Robust Beamfocusing for Secure NFC with Imperfect CSI
Abstract
1. Introduction
1.1. Background
1.2. Related Works
1.3. Main Contributions
- We consider two schemes for near-field secure communication in a unified scenario. Generally, we refer to the Tx, Rx, and eavesdropper as Alice, Bob, and Eve, respectively, all of whom have multiple antennas. In Scheme I, which we call the Tx-AN scheme, Alice simultaneously transmits signals and emits AN to hinder Eve, who is positioned close to Alice, from eavesdropping on the legitimate information. In Scheme II, known as the Rx-AN scheme, Alice transmits signals while Bob operates in full-duplex mode, enabling him to both receive signals and transmit AN simultaneously. This approach aims to prevent Eve, who is close to Bob, from capturing any information. We formulate the robust design of beamforming and AN vectors as a power minimization problem, taking into account the QoS constraint on Bob, the security constraint on Eve, and the total transmission power requirements in the presence of imperfect CSI of the eavesdropping channel.
- To solve the non-convex optimization problem of the joint transmit beamforming, receive beamforming, and AN beamforming design, we decompose the original robust optimization problem into two sub-problems and propose an iterative strategy based on the alternating optimization principle, as follows: (1) When the beamforming and AN vectors at Alice are given, updating the receiving beamforming vector at the Bob simplifies to a generalized Rayleigh quotient problem, which can be solved in a closed form; (2) When the receiving beamforming vector at the receiving end is given, the joint design of the transmit beamforming and AN vectors can be reformulated as a semi-definite programming (SDP) problem and can be solved efficiently by an off-the-shelf convex optimization approach.
- To illustrate the advantages of NFC for PLS more intuitively, we conducted simulations examining the relationship between average transmit power versus several factors, i.e., the number of antennas, the position of Eve. This allowed us to utilize near-field beams for enhancing jamming efficiency. Simulation results indicate that we should select the node closer to Eve for transmitting AN to counter eavesdropping. This strategy not only improves the efficiency of AN transmission but also increases the likelihood of creating a near-field propagation condition that is favorable for jamming.
2. System Model
2.1. System Model for the Proposed Two Schemes
2.1.1. Tx-AN
2.1.2. Rx-AN
2.2. Channel Models
2.3. CSI Error Models
2.4. The Design of
3. Problem Formulation
4. Alternating Optimization Algorithm for the Power Minimization Problem with Imperfect CSI
4.1. Alternating Optimization Algorithm for Tx-AN Scheme
| Algorithm 1: AO-based algorithm for solving (P1) |
|
1: : , , , , and threshold . 2: : , , and 3: : Let the iteration index to be and . Initialize , to be positive semi-definite matrices with and are the right singular vector and basis vector in the null space of , respectively. . 4: 1. Given and , update : 2. Given and , update and : Solve the Problem in (27). 5: until , the rank-one solution can be obtained by singular value decomposition (SVD) of . Otherwise, and repeat Step 1 and Step 2. |
4.2. Alternating Optimization Algorithm for Rx-AN Scheme
5. Simulations
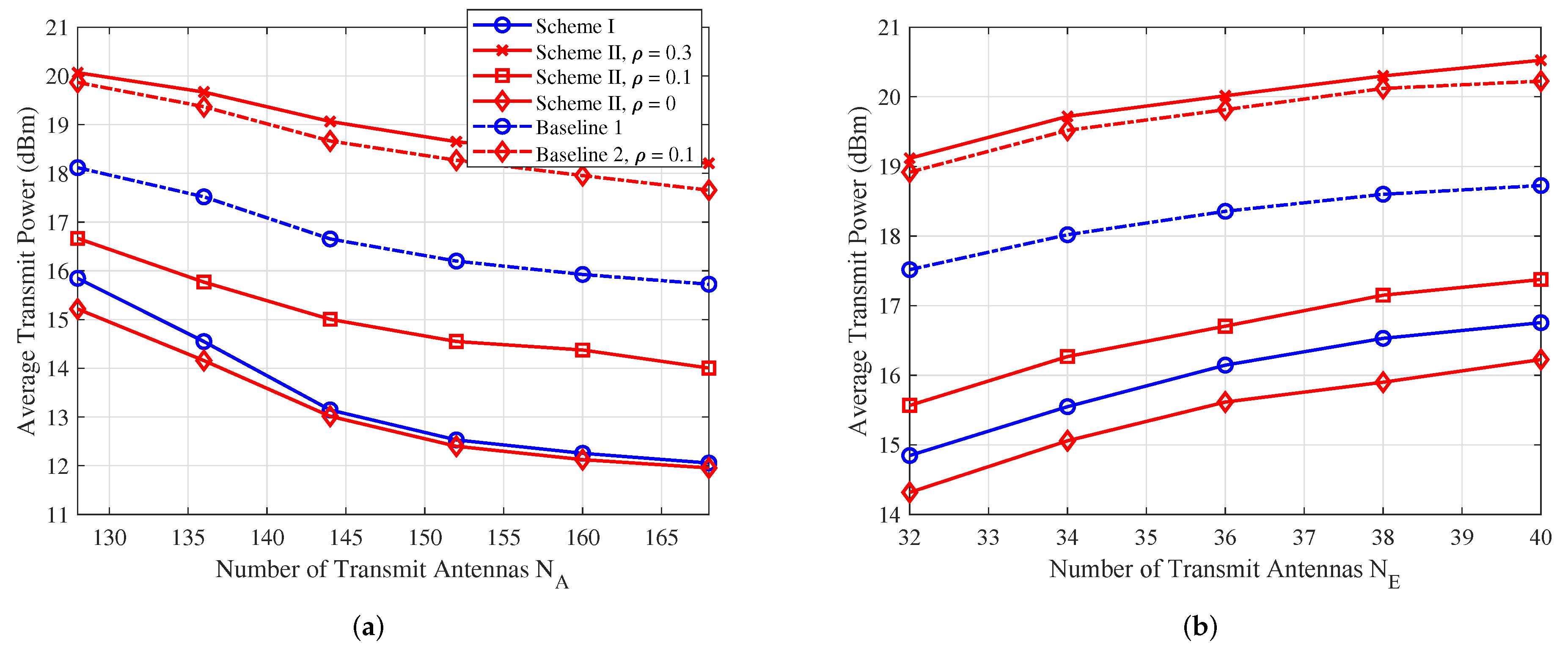
- Baseline 1: Maximum ratio transmission (MRT) is adopted for the beamforming matrix , i.e., , and the AN covariance matrix is chosen to lie in the null space of , such that the AN does not degrade the channel quality of the Bob.
- Baseline 2: The beamforming matrix also adopts the MRT strategy. However, the AN covariance matrix is chosen to lie in the null space of , which helps to minimize the effects of self-interference as much as possible. The self-interference factor is set as .
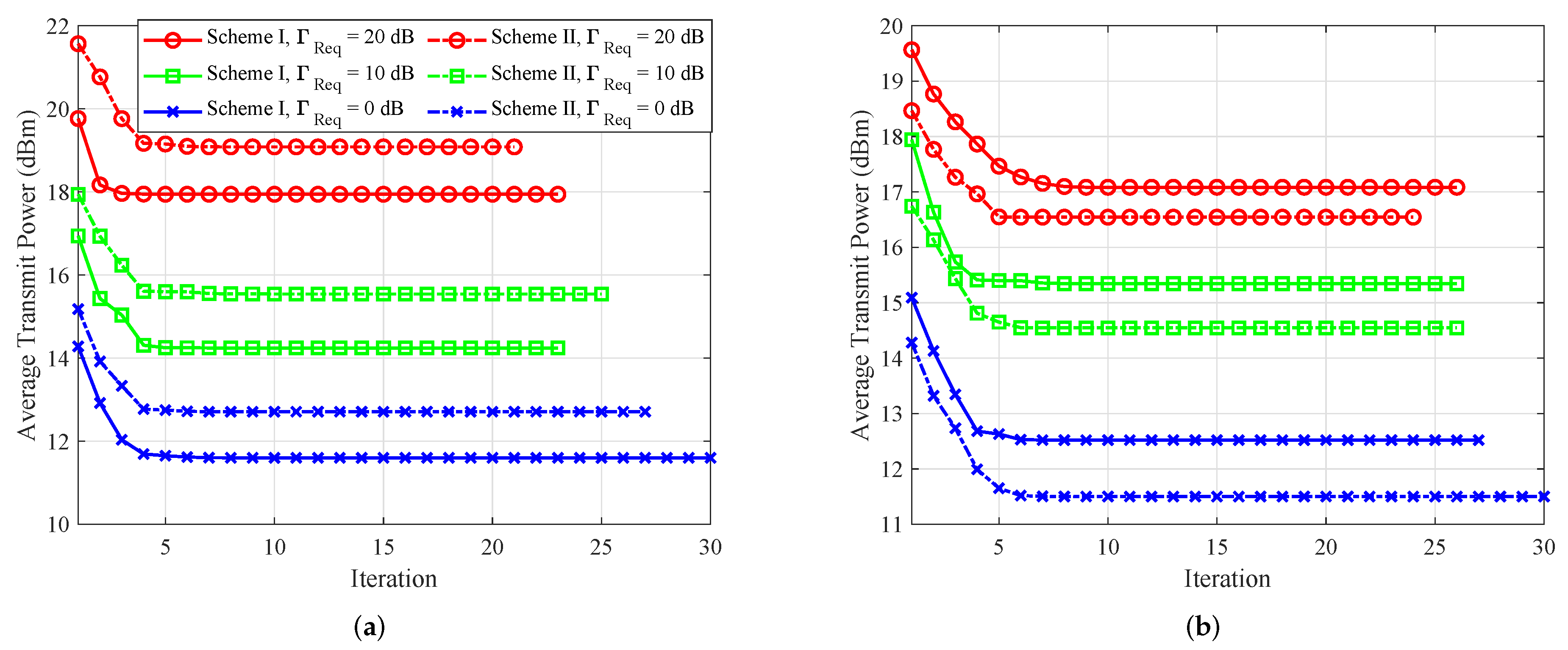
5.1. Convergence Behavior
5.2. Average Total Power Versus Minimum Required SINR
5.3. Average Total Power Versus and
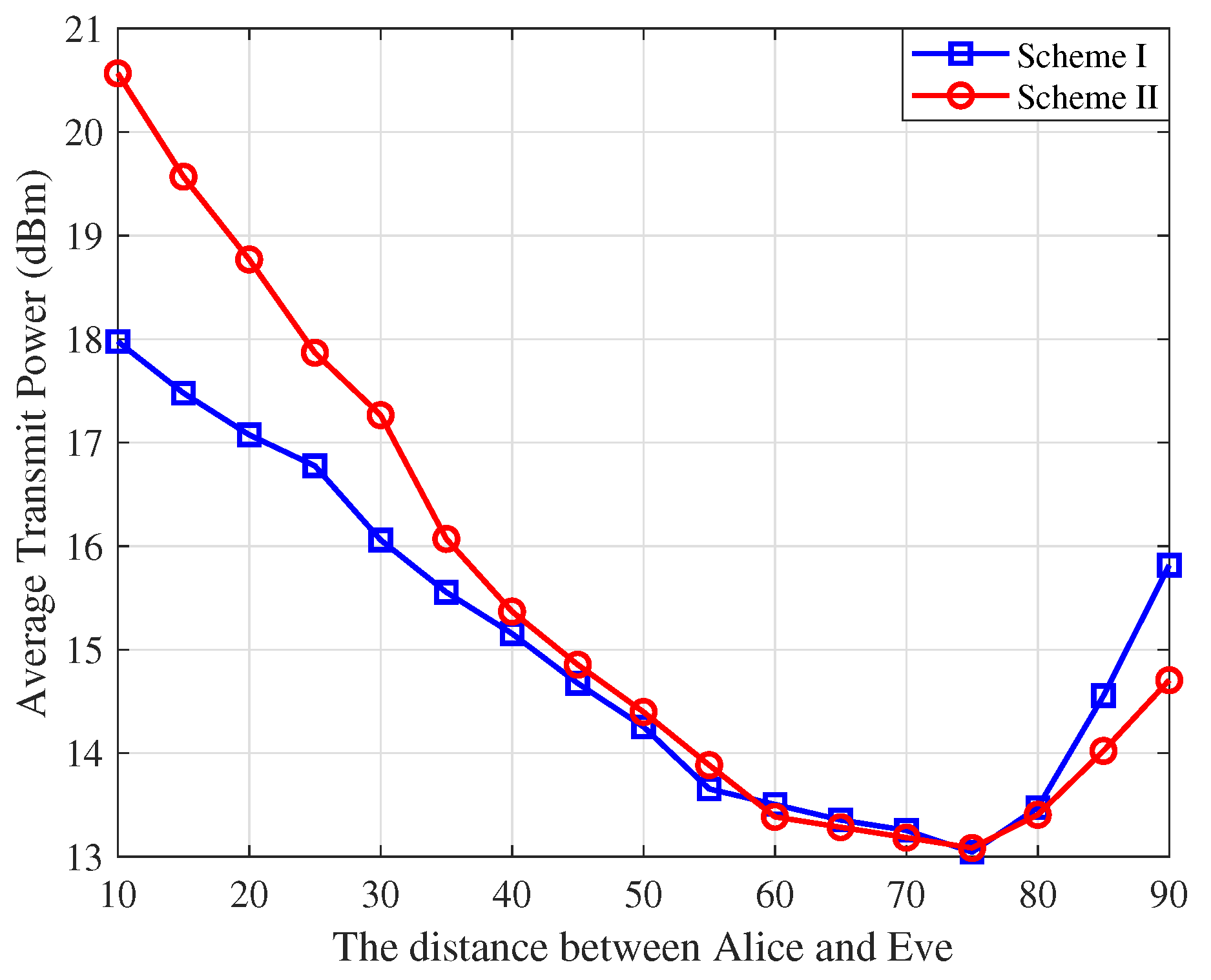
5.4. Average Total Power Versus the Position of Eve
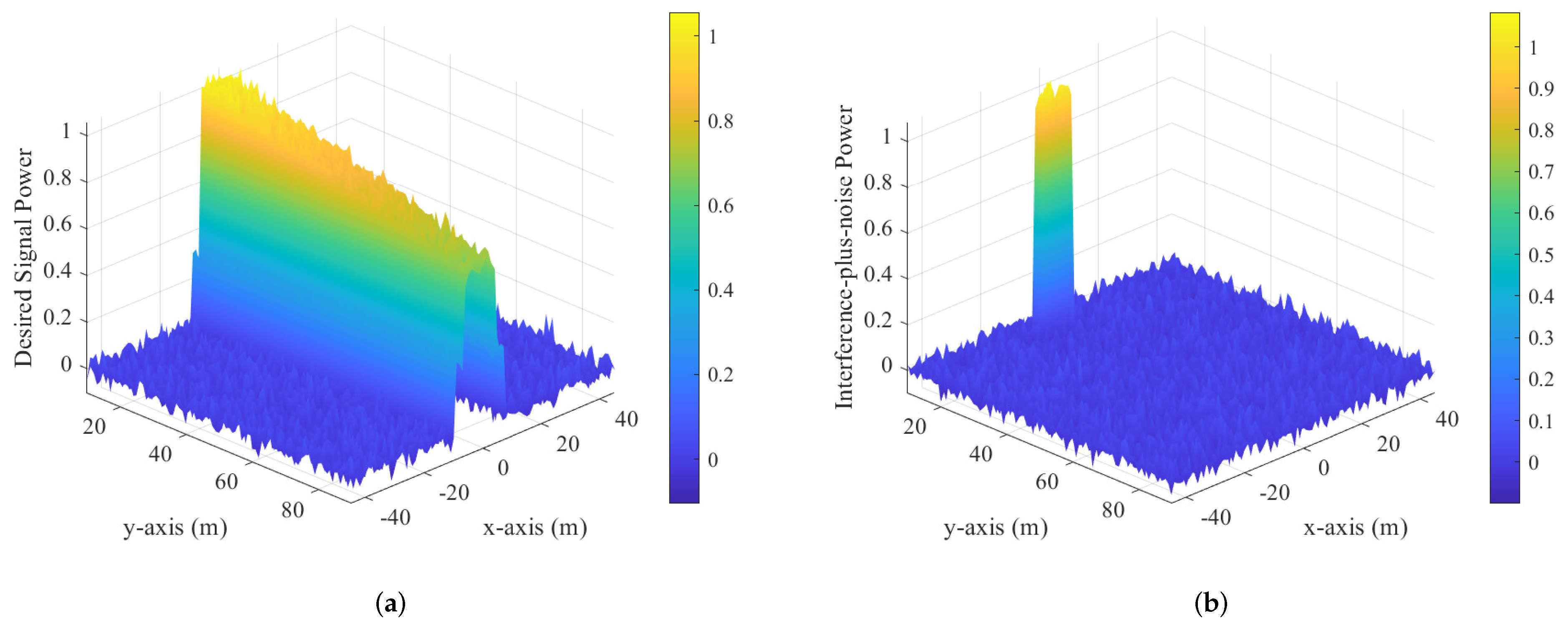
5.5. Protection Zone for the Proposed Two Schemes
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AN | Artificial noise |
| AoA | Angle-of-arrival |
| AoD | Angle-of-departure |
| AWGN | Additive white Gaussian noises |
| BS | Base station |
| CEEs | Channel estimation errors |
| CPU | Central processing unit |
| CSI | Channel estimation information |
| EM | Electromagnetic |
| FD | Full-duplex |
| GSVD | Generalized singular value decomposition |
| MIMO | Multiple-input multiple-output |
| MIMOME | Multiple-input multiple-output multiple-antenna eavesdropper |
| MISO | Multiple-input single-output |
| MUMISO | Multi-user multiple-input single-output |
| NFCs | Near-field communications |
| PLS | Physical layer security |
| QoS | Quality-of-service |
| Rx | Receiver |
| SDP | Semi-definite programming |
| SINR | Signal-to-interference-plus-noise ratio |
| SV | Saleh-Valenzuela |
| SVD | Singular value decomposition |
| Tx | Transmitter |
References
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Shiu, Y.-S.; Chang, S.Y.; Wu, H.-C.; Huang, S.C.-H.; Chen, H.-H. Physical layer security in wireless networks: A tutorial. IEEE Wirel. Commun. 2011, 18, 66–74. [Google Scholar] [CrossRef]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Wyner, A.D. The wiretap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Cui, M.; Wu, Z.; Lu, Y.; Wei, X.; Dai, L. Near-field MIMO communications for 6G: Fundamentals, challenges, potentials, and future directions. IEEE Commun. Mag. 2022, 61, 40–46. [Google Scholar] [CrossRef]
- Zhang, H.; Shlezinger, N.; Guidi, F.; Dardari, D.; Eldar, Y.C. 6G wireless communications: From far-field beam steering to near-field beam focusing. IEEE Commun. Mag. 2023, 61, 72–77. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Z.; Xu, J.; Ouyang, C.; Mu, X.; Schober, R. NFCs: A tutorial review. IEEE Open J. Commun. Soc. 2023, 4, 1999–2049. [Google Scholar] [CrossRef]
- Zhang, Z.; Lung, C.-H.; Wei, X.; Chen, M.; Chatterjee, S.; Zhang, Z. In-Network Caching for ICN-Based IoT (ICN-IoT): A Comprehensive Survey. IEEE Internet Things J. 2023, 10, 14595–14620. [Google Scholar] [CrossRef]
- Wang, L.; Yin, A.; Jiang, X.; Chen, M.; Dev, K.; Qureshi, N.M.F.; Yao, J.; Zheng, B. Resource Allocation for Multi-Traffic in Cross-Modal Communications. IEEE Trans. Netw. Serv. Manag. 2023, 20, 60–72. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, M. Deep Learning Empowered Real-Time Haptic Communications for IoT. IEEE Trans. Consum. Electron. 2024. early access. [Google Scholar]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Khisti, A.; Wornell, G.W. Secure transmission with multiple antennas I: The MISOME wiretap channel. IEEE Trans. Inf. Theory 2010, 56, 3088–3104. [Google Scholar] [CrossRef]
- Oggier, F.; Hassibi, B. The secrecy capacity of the MIMO wiretap channel. IEEE Trans. Inf. Theory 2011, 57, 4961–4972. [Google Scholar] [CrossRef]
- Zhou, X.; McKay, M.R. Physical layer security with artificial noise: Secrecy capacity and optimal power allocation. In Proceedings of the IEEE International Conference on Signal Processing and Communication Systems, Omaha, NE, USA, 30 October 2009; pp. 1–5. [Google Scholar]
- Kobayashi, M.; Debbah, M. On the secrecy capacity of frequency-selective fading channels: A practical vandermonde precoding. In Proceedings of the IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, Cannes, France, 8 December 2008; pp. 1–5. [Google Scholar]
- Yun, S.; Im, S.; Kim, I.-M.; Ha, J. On the secrecy rate and optimal power allocation for artificial noise assisted mimome channels. IEEE Trans. Veh. Technol. 2017, 67, 3098–3113. [Google Scholar] [CrossRef]
- Shafiee, S.; Liu, N.; Ulukus, S. Towards the secrecy capacity of the gaussian MIMO wiretap channel: The 2-2-1 channel. IEEE Trans. Inf. Theory 2009, 55, 4033–4039. [Google Scholar] [CrossRef]
- Geraci, G.; Egan, M.; Yuan, J.; Razi, A.; Collings, I.B. Secrecy sum-rates for multi-user MIMO regularized channel inversion precoding. IEEE Trans. Commun. 2012, 60, 3472–3482. [Google Scholar] [CrossRef]
- Khisti, A.; Wornell, G.W. Secure transmission with multiple antennaspart II: The MIMOME wiretap channel. IEEE Trans. Inf. Theory 2012, 56, 5515–5532. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.-C. Secrecy wireless information and power transfer with MISO beamforming. IEEE Trans. Signal Process. 2014, 62, 1850–1863. [Google Scholar] [CrossRef]
- Mukherjee, A.; Swindlehurst, A.L. Fixed-rate power allocation strategies for enhanced secrecy in MIMO wiretap channels. In Proceedings of the Workshop on Signal Processing Advances in Wireless Communications, Perugia, Italy, 10 July 2009; pp. 344–348. [Google Scholar]
- Liang, Y.; Kramer, G.; Poor, H.V. Compound wiretap channels. EURASIP J. Wirel. Commun. Netw. 2009, 2009, 142374. [Google Scholar] [CrossRef]
- Zheng, G.; Wong, K.-K.; Ng, T.-S. Robust linear MIMO in the downlink: A worst-case optimization with ellipsoidal uncertainty regions. EURASIP J. Adv. Signal Process. 2008, 2008, 609028. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Robust beamforming for secure communication in systems with wireless information and power transfer. IEEE Trans. Wirel. Commun. 2014, 13, 4599–4615. [Google Scholar] [CrossRef]
- Gerbracht, S.; Wolf, A.; Jorswieck, E.A. Beamforming for fading wiretap channels with partial channel information. In Proceedings of the International ITG Workshop on Smart Antennas (WSA), Bremen, Germany, 29 April 2010; pp. 394–401. [Google Scholar]
- Gerbracht, S.; Scheunert, C.; Jorswieck, E.A. Secrecy outage in MISO systems with partial channel information. IEEE Trans. Inf. Forensics Secur. 2011, 7, 704–716. [Google Scholar] [CrossRef]
- Anaya-López, G.J.; González-Coma, J.P.; López-Martínez, F.J. Spatial degrees of freedom for physical layer security in XL-MIMO. In Proceedings of the Vehicular Technology Conference:(VTC2022-Spring), Helsinki, Finland, 25 August 2022; pp. 1–5. [Google Scholar]
- Zhang, Y.; Zhang, H.; Xiao, S.; Tang, W.; Eldar, Y.C. Near-field wideband secure communications: An analog beamfocusing approach. IEEE Trans. Signal Process. 2024, 73, 2173–2187. [Google Scholar] [CrossRef]
- Chen, J.; Xiao, Y.; Liu, K.; Zhong, Y.; Lei, X.; Xiao, M. Physical layer security for near-field communications via directional modulation. IEEE Trans. Veh. Technol. 2024. early access. [Google Scholar]
- Ferreira, J.; Guerreiro, J.; Dinis, R. Physical layer security with near-field beamforming. IEEE Access 2024, 12, 4801–4811. [Google Scholar] [CrossRef]
- Yu, D.; Yang, L.; Gao, X.; Wu, Y.; Yue, G. Physical layer security in spherical-wave channel using massive MIMO. In Proceedings of the IEEE 31st Annual International Symposium on Personal, Indoor and Mobile Radio Communications, London, UK, 31 August–3 September 2020; pp. 1–6. [Google Scholar]
- Zhang, Z.; Liu, Y.; Wang, Z.; Mu, X.; Chen, J. Physical layer security in NFCs. IEEE Trans. Veh. Technol. 2024, 73, 10761–10766. [Google Scholar] [CrossRef]
- Khandaker, M.R.; Masouros, C.; Wong, K.-K. Secure full-duplex device-to-device communication. In Proceedings of the IEEE Globecom Workshops, Singapore, 25 January 2018; pp. 1–6. [Google Scholar]
- El Ayach, O.; Rajagopal, S.; Abu-Surra, S.; Pi, Z.; Heath, R.W. Spatially sparse precoding in millimeter wave MIMO systems. IEEE Trans. Wirel. Commun. 2014, 13, 1499–1513. [Google Scholar] [CrossRef]
- Björnson, E.; Sanguinetti, L. Power scaling laws and near-field behaviors of massive MIMO and intelligent reflecting surfaces. IEEE Open J. Commun. Soc. 2020, 1, 1306–1324. [Google Scholar] [CrossRef]
- Cui, M.; Dai, L. Near-field wideband beamforming for extremely large antenna arrays. IEEE Trans. Wirel. Commun. 2024, 23, 13110–13124. [Google Scholar] [CrossRef]
- Peng, S.; Zhang, C.; Xu, Y.; Wu, Q.; Ou, X.; He, D. Joint antenna position and beamforming optimization with self interference mitigation in MA-ISAC system. arXiv 2024, arXiv:2408.00413. [Google Scholar]
- Zhang, W.; Wen, Z.; Du, C.; Jiang, Y.; Zhou, B. RIS-assisted self-interference mitigation for in-band full-duplex transceivers. IEEE Trans. Commun. 2023, 71, 5444–5454. [Google Scholar] [CrossRef]
- Zhang, Y.; Fang, Y.; Yu, X.; You, C.; Zhang, Y.-J.A. Performance analysis and low-complexity beamforming design for near-field physical layer security. arXiv 2024, arXiv:2407.13491. [Google Scholar]
- Wu, C.; You, C.; Liu, Y.; Chen, L.; Shi, S. Two-stage hierarchical beam training for NFCs. IEEE Trans. Veh. Technol. 2023, 73, 2032–2044. [Google Scholar] [CrossRef]
- Ghojogh, B.; Karray, F.; Crowley, M. Eigenvalue and generalized eigenvalue problems: Tutorial. arXiv 2019, arXiv:1903.11240. [Google Scholar]
- Scherer, C.; Weil, S. Linear Matrix Inequalities in Control; Lecture Notes; Dutch Institute for Systems and Control: Delft, The Netherlands, 2000; Volume 3. [Google Scholar]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Sturm, J.F. Using SeDuMi 1.02, a MATLAB toolbox for optimization over symmetric cones. Optim. Methods Softw. 1999, 11, 625–653. [Google Scholar] [CrossRef]
- Toh, K.-C.; Todd, M.J.; Tütüncü, R.H. SDPT3a MATLAB software package for semidefinite programming, version 1.3. Optim. Methods Softw. 1999, 11, 545–581. [Google Scholar] [CrossRef]
- Liu, J.; Yang, G.; Liu, Y.; Zhou, X. RIS empowered near-field covert communications. IEEE Trans. Wirel. Communi. 2024, 23, 15477–15492. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhang, Y.; Wang, J.; Xiao, S.; Tang, W. Distance-angle beamforming for covert communications via frequency diverse array: Toward two-dimensional covertness. IEEE Trans. Wirel. Commun. 2023, 22, 8559–8574. [Google Scholar] [CrossRef]
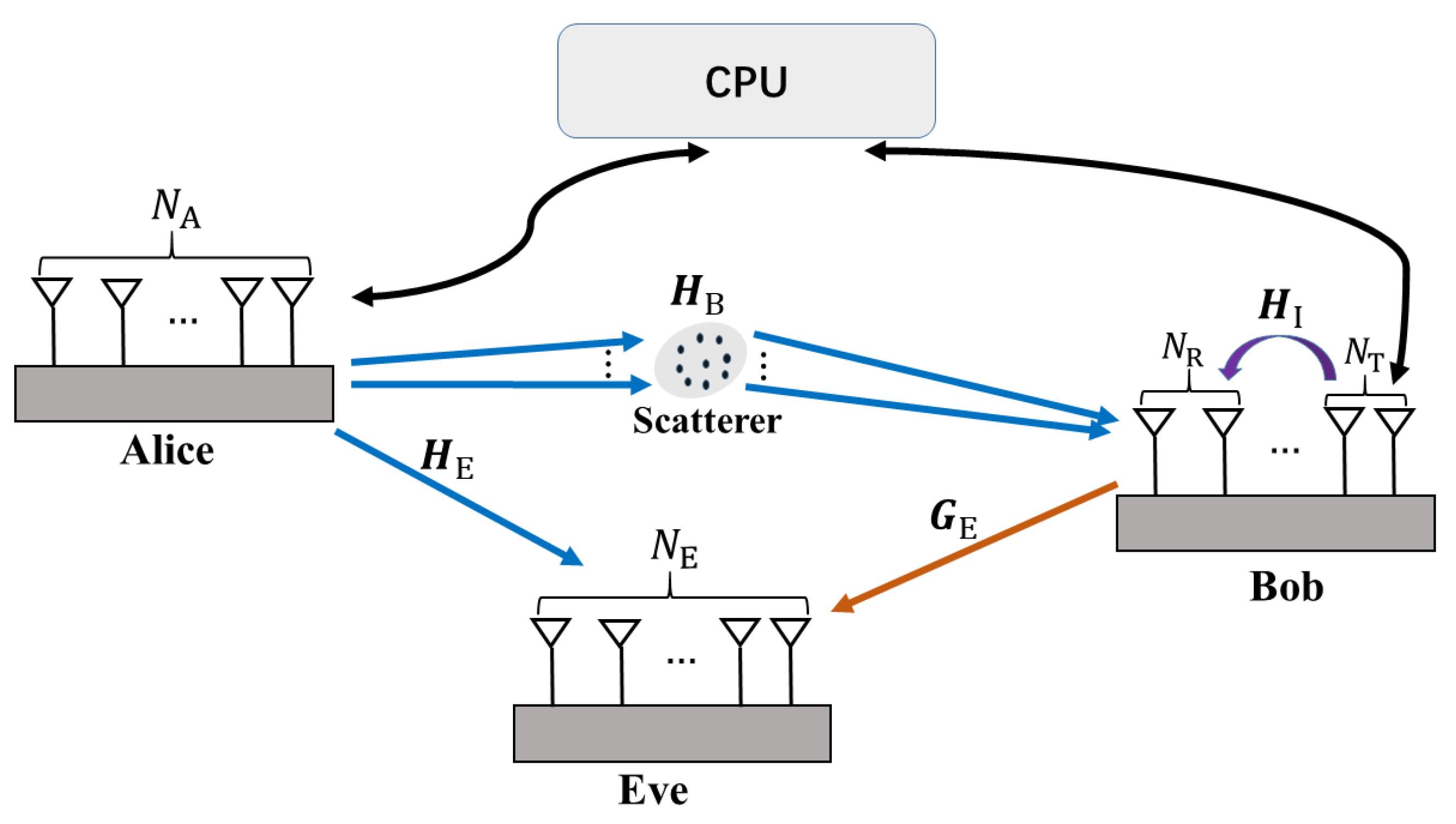


| Scheme | Alice | Bob | Eve | CPU |
|---|---|---|---|---|
| Tx-AN | , | , | ||
| Rx-AN | , | , , | , | , , , |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, W.; Wei, Z.; Yang, Z. Robust Beamfocusing for Secure NFC with Imperfect CSI. Sensors 2025, 25, 1240. https://doi.org/10.3390/s25041240
Chen W, Wei Z, Yang Z. Robust Beamfocusing for Secure NFC with Imperfect CSI. Sensors. 2025; 25(4):1240. https://doi.org/10.3390/s25041240
Chicago/Turabian StyleChen, Weijian, Zhiqiang Wei, and Zai Yang. 2025. "Robust Beamfocusing for Secure NFC with Imperfect CSI" Sensors 25, no. 4: 1240. https://doi.org/10.3390/s25041240
APA StyleChen, W., Wei, Z., & Yang, Z. (2025). Robust Beamfocusing for Secure NFC with Imperfect CSI. Sensors, 25(4), 1240. https://doi.org/10.3390/s25041240








