This paper presents a novel ASVM-GWO-IDEA for safeguarding cloud data in data transmission to shield the data owner’s medical records from intrusion and cyberattacks.
4.1. Medical Data Collection
Initially, medical data were gathered from an IoT-cloud-based healthcare environment. The healthcare environment included hospital centers, patients, cloud storage, and IoT devices. The patient information was collected using wearable sensors such as glucose meters, breathing sensors, accelerometers, and temperature sensors. The gathered information included the patient’s medical data, including temperature, glucose levels, blood pressure, heart rate, pulse rate, sugar level, cholesterol level, oxygen levels, etc. The gathered data were transmitted to the cloud for centralized storage. The presented study utilized the publicly available medical database named “Healthcare-IoT database [
35]”. This database simulates sensor data accumulated from wearable devices in an IoT-assisted healthcare framework, and the information resembles a patient’s health information, such as blood pressure, patient ID, timestamp, sensor type and ID, heart rate, temperature, battery level, and health status. These data were transmitted to healthcare centers for remote monitoring. The database is available in CSV form on the Kaggle site, and its size is 10.86 GB.
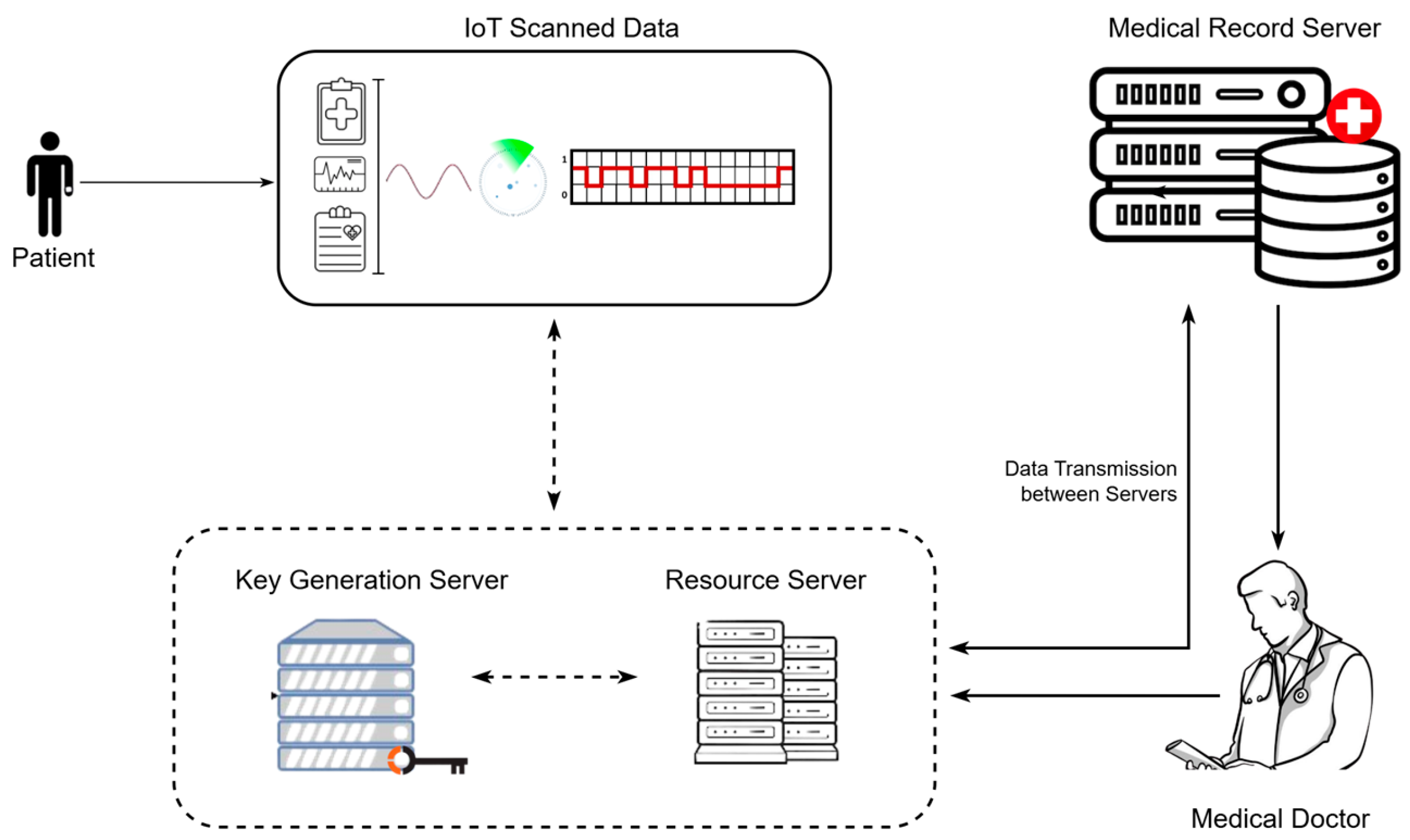
Furthermore, the medical data of data owners in hospitals were taken to evaluate the unauthorized access detection procedure. Consequently, an optimized public cloud scheme was developed to enhance the confidentiality and security of stored medical data in the cloud. As a result, the new ASVM-based GWO-IDEA model was developed in the Python environment. The proposed architecture is detailed in
Figure 3.
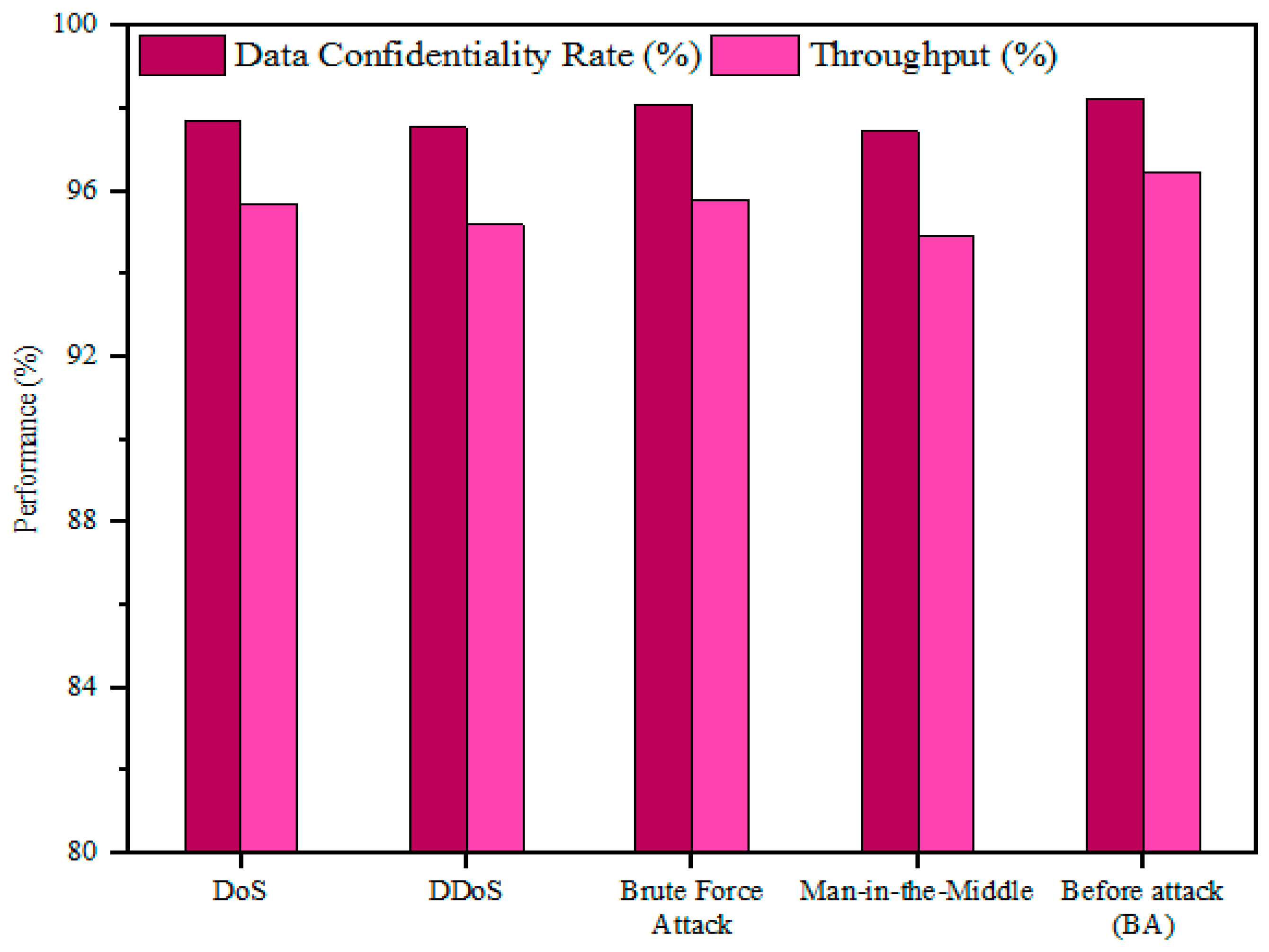
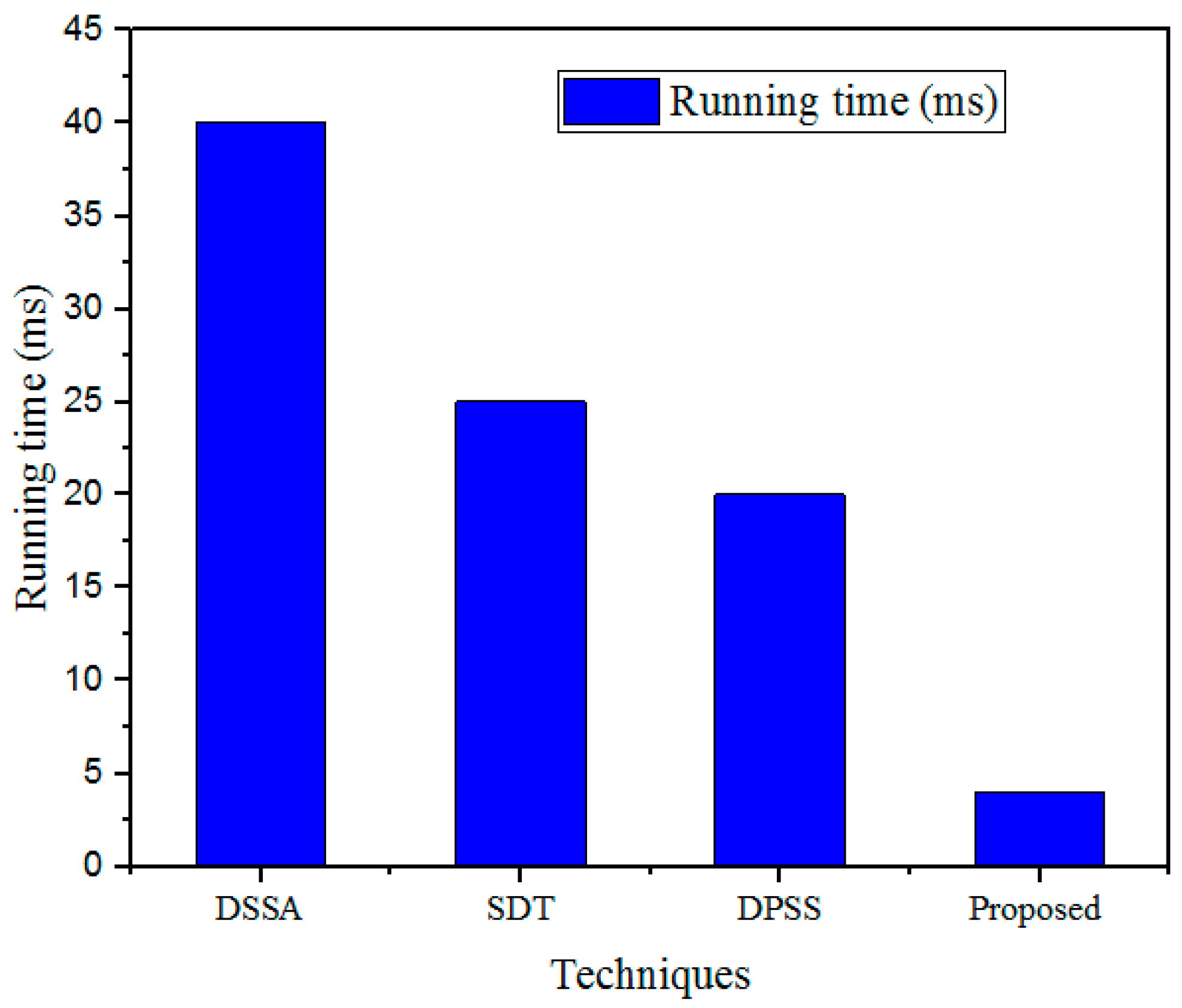
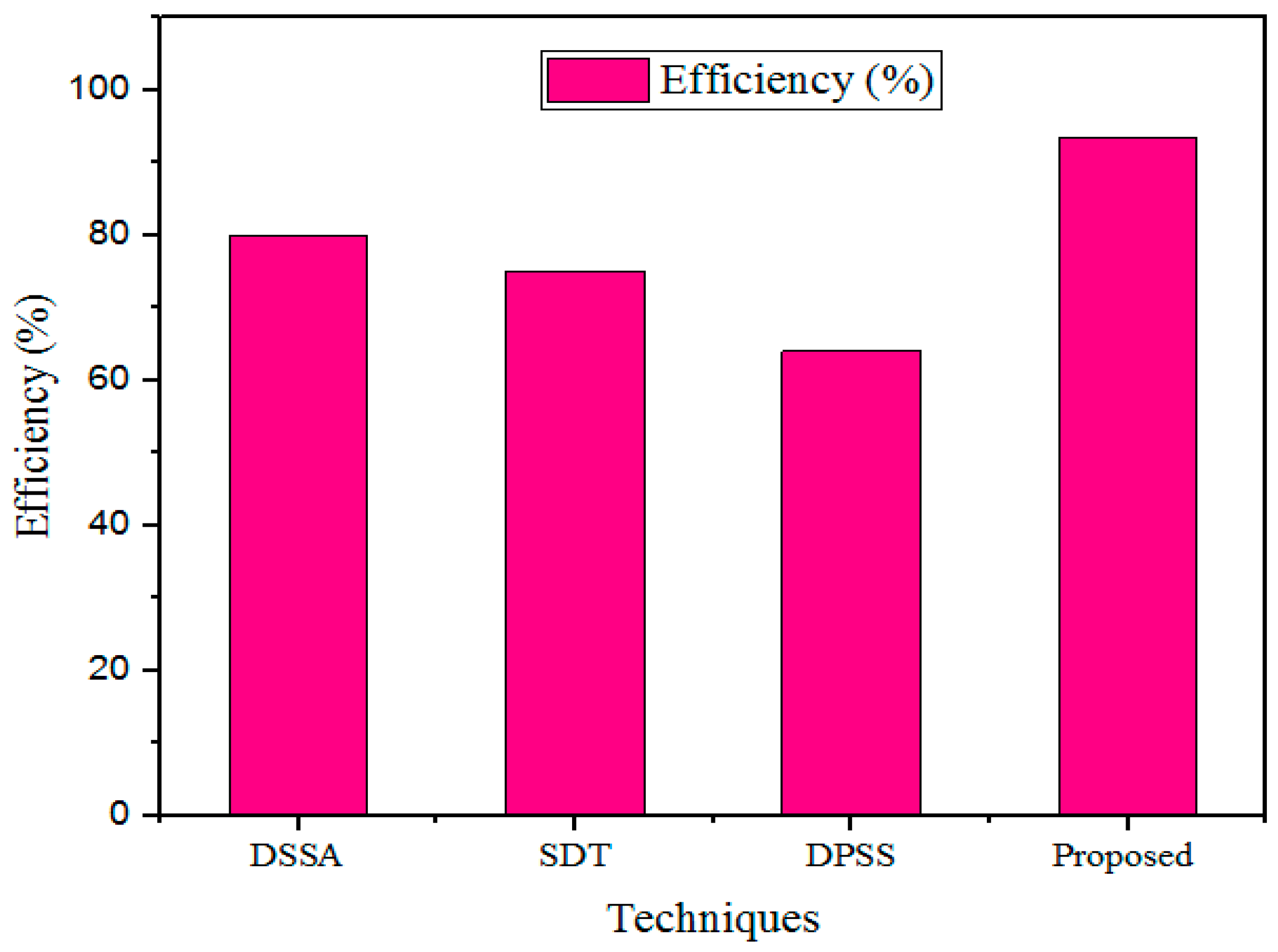
The outcomes attained with the designed model were validated using prevailing methods to prove the efficiency of the developed process. The reason for utilizing grey wolf optimization fitness in the optimized public cloud scheme was to raise awareness of presenting attacks or malicious events at an earlier stage. Furthermore, collected IoT sensor medical data were distributed to the optimized public cloud scheme to improve the performance of healthcare data management. Consequently, the medical dataset included patient healthcare details such as heartbeat rate, blood pressure, sugar level, and body temperature deposited in the optimized public cloud scheme. Additionally, the designed method safeguards the data owner’s medical data during data communication and effectively protects the cloud-stored database.
4.4. Process of ASVM-Based GWO-IDEA
The proposed optimized public cloud scheme method combines the AdaBoost, SVM, grey wolf algorithm, and IDEA. At this point, the information collected about the healthcare of several patients is habitually encrypted with the help of an optimized public cloud scheme, and attacks or unauthorized access to the system are identified using the GWO fitness function. Accordingly, this research endeavored to design a robust, fast, efficient, and successful model by implementing wolf optimization with vast competence in searching and hunting the location of prey, benefitting fitness.
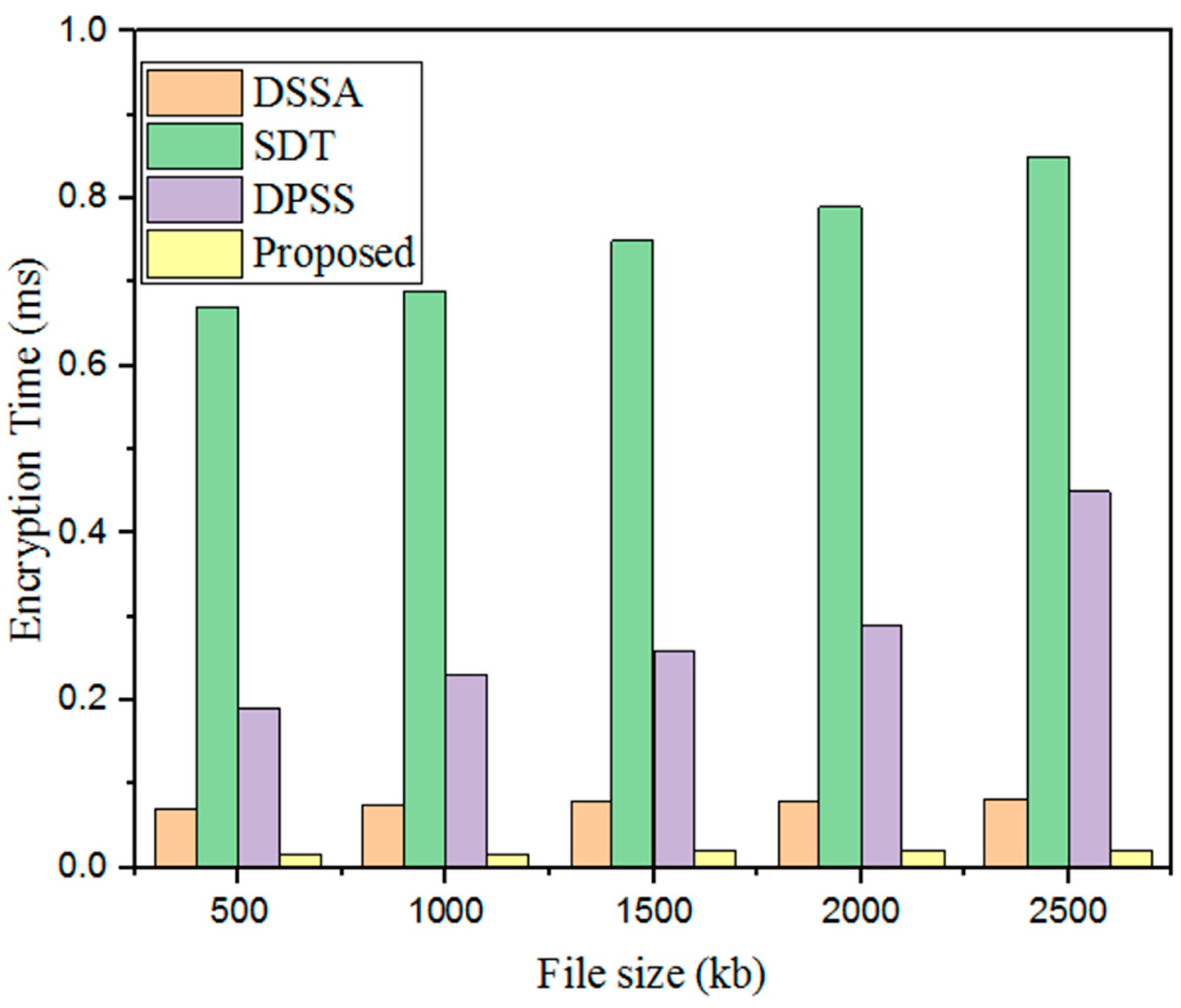
The developed GWO-IDEA is the better security framework for securing healthcare data; it encrypts personal information in the public cloud system. The designed model encrypts the data securely by providing the secret key of each user, and grey wolf optimization fitness continuously monitors the user details to secure the data from third parties. If the user’s secret key is not matched to the stored database, the user is denied access, and healthcare data are secured. Furthermore, GWO-IDEA encrypts the data to secure patients’ details and continuously monitors the users’ details in the auditing phase according to their hunting behavior in terms of grey wolf exploration and exploitation . The parameters used for continuous monitoring in the auditing phase are and .
Generally, the framework uses the AdaBoost algorithm to initialize the training sample weight. The weight of each training sample builds a new decision tree with all the features. Also, it is used to boost performance in terms of accuracy, classification, and regression [
38]. Moreover, AdaBoost in SVM attains better performance in SVM classification problems. It mainly focuses on the correct classification of trained samples and identifies the weak classifier using the weight of the samples. The training sample
stored in the cloud database is initially retrieved using Equation (1).
where
denotes the trained samples and
indicates the number of turns in a single iteration. Then, the weight of the training samples
is modified using Equation (2).
Let
denote the training sample value and
denote the cloud database parameters. The initialization of the weight is used to identify the weak learning classification in SVM and calculate the training errors in the training samples. Thus, the training error
is calculated using Equation (3).
Furthermore, the weight of the training sample
in the developed framework is updated using Equation (4).
Let denote a normalized constant, denote the weight of the trained sample, and denote a binary classification. Then, based on the weight of all the trained samples, the distribution of the best weak classifier is identified, and the weak classifier error rate is determined. Finally, a weak classifier is turned into a robust classifier by updating the weights to improve the performance of the developed framework.
Moreover, SVM collects and classifies objects, information, or data. It is a non-linear mapping function used to convert the original training samples into higher dimensions. It tends to connect the input samples to high-dimensional features and identify the optimal hyperplane. The correct identification of the perfect value is used to solve the problem of overfitting and correctly classify training models. Thus, the process of SVM
in the binary classification was obtained using Equation (5).
Let denote a high-dimensional feature space and denote a binary classification. The SVM is used to identify the features from the collected dataset. Then, these features are updated to the designed GWO-IDEA model to secure the data from third parties. The primary purpose of using AdaBoost SVM in the developed model is to enhance the classification results and minimize the overfitting issue. Moreover, the linear mapping function employed in SVM to attain high-dimension features is used to identify the perfect value.
Several types of patient healthcare data are collected from the patients and stored in the cloud database. Moreover, a cloud database helps to keep the patient’s medical information and history safe [
40]. Nonetheless, the cloud database lacks security, and the patient’s medical data can be hacked by external users, i.e., attackers and third-party applications. This problem may impact the patients’ treatment. Optimized public cloud infrastructure has been created to secure healthcare data from attacks. Additionally, an IDEA mechanism was developed based on the optimized public cloud infrastructure. To block third-party users, cloud data are spontaneously encrypted, and a key is created. Initially, the encryption is performed, and the 64-bit plaintext is shared with the 16-bit plaintext [
41]. Accordingly, the designed framework converts the plaintext into a ciphertext to secure the data from third parties using bits. The IDEA transformation function process
is given in Equation (6).
where
denotes each common disease symptom and
represents a parameter of the stored cloud data. Additionally,
represents the affected patient’s diseases, and
are a combination of some processes realized through encryption. Moreover, using the treatment serial number
, the doctors accidentally produce cards in healthcare data that are obtained using Equation (7).
Let
denote the optimized public cloud hash function,
denote a patient healthcare card,
represent an accidentally nominated value, and
denote a data owner record from the collected medical data. Affected patients are sent to the hospital for treatment. Subsequently, the doctor or physician accesses the cloud database using the secret key and starts the treatment based on the patient’s health status. Thus, the secret key is validated for encrypting private healthcare data. At this stage, numerous security problems have occurred. Thus, the actual data and collected data are validated using Equation (8).
Let
and
denote the actual comparison variables and
represent the collected healthcare information from the cloud. Then, the unusual feature from the dataset is eliminated using Equation (9).
The data owner’s medical data are secured from third parties using the optimization fitness function. At this point, the designed method continuously monitors any unauthorized access and attacks present in the cloud system for healthcare data management. As a result, the user and data owner details in the public cloud system are updated. Furthermore, the performance of the cloud server is determined using data sharing and data assessment and procedures by the users. In the auditing phase, using Equation (10), attacks and unauthorized access are monitored based on the user’s details.
Let
represent the user-detail monitoring performance with exploitation,
describe the user-detail monitoring performance with exploration, and
denote a security function with two parameters,
and
. Because
and
continuously monitor the grey wolf optimization fitness parameter, each user is monitored using the generated secret key (
). Let us suppose that the individual user’s secret key () is not matched to the stored cloud database. In that case, neglecting whether the user’s secret key matches means contacting the user and providing secure transmission, enhancing the developed model’s security. Henceforth, the user’s non-matched secret key is updated in the security function to identify and predict the location using Equation (11).
Let
denote a unit of time. The process is repeated until the prediction of attacks and unauthorized access is complete. Moreover, the process of GWO-IDEA encryption is detailed in Algorithm 1.
| Algorithm 1 Design GWO-IDEA for encryption |
| begin | |
| | input: Plain text | /*- medical dataset of patients -*/ |
| | output: Ciphertext | /*- encrypted information -*/ |
| | initialize the parameters: |
| | | Integers
and | /*- Security parameters -*/ |
| | begin encryption: |
| | | Update 64-bit//plain text |
| | | Shared to the GWO-IDEA |
| | | Common affected diseases of the patient zn(n) | |
| | | Execute function of IDEA transformation using Equation (6) | /*- plaintext is encrypted -*/ |
| | cyphertext: | |
| | | z1(1)= z2(1)= z3(1)= z4(1)= … = zn(n) |
| | | for(z = n; zn; z++) |
| | | | z1(1)= (z1, z1(1)) | |
| | | end for |
| | update the parameter into the public cloud (secure storing): |
| | | Puky | /*- Puky:public key -*/ |
| Prky | /*- Prky:private key -*/ |
| | | Seky | /*- Seky:secret key -*/ |
| | fitness of the cyphertext is measured using Equations (14) and (15) |
| end | |
Key generation is an important part of the developed method for securing cloud data by routinely generating the key. Initially, the sender or users encrypt the patient information using the public key
of the receiver, even though the receiver decrypts the patient information using the private key
. Additionally, the designed public cloud system generates the
using Equation (12).
Let
represent the private key and
denote the collected patient information. Then, the designed public cloud system generates the secret key
using Equation (13).
Afterward, the collected patient healthcare information is also powerfully encrypted, and keys are automatically generated to secure the data in the cloud system. At this point, the key generated and the encrypted dataset contain two cipher texts
,
, which are calculated using Equations (14) and (15).
Let
denote the patient healthcare information and
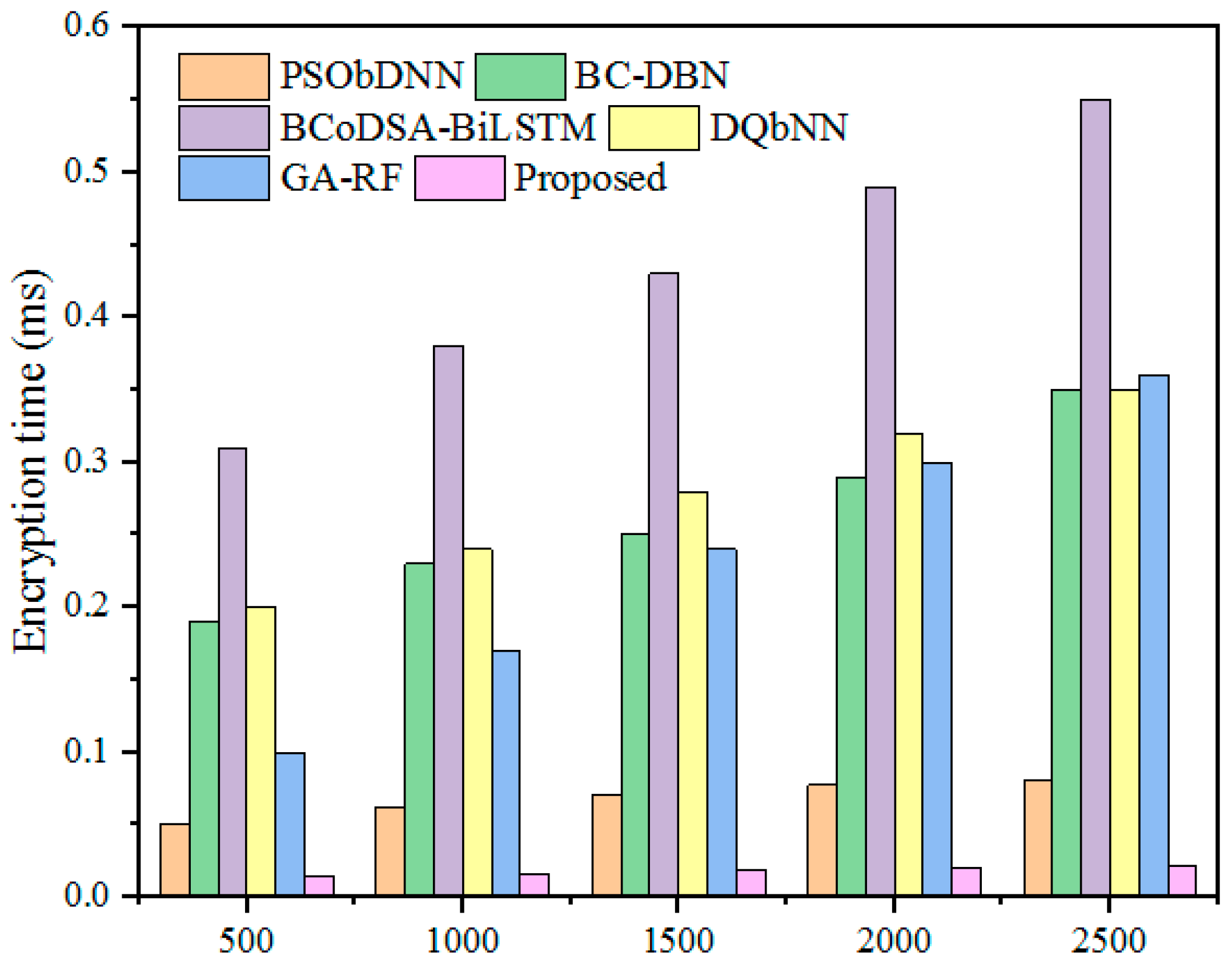
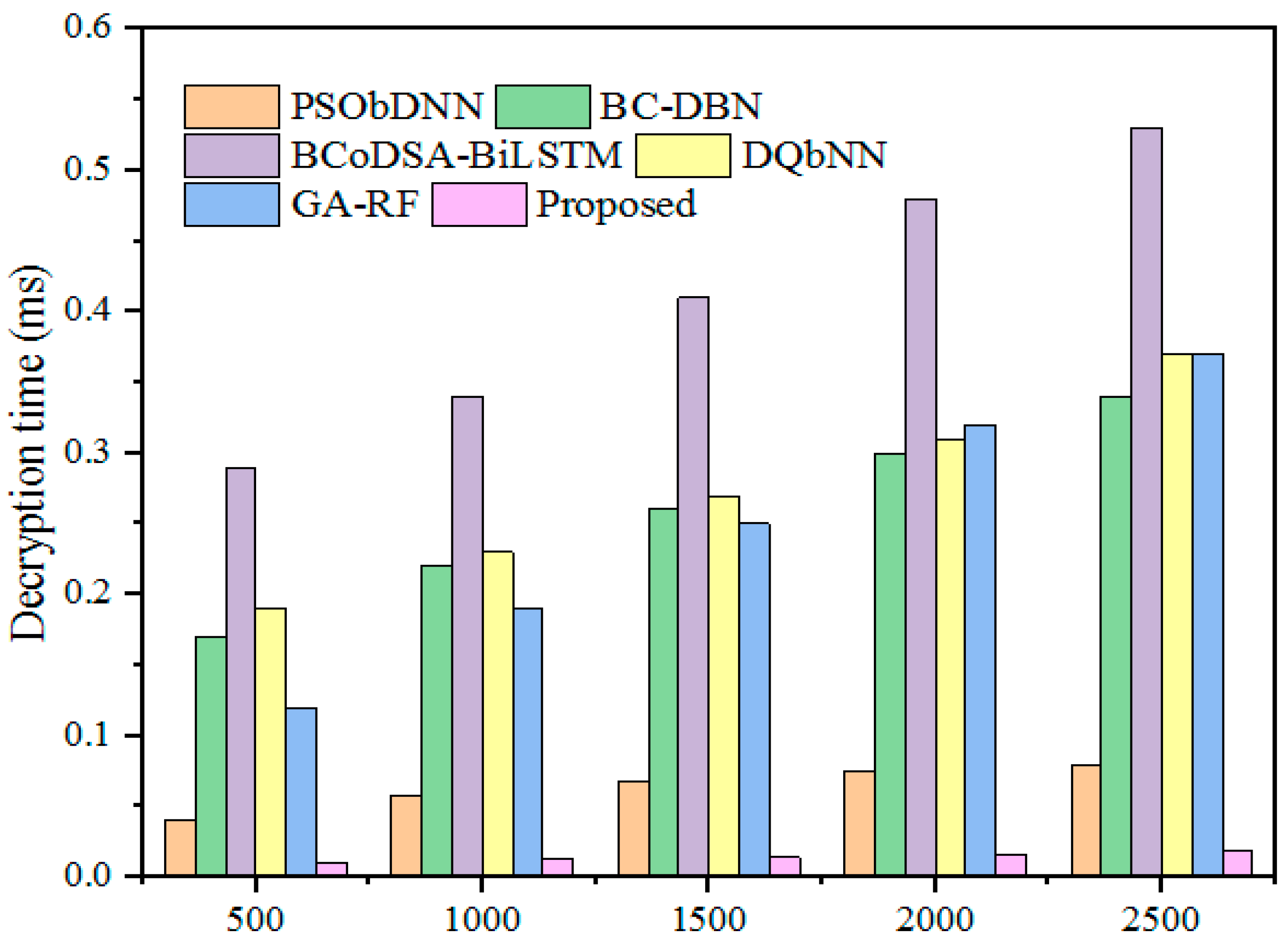
be considered a number casually chosen between 1 and n. Subsequently, security is required for the encrypted healthcare information to be delivered in packets. Thus, the designed model contains security to safeguard the data from attacks. The encrypted data cannot adapt to third parties and attacks in the healthcare environment. Hence, the grey wolf optimization fitness function is used to confirm privacy by delivering proof in the data. The security and decryption processes are expressed in Algorithm 2.
| Algorithm 2 Design GWO-IDEA for decryption and security |
| begin | |
| | input: ciphertext (encrypted data) |
| | output: plaintext | /*- cannot be hacked by third parties -*/ |
| | parameter initialization: |
| | | and | /*- security parameter -*/ |
| | | select a patient | |
| | | Gather from the cloud server | /*- healthcare information -*/ |
| | update grey wolf optimization: |
| | | co-begin | |
| | Au(p) = Q(s) + P(s) [] | /*- auditing phase for monitoring user details -*/ |
| | | co-end | |
| | predict the position: | /*- using Equation (11) -*/ |
| | | co-begin | |
| |
| /*- unit time -*/ |
| | | co-end | |
| | data transmission: |
| | | /*- source to destination -*/ | |
| | | /*- performance of exploration -*/ | |
| | | /*- performance of exploitation -*/ | |
| | stored data from the cloud |
| | objective function |
| | | if (T[] > T[]) | |
| | | conditions satisfied | |
| | | else | |
| | | process repeated | // security level verification |
| | | end if | |
| | | if | /*- s(t) = short duration -*/ |
| | | healthcare data of patient extent at the doctor | |
| | | else | |
| | | not disturb | /*- data communication -*/ |
| | | end if | |
| | start decryption: |
| | | convert ciphertext into plain text | |
| | | evaluating the encrypted key | |
| | | best solution | |
| end |
Initially, a big IoT sensor collects healthcare information from the patient’s body. This can include many illnesses and parameters such as blood pressure and heart rate. Additionally, the gathered healthcare information is stored in the cloud database to secure and manage the data. Consequently, several patients’ healthcare information can be hacked during data communication by attacks and third parties. Thus, an encryption technique is used to secure the information during delivery. Moreover, the fitness function of a grey wolf is initiated in the security level verification system. Then, an attack is introduced, using the designed method to check its efficiency. Therefore, while healthcare information is not disturbed during data communication, third parties and attackers cannot start to decrypt it, and the original text is provided to legitimate users.