Active Defense Research against False Data Injection Attacks of Power CPS Based on Data-Driven Algorithms
Abstract
:1. Introduction
- (1)
- Solving the problem of data imbalance and high dimensionality. By improving the generative adversarial network (GAN) model, balanced processing of historical measurement data was achieved. At the same time, through the joint mutual information maximization (JMIM) algorithm, the selection of the optimal feature set for attack detection was realized;
- (2)
- Solving the challenging problem of difficult sample detection. By introducing the focal loss function, the light gradient boosting machine (LightGBM) is optimized to achieve accurate detection of FDIAs;
- (3)
- Solving the unobservable problem of a local power grid. The data reconstruction of FDIAs is achieved by training a variational auto-encoder (VAE).
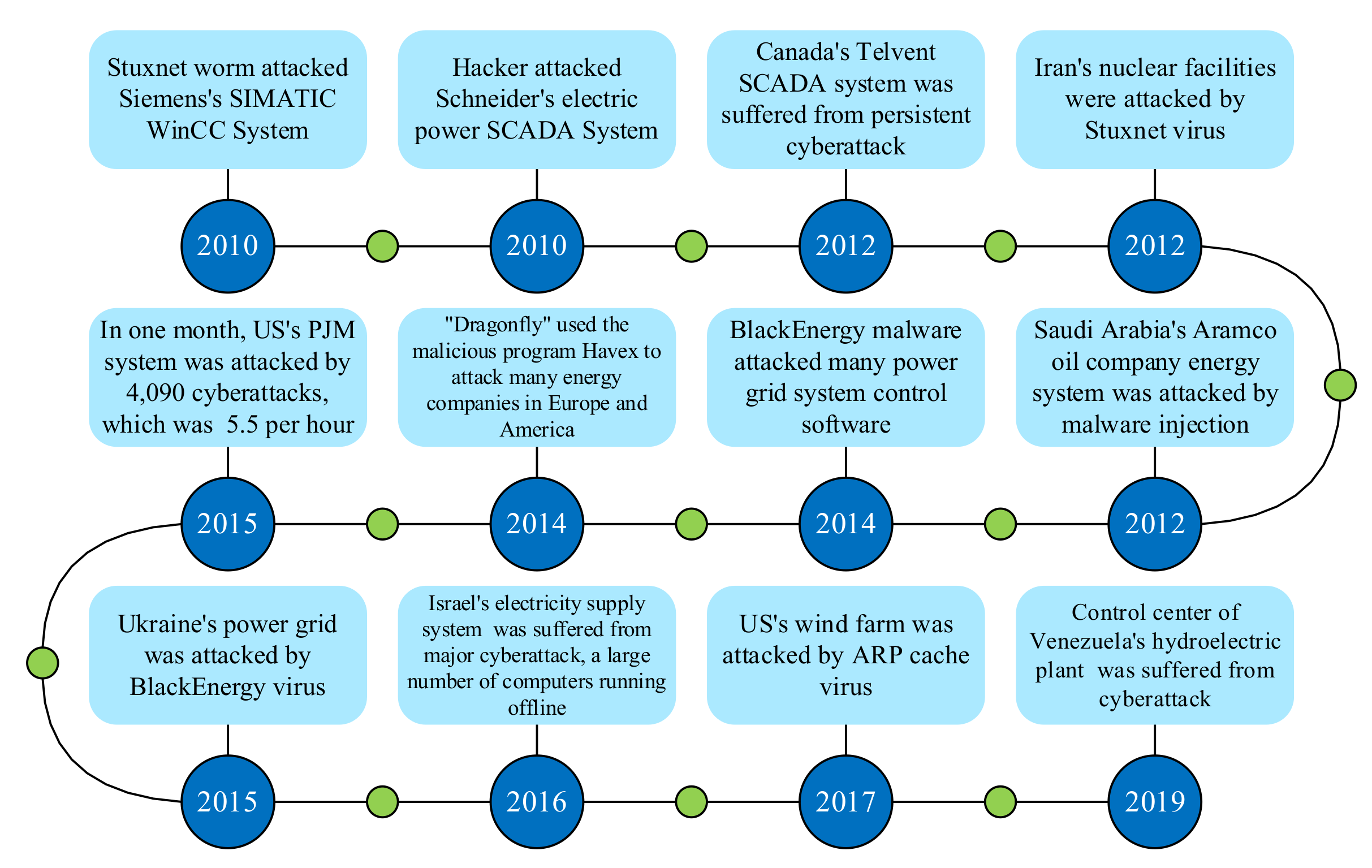
2. FDIAs Principles
2.1. Data Transmission Scenario and False Data Injection Forms
2.2. FDIAs Mathematical Model
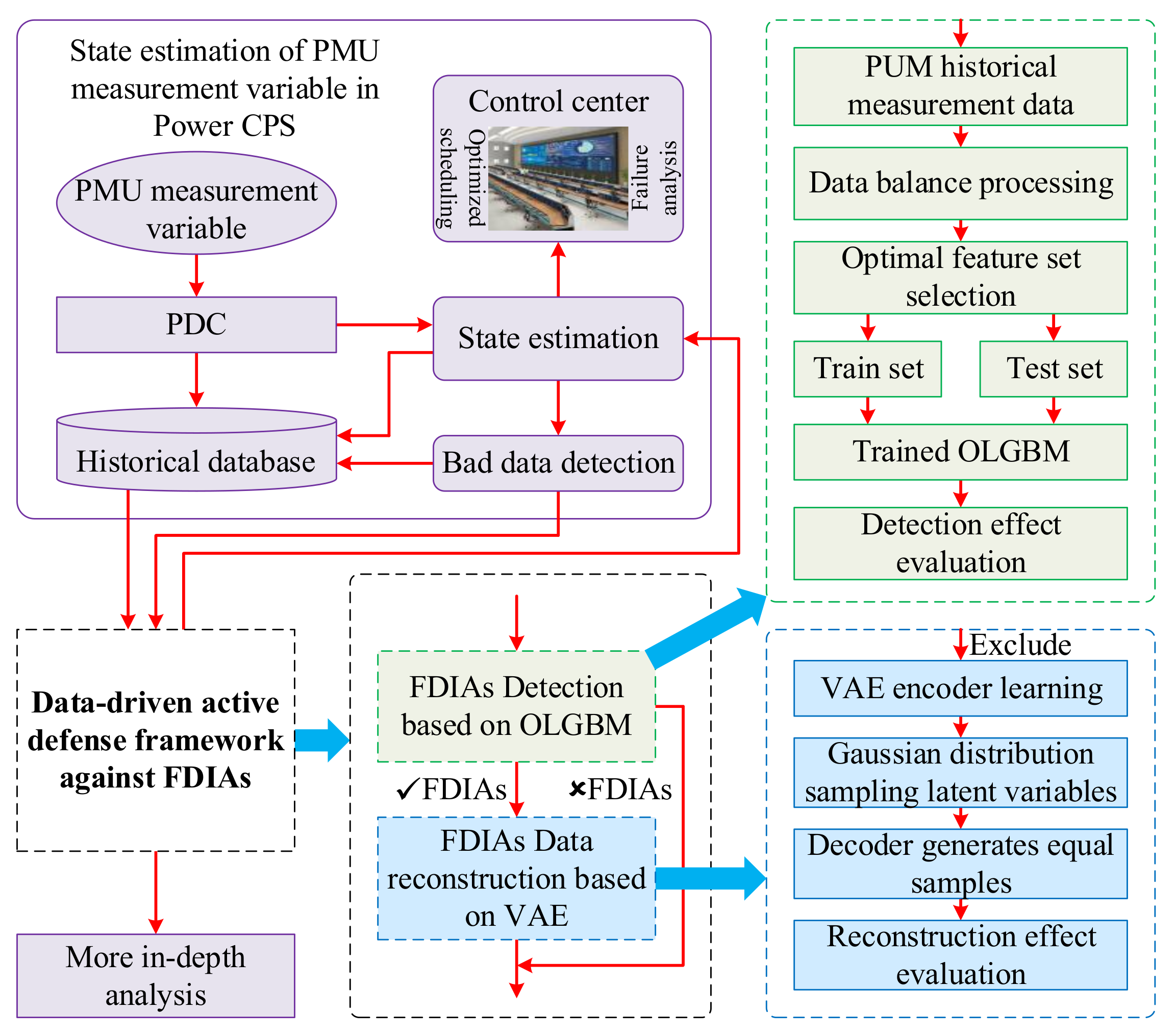
3. Active Defense Framework against FDIAs
3.1. Data Enhancement Methods against FDIAs
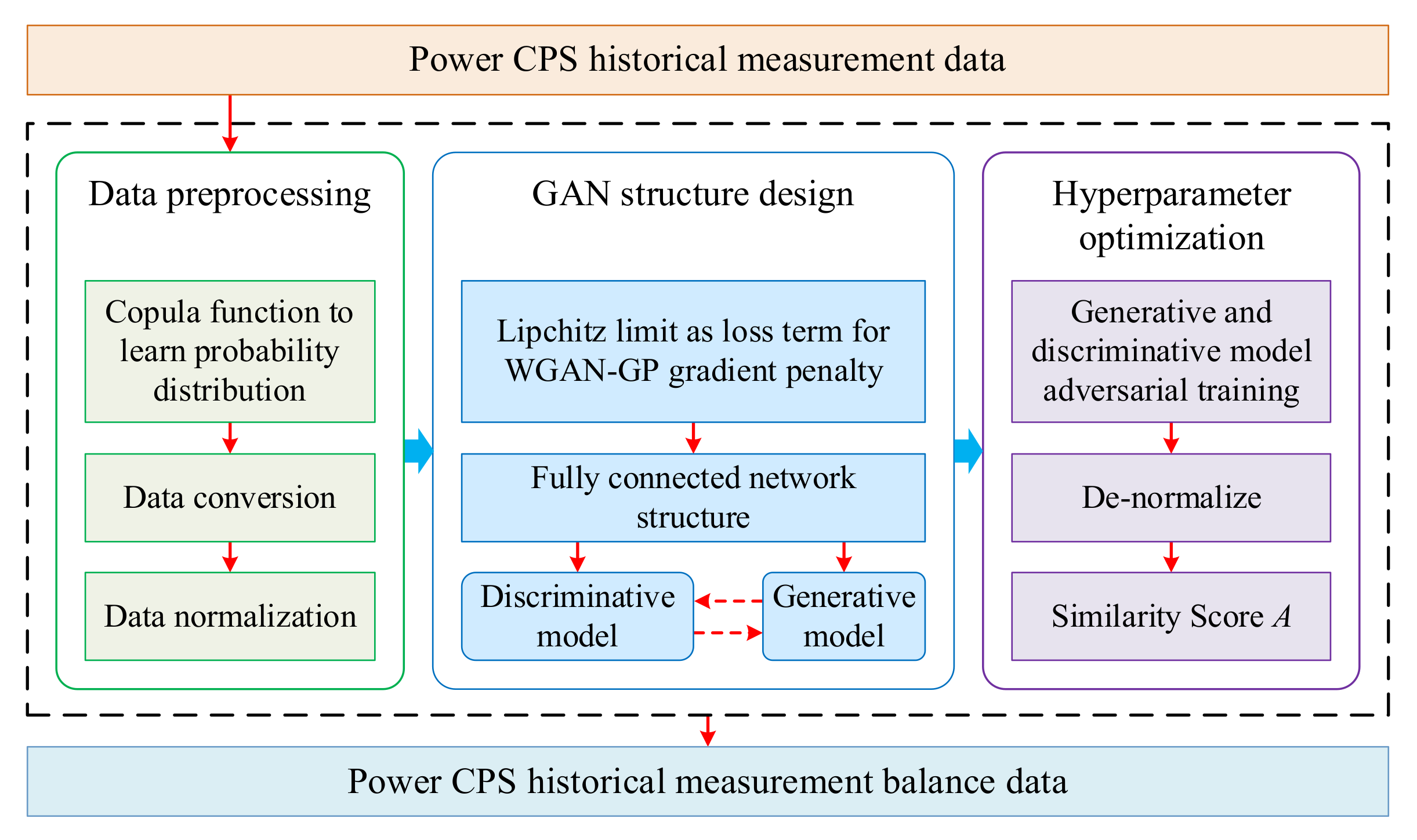
3.1.1. Balanced Processing of Historical Measurement Data
- (1)
- Improved GAN
- (2)
- Data balance process
- (1)
- Data preprocessing. Use the Gauss Copula function to learn the probability distribution of the power CPS historical measurement dataset, describe the correlation between n-dimensional random variables in the dataset, and perform data conversion. Normalize the transformed data;
- (2)
- GAN structure design. The Lipchitz restriction is added as a regular term to the Wasserstein loss of the WGAN-GP (Wasserstein GAN with Gradient Penalty) gradient penalty. The network structure adopts the full connection method. The generative model uses batch normalization and the ReLU activation function; scalar values are activated by the tanh function and discrete values are activated by the softmax function. The discriminative model uses the leaky ReLU function and dropout method [62];
- (3)
- Hyperparameter optimization. The generative and discriminative models conduct alternate adversarial training. Generate multiple sets of datasets containing the same number of normal operation data and FDIA data, and de-normalize each dataset. Use the Kolmogorov–Smirnov (K-S) test and KL divergence to calculate the similarity of data between the generated and original datasets, and obtain the similarity score A. Select the hyperparameters with similarity scores A closest to 1 as the optimal model parameters;
- (4)
- Data balance processing. The original historical measurement data are used as the input of CCTGAN to generate a balanced historical measurement dataset.
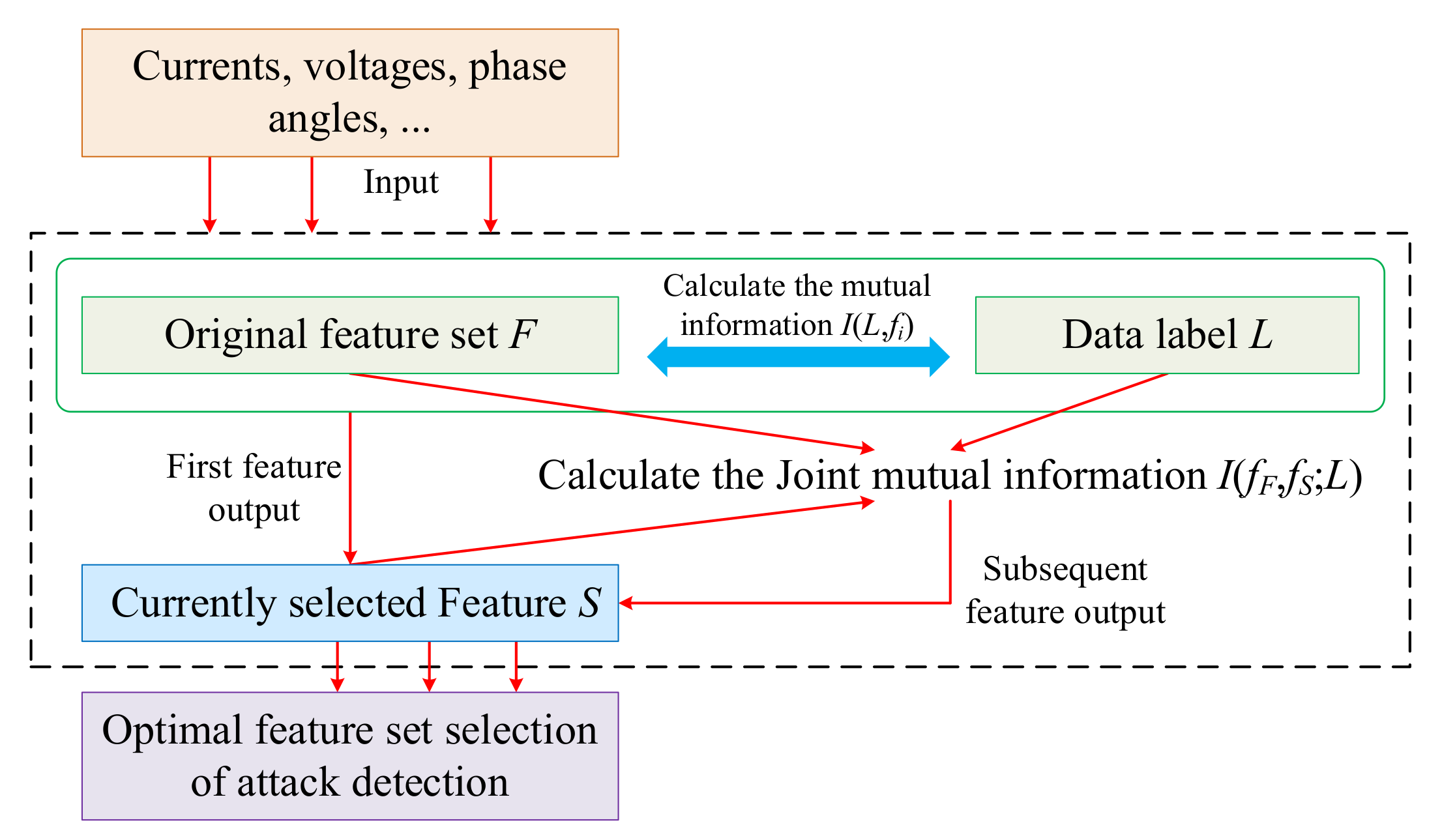
3.1.2. Optimal Feature Set Selection of Attack Detection
- (1)
- JMIM algorithm principle
- (2)
- Optimal feature set selection process
- (a)
- Input features, such as currents, voltages, and phase angles into the original feature set F, and initialize the set S to store the optimal features for screening;
- (b)
- Initialize parameter k, where k is the number of features finally screened by the algorithm;
- (c)
- Calculate the mutual information I(C;fi) between the features and data labels in the original feature set one by one, filter out the feature with the largest mutual information between the original feature set and the data labels, and add it to set S as the first feature;
- (d)
- Calculate the remaining features fF in feature set F, the selected features fS in S, and the joint mutual information I(fF,fS;L) between the data labels in turn;
- (e)
- Screen the next features in turn as fi = arg max fiF-S(min fSS(I(fi,fS;S))) until the k features are screened, add the features of the subsequent screening to the set S, and the final set S is the optimal feature set for attack detection.
3.2. Detection Method against FDIAs
3.2.1. Optimize LightGBM
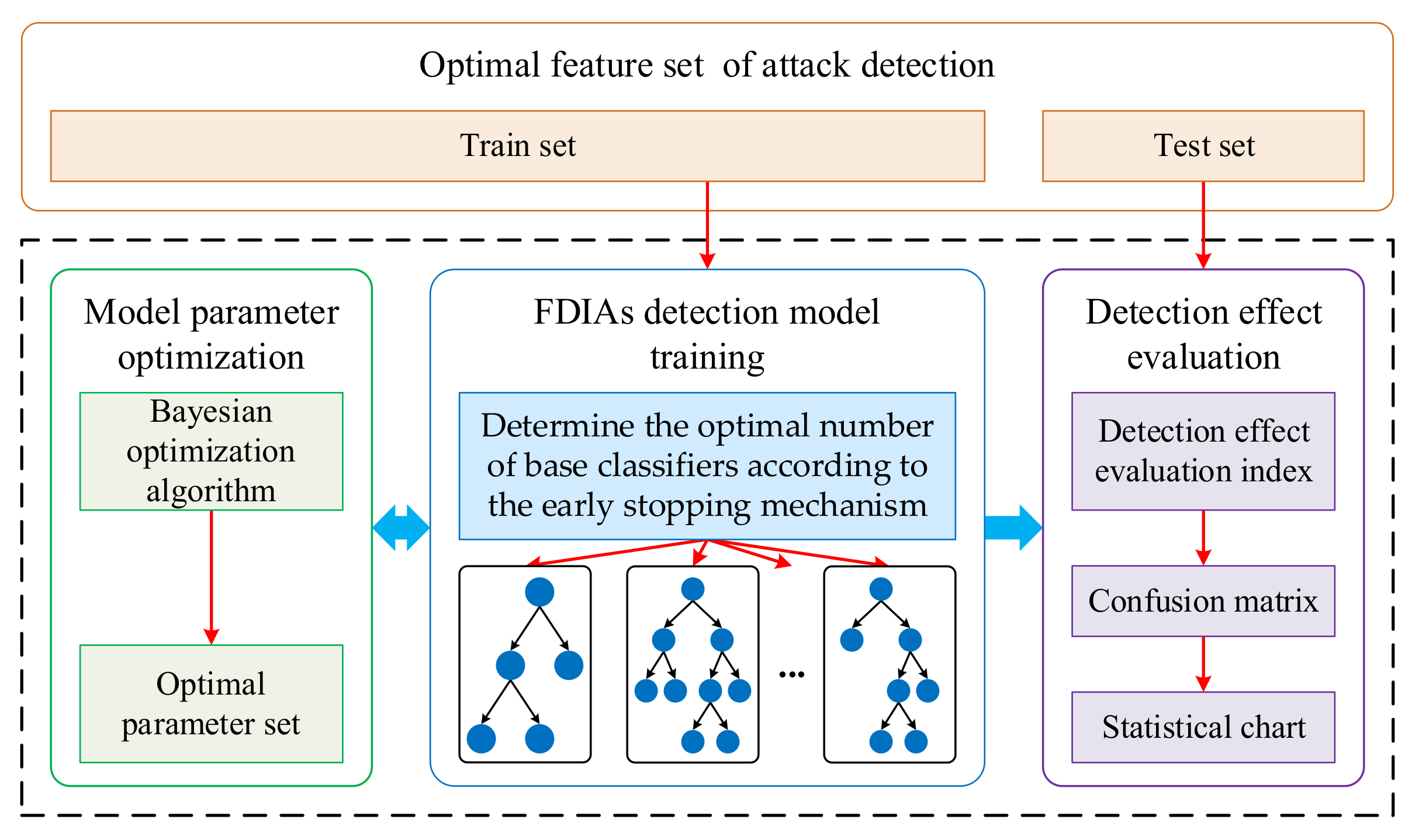
3.2.2. Attack Detection Process
- (a)
- Divide the optimal feature set into a training set and testing set; the training set is used to train the attack-detection model;
- (b)
- Train the OLGBM algorithm on the train set and determine the optimal number of base classifiers according to the early stopping mechanism;
- (c)
- Under the optimal number of classifiers, the Bayesian optimization algorithm is used to search the optimal set of some important parameters of the OLGBM algorithm;
- (d)
- Train the OLGBM algorithm under the optimal parameter set to obtain the final FDIA detection model;
- (e)
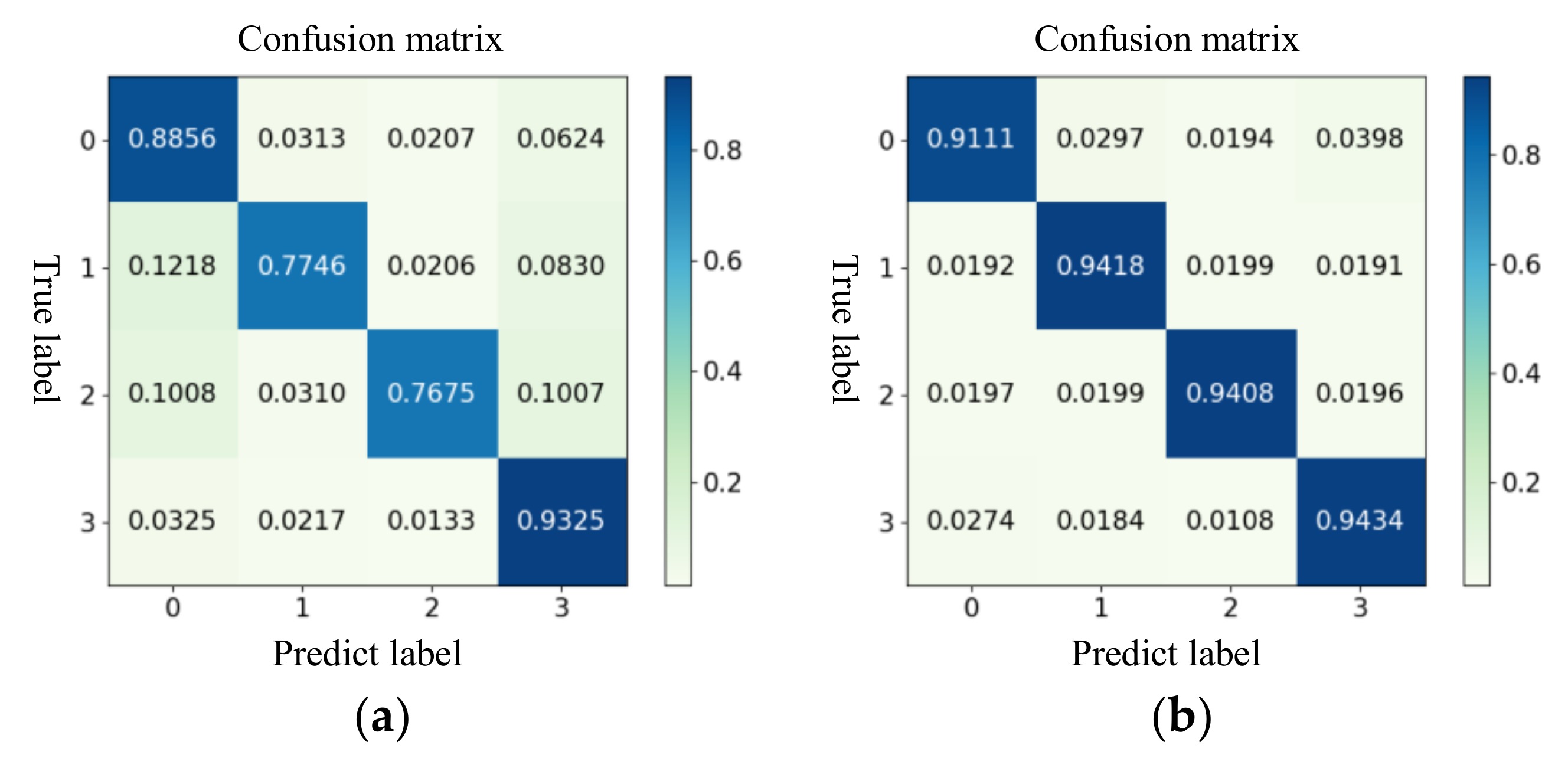
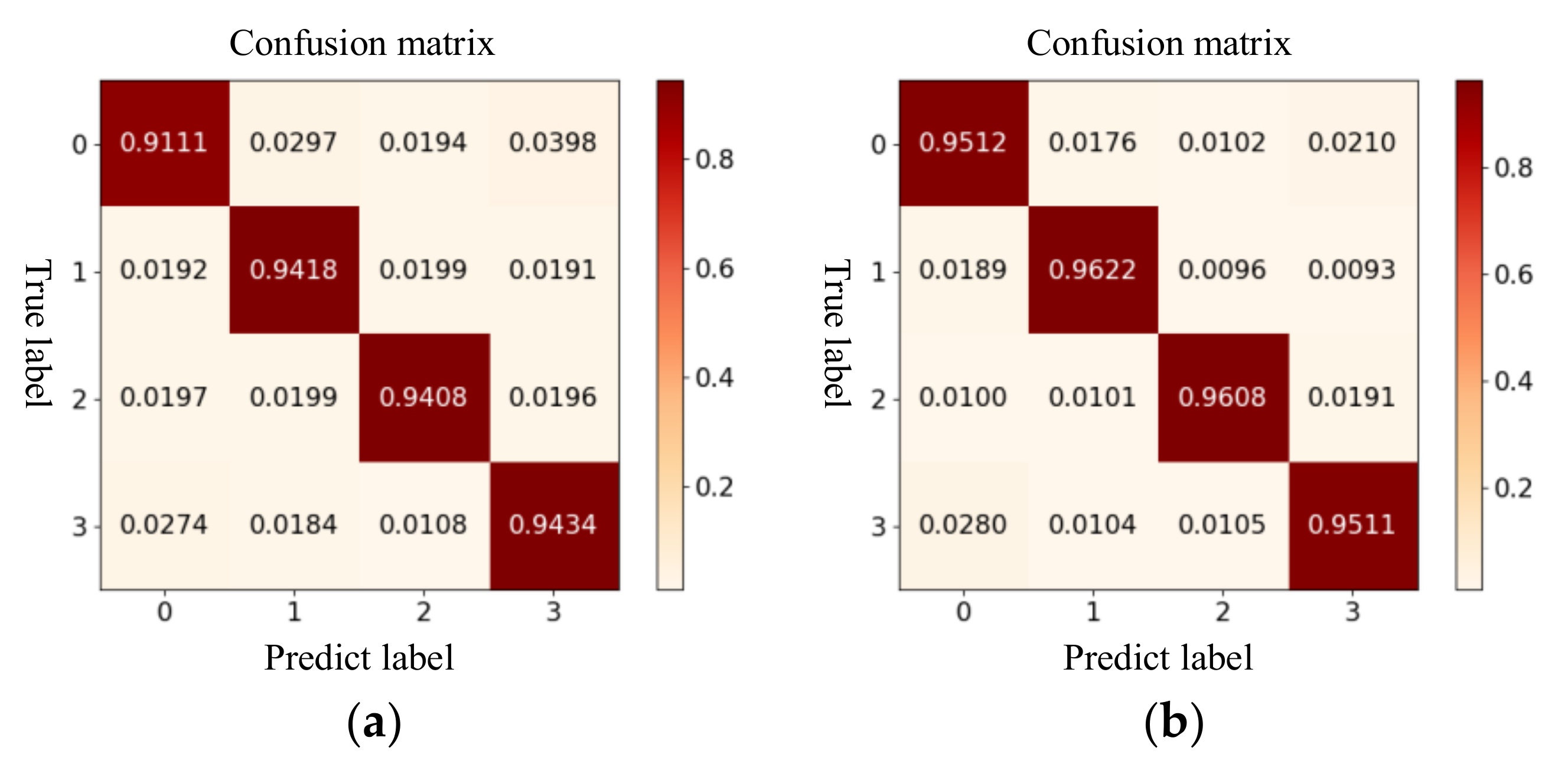
- Select the test set in (a) to evaluate the detection performance of the model and present the model detection results in the form of a confusion matrix and a statistical chart.
3.3. Data Reconstruction against FDIAs
3.3.1. VAE Algorithm Principle
3.3.2. Data Reconstruction Process
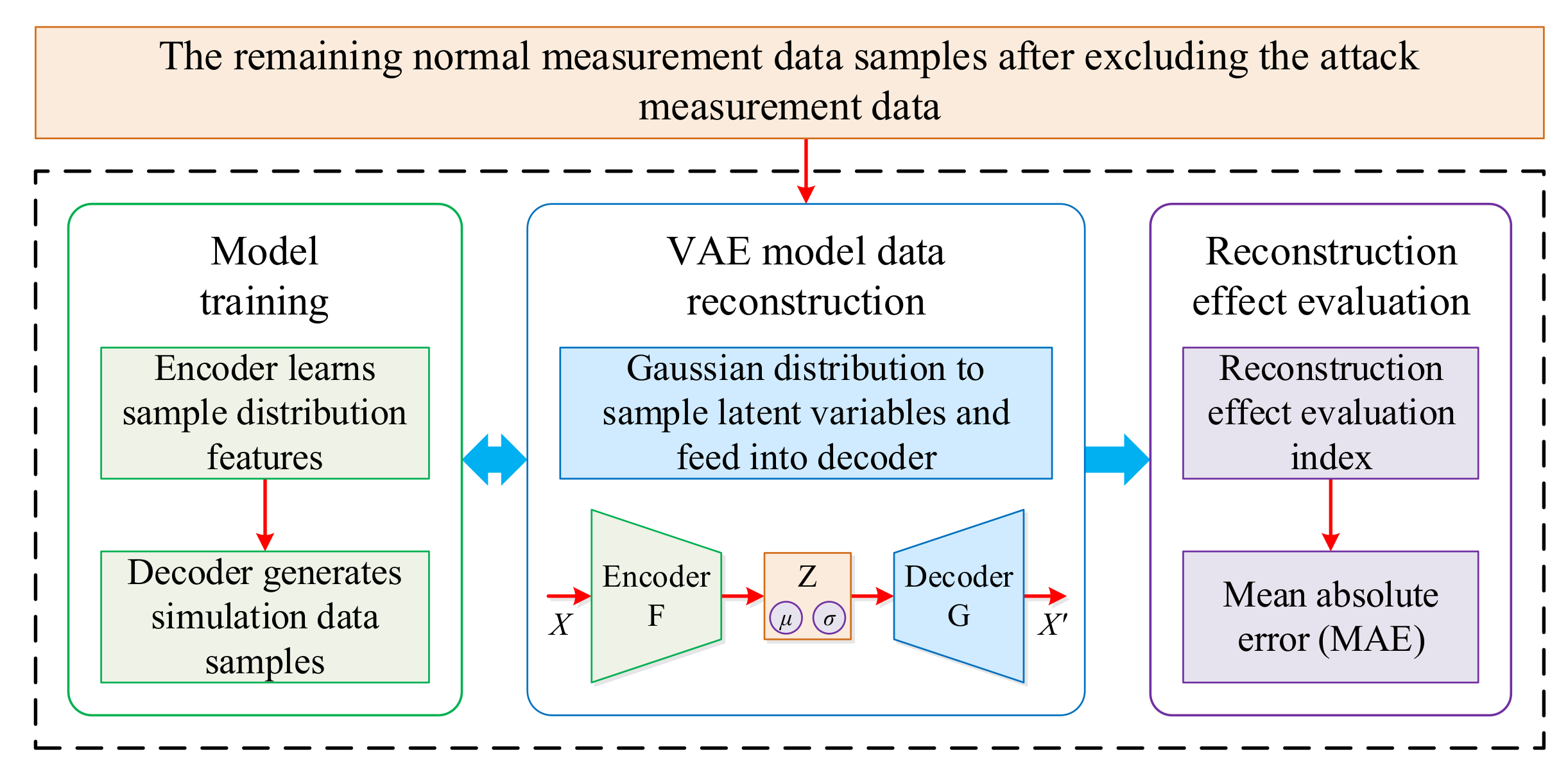
- (a)
- The remaining normal measurement data samples after excluding the attacked measurement data are used as the input to the VAE, and the VAE learns its sample distribution characteristics through the encoder;
- (b)
- The latent variable from the Gaussian distribution is sampled and input into the decoder. The decoder generates the same number of simulated data samples as the attacked measurement data;
- (c)
- The simulation data generated by the VAE are merged with the remaining normal measurement data to complete the original sample, thereby completing the reconstruction of the FDIA data;
- (d)
- The reconstruction rate and mean absolute error (MAE) evaluation indicators are selected to judge the data reconstruction performance of the VAE model.
3.4. Active Defense Framework against FDIAs
4. Example Analysis
4.1. Data Balanced Processing Effect Evaluation
4.2. Optimal Feature Set Selection Effect Evaluation
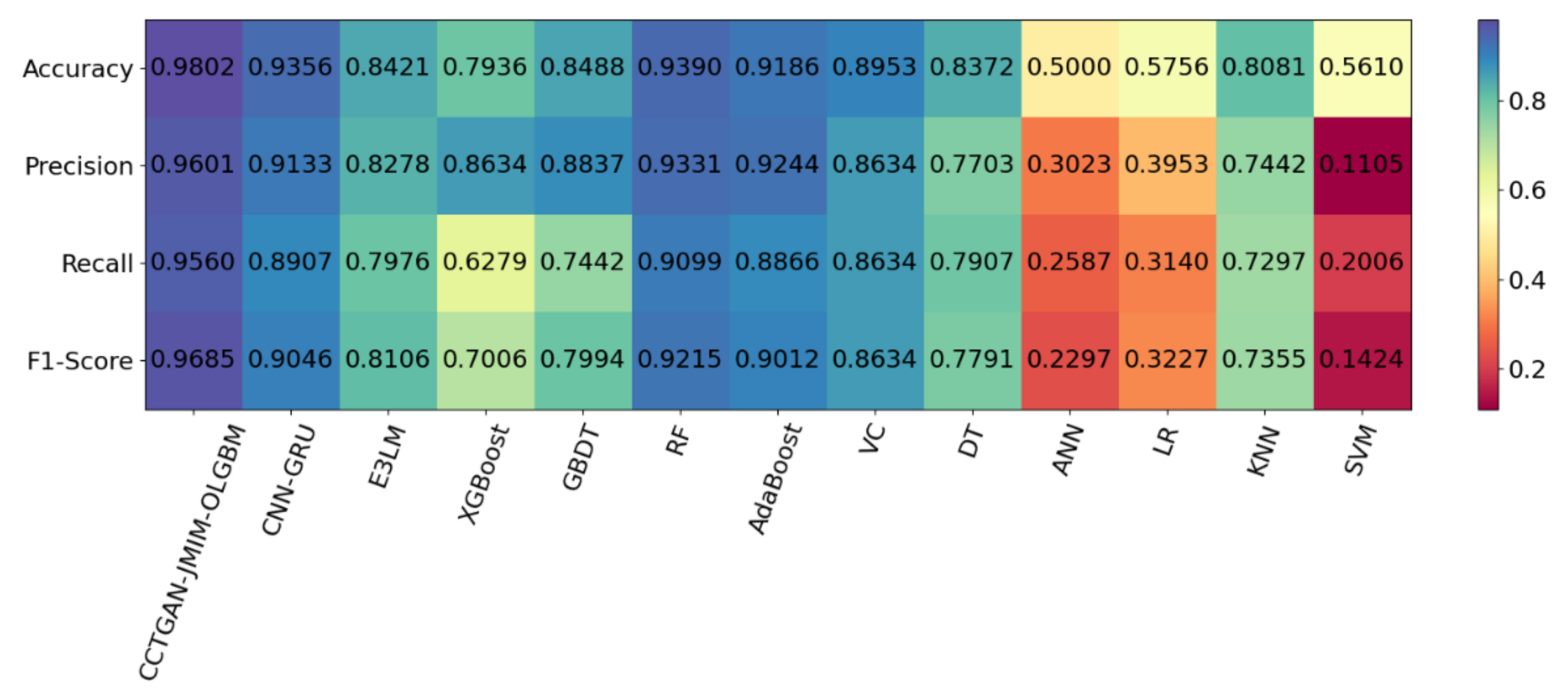
4.3. FDIAs Detection Effect Evaluation
4.4. Data Reconstruction Effect Evaluation against FDIAs
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhou, X.X.; Chen, S.Y.; Lu, Z.X.; Huang, Y.H.; Ma, S.C.; Zhao, Q. Technology Features of the New Generation Power System in China. Proc. CSEE 2018, 38, 1893–1904. [Google Scholar]
- Vallathan, G.; John, A.; Thirumalai, C.; Mohan, S.; Srivastava, G.; Lin, J.C.W. Suspicious activity detection using deep learning in secure assisted living IoT environments. J. Supercomput. 2021, 77, 3242–3260. [Google Scholar] [CrossRef]
- Cheng, C.F.; Chen, Y.C.; Lin, J.C.W. A Carrier-Based Sensor Deployment Algorithm for Perception Layer in the IoT Architecture. IEEE Sens. J. 2020, 20, 10295–10305. [Google Scholar] [CrossRef]
- Wang, L.; Qu, Z.Y.; Li, Y.; Hu, K.W.; Sun, J.; Xue, K.; Cui, M.S. Method for Extracting Patterns of Coordinated Network Attacks on Electric Power CPS Based on Temporal-Topological Correlation. IEEE Access 2020, 8, 57260–57272. [Google Scholar] [CrossRef]
- Qin, B.Y.; Liu, D. Research Progresses and Prospects on Analysis and Control of Cyber-physical System for Power Grid. Proc. CSEE 2020, 40, 5816–5826. [Google Scholar]
- Haes Alhelou, H.; Hamedani-Golshan, M.E.; Njenda, T.C.; Siano, P. A Survey on Power System Blackout and Cascading Events: Research Motivations and Challenges. Energies 2019, 12, 682. [Google Scholar] [CrossRef] [Green Version]
- Yu, T.; Cheng, L.F.; Zhang, X.S. The Weakly-Centralized Web-of-Cells Based on Cyber-Physical-Social Systems Integration and Group Machine Learning: Theoretical Investigations and Key Scientific Issues Analysis. Sci. Sin. Technol. 2019, 49, 1541–1569. [Google Scholar]
- Lin, J.C.W.; Srivastava, G.; Zhang, Y.Y.; Djenouri, Y.; Aloqaily, M. Privacy-Preserving Multiobjective Sanitization Model in 6G IoT Environments. IEEE Internet Things J. 2021, 8, 5340–5349. [Google Scholar] [CrossRef]
- Wu, J.M.T.; Srivastava, G.; Jolfaei, A.; Pirouz, M.; Lin, J.C.W. Security and Privacy in Shared HitLCPS Using a GA-Based Multiple-Threshold Sanitization Model. IEEE Trans. Emerg. Top. Comput. Intell. 2022, 6, 16–25. [Google Scholar] [CrossRef]
- Xu, C.X.; Abur, A. A Massively Parallel Framework for Very Large Scale Linear State Estimation. IEEE Trans. Power Syst. 2017, 33, 4407–4413. [Google Scholar] [CrossRef]
- Kurt, M.N.; Yılmaz, Y.; Wang, X.D. Distributed Quickest Detection of Cyber-Attacks in Smart Grid. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2015–2030. [Google Scholar] [CrossRef]
- BaSin, D.; Cremers, C.; Kim, T.H.J.; Perrig, A.; Sasse, R.; Szalachowski, P. Design, Analysis, and Implementation of ARPKI: An Attack-Resilient Public-Key Infrastructure. IEEE Trans. Dependable Secur. Comput. 2016, 15, 393–408. [Google Scholar] [CrossRef]
- Lin, H.; Slagell, A.; Kalbarczyk, Z.; Sauer, P.W.; Iyer, R.K. Runtime Semantic Security Analysis to Detect and Mitigate Control-Related Attacks in Power Grids. IEEE Trans. Smart Grid 2016, 9, 163–178. [Google Scholar] [CrossRef]
- Qu, Z.Y.; Zhang, Y.; Qu, N.; Wang, L.; Li, Y.; Dong, Y.C. Method for Quantitative Estimation of the Risk Propagation Threshold in Electric Power CPS Based on Seepage Probability. IEEE Access 2018, 6, 68813–68823. [Google Scholar] [CrossRef]
- Lai, K.X.; Illindala, M.; Subramaniam, K. A tri-level optimization model to mitigate coordinated attacks on electric power systems in a cyber-physical environment. Appl. Energy 2019, 235, 204–218. [Google Scholar] [CrossRef]
- Xin, S.J.; Guo, Q.L.; Sun, H.B.; Zhang, B.M.; Wang, J.H.; Chen, C. Cyber-Physical Modeling and Cyber-Contingency Assessment of Hierarchical Control Systems. IEEE Trans. Smart Grid 2015, 6, 2375–2385. [Google Scholar] [CrossRef]
- Guo, Q.L.; Xin, S.J.; Wang, J.H.; Sun, H.B. Comprehensive Security Assessment for a Cyber Physical Energy System: A Lesson from Ukraine’s Blackout. Autom. Electr. Power Syst. 2016, 40, 145–147. [Google Scholar]
- Liu, X.R.; Wu, Z.Q. Online Defense Research of Spatial-hidden Malicious Data Injection Attacks in Smart Grid. Proc. CSEE 2020, 40, 2546–2558. [Google Scholar]
- Liu, Y.; Ning, P.; Reiter, M.K. False Data Injection Attacks against State Estimation in Electric Power Grids. ACM Trans. Inf. Syst. Secur. (TISSEC) 2011, 14, 1–13. [Google Scholar] [CrossRef]
- Liang, J.W.; Sankar, L.; Kosut, O. Vulnerability Analysis and Consequences of False Data Injection Attack on Power System State Estimation. IEEE Trans. Power Syst. 2016, 31, 3864–3872. [Google Scholar] [CrossRef] [Green Version]
- Xie, L.; Mo, Y.; Sinopoli, B. False Data Injection Attacks in Electricity Markets. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010. [Google Scholar]
- Qu, Z.Y.; Dong, Y.C.; Qu, N.; Wang, L.; Li, Y.; Zhang, Y.; Mugemanyi, S. Survivability Evaluation Method for Cascading Failure of Electric Cyber Physical System Considering Load Optimal Allocation. Math. Probl. Eng. 2019, 2019, 1–15. [Google Scholar] [CrossRef] [Green Version]
- Liu, X.R.; Chang, P.; Sun, Q.Y. Grid False Data Injection Attacks Detection Based on XGBoost and Unscented Kalman Filter Adaptive Hybrid Prediction. Proc. CSEE 2021, 41, 5462–5476. [Google Scholar]
- Zhao, J.B.; Mili, L.; Wang, M. A Generalized False Data Injection Attacks Against Power System Nonlinear State Estimator and Countermeasures. IEEE Trans. Power Syst. 2018, 33, 4868–4877. [Google Scholar] [CrossRef]
- Yu, J.J.Q.; Hou, Y.; Li, V.O.K. Online False Data Injection Attack Detection with Wavelet Transform and Deep Neural Networks. IEEE Trans. Ind. Inform. 2018, 14, 3271–3280. [Google Scholar] [CrossRef]
- Singh, S.K.; Khanna, K.; Bose, R.; Panigrahi, B.K.; Joshi, A. Joint Transformation based Detection of False Data Injection Attacks in Smart Grid. IEEE Trans. Ind. Inform. 2018, 14, 89–97. [Google Scholar] [CrossRef]
- Fan, X.Y.; Du, L.; Duan, D.L. Synchrophasor Data Correction Under GPS Spoofing Attack: A State Estimation-Based Approach. IEEE Trans. Smart Grid 2018, 9, 4538–4546. [Google Scholar] [CrossRef]
- Ao, W.; Song, Y.D.; Wen, C.Y. Adaptive cyber-physical system attack detection and reconstruction with application to power systems. IET Control Theory Appl. 2016, 10, 1458–1468. [Google Scholar] [CrossRef]
- Farraj, A.; Hammad, E.; Kundur, D. A Distributed Control Paradigm for Smart Grid to Address Attacks on Data Integrity and Availability. IEEE Trans. Signal Inf. Process. Netw. 2018, 4, 70–81. [Google Scholar] [CrossRef]
- Sikdar, B.; Chow, J.H. Defending Synchrophasor Data Networks Against Traffic Analysis Attacks. IEEE Trans. Smart Grid 2011, 2, 819–826. [Google Scholar] [CrossRef]
- Fan, Y.W.; Zhang, Z.H.; Trinkle, M.; Dimitrovski, A.D.; Song, J.B.; Li, H.S. A Cross-Layer Defense Mechanism Against GPS Spoofing Attacks on PMUs in Smart Grids. IEEE Trans. Smart Grid 2015, 6, 2659–2668. [Google Scholar] [CrossRef]
- Yang, Q.Y.; An, D.; Min, R.; Yu, W.; Yang, X.Y.; Zhao, W. On Optimal PMU Placement-based Defense against Data Integrity Attacks in Smart Grid. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1735–1750. [Google Scholar] [CrossRef]
- Bi, S.Z.; Zhang, Y.J. Graphical Methods for Defense Against False-Data Injection Attacks on Power System State Estimation. IEEE Trans. Smart Grid 2014, 5, 1216–1227. [Google Scholar] [CrossRef] [Green Version]
- Liu, X.; Li, Z.Y.; Li, Z.Y. Optimal Protection Strategy Against False Data Injection Attacks in Power Systems. IEEE Trans. Smart Grid 2017, 8, 1802–1810. [Google Scholar] [CrossRef]
- Davarikia, H.; Barati, M. A tri-level programming model for attack-resilient control of power grids. J. Mod. Power Syst. Clean Energy 2018, 6, 918–929. [Google Scholar] [CrossRef] [Green Version]
- Hao, J.P.; Piechocki, R.J.; Kaleshi, D.; Chin, W.H.; Fan, Z. Sparse Malicious False Data Injection Attacks and Defense Mechanisms in Smart Grids. IEEE Trans. Ind. Inform. 2015, 11, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Han, Y.Q.; Guo, C.X.; Ma, S.Y.; Song, D.W. Modeling cascading failures and mitigation strategies in PMU based cyber-physical power systems. J. Mod. Power Syst. Clean Energy 2018, 6, 944–957. [Google Scholar] [CrossRef]
- Wang, Q.; Tai, W.; Tang, Y.; Ni, M.; You, S. A two-layer game theoretical attack-defense model for a false data injection attack against power systems. Electr. Power Energy Syst. 2019, 104, 169–177. [Google Scholar] [CrossRef]
- Wei, L.F.; Sarwat, A.I.; Saad, W.; Biswas, S. Stochastic Games for Power Grid Protection Against Coordinated Cyber-Physical Attacks. IEEE Trans. Smart Grid 2018, 9, 684–694. [Google Scholar] [CrossRef]
- Tian, J.; Tan, R.; Guan, X.H.; Liu, T. Enhanced Hidden Moving Target Defense in Smart Grids. IEEE Trans. Smart Grid 2019, 10, 2208–2223. [Google Scholar] [CrossRef]
- Morrow, K.L.; Heine, E.; Rogers, K.M.; Bobba, R.B.; Overbye, T.J. Topology Perturbation for Detecting Malicious Data Injection. In Proceedings of the 2012 45th Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2012. [Google Scholar]
- Kuntz, K.; Smith, M.; Wedeward, K.; Collins, M. Detecting, Locating, & Quantifying False Data Injections Utilizing Grid Topology through Optimized D-FACTS Device Placement. In Proceedings of the 2014 North American Power Symposium, Pullman, WA, USA, 7–9 September 2014. [Google Scholar]
- Xu, R.Z.; Wang, R.; Guan, Z.T.; Wu, L.F.; Wu, J.; Du, X.J. Achieving Efficient Detection against False Data Injection Attacks in Smart Grid. IEEE Access 2017, 5, 13787–13798. [Google Scholar] [CrossRef]
- Talebi, M.; Li, C.Y.; Qu, Z.H. Enhanced Protection Against False Data Injection by Dynamically Changing Information Structure of Microgrids. In Proceedings of the 2012 IEEE 7th Sensor Array and Multichannel Signal Processing Workshop, Hoboken, NJ, USA, 17–20 June 2012. [Google Scholar]
- Wang, S.C.; Ren, W. Stealthy False Data Injection Attacks against State Estimation in Power Systems: Switching Network Topologies. In Proceedings of the 2014 American Control Conference, Portland, OR, USA, 4–6 June 2014. [Google Scholar]
- Tang, Y.; Li, M.Y.; Wang, Q.; Ni, M. A Review on Research of Cyber-attacks and Defense in Cyber Physical Power Systems Part Two Detection and Protection. Autom. Electr. Power Syst. 2019, 43, 1–9+18. [Google Scholar]
- Wang, Q.; Cai, X.P.; Tang, Y.; Ni, M. Methods of cyber-attack identification for power systems based on bilateral cyber-physical information. Int. J. Electr. Power Energy Syst. 2021, 125, 106515. [Google Scholar] [CrossRef]
- Liu, S.; Chen, B.; Zourntos, T.; Kundur, D.; Butler-Purry, K. A Coordinated Multi-Switch Attack for Cascading Failures in Smart Grid. IEEE Trans. Smart Grid 2014, 5, 1183–1195. [Google Scholar] [CrossRef]
- Chen, B.; Butler-Purry, K.L.; Kundur, D. Impact Analysis of Transient Stability due to Cyber Attack on FACTS Devices. In Proceedings of the 2013 North American Power Symposium, Manhattan, KS, USA, 22–24 September 2013. [Google Scholar]
- Su, S.; Wu, C.J.; Ma, J.; Zeng, X.J. Attacker’s Perspective Based Analysis on Cyber Attack Mode to Cyber-Physical System. Power Syst. Technol. 2014, 38, 3115–3120. [Google Scholar]
- Ni, M.; Li, M.L.; Li, J.; Wu, Y.J.; Wang, Q. Concept and Research Framework for Coordinated Situation Awareness and Active Defense of Cyber-physical Power Systems Against Cyber-attacks. J. Mod. Power Syst. Clean Energy 2021, 9, 477–484. [Google Scholar] [CrossRef]
- Li, M.L.; Ni, M.; Yan, Y.S.; Si, Q.H.; Xue, F.; Xu, J.B. Cyber-Physical Coordinated Defense Method Against Malicious Attacks for Security and Stability Control System. Autom. Electr. Power Syst. 2021, 45, 113–120. [Google Scholar]
- Li, Y.; Li, Z.; Chen, L. Dynamic State Estimation of Generators Under Cyber Attacks. IEEE Access 2019, 7, 125252–125267. [Google Scholar] [CrossRef]
- Wang, J.Y.; Sun, Z.W.; Bao, B.; Shi, D.Y. Malicious Synchrophasor Detection Based on Highly Imbalanced Historical Operational Data. CSEE J. Power Energy Syst. 2019, 5, 11–20. [Google Scholar] [CrossRef]
- Jiang, X.Y.; Ge, Z.Q. Data Augmentation Classifier for Imbalanced Fault Classification. IEEE Trans. Autom. Sci. Eng. 2021, 18, 1206–1217. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.Z.; Ren, X.G.; Zhou, H.; Diao, X.C. A Classification Method Based on Feature Selection for Imbalanced Data. IEEE Access 2019, 7, 81794–81807. [Google Scholar] [CrossRef]
- Yi, H.K.; Jiang, Q.C.; Yan, X.F.; Wang, B. Imbalanced Classification Based on Minority Clustering Synthetic Minority Oversampling Technique with Wind Turbine Fault Detection Application. IEEE Trans. Ind. Inform. 2021, 17, 5867–5875. [Google Scholar] [CrossRef]
- Xue, T.; Wang, Q. False Data Injection Attack on Power System Data-Driven Methods Based on Generative Adversarial Networks. In Proceedings of the 2021 IEEE Sustainable Power and Energy Conference, Nanjing, China, 22–24 September 2013. [Google Scholar]
- An, C.S.; Sun, J.T.; Wang, Y.F.; Wei, Q.J. A K-means Improved CTGAN Oversampling Method for Data Imbalance Problem. In Proceedings of the 2021 IEEE 21st International Conference on Software Quality, Reliability and Security, Haikou, China, 6–10 December 2021. [Google Scholar]
- Patki, N.; Wedge, R.; Veeramachaneni, K. The Synthetic Data Vault. In Proceedings of the 2016 IEEE International Conference on Data Science and Advanced Analytics, Montreal, QC, Canada, 17–19 October 2016. [Google Scholar]
- Ouyang, T.; He, Y.; Li, H.J.; Sun, Z.Y.; Baek, S. Modeling and Forecasting Short-Term Power Load with Copula Model and Deep Belief Network. IEEE Trans. Emerg. Top. Comput. Intell. 2019, 3, 127–136. [Google Scholar] [CrossRef] [Green Version]
- Xia, Y.S.; Wang, Y.; Zhou, L.; Fan, R.S. False Data Injection Attack Detection Method Based on Improved Generative Adversarial Network. Electr. Power Constr. 2022, 43, 58–65. [Google Scholar]
- Cao, J.; Wang, D.; Qu, Z.Y.; Cui, M.S.; Xu, P.C.; Xue, K.; Hu, K.W. A Novel False Data Injection Attack Detection Model of the Cyber-Physical Power System. IEEE Access 2020, 8, 95109–95125. [Google Scholar] [CrossRef]
- Xuan, Y.; Si, Q.G.; Zhu, J.; Sun, Z.Q.; Zhao, J.; Xu, M.J.; Xu, S.L. Multi-Model Fusion Short-Term Load Forecasting Based on Random Forest Feature Selection and Hybrid Neural Network. IEEE Access 2021, 9, 69002–69009. [Google Scholar] [CrossRef]



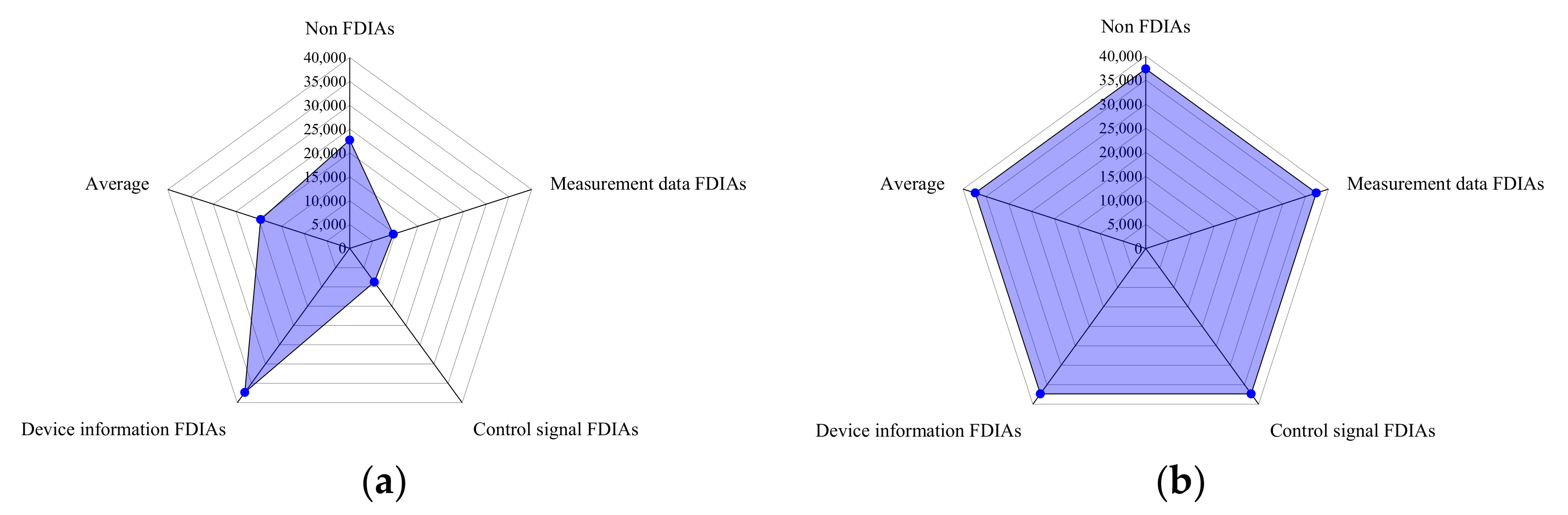



| Relabel Scenario Label | Scenario Category | Original Scenario Label |
|---|---|---|
| 0 | Non FDIAs | 1–6, 13, 14, 41 |
| 1 | Measurement data FDIAs | 7–12 |
| 2 | Control signal FDIAs | 15–20 |
| 3 | Device information FDIAs | 21–30, 35–40 |
| Feature | Feature Description | Feature | Feature Description |
|---|---|---|---|
| PA1:VH-PA3:VH | Phase A-C voltage Phase angle | PM10:V-PM12:V | Pos.-Neg.-Zero current phase magnitude |
| PM1:V-PM3:V | Phase A-C voltage Phase magnitude | F | Frequency for relays |
| PA4:IH-PA6:IH | Phase A-C current Phase angle | DF | Frequency delta (dF/dt) for relays |
| PM4:I-PM6:I | Phase A-C current Phase magnitude | PA:Z | Appearance impedance for relays |
| PA7:VH-PA9:VH | Pos.-Neg.-Zero voltage phase angle | PA:ZH | Appearance impedance angle for relays |
| PM7:VH-PM9:VH | Pos.-Neg.-Zero voltage phase magnitude | S | Status flag for relays |
| PA10:VH-PA12:VH | Pos.-Neg.-Zero current phase angle |
| Feature TOP (1–15) | Mutual Information Value | Feature TOP (16–30) | Mutual Information Value |
|---|---|---|---|
| R2-PA3:VH | 1.3633 | R1-PA4:IH | 1.2026 |
| R1-PA3:VH | 1.3628 | R2-PA10:IH | 1.2023 |
| R4-PM6:I | 1.3622 | R2-PA7:VH | 1.2007 |
| R3-PA4:IH | 1.3602 | R2-PA:Z | 1.1989 |
| R3-PA3:VH | 1.3596 | R2-PA4:IH | 1.1953 |
| R4-PA4:IH | 1.3438 | R4-PM1:V | 1.1951 |
| R3-PM1:V | 1.3276 | R2-PM10:I | 1.1919 |
| R1-PM6:I | 1.3238 | R2-PM6:I | 1.1898 |
| R1-PA7:VH | 1.3206 | R3-PA:ZH | 1.1890 |
| R4-PA6:IH | 1.3201 | R2-PM4:I | 1.1439 |
| R4-PA1:VH | 1.3170 | R1-PA:Z | 1.1274 |
| R1-PA10:IH | 1.3007 | R4-PA:ZH | 1.0992 |
| R3-PA1:VH | 1.2674 | R4-PA:Z | 1.0911 |
| R3-PA:Z | 1.2637 | R1-PA:ZH | 1.0671 |
| R3-PA6:IH | 1.2600 | R2-PM3:V | 1.0397 |
| Sample Number | Number of Original False Data Samples | Number of Detected False Data Samples | Number of Reconstructed False Data Samples | First Reconstruction Rate/% | Second Reconstruction Rate/% |
|---|---|---|---|---|---|
| 1 | 1000 | 1000 | 988 | 98.8 | 100 |
| 2 | 500 | 500 | 497 | 99.4 | 100 |
| 3 | 100 | 100 | 100 | 100 | - |
| 4 | 10 | 10 | 10 | 100 | - |
| Sample Number | MAE Value/p.u. | Sample Number | MAE Value/p.u. | Sample Number | MAE Value/p.u. |
|---|---|---|---|---|---|
| 1 | 0.00535419 | 6 | 0.00533444 | 11 | 0.00544320 |
| 2 | 0.00524969 | 7 | 0.00528232 | 12 | 0.00536028 |
| 3 | 0.00535279 | 8 | 0.00521685 | 13 | 0.00536291 |
| 4 | 0.00533873 | 9 | 0.00533234 | 14 | 0.00536626 |
| 5 | 0.00530187 | 10 | 0.00532769 | 15 | 0.00530528 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bo, X.; Qu, Z.; Wang, L.; Dong, Y.; Zhang, Z.; Wang, D. Active Defense Research against False Data Injection Attacks of Power CPS Based on Data-Driven Algorithms. Energies 2022, 15, 7432. https://doi.org/10.3390/en15197432
Bo X, Qu Z, Wang L, Dong Y, Zhang Z, Wang D. Active Defense Research against False Data Injection Attacks of Power CPS Based on Data-Driven Algorithms. Energies. 2022; 15(19):7432. https://doi.org/10.3390/en15197432
Chicago/Turabian StyleBo, Xiaoyong, Zhaoyang Qu, Lei Wang, Yunchang Dong, Zhenming Zhang, and Da Wang. 2022. "Active Defense Research against False Data Injection Attacks of Power CPS Based on Data-Driven Algorithms" Energies 15, no. 19: 7432. https://doi.org/10.3390/en15197432
APA StyleBo, X., Qu, Z., Wang, L., Dong, Y., Zhang, Z., & Wang, D. (2022). Active Defense Research against False Data Injection Attacks of Power CPS Based on Data-Driven Algorithms. Energies, 15(19), 7432. https://doi.org/10.3390/en15197432











