1. Introduction
With rapidly growing demand for energy and decreasing fossil fuel reserves, renewable energy has attracted great of attention worldwide in the last few decades. Solar power is an important source of renewable energy, and various solar-powered products have become part of our daily-life, such as solar-powered cars [
1] and solar-powered Unmanned Aerial Vehicles (UAVs) [
2]. Powering UAVs by solar energy is a promising solution to overcome the bottleneck of the limited flight time of UAVs powered by onboard battery. Harvesting solar energy while flying allows UAVs to fly longer in the sky, which enables the UAVs to provide uninterrupted service in different applications such as monitoring and surveillance [
3,
4], disaster management [
5], infrastructure inspection [
6,
7], parcel delivery [
8] and wireless communications [
9].
The application of UAVs in wireless communications is a hot topic. Compared to conventional wireless communication systems based on stationary infrastructures, UAV-based communication systems can provide timely and economical services in temporary hotspots, disaster areas, and complex terrains [
9,
10], thanks to their maneuverability. Many research articles relevant to UAV-enabled wireless communication systems have been published, and the UAVs assist existing communication systems by offloading the traffic demand of the stationary access points [
9,
11,
12] and acting as relays to connect remote users to network [
13].
UAVs have also been used to protect wireless communications. Wang et al. [
14] maximized the non-zero secrecy capacity of a UAV-node link in the presence of an eavesdropper by optimally deploying the UAV. Wang et al. [
15] considered a four-entity system with a transmitter, a receiver, an eavesdropper and a UAV relay. They optimized the transmit power of the transmitter and the UAV to maximize the secrecy rate of the system. Li et al. [
16] used a UAV as a jammer that interferes with eavesdroppers. They focused on optimizing the trajectory and the jamming power of the UAV and the transmit power of the transmitter to maximize the average achievable secrecy rate. Cai et al. [
17] studied a protection scheme using two UAVs: one transmits information, and the other interferes with eavesdroppers. The method jointly optimizes the UAVs’ trajectories and the user transmission schedule. Li et al. [
18] investigated a scenario where two UAVs transmit confidential messages to specified ground nodes using the same spectrum in the presence of an eavesdropper. Although the mutual co-channel interferences arising from spectrum sharing may lower the spectral efficiency, the eavesdropping effect can be reduced as the two UAVs act in essence as cooperative jammers for each other. The authors of [
19,
20] secured the wireless data communication between a ground transmitter and a UAV by jointly optimizing the trajectory of the UAV and the transmit power of the ground transmitter to maximize the average secrecy rate over a given period of time. One common setting in [
14,
15,
16,
17,
18,
19,
20] is that the UAV is powered by an onboard capacity-limited battery. Therefore, these designs may not ensure a sustainable defence against eavesdropping.
This paper considers using a solar-powered UAV to secure wireless communications with a ground node in the presence of collaborative eavesdroppers. By securing wireless communication, we mean that the ground node can recover the data sent by the UAV and the eavesdroppers cannot do this at any time. This is a new scenario which has not been considered comprehensively in the literature. Firstly, in light of the method in [
21], we consider a solar-powered UAV which is possible to operate for a longer time than the onboard battery-powered UAVs. Secondly, unlike the methods in [
16,
18,
19,
20], which optimize the integrated jamming or eavesdropping performance, we target on the instantaneous communication protection. Thirdly, in light of the method in [
22], the eavesdroppers can collaborate by combining the collected signals to get a better understanding of the information sent by the UAV. Obviously, this can make it more difficult for the UAV to optimize its trajectory. Moreover, different from most existing publications, which assume that the UAV flies in free space, we consider no-fly zones. The no-fly zones may be tall buildings or areas with high risks of being targeted by ground-to-air missiles [
23,
24,
25]. These different considerations make the problem considered in this paper more general, challenging and practical.
In this paper, we focus on a new trajectory optimization problem for a UAV by taking into account solar power harvesting, instantaneous communication protection, collaborative eavesdropping and no-fly zones. We propose a new optimization model to minimize the energy expenditure of a UAV with a solar-powered rechargeable battery, while securing communications between the UAV and a ground node, avoiding no-fly zones, satisfying the aeronautic maneuverability and preventing depletion of the battery. This is a realistic problem but needs a nonconvex optimization technique, as the solar power is non-smooth and the UAV dynamic model is non-linear. We propose a scheme to plan the UAV trajectory based on Rapidly-exploring Random Tree (RRT). In the proposed method, an RRT can be constructed to capture the non-linear UAV motion model and the secure communication requirements. From the RRT, we can randomly select a set of possible trajectories which end in a pre-defined destination set. (The final position of the UAV is in the destination set.) We verify the energy storage along each possible trajectory and choose the one with the minimum energy expenditure while satisfying all the constraints. Our key contributions include the new problem formulation and the new RRT-based trajectory planning method, which is computational efficient and can quickly explore the flight space to construct UAV trajectory. Computer simulations demonstrate the effectiveness of the proposed approach. By comparing to a baseline method which is unaware of eavesdropping, the proposed method is shown to guarantee the valid wireless communication link with the ground node and prevent eavesdropping. Although a static environment setting is demonstrated in the paper, the proposed RRT-based method can be potentially applied to dynamic environments thanks to its computational efficiency.
RRT falls into the category of sampling-based path planning algorithms. A similar algorithm is the Probabilistic Roadmap (PRM). It first builds up a dense enough roadmap (graph) and finds a path from the start to the destination by a graph search algorithm [
26]. By contrast, the RRT method achieves the best feasible path to the goal all by its own processing procedure, which is more suitable for dynamic cases. Another category of path planning methods is the node-based algorithms such as Dijkstra’s algorithm [
27]. They grid the solution space and need a specific metric to characterize the cost of moving from one grid to another. These algorithms cannot handle the mobility constraints of UAVs, such as the non-holonomic constraints, as they generally regard the robot as a point in the graph [
27]. However, the RRT-based method can account for the mobility constraint in the process of constructing the tree. Furthermore, as shown below, it is not straightforward to define the cost of moving from one grid to another needed for the node-based algorithms. From these discussions, the RRT-based method well suits the considered problem.
The remainder of the paper is organized as follows. In
Section 2, we present the system models and state the problem under investigation. In
Section 3, we present the proposed 3D trajectory optimization method to minimize the energy consumption subject to the constraints of the UAV maneuverability, communication security, battery lifetime and no-fly zones. Computer simulations are presented in
Section 4 to show the performance of the proposed navigation algorithm. Finally, a conclusion is given in
Section 5.
3. Navigation Law
The problem under consideration cannot be solved using convex optimization tools, because of the non-convexity of the objective function in Equation (
14), especially the part for level flight in Equation (
5), the non-smoothness of the solar power harvesting model in Equation (
4) and the non-linearity of the UAV dynamic model in Equation (
1). We propose an RRT-based trajectory planning scheme to solve the problem heuristically and efficiently. The RRT method can tackle the non-linear dynamic model, secure communication requirements and no-fly zones by generating random samples in the searching space and only keeping the samples satisfying all the constraints.
We assume that the UAV knows the locations of the node and the eavesdroppers. We divide
into
L equal intervals (each interval lasts
) and assume that the control inputs
and
are updated at time instants
and remain constant at any interval
,
. The control inputs of the UAV dynamic model are simplified as follows:
for
. Compared to Equation (
1), the input
keeps the maximum value
, and
and
in Equation (
17) either take 0 or the corresponding maximum value, respectively. Although this simplification sacrifices the maneuverability of the UAV, it is still realizable since the selected control inputs are all within the allowed ranges. More importantly, this simplification makes the UAV easy to control and also narrows down the solution space significantly. It is not hard to see that this method can be easily extended to include some more feasible control inputs.
Based on Equation (
17), the models in Equations (
4) and (
11)–(
13) can be discretized directly as they are functions of the UAV position
. To discretize the energy consumption model of the UAV, we rewrite the velocity vector
as
. Then, the discrete forms of Equations (
8) and (
14) can be obtained. Accordingly, the relationship of Equation (
9) is rewritten as:
Considering the battery capacity
, Equation (
18) should be corrected by:
The trajectory of the UAV for the interval
can be found by solving the discrete version of the considered problem. Specifically, having the position and heading of the UAV at
, we can construct an RRT with a certain number of vertices based on Equations (
2), (
3), (
11)–(
13) and (
17). Then, any vertex of the RRT that is reachable from the root via a sequence of control inputs defined in Equation (
17) is within the allowed altitudes, is outside the no-fly zones and can avoid both the individual and collaborative eavesdropping. However, not all the vertices in the RRT are feasible for the UAV to visit due to the constraints in Equations (
15) and (
16). From the RRT, we can randomly select a trajectory with
L consecutive vertices starting from the root. If the last vertex falls into the destination set
, then the constraint in Equation (
16) holds. Furthermore, for each vertex of this trajectory, we verify the constraint in Equation (
15). If Equation (
15) also holds, we finally compute the energy consumption of the UAV along this trajectory according to Equation (
14). We can randomly select a set of trajectories as above, and the one with the minimum energy consumption can be identified. This algorithm is summarized in
Table 1.
The RRT-based method can quickly explore the solution space. It belongs to the group of sampling-based algorithms. Another sampling-based method is the probabilistic roadmap (PRM). This method builds up a roadmap (graph) first which should be dense enough such that a path exists between the start and the destination. Then, a path can be obtained by a shortest path query. Different from RRT-based method, which achieves the best feasible path to the goal all by its own processing procedure, PRM generally calls a graph searching algorithm [
26]. Another group of path planning methods is the node-based algorithms. The Dijkstra’s algorithm and its variants are the typical ones. As node-based, they require to grid the solution space, and a specific metric is needed to characterize the cost of moving from one grid to another [
27]. These algorithms cannot handle the mobility constraints of UAVs such as the non-holonomic constraints. Specifically, in the gridded space, moving from one node to another may be impossible for a UAV having the limited angular speed. If possible, the computation of the feasible linear, angular and vertical speeds is required. However, the developed RRT-based method accounts the mobility constraint in the process of constructing the tree. Thus, the obtained can be tracked directly without any later adjustment. Furthermore, for the problem under consideration, it is not straightforward to define the cost of moving from one grid to another needed for the node-based algorithms. From these discussions, the RRT-based method well suits the considered problem.
4. Simulation Results
In this section, we demonstrate the effectiveness of the proposed method via computer simulations. The parameters used are summarized in
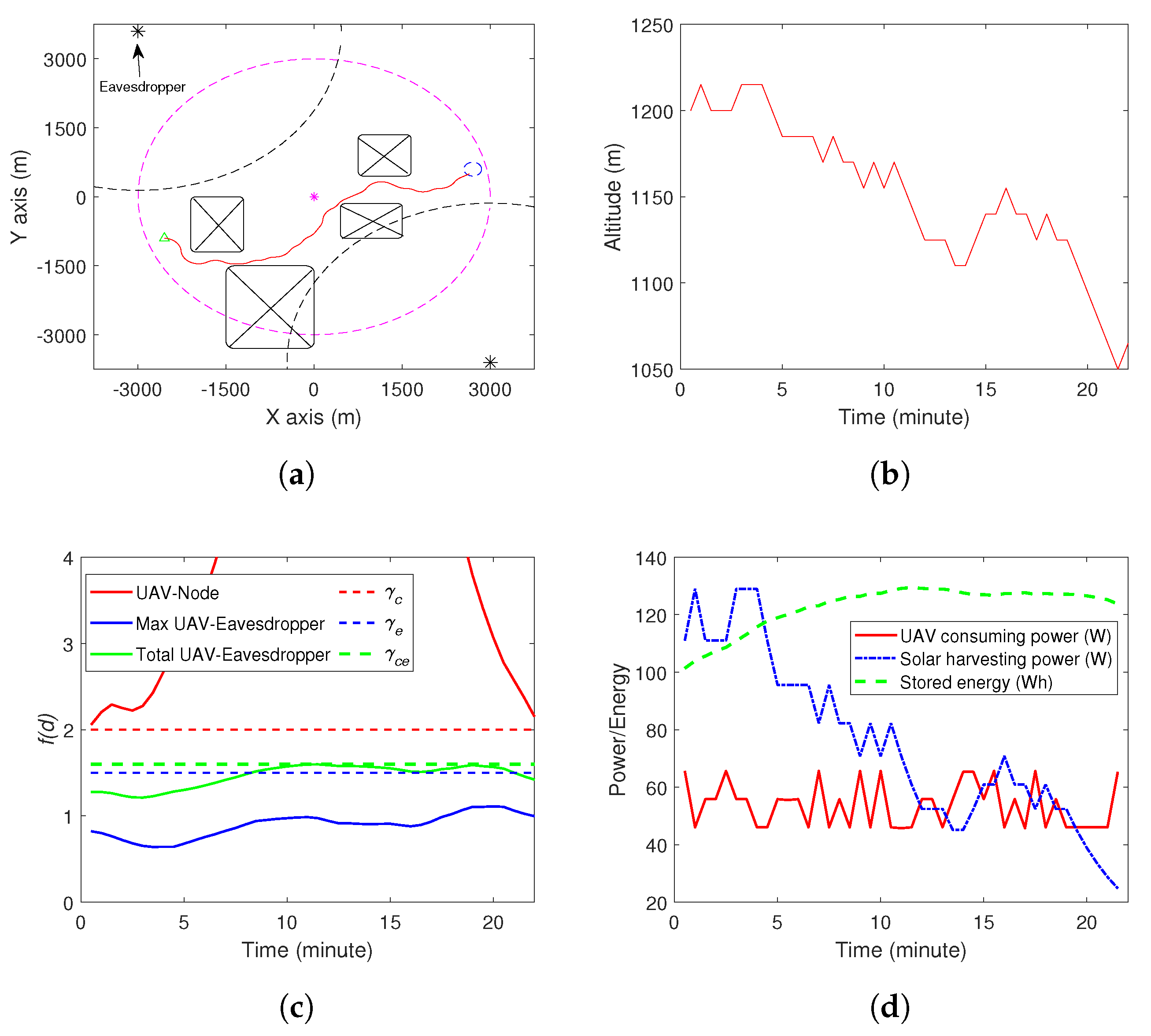
Table 2. We considered two simulation environments, as shown in
Figure 1 and
Figure 2. In
Figure 1, there are two eavesdroppers and four no-fly zones, while, in
Figure 2, there are three eavesdroppers and five zo-fly zones. The ground node locates at (0,0). The UAV starts from the initial position, which is shown by the green triangle in
Figure 1a and
Figure 2a. The destination set is shown by a blue circle on the right side of
Figure 1a and
Figure 2a. In
Figure 1a and
Figure 2a, we also demonstrate some dash lines on the plane of
, i.e., the ground. The purple one indicates the area within which the ground node can effectively recover the sent data by the UAV. The black dash lines represent the area within which the eavesdroppers (marked by the black squares) can recover the captured data. Starting from the initial position, the UAV moves along the red trajectory and reaches the destination set in 22 min in environment 1 and 23.5 min in environment 2, which are before the due time. The altitude of the UAV during the movement is shown in
Figure 1b and
Figure 2b. The communication between the UAV and the ground node is good, as shown in
Figure 1c and
Figure 2c, and this trajectory avoids the individual and collaborative eavesdropping (see
Figure 1c and
Figure 2c). Finally, the energy consumption of the UAV, the solar energy harvesting and the stored amount of energy are shown in
Figure 1d and
Figure 2d. Note that the simulations were conducted on a normal PC with Inter(R) Core(TM) i7-8565U CPU @ 1.8GHz, 1.99GHz and 8G RAM. The average time to find the trajectory was about 3–5 s. Specifically, for the simulation in Environment 1, the algorithm generated about 800–1000 samples. The number of samples generated changed in each simulation as the RRT-based algorithm is a random method. For Environment 2, the algorithm generated more samples, i.e, 10,000–13,000. The reason is that Environment 2 (three eavesdroppers and five no-fly zones) is more complex than Environment 1 (two eavesdroppers and four no-fly zones). Thus, there were more infeasible samples generated in Environment 2.
For comparison, we applied a baseline method to the considered case. This baseline method only considers effectively transmitting data to the ground node while ignoring the eavesdroppers. All the parameters were the same as above. The simulation results are shown in
Figure 3 and
Figure 4. The trajectories of the UAV are shown in
Figure 3a and
Figure 4b. Comparing
Figure 3a and
Figure 1a (
Figure 4a and
Figure 2a), we see that this trajectory is closer to the eavesdropping boundary of one of the eavesdroppers. Although this does not lead to the successful individual eavesdropping by the top eavesdroppers, the two eavesdroppers can recover the captured data by analyzing the combined data. This is shown in
Figure 3c. Between 5 and 13 min, the eavesdropping performance is above the threshold
. A similar finding can be observed in
Figure 4c. From this comparison, we can see that the proposed method can construct a safe trajectory, which ensures the communication with the ground node, avoids eavesdropping and avoids collision with no-fly zones.