Abstract
In this paper, we aim to provide reliable user connectivity and enhanced security for computation task offloading. Physical layer security is studied in a wireless-powered non-orthogonal multiple access (NOMA) mobile edge computing (MEC) system with a nonlinear energy-harvesting (EH) user and a power beacon (PB) in the presence of an eavesdropper. To further provide a friendly environment resource allocation design, wireless power transfer (WPT) is applied. The secure computation efficiency (SCE) problem is solved by jointly optimizing the transmission power, the time allocations for energy transfer, the computation time, and the central processing unit (CPU) frequency in the NOMA-enabled MEC system. The problem is non-convex and challenging to solve because of the complexity of the objective function in meeting constraints that ensure the required quality of service, such as the minimum value of computed bits, limitations on total energy consumed by users, maximum CPU frequency, and minimum harvested energy and computation offloading times. Therefore, in this paper, a low-complexity particle swarm optimization (PSO)-based algorithm is proposed to solve this optimization problem. For comparison purposes, time division multiple access and fully offloading baseline schemes are investigated. Finally, simulation results demonstrate the superiority of the proposed approach over baseline schemes.
1. Introduction
The rapid advances in fifth-generation (5G) wireless networks have improved cutting-edge technology requirements, such as support for massive connectivity due to the proliferation of Internet of Things (IoT) devices and growth in the amount of data in modern society [1]. In this sense, recent technological breakthroughs for next-generation wireless networks have promoted the use of smart applications, such as virtual reality, augmented reality, mobile online games, face recognition, and so on. However, latency sensitivity and high computation intensity are two main features of these applications that represent a challenging task for mobile devices, which have low computing capabilities and a limited battery capacity. To tackle these issues, mobile edge computing (MEC) appears to be a technology that can remarkably decrease the computing burden and improve the computing capabilities of mobile devices [2]. In a MEC system, servers are used by mobile devices to offload tasks for low-latency computing, which can be executed in partial or binary modes. In partial mode, computation tasks can be processed into two parts: one part is executed locally at the mobile device and the other is offloaded to the nearby MEC server. In binary mode, the complete task is executed locally, or the entire task is offloaded to a close-proximity MEC server via uplink [2,3]. Furthermore, future wireless networks should be able to support massive connectivity of devices because of the rapid advancements in the IoT. However, this fact entails the spectrum scarcity issue, which can be handled by the application of a non-orthogonal multiple access (NOMA) transmission strategy that works in the power domain and employs superposition coding and successive interference cancellation techniques. Therefore, NOMA with MEC has aroused attention in recent research work that pointed out the superiority of NOMA in comparison with the conventional orthogonal multiple access (OMA) baseline scheme [4,5,6,7]. In [5], the authors applied NOMA to offload tasks from each user to a MEC server, with the aim being to improve the resource allocation problem in an ultra-dense network. They demonstrated that NOMA outperforms the conventional time division multiple access (TDMA) technique in terms of energy consumption and task delay. A NOMA-based optimization scheme was investigated in cite6 to minimize energy consumption by users in a MEC network through an efficient heuristic algorithm. The simulation results showed significant energy-consumption lowering by applying the NOMA framework. Energy-efficiency maximization in NOMA-enabled massive IoT networks based on resource allocation strategies was investigated by Liu et al. [7]. The paper concluded that NOMA for offloading can save a considerable amount of energy, in comparison with existing baseline schemes such as OMA.
In [2], Lin et al. considered a NOMA-enabled MEC network in which several users perform partial offloading under the presence of an eavesdropper. The authors investigated the maximization of the secure computation efficiency subject to the constraints of minimum computation rate, maximum transmission power allowed by the users, and maximum CPU frequency, where the solution was based on the successive convex approximation (SCA) technique. In [3], Wu et al. considered a MEC system with NOMA composed of two users and one eavesdropper. The authors used a partial offloading set-up with the aim to minimize the weighted sum-energy consumption of the users subject to the constraints of secrecy offloading rates, channel capacity, and maximum tolerable secrecy outage probability. The solution was based on the exhaustive search method and semi-closed form expressions. In [8], Wu et al. studied a multiuser MEC system with NOMA under the presence of an eavesdropper. The partial offloading mode was used and the authors investigated the minimization of the weighted sum-energy consumption subject to the constraints of required bits securely offloaded, channel capacity, and maximum tolerable secrecy outage probability. The solution was based on the bisection method and semi-closed form expressions. However, none of the previous three references have considered a wireless power transfer phase, a PB device, and the presence of an energy harvesting user with its corresponding minimum EH constraint. Therefore, several new variables and constraints are included in the optimization problem proposed in this paper, compared with those in [2,3,8] where the solutions proposed in these references are not suitable for the problem investigated in this paper. For instance, the variable to define the time for the wireless power transfer phase is coupled with the transmission power variables and the variable to define the local computing time is coupled with the variable of the local computing CPU frequency. In addition, the works in [3,8] considered the minimization of the weighted sum-energy consumption which is different to the proposed secure computation efficiency (SCE) maximization in this paper. In [9], Wu et al. considered a NOMA-enabled multi-access MEC system where a single mobile user can offload part of its task to a group of edge-servers. The authors investigated the minimization of the delay in completing the task required by the mobile user under the constraints of maximum available energy at the mobile user and the maximum allowed energy at the edge-server to process the task requirement. However, the authors did not study the physical layer security under the presence of an eavesdropper and did not consider a wireless power transfer phase, a PB device, and the presence of an energy harvesting user with its corresponding minimum EH constraint. Therefore, the solution proposed in [9] cannot be used in the problem proposed in this paper.
Furthermore, wireless power transfer (WPT) has been investigated as a promising solution to deal with the limited battery capacity of wireless devices in MEC networks. WPT can steadily reload the batteries of a large number of low-power wireless devices through a dedicated radio frequency (RF) transmitter. The foremost benefits from WPT are focused on prolonging the wireless network lifetime, reaching sustainability in network operations, and improving the communications capacity in edge wireless devices. In a WPT-aided MEC network, the access point (AP) sends RF energy to customers on downlink. Then, the customers use the harvested energy to perform computation tasks in partial or binary offloading modes. The integration of WPT with MEC is denominated as a wireless-powered MEC system, which has been studied in recent work [10,11,12,13,14] to extend the operational lifetime of the battery in both partial [10] and binary [11,12] offloading modes. In [13], the authors approached energy-efficient computation offloading for a cooperative MEC network where a user near a hybrid AP helps to offload tasks from a distant user, and both users benefit by receiving energy from the hybrid AP through WPT. In [14], a wireless-powered MEC network was studied for local computing and offloading by jointly optimizing energy and task allocation. In addition, the wireless signal experiences attenuation as the distances increase and in the presence of obstacles, where the integration of a power beacon (PB) provides a solution to satisfy energy harvesting (EH) requirements of the users. The PB is a low-cost and low-complexity device that provides wireless energy to users, and it does not need high computational capabilities. In [15], a wireless information and power transfer system aided by a PB was proposed, with the objective being to minimize total transmit power under constraints for QoS and EH requirements. The results showed the benefits from the PB in satisfying the EH requirements of the users.
Although the application of a NOMA system in MEC networks increases the possibilities of meeting 5G requirements, wireless security is still a challenging issue to solve. In particular, confidential information’s vulnerability to being trapped by eavesdroppers increases when computation tasks are offloaded from mobile devices to MEC servers over wireless channels. Physical layer security (PLS) has been considered an alternative to the conventional higher-layer encryption techniques that utilize key management and complex algorithms, and risk being broken by high computational capabilities of the eavesdropper. On the other hand, PLS keeps information safe under wireless communications by exploiting physical layer features of wireless channels, such as noise, interference, fading, and so on, without the use of cryptographic keys and regardless of the computing capability of the eavesdropper. In the literature, there are some recent researches that encompass PLS in NOMA-MEC networks to accomplish a boost in secrecy transmission and to improve energy-efficient resource allocation. In this sense, green communication is an essential topic that has been considered for suitable development in future wireless networks due to excessive energy consumption that will bring plenty of environmental problems [2,3,16]. For instance, in [16], the authors maximized the computation efficiency of the NOMA-MEC network in both partial and binary offloading modes. The paper concluded that the computation efficiency achieved by using partial offloading can exceed the performance obtained by applying binary offloading mode. Moreover, this article pointed out the superiority of NOMA over the TDMA scheme. Although this study did not consider PLS, it opened doors for computation efficiency maximization in different next-generation MEC networks. On the other hand, PLS in a NOMA-enabled MEC system in the presence of a malicious eavesdropper was studied [2,3]. The results demonstrated that partial offloading mode with NOMA outperforms fully offloading mode with NOMA and other the baseline schemes, such as OMA. Moreover, Lin et al. [2] highlighted the concept of computation energy-efficiency, which is defined as the ratio of total computation bits to energy consumption. Different from the uplink transmission schemes proposed in [2,3], our proposed scheme consists of uplink and downlink transmission to further optimize the energy efficiency of the system through the application of WPT service of the AP and the energy transmitted from the PB.
None of the research articles discussed above considered the study of PLS in a PB-assisted wireless-powered NOMA-MEC network with a practical nonlinear EH user. In this paper, we demonstrate through simulations that by employing a PB in the proposed MEC network, the secrecy computation efficiency (SCE) is enhanced. The main advantage of PBs is that they can be densely deployed without a backhaul link installation or complex computational capabilities [17]. We investigate the design of a proper low-complexity resource-allocation scheme to block an eavesdropper in a wireless-powered NOMA-enabled MEC network with a practical nonlinear EH user and PB. From this, we provide a solution based on the particle swarm optimization (PSO) algorithm to maximize the SCE while satisfying the QoS requirements of NOMA users in order to successfully compute their tasks in a safe manner under partial offloading mode. Moreover, the optimization problem is subject to minimum EH by the non-linear EH user. In the literature, PSO is considered a powerful optimization method since it has demonstrated high performance in solving optimization problems. For instance, in our previous works [1,18], the PSO technique has been investigated and applied for maximizing the secrecy sum rate and the secrecy energy efficiency of a cooperative NOMA network, respectively. In both cases, the results showed that the proposed PSO-based method accomplished yield very close to that obtained by the optimal exhaustive search method, but with the benefit of low computational complexity. Furthermore, analytical solutions that provide close-form expressions are rigid for new system model designs. Particularly when the system model includes a new network element, such as mobile device or transmitter, we have to reformulate the optimization problem and find a new solution. Moreover, the procedures to transform non-convex problems into convex problems are not the same for all the cases and depend on the constraints and variables of the optimization problem on a case by case basis. Therefore, most of the solutions offered in related references can not be applied to the proposed problem in this paper. Next, we analyze the optimization problems in related references and the reason why those approaches can not be used in this paper. This motivated us to introduce PSO as a potential optimization solution in an innovative wireless-powered NOMA-enabled MEC system with a practical non-linear EH user. Different from the works in [1,18], where the downlink transmission from the transmitter to the receivers is only considered to carry messages, in this paper an uplink–downlink transmission scheme is studied where the AP integrates a MEC server to alieve the burden of the users. Moreover, the AP provides the WPT service and practical nonlinear EH and PB are integrated into the network.
The main contributions of this paper are as follows.
- We focus on PLS to study the SCE maximization problem in a wireless-powered NOMA-enabled MEC network assisted by a PB under partial offloading mode. Moreover, a practical nonlinear EH and power amplifier coefficient are considered in the design of our proposed scheme.
- We aim to reduce computational complexity. Therefore, we provide a low-complexity PSO-based solution for the proposed challenging non-convex optimization problem, which maximizes SCE by satisfying the QoS requirements of NOMA users and meeting the minimum energy harvested by non-linear EH users. In particular, we jointly optimize the local computing frequency, the computation time for local computing, and the power allocation variables involved in the network. Moreover, we obtain the limits of the search range of each variable to be optimized through mathematical procedures to properly find the global best particle’s position.
- We further investigate SCE maximization for the conventional TDMA-MEC system under partial offloading mode (and for NOMA-MEC system, fully offloading) in order to compare them with our proposed scheme. Numerical results to assess the performance of each scheme show that the SCE obtained under our proposed wireless-power NOMA-enabled MEC scheme is superior to that of other baseline schemes. Moreover, the numerical results show that a system with a PB improves SCE performance.
The rest of the paper is organized as follows. Section 2 presents the proposed system model and two baseline schemes for comparison purposes. Section 3 describes the problem formulation. Section 4 explains the proposed PSO-based solution. The numerical results are given in Section 5. Finally, the conclusions are presented in Section 6.
2. System Model
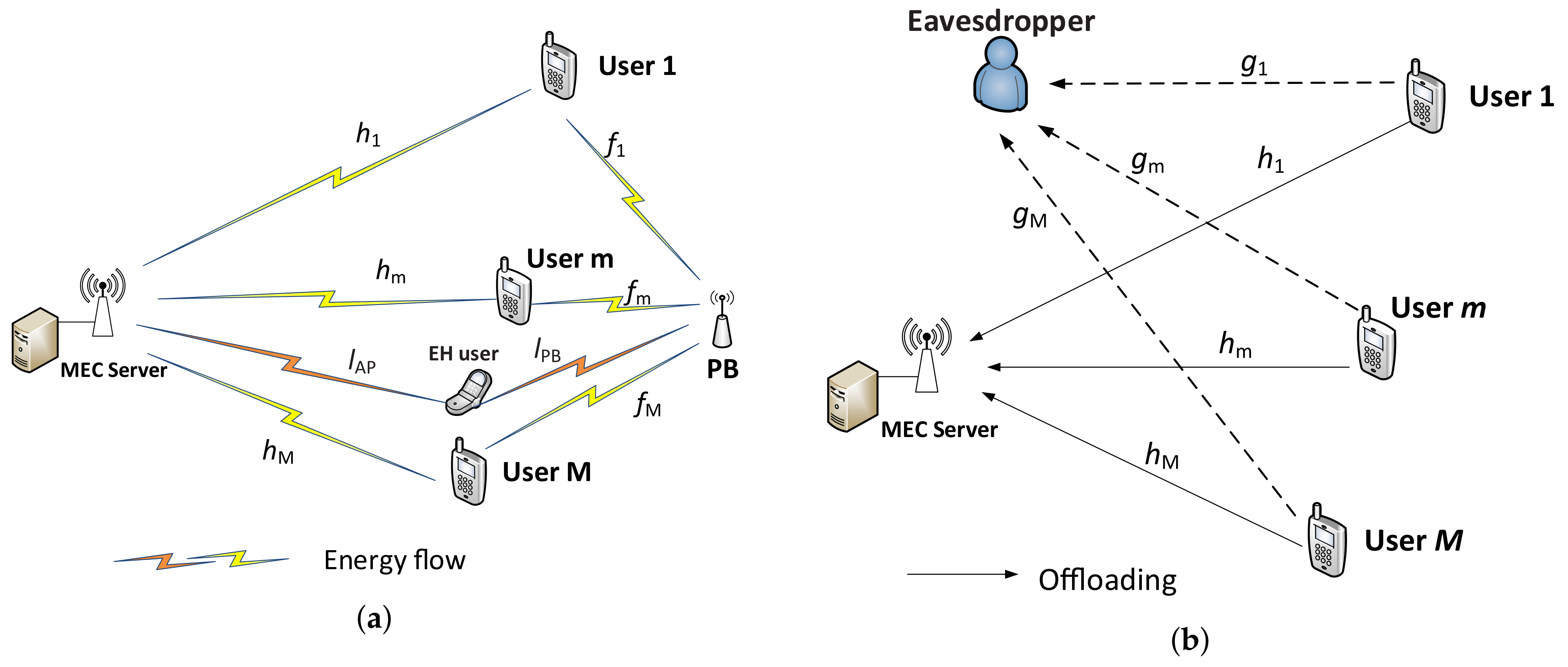
We study a wireless-powered multi-user NOMA-enabled MEC system assisted by a PB in the presence of an eavesdropper, as illustrated in Figure 1, where the AP provides the WPT service for M users and a nonlinear EH user. The AP integrates the MEC server and an RF energy transmitter. Moreover, each user device contains an energy-harvesting circuit and a rechargeable battery that is able to store the collected energy for its operations. It is assumed that the communications and power transferred from the PB and the AP are sent over the same frequency band and that all nodes are equipped with a single antenna, similar to the research in [11,19,20]. In this paper, we consider partial offloading. Note that local computations and the downlink WPT transmission from the AP and PB can be performed simultaneously, but the uplink offloading operation and downlink WPT cannot be simultaneously executed [11,21,22,23,24].
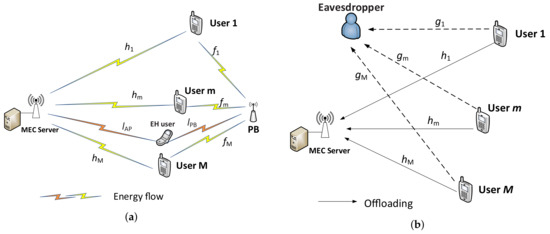
Figure 1.
System model of the wireless-powered non-orthogonal multiple access (NOMA)-enabled mobile edge computing (MEC) system. (a) First phase (for wireless power transfer). (b) Second phase (for offloading).
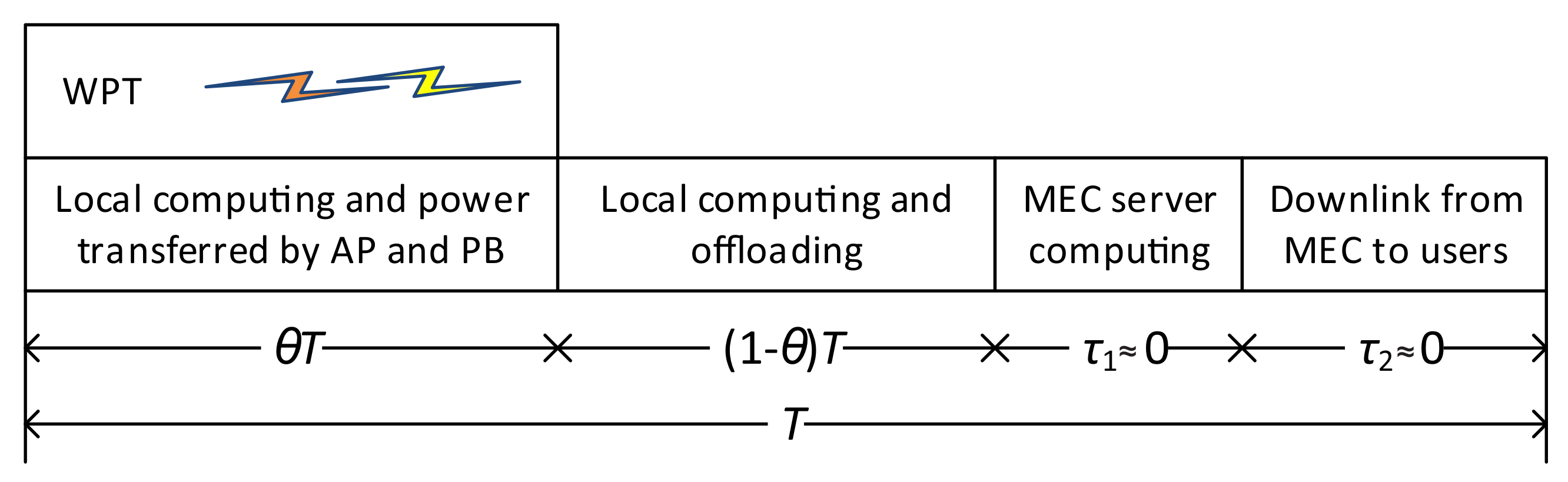
The transmission frame duration, T, illustrated in Figure 2, is based on four phases. First, the AP and the PB broadcast the RF energy to charge the M users and the EH user during the first phase, with duration , . Then, users offload tasks to the MEC server by employing NOMA during the second phase, over duration . In the third and fourth phases, respectively, the MEC server carries out the computation tasks and downloads the computation outcomes. To that end, computation time and downloading time belonging to the MEC server are omitted, as the MEC server is considered to have a stronger computation capability than the users, and the number of bits corresponding to the results of the tasks is negligible [16,19,20,21,22,23,24].
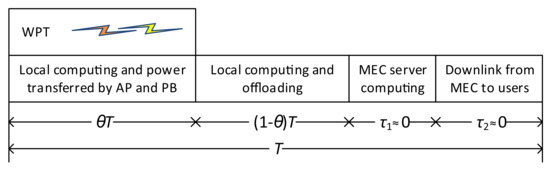
Figure 2.
Frame scheme of the wireless-powered NOMA-MEC network.
The baseband equivalent channels from the AP and PB to NOMA users are defined as and respectively. Meanwhile, the channel from each of the m users to the eavesdropper is defined as . It is understood that the same channel, , is used for both uplink and downlink due to channel reciprocity [11]. Moreover, we consider the noise variance of the MEC server and the eavesdropper to be the same, denoted as
In this paper, we consider a practical non-linear EH model based on the work in [16,25], which was subjected to experimental evaluations to validate effectiveness. In particular, the proposed EH model satisfies the sensitivity property, which states that when the input RF power does not exceed the sensitivity boundary, the harvested energy is zero. This differs from the works in [10,11,12,19,20,21,22,23,24] that employed the ideally linear EH model. Accordingly, the energy harvested by the m–th user is given by
where and are the transmit power from the AP and the PB, respectively. represents the maximum harvested power of the m–th user, ; is the sensitivity boundary; and are the control parameters for the steepness of the function; and selects the bigger value of x and 0. Based on the work in [16,23], the aforementioned parameters were set to
In addition, we consider the EH user to be a sensor node that is regularly powered by a battery with a limited lifetime [26]. Similar to the m-th user, the EH device follows a non-linear EH model and is expressed as follows,
where and are the channels to the EH user from the AP and PB, respectively.
2.1. Local Computing Mode
Each m-th user is able to compute tasks and harvest energy simultaneously, as the computing unit and the energy harvesting circuit are separate [16,27]. This means that the entire frame can be used for local computing. The number of CPU cycles required to compute one bit of raw data at the m-th user is denoted as . Let denote the CPU frequency (in cycles per second) of the m-th user, which should be lower than the maximum computation speed, i.e., . The effective capacitance coefficient of the processor’s chip is denoted by . Then, the energy consumption of the local computing mode can be expressed as , where represents the computation time of the m-th user, . Thus, the number of locally computed bits for the m-th user in local computing mode is defined as the amount of bits processed in the time frame considered, given by
To secure sustainable operation for the m-th user, the utilized energy should not exceed that of the harvested energy, i.e.,
2.2. Partial Offloading Mode with NOMA
As we consider partial offloading to be separate from local computing, each user can offload tasks to the AP after completing the period for harvesting energy, so the period can be utilized for offloading. On uplink, multiple users apply the NOMA transmission strategy to offload their computation tasks simultaneously. Following the processes in [11,16], included in the offloaded task of the m-th user is communications overhead (represented by ), such as a packet header, and it is greater than 1, i.e., . Without loss of generality, the distance between the m-th user and the AP is considered to be sorted as follows, and then channel gain is in descending order: . According to NOMA principles for uplinks employing successive interference cancellation (SIC) techniques, the decoding process is in descending order of channel power, as the received signal power that belongs to the stronger channel’s user corresponds to the M-th user, which is decoded first at the AP and contains interference from all users with relatively weaker channel conditions. Thus, the secrecy offloading computation of the m-th user is given by the total number of computed bits at the MEC server minus the total number of computed bits at the eavesdropper, and can be expressed as follows,
where means the higher value between x and zero, B represents the channel bandwidth, denotes the power of additive white Gaussian noise (AWGN), and denotes the transmission power for the m–th user.
The offloading consumed power indicated in Equation (5) considers the amplifier coefficient, the consumed power during the first phase for receive-signal processing, and the constant circuit power consumption for transmit signal processing, which are denoted as , , and , respectively [16]:
The SCE of the proposed NOMA-enabled MEC WPT system is defined as the ratio of total computed bits to power consumption in both modes, i.e., local computing and offloading mode [2,16], as follows,
2.3. Offloading Mode with TDMA
For comparison purposes, we describe the system model of the TDMA benchmark scheme in which time resource has to be divided among the M users. Let the offloading time for the m-th user be denoted as . Then, the corresponding secrecy computed bits can be given by
Consequently, the offloading SCE of each user is given by
3. SCE Maximization in Wireless-Powered MEC Systems with an EH User
3.1. Problem Formulation of Partial Offloading Mode in the NOMA-MEC System
In this paper, we develop a low-complexity resource allocation scheme based on the PSO algorithm for SCE maximization in a wireless-powered NOMA-MEC system with a nonlinear EH user and in the presence of an eavesdropper. Specifically, period , local computing CPU frequency , computation time , and power allocation are jointly optimized variables subject to the following constraints,
where constraint C1 indicates the minimum computed bits required by the m-th user, and this value is targeted by . Constraint C2 indicates that the total consumed energy by the m-th user for partial offloading cannot exceed the harvested energy. Constraint C3 establishes the maximum CPU frequency for each user, while constraint C4 indicates that power allocation should be higher than zero. Constraint C5 indicates the minimum harvested energy by the EH user, and this target value is represented by . Constraints C6 and C7 define the boundaries for the local and offloading computing times, respectively.
3.2. Problem Formulation of Fully Offloading Mode in the NOMA-MEC System
For comparison purposes, the problem formulation for fully offloading was developed. In offloading mode, local computing is omitted, and problem formulation P2 is given as follows,
3.3. Problem Formulation of Partial Offloading Mode in the TDMA-MEC System
SCE maximization is formulated as follows when partial offloading mode is applied in the TDMA-MEC baseline scheme,
where constraints C3 and C4 define the limits for offloading time, which cannot be longer than , and cannot exceed 1.
4. PSO-Based Resource Allocation Scheme for SCE Maximization
In this paper, we consider a low-complexity resource-allocation scheme based on PSO to maximize the SCE in the proposed wireless-powered MEC network. The PSO-based algorithm has been applied to various optimization problems in the engineering field because it provides high precision and low computational complexity. This optimization technique focuses on achieving an approximately optimal solution by iteratively updating each particle’s position, which leads to the global and local best positions. The position of each particle corresponds to the variables to be optimized. The global best position corresponds to the particle that achieves the best yield in the swarm, while the local best position corresponds to the position that achieves the best yield for that particle. In this context, the global best position is achieved by the particle position that gets the highest value for SCE.
In the following sections, we describe the development of the PSO algorithm for the proposed NOMA-MEC system and the baseline schemes, such as the TDMA-MEC system and the fully offloading MEC system.
4.1. PSO-Based Algorithm for Partial Offloading in the NOMA-MEC System
In the proposed NOMA-MEC system, the s-th particle’s position is given by the set of variables to be optimized, as follows,
where , in which S indicates the number of particles in the swarm, and , , , represent the resource variables , , , and , respectively. Then, we define the search region of the s-th particle according to the boundaries belonging to each variable. For instance, the lower boundary for period is given by (28) and is calculated based on constraint (14):
The lower boundary for transmission power variable is given by (29) and is calculated based on constraint (10):
The lower boundary for variables and are obtained based on constraint (10) as follows,
and
The upper boundary of variable is given by (32), based on constraint (10):
The upper boundary of power allocation variable is denoted as , and the upper boundaries for and are and T under constraints (12) and (15), respectively. Therefore, each particle’s position represents a vector of elements, , for which the limits are , , , and , respectively. The initial values of the s-th particle’s positions are randomly initialized based on the uniform distribution between these limits established for each particle’s position.
Moreover, a penalty function based on objective function of problem P1 is used to deal with the constraint as follows,
where the penalty value is denoted as , and is the i-th constraint of problem P1 corresponding to (10), (11), and (14). In addition, the function based on constraint means that the i-th constraint is satisfied; otherwise, .
Furthermore, the procedures of the proposed PSO-based algorithm to solve SCE maximization problem P1 are described in Algorithm 1, where the input parameters for PSO are the maximum number of iterations, the number of particles in a swarm, the inertia weight for velocity updates, and the cognitive and social parameters, which are denoted as , S, , , and , respectively. The initial values of the m-th particle’s velocities are randomly initialized between the boundaries established for each particle’s position: , , , and . Accordingly, in each successive b-th iteration, the velocity of each s-th particle is updated towards the relative global best position, , and the local best position, , as follows,
where and are random numbers between zero and one.
The update of the particle’s position is based on the current particle’s position plus the corresponding updated velocity. Therefore, the s-th particle’s position is updated as follows,
In this paper, the low-complexity PSO-based optimization technique allows us to find the best values of the variables and to maximize the SCE by iteratively updating the global and local best particle positions until reaching the stopping criterion.
Regarding the computational complexity of the PSO algorithm in solving problem P1, it is necessary to compute the number of iterations used and the number of particles in the swarm. Therefore, the total complexity is given by . We highlight the fact that matrix operations are not needed to solve the proposed optimization problem.
| Algorithm 1: PSO-based algorithm to solve SCE problem P1. |
 |
4.2. PSO-Based Algorithm for Fully Offloading in the MEC
The procedure of the PSO-based algorithm in the fully offloading MEC system is developed in a way similar to that described in Algorithm 1. However, in this case, each particle’s position represents a vector of elements, , for which the limits are , , respectively. These boundaries are indicated as follows,
4.3. PSO-Based Algorithm for Partial Offloading in the TDMA-MEC System
In the TDMA-MEC system, a particle’s position is composed of the following elements: . Thereby, the search space is established according to the following limits,
Then, the procedure to apply the PSO algorithm is similar to that expressed in Algorithm 1.
5. Numerical Results
In this section, we numerically evaluate the performance of our proposed wireless-powered NOMA-MEC system with an EH user and PB. The simulations were programmed in Matlab (R2020a, The MathWorks, Inc., USA) by utilizing a Core i7-6700K CPU with 16 GB of main memory. In addition, the application of TDMA and fully offloading mode are considered baseline schemes to be evaluated and compared with our proposed scheme. The results presented in this paper were averaged over 50 independent channel realizations. In addition, the PSO algorithm was executed ten times for each channel realization, where the average value was used to evaluate the results.
In the considered work, the channels follow circularly symmetric, complex Gaussian random variables as follows, , , , , and , where denotes the distance between node i and j and the path-loss exponent is denoted by v. The distances between the nodes were , , , , , , , and , in meters. Moreover, the simulation parameters listed in Table 1 were chosen based on the work in [16,18,25,26,27,28,29,30,31]. Specifically, the parameters for the nonlinear EH model such as the maximum EH power, sensitivity threshold, circuit parameters were chosen based on the work in [16,25], the communication bandwidth, the minimum computation bits, the number of cycles for one bit, the amplifier coefficient, the constant circuit power were selected based on the work in [16] and the maximum cycles per second was selected based on the work in [26,27].

Table 1.
Simulation parameters.
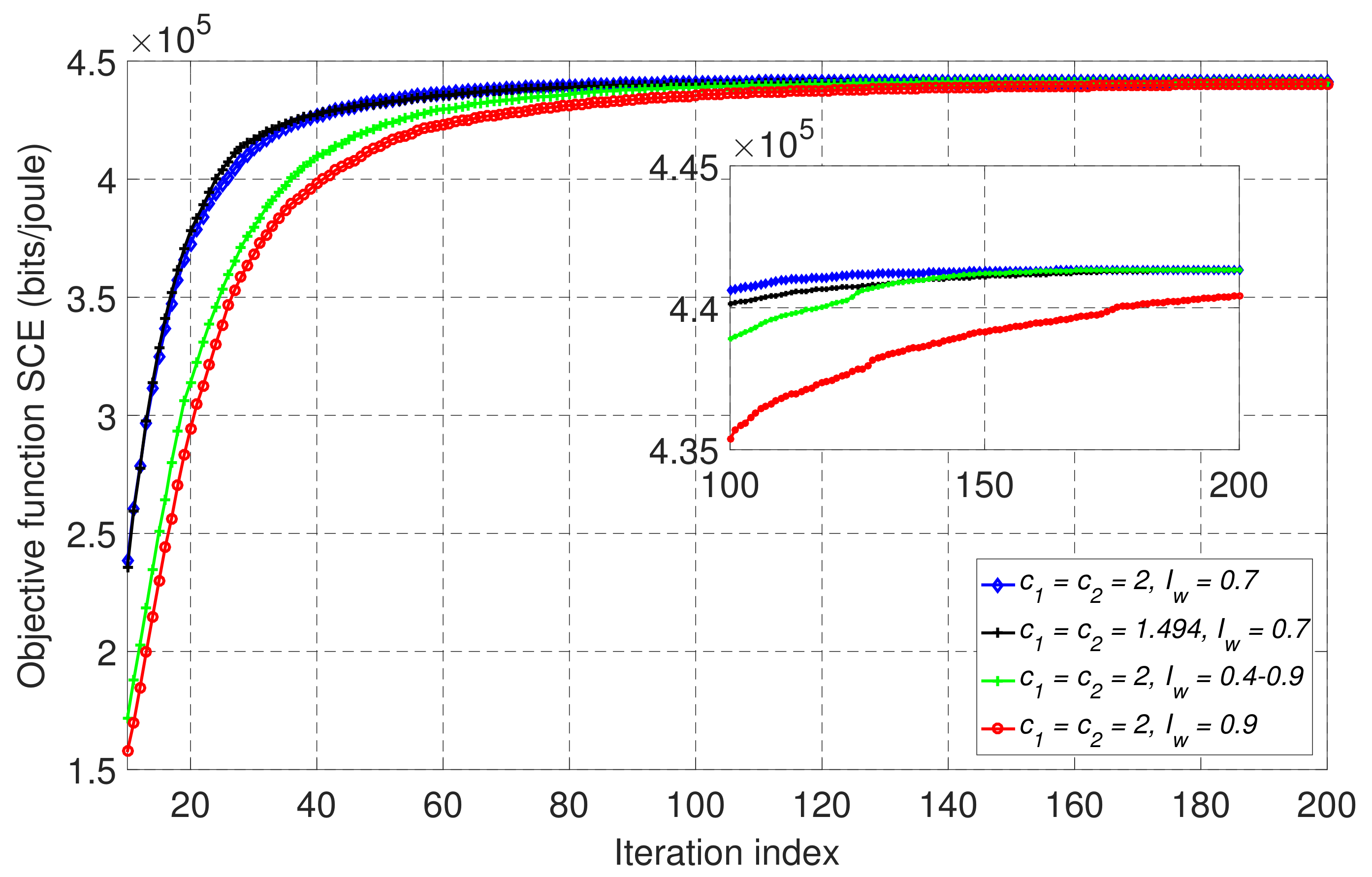
The simulation parameters for PSO are selected based on the works in [18,28,29,30,31] which frequently provide good converge behavior. In addition, simulations were carried out to set the suitable PSO parameters such as inertia weight for velocity update, cognitive and social parameters. Figure 3 shows the convergence of the PSO algorithm of our proposed scheme in partial offloading mode with four different combinations of the inertia weight, cognitive and social parameters where typical values in the literature [18,28,29,30,31] are used. For instance, in [30], the linear decreasing inertia weight is established as , where , , t is the current iteration and is the maximum number of iteration. In addition, we set the number of particles S = 40, cycles/s, , and the rest of the simulation parameters were as indicated in Table 1. We can observe that the case with and achieves the fastest convergence among all the cases. Then, we set and for the rest of the simulations.
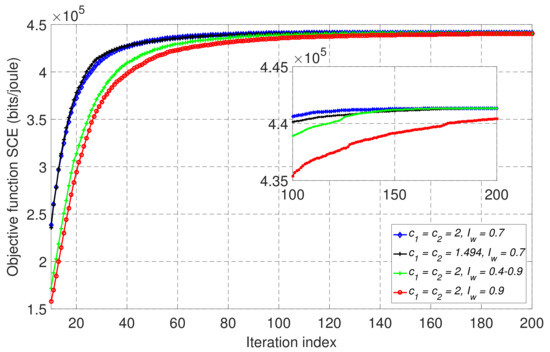
Figure 3.
The convergence behavior of the proposed PSO-based algorithm for different combinations of the inertia weight, cognitive, and social parameters.
In [32], the authors proposed some initialization strategies for the particles’ positions in PSO, such as the logarithmic and normal distributions. In the case of the logarithmic, the position of the particle for the variable is initialized as ), where rnd is a random number from the uniform distribution in [0, 1). In the case of the normal, the position of the particle for the variable θ is initialized based on the normal distribution with mean and the standard deviation between 1 to 5. From the numerical simulations with a number of particles S = 40 and Imax = 200, we obtain a SCE value of 441,342.39 bits/joule for the uniform distribution (used in the proposed approached), a SCE value of 423,160.11 bits/joule with the logarithmic strategy, and a SCE value of 436,509.85 bits/joule for the normal distribution with a standard deviation of 5. We conclude that the uniform distribution strategy achieves a better SCE than the other initialization strategies.
Next, we present the PSO convergence behavior with ten runs of the PSO algorithm by using a different number of particles for each scheme, i.e., the TDMA baseline scheme and the wireless-powered NOMA-MEC system in partial offloading mode and fully offloading mode, with the simulation parameters indicated in Table 1.
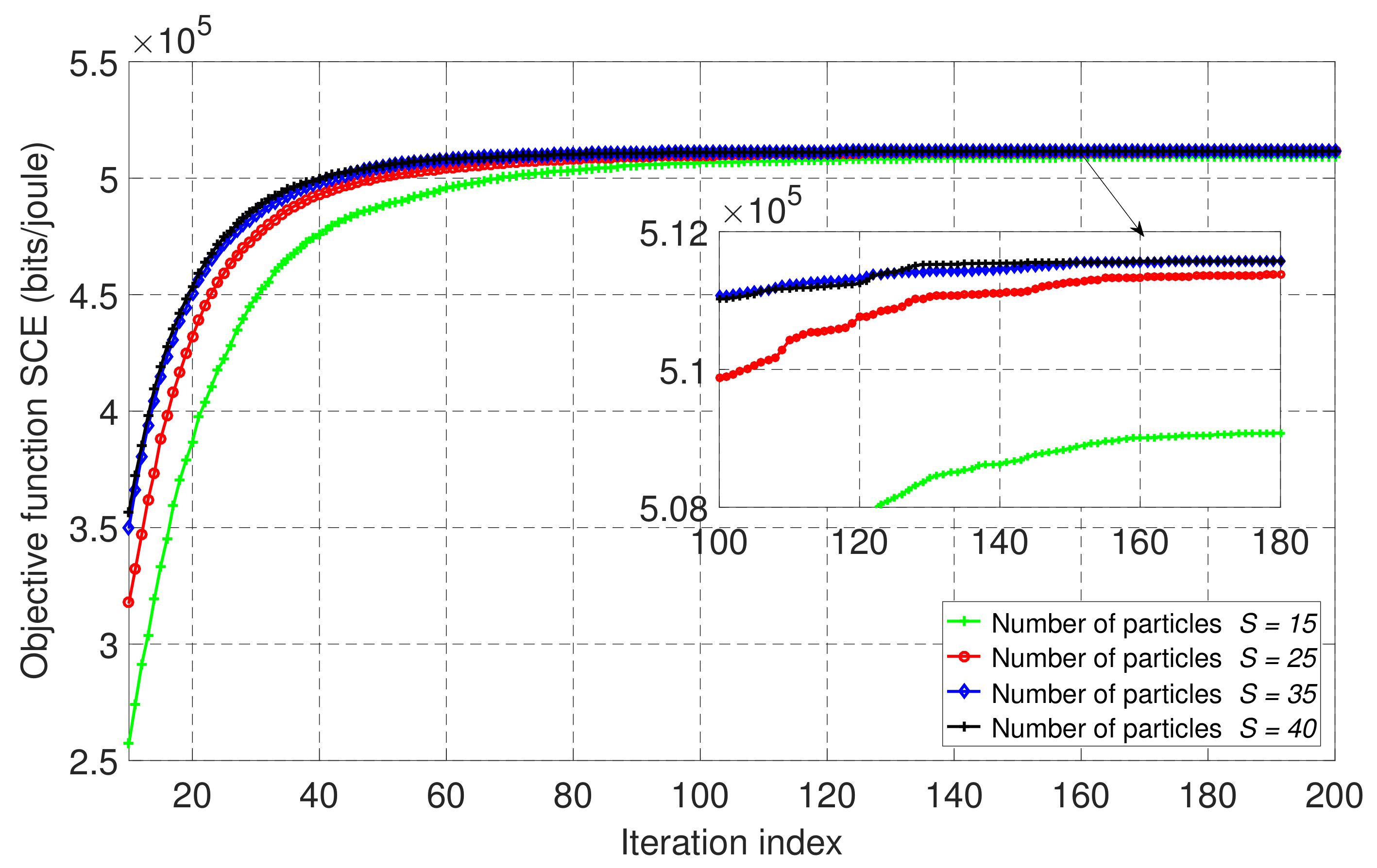
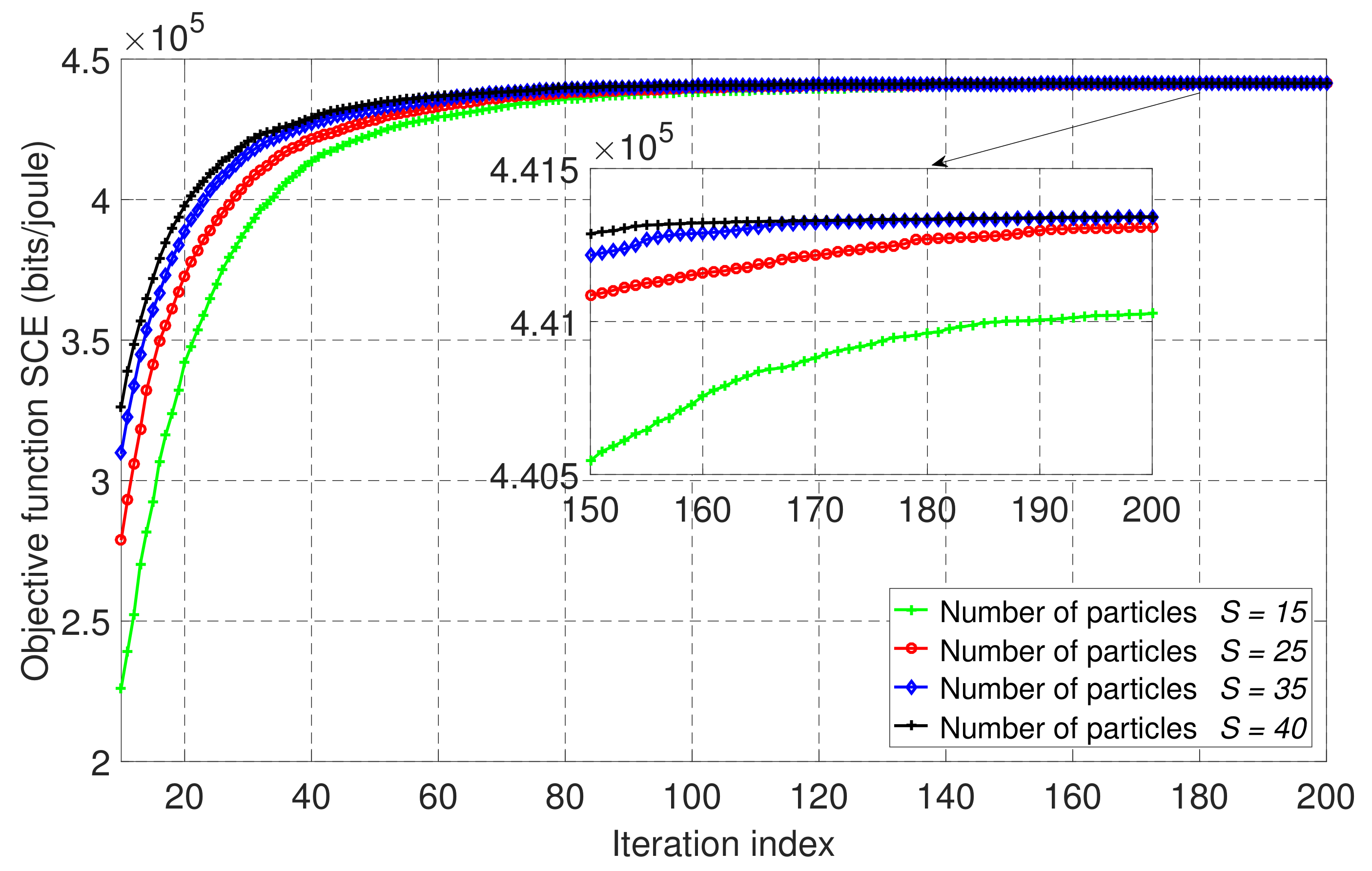
Figure 4 shows the convergence of the PSO algorithm given in Algorithm 1 for our wireless-powered NOMA-MEC system with an EH user and PB, based on four different numbers of particles, , and with . The rest of the simulation parameters were as indicated in Table 1. We can see that the performance of the SCE was enhanced as the iteration index and the number of particles increased. Moreover, we observe that the SCE achieved steady behavior after about 100 iterations. However, as we reached a greater number of particles and iterations, the computational complexity increased, as each particle evaluated the objective function and constraints for a total time equal to the maximum number of iterations.
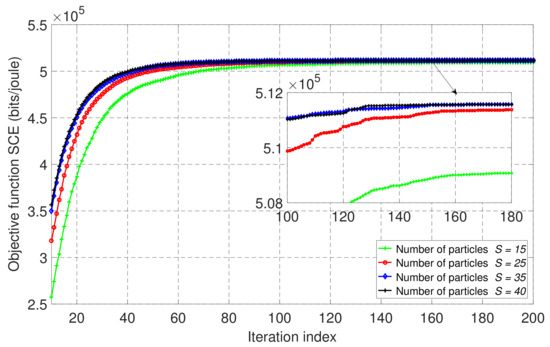
Figure 4.
The convergence behavior of the proposed PSO-based algorithm with different numbers of particles, S, in the proposed wireless-powered NOMA-MEC system for partial offloading mode when .
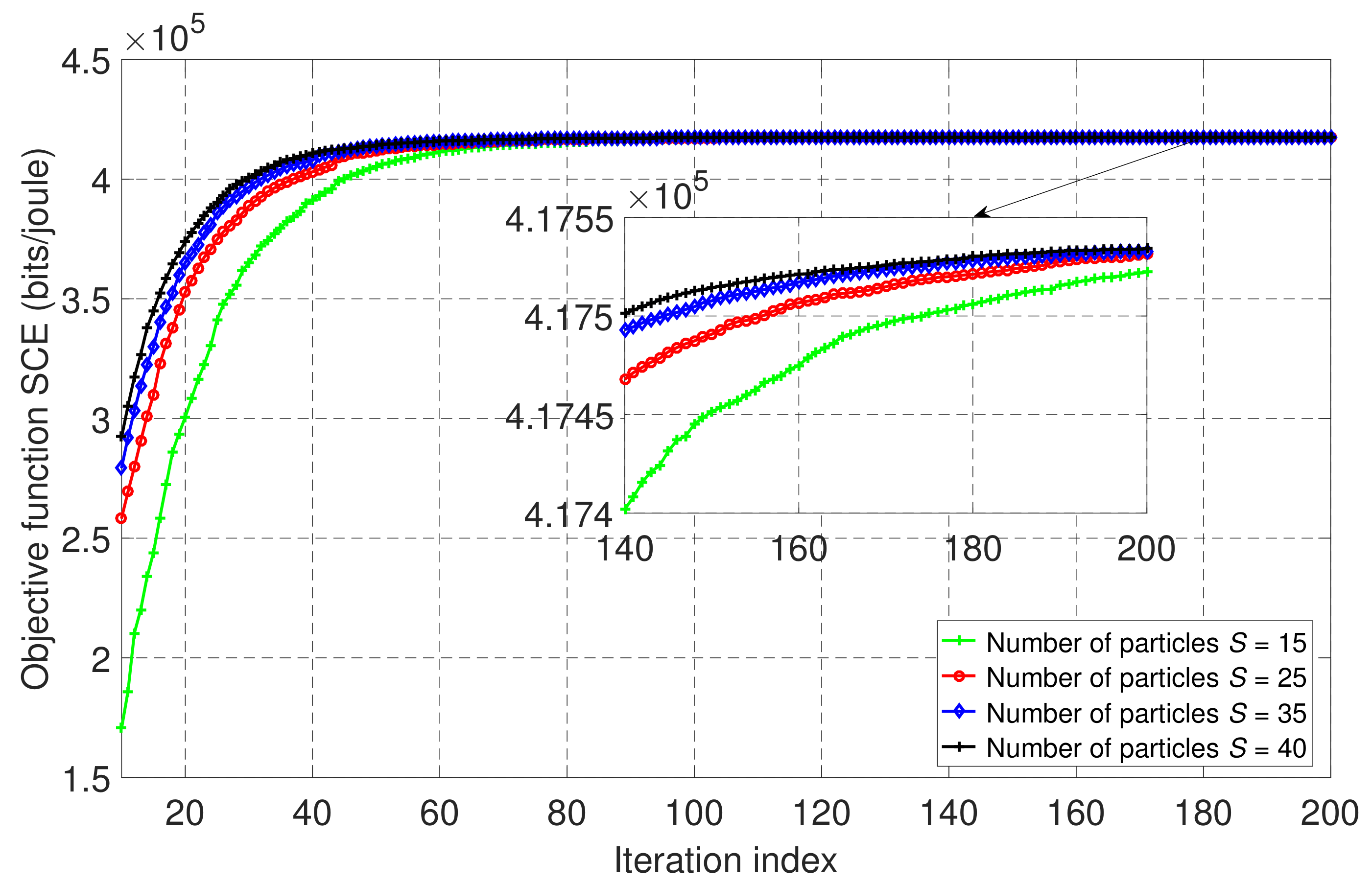
Similar to Figure 4, Figure 5 shows the convergence of the PSO algorithm of our proposed scheme in partial offloading mode with four different numbers of particles, . In this case, we set the value of the maximum CPU frequency parameter at to verify the convergence of our proposed scheme in a different scenario. From Figure 5, we can see that the SCE showed stable behavior from around 100 iterations, and its highest performance was achieved at . In order to select a suitable value for the number of particles and the maximum number of iterations, we have analyzed the computation time of the PSO algorithm and the other baseline schemes. Then, in Table 2, we have compared the incidence for the number of particles in terms of the relative error and computation time of our proposed scheme, NOMA-MEC in fully offloading mode, and those of TDMA-MEC system. To compute relative error, we set the one obtained by using as the true value for each scheme as this value is correspondent to the highest SCE, and the computation time was calculated with 200 as the number of iterations for the proposed scheme and fully offloading mode. On the other hand, the computation time for the TDMA-based scheme was evaluated with 400 iterations. As a result, we can see that the higher number of particles entails the lower relative error at the expense of a longer computation time. Therefore, we set and for further simulations of our proposed wireless-powered NOMA-MEC system.
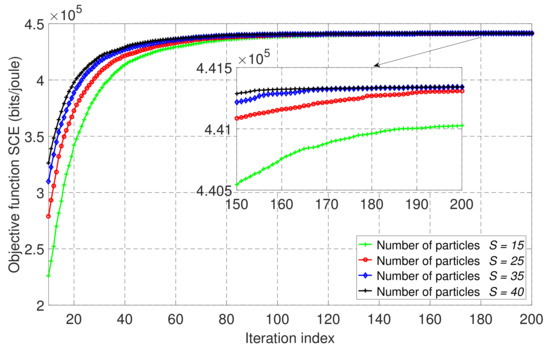
Figure 5.
The convergence behavior of the proposed PSO-based algorithm with different numbers of particles, S, for the proposed wireless-powered NOMA-MEC system in partial offloading mode with .

Table 2.
Effects of the number of particles on PSO.
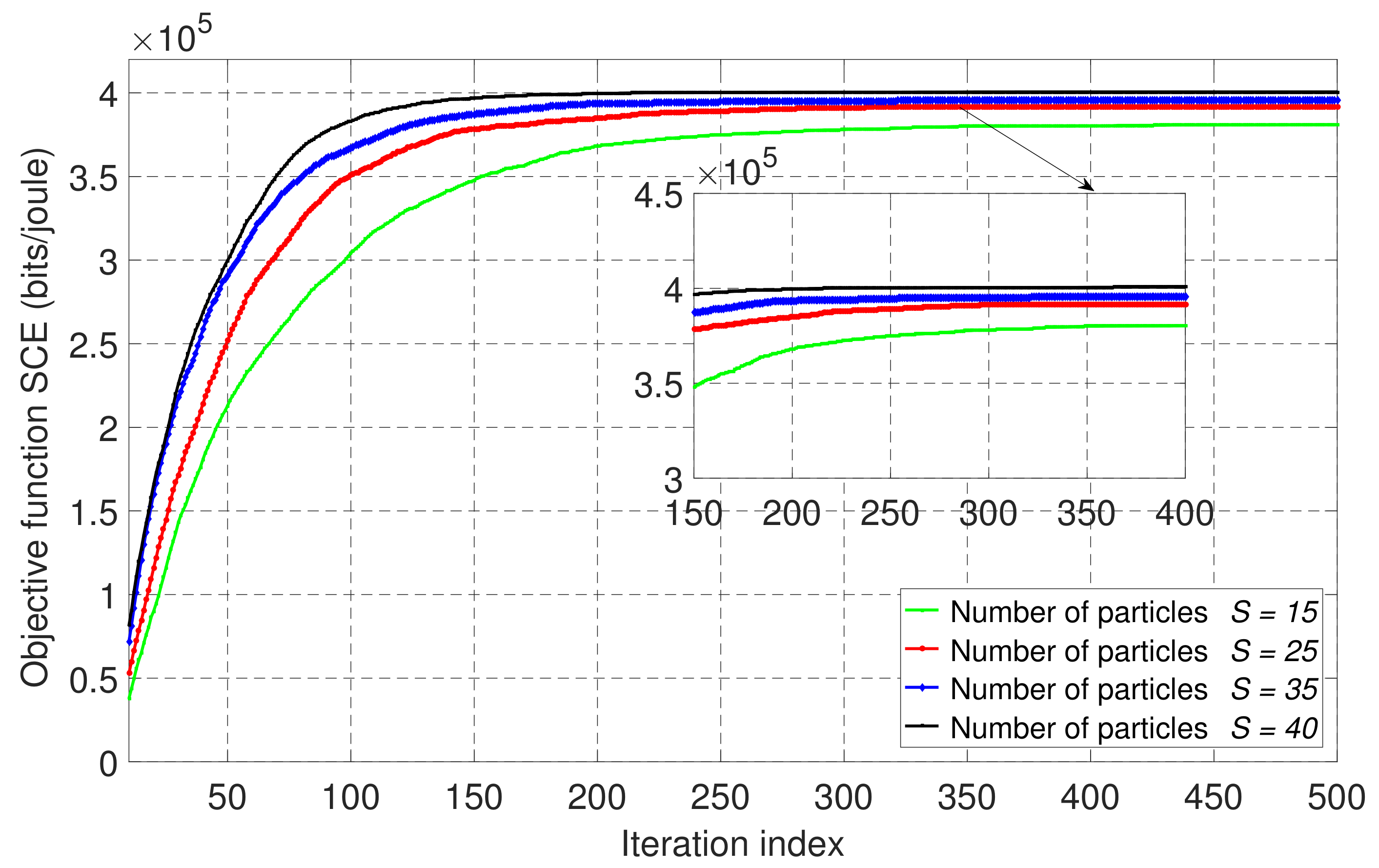
Figure 6 shows the convergence of the PSO algorithm for the wireless-powered NOMA-MEC system in fully offloading mode in accordance with four different numbers of particles, and with . From Figure 6, we can see that the SCE is converged after iteration 180, and its highest performance was achieved with 40 particles, followed slightly by using 35 particles. However, the larger number of particles, the longer the computation time required to complete the process of the PSO algorithm, as shown in Table 2. Therefore, we used and for the simulations performed in the NOMA-MEC system with the fully offloading scheme.
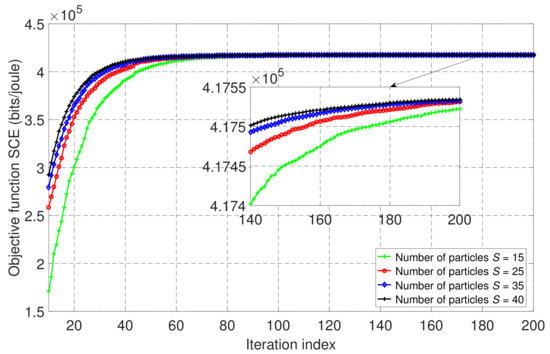
Figure 6.
The convergence behavior of the proposed PSO-based algorithm with different numbers of particles, S, for the wireless-powered NOMA-MEC system in fully offloading mode when .
Figure 7 shows the convergence of the TDMA-MEC system baseline scheme in partial offloading mode. From Figure 7, it is observed that the SCE can be stable after 600 iterations. It is noteworthy that the required number of iterations for convergence of SCE in the TDMA-MEC scheme was higher than those of the previous schemes since an extra variable for offloading time, , needs to be optimized to solve the optimization problem in the TDMA-MEC scheme, as shown in problem P3. Moreover, the SCE performance reached a higher value with . Thus, we used the tradeoff values of and for simulations of the TDMA-MEC baseline system in partial offloading mode.
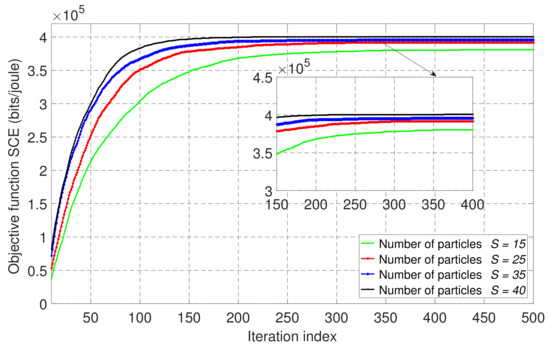
Figure 7.
The convergence behavior of the proposed PSO-based algorithm with different numbers of particles, S, for the wireless-powered TDMA-MEC system in partial offloading mode when .
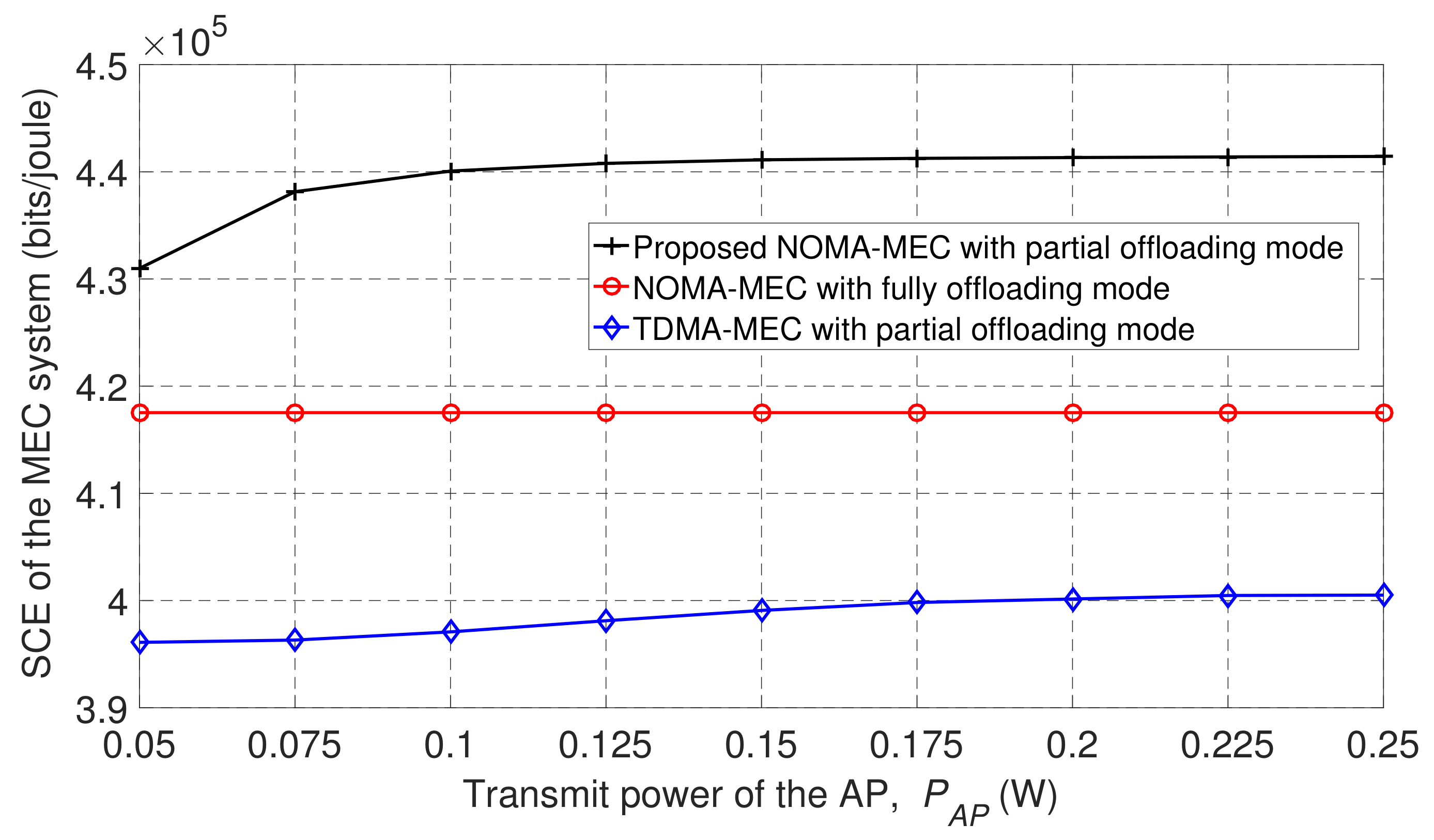
Figure 8 shows a comparison of SCE performance from our proposed scheme applying NOMA in the wireless-powered MEC system in partial offloading mode, from the NOMA-enabled MEC system in fully offloading mode, and from the TDMA-MEC scheme in partial offloading mode. In Figure 8, observe that the NOMA-assisted MEC system outperformed the baseline schemes. We can particularly see that the proposed scheme had a much better SCE performance than that obtained by the conventional TDMA-MEC scheme. This is because only one phase is required to offload the tasks from the users to the MEC server in our proposed NOMA-MEC scheme, where the same time interval can be shared by all users. Thus, resources are efficiently used. Using TDMA in the MEC system, more resources are employed to complete offloading the computation tasks, since each user offloads to the MEC server at different times. Accordingly, the eavesdropper has more opportunities to trap messages that are transmitted in the wireless environment. Therefore, the SCE in the TDMA-MEC system was lower than that achieved in the proposed NOMA-MEC system.
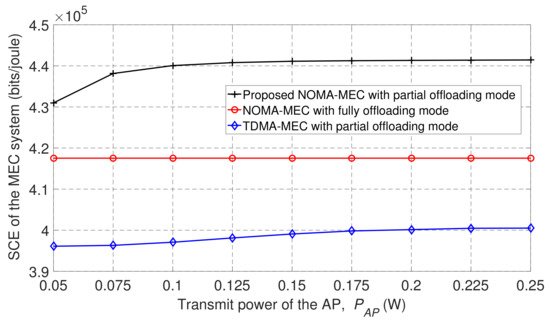
Figure 8.
Secure computation efficiency (SCE) based on the transmission power of the wireless AP.
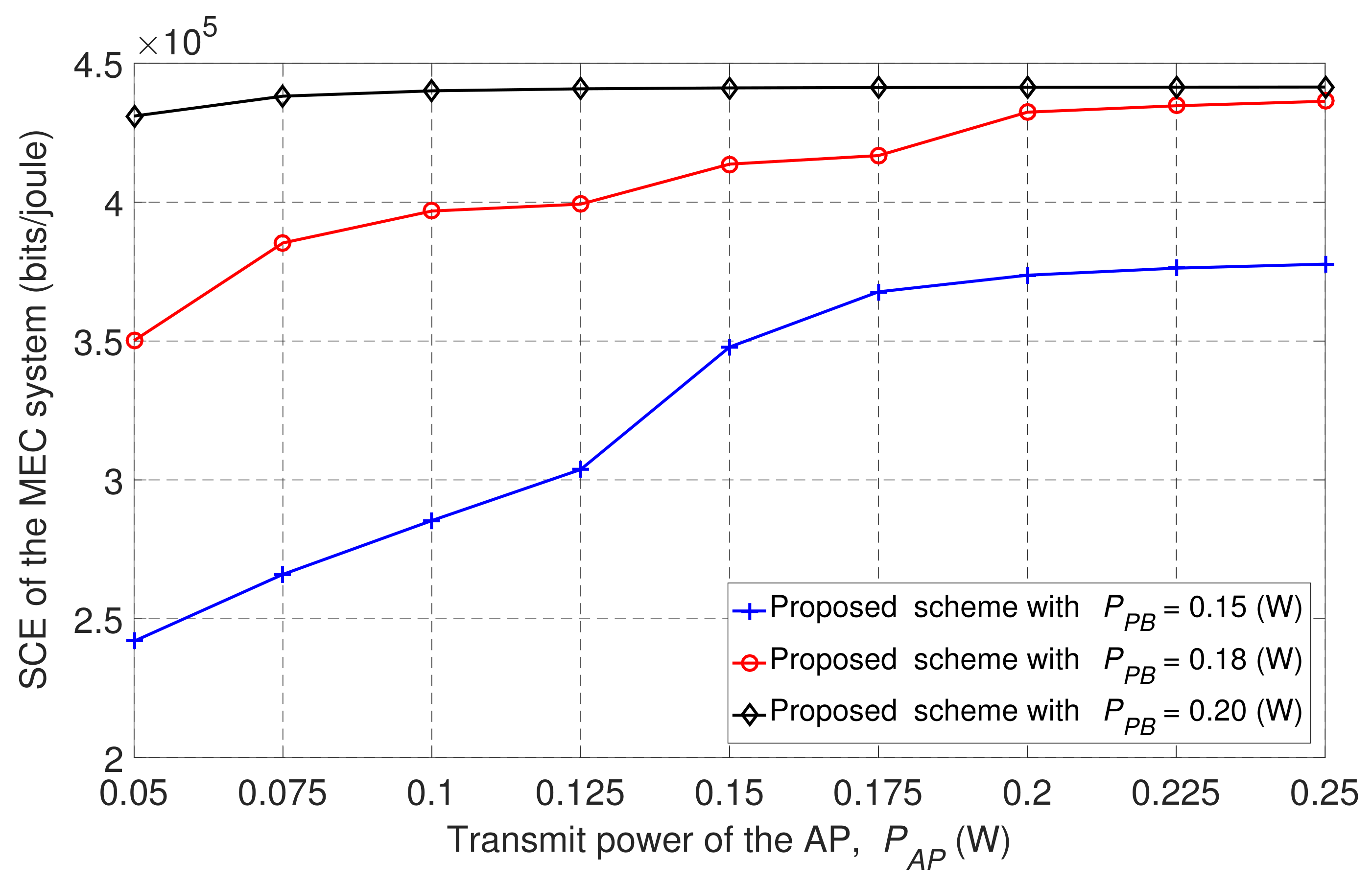
Figure 9 shows the SCE achieved with three different values for transmission power . We can see that the SCE performance increased as the transmission power of the AP and PB increased. This is because when transmission power increases, users can harvest a greater amount of energy to be used in the local computing and offloading processes.
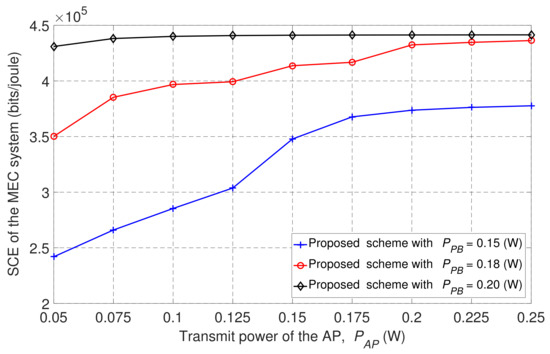
Figure 9.
SCE based on transmission power of the wireless AP at different transmission power levels for the PB.
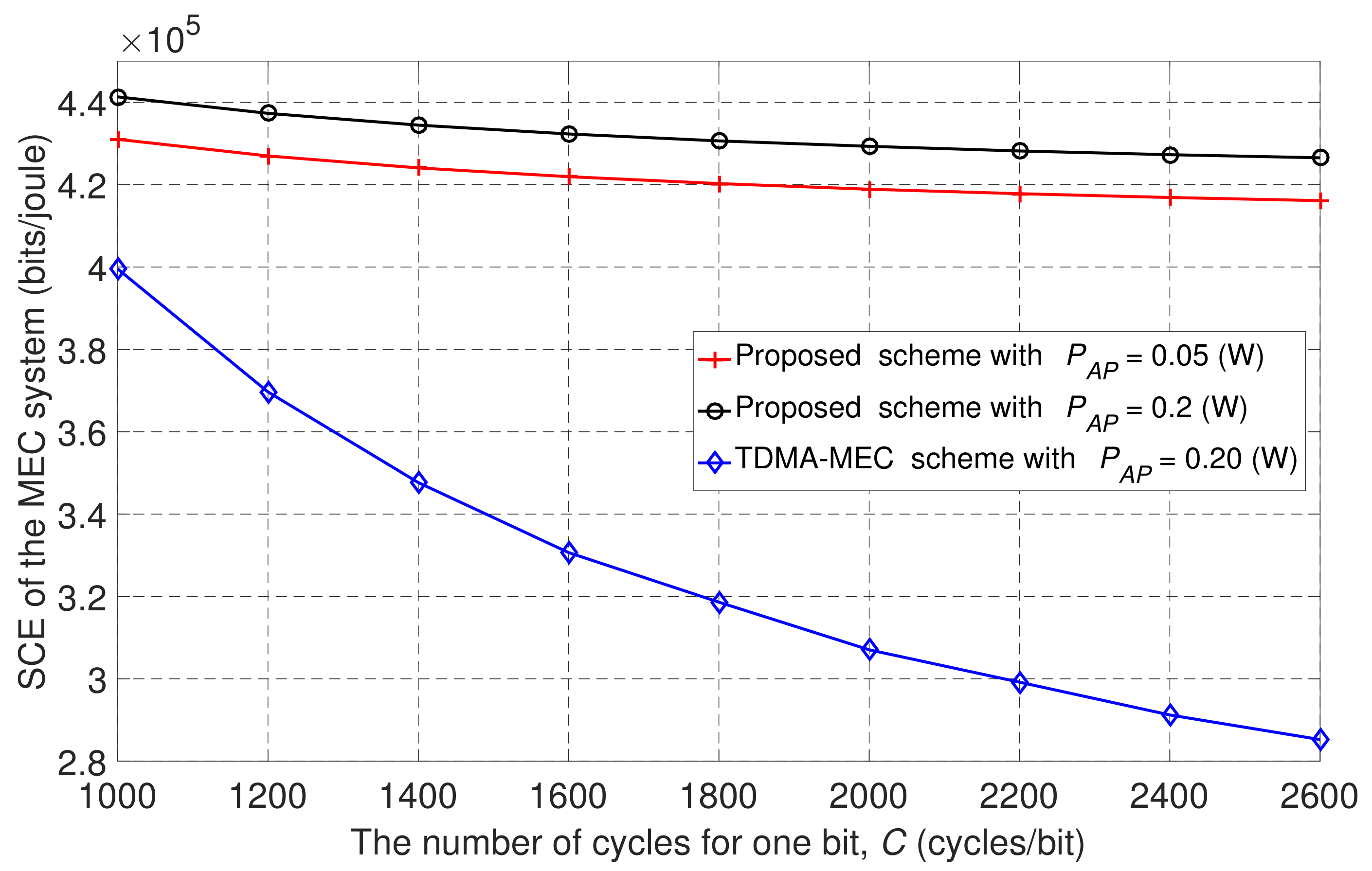
Figure 10 shows the SCE versus the number of cycles for one bit, , for the TDMA-MEC baseline scheme and the proposed scheme with two different transmission power levels at the AP. From Figure 10, we can observe that the SCE performance decreased as C increased. This is because the relation between the number of locally computed bits of the m-th user in local computing mode, , is inversely proportional to , i.e., decreases as C increases. This relation is indicated in Equation (3). The main objective in this paper is to maximize the SCE, and it depends directly on . Consequently, if decreases, the SCE performance also decreases. Moreover, from Figure 10, we verify that our proposed scheme outperforms the TDMA-MEC baseline scheme, and SCE is enhanced with higher values for the wireless power transmitted from the AP to users.
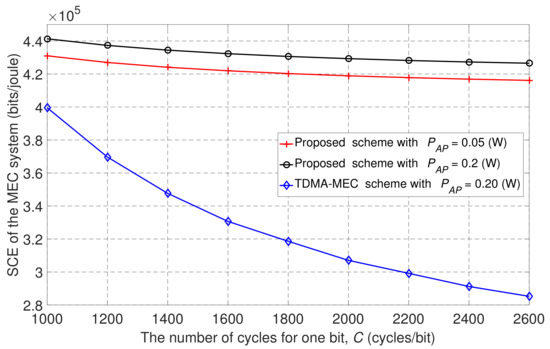
Figure 10.
The SCE versus the number of cycles for one bit, C, at different transmission power levels of the AP.
6. Conclusions
In this paper, we considered a wireless-powered NOMA-enabled MEC system assisted by a PB, with an EH user, and in the presence of an eavesdropper. The objective is to maximize the SCE under the constraints of minimum computation bits required by the users, minimum EH required by the EH user, and a limitation on the consumed energy. We proposed a low-complexity approach based on the PSO algorithm, and achieved high performance with a low computation time. Simulation results demonstrated the superiority of the proposed scheme in comparison with fully offloading mode and TDMA-based mode. The advantages of the NOMA technique were proved, compared with the TDMA method, where NOMA permits more efficient utilization of the spectrum resources. Moreover, numerical results showed that the presence of a low-cost and low-complexity PB allows us to improve the SCE in the studied scenarios.
Author Contributions
C.E.G. conceived and proposed the research idea. All authors designed the experiments. C.E.G. performed the experiments. C.E.G., M.R.C., and I.K. analyzed the experimental results. C.E.G. wrote the paper under the supervision of I.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the National Research Foundation of Korea (NRF) through the Korean Government and the Ministry of Science and ICT (MSIT) under Grant NRF-2018R1A2B6001714.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Garcia, C.E.; Camana, M.R.; Koo, I.; Rahman, M.A. Particle Swarm Optimization-Based Power Allocation Scheme for Secrecy Sum Rate Maximization in NOMA with Cooperative Relaying. In Proceedings of the 2019 International Conference on Intelligent Computing (ICIC), Nanchang, China, 3–6 August 2019. [Google Scholar]
- Lin, H.; Cao, Y.; Zhong, Y.; Liu, P. Secure Computation Efficiency Maximization in NOMA-Enabled Mobile Edge Computing Networks. IEEE Access 2019, 7, 87504–87512. [Google Scholar] [CrossRef]
- Wu, W.; Zhou, F.; Hu, R.Q.; Wang, B. Energy-Efficient Resource Allocation for Secure NOMA-Enabled Mobile Edge Computing Networks. IEEE Trans. Commun. 2020, 68, 493–505. [Google Scholar] [CrossRef]
- Ding, Z.; Xu, J.; Dobre, O.A.; Poor, H.V. Joint Power and Time Allocation for NOMA–MEC Offloading. IEEE Trans. Veh. Technol. 2019, 68, 6207–6211. [Google Scholar] [CrossRef]
- Cheng, Q.; Li, L.; Sun, Y.; Wang, D.; Liang, W.; Li, X.; Han, Z. Efficient Resource Allocation for NOMA-MEC System in Ultra-Dense Network: A Mean Field Game Approach. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020. [Google Scholar]
- Kiani, A.; Ansari, N. Edge Computing Aware NOMA for 5G Networks. IEEE Internet Things J. 2018, 5, 1299–1306. [Google Scholar] [CrossRef]
- Wu, W.; Zhou, F.; Li, P.; Deng, P.; Wang, B.; Leung, V.C.M. Energy-Efficient Secure NOMA-Enabled Mobile Edge Computing Networks. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019. [Google Scholar]
- Wu, Y.; Ni, K.; Zhang, C.; Qian, L.P.; Tsang, D.H.K. NOMA-Assisted Multi-Access Mobile Edge Computing: A Joint Optimization of Computation Offloading and Time Allocation. IEEE Trans. Veh. Technol. 2018, 67, 12244–12258. [Google Scholar] [CrossRef]
- Liu, B.; Liu, C.; Peng, M. Resource Allocation for Energy-Efficient MEC in NOMA-Enabled Massive IoT Networks. IEEE J. Sel. Areas Commun. 2020. [Google Scholar] [CrossRef]
- Wang, F.; Xu, J.; Wang, X.; Cui, S. Joint Offloading and Computing Optimization in Wireless Powered Mobile-Edge Computing Systems. IEEE Trans. Wirel. Commun. 2018, 17, 1784–1797. [Google Scholar] [CrossRef]
- Bi, S.; Zhang, Y.J. Computation Rate Maximization for Wireless Powered Mobile-Edge Computing with Binary Computation Offloading. IEEE Trans. Wirel. Commun. 2018, 17, 4177–4190. [Google Scholar] [CrossRef]
- Zhou, F.; Wu, Y.; Hu, R.Q.; Qian, Y. Computation Rate Maximization in UAV-Enabled Wireless-Powered Mobile-Edge Computing Systems. IEEE J. Sel. Areas Commun. 2018, 36, 1927–1941. [Google Scholar] [CrossRef]
- Ji, L.; Guo, S. Energy-Efficient Cooperative Resource Allocation in Wireless Powered Mobile Edge Computing. IEEE Internet Things J. 2019, 6, 4744–4754. [Google Scholar] [CrossRef]
- Wang, F.; Xu, J.; Cui, S. Optimal Energy Allocation and Task Offloading Policy for Wireless Powered Mobile Edge Computing Systems. IEEE Trans. Wirel. Commun. 2020, 19, 2443–2459. [Google Scholar] [CrossRef]
- Camana, M.R.; Tuan, P.V.; Koo, I. Optimised power allocation for a power beacon-assisted SWIPT system with a power-splitting receiver. Int. J. Electron. 2018, 106, 415–439. [Google Scholar] [CrossRef]
- Zhou, F.; Hu, R.Q. Computation Efficiency Maximization in Wireless-Powered Mobile Edge Computing Networks. IEEE Trans. Wirel. Commun. 2020, 19, 3170–3184. [Google Scholar] [CrossRef]
- Huang, K.; Lau, V.K.N. Enabling Wireless Power Transfer in Cellular Networks: Architecture, Modeling and Deployment. IEEE Trans. Wirel. Commun. 2014, 13, 902–912. [Google Scholar] [CrossRef]
- Garcia, C.E.; Camana, M.R.; Koo, I. Secrecy Energy Efficiency Maximization in an Underlying Cognitive Radio–NOMA System with a Cooperative Relay and an Energy-Harvesting User. Appl. Sci. 2020, 10, 3630. [Google Scholar] [CrossRef]
- You, C.; Huang, K.; Chae, H. Energy Efficient Mobile Cloud Computing Powered by Wireless Energy Transfer. IEEE J. Sel. Areas Commun. 2016, 34, 1757–1771. [Google Scholar] [CrossRef]
- Xu, J.; Chen, L.; Ren, S. Online Learning for Offloading and Autoscaling in Energy Harvesting Mobile Edge Computing. IEEE Trans. Cogn. Commun. Netw. 2017, 3, 361–373. [Google Scholar] [CrossRef]
- Mao, Y.; Zhang, J.; Letaief, K.B. Dynamic Computation Offloading for Mobile-Edge Computing with Energy Harvesting Devices. IEEE J. Sel. Areas Commun. 2016, 34, 3590–3605. [Google Scholar] [CrossRef]
- Hu, X.; Wong, K.-K.; Yang, K. Wireless Powered Cooperation-Assisted Mobile Edge Computing. IEEE Trans. Wirel. Commun. 2018, 17, 2375–2388. [Google Scholar] [CrossRef]
- Mao, S.; Leng, S.; Yang, K.; Huang, X.; Zhao, Q. Fair Energy-Efficient Scheduling in Wireless Powered Full-Duplex Mobile-Edge Computing Systems. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Mao, S.; Leng, S.; Yang, K.; Zhao, Q.; Liu, M. Energy Efficiency and Delay Tradeoff in Multi-User Wireless Powered Mobile-Edge Computing Systems. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Wang, S.; Xia, M.; Huang, K.; Wu, Y.-C. Wirelessly Powered Two-Way Communication with Nonlinear Energy Harvesting Model: Rate Regions Under Fixed and Mobile Relay. IEEE Trans. Wirel. Commun. 2017, 16, 8190–8204. [Google Scholar] [CrossRef]
- Wang, Y.; Sheng, M.; Wang, X.; Wang, L.; Li, J. Mobile-Edge Computing: Partial Computation Offloading Using Dynamic Voltage Scaling. IEEE Trans. Commun. 2016, 64, 4268–4282. [Google Scholar] [CrossRef]
- Liu, C.-F.; Bennis, M.; Poor, H.V. Latency and Reliability-Aware Task Offloading and Resource Allocation for Mobile Edge Computing. In Proceedings of the 2017 IEEE Globecom Workshops (GC Wkshps), Singapore, 4–8 December 2017. [Google Scholar]
- Garcia, C.E.; Tuan, P.V.; Camana, M.R.; Koo, I. Optimized Power Allocation for a Cooperative NOMA System with SWIPT and an Energy-Harvesting User. Int. J. Electron. 2020, 107, 1–30. [Google Scholar] [CrossRef]
- Camana, M.R.; Tuan, P.V.; Garcia, C.E.; Koo, I. Joint power allocation and power splitting for MISO SWIPT RSMA systems with energy-constrained users. Wirel. Netw. 2019, 26, 2241–2254. [Google Scholar] [CrossRef]
- He, Y.; Ma, W.J.; Zhang, J.P. The Parameters Selection of PSO Algorithm Influencing on Performance of Fault Diagnosis. MATEC Web Conf. 2019, 63, 2019. [Google Scholar] [CrossRef]
- Parsopodos, K.E.; Vrahatis, M.N. Particle swarm optimization method for constrained optimization problems. In Intelligent Technologies—Theory and Applications: New Trends in Intelligent Technologies; IOS Press: Amsterdam, The Netherlands, 2002; pp. 214–220. [Google Scholar]
- Cazzaniga, P.; Nobile, M.S.; Besozzi, D. The impact of particles initialization in PSO: Parameter estimation as a case in point. In Proceedings of the 2015 IEEE Conference on Computational Intelligence in Bioinformatics and Computational Biology (CIBCB), Niagara Falls, ON, Canada, 12–15 August 2015. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).