eHealth: A Survey of Architectures, Developments in mHealth, Security Concerns and Solutions
Abstract
1. Introduction
- 1.
- We discuss the various architectures deployed in eHealth from a structural standpoint, narrowing our focus to the various areas in which these architectures are implemented in eHealth. The various architectures noted for eHealth system deployment are extensively discussed, with a focus on Blockchain, IoT, and cloud-based architectures.
- 2.
- We provide an overview of mHealth, a subset of eHealth, and its components, which include mobile computing devices, wireless sensors, and communication technologies. We also highlighted notable cutting-edge mHealth technologies in wireless communication, their bandwidth, coverage area, and mobility, as deployed in eHealth, to provide researchers with an overview of the most recent advances in this domain.
- 3.
- We highlight the special needs of patient privacy, secured data collection, transmission/retransmission, data storage, and eHealth infrastructure management, as well as future research challenges in security and privacy for eHealth record keeping. Recommendations for future improvement are also suggested.
2. Related Literature Surveys
3. Methodology
3.1. Literature Survey Questions
- 1.
- What are the most feasible architectures for establishing eHealth systems, together with their advantages and disadvantages?
- 2.
- How are these architectures implemented for eHealth systems?
- 3.
- What are the fundamental components and current improvements in mHealth that are necessary for the effective implementation of eHealth systems?
- 4.
- What are the relative advantages and disadvantages of these various mHealth elements in relation to eHealth systems, and how has the literature evolved in this regard?
- 5.
- What are the typical threats, goals, and solutions associated with the successful implementation of eHealth systems?
- 6.
- What are the research challenges and possible future prospects for the development/enhancement of architectures, mHealth, and security concerns in eHealth systems?
3.2. Search and Selection Strategy
- 1.
- We searched for articles using the Scopus, ACM Digital Library, IEEExplore, Springer Link, and Google Scholar databases. We considered the Scopus database because of its high-quality indexing and computer science-related information. IEEExplore, which focuses mostly on computer science, engineering, and electronics, received similar consideration. Due of their magnitude and potential to locate relevant papers, we also analyzed the ACM database and Spring Link. Following our exploration of these databases, we performed a last double-check using the Google Scholar database to decrease the number of missing articles.
- 2.
- Then, the terms that define our area of interest, namely “architectures”, “mHealth”, and “security”, were identified. These keywords were derived from a preliminary literature search to locate survey publications that had previously addressed the same issues. In addition, we generated a list of search strings that combine the operators “AND” and “OR” with the keywords and the term “eHealth”.
- 3.
- These keywords and phrases were used to search databases as mentioned above such as Scopus and Google Scholar, among others that were considered.
- 4.
- The search yielded over 22,700 results, which were then reduced based on the time span covered within the previous two decades. Additionally, these results were enhanced based on the following key categories: “architectures”, “mHealth”, and “security”. These keywords were used to manually reduce the number of articles to 250. The excluded articles were those that did not directly contribute to our area of interest.
- 5.
- In addition, survey papers located within this limited list were filtered and assessed to determine the uniqueness of our present article; and our findings are discussed in the related literature survey section (Section 2).
3.3. Assessment and Synthesis of Information
- Inclusion criteria
- 1.
- All articles must be published in journals or conference proceedings.
- 2.
- All relevant survey articles must be very specific and pertinent to the existing elements of an eHealth system, and
- 3.
- Articles relating to the given keywords must emphasize them extensively, as opposed to merely mentioning them.
- Exclusion criteria
- 1.
- All articles without a full text were excluded,
- 2.
- Articles that only mentioned the keywords were disregarded, and
- 3.
- Preprints, reports, lecture notes, and proposals were removed.
- 1.
- We generated a set of questions and answers to evaluate the contextual information of each article.
- 2.
- First, does the article primarily discuss eHealth system architectures? If yes, then the article was accepted to be studied. If no, was the discussion of architectures across a complete section? If yes, the article was studied; if no, it was deemed a simple mention of the term and was thus not considered worthy to be referenced.
- 3.
- Likewise, for each keyword (i.e., mHealth and security in eHealth), the same assessment questions as above were adopted to ensure that the retrieved articles were relevant enough for further synthesis.
3.4. Article Development and Presentation of Information
- 1.
- Following a modification of the well known IMRAD framework (i.e., Introduction, Methods, Results, and Discussion), the outline for our manuscript was constructed. In our case, since we aim to present a traditional literature survey article, the body of the manuscript was separated into three main sections based on the three keywords. Utilizing this strategy assisted in elucidating the scope of our article. However, in the absence of a results and a discussion section, we introduced the summary per section as well as the closing research challenges and future direction section as part of the body of work.
- 2.
- The different pieces of our synthesized information were then clustered depending on how each article relates to the research questions, and then each section was expanded upon to include the pros and cons of the different eHealth-related methods.
- 3.
- The final draft of our manuscript was then revised in accordance with the overarching purpose, which was to give a comprehensive overview of architectures, mHealth, and security in order to facilitate the development of viable eHealth systems.
4. eHealth: An Overview
4.1. Definition of eHealth
4.2. Major Components of eHealth
4.2.1. Health Informatics
- 1.
- Enhance both individual and clinical patient care.
- 2.
- Help improve the health of global populations (such as using data for prediction and prevention of disease outbreaks).
- 3.
- Make it possible for organizations that provide medical care to do so at a lower cost.
4.2.2. Electronic Health Record
- 1.
- Person identifier
- 2.
- Faculty identifier
- 3.
- Provider identifier
- 4.
- Health information
- 5.
- Administrative information
4.2.3. Telemedicine
4.2.4. Computerized Physician Order Entry
- Specific details pertaining to the patient in question
- The function of a required member of the staff.
- The resources, materials, and medication given.
- The procedures that are to be carried out.
- The proper order of operations that must be followed.
- The feedback to be taken into account.
- The documentation unique to each individual case that must be constructed.
- 1.
- Reduce errors and enhance patient safety: At the very least, CPOE can assist an organization in reducing errors. This is accomplished by ensuring that providers produce orders that are standardized, clear, and comprehensive. In addition, CPOE technologies typically incorporate clinical decision support tools that are already built in. These tools enable the technology to perform an automatic check for drug interactions, pharmaceutical allergies, and other potential issues.
- 2.
- Improve efficiency: CPOE can help an organization improve its efficiency by accelerating the delivery of medication, laboratory, and radiology orders to pharmacies, facilities that perform radiology, and laboratories, thereby reducing the amount of time wasted and increasing the amount of time available for other tasks.
- 3.
- Improve reimbursements: Some items require pre-approval from insurance schemes. When CPOE is integrated with an electronic practice management system, it has the ability to highlight orders that need pre-approval, which can help you reduce the number of insurance claims that are rejected.
4.2.5. E-Prescription
5. eHealth: An Overview of Architectures
5.1. Blockchain-Based Architecture
5.1.1. Benefits of the Blockchain-Based Architecture
- 1.
- It ensures that EHRs are stored in a secure and open manner.
- 2.
- Provides regulated controlled access to data.
- 3.
- Ensures the integrity of the data and that they cannot be changed.
- 4.
- Makes it possible to share data.
- 5.
- Provides remote patient monitoring.
- 6.
- Adapts to the challenges posed by constrained IoT devices.
5.1.2. Limitations of the Blockchain-Based Architecture
- 1.
- Several articles have discussed the drawbacks of blockchain technology in the context of eHealth. For example, in [64], the drawbacks of proof-of-work (POW) in a consensus blockchain algorithm were highlighted. To add a block to a POW-based blockchain, miners must perform computationally expensive tasks (carried out by multiple entities), making Sybil attacks nearly impossible. Miners must then be able to perform a certain amount of work in order to calculate the number. When a miner solves a problem, all other nodes must verify that the solution is correct. As a result, POW consumes more energy, rendering it inefficient for use in low-power applications. Furthermore, the increase in block transactions does not correspond to an increase in POW nodes participating in block verification; thus, it is not scalable.
- 2.
- Another disadvantage mentioned in [64] is that the blockchain mining process benefits the wealthiest participants, who may own a larger stake than other nodes.
- 3.
- In a different article [65], the authors stressed the importance of the determination of a data sharing protocol as a difficulty in the implementation of blockchain technology in eHealth. For instance, there is a need for clarification regarding how a patient can pick which data to disclose and with whom they share it. The patient, who is the legal owner of the information, is the one who needs to give permission for a healthcare provider to access it. It is not apparent who has the authority to act on behalf of a patient in the event that the patient is unable to carry out the requested action for any reason. There is also a lack of clarity on the quantity of health data that must be stored online and whether or not that data may be shared indefinitely or for a predetermined period of time.
- 4.
- In addition, a notable limitation of the blockchain-based architecture is the difficulty of achieving both cost-effectiveness and scalability while managing vast quantities of data that have not yet been subjected to quality assurance testing in production settings. When the volume of traffic increases, the length of time it takes to complete a transaction might become prohibitively long, depending on the protocol; this has an effect on the scalability of the system and the amount of computing power that is necessary.
5.2. IoT-Based Architecture
5.2.1. IoT in eHealth
- Patient monitoring: for example, tensiometer sensors have been implanted in hypertensive patients as part of a real time monitoring framework in order to reduce time-consuming and inconvenient follow-up visits to the doctor [69].
- Preservation facilities: for example, medical refrigerators have been designed with IoT devices to control the conditions inside freezers for storing vaccines, drugs, and organic elements [70].
- Elderly home tracking systems: Doctors can monitor elderly patients at home, lowering hospital costs and increasing time intervention to crisis situations [71].
5.2.2. IoT Architectures for eHealth
- 1.
- Perception Layer: The perception layer is similar to the device layer in the three-layer model. It includes physical objects and sensor devices. Depending on the mechanism used to identify the object, the sensors may be based on RFID, 2D-barcode, or infrared technologies. This layer is primarily concerned with the identification and gathering of object-specific data by sensor devices. Depending on the type of sensors, the data may pertain to location, temperature, direction, motion, vibration, acceleration, humidity, chemical changes in the air, to name a few. The acquired information is subsequently transferred to the network layer for transmission to the information processing system in a secure manner.
- 2.
- Network Layer: This layer is often referred to as the transmission layer. The network layer delivers data from sensor devices to the information processing system in a secure manner. Depending on the sensor devices, the transmission method may be wired or wireless, and the technology may be 3G, UMTS, WiFi, Bluetooth, infrared, ZigBee, etc. Consequently, the network layer sends data from the perception layer to the upper layers.
- 3.
- Middleware Layer: IoT devices implement a distinct type of service where each device only connects and communicates with other devices that support the same service type. The layer responsible for facilitating these tasks is called the middle layer, which is in charge of service management and it is connected to the database. It stores the information received from the network layer in the database. It conducts information processing and ubiquitous computation and makes judgments automatically based on the outcomes.
- 4.
- Application Layer: This layer enables global application administration based on the middleware layer’s processing of object information. IoT applications at this layer include smart health, smart farming, smart homes, smart cities, and intelligent transportation, among others.
- 5.
- Business Layer: This layer is responsible for managing the IoT system as a whole, including applications and services. Based on the data received from the application layer, it constructs business models, graphs, flowcharts, etc. The true success of IoT technology is contingent upon sound business strategies. This layer will help identify future actions and company strategies based on outcomes analysis. These five layers are summarized in Figure 9.
5.2.3. Benefits of IoT-Based Architectures
- 1.
- Patient safety and quality of life can both be improved by continuously monitoring patients’ conditions without interfering with their daily lives and allowing for remote assessments.
- 2.
- Individuals will have a greater level of autonomy and initiative with regard to their own health status, which will provide them with a better level of control over their own well being.
- 3.
- By analyzing a massive amount of data, health experts can improve preventative care and make the eHealth system more effective.
- 4.
- It is possible to lower the expenses of patient care provided in hospitals and prevent supply shortages by employing remote monitoring and automated equipment stock management.
5.2.4. Limitations of IoT-Based Architectures
- 1.
- Keeping the sensitive data collected and transmitted by IoT devices secure is difficult as their use expands and evolves. Despite the importance of cybersecurity, IoT devices are not usually incorporated in the plan. Devices must be safeguarded against physical manipulation, Internet-based software assaults, network-based attacks, and hardware attacks.
- 2.
- Although it may appear that IoT devices perform simple functions, such as tracking a patient’s temperature, there is a great deal of technical technology involved in their creation. In addition, if they provide erroneous vital data to another workflow or system, they may negatively impact everything associated with it. Inaccurate measurements can be devastating and may be difficult to detect and correct.
- 3.
- In order for a lot of different IoT devices to work correctly, they need to be connected to the Internet and have constant electricity. If either fails, the gadget as well as anything else that is attached to it will become inoperable. When it comes to today’s enterprises, IoT devices are so interconnected that if they go down, everything can come to a grinding halt. As a result, there is a need for gadgets that are powered by batteries, which raises further concerns about energy management and sustainability.
- 4.
- Because there is presently no consensus over IoT eHealth-based protocols and standards, it is possible that devices manufactured by various companies will not be compatible with the technology that is currently available. It is possible that each one will require a distinct configuration and connection to the hardware, making it difficult to deploy efficiently.
- 5.
- The deployment of sensitive eHealth IoT devices and systems typically calls for significant investments of both time and money. There are a lot of devices that need to be bought and set up, as well as employees who need to install them, others who need to integrate them into the network, and support calls that need to be made to the manufacturer. Health businesses are able to quickly recoup their losses when all of their operations are consolidated into a single location. However, the cost can be expected to increase if the health company or institution decides to distribute them.
5.3. Cloud-Based Architecture
- 1.
- The WSN, which is responsible for collecting patient information regarding their health.
- 2.
- The monitoring applications, which provide specialists in the healthcare industry with access to the data that have been stored.
- 3.
- The healthcare authority (HA), which is responsible for defining and enforcing the safety policies of the healthcare institution.
- 4.
- The cloud servers, which are responsible for ensuring the storage of data.
- 1.
- Cloud computing and web services: The availability of a cloud-based service platform would make it much simpler to construct healthcare apps and services that make use of the vast health-related data set provided by end-user devices.
- 2.
- Home system: This system typically consists of a central controller that collects data from sensors and medical equipment used to monitor a person’s health and serves as a home gateway.
- 3.
- Web portal: The web portal acts as the system’s user interface.
5.3.1. Benefits of Cloud-Based Architectures
- 1.
- Cost reduction: Cloud services rendered in a cloud-based architecture are capable of lowering the expenses associated with building up health-based infrastructure, maintenance, and utility management for the servers. Designers only pay for server time and memory space when using cloud computing services.
- 2.
- Reliability: Cloud-based architectures offer data redundancy because the data is not merely saved on a single server but rather is distributed across numerous servers.
- 3.
- Accessibility: eHealth is a highly accessible and flexible technology as a result of its ability to store information in a cloud-based architecture, which enables users to access the information regardless of the system they are using, whenever they need it, and wherever they are.
- 4.
- Large capacity for data storage: The cloud service provides users with an almost infinite capacity for data storage, which may be expanded at any moment for a very modest additional cost on a monthly basis.
5.3.2. Limitations of Cloud-Based Architectures
- 1.
- Downtime: Cloud-based architecture, like all other architectures, is dependent on the availability of electricity and the Internet. When Internet access is lost, an architecture with this dependency becomes unreachable.
- 2.
- Security: Because data can be accessible by other people while they are in transit or while they are stored in the cloud, there is always a risk of the data’s confidentiality being compromised. The use of a cloud computing system indicates that the architecture has completely put faith in the security and confidentiality of the data being stored on cloud computing servers provided by third-party businesses. Consequently, users cannot necessarily sue the cloud service providers for inaccuracies in the data whenever there is a problem since such challenges are typically not covered in the terms of conditions.
- 3.
- Latency: Due to the obvious great distance that must be traversed to send data to the cloud, there is a problem of delay that emerges, which has the potential to disrupt emergency services provided by the eHealth system. Additionally, the quality of the servers used for cloud computing may also have an effect on the processing speed during peak times, which may result in latency in an electronic health record system.
5.4. Summary of Discussion
5.4.1. Our Take-Aways
- 1.
- From our review, it is worth noting that one prominent and contemporary architecture is the IoT/cloud architecture, which is characterized by a three-layer model, namely the perception (device), network, and application layer. The perception layer is made up of several intelligent objects that are outfitted with sensors to collect and process data as part of the Big Data initiative [79]. The network layer being the second layer includes network, routing, and identification technologies required for application operations, while the application layer, which is the third layer provides services to users. The IoT/cloud architecture is singled out for mention here because it represents a fundamental framework upon which eHealth systems may be designed and implemented. This is because it meets the needs for eHealth services in terms of sensing, processing, and decision-interfacing.
- 2.
- Despite the fact that these architectures have been discussed separately, any realistic and viable architecture must integrate these three different technologies in order to ensure workability. Thus, a unified eHealth architecture is advocated that will incorporate blockchain, IoT, and cloud-based technologies.
- 3.
- A wide range of other architectures and technologies have been used to achieve this integration via the use of 5G, Fibre, and web services.
- 4.
- As shown in Table 3, the literature on architectures for the implementation of eHealth systems has expanded to include a wide variety of architectures with their specific purposes.
5.4.2. Our Recommendations
- 1.
- In eHealth systems, a substantial amount of work has been covered in terms of developing specific designs for various objectives, such as continuous monitoring, remote administration, control, and decision making. However, meaningful comparative assessments of these various architectures in terms of their viability, compactness, and security have much to be desired and more research is needed in this regard.
- 2.
- We also recommend that future survey articles should cover additional topics involving the implementation of Big Data analytics into eHealth designs, which has witnessed tremendous research and could suffice as a standalone survey.
- 3.
- Furthermore, to summarize, we note that there may not be a single best architecture because they all have their respective benefits and drawbacks; rather, we suggest that a unified integrated architecture may be the way forward for the deployment of eHealth infrastructure and services.
6. eHealth: Advances in mHealth
6.1. Definition of mHealth
6.2. Wireless Sensors in mHealth
6.3. Mobile Computing Devices in mHealth
- Mobile phones;
- Personal digital assistants (PDAs);
- Smartphones;
- Portable media players;
- Handheld and ultra-portable computers such as tablets PCs.
- 1.
- Patients are able to receive the care they require regardless of where they are located, in addition to having increased access to their own medical information.
- 2.
- It makes it possible to simply coordinate consultations between different providers located in different parts of the world. It enables clinicians to communicate about a patient and assists in obtaining the necessary therapy for them, particularly in situations where a patient requires the care of a specialist who is not available in their area.
- 3.
- There are a variety of EHRs and/or billing systems that can make things simpler for physicians, billers, and coders by utilizing mobile technology.
- 4.
- It also has the potential to improve accuracy all throughout an organization. When using paper documents, it is difficult to maintain an orderly structure, and it is difficult to identify faults that have been made. Errors are caught by digitized systems, and when those systems are made available on mobile devices, accuracy increases at every step of the process.
- 5.
- It enables hospitals and medical practices that are more efficient. Better outcomes are typically the result of improved communication between healthcare practitioners and patients, decreased rates of medical errors, and increased ease of access for patients.
6.4. Communication Technologies for mHealth
6.4.1. Short-Ranged Technologies
6.4.2. Satellite Communication for mHealth
- Advantages:
- 1.
- Comprehensive geographic coverage, along with the integration of isolated terrestrial networks (“islands”).
- 2.
- It is capable of providing Demand Assignment Multiple Access (DAMA), also known as bandwidth on demand.
- 3.
- It serves as an optional replacement for damaged fiber-optic networks for disaster recovery.
- 4.
- The Internet and satellites’ broadcasting capabilities promote multipoint-to-multipoint communications.
- Disadvantages:
- 1.
- It has asymmetric transmission rates [128]. Even in advanced services utilizing a dish with a diameter of 1.2 m, the uplink speed is less than 2 Mbps, while the downlink speed can reach 60 Mbps. Uplink speeds are crucial for the provision of telemedicine, as high-quality still or live video images of patients must be transmitted to hospitals using uplink communication. These images are crucial for doctors to diagnose the medical conditions of victims.
- 2.
- Secondly, VSAT equipment items are frequently cumbersome [131]. When a large-scale natural catastrophe happens, it may be hard to transport VSAT equipment to some devastated areas due to severely damaged roads and halted traffic.
- 3.
- Large latency resulting from the distance traversed by data over VSAT systems, which makes them inefficient for eHealth emergency services.
- 1.
- Significant advancements have been made in the signal capacity of geostationary satellites (GEOs), which can currently receive and broadcast at hundreds of gigabits per second [132]. Modern GEO satellites also operate for longer periods of time and with higher power than ever before. They will undoubtedly play a significant role in the provision of broadband Internet to developing nations with lower average earnings. This has the potential to significantly improve the delivery of eHealth services in low-income contexts.
- 2.
- Developments in Ka-band Systems for Mobile Satellite Communications (KASYMOSA) intends to expand the mobile space’s use of satellite technology. This requires advancements in antenna array, new location strategies, and a major increase in bits-per-second attributes [133]. In this regard, engineers believe that further Ka-band development will enable consumer-level satellite phone calls, enhanced emergency response efforts, and other revolutionary functions [134].
- 3.
- In recent years, there has been a significant effort to build satellite phased array antennas for broadband communications [135]. This will provide broadband capabilities to both land and marine vehicles, as well as boost worldwide Internet connectivity, which will ultimately enhance the delivery of eHealth services [136].
- 4.
- Advances in software-defined satellites will enable satellites to carry digital payloads with the essential components to transmit and receive data at ranges unimaginable a decade ago, regardless of environmental impediments such as canopy forests or mountains [137]. This innovation would eliminate the requirement for prelaunch testing, saving considerable time and money and enhancing the delivery of eHealth services.
6.4.3. Mobile Cellular Systems for mHealth
3G Systems
- Advantages:
- 1.
- In addition to providing access to the Internet from any location, multimedia services are also accessible.
- 2.
- It offers interoperability across service providers as well as inexpensive call rates all around the world.
- 3.
- Customers are able to make use of wireless broadband, and it is able to support applications that are fairly data-intensive.
- 4.
- It is a lot faster than the previous networks.
- Disadvantages:
- 1.
- It is possible that it will not supply sufficient bandwidth due to the data-intensive requirements of mHealth applications.
- 2.
- It has a high power consumption rate overall.
- 3.
- It requires base stations to be densely deployed in order to achieve quicker rates, and as a result, medical applications that use this technology may be expensive to deploy.
- 4.
- Roaming, data/voice services, and integration of these features for health applications have not yet been fully implemented.
4G Systems
- Advantages:
- 1.
- In comparison to 3G systems, it offers superior spectral efficiency as well as increased speed, capacity, and bandwidth.
- 2.
- It is possible to attain a higher level of network security, which in turn makes it possible to have a high level of usability: at any time, anywhere, and with any type of technology. This provides support for multimedia services at a low transmission cost, which is very much needed in mHealth applications.
- 3.
- It is able to achieve lower cost per bit, in addition to providing a seamless network of multiple protocols and air interfaces, which ultimately results in a communication system that is substantially more cost-effective.
- 4.
- It increases the level of synchronization among different devices, which in turn provides worldwide access, service portability, and a variety of service quality options, all of which will enhance mHealth application capabilities.
- Disadvantages:
- 1.
- There are not currently many regions that have 4G connectivity, which may restrict its use for mobile health applications on a wider scale.
- 2.
- Protocols and standardization for networks used in medical applications have not yet been determined.
- 3.
- The rate at which it consumes power is still fairly high, which means that it will be disadvantageous to sensors that are used in medical applications and are limited by battery life.
5G Systems
- Advantages:
- 1.
- It possesses a very high speed (>1 Gbps in high mobility), much higher capacity than previous technologies, increased efficiency, and is optimized for longer battery lifetime.
- 2.
- It has a lower cost per bit, supports multimedia, voice, and Internet services, and enables the delivery of images at significantly higher resolutions.
- 3.
- It provides large bidirectional bandwidth for mobile users, the highest possible quality of service (QoS), and the ability to deliver uniform, continuous, and consistent connectivity across the entire world.
- 4.
- In addition to providing worldwide access and service portability as well as support for a variety of service types, it intends to provide a technology that brings together all similar 5G networks on a single platform.
- Disadvantages:
- 1.
- Due to the fact that it is a relatively new technology, the cost of its development infrastructure is expensive.
- 2.
- There are still some privacy and security concerns that have not been fully addressed, such as the prevention of eavesdropping, and these concerns need to be addressed for flawless eHealth service delivery.
- 3.
- It will be a costly endeavor because many of the older devices (1G, 2G, 3G, and 4G) will not be compatible with the 5G standard and will need to be replaced with brand-new models.
- 4.
- This technology is still in the process of being developed, and investigations into its practicality are now taking place.
6.5. Summary of Discussion
6.5.1. Our Take-Aways
- 1.
- The development of mobile sensors has seen significant progress in recent years, which has led to improvements in the accuracy with which medical parameters may be measured. The widespread adoption of more advanced smartphones, which come equipped with in-built sensors such as accelerometers and gyroscopes, is largely responsible for the recent advances made in sensor technologies.
- 2.
- On the basis of the progress made in computing devices, there are many new and improved mobile phones, PDAs, and portable media devices that can process information faster. These gadgets have increased the potential for not just measuring health data, but also processing and analyzing them and providing feedback to patients.
- 3.
- In terms of advancements in communication technologies, 5G technology stands out as the future technology for the delivery of eHealth services. Because of its ability to provide higher peak data transmission speeds of multiple gigabits per second (Gbps), extremely low latency, and increased reliability, 5G wireless technology will have a substantial impact on the enhancement of mHealth services and applications. Additionally, it will deliver huge network capacity, increased availability, and a more consistent user experience to a larger number of people.
6.5.2. Our Recommendations
- 1.
- While much has been published about the development of wireless biosensors for use in wireless body area networks and general eHealth systems, enhanced mobile computing devices based on new smart phone technologies, and communication technologies pertaining to 5G systems, there is still a great deal to be covered in the literature. For instance, further miniaturization of biosensors within the scope of nanotechnologies, and standardized frameworks for the risk assessment of the use of mHealth applications in eHealth systems are areas that may require more research and future synthesis of existing literature.
- 2.
- Despite the fact that 5G networks have the potential to improve the reach and functionality of eHealth systems, their coverage regions remain inadequate. Therefore, it is suggested that future research should concentrate on the potentials for seamless integration between 5G and satellite communications technologies in order to increase the performance of eHealth coverage.
- 3.
- Improving the degree of eHealth system awareness and utilization literacy among users is a source of concern. In this regard, there are less studies and investigations on novel literacy models for increasing mHealth acceptance among users, and it is advised that more research be conducted in this area.
7. eHealth: Security and Privacy Concerns
7.1. Goals of Securing eHealth Systems
- 1.
- Confidentiality: This entails the assurance that sensitive data will not be disclosed to unauthorized elements. Such a requirement must be maintained to safeguard a patient’s anonymity [164]. However, because eHealth systems are typically either based on an edge- or cloud-designed architecture, thus when data control is handed over to a cloud service, the information in question becomes accessible to an increased number of users, which in turn increases the likelihood that the data may be compromised [165]. This challenge is presently aggravated owing to the ever increasing number of parties, devices, and applications involved in eHealth systems, which results in an increase in the number of potential threats to the confidentiality of data circulating in the system. Thus, it is imperative for a patient to have confidence that the eHealth system would maintain the confidentiality of his or her information in order for the patient–doctor interaction to be trusted. If the patient believes that the information provided to a doctor is not safeguarded and that their privacy is compromised, trust breaks down, which can ultimately ruin the essence of eHealth systems in general.
- 2.
- Integrity: This refers to the prevention of illegal changes to any component of the data within an eHealth system. It is absolutely necessary that there is never a breach in the validity of the data that is recorded or sent within an eHealth system. This is crucial to ensuring that the medical records of patients are correct and consistent with the information that was intended. Because medical records of patients are required for physicians to make diagnoses and decisions regarding treatment, any unauthorized access to those data, change or loss of such records can be immensely destructive to the whole existence and sustaining of eHealth systems in general [166]. Consequently, the HIPAA Security Rule (Section 164.312(c) (1) Integrity) [167] stipulates that public resources are required to “implement policies and procedures to protect electronic personal healthcare information from improper alteration or destruction”. Thus, before accessing the data, applications that store and handle patient information in a healthcare context are required to incorporate integrity and verification features, just as is the case with non-medical applications. This can be accomplished through the use of checksums or hashes. In the event that the integrity check is unsuccessful, the healthcare application is required to report an error and exit without processing any of the data [165].
- 3.
- Availability: This means that the service or data rendered by eHealth systems should always be available when required. The availability of eHealth systems is indeed critical because a patient’s life may be jeopardized if medical services are denied [168]. Such accessibility of data encompasses the ability to continue operations despite the misbehavior of some authorities as well as following a breach in security. Furthermore, eHealth systems should be able to minimize service interruptions caused by events such as power failures, failed hardware, system upgrades, and denial-of-service assaults. In addition, such systems should be able to maintain the usability of medical records after HIPAA security and privacy regulations have been enforced.
7.2. Security Threats against eHealth Systems
- 1.
- Eavesdropping: As medical information is collected, transferred, and stored across different eHealth systems, attackers could attempt to obtain access to such information. An example of this would be an unauthorized listen-in on a radio conversation that is taking place between wireless sensors, followed by the capturing of data. Because medical information is both private and highly sensitive to alternations, this must be avoided.
- 2.
- Inaccurate patient information and erroneous system actions may occur from attackers being able to edit medical data while they are being gathered, sent, or stored. This can happen when attackers are able to alter the information when it is being acquired, sent, or stored. This may result in false alarms, such as the activation of alerts, and may lead, for example, to rescue operations that are not essential. Even worse, false negatives, in which worrisome data are changed to produce normal results, can conceal abnormal or emergency situations.
- 3.
- Similar to the preceding point, attackers are able to forge alarms on medical data by simply creating phony messages rather than changing legitimate ones. Forgery of alarms on medical data is a common form of cybercrime. This can once again result in inaccurate data recordings or a bogus system.
- 4.
- Denial of Service: When a system is jammed or overloaded, it becomes inoperable. In the worst-case scenario, sick or injured people will be unable to receive the necessary care, which can lead to fatalities. In [169], the impacts of denial of service on the routing of data in mobile eHealth networks were examined. Different solutions to the problem of denial of service are often accompanied by additional constraints related to the use of cryptography, such as the difficulty in authenticating routing packets. Therefore, denial of service remains a problem that must be resolved in order to improve the performance of eHealth systems.
- 5.
- User location tracking: Because eHealth system users leave continuous records of messages sent out, and because the system also might expressly support person localization, this data might be gathered, consolidated, and analyzed to obtain very detailed location profiles. This is certainly an invasion of privacy that must be avoided. Nonetheless, as noted by [170], token-based employee mobility monitoring remains a widespread technique of staff management today. Employees who do not use or possess the device may be refused access to certain places. Such transaction-logging techniques also permit mobility tracking, retrospective evaluation of movements, and maybe even real time prediction capabilities relating to the person’s likely destination. The surveillance of people’s locations is generating concern among privacy activists [171]. The terms “Uberveillance” and “dataveillance” (a combination of data and surveillance) have both become buzz terms in the fight against overwatching (surveillance) systems [172]. Such movements may create a challenge for eHealth systems as it will be argued that sensors can be hijacked and used to invade the privacy of individuals for malicious purposes.
- 6.
- User activity tracking: This form of threat is unique to eHealth systems. It may be feasible to examine people’s activities based on the data collected. When an individual is constantly monitored, it may be able to determine their activities merely by examining their heartrate and oxygen concentration data [173]. Such medical monitoring is a feature of ReMoteCare, as explained in [174]. Insurance providers could use this knowledge to deny benefits to persons who live an unhealthy lifestyle. This, once again, has an impact on a user’s privacy. Furthermore, smart phones with GPS modules can enable network operators to conduct a location estimate within minutes after receiving a police inquiry [175]. Furthermore, location intelligence can expose a considerable measure about one’s tastes, acquaintances, relationships, and behaviors [175].
- 7.
- Physical manipulation: Because it may not be particularly difficult to gain access to the wireless sensors, particular those attached to equipment, attackers may try to steal equipment, tamper with the sensor devices in order to change the sensor values, or just throw them away, or damage them.
7.3. Security Solutions for eHealth Systems
7.3.1. Safe Data Collection
7.3.2. Data Transmission/Retransmission Security
7.3.3. Safe Data Storage
7.4. Summary of Discussion
7.4.1. Our Take-Aways
- 1.
- The goal of securing eHealth systems is broadly covered in terms of guaranteeing confidentiality, integrity, and availability. Other goals fall under these areas such as ownership and privacy of healthcare information, nonrepudiation, and access control anonymity, falling under confidentiality, whereas authenticity, auditing, unlinkability, and secured transmission falling under integrity.
- 2.
- Due to the sensitive nature of the eHealth industry, it is crucial that all of the threats such as denial of service, eavesdropping, and data falsification, are adequately addressed, with some security solutions mentioned in Section 7.2.
- 3.
- In a nutshell, methods relating to the use of cryptographic encryption techniques, solutions based on blockchain technology, heuristic algorithms, and the physical protection of end nodes have been well documented in the literature.
7.4.2. Our Recommendations
- 1.
- It is evident that there is no one solution that can address all of the concerns regarding the security of eHealth systems. As a result, data should be protected either at the site of generation, i.e., at the sensors themselves, or during transmission or retransmission, and ultimately, during storage or access of the data. This should be the focus of both current and future solutions.
- 2.
- There are further understudied areas, such as enhanced consensus methodologies for strengthening blockchain solutions, the creation of privacy-enforced eHealth systems, and optimizing key management complications to decrease communication overheads. As a result of the lack of study on these and many other topics, this section cannot be considered exhaustive. Nonetheless, in its present state, this section has provided some minimum context and synthesized information to developers who are either involved in developing or implementing secured eHealth systems towards improving the performance of such systems.
8. eHealth: Research Challenges and Future Directions
8.1. Research Challenges in Architectures
- Standardization: eHealth is currently undergoing a period of rapid transition on multiple fronts, including the economic, social, and technical levels. Standardization is an innately delicate subject, and the fact that there are many initiatives taking place in a variety of countries only adds to the complexity. There are already established norms and frameworks in the field of security, but little to none within the unifying the architectural domain. Consequently, there is need for research in this regard to avoid compatibility issues. In terms of research, it is still unclear what the proper procedure needs to be in order to guarantee compatibility of technologies, consistency of manufacturing, and objectivity of measurement. This difficulty may be connected to the fact that different tasks are required at different times of the lifespan of standards, which further affects the various players. In order to accomplish this goal, some sort of systematic and conceptual framework will be required; hence, more research activities will be necessary. For the purpose of carrying out a survey that is more accurate regarding the present status and the desired state of the field, improved data collection procedures will also be necessary. This will make it possible to enhance standardization processes. In addition, the methods of standardization that will be necessary to achieve uniformity in the endorsement and description of healthcare systems, the structure of information, types of data, semantic consistency, and the handling of electronic patient records are not yet known. This is another area in which there is a lack of knowledge. These significant research obstacles need to be overcome in order to make progress toward the development of unified architectures for eHealth systems.
- Weak interdisciplinary collaborations: There is a lack of synergy between the engineers and IT specialists who are in charge of creating eHealth technologies and the health experts who are responsible for producing the theoretical contents. This frequently results in poorly constructed designs that do not fulfill all of the requirements posed by the people utilizing the health services. For instance, those who specialize in technology may create websites that are engaging and entertaining but are not founded on any health behavior theory, whereas those who specialize in health education may create programs that are grounded in theory but do not make full use of the potential offered by technology to bring the subject matter to life [201]. In terms of research, it remains to be determined which strategy for message tailoring will be most effective for enhancing inter-disciplinary collaborations. In this instance, tailored (i.e., customized) messaging generates individualized communication with a higher likelihood of conveying convincing health messages to target groups. Other research obstacles include establishing the optimal method for delivering eHealth interventions that foster stronger partnerships and result in enhanced eHealth content. In addition, the construction of objective metrics and machine learning algorithms for evaluating and finding the most relevant specialists better suited to multidisciplinary collaborations remains an untapped field of research that deserves further study.
- Need for higher communication speed: High-speed transmission of data from some source (such as a patient or record server) to a destination (a medical practicioner or administrator) will be essential to the success of any and all prospective eHealth designs. Consequently, the adoption of eHealth systems and the provision of services will require enhanced data rates that go beyond the capabilities of the currently available 5G technology. Specifically, it is well known that existing 5G technologies cannot completely support eHealth systems, particularly those that require ultra-reliable low latency communications (URLLC). According to [161], even though retransmission and grant-free transmission (GFT) can improve communication reliability, it will also result in increased transmission delay. Therefore, further study will be necessary in the field of data speed optimization in order to overcome these concerns. Other areas of research required to increase transmission speed include the improvement of medical data fusion and mining algorithms, as well as compression techniques.
- Latency between edge–cloud interactions: It is common knowledge that using cloud services will result in delays, particularly delays caused by the communication channel or the processing power of the cloud server. Consequently, such latencies can be extremely detrimental to the provision of eHealth services, particularly in circumstances involving an emergency. Such limitations can lead to non-availability of cloud services, which can be further detrimental to eHealth service delivery. In terms of research, it is necessary to develop self-organizing networks that can automatically and rapidly adjust to congested links in order to improve transmission performance. To control service outages that may result from edge–cloud interactions, improved software and hardware installation, updates, and reconfiguration methods must be established. These are areas of unknown knowledge, which will require further studies. In addition, this will also demand specialized eHealth platforms to enhance service delivery, necessitating more study into the development of improved data capture algorithms and aggregation techniques to identify novel medical patterns for heterogeneous data sourcing and transmission.
8.2. Future Directions in eHealth Architectures
- When designing and developing eHealth systems and architectures, it is essential to utilize multidisciplinary teams and formative research. Consequently, academic boards, as well as commercial and governmental organizations that award grants, need to devise and implement rules that demand a diverse group of researchers and developers with expertise across the several fields that are relevant to the health business.
- New architectures should be developed based on the use of better technologies. An example of this can be seen in [158] where 5G technology was combined with optical camera communication (OCC) to develop a reliable and low-latency architecture for eHealth solutions.
- Architectures that are highly distributed, component-based, and self-organizing should be the target of future research and development activities. In this context, a variety of different ideas, such as edge intelligence, machine learning techniques, and quantum computing technologies, can be utilized to great effect.
8.3. Research Challenges in mHealth
- Low levels of health literacy: It is of the utmost importance to determine how mHealth applications are created, developed, and supplied in order to guarantee that such applications are comprehensible to all people and can be acted on by them. This is significant since the effectiveness of the intervention of mHealth applications can only be achieved for users with a high level of health literacy, but users with a low level of health literacy are frequently disregarded, which is something that continues to be a challenge. As a result, mobile health applications need to be designed following methodologies that are considered industry standard in order to provide information in a manner that is accessible to the various audiences they are aimed at. Research-wise, the optimal framework for defining eHealth literacy demands and barriers toward producing new solutions remains unknown, thus warranting future studies. Furthermore, improved methodologies for literacy type profiling will be necessary to generate a more comprehensive list of resources to benefit health practitioners in promoting literacy improvement. Lastly, further research will be required in developing new eHealth literacy models that will enhance existing models such as the Lily model toward providing additional dimensions that will improve eHealth literacy [202].
- The price of smartphones and miniaturization of sensors: Even though the price of smartphones may be coming down as a result of advancements in technology, the reality is that not everyone can afford such devices. As a result, this can be a barrier for those unfortunate people who do not have the financial means to purchase a smartphone. Therefore, the ability to supply specialized low cost devices for the delivery of eHealth services should be considered a subject of urgent study by both developers and policy managers. In this case, a great deal of research must be undertaken in order to enhance access to eHealth services through the miniaturization of biosensors. Efforts to improve the sensitivity of point-of-care (PoC) diagnostics, for instance, have become crucial for the early diagnosis of illnesses. In this instance, it is vital to investigate how new materials might be created to enable the re-use of microfluidic systems in order to build cheaper and more ecologically friendly technologies [203]. The synergistic integration of optics and microfluids to allow new capabilities without sacrificing integrability or compactness is another area of study that has the potential to lower costs and warrants further investigation. This kind of research into microfluids and optics can lead to better microfluidic drug delivery and screening methods that are less dangerous and work better.
- Lack of frameworks for conducting risk assessments of mHealth applications: The fast growth of mHealth applications makes it necessary for government health agencies to pay attention to legislation regarding the risk assessment of mHealth apps. Unfortunately, these current and future frameworks have not yet been defined, especially with regards to the use of mobile auditing systems that permit real time monitoring of mHealth apps. This raises research problems in identifying how mHealth apps consume resources and the capacity to warn users if abnormal resource usage patterns are discovered. In this context, more research is required to create algorithms that allow the recording of fetal cardiac events onto a mobile phone for subsequent processing and evaluation of fetal risk [204]. How to design methods and procedures for identifying harmful mHealth apps, where the accuracy of mHealth apps can be simply evaluated and determined, continues to be investigated. In addition, it is crucial to conduct research on how to combine multiple usage situations, contextual variables, and program complexity in order to estimate the total probability and degree of harm caused by mHealth apps. By finding answers in these areas of research, it will be possible to make and use eHealth applications that are safer.
- Poor or lack of communication network coverage: Once more, all mHealth applications are dependent on communication technologies, particularly wireless solutions. On the other hand, there are regions that are not covered or places that are difficult to access, such as rural areas or the outskirts of towns and cities. When this transpires, mHealth and eHealth services, in general, will be rendered completely inoperable. An area of research interest is the need for ways to offset such occurrences or inadequately covered regions. In this context, further studies on long-distance communication technologies will be necessary. In this case, this may involve investigations and studies into the fields of satellite and low-power long-range communications for the delivery of eHealth services. Particularly intriguing will be research into the improvement of miniature satellites (also known as CubeSats) for eHealth applications. This will need tackling obstacles such as how to create ways for effectively integrating CubeSats with other communication technologies, such as geostationary and medium Earth orbit satellites and 5G technologies, as well as how to optimize the amount of onboard transceivers in CubeSats to enhance data scheduling. These and other intriguing research gaps, such as the development of software-defined networking solutions for broadband satellite communications, should also be investigated in the future to improve the delivery of eHealth services.
8.4. Future Directions in mHealth
- It is recommended that more medical research be carried out in order to create sensor-based technologies that may be utilized in the process of monitoring patients, carrying out patient diagnoses, and administering treatments. These have the potential to make use of cutting-edge sensor technologies in the area of nanoscience and nanotechnology.
- The development of home monitoring systems that include affordable terminals for caregivers and patients, in addition to a central monitoring system, is an area for future consideration. Such centralized hubs may take the form of web-based systems that hold a central database, or they may even be mist or edge computing solutions. These concepts may assist to reduce the cost of purchasing medical devices as well as increase the quality of service that is provided by eHealth systems.
- The requirement for specialized working groups has become necessary in order to hasten the pace at which breakthroughs in mHealth are being made. In fields such as wireless body area networks (WBANs), work groups such as the IEEE 802.15.6 have been established for low-power wearable devices or body implants. These groups are intended for use in the human body. Additionally, such organizations are required in the field of mHealth in order to better specialize their efforts.
- Long-range communication: The potentials of long-range communications may be utilized in the provision of eHealth services to hard-to-reach locations such as rural areas or the outskirts of towns. These kinds of technologies include LoRa, SigFox, NB-IoT, and a variety of other types of long-range communication systems. However, before these technologies can be put to use, a number of research issues, including efficient management of energy and high data rates, need to be resolved. This may be a topic for more investigation in the future.
8.5. Research Challenges in eHealth Security
8.5.1. Challenges with Blockchain Technology
- Lack of awareness: In the first place, there is a lack of awareness of how the technology may need to function in the eHealth sector, as well as a lack of awareness of the technology itself, particularly in industries other than banking. This, in turn, may make it more difficult to invest in and investigate the viability of this concept across eHealth systems.
- Scalability: The capacity to handle a large number of users simultaneously is still a concern for the blockchain business. The processing of a single transaction using blockchain technology requires the use of several complicated algorithms. Because of the potentially enormous number of users, which often spans both national and international boundaries, this will be a significant obstacle for its implementation inside eHealth systems. In particular, it will be required to investigate how to optimize the huge block sizes, which are frequently the cause of the slow propagation speed in blockchain technologies. This will entail research activities aimed at resolving the blockchain problem, i.e., blockchain storage optimization. On the other hand, it may necessitate a complete redesign of the blockchain, which may necessitate new knowledge on how to decouple traditional blocks into smaller, efficient blocks with improved building techniques.
- Confidentiality: Despite the fact that blockchain is suitable as a solution to security concerns in eHealth systems, blockchain remains an open ledger that is viewable by everyone. This makes it possible for anybody to verify the accuracy of the blockchain. This has the potential to become a liability, especially in delicate contexts like those seen in eHealth system setups. In this situation, more research may be necessary to address privacy leakage concerns, which may include the development of information regarding how to use mixing services. The use of mixing services offers anonymity by adopting many input addresses to multiple output addresses, making it challenging to determine the origins of information. In addition, further study is necessary to create zero-knowledge proof. In this scenario, blockchain miners would not be needed to validate a transaction using a digital signature, but would instead validate currencies against a list of valid coins [205]. It is largely uncertain how such an approach would function, thus necessitating additional research and investigation.
- Cost: Blockchain is still in its infancy as a technology, and despite the fact that it could be useful in eHealth systems, there is still a significant amount of work to be done in the field of study about this topic. Consequently, it will be challenging to integrate it into existing systems, necessitating the development of whole new systems, which will result in substantial additional expenses. Because of this, its adoption by participants in the private or even public health industries may be hampered.
8.5.2. Challenges with Cloud Services
- How can fool-proof security measures be enabled in cloud services?
- How can enforced privacy be achieved in eHealth systems?
- Are there better access control mechanisms for the secured transfer of EHRs?
- How can health data can be effectively shared among multiple healthcare providers?
- How can insider attacks be minimized, particularly involving administrative staff with accessibility options?
- How can key management complexity be handled while sharing healthcare data between disparate healthcare providers?
8.5.3. Other General Challenges with eHealth Security
- The need for dependable user and entity authentication methods and systems, which must be capable of achieving the goals of unique identity, multi-factor authentication, and role-based authorization.
- A lack of robust access control measures that are particularly stringent, such as those that offer emergency access protocols, automated logouts (i.e., system time outs), device control lists, physical access restrictions, and enforced policies for system and data access control.
- Inadequate audit control systems with robust capabilities for logging and monitoring activities.
- There is need for enhanced data and record transmission security mechanisms over wireless communication channels.
- A lack of an integrated solutions that include the deployment of administrative, technological, and physical safeguard mechanisms, as well as security training and awareness of such tools as being part of compliance preparation for the uptake of eHealth systems.
8.6. Future Directions in eHealth Security
- There may be a need to accelerate policies and blueprints for research in blockchain for digital health and patient uptake. This could include initiating government-led digital education and adoption campaigns about the technology. This may improve awareness about the technology and enable smoother application integration to prevent information overload and confusion among health care workers (HCWs) and patients concerning the technology.
- Certificates, like any other public key infrastructure, must be managed to assure the authenticity of key holders (smartcards, connections, servers, and so on). This involves certificate issuance and distribution, as well as updating revocation lists.
- Other components, in addition to the cryptographic infrastructure, must be handled and maintained. This comprises the hardware and software components used in EHR servers, billing servers, and health care provider computer devices. Smartcard readers and connectors to secured networks, for example, should be properly approved and tested. A secure distribution system is required for the installation and updating of software components. On the one hand, valid software upgrades must be able to cause changes in program configuration. Unauthorized and malicious alterations, on the other hand, must be detectable in order to stop future usage or to exclude infected components from the eHealth infrastructure.
- A permitted patient-centric blockchain for EHRs that overcomes most of the present obstacles in the cloud might be a future solution and path for dealing with eHealth privacy problems.
- A variety of systems have used the role-based access control (RBAC) approach to protect eHealth security and privacy. We believe that future study should look at the use of the attribute-based access control (ABAC) architecture, which may offer superior scalability and flexibility for authentications and authorizations. This remains an opinion and could probably be an area for future research.
- Attribute-based encryption (ABE) is also acknowledged to be effective at protecting privacy in eHealth; nevertheless, excessive calculations during decryption of data are impending, thereby impacting its efficiency. We also believe that finding a solution to these bi-linear procedures would improve ABE’s efficiency. The hunt for a solution is seen as a promising eHealth topic of interest.
- General enforcement of privacy standards (termed enforced privacy) should be implemented. The majority of the proposed solutions concentrated their efforts primarily on protecting the patients’ confidentiality and safety. However, all parties participating in eHealth systems should have their privacy enforced. Thus, devising the right mechanisms in this regard will be a useful future direction in eHealth studies.
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mercier, G.; Arquizan, C.; Roubille, F. Understanding the effects of COVID-19 on health care and systems. Lancet Public Health 2020, 5, e524. [Google Scholar] [CrossRef]
- Bai, G.; Guo, Y. A General Architecture for Developing a Sustainable elderly Care E-health System. Int. J. Inf. Technol. Bus. Manag. 2014, 27, 95–101. [Google Scholar]
- Lentferink, A.J.; Oldenhuis, H.K.; de Groot, M.; Polstra, L.; Velthuijsen, H.; van Gemert-Pijnen, J.E. Key components in eHealth interventions combining self-tracking and persuasive eCoaching to promote a healthier lifestyle: A scoping review. J. Med. Internet Res. 2017, 19, e7288. [Google Scholar] [CrossRef]
- Milosevic, Z. Addressing interoperability in e-health: An Australian approach. In Proceedings of the 2006 10th IEEE International Enterprise Distributed Object Computing Conference Workshops, EDOCW2006, Hong Kong, China, 16–20 October 2006; p. 39. [Google Scholar] [CrossRef][Green Version]
- Hoque, M.R.; Mazmum, M.F.A.; Bao, Y. e-Health in Bangladesh: Current Status, Challenges, and Future Direction. Int. Technol. Manag. Rev. 2014, 4, 87. [Google Scholar] [CrossRef]
- Fan, Z.; Haines, R.; Kulkarni, P. M2M communications for E-health and smart grid: An industry and standard perspective. IEEE Wirel. Commun. 2014, 21, 62–69. [Google Scholar] [CrossRef]
- Thuemmler, C. Determinants of next generation e-Health network and architecture specifications. In Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016; pp. 1–6. [Google Scholar]
- Farhangi, H. Smart grid system integration. In Smart Microgrids; Number February; CRC Press: Boca Raton, FL, USA, 22 August 2016; pp. 31–63. [Google Scholar] [CrossRef]
- Chowdhary, S.K.; Yadav, A.; Garg, N. Cloud computing: Future prospect for e-Health. In Proceedings of the 2011 3rd International Conference on Electronics Computer Technology, Kanyakumari, India, 8–10 April 2011; pp. 297–299. [Google Scholar]
- AbuKhousa, E.; Mohamed, N.; Al-Jaroodi, J. e-Health Cloud: Opportunities and Challenges. Future Internet 2012, 4, 621–645. [Google Scholar] [CrossRef]
- Scarpato, N.; Pieroni, A.; Nunzio, L.D.; Fallucchi, F. E-health-IoT Universe: A Review. Int. J. Adv. Sci. Eng. Inf. Technol. 2017, 7, 2328. [Google Scholar] [CrossRef]
- Gonzalez, E.; Peña, R.; Avila, A.; Vargas-Rosales, C.; Munoz-Rodriguez, D. A systematic review on recent advances in mhealth systems: Deployment architecture for emergency response. J. Healthc. Eng. 2017, 2017, 9186270. [Google Scholar] [CrossRef] [PubMed]
- Bhopale, A.P.; Shevgoor, S.K. Temporal topic modeling of scholarly. In Lecture Notes in Computer Science: Proceedings of the International Conference on Big Data Analytics; Springer: Cham, Switzerland, 2017; Volume 2, pp. 144–163. [Google Scholar] [CrossRef]
- Chenthara, S.; Ahmed, K.; Wang, H.U.A. Security and Privacy-Preserving Challenges of e-Health Solutions in Cloud Computing. IEEE Access 2019, 7, 74361–74382. [Google Scholar] [CrossRef]
- Okoh, E.; Awad, A.I. Biometrics applications in e-Health security: A preliminary survey. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Yin, X., Ho, K., Zeng, D., Aickelin, U., Zhou, R., Wang, H., Eds.; Springer International Publishing: Cham, Switzerland, 2015; Volume 9085, pp. 92–103. [Google Scholar] [CrossRef]
- Kotsiuba, I.; Velvkzhanin, A.; Yanovich, Y.; Bandurova, I.S.; Dyachenko, Y.; Zhygulin, V. Decentralized e-Health architecture for boosting healthcare analytics. In Proceedings of the 2018 Second World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 30–31 October 2018; pp. 44–50. [Google Scholar] [CrossRef]
- Butpheng, C.; Yeh, K.H. SS symmetry Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review. Symmetry 2020, 12, 1191. [Google Scholar] [CrossRef]
- Selem, E.; Fatehy, M. E-Health applications over 5G networks: Challenges and state of the art. In Proceedings of the 2019 6th International Conference on Advanced Control Circuits and Systems (ACCS) & 2019 5th International Conference on New Paradigms in Electronics & Information Technology (PEIT), Hurghada, Egypt, 17–20 November 2019; pp. 111–118. [Google Scholar]
- Zubair, M.; Unal, D.; Al-Ali, A.; Shikfa, A. Exploiting bluetooth vulnerabilities in e-Health IoT devices. In Proceedings of the 3rd International Conference on Future Networks and Distributed Systems, Paris, France, 1–2 July 2019; ACM International Conference Proceeding Series. ACM: New York, NY, USA, 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Zvikhachevskaya, A.; Markarian, G.; Mihaylova, L. Quality of Service consideration for the wireless telemedicine and e-health services. In Proceedings of the 2009 IEEE Wireless Communications and Networking Conference WCNC, Budapest, Hungary, 5–8 April 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Algaet, M.A.; Noh, Z.A.B.M.; Shibghatullah, A.S.; Milad, A.A.; Mustapha, A. Provisioning Quality of Service of Wireless Telemedicine for e-Health Services: A Review. Wirel. Pers. Commun. 2014, 78, 375–406. [Google Scholar] [CrossRef]
- Maeen, S.; Zykov, S. Towards Social Network—Integrated e-Health: Identify User Attitudes. Procedia Comput. Sci. 2015, 55, 1174–1182. [Google Scholar] [CrossRef][Green Version]
- Tachakra, S.; Wang, X.H.; Istepanian, R.S.; Song, Y.H. Mobile e-Health: The Unwired Evolution of Telemedicine. Telemed. J. e-Health 2003, 9, 247–257. [Google Scholar] [CrossRef]
- Jia, X.; Chen, H.; Qi, F. Technical models and key technologies of e-Health monitoring. In Proceedings of the 2012 IEEE 14th International Conference on e-Health Networking, Applications and Services (Healthcom), Beijing, China, 10–13 October 2012; pp. 23–26. [Google Scholar] [CrossRef]
- Abbas, A.; Khan, S.U.; Member, S. A Review on the State-of-the-Art Privacy-Preserving Approaches in the e-Health Clouds. IEEE J. Biomed. Health Inform. 2014, 18, 1431–1441. [Google Scholar] [CrossRef] [PubMed]
- Bhalla, S.; Sachdeva, S.; Batra, S. Semantic interoperability in electronic health record databases: Standards, architecture and e-Health systems. In Big Data Analytics; Reddy, P.K., Sureka, A., Chakravarthy, S., Bhalla, S., Eds.; Springer International Publishing: Cham, Switzerland, 2017; Volume 10721, pp. 235–242. [Google Scholar] [CrossRef]
- Hameed, R.T.; Mohamad, O.A.; Hamid, O.T.; Tapus, N. Patient monitoring system based on e-health sensors and web services. In Proceedings of the 8th International Conference on Electronics, Computers and Artificial Intelligence, ECAI 2016, Ploiesti, Romania, 30 June–2 July 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Riedl, B.; Jorns, O. Secure access to emergency data in an e-Health architecture. In Proceedings of the Ninth International Conference on Information Integration and Web-Based Applications Services (iiWAS), Jakarta, Indonesia, 3–5 December 2007; pp. 297–306. [Google Scholar]
- Michalas, A.; Paladi, N.; Gehrmann, C. Security aspects of e-Health systems migration to the cloud. In Proceedings of the 2014 IEEE 16th International Conference on e-Health Networking, Applications and Services, Healthcom 2014, Natal, Brazil, 15–18 October 2014; pp. 212–218. [Google Scholar] [CrossRef]
- Fengou, M.A.; Mantas, G.; Lymberopoulos, D.; Komninos, N.; Fengos, S.; Lazarou, N. A New Framework Architecture for Next Generation e-Health Services. IEEE J. Biomed. Health Inform. 2013, 17, 9–18. [Google Scholar] [CrossRef]
- Bomba, D. A comparative study of the diffusion of computerized health records among general practitioners in Australia and Sweden. In Human and Organizational Dynamics in E-Health; CRC Press: London, UK, 14 February 2005; p. 187. [Google Scholar]
- Imhoff, M. Health informatics. In Evaluating Critical Care; Springer: Berlin/Heidelberg, Germany, 2002; Volume 35, pp. 255–269. [Google Scholar]
- Bath, P.A. Health informatics: Current issues and challenges. J. Inf. Sci. 2008, 34, 501–518. [Google Scholar] [CrossRef]
- Holzinger, A. Machine learning for health informatics. In Machine Learning for Health Informatics; Springer: Berlin/Heidelberg, Germany, 2016; pp. 1–24. [Google Scholar]
- Christopoulou, S.C. Impacts on Context Aware Systems in Evidence-Based Health Informatics: A Review. Healthcare 2022, 10, 685. [Google Scholar] [CrossRef] [PubMed]
- Jabali, A.K.; Waris, A.; Khan, D.I.; Ahmed, S.; Hourani, R.J. Electronic health records: Three decades of bibliometric research productivity analysis and some insights. Inform. Med. Unlocked 2022, 29, 100872. [Google Scholar] [CrossRef]
- Keshta, I.; Odeh, A. Security and privacy of electronic health records: Concerns and challenges. Egypt. Inform. J. 2021, 22, 177–183. [Google Scholar] [CrossRef]
- Ryu, S. History of telemedicine: Evolution, context, and transformation. Healthc. Inform. Res. 2010, 16, 65–66. [Google Scholar] [CrossRef]
- Lovejoy, J.F.; Read, M. History and evolution of telemedicine. In Telemedicine in Orthopedic Surgery and Sports Medicine; Springer: Berlin/Heidelberg, Germany, 2021; pp. 3–10. [Google Scholar]
- Barbosa, W.; Zhou, K.; Waddell, E.; Myers, T.; Dorsey, E.R. Improving access to care: Telemedicine across medical domains. Annu. Rev. Public Health 2021, 42, 463–481. [Google Scholar] [CrossRef] [PubMed]
- Sageena, G.; Sharma, M.; Kapur, A. Evolution of smart healthcare: Telemedicine during COVID-19 pandemic. J. Inst. Eng. (India) Ser. B 2021, 102, 1319–1324. [Google Scholar] [CrossRef]
- Mogharbel, A.; Dowding, D.; Ainsworth, J. Physicians’ Use of the Computerized Physician Order Entry System for Medication Prescribing: Systematic Review. JMIR Med. Inform. 2021, 9, e22923. [Google Scholar] [CrossRef] [PubMed]
- Srinivasamurthy, S.K.; Ashokkumar, R.; Kodidela, S.; Howard, S.C.; Samer, C.F.; Chakradhara Rao, U.S. Impact of computerised physician order entry (CPOE) on the incidence of chemotherapy-related medication errors: A systematic review. Eur. J. Clin. Pharmacol. 2021, 77, 1123–1131. [Google Scholar] [CrossRef] [PubMed]
- Delpierre, C.; Cuzin, L.; Fillaux, J.; Alvarez, M.; Massip, P.; Lang, T. A systematic review of computer-based patient record systems and quality of care: More randomized clinical trials or a broader approach? Int. J. Qual. Health Care 2004, 16, 407–416. Available online: https://academic.oup.com/intqhc/article-pdf/16/5/407/5158720/mzh064.pdf (accessed on 25 September 2022). [CrossRef] [PubMed]
- Keenan, R.; Borycki, E.M.; Kushniruk, A.W. Computerized provider order entry and patient safety: A scoping review. Knowl. Manag. E-Learn. Int. J. 2021, 13, 452–476. [Google Scholar]
- Prgomet, M.; Li, L.; Niazkhani, Z.; Georgiou, A.; Westbrook, J.I. Impact of commercial computerized provider order entry (CPOE) and clinical decision support systems (CDSSs) on medication errors, length of stay, and mortality in intensive care units: A systematic review and meta-analysis. J. Am. Med. Inform. Assoc. 2017, 24, 413–422. [Google Scholar] [CrossRef]
- Campbell, E.M.; Guappone, K.P.; Sittig, D.F.; Dykstra, R.H.; Ash, J.S. Computerized provider order entry adoption: Implications for clinical workflow. J. Gen. Intern. Med. 2009, 24, 21–26. [Google Scholar] [CrossRef]
- Berger, R.G.; Kichak, J. Computerized physician order entry: Helpful or harmful? J. Am. Med. Inform. Assoc. 2004, 11, 100–103. [Google Scholar] [CrossRef]
- Kuperman, G.J.; Gibson, R.F. Computer physician order entry: Benefits, costs, and issues. Ann. Intern. Med. 2003, 139, 31–39. [Google Scholar] [CrossRef]
- Jakubowski, S.; Romaszewski, A.; Wypyszewska, J.; Gajda, K.; Kielar, M. E-prescription: Selected legal and functional aspects. Zesz. Naukowe Ochr. Zdrowia Zdrowie Public. Zarz. 2018, 16, 137–148. [Google Scholar] [CrossRef]
- Savoska, S.; Jolevski, I. Architectural model of e-health PHR to support the integrated cross-border services. In Proceedings of the ISGt Conference 2018, Washington DC, USA, 19–22 February 2018; pp. 42–49. [Google Scholar]
- Lu, S.; Ranjan, R.; Strazdins, P. Reporting an experience on design and implementation of e-Health systems on Azure cloud: Deploying of e-health systems on azure cloud. Concurr. Comput. Pract. Exp. 2015, 27, 2602–2615. [Google Scholar] [CrossRef]
- Roosan, D.; Tatla, V.; Li, Y.; Kugler, A.; Chok, J.; Roosan, M.R. Framework to enable pharmacist access to healthcare data using blockchain technology and artificial intelligence. J. Am. Pharm. Assoc. 2022, 62, 1124–1132. [Google Scholar] [CrossRef] [PubMed]
- Dias, J.P.; Sereno Ferreira, H.; Martins, A. A Blockchain-Based Scheme for Access Control in e-Health Scenarios. Adv. Intell. Syst. Comput. 2020, 942, 238–247. [Google Scholar] [CrossRef]
- Weber, A.S.; Turjoman, R.; Shaheen, Y.; Al Sayyed, F.; Hwang, M.J.; Malick, F. Systematic thematic review of e-health research in the Gulf Cooperation Council (Arabian Gulf): Bahrain, Kuwait, Oman, Qatar, Saudi Arabia and United Arab Emirates. J. Telemed. Telecare 2017, 23, 452–459. [Google Scholar] [CrossRef] [PubMed]
- Sai, A.R.; Buckley, J.; Fitzgerald, B.; Le Gear, A. Taxonomy of centralization in public blockchain systems: A systematic literature review. Inf. Process. Manag. 2021, 58, 102584. [Google Scholar] [CrossRef]
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.; Alshamari, M.; Cao, Y. A survey on blockchain technology: Evolution, architecture and security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Corchado, J. Distributed e-health wide-world accounting ledger via blockchain. J. Intell. Fuzzy Syst. 2019, 36, 2381–2386. [Google Scholar] [CrossRef]
- Alonso, S.G.; Arambarri, J.; López-Coronado, M.; de la Torre Díez, I. Proposing new blockchain challenges in ehealth. J. Med. Syst. 2019, 43, 64. [Google Scholar] [CrossRef]
- Sun, Y.; Zhang, R.; Wang, X.; Gao, K.; Liu, L. A decentralizing attribute-based signature for healthcare blockchain. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018; pp. 1–9. [Google Scholar]
- Zhang, A.; Lin, X. Towards secure and privacy-preserving data sharing in e-health systems via consortium blockchain. J. Med. Syst. 2018, 42, 140. [Google Scholar] [CrossRef]
- Tagde, P.; Tagde, S.; Bhattacharya, T.; Tagde, P.; Chopra, H.; Akter, R.; Kaushik, D.; Rahman, M. Blockchain and artificial intelligence technology in e-Health. Environ. Sci. Pollut. Res. 2021, 28, 52810–52831. [Google Scholar] [CrossRef] [PubMed]
- Hussien, H.M.; Yasin, S.M.; Udzir, N.I.; Ninggal, M.I.H.; Salman, S. Blockchain technology in the healthcare industry: Trends and opportunities. J. Ind. Inf. Integr. 2021, 22, 100217. [Google Scholar] [CrossRef]
- Zubaydi, H.D.; Chong, Y.W.; Ko, K.; Hanshi, S.M.; Karuppayah, S. A review on the role of blockchain technology in the healthcare domain. Electronics 2019, 8, 679. [Google Scholar] [CrossRef]
- Alla, S.; Soltanisehat, L.; Tatar, U.; Keskin, O. Blockchain technology in electronic healthcare systems. In Proceedings of the IISE Annual Conference and Expo 2018, Orlando, FL, USA, 19–22 May 2018; pp. 901–906. [Google Scholar]
- Alihamidi, I.; Madi, A.A.; Addaim, A. Proposed architecture of e-health IoT. In Proceedings of the 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 29 October–1 November 2019; pp. 1–7. [Google Scholar]
- Olakanmi, O.; Odeyemi, K. FEACS: A fog enhanced expressible access control scheme with secure services delegation among carers in e-health systems. Internet Things 2020, 12, 100278. [Google Scholar] [CrossRef]
- Goncalves, F.; Macedo, J.; Nicolau, M.J.; Santos, A. Security architecture for mobile e-health applications in medication control. In Proceedings of the 2013 21st International Conference on Software, Telecommunications and Computer Networks, SoftCOM 2013, Split-Primosten, Croatia, 18–20 September 2013; pp. 1–8. [Google Scholar] [CrossRef]
- Jégaden, D. Concerning the relationship between noise on board ship and the onset of hypertension in seafarers. Arch. Prev. Med. 2021, 6, 001–002. [Google Scholar]
- Putrada, A.G.; Abdurohman, M. Anomaly detection on an IoT-based vaccine storage refrigerator temperature monitoring system. In Proceedings of the 2021 International Conference on Intelligent Cybernetics Technology & Applications (ICICyTA), Virtual Conference, Jawa Barat, Indonesia, 1–2 December 2021; pp. 75–80. [Google Scholar]
- Najim, A.H.; Elkhediri, S.; Alrashidi, M.; Nasri, N. The impact of using IoT for elderly and disabled peoples healthcare: An overview. In Proceedings of the 2022 2nd International Conference on Computing and Information Technology (ICCIT), Tabuk, Saudi Arabia, 25–27 January 2022; pp. 394–398. [Google Scholar]
- Scarpato, N.; Pieroni, A.; Di Nunzio, L.; Fallucchi, F. E-health-IoT universe: A review. Management 2017, 21, 46. [Google Scholar] [CrossRef]
- Firouzi, F.; Rahmani, A.M.; Mankodiya, K.; Badaroglu, M.; Merrett, G.V.; Wong, P.; Farahani, B. Internet-of-Things and big data for smarter healthcare: From device to architecture, applications and analytics. Future Gener. Comput. Syst. 2018, 78, 583–586. [Google Scholar] [CrossRef]
- Lounis, A.; Hadjidj, A.; Bouabdallah, A.; Challal, Y. Secure and scalable cloud-based architecture for e-Health wireless sensor networks. In Proceedings of the 2012 21st International Conference on Computer Communications and Networks (ICCCN), Munich, Germany, 30 July–2 August 2012. [Google Scholar]
- Pescosolido, L.; Berta, R.; Scalise, L.; Revel, G.M.; De Gloria, A.; Orlandi, G. An IoT-inspired cloud-based web service architecture for e-Health applications. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2), Trento, Italy, 12–15 September 2016; pp. 1–4. [Google Scholar] [CrossRef]
- Gómez, D.; Romero, J.; López, P.; Vázquez, J.; Cappo, C.; Pinto, D.; Villalba, C. Cloud architecture for electronic health record systems interoperability. Technol. Health Care 2021, 30, 551–564. [Google Scholar] [CrossRef]
- Dang, X.T.; Knauer, R.; Peters, S.; Sivrikaya, F. A converged cloud-fog architecture for future eHealth applications. In Proceedings of the 2021 Sixth International Conference on Fog and Mobile Edge Computing (FMEC), Gandia, Spain, 6–9 December 2021; pp. 1–8. [Google Scholar]
- Memos, V.A.; Psannis, K.E.; Goudos, S.K.; Kyriazakos, S. An enhanced and secure cloud infrastructure for e-health data transmission. Wirel. Pers. Commun. 2021, 117, 109–127. [Google Scholar] [CrossRef]
- Abbas van der Molen, I.N.; Nader, M.R.; Lovett, J.C. Trust and Cooperation Relations in Environmental Management of Lebanon. Eur. Sci. J. 2014, 2, 289–299. [Google Scholar]
- El Jaouhari, S.; Bouabdallah, A.; Bonnin, J.M.; Lemlouma, T. Toward a smart health-care architecture using WebRTC and WoT. In Advances in Intelligent Systems and Computing; Rocha, Á., Correia, A.M., Adeli, H., Reis, L.P., Costanzo, S., Eds.; Springer International Publishing: Cham, Switzerland, 2017; Volume 571, pp. 531–540. [Google Scholar] [CrossRef]
- Rhahla, M.; Abdellatif, T.; Attia, R.; Berrayana, W. A GDPR controller for IoT systems: Application to e-Health. In Proceedings of the 2019 IEEE 28th International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises, WETICE 2019, Napoli, Italy, 12–14 June 2019; pp. 170–173. [Google Scholar] [CrossRef]
- Li, M.; Moll, E.; Chituc, C.M. IoT for healthcare: An architecture and prototype implementation for the remote e-health device management using continua and LwM2M protocols. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 20–23 October 2018; pp. 2920–2926. [Google Scholar] [CrossRef]
- Koutli, M.; Theologou, N.; Tryferidis, A.; Tzovaras, D.; Kagkini, A.; Zandes, D.; Karkaletsis, K.; Kaggelides, K.; Almela Miralles, J.; Oravec, V.; et al. Secure IoT e-Health applications using VICINITY framework and GDPR guidelines. In Proceedings of the 15th Annual International Conference on Distributed Computing in Sensor Systems, DCOSS 2019, Santorini Island, Greece, 29–31 May 2019; pp. 263–270. [Google Scholar] [CrossRef]
- Santamaria, A.F.; De Rango, F.; Serianni, A.; Raimondo, P. A real IoT device deployment for e-Health applications under lightweight communication protocols, activity classifier and edge data filtering. Comput. Commun. 2018, 128, 60–73. [Google Scholar] [CrossRef]
- Domingues, M.F.; Alberto, N.; Leitao, C.S.J.; Tavares, C.; de Lima, E.; Radwan, A.; Sucasas, V.; Rodriguez, J.; Andre, P.S.B.; Antunes, P.F.C. Insole Optical Fiber Sensor Architecture for Remote Gait Analysis—An e-Health Solution. IEEE Internet Things J. 2019, 6, 207–214. [Google Scholar] [CrossRef]
- Said, O.; Tolba, A. SEAIoT: Scalable E-Health Architecture based on Internet of Things. Int. J. Comput. Appl. 2012, 59, 44–48. [Google Scholar] [CrossRef]
- Garai, Á.; Péntek, I.; Adamkó, A.; Németh, Á. Methodology for clinical integration of e-Health sensor-based smart device technology with cloud architecture. Pollack Period. 2017, 12, 69–80. [Google Scholar] [CrossRef]
- Qiao, L.; Koutsakis, P. Guaranteed bandwidth allocation and QoS support for mobile telemedicine traffic. In Proceedings of the 2008 IEEE Sarnoff Symposium SARNOFF, Princeton, NJ, USA, 28–30 April 2008. [Google Scholar] [CrossRef]
- Istepanian, R.S.; Lacal, J.C. Emerging mobile communication technologies for health: Some imperative notes on m-health. In Proceedings of the 25th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, Cancun, Mexico, 17–21 September 2003; Volume 2, pp. 1414–1416. [Google Scholar] [CrossRef]
- Garai, Á.; Péntek, I.; Adamkó, A. Revolutionizing healthcare with IoT and cognitive, cloud-based telemedicine. Acta Polytech. Hung. 2019, 16, 163–181. [Google Scholar] [CrossRef]
- Raskovic, D.; Milenkovic, A.; De Groen, P.C.; Jovanov, E. From telemedicine to ubiquitous m-health: The evolution of e-health systems. Biomed. Inf. Technol. 2008, 1, 479–496. [Google Scholar] [CrossRef]
- Tarín, C.; Traver, L.; Cardona, N.; Valencia, U.P.D. Wireless Body Area Networks for Telemedicine Applications. Mag. Waves 2009, 1, 124–132. [Google Scholar]
- Chan, M.; Estève, D.; Fourniols, J.Y.; Escriba, C.; Campo, E. Smart wearable systems: Current status and future challenges. Artif. Intell. Med. 2012, 56, 137–156. [Google Scholar] [CrossRef] [PubMed]
- Castillejo, P.; Martinez, J.F.; Rodriguez-Molina, J.; Cuerva, A. Integration of wearable devices in a wireless sensor network for an e-health application. IEEE Wirel. Commun. 2013, 20, 38–49. [Google Scholar] [CrossRef]
- Benharref, A.; Serhani, M.A. Novel cloud and SOA-based framework for e-Health monitoring using wireless biosensors. IEEE J. Biomed. Health Inform. 2013, 18, 46–55. [Google Scholar] [CrossRef] [PubMed]
- Caldeira, J.M.; Rodrigues, J.J.; Garcia, J.F.; de la Torre, I. A new wireless biosensor for intra-vaginal temperature monitoring. Sensors 2010, 10, 10314–10327. [Google Scholar] [CrossRef] [PubMed]
- Giorgi, G.; Tonello, S. Wearable Biosensor Standardization: How to Make Them Smarter. Standards 2022, 2, 25. [Google Scholar] [CrossRef]
- Teja, M.S.; Konatham, T.R.; Muralidharan, V.; Murugesan, A.; Vasantha, N.; Hyandavi, M. A Review on Biosensors for COVID-19. Int. J. Appl. Pharm. Sci. Res. 2022, 7, 9–14. [Google Scholar]
- Appelboom, G.; Camacho, E.; Abraham, M.E.; Bruce, S.S.; Dumont, E.L.; Zacharia, B.E.; D’Amico, R.; Slomian, J.; Reginster, J.Y.; Bruyère, O.; et al. Smart wearable body sensors for patient self-assessment and monitoring. Arch. Public Health 2014, 72, 28. [Google Scholar] [CrossRef]
- Site, A.; Nurmi, J.; Lohan, E.S. Systematic review on machine-learning algorithms used in wearable-based eHealth data analysis. IEEE Access 2021, 9, 112221–112235. [Google Scholar] [CrossRef]
- Pierleoni, P.; Belli, A.; Concetti, R.; Palma, L.; Pinti, F.; Raggiunto, S.; Sabbatini, L.; Valenti, S.; Monteriù, A. Biological age estimation using an eHealth system based on wearable sensors. J. Ambient Intell. Humaniz. Comput. 2021, 12, 4449–4460. [Google Scholar] [CrossRef]
- Kulkarni, P.; Kirkham, R.; McNaney, R. Opportunities for Smartphone Sensing in E-Health Research: A Narrative Review. Sensors 2022, 22, 3893. [Google Scholar] [CrossRef]
- Rai, R.S.; Indumathi, S.; Pritima, D.; Rani, S.S. IoT secure framework for wearable sensor data for e-health system. In Proceedings of the 2021 Fifth International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 11–13 November 2021; pp. 211–215. [Google Scholar]
- Khairuddin, A.; Azir, K.F.K.; Kan, P.E. Limitations and future of electrocardiography devices: A review and the perspective from the internet of things. In Proceedings of the 2017 International Conference on Research and Innovation in Information Systems (ICRIIS), Langkawi, Malaysia, 16–17 July 2017; pp. 1–7. [Google Scholar]
- Jost, K.; Scherer, S.; De Angelis, C.; Büchler, M.; Datta, A.N.; Cattin, P.C.; Frey, U.; Suki, B.; Schulzke, S.M. Surface electromyography for analysis of heart rate variability in preterm infants. Physiol. Meas. 2017, 39, 015004. [Google Scholar] [CrossRef] [PubMed]
- Marras, W.S. Overview of electromyography in ergonomics. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting, Los Angeles, CA, USA, 30 July–4 August 2000; SAGE Publications Sage: Los Angeles, CA, USA, 2000; Volume 44, pp. 5–534. [Google Scholar]
- Parvizi, J.; Kastner, S. Promises and limitations of human intracranial electroencephalography. Nat. Neurosci. 2018, 21, 474–483. [Google Scholar] [CrossRef] [PubMed]
- Jebelli, H.; Khalili, M.M.; Lee, S. Mobile EEG-based workers’ stress recognition by applying deep neural network. In Advances in Informatics and Computing in Civil and Construction Engineering; Springer: Berlin/Heidelberg, Germany, 2019; pp. 173–180. [Google Scholar]
- Longmore, S.K.; Lui, G.Y.; Naik, G.; Breen, P.P.; Jalaludin, B.; Gargiulo, G.D. A comparison of reflective photoplethysmography for detection of heart rate, blood oxygen saturation, and respiration rate at various anatomical locations. Sensors 2019, 19, 1874. [Google Scholar] [CrossRef] [PubMed]
- Vulcan, R.S.; André, S.; Bruyneel, M. Photoplethysmography in normal and pathological sleep. Sensors 2021, 21, 2928. [Google Scholar] [CrossRef]
- Hosanee, M.; Chan, G.; Welykholowa, K.; Cooper, R.; Kyriacou, P.A.; Zheng, D.; Allen, J.; Abbott, D.; Menon, C.; Lovell, N.H.; et al. Cuffless single-site photoplethysmography for blood pressure monitoring. J. Clin. Med. 2020, 9, 723. [Google Scholar] [CrossRef] [PubMed]
- Peng, K.C.; Sung, M.C.; Wang, F.K.; Horng, T.S. Non-contact vital sign detection using gain detection technique. In Proceedings of the 2021 IEEE International Symposium on Radio-Frequency Integration Technology (RFIT), Virtual Conference, Taiwan, China, 25–27 August 2021; pp. 1–2. [Google Scholar]
- Rauen, K.; Schaffrath, J.; Pradhan, C.; Schniepp, R.; Jahn, K. Accelerometric trunk sensors to detect changes of body positions in immobile patients. Sensors 2018, 18, 3272. [Google Scholar] [CrossRef] [PubMed]
- Zahradka, N.; Behboodi, A.; Wright, H.; Bodt, B.; Lee, S. Evaluation of gait phase detection delay compensation strategies to control a gyroscope-controlled functional electrical stimulation system during walking. Sensors 2019, 19, 2471. [Google Scholar] [CrossRef] [PubMed]
- Oldroyd, A.; Little, M.A.; Dixon, W.; Chinoy, H. A review of accelerometer-derived physical activity in the idiopathic inflammatory myopathies. BMC Rheumatol. 2019, 3, 41. [Google Scholar] [CrossRef] [PubMed]
- Wixley, H. Smart application for fall detection using wearable ECG & accelerometer sensors. arXiv 2022, arXiv:2207.00008. [Google Scholar]
- França, R.P.; Monteiro, A.C.B.; Arthur, R.; Iano, Y. Overview of ubiquitous computing and a modern look in current times. In Integration of WSNs into Internet of Things; CRC Press: Boca Raton, FL, USA, 2021; pp. 45–63. [Google Scholar]
- Shakkeera, L.; Sharmasth Vali, Y.; Viswanathan, S.K. An insight on context-aware mobile application execution in mobile cloud IoT (MCIoT). In International Virtual Conference on Industry 4.0; Springer: Berlin/Heidelberg, Germany, 2021; pp. 69–86. [Google Scholar]
- Khaddar, M.A.E.; Harroud, H.; Boulmalf, M.; Elkoutbi, M.; Habbanil, A. Emerging wireless technologies in e-Health. In Proceedings of the Multimedia Computing and Systems, International Conference, Tangiers, Morocco, 10–12 May 2012; pp. 440–445. [Google Scholar]
- Memon, S.K.; Nisar, K.; Hijazi, M.H.A.; Chowdhry, B.; Sodhro, A.H.; Pirbhulal, S.; Rodrigues, J.J. A survey on 802.11 MAC industrial standards, architecture, security & supporting emergency traffic: Future directions. J. Ind. Inf. Integr. 2021, 24, 100225. [Google Scholar]
- Famitafreshi, G.; Afaqui, M.S.; Melià-Seguí, J. Enabling Energy Harvesting-Based Wi-Fi System for an e-Health Application: A MAC Layer Perspective. Sensors 2022, 22, 3831. [Google Scholar] [CrossRef]
- Hossain, M.J.; Bari, M.A.; Khan, M.M. Development of an IoT based health monitoring system for e-Health. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022; pp. 0031–0037. [Google Scholar]
- Jha, A.V.; Mishra, S.K.; Appasani, B.; Ghazali, A.N. Communication networks for metropolitan E-health applications. IEEE Potentials 2021, 40, 34–42. [Google Scholar] [CrossRef]
- Chandrasekaran, V.; Babu, D.V.; Thanikaiselvan, V.; Somasundaram, K. Designing of Tele-Health Smart Sensor Device to assist home care staff. J. Phys. Conf. Ser. 2021, 1964, 062106. [Google Scholar] [CrossRef]
- Abbasi, J.; Alina, L.; Abro, A.M.; Lal, B. SEHAT: Smart e-Health app for telediagnosis and first opinion. In Proceedings of the 2021 6th International Multi-Topic ICT Conference (IMTIC), Jamshoro, Sindh, Pakistan, 10–12 November 2021; pp. 1–6. [Google Scholar]
- Ramírez-Faz, J.; Fernández-Ahumada, L.M.; Fernández-Ahumada, E.; López-Luque, R. Monitoring of temperature in retail refrigerated cabinets applying IoT over open-source hardware and software. Sensors 2020, 20, 846. [Google Scholar] [CrossRef]
- El-Tawab, S.; Olariu, S.; Almalag, M. Making traffic-related decisions in FRIEND: A cyber-physical system for traffic flow related information aggregation and dissemination. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; pp. 939–944. [Google Scholar]
- Nakamura, M.; Kubota, S.; Takagi, H.; Einaga, K.; Yokoyama, M.; Mochizuki, K.; Takizawa, M.; Murase, S. Development of long-range and high-speed wireless LAN for the transmission of telemedicine from disaster areas. Eur. J. Wirel. Commun. Netw. 2008, 2008, 724010. [Google Scholar] [CrossRef]
- Murakami, H.; Shimizu, K.; Yamamoto, K.; Mikami, T.; Hoshimiya, N.; Kondo, K. Telemedicine using mobile satellite communication. IEEE Trans. Biomed. Eng. 1994, 41, 488–497. [Google Scholar] [CrossRef]
- Srivastava, S.; Pant, M.; Abraham, A.; Agrawal, N. The technological growth in eHealth services. Comput. Math. Methods Med. 2015, 2015, 894171. [Google Scholar] [CrossRef]
- Meethal, S.P.; Jyothish, J. A low cost connectivity solution for rural mobile telemedicine. In Proceedings of the 2011 IEEE Global Humanitarian Technology Conference, Seattle, WA, USA, 30 October–1 November 2011; pp. 506–511. [Google Scholar] [CrossRef]
- Isca, A.; Alagha, N.; Andreotti, R.; Andrenacci, M. Recent Advances in Design and Implementation of Satellite Gateways for Massive Uncoordinated Access Networks. Sensors 2022, 22, 565. [Google Scholar] [CrossRef]
- Al-Janabi, F.; Singh, M.J.; Pharwaha, A.P.S. Development of Microstrip Antenna for Satellite Application at Ku/Ka Band. J. Commun. 2021, 16, 118–125. [Google Scholar] [CrossRef]
- Tsuji, H.; Miura, A.; Tomoshige, K.; Takahashi, T.; Ohkawa, M.; Okura, T.; Yuma, A.; Toyoshima, M. Effective use of Ka-band based on antenna and radio wave propagation for mobile satellite communications. In Proceedings of the 2020 International Symposium on Antennas and Propagation (ISAP), Osaka, Japan, 25–28 January 2021; pp. 57–58. [Google Scholar]
- Karami, F.; Rezaei, P.; Amn-e Elahi, A.; Abolfathi, A.; Kishk, A.A. Broadband and efficient patch array antenna fed by substrate integrated waveguide feed network for Ku-band satellite applications. Int. J. RF Microw. Comput.-Aided Eng. 2021, 31, e22772. [Google Scholar] [CrossRef]
- Chen, Z.N.; Qing, X.; Tang, X.; Liu, W.E.; Xu, R. Phased Array Metantennas for Satellite Communications. IEEE Commun. Mag. 2022, 60, 46–50. [Google Scholar] [CrossRef]
- Yamashita, Y.; Tani, S.; Uchida, S.; Hangai, M.; Aruga, H. An error tolerant digital payload based on stochastic computing for software defined satellite. In Proceedings of the 38th International Communications Satellite Systems Conference (ICSSC 2021), IET, Arlington, VA, USA, 27–30 September 2021; Volume 2021, pp. 208–213. [Google Scholar]
- Istepanian, R.S.; Pattichis, C.S.; Laxminarayan, S. Ubiquitous m-Health systems and the convergence towards 4G mobile technologies. In M-Health; Springer: Berlin/Heidelberg, Germany, 2006; pp. 3–14. [Google Scholar]
- Editorial, G. M-Health: Beyond seamless mobility and global wireless healthcare connectivity. IEEE Trans. IT Biomed. 2004, 8, 405–413. [Google Scholar]
- Chu, Y.; Ganz, A. Mobile telemedicine systems using 3G wireless networks. Bus. Brief. US Healthc. Strateg. 2005, 1, 1–6. [Google Scholar]
- Chu, Y.; Ganz, A. A mobile teletrauma system using 3G networks. IEEE Trans. Inf. Technol. Biomed. 2004, 8, 456–462. [Google Scholar] [CrossRef]
- Kamsu-Foguem, B.; Foguem, C. Telemedicine and mobile health with integrative medicine in developing countries. Health Policy Technol. 2014, 3, 264–271. [Google Scholar] [CrossRef]
- Sultana, N.; Islam, M.A. Ubiquitous future m-Health system including wireless 3G technologies in Bangladesh. J. Adv. Technol. Eng. Res. 2015, 1, 22–29. [Google Scholar]
- Ezhilarasan, E.; Dinakaran, M. A review on mobile technologies: 3G, 4G and 5G. In Proceedings of the 2017 Second International Conference on Recent Trends and Challenges in Computational Models (ICRTCCM), Tamilnadu, India, 3–4 February 2017; pp. 369–373. [Google Scholar]
- Kumar, A.; Aswal, A.; Singh, L. 4G wireless technology: A brief review. Int. J. Eng. Manag. Res. 2013, 3, 35–43. [Google Scholar]
- Nam, W.; Bai, D.; Lee, J.; Kang, I. Advanced interference management for 5G cellular networks. IEEE Commun. Mag. 2014, 52, 52–60. [Google Scholar] [CrossRef]
- Shen, Z.; Papasakellariou, A.; Montojo, J.; Gerstenberger, D.; Xu, F. Overview of 3GPP LTE-advanced carrier aggregation for 4G wireless communications. IEEE Commun. Mag. 2012, 50, 122–130. [Google Scholar] [CrossRef]
- Barb, G.; Otesteanu, M. 4G/5G: A comparative study and overview on what to expect from 5G. In Proceedings of the 2020 43rd International Conference on Telecommunications and Signal Processing (TSP), Milan, Italy, 7–9 July 2020; pp. 37–40. [Google Scholar]
- Zaki, R.M.; Wahab, H.B.A. 4G Network Security Algorithms: Overview. Int. J. Interact. Mob. Technol. 2021, 15, 127–143. [Google Scholar] [CrossRef]
- Istepanian, R.S.; Alinejad, A.; Philip, N.Y. Medical quality of service (m-QoS) and quality of experience (m-QoE) for 4G-health systems. In Multimedia Networking and Coding; IGI Global: Hershey, PA, USA, 2013; pp. 359–376. [Google Scholar]
- Istepanaian, R.S.; Zhang, Y.T. Guest editorial introduction to the special section: 4G health—The long-term evolution of m-health. IEEE Trans. Inf. Technol. Biomed. 2012, 16, 1–5. [Google Scholar] [CrossRef]
- Heneghan, M.B.; Hussain, T.; Barrera, L.; Cai, S.W.; Haugen, M.; Morgan, E.; Rossoff, J.; Weinstein, J.; Hijiya, N.; Cella, D.; et al. Access to technology and preferences for an mHealth intervention to promote medication adherence in pediatric acute lymphoblastic leukemia: Approach leveraging behavior change techniques. J. Med. Internet Res. 2021, 23, e24893. [Google Scholar] [CrossRef]
- Joshi, V.; Holtzman, M.; Arcelus, A.; Goubran, R.; Knoefel, F. Highly survivable bed pressure mat remote patient monitoring system for mHealth. In Proceedings of the 2012 Annual International Conference of the IEEE Engineering in Medicine and Biology Society, San Diego, CA, USA, 28 August–1 September 2012; pp. 268–271. [Google Scholar]
- Iqbal, S.; Ahsan, K.; Hussain, M.A.; Nadeem, A. Social media as assistive technology for elderly. J. Basic Appl. Sci. 2016, 12, 211–222. [Google Scholar]
- Lee, Y.; Hong, S.; Nam, M. Design strategy of smart phone-based diabetic patient management system. In Computer Applications for Security, Control and System Engineering; Springer: Berlin/Heidelberg, Germany, 2012; pp. 306–313. [Google Scholar]
- Padmashree, T.; Nayak, S.S. 5G technology for e-Health. In Proceedings of the 2020 Fourth International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 7–9 October 2020; pp. 211–216. [Google Scholar]
- El-Shorbagy, A.m. 5G Technology and the Future of Architecture. Procedia Comput. Sci. 2021, 182, 121–131. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Hossan, M.T.; Shahjalal, M.; Hasan, M.K.; Jang, Y.M. A new 5G ehealth architecture based on optical camera communication: An overview, prospects, and applications. IEEE Consum. Electron. Mag. 2020, 9, 23–33. [Google Scholar] [CrossRef]
- Lloret, J.; Parra, L.; Taha, M.; Tomás, J. An architecture and protocol for smart continuous eHealth monitoring using 5G. Comput. Netw. 2017, 129, 340–351. [Google Scholar] [CrossRef]
- Kapassa, E.; Touloupou, M.; Mavrogiorgou, A.; Kiourtis, A.; Giannouli, D.; Katsigianni, K.; Kyriazis, D. An innovative ehealth system powered by 5G network slicing. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; pp. 7–12. [Google Scholar]
- Zhang, D.; Rodrigues, J.J.; Zhai, Y.; Sato, T. Design and Implementation of 5G e-Health Systems: Technologies, Use Cases, and Future Challenges. IEEE Commun. Mag. 2021, 59, 80–85. [Google Scholar] [CrossRef]
- Siriwardhana, Y.; Gür, G.; Ylianttila, M.; Liyanage, M. The role of 5G for digital healthcare against COVID-19 pandemic: Opportunities and challenges. ICT Express 2021, 7, 244–252. [Google Scholar] [CrossRef]
- Andress, J. The Basics of Information Security: Understanding the Fundamentals of InfoSec in Theory and Practice; Syngress: Waltham, MA, USA, 2014. [Google Scholar]
- Shenoy, A.; Appel, J.M. Safeguarding confidentiality in electronic health records. Camb. Q. Healthc. Ethics 2017, 26, 337–341. [Google Scholar] [CrossRef]
- Al-Issa, Y.; Ottom, M.A.; Tamrawi, A. eHealth cloud security challenges: A survey. J. Healthc. Eng. 2019, 2019, 7516035. [Google Scholar] [CrossRef]
- Vimalachandran, P.; Wang, H.; Zhang, Y.; Heyward, B.; Whittaker, F. Ensuring data integrity in electronic health records: A quality health care implication. In Proceedings of the 2016 International Conference on Orange Technologies (ICOT), Piscataway, NJ, USA, 18–20 December 2016; pp. 20–27. [Google Scholar]
- Scholl, M.; Stine, K.; Hash, J.; Bowen, P.; Johnson, A.; Smith, C.; Steinberg, D. An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule (NIST Special Publication 800-66, Rev. 1). Computer Security Division: Gaithersburg, MD, USA. Information Technology Laboratory, National Institute of Standards and Technology. 2008. Available online: http://csrc.nist.gov/publications/nistpubs/800-66-Rev1/SP-800-66-Revision1.pdf (accessed on 25 September 2022).
- Vergouw, J.W.; Smits-Pelser, H.; Kars, M.C.; van Houwelingen, T.; van Os-Medendorp, H.; Kort, H.; Bleijenberg, N. Needs, barriers and facilitators of older adults towards eHealth in general practice: A qualitative study. Prim. Health Care Res. Dev. 2020, 21, e54. [Google Scholar] [CrossRef] [PubMed]
- Alanazi, S.; Saleem, K.; Al-Muhtadi, J.; Derhab, A. Analysis of denial of service impact on data routing in mobile eHealth wireless mesh network. Mob. Inf. Syst. 2016, 2016, 4853924. [Google Scholar] [CrossRef]
- Tanvi, P.; Sonal, G.; Kumar, S.M. Token based authentication using mobile phone. In Proceedings of the 2011 International Conference on Communication Systems and Network Technologies, Washington, DC, USA, 3–5 June 2011; pp. 85–88. [Google Scholar]
- Michael, K.; Michael, M. Uberveillance. In Innovative Automatic Identification and Location-Based Services: From Bar Codes to Chip Implants; IGI Global: Hershey, PA, USA, 2009; pp. 464–484. [Google Scholar]
- Mann, S. Veillance: Beyond surveillance, dataveillance, uberveillance, and the hypocrisy of one-sided watching. In Biometrics: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2017; pp. 1575–1590. [Google Scholar]
- Rollo, M.E.; Aguiar, E.J.; Williams, R.L.; Wynne, K.; Kriss, M.; Callister, R.; Collins, C.E. eHealth technologies to support nutrition and physical activity behaviors in diabetes self-management. Diabetes Metab. Syndr. Obes. Targets Ther. 2016, 9, 381. [Google Scholar] [CrossRef]
- Lim, Y.Y.; Messina, M.; Kargl, F.; Ganguli, L.; Fischer, M.; Tsang, T. Snmp proxy for wireless sensor network. In Proceedings of the Fifth International Conference on Information Technology: New Generations (ITNG 2008), Washington, DC, USA, 7–9 April 2008; pp. 738–743. [Google Scholar]
- Shi, E.; Perrig, A. Designing secure sensor networks. IEEE Wirel. Commun. 2004, 11, 38–43. [Google Scholar]
- Lee, C.I.; Chien, H.Y. An elliptic curve cryptography-based RFID authentication securing e-health system. Int. J. Distrib. Sens. Netw. 2015, 11, 642425. [Google Scholar] [CrossRef]
- Sahebi, G.; Majd, A.; Ebrahimi, M.; Plosila, J.; Karimpour, J.; Tenhunen, H. SEECC: A secure and efficient elliptic curve cryptosystem for e-Health applications. In Proceedings of the 2016 International Conference on High Performance Computing & Simulation (HPCS), Innsbruck, Austria, 18–22 July 2016; pp. 492–500. [Google Scholar]
- Gomes, H.; Cunha, J.P.; Zúquete, A. Authentication architecture for ehealth professionals. In Proceedings of the OTM Confederated International Conferences “On the Move to Meaningful Internet Systems”, Vilamoura, Portugal, 25–30 November 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1583–1600. [Google Scholar]
- Spychalski, D.; Rode, O.; Ritthaler, M.; Raptis, G. Conceptual design and analysis of a mobile digital identity for eHealth applications. In Proceedings of the 2021 IEEE EMBS International Conference on Biomedical and Health Informatics (BHI), Virtual Conference, 27–30 July 2021; pp. 1–4. [Google Scholar]
- El-Shafai, W.; Khallaf, F.; El-Rabaie, E.S.M.; El-Samie, F.E.A. Proposed 3D chaos-based medical image cryptosystem for secure cloud-IoMT eHealth communication services. J. Ambient. Intell. Humaniz. Comput. 2022, 1, 1–28. [Google Scholar] [CrossRef]
- Sawand, A.; Djahel, S.; Zhang, Z.; Nait-Abdesselam, F. Toward energy-efficient and trustworthy eHealth monitoring system. China Commun. 2015, 12, 46–65. [Google Scholar] [CrossRef]
- Morchón, O.G.; Baldus, H.; Sánchez, D.S. Resource-efficient security for medical body sensor networks. In Proceedings of the International Workshop on Wearable and Implantable Body Sensor Networks (BSN’06), Cambridge, MA, USA, 3–5 April 2006; pp. 4–8. [Google Scholar]
- Lin, X.; Lu, R.; Shen, X.; Nemoto, Y.; Kato, N. Sage: A strong privacy-preserving scheme against global eavesdropping for ehealth systems. IEEE J. Sel. Areas Commun. 2009, 27, 365–378. [Google Scholar]
- Barua, M.; Liang, X.; Lu, R.; Shen, X. PEACE: An efficient and secure patient-centric access control scheme for eHealth care system. In Proceedings of the 2011 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Shanghai, China, 10–15 April 2011; pp. 970–975. [Google Scholar]
- Barua, M.; Liang, X.; Lu, R.; Shen, X. ESPAC: Enabling Security and Patient-centric Access Control for eHealth in cloud computing. Int. J. Secur. Netw. 2011, 6, 67–76. [Google Scholar] [CrossRef]
- Khasim, S.; Basha, S.S. An Improved Fast and Secure CAMEL Based Authenticated Key in Smart Health Care System. Cloud Comput. Data Sci. 2022, 1, 39–53. [Google Scholar] [CrossRef]
- Hämäläinen, M.; Mucchi, L.; Paso, T. Remote secure eHealth provision: ETSI SmartBAN as an enabler. In Proceedings of the 2022 IEEE 16th International Symposium on Medical Information and Communication Technology (ISMICT), Lincoln, NE, USA, 2–4 May 2022; pp. 1–4. [Google Scholar]
- Moosavi, S.R.; Izadifar, A. End-to-end security scheme for e-Health systems using DNA-based ECC. In Proceedings of the Silicon Valley Cybersecurity Conference, San Jose, CA, USA, 2–3 December 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 77–89. [Google Scholar]
- Cholakoska, A.; Pfitzner, B.; Gjoreski, H.; Rakovic, V.; Arnrich, B.; Kalendar, M. Differentially private federated learning for anomaly detection in eHealth networks. In Proceedings of the Adjunct Proceedings of the 2021 ACM International Joint Conference on Pervasive and Ubiquitous Computing and Proceedings of the 2021 ACM International Symposium on Wearable Computers, Virtual, USA, 21–26 September 2021; pp. 514–518. [Google Scholar]
- Camilo, T.; Oscar, R.; Carlos, L. Biomedical signal monitoring using wireless sensor networks. In Proceedings of the 2009 IEEE Latin-American Conference on Communications, LATINCOM’09—Conference Proceedings, Medellín, Colombia, 10–11 September 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Koivu, A.; Mavengere, N.; Ruohonen, M.; Hederman, L.; Grimson, J. Exploring the information and ICT skills of health professionals in low-and middle-income countries. In Proceedings of the International Conference on Stakeholders and Information Technology in Education, Guimarães, Portugal, 5–8 July 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 152–162. [Google Scholar]
- Thuemmler, C.; Fan, L.; Buchanan, W.; Lo, O.; Ekonomou, E.; Khedim, A.S. E-health: Chances and challenges of distributed, service oriented architectures. J. Cyber Secur. Mobil. 2012, 1, 37–52. [Google Scholar] [CrossRef]
- Abhishek, B.; Panjanathan, R.; Sarobin, V.R.; Raja, B.E.; Narendra, M. Data security in e-health monitoring system. Mater. Today Proc. 2022, 62, 4620–4628. [Google Scholar] [CrossRef]
- Sathya, D.; Ganesh Kumar, P. Secured remote health monitoring system. Healthc. Technol. Lett. 2017, 4, 228–232. [Google Scholar] [CrossRef]
- Wei, K.; Zhang, L.; Guo, Y.; Jiang, X. Health monitoring based on Internet of medical things: Architecture, enabling technologies, and applications. IEEE Access 2020, 8, 27468–27478. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for secure ehrs sharing of mobile cloud based e-health systems. IEEE Access 2019, 7, 66792–66806. [Google Scholar] [CrossRef]
- Perumal, A.M.; Nadar, E.R.S. Architectural framework of a group key management system for enhancing e-healthcare data security. Healthc. Technol. Lett. 2020, 7, 13–17. [Google Scholar] [CrossRef]
- Yao, X.; Lin, Y.; Liu, Q.; Zhang, J. Privacy-preserving search over encrypted personal health record in multi-source cloud. IEEE Access 2018, 6, 3809–3823. [Google Scholar] [CrossRef]
- Wu, Z.Y. Group-oriented cryptosystem for personal health records exchange and sharing. IEEE Access 2019, 7, 146495–146505. [Google Scholar] [CrossRef]
- Gatiti, P.; Ndirangu, E.; Mwangi, J.; Mwanzu, A.; Ramadhani, T. Enhancing Healthcare Quality in Hospitals through Electronic Health Records: A Systematic Review. J. Health Inform. Dev. Ctries. 2021, 15, 1. [Google Scholar]
- Atkinson, N.L.; Gold, R.S. The promise and challenge of eHealth interventions. Am. J. Health Behav. 2002, 26, 494–503. [Google Scholar] [CrossRef]
- Norman, C.D.; Skinner, H.A. eHealth literacy: Essential skills for consumer health in a networked world. J. Med. Internet Res. 2006, 8, e506. [Google Scholar] [CrossRef]
- Isiksacan, Z.; Guler, M.T.; Aydogdu, B.; Bilican, I.; Elbuken, C. Rapid fabrication of microfluidic PDMS devices from reusable PDMS molds using laser ablation. J. Micromech. Microeng. 2016, 26, 035008. [Google Scholar] [CrossRef]
- Stroux, L.; Martinez, B.; Coyote Ixen, E.; King, N.; Hall-Clifford, R.; Rohloff, P.; Clifford, G.D. An mHealth monitoring system for traditional birth attendant-led antenatal risk assessment in rural Guatemala. J. Med. Eng. Technol. 2016, 40, 356–371. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Burde, H. The HITECH act: An overview. AMA J. Ethics 2011, 13, 172–175. [Google Scholar]
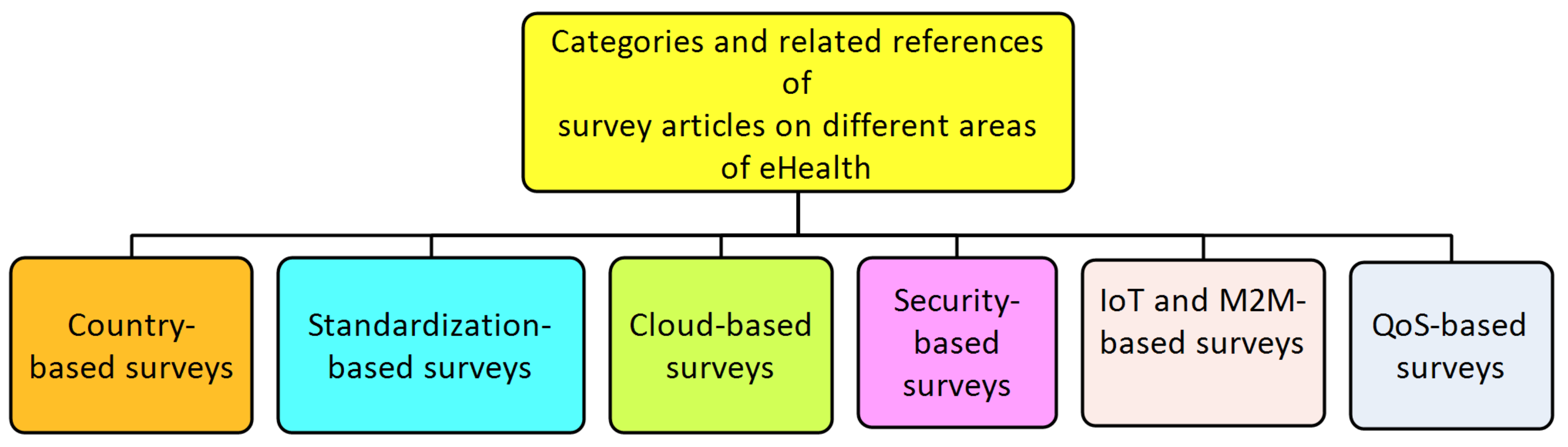
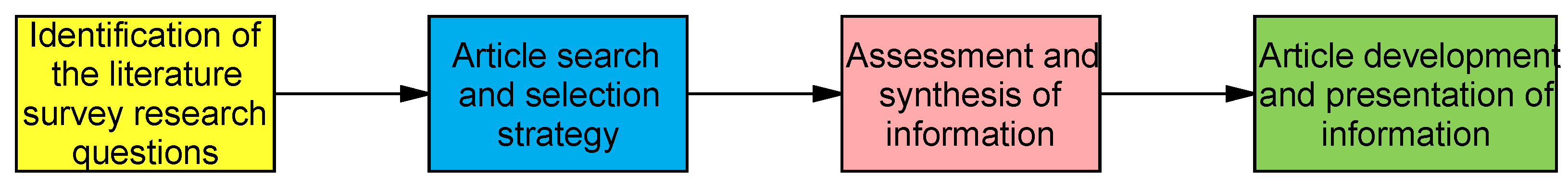
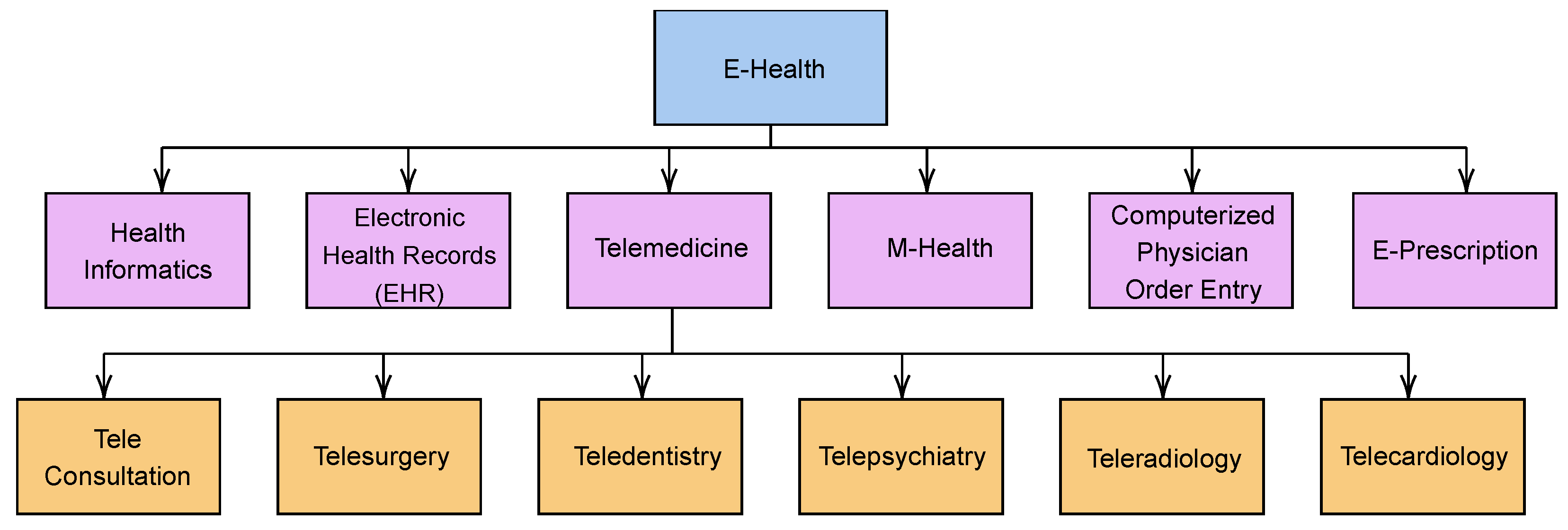

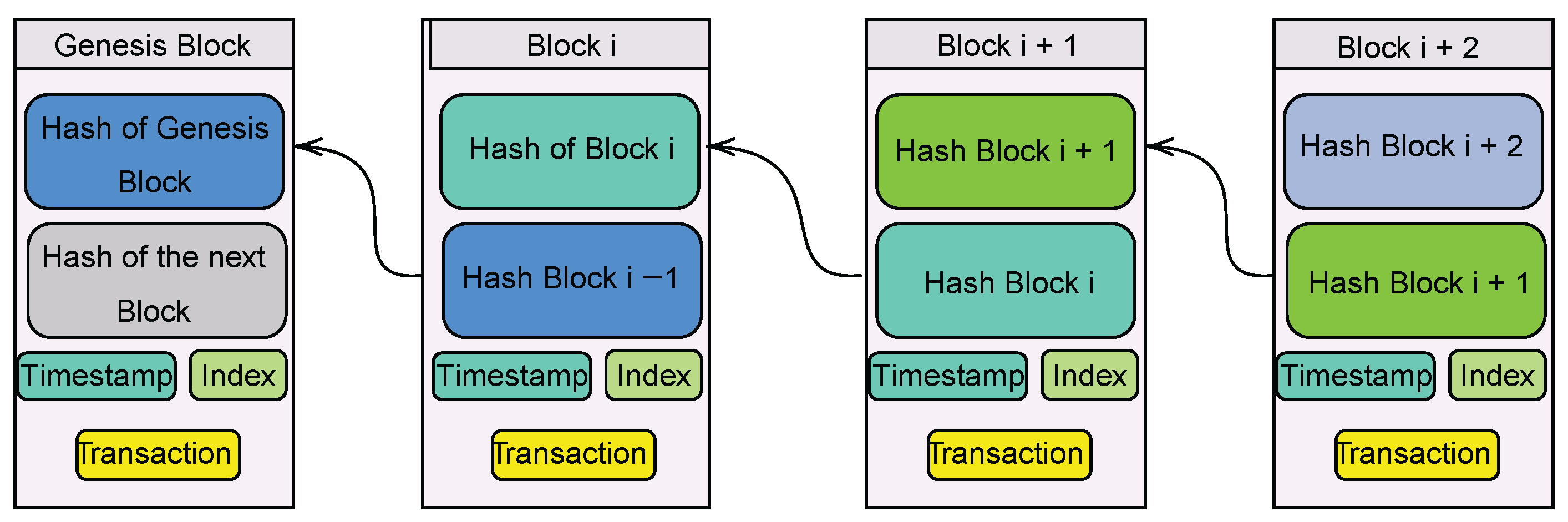

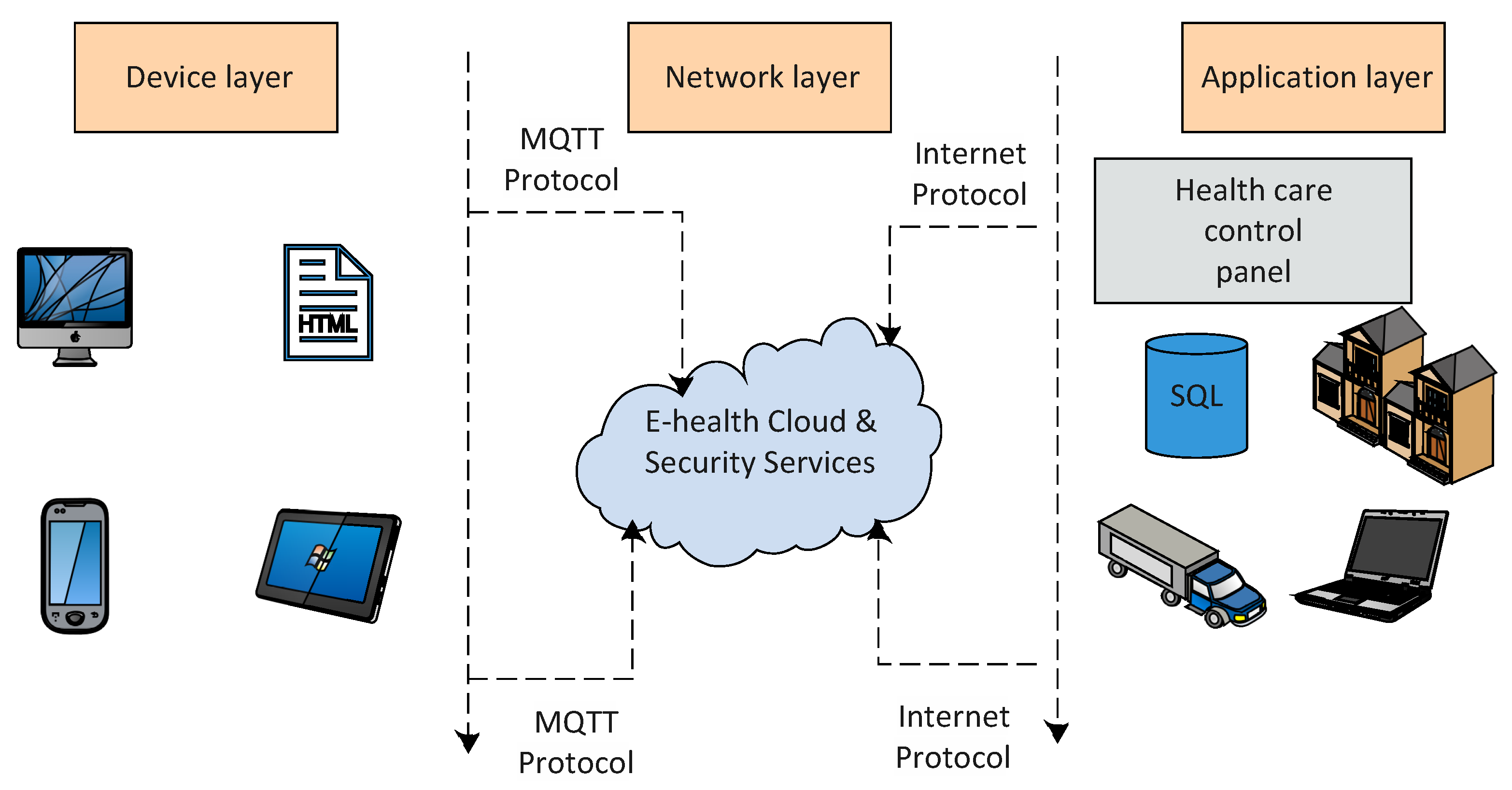
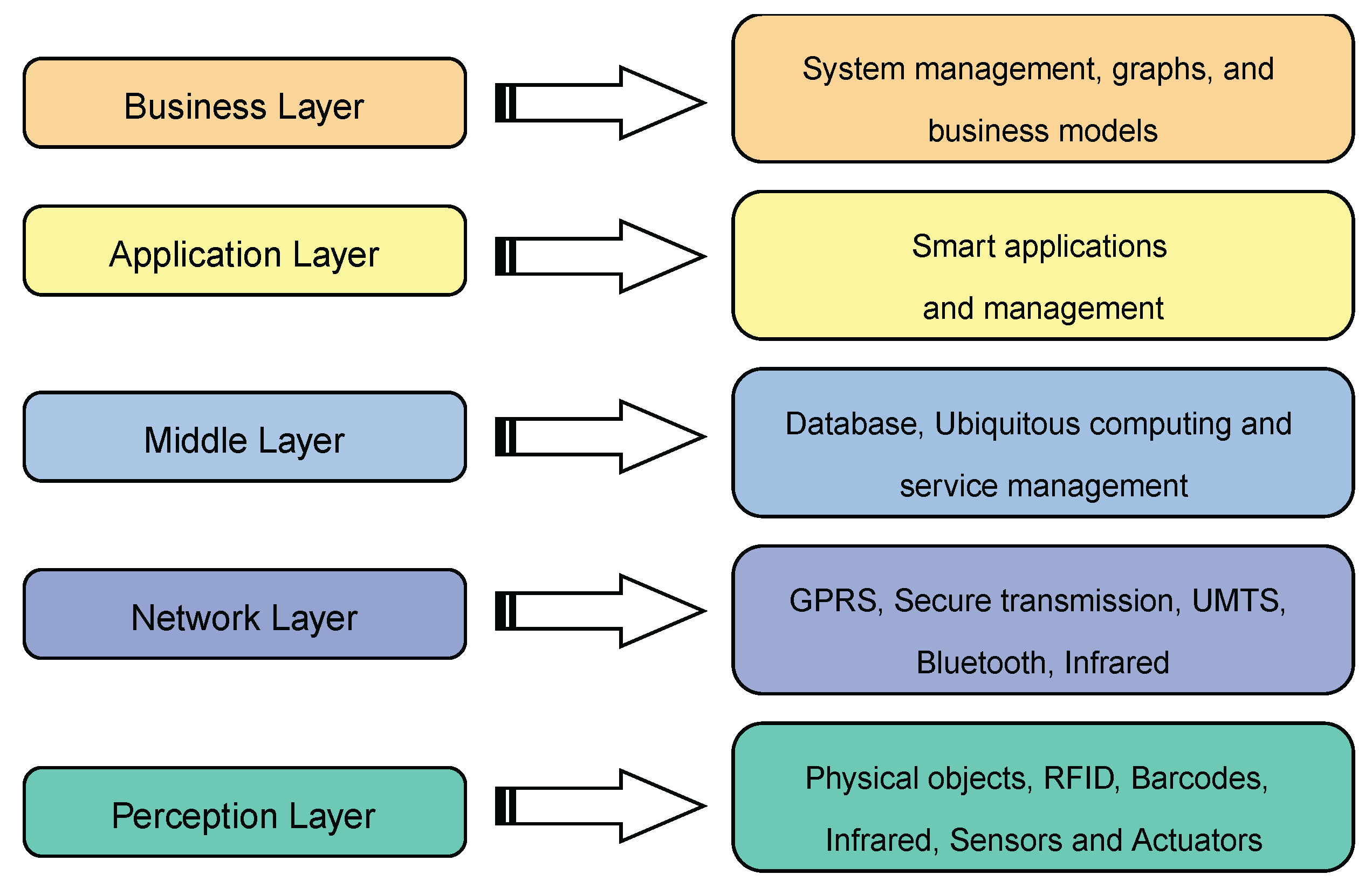
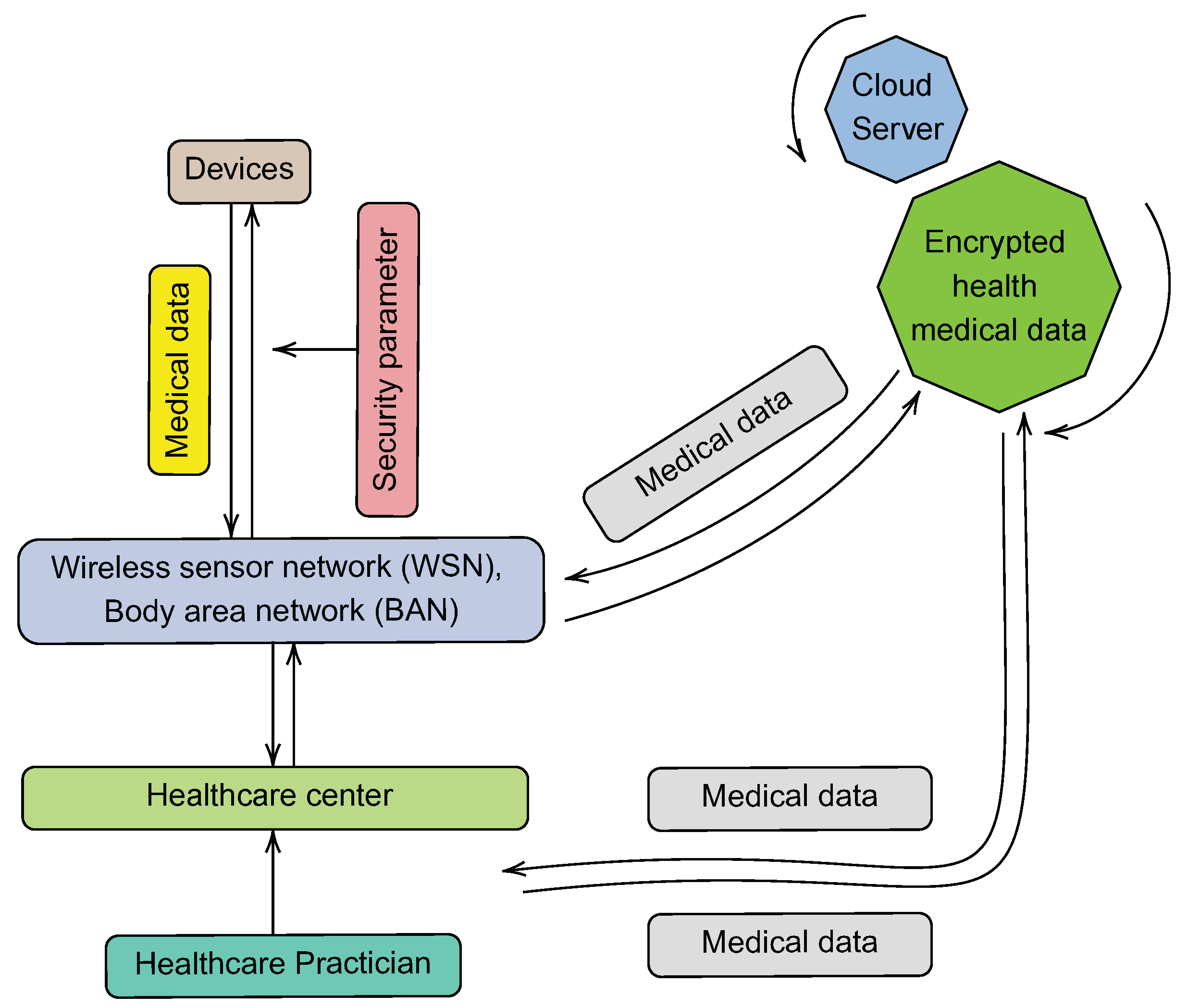


| Title | Year | Category | Specific Details |
|---|---|---|---|
| [23] | 2003 | QoS |
|
| [4] | 2006 | Country |
|
| [20] | 2009 | QoS |
|
| [9] | 2011 | Cloud |
|
| [24] | 2012 | IoT |
|
| [6] | 2012 | IoT/M2M |
|
| [10] | 2012 | Cloud |
|
| [5] | 2014 | Country |
|
| [21] | 2014 | QoS |
|
| [25] | 2014 | Security |
|
| [22] | 2015 | QoS |
|
| [15] | 2015 | Security |
|
| [7] | 2016 | Standardization |
|
| [6] | 2016 | Standardization |
|
| [11] | 2017 | IoT |
|
| [26] | 2017 | Standardization |
|
| [18] | 2019 | IoT |
|
| [19] | 2019 | Security |
|
| [16] | 2019 | Security |
|
| [14] | 2019 | Security |
|
| [17] | 2020 | IoT |
|
| Characteristics | Blockchain | Cloud Services |
|---|---|---|
| Data ownership | Cryptographic keys and Algorithm | Central Authority |
| Privacy and Security | Cryptographic Authentication | Central Authority |
| Access Control | Inherently Identical for all permissioned nodes | Central Authority |
| Trust | Native via Immutable records | Established via Central Authority |
| Stored Procedures | Smart contracts | Not Available |
| Transaction creation | Available to all permissioned parties | Managed via Central authority |
| Architectures | Purpose |
|---|---|
| WEBRTC [80] | Remote examination of patients and injured persons in case of accident |
| IoT GDPR controller [81] | Gives data owner a full control of his data, setting security policies, modifying them on run time, tracking data flow and notification |
| IoT Continua [82] | Ensure the remote management of personal health devices and gateways |
| Vicinity [83] | Combine AAL (Ambient Assisted Living) and mHealth to provide functionalities such as authentication, authorization and end-to-end encryption |
| Fuzzy-based HAR [84] | An IoT-based architecture used to continuously acquire data from body sensors |
| Insole optical fibre sensor [85] | Adaptable to shoe sole for plantar monitoring. Monitors the foot plantar pressure distribution during gait (Walking movement) |
| Scalable eHealth [86] | Clinic hardware communication with other clinic hardware remotely without human interaction |
| Sensors | Functions |
|---|---|
| ECG (Electrocardiograph) | Monitors heart activity, cardiac arrhythmias, heart failure [104] |
| EMG (Electromyography) | Monitors muscle activity [105] & Ergonomics [106] |
| EEG (Electroencephalography) | Monitors brain electrical activity [107] & Stress recognition [108] |
| PPG (Photoplethysmograph) | Monitors pulse and blood oxygen saturation [109] & monitor hypopnea (i.e., sleep condition) [110] |
| Cuff-based pressure sensor | Monitors blood pressure [111] |
| Resistive or Piezo Elelctric chest bell sensor | Monitors respiration & Respiratory tract infections [112] |
| Tilt sensor | Monitoring trunk position [113] |
| Gyroscope Sensor | Gait-phase detection [114] |
| Accelerometer | Estimates type and level of users activity [115] |
| Smart sock/insole sensor | Count steps/fall detection [116] |
| Technology | Bandwidth | Coverage | Mobility |
|---|---|---|---|
| 2G/2.5G (GSM/GPRS) | Low | Rural/Suburban/Urban | Low |
| 3G (UMTS) | Average | Suburban/Urban | Average |
| 3.5G (Wimax, LTE) | High | Suburban/Urban | Average |
| 4G (Wimax-ver2 LTE Advance) | High | Rural/Suburban/Urban | High |
| 5G | Very high | Rural/suburban/Urban | Very high |
| VANET | High | Urban | High |
| Zigbee | Low | Rural/suburban/Urban | Low |
| Bluetooth | Low | Rural/Suburban/Urban | Low |
| Wi-Fi | High | Suburban/Urban | Low |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alenoghena, C.O.; Onumanyi, A.J.; Ohize, H.O.; Adejo, A.O.; Oligbi, M.; Ali, S.I.; Okoh, S.A. eHealth: A Survey of Architectures, Developments in mHealth, Security Concerns and Solutions. Int. J. Environ. Res. Public Health 2022, 19, 13071. https://doi.org/10.3390/ijerph192013071
Alenoghena CO, Onumanyi AJ, Ohize HO, Adejo AO, Oligbi M, Ali SI, Okoh SA. eHealth: A Survey of Architectures, Developments in mHealth, Security Concerns and Solutions. International Journal of Environmental Research and Public Health. 2022; 19(20):13071. https://doi.org/10.3390/ijerph192013071
Chicago/Turabian StyleAlenoghena, Caroline Omoanatse, Adeiza James Onumanyi, Henry Ohiani Ohize, Achonu Oluwole Adejo, Maxwell Oligbi, Shaibu Ibrahim Ali, and Supreme Ayewoh Okoh. 2022. "eHealth: A Survey of Architectures, Developments in mHealth, Security Concerns and Solutions" International Journal of Environmental Research and Public Health 19, no. 20: 13071. https://doi.org/10.3390/ijerph192013071
APA StyleAlenoghena, C. O., Onumanyi, A. J., Ohize, H. O., Adejo, A. O., Oligbi, M., Ali, S. I., & Okoh, S. A. (2022). eHealth: A Survey of Architectures, Developments in mHealth, Security Concerns and Solutions. International Journal of Environmental Research and Public Health, 19(20), 13071. https://doi.org/10.3390/ijerph192013071







