Optimized Identity Authentication via Channel State Information for Two-Factor User Verification in Information Systems
Abstract
1. Introduction
| Methods | Patterns Utilized | Target Values | Accuracy | Strengths | Weaknesses |
|---|---|---|---|---|---|
| Gait-based methods [18,19] | CSI amplitude-phase from walking | User identities | 86.75% | Non-invasive, continuous authentication. | Requires fixed walking distance; sensitive to environmental changes. |
| Signature-based methods [13] | CSI fluctuations from handwriting | Signature authenticity | 79% | Integrates with passwords; no special hardware. | Accuracy affected by writing speed/angle. |
| Lip-movement-based methods [17] | Subtle CSI changes from speech | Spoken words/user IDs | 88.75% | Non-intrusive, covert. | Weak signal impact; noise-sensitive. |
| FWiA (Proposed) | CSI perturbations from keystrokes | User identities | 90.9% | Resistant to theft; enhanced by Fresnel zone. | Requires fixed string input; indoor dependency. |
| DeepCWiA (Proposed) | Multi-antenna phase variance | Continuous user IDs | 94.8% | No user action needed. | Requires multi-antenna setup; computational complexity. |
- Scalars and Variables: Lowercase italic letters (e.g., , , ) denote scalar values or variables, such as time , frequency , or noise . Uppercase italic letters (e.g., , , , ) represent integer constants or parameters, such as the number of transmitting antennas , receiving antennas , subcarriers , or time samples .
- Vectors and Matrices: Bold lowercase letters (e.g., , ) denote vectors. For instance, represents the Lagrangian multiplier vector in SVM optimization. Bold uppercase letters (e.g., , ) represent matrices. The CSI data stream is a complex matrix where is the number of subcarriers and is the number of time samples.
- Mathematical Sets: and denote the sets of real and complex numbers, respectively.
- Operators and Norms: The Euclidean norm is used for vector magnitude calculations, such as in SVM optimization. Statistical operators (e.g., var(⋅), ) denote variance and expectation, respectively.
- Special Functions and Indices: Subscripts (e.g., , ) index subcarriers, antennas, or time-dependent components. Superscripts (e.g., , ) indicate matrix transposition or optimal solutions.
2. Basic Theory
3. System Design
3.1. System Work Flow
3.2. Signal Processing
3.3. Feature Extraction
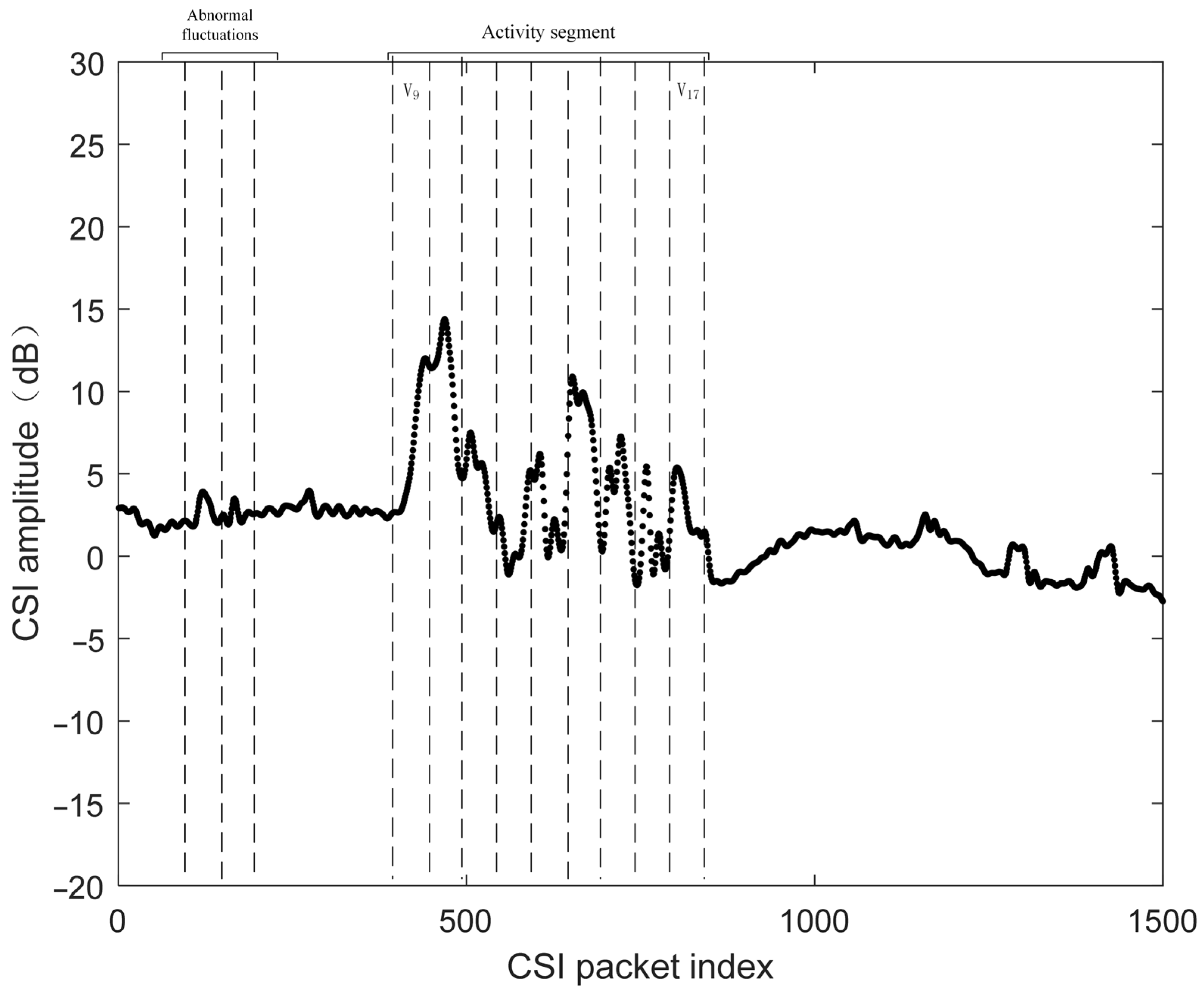
| Algorithm 1 Active Segment detection algorithm. |
| Input: : Window signal variance vector, where m is the total number of nonoverlapping windows. : Variance threshold for activity detection. : Threshold for minimum consecutive active windows. Output: : Index of the first window containing user activity. : Index of the last window containing user activity. // Initialize variables for do if then ; // Store the location of the window that may contain user activity else ; if then ; ; // Obtain the start and end points of the user activity window else ; // Filter short-term abnormal fluctuations by emptying Pos end if end if end for |
| Algorithm 2 Subcarrier selection algorithm. |
| Input: : Matrix of user activity segments, where K is the number of subcarriers and N is the number of time samples. : Lower threshold for subcarrier variance. : Upper threshold for subcarrier variance. Output: : New sample matrix containing two randomly selected subsets of 30 subcarriers. ; // Initialize the new sample matrix for do // Iterate through K subcarriers ; while do ; // Delete subcarrier end while end for for do ; // Randomly select 30 columns ; // Store the new sample in matrix end for |
3.4. Match Strategy
- Predefine the parameter search range, which can consist of either discrete values or continuously distributed intervals.
- If the parameter value is discrete, sample with a certain probability at the given value; if it is from a continuously distributed interval, sample randomly within that interval. A total of sets of sampling results are obtained.
- Iterate through the sets of sampling results to find the set of parameters that optimize the SVM model’s performance, which are the optimal parameters.
4. Results and Discussion
4.1. Optimal Parameters and Information Retention Rate in the PCA Process
4.2. Impact of SVM Kernel Functions and Penalty Parameters
4.3. Accuracy-Complexity Trade-Off Analysis
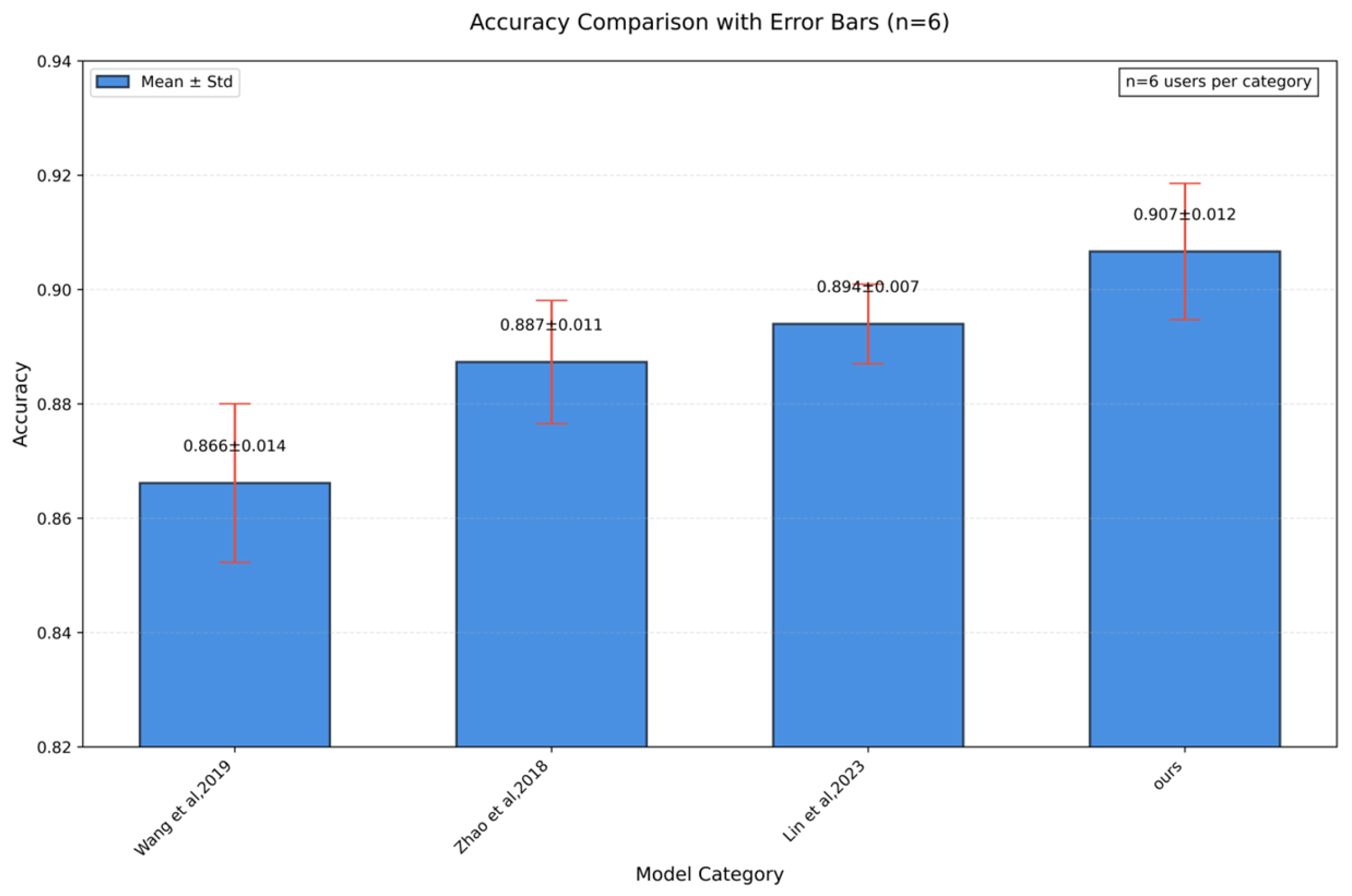
4.4. Contrast Analysis
| Literature | Signal Processing | Feature Extraction | Match Strategy |
|---|---|---|---|
| [1] | Low-pass filtering, Phase difference | Statistical Eigenvalues, PCA descending | Bayesian classification |
| [17] | short-time Fourier transform (STFT), band-pass filtering | short-window segmentation, wavelet decomposition | k-Nearest Neighbors (k-NN), probabilistic distance metric |
| [16] | Hampel filtering, Butterworth low-pass filtering, wavelet threshold denoising | time-domain statistical features, Principal Component Analysis (PCA) | Support Vector Machine (SVM), grid search and cross-validation |
| ours | Hampel filtering, low-pass filtering, wavelet transform threshold denoising | PCA plus moving window to detect active segments, subcarrier selection followed by the extraction of statistical feature values, PCA downscaling | Random Search-Kernel SVM |
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wang, F.; Li, Z.; Han, J. Continuous User Authentication by Contactless Wireless Sensing. IEEE Internet Things J. 2019, 6, 8323–8331. [Google Scholar] [CrossRef]
- Gui, G.; Mao, S.; Wang, Y. New Frontier of Communication Security on Radio Frequency Fingerprints. IEEE Wirel. Commun. 2024, 31, 156–163. [Google Scholar]
- Wang, Z.; Jiang, K.; Hou, Y.; Dou, W.; Zhang, C.; Huang, Z.; Guo, Y. A Survey on Human Behavior Recognition Using Channel State Information. IEEE Access 2019, 7, 155986–156024. [Google Scholar] [CrossRef]
- Lin, F.; Song, C.; Zhuang, Y.; Xu, W.; Li, C.; Ren, K. Cardiac Scan: A Non-contact and Continuous Heart-based User Authentication System. In Proceedings of the 23rd Annual International Conference on Mobile Computing and Networking (MobiCom ’17), Snowbird, UT, USA, 16–20 October 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 315–328. [Google Scholar]
- Cao, C.; Ding, Y.; Dai, M.; Gong, W. Real-time Cross-Domain Gesture and User Identification via COTS WiFi. IEEE Trans. Signal Process. 2025. [CrossRef]
- Duan, P.; Fang, T.; Wu, C.; Cao, Y. WiDoor: Wi-Fi Based Contactless Close-range Identity Recognition. IEEE Internet Things J. 2024, 12, 8599–8613. [Google Scholar] [CrossRef]
- Halperin, D.; Hu, W.; Sheth, A.; Wetherall, D. Tool release: Gathering 802.11n traces with channel state information. SIGCOMM Comput. Commun. Rev. 2011, 41, 53. [Google Scholar] [CrossRef]
- Chen, C.; Lv, Z.; Li, N.; Chang, H. An Anomalous Traffic Detection Method for Distributed Photovoltaic Safety State Baseline. In Proceedings of the 2023 International Conference on Artificial Intelligence and Automation Control (AIAC), Xiamen, China, 17–19 November 2023; pp. 99–103. [Google Scholar] [CrossRef]
- Zhou, Z.; Liu, C.; Yu, X.; Yang, C.; Duan, P.; Cao, Y. Deep-WiID: WiFi-Based Contactless Human Identification via Deep Learning. In Proceedings of the 2019 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Leicester, UK, 19–23 August 2019; pp. 877–884. [Google Scholar] [CrossRef]
- Wang, D.; Zhou, Z.; Yu, X.; Cao, Y. CSIID: WiFi-based Human Identification via Deep Learning. In Proceedings of the 2019 14th International Conference on Computer Science & Education (ICCSE), Toronto, ON, Canada, 19–21 August 2019; pp. 326–330. [Google Scholar] [CrossRef]
- Pokkunuru, A.; Jakkala, K.; Bhuyan, A.; Wang, P.; Sun, Z. NeuralWave: Gait-Based User Identification Through Commodity WiFi and Deep Learning. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 758–765. [Google Scholar] [CrossRef]
- Chen, Y.; Dong, W.; Gao, Y.; Liu, X.; Gu, T. Rapid: A Multimodal and Device-free Approach Using Noise Estimation for Robust Person Identification. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2017, 1, 41. [Google Scholar] [CrossRef]
- Manjunatha, K.; Manjunath, S.; Guru, D.S.; Somashekara, M.T. Online signature verification based on writer dependent features and classifiers. Pattern Recognit. Lett. 2016, 80, 129–136. [Google Scholar] [CrossRef]
- Xin, T.; Guo, B.; Wang, Z.; Li, M.; Yu, Z.; Zhou, X. FreeSense: Indoor Human Identification with Wi-Fi Signals. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Ming, X.; Feng, H.; Bu, Q.; Zhang, J.; Yang, G.; Zhang, T. HumanFi: WiFi-Based Human Identification Using Recurrent Neural Network. In Proceedings of the 2019 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Leicester, UK, 19–23 August 2019; pp. 640–647. [Google Scholar] [CrossRef]
- Lin, C.; Wang, P.; Obaidat, M.S.; Wang, L. A Contactless Authentication System Based on WiFi CSI. ACM Trans. Sens. Netw. 2023, 19, 29. [Google Scholar] [CrossRef]
- Zhao, Z.; Zhao, Z.; Min, G.; Shu, C.; Wang, Z.; Duan, H. Non-Intrusive Biometric Identification for Personalized Computing Using Wireless Big Data. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018. [Google Scholar]
- Wang, C.; Fu, X.; Yang, Z.; Li, S. NeuralWiGait: WiFi-based gait recognition using hybrid deep learning. J. Supercomput. 2025, 81, 373. [Google Scholar] [CrossRef]
- Wang, J.; Huang, Y.; Zhao, F.; Wang, W.; Zhang, D.; Wang, W. CSI-Based Gait Recognition. arXiv 2024, arXiv:2408.06848. [Google Scholar]
- Wang, Z.; Li, J.; Wang, W.; Dong, Z.; Zhang, Q. Review of few-shot learning application in CSI human sensing. Artif. Intell. Rev. 2024, 57, 195. [Google Scholar] [CrossRef]
- Kim, T.; Park, S. WiFi Channel State Information Sensing Based on Introspective Metric Learning. In Proceedings of the 2024 7th International Conference on Signal Processing and Information Security (ICSPIS), Dubai, United Arab Emirates, 12–14 November 2024. [Google Scholar]
- Teramoto, K.; Haruyama, T.; Shimoyama, T. Human Activity Recognition Using FixMatch-based Semi-supervised Learning with CSI. J. Inf. Process. 2024, 32, 596–604. [Google Scholar] [CrossRef]
- Wang, J.; Huang, Y.; Zhao, F.; Zhang, D. Improving WiFi CSI Fingerprinting with IQ Samples. In Proceedings of the Advanced Intelligent Computing Technology and Applications: 20th International Conference, ICIC 2024, Tianjin, China, 5–8 August 2024. [Google Scholar]
- De Silva, V.; Artaud, C. Adversarial Contrastive Representation Learning for Passive WiFi Fingerprinting. In Proceedings of the 2024 14th International Conference on Pattern Recognition Systems (ICPRS), London, UK, 15–18 July 2024. [Google Scholar]
- Yao, Z.; Wang, Y.; Mao, S. Secure Wireless Communication Using Advanced RF Concealment. IEEE Commun. Mag. 2024, 31, 156–163. [Google Scholar]
- Ahmed, A.A.; Hasan, M.K. Deep Learning Based Side-Channel Attack Detection for Mobile Devices Security. Tsinghua Sci. Technol. 2024, 30, 1012–1026. [Google Scholar] [CrossRef]



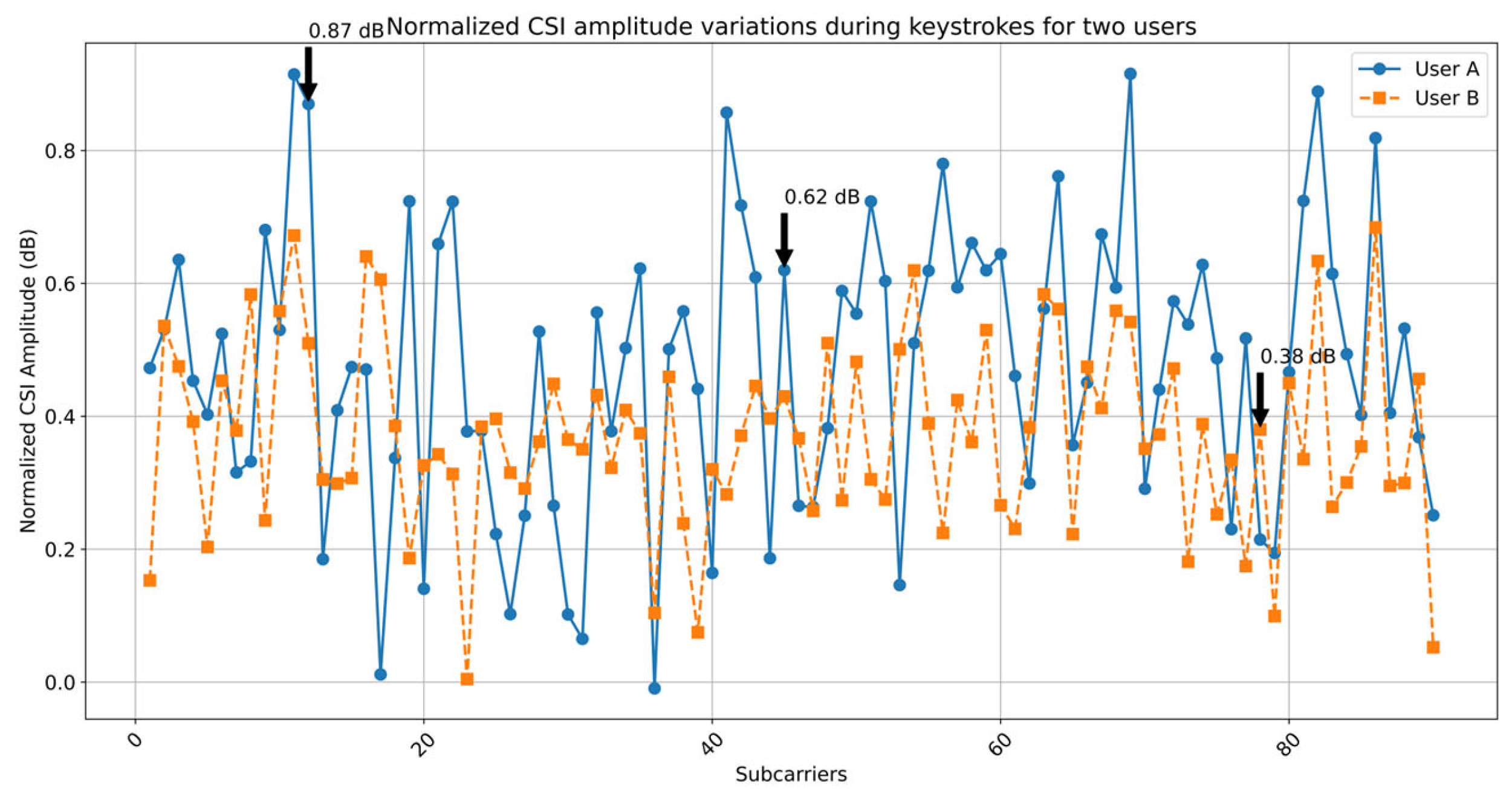

| Subcarrier ID | Variance | Sensitivity | Explanation |
|---|---|---|---|
| 12 | 0.87 | High | Strong fluctuations due to hand proximity |
| 45 | 0.62 | Medium | Moderate response to typing motion |
| 78 | 0.12 | Low | Minimal perturbation from human activity |
| Tool Category | Name/Model | Description |
|---|---|---|
| Operating System | Windows 10 (64-bit) | Primary OS for data collection and processing |
| CPU | Intel Core i7-8700 | 6-core, 12-thread, 3.2 GHz |
| GPU | NVIDIA GeForce RTX 2080 Ti (Santa Clara, CA, USA) | 11 GB VRAM for parallel computation |
| Wireless NIC | Intel 5300 | 802.11n-compliant, 30 subcarriers per antenna |
| Custom Linux-based software | CSI Tool 1.0 | Real-time CSI data collection tool |
| Programming Language | Python 3.8 | Data processing, machine learning |
| Parameters | Kernel Functions | Penalty Function C | Gamma | Degree |
|---|---|---|---|---|
| Search range | Linear, Poly, rbf, sigmoid | 0.01, 0.1, 1, 5, 10 | Scale, auto | 2, 3 |
| Optimal parameters | Poly | 1 | Scale | 3 |
| PCA Retention Information Rate | Average Recognition Accuracy ± SD |
|---|---|
| 80% | 89.96% ± 0.42% |
| 90% | 90.9% ± 0.35% |
| 95% | 90.12% ± 0.48% |
| 98% | 90.12% ± 0.51% |
| Method | Accuracy (%) | Runtime (ms) | Memory Usage (MB) |
|---|---|---|---|
| Traditional SVM | 88.8 | 125 | 42 |
| Wi-Sign | 79.0 | 85 | 30 |
| BioID | 88.75 | 112 | 38 |
| Proposed Method | 90.9 | 158 | 51 |
| Predicted/User | User 1 | User 2 | User 3 | User 4 | User 5 | User 6 | Total |
|---|---|---|---|---|---|---|---|
| User 1 | 92.3% | 2.1% | 1.2% | 1.8% | 1.1% | 1.5% | 100% |
| User 2 | 1.9% | 93.4% | 1.7% | 1.1% | 1.0% | 0.9% | 100% |
| User 3 | 1.5% | 1.3% | 89.2% | 2.1% | 1.8% | 4.1% | 100% |
| User 4 | 1.7% | 1.2% | 1.9% | 91.5% | 2.0% | 1.7% | 100% |
| User 5 | 1.2% | 1.0% | 1.5% | 1.7% | 92.5% | 2.1% | 100% |
| User 6 | 1.3% | 1.1% | 4.0% | 1.6% | 2.0% | 90.0% | 100% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, C.; Li, F.; Liu, X.; Li, J. Optimized Identity Authentication via Channel State Information for Two-Factor User Verification in Information Systems. Sensors 2025, 25, 2465. https://doi.org/10.3390/s25082465
Tian C, Li F, Liu X, Li J. Optimized Identity Authentication via Channel State Information for Two-Factor User Verification in Information Systems. Sensors. 2025; 25(8):2465. https://doi.org/10.3390/s25082465
Chicago/Turabian StyleTian, Chuangeng, Fanjia Li, Xiaomeng Liu, and Juanjuan Li. 2025. "Optimized Identity Authentication via Channel State Information for Two-Factor User Verification in Information Systems" Sensors 25, no. 8: 2465. https://doi.org/10.3390/s25082465
APA StyleTian, C., Li, F., Liu, X., & Li, J. (2025). Optimized Identity Authentication via Channel State Information for Two-Factor User Verification in Information Systems. Sensors, 25(8), 2465. https://doi.org/10.3390/s25082465






