Intelligent One-Class Classifiers for the Development of an Intrusion Detection System: The MQTT Case Study
Abstract
1. Introduction
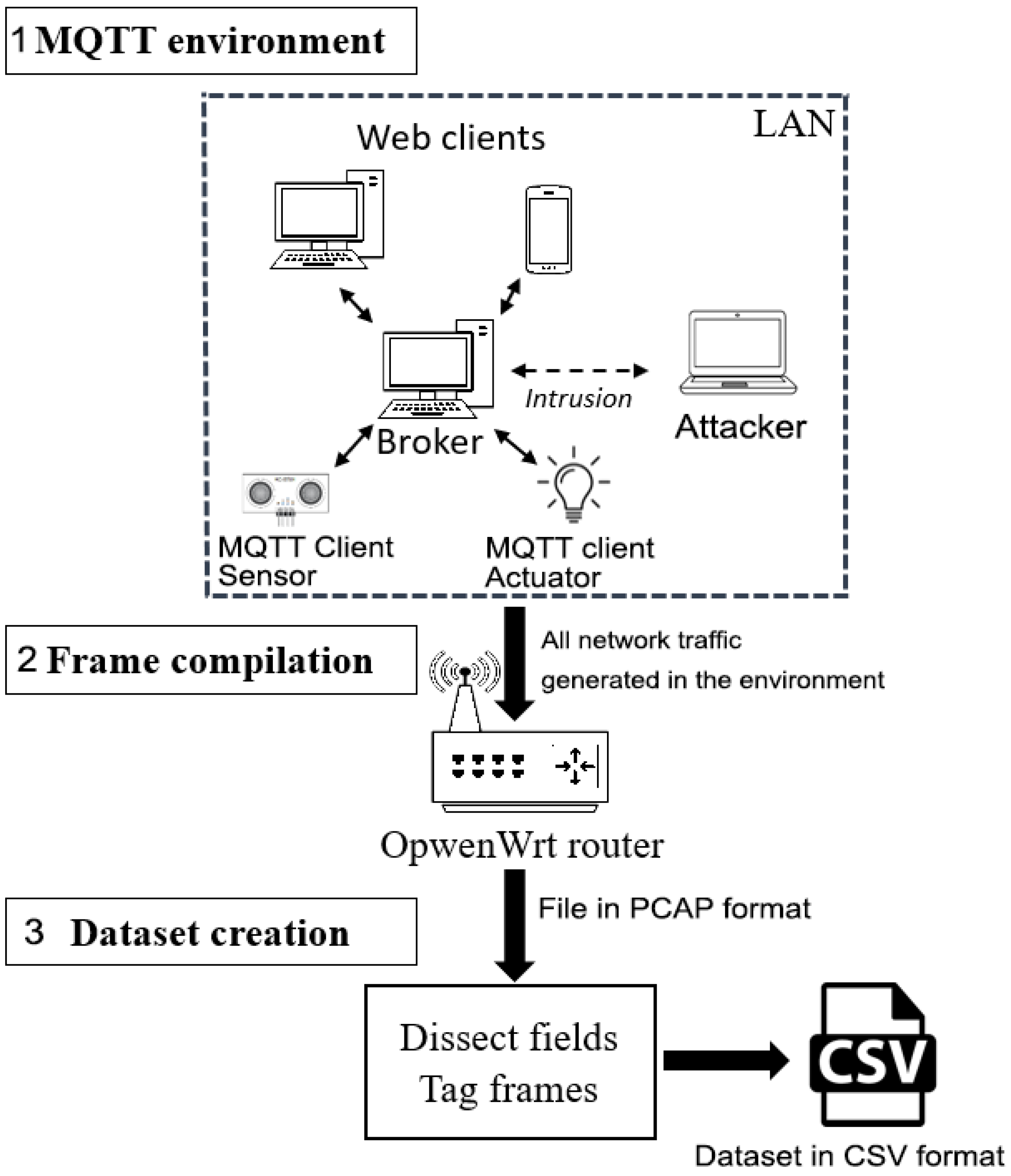
2. Case Study
- -
- Actuators and sensors: Comprised of two integrated boards NodeMCU, including a low-power micro controller connected to a wireless network via a ESP8266 chip [41]. The NodeMCU chip is connected to a HC-SR04 ultrasonic sensor, which subscribes to the topic “distance/ultrasonic1”, where it publishes the distance to any element in front of it, up to a range of 40 centimetres. The other NodeMCU is connected to an actuator consisting of a relay that turns a desk light on and off, subscribes to the topic “light/relay”, and, depending on the value, changes the state to “0” off, “1” on.
- -
- The server: Developed in node.js due to its efficiency in controlling multiple and simultaneous connections, with the npm package manager, which has installed the “Aedes’ ’library [42], with which a MQTT broker server has been programmed. The server also hosts the client web application.
- -
- Web application:Developed using angular.js, which connects to the broker as another client with the angular-MQTT library. The difference is that it implements web sockets instead of the MQTT protocol for the communication with the broker. The web application has an interface that shows the status of the different devices and allows for interaction with them in real time.
- -
- System clients: A PC and a smartphone interacting with the sensors through the web app connected via WiFi while generating network traffic.
3. Intrusion Detection Classifier
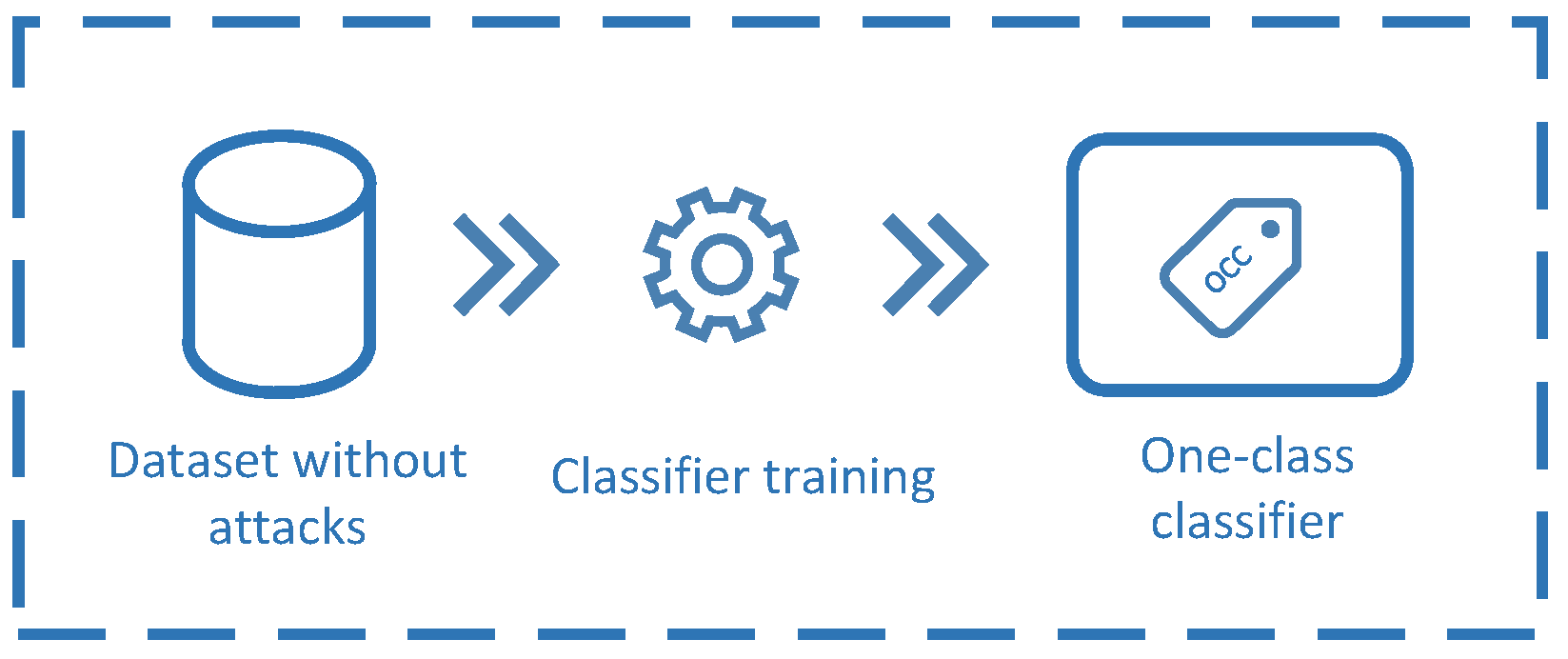
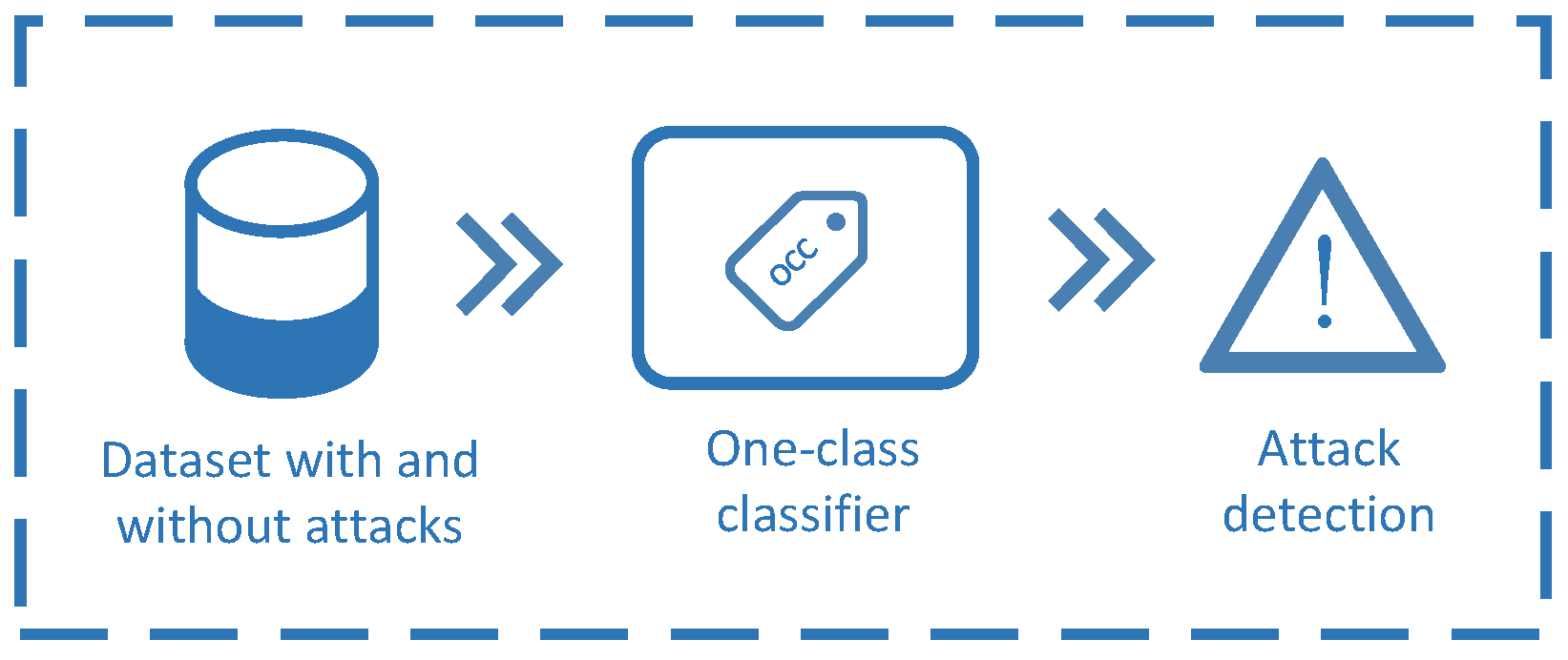
3.1. Classifier Approach
- The target set comprised only of legitimate samples is divided into 10 random groups:
- for i = 1:1:10
- The mean value from the 10 iterations is used as a measure of the classifier performance.
- Finally, the classifier’s performance is best selected and trained with all the target samples.
3.2. Methods
3.2.1. Approximate Convex Hull
3.2.2. Non-Convex Boundary over Projections
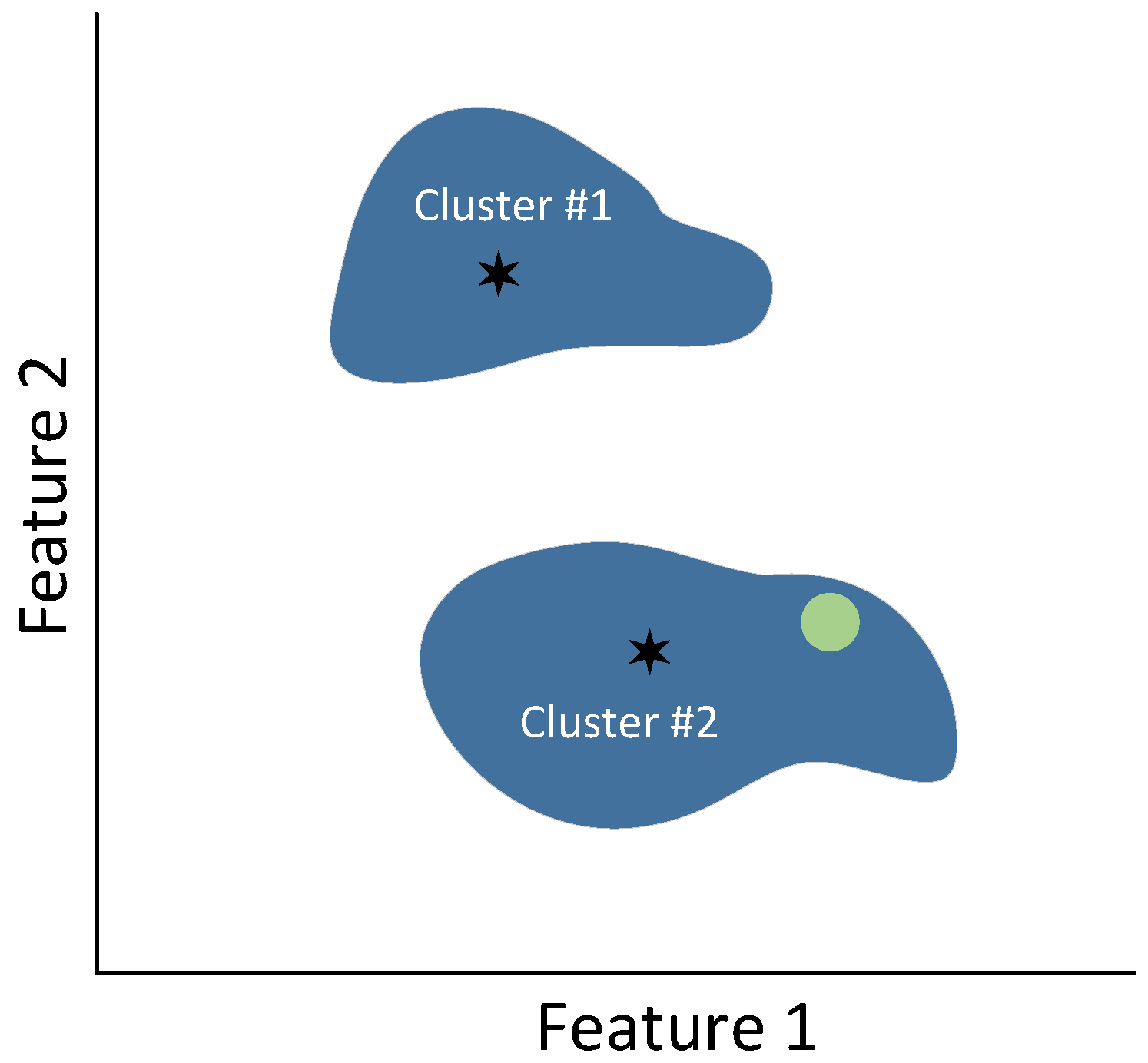
3.2.3. K-Means
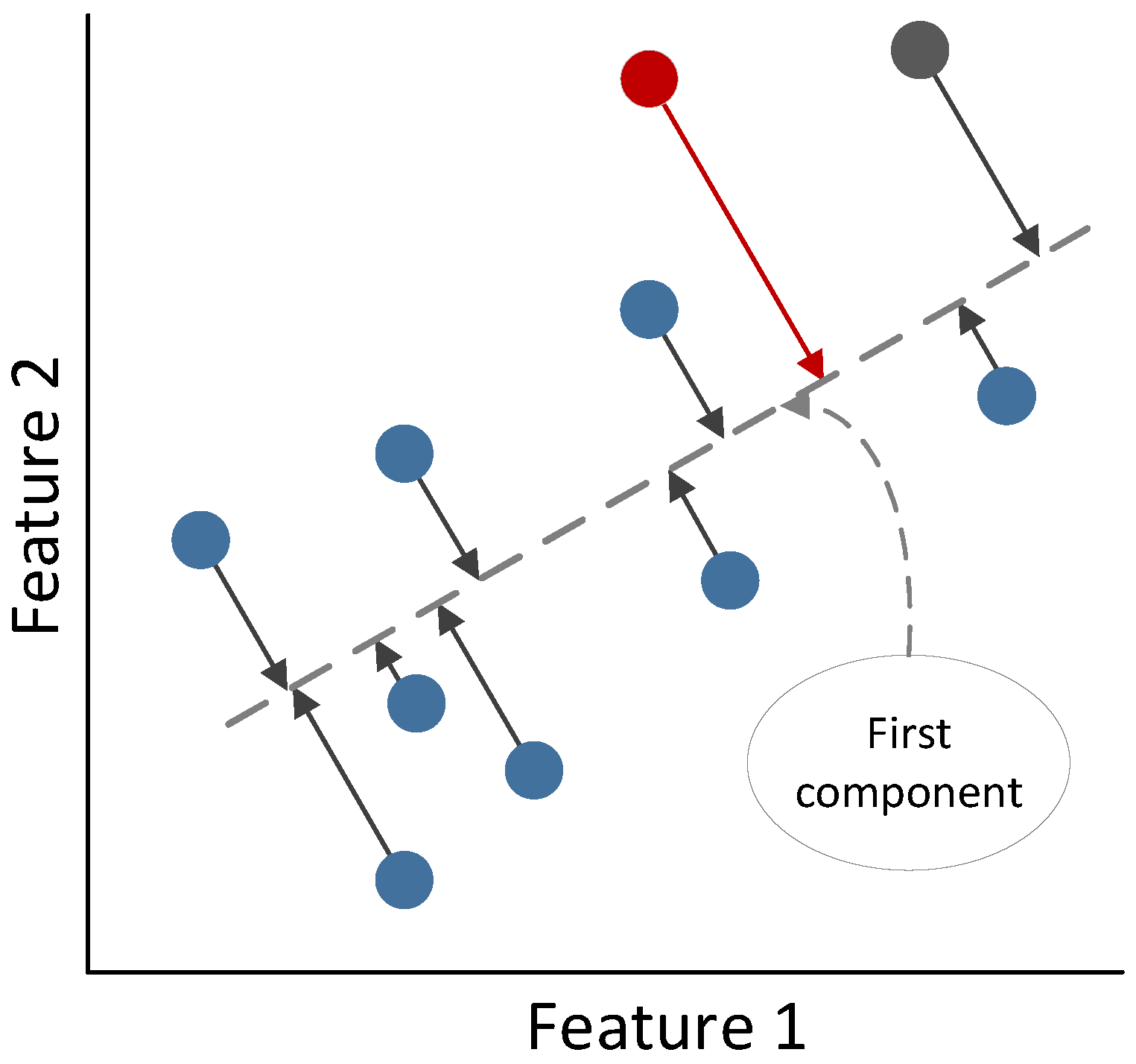
3.2.4. Principal Component Analysis
3.2.5. One-Class Support Vector Machine
4. Experiments and Results
4.1. Experiments Setup
4.1.1. Techniques Configuration
- ACH and NCBoP: Values for projections checked [10, 50, 100, 500].Values for the parameter in order to further evaluate restriction limits: [0.8, 0.9, 1, 1.1, 1].
- K-means: Number of clusters to divide the dataset into [1–15].Values defined for the outlier percentage in the training data: [0, 5, 10, 15, 20, 25].
- PCA: The amount of main components ranges from 1 to , with n being the number of variables in the training set. The K-means algorithm outlier fraction is taken into consideration as well.
- SVM: An outlier percentage is also considered, similarly to the K-means and PCA cases.
4.1.2. Data Pre-Processing
4.1.3. Performance Measurement
4.2. Results
5. Conclusions and Futures Works
Author Contributions
Funding
Conflicts of Interest
References
- Green, J. The Internet of Things Reference Model. In Internet of Things World Forum; CISCO: San Jose, CA, USA, 2014; pp. 1–12. [Google Scholar]
- Ramamoorthy, K.; Karthikeyan, S.; Chelladurai, T. An investigation on Industrial Internet of Things for Mission Critical things in Industry 4.0.2. Literature Review. Seybold Rep. 2020, 15, 3294–3300. [Google Scholar]
- Wollschlaeger, M.; Sauter, T.; Jasperneite, J. The Future of Industrial Communication. IEEE Ind. Electron. Mag. 2017, 11, 17–27. [Google Scholar] [CrossRef]
- Jove, E.; Casteleiro-Roca, J.L.; Quintián, H.; Méndez-Pérez, J.A.; Calvo-Rolle, J.L. Virtual Sensor for Fault Detection, Isolation and Data Recovery for Bicomponent Mixing Machine Monitoring. Informatica 2019, 30, 671–687. [Google Scholar] [CrossRef]
- Hamid, H.; Noor, R.M.; Omar, S.N.; Ahmedy, I.; Anjum, S.S.; Shah, S.A.A.; Kaur, S.; Othman, F.; Tamil, E.M. IoT-based botnet attacks systematic mapping study of literature. Scientometrics 2021, 126, 2759–2800. [Google Scholar] [CrossRef]
- Al-sarawi, S.; Anbar, M.; Alieyan, K.; Alzubaidi, M. Internet of Things (IoT) Communication Protocols: Review. In Proceedings of the 2017 8th International Conference on Information Technology (ICIT), Amman, Jordan, 17–18 May 2017; pp. 685–690. [Google Scholar]
- Alobaidy, H.A.H.; Mandeep, J.S.; Nordin, R.; Abdullah, N.F. A Review on ZigBee Based WSNs: Concepts, Infrastructure, Applications, and Challenges. Int. J. Electr. Electron. Eng. Telecommun. 2020, 9, 189–198. [Google Scholar] [CrossRef]
- Zorbas, D.; Abdelfadeel, K.; Kotzanikolaou, P.; Pesch, D. TS-LoRa: Time-slotted LoRaWAN for the Industrial Internet of Things. Comput. Commun. 2020, 153, 1–10. [Google Scholar] [CrossRef]
- Razzaq, M.A.; Gill, S.H.; Qureshi, M.A.; Ullah, S. Security Issues in the Internet of Things (IoT): A Comprehensive Study. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 383. [Google Scholar] [CrossRef]
- Ordóñez Galán, C.; Sánchez Lasheras, F.; de Cos Juez, F.J.; Bernardo Sánchez, A. Missing Data Imputation of Questionnaires by Means of Genetic Algorithms with Different Fitness Functions. J. Comput. Appl. Math. 2017, 311, 704–717. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Hamed, T.; Ernst, J.B.; Kremer, S.C. A Survey and Taxonomy of Classifiers of Intrusion Detection Systems. In Computer and Network Security Essentials; Springer: Berlin/Heidelberg, Germany, 2018; pp. 21–39. [Google Scholar]
- Perdisci, R.; Ariu, D.; Fogla, P.; Giacinto, G.; Lee, W. McPAD: A multiple classifier system for accurate payload-based anomaly detection. Comput. Netw. 2009, 53, 864–881. [Google Scholar] [CrossRef]
- Zhou, Q.; Pezaros, D. Evaluation of machine learning classifiers for Zero-Day intrusion detection—An analysis on CIC-AWS-2018 dataset. arXiv 2019, arXiv:1905.03685. [Google Scholar]
- Ben-Asher, N.; Gonzalez, C. Effects of cyber security knowledge on attack detection. Comput. Hum. Behav. 2015, 48, 51–61. [Google Scholar] [CrossRef]
- Prabha, K.; Sudha, S. A Survey on IPS Methods and Techniques. Int. J. Comput. Sci. Issues 2016, 13, 38–43. [Google Scholar] [CrossRef][Green Version]
- Samrin, R.; Vasumathi, D. Review on anomaly based network intrusion detection system. In Proceedings of the International Conference on Electrical, Electronics, Communication Computer Technologies and Optimization Techniques, ICEECCOT 2017, Mysuru, India, 15–16 December 2018; pp. 141–147. [Google Scholar] [CrossRef]
- Hasan, M.; Nasser, M.; Pal, B.; Ahmad, S. Support Vector Machine and Random Forest Modeling for Intrusion Detection System (IDS). J. Intell. Learn. Syst. Appl. 2014, 2014, 45–52. [Google Scholar] [CrossRef]
- Nieto, P.G.; Fernández, J.A.; Lasheras, F.S.; de Cos Juez, F.; Muñiz, C.D. A new improved study of cyanotoxins presence from experimental cyanobacteria concentrations in the Trasona reservoir (Northern Spain) using the MARS technique. Sci. Total Environ. 2012, 430, 88–92. [Google Scholar] [CrossRef]
- Chakrabarty, B.; Chanda, O.; Saiful, M. Anomaly based Intrusion Detection System using Genetic Algorithm and K-Centroid Clustering. Int. J. Comput. Appl. 2017, 163, 13–17. [Google Scholar] [CrossRef]
- Tao, X.; Kong, D.; Wei, Y.; Wang, Y. A Big Network Traffic Data Fusion Approach Based on Fisher and Deep Auto-Encoder. Information 2016, 7, 20. [Google Scholar] [CrossRef]
- Li, Y.; Ma, R.; Jiao, R. A hybrid malicious code detection method based on deep learning. Int. J. Secur. Its Appl. 2015, 9, 205–216. [Google Scholar] [CrossRef]
- Nieto, P.G.; Torres, J.M.; de Cos Juez, F.J.; Lasheras, F.S. Using multivariate adaptive regression splines and multilayer perceptron networks to evaluate paper manufactured using Eucalyptus globulus. Appl. Math. Comput. 2012, 219, 755–763. [Google Scholar]
- Alaiz-Moreton, H.; Aveleira-Mata, J.; Ondicol-Garcia, J.; Muñoz-Castañeda, A.L.; García, I.; Benavides, C. Multiclass Classification Procedure for Detecting Attacks on MQTT-IoT Protocol. Complexity 2019, 2019, 6516253. [Google Scholar] [CrossRef]
- Kim, J.; Kim, J.; Thu, H.L.T.; Kim, H. Long Short Term Memory Recurrent Neural Network Classifier for Intrusion Detection. In Proceedings of the 2016 International Conference on Platform Technology and Service (PlatCon), Jeju, Korea, 15–17 February 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Pajouh, H.H.; Javidan, R.; Khayami, R.; Dehghantanha, A.; Choo, K.K.R. A Two-Layer Dimension Reduction and Two-Tier Classification Model for Anomaly-Based Intrusion Detection in IoT Backbone Networks. IEEE Trans. Emerg. Top. Comput. 2019, 7, 314–323. [Google Scholar] [CrossRef]
- Liu, J.; Kantarci, B.; Adams, C. Machine learning-driven intrusion detection for Contiki-NG-based IoT networks exposed to NSL-KDD dataset. In Proceedings of the WiseML 2020-Proceedings of the 2nd ACM Workshop on Wireless Security and Machine Learning, Linz, Austria, 13 July 2020; pp. 25–30. [Google Scholar] [CrossRef]
- Thakkar, A.; Lohiya, R. A Review on Machine Learning and Deep Learning Perspectives of IDS for IoT: Recent Updates, Security Issues, and Challenges; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar] [CrossRef]
- Da Costa, K.A.; Papa, J.P.; Lisboa, C.O.; Munoz, R.; de Albuquerque, V.H.C. Internet of Things: A survey on machine learning-based intrusion detection approaches. Comput. Netw. 2019, 151, 147–157. [Google Scholar] [CrossRef]
- Alsakran, F.; Bendiab, G.; Shiaeles, S.; Kolokotronis, N. Intrusion Detection Systems for Smart Home IoT Devices: Experimental Comparison Study. In Communications in Computer and Information Science; CCIS; Springer: Singapore, 2020; Volume 1208, pp. 87–98. [Google Scholar] [CrossRef]
- OASIS (Organization for the Advancement of Structured Information Standards). MQTT, Version 3.1.1. 2014. Available online: https://docs.oasis-open.org/mqtt/mqtt/v3.1.1/os/mqtt-v3.1.1-os.html (accessed on 1 December 2021).
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Towards generating real-life datasets for network intrusion detection. Int. J. Netw. Secur. 2015, 17, 683–701. [Google Scholar]
- Stolfo, S.J. KDD Cup 1999 Dataset. 1999. Available online: https://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html (accessed on 1 December 2021).
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Gritzalis, S. Intrusion detection in 802.11 networks: Empirical evaluation of threats and a public dataset. IEEE Commun. Surv. Tutor. 2016, 18, 184–208. [Google Scholar] [CrossRef]
- Jove, E.; Casteleiro-Roca, J.L.; Quintián, H.; Méndez-Pérez, J.A.; Calvo-Rolle, J.L. A new method for anomaly detection based on non-convex boundaries with random two-dimensional projections. Inf. Fusion 2021, 65, 50–57. [Google Scholar] [CrossRef]
- Sethi, P.; Sarangi, S.R. Internet of Things: Architectures, Protocols, and Applications. J. Electr. Comput. Eng. 2017, 2017, 9324035. [Google Scholar] [CrossRef]
- Gupta, A.B.R. MQTT version 3.1.1. OASIS Standard. 2014. Available online: https://www.oasis-open.org/ (accessed on 1 December 2021).
- Andy, S.; Rahardjo, B.; Hanindhito, B. Attack scenarios and security analysis of MQTT communication protocol in IoT system. In Proceedings of the 2017 4th International Conference on Electrical Engineering, Computer Science and Informatics (EECSI), Yogyakarta, Indonesia, 19–21 September 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Dinculeană, D.; Cheng, X. Vulnerabilities and Limitations of MQTT Protocol Used between IoT Devices. Appl. Sci. 2019, 9, 848. [Google Scholar] [CrossRef]
- NodeMCU. NodeMCU—An Open-Source Firmware Based on ESP8266 Wifi-Soc. 2014. Available online: https://nodemcu.readthedocs.io/en/release/ (accessed on 1 December 2021).
- aedes. GitHub-moscajs/aedes: Barebone MQTT Broker That Can Run on any Stream Server, the Node Way. Available online: https://github.com/moscajs/aedes (accessed on 1 December 2021).
- Light, R.A. Mosquitto: Server and client implementation of the MQTT protocol. J. Open Source Softw. 2017, 2, 265. [Google Scholar] [CrossRef]
- openwrt. openwrt.org. Available online: https://openwrt.org/ (accessed on 1 December 2021).
- Casale, P.; Pujol, O.; Radeva, P. Approximate convex hulls family for one-class classification. In International Workshop on Multiple Classifier Systems; Springer: Berlin/Heidelberg, Germany, 2011; pp. 106–115. [Google Scholar]
- Jove, E.; Casteleiro-Roca, J.L.; Quintián, H.; Simić, D.; Méndez-Pérez, J.A.; Luis Calvo-Rolle, J. Anomaly detection based on one-class intelligent techniques over a control level plant. Logic J. IGPL 2020, 28, 502–518. [Google Scholar] [CrossRef]
- Jove, E.; López, J.A.V.; Fernández-Ibáñez, I.; Casteleiro-Roca, J.L.; Calvo-Rolle, J.L. Hybrid intelligent system to predict the individual academic performance of engineering students. Int. J. Eng. Educ. 2018, 34, 895–904. [Google Scholar]
- Jove, E.; Casteleiro-Roca, J.L.; Quintián, H.; Zayas-Gato, F.; Vercelli, G.; Calvo-Rolle, J.L. A One-class Classifier Based on a Hybrid Topology to Detect Faults in Power Cells. Log. J. IGPL 2021, 13, 801. [Google Scholar] [CrossRef]
- Wu, J.; Zhang, X. A PCA classifier and its application in vehicle detection. In Proceedings of the IJCNN’01. International Joint Conference on Neural Networks. Proceedings (Cat. No. 01CH37222), Washington, DC, USA, 15–19 July 2001; Volume 1, pp. 600–604. [Google Scholar]
- Jove, E.; Casteleiro-Roca, J.L.; Quintián, H.; Méndez-Pérez, J.A.; Calvo-Rolle, J.L. A fault detection system based on unsupervised techniques for industrial control loops. Expert Syst. 2019, 36, e12395. [Google Scholar] [CrossRef]
- Jove, E.; Casteleiro-Roca, J.L.; Quintián, H.; Méndez-Pérez, J.A.; Calvo-Rolle, J.L. Anomaly detection based on intelligent techniques over a bicomponent production plant used on wind generator blades manufacturing. Rev. Iberoam. Autom. Inform. Ind. 2020, 17, 84–93. [Google Scholar] [CrossRef]
- Jove, E.; Aláiz-Moretón, H.; Casteleiro-Roca, J.L.; Corchado, E.; Calvo-Rolle, J.L. Modeling of bicomponent mixing system used in the manufacture of wind generator blades. In International Conference on Intelligent Data Engineering and Automated Learning; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8669, pp. 275–285. [Google Scholar]
- Li, K.L.; Huang, H.K.; Tian, S.F.; Xu, W. Improving one-class SVM for anomaly detection. In Proceedings of the 2003 International Conference on Machine Learning and Cybernetics (IEEE Cat. No.03EX693), Xi’an, China, 5 November 2003; Volume 5, pp. 3077–3081. [Google Scholar]
- Quintián, H.; Corchado, E. Beta scale invariant map. Eng. Appl. Artif. Intell. 2017, 59, 218–235. [Google Scholar] [CrossRef]
- Shalabi, L.A.; Shaaban, Z. Normalization as a Preprocessing Engine for Data Mining and the Approach of Preference Matrix. In Proceedings of the 2006 International Conference on Dependability of Computer Systems, Szklarska Poreba, Poland, 25–27 May 2006; pp. 207–214. [Google Scholar] [CrossRef]
- Bradley, A.P. The use of the area under the ROC curve in the evaluation of machine learning algorithms. Pattern Recognit. 1997, 30, 1145–1159. [Google Scholar] [CrossRef]
- Fawcett, T. An introduction to ROC analysis. Pattern Recognit. Lett. 2006, 27, 861–874. [Google Scholar] [CrossRef]

| Technique | Features | Normalization | AUC (%) | Time (s) |
|---|---|---|---|---|
| ACH | 500 projections = 1 | Zscore | 52.063 | 3.11 |
| NCBoP | 500 projections = 1 | No | 60.317 | 1211.73 |
| K-means | Clusters = 10 Outlier Fraction = 15% | No | 76.496 | 0.84 |
| PCA | Components = 15 Outlier Fraction = 20% | 0-1 | 89.296 | 0.21 |
| SVM | Outlier Fraction = 0% | No | 69.235 | 285.56 |
| Technique | Features | Normalization | AUC (%) | Time (s) |
|---|---|---|---|---|
| ACH | 100 projections = 1 | No | 89.564 | 0.33 |
| NCBoP | 500 projections = 1 | No | 90.317 | 2211.73 |
| K-means | Clusters = 6 Outlier Fraction = 10% | No | 91.696 | 0.48 |
| PCA | Components = 8 Outlier Fraction = 10% | ZScore | 92.628 | 0.27 |
| SVM | Outlier Fraction = 10% | 0–1 | 79.588 | 313.08 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jove, E.; Aveleira-Mata, J.; Alaiz-Moretón, H.; Casteleiro-Roca, J.-L.; Marcos del Blanco, D.Y.; Zayas-Gato, F.; Quintián, H.; Calvo-Rolle, J.L. Intelligent One-Class Classifiers for the Development of an Intrusion Detection System: The MQTT Case Study. Electronics 2022, 11, 422. https://doi.org/10.3390/electronics11030422
Jove E, Aveleira-Mata J, Alaiz-Moretón H, Casteleiro-Roca J-L, Marcos del Blanco DY, Zayas-Gato F, Quintián H, Calvo-Rolle JL. Intelligent One-Class Classifiers for the Development of an Intrusion Detection System: The MQTT Case Study. Electronics. 2022; 11(3):422. https://doi.org/10.3390/electronics11030422
Chicago/Turabian StyleJove, Esteban, Jose Aveleira-Mata, Héctor Alaiz-Moretón, José-Luis Casteleiro-Roca, David Yeregui Marcos del Blanco, Francisco Zayas-Gato, Héctor Quintián, and José Luis Calvo-Rolle. 2022. "Intelligent One-Class Classifiers for the Development of an Intrusion Detection System: The MQTT Case Study" Electronics 11, no. 3: 422. https://doi.org/10.3390/electronics11030422
APA StyleJove, E., Aveleira-Mata, J., Alaiz-Moretón, H., Casteleiro-Roca, J.-L., Marcos del Blanco, D. Y., Zayas-Gato, F., Quintián, H., & Calvo-Rolle, J. L. (2022). Intelligent One-Class Classifiers for the Development of an Intrusion Detection System: The MQTT Case Study. Electronics, 11(3), 422. https://doi.org/10.3390/electronics11030422










