A Method for Enhancing Inventory Efficiency of Densely Stacked Tags in RFID Cabinets
Abstract
1. Introduction
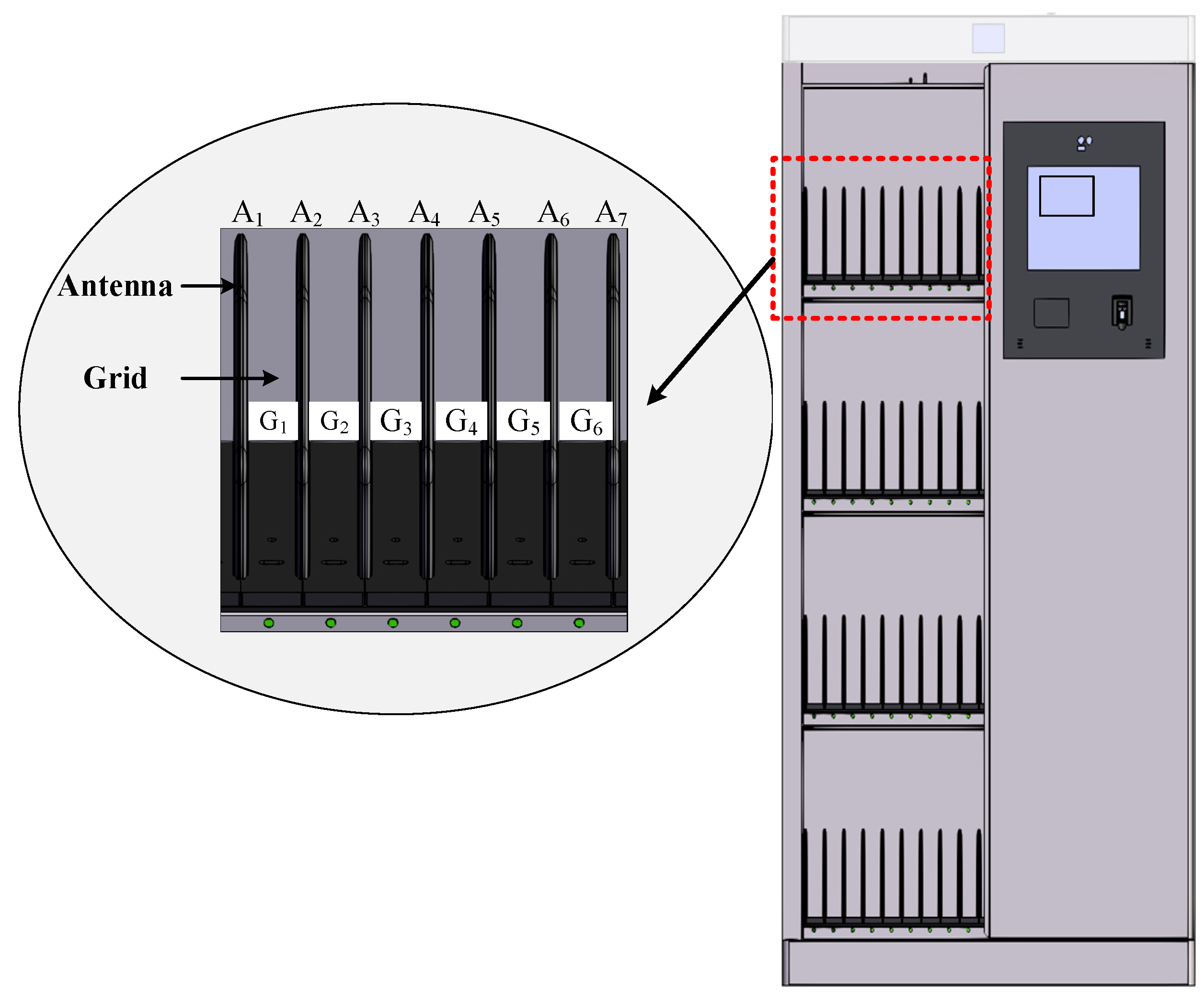
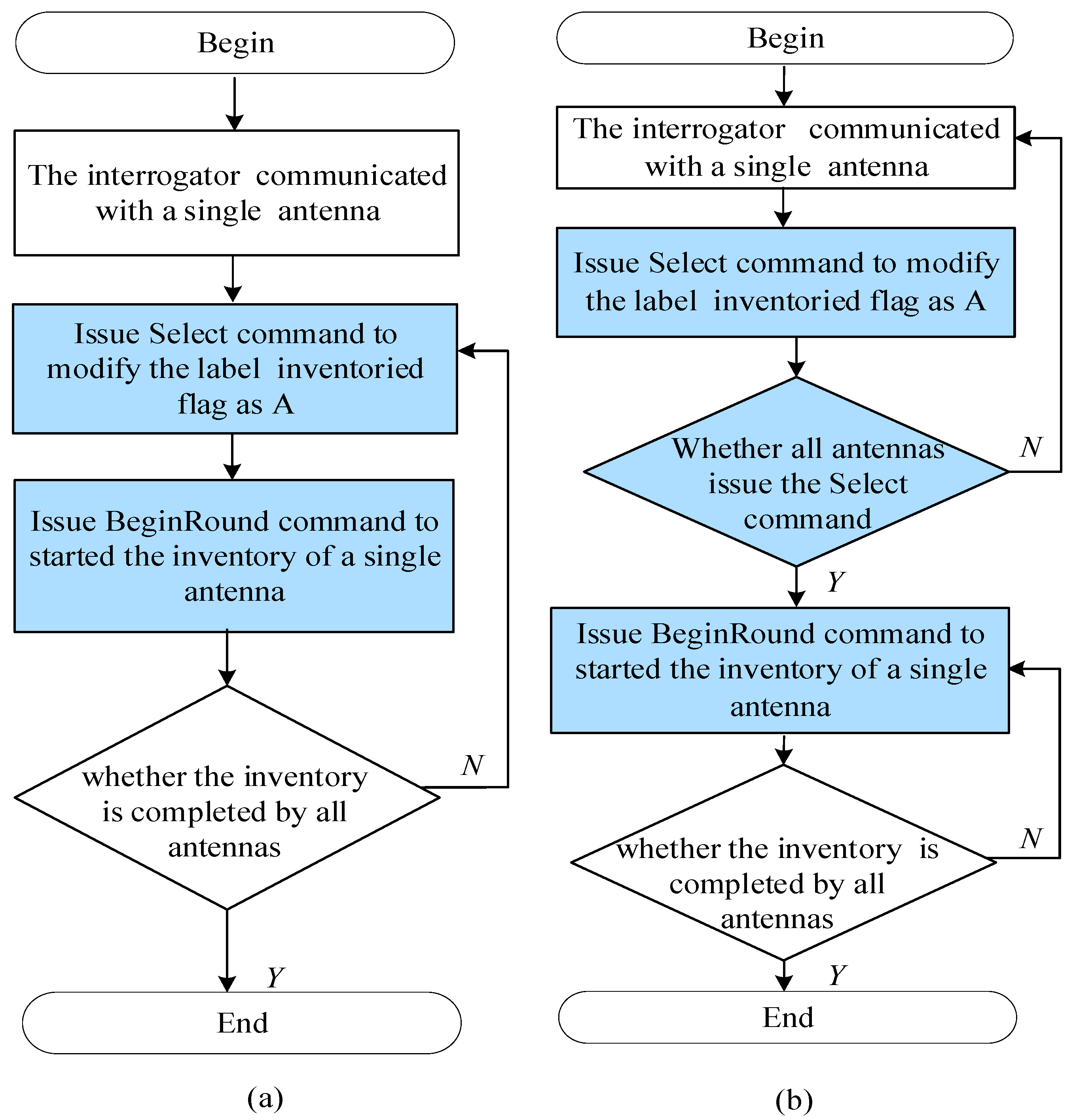
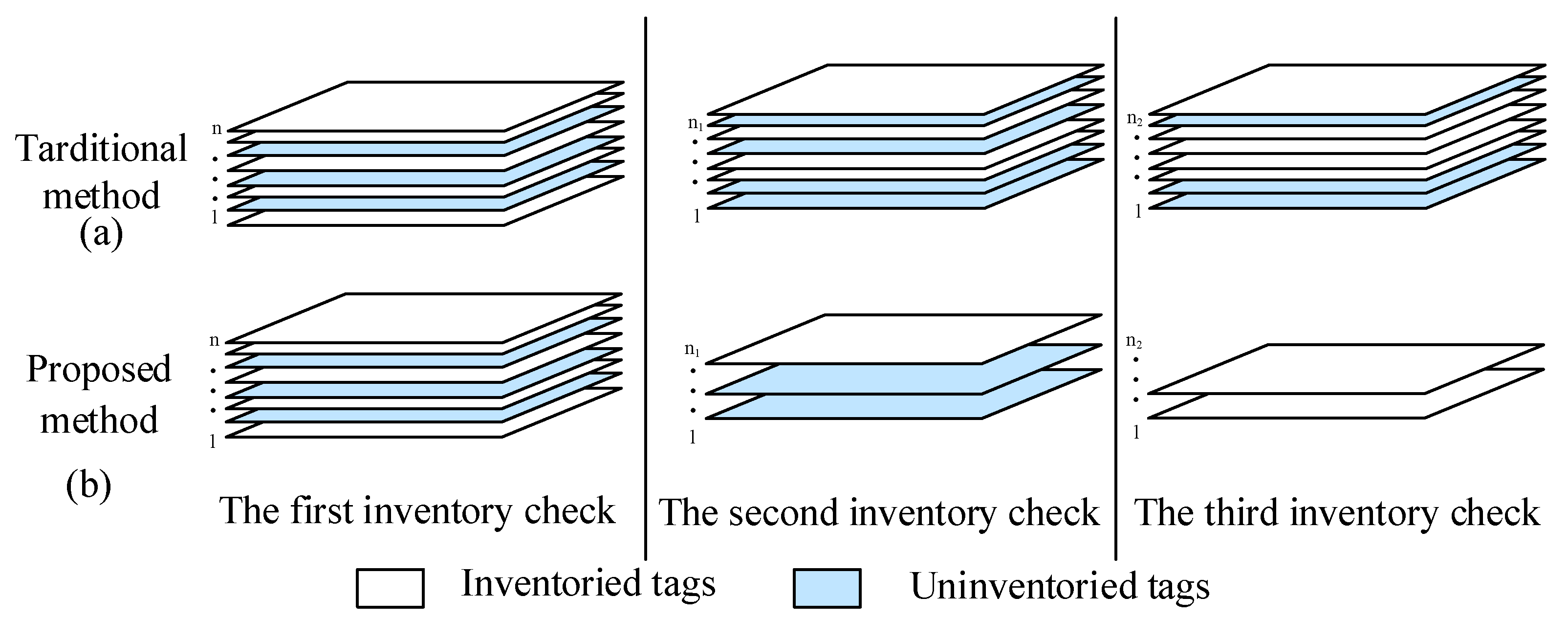
2. Analysis
3. Experimental Results and Discussion
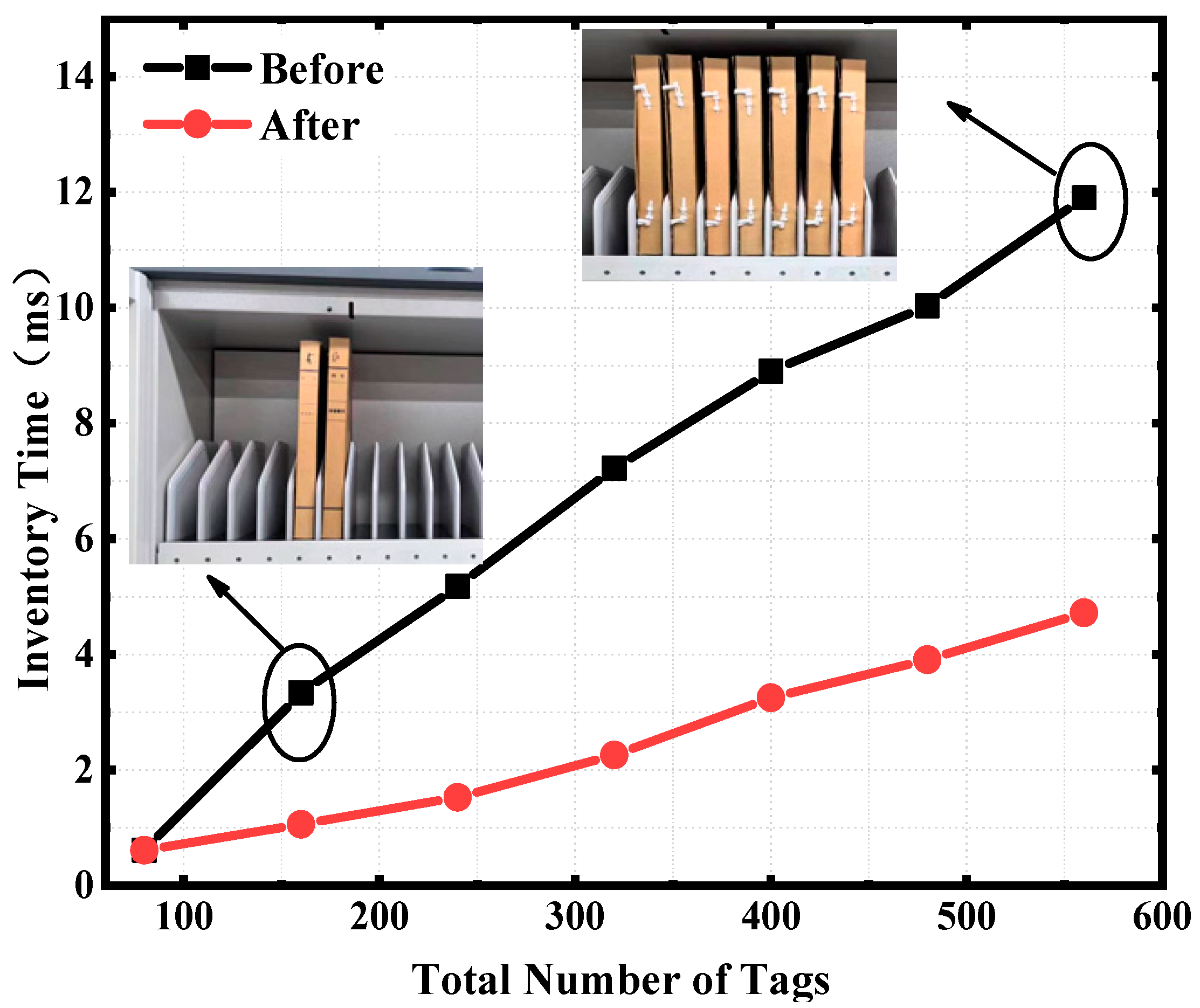
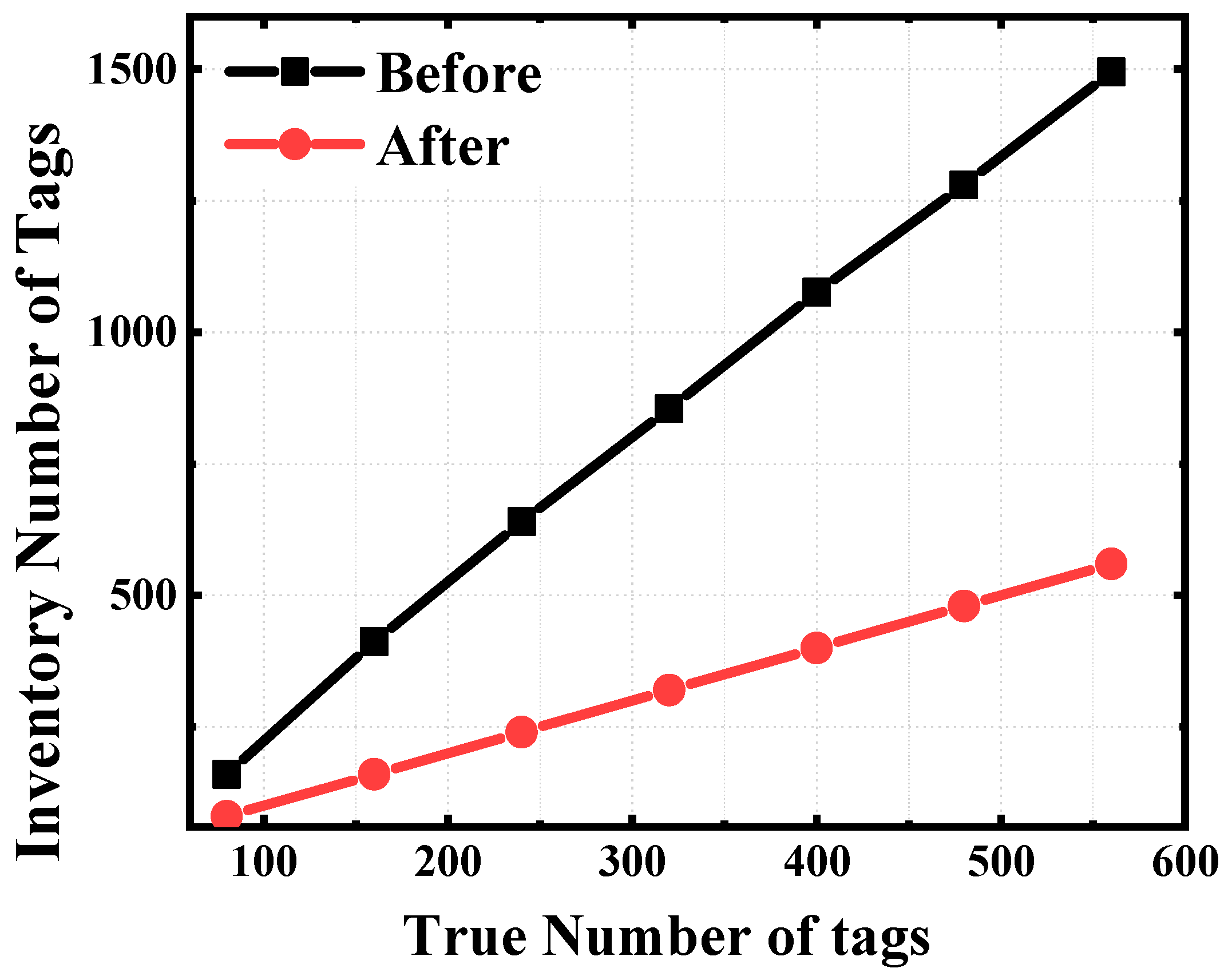
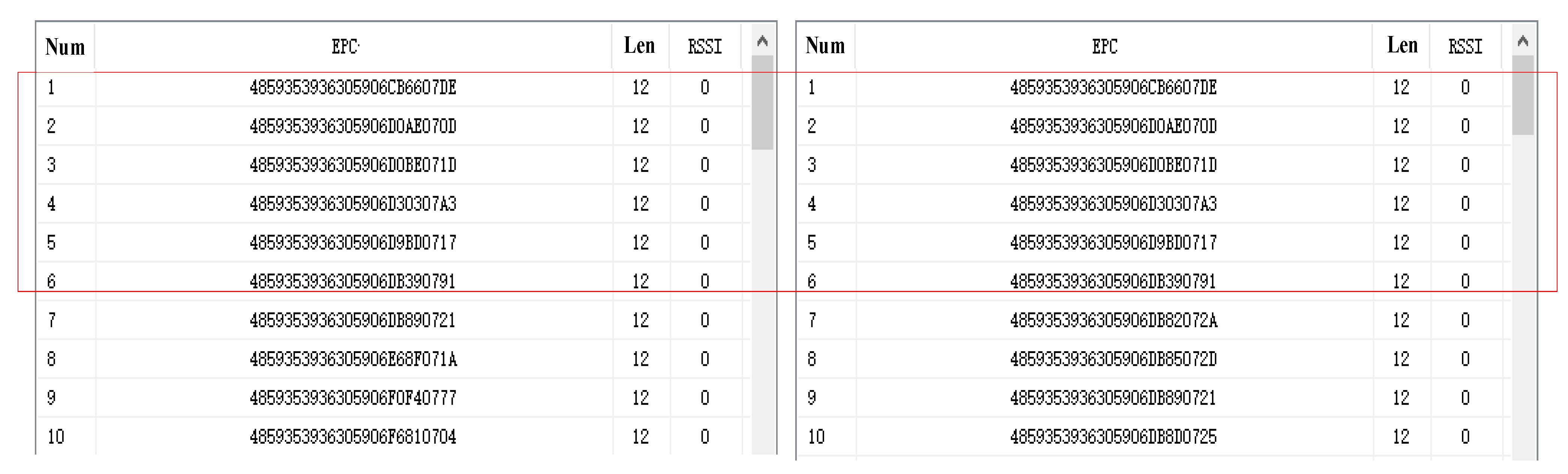
3.1. Inventory Process
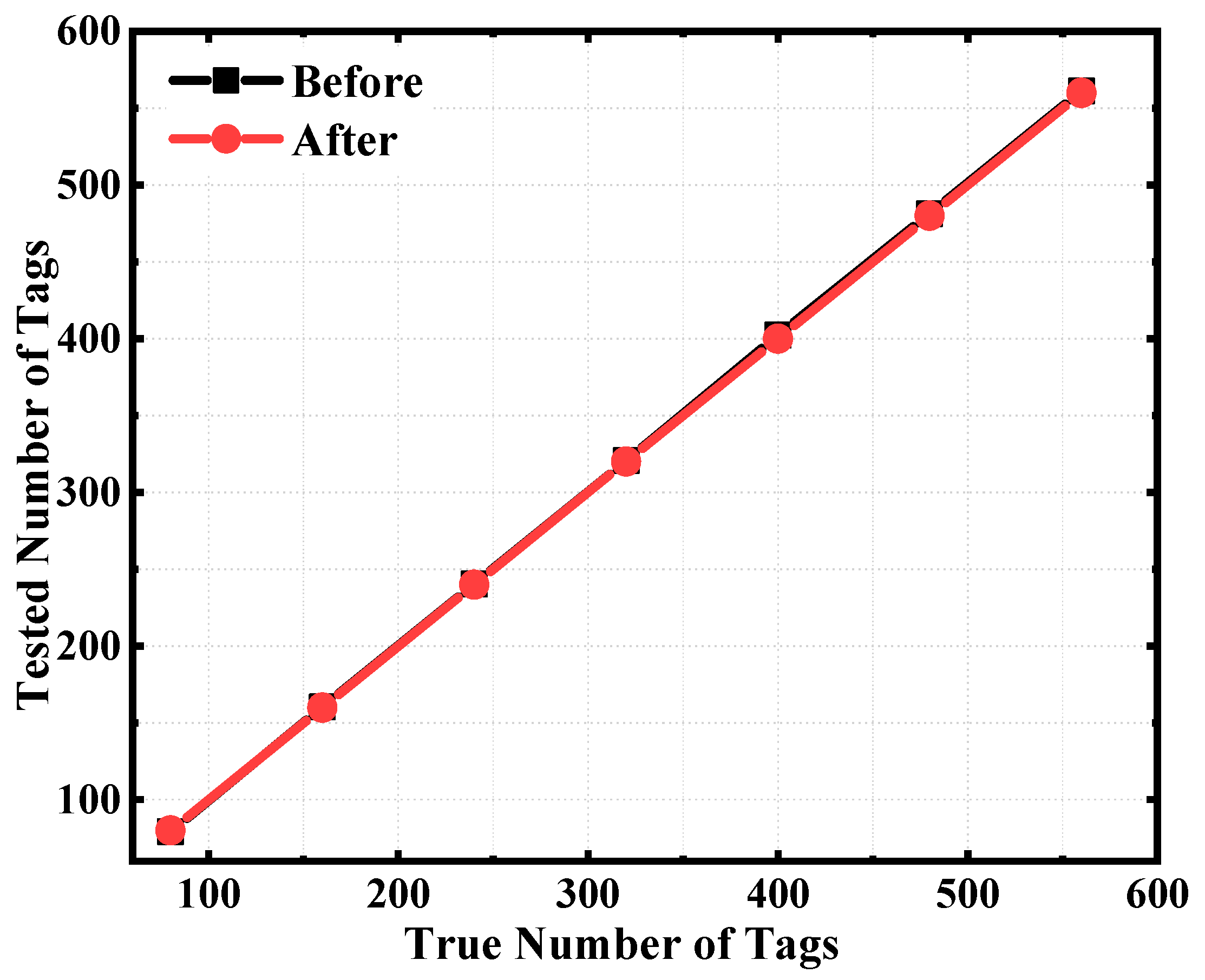
3.2. Simulation and Measurement Results
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Guerrieri, J.R.; Novotny, D.R.; Francis, M.H.; Remley, K. Electromagnetic Emissions and Performance for Proximity RFID. In Proceedings of the 3rd European Conference on Antennas and Propagation, Berlin, Germany, 23–27 March 2009; pp. 1997–2001. [Google Scholar]
- Qing, X.; Chen, Z.N. Proximity Effects of Metallic Environments on High Frequency RFID Reader Antenna: Study and Applications. IEEE Trans. Antennas Propag. 2007, 55, 3105–3111. [Google Scholar] [CrossRef]
- Finkenzeller, K. RFID Handbook: Fundamentals and Applications in Contactless Smart Cards, Radio Frequency Identification and Identification and Near-Field Communication; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2010; pp. 29–110. [Google Scholar]
- Finkenzeller, K. RFID Handbook: Fundamentals and Applications in Contactless Smart Cards and Identification, 2nd ed.; John Wiely & Sons, Ltd.: Hoboken, NJ, USA, 2003. [Google Scholar]
- Occhiuzzi, C.; Caizzone, S.; Marrocco, G. Passive UHF RFID antennas for sensing applications: Principles, methods, and classifcations. IEEE Antennas Propag. Mag. 2013, 55, 14–34. [Google Scholar] [CrossRef]
- Caso, R.; Michel, A.; Buffi, A.; Nepa, P.; Isola, G. A modular antenna for UHF RFID near-field desktop reader. In Proceedings of the IEEE RFID Technology and Applications Conference (RFID-TA), Tampere, Finland, 8–9 September 2014; pp. 204–207. [Google Scholar]
- Caizzone, S.; Marrocco, G. RFID Grids: Part II-Experimentations. IEEE Trans. Antennas Propag. 2011, 59, 2896–2904. [Google Scholar] [CrossRef]
- Zou, X.C.; Lin, H.; Lin, H.; Liu, D.S.; Guo, L.; Yao, K. Design and implementation of an analog front-end circuit for semi-passive HF RFID tag. In IEEE Radio Frequency Integrated Circuits Symposium; IEEE: Piscataway, NJ, USA, 2014. [Google Scholar]
- Chang, L.; Wang, H.; Zhang, Z.; Li, Y.; Feng, Z. A dual-environment active RFID tag antenna mountable on metallic objects. IEEE Antennas Wirel. Propag. Lett. 2016, 15, 1759–1762. [Google Scholar] [CrossRef]
- ISO/IEC 14443-2:2001; Identification Cards-Contactless Integrated Circuit(s) Cards-Proximity Cards-Part 2: Radio Frequency Power and Signal Interface. ISO/IEC: Geneva, Switzerland, 2001.
- ISO/IEC 15693-2:2006; Identification Cards-Contactless Integrated Circuit Cards-Vicinity Cards-Part 2: Air Interface and Initialization. ISO/IEC: Geneva, Switzerland, 2006.
- Quan, C.H.; Choi, J.C.; Choi, G.Y.; Lee, C.W. The Slotted-LBT: A RFID Reader Medium Access Scheme in Dense Reader Environments. In Proceedings of the IEEE International Conference on RFID, Las Vegas, NV, USA, 16–17 April 2008; pp. 207–214. [Google Scholar]
- Bueno-Delgado, M.V.; Ferrero, R.; Gandino, F.; Pavon-Marino, P.; Rebaudengo, M. A geometric distribution reader anti-collision protocol for RFID dense reader Environments. In Proceedings of the IEEE Transactions on Automation Science and Engineering, Madison, WI, USA, 17–20 August 2013; Volume 10, pp. 296–306. [Google Scholar]
- Wijayasekara, S.K.; Saadi, M.; Sriprasert, T.; Sasithong, P.; Wuttisittikulkij, L. An efficient aloha based collision resolution algorithm for RFID. In Proceedings of the 2020 International Conference on Electronics, Information, and Communication (ICEIC), Barcelona, Spain, 19–22 January 2020; pp. 1–4. [Google Scholar]
- Su, Y.S.; Lin, J.R.; Tonguz, O.K. Grouping of RFID Tags via Strongly Selective Families. IEEE Commun. Lett. 2013, 17, 1120–1123. [Google Scholar]
- Zhu, L.; Yum, T.S.P. Optimal framed aloha based anti-collision algorithms for RFID systems. IEEE Trans. Commun. 2010, 58, 3583–3592. [Google Scholar] [CrossRef]
- Su, J.; Sheng, Z.; Hong, D.; Wen, G. An effective frame breaking policy for dynamic framed slotted Aloha in RFID. IEEE Commun. Lett. 2016, 20, 692–695. [Google Scholar] [CrossRef]
- Jing, W.; Xia, T.H.; Wei, C.X.; Jie, W.Y. Multi-tag RFID identification and anti-collision algorithm. In Applied Mechanics and Materials; Trans Tech Publications Ltd.: Wollerau, Switzerland, 2015; Volume 742, pp. 730–733. [Google Scholar]
- Jia, X.; Feng, Q.; Ma, C. An efficient anti-collision protocol for RFID tag identification. IEEE Commun. Lett. 2010, 14, 1014–1016. [Google Scholar] [CrossRef]
- Seo, M.W.; Choi, Y.C.; Kim, Y.H.; Yoo, H.J. A 13.56MHz RFID transceiver SoC for multi-standard reader. In Proceedings of the 2009 IEEE Radio and Wireless Symposium, San Diego, CA, USA, 18–22 January 2009; pp. 75–78. [Google Scholar]
- Song, H.J.; Yoo, S.S.; Yoo, H.J. Implementation of HF multi-standard RFID transceiver for compact mobile devices. In Proceedings of the IEEE International Conference of Electron Devices and Solid-State Circuits (EDSSC), Hong Kong, China, 15–17 December 2010; pp. 1–4. [Google Scholar]
- EPC™ Radio-Frequency Identity Protocols EPC Class-1 HF RFID Air Interface Protocol for Communications at 13.56 MHz, Version 2.0.3. Available online: https://developer.digitalhealth.gov.au/standards/epc-radio-frequency-identity-protocols-epc-class-1-hf-rfid-air-interface-protocol-for-communications-at-13-56-mhz (accessed on 7 December 2024).
- ISO/IEC 18000-3; Information Technology—Radio Frequency Identification for Item Management—Part 3: Parameters for Air Interface Communications at 13.56 MHz. ISO: Geneva, Switzerland, 2004.
- Huang, H.; Ye, T.; Lee, T.T. Gated Slotted Aloha Protocol for Wireless Communication Network. In Proceedings of the 2018 International Conference on Networking and Network Applications (NaNA), Xi’an, China, 12–15 October 2018; pp. 22–28. [Google Scholar]
- Yuen, M.H.; Ko, K.T. Home private optical fiber network: Bus topology with multi-channel Aloha and Slotted Aloha schemes. In Proceedings of the IEEE Youth Conference on Information, Computing and Telecommunications, Beijing, China, 28–30 November 2010; pp. 343–346. [Google Scholar]
- Yan, X.Q.; Zhang, F. Rapid RFID tag collision resolution with the frame slotted ALOHA protocol. In Proceedings of the International Conference on Computer Application and System Modeling (ICCASM 2010), Taiyuan, China, 22–24 October 2010; pp. V1-517–V1-521. [Google Scholar]
- Yang, J.T.; Yan, S.J.; Chen, Q.; Duan, J.Y.; Tong, M.S. An Accurate Anti-collision Algorithm of Chipless RFID Tags Based on Deep Learning. In Proceedings of the PhotonIcs & Electromagnetics Research Symposium (PIERS), Prague, Czech Republic, 3–6 July 2023; pp. 1456–1462. [Google Scholar]
- Piao, C.; Fan, Z.; Yang, C.; Han, X. Research on RFID security protocol based on grouped tags and re-encryption scheme. In Proceedings of the 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, Beijing, China, 25–27 June 2010; pp. 568–572. [Google Scholar]
- Xue, Y.F.; Sun, H.L.; Zhu, Z.T. RFID Dynamic Grouping Anti-collision Algorithm Based on FCM. In Proceedings of the 2009 International Joint Conference on Bioinformatics, Systems Biology and Intelligent Computing, Shanghai, China, 3–5 August 2009; pp. 619–622. [Google Scholar]


| Name | Value |
|---|---|
| Air interface communications protocol | ISO 18000-3 Mode 3 |
| Operating frequency | 13.56 MHz |
| Reverse coding | Manchester coding |
| Output power | 5–7 W |
| Modulation mode | Amplitude Shift Keying |
| Forward coding | Pulse coding |
| Reverse baud rate | 106 kbit/s |
| Tari | 10 μs |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ma, C.; Chai, J.; Ren, K.; Xie, T.; Ruan, Z.; Liu, Y.; Zhang, D.; Jiang, S. A Method for Enhancing Inventory Efficiency of Densely Stacked Tags in RFID Cabinets. Sensors 2025, 25, 1617. https://doi.org/10.3390/s25051617
Ma C, Chai J, Ren K, Xie T, Ruan Z, Liu Y, Zhang D, Jiang S. A Method for Enhancing Inventory Efficiency of Densely Stacked Tags in RFID Cabinets. Sensors. 2025; 25(5):1617. https://doi.org/10.3390/s25051617
Chicago/Turabian StyleMa, Chengzhen, Jia Chai, Kaiqi Ren, Tingting Xie, Zhicheng Ruan, Yuzhu Liu, Dan Zhang, and Suiping Jiang. 2025. "A Method for Enhancing Inventory Efficiency of Densely Stacked Tags in RFID Cabinets" Sensors 25, no. 5: 1617. https://doi.org/10.3390/s25051617
APA StyleMa, C., Chai, J., Ren, K., Xie, T., Ruan, Z., Liu, Y., Zhang, D., & Jiang, S. (2025). A Method for Enhancing Inventory Efficiency of Densely Stacked Tags in RFID Cabinets. Sensors, 25(5), 1617. https://doi.org/10.3390/s25051617





