UAV Support for Mission Critical Services
Abstract
:1. Introduction
- Exploits UAV mobility for on-demand deployments of MCS. This covers both the delivery capability of UAVs and using UAVs as a mobile communications node.
- Exploits the virtualization of commercial mobile network terminals to use them for MCS communications and ad hoc implementation of service platforms. These service platforms can replace platforms that stopped functioning due to disaster or power grid failure but also platforms that are dedicated solely to MCS services.
2. Status of Mission-Critical Solutions
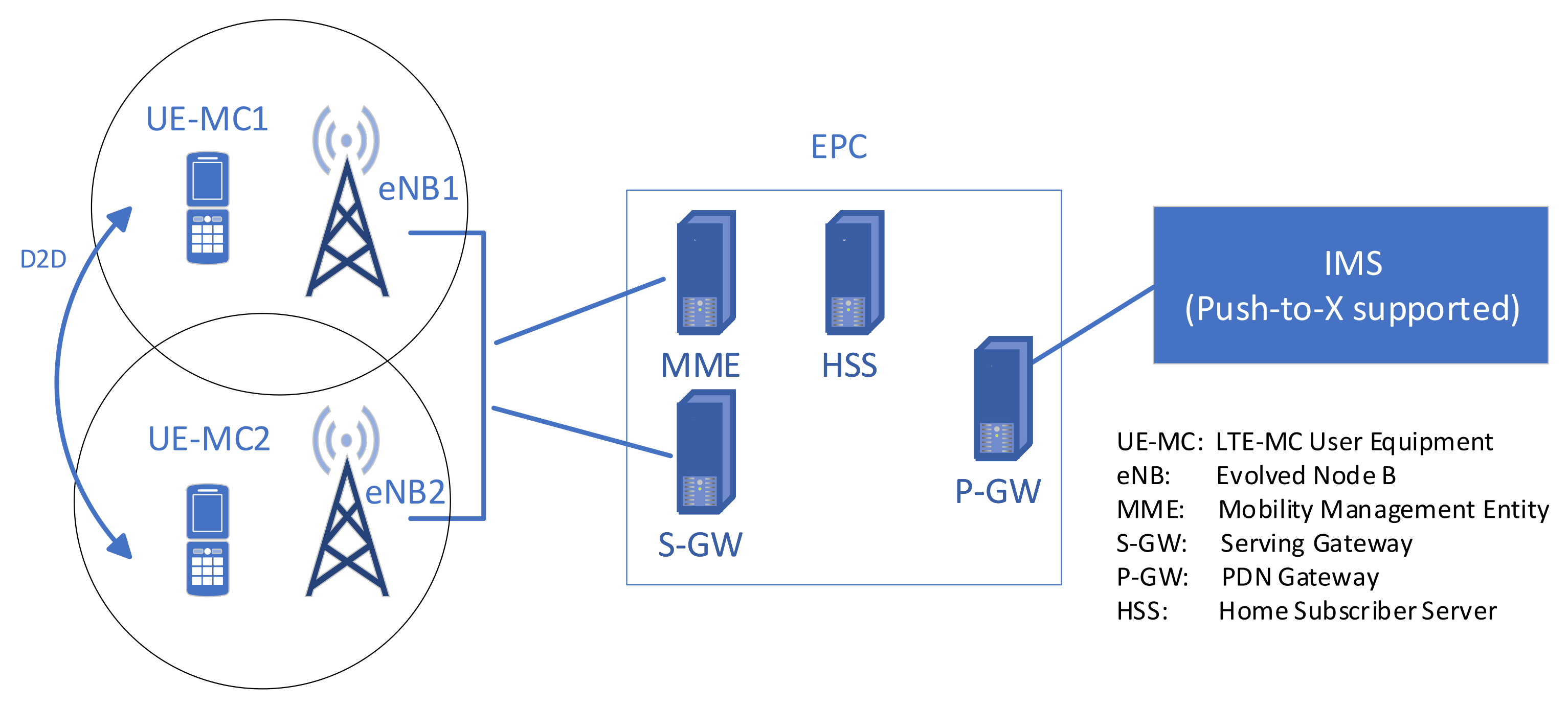
- Trunked Mode Operation (TMO). In this mode, a fixed private TETRA infrastructure with TETRA base stations is used. This mode, in general, cannot be used in disasters.
- Direct Mode Operation (DMO). This mode allows direct communication between the TETRA mobile nodes (TMNs) without support from the TETRA infrastructure.
3. UAV Characteristics, Classifications and Commercial Deployments Status
3.1. Classification of UAVs
3.2. UAVs as Transportation Means
3.3. UAVs as a Part of the Communication Infrastructure
4. Potential Roles of UAV in MCS
- zin the case of properly working infrastructure, the UAVs as a part of a MCS can be deployed to extend the coverage and to provide MCS-specific services and platforms for their deployment. In such a case UAVs can be used for rescue action or to perform a dedicated task; however, they may benefit from the connectivity and services offered by the infrastructure.
- If the infrastructure is not functioning correctly (in a case of disasters, power grid failure, etc.), the UAVs can be used for providing ad hoc connectivity or as an ad hoc service platform. In this scenario, it is assumed that UAVs’ computing capabilities will be used for MCS services and other purposes (support for Smart City, etc.).
4.1. Scenario 1
- UAV as a transporter. UAVs can move to areas where the presence of humans is dangerous (radiation, chemical toxins, bacteria, high temperature). Moreover, they can take some action depending on the capability of the robotic part of the drone. Thus, the delivery UAV can be used to install dedicated sensors and bring food, water, medicines, etc., to remote, non-accessible human locations. Several subsequent missions of such delivery UAVs can be needed to achieve the goal. For example, more complicated and larger devices can be transported by UAVs in several missions. As has been mentioned, the combined UAV-robot solutions for parcel delivery do not exist. A solution to this problem will be the transportation of a small, autonomic robot to the destination. Such an intelligent robot can assemble the delivered parts.
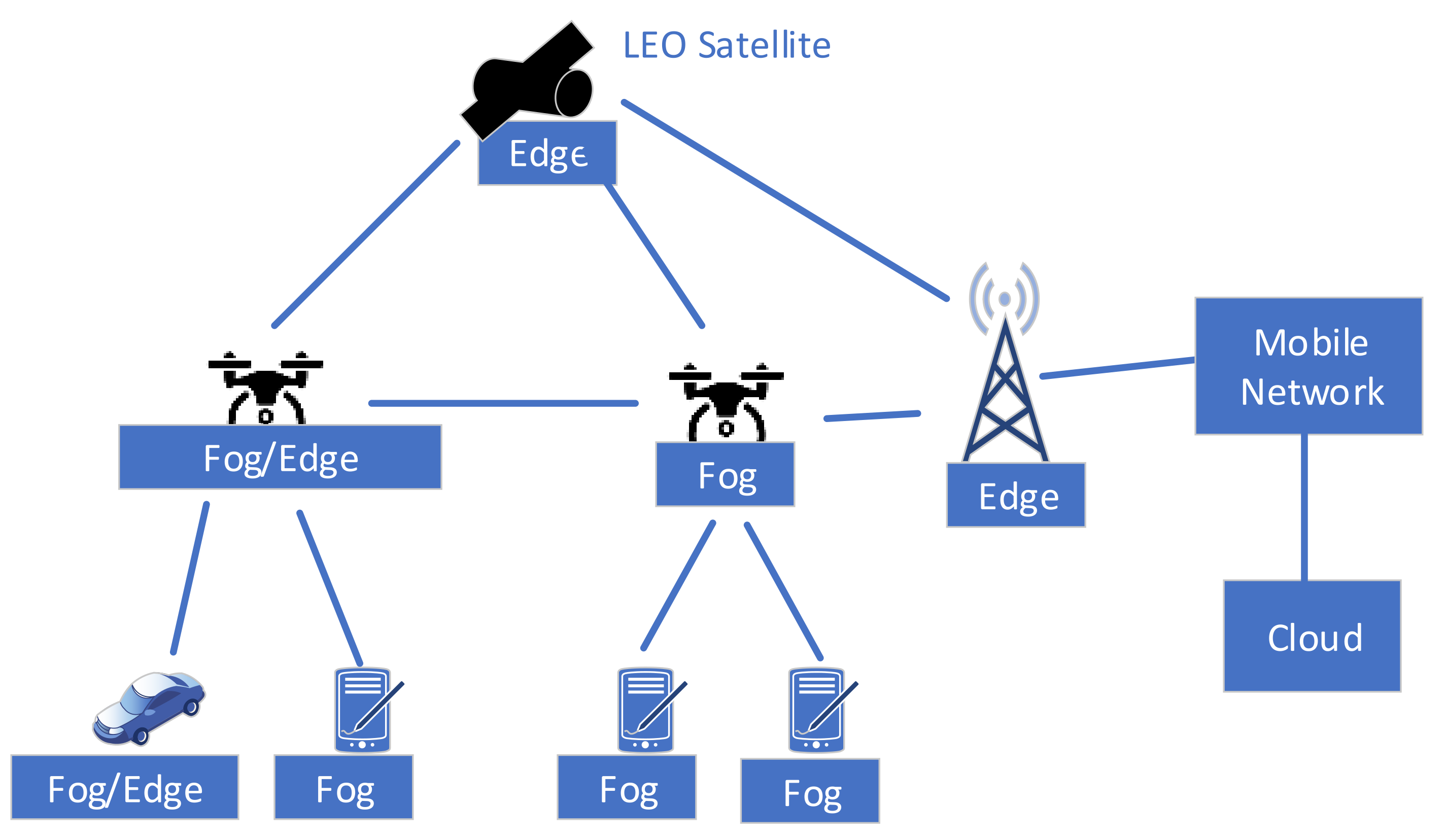
- UAV as a deployer of local wireless network or access network extension. In this case, the UAV can transport and deploy a local base station that can provide connectivity combined with required services. There is an assumption that such wireless networks will use popular and standardized solutions to allow users equipped with commercial mobile network terminals to use the system. It mainly concerns WiFi and LTE—for both solutions, a ‘mobile’ base station with a dedicated uplink can be provided in a small form factor. It can be a Private LTE variant that is simpler than the classical LTE version. As already mentioned, there exist on a market LTE complete solutions in the form of a backpack. The creation of a local network has, in some cases, value per se; however, in other cases, it may be needed to provide a link that connects the local wireless network with the external world. In most cases, such backbone links will be wireless. It can be created in two ways.The first lies in using the same wireless technology as the one used for local networks, but with a directional antenna that enables the creation of a relatively long-range link. This approach is well suited to WiFi networks. The second approach lies in using a gateway that connects the local network to the wide-area network. Such a solution can be created, for example, using pretty popular WiFi-LTE gateways (please note that in this scenario, proper functioning of infrastructure-based networking solutions is assumed).Another option is to use an LEO or MEO satellites as a backbone. As LEO, the Starlink solution can be used [47]. As in the previous case, the installation of the complete solution may require several UAVs flights to transport the base station, battery, antenna subsystem and a robot able to assemble these components. The UAVs with computing capabilities can be used as virtualized, mobile mini data centres with predefined MCS services.
- UAV as a deployer of dedicated sensors in remote locations. Here, UAVs are used to deploy remote sensors needed to provide more information about the environment. There can be sensors of specific chemical substances, temperature, humidity, radiations, vibrations, etc. In most cases, such sensors’ size and weight are insignificant. They can be deployed as independent nodes that record sensor(s) specific parameters and transmit them. In some cases, nodes that aggregate the sensor traffic and/or perform the role of a gateway to another network can also be used. The UAV also can play a role of a ‘mobile sensor’ flying autonomously between pre-programmed waypoints and collecting environmental data or conducting audio–video surveillance.
4.2. Scenario 2
- Provide connectivity between the nodes and terminals of MCS. If possible, eventual integration with NTN (LEO satellites, etc.) should be provided for that purpose.
- Provide MCS services to support rescue teams. This is so far the role of solutions, such as TETRA (narrowband) and recently-designed LTE-MC (broadband). In such a solution, the MCS provides voice, short message and data transmission to a small group of users of a dedicated network. In LTE-MC, multimedia communication is allowed due to high bandwidth and the use of a flexible platform (IP Multimedia Subsystem (IMS)).
- Provide basic communication services to persons in the impacted area. It assumes the use of battery-powered commercial terminals (i.e., smartphones).
- Provide backup software platforms to solutions that should be working despite the lack of support from infrastructure-based service platforms—for example, processing data from IoT sensors, control of utilities, road traffic, Smart City solutions, Supervisory Control Furthermore, Data Acquisition (SCADA) systems, etc. Adding an ad hoc service platform is not supported by TETRA nor LTE-MC.
5. VMCS Concept
- The analysis of the services offered by TETRA and LTE-MC discussed in Section 2, as well as shortcomings of the technologies. In both cases, the set of services is predefined. Such an approach is relatively simple but has two drawbacks. Foremost, it does not allow using commercial terminals of wireless networks not supporting LTE-MC, for example, LTE/WiFi smartphones. Using such terminals is of premium importance in the case of disasters as it allows for establishing communication with any user of the commercial mobile network via MCS without using dedicated MCS terminals. The second problem is the necessity of supporting by MCS the existing IoT or SCADA solutions that lost connectivity to their service platforms. Both mentioned solutions provide no such support nor support for programmability.
- The analysis of the concepts concerning the use of UAVs as flying communication nodes (or networks) with computing capabilities presented in Section 3. The UAV transportation and endurance capabilities enable to use them as can be used for quick provisioning of connectivity on a relatively large area.
- The analysed in Section 4 concepts that propose the use of UAV computing capabilities, typically marked as edge computing or MEC.
- Analysis of the two scenarios presented in Section 4 shows that, in some cases, MCS can be a part of a larger networking/computing solution or can be deployed on an island basis. The second case raises issues of management and orchestration of ad hoc deployed MCS.
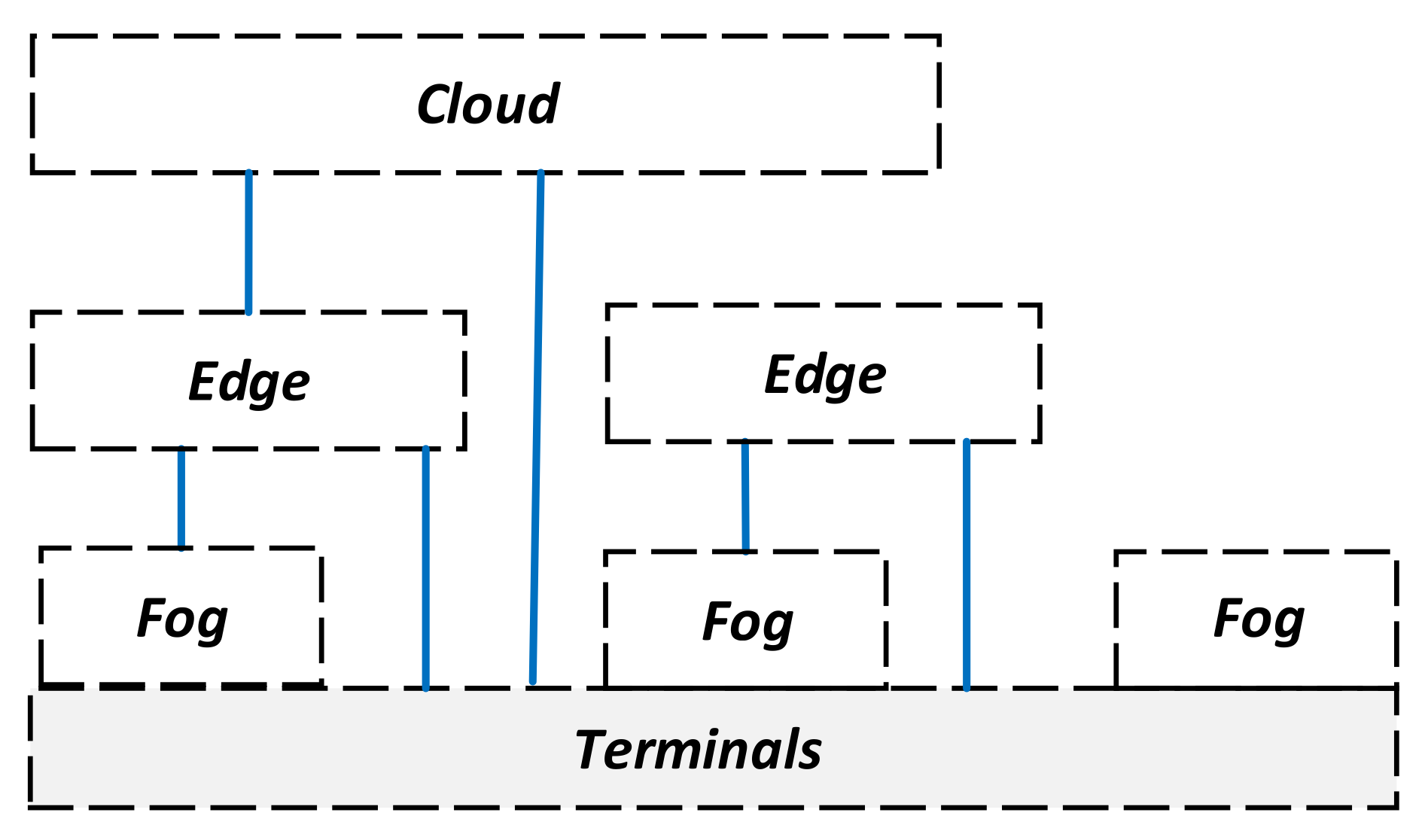
- Uses a combined Fog/Edge/Cloud approach, i.e., exploits computing capabilities of all system nodes, including terminals. Due to Fog, the use of all system resources is maximised, and terminals can be dynamically adapted to service needs (there is no need to make dedicated terminals, commercial smartphones can be a part of the system).
- Uses distributed, combined Fog/Edge/Cloud orchestration with redundancy that is needed in an unreliable, distributed computing environment.
- Exploits the mobility of UAVs as a part of the orchestration.
5.1. VMCS Foundations
- Terminal nodes. VMCS end-users operate such nodes. Some may be dedicated to VMCS, whereas others are just commercial terminals. Most have cloudlets; however, vehicular terminals may provide mini data centres.
- Edge nodes are nodes between the terminals and the core part of the network. They typically may have mini data centres.
- Core nodes. These nodes typically are connected to a reliable infrastructure and clouds by high bit rate links. Their functions can be implemented using Cloud. In Scenario 2 (Section 4), such components may not exist, and the Edge nodes take their role.
5.2. VMCS Orchestration
5.2.1. VMCS Cloud Orchestration
5.2.2. VMCS Edge Orchestration
- Dynamic Edge infrastructure. There is a need to efficiently collect, process and maintain information about the state of the VMCS Edge infrastructure. It includes operations for discovering new nodes and links, their geo-position, evaluating nodes’ battery state and amount of offered resources and links, providing nodes’ and links’ reputation evaluation (in terms of reliability) and predicting resources status. The information about the resource state (offered and consumed resources) should be, for reliability, kept in a lightweight, distributed database.
- Distributed and reliable management and orchestration of the Edge. To cope with unreliability, there is a need for using multiple, synchronised copies of functional entities involved in orchestration. It implies a definition of an orchestrator that can cope with vanishing orchestrator functions—when one of them disappears (due to lack of energy or communication link breakdown), the backup function should conclude the management or orchestration task. Moreover, the orchestration commands should have multiple copies transferred using a disjoint path (if possible) to cope with the unreliability of links. Some network nodes should be used as relays for management and orchestration messages, with additional mechanisms ensuring their reliable delivery.
- Exploitation of Edge nodes mobility: In VMCS, some nodes, particularly UAVs, are mobile. The Edge orchestrator should cope with the nodes’ mobility and should be able to exploit it—if possible, the orchestrator should define their optimal position and steer them to achieve this position.
- Edge service templates specifics. The service template (aka blueprint) of VMCS needs to have a different form than the templates used by the MANO orchestrator. It should allow for the implementation of DTN [56] based services, i.e., the temporary absence of a link should be accepted as a normal state and information collected by a node should be transferred to another node when connectivity is restored. The template should include duplicated nodes/functions (in case of failure or node disconnection), a specific mechanism for delivery and delivery confirmation of sent messages. More details about VMCS services implementation will be provided in the subsequent subsection.
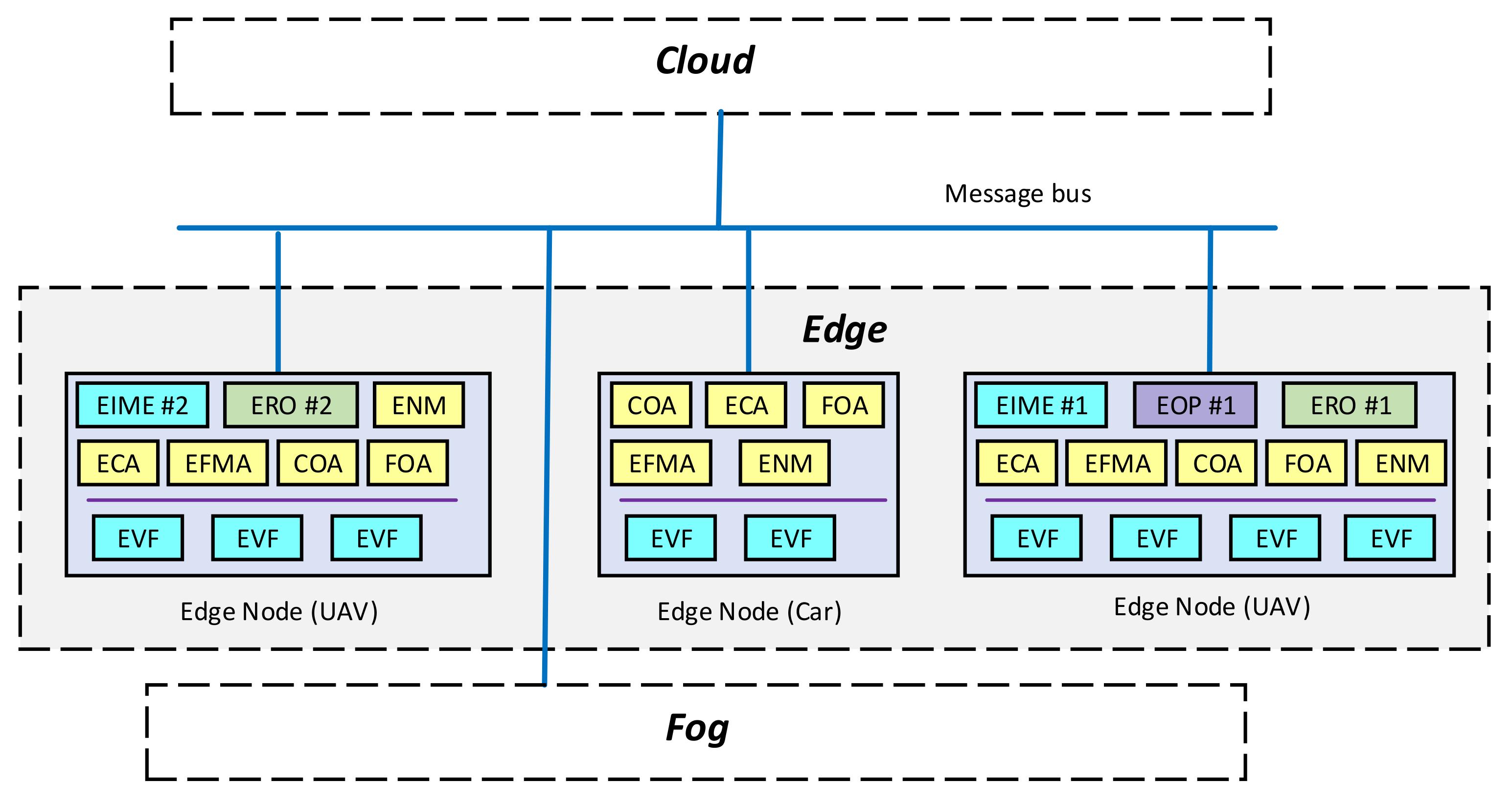
- Edge Node Manager (ENM). This is a component of each Edge node. It performs overall management of the node and, via COA and FOA, interacts with Fog and Cloud orchestrators. It discovers entities of the Edge orchestration system.
- Fog Orchestration Agent (FOA). This is a component of each Edge node. It is involved in Fog orchestration (if applicable), playing a master role. It monitors the Fog infrastructure and drives Fog orchestration.
- Cloud Orchestration Agent (COA). This is a component of each Edge node. It takes orders from the Cloud orchestrator (if applicable) regarding Edge orchestration.
- Edge Connectivity Agent (ECA). This is a component of each Edge node that is responsible for the reliable delivery of orchestration and management messages between the Edge nodes.
- Edge Functions Migration Agent (EFMA). This is a component of the distributed Edge orchestrator that is responsible for decisions regarding migration Edge Virtual Functions (EVF) and functions of the distributed orchestrator, i.e., VOP, ERO and EIME. For the sake of reliability, multiple instances of EFMA are allowed.
- Edge Infrastructure Monitoring Entities (EIME). EIME is a set of entities that keeps the information about the infrastructure resources’ state and location. They also try to predict the resource state based on historical data. In the case of mobile Edge nodes, EIME obtains their position, and at the request of ERO, can change it. For the sake of reliability, there are multiple synchronised EIME instances.
- Edge Reliable Orchestrator (ERO). This logical entity is responsible for the orchestration process. It interacts with EIME to obtain information about the state of resources. Based on the VMCS service template analysis and the state of resources, it deploys Edge Virtual Functions (EVFs). For reliability, there are multiple synchronised ERO instances in the system.
- Edge Virtual Functions (EVFs). These functions implement the required VMCS services in the Edge and are part of the service template. Please note that part of the Service can be implemented in a Fog and/or in a Cloud.
- Edge Operator Portal (EOP). The Edge Operator Portal is the functionality that allows the operator to interact with the Edge platform. It can be used to monitor Edge status and to enforce some Edge node actions, including the definition of mobile nodes’ position. Logically it is a single entity but, for the sake of reliability, can be implemented as a set of multiple, synchronised components with assigned priorities of operations.
5.2.3. VMCS Fog Orchestration
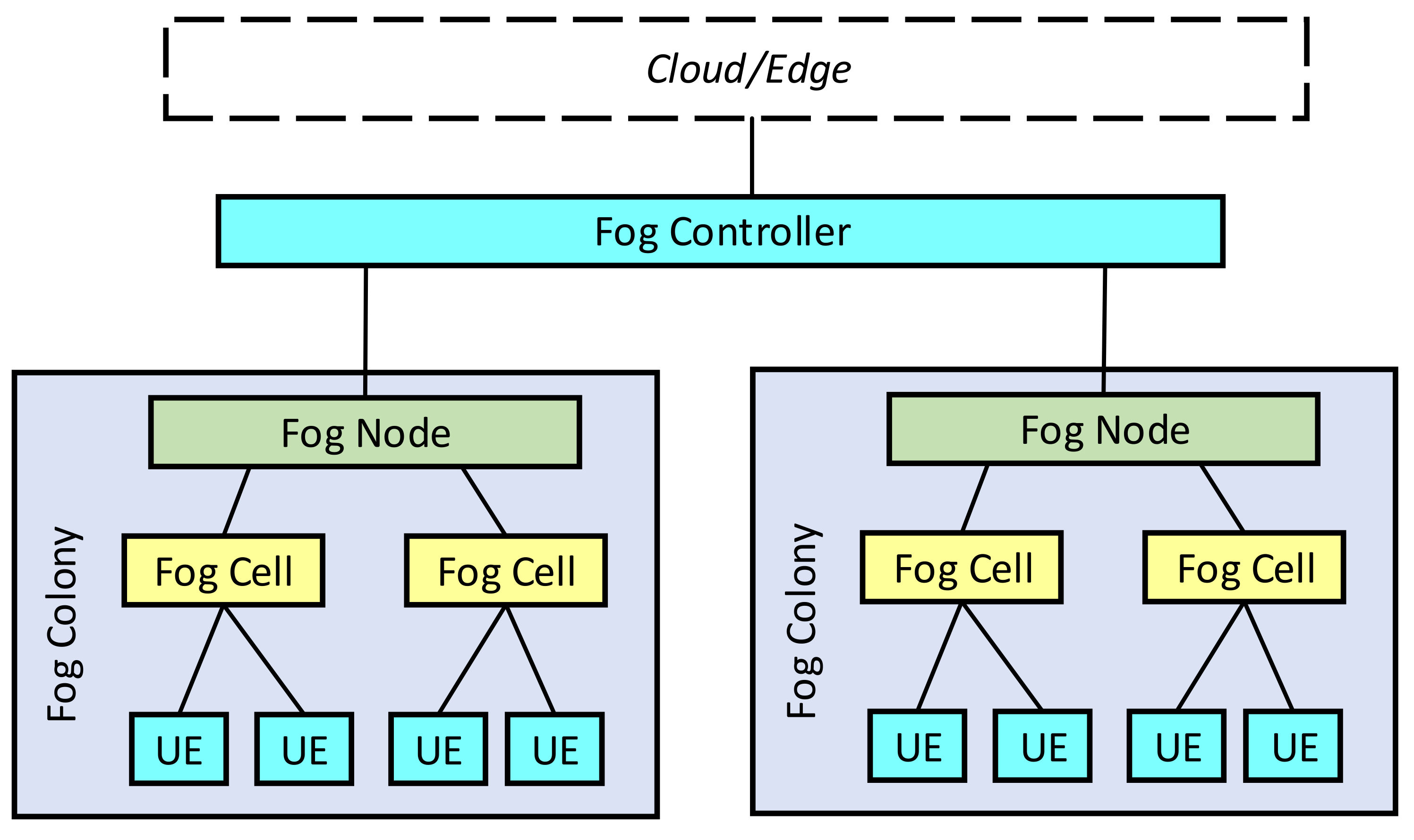
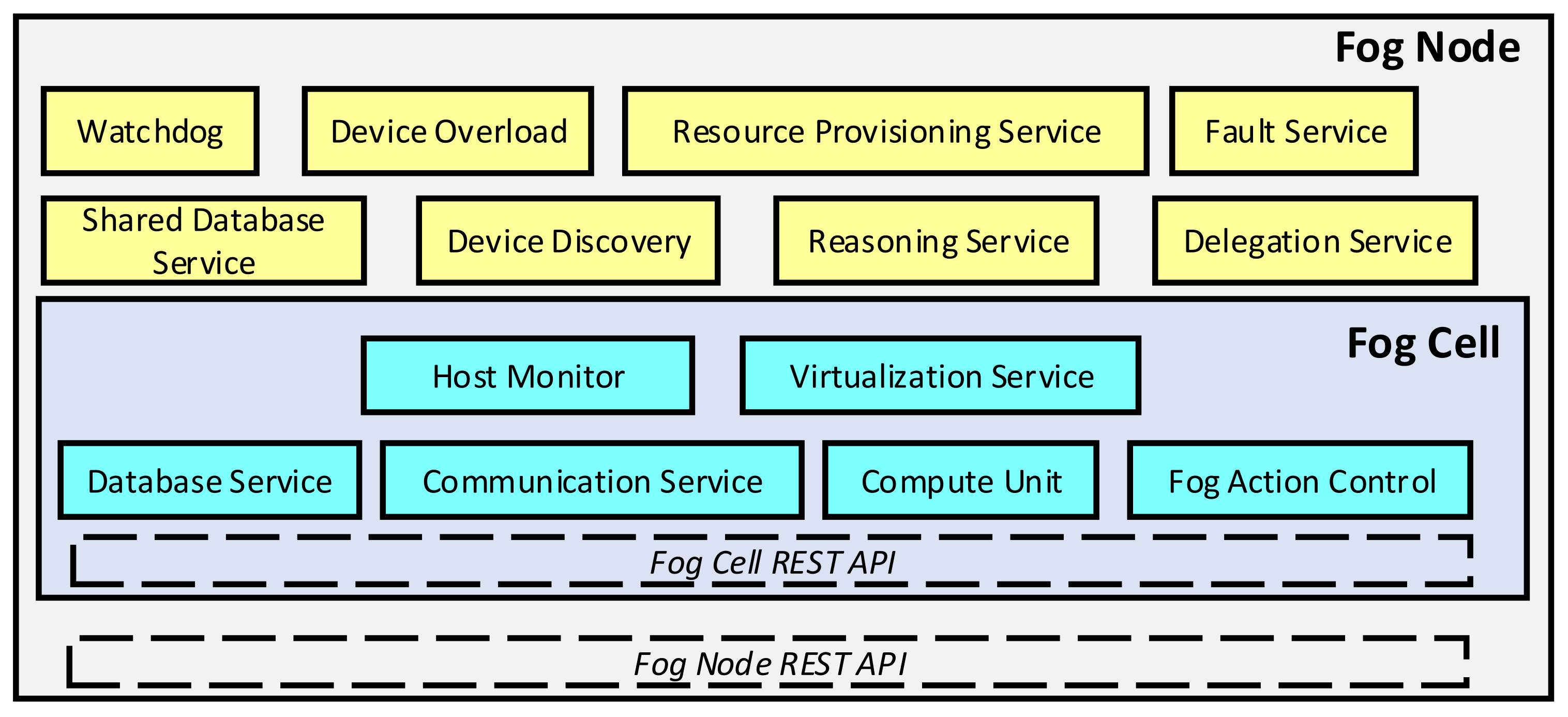
- Fog Cells represent virtual resources of UEs (also the IoT devices) that Fog services use.
- Fog Nodes are specific Fog Cells that act as access points for other Fog cells and provide connectivity with other Fog Nodes.
- Fog Colonies act as micro data centres composed of distributed resources that consist of Fog Cells and their terminals connected to a Fog Node. Each Fog colony has one Head Fog Node.
- The Fog Controller is used for the discovery of new resources. It provisions resources in the Edge or Cloud that support Fog operations. If Cloud or Edge is available, the Fog controlled can be placed in the Edge or Cloud, respectively.
5.2.4. Remarks on VMCS Orchestration
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| 3GPP | 3rd Generation Partnership Project |
| 5G | 5th Generation |
| 5GC | 5G Core |
| BVLOS | Beyond Visual Line of Sight |
| C2 | Command and Control |
| CNF | Cloud-native Network Function |
| CU | Centralised Unit |
| DTN | Disruption Tolerant Networking |
| DU | Distributed Unit |
| EPC | Evolved Packet Core |
| ETSI | European Telecommunications Standards Institute |
| EU | European Union |
| GCS | Ground Control Station |
| GPS | Global Positioning System |
| HAPS | High Altitude Platform System |
| ICT | Information and Communications Technology |
| IMS | IP Multimedia Subsystem |
| IoT | Internet of Things |
| ISM | Industrial, Scientific and Medical |
| LEO | Low Earth Orbit |
| LoraWAN | Long Range Wide Area Network |
| LTE | Long Term Evolution |
| LTE-M | LTE Machine Type Communication |
| LTE-MC | LTE Mission Critical |
| MANET | Mobile Ad hoc Network |
| MANO | Management and Orchestration |
| MCS | Mission-Critical System |
| MEC | Multi-access Edge Computing |
| MEO | Medium Earth Orbit |
| MIMO | Multiple Input Multiple Output |
| NASA | National Aeronautics and Space Administration |
| NB-IoT | Narrowband Internet of Things |
| NF | Network Function |
| NFV | Network Function Virtualisation |
| NFVI | NFV Infrastructure |
| NR | New Radio |
| NS | Network Slicing |
| NTN | Non-Terrestrial Network |
| P25 | Project 25 |
| POTS | Plain Old Telephone Service |
| PPDR | Public Protection & Disaster Relief |
| ProSe | Proximity-based Services |
| QoS | Quality of Service |
| RRH | Remote Radio Head |
| SBA | Service-Based Architecture |
| SCADA | Supervisory Control And Data Acquisition |
| SMS | Short Message Service |
| TDMA | Time-Division Multiple Access |
| TEDS | TETRA Enhanced Data Service |
| TETRA | Terrestrial Trunked Radio |
| TETRAPOL | Terrestrial Trunked Radio Police |
| UAS | Unmanned Aircraft System |
| UAV | Unmanned Aerial Vehicle |
| UE | User Equipment |
| UTM | Unmanned Aircraft Systems Traffic Management |
| V2X | Vehicle to Everything |
| VLOS | Visual Line of Sight |
| VMCS | Virtualized Mission Critical System |
| VNF | Virtual Network Function |
| VoIP | Voice over IP |
| VTOL | Vertical Take-Off and Landing |
| WiFi | WiFi |
References
- ETSI EN 300 392-1; Terrestrial Trunked Radio (TETRA); Voice Plus Data (V+D); Part 1: General Network Design. ETSI: Sophia Antipolis, France, 2009.
- PAS 0001-1-1; TETRAPOL Specifications; Part 1: General Network Design; Part 1: Reference Model. TETRAPOL: Bois d’Arcy, France, 1999.
- TIA-102.AABA-C; Project 25 Trunking Overview Digital Radio Technical. TIA: Arlington, VA, USA, 2019.
- 3GPP TE 23.002; Technical Specification Group Services and System Aspects; Network architecture (Release 15). ETSI: Sophia Antipolis, France, 2018.
- 3GPP TS 23.179; Functional Architecture and Information Flows to Support Mission-Critical Communication Services. ETSI: Sophia Antipolis, France, 2017.
- Fragkiadakis, A.; Askoxylakis, I.; Tragos, E.; Verikoukis, C. Ubiquitous Robust Communications for Emergency Response using Multi-Operator. EURASIP J. Wirel. Commun. Netw. 2011. [Google Scholar] [CrossRef] [Green Version]
- 3GPP TS 23.246; Multimedia Broadcast/Multicast Service (MBMS); Architecture and Functional Description. ETSI: Sophia Antipolis, France, 2022.
- 3GPP TS 24 481; Mission Critical Services (MCS) Group Management; Protocol Specification. ETSI: Sophia Antipolis, France, 2019.
- 3GPP TS 23.228; IP Multimedia Subsystem (IMS), Stage 2. ETSI: Sophia Antipolis, France, 2021.
- 3GPP TS 23.303; Proximity-Based Services (ProSe); Stage 2. ETSI: Sophia Antipolis, France, 2021.
- 3GPP TS 22.179; Mission Critical Push to Talk (MCPTT); Stage 1. ETSI: Sophia Antipolis, France, 2022.
- 3GPP TS 22.280; Mission Critical Services Common Requirements (MCCoRe); Stage 1. ETSI: Sophia Antipolis, France, 2022.
- 3GPP TS 22.281; Mission Critical (MC) Video. ETSI: Sophia Antipolis, France, 2022.
- 3GPP TS 22.282; Mission Critical (MC) Data. ETSI: Sophia Antipolis, France, 2022.
- Kaleem, Z.; Yousaf, M.; Qamar, A.; Ahmad, A.; Duong, T.Q.; Choi, W.; Jamalipour, A. UAV-Empowered Disaster-Resilient Edge Architecture for Delay-Sensitive Communication. IEEE Netw. 2019, 33, 124–132. [Google Scholar] [CrossRef]
- 3GPP TS 23.180; Mission Critical Services Support in the Isolated Operation for Public Safety (IOPS) Mode of Operation. ETSI: Sophia Antipolis, France, 2022.
- 3GPP TR 23.744; Study on Location Enhancements for Mission-Critical Services. ETSI: Sophia Antipolis, France, 2020.
- 3GPP TS 23.501; System Architecture for the 5G System (5GS); Stage 2 (Release 17). ETSI: Sophia Antipolis, France, 2022.
- 3GPP TS 28.530; Management and Orchestration; Concepts, Use Cases and Requirements. ETSI: Sophia Antipolis, France, 2021.
- 3GPP TS 23.289; Mission Critical Services over 5G Systems. ETSI: Sophia Antipolis, France, 2022.
- Lin, X.; Rommer, S.; Euler, S.; Yavuz, E.A.; Karlsson, R.S. 5G from Space: An Overview of 3GPP Non-Terrestrial Networks. IEEE Commun. Stand. Mag. 2021, 5, 147–153. [Google Scholar] [CrossRef]
- Gupta, A.; Afrin, T.; Scully, E.; Yodo, N. Advances of UAVs toward Future Transportation: The State-of-the-Art, Challenges, and Opportunities. Future Transp. 2021, 1, 326–350. [Google Scholar] [CrossRef]
- Watts, A.C.; Ambrosia, V.G.; Hinkley, E.A. Unmanned Aircraft Systems in Remote Sensing and Scientific Research: Classification and Considerations of Use. Remote Sens. 2012, 4, 1671–1692. [Google Scholar] [CrossRef] [Green Version]
- Eisenbeiß, H. UAV Photogrammetry. Ph.D. Thesis, ETH Zurich, Zurich, Switzerland, 2009. [Google Scholar]
- Qi, S.; Wang, F.; Jing, L. Unmanned aircraft system pilot/operator qualification requirements and training study. MATEC Web Conf. 2018, 179, 03006. [Google Scholar] [CrossRef] [Green Version]
- Jeziorska, J. UAS for Wetland Mapping and Hydrological Modeling. Remote Sens. 2019, 11, 1997. [Google Scholar] [CrossRef] [Green Version]
- 3GPP TS 22.125; Unmanned Aerial System (UAS) Support in 3GPP. ETSI: Sophia Antipolis, France, 2022.
- Thiels, C.A.; Aho, J.M.; Zietlow, S.P.; Jenkins, D.H. Use of Unmanned Aerial Vehicles for Medical Product Transport. Air Med. J. 2015, 34, 104–108. [Google Scholar] [CrossRef]
- Zipline. Zipline Delivers 1 Million COVID-19 Vaccines in Ghana. Available online: https://www.flyzipline.com/press/zipline-delivers-1-million-covid-19-vaccines-in-ghana (accessed on 27 May 2022).
- Wing. Available online: https://wing.com/ (accessed on 1 June 2022).
- FlyingBasket Company Webpage. Available online: https://flyingbasket.com/ (accessed on 1 June 2022).
- Zeng, Y.; Wu, Q.; Zhang, R. Accessing From the Sky: A Tutorial on UAV Communications for 5G and Beyond. Proc. IEEE 2019, 107, 2327–2375. [Google Scholar] [CrossRef] [Green Version]
- 3GPP TS 23.256; Support of Uncrewed Aerial Systems (UAS) Connectivity, Identification and Tracking; Stage 2. ETSI: Sophia Antipolis, France, 2022.
- The Concept of Operations for European Unmanned Traffic Management (UTM) Systems (CORUS). Available online: https://www.sesarju.eu/projects/corus (accessed on 31 May 2022).
- Tomaszewski, L.; Kołakowski, R.; Dybiec, P.; Kukliński, S. Mobile Networks’ Support for Large-Scale UAV Services. Energies 2022, 15, 4974. [Google Scholar] [CrossRef]
- Viana, J.; Cercas, F.; Correia, A.; Dinis, R.; Sebastião, P. MIMO Relaying UAVs Operating in Public Safety Scenarios. Drones 2021, 5, 32. [Google Scholar] [CrossRef]
- Bekkouche, O.; Samdanis, K.; Bagaa, M.; Taleb, T. A Service-Based Architecture for Enabling UAV Enhanced Network Services. IEEE Netw. 2020, 34, 328–335. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Shvetsov, A.V.; Kumar, S.; Shvetsova, S.V.; Alhartomi, M.A.; Hawbani, A.; Rajput, N.S.; Srivastava, S.; Saif, A.; Nyangaresi, V.O. UAV Computing-Assisted Search and Rescue Mission Framework for Disaster and Harsh Environment Mitigation. Drones 2022, 6, 154. [Google Scholar] [CrossRef]
- Cheng, N.; Xu, W.; Shi, W.; Zhou, Y.; Lu, N.; Zhou, H.; Shen, X. Air-ground integrated mobile edge networks: Architecture, challenges, and opportunities. IEEE Commun. Mag. 2018, 56, 26–32. [Google Scholar] [CrossRef] [Green Version]
- Alsamhi, S.H.; Shvetsov, A.V.; Kumar, S.; Hassan, J.; Alhartomi, M.A.; Shvetsova, S.V.; Sahal, R.; Hawbani, A. Computing in the Sky: A Survey on Intelligent Ubiquitous Computing for UAV-Assisted 6G Networks and Industry 4.0/5.0. Drones 2022, 6, 177. [Google Scholar] [CrossRef]
- Yazid, Y.; Ez-Zazi, I.; Guerrero-González, A.; El Oualkadi, A.; Arioua, M. UAV-Enabled Mobile Edge-Computing for IoT Based on AI: A Comprehensive Review. Drones 2021, 5, 148. [Google Scholar] [CrossRef]
- Dicandia, F.A.; Fonseca, N.; Bacco, M.; Mugnaini, S.; Genovesi, S. Space-Air-Ground Integrated 6G Wireless Communication Networks: A Review of Antenna Technologies and Application Scenarios. Sensors 2022, 22, 3136. [Google Scholar] [CrossRef]
- Grasso, C.; Schembra, G. A fleet of MEC UAVs to extend a 5G network slice for video monitoring with low-latency constraints. J. Sens. Actuator Netw. 2019, 8, 3. [Google Scholar] [CrossRef] [Green Version]
- Wheeb, A.H.; Nordin, R.; Samah, A.A.; Alsharif, M.H.; Khan, M.A. Topology-Based Routing Protocols and Mobility Models for Flying Ad Hoc Networks: A Contemporary Review and Future Research Directions. Drones 2022, 6, 9. [Google Scholar] [CrossRef]
- Siddiqui, A.B.; Aqeel, I.; Alkhayyat, A.; Javed, U.; Kaleem, Z. Prioritized User Association for Sum-Rate Maximization in UAV-Assisted Emergency Communication: A Reinforcement Learning Approach. Drones 2022, 6, 45. [Google Scholar] [CrossRef]
- Chen, X.; Wu, C.; Chen, T.; Liu, Z.; Zhang, H.; Bennis, M.; Liu, H.; Ji, Y. Information Freshness-Aware Task Offloading in Air-Ground Integrated Edge Computing Systems. IEEE J. Sel. Areas Commun. 2022, 40, 243–258. [Google Scholar] [CrossRef]
- Starlink. Available online: https://www.starlink.com/satellites (accessed on 1 June 2022).
- Wang, Z.; Goudarzi, M.; Aryal, J.; Buyya, R. Container Orchestration in Edge and Fog Computing Environments for Real-Time IoT Applications. arXiv 2022, arXiv:2203.05161. [Google Scholar]
- Satyanarayanan, M.; Bahl, P.; Caceres, R.; Davies, N. The case for vm-based cloudlets in mobile computing. IEEE Pervasive Comput. 2009, 8, 14–23. [Google Scholar] [CrossRef]
- ETSI GR NFV-MAN 001; Network Functions Virtualisation (NFV); Management and Orchestration; Report on Management and Orchestration Framework. ETSI: Sophia Antipolis, France, 2021.
- ETSI GS NFV-IFA 040; Network Functions Virtualisation (NFV) Release 4; Management and Orchestration; Requirements for Service Interfaces and Object Model for OS Container Management and Orchestration Specification. ETSI: Sophia Antipolis, France, 2020.
- 3GPP TS 28.533; Management and Orchestration; Architecture Framework (Release 15). ETSI: Sophia Antipolis, France, 2018.
- Martins, J.; Ahmed, M.; Raiciu, C.; Olteanu, V.; Honda, M.; Bifulco, R.; Huici, F. ClickOS and the Art of Network Function Virtualization. In Proceedings of the 11th USENIX Conference on Networked Systems Design and Implementation, Seattle, WA, USA, 2 April 2014. [Google Scholar]
- OSGI Alliance, OSGI Specifications. Available online: https://docs.osgi.org/specification/ (accessed on 1 June 2022).
- Lange, D.B.; Oshima, M. Seven good reasons for mobile agents. Commun. ACM 1999, 42, 88–89. [Google Scholar] [CrossRef]
- Caini, C.; Cruickshank, H.; Farrell, S.; Marchese, M. Delay-and disruption-tolerant networking (DTN): An alternative solution for future satellite networking applications. Proc. IEEE 2011, 99, 1980–1997. [Google Scholar] [CrossRef]
- Kuklinski, S.; Tomaszewski, L. DASMO: A scalable approach to network slices management and orchestration. In Proceedings of the NOMS 2018, Taipei, Taiwan, 9 July 2018. [Google Scholar]
- Costa, B.; Bachiega, J., Jr.; De Carvalho, L.R.; Araujo, A.P.F. Orchestration in Fog Computing: A Comprehensive Survey. ACM Comput. Surv. 2022, 55, 2. [Google Scholar] [CrossRef]
- Velasquez, K.; Abreu, D.P.; Assis, M.R.M.; Senna, C.; Aranha, D.F.; Bittencourt, L.F.; Laranjeiro, N.; Curado, M.; Vieira, M.; Monteiro, E.; et al. Fog orchestration for the Internet of Everything: State-of-the-art and research challenges. J. Internet Serv. Appl. 2018, 9, 14. [Google Scholar] [CrossRef] [Green Version]
- Group OCAW. OpenFog Reference Architecture for Fog Computing; Technical Report; OpenFog Consortium: Freemont, CA, USA, 2017. [Google Scholar]
- Guerrero, C.; Lera, I.; Juiz, C. Evaluation and efficiency comparison of evolutionary algorithms for service placement optimization in fog architectures. Future Gener. Comput. Syst. 2019, 97, 131–144. [Google Scholar] [CrossRef]
- Skarlat, O.; Nardelli, M.; Schulte, S.; Borkowski, M.; Leitner, P. Optimized IoT service placement in the fog. SOCA 2017, 11, 427–443. [Google Scholar] [CrossRef]
- Salaht, F.A.; Desprez, F.; Lebre, A.; Prud’homme, C.; Abderrahim, M. Service Placement in Fog Computing Using Constraint Programming. In Proceedings of the 2019 IEEE International Conference on Services Computing (SCC), Milan, Italy, 8–13 July 2019; pp. 19–27. [Google Scholar] [CrossRef] [Green Version]
- Farah, A.S.; Frédéric, D.; Adrien, L. An Overview of Service Placement Problem in Fog and Edge Computing. ACM Comput. Surv. 2020, 53, 1–35. [Google Scholar] [CrossRef]
- Souza, V.B.; Masip-Bruin, X.; Marín-Tordera, E.; Sànchez-López, S.; Garcia, J.; Ren, G.J.; Jukan, A.; Ferrer, A.J. Towards a proper service placement in combined Fog-to-Cloud (F2C) architectures. Future Gener. Comput. Syst. 2018, 87, 1–15. [Google Scholar] [CrossRef]
- Skarlat, O.; Karagiannis, V.; Rausch, T.; Bachmann, K.; Schulte, S. A Framework for Optimization, Service Placement, and Runtime Operation in the Fog. In Proceedings of the 2018 IEEE/ACM 11th International Conference on Utility and Cloud Computing (UCC), Zurich, Switzerland, 17–20 December 2018; pp. 164–173. [Google Scholar] [CrossRef]


| System | TETRA | LTE-MC |
|---|---|---|
| Spectral efficiency | Low | High |
| Push-to-Talk | Yes | Yes |
| Push-to-Video | No | Yes |
| Data Transmission capabilities | ∼20–150 Kbps | ∼1–100 Mbps |
| Direct Mode of operations | Yes | Yes |
| Group communication | Yes | Yes |
| Dedicated terminals | Yes | Yes |
| UAV Type | Weight [kg] | Altitude [feet ASL] | Radius [km] | Endurance [h] |
|---|---|---|---|---|
| Micro | 0.25–2 | <200 | <5 | <1 |
| Mini | 2–20 | <3000 | <25 | 1–2 |
| Small | 20–150 | <5000 | <50 | 1–5 |
| Tactical | 150–600 | <10,000 | 100–300 | 4–15 |
| MALE | >600 | <45,000 | >500 | >24 |
| HALE | >600 | <60,000 | global | >24 |
| Multi-Rotor | Fixed Wing | |
|---|---|---|
| Advantages | greater maneuverability lower price more compact and portable easy to use higher payload capacity ability to hover small landing/takeoff zone | longer flight autonomy larger areas covered in less time better control of flight parameters higher control of image quality better aerodynamic performance minor influence of the environment higher flight safety |
| Disadvantages | shorter range less stable in the wind | less compact less portable higher price challenging to fly larger takeoff (landing site needed) |
| Flight Mechanism | Multi-Rotor | Fixed-Wing |
|---|---|---|
| Mass (kg) | 0.01–100 | 0.1–400,000 |
| Payload (kg) | 0–50 | 0–1000 |
| Ceiling altitude (km) | 4 | 0.1–30 |
| Endurance (min) | 6–180 | 60–3000 |
| Range (km) | 0.05–200 | 3–35 |
| Energy source | battery | fuel or battery |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kukliński, S.; Szczypiorski, K.; Chemouil, P. UAV Support for Mission Critical Services. Energies 2022, 15, 5681. https://doi.org/10.3390/en15155681
Kukliński S, Szczypiorski K, Chemouil P. UAV Support for Mission Critical Services. Energies. 2022; 15(15):5681. https://doi.org/10.3390/en15155681
Chicago/Turabian StyleKukliński, Sławomir, Krzysztof Szczypiorski, and Prosper Chemouil. 2022. "UAV Support for Mission Critical Services" Energies 15, no. 15: 5681. https://doi.org/10.3390/en15155681
APA StyleKukliński, S., Szczypiorski, K., & Chemouil, P. (2022). UAV Support for Mission Critical Services. Energies, 15(15), 5681. https://doi.org/10.3390/en15155681








