The IEC 61850 Sampled Measured Values Protocol: Analysis, Threat Identification, and Feasibility of Using NN Forecasters to Detect Spoofed Packets †
Abstract
1. Introduction
- (1)
- Manufacturing Message Specification (MMS) protocol, which is utilized in high-level control layers and automation functionalities;
- (2)
- Generic Object-Oriented Substation Event (GOOSE), which is used in real-time event-driven situations (e.g., sending a signal to open a circuit breaker);
- (3)
- Sampled Measured Values (SMV) that is utilized in continuous real-time monitoring and control.
- The authors’ previous work examined the SMV protocol, its pros and cons, and the feasibility of incorporating it for smart grid applications. A discussion and explanation of the current cyber vulnerabilities of the smart grid and the possible counter measures, emphasizing on the SMV cyber threats were presented. Finally, an investigation of the feasibility of using a Neural Network Forecaster (NN-F) to detect spoofed SMV packets on a simulated microgrid was presented.
- (1)
- Proposing a lightweight bi-layer algorithm that is able to detect the accumulation of forecasting error and successfully identify spoofed packets.
- (2)
- Implementing and verifying the proposed bi-layer algorithm on a hardware hybrid microgrid with microcontrollers running a Linux kernel and communicating over a real IEC 61850 network.
- Section 2 highlights the work related to the applications of artificial intelligence tools (e.g., Machine learning) in cybersecurity;
- Section 3 discusses the structure of the SMV datagram and gives a general overview about the SMV advantages;
- Section 4 explains the various types of cyber threats and the possible protection actions. Also, it emphasizes on SMV spoofing attack and outlines the conducted research regarding this topic;
- Section 5 introduces a bi-layer forecasting algorithm to detect the SMV spoofing attacks using NN-F. Also, it discusses in detail the construction of Neural Network Forecaster (NN-F) detection-based framework;
- Section 6 describes the simulation model used for creating rich training and testing data sets.
- Section 7 discusses the results.
- Section 8 concludes the paper.
2. Applications of Artificial Intelligence Tools in Attack Detection
3. The Sampled Measure Values Protocol
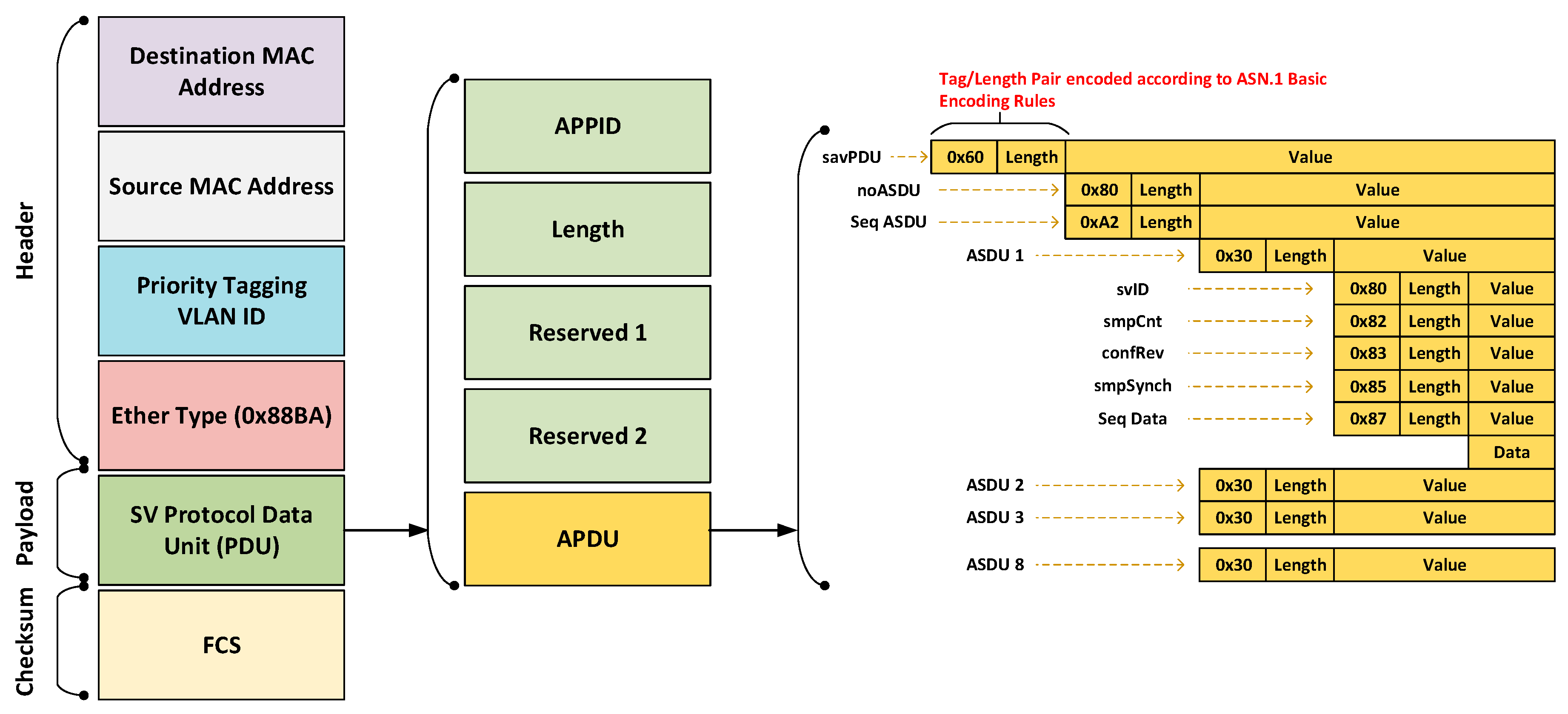
3.1. Structure of the SMV Datagram
- svID: Sample Value ID;
- SmpCnt: Counter that increments each time a new sampling value is taken;
- ConfRev: Value that indicates the number of configuration changes;
- SmpSynch: A Boolean value that is true if the SV is synchronized by a clock signal and false if it is not;
- Seq Data: Sequence of data;
- Data: The actual dataset.
3.2. Advantages of an SMV Process Bus
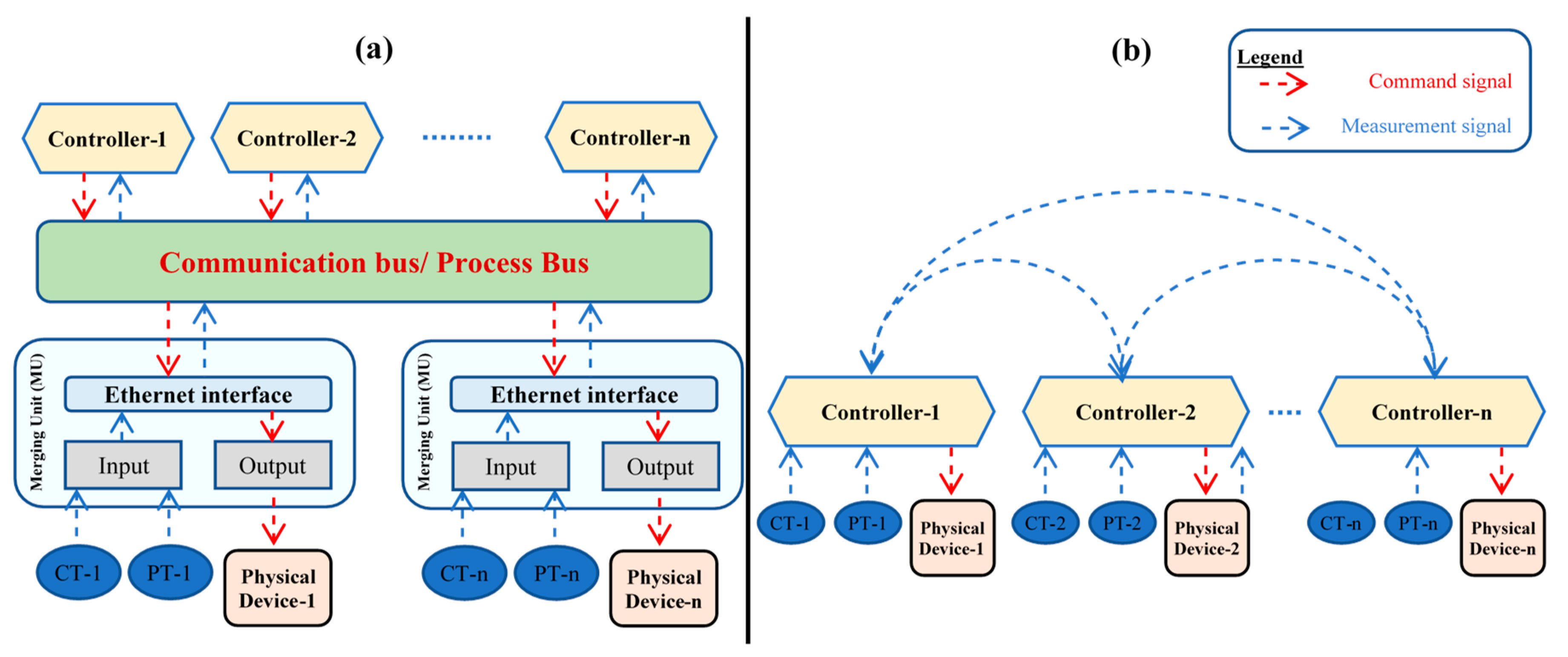
- In terms of system monitoring, the messages stream on a networked process bus will be composed of well-structured SMV packets, each with its unique identifier. This will allow for easy classification and improve the visibility of the power network [2].
- In terms of cost, the networked process bus replaces point-to-point analogue connections between devices as shown in Figure 1b. This will drastically reduce the copper wiring involved, thus reducing costs and saving on installation and maintenance.
- In terms of control, the SMV process bus facilitates the migration to decentralized and/or distributed control from the current centralized control scheme, which will enhance the reliability of the power network. Centralized control is characterized by a single server, which receives measurements from all the sensors in a system and gives actuation commands. A centralized server is considered as a single-point-of-failure (i.e., a bottleneck). Decentralized and distributed control avoid this vulnerability.
- In terms of data handling, the SMV process bus provides vendor-independence. That is, IEC 61850 SMV-compliant devices should abide by the message structure shown in Figure 2. Therefore, achieving data interoperability.
4. Threat Identification and Current Mitigation Strategies
4.1. Denial of Service (DoS)
4.2. Eavesdropping
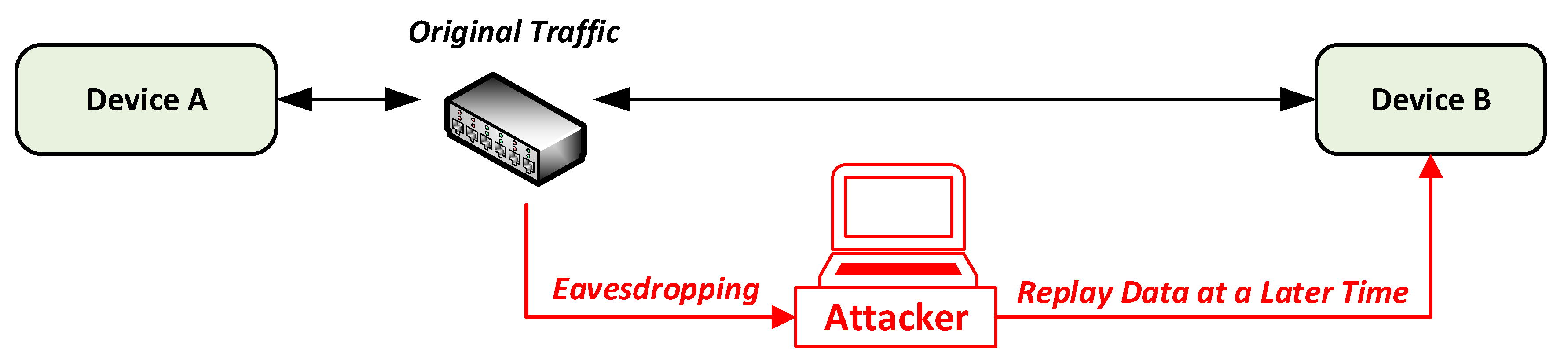
4.3. Replay
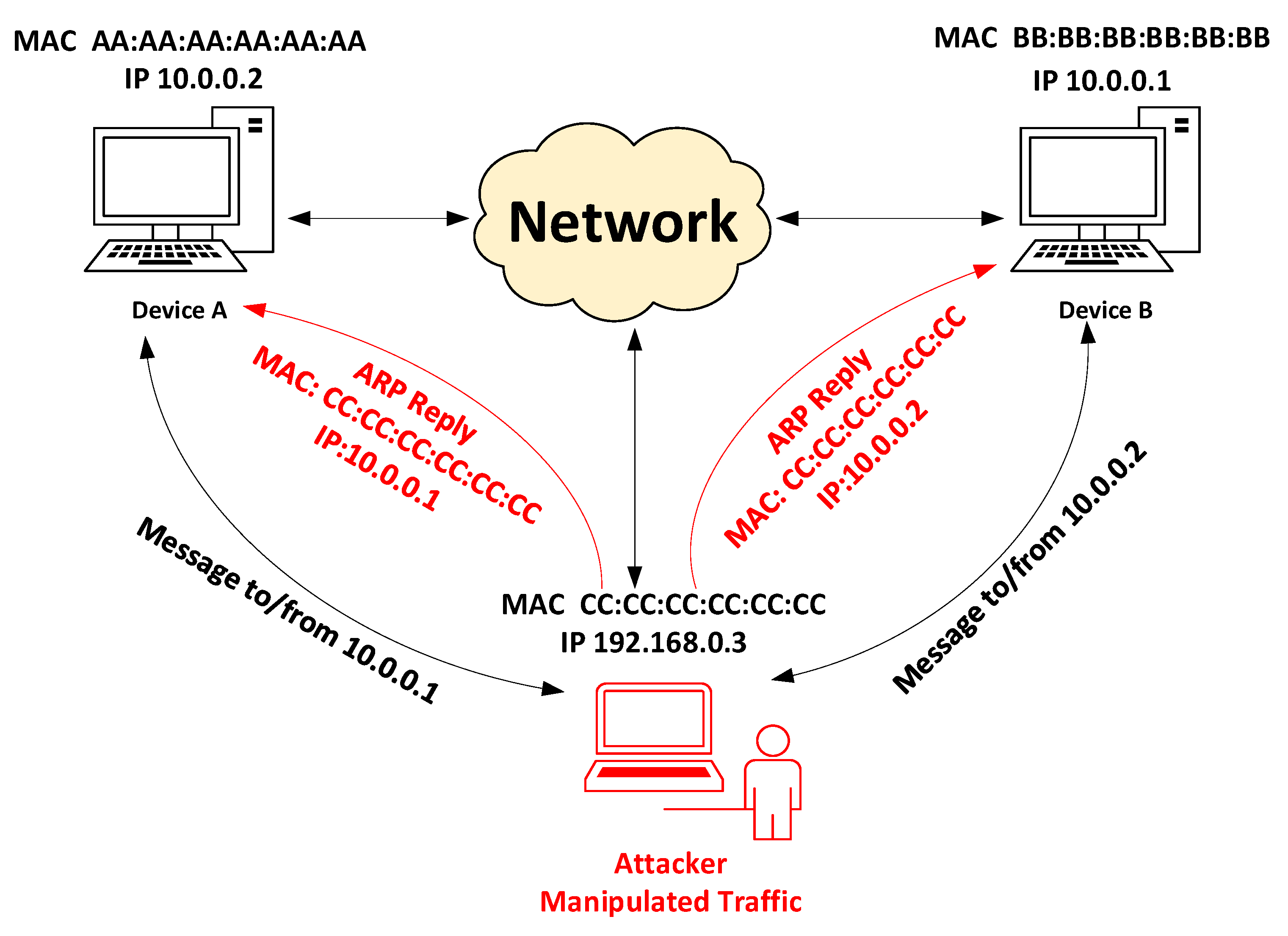
4.4. Man-in-the-Middle (MITM)
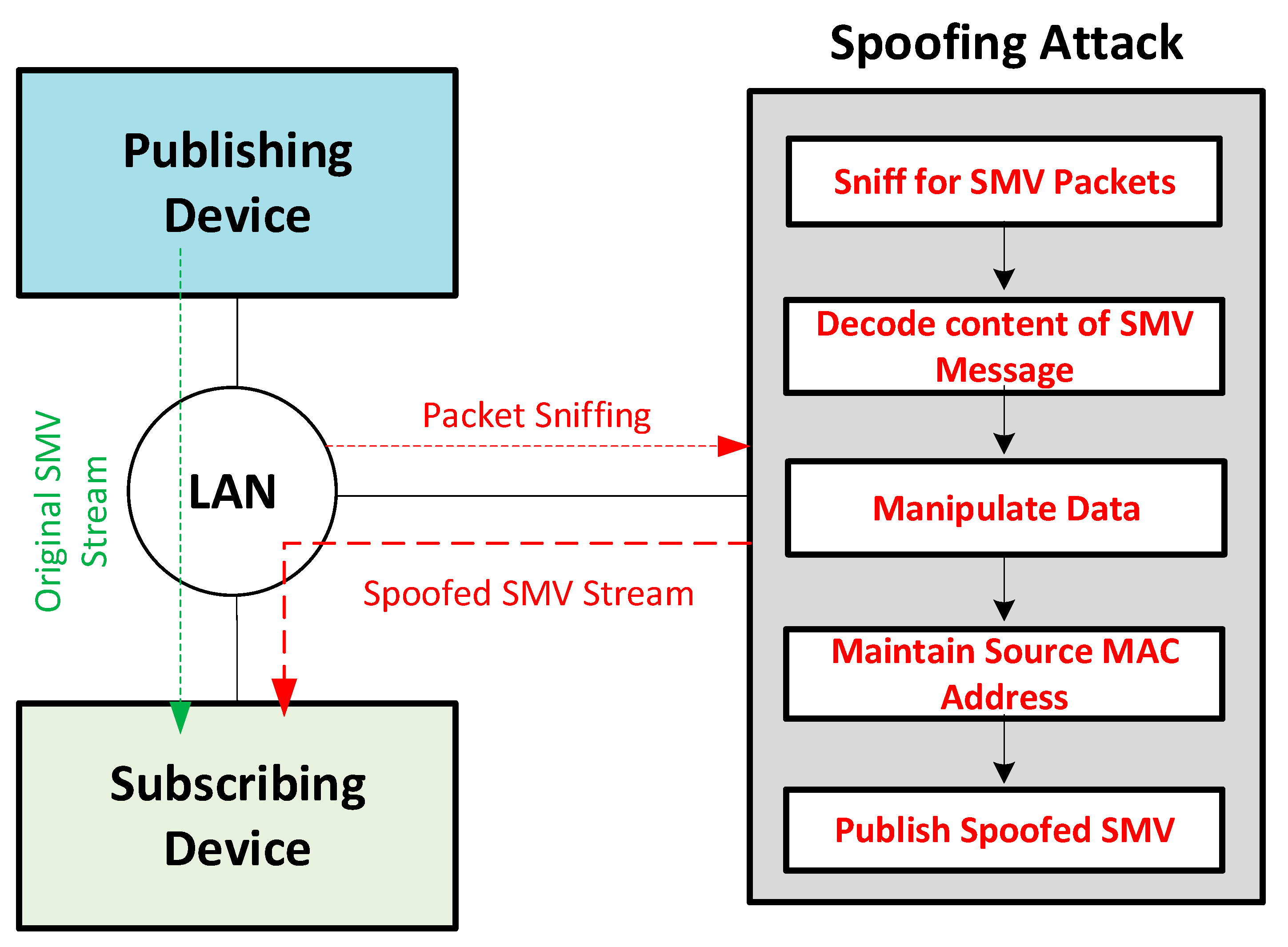
4.5. SMV Spoofing
5. Feasibility Study and Detailed Description of Using Neural-Network-Forecasters in Power Systems for Detection of SMV Spoofing Attacks
- -
- Firstly, describe the system understudy and the flow/exchange of data within this system;
- -
- Secondly, explain the SMV spoofing attack formulation;
- -
- Finally, introduce a bi-layer Neural-Network-forecasting algorithm to detect and prevent such attacks.
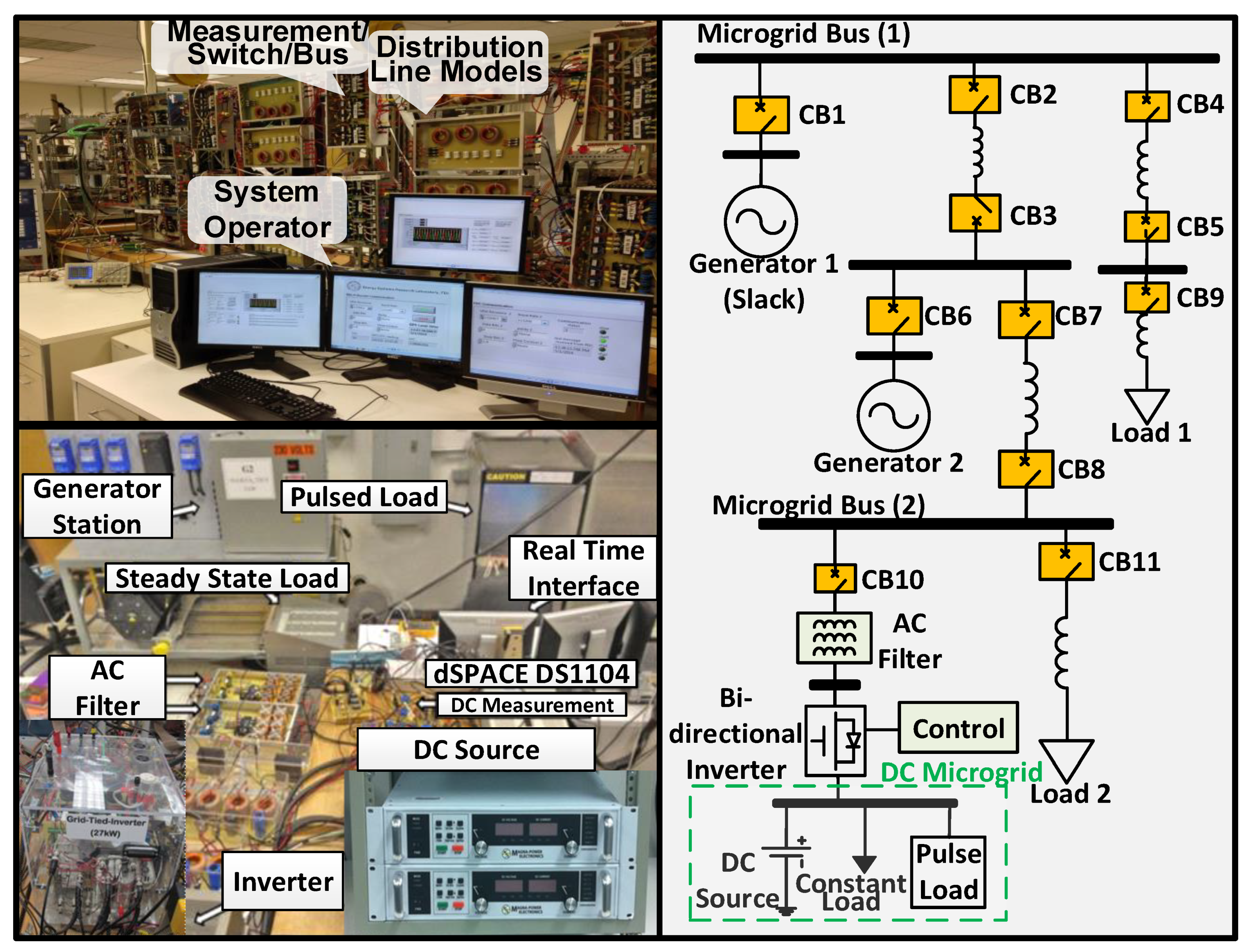
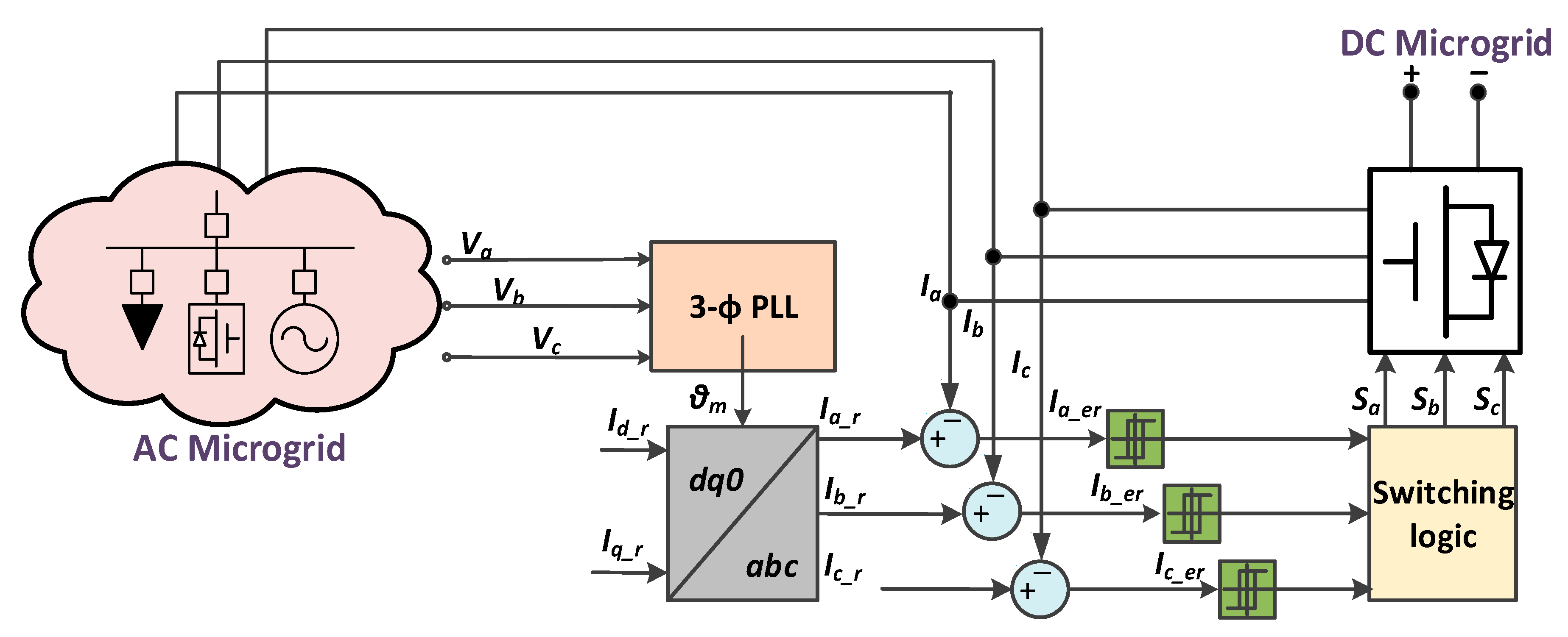
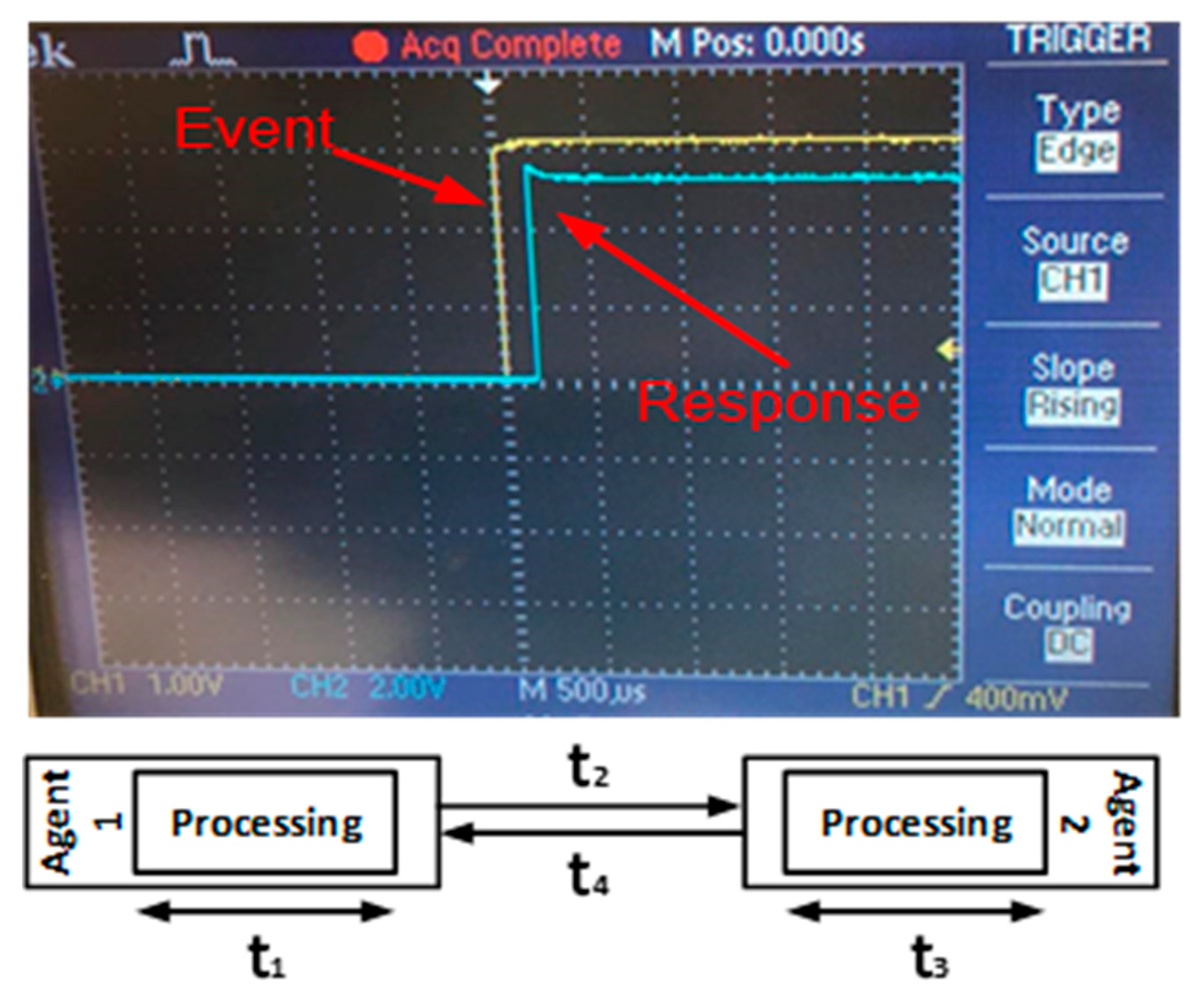
5.1. System Understudy
- -
- Generators 1 and 2 with ratings 13.8 KVA and 10.3 KVA, respectively. Both are 230 V;
- -
- Two variable loads, each has 10 steps (300 W to 3 kW). Both loads were set to 600 W during the experiment;
- -
- Measurement and protection devices: each bus has a 3-phase input/output relay, and each phase has its own potential and current transformer for measurements.
- -
- A DC source resembling a DER;
- -
- A 60 ohms constant DC load and a 12 ohms resistive pulse DC load.
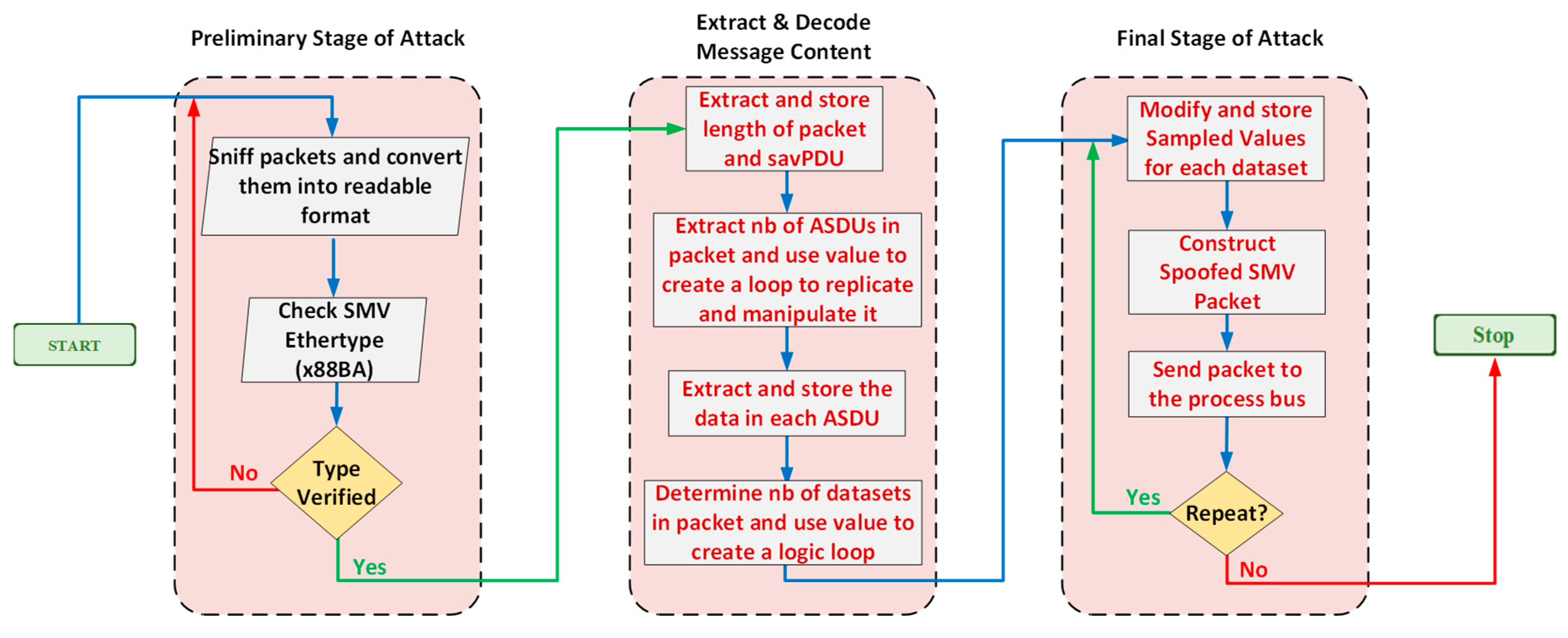
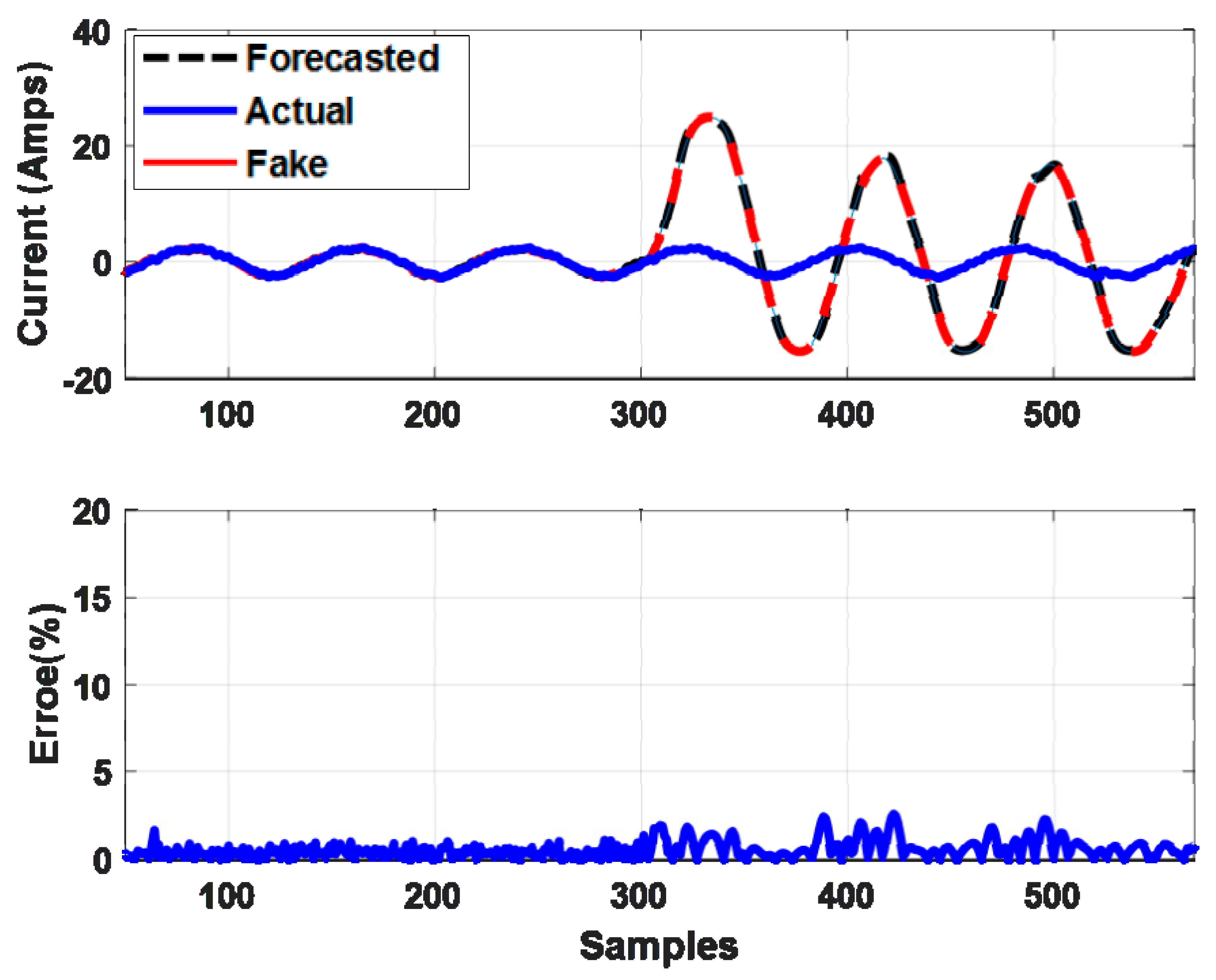
5.2. SMV Spoofing Attack Scenario
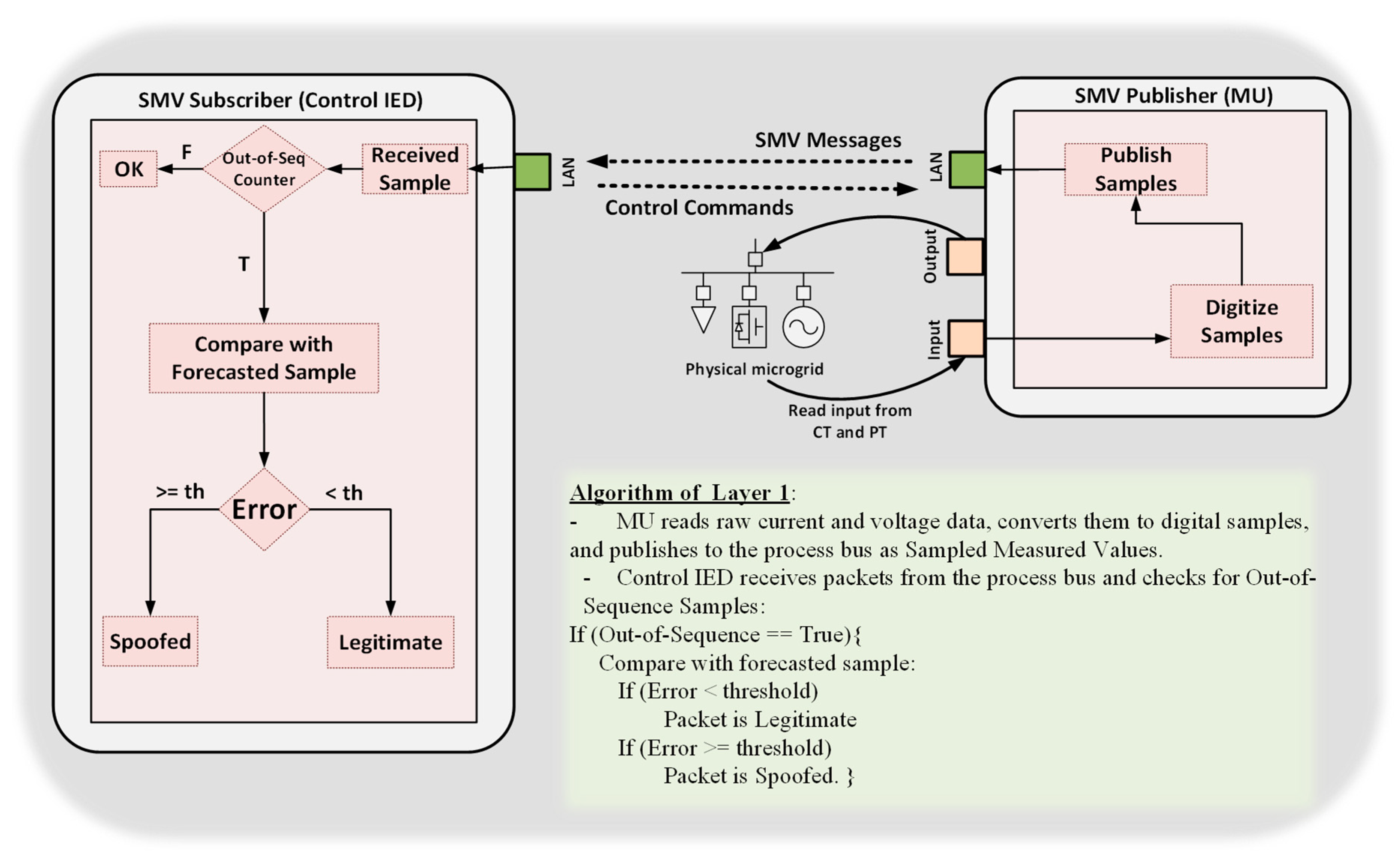
5.3. The Bi-Layer Neural-Network-Forecasting Algorithm to Detect Spoofed SMV Attack
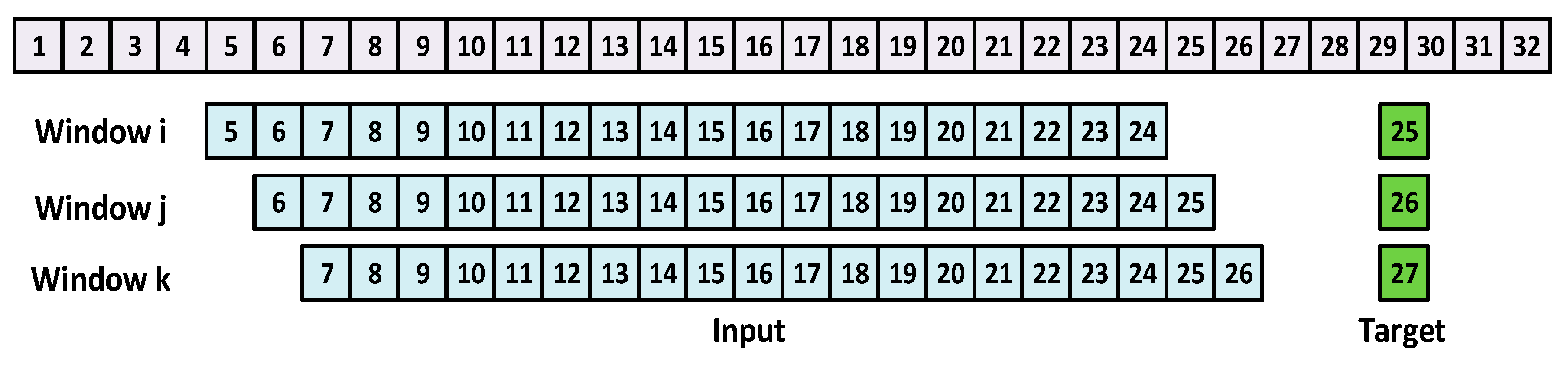
5.3.1. Layer 1: The Neural-Network-Forecaster
- (1)
- Prevention: to develop cyber security solutions that ensure resilient delivery of energy. Work in this area includes authentication, encryption, key management and storage, and others.
- (2)
- Detection: to develop cyber security solutions that are capable of identifying the occurrence of cyber incidents. Work in this area includes anomaly detection, detection of false (or spoofed) data injection attacks, detection of password cracking attempts, and others.
- (3)
- Response: to develop cyber security solutions that take appropriate measures in response to the detected cyber incidents.
- (4)
- Recovery: to develop tools and techniques that allow the restoration of energy and other services that were lost due to cyber incidents.
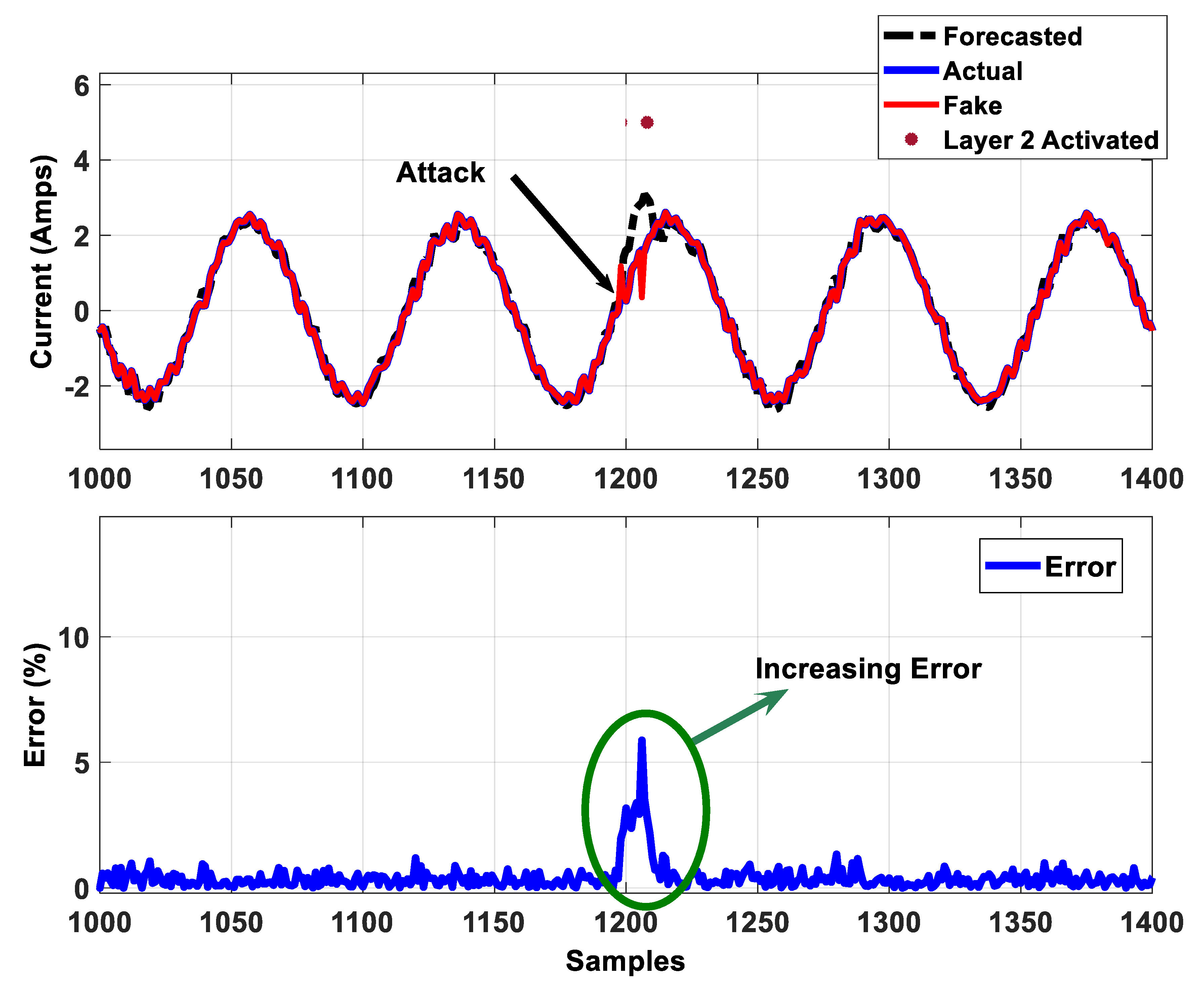
5.3.2. Layer 2: Enhancing the Resiliency of the Neural Network Forecaster
- (1)
- The first set contains one of the suspected samples (Sample A), five previous samples, and the five new samples, which were monitored.
- (2)
- The second dataset contains the other suspected sample (Sample B), five previous samples, and the five new monitored samples.
6. Model Development and Verification
7. Results and Discussion
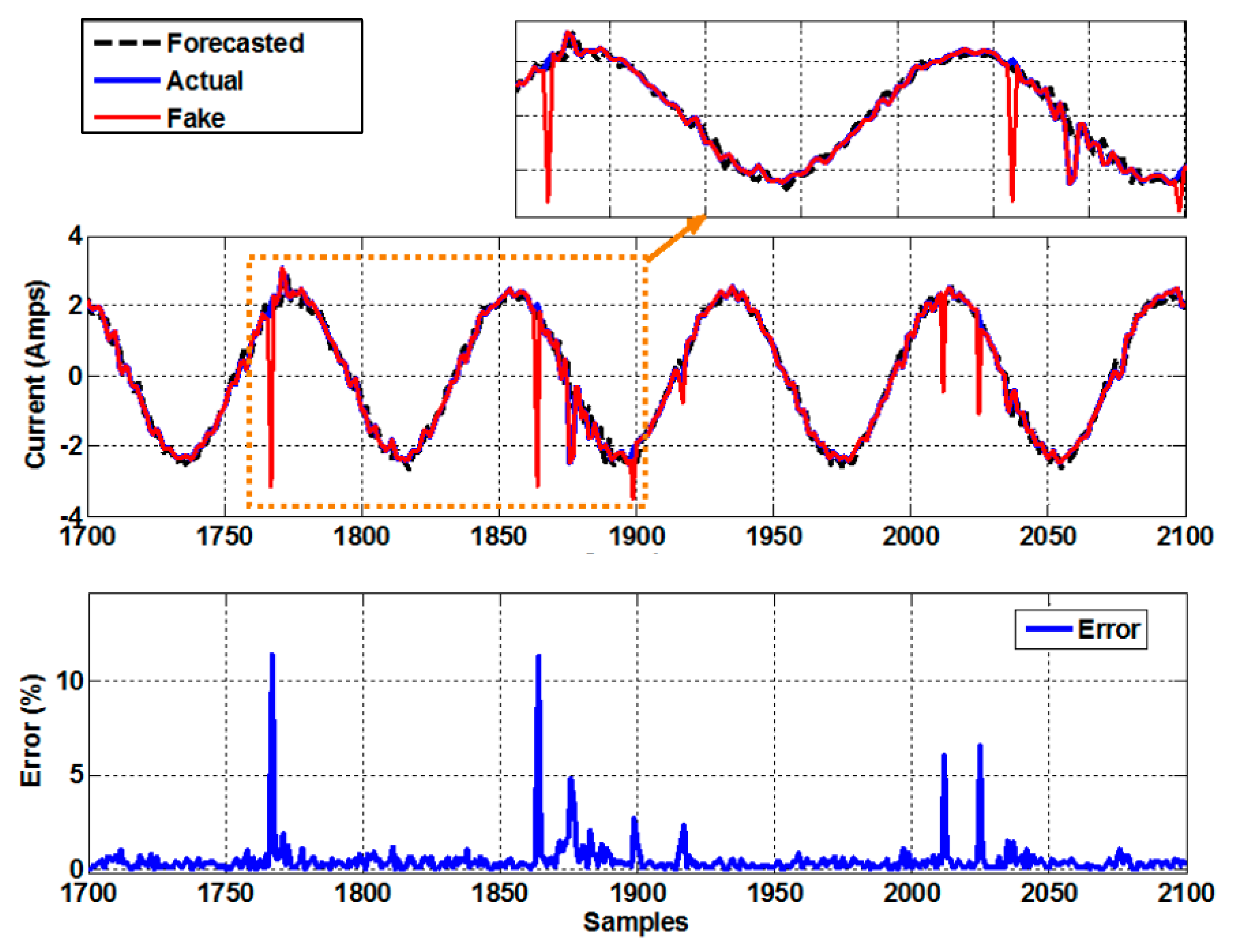
7.1. Experiment 1
7.2. Experiment 2
7.3. Experiment 3
8. Conclusions and Recommendations for Future Work
8.1. Conclusions
8.2. Recommendations for Future Work
9. Patents
Author Contributions
Funding
Conflicts of Interest
References
- Cintuglu, M.H.; Youssef, T.; Mohammed, O.A. Development and Application of a Real-Time Testbed for Multiagent System Interoperability: A Case Study on Hierarchical Microgrid Control. IEEE Trans. Smart Grid 2016, 9, 1759–1768. [Google Scholar] [CrossRef]
- el Hariri, M.; Youssef, T.A.; Mohammed, O.A. On the Implementation of the IEC 61850 Standard: Will Different Manufacturer Devices Behave Similarly under Identical Conditions? Electronics 2016, 5, 85. [Google Scholar] [CrossRef]
- Hariri, M.E.; Youssef, T.; Harmon, E.; Habib, H.; Mohammed, O. The IEC 61850 Sampled Measured Values Protocol: Analysis, Threat Identification, and Feasibility of Using NN Forecasters to Detect of Spoofed Packets. In Proceedings of the 2019 IEEE International Conference on Environment and Electrical Engineering and 2019 IEEE Industrial and Commercial Power Systems Europe (EEEIC / I&CPS Europe), Genova, Italy, 10–14 June 2019; pp. 1–6. [Google Scholar]
- Borges, C.E.; Penya, Y.K.; Fernández, I. Evaluating combined load forecasting in large power systems and smart grids. IEEE Trans. Ind. Inform. 2012, 9, 1570–1577. [Google Scholar] [CrossRef]
- Bessa, R.J.; Trindade, A.; Miranda, V. Spatial-Temporal Solar Power Forecasting for Smart Grids. IEEE Trans. Ind. Inf. 2014, 11, 232–241. [Google Scholar] [CrossRef]
- Evangelos, F.; Brett, A.; Reza, A.; Daniel, B.; Pavel, E.; Murph, S. Data Mining Techniques and Tools for Synchrophasor Data; NASPI WHITE PAPER; Engineering Analysis Task Team: San Diego, CA, USA, January 2019. [CrossRef]
- Ozay, M.; Esnaola, I.; Vural, F.T.Y.; Kulkarni, S.R.; Poor, H.V. Machine Learning Methods for Attack Detection in the Smart Grid. IEEE Trans. Neural Netw. Learn. Syst. 2016, 27, 1773–1786. [Google Scholar] [CrossRef] [PubMed]
- Wu, Y.; Xiao, Y.; Hohn, F.; Nordstrom, L.; Wang, J.; Zhao, W. Bad Data Detection Using Linear WLS and Sampled Values in Digital Substations. IEEE Trans. Power Deliv. 2017, 33, 150–157. [Google Scholar] [CrossRef]
- Vimalkumar, K.; Radhika, N. A big data framework for intrusion detection in smart grids using apache spark. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Udupi, India, 13–16 September 2017; pp. 198–204. [Google Scholar]
- Faisal, M.A.; Aung, Z.; Williams, J.R.; Sanchez, A. Data-Stream-Based Intrusion Detection System for Advanced Metering Infrastructure in Smart Grid: A Feasibility Study. IEEE Syst. J. 2015, 9, 31–44. [Google Scholar] [CrossRef]
- Hong, J.; Liu, C.; Govindarasu, M. Integrated Anomaly Detection for Cyber Security of the Substations. IEEE Trans. Smart Grid 2014, 5, 1643–1653. [Google Scholar] [CrossRef]
- Pan, S.; Morris, T.; Adhikari, U. Developing a Hybrid Intrusion Detection System Using Data Mining for Power Systems. IEEE Trans. Smart Grid 2015, 6, 3104–3113. [Google Scholar] [CrossRef]
- Leu, F.; Tsai, K.; Hsiao, Y.; Yang, C. An Internal Intrusion Detection and Protection System by Using Data Mining and Forensic Techniques. IEEE Syst. J. 2017, 11, 427–438. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Fouda, M.M.; Kato, N.; Shen, X.; Nozaki, Y. An early warning system against malicious activities for smart grid communications. IEEE Netw. 2011, 25, 50–55. [Google Scholar] [CrossRef]
- Koutsandria, G.; Muthukumar, V.; Parvania, M.; Peisert, S.; McParland, C.; Scaglione, A. A hybrid network IDS for protective digital relays in the power transmission grid. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 908–913. [Google Scholar]
- Ten, C.W.; Hong, J.; Liu, C.C. Anomaly Detection for Cybersecurity of the Substations. IEEE Trans. Smart Grid 2011, 2, 865–873. [Google Scholar] [CrossRef]
- Sridhar, S.; Govindarasu, M. Model-Based Attack Detection and Mitigation for Automatic Generation Control. IEEE Trans. Smart Grid 2014, 5, 580–591. [Google Scholar] [CrossRef]
- Zhao, J.; Zhang, G.; la Scala, M.; Dong, Z.Y.; Chen, C.; Wang, J. Short-Term State Forecasting-Aided Method for Detection of Smart Grid General False Data Injection Attacks. IEEE Trans. Smart Grid 2015, 8, 1580–1590. [Google Scholar] [CrossRef]
- Ali, M.Q.; Yousefian, R.; Al-Shaer, E.; Kamalasadan, S.; Zhu, Q. Two-tier data-driven intrusion detection for automatic generation control in smart grid. In Proceedings of the 2014 IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; pp. 292–300. [Google Scholar]
- Mashima, D.; Chen, B.; Zhou, T.; Rajendran, R.; Sikdar, B. Securing Substations through Command Authentication Using On-the-fly Simulation of Power System Dynamics. In Proceedings of the 2018 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aalborg, Denmark, 29–31 October 2018; pp. 1–7. [Google Scholar]
- Meliopoulos, S.; Cokkinides, G.; Fan, R.; Sun, L.; Cui, B. Command authentication via faster than real time simulation. In Proceedings of the 2016 IEEE Power and Energy Society General Meeting (PESGM), Boston, MA, USA, 19 July 2016; pp. 1–5. [Google Scholar]
- Yang, Y.; McLaughlin, K.; Sezer, S.; Littler, T.; Im, E.G.; Pranggono, B.; Wang, H.F. Multiattribute SCADA-Specific Intrusion Detection System for Power Networks. IEEE Trans. Power Deliv. 2014, 29, 1092–1102. [Google Scholar] [CrossRef]
- Kaliski, B.S., Jr. A Layman’s Guide to a Subset of ASN.1, BER, and DER, AN RSA Laboratories Technical Note. Available online: http://luca.ntop.org/Teaching/Appunti/asn1.html (accessed on 19 August 2019).
- International Electrotechnical Commission. Security for IEC 61850 Profiles; IEC 62351-6; International Electrotechnical Commission: Geneva, Switzerland.
- Kanabar, M.G.; Sidhu, T.S. Performance of IEC 61850-9-2 Process Bus and Corrective Measure for Digital Relaying. IEEE Trans. Power Deliv. 2010, 26, 725–735. [Google Scholar] [CrossRef]
- Ingram, D.M.E.; Schaub, P.; Taylor, R.R.; Campbell, D.A. Performacnce Analysis of IEC 61850 Sampled value Process Bus. IEEE Trans Ind. Inform. 2012, 9, 1445–1454. [Google Scholar] [CrossRef]
- IEC 61850-9-2 International Standard Communication Networks and Systems in Substations; International Electrotechnical Commission: Geneva, Switzerland, 2004.
- Hoyos, J.; Dehus, M.; Brown, T.X. Exploiting the goose protocol: A practical attack on cyber-infrastructure. In Proceedings of the 2012 IEEE Globecom Workshops (GC Wkshps), Anaheim, CA, USA, 3–7 December 2012; pp. 1508–1513. [Google Scholar]
- Lin, H.; Slagell, A.; Kalbarczyk, Z.; Sauer, P.; Iyer, R. Runtime Semantic Security Analysis to Detect and Mitigate Control-related Attacks in Power Grids. IEEE Trans. Smart Grid 2016, 9, 163–178. [Google Scholar] [CrossRef]
- Falliere, N.; Murchu, L.O.; Chien, E. W32.Stuxnet Dossier, Symantic Security Response Report. Version 1.4. Available online: https://dragos.com/wp-content/uploads/CrashOverride-01.pdf (accessed on 15 September 2019).
- DRAGOS INC. Report Version 2.20170613 Crashoverride: Analyses of the Threat to Electric Grid Operation. Available online: https://dragos.com/wp-content/uploads/CrashOverride-01.pdf (accessed on 15 September 2019).
- Packet Sniffing Attack Prevention. Available online: https://cconell2858.wordpress.com/packet-sniffing-attack-prevention/ (accessed on 15 September 2019).
- Youssef, T.A.; Hariri, M.E.; Bugay, N.; Mohammed, O.A. IEC 61850: Technology standards and cyber-threats. In Proceedings of the 2016 IEEE 16th International Conference on Environment and Electrical Engineering (EEEIC), Florence, Italy, 7–10 June 2016; pp. 1–6. [Google Scholar]
- Fuloria, S.; Anderson, R.; Mcgrath, K.; Hansen, K.; Alvarez, F. The Protection of Substation Communications. In Proceedings of the SCADA Security Scientific Symposium, Miami, FL, USA, 18–19 January 2010. [Google Scholar]
- Obermeier, S.; Schlegel, R.; Obermeier, S.; Schneider, J. Assessing the Security of IEC 6235. In Proceedings of the 3rd International Symposium for ICS & SCADA Cyber Security Research 2015, Ingolstadt, Germany, 17–18 September 2015. [Google Scholar]
- Pubudu Weerathunga, Security Aspects of Smart Grid Communication. Master’s Thesis, The School of Graduate and Postdoctoral Studies Western University London, London, UK, 2012.
- Intel DPDK Validation team, DPDK Intel Cryptodev Performance Report. Available online: https://fast.dpdk.org/doc/perf/DPDK_18_02_Intel_crypto_performance_report.pdf (accessed on 15 September 2019).
- Peyrin, T.; Sasaki, Y.; Wang, L.; Wang, X.; Sako, K. Generic Related-Key Attacks for HMAC. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, 2–6 December 2012; pp. 580–597. [Google Scholar]
- Jayarin, P.J.; Visumathi, J.; Srilakshmi, R.; Pendyala, M. A Secured Key Distribution for Effective File Transfer Using HMAC-SHA Algorithm with Self-Healing Property. J. Appl. Secur. Res. 2015, 10, 221–237. [Google Scholar] [CrossRef]
- Fouque, P.-A.; Leurent, G.; Nguyen, P.Q. Full Key-Recovery Attacks on HMAC/NMAC-MD4 and NMAC-MD5. In Proceedings of the 27th Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2007. [Google Scholar]
- Shmueli, G.; Lichtendahl, K.C. Practical Time Series Forecasting with R: A Hands-On Guide; Axelrod Schnall Publishers: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Lapedes, A.; Farber, R. Nonlinear Signal Processing Using Neural Networks: Prediction and System Modeling; Los Alamos National Laboratory Technical Report: LA-UR-87-2662; IEEE: Piscataway, NJ, USA, 1987. [Google Scholar]
- Zhang, G.P. Neural Networks for Time-Series Forecasting from the Handbook of Natural Computing; Springer: Berlin/Heidelberg, Germany, 2012; pp. 461–477. [Google Scholar]





| G1 Bus | G2 Bus | AC Load 1 | AC Load 2 | DC Microgrid | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| S | E | S | E | S | E | S | E | S | E | |
| Irms | 2.1 | 2.6 | 0.7 | 0.8 | 1.5 | 1.2 | 1.3 | 1.5 | 0.4 | 0.4 |
| Vrms | 120 | 119 | 120 | 120 | 116 | 116 | 118 | 119 | 118 | 118 |
| P (W) | 761 | 758 | 243 | 255 | 431 | 435 | 441 | 442 | 170 | 170 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
El Hariri, M.; Harmon, E.; Youssef, T.; Saleh, M.; Habib, H.; Mohammed, O. The IEC 61850 Sampled Measured Values Protocol: Analysis, Threat Identification, and Feasibility of Using NN Forecasters to Detect Spoofed Packets. Energies 2019, 12, 3731. https://doi.org/10.3390/en12193731
El Hariri M, Harmon E, Youssef T, Saleh M, Habib H, Mohammed O. The IEC 61850 Sampled Measured Values Protocol: Analysis, Threat Identification, and Feasibility of Using NN Forecasters to Detect Spoofed Packets. Energies. 2019; 12(19):3731. https://doi.org/10.3390/en12193731
Chicago/Turabian StyleEl Hariri, Mohamad, Eric Harmon, Tarek Youssef, Mahmoud Saleh, Hany Habib, and Osama Mohammed. 2019. "The IEC 61850 Sampled Measured Values Protocol: Analysis, Threat Identification, and Feasibility of Using NN Forecasters to Detect Spoofed Packets" Energies 12, no. 19: 3731. https://doi.org/10.3390/en12193731
APA StyleEl Hariri, M., Harmon, E., Youssef, T., Saleh, M., Habib, H., & Mohammed, O. (2019). The IEC 61850 Sampled Measured Values Protocol: Analysis, Threat Identification, and Feasibility of Using NN Forecasters to Detect Spoofed Packets. Energies, 12(19), 3731. https://doi.org/10.3390/en12193731









