NY, USA, 2020; pp. 415–427, ISBN 9781450380089. [Google Scholar]
- Durieux, T.; Ferreira, J.F.; Abreu, R.; Cruz, P. Empirical review of automated analysis tools on 47,587 Ethereum smart contracts. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–19 July 2020; ACM: New York, NY, USA, 2020. [Google Scholar]
- Luu, L.; Chu, D.-H.; Olickel, H.; Saxena, P.; Hobor, A. Making Smart Contracts Smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security (CCS’16), Vienna Austria, 24–28 October 2016; Weippl, E., Katzenbeisser, S., Kruegel, C., Myers, A., Halevi, S., Eds.; ACM: New York, NY, USA, 2016; pp. 254–269, ISBN 9781450341394. [Google Scholar]
- Prechtel, D.; Gros, T.; Muller, T. Evaluating Spread of ‘Gasless Send’ in Ethereum Smart Contracts. In 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; IEEE: Piscataway, NJ, USA, 2019. [Google Scholar]
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. SmartCheck. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg Sweden, 27 May 2018; Tonelli, R., Destefanis, G., Counsell, S., Marchesi, M., Eds.; ACM: New York, NY, USA, 2018; pp. 9–16, ISBN 9781450357265. [Google Scholar]
- Jatnika, D.; Bijaksana, M.A.; Suryani, A.A. Word2Vec Model Analysis for Semantic Similarities in English Words. Procedia Comput. Sci. 2019, 157, 160–167. [Google Scholar] [CrossRef]

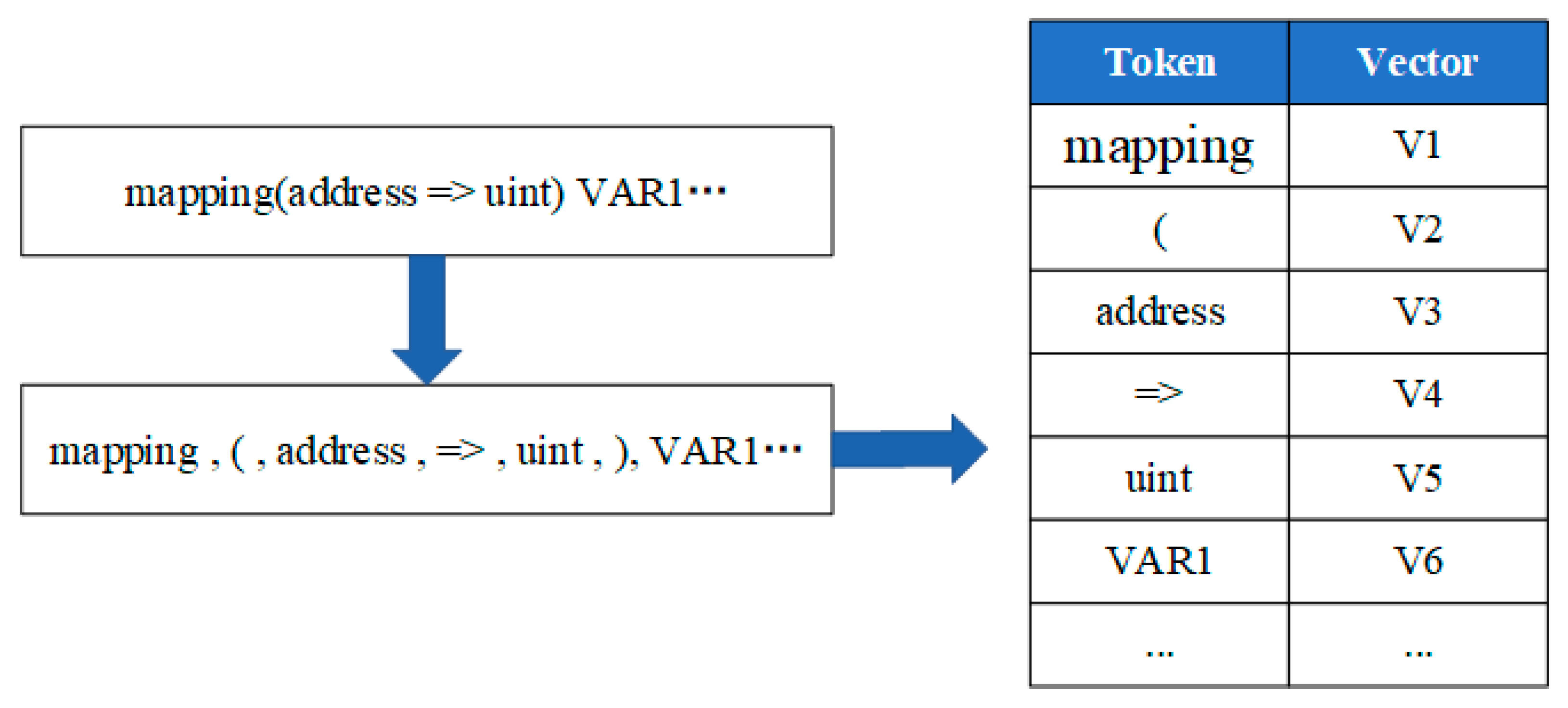

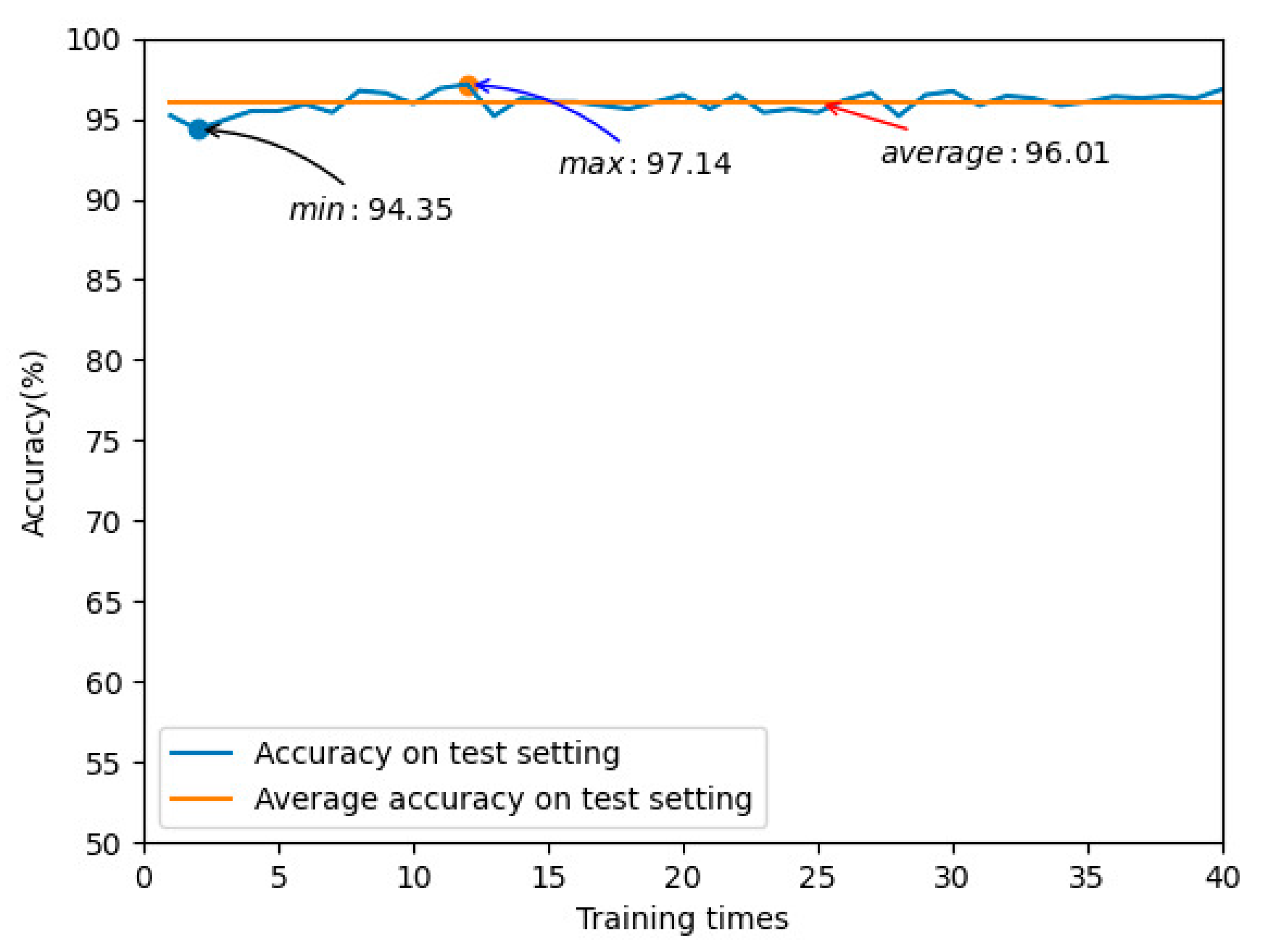
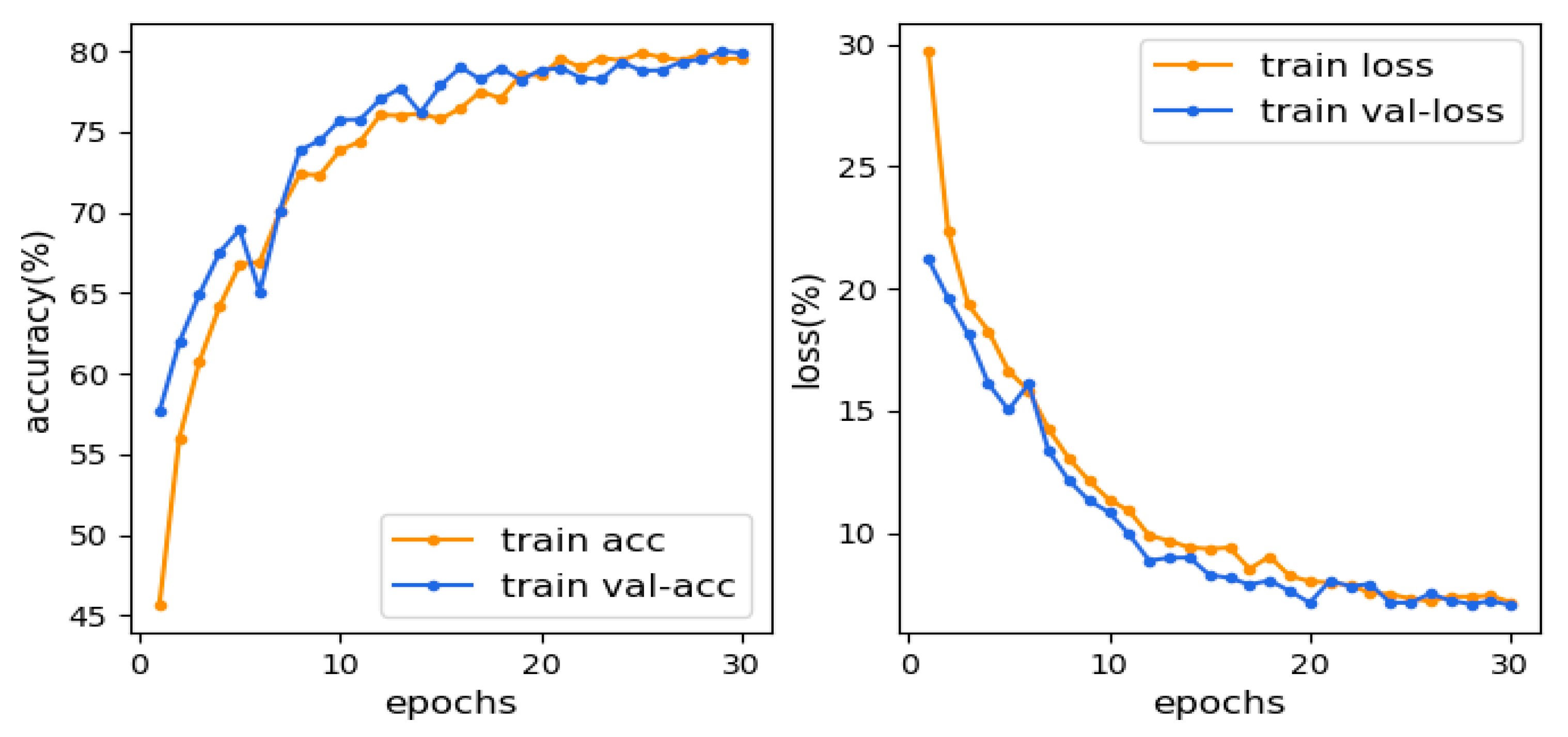
| Symbol | Explain |
|---|---|
| C | sample smart contracts |
| X | the feature values |
| the distance between two smart contracts | |
| the database used for training models | |
| The label of dataset | |
| a | a smart contract |
| b | a smart contract |
| y | the label of weather two smart contract samples match |
| m | the threshold of the distance between two samples |
| Units | Lr | ACC (%) | T(s) |
|---|---|---|---|
| 250 | 0.001 | 94.51 | 70.28 |
| 300 | 0.001 | 96.01 | 75.70 |
| 250 | 0.001 | 96.00 | 83.94 |
| 300 | 0.002 | 95.99 | 75.44 |
| 300 | 0.003 | 95.89 | 74.54 |
| Model | ACC (%) | REC (%) | PRE (%) | F1 (%) |
|---|---|---|---|---|
| SCVSN | 96.01 | 96.04 | 94.25 | 94.78 |
| DeeSCVHunter [14] | 93.02 | 83.46 | 90.70 | 86.87 |
| VSCL [13] | 95 | 95 | 99 | 95 |
| Peculiar [12] | 92.37 | 92.4 | 91.80 | 92.10 |
| BLSTM-ATT [15] | 88.47 | 88.48 | 88.5 | 88.26 |
| TMP [16] | 84.48 | 82.63 | 74.06 | 83.82 |
| DR-GCN [16] | 81.47 | 80.89 | 72.36 | 76.39 |
| LSTM | 81.91 | 91.43 | 76.80 | 83.48 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guo, R.; Chen, W.; Zhang, L.; Wang, G.; Chen, H. Smart Contract Vulnerability Detection Model Based on Siamese Network (SCVSN): A Case Study of Reentrancy Vulnerability. Energies 2022, 15, 9642. https://doi.org/10.3390/en15249642
Guo R, Chen W, Zhang L, Wang G, Chen H. Smart Contract Vulnerability Detection Model Based on Siamese Network (SCVSN): A Case Study of Reentrancy Vulnerability. Energies. 2022; 15(24):9642. https://doi.org/10.3390/en15249642
Chicago/Turabian StyleGuo, Ran, Weijie Chen, Lejun Zhang, Guopeng Wang, and Huiling Chen. 2022. "Smart Contract Vulnerability Detection Model Based on Siamese Network (SCVSN): A Case Study of Reentrancy Vulnerability" Energies 15, no. 24: 9642. https://doi.org/10.3390/en15249642
APA StyleGuo, R., Chen, W., Zhang, L., Wang, G., & Chen, H. (2022). Smart Contract Vulnerability Detection Model Based on Siamese Network (SCVSN): A Case Study of Reentrancy Vulnerability. Energies, 15(24), 9642. https://doi.org/10.3390/en15249642








