Clock Glitch Fault Attacks on Deep Neural Networks and Their Countermeasures
Abstract
1. Introduction
- We launch fault injection attacks on the output layer activation functions of two models: a multi-class classification model trained on the MNIST (10 digits) and CIFAR-10 datasets, and a binary classification model trained on the MNIST (two digits) and Kaggle (Dogs vs. Cats) datasets.
- Considering the practical feasibility of fault injection attacks, we conducted experiments by generating glitches outside the target device. Furthermore, we used a waveform pattern-matching algorithm based on the power consumption waveform at the attack point to determine the timing for the clock glitch injection.
- We implemented several classification DNN models on the target chip ARM Cortex-M4 STM32F303, and confirmed that these models are vulnerable to fault attacks.
- Considering that only a negligible computational overhead should be added, the proposed countermeasures effectively mitigate the attacks on Softmax and Sigmoid functions through additional detection processes at the algorithmic level.
2. Backgrounds and Methods on Fault Injection Attacks
2.1. The DNN Structure
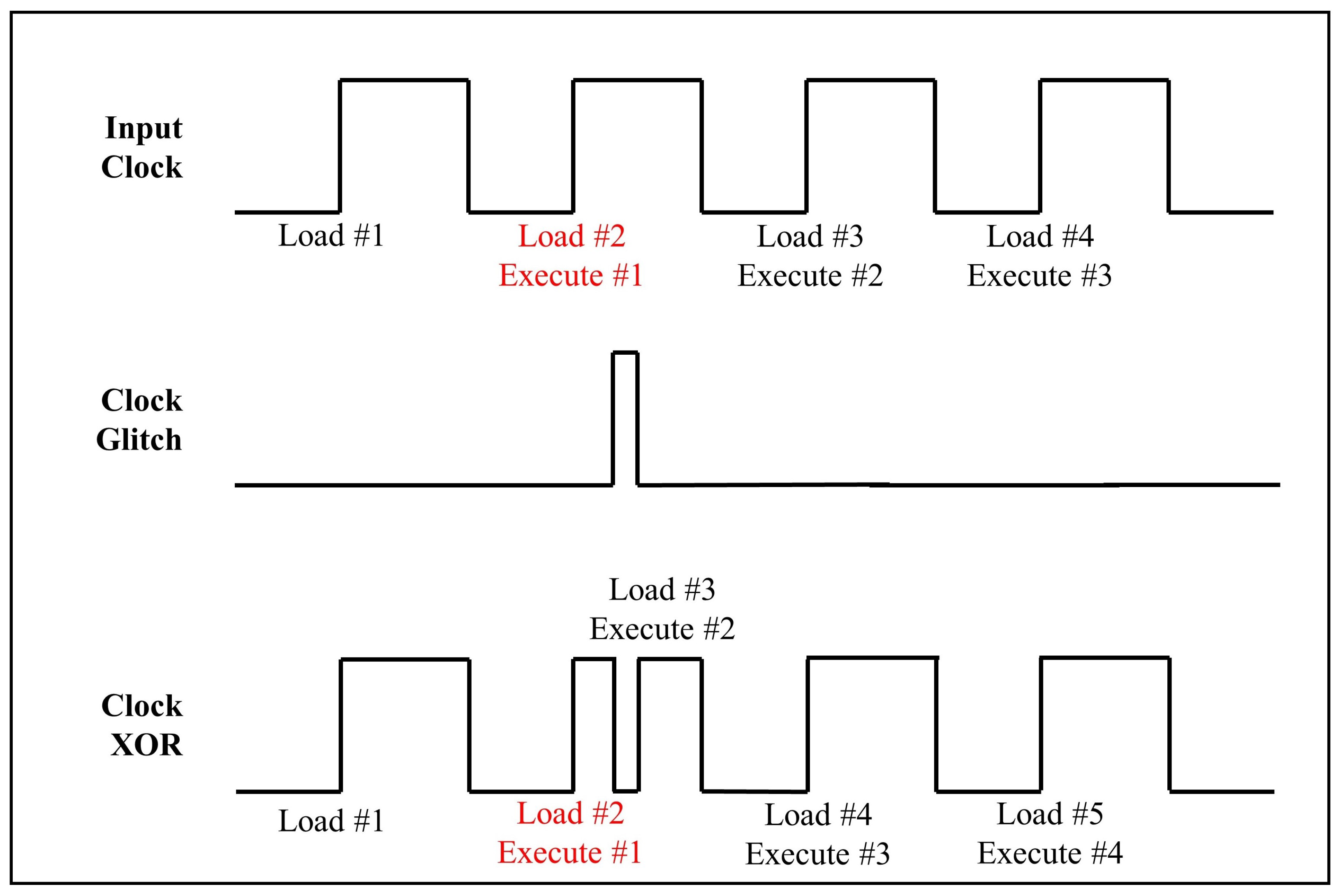
2.2. Fault Injections
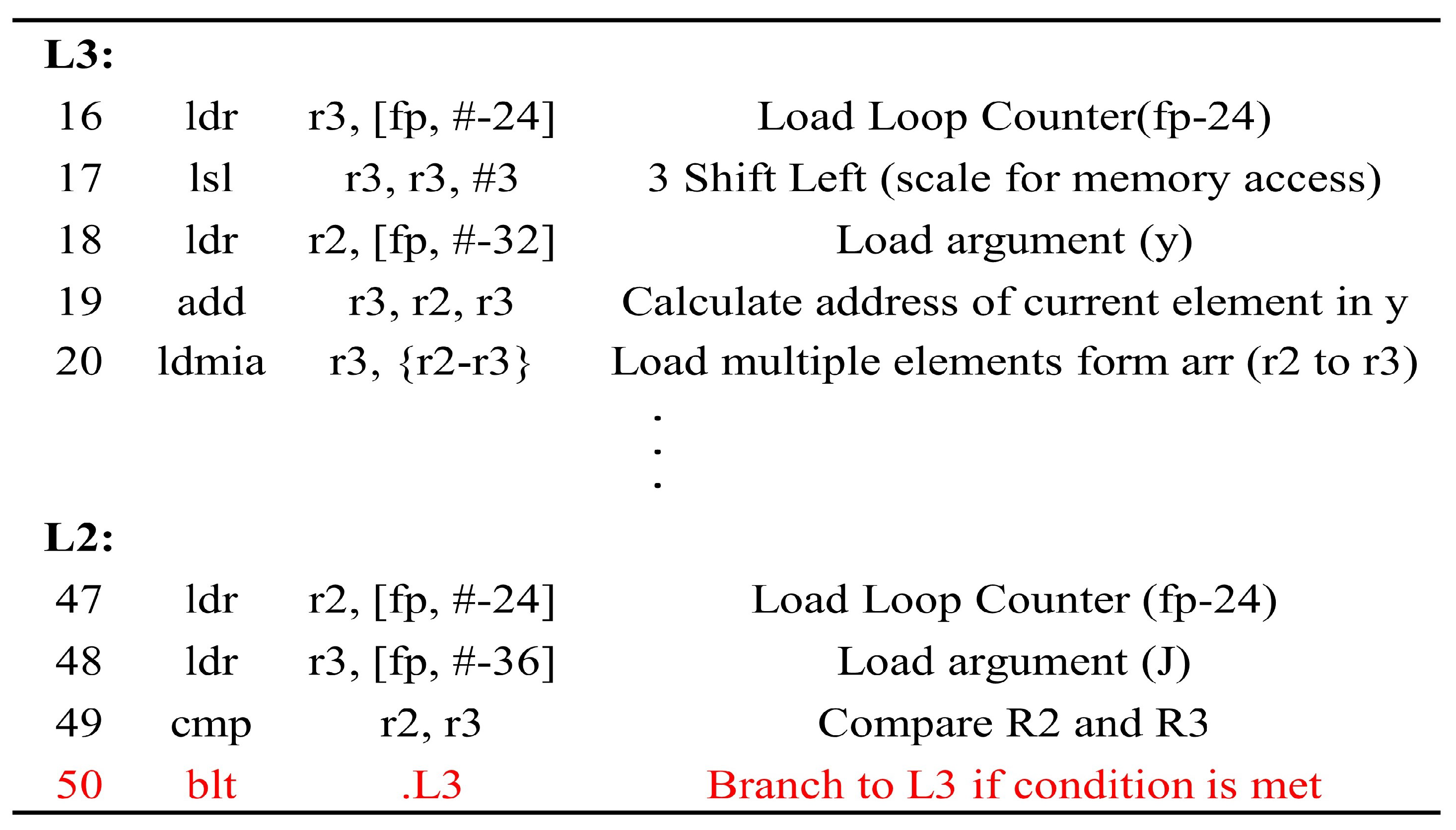
3. The Fault Injection Model
| Algorithm 1 The Softmax function |
| Require:
Ensure:
|
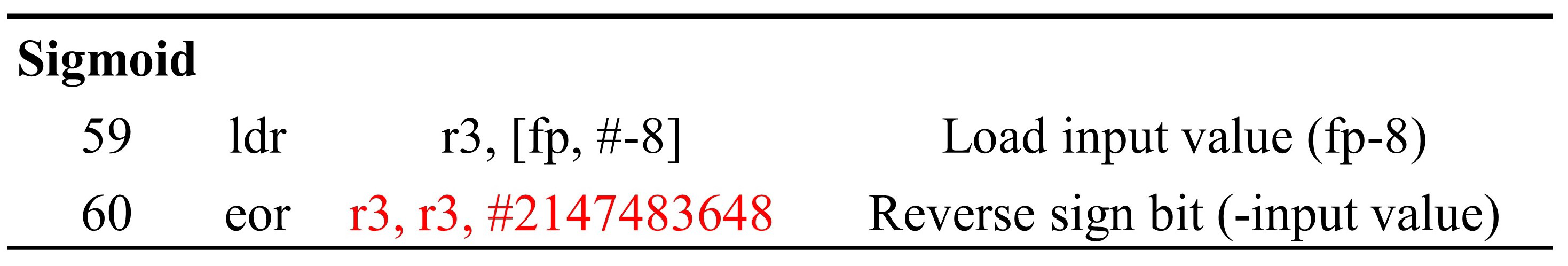
| Algorithm 2 The Sigmoid function. |
| Require: x Ensure: y
|
4. Clock Glitch Fault Attacks on a DNN
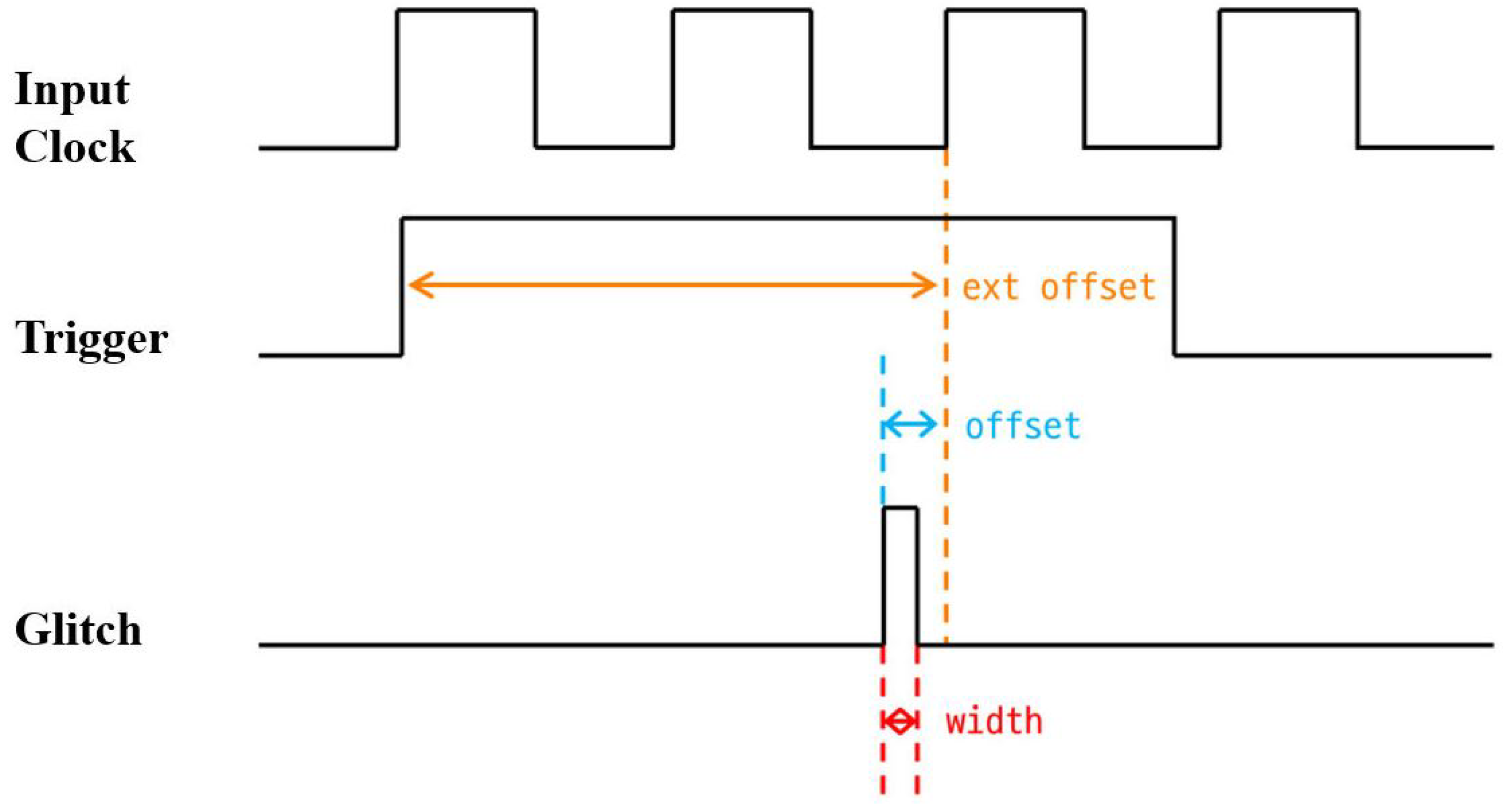
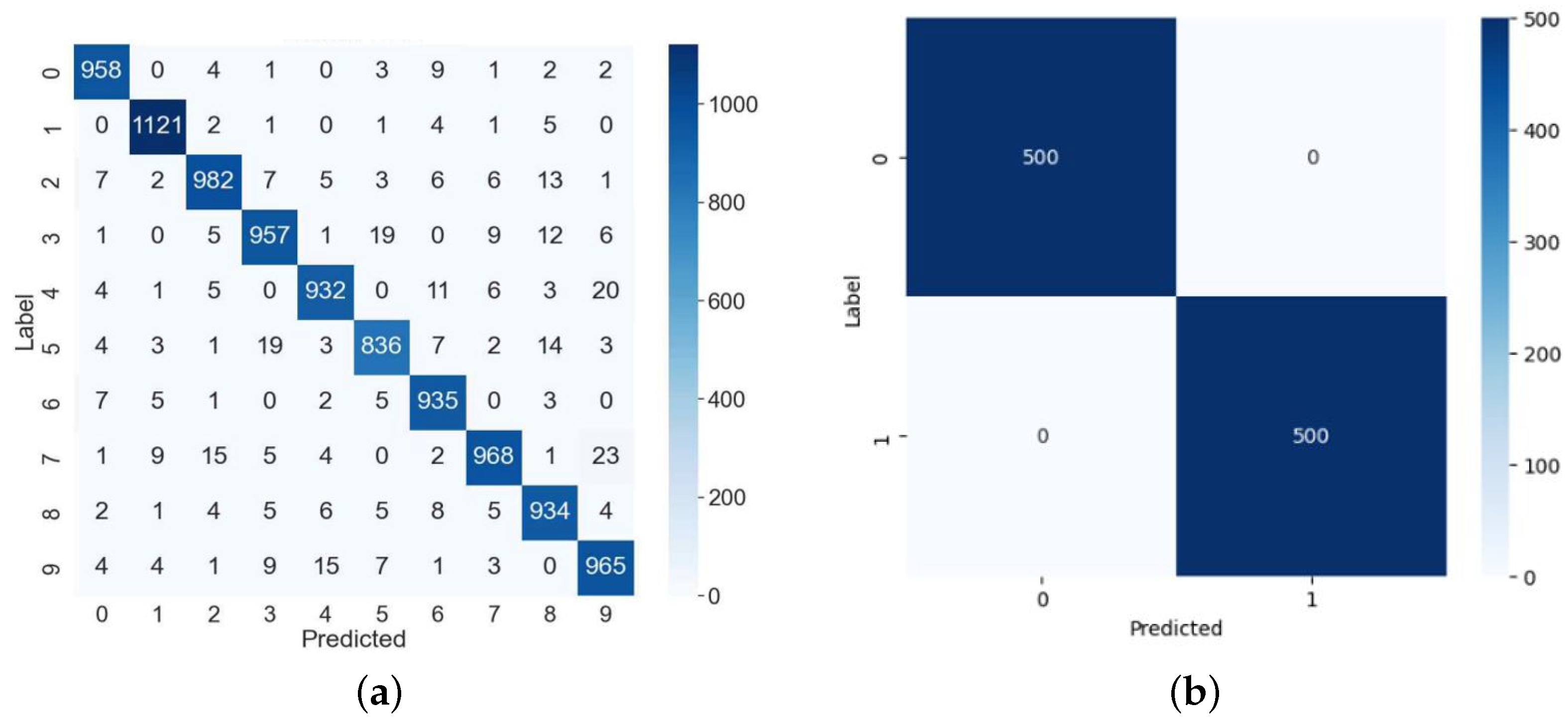
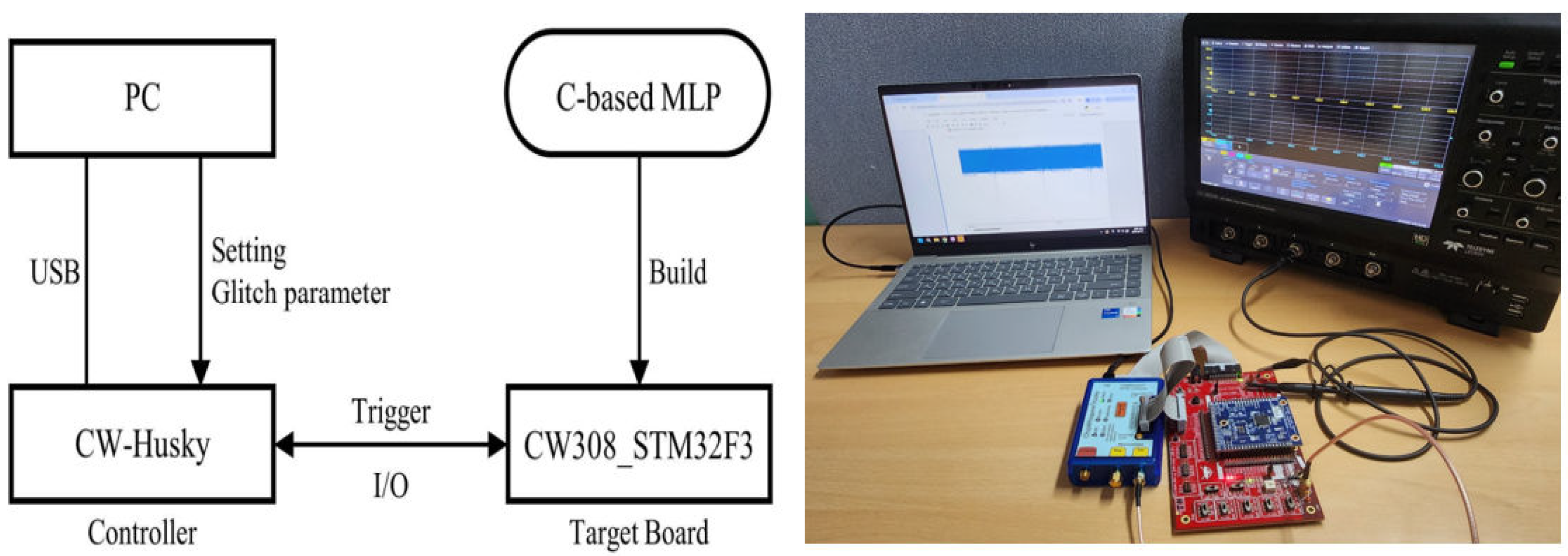
4.1. Experimental Setup
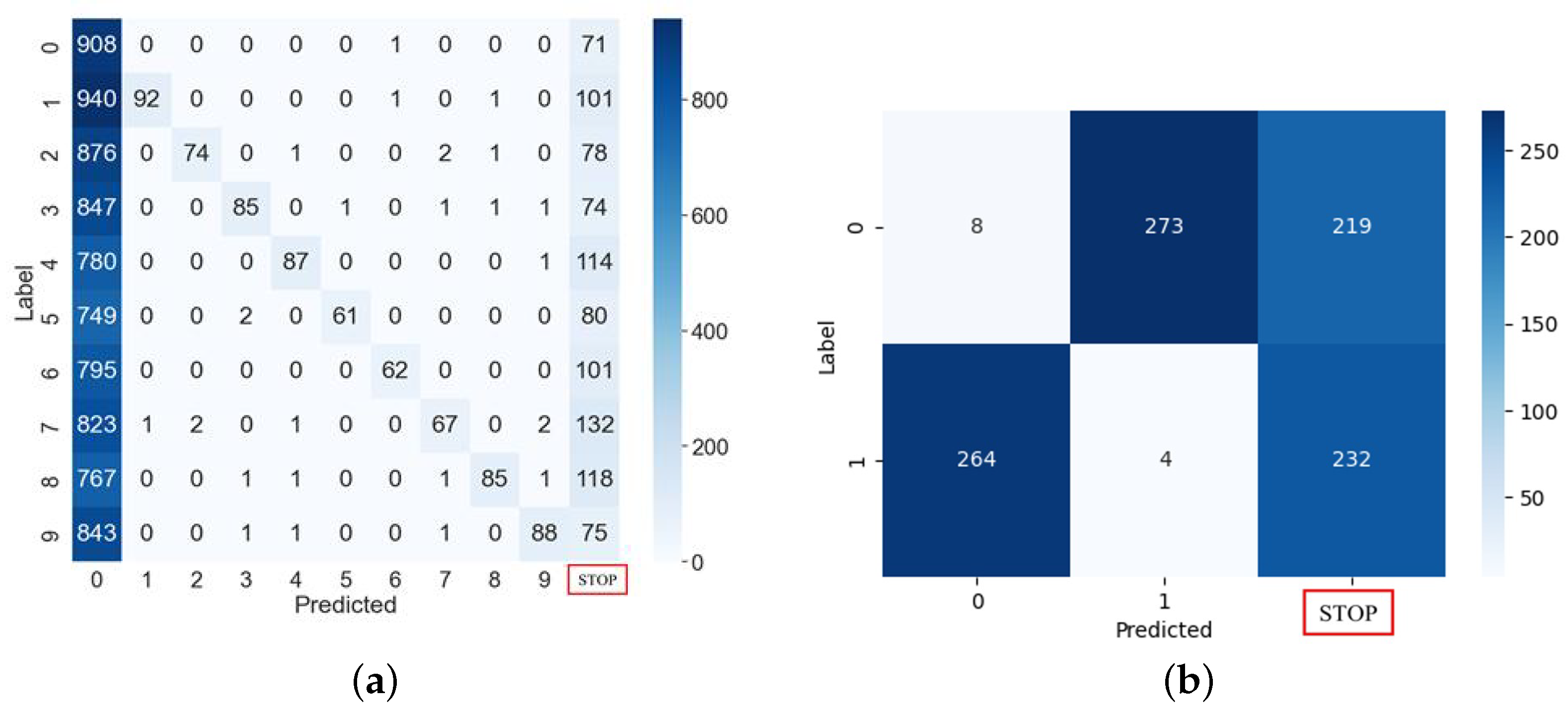
4.2. The Results of Clock Glitch Fault Injection
5. Countermeasure
5.1. Proposed Activation Algorithm
| Algorithm 3 The proposed Softmax function. |
| Require:
Ensure:
|
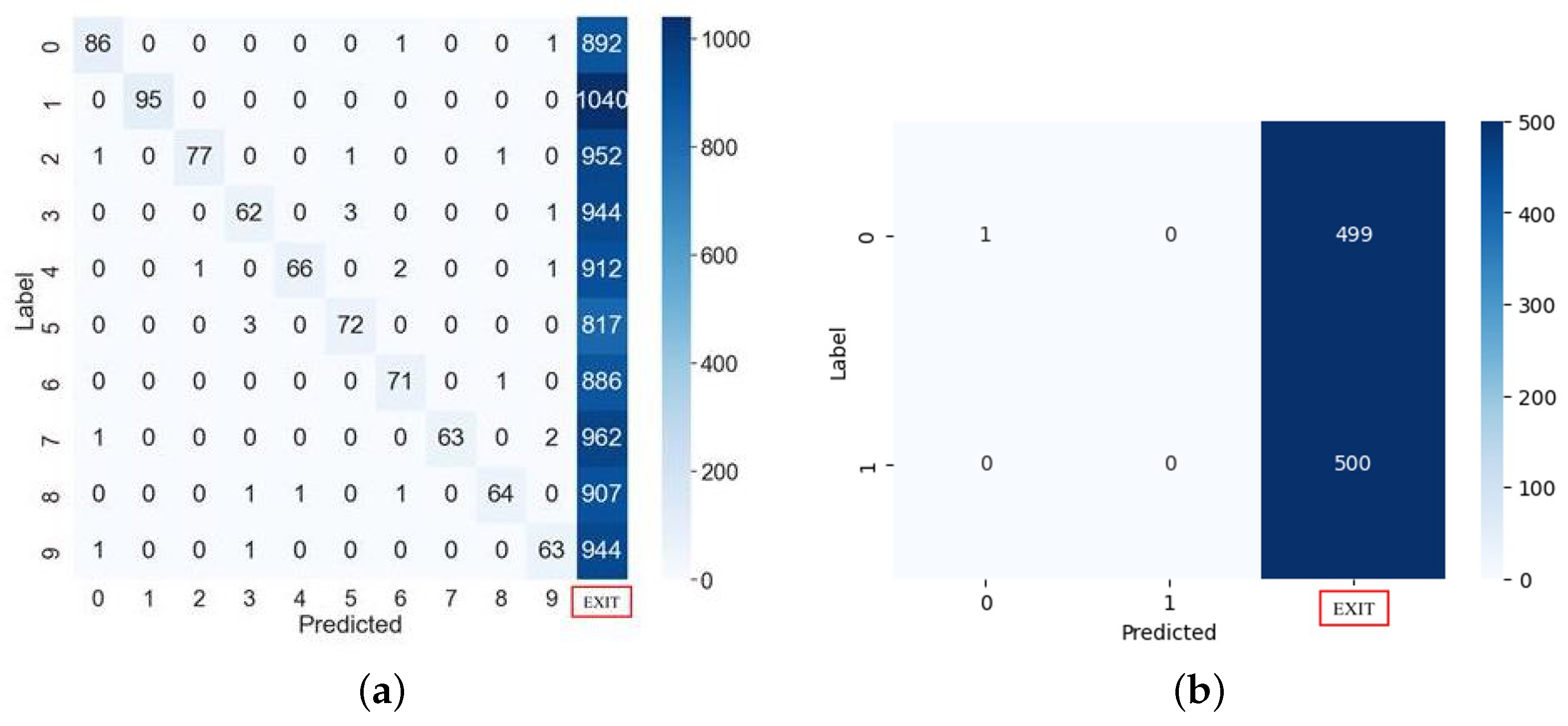
5.2. Fault Attacks on the Proposed Algorithm
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| CNN | convolution neural network |
| DNN | deep neural network |
| EM | electromagnetic |
| FPGA | field-programmable gate array |
| IoT | Internet of Things |
| MLP | multilayer perceptron |
References
- Khamaiseh, S.Y.; Bagagem, D.; Al-Alaj, A.; Mancino, M.; Alomari, H.W. Adversarial deep learning: A survey on adversarial attacks and defense mechanisms on image classification. IEEE Access 2022, 10, 102266–102291. [Google Scholar] [CrossRef]
- Zhu, W.; Ji, X.; Cheng, Y.; Zhang, S.; Xu, W. TPatch: A Triggered Physical Adversarial Patch. 2023, pp. 661–678. Available online: https://www.usenix.org/conference/usenixsecurity23/presentation/zhu (accessed on 1 January 2025).
- Zhang, C.; Xu, X.; Wu, J.; Liu, Z.; Zhou, L. Adversarial attacks of vision tasks in the past 10 years: A survey. arXiv 2024, arXiv:2410.23687. [Google Scholar]
- Liu, Y.; Dachman-Soled, D.; Srivastava, A. Mitigating reverse engineering attacks on deep neural networks. In Proceedings of the 2019 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Miami, FL, USA, 15–17 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 657–662. [Google Scholar] [CrossRef]
- Fang, Q.; Lin, L.; Zhang, H.; Wang, T.; Alioto, M. Voltage scaling-agnostic counteraction of side-channel neural net reverse engineering via machine learning compensation and multi-level shuffling. In Proceedings of the 2023 IEEE Symposium on VLSI Technology and Circuits (VLSI Technology and Circuits), Kyoto, Japan, 11–16 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–2. [Google Scholar] [CrossRef]
- Athanasiou, K.; Wahl, T.; Ding, A.A.; Fei, Y. Masking feedforward neural networks against power analysis attacks. Proc. Priv. Enhancing Technol. 2022, 2022, 501–521. [Google Scholar] [CrossRef]
- Wang, C.; Zhao, P.; Wang, S.; Lin, X. Detection and recovery against deep neural network fault injection attacks based on contrastive learning. arXiv 2021, arXiv:2401.16766. [Google Scholar]
- Javaheripi, M.; Koushanfar, F. Hashtag: Hash signatures for online detection of fault-injection attacks on deep neural networks. In Proceedings of the 2021 IEEE/ACM International Conference on Computer Aided Design (ICCAD), Munich, Germany, 1–4 November 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–9. [Google Scholar] [CrossRef]
- Nagarajan, K.; Li, J.; Ensan, S.S.; Kannan, S.; Ghosh, S. Fault injection attacks in spiking neural networks and countermeasures. Front. Nanotechnol. 2022, 3, 801999. [Google Scholar] [CrossRef]
- Hou, X.; Breier, J.; Jap, D.; Ma, L.; Bhasin, S.; Liu, Y. Physical security of deep learning on edge devices: Comprehensive evaluation of fault injection attack vectors. Microelectron. Reliab. 2021, 120, 114116. [Google Scholar] [CrossRef]
- Agoyan, M.; Dutertre, J.M.; Naccache, D.; Robisson, B.; Tria, A. When clocks fail: On critical paths and clock faults. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, Passau, Germany, 14–16 April 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 182–193. [Google Scholar] [CrossRef]
- Barenghi, A.; Bertoni, G.; Parrinello, E.; Pelosi, G. Low voltage fault attacks on the RSA cryptosystem. In Proceedings of the 2009 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Lausanne, Switzerland, 6 September 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 23–31. [Google Scholar] [CrossRef]
- Xagawa, K.; Ito, A.; Ueno, R.; Takahashi, J.; Homma, N. Fault-injection attacks against NIST’s post-quantum cryptography round 3 KEM candidates. In Proceedings of the Advances in Cryptology–ASIACRYPT 2021: 27th International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 6–10 December 2021; Proceedings, Part II 27. Springer: Berlin/Heidelberg, Germany, 2021; pp. 33–61. [Google Scholar]
- Breier, J.; Jap, D.; Chen, C.N. Laser profiling for the back-side fault attacks: With a practical laser skip instruction attack on AES. In Proceedings of the 1st ACM Workshop on Cyber-Physical System Security, Singapore, 14 April 2015; pp. 99–103. [Google Scholar] [CrossRef]
- Selmke, B.; Strieder, E.; Heyszl, J.; Freud, S.; Damm, T. Breaking black box crypto-devices using laser fault injection. In Proceedings of the International Symposium on Foundations and Practice of Security, Paris, France, 7–10 December 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 75–90. [Google Scholar]
- Dehbaoui, A.; Dutertre, J.M.; Robisson, B.; Orsatelli, P.; Maurine, P.; Tria, A. Injection of Transient Faults Using Electromagnetic Pulses Practical Results on a Cryptographic System. ACR Cryptology ePrint Archive. 2012. Available online: https://eprint.iacr.org/2012/123.pdf (accessed on 1 January 2025).
- Nishiyama, H.; Fujimoto, D.; Sone, H.; Hayashi, Y. Efficient Noninvasive Fault Injection Method Utilizing Intentional Electromagnetic Interference. IEEE Trans. Electromagn. Compat. 2023, 65, 1211–1219. [Google Scholar] [CrossRef]
- Boneh, D.; DeMillo, R.A.; Lipton, R.J. On the importance of checking cryptographic protocols for faults. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Konstanz, Germany, 11–15 May 1997; Springer: Berlin/Heidelberg, Germany, 1997; pp. 37–51. [Google Scholar] [CrossRef]
- Biham, E.; Shamir, A. Differential fault analysis of secret key cryptosystems. In Proceedings of the Advances in Cryptology—CRYPTO’97: 17th Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997; Proceedings 17. Springer: Berlin/Heidelberg, Germany, 1997; pp. 513–525. [Google Scholar] [CrossRef]
- Delarea, S.; Oren, Y. Practical, low-cost fault injection attacks on personal smart devices. Appl. Sci. 2022, 12, 417. [Google Scholar] [CrossRef]
- Nishiyama, H.; Fujimoto, D.; Hayashi, Y. Fault injection caused by phase-locked loop compromised with IEMI. IEEE Trans. Electromagn. Compat. 2024, 67, 538–544. [Google Scholar] [CrossRef]
- Liu, Y.; Wei, L.; Luo, B.; Xu, Q. Fault injection attack on deep neural network. In Proceedings of the 2017 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Irvine, CA, USA, 13–16 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 131–138. [Google Scholar] [CrossRef]
- Zhao, P.; Wang, S.; Gongye, C.; Wang, Y.; Fei, Y.; Lin, X. Fault sneaking attack: A stealthy framework for misleading deep neural networks. In Proceedings of the 56th Annual Design Automation Conference 2019, Las Vegas, NV, USA, 2–6 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Breier, J.; Hou, X.; Jap, D.; Ma, L.; Bhasin, S.; Liu, Y. Practical fault attack on deep neural networks. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 2204–2206. [Google Scholar] [CrossRef]
- Alam, M.M.; Tajik, S.; Ganji, F.; Tehranipoor, M.; Forte, D. RAM-Jam: Remote temperature and voltage fault attack on FPGAs using memory collisions. In Proceedings of the 2019 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Atlanta, GA, USA, 24 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 48–55. [Google Scholar] [CrossRef]
- Fukuda, Y.; Yoshida, K.; Fujino, T. Fault injection attacks utilizing waveform pattern matching against neural networks processing on microcontroller. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2022, 105, 300–310. [Google Scholar] [CrossRef]
- Ordoñez, J.; Yang, C. Derailed: Arbitrarily Controlling DNN Outputs with Targeted Fault Injection Attacks. In Proceedings of the 2024 Design, Automation & Test in Europe Conference & Exhibition (DATE), Lyon, France, 31 March–2 April 2025; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar]
- Das, S.; Bhattacharya, S.; Kundu, S.; Kundu, S.; Menon, A.; Raha, A.; Basu, K. AttentionBreaker: Adaptive Evolutionary Optimization for Unmasking Vulnerabilities in LLMs through Bit-Flip Attacks. arXiv 2024, arXiv:2411.13757. [Google Scholar]
- Beckers, A.; Balasch, J.; Gierlichs, B.; Verbauwhede, I. Design and Implementation of a Waveform-Matching Based Triggering System. Lect. Notes Comput. Sci. 2016, 9689, 184–198. [Google Scholar] [CrossRef]
- LeCun, Y.; Cortes, C.; Burges, C. MNIST Handwritten Digit Database. ATT Labs. 2010. Volume 2. Available online: http://yann.lecun.com/exdb/mnist (accessed on 1 February 2020).
- Liu, W.; Chang, C.H.; Zhang, F.; Lou, X. Imperceptible misclassification attack on deep learning accelerator by glitch injection. In Proceedings of the 2020 57th ACM/IEEE Design Automation Conference (DAC), Francisco, CA, USA, 20–24 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Kazemi, Z.; Papadimitriou, A.; Souvatzoglou, I.; Aerabi, E.; Ahmed, M.M.; Hely, D.; Beroulle, V. On a low cost fault injection framework for security assessment of cyber-physical systems: Clock glitch attacks. In Proceedings of the 2019 IEEE 4th International Verification and Security Workshop (IVSW), Rhodes Island, Greece, 1–3 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 7–12. [Google Scholar]
- Alshaer, I.; Al-Kaf, A.; Egloff, V.; Beroulle, V. Modeling Clock Glitch Fault Injection Effects on a RISC-V Microcontroller. In Proceedings of the 2024 IEEE 30th International Symposium on On-Line Testing and Robust System Design (IOLTS), Rennes, France, 3–5 July 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–3. [Google Scholar]
- Krizhevsky, A. Learning Multiple Layers of Features From Tiny Images. Technical Report. 2009. Available online: https://www.cs.toronto.edu/~kriz/learning-features-2009-TR.pdf (accessed on 1 February 2025).
- Rakin, A.S.; He, Z.; Fan, D. Bit-flip attack: Crushing neural network with progressive bit search. In Proceedings of the IEEE/CVF International Conference on Computer Vision, Seoul, Republic of Korea, 27 October–2 November 2019; pp. 1211–1220. [Google Scholar]



| Layer | Number of Neurons (Binary) | Activation Function (Binary) |
|---|---|---|
| Input layer | 784 | - |
| Hidden layer-1 | 64 | ReLU |
| Hidden layer-2 | 32 | ReLU |
| Output layer | 10 (1) | Softmax (Sigmoid) |
| Dataset | Accuracy | ||
|---|---|---|---|
| Normal | Attack | ||
| MLP | MNIST (10 digits, 0∼9) | 95.88% | 16.09% |
| InceptionNet | CIFAR-10 | 91.66% | 10.61% |
| ResNet | CIFAR-10 | 88.38% | 10.92% |
| VGGNet | CIFAR-10 | 93.30% | 10.00% |
| Dataset | Accuracy | ||
|---|---|---|---|
| Normal | Attack | ||
| MLP | MNIST (2 digits, 0 vs. 1) | 100% | 1.20% |
| InceptionNet | Kaggle (Dogs vs. Cats) | 96.25% | 1.10% |
| ResNet | Kaggle (Dogs vs. Cats) | 91.00% | 4.40% |
| VGGNet | Kaggle (Dogs vs. Cats) | 90.45% | 1.75% |
| Target | Method | Goal | Effect | |
|---|---|---|---|---|
| Bereir et al. [24] | Activation | Laser | Random | ≥50% |
| functions | injection | misclassification | Misclassification | |
| Khoshavi et al. [35] | Clock | Clock glitch | Accuracy | 20%∼80% accuracy |
| signal | degradation | degradation | ||
| Liu et al. [31] | Clock | Clock glitch | Misclassification | ≥98% |
| signal | Misclassification | |||
| Fukuda et al. [26] | Softmax | Clock glitch | Misclassification | |
| function | to class 0 | Accuracy | ||
| Ours | Softmax/Sigmoid | Clock glitch | Misclassification | |
| function | to class 0 or others | Accuracy |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, S.; Kim, S.; Hong, S.; Ha, J. Clock Glitch Fault Attacks on Deep Neural Networks and Their Countermeasures. Sensors 2025, 25, 2793. https://doi.org/10.3390/s25092793
Lee S, Kim S, Hong S, Ha J. Clock Glitch Fault Attacks on Deep Neural Networks and Their Countermeasures. Sensors. 2025; 25(9):2793. https://doi.org/10.3390/s25092793
Chicago/Turabian StyleLee, Sangwon, Suhyung Kim, Seongwoo Hong, and Jaecheol Ha. 2025. "Clock Glitch Fault Attacks on Deep Neural Networks and Their Countermeasures" Sensors 25, no. 9: 2793. https://doi.org/10.3390/s25092793
APA StyleLee, S., Kim, S., Hong, S., & Ha, J. (2025). Clock Glitch Fault Attacks on Deep Neural Networks and Their Countermeasures. Sensors, 25(9), 2793. https://doi.org/10.3390/s25092793







