A Scheduling Method Based on Packet Combination to Improve End-to-End Delay in TSCH Networks with Constrained Latency
Abstract
1. Introduction
2. Related Work
- ✓
- In [12], the authors proposed a scheduling approach (TEACSA) which is based on the concept of an aggregation tree. A time slot scheduling method is used so this approach minimizes the time required for data gathering by aggregation convergecast. The value of the transmission is determined by the sum of number of children and receiver’s depth. The tree is constructed by appending to it the path which has least overhead in each iteration. To supplement the scheduling algorithm a neighbor degree ranking scheme is implemented to assign time slots to the SNs in an effective manner [17]. It reduces data traffic, however, data transmissions are not periodical and the latency of each node is not constrained.
- ✓
- In [13], the authors proposed a new algorithm named Dynamic Adaptive Hierarchical Data Aggregation (DAHDA) which extended the functionality of LEACH-C. In DAHDA, all of clusters are assigned weights which are based on their residual energy and density. Based on the weights, the algorithms decide which node should be a cluster head (CH) where data packets are combined. It improves energy consumption because it reduces data traffic, however, data transmissions are not periodical and the latency of each node is not constrained.
- ✓
- In [14], the authors proposed a new method named Optimal Clustering in Circular Networks (OCCN) which aims to reduce energy consumption, data traffic and increase the lifetime of wireless sensor networks [18]. In that method, which was proposed for a circular area surrounding a sink, one hop communication between the cluster heads and the sink was replaced by an optimal multi-hop communication. Data packets are combined at cluster head nodes. It reduces the amount of traffic, however, data transmission is not periodical and the latency of each node is not constrained.
- ✓
- In [15], the authors proposed a distributed energy-balance algorithm (DAS) which aims to balance the energy consumption for aggregators. In this algorithm, first, trees rooted at nodes are formed which are termed virtual sinks, to balance the number of children at a given level to level the energy consumption and then try to assign timeslots for all nodes to satisfy the minimum latency and energy consumption demand. Data packets are combined at parent nodes. This algorithm reduces latency and data traffic, but data transmission is not periodical and the latency of each node is not constrained.
- ✓
- In [16], the authors proposed a privacy-preserving in-network aggregation protocol (PPSDA) for wireless sensor networks which is based on the concept of data slicing, mixing and merging. Sensor nodes slice the data into some pieces then send these pieces to neighbor nodes which have the same key as this node. After receiving pieces of data from neighbor nodes, this node combines its own data then sends in to a sink node. This algorithm doesn’t reduce the amount traffic and is low reliability.
3. System Model
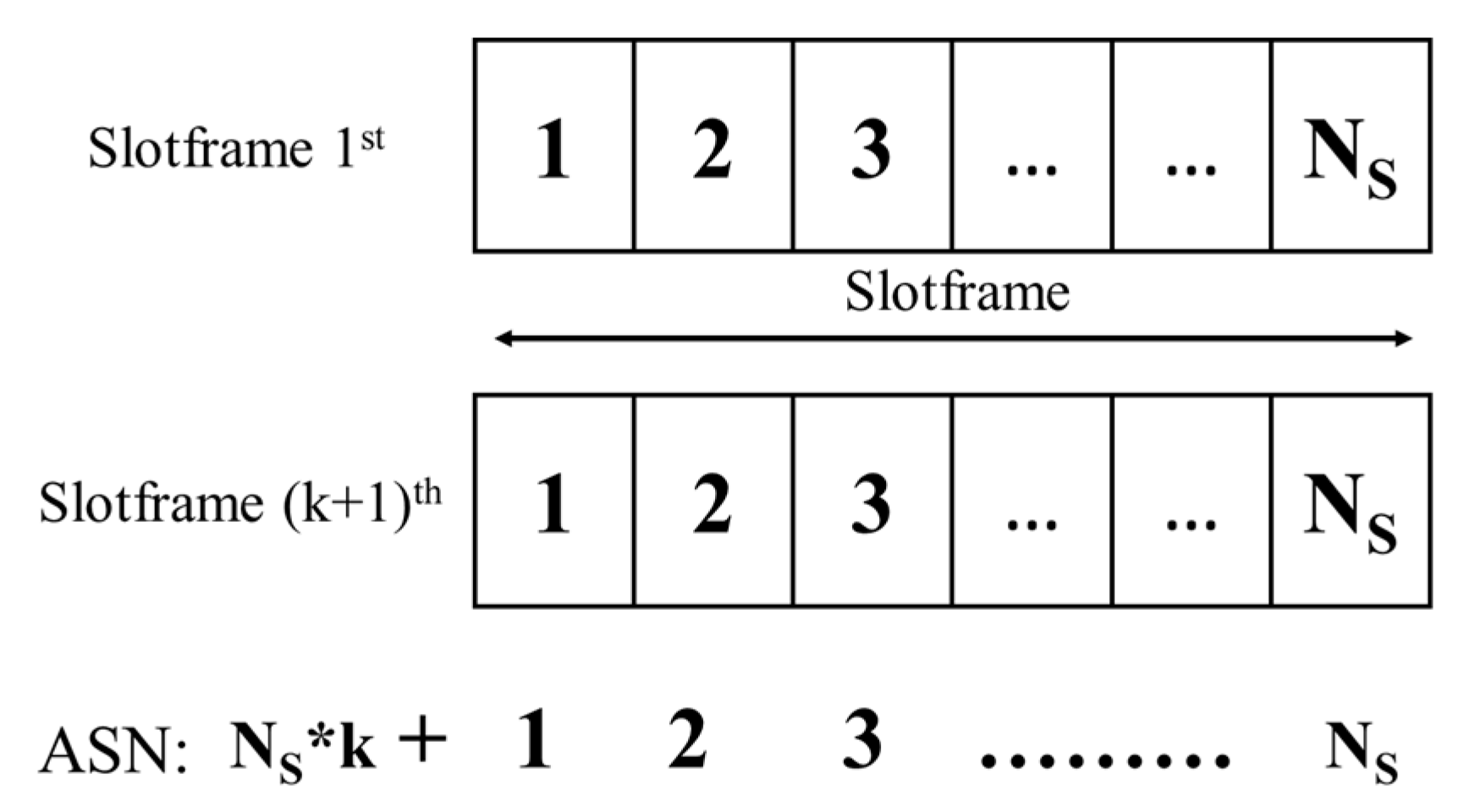
3.1. System Model
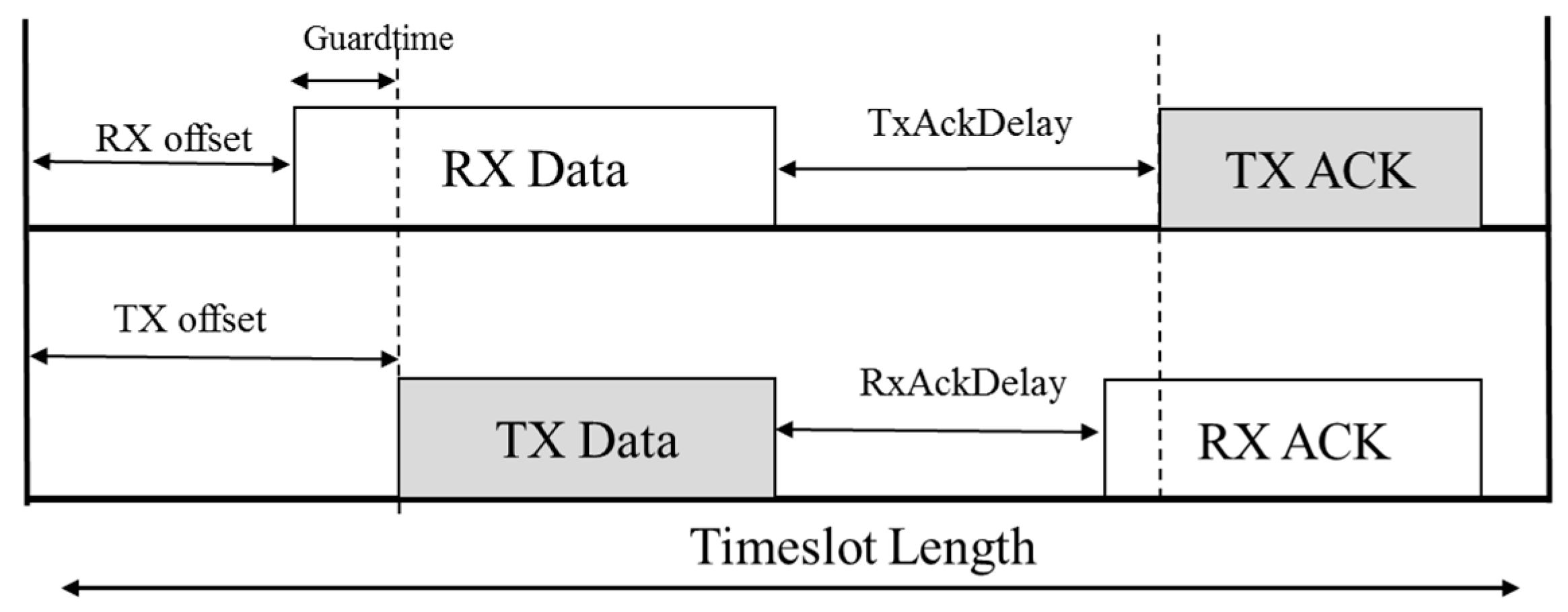
3.2. Application Model
4. Our Approach
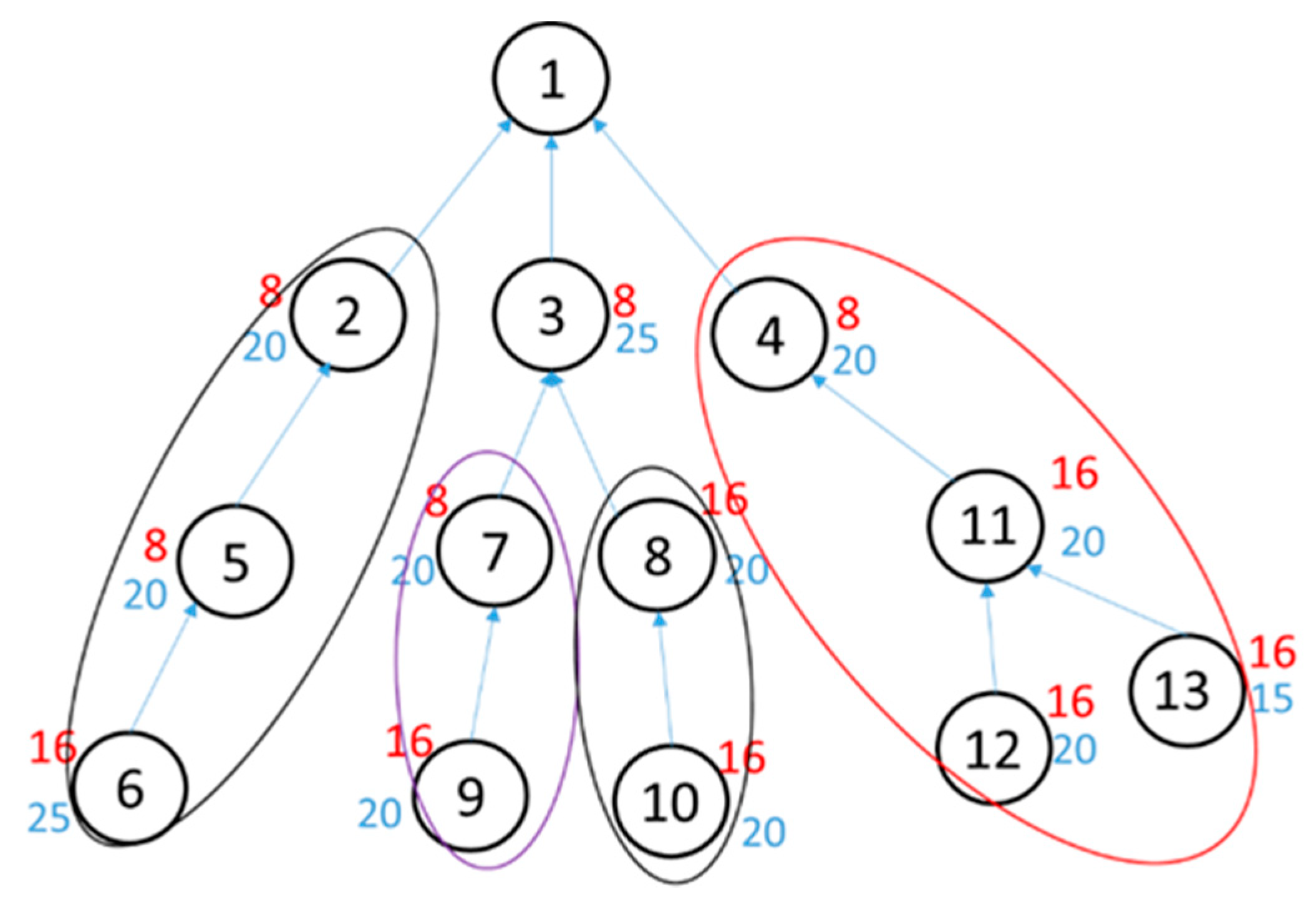
4.1. Grouping Node Mechanism and Dynamically Combining Packet
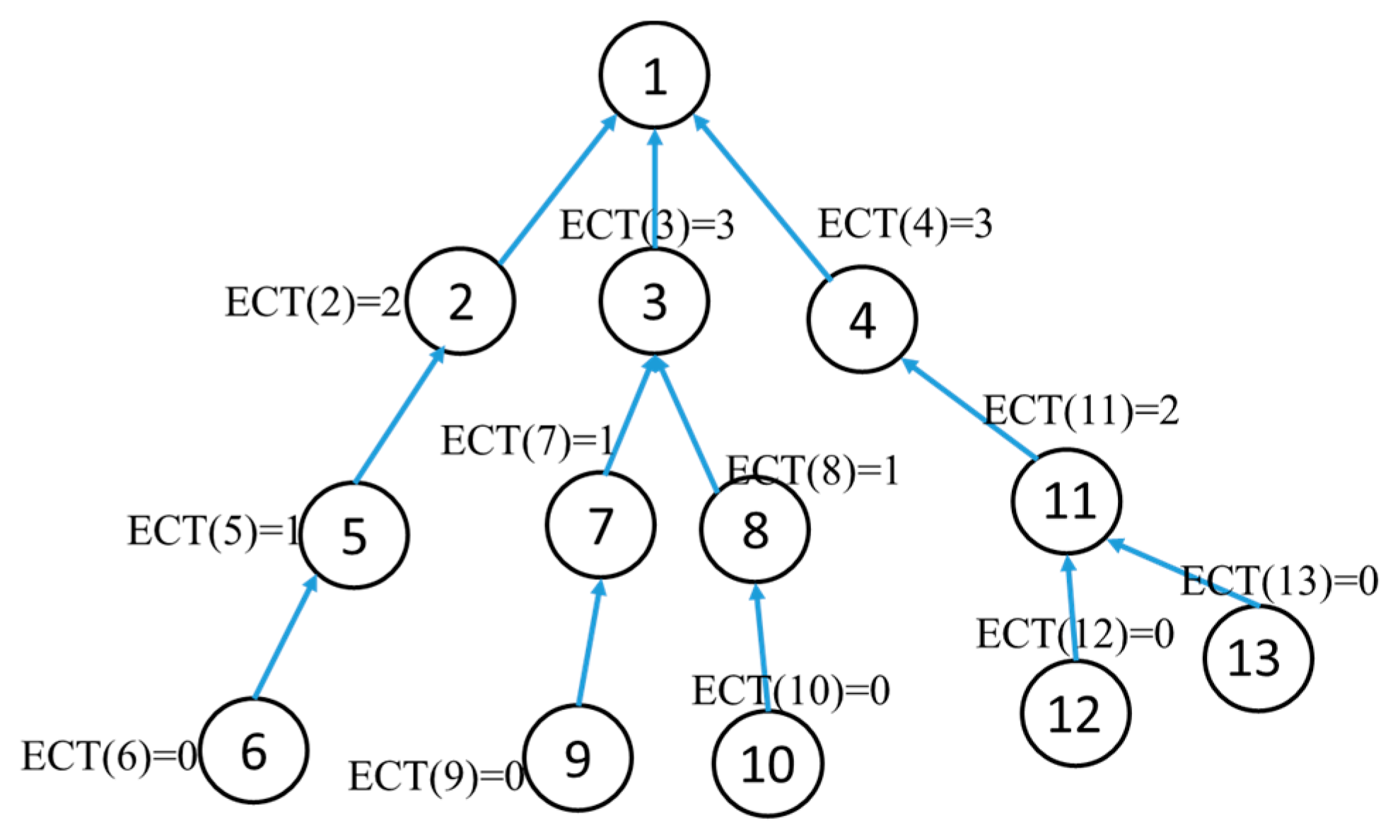
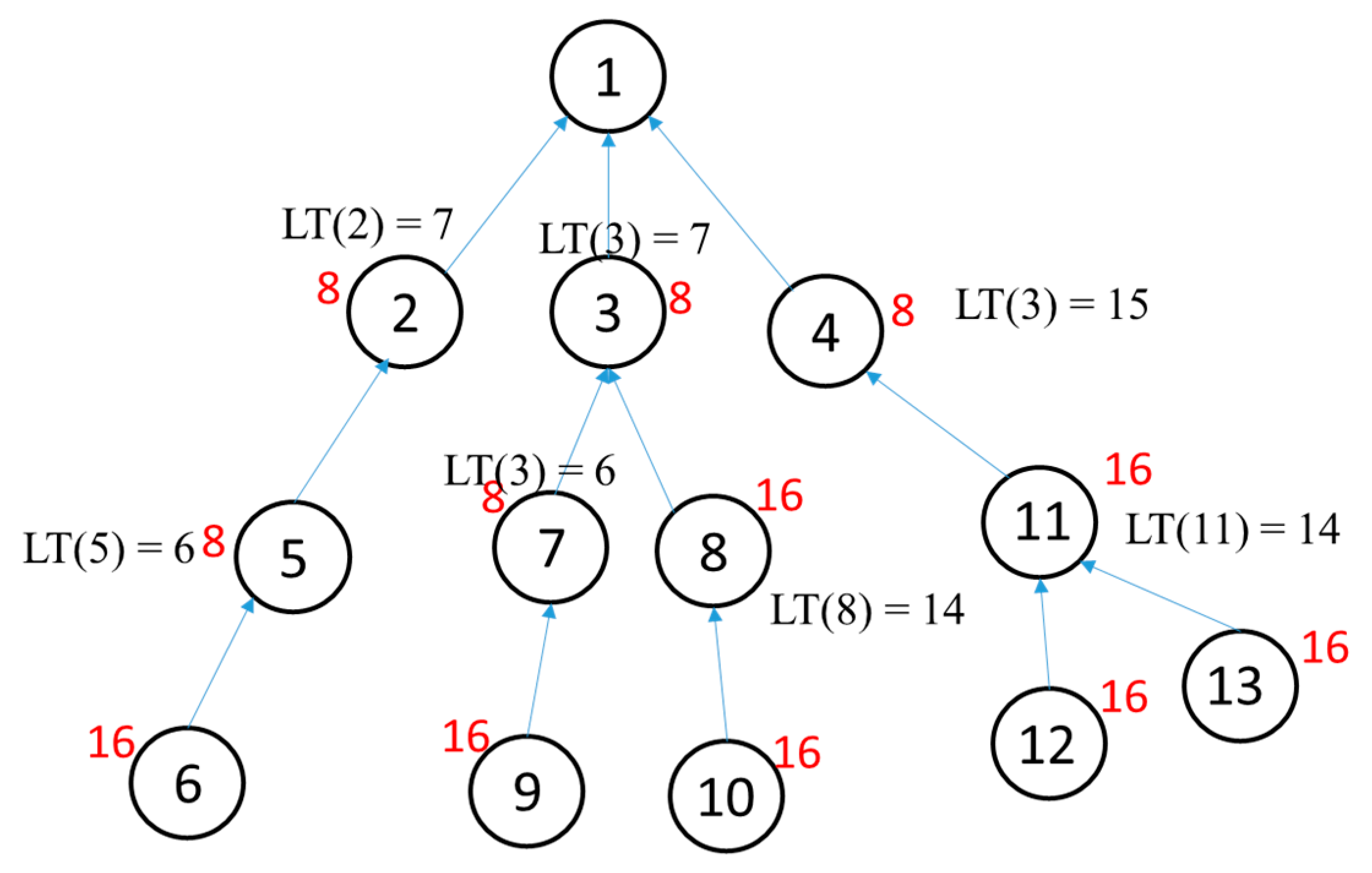
- Total data size in a subtree at this time slot where a root node is the node we consider is less than the maximum payload size (MPS).
- LT(i) − ECT(i) > = NCi where NCi is the number of child nodes which has packets in queue in the timeslot of node i.
- ECT(i) = MAX(ETR(j)) + NCi where j is the child of node i and NCi is the number of children of node i.
- ECT(i) = current timeslot if the node has the highest hop-count to a sink node when node i has packets in a queue in the path that contains node i.
- LT(i) depends on the deadline of packets in the subtree.
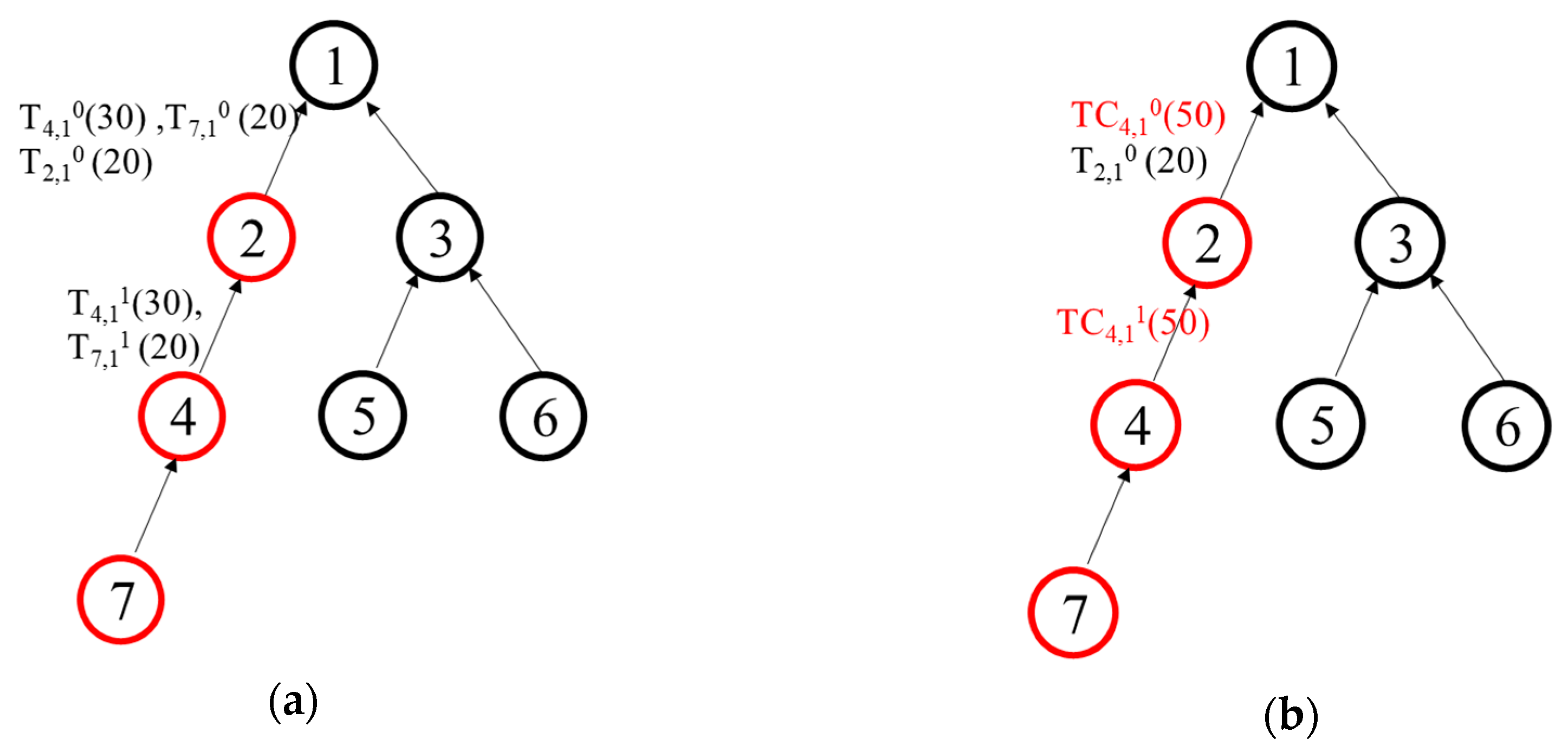
- T4,11(30) + T7,11 (20) → TC4,11(50) we remove T4,11(30), T7,11 (20) and add TC4,11(50) to the transmission list.
- T4,01(30) + T7,01 (20) → TC4,01(50) we remove T4,01(30), T7,01 (20) and add TC4,01(50) to the transmission list.
4.2. Packet Combining Mechanism
4.3. Priority Assignment
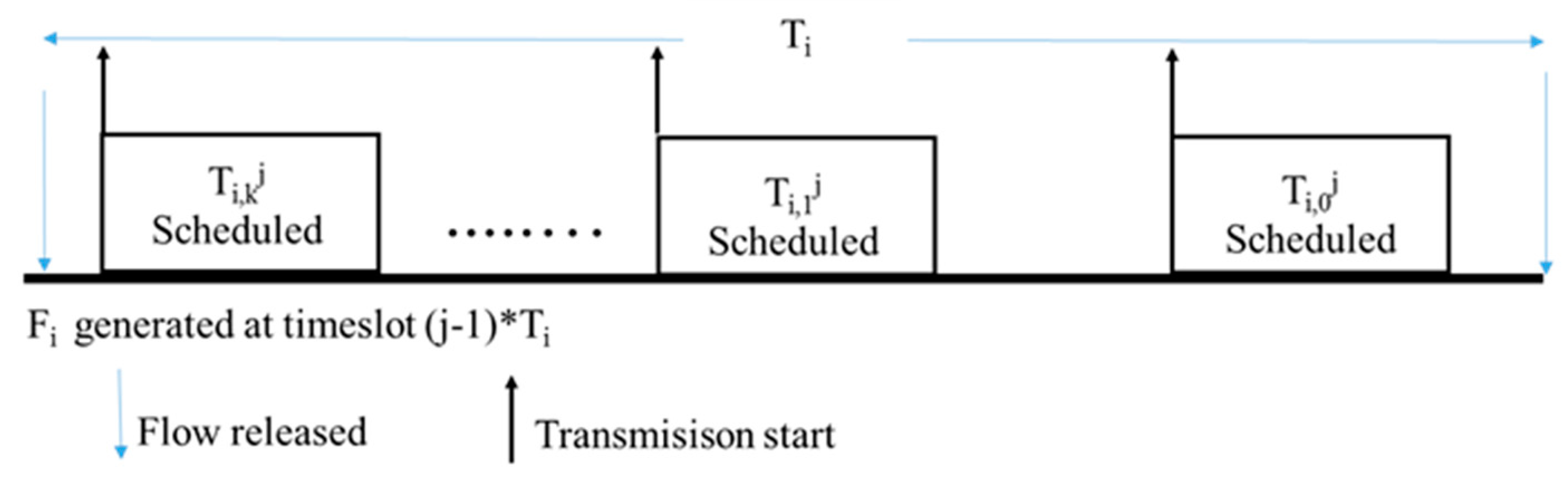
- ET(Ti,k j) = MAX (Ni − k + Ti *j, S)
- LST(Ti,k j) = Ti*j − k − 1
- Ta,bk [x:y] + Tc,dz [t:q] → TCa,bk [ MAX(x,t):MIN(y,q)]: adds transmission TCabk and removes Ta,bk, Tc,dz.
- Ncnfavg(Ti,kj, S) = Σi<=k Ncnf(Ti,kj, S)/(k + 1)
- PR(Ti,kj, S) = |TW(Ti,kj,S)| − Ncnfavg(Ti,kj,S) [1]
- PR(TCi,kj, S) = |TW(TCi,kj, S)| − Ncnfavg(TCi,kj, S).
4.4. PC-PCLLF: Packet Combining with Path Conflict Aware Least Laxity First Algorithm
| Algorithm 1: PC-PCLLF (G, F, D, P, nch) |
| 1: Initiate the current time slot S = 0, calculate transmission list, and define Pr(Ti,kj,0) for each Ti,kj |
| 2: While (not all the transmissions are scheduled) do |
| 2.1: Grouping node, combine packet, and update transmission list |
| 2.2: Calculate the set Released(S) |
| 2.3: Calculate Pr(Ti,kj, S) for all transmissions in Released(S) |
| 2.4: If there is a transmission miss deadline (LST(Ti,kj, S) > S) |
| 2.4.1 Return “unschedulable”, Exit. |
| 2.5: Else |
| 2.5.1 Initiate the channel counter, n = 0 |
| 2.5.2 While (n ≤ nch) do |
|
| 2.5.3 End while |
| 2.5.4 Go to next time slot S = S + 1 |
| 2.6 End if |
| 3: End While |
| 4: Return the Schedule table |
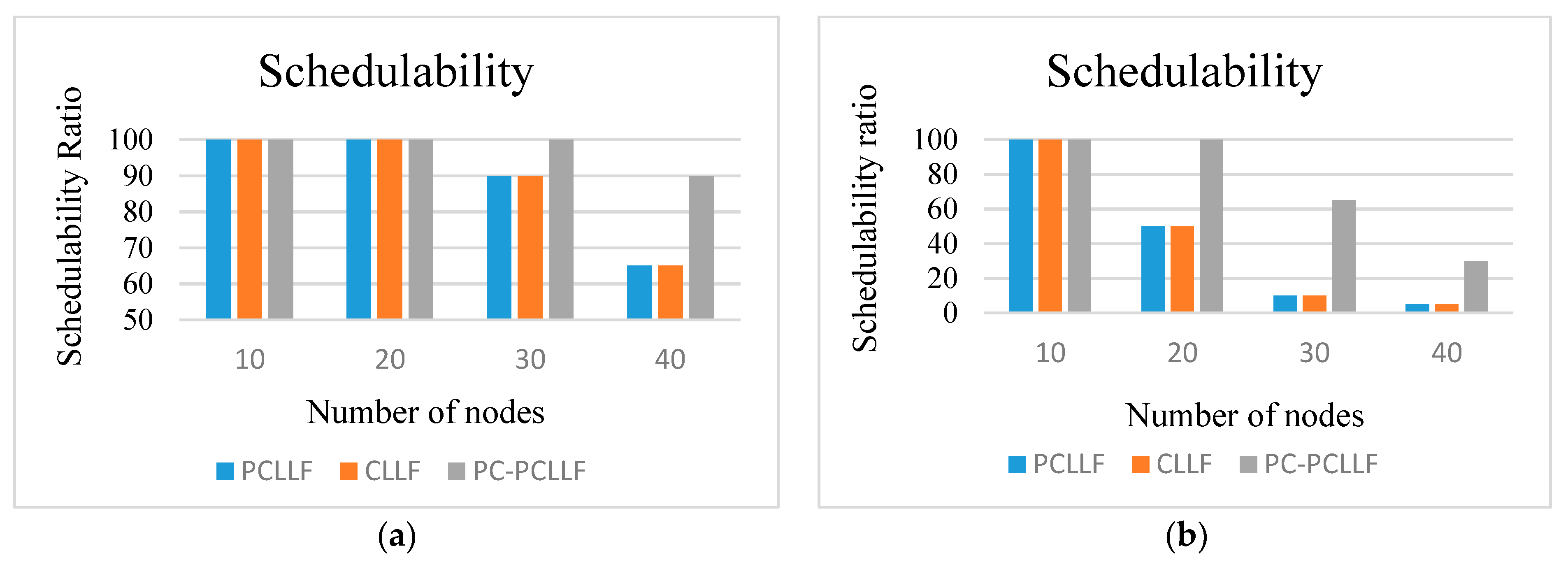
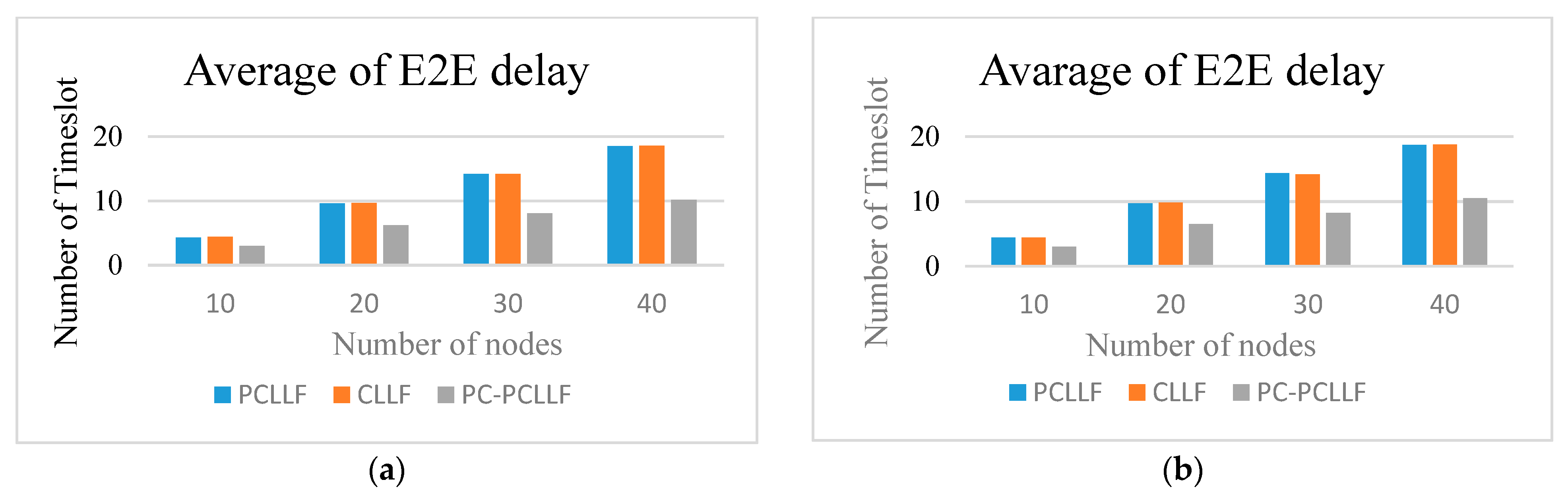
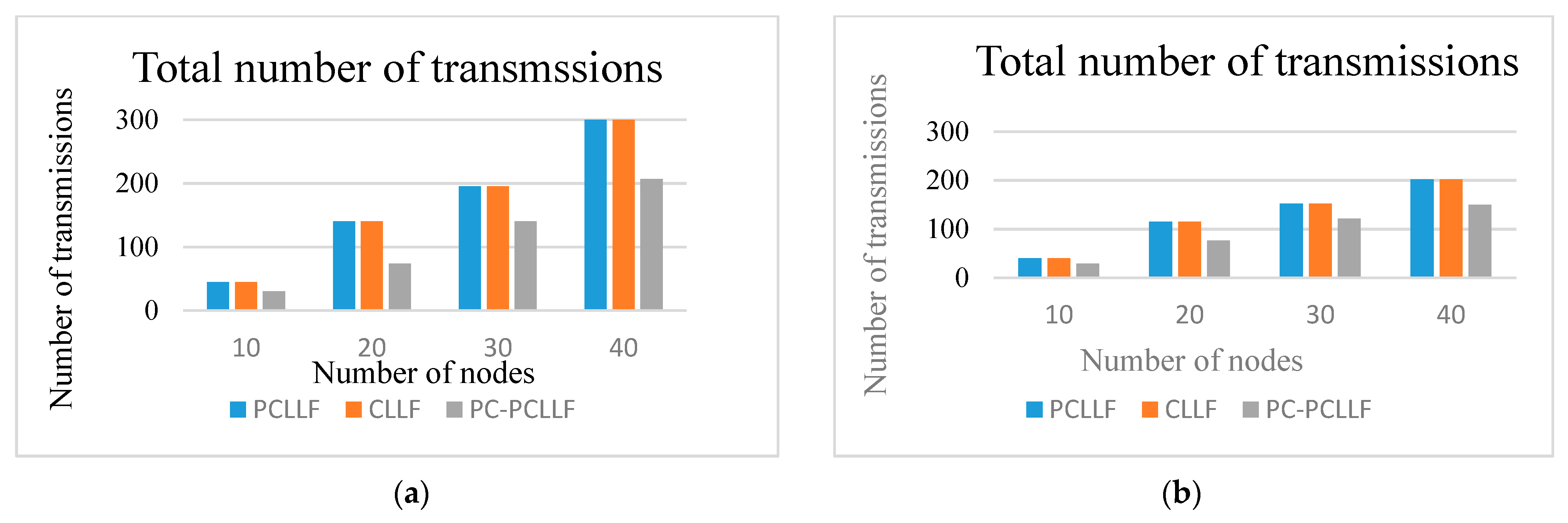
5. Performance Evaluation
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Notations
| ET(Ti,kj, S) | Earliest start time for Ti,kj in time slot S |
| LT(i) | Latest timeslot node i must to transmit packet to parent of node i to guarantee schedulability. |
| Ncnfavg(Ti,kj, S) | Number of transmissions duplex conflicting with Ti,kj in time slot S |
| PR(Ti,kj, S) | Priority value of Ti,kj in time slot S |
| LST(Ti,kj, S) | Latest start time for Ti,kj in time slot S |
| ECT(i) | Earliest combined timeslot when all of packet in subtree node i can arrive to node i. |
| TW(Ti,kj, S) | Time window with Ti,kj in time slot S |
References
- Darbandi, A.; Kim, M.K. Path collision-aware real-time link scheduling for TSCH wireless networks. KSII Trans. Internet Inf. Syst. 2019, 13, 4429–4445. [Google Scholar]
- Nguyen, T.T.; Oh, H. SCSMA: A Smart CSMA/CA Using Blind Learning for Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2019, 1. [Google Scholar] [CrossRef]
- Gutierrez, J.A.; Callaway, E.H.; Barrett, R.L. The WirelessHART Physical Layer and Data Link Layer. In Low-Rate Wireless Personal Area Networks: Enabling Wireless Sensors with IEEE 802.15.4; IEEE: Piscataway, NJ, USA, 2007; pp. 207–217. ISBN 9781118098882. [Google Scholar]
- Ishii, Y. Exploiting Backbone Routing Redundancy in Industrial Wireless Systems. IEEE Trans. Ind. Electron. 2009, 56, 4288–4295. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Oh, H. A Receiver for Resource-Constrained Wireless Sensor Devices to Remove the Effect of Multipath Fading. IEEE Trans. Ind. Electron. 2018, 65, 6009–6016. [Google Scholar] [CrossRef]
- Nguyen, T.T. Design and Implementation of Smart Multi-Channel MAC Protocol for Industrial Wireless Sensor Networks. Ph.D. Thesis, University of Ulsan, Ulsan, Korea, February 2020. [Google Scholar]
- Palattella, M.R.; Accettura, N.; Dohler, M.; Grieco, L.A.; Boggia, G. Traffic Aware Scheduling Algorithm for reliable low-power multi-hop IEEE 802.15.4e networks. In Proceedings of the 2012 IEEE 23rd International Symposium on Personal, Indoor and Mobile Radio Communications-(PIMRC), Sydney, Australia, 9–12 September 2012; pp. 327–332. [Google Scholar]
- Aijaz, A.; Raza, U. DeAMON: A Decentralized Adaptive Multi-Hop Scheduling Protocol for 6TiSCH Wireless Networks. IEEE Sens. J. 2017, 17, 6825–6836. [Google Scholar] [CrossRef]
- Kang, B.; Nguyen, P.K.H.; Zalyubovskiy, V.; Choo, H. A Distributed Delay-Efficient Data Aggregation Scheduling for Duty-Cycled WSNs. IEEE Sens. J. 2017, 17, 3422–3437. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Oh, H. Constructing an optimally balanced tree to maximize data throughput with multiple channels. Wirel. Netw. 2018, 24, 993–1005. [Google Scholar] [CrossRef]
- Saifullah, A.; Xu, Y.; Lu, C.; Chen, Y. Real-time scheduling for WirelessHART networks. In Proceedings of the 2010 31st IEEE Real-Time Systems Symposium, San Diego, CA, USA, 30 November–3 December 2010; pp. 150–159. [Google Scholar]
- Pan, C.; Zhang, H. A time efficient aggregation convergecast scheduling algorithm for wireless sensor networks. Wirel. Netw. 2016, 22, 2469–2483. [Google Scholar] [CrossRef]
- Randhawa, S.; Jain, S. DAHDA: Dynamic Adaptive Hierarchical Data Aggregation for Clustered Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 97, 6369–6399. [Google Scholar] [CrossRef]
- Arghavani, M.; Esmaeili, M.; Esmaeili, M.; Mohseni, F.; Arghavani, A. Optimal energy aware clustering in circular wireless sensor networks. Ad Hoc Netw. 2017, 65, 91–98. [Google Scholar] [CrossRef]
- Saginbekov, S.; Jhumka, A. Many-to-many data aggregation scheduling in wireless sensor networks with two sinks. Comput. Netw. 2017, 123, 184–199. [Google Scholar] [CrossRef]
- Singh, V.K.; Verma, S.; Kumar, M. Privacy Preserving In-network Aggregation in Wireless Sensor Networks. In Proceedings of the FNC/MobiSPC, Montreal, QC, Canada, 15–18 August 2016; pp. 216–223. [Google Scholar]
- Mehak; Khandnor, P. Structure and structure-free data aggregation protocols in wireless sensor networks-a review. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 2136–2140. [Google Scholar]
- Li, C.; Bai, J.; Gu, J.; Yan, X.; Luo, Y. Clustering routing based on mixed integer programming for heterogeneous wireless sensor networks. Ad Hoc Netw. 2018, 72, 81–90. [Google Scholar] [CrossRef]


| TW(Ti,kj,0) | TW(Ti,kj,0) | TW(Ti,kj,0) | TW(Ti,kj,0) | TW(Ti,kj,0) | |||||
|---|---|---|---|---|---|---|---|---|---|
| T2,01 | [0:7] | T6,21 | [0:13] | T7,11 | [0:6] | T8,11 | [0:14] | T13,21 | [0:13] |
| T2,02 | [8:15] | T6,11 | [1:14] | T7,01 | [1:7] | T8,01 | [1:15] | T13,11 | [1:14] |
| T5,11 | [0:6] | T6,01 | [2:15] | T7,02 | [8:14] | T11,11 | [0:14] | T13,01 | [2:15] |
| T5,01 | [1:7] | T3,01 | [0:7] | T7,12 | [9:15] | T11,01 | [1:15] | T10,21 | [0:13] |
| T5,12 | [8:14] | T3,02 | [8:15] | T9,21 | [0:13] | T12,21 | [0:13] | T10,11 | [1:14] |
| T5,02 | [9:15] | T4,01 | [0:7] | T9,11 | [1:14] | T12,11 | [1:14] | T10,01 | [2:15] |
| T4,02 | [8:15] | T9,01 | [2:15] | T12,01 | [2:15] |
| TW(Ti,kj,0) | TW(Ti,kj,0) | TW(Ti,kj,0) | TW(Ti,kj,0) | TW(Ti,kj,0) | |||||
|---|---|---|---|---|---|---|---|---|---|
| T2,02 | [8:15] | T6,21 | [0:13] | T3,01 | [0:7] | T10,21 | [0:13] | T9,21 | [0:13] |
| T5,12 | [8:14] | TC6,11 | [1:6] | T3,02 | [8:15] | TC10,11 | [1:14] | TC9,11 | [1:6] |
| T5,02 | [9:15] | TC6,01 | [2:7] | T13,21 | [0:13] | TC10,01 | [2:15] | TC9,01 | [2:7] |
| T4,02 | [8:15] | T7,02 | [8:14] | TC13,11 | [1:14] | ||||
| T12,21 | [0:13] | T7,12 | [9:15] | TC13,01 | [2:15] |
| TW(Ti,kj,0) | Ncnfavg(Ti, kj,0) | Priority Value | TW(Ti,kj,0) | Ncnfavg(Ti, kj,0) | Priority Value | ||
|---|---|---|---|---|---|---|---|
| T12,21 | [0:13] | 3.33 | 9.67 | T3,01 | [0:7] | 6 | 1 |
| T9,21 | [0:13] | 2.33 | 11.67 | T6,21 | [0:13] | 2.67 | 11.23 |
| T10,21 | [0:13] | 5 | 8 | T13,21 | [0:13] | 3.33 | 9.67 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mai, D.L.; Kim, M.K. A Scheduling Method Based on Packet Combination to Improve End-to-End Delay in TSCH Networks with Constrained Latency. Energies 2020, 13, 3031. https://doi.org/10.3390/en13123031
Mai DL, Kim MK. A Scheduling Method Based on Packet Combination to Improve End-to-End Delay in TSCH Networks with Constrained Latency. Energies. 2020; 13(12):3031. https://doi.org/10.3390/en13123031
Chicago/Turabian StyleMai, Dinh Loc, and Myung Kyun Kim. 2020. "A Scheduling Method Based on Packet Combination to Improve End-to-End Delay in TSCH Networks with Constrained Latency" Energies 13, no. 12: 3031. https://doi.org/10.3390/en13123031
APA StyleMai, D. L., & Kim, M. K. (2020). A Scheduling Method Based on Packet Combination to Improve End-to-End Delay in TSCH Networks with Constrained Latency. Energies, 13(12), 3031. https://doi.org/10.3390/en13123031




