Energy-Efficient Topology Control for UAV Networks
Abstract
:1. Introduction
- With our proposed network topology control method, a UAV network can be formed with energy-efficient network properties.
- Our scheme does not require the UAV or the Network Manager to know the whole information about all UAVs, such as position, routing path, and so on. Instead, by using the concept of swarm intelligence, each UAV is only concerned about their next one-hop connection in each partition, which will consequently make the effective network topology.
- The number of the partitions can be varied for each UAV. The number of the divided spaces can be customized with network density.
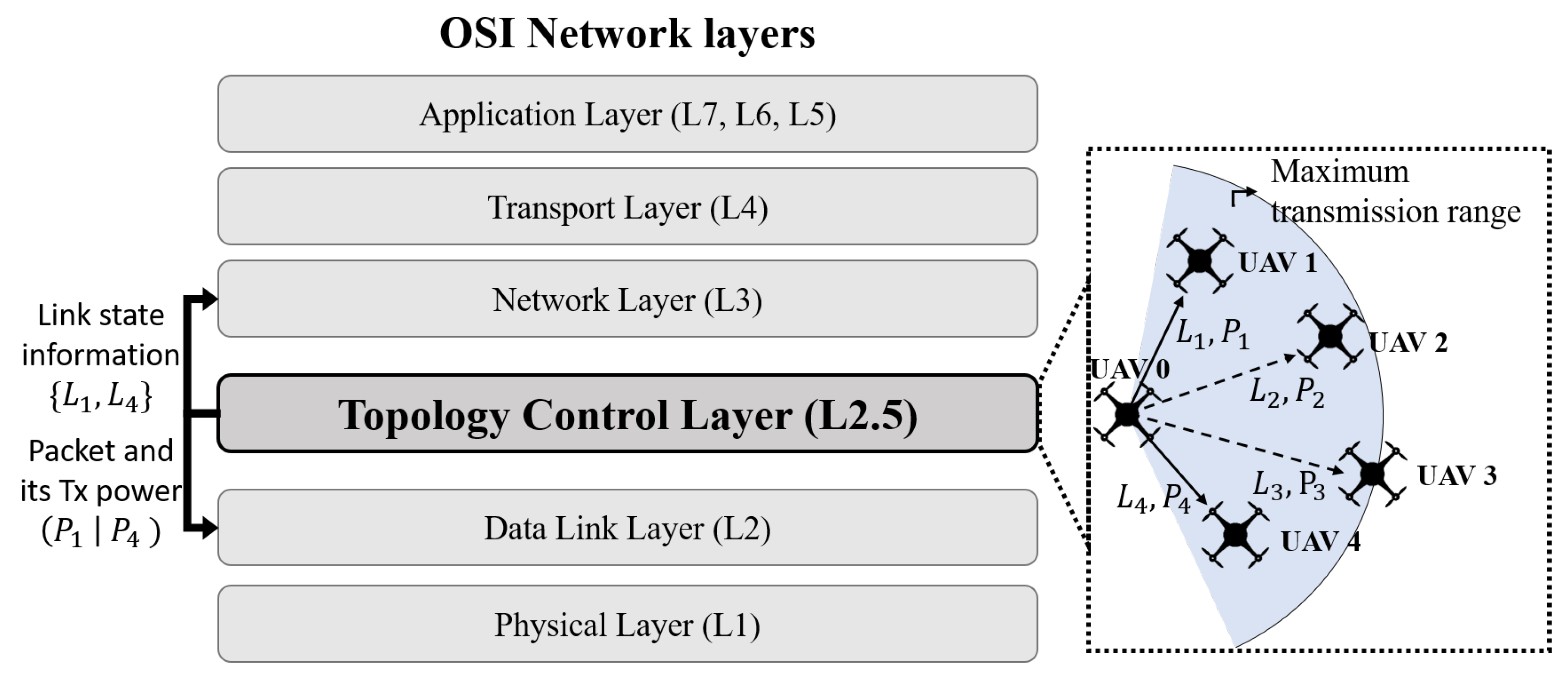
- Our research can be compatible with other network layers in the OSI model. Also, the topology control layer acts just between the data link layer (L2) and network layer (L3), which possibly can be expressed as L2.5.
2. Related Work
- UAV formation: The construction of an appropriate formation with many UAVs is progressing in various aspects. In fact, UAV positioning algorithms have been studied in consideration of network throughput [13], obstacle collision avoidance [14], and mission conditions [15]. Sabino et al. [16] proposed the multi-UAV placement scheme through the genetic algorithm. It should be noted that UAV formation control algorithms can be joined with our proposed system, since our system aims to improve the network topology of UAVs, which have the potential to frequently change their shape in three-dimensional space. With our dynamic topology control scheme, the UAV network can sustain an energy-efficient network while changing each UAV’s position according to their mission.
- Energy Efficiency: Research to improve the energy efficiency of the UAV network is proceeding by way of reducing the energy in the operation of UAV itself (e.g., optimized path planning for efficient aircraft propulsion), and the arrangement to minimize the energy on the entire network (e.g., optimal network recovery with additional UAV) [17]. In this paper, we compose an energy-efficient topology that is based on network management, which can be applied a priori to other related previous research.
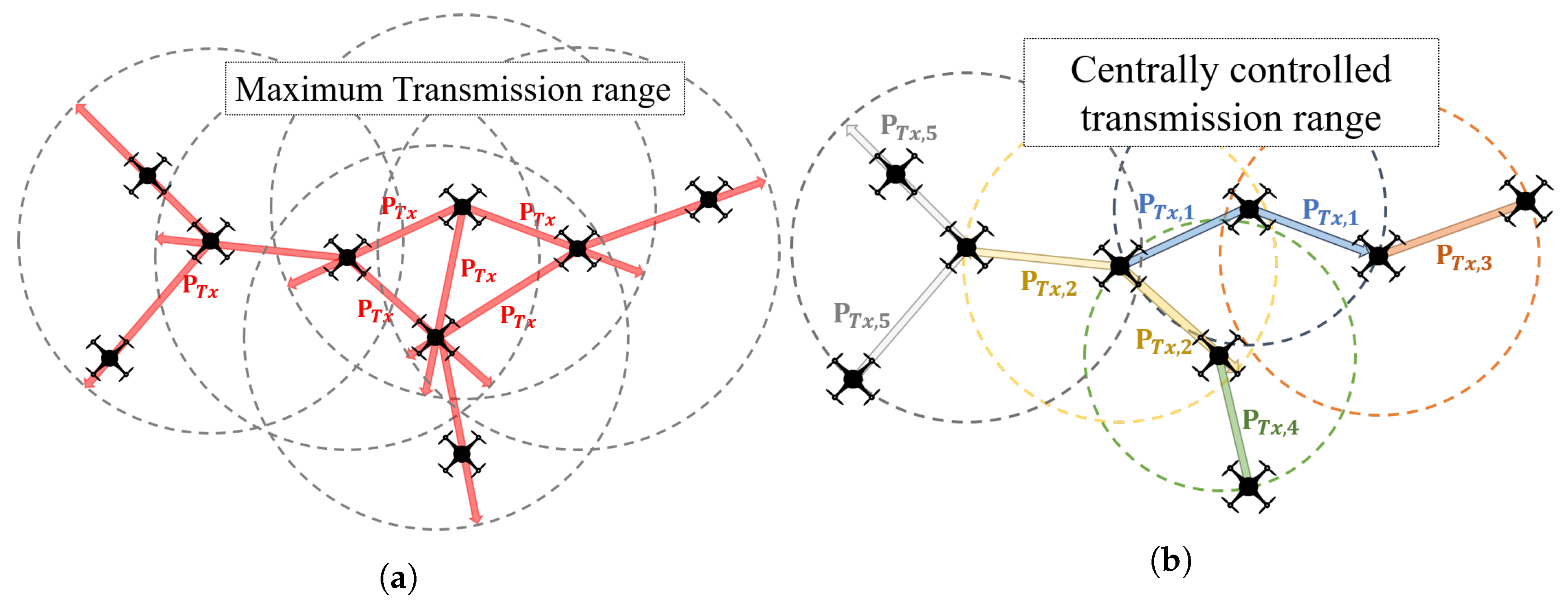
- Transmission Power Control: Many studies have been made to change transmission strength according to its conditions for effective communication. For example, power-controlled multiple access MAC protocols (PCMA) were presented to improve the channel use [18], and a tunable circuit system was studied to generate range-adaptive transmit signals [19]. However, these studies have not been used for UAV networks with mobility characteristics. Moreover, these studies are still inefficient since all nodes in the transmission range attempt to connect without any adjustment. However, our research uses the transmission power control in the UAV network and forms the network by controlling the number of the available links.
- 3D topology control schemes: Emerging research on the unmanned vehicle system emphasizes the importance of the dynamic network control problem for expanding its usage. Continuously adapting the network topology in the 3D space has been largely studied for both energy efficiency and network quality. Zhang et al. [20] proposed a cluster sleep–wake scheduling algorithm for underwater sensor networks. One of the main differences with our system is that this algorithm produces an on–off schedule of the links, while our one results in selected links which guarantee global connectivity (Section 3.3). Also, it adopts a centralized partitioning concept, while each UAV partitions the space, centering itself, in our algorithm. Our distributed concept has the advantage of scalability of the network, since the processing overhead remains the same with larger-scale networks. Kim et al. [21] addresses the 3D topology control method considering interference. In this paper, Cone-Based Topology Control (CBTC) has been introduced for partitioning each node’s space. The major difference with our work is the group of the selecting nodes. Our system selects the adjacent UAVs of the MST constructed in each partition (Section 3.2), while CBTC selects only the nearest one in each partition. This difference shows the limitation of the number of partitions, where CBTC restricts the angle of the division section while our system does not. The flexibility of the number of partitions results in the variety of the partition models, which enlarges the adaptability of the network scale (e.g., density of the UAVs).
3. System Design
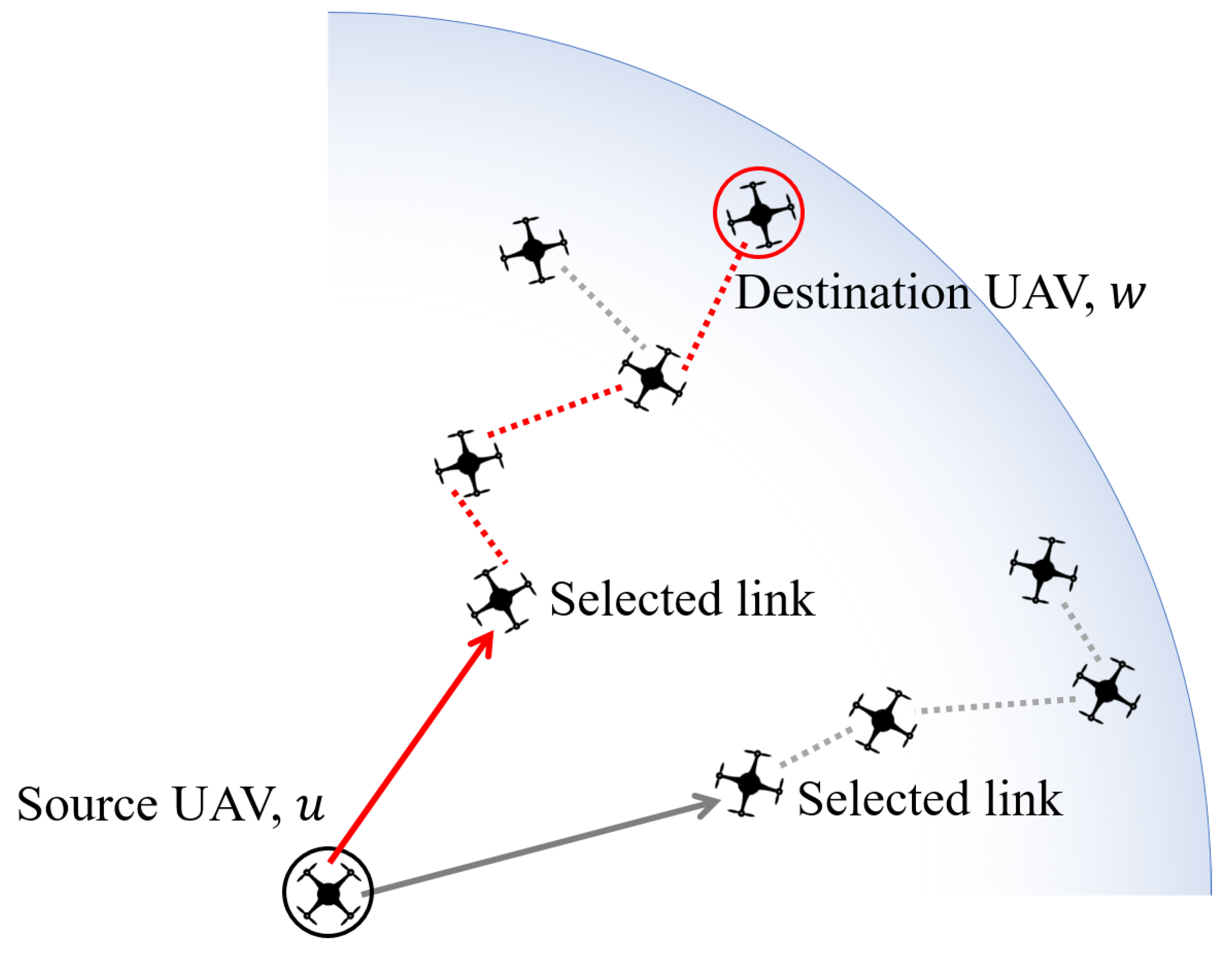
3.1. Topology Control Layer
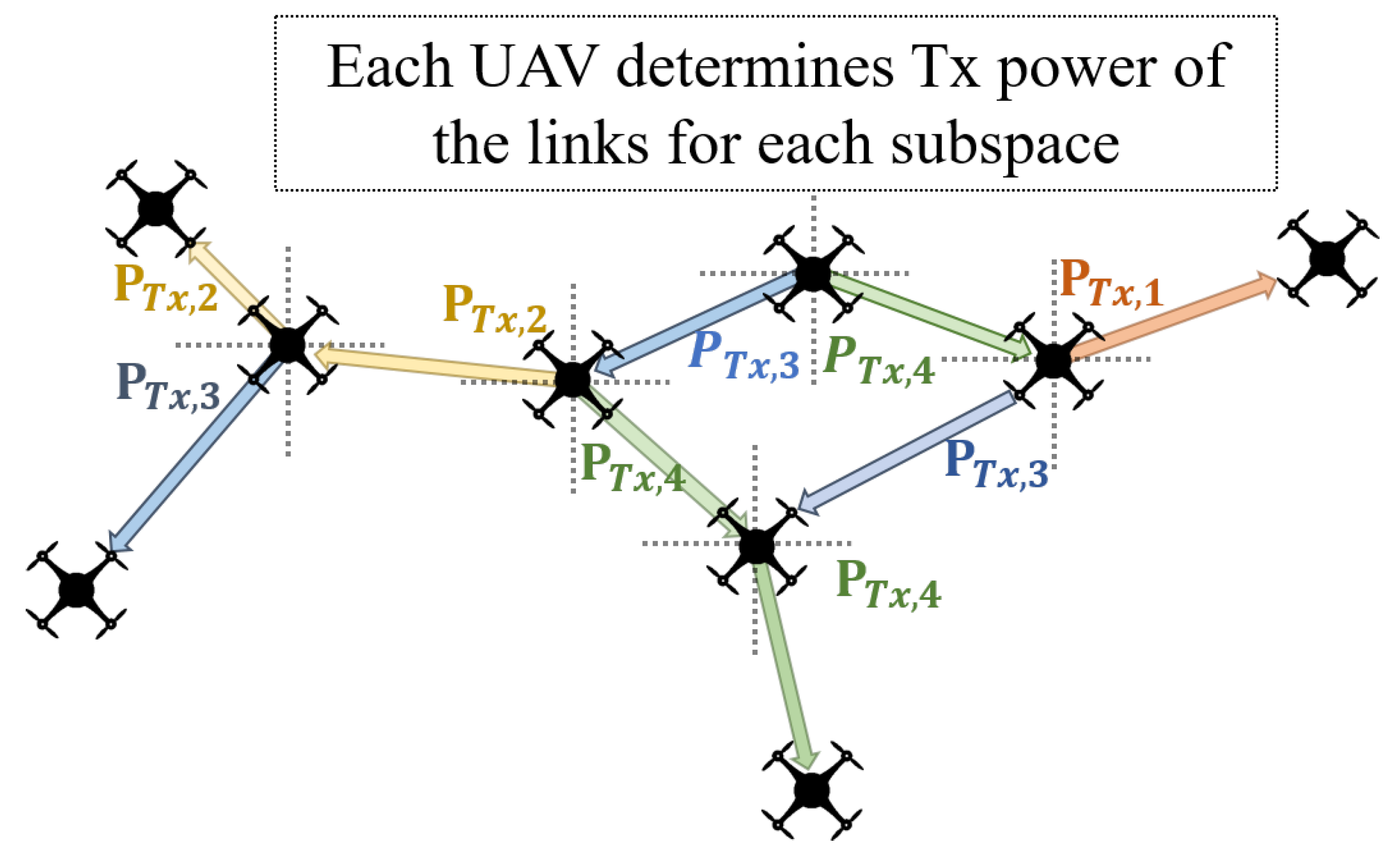
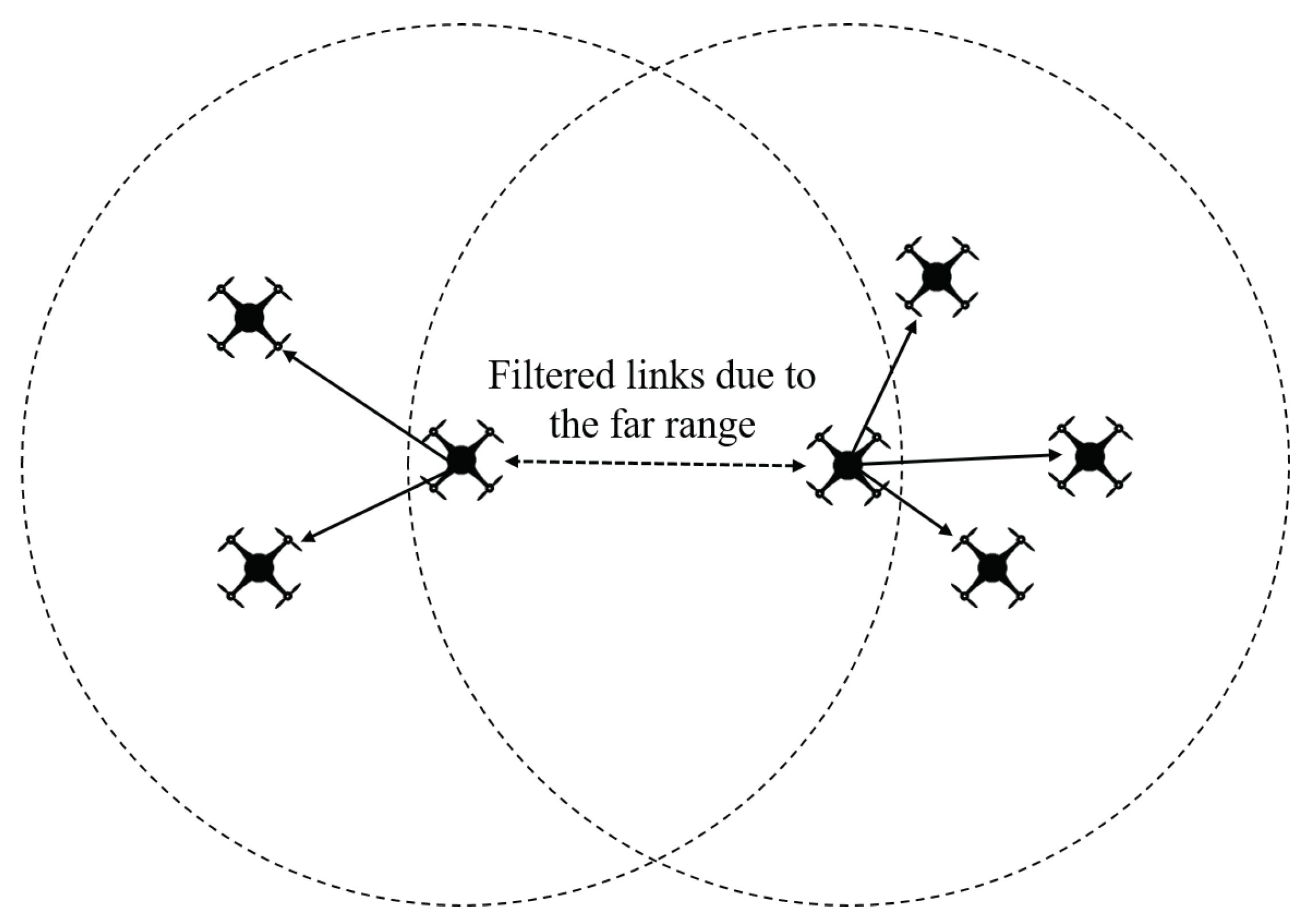
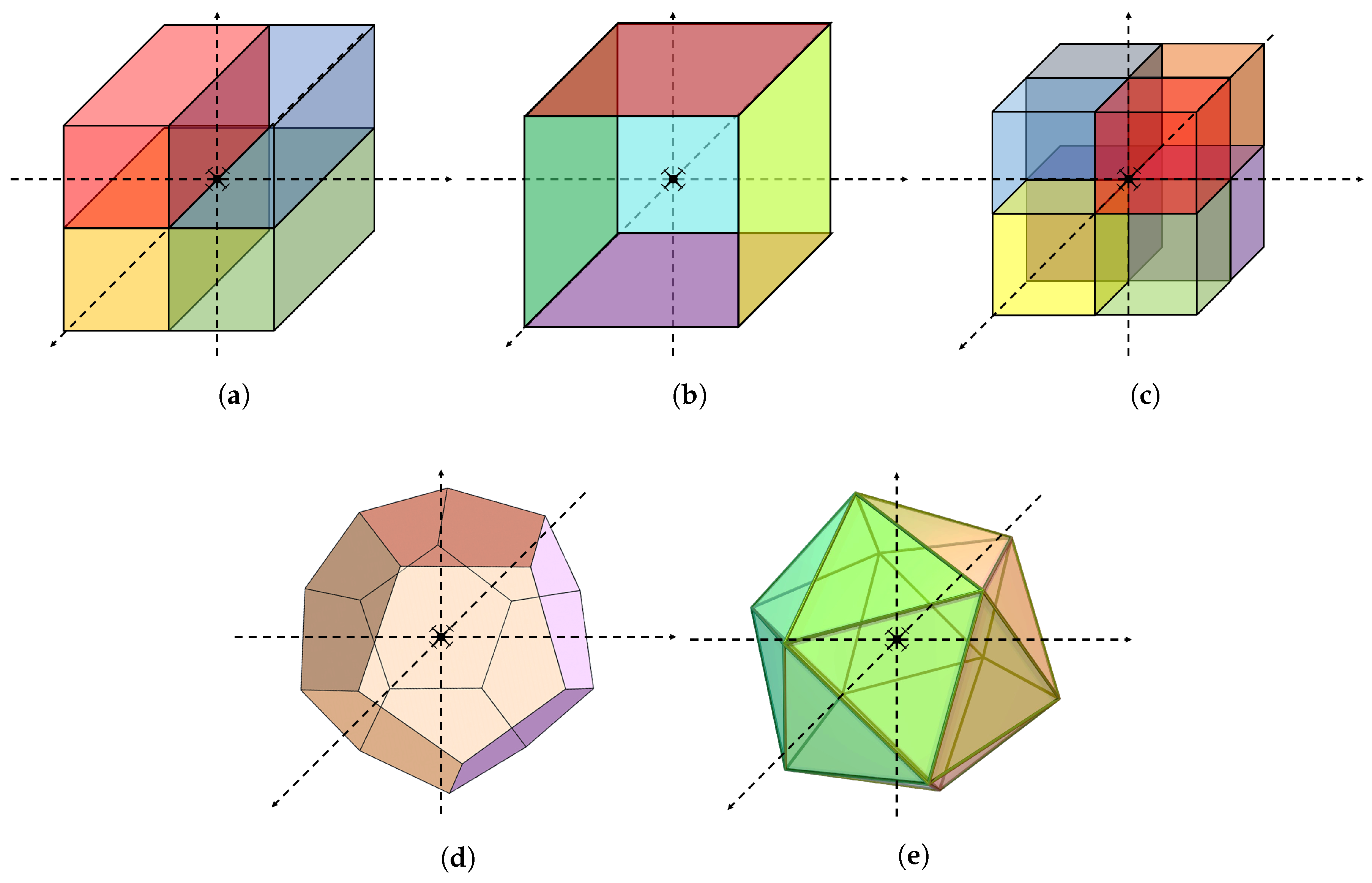
3.2. Space Partition Method
| Algorithm 1 Topology control layer. |
|
- The partitions should have the same volume.
- The partitions should contain the origin of the sphere.
- The partitions should have the same area of the surface.
3.3. Connectivity Proof
3.4. Swarm Intelligence Point of View
- Scalability. Compared to centralized methods, our proposed system does not need any centralized protocols or regulations. This feature prominently appears when the maximum hop count increases due to a large-scale network, where farthest UAVs take much longer to update its network configuration in the centralized system. In the topology control layer, each UAV determines the next available hops by itself, so the network size does not affect the network configuration delay.
- Mobility. Considering the high mobility of the UAV, our distributed concept based on the location has strong advantage during network topology changes. Since each UAV periodically updates its available neighbors, a network layer can rapidly drop or append the available links without hesitation.
- Simplicity. In the case of the micro UAVs, the computational resource is too small to input the high intelligence necessary for networking [22]. Our proposed system is composed of simple calculations augmented at the existing network stack, so it has much less occupancy of the system resources, which also contributes to the energy efficiency.
4. Evaluation
- Fully connected (FC): UAV networking that is fully connected with all UAVs that are in their transmission range.
- Simple MST (SMST): UAV networking appending the simple minimum spanning tree method.
- Topology Control (TC): UAV networking with a proposed topology control method. For each n value, we abbreviate the TC with n partitions as TC-n.
- Node degree: We exploit one of the general terms used in the graph theory. In this paper, the term node degree refers to the number of the edges which are incident to a UAV. At the viewpoint of the network topology, high node degree implies high stability of the network. If one of the connected neighbor UAVs fails (due to the emergency landing or return to home), the UAV should use the other connections to sustain the network connectivity. However, if UAVs have low degrees, the network has higher potential to lose the whole connectivity even with the loss of some centric nodes.
- Hop count: Hop count of an end-to-end connection is the number of the edges of the optimal path between them, which can be derived by the aforementioned Dijkstra algorithm. Higher hop count not only increases the delay of the connection but also has the potential to drop the end-to-end throughput, since the packet is repeatedly propagated through the wireless medium per each hop. Thus, lower hop count results in less use of the wireless medium with low latency, which results in the overall throughput improvement of the UAV network.
- Power consumption: As discussed in Section 3, our proposed system determines the transmission power of each link. We summed the amounts of the transmission power required at all links on each end-to-end connection. In the case of FC, we assumed there is no power control method equipped, so the expected power consumption is the multiplication of the average hop count by the maximum transmission power. On the other hand, in other cases, the transmission power of each link is calculated from the distance using the Friis equation. Please note that excessively high hop count results in the higher power consumption of the end-to-end communication, despite the low power consumption due to the short distance of the links.
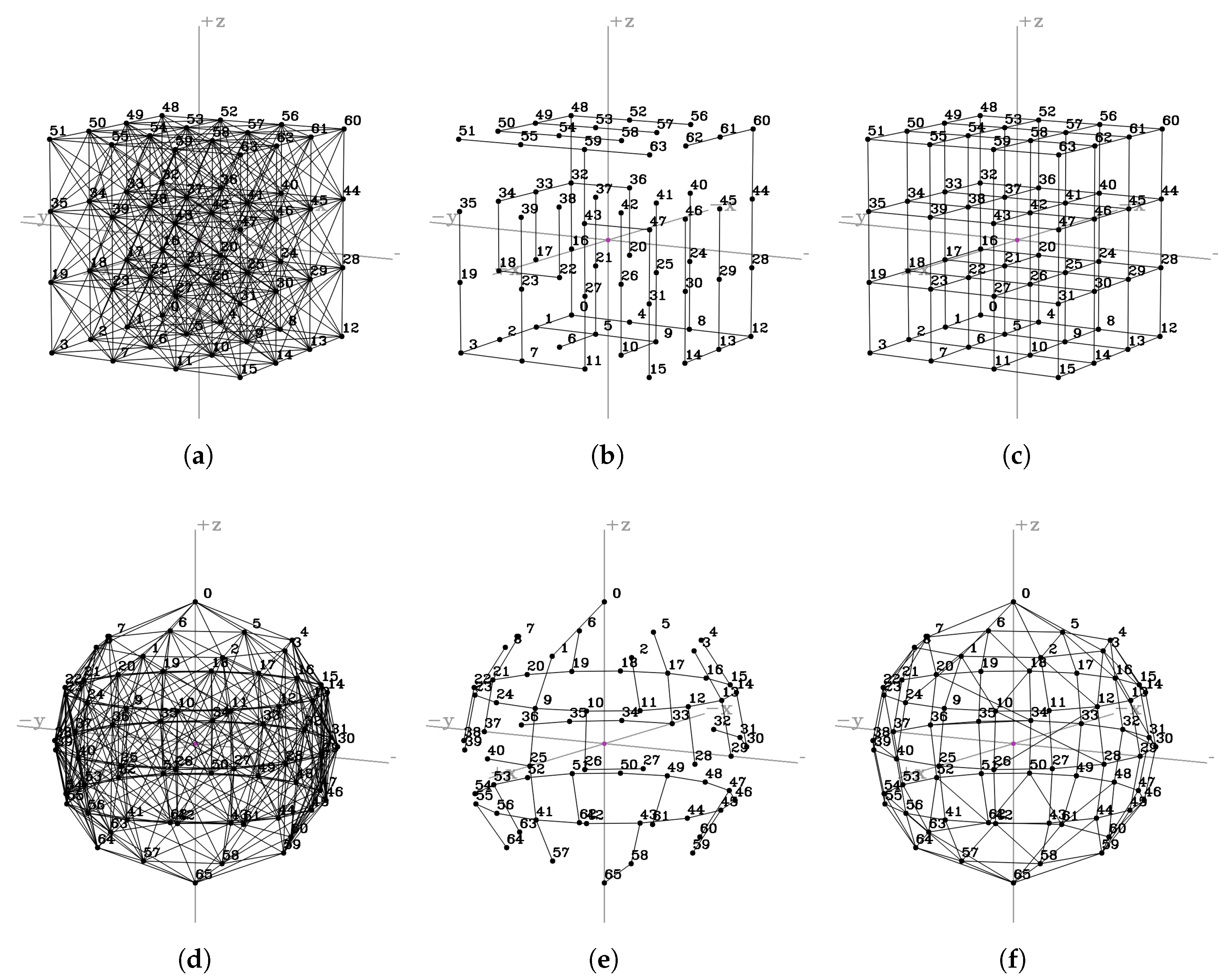
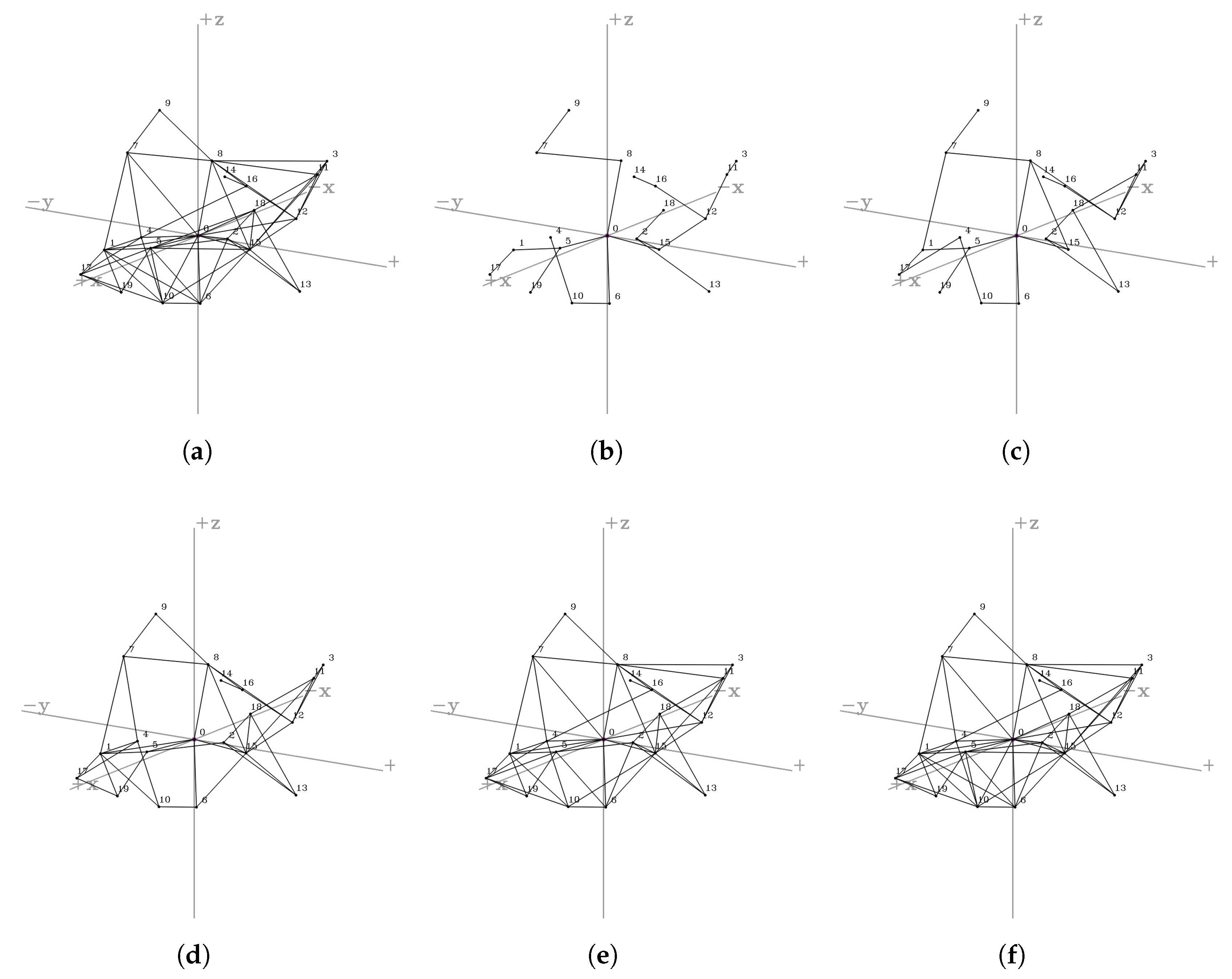
4.1. Regular Formations
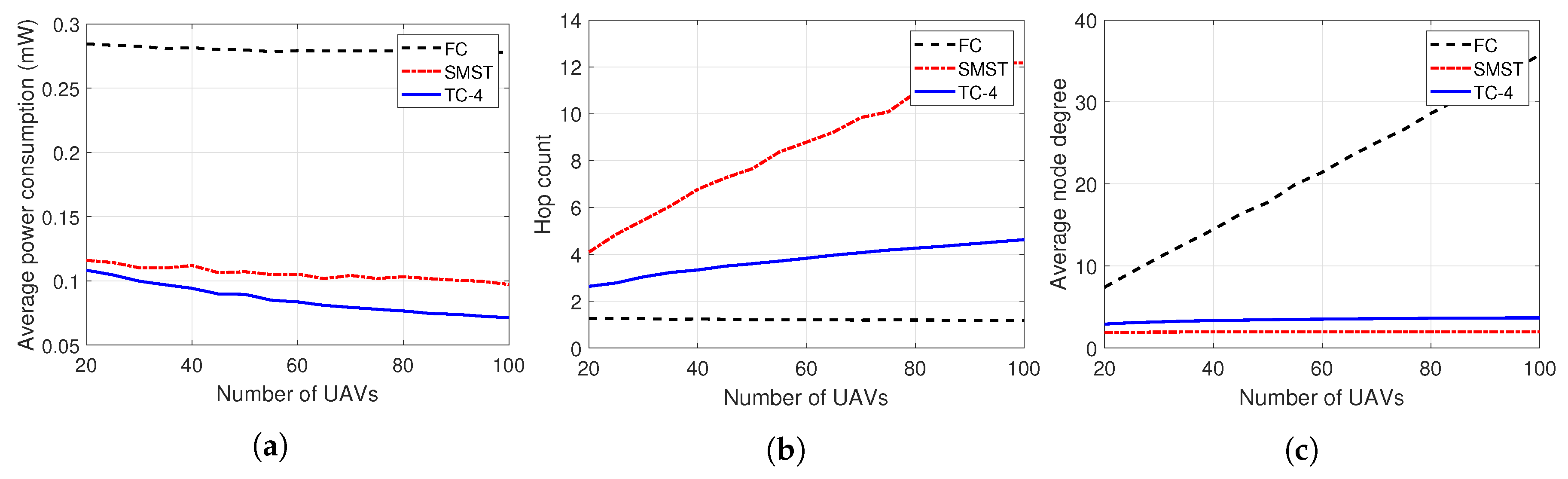
4.2. Network Size
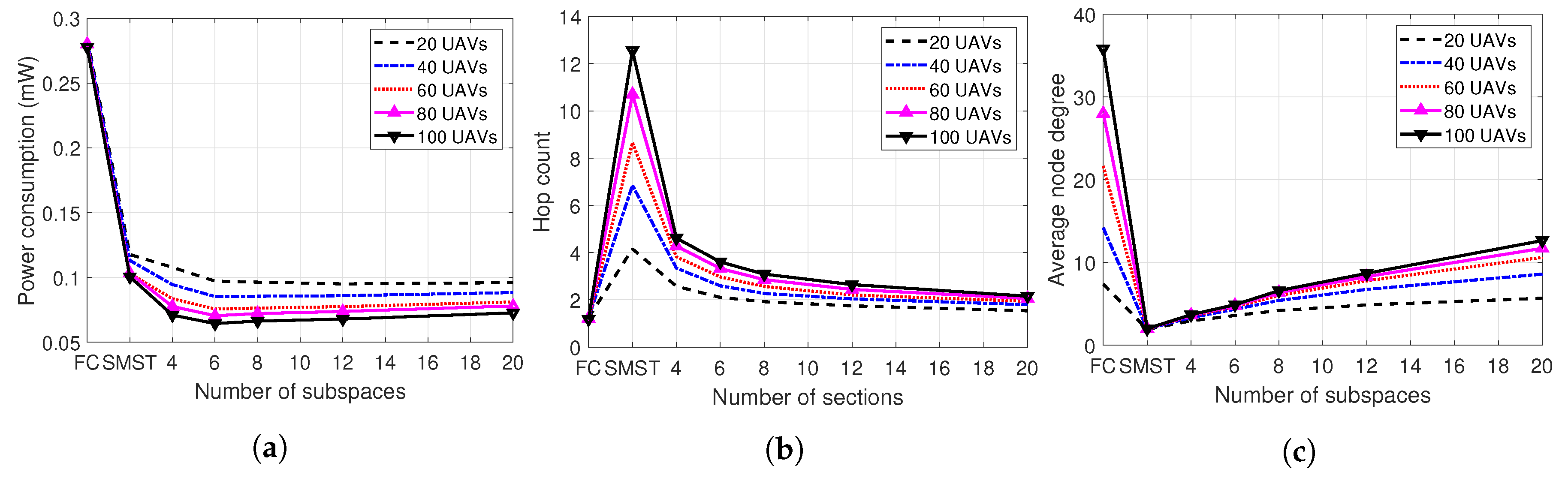
4.3. Number of Partitions
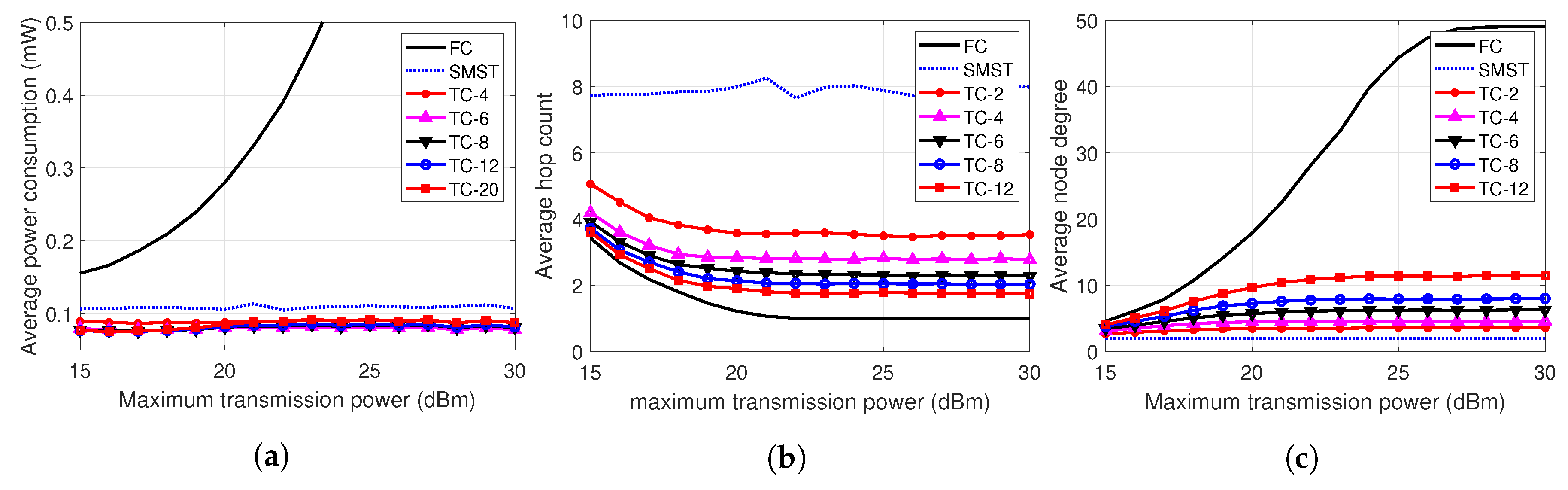
4.4. Transmission Range
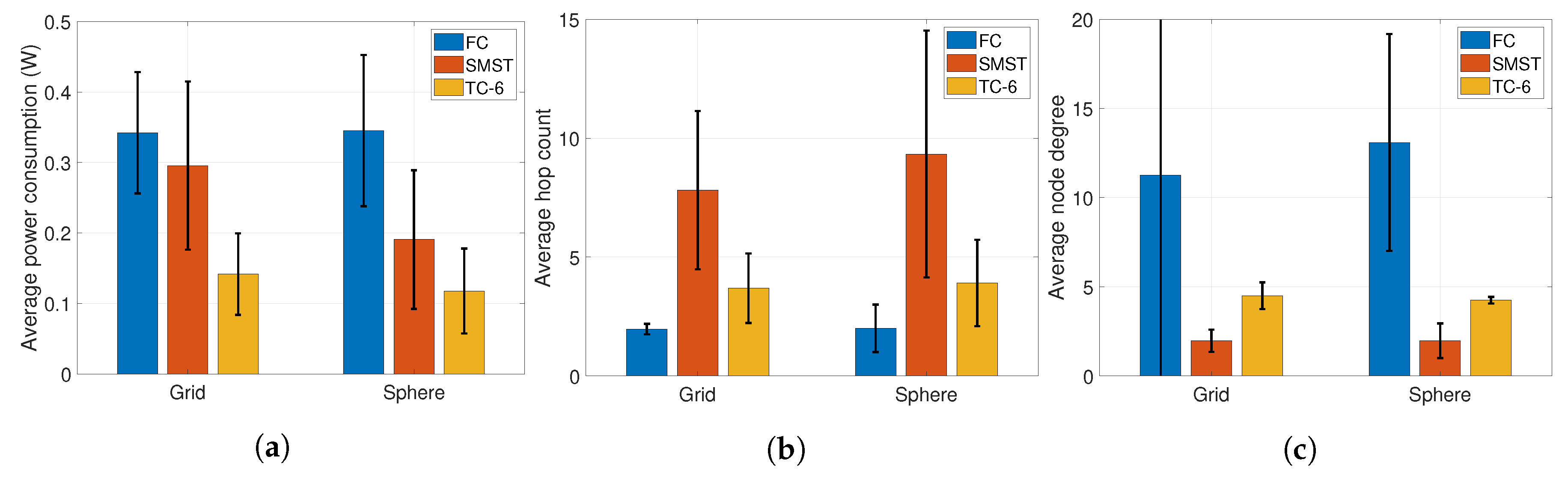
- We evaluated our proposed system topology control layer while varying the network size, number of partitions, and the transmission power. In every evaluation, our system shows outperforming results in average power consumption, while sustaining moderate values of the average node degrees and the hop counts.
- While varying the network size, the topology control layer shows a larger decrement in power consumption, because our system keeps a proper number of links and fits the transmission power of them.
- While increasing the number of the partitions, hop count shortly decreases and degree shortly increases due to the larger number of the selected links. In Figure 12a, TC-6 and TC-8 nearly show the lowest amount of the average power consumption regardless of the number of UAVs.
- Increasing the transmission range results in great advantages in power consumption, compared to the FC case. Also, we found that power consumption of lower n is relatively small in a large transmission range, while the consumption of higher n is relatively small in small transmission ranges.
5. Discussions
- Multi-input, Multi-output (MIMO) adaptation. MIMO targets concurrent communications in several directions, which fits our concept well. Through the combination with MIMO technology, each UAV can use the links of several partitions concurrently, which leads to great improvement in network throughput. If MIMO capacities (number of the available concurrent transmissions) differs from the number of the partitions (n), the difference can be handled by the partition scheduling.
- Link space improvement. If UAVs are flying in obstacle-rich environments such as an urban canyon, the relative distance between the UAVs does not directly refer to the link cost. Also, with the link quality improvement strategies such as packet recovery mechanism [25], a simple, distance-based space partition method cannot result in optimal network topology. To embrace these cases, we can design the space considering more than the positions, which can result in a more than 3-dimensional space. By formatting the partition vectors for the augmented space, our topology control layer can operate as Algorithm 1.
- n granularity. In Section 3.2, we listed some of the n values, based on the regular polyhedrons derived before. If we can design more S with variable n values following the basic rules in Section 3.2, there are more possibilities to control n in detail, which is advantageous according to Section 4.4.
- Empirical evaluation. In Section 4, we measured the performance of the network topologies with our own simulator, which is specialized to measure the property of the topology with power consumption. In this paper, we intended to focus on the clarified improvements in terms of the network topology, so we developed a simulator letting the numerical results be directly derived from the resulting network topology. By inserting our intermediate layer in practical network designs, we can evaluate our proposed scheme into a variety of network environments, by actually implementing devices or the public domain network simulator such as Network Simulator 3 (ns-3).
- Applications. As our topology control scheme acts as an intermediate layer between the data link layer and the network layer, it can be broadly used in a wireless network domain. In the case of the UAV network, our system can contribute to performance improvements in multi-UAV surveillance [3], where extending the mission time and guaranteeing the quality of the video transmission service are essential. In addition, our topology control can be deployed in the Wireless Sensor Network (WSN) scenario since the WSN nodes commonly have intensive power constraints. Due to the compatibility of the system, our proposed scheme can be the breakthrough to solve energy-efficiency and performance-degradation problems in wireless network domains.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| UAV | Unmanned Aerial Vehicle |
| FC | Fully Connected |
| SMST | Simple Minimum Spanning Tree |
| SI | Swarm Intelligence |
References
- Hambling, D. Swarm Troopers: How Small Drones Will Conquer the World; Archangel Ink: Venice, FL, USA, 2015. [Google Scholar]
- Chung, A.Y.; Jung, J.; Kim, K.; Lee, H.K.; Lee, J.; Lee, S.K.; Yoo, S.; Kim, H. Poster: Swarming drones can connect you to the network. In Proceedings of the 13th Annual International Conference on Mobile Systems, Applications, and Services, MobiSys 2015, Florence, Italy, 19–22 May 2015; Association for Computing Machinery, Inc.: New York, NY, USA, 2015; p. 477. [Google Scholar]
- Jung, J.; Yoo, S.; La, W.; Lee, D.; Bae, M.; Kim, H. Avss: Airborne video surveillance system. Sensors 2018, 18, 1939. [Google Scholar] [CrossRef] [PubMed]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE Commun. Surv. Tutor. 2015, 18, 1123–1152. [Google Scholar] [CrossRef]
- Bekmezci, I.; Sahingoz, O.K.; Temel, Ş. Flying ad-hoc networks (FANETs): A survey. Ad Hoc Netw. 2013, 11, 1254–1270. [Google Scholar] [CrossRef]
- Li, X.; Guo, D.; Yin, H.; Wei, G. Drone-assisted public safety wireless broadband network. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), New Orleans, LA, USA, 9–12 March 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 323–328. [Google Scholar]
- Kagawa, T.; Ono, F.; Shan, L.; Takizawa, K.; Miura, R.; Li, H.B.; Kojima, F.; Kato, S. A study on latency-guaranteed multi-hop wireless communication system for control of robots and drones. In Proceedings of the 2017 20th International Symposium on Wireless Personal Multimedia Communications (WPMC), Bali, Indonesia, 17–20 December 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 417–421. [Google Scholar]
- Katila, C.J.; Okolo, B.; Buratti, C.; Verdone, R.; Caire, G. UAV-to-Ground Multi-Hop Communication Using Backpressure and FlashLinQ-Based Algorithms. In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1179–1184. [Google Scholar]
- Ebert, J.P.; Wolisz, A. Combined tuning of RF power and medium access control for WLANs. Mob. Netw. Appl. 2001, 6, 417–426. [Google Scholar] [CrossRef]
- Ebert, J.P.; Stremmel, B.; Wiederhold, E.; Wolisz, A. An energy-efficient power control approach for WLANs. J. Commun. Netw. 2000, 2, 197–206. [Google Scholar] [CrossRef]
- Iwai, K.; Ohnuma, T.; Shigeno, H.; Tanaka, Y. Improving of Fairness by Dynamic Sensitivity Control and Transmission Power Control with Access Point Cooperation in Dense WLAN. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Vegas, NV, USA, 11–14 January 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–4. [Google Scholar]
- Lee, W.; Lee, J.; Lee, J.; Kim, K.; Yoo, S.; Park, S.; Kim, H. Ground Control System Based Routing for Reliable and Efficient Multi-Drone Control System. Appl. Sci. 2018, 8, 2027. [Google Scholar] [CrossRef]
- Ur Rahman, S.; Kim, G.H.; Cho, Y.Z.; Khan, A. Positioning of UAVs for throughput maximization in software-defined disaster area UAV communication networks. J. Commun. Netw. 2018, 20, 452–463. [Google Scholar] [CrossRef]
- Wang, X.; Yadav, V.; Balakrishnan, S. Cooperative UAV formation flying with obstacle/collision avoidance. IEEE Trans. Control. Syst. Technol. 2007, 15, 672–679. [Google Scholar] [CrossRef]
- Park, S.; Kim, K.; Kim, H.; Kim, H. Formation control algorithm of multi-UAV-based network infrastructure. Appl. Sci. 2018, 8, 1740. [Google Scholar] [CrossRef]
- Sabino, S.; Horta, N.; Grilo, A. Centralized unmanned aerial vehicle mesh network placement scheme: A multi-objective evolutionary algorithm approach. Sensors 2018, 18, 4387. [Google Scholar] [CrossRef] [PubMed]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef]
- Monks, J.P.; Bharghavan, V.; Hwu, W.M. A power controlled multiple access protocol for wireless packet networks. In Proceedings of the IEEE INFOCOM 2001, Conference on Computer Communications, Twentieth Annual Joint Conference of the IEEE Computer and Communications Society (Cat. No. 01CH37213), Anchorage, AK, USA, 22–26 April 2001; IEEE: Piscataway, NJ, USA, 2001; Volume 1, pp. 219–228. [Google Scholar]
- Kim, J.; Jeong, J. Range-adaptive wireless power transfer using multiloop and tunable matching techniques. IEEE Trans. Ind. Electron. 2015, 62, 6233–6241. [Google Scholar] [CrossRef]
- Zhang, W.; Wang, J.; Han, G.; Zhang, X.; Feng, Y. A cluster sleep-wake scheduling algorithm based on 3D topology control in underwater sensor networks. Sensors 2019, 19, 156. [Google Scholar] [CrossRef] [PubMed]
- Kim, J.; Kwon, Y. 3-dimensional topology control for wireless sensor networks in presence of interference. In Proceedings of the 2010 Digest of Technical Papers International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 9–13 January 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 471–472. [Google Scholar]
- Rauch, H.E.; Winarske, T. Neural networks for routing communication traffic. IEEE Control. Syst. Mag. 1988, 8, 26–31. [Google Scholar] [CrossRef]
- Broumi, S.; Bakal, A.; Talea, M.; Smarandache, F.; Vladareanu, L. Applying Dijkstra algorithm for solving neutrosophic shortest path problem. In Proceedings of the 2016 International Conference on Advanced Mechatronic Systems (ICAMechS), Melbourne, Australia, 30 November–3 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 412–416. [Google Scholar]
- Kumaran, S.; Sankaranarayanan, V. Congestion Free Routing in ad-hoc Networks. J. Comput. Sci. 2012, 8, 971–977. [Google Scholar]
- Samaraweera, N.K.; Fairhurst, G. Reinforcement of TCP error recovery for wireless communication. ACM SIGCOMM Comput. Commun. Rev. 1998, 28, 30–38. [Google Scholar] [CrossRef]

| Item | Value |
|---|---|
| Space size | 1000 m × 1000 m × 1000 m |
| Number of UAVs | 50 |
| Maximum transmission power | 20 dBm |
| Frequency band | 2.4 GHz |
| Antenna gain | 2.5 dBi |
| Receive signal threshold | −70 dBm |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, S.; Kim, H.T.; Kim, H. Energy-Efficient Topology Control for UAV Networks. Energies 2019, 12, 4523. https://doi.org/10.3390/en12234523
Park S, Kim HT, Kim H. Energy-Efficient Topology Control for UAV Networks. Energies. 2019; 12(23):4523. https://doi.org/10.3390/en12234523
Chicago/Turabian StylePark, Seongjoon, Hyeong Tae Kim, and Hwangnam Kim. 2019. "Energy-Efficient Topology Control for UAV Networks" Energies 12, no. 23: 4523. https://doi.org/10.3390/en12234523
APA StylePark, S., Kim, H. T., & Kim, H. (2019). Energy-Efficient Topology Control for UAV Networks. Energies, 12(23), 4523. https://doi.org/10.3390/en12234523






