Abstract
Recently, piracy and copyright violations of digital content have become major concerns as computer science has advanced. In order to prevent unauthorized usage of content, digital watermarking is usually employed. This work proposes a new approach to digital image watermarking that makes use of the discrete cosine transform (DCT), discrete wavelet transform (DWT), dipper-throated optimization (DTO), and stochastic fractal search (SFS) algorithms. The proposed approach involves computing the discrete wavelet transform (DWT) on the cover image to extract its sub-components, followed by the performance of a discrete cosine transform (DCT) to convert these sub-components into the frequency domain. Finding the best scale factor for watermarking is a significant challenge in most watermarking methods. The authors used an advanced optimization algorithm, which is referred to as DTOSFS, to determine the best two parameters—namely, the scaling factor and embedding coefficient—to be used while inserting a watermark into a cover image. Using the optimal values of these parameters, a watermark image can be inserted into a cover image more efficiently. The suggested approach is evaluated in comparison with the current gold standard. The normalized cross-correlation (NCC), peak-signal-to-noise ratio (PSNR), and image fidelity (IF) are used to measure the success of the proposed approach. In addition, a statistical analysis is performed to evaluate the significance and superiority of the proposed approach. The experimental results confirm the effectiveness of the proposed approach in improving upon standard watermarking methods based on the DWT and DCT. Moreover, a set of attacks is considered to study the robustness of the proposed approach, and the results confirm the expected outcomes. It is shown by the achieved results that the proposed approach can be utilized for practical digital image watermarking, and that it significantly outperforms other digital image watermarking methods.
1. Introduction
The progression in digital communication supports the exchange of large amounts of data through networks in real time [1]. As a result of this progression, smart healthcare companies provide remote medical services to patients [2]. These services include transmitting medical data and images of patients to faraway specialists to save time and achieve rapid medical diagnoses [3]. Security and privacy issues appear when these data is transmitted over open communication networks [4]. Different instructions and rules are used to preserve patients’ privacy when sending and receiving their medical data for diagnosis or research [5,6]. Regardless of the several advantages in this, medical data and images may reach unlicensed people, thus threatening privacy. During the COVID-19 pandemic, the need for data security increased [7,8,9].
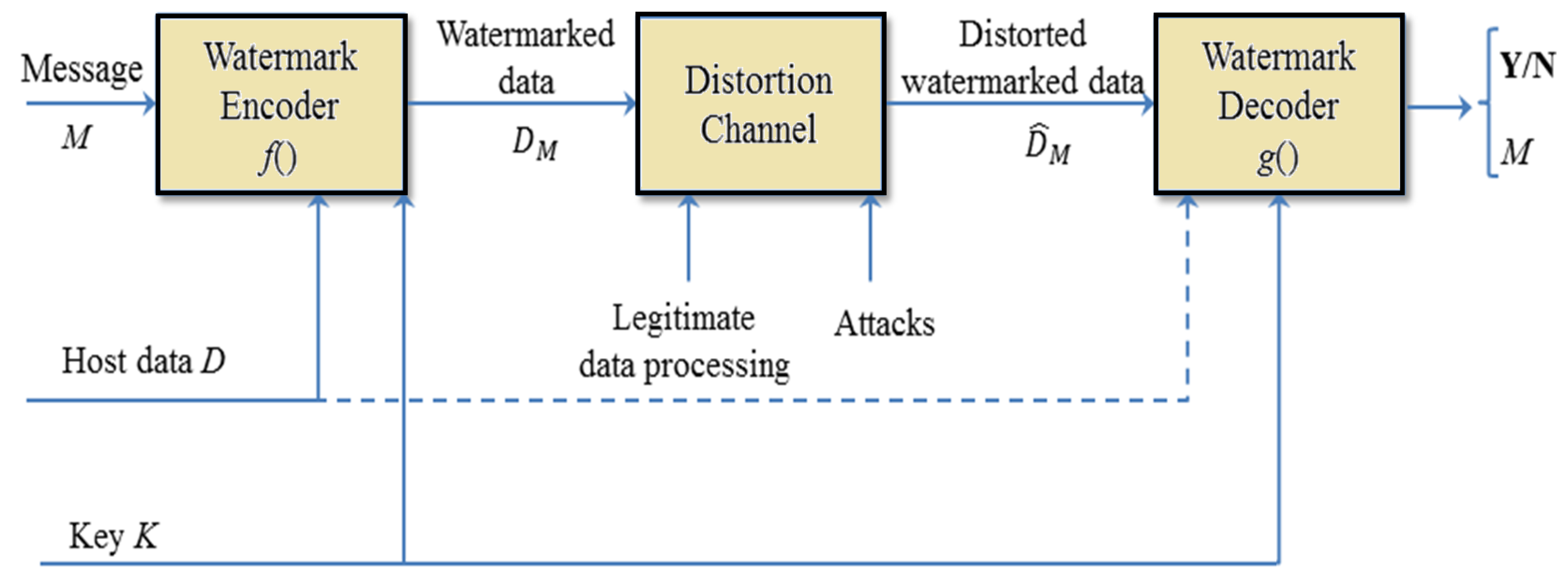
During the transmission of medical images, a watermark is added to the original images. A watermark can be data, an image, or a logo indicating a patient’s identity or data about a hospital or clinic. An important point that must be taken into account is that the watermark should not cause significant degradation in the quality of the original image [10]. Watermarking algorithms are vastly used for biomedical images for efficient results. In watermarking, a logo or data are hidden in the cover or original image to detect ownership at any stage [11]. In watermarking, there are two main properties: robustness and invisibility. These should be balanced in order to provide high performance [12]. Nowadays, optimization algorithms are used in different fields, mainly to perform this task efficiently [13,14,15,16,17,18]. Optimization algorithms provide the optimal level of embedding of the message in the best regions in the cover image [19]. Figure 1 shows a block diagram of a basic watermarking system. In this figure, the dotted line indicates the possibility of accessing the original data in the decoding process, representing informed watermark detection. In the case of the absence of the original data, such a system is a blind watermark system.
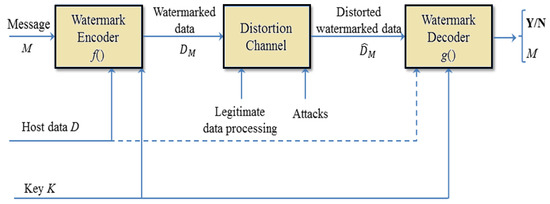
Figure 1.
The typical process of watermarking systems.
Research on digital watermarking has increased dramatically in recent years. As a concept, watermarking was developed around 1990, and several implementations have been described in the literature [20]. Applications, source types (such as images, videos, or audio files), and watermarking methods all play a role in categorizing digital watermarking approaches. Many people favor discrete wavelet transform (DWT)- and discrete cosine transform (DCT)-based approaches because watermarks may be used in both the spatial and frequency domains. In the context of image watermarking, several techniques are ubiquitous. A watermark image and a cover image are used to watermark photographs. The goal is to seamlessly incorporate the watermark into the cover art without anybody being able to tell.
Using the DCT, the authors of [21] presented a new approach to digital image watermarking that is resistant to JPEG compression. For stealthy and long-lasting audio watermarking, a different technique using the SVD and DCT was applied in [22]. In [23], the pros and cons of a QIM-based digital watermarking system were weighed. By combining the DWT and DCT, the researchers improved watermarking approaches. An enhanced DCT–DWT approach based on a hybrid intelligent SVD model was suggested in [24]. In [25], one can see an alternative digital watermarking method for spotting and restoring altered photos. DCT (discrete cosine transform) watermarking was the basis for this technology. The watermarking of color photographs involved the combination of the DCT, DWT, and singular value decomposition (SVD). Watermarking methods for still images and moving ones may be found in the literature, with many employing the DCT and DWT in some way. Using a shift in the inter-block coefficients, the authors of [26] described a method for embedding a watermark into data that was both undetectable and extremely secure; this method was based on DCT blocks. Digital watermarks can be created by using these techniques, but their quality is severely restricted. To a large extent, the scaling factor determines the watermark’s quality. The scaling factor determines the combination of the cover and watermark images in a specific proportion. The method’s robustness, i.e., the quality of the recovered image, will suffer if the scaling factor is set to a low number. The quality of the watermarked image and, therefore, its imperceptibility will suffer, however, if the scaling factor is set to a large number. Accordingly, it is necessary to maximize the scaling factor. To optimize many different types of problems, meta-heuristic algorithms are frequently utilized [25].
This paper proposes a new algorithm for improving the watermarking approach based on the DWT and DCT. The proposed algorithm combines the dipper-throated optimization (DTO) algorithm with the stochastic fractal search (SFS) algorithm and is referred to as DTOSFS. The proposed algorithm’s advantage is that it can find the optimal regions in a cover image to implant a target message. The target message in our case is a medical image, which is sensitive for patients who wish to store it securely through transmission and communication with health agencies. The main contributions of this work can be summarized in the following points:
- A new algorithm is proposed in order to improve the watermarking of sensitive images.
- The proposed optimization algorithm is tested in terms of the DWT+DCT watermarking method to prove its effectiveness.
- The proposed approach is compared with the original DWT+DCT and the original DTO and SFS, in addition to another watermarking method based on the discrete Fourier transform (DFT) + singular value decomposition, to prove the effectiveness and superiority of the proposed approach.
- The proposed approach is tested in terms of various methods of attack, including the average filtering, Gaussian filtering, median filtering, and Wiener filtering methods, to show its robustness.
- The proposed approach is tested in terms of various cover images.
The structure of this paper is as follows. A review of previous studies addressing recent watermarking approaches is presented in Section 2. The materials and methods employed in the proposed methodology are described in Section 3. The proposed methodology is then illustrated in Section 4. The achieved results and the corresponding analysis are explained in Section 5. Finally, the conclusion and future perspectives are presented in Section 6.
2. Literature Review
Digital image watermarking has been targeted by many researchers in recent years [27,28,29,30,31]. As a platform, the Internet of Things (IoT) has enhanced the development of many types of research in the medical field. A medical image algorithm based on IoT was proposed in which the doctor’s signature was embedded into different images to provide robustness and security [32]. The drawbacks of this method were its low robustness in the case of geometric attacks and that the capacity of the data payload was not recognized. So, a different optimization method would provide a trade-off between robustness and size. An idea for saving time consumption was presented by using ant colony optimization and the light gradient boosting algorithm. The embedding was performed by using the discrete cosine transform, and the optimizer was used to obtain the optimal embedding parameters [33]. A different deep learning algorithm was used in watermarking systems to allow automation of the process. The available deep learning algorithms did not guarantee robust and blind embedding simultaneously. A new technique based on deep learning was proposed in which the functions of both embedding and extraction were performed by using automation [34]. The use of particle swarm optimization with a watermarking system depended on the discrete wavelet transform and the discrete cosine transform in [35], and this provided efficient results. The results of this method were satisfying compared to those of existing methods.
An optimized blind watermarking technique for protecting copyright data used principal component analysis; it operated on a redundant discrete wavelet domain and used an improved gray wolf optimizer [36]. The proposed technique achieved efficient imperceptibility and robustness. Now, neural networks are being used to develop the efficiency of watermarking techniques. An efficient blind image watermarking technique based on thirteen layers of a convolutional neural network was proposed in [37]. The new method increased the image resolution by increasing the invisibility of the watermark image. The trade-off was carried out according to user desire. The results indicate satisfactory robustness in the cases of both geometric and pixel value change attacks. A new protocol for watermarking systems called a buyer and seller protocol has appeared in recent years to ensure security for systems depending on the blockchain technology [38]. A proposed watermarking framework based on a neural network in which the watermark logo was embedded into the edge of the host image was presented in [39]. This method used an optimizer with a genetic algorithm to insert the logo data and used a multilayer perceptron to extract the logo with high performance. Another secure watermarking algorithm used a particle swarm optimizer in which a color logo was embedded into the three primary colors in color images (red, green, and blue) of the original image by using the discrete cosine transform [40]. The three primary colors were arranged according to the fuzzy entropy value, and a particle swarm optimizer determined the performance of the embedding in order to achieve a balance between invisibility and robustness.
A hybrid method was used to perform watermarking with the discrete cosine transform, and the discrete wavelet transform was proposed by the authors of [41]. In this method, the watermark was extracted from the original image without using the host image, but this depended on a two-stage neural network. The system achieved better invisibility with high robustness. Another hybrid system aimed to protect copyright data and was based on the discrete cosine transform (DCT), discrete wavelet transform (DWT), singular value decomposition (SVD), and hologram presented in [42]. The steps of this method were as follows: First, the watermark logo was embedded into the three-color components of the required original image. Second, a blind algorithm was used to extract the watermark image; third, the hologram was used to improve the invisibility of the watermark, provide the best performance against noise attacks, and perform encryption. A proposed watermarking system that ensured all the requirements simultaneously was proposed in [43]. Different researchers that were dependent on blockchain for digital image watermarking to prove ownership [44,45,46] could not rely on a relational database because it was different from another database format, such as the image format. Another algorithm that used blockchain to detect tampering in the database was presented in [47]. Another algorithm that used blockchain for the digital watermarking of big data was presented in [48].
Particle swarm optimization, gray wolf optimization, genetic algorithms, firefly algorithms, bat optimization, the artificial bee colony, and ant colony optimization are a few examples of nature-inspired algorithms that employ swarm intelligence ideas to achieve optimal outcomes. To get the best possible results, several authors have turned to these methods. In [49], a novel and optimal function was introduced that was secure against a wide range of attacks while retaining the desired level of quality. In this method, the embedding factor was determined by using the PSNR and bit correction rate (BCR), and optimization algorithms were utilized to perform the calculations. Numerous hybrid methods, including the use of various algorithms inspired by nature, have been employed by researchers to successfully embed watermarks. The watermarking of color photographs with a combination of the bat method and the firefly algorithm was presented in [50]. A second DCT-based watermarking system was described in [51], which employed the PSO algorithm to find the optimal strength factor value. In [52], the author proposed a watermarking system that used a special variant of the Whale algorithm. To determine the multiscale factor, this approach employed DWT–SVD-based watermarking with a twist: modified whale optimization. In [53], the watermark embedding position is determined by using the firefly method. In [54], an optimization strategy based on the ABC algorithm was used to incorporate the watermark using the IWT and SVD. In [55], the notion of an artificial bee colony was proposed; this system was based on the intelligence of real honey bees. The dipper-throated optimization (DTO) and stochastic fractal search (SFS) optimization methods were proven to perform better than many other optimization algorithms. Still, these algorithms have not been addressed for the problem of watermarking [56,57]. Therefore, these methods were adopted in developing the new algorithm proposed in this paper in order to improve the performance of a standard watermarking method to preserve the security and privacy of medical images while being transmitted over networks.
3. Background
In this section, the basic materials and methods employed in the proposed methodology are briefly presented. The proposed methodology is based on a standard watermarking approach that combines the DWT and DCT methods in order to implant messages in a cover image. Therefore, this section briefly introduces these methods. On the other hand, the proposed approach is based on a new optimization algorithm that was developed to improve the standard DWT+DCT. This new optimization algorithm is based on the original DTO and SFS optimization methods. Therefore, these underlying optimization algorithms are briefly introduced in this section.
3.1. Discrete Cosine Transform (DCT)
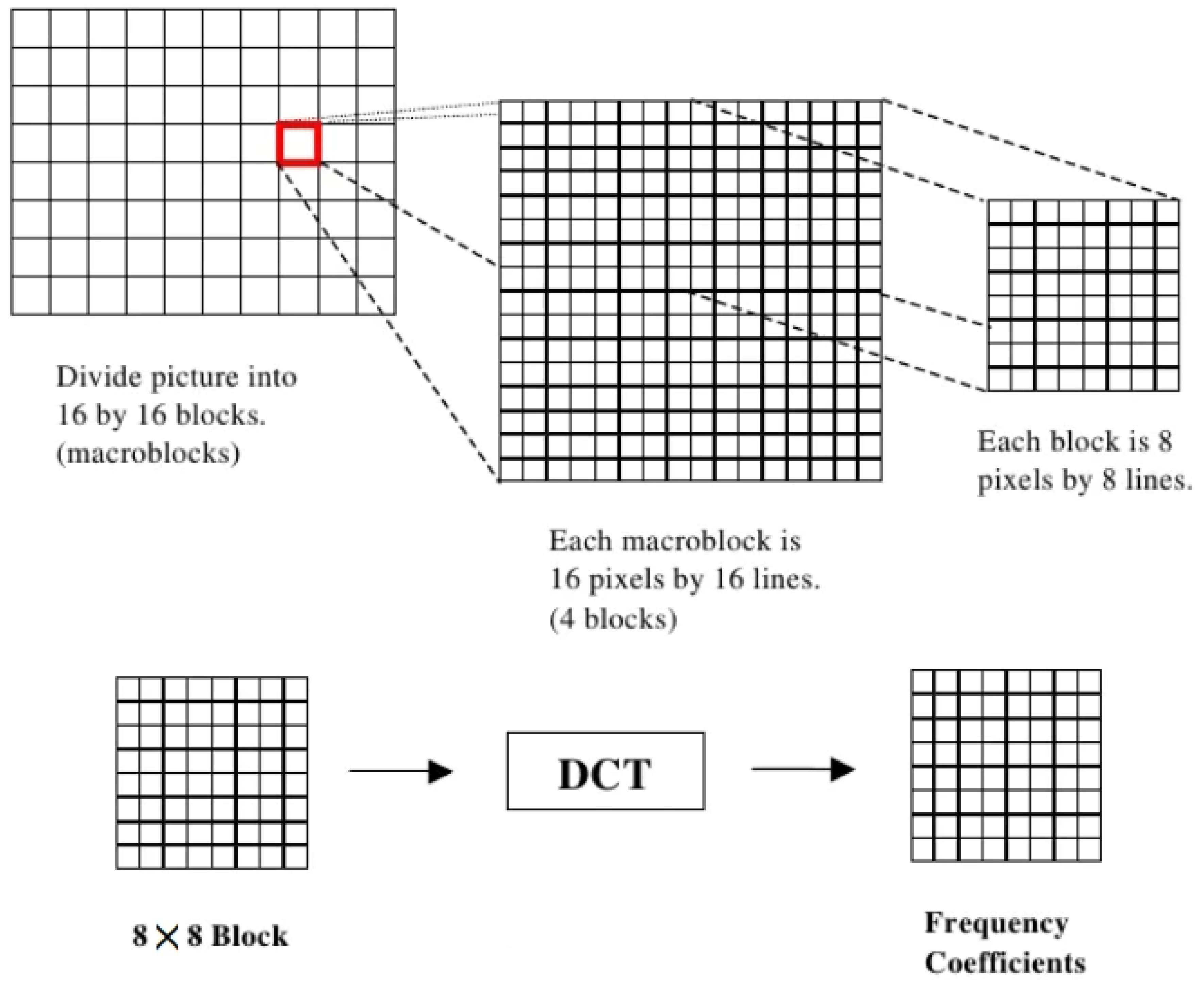
To illustrate an image as the sum of data points, the discrete cosine transform (DCT) is frequently used. The variable magnitudes and frequencies of sinusoids are shown here [58]. Separating an image into its component sub-bands or spectral sub-bands allows for more control over the image’s overall visual quality. If one wants to move a signal or image from the spatial domain to the frequency domain, one can use the discrete cosine transform (DCT). The image can be separated into its high- and low-frequency components. Reflectance is reflected in the low-energy, high-frequency component. The image’s brightness is conveyed via the low-frequency component, which is also quite energetic. Images may be compressed and watermarked using DCTs, just to name a couple of their many uses. The function of the DCT is shown in Figure 2. With the DCT, an image in the spatial domain is transformed into one in the frequency domain. Aside from its low mistake rate, it also features a high compression ratio and computational complexity. The following equation is used to get the DCT of an image.
where

Figure 2.
The process of the discrete cosine transform.
The reconstruction of the image is achieved by applying the following equation:
It is common practice to apply the DCT to each non-overlapping block of an image when using the popular block-based DCT transform. There are, therefore, three distinct frequency ranges resulting from this process: the low-frequency range, the intermediate-frequency range, and the high-frequency range. The foundation for DCT-based watermarking comprises a couple of simple facts. In the first place, an image’s most crucial visual aspects are located in the low-frequency sub-band, where much of the signal energy is. The second reality is that compression and noise attacks typically get rid of the high-frequency components of an image. Therefore, the watermark is encoded by altering the coefficients of the middle-frequency sub-band, guaranteeing that it will remain in place through decompression and viewing.
3.2. Discrete Wavelet Transform (DWT)
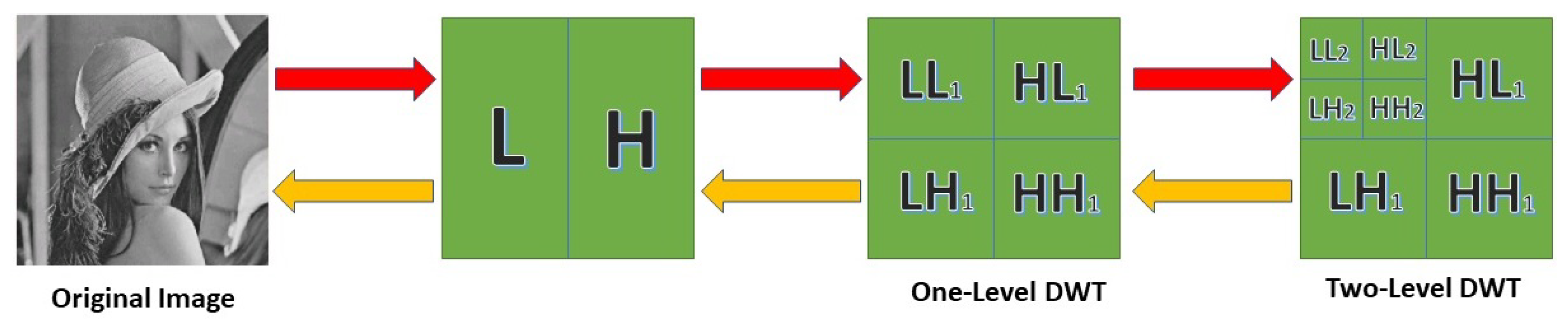
Multi-resolution analysis (MRA) of images is a very recent technique, and it relies on the mathematical framework provided by the relatively new theory of wavelets [59]. The concept is a wavelet- and transform-based image processing method. These are helpful, since they tell us about the frequency and timescale of an image. When a 2D wavelet transform is applied, the resulting representation of the image is a four-component sum across all resolutions. The analysis and representation of images and information at several resolutions are the goals of multi-resolution theory. It draws from a wide variety of disciplines to create a new method. Sub-band encoding is a technique from digital signal processing, and quadrature mirror filtering originates in the field of pyramidal imaging. Multi-resolution analysis is the popular name for a theoretical framework supporting many resolutions (MRA). MRA’s main benefit is that it can often identify previously invisible details at lower magnifications. An iterative succession of scaled-down versions of the input image is generated mathematically. At each tier, the resolution is multiplied by 2. For an image of size , the discrete wavelet transform is calculated as follows:
where
where i = {Diagonal, Vertical, Horizontal}, and is used to denote the scale, which is initially selected arbitrarily. The approximate value of at scale has approximate coefficient values that are denoted by . Coefficients of the form are appended for scales above , allowing for higher diagonal, vertical, and horizontal specificity. If and , then and are chosen. The inverse discrete wavelet transform yields when given and . To illustrate the two-level DFT that is used to decompose the input, Figure 3 shows this process.
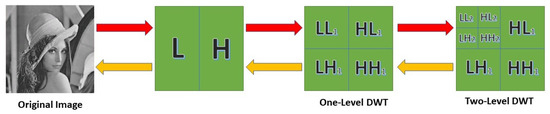
Figure 3.
The process of two-level decomposition using the discrete wavelet transform.
To calculate wavelet components, the Haar wavelet transform is utilized. The Haar transform is used to calculate wavelets, and this transformation is the most basic kind of wavelet. It is the basis for all subsequent refined wavelet types [60]. The mathematical expression for the mother wavelet function of the Haar wavelet is provided by the following equation:
The scaling function of the Haar function is denoted by , which is defined as follows:
The transform calculates the data points by summing and subtracting neighboring points. The horizontal and vertical components of the discrete wavelet transform are calculated by using these equations.
3.3. Dipper-Throated Optimization (DTO)
Meta-heuristic optimization is considered one of the best approaches that can be used to find the best parameters of artificial intelligence tasks [57,61,62,63,64]. The distinctive hunting technique, swift bowing movements, and the dipper-throated bird’s white breast inspired this optimization procedure. No matter how choppy or swift the current, it plunges headfirst into the sea to catch its victim. It can also dive into the water and stay submerged for long periods, using its wings as fins to drive itself through the water. The birds in the dipper-throated optimization (DTO) approach are presumed to be swimming about in search of food. The following matrices represent the birds’ positions (P) and speeds (S).
where and represent the bird in dimension i, and represents the bird in dimension j. For each pair where and , the speed of the bird in the jth dimension is denoted by . The values of are distributed normally at the outset. The fitness function values denoted by are calculated for each bird in the following array.
The fitness score of the mother bird is higher than those of her offspring because it has a greater advantage in the struggle for survival. The values are sorted upwards. The best solution, which is denoted , is declared. Birds with a regular appearance () are most suited for the role of followers. The best solution in the world is . The optimizer uses the following equations as the basis for the first DTO approach used to update the position of the swimming bird:
For each iteration i, we get the average position of the birds , the position of the best birds , and the speed of the birds . Weight values are denoted by , , and , whereas and are constants. Both and can take on any value between 0 and 1 at random.
The DTO algorithm is employed in the proposed optimization algorithm to find the optimal values of the scaling factor and the embedding coefficient to improve the performance of the standard DWT+DCT watermarking method.
3.4. Stochastic Fractal Search (SFS)
An algorithm that uses random fractals to inspire meta-heuristic algorithms can be as efficient and accurate as the original fractal technique. The fractal search (FS) technique follows three basic rules to find a solution to a given problem.
- The best particles are kept, while the others are removed with each new generation.
- There are several ways to make and disperse new particles. In the new particles, the original particle energy is shared.
- A particle can have electrical potential energy.
Finding fractals in any given object is possible using the stochastic fractal search (SFS), as explained in detail in [65]. The fractal-shaped objects are built using the diffusion-limited aggregation (DLA) process. Compared to the original FS approach, the SFS method uses diffusion and two distinct types of update processes. This solution BP might be surrounded by the solutions BP1–BP5 to arrive at the best potential outcome. The Gaussian distribution approach is used in the DLA growth process to produce new particles based on the diffusion procedure of SFS. A list of walks created by the best solution may be determined in the diffusion process.
where P denotes the updated best solution. The values of and are selected randomly from the range [0, 1]. The point in the group is denoted by V, whereas the position of the best point is referred to as P. In addition, is equal to and is equal to . A better solution can be found by applying SFS to the DTO process, which is an exploration method based on the algorithm’s diffusion process.
In the proposed optimization algorithm, the SFS is harnessed with the DTO algorithm to improve the exploration of the search space to efficiently find the best set of parameters. The steps of the proposed optimization algorithm are presented in the next section.
4. The Proposed Methodology
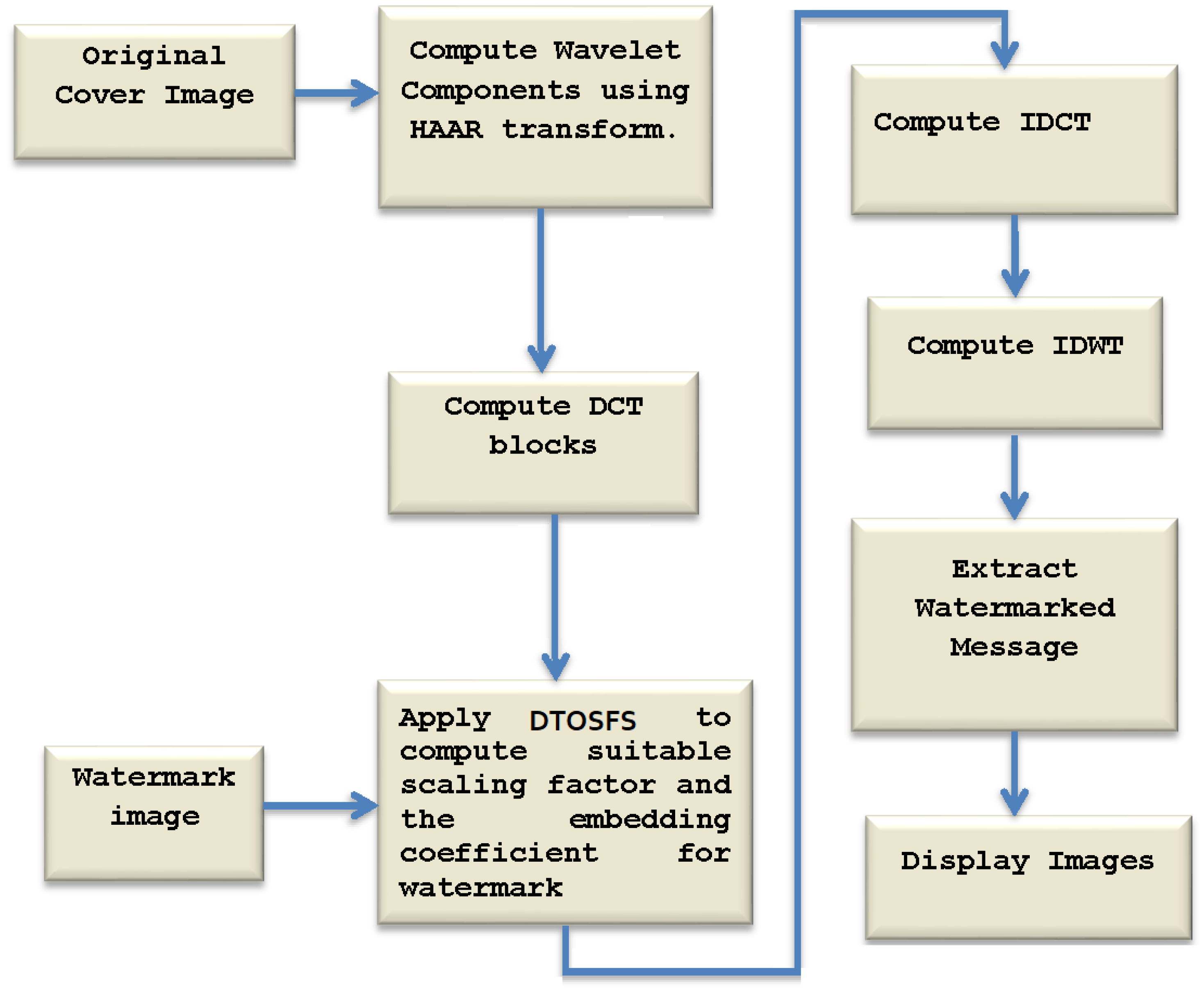
In images that are created digitally by using watermarking, an image is secretly implanted into a carrier image, and it is difficult to remove. Two processes make up watermarking: embedding and detection. The watermark image is embedded into the cover image to create a watermarked image. The scaling factor is crucial in creating a reliable and effective watermark. An optimal scaling factor is calculated to improve the algorithm’s reliability and performance. The suggested technique utilizes DTOSFS to calculate the scaling factor. The DCT coefficients of both the cover and watermark images are modified by a scaling factor for embedding purposes. Extracting them means getting the watermark with as little damage as possible. The inverse DWT and inverse DCT are used to extract the information. Figure 4 shows the flow of the steps included in the proposed methodology. These steps are described in the following.

Figure 4.
The detailed steps of the proposed approach.
- The cover image () and watermark images () are initially used for the watermarking process.
- The Haar wavelet transform is used to calculate the cover image’s wavelet transform [20]. The approximate result is the application of the Haar wavelet transform in two dimensions, with further computations for the horizontal, vertical, and diagonal components. Therefore, the discrete wavelet transform of the cover image () is:
- Applying the DCT transform to the wavelet transform results in a transformation from the time domain to the frequency domain. The formula for this step is as follows:The computation of the inverse of the DCT can be applied as follows:whereThe proposed algorithm is presented in Algorithm 1.
- The DTOSFS algorithm is applied to search for the optimal scaling factor and the coefficient for embedding the watermark. The result of using DTOSFS is the computation of the optimal value of , which is the invisibility or weighting coefficient.
- The watermark is inserted into the cover image by using an additive technique that is applied using the following formula.For the original image, the DWT coefficient is denoted by I. In contrast, refers to the DWT coefficient for the watermarked image, and for the watermark image, the DWT coefficient is denoted by W.
- The inverse DCT and inverse DWT of are applied to obtain the watermarked image.
- The inverse of the additive formula is applied to extract the watermark.Finally, the inverse DWT of W is applied to compute the raw watermark image .
| Algorithm 1 The Proposed DTOSFS Algorithm |
|
5. Results and Discussion
The proposed optimization algorithm is evaluated in terms of the digital image watermarking task to prove its superiority in finding the best parameters to help better embed the image in a cover image. The experiments were carried out on the three different cover images shown in Figure 5. The message embedded in the cover image was a sample Monkeypox image, which is shown in Figure 6.

Figure 5.
The cover images used in the conducted experiments. (a) Lena. (b) Cameraman. (c) Baboon.

Figure 6.
A Monkeypox image was employed as a message to be embedded in the cover image.
5.1. Evaluation Criteria
To measure the performance of the proposed approach, a set of evaluation criteria was employed to assess the achieved results. These criteria included the normalized correlation coefficient (NCC), image fidelity (IF), and peak-signal-to-noise ratio (PSNR). The formulas used to calculate these criteria are presented in the following:
where is the first image, is the second image, and are the means of the images, and and are the standard deviations of all of the points in I and , respectively.
where is the pixel at position , and is the stego image at the same position.
5.2. Experimental Results
The evaluation results of the proposed approach in comparison with four other watermarking methods in terms of the adopted criteria, which are presented in the previous section, are listed in Table 1. It can be noted in this table that the proposed approach (DWT+DCT+DTOSFS) was able to achieve the best values for the three cover images from Figure 5 when compared to the four other watermarking approaches. The other watermarking approaches included in the conducted experiment were the original DFT+SVD, the original DWT+DCT, the optimized DWT+DCT using the original SFS, and the optimized DWT+DCT optimized using the original DTO. The presented results show the effectiveness and superiority of the proposed approach. In the table, the PSNR value achieved by the proposed approach was 68.87, which was higher than the corresponding values achieved by the other approaches. Similarly, the values achieved using the proposed approach outperformed those of the competing approaches included in the experiment.

Table 1.
Assessment of the results achieved by the proposed approach in comparison with those of the other competing approaches.
On the other hand, a set of experiments were conducted to analyze the proposed approach’s statistical significance. The statistical analysis was performed based on the results achieved by the proposed method and the four other competing approaches. Table 2 presents the results of the statistical analysis. In this table, the number of samples included in the statistical analysis was 10. The standard error of the mean was 0.07676, and the standard deviation was 0.2427 when using the proposed approach; these were better than the values achieved by the other approaches. The measured values in this table demonstrate the stability of the proposed approach.

Table 2.
Statistical analysis of the proposed approach compared to other approaches.
In addition, two tests were applied to study the significance of the proposed approach. These tests were the one-way analysis of variance (ANOVA) test and the Wilcoxon test. The results of these tests are presented in Table 3 and Table 4, respectively. The difference between the proposed watermarking approach and each method of the competing watermarking methods was measured using the Wilcoxon test. The results of this test are shown in Table 4. In this table, the p-value is 0.002, which confirms the statistical difference in each watermarking method. As shown in Table 3, the measured p-value was less than 0.0001, which means that the proposed approach was statistically different from the other four watermarking methods.

Table 3.
Evaluation of the ANOVA test based on the recorded results.

Table 4.
Evaluation of the Wilcoxon signed rank test based on the recorded results.
In addition, another experiment was conducted to focus on the study of the significance of the proposed approach using the linear regression test. The results of this experiment are presented in Table 5. In this test, if the p-value was smaller than 0.05, then the null hypothesis was rejected and it was concluded that the relationship between the proposed approach and the approach presented in the test was significant. The results presented in the table show that the p-values for all methods included in the experiment were less than 0.05, and thus, there was a significant relationship between these methods and the proposed method. Moreover, an additional experiment was conducted to study the stability of the proposed watermarking approach. This experiment was based on the regression test. The results of this test are presented in Table 5. In this test, the results achieved by the proposed watermarking approach were analyzed with respect to the results achieved by the four other competing methods. The results shown in this table emphasize the stability of the proposed approach when compared to the other methods. The analysis of the area under the curve (AUC) was another experiment conducted to study the proposed approach’s effectiveness. The results of this experiment are presented in Table 6. In this table, it can be noted that the %Area was 100%, reflecting the proposed approach’s effectiveness.

Table 5.
The regression test between the proposed watermarking method and each one of the other competing watermarking methods.

Table 6.
Analysis of the area under the curve (AUC) of the results achieved with the proposed approach in comparison with the other approaches.
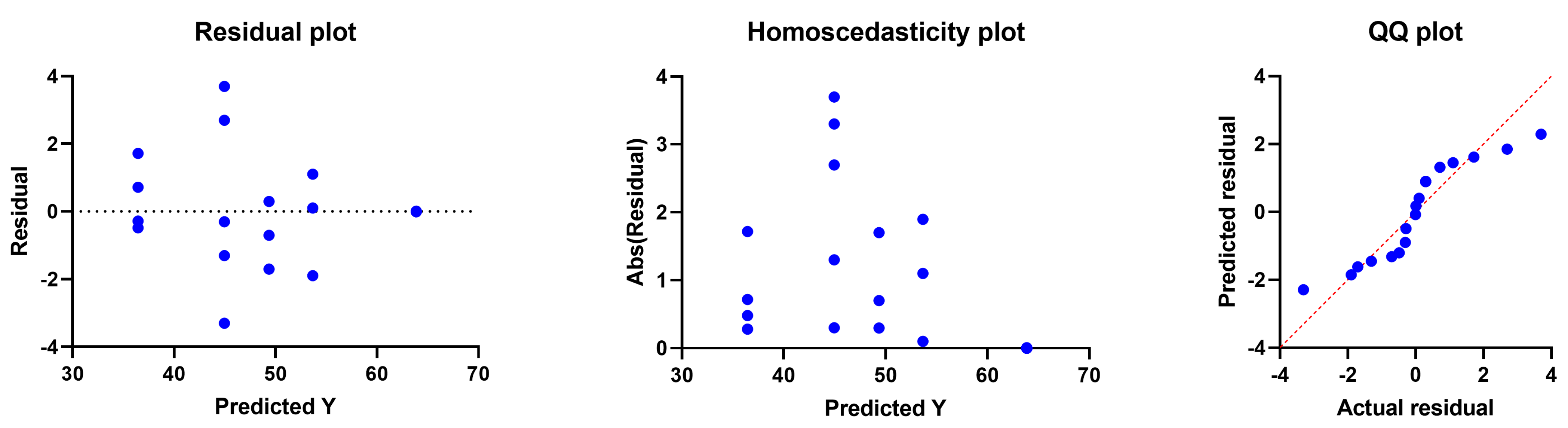
Moreover, the plots shown in Figure 7 illustrate the behavior of the residual, homoscedasticity, and quartile–quartile (QQ) of the results achieved by using the proposed DTOSFS approach. In these plots, it can be seen that the residual values were minor, reflecting the high accuracy of the proposed approach in efficiently recovering the watermark image compared to the other methods. Similarly, the behavior of the homoscedasticity and QQ was promising and showed the effectiveness of the proposed watermarking approach.

Figure 7.
The residual, homoscedasticity, and QQ plots of the results achieved by using the pro- posed approach.
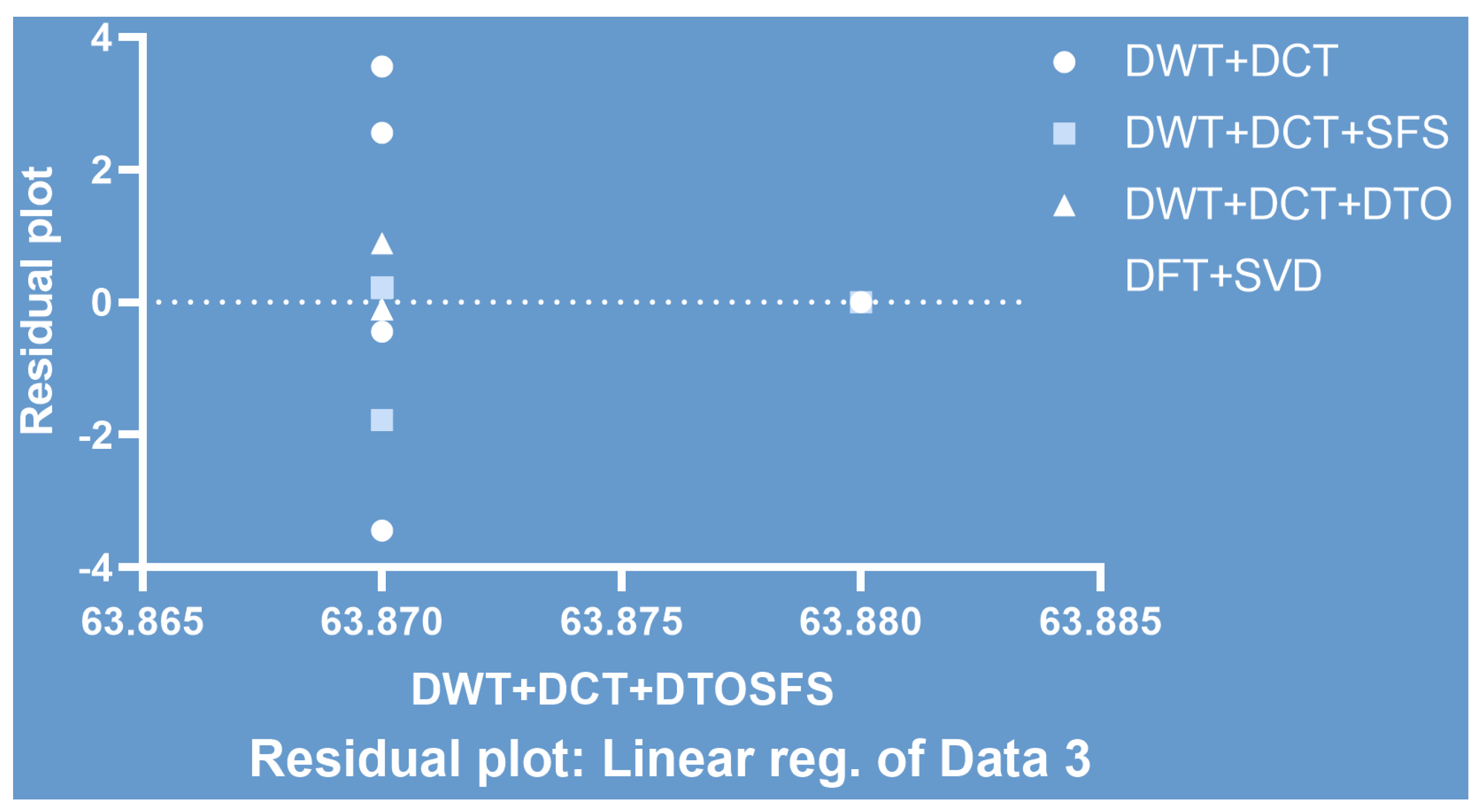
A residual plot of the comparitive results between the proposed method and the competing approaches is depicted in Figure 8. In addition, the receiver operating characteristic (ROC) is shown in Figure 9, and a histogram of the PSNR values is illustrated in Figure 10. As shown in these figures, the proposed approach outperformed the other methods, which confirmed the superiority of the proposed watermarking approach.

Figure 8.
The residual plot of the competing approaches compared to the proposed DWT+ DCT+DTOSFS.

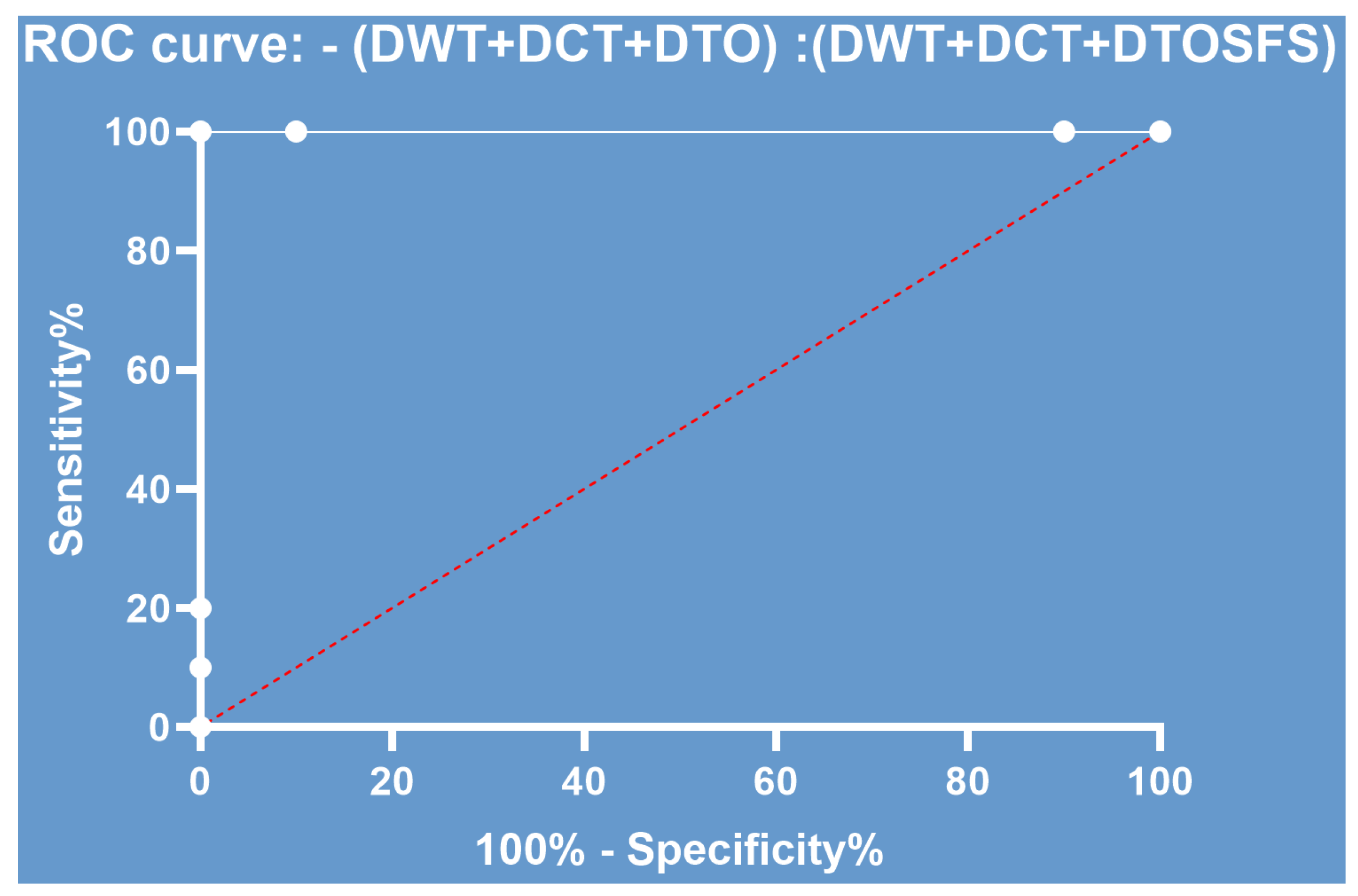
Figure 9.
The ROC curve of the results achieved with the proposed approach.

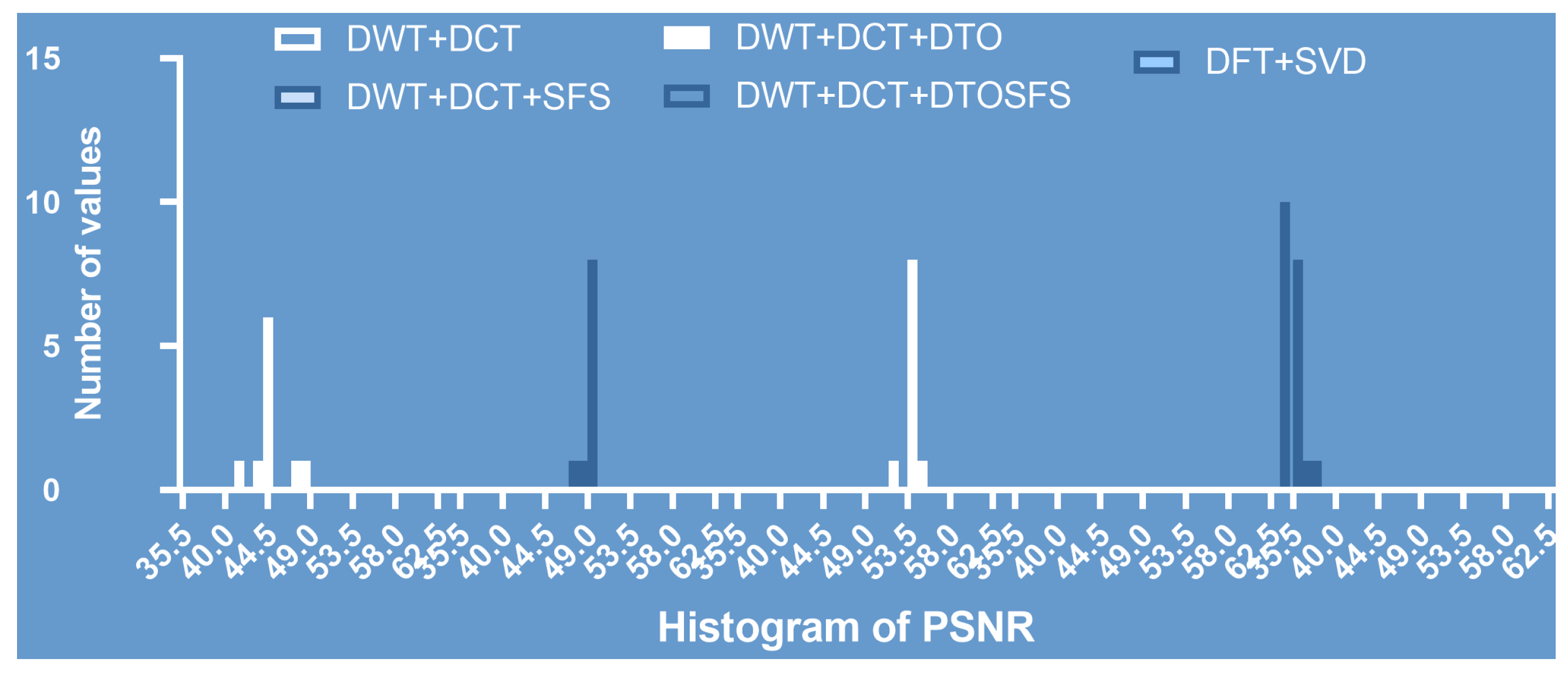
Figure 10.
Histogram of the PSNR values achieved with the proposed approach.
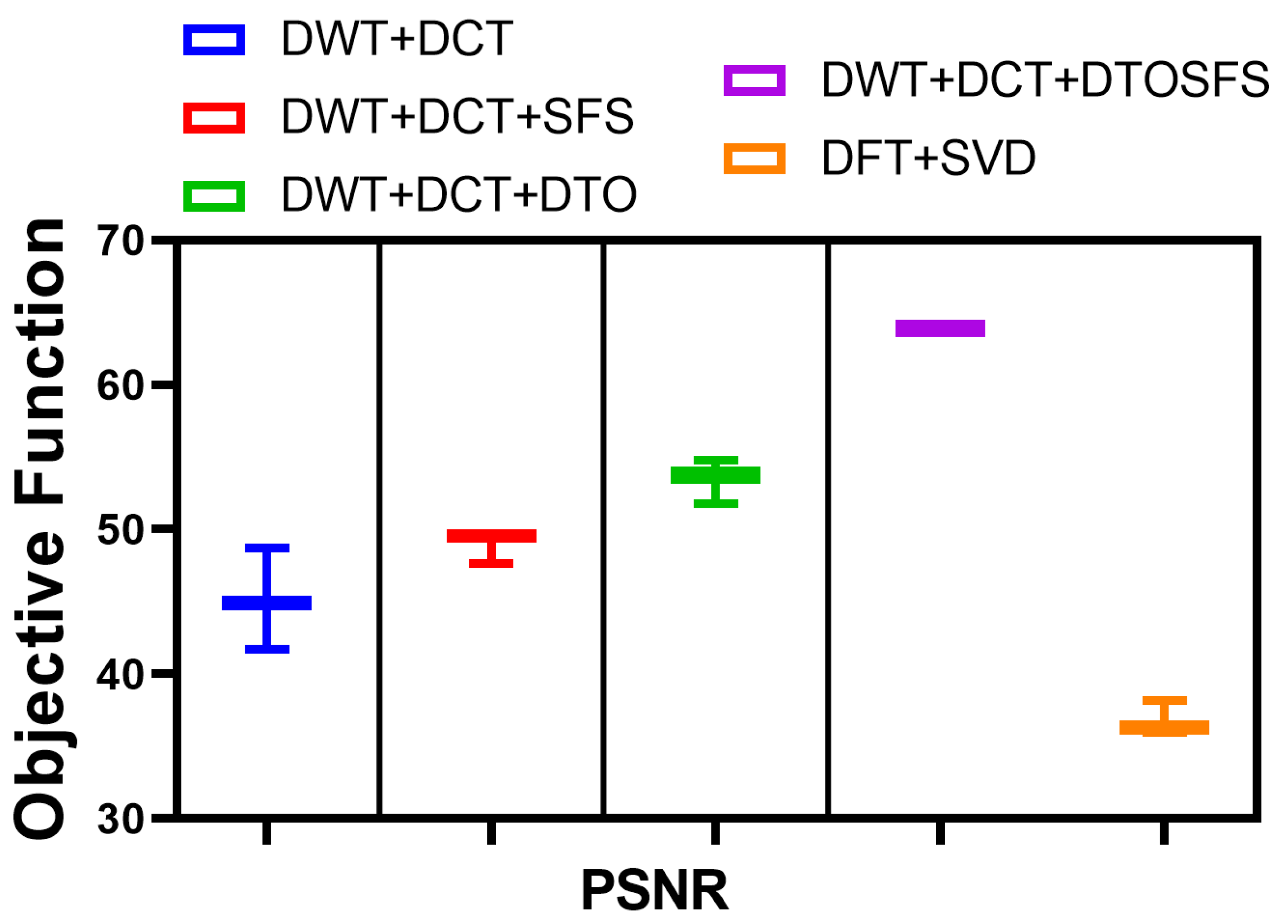
To emphasize the promising performance of the proposed approach, Figure 11 depicts the range of the PSNR values achieved with the proposed approach compared to those of the other four watermarking methods. In this figure, it is obvious that the proposed (DWT+DCT+DTOSFS) watermarking approach achieved the highest PSNR value, which strongly emphasized the proposed approach’s promising performance in digital watermarking.

Figure 11.
The PSNR values achieved by the proposed approach in comparison with the other approaches.
From the perspective of attacks on watermarked images, another experiment was conducted to study the effects of various types of attacks on the performance of the proposed approach when the Monkeypox was recovered. In this experiment, four types of attacks were considered: Gaussian filtering, median filtering, Wiener filtering, and average filtering. Table 7 presents the effect of each type of attack on the image recovered by the proposed watermarking approach in terms of the NCC and structural similarity index matrix (SSIM), along with their standard deviation (SD). As shown in the table, the quality of the recovered Monkeypox image was slightly affected by these attacks, especially when the Gaussian filtering attack was tested. In addition, the filter that significantly affected the recovered image was the average filter, for which the NCC value was 0.886 and the SSIM was 0.813. These results prove that the proposed watermarking approach was robust against certain types of attacks, such as Gaussian and median filtering attacks. Figure 12 shows the recovered Monkeypox image for each type of attack. On the other hand, the recovery time of the Monkeypox image using the proposed approach and the other four methods is listed in Table 8. In this table, it is shown that the proposed approach was able to recover/extract the Monkeypox image from the cover image faster than the other methods for the three cover images. These results clearly emphasize the superiority of the proposed watermarking approach. More comparison results are shown in Table A1 in Appendix A.

Table 7.
Comparison of the NC and SSIM values under various attacks.

Figure 12.
The watermarking results achieved by the proposed approach when applied to the Lena image.

Table 8.
The recovery time of the Monkeypox image in seconds.
6. Conclusions
In this paper, a new meta-heuristic optimization approach was proposed for the improvement of the performance of watermarking methods. The proposed optimization method was based on the DTO and SFS optimization algorithms, and DWT+DCT denotes the adopted watermarking method. Due to the increasing demand for hiding private health information, the proposed optimization algorithm was tested on the watermarking of a medical image in a cover image. The proposed optimization algorithm was used to optimize the watermark scaling factor. Because of the appropriate scaling factor provided by DTOSFS, the proposed approach was both reliable and efficient. To gauge how well the proposed approach worked, it was compared with four other watermarking approaches, and the results were recorded and analyzed. A set of statistical tests were conducted to study the proposed approach’s effectiveness, significance, and robustness. On the other hand, the proposed approach was evaluated in terms of various attack types. The experimental results confirmed the robustness and superiority of the proposed approach when compared with other optimization algorithms and different watermarking approaches. The potential future perspectives include improving the proposed optimization algorithm to boost the NCC and SSIM values of the recovered images when embedded in a cover image by using the proposed approach.
Author Contributions
Conceptualization, E.-S.M.E.-K. and A.A.A. (Amel Ali Alhussan); methodology, N.K.; software, E.-S.M.E.-K.; validation, S.M., A.A.A. (Abdelaziz A. Abdelhamid) and D.S.K.; formal analysis, A.I.; investigation, E.-S.M.E.-K.; resources, A.K.; data curation, S.M.; writing—original draft preparation, A.A.A. (Amel Ali Alhussan); writing—review and editing, A.A.A. (Amel Ali Alhussan); visualization, E.-S.M.E.-K.; supervision, S.M.; project administration, A.I.; funding acquisition, A.A.A. (Abdelaziz A. Abdelhamid), D.S.K. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Princess Nourah bint Abdulrahman University Researcher Supporting Project (number PNURSP2022R308), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
In this appendix, we present additional results to highlight the effectiveness and robustness of the proposed watermarking approach. The additional results were achieved by running the proposed approach on more cover images. Table A1 presents the PSNR values achieved with the proposed approach in comparison with methods that have recently been published in the literature. Each method in the previously published methods was proposed by using a different optimization algorithm. The results presented in this table emphasize the superiority of the proposed approach, as the PSNR value achieved by the proposed approach outperformed those of the other methods when tested on six other cover images.

Table A1.
Comparison of watermarking quality, measured using the PSNR.
Table A1.
Comparison of watermarking quality, measured using the PSNR.
| Abdelhakim et al. [66] | Abdelhakim et al. [67] | Vipul [33] | Proposed Approach | |||
|---|---|---|---|---|---|---|
| Bees | ABC | K-NN | ACO | LGBA | DWT+DCT+DTOSFS | |
| Elaine | 52.443 | 52.645 | 52.719 | 57.861 | 57.978 | 66.858 |
| House1 | 51.431 | 51.993 | 51.973 | 55.667 | 56.062 | 64.942 |
| Pirate | 51.477 | 52.523 | 52.683 | 57.165 | 57.271 | 66.151 |
| Boat | 51.434 | 52.163 | 52.109 | 55.898 | 56.278 | 65.158 |
| House2 | 53.007 | 56.749 | 56.805 | 60.992 | 61.302 | 70.182 |
| Zelda | 52.815 | 54.762 | 54.827 | 59.131 | 59.378 | 68.258 |
References
- Mathivanan, P.; Balaji Ganesh, A. QR code based color image cryptography for the secured transmission of ECG signal. Multimed. Tools Appl. 2019, 78, 6763–6786. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K.; Lv, Z.; Bhatnagar, G. Compression-Then-Encryption-Based Secure Watermarking Technique for Smart Healthcare System. IEEE MultiMedia 2020, 27, 133–143. [Google Scholar] [CrossRef]
- Abuadbba, A.; Khalil, I. Walsh–Hadamard-Based 3-D Steganography for Protecting Sensitive Information in Point-of-Care. IEEE Trans. Biomed. Eng. 2017, 64, 2186–2195. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. An improved DWT-SVD domain watermarking for medical information security. Comput. Commun. 2020, 152, 72–80. [Google Scholar] [CrossRef]
- Banerjee, S.; Singh, G.K. A new approach of ECG steganography and prediction using deep learning. Biomed. Signal Process. Control 2021, 64, 102151. [Google Scholar] [CrossRef]
- Mathivanan, P.; Balaji Ganesh, A. ECG steganography based on tunable Q-factor wavelet transform and singular value decomposition. Int. J. Imaging Syst. Technol. 2021, 31, 270–287. [Google Scholar] [CrossRef]
- Almeida, B.d.A.; Doneda, D.; Ichihara, M.Y.; Barral-Netto, M.; Matta, G.C.; Rabello, E.T.; Gouveia, F.C.; Barreto, M. Personal data usage and privacy considerations in the COVID-19 global pandemic. Cienc. Saude Coletiva 2020, 25, 2487–2492. [Google Scholar] [CrossRef] [PubMed]
- Bose, B.; Dey, D.; Sengupta, A.; Mulchandani, N.; Patra, A. A Novel Medical Image Encryption using Cyclic Coding in COVID-19 Pandemic Situation. J. Phys. Conf. Ser. 2021, 1797, 012035. [Google Scholar] [CrossRef]
- Reyad, O.; Karar, M.E. Secure CT-Image Encryption for COVID-19 Infections Using HBBS-Based Multiple Key-Streams. Arab. J. Sci. Eng. 2021, 46, 3581–3593. [Google Scholar] [CrossRef] [PubMed]
- Sanivarapu, P.V.; Rajesh, K.N.V.P.S.; Reddy, N.V.R.; Reddy, N.C.S. Patient data hiding into ECG signal using watermarking in transform domain. Phys. Eng. Sci. Med. 2020, 43, 213–226. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. Watermarking techniques for medical data authentication: A survey. Multimed. Tools Appl. 2021, 80, 30165–30197. [Google Scholar] [CrossRef]
- Mishra, A.; Agarwal, C.; Sharma, A.; Bedi, P. Optimized gray-scale image watermarking using DWT–SVD and Firefly Algorithm. Expert Syst. Appl. 2014, 41, 7858–7867. [Google Scholar] [CrossRef]
- El-Kenawy, E.S.M.; Mirjalili, S.; Abdelhamid, A.A.; Ibrahim, A.; Khodadadi, N.; Eid, M.M. Meta-Heuristic Optimization and Keystroke Dynamics for Authentication of Smartphone Users. Mathematics 2022, 10, 2912. [Google Scholar] [CrossRef]
- Khodadadi, N.; Snasel, V.; Mirjalili, S. Dynamic arithmetic optimization algorithm for truss optimization under natural frequency constraints. IEEE Access 2022, 10, 16188–16208. [Google Scholar] [CrossRef]
- Mirjalili, S.M.; Davar, S.; Khodadadi, N.; Mirjalili, S. Design Optimization of Photonic Crystal Filter Using Moth-Flame Optimization Algorithm. In Handbook of Moth-Flame Optimization Algorithm; CRC Press: Boca Raton, FL, USA, 2022; pp. 313–322. [Google Scholar]
- Khodadadi, N.; Soleimanian Gharehchopogh, F.; Mirjalili, S. MOAVOA: A new multi-objective artificial vultures optimization algorithm. Neural Comput. Appl. 2022, 1–39. [Google Scholar] [CrossRef]
- Abualigah, L.; Elaziz, M.A.; Khodadadi, N.; Forestiero, A.; Jia, H.; Gandomi, A.H. Aquila Optimizer Based PSO Swarm Intelligence for IoT Task Scheduling Application in Cloud Computing. In Integrating Meta-Heuristics and Machine Learning for Real-World Optimization Problems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 481–497. [Google Scholar]
- Alotaibi, S.S. Optimization insisted watermarking model: Hybrid firefly and Jaya algorithm for video copyright protection. Soft Comput. 2020, 24, 14809–14823. [Google Scholar] [CrossRef]
- S, E.J.; Ramu, P.; Swaminathan, R. Imperceptibility—Robustness tradeoff studies for ECG steganography using Continuous Ant Colony Optimization. Expert Syst. Appl. 2016, 49, 123–135. [Google Scholar] [CrossRef]
- Sharma, S.; Chauhan, U.; Khanam, R.; Singh, K.K. Digital Watermarking using Grasshopper Optimization Algorithm. Open Comput. Sci. 2021, 11, 330–336. [Google Scholar] [CrossRef]
- Savelyev, A. Copyright in the blockchain era: Promises and challenges. Comput. Law Secur. Rev. 2018, 34, 550–561. [Google Scholar] [CrossRef]
- Fujimura, S.; Watanabe, H.; Nakadaira, A.; Yamada, T.; Akutsu, A.; Kishigami, J.J. BRIGHT: A concept for a decentralized rights management system based on blockchain. In Proceedings of the 2015 IEEE 5th International Conference on Consumer Electronics—Berlin (ICCE-Berlin), Berlin, Germany, 6–9 September 2015; pp. 345–346. [Google Scholar] [CrossRef]
- Xu, R.; Zhang, L.; Zhao, H.; Peng, Y. Design of Network Media’s Digital Rights Management Scheme Based on Blockchain Technology. In Proceedings of the 2017 IEEE 13th International Symposium on Autonomous Decentralized System (ISADS), Bangkok, Thailand, 22–24 March 2017; pp. 128–133. [Google Scholar] [CrossRef]
- Divecha, N.; Jani, N.N. Implementation and performance analysis of DCT-DWT-SVD based watermarking algorithms for color images. In Proceedings of the 2013 International Conference on Intelligent Systems and Signal Processing (ISSP), Anand, India, 1–2 March 2013; pp. 204–208. [Google Scholar] [CrossRef]
- Soltani Panah, A.; Van Schyndel, R.; Sellis, T.; Bertino, E. On the Properties of Non-Media Digital Watermarking: A Review of State of the Art Techniques. IEEE Access 2016, 4, 2670–2704. [Google Scholar] [CrossRef]
- Parah, S.A.; Sheikh, J.A.; Loan, N.A.; Bhat, G.M. Robust and blind watermarking technique in DCT domain using inter-block coefficient differencing. Digit. Signal Process. 2016, 53, 11–24. [Google Scholar] [CrossRef]
- Feng, L.P.; Zheng, L.B.; Cao, P. A DWT-DCT based blind watermarking algorithm for copyright protection. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; Volume 7, pp. 455–458. [Google Scholar] [CrossRef]
- Rahman, A.U.; Sultan, K.; Musleh, D.; Aldhafferi, N.; Alqahtani, A.; Mahmud, M. Robust and Fragile Medical Image Watermarking: A Joint Venture of Coding and Chaos Theories. J. Healthc. Eng. 2018, 2018, e8137436. [Google Scholar] [CrossRef] [PubMed]
- Begum, M.; Uddin, M.S. Analysis of Digital Image Watermarking Techniques through Hybrid Methods. Adv. Multimed. 2020, 2020, e7912690. [Google Scholar] [CrossRef]
- Hu, H.T.; Hsu, L.Y. Collective blind image watermarking in DWT-DCT domain with adaptive embedding strength governed by quality metrics. Multimed. Tools Appl. 2017, 76, 6575–6594. [Google Scholar] [CrossRef]
- Natu, S.; Natu, P.; Sarode, T. Improved robust digital image watermarking with SVD and hybrid transform. In Proceedings of the 2017 International Conference on Intelligent Communication and Computational Techniques (ICCT), Jaipur, India, 22–23 December 2017; pp. 177–181. [Google Scholar] [CrossRef]
- Al-Shayea, T.K.; Batalla, J.M.; Mavromoustakis, C.X.; Mastorakis, G. Embedded Dynamic Modification for Efficient Watermarking Using Different Medical Inputs in IoT. In Proceedings of the 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Limassol, Cyprus, 11–13 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Sharma, V.; Mir, R.N. An enhanced time efficient technique for image watermarking using ant colony optimization and light gradient boosting algorithm. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 615–626. [Google Scholar] [CrossRef]
- Zhong, X.; Huang, P.C.; Mastorakis, S.; Shih, F.Y. An Automated and Robust Image Watermarking Scheme Based on Deep Neural Networks. IEEE Trans. Multimed. 2021, 23, 1951–1961. [Google Scholar] [CrossRef]
- Yadav, N.; Rajpoot, D.; Dhakad, S.K. Optimization of Watermarking in Image by Using Particle Swarm Optimization Algorithm. In Proceedings of the 2020 6th International Conference on Signal Processing and Communication (ICSC), Noida, India, 5–7 March 2020; pp. 85–90. [Google Scholar] [CrossRef]
- Rajani, D.; Kumar, P.R. An optimized blind watermarking scheme based on principal component analysis in redundant discrete wavelet domain. Signal Process. 2020, 172, 107556. [Google Scholar] [CrossRef]
- Lee, J.E.; Seo, Y.H.; Kim, D.W. Convolutional Neural Network-Based Digital Image Watermarking Adaptive to the Resolution of Image and Watermark. Appl. Sci. 2020, 10, 6854. [Google Scholar] [CrossRef]
- Frattolillo, F. A Watermarking Protocol Based on Blockchain. Appl. Sci. 2020, 10, 7746. [Google Scholar] [CrossRef]
- Kazemi, M.F.; Pourmina, M.A.; Mazinan, A.H. Analysis of watermarking framework for color image through a neural network-based approach. Complex Intell. Syst. 2020, 6, 213–220. [Google Scholar] [CrossRef]
- Garg, P.; Kishore, R.R. Optimized color image watermarking through watermark strength optimization using particle swarm optimization technique. J. Inf. Optim. Sci. 2020, 41, 1499–1512. [Google Scholar] [CrossRef]
- Kavitha, R.S.; Eranna, U.; Giriprasad, M.N. DCT-DWT Based Digital Watermarking and Extraction using Neural Networks. In Proceedings of the 2020 International Conference on Artificial Intelligence and Signal Processing (AISP), Amaravati, India, 10–12 January 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Song, M.; Wang, H.; Wu, J.; Yan, X.; Yuan, L.; Tu, Y. A robust watermarking hybrid algorithm for color image. MATEC Web Conf. 2021, 336, 07012. [Google Scholar] [CrossRef]
- Begum, M.; Uddin, M.S. Multiple Image Watermarking with Discrete Cosine Transform. J. Comput. Commun. 2021, 9, 88–94. [Google Scholar] [CrossRef]
- Evsutin, O.; Meshcheryakov, Y. The Use of the Blockchain Technology and Digital Watermarking to Provide Data Authenticity on a Mining Enterprise. Sensors 2020, 20, 3443. [Google Scholar] [CrossRef]
- Ma, Z.; Jiang, M.; Gao, H.; Wang, Z. Blockchain for digital rights management. Future Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Pérez Gort, M.L.; Feregrino-Uribe, C.; Cortesi, A.; Fernández-Peña, F. HQR-Scheme: A High Quality and resilient virtual primary key generation approach for watermarking relational data. Expert Syst. Appl. 2019, 138, 112770. [Google Scholar] [CrossRef]
- Rani, K.; Sharma, C. Tampering Detection of Distributed Databases using Blockchain Technology. In Proceedings of the 2019 Twelfth International Conference on Contemporary Computing (IC3), Noida, India, 8–10 August 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Sahoo, S.; Roshan, R.; Singh, V.; Halder, R. BDmark: A Blockchain-Driven Approach to Big Data Watermarking. In Proceedings of the Intelligent Information and Database Systems, Phuket, Thailand, 23–26 March 2020; Sitek, P., Pietranik, M., Krótkiewicz, M., Srinilta, C., Eds.; Communications in Computer and Information Science. Springer: Singapore, 2020; pp. 71–84. [Google Scholar] [CrossRef]
- Abdelhakim, A.M.; Saleh, H.I.; Nassar, A.M. A quality guaranteed robust image watermarking optimization with Artificial Bee Colony. Expert Syst. Appl. 2017, 72, 317–326. [Google Scholar] [CrossRef]
- Sejpal, S.; Shah, N. A novel multiple objective optimized color watermarking scheme based on LWT-SVD domain using nature based Bat Algorithm and Firefly algorithm. In Proceedings of the 2016 IEEE International Conference on Advances in Electronics, Communication and Computer Technology (ICAECCT), Pune, India, 2–3 December 2016; pp. 38–44. [Google Scholar] [CrossRef]
- Sisaudia, V.; Vishwakarma, V.P. Copyright protection using KELM-PSO based multi-spectral image watermarking in DCT domain with local texture information based selection. Multimed. Tools Appl. 2021, 80, 8667–8688. [Google Scholar] [CrossRef]
- Maloo, S.; Kumar, M.; Lakshmi, N. A Modified Whale Optimization Algorithm Based Digital Image Watermarking Approach. Sens. Imaging 2020, 21, 26. [Google Scholar] [CrossRef]
- Kazemivash, B.; Moghaddam, M.E. A robust digital image watermarking technique using lifting wavelet transform and firefly algorithm. Multimed. Tools Appl. 2017, 76, 20499–20524. [Google Scholar] [CrossRef]
- Ansari, I.A.; Pant, M.; Ahn, C.W. Artificial bee colony optimized robust-reversible image watermarking. Multimed. Tools Appl. 2017, 76, 18001–18025. [Google Scholar] [CrossRef]
- Moeinaddini, E. Selecting optimal blocks for image watermarking using entropy and distinct discrete firefly algorithm. Soft Comput. 2019, 23, 9685–9699. [Google Scholar] [CrossRef]
- Takieldeen, A.E.; El-kenawy, E.-S.M.; Hadwan, M.; Zaki, R.M. Dipper Throated Optimization Algorithm for Unconstrained Function and Feature Selection. Comput. Mater. Contin. 2022, 72, 1465–1481. [Google Scholar] [CrossRef]
- Abdelhamid, A.A.; El-Kenawy, E.S.M.; Alotaibi, B.; Amer, G.M.; Abdelkader, M.Y.; Ibrahim, A.; Eid, M.M. Robust Speech Emotion Recognition Using CNN+LSTM Based on Stochastic Fractal Search Optimization Algorithm. IEEE Access 2022, 10, 49265–49284. [Google Scholar] [CrossRef]
- Strang, G. The Discrete Cosine Transform. SIAM Rev. 1999, 41, 135–147. [Google Scholar] [CrossRef]
- Bruce, L.; Koger, C.; Li, J. Dimensionality reduction of hyperspectral data using discrete wavelet transform feature extraction. IEEE Trans. Geosci. Remote Sens. 2002, 40, 2331–2338. [Google Scholar] [CrossRef]
- Reisenhofer, R.; Bosse, S.; Kutyniok, G.; Wiegand, T. A Haar wavelet-based perceptual similarity index for image quality assessment. Signal Process. Image Commun. 2018, 61, 33–43. [Google Scholar] [CrossRef]
- El-Kenawy, E.S.M.; Mirjalili, S.; Alassery, F.; Zhang, Y.D.; Eid, M.M.; El-Mashad, S.Y.; Aloyaydi, B.A.; Ibrahim, A.; Abdelhamid, A.A. Novel Meta-Heuristic Algorithm for Feature Selection, Unconstrained Functions and Engineering Problems. IEEE Access 2022, 10, 40536–40555. [Google Scholar] [CrossRef]
- Khafaga, D.S.; Alhussan, A.A.; El-Kenawy, E.S.M.; Ibrahim, A.; Eid, M.M.; Abdelhamid, A.A. Solving Optimization Problems of Metamaterial and Double T-Shape Antennas Using Advanced Meta-Heuristics Algorithms. IEEE Access 2022, 10, 74449–74471. [Google Scholar] [CrossRef]
- Khafaga, D.S.; El-kenawy, E.-S.M.; Karim, F.K.; Alshetewi, S.; Ibrahim, A.; Abdelhamid, A.A. Optimized Weighted Ensemble Using Dipper Throated Optimization Algorithm in Metamaterial Antenna. Comput. Mater. Contin. 2022, 73, 5771–5788. [Google Scholar] [CrossRef]
- Alhussan, A.A.; Khafaga, D.S.; El-Kenawy, E.S.M.; Ibrahim, A.; Eid, M.M.; Abdelhamid, A.A. Pothole and Plain Road Classification Using Adaptive Mutation Dipper Throated Optimization and Transfer Learning for Self Driving Cars. IEEE Access 2022, 10, 84188–84211. [Google Scholar] [CrossRef]
- El-Kenawy, E.S.M.; Eid, M.M.; Saber, M.; Ibrahim, A. MbGWO-SFS: Modified Binary Grey Wolf Optimizer Based on Stochastic Fractal Search for Feature Selection. IEEE Access 2020, 8, 107635–107649. [Google Scholar] [CrossRef]
- Abdelhakim, A.M.; Saleh, H.I.; Nassar, A.M. Quality metric-based fitness function for robust watermarking optimisation with Bees algorithm. IET Image Process. 2016, 10, 247–252. [Google Scholar] [CrossRef]
- Abdelhakim, A.M.; Abdelhakim, M. A time-efficient optimization for robust image watermarking using machine learning. Expert Syst. Appl. 2018, 100, 197–210. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).