1. Introduction
The development of global supply chains and the increasing volatility of the environment require companies to adjust their standards in the area of the applicable logistics service. If they want to maintain the continuity of supplies in their material flows, then apart from cost optimisation, building the system’s resilience to disruptions becomes an important aspect. For this reason, the study of resilience in functioning chains is an important research topic today, which is interested not only in the scientific community and industry. The importance of this area issues may be confirmed, e.g., by the Supply Chain Resilience Reports, which have been published since 2009 (see:
www.thebci.org, accessed on 15 May 2021). These reports inform about the level, range and cost of disruptions that organisations face and demonstrate how a disturbance in one organisation can spread out over the entire supply chain [
1]. At the same time, it observed that many companies, such as Boeing, Cisco, Coca-Cola and Proctor and Gamble, are working with organisations across their supply chains to create resilience [
2]. It is necessary to identify them and assess the related risks to prepare the process for the occurrence and effects of potential disruption. For this reason, risk management in the supply chain becomes the most crucial element in building the resilience of these systems.
The resilience of supply chains is critical in supplying selected products for the army, which carries out specific military missions in a foreign territory. The role of timely and complete deliveries, in this case, has a different meaning with the functioning of civil supply chains. In the case of deliveries carried out on the industrial or consumer market, the lack of high resilience to disruptions will affect the level of logistics services offered. The result of failure to deliver products by the adopted standards will be costs related to contractual penalties or fees of lost sales. In the case of military supply chains, the lack of timely and complete delivery of products, such as fuel or weapons, may endanger the lives and health of the mission participants. For this reason, the construction of delivery resilience is of particular importance in military procurement processes.
As presented in the second point of the article, there are numerous publications in the literature on the safety and resilience of supply chains and risk management for building this resilience. However, there are no publications on risk assessment in military supply chains responsible for supplying the army with strategic products necessary to implement the mission. Searching the databases of journals according to the key “army + resilience + supply chain”, “resilience + military + supply chain” returns only one publication. In contrast, the search according to the words “risk + military + supply chain”, “army + risk + supply” chain “returns only individual publications related to this topic. Therefore, it concluded that the scope of the research presented in this article fills the identified research gap, what is the lack of publications on risk assessment for the operation of chains supplying military missions.
The article aims to present the method of tactical risk assessment to build the resilience of military fuel supply chains for the military peacekeeping operation. The novelty of the proposed approach is the identification of scenarios of adverse events occurring in the supply of fuel for military operations and the assessment of the risk of their occurrence at the level of tactical management. The risk analysis model was built based on the fuzzy inference system, and the fuzzy rules were created based on the knowledge of NATO experts. The proposed approach was verified on the example of the ISAF (International Security Assistance Force) mission in Afghanistan. Following this, the main contribution of this study is that:
Identify the gap in research on tactical risk assessment in supply chains to supply military operations and use the assessment results to build supply chain resilience.
Identification of adverse events at the tactical level occurring in supply chains that deliver products for military missions. The identified scenarios include adverse events specific to fuel supply chains and the specificity of servicing military missions.
Development of a tactical risk assessment method for fuel supply chains based on a fuzzy inference system. Defining and measuring the probability and consequences of the assessed scenarios based on a survey of experienced NATO experts.
Verification of the proposed approach on the example of a selected military mission.
Therefore, apart from the Introduction section, the article structure includes reviewing the literature in supply chain risk management and resilience supply chain in
Section 2. Next, a proposed model of tactical risk assessment method for military supply chains. In
Section 4, the research area and characteristics of military fuel supply chains are characterised.
Section 5 presents results and their interpretation.
Section 6 discusses the applicability of the proposed method and its limitations. Finally,
Section 7 provides conclusions and suggestions for the authors’ future research works.
2. Literature Review
The results presented in the article require the presentation of basic research concepts, which are considered when preparing the research methodology. For this reason, based on the literature review, there were the base characteristics of the analysed research areas designed.
2.1. Supply Chain Resilience
We are currently observing an intensive development of the concept of resilience. It is the subject of analysis in many research areas, such as engineering, social sciences and economics [
3]. Resilience is defined in the literature as returning to its original operational state or moving to a more desirable state after being [
2]. This concept is also developed in assessing the functioning of logistics systems, including supply chain management. The most cited approach to the resilience of delivery systems is the definition of Christopher & Peck [
4], who defined it as the ability of a supply chain to return to normal operating performance, within an acceptable period, after being disturbed. Noteworthy is also the approach taken by Ponomarov and Holcomb [
5]. They have defined resilience as the adaptive capability of the supply chain to prepare for unexpected events, respond to disruptions, and recover from them by maintaining continuity of operations at the desired level of connectedness and control over structure and function. It should be clarified that by the term “supply chain disruption”, we shall understand any interruption in material flow [
6]. These disruptions generate a certain level of turbulence [
7] and uncertainty in the supply chain [
8], which together hurt the current operations [
9].
The primary sources of disruption include [
10]:
Terrorist incidents;
Accidents, like the fire of supplier’s factory;
Operational difficulties, connected, e.g., with variability in supply, demand uncertainties, price variability;
Natural disasters, such as earthquakes, cyclones, epidemics.
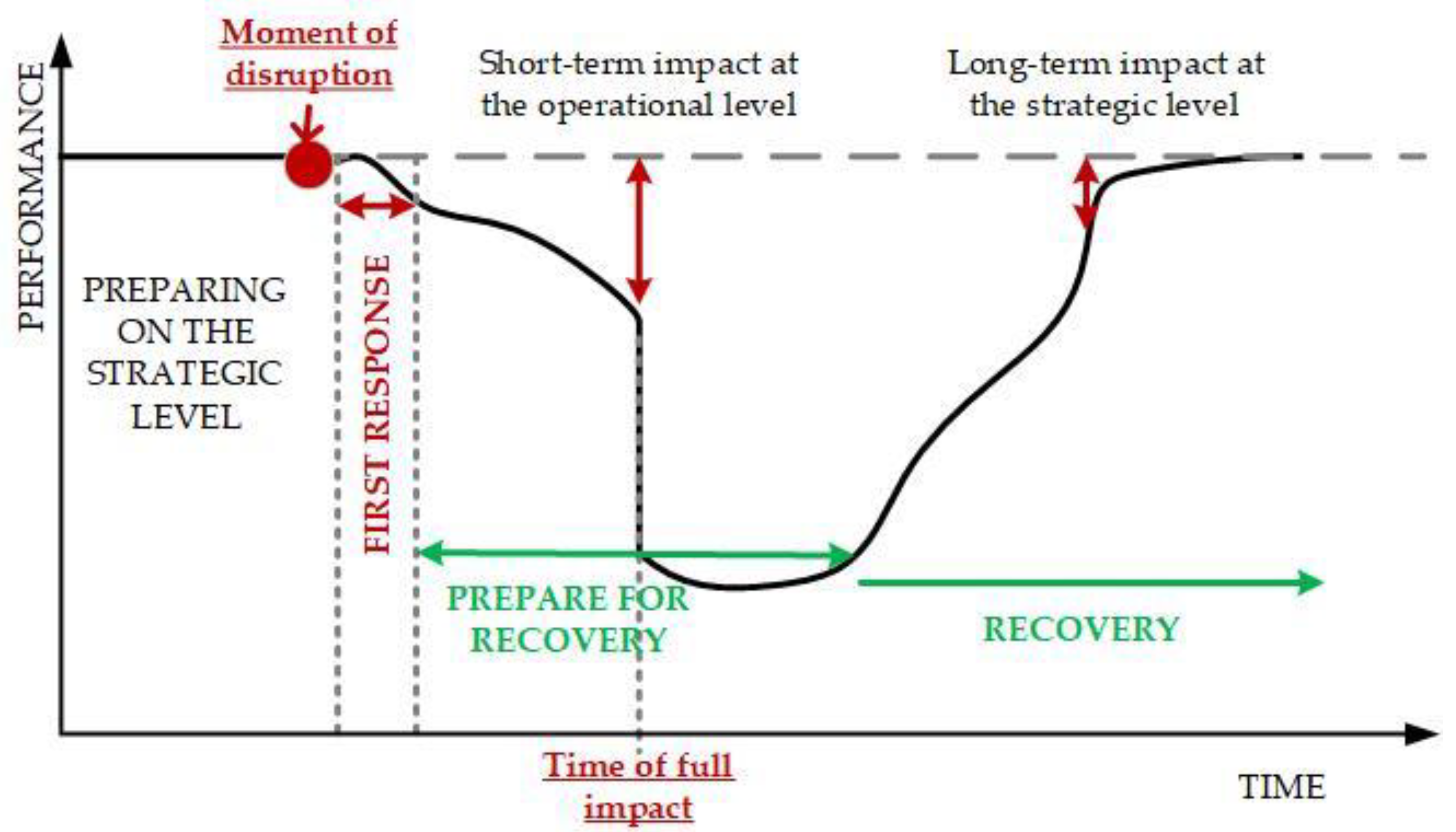
In their research, Sheffi and Rice emphasise that the nature of the disruption and the dynamics of the company’s response can be characterised by the eight phases [
11]: (1) Preparation, (2) disruptive event, (3) first response, (4) initial impact, (5) full impact, (6) recovery preparations, (7) recovery, (8) long-term impact. The highlighted phases are shown in
Figure 1.
In line with the approach presented by Sheffi and Rice [
11], the greater the system’s resilience, the shorter the recovery time and the lower the impact on the implementation of logistics operations. Therefore, increasing the resilience of supply chains should be seen as a positive phenomenon [
12]. For this reason, many authors focus their research on providing guidelines for strengthening the resilience of enterprises in supply chains (e.g., [
13,
14].
Numerous publications from the last decade also confirm the importance of building and assessing the resilience of supply chains. The purpose is to review the literature in each area. The most important of them include [
15,
16,
17]. However, published reviews of the literature mainly cover industrial supply chains. Meanwhile, the resilience of supply chains is of particular importance in logistics systems supplying military operations. The importance attributed to resistance to these chains is unique, as the lack of timely and complete deliveries of specific product groups determines the success of the military operation and the life and health of its participants.
The conducted review of publications available in civilian journal databases resulted in one publication on the resistance of military supply chains. This research proposes a “Parallel Model” as a new Military Supply Chain structure and simulates its performance in wartime resilience [
18]. Meanwhile, the subject of military supply chains can be considered from the perspective of developing the concept of building the resilience of systems supporting material flows, considering the specificity of this sector. Therefore, this research area can be considered as a research gap.
2.2. Supply Chain Risk Management
An essential element of building the supply chain’s resilience is implementing a risk assessment and management system. Resilience must be strengthened by tools and procedures that will allow enterprises to return to the standard or desired logistics processes in the shortest possible time. The scope of applied solutions is developed as part of risk management and corresponds to identifying and analysing adverse events.
We can find various definitions of risk in the literature. Noteworthy is the literature review prepared by Aven [
19]. Due to the diversity of approaches presented in the literature, it is worth referring to the definition described in the ISO31000: 2018 standard. In line with the proposed method, risk is defined as the effect of uncertainty on objectives [
20]. However, according to the definition adopted in this way, risk can be perceived in both a negative and a positive aspect. Thanks to this, it is possible to identify two main trends in risk analysis [
21]:
In the conducted research, we adopted approach 1, as it is consistent with the guidelines described in the military documentation and corresponds to the specificity of military operations. It is also a dominant approach in many scientific studies. As the analyses presented in [
22] show, most articles on risk management focus on measuring the effectiveness of various risk management systems, examining only the effectiveness of risk management in the area of protection against adverse events.
Risk is a measurable phenomenon [
23], and therefore, it can be described by quantitative parameters. It is most often expressed as the product of the probability of its occurrence and its effects. However, some assessment methods also add other risk assessment parameters (e.g., FMEA analysis).
There are three basic risk management strategies [
24,
25]: (1) Risk communication strategy; (2) risk prevention/reduction strategy; (3) discursive strategy. However, as Aven [
19] notes, the appropriate approach to risk management is a mixture of all three strategies in most cases. The structure of the risk management process is described in detail in ISO 31000: 2018 [
20]. It assumes three main stages of the procedure: (1) Establishing the context, (2) risk assessment (which consists of three steps: Risk identification, analysis and evaluation), (3) risk management. These three stages of the procedure are continuously accompanied by two supporting processes: (1) Communication and consultation and (2) monitoring and review. The method prepared by us will consider the analytical approach recommended by the ISO standard.
Risk management is a fundamental issue in the operation of complex systems, such as supply chains. For this reason, the Supply Chain Risk Management (SCRM) concept was developed for their management. However, as Sodhi et al. [
26] note, currently, there is no single standard definition for determining the concept of supply chain risk or Supply Chain Risk Management. In the prepared literature review, Ho et al. [
27] presented the definitions of various authors presented over the last 20 years. According to supply chain risk, they prepared an illustration of the likelihood and impact of unexpected macro and/or micro-level events or conditions that adversely influence any part of a supply chain leading to operational, tactical, or strategic level failures or irregularities [
27].
Based on the literature review, most authors classify risks in supply chains and divide them into internal and external threats. Examples of classifications proposed by selected authors are shoved in
Table 1.
Ho et al. distinguished seven areas of assessment under SCRM based on their research. These are [
27]: (1) Macro risk assessment; (2) demand risk assessment; (3) manufacturing risk assessment; (4) supply risk assessment; (5) financial risk assessment; (6) information risk assessment; (7) general risk assessment. The following events can be included in the most frequently assessed scenarios [
31,
32]:
Warehousing and production interruption;
Low integration between intermediate and final-product suppliers;
Lack of information transparency;
Damages in transport;
No transport solution alternatives;
Unplanned machine stoppages;
Serious forecasting errors;
Poor quality of raw material.
These are areas dedicated to civil supply chains, but they were the starting point for our research. Of course, they supplemented with the specifics of military delivery processes.
Both quantitative, qualitative and hybrid methods are used to assess the risk [
33]. Qualitative techniques are primarily used for risk identification and risk analysis steps [
34]. Quantitative methods are based on analytical and simulation models and are used in the risk assessment stage. Research on applying analytical optimisation models for analysing supply disruptions and selecting the optimal mitigation strategies is presented, among other things, in [
35,
36]. Researchers are currently watching an increasing trend in using simulation techniques for supply chain design, management and risk analysis, due to its modelling flexibility [
34].
Additionally, simulation can be an effective tool for visualising supply chain risks. Hence, its increasingly widespread use. Simulation models were used for risk assessment in the following publications [
37,
38,
39]. Hybrid models combine quantitative and qualitative techniques. They are used in situations with high uncertainty or in the absence of complete quantitative data on the assessed phenomenon/event [
34]. The most common tools used for the hybrid modelling of risks in supply chains are: AHP [
40,
41], fuzzy logic [
34,
42] and cluster analysis [
43]. In the research procedure proposed by us, the concept of fuzzy logic was applied. Its use is justified in the proposed risk assessment method for military supply chains, due to the lack of access to reliable historical data.
2.3. Fuzzy Theory in Risk Assessment
In the proposed assessment model, we used fuzzy set theory to estimate the probability measures and the occurrence of each of the analysed scenarios. The fuzzy set theory was developed in 1965 by Zadeh [
44], who dedicated it to support the analysis of challenging and complex problems. According to [
45], the researcher should use this method in a situation where vague phenomenon (vague relations in modelling the issues), information vagueness and heuristic algorithms. Then, one may use linguistic variables when assessing qualitatively or give intervals instead of exact crisp values in evaluating the data quantitatively [
46].
Fuzzy logic is implemented through a “fuzzy inference system” (FIS) [
47]. A FIS is a nonlinear procedure that derives its output based on fuzzy reasoning and a set of IF-THEN rules. The strength of FIS relies on their twofold identity [
48]: (1) It can handle linguistic concepts; (2) it is a universal approximator able to perform nonlinear mappings between inputs and outputs. Novak [
49] presented a procedure involving three basic steps:
Define and measure the likelihood of occurrence and severity of the risk in verbal opinions and transform them into fuzzy numbers accordingly.
Define the fuzzy inference to connect input and output parameters using fuzzy IF-THEN rules and “fuzzy arithmetic operators”.
Defuzzification of the fuzzy outcomes into numerical values using appropriate quantifiers.
It should also be noted that, based on literature review in the area of fuzzy logic implementation, Guillaume [
48] distinguished two kinds of FIS: (1) Fuzzy expert systems or fuzzy controllers—fuzzy rules built on expert knowledge. This kind of FIS uses fuzzy logic to model natural language; and (2) Automatic learning from data—neural networks have become the most popular tool using a numerical performance index, typically based on the mean square error. Their accuracy distinguishes these kinds of development, and their main drawback is their “black-box” approach. We used the first type of FIS in the proposed model because fuzzy expert systems provide an easy way to deal with situations involving fuzzy sets, both linear and uncertain properties [
50]. The results are based on expert judgment, quality assessment, causal relationships and impact analysis in these proceedings. [
51]. At the same time, Fakhravar [
52] notes that any fuzzy expert system should have three essential components: Fuzzy membership function, fuzzy rules and fuzzy inference mechanism. We used the Mamdani inference because it is an improved, more general method and well-accepted in the fuzzy expert system [
53].
Fuzzy methods are currently widely used in various research and models supporting decision-making processes. In the literature, its implementations can be found in decision support methods, such as AHP fuzzy [
54], TOPSIS fuzzy [
55] and many others. Fuzzy set theory is also prevalent in risk assessment models. Its implementations concerning the estimation of the size of the occurring risks appear, among other things, in the area of cybersecurity [
46]; gas and dust explosion risk [
56], but also supply chain risk assessment [
37,
42].
The fuzzy set theory has gained popularity as it provides the opportunity to use numerical and qualitative approaches to improve decision analysis in uncertainty. However, as Fakhravar [
52] notes, the coding of linguistic expression, its quantitative aggregation process, choice of relationships for data, and computational methods are identified as complex problems. Greavery et al. [
57] underline in their results that the validation technique of fuzzy-based decision analysis is also neglected in studies. However, this research stage is critical from the perspective of practical implementations of the developed models. Choi and Mahadevan [
58] also note that fuzzy-based risk assessment models do not provide realistic risk assessment. Sometimes, avoiding complex risk makes it impossible for experts to capture all possible risk scenarios when making risk assessment judgments.
3. Fuzzy-Based Risk Assessment Method for Military Supply Chain
The subject of the assessment is the risk of adverse events occurring at the level of tactical supply chain management. Therefore, the authors describe risk by the Kaplan and Garrick approach, which is defined as follows [
59]:
where:
R—risk; {}—must be interpreted as a “set of”;
S—a scenario (undesirable event) description;
P—the probability of a scenario;
C—the measure of consequences or damage caused by a scenario;
N—the number of possible scenarios.
The formulation of the stages of the procedure in the risk assessment method was based on the guidelines defined in ISO 31000: 2018 [
20]. Thanks to this, the proposed approach meets the quality standards indicated for risk management systems in modern organisations. The model also takes into account the assumptions defined in NATO’s internal documentation [
60].
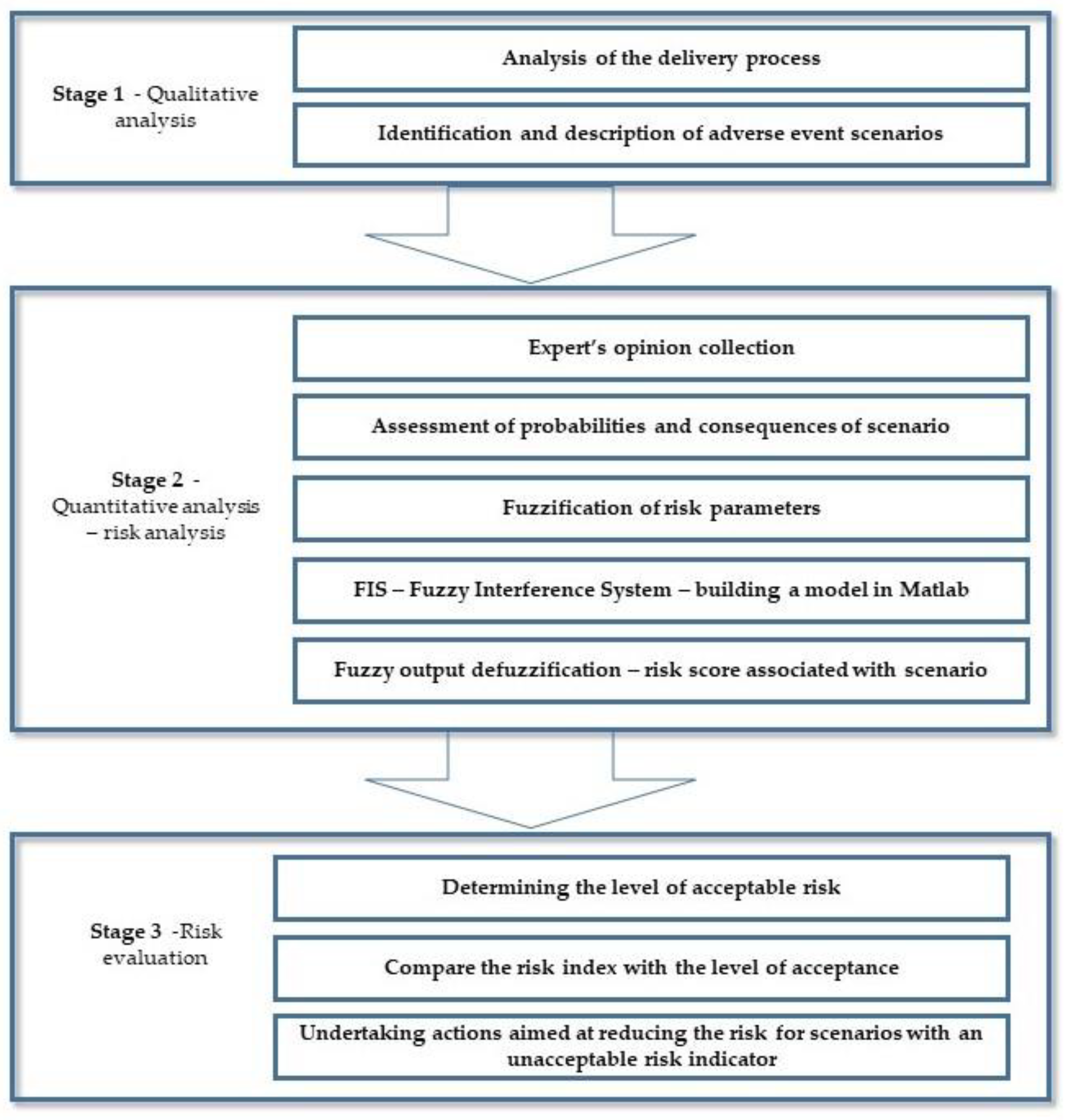
The proposed method of risk assessment is qualitative and quantitative. Following the guidelines of ISO 31000: 2018, it includes three main phases of the analytical procedure related to the identification, analysis, and evaluation of risk in processes. The detailed research procedure is presented in
Figure 2.
The first stage of the proposed method aims to identify the scenarios describing the potential adverse events at the tactical level of securing the continuity of fuel supplies for the mission. According to the guidelines [
61], a hazard can be defined as conditions with the potential of causing injury to personnel, damage to equipment, loss of material, or lessening the ability to perform a task or mission. The most probable hazards are those created by readiness shortcomings in the operational environment. Selected analytical tools described, among others in ISO 31000:2018, were used in the identification process. An important issue at this stage is preparing an analysis considering the process approach used in research on supply chains. It allows for identifying inputs and outputs for individual steps of the process, the relations between separate operations and the required resources (physical and nonphysical assets) needed for their implementation. The process analysis will determine the existing limitations of the logistics system and potential disruptions in the performance of goods flow. Used it, it will be possible to describe the characteristics of conceivable scenarios with the highest frequency of occurrence. The detailed qualitative procedure is presented in
Section 3.1.
The next stage of the procedure includes estimating the probability and effects of each of the analysed scenarios. The frequency of undesirable events occurring during military missions in a foreign territory is characterised by statistical nonrepeatability. In addition, information about them appears only in military reports and is not always the subject of quantitative analyses—rather, cause-effect analyses. The lack of detailed historical data makes it impossible for analysts to estimate the actual probability and the potential effects of the analysed scenarios. For this reason, the described method proposes the estimation of both parameters by selected NATO experts, using the fuzzy logic concept. The analytical procedure is presented in
Section 3.2.
The final step in the proposed method is to evaluate the risk and make decisions about future actions. In this case, the primary purpose of using the analysis results is to ensure the required liquidity of supplies and high fuel availability during the mission. Its lack may determine the level of the mission’s goal achievement and the safety of its participants. Possible directions of activities are presented in
Section 3.3.
3.1. Qualitative Analysis
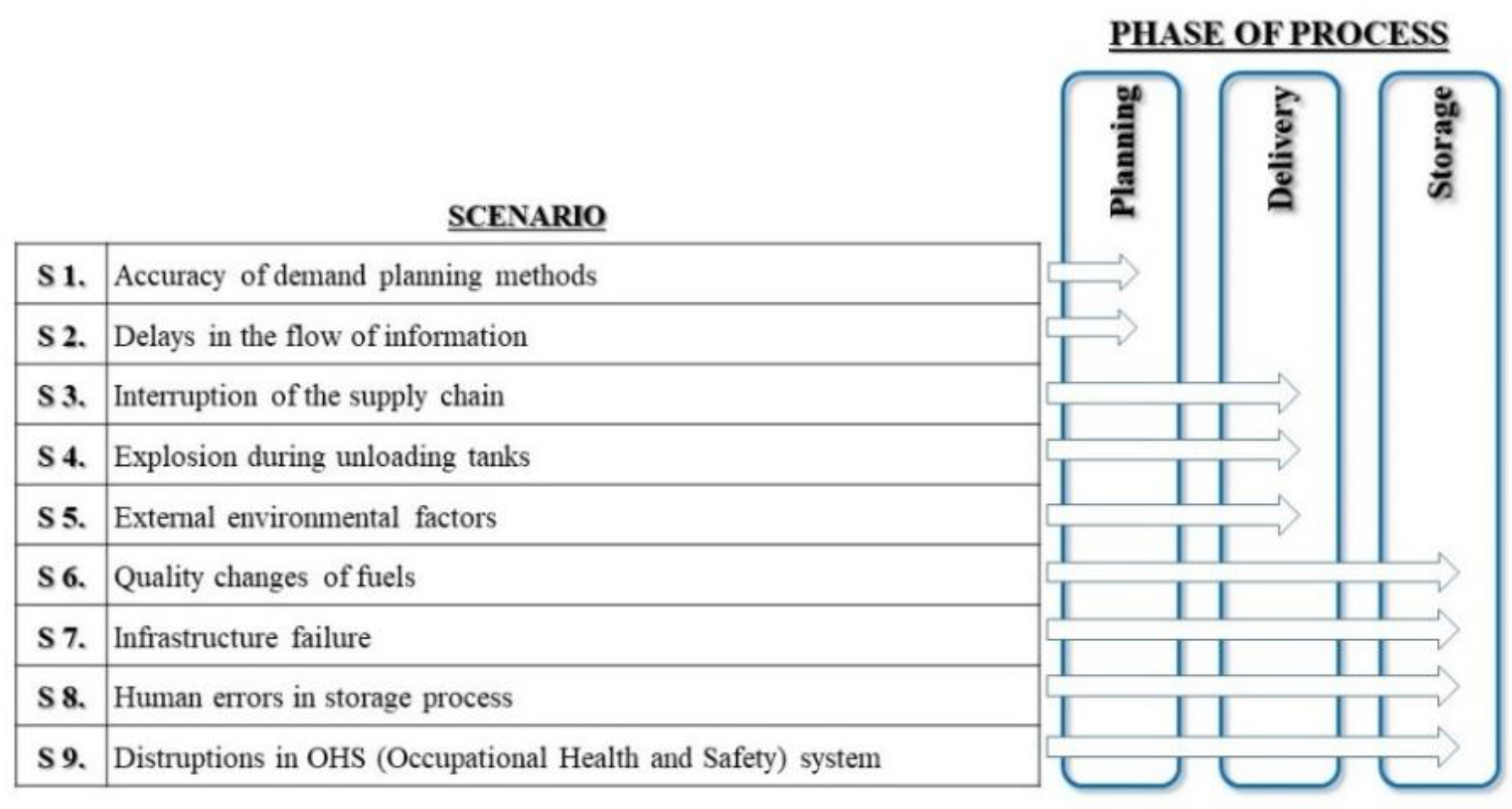
The adverse event scenarios were identified based on the analysis of previous military missions carried out in Afghanistan. First, three basic logistics processes were distinguished within the supply chain supplying military missions with fuel. They are (1) the planning process, (2) the delivery process, and (3) the storage process. The process structure defined in this way has become the starting point for describing the scenarios of undesirable events. The qualitative
what-if technique was used to identify adverse events and the studies conducted among selected participants of previous missions. On this basis, nine scenarios are distinguished, which are described in
Table 2.
According to the adopted process approach, each of the above scenarios is assigned to the appropriate phase of the logistics service of fuel supplies. These relations are presented in
Figure 3.
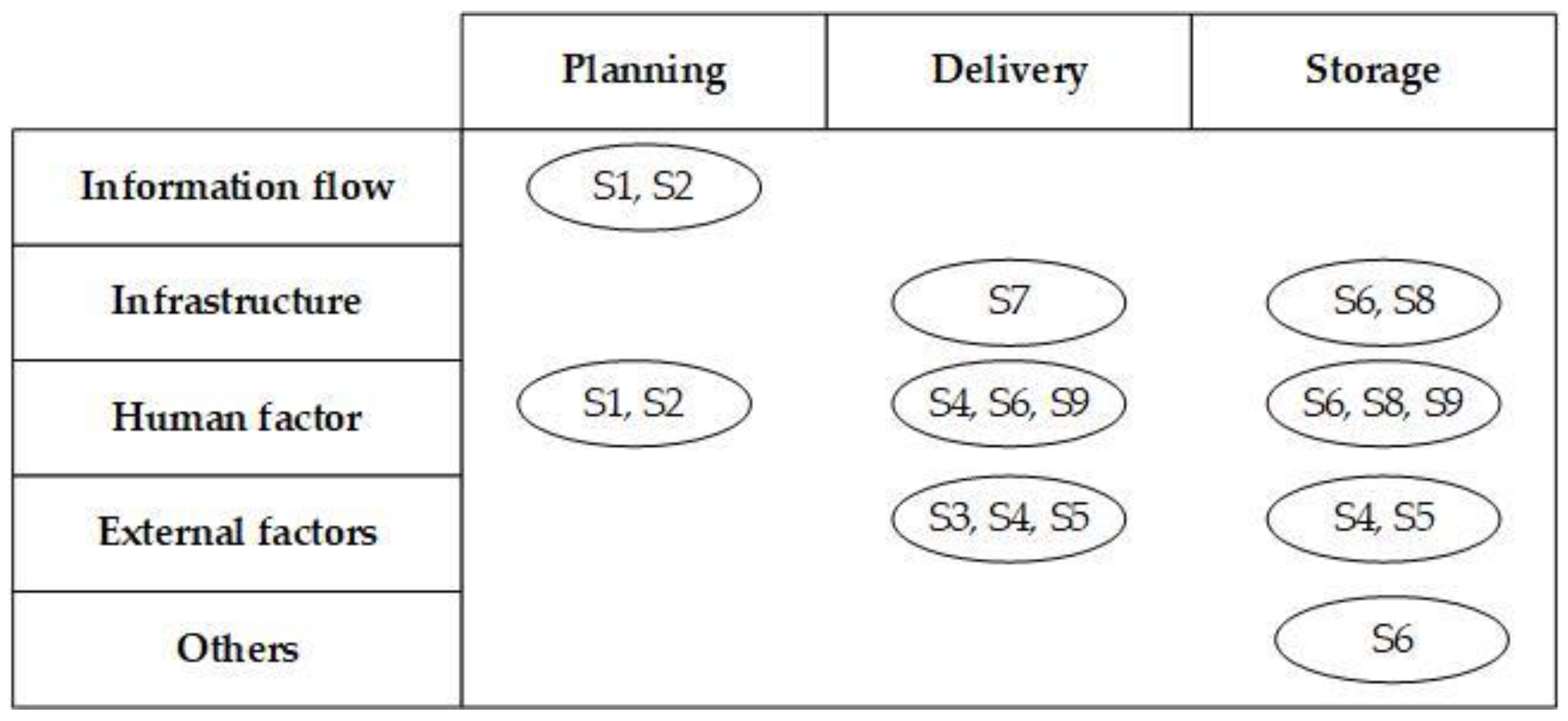
At the same time, it noted that individual scenarios could also be grouped according to the reason for their occurrence. The analysis of the nine described scenarios distinguishes the following sources of hazards: Information flow, infrastructure, human factor, participation of third parties, organisation of the process. On this basis, an additional classification of events can be performed, which is presented in
Figure 4.
Identification of the source of the analysed scenario is crucial for further risk management decisions. The remedial proceedings undertaken may be related to prevention or only to reduce the effects. The choice of the procedure depends on the level of influence (control) over the hazards. The critical task here is to identify those scenarios whose source of hazard is specific only to military missions.
3.2. Qualitative Analysis—Assessment of Risk Score
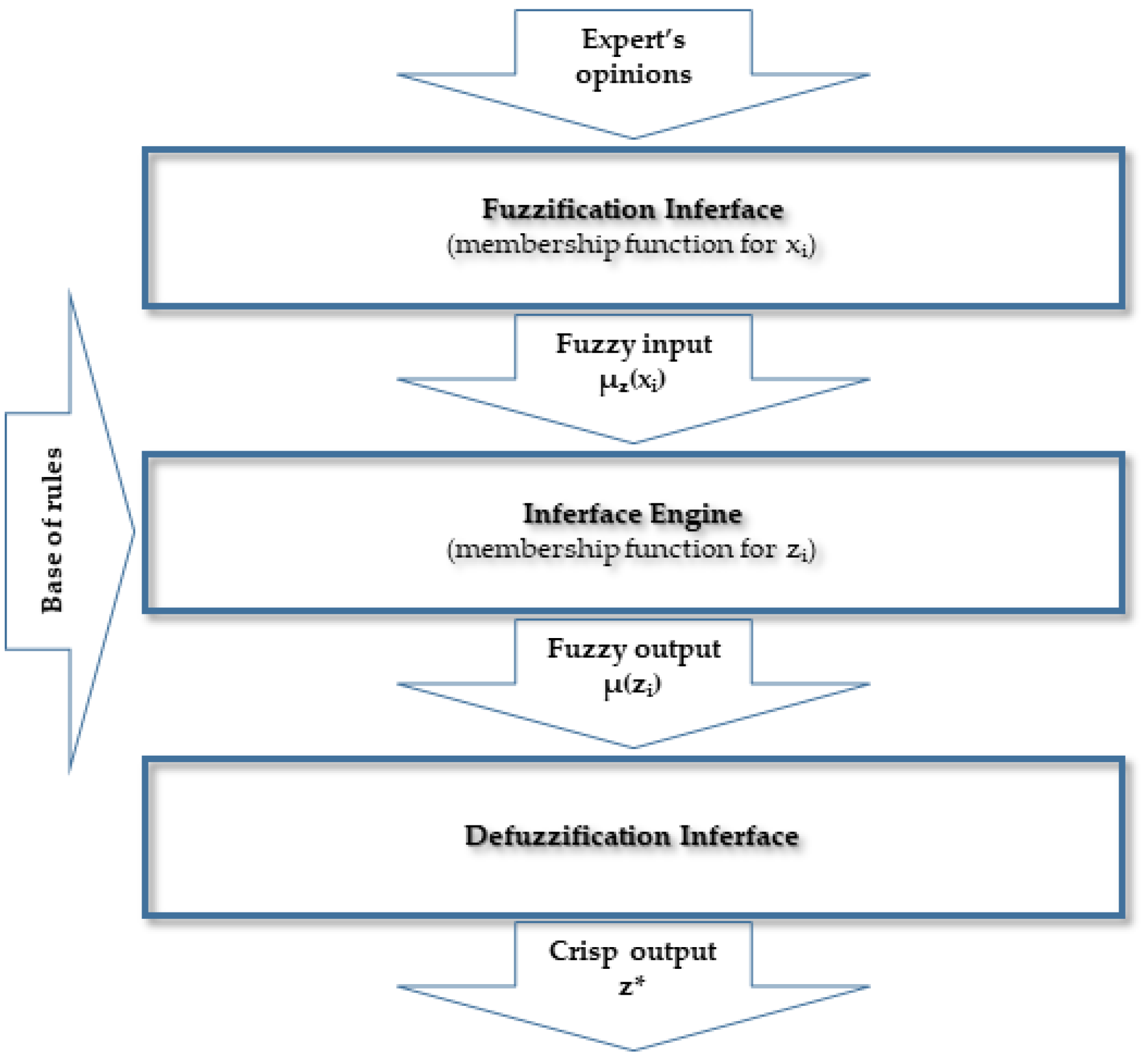
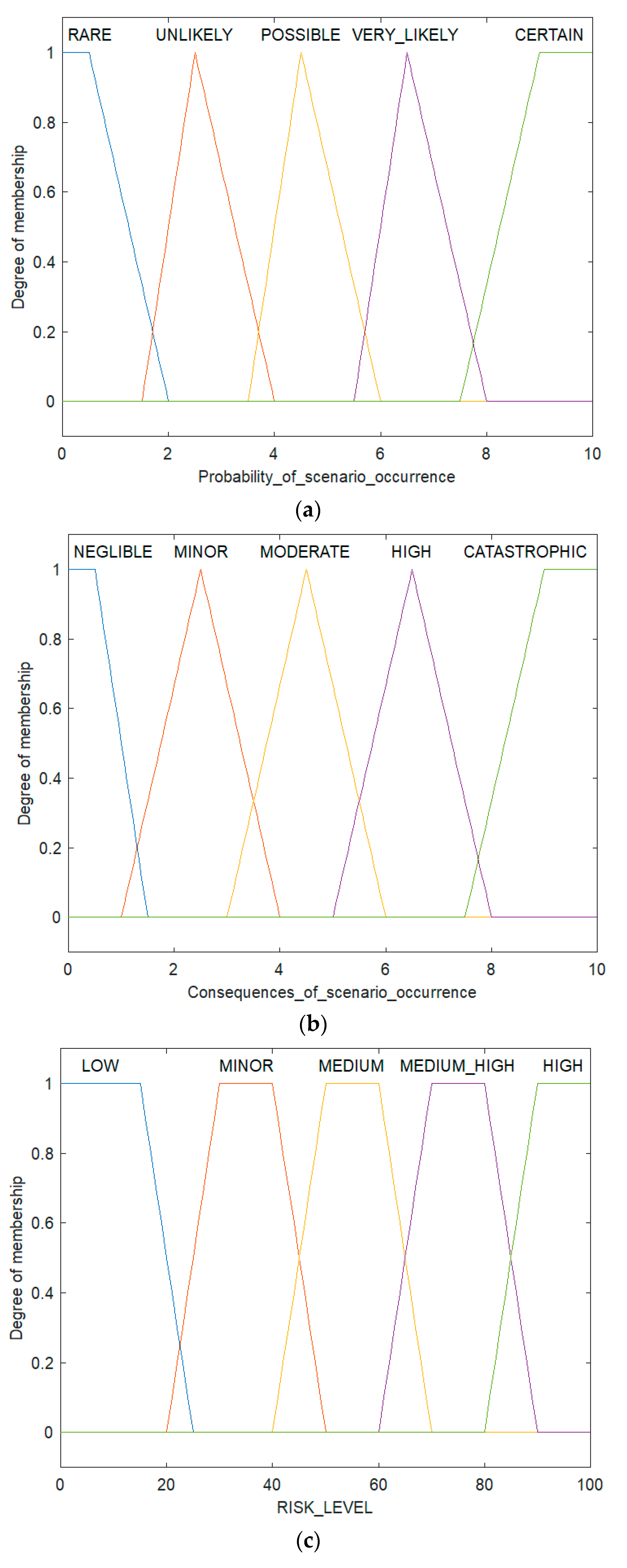
To estimate each scenario’s probability and effects, direct interviews were conducted with a group of NATO experts who were directly involved in the planning, organisation, and supervision of the proper functioning of the fuel supply chains in Afghanistan. Linguistic variables were used to express the opinions of experts on both assessed parameters. Then these variables were modelled using the fuzzy set theory. According to this theory, the risk parameters of each scenario, consequences and the risk level are treated as a fuzzy number (FN) and the associated membership function (MF). Membership functions can take various shapes. Shape selection for some fuzzy set (linguistic attribute/value) is subjective and depends on the problem. The presented risk assessment method proposed using a triangular MF (probability and consequences of scenario) and trapezoidal MF (level of risk).
A triangular FN is presented by a triplet A
z = (a, b, c), and its MF is given by (2):
The MF parameters meaning is straightforward—a and c are the lower and upper bounds of fuzzy number A
z, respectively, and b is the modal value of fuzzy number A
z. Following the up notations, a trapezoidal FN defined as A
z = (a, b, c, d) has its MF given by (3):
The linguistic variables of chosen membership functions are presented in
Table 3 (probability) and
Table 4 (consequences). The output variables for the risk level are given in
Table 5.
To perform aggregation operations to obtain the risk level, it is necessary to use expert opinion. One of the methods [
62] is the use of the arithmetic mean aggregation operator. The aggregation represent operator, defined on triangular FN (a
1, b
1, c
1), (a
2, b
2, c
2) … (a
n, b
n, c
n), where n is a number of experts, delivers the result as (x, y, z) according to the formulae:
The individual stages of this phase are aimed at risk quantification. This process is based on the use of the Mamdani fuzzy model [
63]. The Mamdani fuzzy interference mechanism is based on the method proposed by Zadeh [
44]. According to this rule, the elements of the Mamdani fuzzy model are four modules: Fuzzification, Knowledge base, Fuzzy Interference System and Defuzzification [
64].
Figure 5 shows a diagram of the implemented Mamdani fuzzy model in the defined research area.
From the beginning of
Section 3.2, we know that the fuzzification process is based on triangular FNs. The triangular FN transforms linguistic scales in the 0–1 range by using its MF.
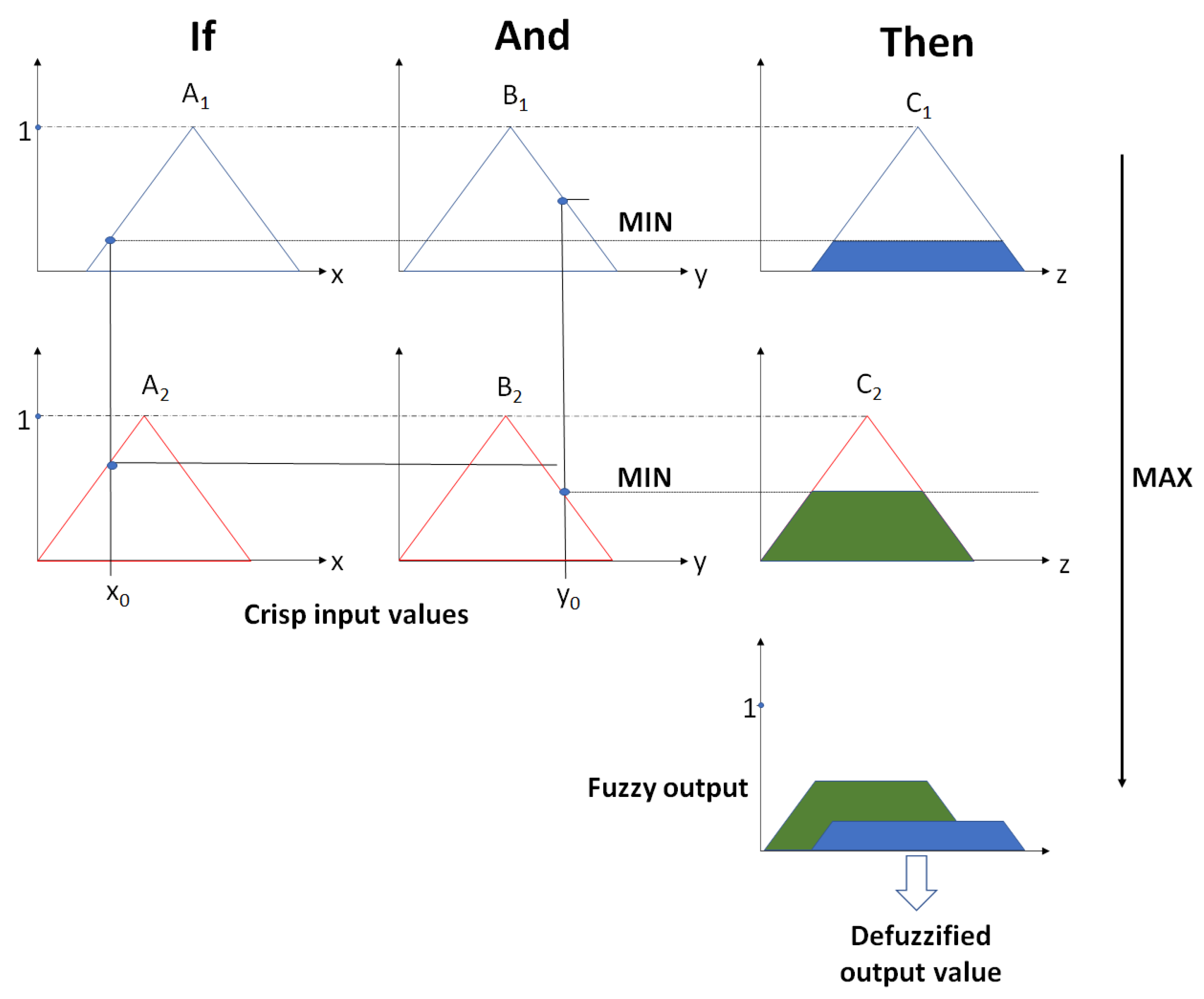
The system’s task is to map the fuzzy inputs and control the outputs using the fuzzy set theory. Due to the use of the Mamdani model, FIS relied on the implementation of the MIN and MAX operators. The MIN operator is used in combination and implication operations. In comparison, MAX is used to fuzzy aggregate results [
65]. The composition of MIN-MAX is shown in
Figure 6.
The last stage of the proposed model is the process of defuzzification. Its purpose is to convert the fuzzy output into a crisp output signal. Thus, the method of defuzzification of the centroid of area, following the research results given, for example, in [
66,
67]. The output value is determined by the Equation [
64]:
where: z*—defuzzified output;
—the aggregated output MF; z—the universe of discourse.
The effect of defuzzification is a clear output value entering the output phase.
3.3. Overall Scenario Risk Level Assessment
The risk evaluation stage is the last step in the proposed tactical risk assessment method, following the ISO 31000: 2018 standard. It is necessary to define the level of acceptance for the estimated risk amounts in the evaluation process. Policymakers can subjectively determine this level, and, as research shows, it may depend on many factors, such as age, gender, character and education [
21]. The values of the estimated risk for individual scenarios are compiled with the adopted level of acceptance, and on this basis, future actions related to risk management are determined. This stage is crucial because of the conducted procedure; priority is given to activities. As a result, the necessary solutions implemented that increase the security of mission implementation and the resistance of the supply chain to adverse events.
A critical issue for the performance of the mission is the implementation of risk reduction measures for scenarios where the current indicator is not acceptable. Actions taken by the mission command should be aimed at reducing risk through:
Limiting the likelihood of the scenario occurrence—taking protective/predictive actions, connected with, e.g., introducing systems/procedures securing external access to the mission’s resources, techniques for monitoring fuel supplies and fuel storage systems, employee training;
Minimising the scenario occurrence effects—building rapid response systems to adverse events (resilience aspects).
For scenarios where the current risk indicator is at the acceptance level, no reduction measures are usually taken. However, this does not exclude the need to constantly monitor its class in terms of changes in the size of any of the parameters. If the increase of one of the parameters causes the risk indicator to exceed the acceptance level, the command should take immediate actions to reduce it.
3.4. Application of the Proposed Approach
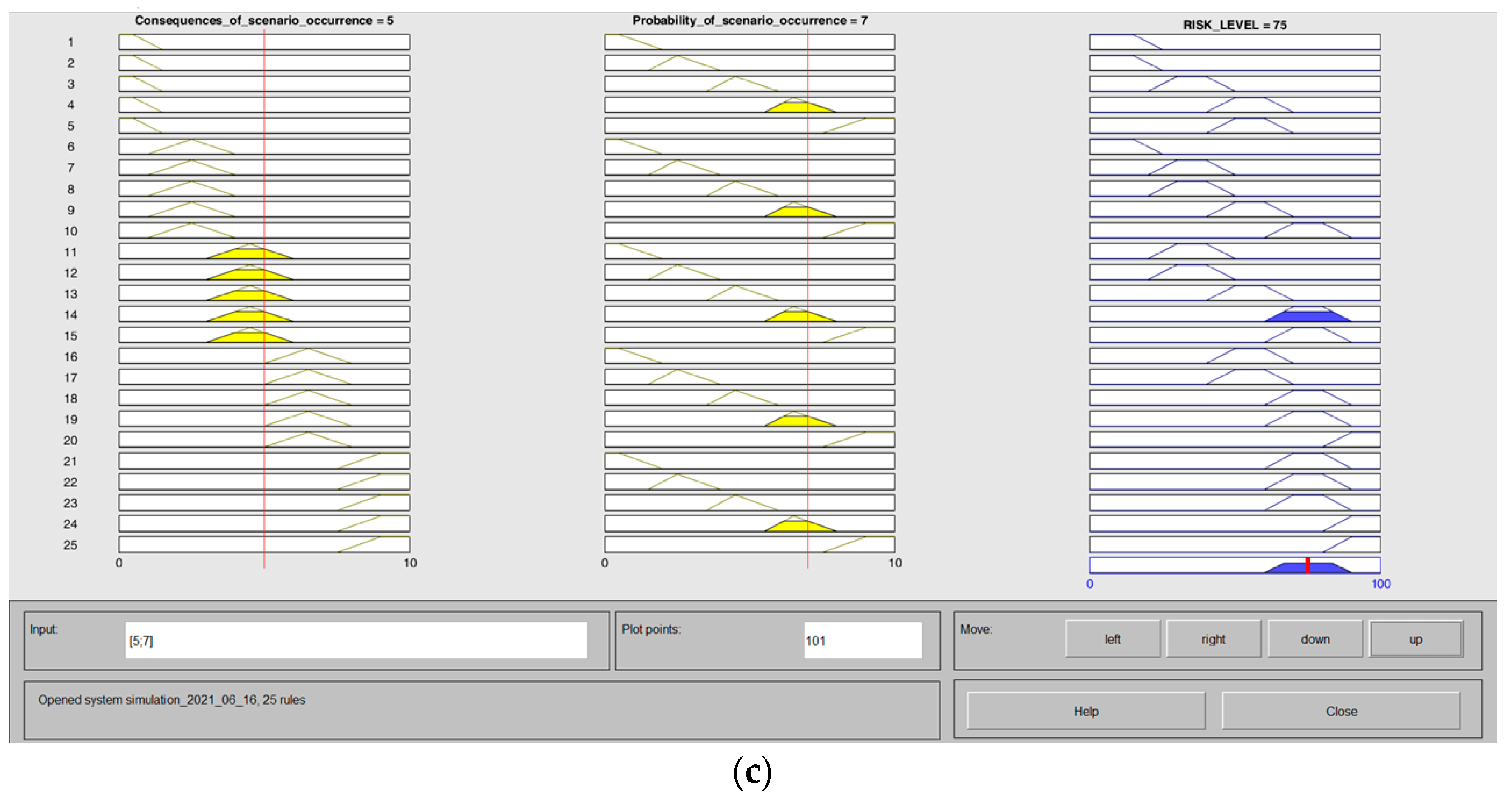
In the first step of building a fuzzy model, the input parameters must be fuzzy. The next step is to transform expert linguistic assessments into appropriate numbers of fuzzy sets. In the constructed Matlab Mamdani model, the input variables are the probability and consequences of selected scenarios, and the output variable is the risk level for the scenario. Membership functions (triangular and trapezoidal) used in the analysed case study to represent the linguistic scales of the input and output parameters are shown in
Figure 7 (according to
Table 2,
Table 3 and
Table 4).
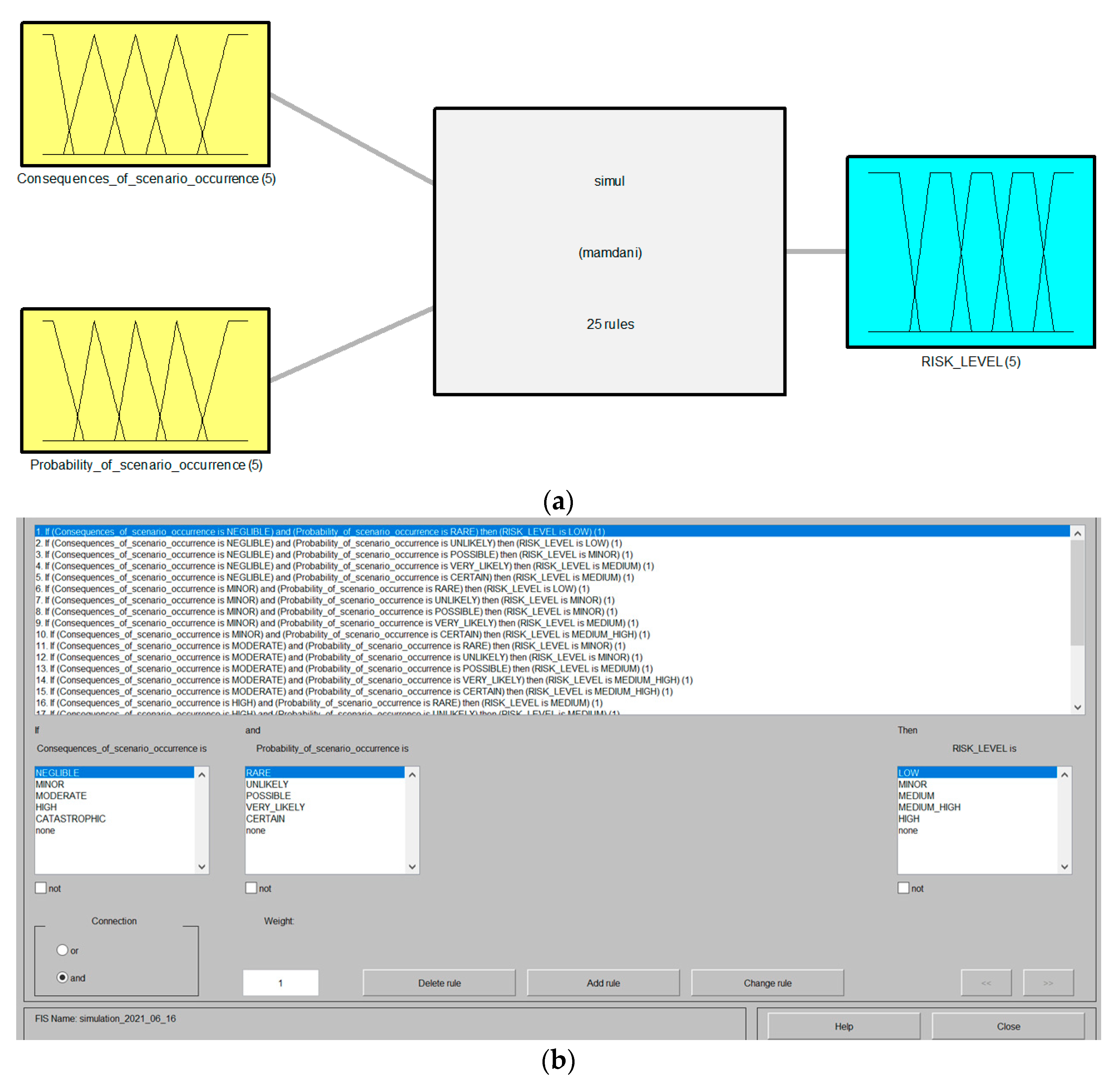
The final phase of building the risk assessment model includes formulating IF-THEN rules to calculate the risk level. According to the expert knowledge in the safe operation of fuel supply chains, 25 rules were proposed, as shown in
Table 6.
The fuzzy inference engine analyses all user-defined fuzzy rules in the rule base, and the results of these rules are interpreted using the Mamdani algorithm (
Figure 8). To obtain the final value of the risk level from the constructed FIS, Equation (3) is used to defuse the fuzzy set.
4. Characteristics of the Research Area
The area of research is related to the functioning of supply chains supplying military missions carried out in a foreign territory. Such chains provide a wide range of essential products necessary for maintaining the army and carrying out assigned tasks—e.g., food, water, medical supplies, fuel, spare parts. Therefore, timely and complete deliveries determine the achievement of the assumed mission objectives and often determine the health and life of soldiers. For this reason, the role of building the resilience of supply chains to disruptions, the type and frequency of which is entirely different from the adverse events occurring in civil goods flows, is increasing.
The proposed risk assessment method was validated against the ISAF (International Security Assistance Force) operation in Afghanistan. The specificity of the war in Afghanistan was using one type of fuel (with various additives) to supply engines, regardless of the type of engine (diesel engines, spark-ignition engines, turbojet engines). This concept is called “the concept of Single Fuel Policy”. Therefore, fuel was the most sensitive part of the entire chain. Additionally, Afghanistan has no oil refinery; therefore, 100% of the fuel is imported. This fact forced additional measures to increase the reliability of fuel supply chains.
NATO forces have begun efforts to build resilience in critical supply chains. Therefore, a logistic fuel supply network developed at a strategic level based on the diversification of supply sources.
DLA Energy became the leading organisation responsible for the supply. DLA is an agency of the US Department of Defense (DoD) and reports to the Secretary of Defense. DLA is the leading supplier of consumables and logistics for DoD. It provides the armed forces with food, supplies, equipment and fuel. DLA Energy is a field activity of DLA, whose task is to provide effective and efficient energy solutions. DLA Energy manages the oil supply chain from the source of supply to the customer’s collection point. As an integrated fuel manager, DLA Energy’s responsibilities include the consolidation and review of bulk oil requirements, procurement, financing, budgeting, storage and designated distribution of crude oil to meet the commander’s operational needs. DLA Energy has contracted several Pakistan and Central Asia companies to complete the service requirements, including Red Star Enterprises Limited and Supreme Fuels Trading FZE [
68]. Contractors were required to supply fuel to the main fuel hubs in Afghanistan, from which they would further distribute fuel to military units in fuel tanks. DLA Energy began to award contracts covering the entire supply chain, and ISAF forces began to rely more and more on contractors who went beyond the main fuel hubs and supplied fuel directly to end-users.
However, the beginnings of the missions conducted in Afghanistan proved that the supplies carried out by military supply chains do not ensure the required fuel availability, which should be in line with the reported demand. For this reason, the ISAF Operational Command in Europe, together with Brunssum’s Joint Force Command (JFC HQ), developed the concept of agreements to provide commercial fuel support to NATO ISAF members. These agreements are commonly known as NATO Fuel Basic Ordering Agreement or, in short, Basic Ordering Agreement (BOA). BOA was a unique solution that allowed NATO to provide fuel support to ISAF member states that could not independently provide fuel support to their fighting forces without financial support from NATO’s joint budgets [
69]. BOA was not a single contract. Instead, it was a series of commercial fuel support agreements granted by acquiring and contracting companies from NATO member states. Because NATO owned and managed the BOA fuel supply chain, it acted as an intermediary between ISAF members and contractors. At any time, a member country could decide whether to use BOA fuel services. Individual countries paid for fuel only when contractors provided services or delivered fuel to designated locations. ISAF members did not incur any additional costs and paid for the fuel supplied. The contractors selected under BOA helped in many cases to provide complete logistics services, such as strategic fuel acquisition, management and operation of domestic fuel infrastructure, organisation of local fuel storage systems, internal distribution systems and delivery to the end-user (aircraft, generator, vehicle, the base of operations).
Although BOAs ensure full fuel distribution, not all customers choose to use these services. Similarly, BOA cannot operate in specific locations, such as RC East, because it is outside the BOA’s area of responsibility. To ensure fuel supplies throughout Afghanistan, the NATO Support Agency (NSPA) and US Sustainable Command Afghanistan (JSC-A) have developed contract transport solutions. NSPA provides a NATO mass transport contract managed by the commercial company XeLES. The system is very similar to the US Universal Purchase Agreement. Instead of contacting the supplier directly, however, NSPA instructs XeLES to mediate in obtaining offers from various transport subcontractors. In addition to NSPA, JSC-A is the second element involved in contracted transport. However, JSC-A focuses on a concept at the national and regional level that legally restricts competition for Afghan companies. National Afghan Trucking Agreements provide transport services throughout Afghanistan and use private security companies, Afghan public security forces, or US government security services to protect shipments. The Afghan Transport Network (ATN) contracts are a typical US collective purchase agreement because they meet the repetitive needs of supplies or services. ATN is headquartered and uses local Afghan leaders to provide secure transport support. JSC-A sets the concessions and penalties for the contractor for nondelivery, delay, contaminated shipments, excessive parking times and lost fuel in fuel supplies. Contracting Officer Technical Representatives supervise ATN contracts.
The creation of additional support for supplying the mission with fuel through deliveries in the BOA and contract transport solutions systems contributed to an increase in the resilience of the analysed supply chain to the occurring disruptions and limitations in supplies at the strategic level. However, due to the specific supply environment of Afghanistan, the ongoing war, the proper functioning of the fuel supply chain was a challenging operation, an operation at high risk on a tactical level. Therefore, a need identified to develop a tactical risk assessment method for supply chains supporting the flows of critical products for military missions.
5. Results
The proposed tactical risk assessment method was implemented for ad post-analysis of a selected military operation in Afghanistan. The conducted analytical procedure made it possible to verify the correctness of the adopted assumptions and the developed evaluation model. The proposed approach makes it possible to translate the knowledge and experience of the military command into the language of linguistic variables that describes the assessed scenarios.
The data used in the case study section was obtained during face-to-face expert interviews with senior NATO officials who are directly responsible for the organisation of the fuel supply chain in Afghanistan. The selection of experts was not random—the critical factor was experience measured in months of direct service under ISAF—the shortest internship was 17 months, the longest 39 months. In addition, the authors made sure that the experts represented both officers working directly at the ISAF Headquarters and the so-called liaisons officers of the national components of the coalition states that make up the ISAF. The obtained responses were convergent and were averaged—however, it should emphasise that they were always within the same blur intervals. A detailed analysis was carried out in a response that differs significantly from the others, whether it is an unexpected situation or an essential component of the model that the authors did not consider. In such a situation, each time, it turned out that we are dealing with a single incident resulting from the specificity of operations in the area covered by the war and rejected such a response.
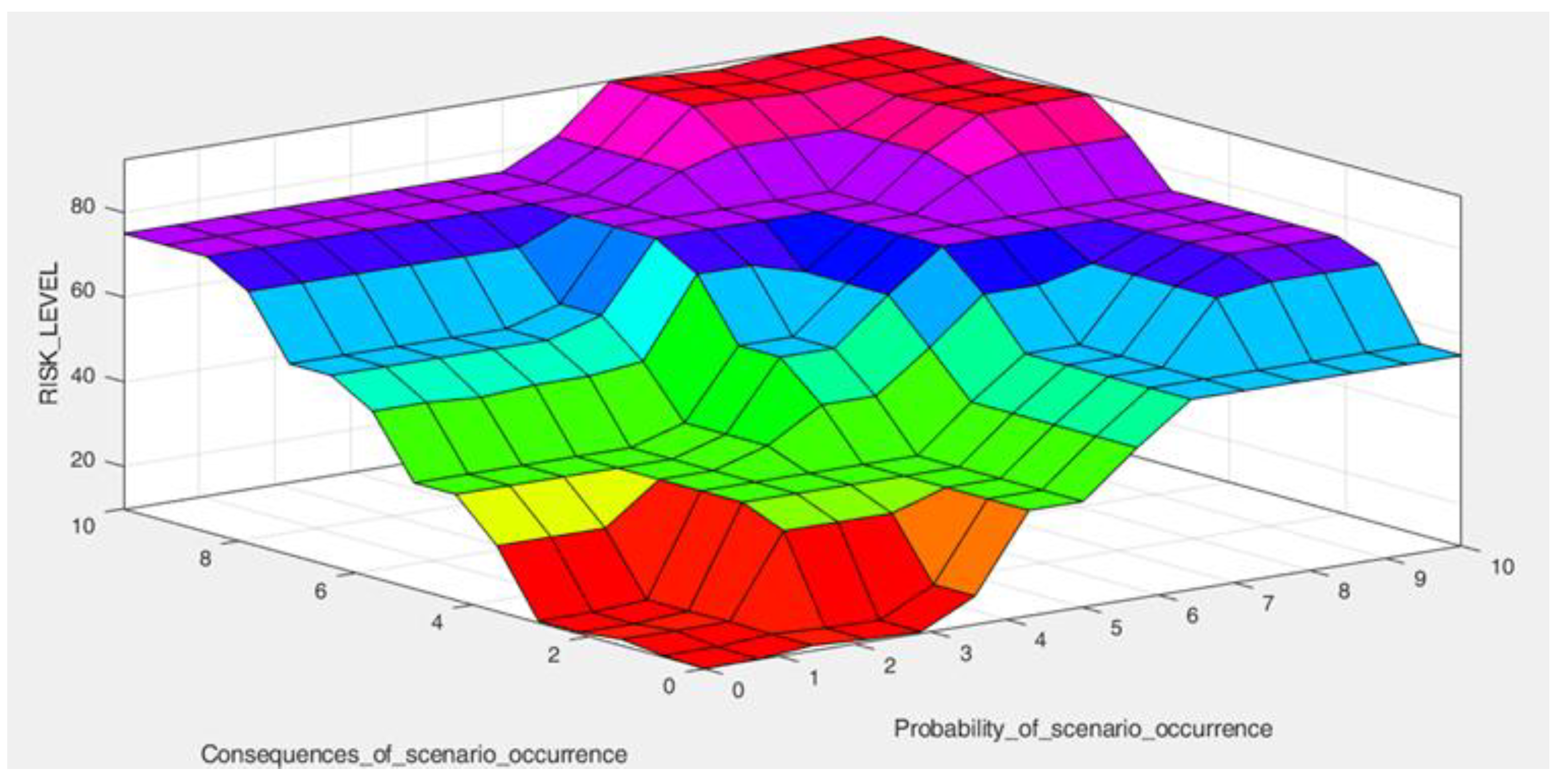
Figure 9 show the resultant values of preliminarily estimated: The probability of assessed adverse event scenarios and their consequences, which have been calculated based on the knowledge of NATO experts. The assessment of consequences was related to the possibility of complete and uninterrupted execution of the military operation and the safety of its participants. The lowest, orange-red part of the plot represents the resultant level of risk caused by low-frequency scenarios, with insignificant damage potential. The highest level, red-pink part of the plot represents catastrophic risks related to high-probability scenarios that may result in loss of ability to accomplish the mission. Events that will be assessed at such a high-risk level become scenarios of a critical nature, requiring immediate action, with a wide range of impact.
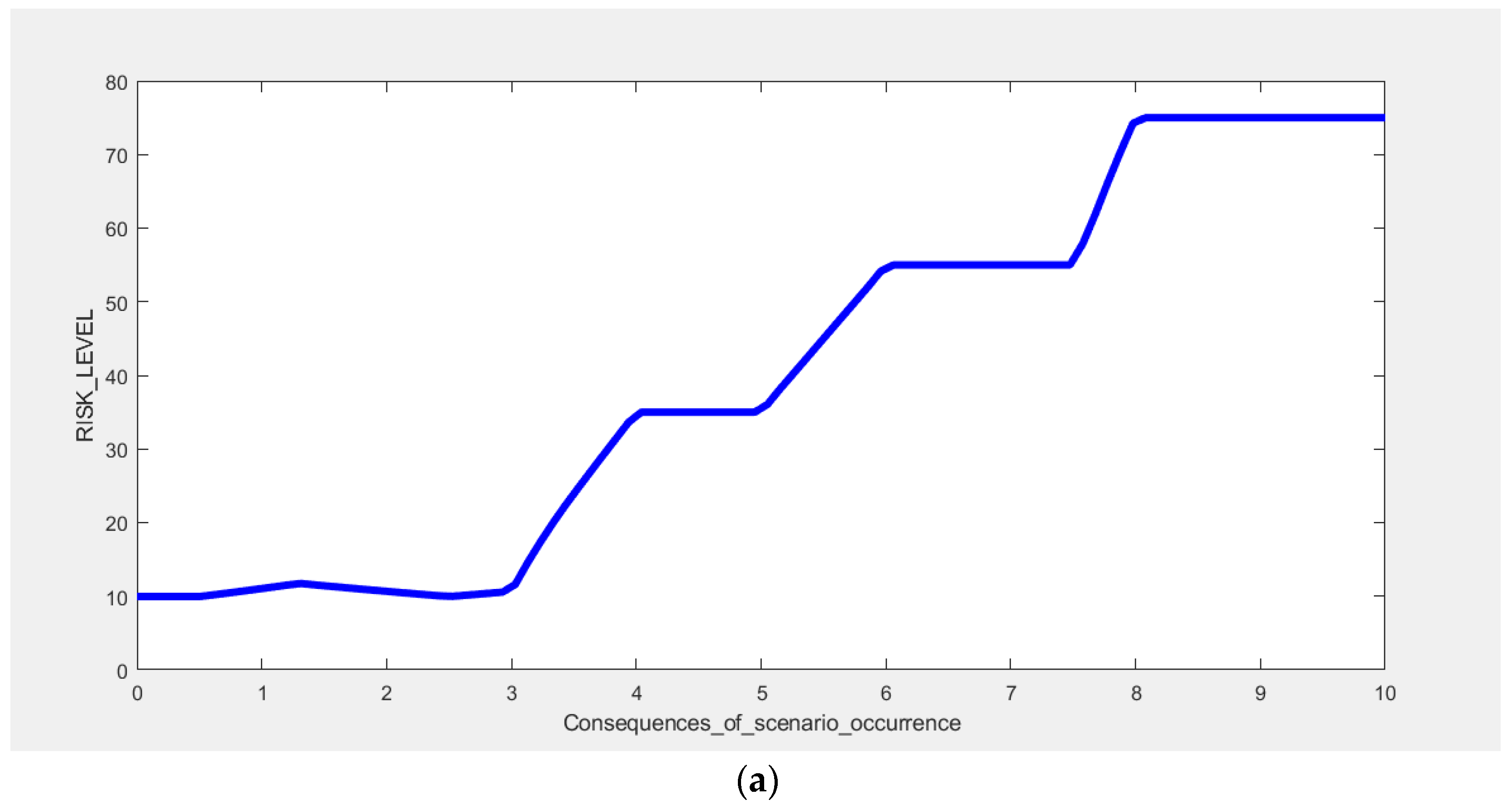
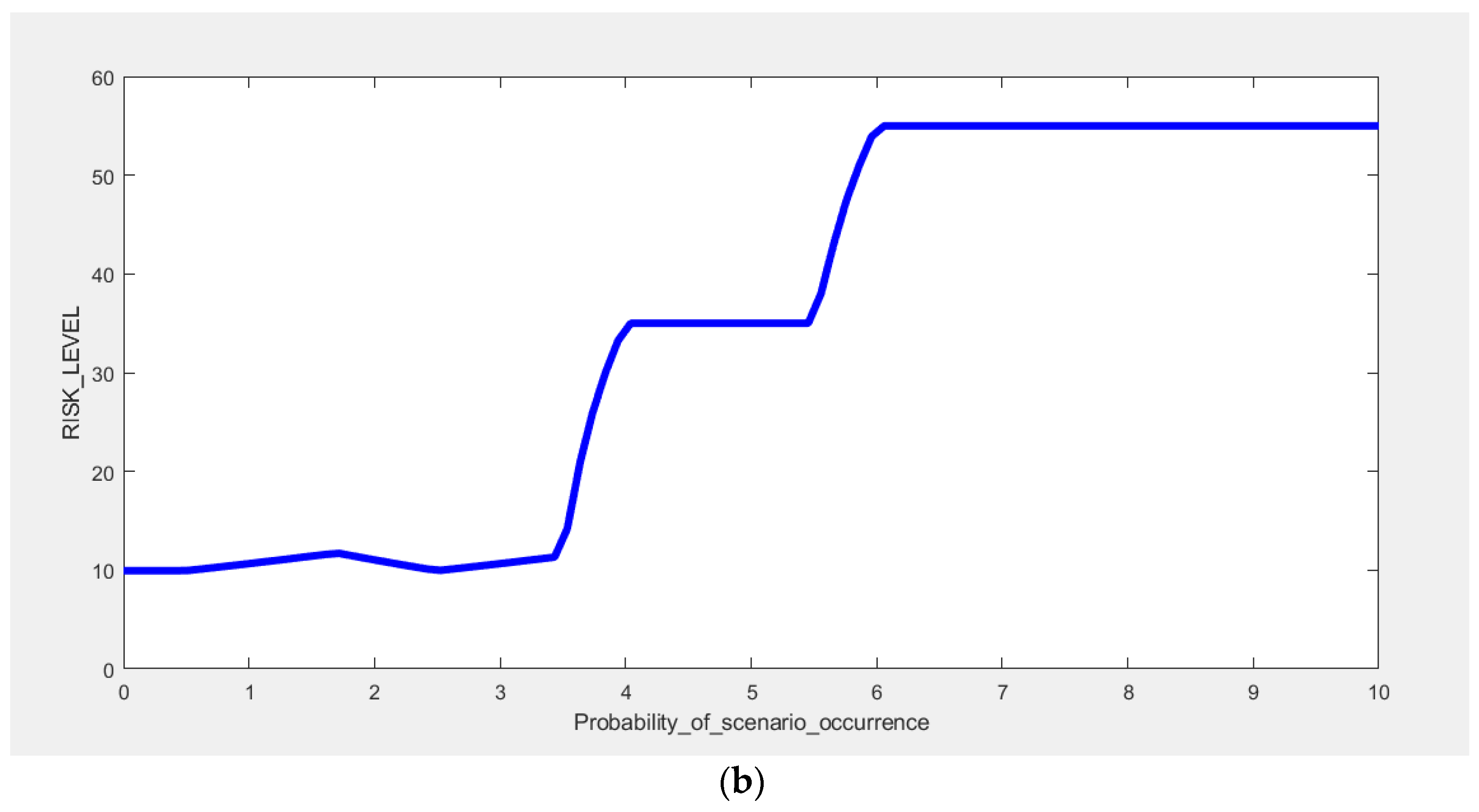
Figure 10 shows the influence of the course of the input functions on the obtained risk level at the output of the proposed model. When analysing the content of these charts, one should remember the specific properties of the Mamdani system implemented in Fuzzy Logic Designer in Matlab. For Mamdani systems, the output range depends on both the input and output MF ranges because both inputs and outputs are fuzzy sets. The MF ranges are defined by the “parameter” field of each MF. The output signal range should usually be chosen to include the minimum and maximum values of all output MF. A completely different situation occurs in Sugeno systems, where the output range is uniquely defined by the scope and type of input membership functions. Therefore, the selection of the input range does not affect the course of the surface. For Sugeno systems, this approach should be considered a limitation as the output data are not fuzzy sets.
In military operations, the most important are preventive measures to reduce adverse events with the highest risk level—i.e., those scenarios whose occurrence threatens the performance of the mission and the health and life of soldiers. At the same time, decision-making officers are characterised by the level of risk perception, which determines the greater propensity to undertake risk-bearing activities.
For this reason, the level of accepted risk is very high, and, according to experts’ assessment, it may be as high as RS = 70. Risk reduction actions are taken for scenarios with such a determined acceptance level, and the risk score is above 70 points. These will, therefore, be those adverse events that fall into the High (R5) and Medium-high (R4) categories, according to
Table 5.
The lack of risk acceptance concerns the S1, S3, S4, S5 and S8 scenarios in the analysed case. Specific risk mitigation actions are taken immediately in the events described in the S3 and S5 scenarios. These are the events where the risk score reaches the maximum level (above 90 points). This means the necessity to undertake multidirectional actions to simultaneously reduce the probability of occurrence and limit the possible consequences. However, in the S1, S4 and S8 scenarios, appropriate preventive actions should be taken, significantly reducing the frequency of occurrence of the events described. The risk index for the S2, S6 and S9 scenarios, is at the acceptance level. However, their value is close to the acceptance threshold. For this reason, it is necessary to monitor the probability parameter of these events constantly. The increase in the frequency of their registration in prepared reports will require immediate actions to reduce the level of risk, primarily through preventive actions.
6. Discussion
The tactical risk assessment method presented in the article applied to fuel supply chains. This is reflected when identifying adverse event scenarios and later estimating the parameters of the risk involved. Due to the lack of complete and reliable historical data on adverse events in the assessed fuel chain, we implemented the fuzzy inference system (FIS) to estimate the risk. We chose it, among other reasons, because it is one of the most famous applications of fuzzy logic and fuzzy sets theory [
48]. The proposed risk assessment model uses fuzzy rules built based on the knowledge of NATO experts. According to research by Guillaume [
48], this kind of FIS offers a high semantic level and a good generalisation capability.
However, the FIS model used in the proposed method has some limitations. If the FIS model is based solely on expert knowledge, it may show insufficient measurement accuracy in complex systems. Therefore, if the researchers require a very accurate model, some other techniques are better (like Neural Nets, multilayer perceptions and radial basis functions). These techniques do not have the inconvenience that fuzzy has, e.g., the curse of dimensionality [
70]. The critical issue, in this case, is also the selection of experts. The obtained results are highly dependent on the knowledge and experience of people participating in the study as experts. In the conducted research, the selection of experts was not random. The researchers were guided primarily by the experience and knowledge of experts in logistics services for military missions, particularly those carried out in Afghanistan. However, their readiness to cooperate in the research conducted was also not without significance. However, it should be noted that the selection of experts with different qualifications or experience (e.g., in other areas) could provide completely different results for the conducted assessment. For this reason, the process of selecting experts for research should be carried out with due diligence.
Proper selection of experts applies to each stage of the procedure carried out. Their qualifications and experience are essential to measuring the probability and effects of each of the analysed scenarios and identifying possible adverse events. The scenarios presented in the article were identified based on the knowledge of NATO experts on the research day. However, this collection cannot be considered closed. Each subsequent stage of the ongoing mission may provide new scenarios that should also be assessed. For this reason, the assessment procedure cannot be carried out once. However, it should be repeated periodically, and the results should be updated with new scenarios and the effects of the implemented preventive actions.
The results described above should become the basis for improving planning fuel supplies for the needs of military operations performed in the selected territory. By taking preventive actions and creating emergency scenarios, it will be possible to increase the resilience of military supply chains serving missions. The periodic risk analysis will identify those disruptions under the control of the army operations command and operators serving the supply chains. Thanks to this, it will be possible to make rational decisions aimed at mitigating the occurring risk. It is also possible to prepare contingency scenarios in advance by indicating critical events whose sources are independent of the organised military operation (natural disaster or terrorist incidents). This will shorten the reaction time of decision-makers and increase the flexibility of military supply chains. Thanks to such actions, the supply chain resilience to disruptions will be increased, and the security of the supported military operation will be improved.
7. Conclusions
NATO documents recommend preparing a risk assessment to implement military operations, particularly those carried out in areas affected by hostilities. Such analyses are organised regularly, but they usually concern the level of strategic management of supply chains. Meanwhile, such studies also need such studies at the tactical decisions regarding securing the continuity of supplies. Such risk analyses are mainly required for chains supplying critical products, such as food, fuel, or medical supplies. In these supply systems, the key is to build the resilience of supply chains not only at the strategic level and at the operational level. Meanwhile, the prepared literature review indicates a research gap for this area of analysis. Therefore, the article proposes a method of tactical risk assessment for the supply chain, which is responsible for coordinated deliveries to military units carrying out missions in a foreign territory.
The authors’ significant contribution is that the conducted research considered the specificity of both fuel supplies and the organisation of military operations. This was reflected in the identified adverse event scenarios and at the stage of estimating the probability and consequences of their occurrence. Thanks to the involvement of NATO experts in evaluating these values, unique research material was obtained based on specialist knowledge and experience that is difficult to obtain. Their participation made it possible to estimate the value of risk parameters reliably and evaluate each identified scenario using the fuzzy set theory. As a result, the obtained results may constitute a practical contribution to improving the preparation of future military operations. At the same time, it is possible to use the model to assess other scenarios of emerging new adverse events for the assessed supply chain. However, in recording quantitative data on the frequency and effects of the analysed adverse events in military reports, it would be possible to use other strictly quantitative assessment techniques, such as event trees, Petri nets, or Bayesian networks.
The authors can further develop the proposed tactical risk assessment method. One of the planned directions of further research work is the introduction of weights for experts’ opinions, which will depend on the experience of the expert. It is a method to strengthen the opinion of those experts who can demonstrate knowledge and expertise strategically and operational (e.g., higher weight for the views of experts participating in similar missions and similar environmental conditions). Thanks to the comparative analysis, the impact of the selection of experts on the obtained results of the risk analysis can be assessed.
The authors plan to implement the proposed method for other critical supply chains serving the supplies of military missions. Each military operation is unique and depends on many factors, both internal and external. Therefore, while the proposed assessment procedure is universal, the results obtained are specific for a given supply chain of a selected product. In the presented method, the adverse event scenarios assessed in the proposed way can be divided into two groups. The first group includes those adverse events that are characteristic of fuel supply chains. This group consists of the S4, S5, S6 and S7 scenarios. The second group of adverse events considers the specific conditions of implementing military missions in a foreign territory. These include scenarios S1, S2, S3, S8, S9. These scenarios can also be analysed when assessing logistics systems that also supply soldiers with other products. Therefore, in further research, it is necessary to estimate the risk of these scenarios and the conditions accompanying the logistical handling of different supply chains. It is also reasonable to supplement these scenarios with adverse events characteristic of the analysed group of products (e.g., food, clothing, weapons, drugs). Selected experts will assess all these scenarios with knowledge and experience handling the analysed supply chains for the assessed military missions. The envisaged direction for further research includes risk assessments for military supply chains at the tactical level.