RWA-BFT: Reputation-Weighted Asynchronous BFT for Large-Scale IoT
Abstract
1. Introduction
1.1. Background
1.2. Difficulties
- To address the issue of limited scalability in existing IoT architectures integrated with blockchain in asynchronous network environments, this paper proposes a two-layer blockchain-based model. This model facilitates fine-grained transactions in the IoT, enabling seamless integration of the IoT device layer with the blockchain network layer.
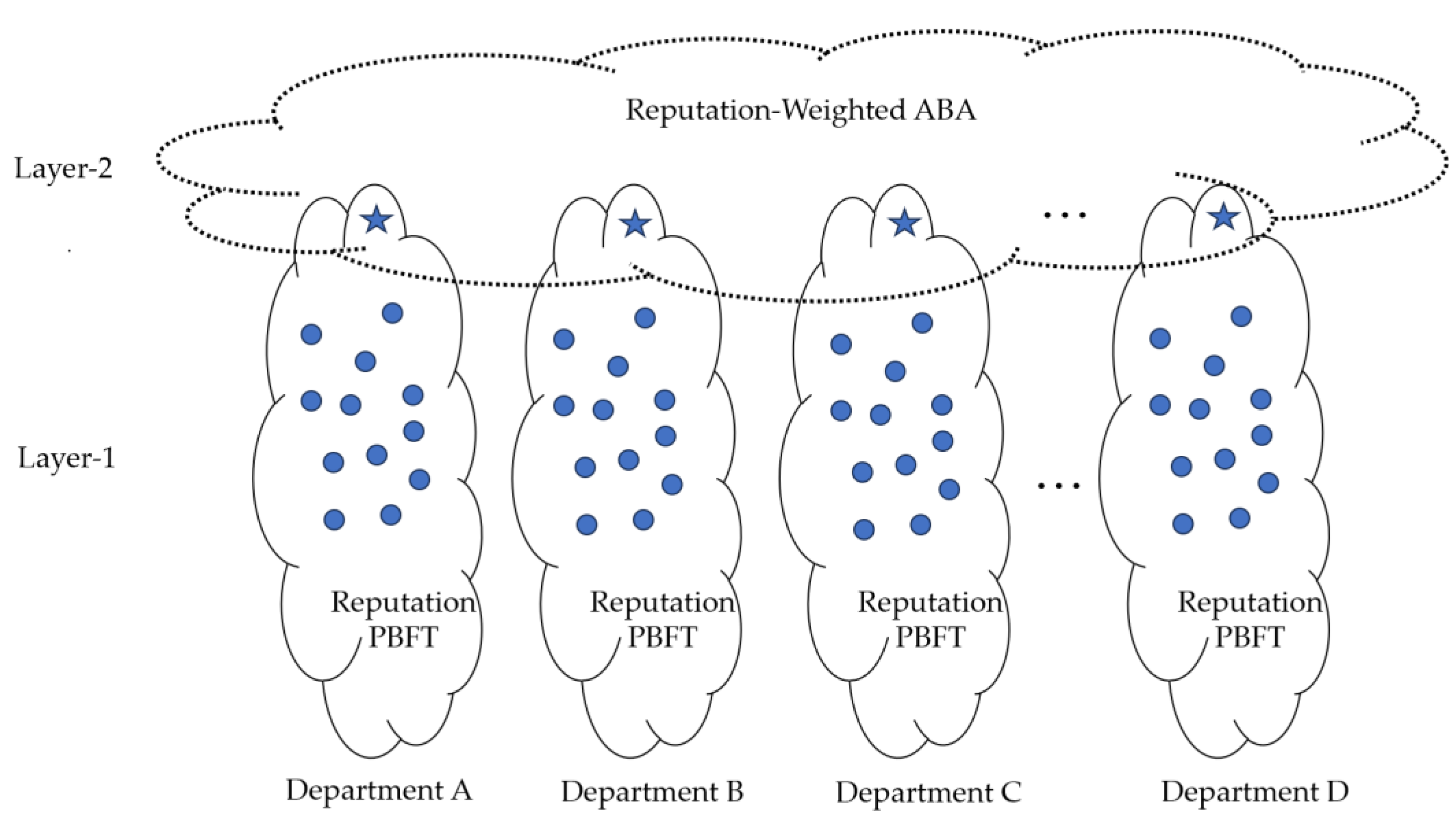
- This paper proposes a reputation-weighted asynchronous BFT consensus algorithm. The algorithm's core idea is to assess the reputation of nodes across the network, elect consensus nodes through voting, group them evenly, and monitor their behavior. It adopts intra-group consensus within groups and global consensus among master nodes to lower the communication complexity of the traditional PBFT algorithm, thereby enhancing consensus efficiency. The first layer (device layer) uses a reputation mechanism to exclude malicious IoT nodes from the current consensus process. The second layer (network layer) facilitates consensus among departmental entity nodes, ensuring secure IoT data interactions.
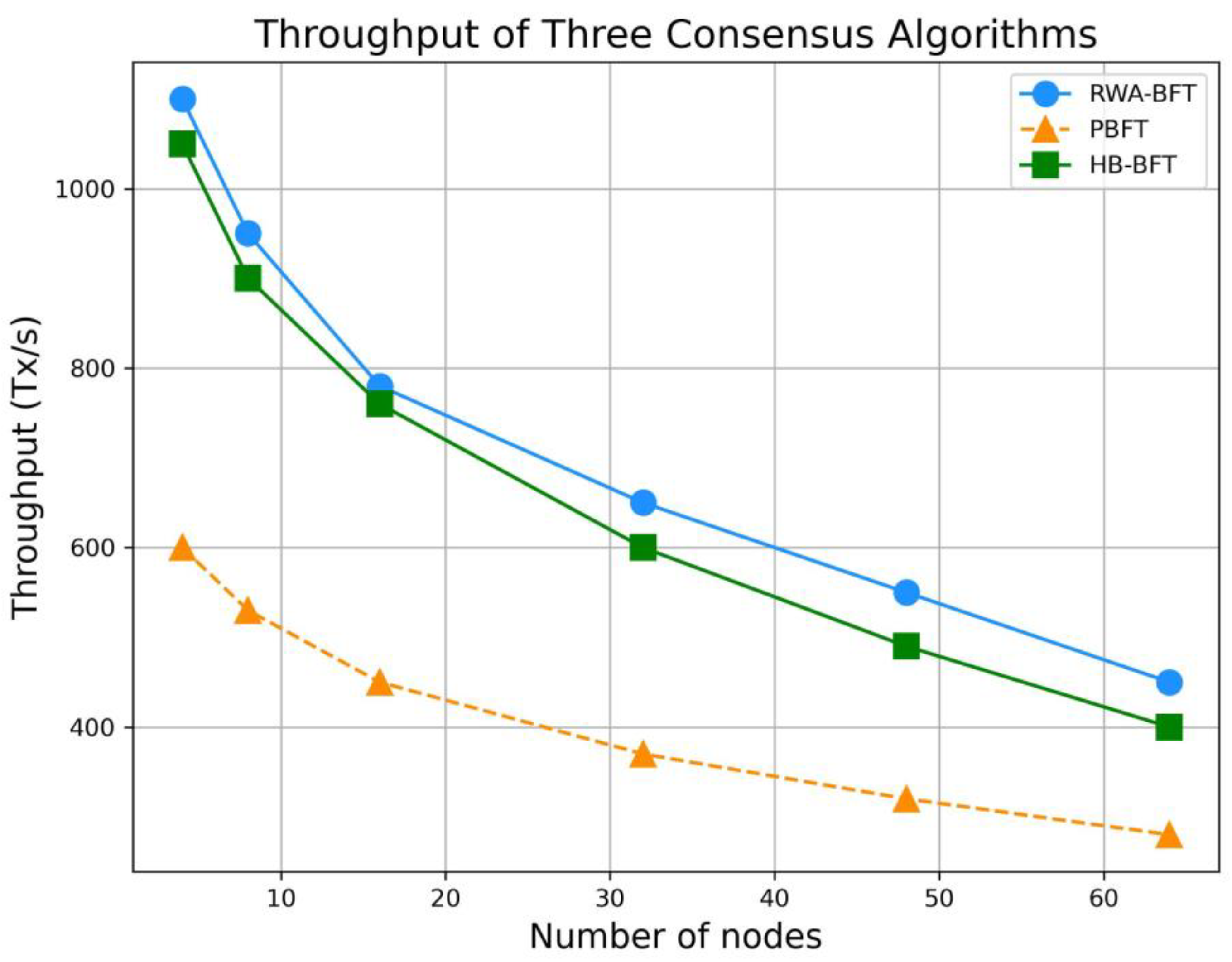
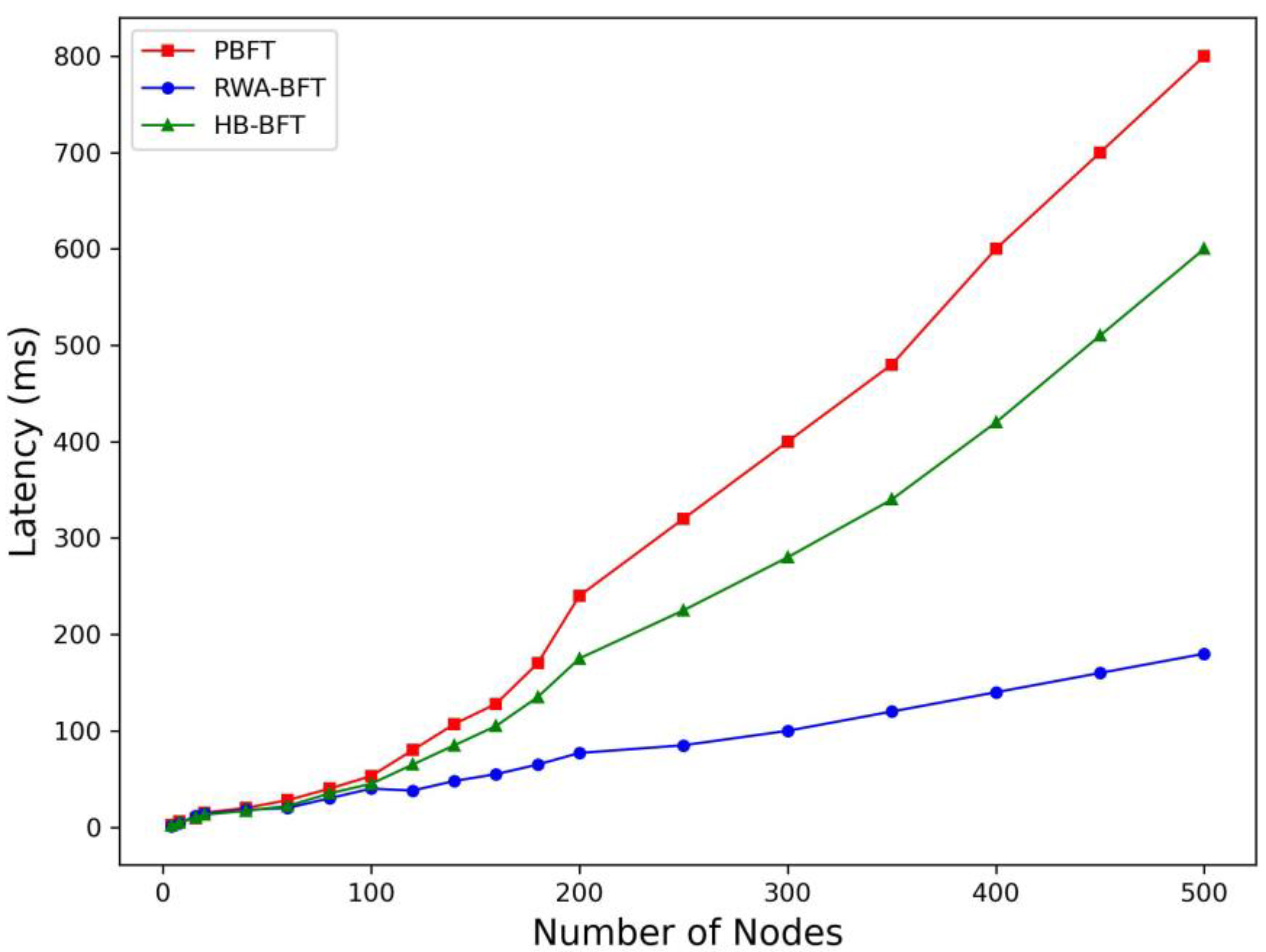
- To simulate the asynchronous network environment of the Internet of Things, the proportion of malicious nodes was increased, and random delays were introduced. A comparative experiment was then conducted with two baseline algorithms, PBFT and HB-BFT, to validate the proposed algorithm’s ability to improve throughput, reduce delays, and maintain robustness in IoT scenarios.
2. Related Work
2.1. Blockchain Characteristics
- Decentralization: Decentralization is the core characteristic of blockchain. In a blockchain system, all decisions and consensus are achieved through the participation of all nodes. Each node in the system holds equal importance and maintains an identical ledger, recording the same transaction information. Any qualifying node can join or leave the blockchain system freely and swiftly, without requiring approval from a central authority.
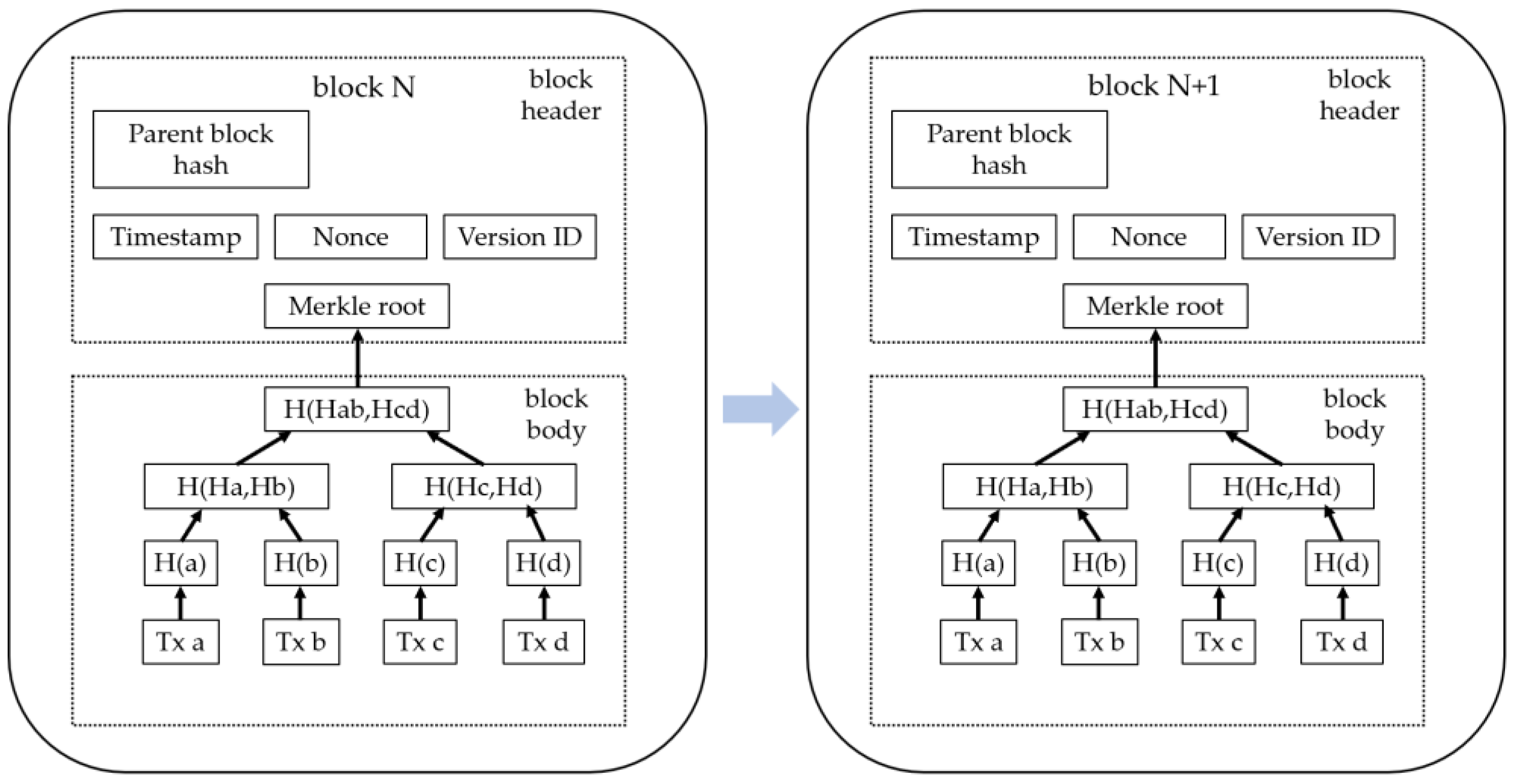
- Immutability: Since blockchain is decentralized, each node retains an identical copy of the ledger. If a malicious node attempts to tamper with its ledger, it cannot alter the records stored on other nodes, rendering its local modifications ineffective. This is one of the reasons why blockchain ensures immutability. Another reason for immutability is that each block's header contains the hash value of the previous block and the Merkle root, derived from all transactions within the block. For a malicious node to alter a transaction in a block, it must ensure that the altered transactions still pass the Merkle tree verification, which, due to the collision resistance of hash functions, is nearly impossible. Similarly, if a malicious node attempts to construct a “legitimate” block to replace an existing one, it would need to generate a hash value for the new block that matches the original block’s hash value. Similarly, the collision resistance of hash functions ensures the impossibility of replacing an entire block.
- Transparency: Because blockchain is decentralized, every node retains an identical copy of the ledger, allowing each node to access the same information. Nodes can freely join or leave the blockchain system, and all nodes within the system can verify the transaction records, making the ledger public and transparent to anyone. Although this results in substantial redundancy, transparency is a crucial characteristic of blockchain and is of paramount importance in specific application scenarios.
2.2. BFT Consensus
- Semi-Synchronous Network Model: In this model, the message delivery time between any two nodes is not fixed and can vary over time, but its variation remains within polynomial bounds. The classic PBFT [16] algorithm operates under this model.
- Asynchronous Network Model: In this model, an adversary may arbitrarily alter the order of messages and introduce any delays in message transmission. In this system, the delivery time and order of messages are unpredictable.
2.2.1. Synchronous and Semi-Synchronous Protocols
2.2.2. Asynchronous Protocols
2.2.3. Byzantine Broadcast Protocol
- Reliable Broadcast Protocol (RBC)
- Validity: If an honest node broadcasts a message mi, then all honest nodes will deliver mi.
- Consistency: If an honest node delivers a message mi and another node delivers a message m′, then mi = m′.
- Completeness: If an honest node delivers mi, then all correct nodes will also deliver mi.
- Correctness: Each honest node delivers m only once, and m must have been previously broadcast.
- 2.
- Consistent Broadcasting Protocol (CBC)
- Validity: If an honest node broadcasts a message mi, then that node will eventually deliver mi.
2.2.4. Byzantine Consensus Protocol
- Asynchronous Binary Consensus Protocol (ABA)
- Validity: If all honest nodes input v, then any honest node outputs v.
- Consistency: If an honest node outputs v, then all honest nodes output v.
- Termination: If all honest nodes have inputs, then every honest node will eventually output some value.
- Correctness: Honest nodes do not produce duplicate outputs.
- 2.
- Verifiable Multi-Valued Byzantine Consensus (MVBA)
- External Validation Correctness: Every honest node will eventually output a message that passes external validation.
- Consistency: All honest nodes will output the same message at a specific point in time.
- Completeness: If an honest node outputs a value v, there must be at least one node that submitted v for external verification.
- 3.
- Asynchronous Common Subset Protocol (ACS)
- Validity: If a correct node delivers a set V, then V must contain at least n − f values, originating from at least n − 2f honest nodes.
- Consistency: If an honest node delivers the information set V, then all other honest nodes will deliver the same V.
- Completeness: If at least n − f honest nodes provide input, all honest nodes will eventually output a collection of the input information.
3. Two-Layer Consensus for Large-Scale IoT
3.1. System Model
3.2. Two-Layer Chain Design
3.3. Layer-1: Reputation-Weighted BFT
3.3.1. Reputation Mechanism
- Excellent Nodes: These nodes actively participate in voting, generate valid blocks, or positively engage in consensus, with their reputation values falling within the range of (b,c].
- Good Nodes: These nodes actively participate in voting, generate valid blocks, or engage positively in consensus, with their reputation values falling within the range of (a,b].
- Average Nodes: These nodes have not generated invalid blocks and have not failed to respond during the PBFT consensus process.
- Malicious Nodes: These nodes have failed to actively participate in voting, have generated invalid blocks, or have failed to respond during the PBFT consensus process.
3.3.2. Weight Calculation
- 1.
- Group leaders who receive the corresponding REPLY messages (including their own REPLY messages, if applicable) invoke the aggregation function to combine the signatures of in all received REPLY messages. If a group leader receives REPLY messages, the leader’s weight is . This weight is directly influenced by the number of group leaders participating in the group announcement, as only nodes with sufficiently high reputation (not removed from the current consensus round) will send messages. Along with the aggregated signature, the group leader must also provide the relevant set and set within the aggregated signature, enabling other group leaders to verify the weight.
- 2.
- Group leaders who have not received the corresponding REPLY message broadcast the NO_REPLY message to the nodes in the group, start a timer, and set an appropriate duration. Upon receiving the NO_REPLY message, node in the group verifies whether it has received a block that satisfies the condition . If it is confirmed that no block satisfying the condition has been received, sends a NO_BLOCK message to its group leader, where is included in the NO_ BLOCK message. The value represents the input for the subsequent RWABA algorithm. Once the timer set by the group leader expires, the group leader aggregates the signatures of from all received NO_BLOCK messages. Therefore, if the group leader receives NO_BLOCK messages, the leader’s weight is .
3.4. Layer-2: RWBFT
3.4.1. RWABA
| Algorithm 1. Layer-2: RWABA | |
| Initialization: . | |
| 1: | ; |
| 2: | |
| 3: | Upon do |
| 4: | ; |
| 5: | Upon do |
| 6: | If has not been sent, then broadcast . |
| 7: | Upon do |
| 8: | ; |
| 9: | Upon do |
| 10: | |
| 11: | . |
| 12: | ; |
| 13: | if then |
| 14: | if then |
| 15: | if then |
| 16: | ; |
| 17: | ; |
| 18: | else: |
| 19: | terminate program; |
| 20: | ; |
| 21: | else: |
| 22: | ; |
| 23: | ; |
| 24: | goto line 1; |
- Phase 1: Lines 1–8, in which the primary task is exchanging and propagating the estimated values. Node first adds its own weight to the local “weight sum” variable and broadcasts a message , which contains its current estimated value and weight, to all other nodes. Upon receiving a message from other nodes, the weight from the message is added to the corresponding . Once the weight for a particular estimated value exceeds , it proves that at least one honest node has sent the message (since the adversary’s control cannot exceed , and if no corresponding message was sent earlier, the adversary can follow by sending the same estimated value along with its own reputation-weight). When the weight of a particular estimated value exceeds , the value is considered to have been sufficiently exchanged, and it is placed into the set , allowing the algorithm to proceed to the next phase.
- Phase 2: Lines 9-11: The main task in this phase is still the exchange and dissemination of information. Once a node finds that its local set is not empty, it will broadcast the message , informing other nodes that the estimated value has entered the second phase. As in the first phase, when the node receives enough messages such that the reputation-weight of the estimated value entering the second phase exceeds , it can be assumed that enough honest nodes have taken this estimated value as a candidate for consensus, and the node can proceed to the third phase.
- Phase 3: Lines 12–23, where the primary task is to reach the final consensus. At the beginning of the third phase, it is confirmed that a sufficient number of honest nodes are ready to reach a consistent consensus result, which corresponds to their local estimated value. In this phase, a common coin is introduced to bring in randomization, which is crucial for allowing the protocol to function in an asynchronous network. When the common coin’s value aligns with the local estimated value, the local value can be adopted as the final consensus result. If the values do not match, all honest nodes’ estimated values are unified, and the process continues to the next round. Once in the third phase, the probability of reaching final consensus in each round is 50%. As the number of rounds increases, the probability of remaining stuck in the loop decreases exponentially, leading to the conclusion that the expected number of rounds for the algorithm is constant.
3.4.2. Safety and Feasibility Analysis
- Validity: The consensus result ultimately obtained by honest nodes is guaranteed to originate from inputs provided by honest nodes.
- Consistency: All honest nodes will eventually agree on the same consensus result.
- Conclusion Singleness: In each round of consensus, honest nodes will only reach a single consensus decision.
- Terminability: All honest nodes will eventually reach a consensus, ensuring the process does not remain perpetually unresolved.
- Third bullet.
4. Experiment Results
4.1. Throughput
4.2. Latency
4.3. The Impact of the Proportion of Malicious Nodes
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- International Data Corporation (IDC). Worldwide Internet of Things Forecast, 2019–2025. Available online: https://www.networkworld.com/article/966746/idc-expect-175-zettabytes-of-data-worldwide-by-2025.html (accessed on 6 January 2025).
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Haque, F. Predicting seismic sustainability for a complex CHESST interaction by AHP using LWST. J. Saf. Sustain. 2024, 1, 181–188. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://assets.pubpub.org/d8wct41f/31611263538139.pdf (accessed on 6 January 2025).
- Crosby, M.; Nachiappan, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 6–10. [Google Scholar]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform. Ethereum White Pap. 2014, 37, 2-1. [Google Scholar]
- Croman, K.; Decker, C.; Eyal, I.; Gencer, A.E.; Juels, A.; Kosba, A.; Miller, A.; Saxena, P.; Shi, E.; Gün Sirer, E.; et al. On Scaling Decentralized Blockchains. A Position Paper from the First Workshop on Blockchain of Things; Springer: Berlin/Heidelberg, Germany, 2016; pp. 17–27. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in Internet of Things: Challenges and Solutions; Elsevier: Amsterdam, The Netherlands, 2017. [Google Scholar]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Hu, Q.; Dai, Y.; Li, S.; Jiang, T. Enhancing Account Privacy in Blockchain-based IoT Access Control via Zero Knowledge Proof. IEEE Netw. 2022, 37, 117–123. [Google Scholar] [CrossRef]
- Zhong, J.; Li, Y.; Wu, Y.; Cao, Y.; Li, Z.; Peng, Y.; Shahidehpour, M. Optimal operation of energy hub: An integrated model combined distributionally robust optimization method with stackelberg game. IEEE Trans. Sustain. Energy 2023, 14, 1835–1848. [Google Scholar] [CrossRef]
- Lamport, L. Paxos made simple. ACM SIGACT News (Distrib. Comput. Column) 32 4 (Whole Number 121 Dec. 2001) 2001, 32, 51–58. [Google Scholar]
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm. In Proceedings of the 2014 USENIX annual technical conference (USENIX ATC 14), Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. OsDI 1999, 99, 173–186. [Google Scholar]
- Abraham, I.; Malkhi, D.; Nayak, K.; Ren, L.; Yin, M. Sync hotstuff: Simple and practical synchronous state machine replication. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020. [Google Scholar]
- Duan, S.; Levitt, K.; Meling, H.; Peisert, S.; Zhang, H. ByzID: Byzantine fault tolerance from intrusion detection. In Proceedings of the 2014 IEEE 33rd International Symposium on Reliable Distributed Systems, Nara, Japan, 6–9 October 2014. [Google Scholar]
- Liu, J.; Li, W.; Karame, G.O.; Asokan, N. Scalable byzantine consensus via hardware-assisted secret sharing. IEEE Trans. Comput. 2018, 68, 139–151. [Google Scholar] [CrossRef]
- Aublin, P.L.; Guerraoui, R.; Knežević, N.; Quéma, V.; Vukolić, M. The next 700 BFT protocols. ACM Trans. Comput. Syst. (TOCS) 2015, 32, 1–45. [Google Scholar] [CrossRef]
- Bahsoun, J.P.; Guerraoui, R.; Shoker, A. Making BFT protocols really adaptive. In Proceedings of the 2015 IEEE International Parallel and Distributed Processing Symposium, Hyderabad, India, 25–29 May 2015. [Google Scholar]
- Duan, S.; Li, Y.; Levitt, K. Cost sensitive moving target consensus. In Proceedings of the 2016 IEEE 15th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 31 October–2 November 2016. [Google Scholar]
- Amir, Y.; Danilov, C.; Dolev, D.; Kirsch, J.; Lane, J.; Nita-Rotaru, C.; Olsen, J.; Zage, D. Steward: Scaling byzantine fault-tolerant replication to wide area networks. IEEE Trans. Dependable Secure Comput. 2008, 7, 80–93. [Google Scholar] [CrossRef]
- Yin, M.; Malkhi, D.; Reiter, M.K.; Gueta, G.G.; Abraham, I. HotStuff: BFT consensus in the lens of blockchain. arXiv 2018, arXiv:1803.05069. [Google Scholar]
- Gueta, G.G.; Abraham, I.; Grossman, S.; Malkhi, D.; Pinkas, B.; Reiter, M.; Tomescu, A. SBFT: A scalable and decentralized trust infrastructure. In Proceedings of the 2019 49th Annual IEEE/IFIP international conference on dependable systems and networks (DSN), Portland, OR, USA, 24–27 June 2019. [Google Scholar]
- Buchman, E. Tendermint: Byzantine Fault Tolerance in the Age of Blockchains. Ph.D. Thesis, University of Guelph, Guelph, ON, Canada, 2016. [Google Scholar]
- Miller, A.; Xia, Y.; Croman, K.; Shi, E.; Song, D. The honey badger of BFT protocols. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Duan, S.; Reiter, M.K.; Zhang, H. BEAT: Asynchronous BFT made practical. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018. [Google Scholar]
- Guo, B.; Lu, Z.; Tang, Q.; Xu, J.; Zhang, Z. Dumbo: Faster asynchronous bft protocols. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, 2020; Association for Computing Machinery, New York, NY, USA, 9–13 November 2020; pp. 803–818. [Google Scholar]
- Liu, C.; Duan, S.; Zhang, H. Epic: Efficient asynchronous bft with adaptive security. In Proceedings of the 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Valencia, Spain, 29 June–2 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 437–451. [Google Scholar]
- Ben-Or, M.; Canetti, R.; Goldreich, O. Asynchronous secure computation. In Proceedings of the twenty-fifth annual ACM symposium on Theory of computing, San Diego, CA, USA, 16–18 May 1993. [Google Scholar]
- Cachin, C.; Kursawe, K.; Petzold, F.; Shoup, V. Secure and efficient asynchronous broadcast protocols. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Springer: Berlin/Heidelberg, Germany; pp. 524–541. [Google Scholar]
- Cachin, C.; Poritz, J.A. Secure intrusion-tolerant replication on the Internet. Proceedings International Conference on Dependable Systems and Networks, Washington, DC, USA, 23–26 June 2002; IEEE: Piscataway, NJ, USA, 2002; pp. 167–176. [Google Scholar]
- Moniz, H.; Neves, N.F.; Correia, M.; Verissimo, P. RITAS: Services for randomized intrusion tolerance. IEEE Trans. Dependable Secur. Comput. 2008, 8, 122–136. [Google Scholar] [CrossRef]
- Abraham, I.; Malkhi, D.; Spiegelman, A. Asymptotically optimal validated asynchronous byzantine agreement. In Proceedings of the 2019 ACM Symposium on Principles of Distributed Computing, Toronto, ON, Canada, 27 July–2 August 2019; ACM: New York, NY, USA, 2019; pp. 337–346. [Google Scholar]
- Bracha, G. Asynchronous Byzantine agreement protocols. Inf. Comput. 1987, 75, 130–143. [Google Scholar] [CrossRef]
- Cachin, C.; Tessaro, S. Asynchronous verifiable information dispersal. In Proceedings of the 24th IEEE Symposium on Reliable Distributed Systems (SRDS'05), Orlando, FL, USA, 26–28 October 2005; IEEE: Piscataway, NJ, USA, 2005; pp. 191–201. [Google Scholar]
- Cachin, C.; Kursawe, K.; Shoup, V. Random oracles in constantipole: Practical asynchronous byzantine agreement using cryptography. In Proceedings of the Nineteenth Annual ACM Symposium on Principles of Distributed Computing, Portland, OR, USA, 16–19 July 2000; ACM: New York, NY, USA, 2000; pp. 123–132. [Google Scholar]



| Node Classification | Reputation Value Range |
|---|---|
| Malicious Node | |
| Initial Node | |
| Good Node | |
| Excellent Node |
| Configuration Items | Configuration Details |
|---|---|
| Operating system | Ubuntu 22.04 |
| CPU | Intel(R) Core(TM) Ultra 5 125H 1.20 GHz |
| Memory size | 32 GB |
| Disk capacity | 1TB |
| Development environment | Visual Studio Code |
| Golang version | Go1.23.1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jia, G.; Shen, Z.; Sun, H.; Xin, J.; Wang, D. RWA-BFT: Reputation-Weighted Asynchronous BFT for Large-Scale IoT. Sensors 2025, 25, 413. https://doi.org/10.3390/s25020413
Jia G, Shen Z, Sun H, Xin J, Wang D. RWA-BFT: Reputation-Weighted Asynchronous BFT for Large-Scale IoT. Sensors. 2025; 25(2):413. https://doi.org/10.3390/s25020413
Chicago/Turabian StyleJia, Guanwei, Zhaoyu Shen, Hongye Sun, Jingbo Xin, and Dongyu Wang. 2025. "RWA-BFT: Reputation-Weighted Asynchronous BFT for Large-Scale IoT" Sensors 25, no. 2: 413. https://doi.org/10.3390/s25020413
APA StyleJia, G., Shen, Z., Sun, H., Xin, J., & Wang, D. (2025). RWA-BFT: Reputation-Weighted Asynchronous BFT for Large-Scale IoT. Sensors, 25(2), 413. https://doi.org/10.3390/s25020413






