Securing IoT Sensors Using Sharding-Based Blockchain Network Technology Integration: A Systematic Review
Abstract
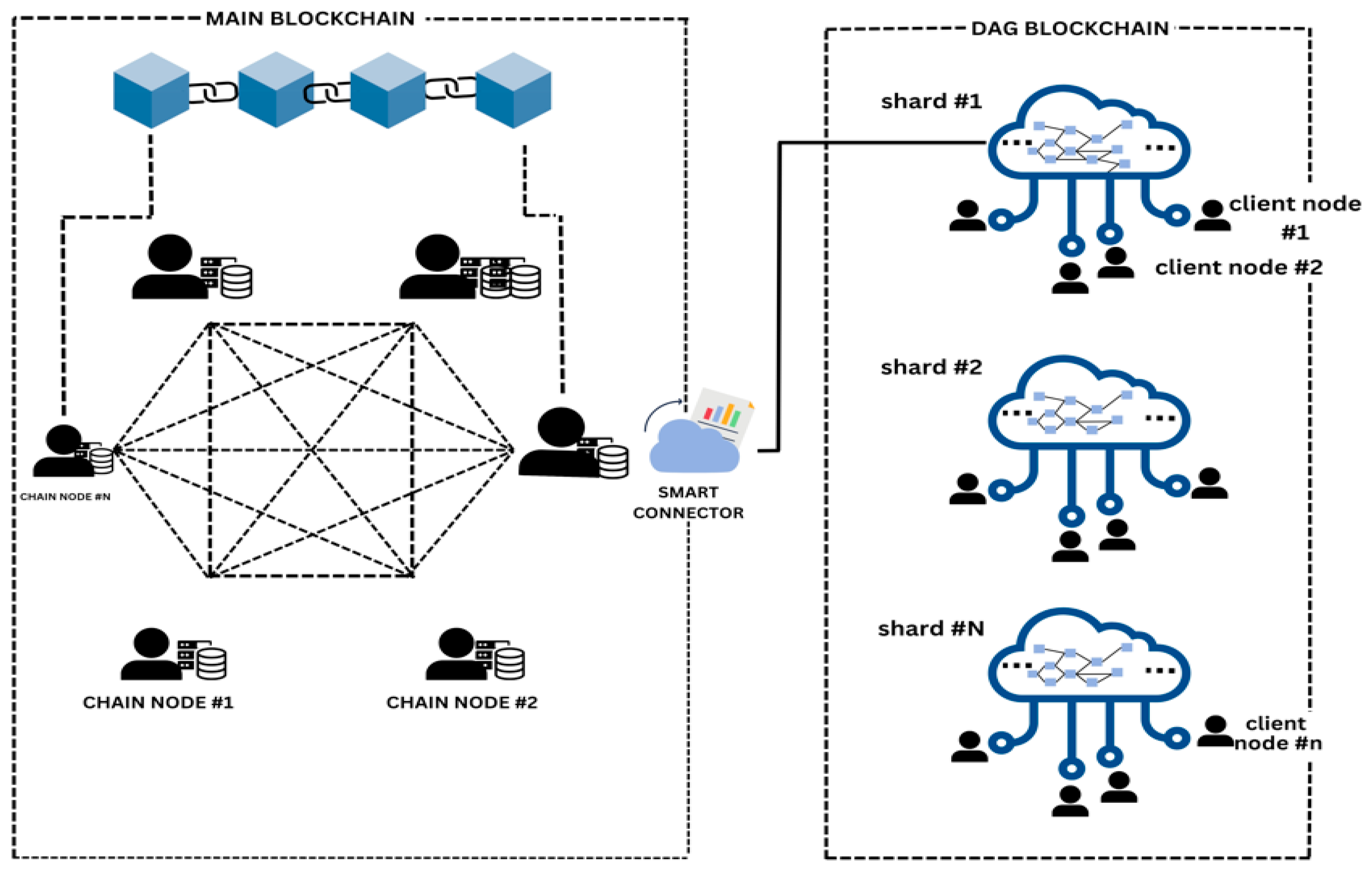
:1. Introduction
1.1. Significance of Study
1.2. Research Aims, Objectives, and Questions
- The presentation of the potential of sharding-based blockchain technology for environmental monitoring.
- The determination of the benefits of sharding-based blockchain network technology in securing IoT sensors.
- The examination of the complexities in the existing literature during the implementation of sharding-based blockchain network technology in securing IoT sensors.
- ➢
- What are the potential impacts of sharding-based blockchain technology on securing IoT sensors?
- ➢
- What are the significant advantages of sharding-based blockchain network technologies?
- ➢
- What have previous studies determined about the disadvantages of the integration of sharding-based blockchain network technology?
2. Materials and Methods
2.1. Systematic Literature Review
2.2. Article Search and Selection
2.2.1. Database Search
2.2.2. Inclusion and Exclusion Criteria
2.2.3. Overview of Publications
2.3. Classification of Articles
- The potential impact of sharding-based blockchain technology in securing IoT sensors: Papers related to environmental monitoring, with an increased focus on sharding-based blockchain technology in the field of IoT sensors have been explored. It further involves how it affects the environment by determining the significant advantages of its implementation.
- The benefits of implementing sharding-based blockchain technology in securing IoT sensors: Various articles have been explored to determine the benefits of sharding-based technology by effectively identifying the significant effects of this technology in various fields.
- The complexities in integrating sharding-based blockchain technology to secure IoT sensors: Studies have explored the difficulties faced in the integration of this emerging technology. Further, this would also help in understanding the positive and negative effects by incorporating sharding-based blockchain technology in different fields, such as agriculture, healthcare, and others.
2.4. Thematic Analysis
3. Results of Literature Review
3.1. Impact of Sharding-Based Blockchain Network Technology on Securing IoT Sensors in Environmental Monitoring
3.2. Benefits of Sharding-Based Blockchain Technology Network in Environment Monitoring
3.3. Challenges of Sharding-Based Blockchain Network Technology in Environment Monitoring
3.4. Security Issues of IoT Sensors in Various Aspects
- Firmware updates: These are special software that are directly placed into device hardware which can be easily installed and uninstalled from the IoT device. However, they also have security issues due to weak authentication, insider threats, a lack of encryption, tampering, alteration, storing sensitive information, and a lack of update mechanisms. As compared to sharding-based technology, these lead to unauthorized access, data tampering, the denial of services, and MitM attacks [22].
- Data routing: These security issues affect the dynamic environment which is prone to routing attacks. These can occur due to various reasons, like physical vulnerabilities, a lack of physical hardening, inadequate update mechanisms and password protection, poor device management, and MitM attacks. In comparison with sharding-based blockchain technology, it results in eavesdropping, routing attacks, MitM attacks, DoS, and data tampering [24].
- Encryption: Encryption is another important threat that should be focused on IoT devices. These result in corrupting the data by compromising the security of IoT devices, along with weak passwords that can be easily cracked by attackers, and poor encryption which put the data sending and receiving information at risk. Compared to sharding-based blockchain technology, significant encryption issues such as data integrity, confidentiality, authenticity, scalability, and key management can occur [46].
- Communication: Security issues relating to communication also occur within IoT devices due to DNS threats, leading to issues including data integrity, firmware exploits that can be exploited by attackers, insecure interfaces leading to security issues, and brute force attacks where attackers use possible username and passwords to find the correct combination. Compared to sharding-based blockchain technology, several communication security issues such as replay attacks, MitM attacks, DoS, eavesdropping, and data tampering can occur [29,78].
- Resistance to cyberattacks: Mostly, IoT devices largely focus on connectivity instead of security, which leads to the inadequate management of the device because of a lack of built-in safeguards, not supporting the installation of endpoint agents, not producing logs, and an inability to be updated and patched easily. In comparison with sharding-based technology, it can result in Sybil attacks, eclipse attacks, DoS, DDoS, and quantum computer attacks [43,54].
3.5. Existing Projects That Have Implemented Blockchain Technology in the IoT
4. Discussion
4.1. Impact of Sharding-Based Blockchain Network Technology in Securing IoT Sensors
4.2. Benefits of Sharding-Based Blockchain Technology Network in Securing IoT Sensors
4.3. Challenges of Sharding-Based Blockchain Network Technology in Securing IoT Sensors
- Replay attacks.
- Consistency issues.
- Synchronization issues.
- A cross-shard transaction protocol to ensure the security and consistency of transactions.
- Synchronization mechanisms to ensure that all the nodes view the blockchain state in a similar manner.
4.4. Gaps
5. Conclusions
5.1. Future Research Directions
5.2. Contributions to the Research
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Shirvanian, N.; Shams, M.; Rahmani, A.M. Internet of Things data management: A systematic literature review, vision, and future trends. Int. J. Commun. Syst. 2022, 35, e5267. [Google Scholar] [CrossRef]
- Viriyasitavat, W.; Anuphaptrirong, T.; Hoonsopon, D. When blockchain meets Internet of Things: Characteristics, challenges, and business opportunitie. J. Ind. Inf. Integr. 2019, 15, 21–28. [Google Scholar] [CrossRef]
- Hashim, F.; Shuaib, K.; Zaki, N. Sharding for scalable blockchain networks. SN Comput. Sci. 2022, 4, 2. [Google Scholar] [CrossRef]
- Dang, H.; Dinh, T.; Loghin, D.; Chang, E.; Lin, Q.; Ooi, B. Towards scaling blockchain systems via sharding. In Proceedings of the 2019 International Conference on Management of Data, Amsterdam, The Netherlands, 30 June–5 July 2019; pp. 123–140. [Google Scholar]
- Yu, D.; Xu, H.; Zhang, L.; Cao, B.; Imran, M. Security analysis of sharding in the blockchain system. In Proceedings of the 2021 IEEE 32nd Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Helsinki, Finland, 13–16 September 2021; pp. 1030–1035. [Google Scholar]
- Zhang, P.; Guo, W.; Liu, Z.; Zhou, M.; Huang, B.; Sedraoui, K. Optimized blockchain sharding model based on node trust and allocation. IEEE Trans. Netw. Serv. Manag. 2023, 20, 2804–2816. [Google Scholar] [CrossRef]
- Liu, X.; Xie, H.; Yan, Z.; Liang, X. A survey on blockchain sharding. ISA Trans. 2023, 141, 30–43. [Google Scholar] [CrossRef] [PubMed]
- Chigbu, U.; Atiku, S.; Plessis, C.D. The Science of Literature Reviews: Searching, Identifying, Selecting, and Synthesising. Publications 2023, 11, 2. [Google Scholar] [CrossRef]
- Azarian, M.; Yu, H.; Shiferaw, A.T.; Stevik, T.K. Do We Perform Systematic Literature Review Right? A Scientific Mapping and Methodological Assessment. Logistics 2023, 7, 89. [Google Scholar] [CrossRef]
- Smela, B.; Toumi, M.; Świerk, K.; Francois, C.; Biernikiewicz, M.; Clay, E.; Boyer, L. Rapid literature review: Definition and methodology. J. Mark. Access Health Policy 2023, 11, 2241234. [Google Scholar] [CrossRef] [PubMed]
- Atkinson, C. Cheap, quick, and rigorous: Artificial intelligence and the systematic literature review. Soc. Sci. Comput. Rev. 2024, 42, 376–393. [Google Scholar] [CrossRef]
- Cabrera, D.; Cabrera, L. The steps to doing a Systems literature review (SLR). J. Syst. Think. Prepr. 2023. [Google Scholar]
- Varsha, P.; Chakraborty, A.; Kar, A. How to Undertake an Impactful Literature Review: Understanding Review Approaches and Guidelines for High-impact Systematic Literature Reviews. South Asian J. Bus. Manag. Cases 2024, 13, 18–35. [Google Scholar] [CrossRef]
- Uttley, L.; Quintana, D.; Montgomery, P.; Carroll, C.; Page, M.; Falzon, L.; Sutton, A.; Moher, D. The problems with systematic reviews: A living systematic review. J. Clin. Epidemiol. 2023, 156, 30–41. [Google Scholar] [CrossRef] [PubMed]
- Hiebl, M. Sample selection in systematic literature reviews of management research. Organ. Res. Methods 2023, 26, 229–261. [Google Scholar] [CrossRef]
- García-Peñalvo, F. Developing robust state-of-the-art reports: Systematic Literature Reviews. Educ. Knowl. Soc. 2022. [Google Scholar]
- Wasserfuhr, V. A Literature Review of Methods, Approaches and Tools to Automate the Process of Systematic Literature Reviews. Master’s Thesis, University of Twent, Enschede, The Netherlands, 2022. [Google Scholar]
- Braun, V.; Clarke, V. Conceptual and design thinking for thematic analysis. Qual. Psychol. 2022, 9, 3. [Google Scholar] [CrossRef]
- Squires, V. Thematic analysis. In Varieties of Qualitative Research Methods: Selected Contextual Perspectives; Springer International Publishing: Cham, Switzerland, 2023; pp. 463–468. [Google Scholar]
- Sauer, P.; Seuring, S. How to conduct systematic literature reviews in management research: A guide in 6 steps and 14 decisions. Rev. Manag. Sci. 2023, 17, 899–933. [Google Scholar] [CrossRef]
- Freire, W.P.; Melo, W.S., Jr.; do Nascimento, V.D.; Nascimento, P.R.; de Sá, A.O. Towards a secure and scalable maritime monitoring system using blockchain and Low-Cost IoT technology. Sensors 2022, 22, 4895. [Google Scholar] [CrossRef] [PubMed]
- Shin, Y.; Jeon, S. MQTREE: Secure OTA Protocol using MQTT and MerkleTree. Sensors 2024, 24, 1447. [Google Scholar] [CrossRef] [PubMed]
- Antwi, R.; Gadze, J.D.; Tchao, E.T.; Sikora, A.; Nunoo-Mensah, H.; Agbemenu, A.S.; Obour Agyekum, K.O.B.; Agyemang, J.O.; Welte, D.; Keelson, E. A survey on network Optimization techniques for blockchain systems. Algorithms 2022, 15, 193. [Google Scholar] [CrossRef]
- Albakri, A.; Alshahrani, R.; Alharbi, F.; Ahamed, S.B. Fully Homomorphic Encryption with Optimal Key Generation Secure Group Communication in Internet of Things Environment. Appl. Sci. 2023, 13, 6055. [Google Scholar] [CrossRef]
- Akrasi-Mensah, N.K.; Tchao, E.T.; Sikora, A.; Agbemenu, A.S.; Nunoo-Mensah, H.; Ahmed, A.R.; Welte, D.; Keelson, E. An overview of technologies for improving storage efficiency in Blockchain-Based IIoT applications. Electronics 2022, 11, 2513. [Google Scholar] [CrossRef]
- Khan, M.; Hartog, F.D.; Hu, J. Toward Verification of DAG-Based Distributed Ledger Technologies through Discrete-Event Simulation. Sensors 2024, 24, 1583. [Google Scholar] [CrossRef]
- Lee, J.; Kim, W. DAG-Based Blockchain Sharding for Secure Federated Learning with Non-IID Data. Sensors 2022, 22, 8263. [Google Scholar] [CrossRef]
- Chen, R.; Wang, L.; Peng, C.; Zhu, R. An effective sharding consensus algorithm for blockchain systems. Electronics 2022, 11, 2597. [Google Scholar] [CrossRef]
- Zhao, Y.; Ding, N. Cache optimization methods involving node and content sharding of blockchain in internet of vehicles. Electronics 2024, 13, 560. [Google Scholar] [CrossRef]
- Ali, W.; Ahmed, A.A. An Authenticated Group Shared Key Mechanism Based on a Combiner for Hash Functions over the Industrial Internet of Things. Processes 2023, 11, 1558. [Google Scholar] [CrossRef]
- Cholevas, C.; Angeli, E.; Sereti, Z.; Mavrikos, E.; Tsekouras, G.E. Anomaly detection in blockchain networks using Unsupervised Learning: A survey. Algorithms 2024, 17, 201. [Google Scholar] [CrossRef]
- Prieto, J.; Durán Barroso, R.J. Emerging technologies in edge computing and networking. Sensors 2024, 24, 1271. [Google Scholar] [CrossRef] [PubMed]
- Alam, T. Blockchain-Based Internet of Things: Review, current trends, applications, and future challenges. Computers 2022, 12, 6. [Google Scholar] [CrossRef]
- Pelekoudas-Oikonomou, F.; Zachos, G.; Papaioannou, M.; de Ree, M.; Ribeiro, J.C.; Mantas, G.; Rodriguez, J. Blockchain-Based security mechanisms for IOMT edge networks in IOMT-Based healthcare monitoring systems. Sensors 2022, 22, 2449. [Google Scholar] [CrossRef]
- Kandpal, M.; Goswami, V.; Priyadarshini, R.; Barik, R.K. Towards data storage, scalability, and availability in blockchain systems: A bibliometric analysis. Data 2023, 8, 148. [Google Scholar] [CrossRef]
- George, W.; Al-Ansari, T. Review of blockchain applications in food supply chain. Blockchains 2023, 1, 34–57. [Google Scholar] [CrossRef]
- Marco-Detchart, C.; Carrascosa, C.; Julian, V.; Rincon, J. Robust Multi-Sensor consensus plant disease detection using the choquet integral. Sensors 2023, 23, 2382. [Google Scholar] [CrossRef]
- Hashim, F.; Shuaib, K.; Sallabi, F. MedShard: Electronic Health record Sharing using Blockchain sharding. Sustainability 2022, 13, 5889. [Google Scholar] [CrossRef]
- Ahakonye, L.A.C.; Nwakanma, C.I.; Kim, D.S. Tides of Blockchain in IoT Cybersecurity. Sensors 2024, 24, 3111. [Google Scholar] [CrossRef] [PubMed]
- Na, D.; Park, S. IoT-Chain and Monitoring-Chain using multilevel blockchain for IoT security. Sensors 2022, 22, 8271. [Google Scholar] [CrossRef] [PubMed]
- Adhikari, N.; Ramkumar, M. IoT and Blockchain Integration: Applications, Opportunities, and Challenges. Network 2023, 3, 115–141. [Google Scholar] [CrossRef]
- Zubaydi, H.D.; Varga, P.; Molnár, S. Leveraging blockchain technology for ensuring security and privacy aspects in Internet of Things: A Systematic Literature review. Sensors 2023, 23, 788. [Google Scholar] [CrossRef] [PubMed]
- Arachchige, K.G.; Branch, P.; But, J. An analysis of Blockchain-Based IoT sensor network distributed denial of service attacks. Sensors 2024, 24, 3083. [Google Scholar] [CrossRef]
- Wang, X.; Guan, Y. A hierarchy Byzantine fault tolerance consensus protocol based on node reputation. Sensors 2022, 22, 5887. [Google Scholar] [CrossRef] [PubMed]
- Taherdoost, H. Blockchain-Based internet of medical things. Appl. Sci. 2023, 13, 1287. [Google Scholar] [CrossRef]
- Zhao, J.; Zhang, D.; Liu, W.; Qiu, X.; Brusic, V. DHT-Based Blockchain Dual-Sharding Storage Extension Mechanism. Appl. Sci. 2022, 12, 9635. [Google Scholar] [CrossRef]
- Kuleto, V.; Bucea-Manea-Țoniş, R.; Bucea-Manea-Țoniş, R.; Ilić, M.P.; Martins, O.M.; Ranković, M.; Coelho, A.S. The potential of blockchain technology in higher education as perceived by students in Serbia, Romania, and Portugal. Sustainability 2022, 14, 749. [Google Scholar] [CrossRef]
- Wenhua, Z.; Qamar, F.; Abdali, T.A.N.; Hassan, R.; Jafri, S.T.A.; Nguyen, Q.N. Blockchain technology: Security issues, healthcare applications, challenges and future trends. Electronics 2023, 12, 546. [Google Scholar] [CrossRef]
- Schmid, P.; Schaffhäuser, A.; Kashef, R. IoTBChain: Adopting Blockchain Technology to Increase PLC Resilience in an IoT Environment. Information 2023, 14, 437. [Google Scholar] [CrossRef]
- Guo, X.; Zhang, G.; Zhang, Y. A Comprehensive review of Blockchain Technology-Enabled Smart Manufacturing: A Framework, challenges and future research directions. Sensors 2022, 23, 155. [Google Scholar] [CrossRef]
- Florea, A.I.; Anghel, I.; Cioara, T. A review of blockchain technology applications in ambient Assisted living. Future Internet 2022, 14, 150. [Google Scholar] [CrossRef]
- Jafar, U.; Ab Aziz, M.J.; Shukur, Z.; Hussain, H.A. A Systematic Literature Review and Meta-Analysis on Scalable Blockchain-Based Electronic Voting Systems. Sensors 2022, 22, 7585. [Google Scholar] [CrossRef] [PubMed]
- Hafid, A.; Hafid, A.S.; Makrakis, D. Sharding-Based Proof-of-Stake Blockchain Protocols: Key Components & Probabilistic Security Analysis. Sensors 2023, 23, 2819. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Mishra, A. Techniques to alleviate blockchain bloat: Potentials, challenges, and recommendations. Comput. Electr. Eng. 2024, 116, 109216. [Google Scholar] [CrossRef]
- Lai, R.; Zhao, G.; He, Y.; Hou, Z. A Robust Sharding-Enabled Blockchain with Efficient Hashgraph Mechanism for MANETs. Appl. Sci. 2023, 13, 8726. [Google Scholar] [CrossRef]
- Shitharth, S.; Manoharan, H.; Shankar, A.; Alsowail, R.A.; Pandiaraj, S.; Edalatpanah, S.A.; Viriyasitavat, W. Federated learning optimization: A computational blockchain process with offloading analysis to enhance security. Egypt. Inform. J. 2023, 24, 100406. [Google Scholar] [CrossRef]
- Vladyko, A.; Elagin, V.; Spirkina, A.; Muthanna, A.; Ateya, A.A. Distributed Edge Computing with Blockchain Technology to Enable Ultra-Reliable Low-Latency V2X Communications. Electronics 2022, 11, 173. [Google Scholar] [CrossRef]
- Bhat, S.A.; Huang, N.F.; Sofi, I.B.; Sultan, M. Agriculture-Food Supply chain Management Based on Blockchain and IoT: A Narrative on Enterprise Blockchain Interoperability. Agriculture 2022, 12, 40. [Google Scholar] [CrossRef]
- Ali, A.; Almaiah, M.A.; Hajjej, F.; Pasha, M.F.; Fang, O.H.; Khan, R.; Teo, J.; Zakarya, M. An industrial IoT-Based Blockchain-Enabled secure searchable encryption approach for healthcare systems using neural network. Sensors 2022, 22, 572. [Google Scholar] [CrossRef] [PubMed]
- Alajlan, R.; Alhumam, N.; Frikha, M. Cybersecurity for Blockchain-Based IoT Systems: A review. Appl. Sci. 2023, 13, 7432. [Google Scholar] [CrossRef]
- Bobde, Y.; Narayanan, G.; Jati, M.; Raj, R.S.P.; Cvitić, I.; Peraković, D. Enhancing Industrial IoT Network Security through Blockchain Integration. Electronics 2024, 13, 687. [Google Scholar] [CrossRef]
- Liu, C.; Wan, J.; Li, L.; Yao, B. Throughput Optimization for Blockchain System with Dynamic Sharding. Electronics 2023, 12, 4915. [Google Scholar] [CrossRef]
- Wijesekara, P.A.D.S.N.; Gunawardena, S. A review of Blockchain Technology in Knowledge-Defined Networking, its application, benefits, and challenges. Network 2023, 3, 343–421. [Google Scholar] [CrossRef]
- Ali, A.; Al-Rimy, B.A.S.; Alsubaei, F.S.; Almazroi, A.A.; Almazroi, A.A. HealthLock: Blockchain-Based privacy preservation using homomorphic encryption in internet of things healthcare applications. Sensors 2023, 23, 6762. [Google Scholar] [CrossRef]
- Huang, H.; Peng, X.; Zhan, J.; Zhang, S.; Lin, Y.; Zheng, Z.; Guo, S. Brokerchain: A cross-shard blockchain protocol for account/balance-based state sharding. In Proceedings of the IEEE INFOCOM 2022-IEEE Conference on Computer Communications, London, UK, 2–5 May 2022; pp. 1968–1977. [Google Scholar]
- Alshahrani, H.; Islam, N.; Syed, D.; Sulaiman, A.; Al Reshan, M.S.; Rajab, K.; Shaikh, A.; Shuja-Uddin, J.; Soomro, A. Sustainability in Blockchain: A Systematic literature review on scalability and power consumption issues. Sensors 2023, 16, 1510. [Google Scholar] [CrossRef]
- Cai, T.; Chen, W.; Zhang, J.; Zheng, Z. SmartChain: A Dynamic and Self-Adaptive Sharding Framework for IoT Blockchain. IEEE Trans. Serv. Comput. 2024, 17, 674–688. [Google Scholar] [CrossRef]
- Yuan, S.; Cao, B.; Sun, Y.; Wan, Z.; Peng, M. Secure and efficient federated learning through layering and sharding blockchain. IEEE Trans. Netw. Sci. Eng. 2024, 11, 3120–3134. [Google Scholar] [CrossRef]
- Zheng, P.; Xu, Q.; Zheng, Z.; Zhou, Z.; Yan, Y.; Zhang, H. Meepo: Multiple execution environments per organization in sharded consortium blockchain. IEEE J. Sel. Areas Commun. 2022, 40, 3562–3574. [Google Scholar] [CrossRef]
- Shi, J.; Zeng, X.; Li, Y. Reputation-Based sharding consensus model in Information-Centric networking. Electronics 2022, 11, 830. [Google Scholar] [CrossRef]
- Valadares, D.C.G.; Perkusich, A.; Martins, A.F.; Kamel, M.B.; Seline, C. Privacy-Preserving blockchain technologies. Sensors 2023, 23, 7172. [Google Scholar] [CrossRef] [PubMed]
- Han, H.; Chen, S.; Xu, Z.; Dong, X.; Zeng, J. Trust Management Scheme of IOV based on dynamic sharding Blockchain. Electronics 2024, 13, 1016. [Google Scholar] [CrossRef]
- Christidis, J.; Karkazis, P.A.; Papadopoulos, P.; Leligou, H.C. Decentralized Blockchain-Based IoT Data Marketplaces. J. Sens. Actuator Netw. 2022, 11, 39. [Google Scholar] [CrossRef]
- Alsadhan, A.; Alhogail, A.; Alsalamah, H. Blockchain-Based Privacy Preservation for the Internet of Medical Things: A Literature Review. Electronics 2024, 13(19), 3832. [Google Scholar] [CrossRef]
- Olanrewaju, R.F.; Khan, B.U.I.; Kiah, M.L.M.; Abdullah, N.A.; Goh, K.W. Decentralized blockchain network for Resisting Side-Channel Attacks in Mobility-Based IoT. Electronics 2022, 11, 3982. [Google Scholar] [CrossRef]
- Musa, H.S.; Krichen, M.; Altun, A.A.; Ammi, M. Survey on Blockchain-Based Data Storage Security for Android Mobile Applications. Sensors 2023, 23, 8749. [Google Scholar] [CrossRef]
- Wu, J.; Du, H.; Chen, J.; Ren, W. Solving Confirmation Time in Sharded Blockchain with PFQN. Electronics 2024, 13, 1220. [Google Scholar] [CrossRef]
- Huang, H.; Zhao, Q.; Ran, X. Secure sharding scheme of blockchain-based on reputation. In Proceedings of the 2022 IEEE 2nd International Conference on Data Science and Computer Application (ICDSCA), Dalian, China, 28–30 October 2022; pp. 1324–1327. [Google Scholar]




| Themes |
|---|
| 1. Impact of sharding-based blockchain network technology in securing IoT sensors |
| 2. Benefits of sharding-based blockchain technology network in securing IoT sensors |
| 3. Challenges of sharding-based blockchain network technology in securing IoT sensors |
| Reference | Methodology | Consensus Algorithm | Key Findings |
|---|---|---|---|
| Freire et al. (2022) [21] | Primary quantitative method | AISs |
|
| Shin and Jeon (2024) [22] | Secondary method | SHA-256 hash algorithm |
|
| Antwi et al. (2022) [23] | Primary quantitative method | PBFT, RBFT, WBFT |
|
| Albakri et al. (2023) [24] | Secondary method | PTA, SCA |
|
| Kuleto et al. (2022) [47] | Primary method | Unspecified |
|
| Akrasi-Mensah et al. (2022) [25] | Secondary method | Compression algorithm, NSGA-C, MA-DDPG, PoR |
|
| Khan, Hartog, and Hu (2024) [26] | Primary quantitative method | RSA, TSA |
|
| Lee and Kim (2022) [27] | Secondary method | PoW, DRL |
|
| Chen et al. (2022) [28] | Secondary method | Jump consistent hash algorithm |
|
| Ali and Ahmed (2023) [30] | Secondary method | AGSK |
|
| Wang and Guan (2022) [44] | Secondary qualitative method | HBFT |
|
| Cholevas et al. (2024) [31] | Primary quantitative method | Avant-garde algorithm |
|
| Prieto and Barroso (2024) [32] | Secondary method | Unspecified |
|
| Zhao and Ding (2024) [29] | Secondary method | TDGA |
|
| George and Al-Ansari (2023) [36] | Secondary method | Hash algorithm |
|
| Marco-Detchart et al. (2023) [37] | Secondary method | Data fusion algorithm |
|
| Alam (2022) [33] | Secondary method | Sha-256 cryptographic algorithm |
|
| Ahakonye, Nwakanma, and Kim (2024) [39] | Secondary method | DDoS, prompting control algorithm |
|
| Na and Park, (2022) [40] | Secondary method | PoW, PBFT |
|
| Zubaydi, Varga, and Molnár (2023) [42] | Primary quantitative method | PoA |
|
| Arachchige, Branch, and But (2024) [43] | Secondary method | DDoS, XXHASH algorithm |
|
| Adhikari and Ramkumar (2023) [41] | Secondary method | BCN |
|
| Taherdoost (2023) [45] | Secondary method | Unspecified |
|
| Schmid, Schaffhäuser, and Kashef (2023) [49] | Secondary method | PoW |
|
| Zhao et al. (2022) [46] | Secondary method | Hybrid query algorithm |
|
| Wenhua et al. (2023) [48] | Secondary method | PoW |
|
| References | Service Quality | Efficacy | Scalability | Security |
|---|---|---|---|---|
| Freire et al. (2022) [21] | Positively affects the service quality | Effective and feasible solution | - | - |
| Shin and Jeon (2024) [22] | - | Fortifies efficacy of firmware update | - | - |
| Antwi et al. (2022) [23] | - | - | - | IoT calls are secured |
| Albakri et al. (2023) [24] | - | Effective through data routing | - | Improves communication process |
| Kuleto et al. (2022) [47] | - | - | - | Provides security and offers anonymity |
| Akrasi-Mensah et al. (2022) [25] | - | Storage efficiency | - | - |
| Khan, Hartog, and Hu (2024) [26] | - | Effective in node convergence | - | - |
| Lee and Kim (2022) [27] | Potential performance bottlenecks | - | - | Provides security to model-poisoning attacks |
| Chen et al. (2022) [28] | Improved cross-shard transaction | - | - | Enhanced security |
| Ali and Ahmed (2023) [30] | High productivity | - | - | Countermeasures against cyberattacks |
| Wang and Guan (2022) [44] | Better performance | - | - | Improved security and integrity |
| Cholevas et al. (2024) [31] | - | - | - | Improved security and integrity |
| Prieto and Barroso (2024) [32] | Generates large data volume | Efficient technology | Increased scalability | - |
| Zhao and Ding (2024) [29] | - | Optimizes effectively | - | Enhanced data security needs |
| George and Al-Ansari (2023) [36] | - | - | - | Vital in food security |
| Marco-Detchart et al. (2023) [37] | Better robustness and classification process | Effective in determining diseases | - | - |
| Alam (2022) [33] | - | - | - | Increased data security |
| Ahakonye, Nwakanma, and Kim (2024) [39] | Enhanced performance | - | Increased scalability | - |
| Na and Park (2022) [40] | - | Vulnerabilities are resolved effectively | - | - |
| Zubaydi, Varga, and Molnár (2023) [42] | - | Provides effective solution | - | Concerned about data security |
| Arachchige, Branch, and But (2024) [43] | - | - | - | Determines vulnerable attacks |
| Adhikari and Ramkumar, (2023) [41] | Validate transactions and maintain ledger | - | - | - |
| Taherdoost, (2023) [45] | - | - | Better scalability | - |
| Schmid, Schaffhäuser, and Kashef (2023) [49] | - | - | - | Maintain security |
| Zhao et al. (2022) [46] | - | Effective transaction query | - | - |
| Wenhua et al. (2023) [48] | Better transaction process | - | - | Better security |
| Reference | Methodology | Consensus Algorithm | Key Findings |
|---|---|---|---|
| Guo, Zhang, and Zhang (2022) [50] | Quantitative method | PoW, PoS, DPoS, PBFT |
|
| Florea, Anghel, and Cioara (2022) [51] | Secondary method | IPFS |
|
| Hafid, Hafid, and Makrakis (2023) [53] | Secondary method | PoS |
|
| Jafar et al. (2022) [52] | Secondary method | DSA, RSA, ECC |
|
| Alzoubi and Mishra (2024) [54] | Secondary method | Unspecified |
|
| Lai et al. (2023) [55] | Secondary method | Unspecified |
|
| Prieto and Barroso (2024) [32] | Secondary method | Unspecified |
|
| Shitharth et al. (2023) [56] | Secondary method | Unspecified |
|
| Vladyko et al. (2022) [57] | Secondary method | PBFT |
|
| Alajlan, Alhumam, and Frikha (2023) [60] | Secondary method | Unspecified |
|
| Bobde et al. (2024) [61] | Secondary method | PoA |
|
| Zubaydi, Varga, and Molnár (2023) [42] | Primary quantitative method | PoA |
|
| Arachchige, Branch, and But (2024) [43] | Secondary method | DDoS, XXHASH algorithm |
|
| Ali et al. (2023) [64] | Secondary methods | BSS |
|
| Liu et al. (2023) [62] | Secondary method | BDQ |
|
| Wijesekara and Gunawardena (2023) [63] | Secondary method | SIDH, DAG, digital |
|
| Wenhua et al. (2023) [48] | Secondary method | PoW |
|
| Bhat et al. (2022) [58] | Secondary method | PoW, PoS |
|
| Pelekoudas-Oikonomou et al. (2022) [34] | secondary method | PoW |
|
| References | Scalability | Security | Effectiveness | Trustworthiness |
|---|---|---|---|---|
| Guo, Zhang, and Zhang (2022) [50] | Increased scalability | - | Increased efficiency | - |
| Florea, Anghel, and Cioara (2022) [51] | - | Secure data transfer | - | - |
| Hafid, Hafid, and Makrakis (2023) [53] | Better scalability if not limited | - | - | - |
| Jafar et al. (2022) [52] | - | - | Saves time, cost-effective, and better speed | - |
| Alzoubi and Mishra (2024) [54] | - | - | - | Handles and bundles transaction |
| Lai et al. (2023) [55] | - | Secures technology | Efficiently prevents Sybil attacks | - |
| Prieto and Barroso, (2024) [32] | Increased scalability | - | - | - |
| Shitharth et al. (2023) [56] | - | Secures data processing | - | - |
| Vladyko et al. (2022) [57] | - | - | Energy-efficient and manages traffic | - |
| Alajlan, Alhumam, and Frikha (2023) [60] | Increased transparency | Improved security | - | - |
| Bobde et al. (2024) [61] | - | Increased security | - | Increased trustworthiness |
| Zubaydi, Varga, and Molnár (2023) [42] | - | Better security and anonymity | - | - |
| Arachchige, Branch, and But (2024) [43] | - | Improved security | Effective decentralization and encryption | - |
| Ali et al. (2023) [64] | Provides transparency | Offers security | Cost-effective and efficient | - |
| Liu et al. (2023) [62] | - | - | Effectively overcomes space issues | - |
| Wijesekara and Gunawardena (2023) [63] | - | Secured transactions | - | Develops trustworthiness |
| Wenhua et al. (2023) [48] | Offers decentralized solution | Data integrity and confidentiality | - | - |
| Bhat et al. (2022) [58] | - | Mitigates security threats | - | Enhances customer trust |
| Pelekoudas-Oikonomou et al. (2022) [34] | Offers better life quality | - | Abstain unauthorized access | - |
| Reference | Methodology | Consensus Algorithms | Key Findings |
|---|---|---|---|
| Huang et al. (2022) [65] | Primary quantitative method | Unspecified |
|
| Alshahrani et al. (2023) [66] | Secondary method | QoS and Ethereum |
|
| Cai et al. (2024) [67] | Secondary method | Unspecified |
|
| Antwi et al. (2022) [23] | Primary quantitative method | PBFT, RBFT, WBFT |
|
| Florea, Anghel, and Cioara (2022) [51] | Secondary method | IPFS |
|
| Yuan et al. (2024) [68] | Secondary method | Unspecified |
|
| Huang et al. (2022) [78] | Secondary method | PoS, PoW, CFT, BFT |
|
| Zheng et al. (2022) [69] | Secondary method | Unspecified |
|
| Hafid, Hafid, and Makrakis (2023) [53] | Secondary method | PoS |
|
| Jafar et al. (2022) [52] | Secondary method | DSA, RSA, ECC |
|
| Shi, Zeng, and Li (2022) [70] | Secondary method | AP algorithm |
|
| Alzoubi and Mishra (2024) [54] | Secondary method | Unspecified |
|
| Ali and Ahmed (2023) [30] | Secondary method | AGSK |
|
| Wang and Guan (2022) [44] | Secondary qualitative method | HBFT |
|
| Zhao and Ding (2024) [29] | Secondary method | TDGA |
|
| Valadares et al. (2023) [71] | Secondary method | Byzantine fault-tolerant, Diffie–Hellman |
|
| Han et al. (2024) [72] | Secondary method | Graph-partitioning algorithm |
|
| Ahakonye, Nwakanma, and Kim (2024) [39] | Secondary method | DDoS, prompting control algorithm |
|
| Zubaydi, Varga, and Molnár (2023) [42] | Primary quantitative method | PoA |
|
| Adhikari and Ramkumar (2023) [41] | Secondary method | BCN |
|
| Schmid, Schaffhäuser, and Kashef (2023) [49] | Secondary method | PoW |
|
| Ali et al. (2022) [59] | Secondary methods | BSS |
|
| Olanrewaju et al. (2022) [75] | Secondary method | Sophisticated hashing algorithm |
|
| Huang, Zhao, and Ran (2022) [78] | Secondary method | Unspecified |
|
| Wijesekara and Gunawardena (2023) [63] | Secondary method | SIDH, DAG, digital signature algorithm |
|
| Musa et al. (2023) [76] | Primary quantitative method | PoW, PoS |
|
| Wu et al. (2024) [77] | Secondary qualitative method, | PQFN |
|
| Christidis et al. (2022) [73] | Secondary method | Unspecified |
|
| Hashim, Shuaib, and Sallabi (2022) [38] | Secondary method | PoA |
|
| Ali et al. (2023) [64] | Secondary method | ECC, hybrid encryption framework algorithm |
|
| References | Scalability | Security | Interoperability | Transactional Issues |
|---|---|---|---|---|
| Huang et al. (2022) [65] | - | - | - | Imbalanced transaction distribution |
| Alshahrani et al. (2023) [66] | Scalability issues and power consumption | - | - | - |
| Cai et al. (2024) [67] | - | Failed security and throughput | - | - |
| Antwi et al. (2022) [23] | Scalability issues | Restricts achieving throughput | - | - |
| Florea, Anghel, and Cioara (2022) [51] | - | Data personalization | Interoperability issues | Transactional costs |
| Yuan et al. (2024) [68] | - | - | Complex communication | Limited transaction throughput |
| Huang et al. (2022) [78] | - | Increased e-waste affects the environment | - | - |
| Zheng et al. (2022) [69] | - | - | - | Strict transaction atomicity and consortium issues |
| Hafid, Hafid, and Makrakis (2023) [53] | Good throughput and performance | Security issues and reasonable latency | - | - |
| Jafar et al. (2022) [52] | Scalability issues | Data integrity, privacy, and transparency | - | - |
| Shi, Zeng, and Li (2022) [70] | Scalability issues | Cybersecurity issues | Reduced efficiency | - |
| Alzoubi and Mishra (2024) [54] | - | Data loss, security, and privacy | - | |
| Ali and Ahmed (2023) [30] | - | - | Secured communication | - |
| Wang and Guan (2022) [44] | - | - | Communication difficulties | Transaction consistency |
| Zhao and Ding (2024) [29] | Affects performance | - | - | - |
| Valadares et al. (2023) [71] | - | Data security and privacy | Traceability issues | - |
| Han et al. (2024) [72] | Reduced performance | - | - | - |
| Ahakonye, Nwakan-ma, and Kim (2024) [39] | - | Cybersecurity and privacy issues | Resource constraints | - |
| Zubaydi, Varga, and Molnár (2023) [42] | Scalability and legal issues | - | - | Scalability of transaction rates |
| Adhikari and Ram Kumar (2023) [41] | Scalability issues | Security concerns | Interoperability concerns | - |
| Schmid, Schaffhäuser, and Kashef (2023) [49] | - | Privacy and security concerns | - | - |
| Ali et al. (2022) [59] | - | Security and confidentiality issues | - | - |
| Olanrewaju et al. (2022) [75] | Latency, computational overhead | Security architecture | - | - |
| Huang, Zhao, and Ran (2022) [78] | Insufficient scalability | - | - | Maximizes transaction process |
| Wijesekara and Guna-wardena (2023) [63] | Increased energy consumption and scalability issues | Data processing issues | - | - |
| Musa et al. (2023) [76] | Scalability and performance issues | - | - | Transactional costs issues |
| Wu et al. (2024) [77] | - | - | - | Extended transaction confirmation and delay |
| Christidis et al. (2022) [73] | - | - | Uncertain authenticity and limited storage | - |
| Hashim, Shuaib, and Sallabi (2022) [38] | Scalability issues, ledger replication | - | - | - |
| Ali et al. (2023) [74] | - | Data confidentiality and privacy | - | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aslam, A.; Postolache, O.; Oliveira, S.; Pereira, J.D. Securing IoT Sensors Using Sharding-Based Blockchain Network Technology Integration: A Systematic Review. Sensors 2025, 25, 807. https://doi.org/10.3390/s25030807
Aslam A, Postolache O, Oliveira S, Pereira JD. Securing IoT Sensors Using Sharding-Based Blockchain Network Technology Integration: A Systematic Review. Sensors. 2025; 25(3):807. https://doi.org/10.3390/s25030807
Chicago/Turabian StyleAslam, Ammad, Octavian Postolache, Sancho Oliveira, and José Dias Pereira. 2025. "Securing IoT Sensors Using Sharding-Based Blockchain Network Technology Integration: A Systematic Review" Sensors 25, no. 3: 807. https://doi.org/10.3390/s25030807
APA StyleAslam, A., Postolache, O., Oliveira, S., & Pereira, J. D. (2025). Securing IoT Sensors Using Sharding-Based Blockchain Network Technology Integration: A Systematic Review. Sensors, 25(3), 807. https://doi.org/10.3390/s25030807










