T2S2G: A Novel Two-Tier Secure Smart Grid Architecture to Protect Network Measurements
Abstract
1. Introduction
- A novel two-tier secure smart grid (T2S2G) architecture is designed with RTUs, aggregators in first tier and control server in second tier. T2S2G protects SG system from FDI attacks and detects compromised meters.
- Initially the entire T2S2G system is segregated into four sections by the weighted quad tree (WQT) method in order to support the distributed SE process. In each section, an aggregator is deployed in the static position.
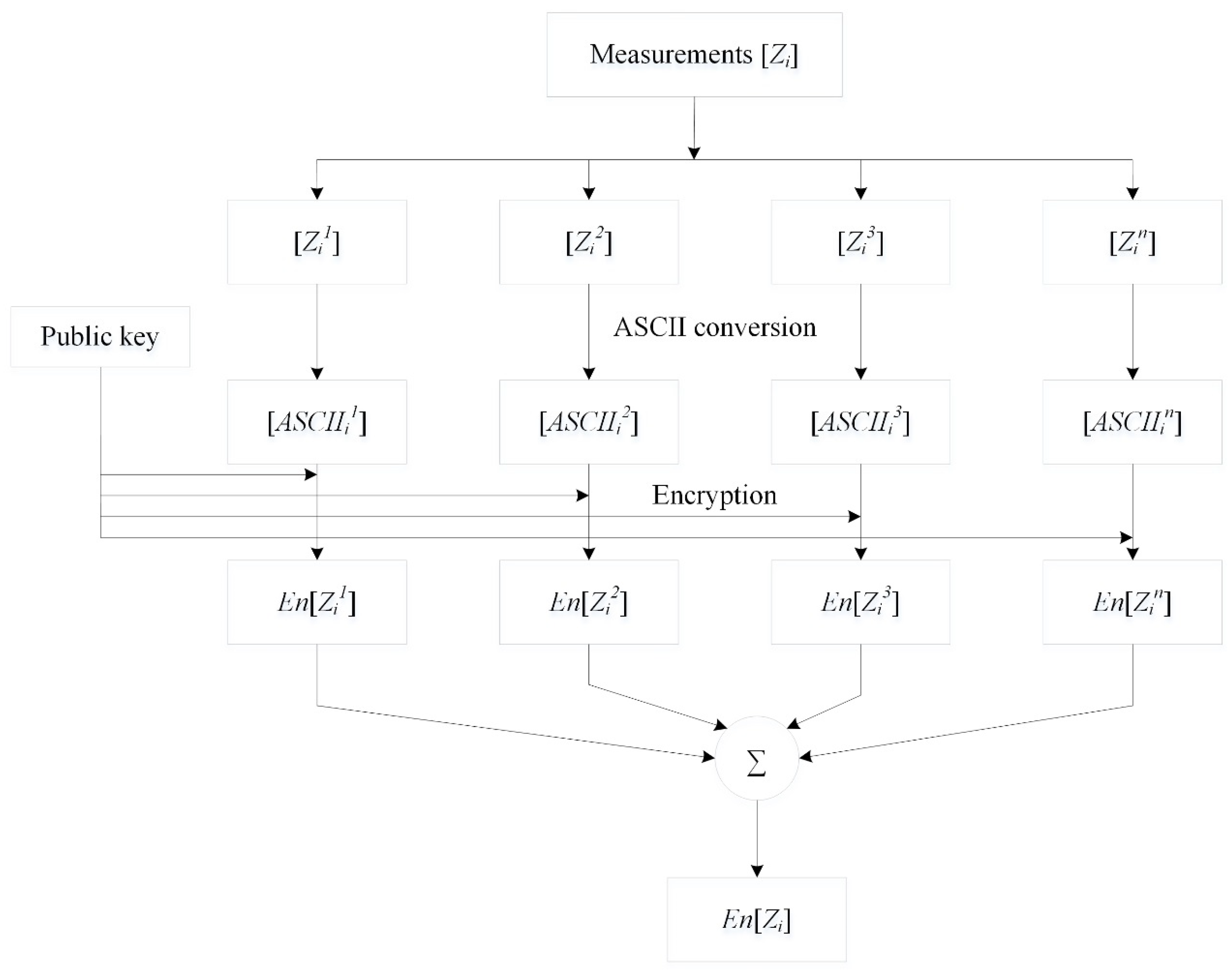
- All measurements are secured by RTUs using the parallel enhanced elliptic curve cryptography (PEECC) algorithm, which ensures high level data security with minimum time consumption.
- After receiving all measurements from RTUs in the section, aggregator performs SE. For SE, we proposed an amended PSO (APSO) algorithm. The proposed SE method minimizes computational overhead as well as estimation error.
- For verifying authenticity of aggregators, each aggregator is authenticated at the control server by using the logical schedule based authentication (LSA) scheme. Involvement of the LSA scheme prevents processing of unnecessary measurements from intruders in the control server.
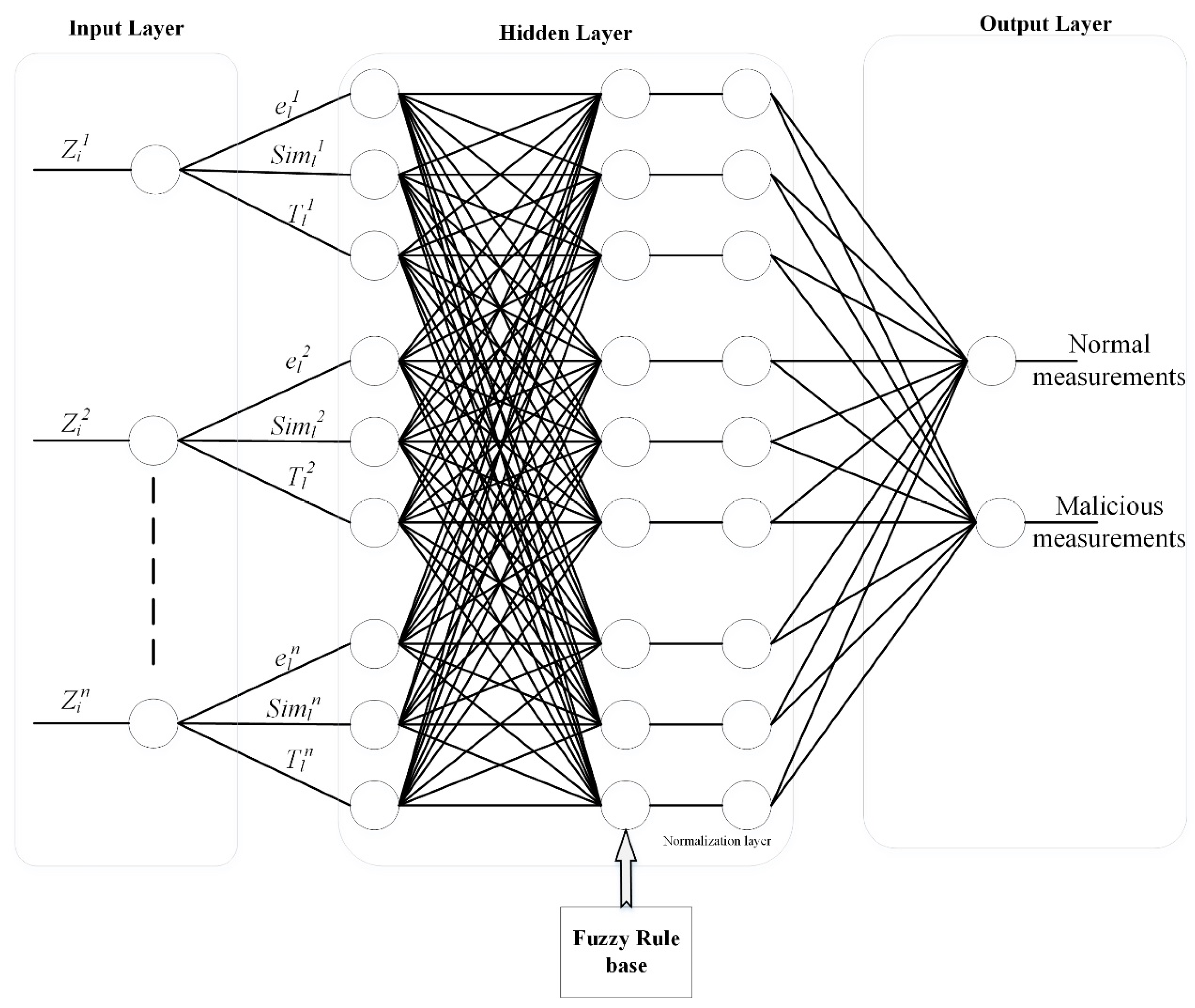
- Compromised meters in the system are identified effectually by analyzing received SE information of each meter. For compromised meter detection, the fuzzy with neural network (FNN) algorithm is employed in the control server.
2. Background Overview
2.1. Security in SG
- Provides more efficient transmission of electricity,
- Supports quick restoration of electricity after power disturbances,
- Efficient in terms of operational and management costs for utilities,
- SG helps to lower the power costs for consumers,
- Provides reduced peak amount as well as electricity rates,
- Supports large-scale renewable energy systems,
- Integrates consumer–owner power generation systems.
2.2. State Estimation in SG
- Bad data detection,
- Minimizing small errors found in measurements,
- Topology errors and wrong switch statuses detection,
- Managing missing and delayed measurements through providing estimation for unmonitored parts of the system,
- Analyzing measurements redundancy for estimating network parameters.
3. Related Works
3.1. Related Works on FDI Attack Detection
3.2. Related Works on SE and Security in SG
4. Problem Definition
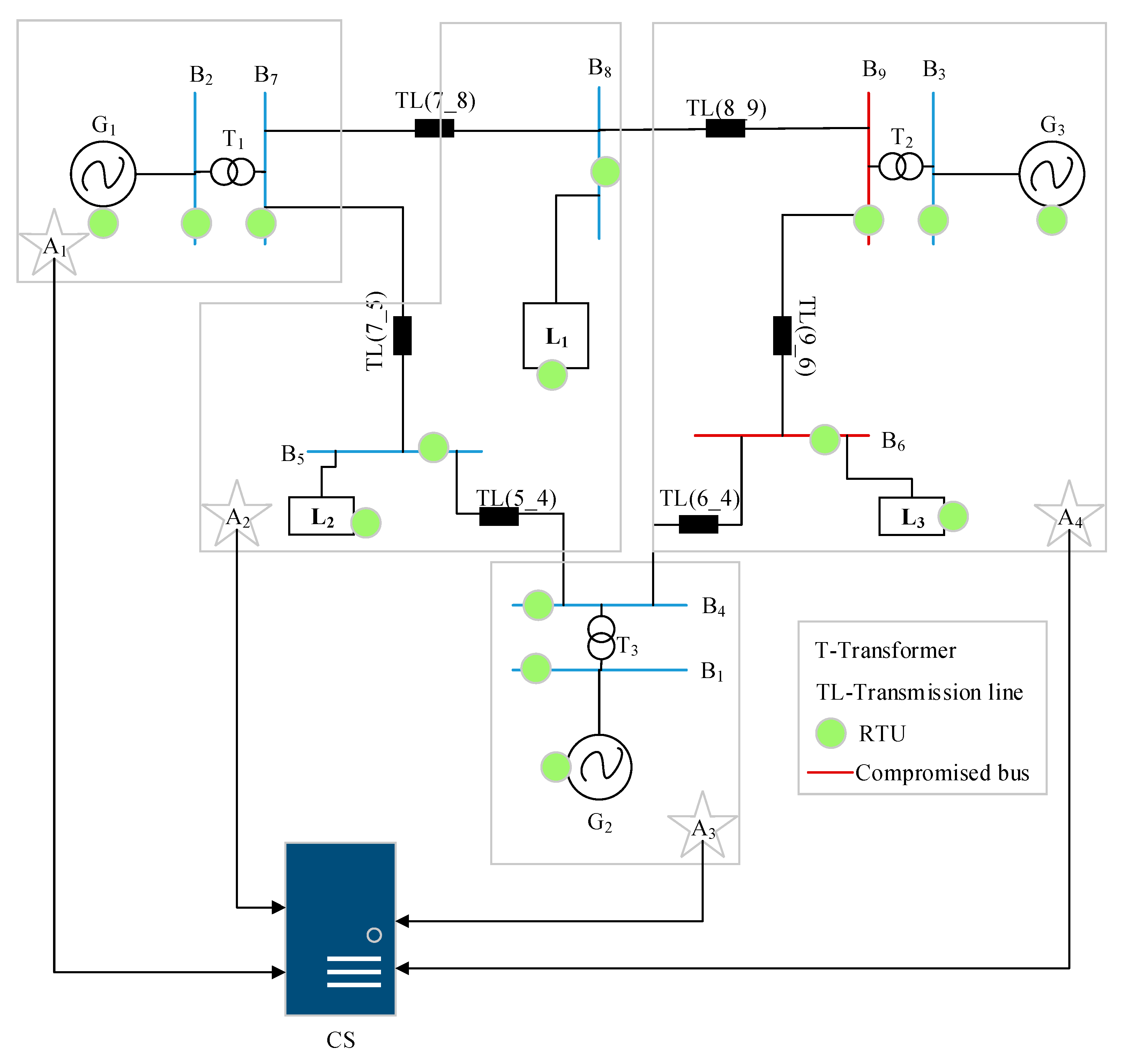
5. Proposed T2S2G System
5.1. System Overview
5.2. WQT Method Based System Partitioning
5.3. PEECC Algorithm for Measurements Protection
- Select a random number ‘’ between the range of [] where ‘’ is a prime number that satisfies Equation (11).
- Generate the public key ‘’ as follows:where ‘’ is a base point in ECC curve. In this manner the public key is generated in the ECC algorithm.
- Generate the private key ‘’ using the public key.
| Algorithm 1 PEECC algorithm |
| Input: Plain text of Output: Cipher text of ()
|
5.4. APSO Algorithm Based Distributed SE
- Step 1: In this step, all particles are initialized in the APSO algorithm. In APSO based SE, the state variables such as are initialized as particles.
- Step 2: The next step is to evaluate the fitness value of each particle initialized. In APSO, the fitness value () of each particle is computed as follows:The penalty function () is computed as follows:The penalty function is computed in terms of the number of penalized control variables (), scalar quadratic penalty weight (), current value of control variable (), and control variable penalty offset ().
- Step 3: In this step, the velocity of each particle is updated based on ‘’. Firstly, the fitness value of the particle in the current iteration is compared with the previous value in order to update the particle best ( value. If the current ‘’ value is higher than the previous ‘’ then the current value is updated as ‘’, otherwise the previous value is maintained as ‘’. Then the current ‘’ of a particle is compared with ‘’ of other particles in order to update the global best () value. After the update of ‘’ and ‘’, the velocity of each particle is updated as follows:Current velocity of the particle ( is computed in terms of the previous velocity of the particle (), two learning factors (), and random number (). The current position of particle is updated as:Current position is computed based on the previous position () and current velocity ().
- Step 4: This step in the APSO algorithm differs from the traditional PSO algorithm. In this step, new solutions are generated by employing in the PSO algorithm. In this step, new solutions are generated as follows:Here ‘’ is step size and always ‘ while ‘’ is the transition probability. Then the new solutions also are evaluated based on the fitness value as in Step 2 until maximum iteration has been reached. After completion of the maximum iteration, the optimal solution for each state variable is estimated.
- Step 5: In this step, attack detection is carried out based on estimated states. For standard direct current (DC) power flow, the measurements are received by aggregators as follows in the absence of an attacker:
| Algorithm 2 APSO based SE |
| Input: Measurements from RTUs Output: Estimated state variables
|
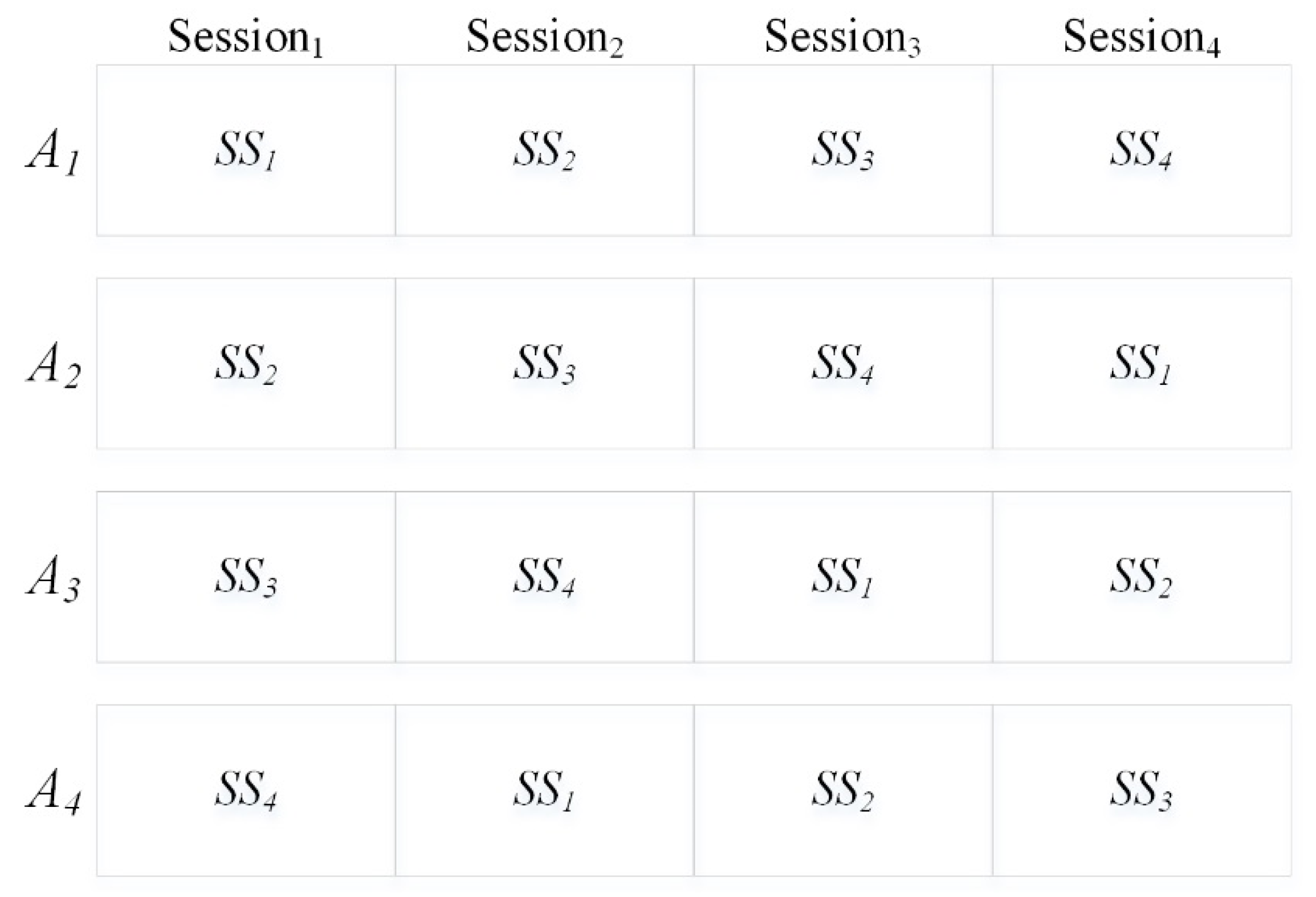
5.5. LSA Based Authentication and FNN Based Classification
- First stage: In LSA, the first stage is initiated by the aggregator. In this stage, the aggregator submits the ID and password () to the CS. The CS verifies the ID and ‘’, if ID and ‘’ is matched then it considers the aggregator request for the second stage. In this stage, AND logic is utilized. Otherwise, the aggregator request is denied.
- Second stage: The aggregator that completes the first stage is considered for the second stage. In this stage, the CS requests for a shared secret value () for the current session from the aggregator. Each aggregator is provided with a set of ‘’ including four secret values initially. Each value is scheduled for different sessions. Upon receiving a ‘’ request, the aggregator submits its current session ‘’. If the current session ‘’ submitted by the aggregator is true, then the aggregator is authenticated at the CS.
6. Performance Evaluation
6.1. Simulation Setup
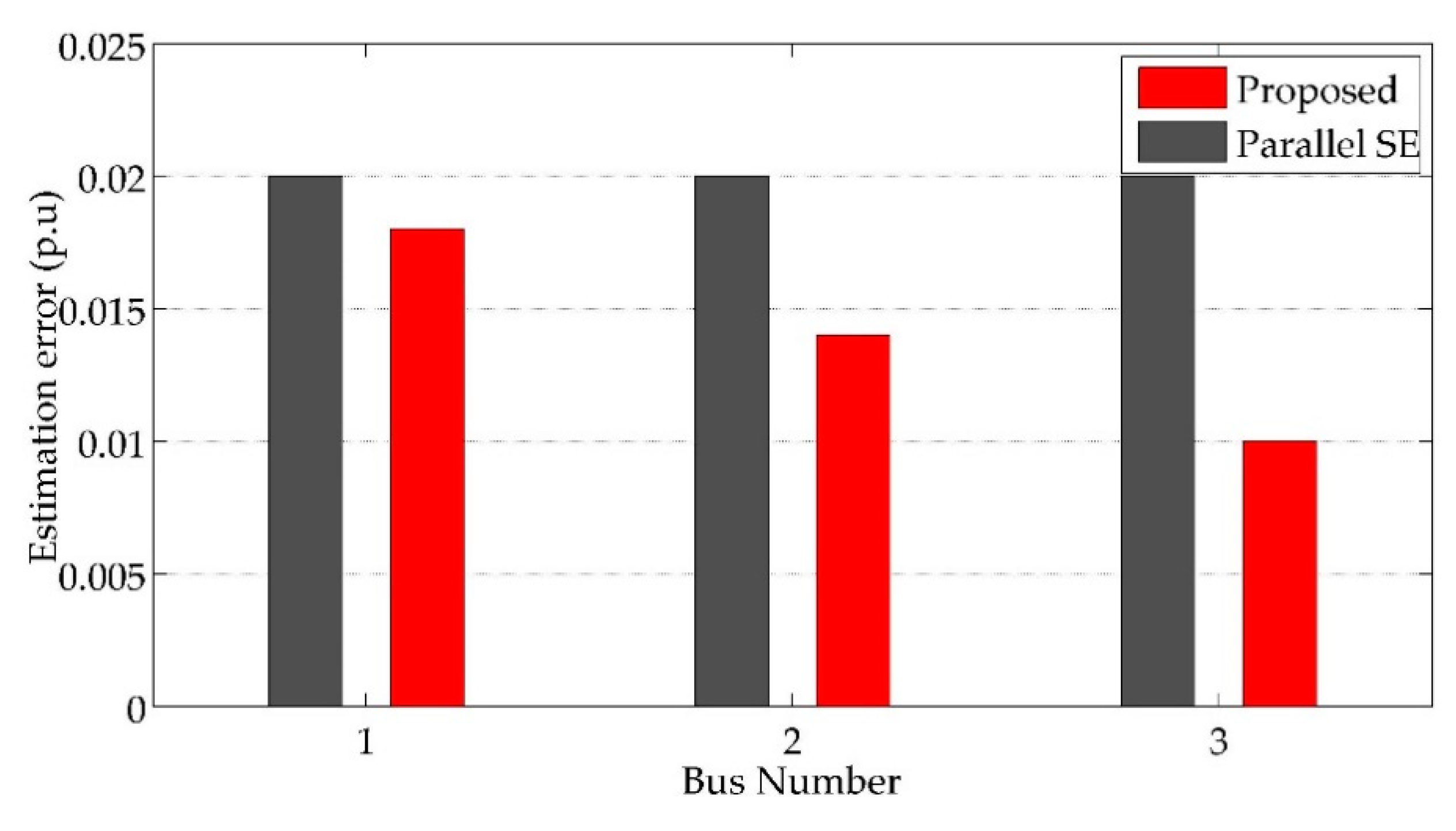
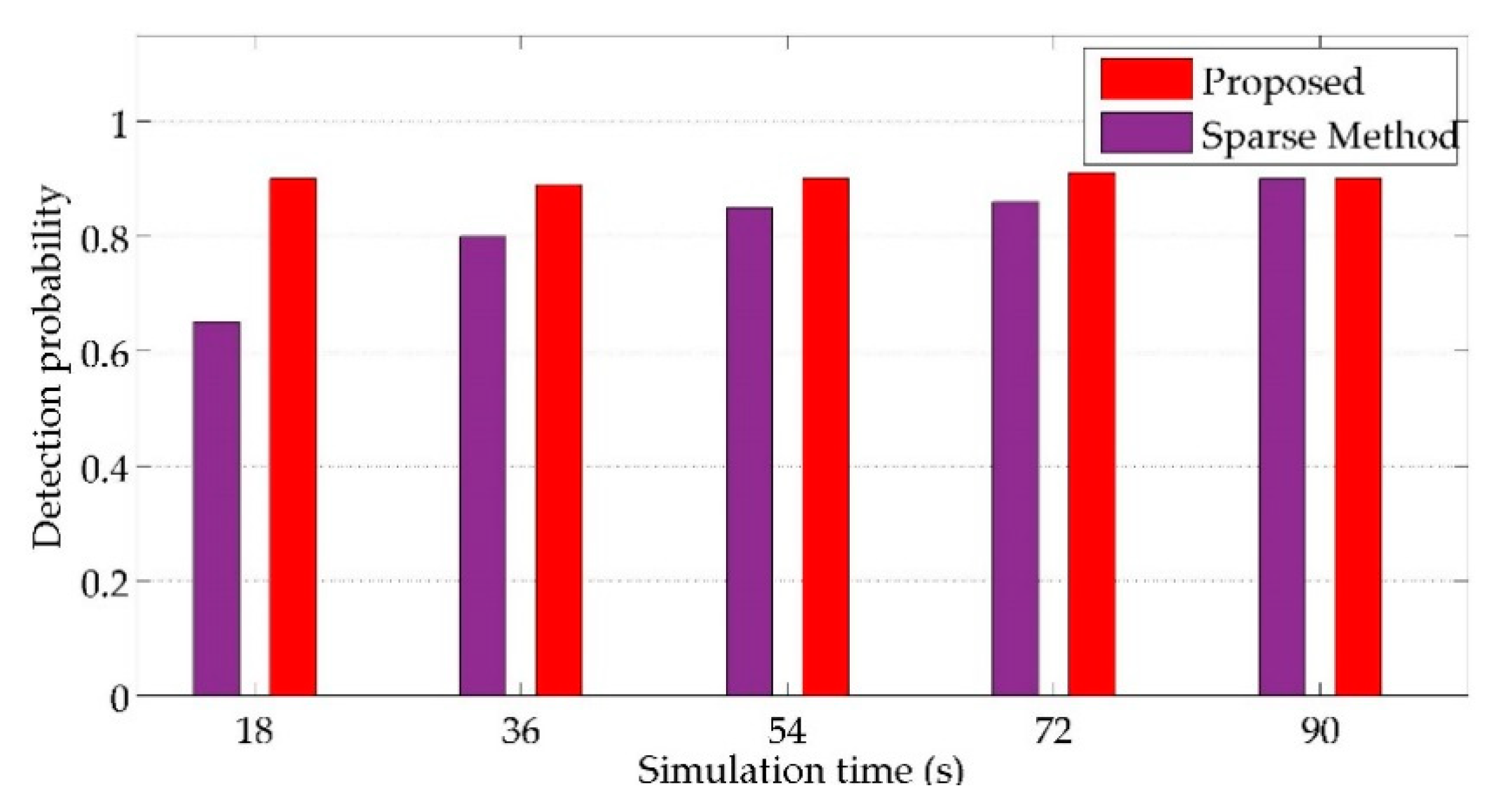
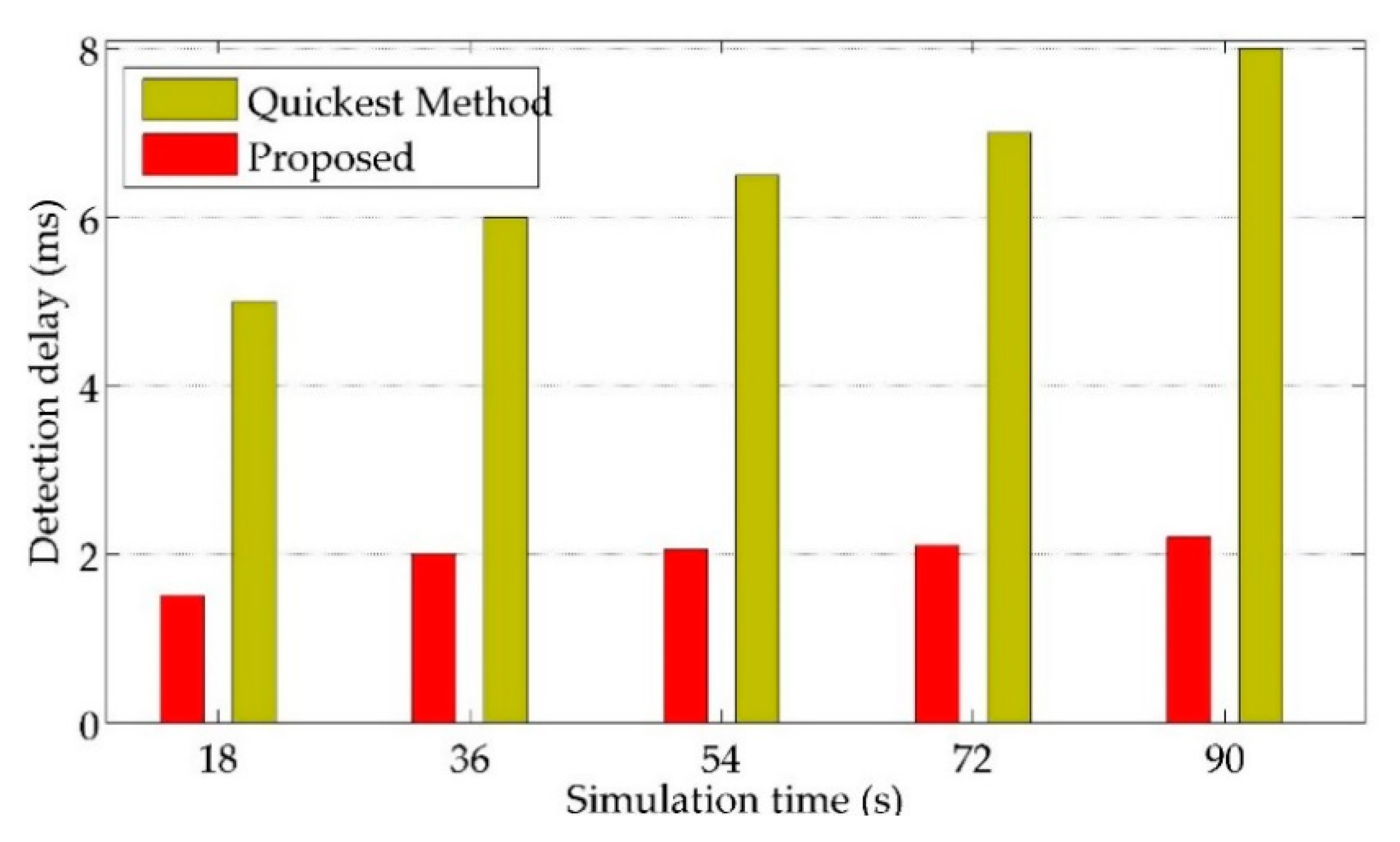
6.2. Comparative Analysis
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Acronyms
| Acronyms | Parameter |
| 3DES | Triple Data Encryption Standard |
| APSO | Amended Particle Swarm Optimization |
| BDD | Bad Data Detection |
| CS | Control Server |
| CS-PSO | Constriction Factor Particle Swarm Optimization |
| ECC | Elliptic Curve Cryptography |
| FDI | False Data Injection |
| FNN | Fuzzy with Neural Network |
| GA | Genetic Algorithm |
| HPSO | Hybrid Particle Swarm Optimization |
| ISE | Interval State Estimation |
| LSA | Logical Schedule Based Authentication |
| MM | Mathematical Morphology |
| PCA | Principal Component Analysis |
| PEECC | Parallel Enhanced Elliptic Curve Cryptography |
| PMU | Phasor Measurement Unit |
| PRSEM | PMU based Robust State Estimation Method |
| PSO | Particle Swarm Optimization |
| RPCA | Robust Principal Component Analysis |
| RSC | Recursive Systematic Convolutional |
| RTU | Remote Terminal Unit |
| SAE | Stacked Auto Encoder |
| SCADA | Supervisory Control and Data Acquisition |
| SE | State Estimation |
| SEDEA | State Estimation Based Dynamic Encryption and Authentication |
| SG | Smart Grid |
| SVM | Support Vector Machine |
| T2S2G | Two-Tier Secure Smart Grid |
| WQT | Weighted Quad Tree |
References
- Tuballa, M.L.; Abundo, M.L. A review of the development of Smart Grid technologies. Renew. Sustain. Energy Rev. 2016, 59, 710–725. [Google Scholar] [CrossRef]
- Cintuglu, M.H.; Mohammed, O.A.; Akkaya, K.; Uluagac, A.S. A survey on smart grid cyber-physical system testbeds. IEEE Commun. Surv. Tutor. 2016, 19, 446–464. [Google Scholar] [CrossRef]
- Bayindir, R.; Colak, I.; Fulli, G.; Demirtas, K. Smart grid technologies and applications. Renew. Sustain. Energy Rev. 2016, 66, 499–516. [Google Scholar] [CrossRef]
- Asghar, M.R.; Dán, G.; Miorandi, D.; Chlamtac, I. Smart meter data privacy: A survey. IEEE Commun. Surv. Tutor. 2017, 19, 2820–2835. [Google Scholar] [CrossRef]
- Tan, S.; De, D.; Song, W.-Z.; Yang, J.; Das, S.K. Survey of security advances in smart grid: A data driven approach. IEEE Commun. Surv. Tutor. 2017, 19, 397–422. [Google Scholar] [CrossRef]
- Liang, G.; Zhao, J.; Luo, F.; Weller, S.R.; Dong, Z.Y. A review of false data injection attacks against modern power systems. IEEE Trans. Smart Grid 2017, 8, 1630–1638. [Google Scholar] [CrossRef]
- Yu, Z.-H.; Chin, W.-L. Blind false data injection attack using PCA approximation method in smart grid. IEEE Trans. Smart Grid 2015, 6, 1219–1226. [Google Scholar] [CrossRef]
- Sanjab, A.; Saad, W. Data injection attacks on smart grids with multiple adversaries: A game-theoretic perspective. IEEE Trans. Smart Grid 2016, 7, 2038–2049. [Google Scholar] [CrossRef]
- Khanna, K.; Panigrahi, B.K.; Joshi, A. Bi-level modelling of false data injection attacks on security constrained optimal power flow. IET Gener. Transm. Distrib. 2017, 11, 3586–3593. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Vural, F.T.Y.; Kulkarni, S.R.; Poor, H.V. Machine learning methods for attack detection in the smart grid. IEEE Trans. Neural Netw. Learn. Syst. 2015, 27, 1773–1786. [Google Scholar] [CrossRef]
- Bi, S.; Zhang, Y.J.A. Graph-based cyber security analysis of state estimation in smart power grid. IEEE Commun. Mag. 2017, 99, 2–9. [Google Scholar] [CrossRef]
- Dehghanpour, K.; Wang, Z.; Wang, J.; Yuan, Y.; Bu, F. A survey on state estimation techniques and challenges in smart distribution systems. IEEE Trans. Smart Grid 2018, 10, 2312–2322. [Google Scholar] [CrossRef]
- Hu, L.; Wang, Z.; Rahman, I.; Liu, X. A constrained optimization approach to dynamic state estimation for power systems including PMU and missing measurements. IEEE Trans. Control Syst. Technol. 2015, 24, 703–710. [Google Scholar] [CrossRef]
- Wang, H.; Ruan, J.; Wang, G.; Zhou, B.; Liu, Y.; Fu, X.; Peng, J. Deep learning-based interval state estimation of AC smart grids against sparse cyber attacks. IEEE Trans. Ind. Inform. 2018, 14, 4766–4778. [Google Scholar] [CrossRef]
- Weng, Y.; Negi, R.; Faloutsos, C.; Ilić, M.D. Robust data-driven state estimation for smart grid. IEEE Trans. Smart Grid 2016, 8, 1956–1967. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Nikooghadam, M. An anonymous ECC-based self-certified key distribution scheme for the smart grid. IEEE Trans. Ind. Electron. 2018, 65, 7996–8004. [Google Scholar] [CrossRef]
- He, D.; Chan, S.; Guizani, M. Cyber security analysis and protection of wireless sensor networks for smart grid monitoring. IEEE Wirel. Commun. 2017, 24, 98–103. [Google Scholar] [CrossRef]
- Hossain, M.; Madlool, N.; Rahim, N.; Selvaraj, J.; Pandey, A.; Khan, A.F. Role of smart grid in renewable energy: An overview. Renew. Sustain. Energy Rev. 2016, 60, 1168–1184. [Google Scholar] [CrossRef]
- Nafi, N.S.; Ahmed, K.; Gregory, M.A.; Datta, M. A survey of smart grid architectures, applications, benefits and standardization. J. Netw. Comput. Appl. 2016, 76, 23–36. [Google Scholar] [CrossRef]
- Jokar, P.; Arianpoo, N.; Leung, V.C. A survey on security issues in smart grids. Secur. Commun. Netw. 2016, 9, 262–273. [Google Scholar] [CrossRef]
- Eder-Neuhauser, P.; Zseby, T.; Fabini, J. Resilience and security: A qualitative survey of urban smart grid architectures. IEEE Access 2016, 4, 839–848. [Google Scholar] [CrossRef]
- Deng, R.; Xiao, G.; Lu, R.; Liang, H.; Vasilakos, A.V. False data injection on state estimation in power systems—Attacks, impacts, and defense: A survey. IEEE Trans. Ind. Inform. 2017, 13, 411–423. [Google Scholar] [CrossRef]
- Khorshidi, R.; Shabaninia, F.; Niknam, T. A new smart approach for state estimation of distribution grids considering renewable energy sources. Energy 2016, 94, 29–37. [Google Scholar] [CrossRef]
- Ahmad, F.; Rasool, A.; Ozsoy, E.; Sekar, R.; Sabanovic, A.; Elitaş, M. Distribution system state estimation-A step towards smart grid. Renew. Sustain. Energy Rev. 2018, 81, 2659–2671. [Google Scholar] [CrossRef]
- Xia, S.; Zhang, Q.; Jing, J.; Ding, Z.; Yu, J.; Chen, B.; Wu, H. Distributed state estimation of multi-region power system based on consensus theory. Energies 2019, 12, 900. [Google Scholar] [CrossRef]
- Grahn, P.; Briggner, V.; Johansson, L.; Babazadeh, D.; Nordstrom, L. Centralized versus distributed state estimation for hybrid AC/HVDC grid. In Proceedings of the IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Torino, Italy, 26–29 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Ahmed, S.; Lee, Y.; Hyun, S.-H.; Koo, I. Feature selection–based detection of covert cyber deception assaults in smart grid communications networks using machine learning. IEEE Access 2018, 6, 27518–27529. [Google Scholar] [CrossRef]
- Rawat, D.B.; Bajracharya, C. Detection of false data injection attacks in smart grid communication systems. IEEE Signal Process. Lett. 2015, 22, 1652–1656. [Google Scholar] [CrossRef]
- Rana, M.M.; Li, L.; Su, S.W. Cyber attack protection and control of microgrids. IEEE CAA J. Autom. Sin. 2018, 5, 602–609. [Google Scholar] [CrossRef]
- Huang, Y.; Tang, J.; Cheng, Y.; Li, H.; Campbell, K.A.; Han, Z. Real-time detection of false data injection in smart grid networks: An adaptive CUSUM method and analysis. IEEE Syst. J. 2014, 10, 532–543. [Google Scholar] [CrossRef]
- Liu, X.; Zhu, P.; Zhang, Y.; Chen, K. A collaborative intrusion detection mechanism against false data injection attack in advanced metering infrastructure. IEEE Trans. Smart Grid 2015, 6, 2435–2443. [Google Scholar] [CrossRef]
- Nanchian, S.; Majumdar, A.; Pal, B.C. Three-phase state estimation using hybrid particle swarm optimization. IEEE Trans. Smart Grid 2015, 8, 1035–1045. [Google Scholar] [CrossRef]
- Zhao, J.; Zhang, G.; Das, K.; Korres, G.N.; Manousakis, N.M.; Sinha, A.K.; He, Z. Power system real-time monitoring by using PMU-based robust state estimation method. IEEE Trans. Smart Grid 2015, 7, 300–309. [Google Scholar] [CrossRef]
- Leite, J.B.; Mantovani, J.R.S. Distribution system state estimation using the Hamiltonian cycle theory. IEEE Trans. Smart Grid 2015, 7, 366–375. [Google Scholar] [CrossRef]
- Cui, Y.; Bai, F.; Liu, Y.; Liu, Y. A measurement source authentication methodology for power system cyber security enhancement. IEEE Trans. Smart Grid 2018, 9, 3914–3916. [Google Scholar] [CrossRef]
- Chen, L.; Dong, X.; Wu, Z.; Liu, Z.; Chen, B. Evaluating the reliability and security of power distribution wireless network. CIRED Open Access Proc. J. 2017, 2017, 1102–1106. [Google Scholar] [CrossRef]
- Liu, T.; Tian, J.; Gui, Y.; Liu, Y.; Liu, P. SEDEA: State estimation-based dynamic encryption and authentication in smart grid. IEEE Access 2017, 5, 15682–15693. [Google Scholar] [CrossRef]
- Li, B.; Lu, R.; Wang, W.; Choo, K.-K.R. Distributed host-based collaborative detection for false data injection attacks in smart grid cyber-physical system. J. Parallel Distrib. Comput. 2017, 103, 32–41. [Google Scholar] [CrossRef]
- Karimipour, H.; Dinavahi, V. Robust massively parallel dynamic state estimation of power systems against cyber-attack. IEEE Access 2017, 6, 2984–2995. [Google Scholar] [CrossRef]
- Hao, J.; Piechocki, R.J.; Kaleshi, D.; Chin, W.H.; Fan, Z. Sparse malicious false data injection attacks and defense mechanisms in smart grids. IEEE Trans. Ind. Inform. 2015, 11, 1–12. [Google Scholar] [CrossRef]
- Anwar, A.; Mahmood, A.N.; Tari, Z. Identification of vulnerable node clusters against false data injection attack in an AMI based smart grid. Inf. Syst. 2015, 53, 201–212. [Google Scholar] [CrossRef]
- Li, S.; Yılmaz, Y.; Wang, X. Quickest detection of false data injection attack in wide-area smart grids. IEEE Trans. Smart Grid 2015, 6, 2725–2735. [Google Scholar] [CrossRef]
- Azarderakhsh, R.; Reyhani-Masoleh, A. Parallel and high-speed computations of elliptic curve cryptography using hybrid-double multipliers. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 1668–1677. [Google Scholar] [CrossRef]





| Generator | Power | Load | Power |
|---|---|---|---|
| 512 | 125 | ||
| 270 | 90 | ||
| 125 | 100 |
| Input | Output | ||
|---|---|---|---|
| <0.5 | <0.5 | <50 | Malicious |
| <0.5 | <0.5 | >50 | Normal |
| <0.5 | >0.5 | <50 | Normal |
| <0.5 | >0.5 | >50 | Normal |
| >0.5 | <0.5 | <50 | Malicious |
| >0.5 | <0.5 | >50 | Malicious |
| >0.5 | >0.5 | <50 | Malicious |
| >0.5 | >0.5 | >50 | Medium |
| Parameter | Value | |
|---|---|---|
| Bus system | IEEE-9 bus system | |
| Measurement variables | ||
| Number of RTUs | 15 | |
| Number of aggregators | 4 | |
| Number of attackers | 1 | |
| Number of compromised meters/buses | 2 | |
| Total number of measurements | 350 | |
| Number of malicious measurements | 35 | |
| APSO | Initial population | 100 |
| 2 | ||
| 1 | ||
| Maximum iteration | 100 | |
| PEECC | Number of keys | 4 |
| Key size | 256 bits | |
| Value of ‘’ | 10 (Maximum) | |
| Parameter | Parallel SE | Sparse Method | Quickest Detection |
|---|---|---|---|
| SE | Dynamic SE | Centralized SE | Centralized SE |
| Attack detection | Markov chain model | RPCA method | Sequential detector |
| Demerits |
|
|
|
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aziz, I.T.; Jin, H.; Abdulqadder, I.H.; Alturfi, S.M.; Alobaidi, W.H.; Flaih, F.M.F. T2S2G: A Novel Two-Tier Secure Smart Grid Architecture to Protect Network Measurements. Energies 2019, 12, 2555. https://doi.org/10.3390/en12132555
Aziz IT, Jin H, Abdulqadder IH, Alturfi SM, Alobaidi WH, Flaih FMF. T2S2G: A Novel Two-Tier Secure Smart Grid Architecture to Protect Network Measurements. Energies. 2019; 12(13):2555. https://doi.org/10.3390/en12132555
Chicago/Turabian StyleAziz, Israa T., Hai Jin, Ihsan H. Abdulqadder, Sabah M. Alturfi, Wisam H. Alobaidi, and Firas M.F. Flaih. 2019. "T2S2G: A Novel Two-Tier Secure Smart Grid Architecture to Protect Network Measurements" Energies 12, no. 13: 2555. https://doi.org/10.3390/en12132555
APA StyleAziz, I. T., Jin, H., Abdulqadder, I. H., Alturfi, S. M., Alobaidi, W. H., & Flaih, F. M. F. (2019). T2S2G: A Novel Two-Tier Secure Smart Grid Architecture to Protect Network Measurements. Energies, 12(13), 2555. https://doi.org/10.3390/en12132555





