MEDIotWALL: Securing Smart Healthcare Environments Through IoT Firewalls
Abstract
1. Introduction
- A total of 64% of healthcare delivery organizations (HDOs) have more IoT devices connected to their networks than computers.
- In a typical hospital, over 50% of connected devices carry significant risks.
- Nearly 75% of IV pumps have vulnerabilities that could endanger patient safety if exploited.
- More than half of the devices in oncology, pharmacology, and laboratory departments are running outdated versions of Windows that are no longer supported.
- A total of 63% of HDOs have encountered at least one security incident involving unmanaged or IoT devices.
- While new vulnerabilities attract attention, insecure passwords remain the most common device risk.
- Around 80% of security managers in HDOs believe their current spending on IoT device security is insufficient.
- Over 80% express serious concern about the risks associated with IoT devices.
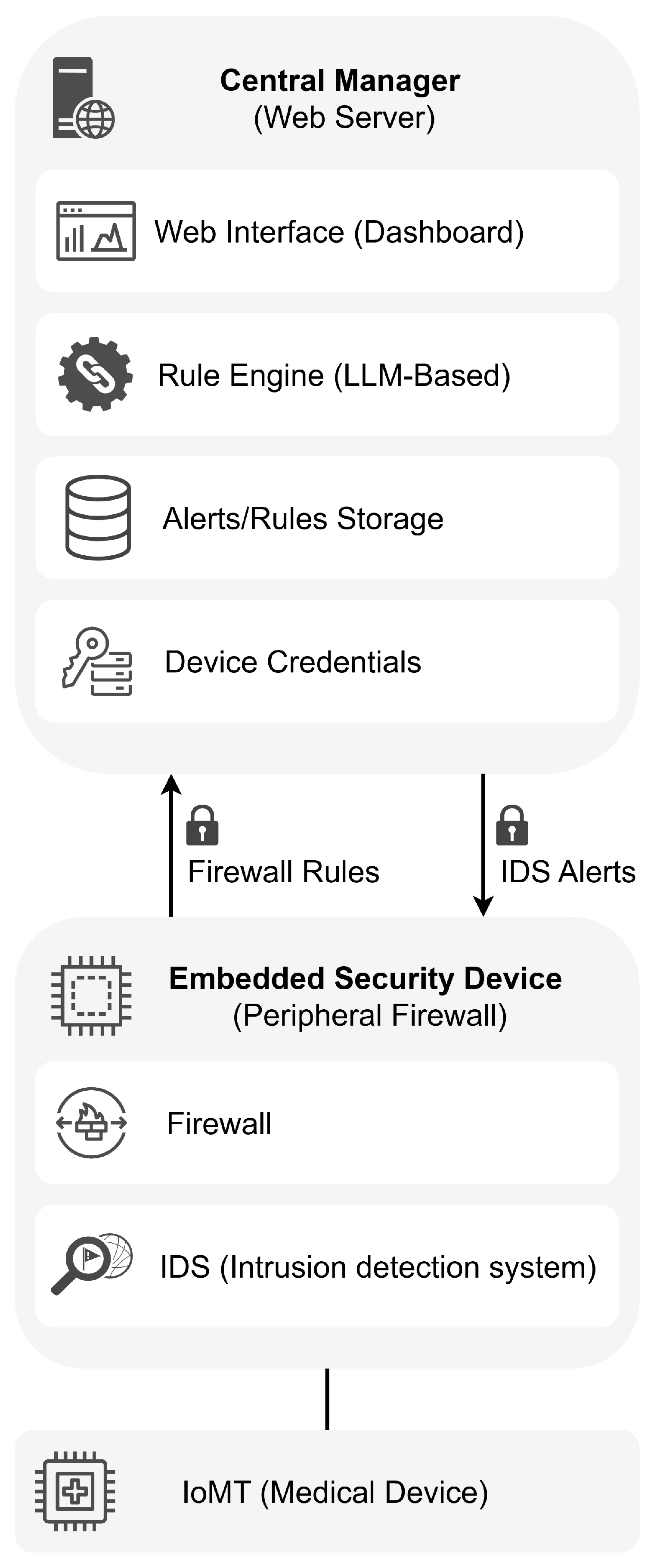
- It is supported on a two-tier approach, with two main security-related components: (a) a set of low-cost Raspberry Pi-based distributed firewalls, with each IoMT device (e.g., MRI machines, infusion pumps, incubators) in the environment assigned to a dedicated firewall; and (b) a web-based central unit, responsible for overseeing and managing the entire environment.
- According to this two-level architecture, the approach considers two separate monitoring procedures: (a) one central, where integral platforms like Claroty can be considered, and (b) a distributed one, associated with each of the firewalls around the environment.
- Automatic AI-based generation of traffic filtering rules to respond to the alerts provided from the firewalls associated with each of the IoMT devices.
2. Background
- Perception layer: This refers to the physical level where sensors are deployed and involves the collection of information. The perception layer includes multiple communication protocols (i.e., Radio Frequency Identification, Bluetooth Low Energy, Wireless Sensor Networks, Zigbee, IPv6 over Low-Power Wireless Personal Area Networks) and is susceptible to multiple attacks affecting the infrastructure in various ways: jamming, eavesdropping, injection, cloning, tampering, etc.
- Network layer: This layer provides network transmission and information security, and delivers pervasive access environment to the perception layer. The network layer can be enabled with different wireless networks like Wi-Fi 6, 5G, Bluetooth, NB-IoT, and LTE, which are vulnerable to threats and attacks like spoofing, DDoS, routing, sybil, sinkhole, or Man-in-the-Middle.
- Cloud layer: To differentiate between transmission itself and intermediate storage, the network layer is sometimes divided so a fourth layer appears [23]: the cloud or edge layer. This allows secure backup and preservation of confidential health information, and sharing between authorized parties (doctors, insurance providers, medical staff, and pharmacies). In this case, attacks like flooding, web attacks and injection attacks may be deployed here.
- Application layer: This layer is visible to the end-user as it resides at the top level, and provides the user interface for each of the specific healthcare services. Attacks like phishing, DDoS (Distributed Denial of Service), buffer overflow, malware, XSS and code injection exist here.
- As a two-level solution, it comprises two main security-related components:
- −
- A set of Raspberry Pi-based firewalls, with each IoMT device (e.g., MRI machines, infusion pumps, incubators) in the environment assigned to a dedicated firewall.
- −
- A web-based central management unit, responsible for overseeing and managing the entire environment.
- The overall operation of MEDIotWALL can be summarized as follows:
- −
- Each IoMT device–firewall pair must be first activated through the central management unit. During this process:
- *
- Relevant security rules (e.g., nftables filtering rules) are identified for each IoMT device using a specialized centralized platform such as Claroty.
- *
- These rules are communicated to the corresponding firewall to ensure proper enforcement for the associated IoMT.
- −
- Additionally, each firewall monitors the traffic to/from its associated medical device over time so that
- *
- The traffic is locally analyzed by an IDPS (Intrusion Detection and Prevention System), and the potential alerts generated, if so, sent to the central management unit.
- *
- The alerts are studied and passed through an AI-based tool to automatically generate additional security rules at the central management unit, which should be manually confirmed by the administrator.
- *
- Upon confirmation, the rules are transmitted to the associated firewall for enforcement.
3. MEDIotWALL: An IoT Firewall Solution to Protect Medical Environments
3.1. Functional Architecture
- Central manager (Web server). This component serves as the core for system monitoring and control. Its primary functions include
- −
- Provision of a web interface for real-time monitoring of security events and alert management.
- −
- Reception of alerts transmitted by embedded security devices deployed across the hospital network.
- −
- Automatic analysis of alerts using Large Language Models (LLMs) to generate firewall rule suggestions based on detected threats and activities.
- −
- Filter and enable the remote application of firewall rules—subject to human approval—to prevent automated actions that could compromise the availability of medical devices.
- −
- Secure storage of the private keys of each device, ensuring the integrity and authenticity of communications with peripheral security devices.
- Embedded security devices (ESDs, peripheral firewalls). Each critical medical device is protected by an embedded module that acts as a local firewall deployed transparently within the network. This module inspects and filters traffic without altering IP configurations or affecting device certification. Its capabilities include
- −
- Traffic inspection using an open-source intrusion detection system (IDS) to identify anomalous behavior or attack patterns.
- −
- Secure transmission of alerts to the central manager, protected with device-specific cryptographic keys to ensure integrity and authenticity.
- −
- Reception of updated rules with mutual authentication from the central manager, ensuring authorized configuration.
- −
- Traffic filtering based on centrally generated rules, which are applied locally through an open-source firewall.
- 1.
- Local monitoring: Each embedded security module monitors network traffic from its associated medical device using an open-source IDS. This system detects anomalous behaviors or known attack patterns in real time without disrupting device operation.
- 2.
- Alert generation: Upon identifying suspicious activity, the local module generates an alert containing relevant metadata, including source/destination IP, ports or signature ID, and transmits it securely—protected with the device’s cryptographic key pair—to the central manager, ensuring authenticity and integrity.
- 3.
- Centralized alert analysis: The central manager processes the alert using a LLM, which analyzes the threat context and proposes a tailored firewall rule to mitigate the risk while preserving device functionality.
- 4.
- Human supervision: Proposed rules are announced to an authorized operator via the system’s web interface, requiring explicit human approval before implementation. This human-in-the-loop approach ensures accountability and protects patient safety.
- 5.
- Remote rule deployment: Approved rules are securely transmitted to the relevant embedded security module and applied using mutual authentication to verify both source and destination, ensuring a secure configuration update.
- Device transparency: The security local modules operate as a transparent inline component—an invisible intermediary that maintains the original network settings of the medical devices. By avoiding modifications to IP addresses or device configurations, this bump-in-the-wire deployment aligns with best practices in commercial-grade NGIPS platforms [34], preserving device sercurity and ensuring uninterrupted clinical functionality.
- Scalability and cost: Each embedded security module operates autonomously, enabling distributed deployment across clinical zones. This modular and low-cost design supports progressive, large-scale rollouts and localized policy enforcement without network-wide reconfiguration, adapting to evolving threat landscapes [18,23].
- Network segmentation: Each IoMT device is logically isolated through its own embedded firewall module, enabling fine-grained policy enforcement per device. This architecture minimizes lateral threat propagation and enhances containment in case of a breach.
- Mandatory human supervision: In critical healthcare environments, all automatically generated firewall rules (e.g., those produced by AI-based analysis) must be reviewed and approved by authorized personnel prior to deployment, ensuring accountability and preventing unintended service disruption. This human-in-the-loop approach prevents disruptions to critical medical services and ensures accountability.
- Secure and authenticated communication: All interactions between embedded security devices and the central manager use encrypted channels with mutual authentication. This ensures both the authenticity of the communicating parties and the confidentiality and integrity of transmitted alerts and rule updates.
3.2. Implementation
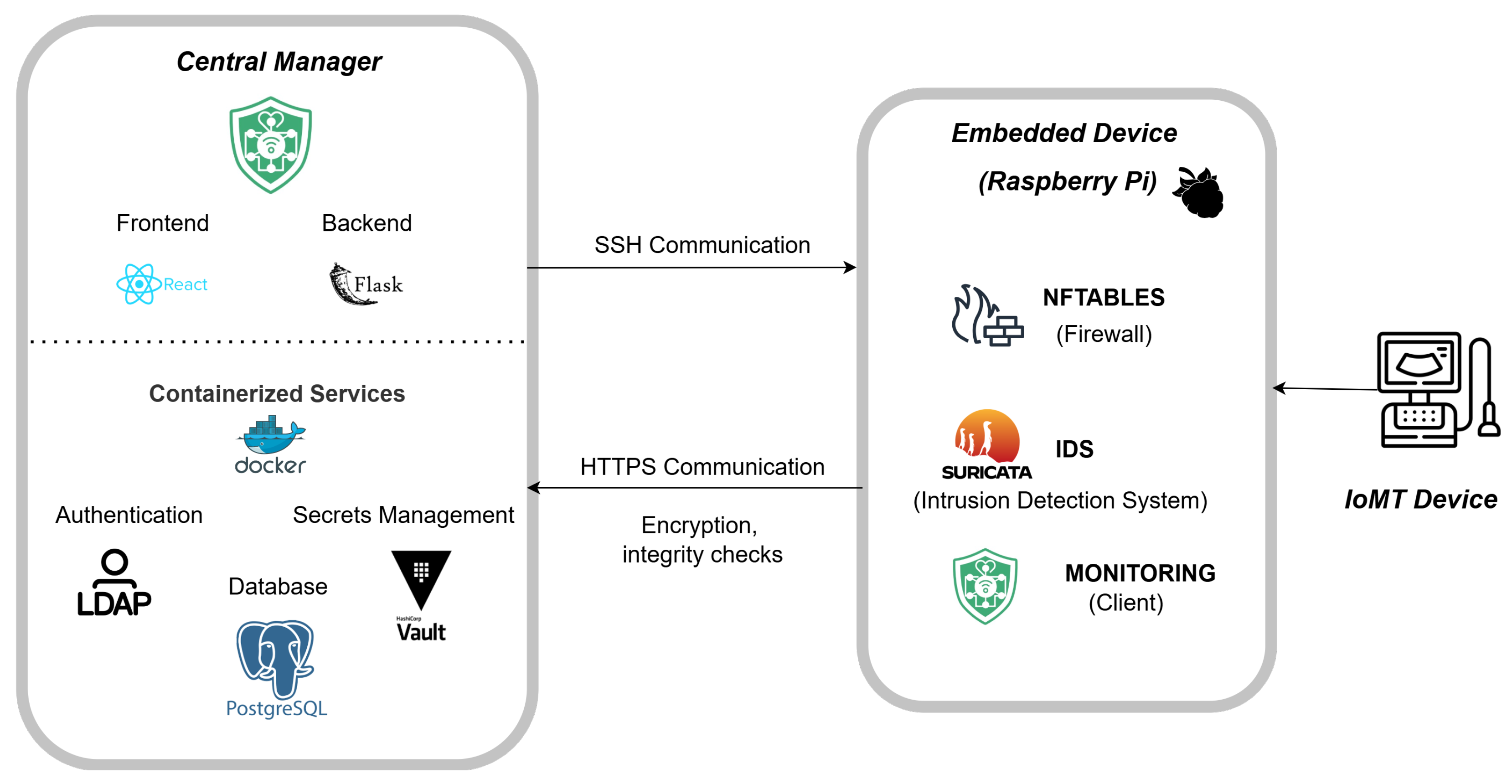
3.2.1. Centralized Manager
- Web service: This is the main interface between the CM and the IoMT devices. It exposes a REST API for communication, validates cryptographically protected alerts, and coordinates device registration and firewall rule management. The service is implemented with Flask, its frontend and backend-related functionalities being described below.
- Database: This component provides the persistent data layer of the system. A PostgreSQL instance stores critical information such as device metadata, alert histories, and firewall rules with their associated lifecycle states.
- Authentication: This service delivers centralized identity and access management. Built on OpenLDAP, it maintains user credentials and enforces group-based access control, enabling scalable administration of authorized users. By decoupling policy management from backend configuration, it supports flexibility and seamless adaptation as the system grows.
- Key management: This service ensures the protection of sensitive cryptographic material, including private keys and credentials. HashiCorp Vault is employed to securely store and manage these assets while enforcing fine-grained access policies. Its AppRole mechanism issues short-lived credentials that minimize long-term exposure and strengthen incident response capabilities by allowing rapid revocation and rotation when necessary.
CM Frontend
CM Backend
- 1.
- REST API orchestration: The backend provides a set of REST endpoints (implemented in Flask) that serve as the primary communication interface between embedded devices, security operators, and internal services. These endpoints support core functions such as device registration, reception of security alerts, firewall rule management across workflow states (pending, approved, rejected), and administrator authentication. All requests undergo strict validation and authentication to prevent unauthorized access or propagation of malformed data.The modular design also supports extensibility, allowing the integration of additional device types, intrusion detection systems (e.g., Suricata, Snort), or logging frameworks (e.g., Syslog, Wazuh, ELK) without altering the core backend.
- 2.
- Session and access control: Administrative access is enforced through authenticated sessions over HTTPS. User credentials are validated against the centralized LDAP directory, ensuring that only directory-registered accounts can log in. Session cookies are also configured with security flags (HttpOnly, Secure, expiration). Access to sensitive endpoints—including firewall rule management, device registration, and alert handling—is restricted to authenticated administrator/s, ensuring that only authorized personnel can perform critical operations.
- 3.
- Device registration: The backend incorporates a structured registration workflow that guarantees the secure onboarding of new IoMT devices. The registration process supports both manual enrollment and automated discovery via the specialized industrial cybersecurity platform Claroty, for asset visibility and threat management, ensuring that each device is provisioned with unique credentials, network parameters, and security policies required for safe integration. The process can be grouped into four main phases:
- -
- Parameter acquisition and enrichment: Devices provide identifiers such as MAC address and optional metadata. When available, additional information is automatically retrieved from the Claroty API (e.g., type, model, IP addresses, VLAN), complementing the record with some relevant network parameters.
- -
- Cryptographic protection: Critical fields (e.g., IP addres, VLAN, MAC) are encrypted using Fernet before storage. Additionally, SHA-256 hashes of these identifiers are computed to enable efficient device lookup and authentication when processing incoming alerts.
- -
- Secure persistence: Enriched and protected records are stored in the system database, ensuring data consistency and traceability. During alert processing, the hashed identifiers from the alert (e.g., IP, MAC) are matched against the database to recover the corresponding device ID and retrieve its public key from Vault for cryptographic verification of the alert.
- -
- Credential provisioning: Each device is assigned a unique SSH key pair, with private keys securely stored in a centralized vault and isolated per device. This approach ensures confidentiality, prevents cross-device credential exposure, and supports auditability and secure lifecycle management.
As a part of the registration process, each device is asigned unique Vault credentials, the generation and delivery of which is detailed in the “Secret management” process below. - 4.
- Secret management: A central pillar of the backend architecture is its integration with HashiCorp Vault, which provides centralized and secure management of credentials for both devices and the manager. Vault is deployed as an independent container and enforces fine-grained policies and authentication mechanisms tailored to distributed IoMT environments. The integration covers four main aspects:
- -
- Secure key provisioning: During device registration, each device is assigned a unique SSH key pair. The private key, protected with a passphrase, is securely stored in Vault under a device-specific path, while the public key remains available for verification. This avoids hardcoded credentials and enables subsequent key rotation.
- -
- Policy-based access control: Vault automatically issues per-device policies granting exclusive access to their own secrets, strictly following the principle of least privilege and preventing lateral credential exposure.
- -
- Authentication: Devices authenticate through Vault’s AppRole mechanism, which exchanges identifiers for short-lived tokens limited to the assigned policy. This mechanism is first used during device registration to retrieve their unique credentials and is subsequently reused for secure interactions with the backend, ensuring continuous policy enforcement.
- -
- Isolation and auditability: All interactions between the backend and Vault occur over an internal Docker network with encryption in transit and at rest. This setup supports immediate revocation, periodic rotation of credentials, and detailed auditing of all secret-related operations, enhancing resilience and compliance to medical IoMT deployments.
- 5.
- Rule generation with LLMs: To accelerate firewall rule creation and maintain adaptability in heterogeneous IoMT environments, the system leverages Large Language Models (LLMs) via the OpenRouter API to synthesize candidate rules from structured alert data (For the experiments described in Section 4, we used the shisa-ai/shisa-v2-llama3.3-70b:free model.). Only alerts that have been successfully decrypted and cryptographically verified using device-specific keys, and matched against device records in Vault, are used as input—ensuring all automated actions are based on trustworthy events.The LLM framework automatically tailors rules to the characteristics of each detected event, providing immediate proposals while maintaining auditability and traceability. During development, multiple LLMs were evaluated to select the model producing the most syntactically correct and semantically coherent firewall rules.The rule generation procedure is as follows:
- -
- Automated rule synthesis: Verified alerts are converted into a standardized JSON format that captures source and destination addresses, affected services or ports, and event type or severity. This structured representation is incorporated into a dynamic prompt that guides the LLM in generating firewall rules in nftables format). The generated rules initially take the form of abstract templates with placeholders (e.g., src_ip, dest_port), which are subsequently populated with actual alert values.
- -
- Human-in-the-loop validation: Candidate rules are stored in a pending state and reviewed by the administrator/s. Only approved rules are deployed, preserving operational control, security, and compliance with regulatory requirements.
- 6.
- Policy enforcement: The backend implements a controlled lifecycle for firewall rules, encompassing three primary actions:
- -
- Approval and deployment: Once a rule has been reviewed and accepted by an administrator, it is securely deployed to the target embedded device. Deployment occurs through an encrypted SSH connection using a private key dynamically retrieved from a centralized secret vault. Prior to execution, the system verifies the existence of required nftables tables and chains (input, forward, and output), creating them if absent, and selects the appropriate network family (ip, inet, or bridge) to ensure compatibility with the device environment.Commands are executed on the remote firewall, and upon success, the rule’s status is updated to ‘accepted’, and the timestamp of deployment is recorded, providing full auditability.
- -
- Rejection: The administrator/s can explicitly reject rules considered inappropriate, redundant, or unsafe. Rejected rules remain in the database with a rejected status and timestamp, preserving historical traceability. No changes are made to the firewall during rejection, guaranteeing that only vetted rules impact the network. This mechanism ensures a strict human validation step while maintaining a comprehensive audit trail.
- -
- Controlled removal: The system allows manual deletion of firewall rules to retire obsolete policies, correct misapplied rules, or perform maintenance. For rules in the ‘accepted’ state, deletion triggers removal from both the database and the remote firewall using secure SSH execution. For ‘pending’ or ‘rejected’ rules, deletion affects only the database entry. All deletion actions are logged irreversibly, including timestamps.
- 7.
- Alert verification and processing: The backend enforces a secure, end-to-end workflow for handling alerts from IoMT devices. This workflow integrates secure verification and structured data processing:
- -
- Key provisioning: Each device receives a unique SSH key pair, with private keys confined to the device and public keys securely stored in HashiCorp Vault, avoiding shared credentials.
- -
- Alert reception and cryptographic verification: Alerts are transmitted from devices via HTTPS endpoints. Instead of using formal digital signatures (e.g., X.509 or COSE), each device encrypts and authenticates its alert payload by using its device-specific key pair securely stored in Vault. Only alerts that successfully pass cryptographic verification are accepted into the processing workflow, effectively preventing unauthorized injection or tampering by non-registered devices.Upon reception, the backend: (i) matches hashed device identifiers from the alert (e.g., IP and MAC) against the database to retrieve the corresponding device ID; (ii) obtains the device’s public key from Vault; and (iii) use this public key to decrypt and cryptographically verify the alert payload, ensuring it was generated by the corresponding device and has not been tampered with.
- -
- Structured storage: Verified alerts are parsed into a standardized JSON format capturing source/destination addresses, affected services or ports, and event severity. This structured representation ensures that alerts can be reviewed and traced during operational monitoring.
- 8.
- Administrator notification: To enhance situational awareness and ensure human oversight, the backend integrates an automated notification mechanism that informs the security administrator/s whenever a new firewall rule enters the review phase. Upon generation of a candidate rule by the LLM, the system immediately dispatches an email to the designated administrator, including the rule identifier and a concise description.The notification system is designed to support flexible configuration for different deployment environments, allowing administrator/s to customize sender and recipient addresses, mail servers, ports, and authentication credentials through environment-specific settings. This ensures timely delivery of alerts while maintaining operational security.Moreover, all notification events, including dispatch attempts and delivery status, are logged to provide full auditability and traceability. This guarantees that no automated rule changes go unnoticed and that all human interventions prior to rule deployment are properly recorded.
Overall CM Workflow
- 1.
- Distributed Raspberry Pi-based firewalls generate security alerts protected with device-specific cryptographic keys.
- 2.
- The CM receives the alerts via the REST API, authenticates them, and performs cryptographic verification.
- 3.
- Verified alerts are normalized, stored, and forwarded to the LLM for candidate firewall rule generation.
- 4.
- The administrator/s is notified, who must validate proposed rules (approve, reject, or remove).
- 5.
- Approved rules are securely deployed to embedded devices via SSH.
- 6.
- All operations are logged for auditability and compliance.
3.2.2. Embedded Security Devices
Firewall Functionality
Intrusion Detection on ESDs
Monitoring and Communication
4. Deployment and Evaluation
4.1. Experimental Scenario
- The hospital network was conceptually segmented to separate management traffic from patient-care devices.
- A dedicated management VLAN interconnects the CM and the ESDs, while IoMT devices operate on isolated VLANs to limit lateral exposure.
- Each ESD is configured in bridge mode, linking the interfaces between medical equipment and the hospital network to preserve clinical workflow continuity.
- The bridge interface is assigned a static IP for communication with the CM, while the underlying physical interfaces operate in promiscuous mode to enable full traffic inspection.
- The CM was deployed as a virtual machine within the management VLAN.
- ESDs refer to Raspberry Pi 5 devices and FriendlyElec NanoPi R5C boards, each running the following:
- −
- Suricata IDS with an IoMT-specific rule set. To reduce false positives from routine broadcast and management traffic, alert thresholds in the IDS were tuned based on normal operational patterns. Specific parameter values are omitted to maintain network confidentiality.
- −
- The nftables firewall.
- −
- A custom monitoring client.
- Internet access for the ESDs was provided through the institutional proxy, supporting system updates and connectivity to the LLM API for proof-of-concept rule generation.
- As mentioned in the previous section, secure communications between the central manager and embedded devices were ensured using SSH with public/private key authentication.
- As IoMT devices, two representative medical devices are used: a BeneHeart R12 electrocardiograph (ECG) and a Siemens ultrasound machine (UM).
4.2. Operation and Evaluation
- 1.
- Establishment of the physical connectivity among all elements: CM, ESDs and ECG/UM IoMT devices.
- 2.
- Configuration of the network aspects, including bridge mode operation for the ESDs.
- 3.
- Registration of the ESDs in the CM.
- 4.
- Deployment of initial configuration for the ESDs: Suricata, nftables, and the monitoring client adapted for bridge mode operation.
- 5.
- Running Suricata and the monitoring client on all ESDs.
- 6.
- Generation of controlled network traffic and simulated attacks from a dedicated host, targeting the IoMTs through the ESDs in a controlled manner.
- 7.
- Verification that alerts generated by the ESDs are received by the CM.
- 8.
- Reviewing and approval of automatically suggested firewall rules through the manager interface.
- 9.
- Application of the approved rules to the ESDs from the CM.
- 10.
- Confirmation that the firewall rules have been correctly enforced on the ESDs.
- 11.
- Repetition of the controlled attacks to validate mitigation effectiveness, monitoring packet drops and responses.
- 12.
- In a controlled environment with a simulated device, the system’s performance was further evaluated by measuring CPU and RAM usage at the ESDs, as well as the estimated end-to-end latency from detection to rule enforcement during systematically reproduced attacks.
- Electrocardiograph (ECG): Two attacks against ECG were implemented as follows:
- −
- A TCP SYN flood using hping3 against port 481 of the device, representing a volumetric denial-of-service scenario.
- −
- Multiple reconnaissance scans with nmap, including Null scans, FIN scans, and OS fingerprinting, simulating adversarial attempts to enumerate services and infer OS characteristics.
- Ultrasound machine (UM): For the UM, the experimental focus was on targeted reconnaissance through OS fingerprinting with nmap. This scan aimed to identify exposed services and gather system information in order to simulate the early stages of a targeted attack campaign.
4.3. Results and Discussion
- The mitigation mechanisms rely primarily on source-IP based filtering and simple rate-limiting. While this approach is effective for single-source attacks, distributed attacks or source address spoofing would require more advanced correlation mechanisms and group-based rule enforcement.
- EDSs now constitute potential failure points, since a device crash would imply the loss of connectivity for the associated medical device. Such an undesirable loss of connectivity in medical devices could be automatically detected by implementing a simple neighborhood procedure, in which the CM and each EDS periodically exchange accessibility messages.
- The current system focuses exclusively on network- and transport-layer attacks; application-layer exploits (e.g., SQL injection, XSS on web-based medical interfaces), encrypted traffic, and insider threats remain outside its detection scope. Furthermore, the current evaluation does not include advanced evasion techniques, which will be considered in future work.
- The implementation of MEDIotWALL employed an external LLM API for rule generation; however, in real IoMT deployments, a locally trained should be preferable. Due to privacy concerns and the risk of potential data leaks associated with proprietary LLMs typically provided via external APIs, locally deployed open-source LLMs on an infrastructure controlled by healthcare institutions are recommended, as discussed in [41].
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| API | Application Programming Interface |
| CM | Central Manager |
| CSF | Common Security Framework |
| DDoS | Distributed Denial of Service |
| ECG | Electrocardiograph |
| ESD | Embedded Security Device |
| HDO | Healthcare Delivery Organizations |
| H-IoT | Healthcare Internet of Things |
| HIPAA | Health Insurance Portability and Accountability Act |
| HITRUST | Health Information Trust Alliance |
| IDC | International Data Corporation |
| IDPS | Intrusion Detection and Prevention System |
| IoMT | Internet of Medical Thing |
| IoT | Internet of Things |
| IP | Internet Protocol |
| LLM | Large Language Model |
| MRI | Magnetic Resonance Imaging |
| OS | Operating System |
| PHI | Protected Health Information |
| SSH | Secure SHell |
| TCP | Transmission Control Protocol |
| UM | Ultrasound Machine |
References
- Exploding Topics. 60+ Amazing IoT Statistics (2024–2030). Report. 2024. Available online: https://explodingtopics.com/blog/iot-stats (accessed on 5 October 2025).
- OiT Analytics. State of IoT 2024. Available online: https://iot-analytics.com/number-connected-iot-devices/ (accessed on 5 October 2025).
- Statista. Internet of Things (IoT)—Statistics & Facts. Report. 2024. Available online: https://statista.com/topics/2637/internet-of-things/#topicOverview (accessed on 5 October 2025).
- AON. Cyber Security of Medical IoT Devices. Managing Risk in the Digital Health Age. Report. 2025. Available online: https://www.aon.com/unitedkingdom/insights/cyber-security-of-iot-medical-devices.jsp (accessed on 5 October 2025).
- Parihar, A.; Prajapati, J.B.; Prajapati, B.G.; Trambadiya, B.; Thakkar, A.; Engineer, P. Role of IOT in healthcare: Applications, security & privacy concerns. Intell. Pharm. 2024, 2, 707–714. [Google Scholar] [CrossRef]
- Armis. Medical and IoT Device Security for Healthcare. Managing Risk and Ensuring Patient Safety with 21st Century Healthcare. White Paper Armis Inc., 2024. Available online: https://media.armis.com/pdfs/wp-medical-iot-device-security-en.pdf (accessed on 5 October 2025).
- Armis Security. State of Enterprise IoT Security: A Spotlight on Healthcare. Report. 2019. Available online: https://info.armis.com/rs/645-PDC-047/images/State-Of-Enterprise-IoT-Security-Healthcare-Spotlight.pdf (accessed on 5 October 2025).
- Armis Security. Forrester State of Enterprise IoT Security: A Spotlight on Healthcare. Report. 2021. Available online: https://databreachtoday.com/whitepapers/forrester-state-enterprise-iot-security-spotlight-on-healtcare-w-7776 (accessed on 5 October 2025).
- Cynerio. The State of Healthcare IoT Device Security 2022. Research Report. 2022. Available online: https://www.cynerio.com/landing-pages/the-state-of-healthcare-iot-device-security-2022 (accessed on 5 October 2025).
- Abdi, I. IOT Devices in Healthcare: Vulnerabilities, Threats and Mitigations. Master’s Thesis, Herberger School of Business, St. Cloud, MN, USA, 2023. Available online: https://repository.stcloudstate.edu/cgi/viewcontent.cgi?article=1196&context=msia_etds (accessed on 5 October 2025).
- HITRUST. HITRUST and HIPAA. How the HITRUST Approach Can Help Healthcare Organizations Demonstrate Compliance with HIPAA. HITRUST Report. 2023. Available online: https://hitrustalliance.net/hubfs/Thought%20Leadership/HITRUST-and-HIPAA.pdf (accessed on 5 October 2025).
- Martinez, J. The HIPAA Minimum Necessary Standard Explained. Available online: https://www.strongdm.com/blog/hipaa-minimum-necessary-standard (accessed on 5 October 2025).
- HS. Health Information Privacy. Available online: https://www.hhs.gov/hipaa/for-professionals/security/hipaa-security-rule-nprm/index.html (accessed on 5 October 2025).
- CSF. HITRUST CSF—Our Cybersecurity Framework. Available online: https://hitrustalliance.net/hitrust-framework (accessed on 5 October 2025).
- The Intake. The Largest Healthcare Cyberattacks in 2024. Report. 2024. Available online: https://www.tebra.com/theintake/practice-operations/medical-news/the-major-cyberattacks-that-have-affected-healthcare-systems-in-2024 (accessed on 5 October 2025).
- UpGuard. 14 Biggest Healthcare Data Breaches [Updated 2025]. Report. 2025. Available online: https://www.upguard.com/blog/biggest-data-breaches-in-healthcare (accessed on 5 October 2025).
- Jena, A.B.; Mann, N.C.; Olenski, W.J.N.A. Delays in emergency care and mortality during major U.S. marathons. N.-Engl. Med. Rev. J. 2017, 376, 1441–1450. [Google Scholar] [CrossRef] [PubMed]
- IoT Security Foundation. IoT Security Reference Architecture for the Healthcare Industry. Best Practice User, IoT Security Foundation. 2019. Available online: https://www.iotsecurityfoundation.org/wp-content/uploads/2019/05/IoT-Security-Reference-Architecture-For-The-Healthcare-Industry.pdf (accessed on 5 October 2025).
- Salih, F.I.; Bakar, N.A.A.; Hassan, N.H.; Yahya, F.; Kama, N.; Shah, J. IOT Security Risk Management Model for Healthcare Industry. Malays. J. Comput. Sci. 2019, 131–144. [Google Scholar] [CrossRef]
- Klas. Healthcare IoT Security 2023. Performance Report. 2023. Available online: https://go.ordr.net/rs/976-OJA-437/images/ordr_report_klas_healthcare_iot_security_2023.pdf (accessed on 5 October 2025).
- Zawalnyski, A.; Iannini, L. The Top 10 IoT Security Solutions For Healthcare. Report. 2024. Available online: https://expertinsights.com/insights/the-top-iot-security-solutions-for-healthcare (accessed on 5 October 2025).
- Shepherd, A.; Kesa, C.; Cooper, J. Internet of Things (IoT) Medical Security: Taxonomy and Perception. Issues Inf. Syst. 2020, 1, 227–235. [Google Scholar] [CrossRef]
- Khatun, M.A.; Memon, S.F.; Eising, C.; Dhirani, L.L. Machine Learning for Healthcare-IoT Security: A Review and Risk Mitigation. IEEE Access 2023, 11, 145869–145896. [Google Scholar] [CrossRef]
- HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Aledhari, M.; Karimipour, H. A survey on internet of things security: Requirements, challenges, and solutions. Internet Things 2021, 14, 100129. [Google Scholar] [CrossRef]
- Alharbi, F.M. Network Attacks and Defenses for IoT Environments. Ph.D. Thesis, University of California, Riverside, CA, USA, 2020. Available online: https://escholarship.org/uc/item/6b80g2jc (accessed on 5 October 2025).
- Akhtar, M.S.; Feng, T. A Systemic Security and Privacy Review: Attacks and Prevention Mechanisms over IoT Layers. In Big Data Analytics and Computational Intelligence for Cybersecurity; EAI Endorsed Transactions on Security and Safety; Springer: Cham, Switzerland, 2022; Volume 8, pp. 1–12. [Google Scholar] [CrossRef]
- Nasralla, M.M.; García-Magariño, I.; Lloret, J. Defenses against perception-layer attacks on IoT smart furniture for impaired people. IEEE Access 2020, 8, 119795–119805. [Google Scholar] [CrossRef]
- Singh, N.; Buyya, R.; Kim, H. Securing Cloud-Based Internet of Things: Challenges and Mitigations. Sensors 2025, 25, 79. [Google Scholar] [CrossRef] [PubMed]
- Afraji, D.M.A.A.; Lloret, J.; Peñalver, L. Deep Learning-Driven Defense Strategies for Mitigating DDoS Attacks in Cloud Computing Environments. Cyber Secur. Appl. 2025, 3, 100085. [Google Scholar] [CrossRef]
- Abbasi, M.; Plaza-Hernández, M.; Prieto, J.; Corchado, J.M. Security in the Internet of Things Application Layer: Requirements, Threats, and Solutions. IEEE Access 2022, 10, 97197–97216. [Google Scholar] [CrossRef]
- Zenarmor. IoT Firewall: Definition, Features, Advantages and Disadvantages. Report. 2024. Available online: https://www.zenarmor.com/docs/network-security-tutorials/what-is-iot-firewall (accessed on 5 October 2025).
- Maricheva, A. What Is Firewall in IoT: Safeguarding Your Connected Ecosystem. Softteco Report. 2024. Available online: https://softteco.com/blog/what-is-iot-firewall (accessed on 5 October 2025).
- Raeisi-Varzaneh, M.; Habbal, A.; Dakkak, O. Firewalls and Internet of Things Security: A Survey. Curr. Trends Comput. 2023, 1, 22–43. Available online: https://www.researchgate.net/publication/375379677_FIREWALLS_AND_INTERNET_OF_THINGS_SECURITY_A_SURVEY (accessed on 5 October 2025).
- Anwar, R.; Abdullah, T.; Pastore, F. Firewall Best Practices for Securing Smart Healthcare Environment: A Review. Appl. Sci. 2021, 11, 9183. [Google Scholar] [CrossRef]
- Karahan, O.; Kaya, B. Raspberry-Pi Firewall and Intrusion Detection System. J. Intell. Syst. Theory Appl. 2020, 3, 21–24. [Google Scholar] [CrossRef]
- Fei, W.; Ohno, H.; Sampalli, S. Design and Implementation of Raspberry House: An IoT Security Framework. In Proceedings of the IEEE International Conference on Internet of Things and Intelligence System (IoTaIS), Bali, Indonesia, 23–24 November 2021. [Google Scholar] [CrossRef]
- Álvarez Ramírez, A.M. Diseño e Implementación de un Firewall para Dispositivos IoT Utilizando Raspberry, Aplicando Tecnologías IPS para Detectar Tráfico Malicioso. End of BsC Project. 2022. Available online: http://dspace.espoch.edu.ec/bitstream/123456789/20827/1/98T00370.pdf (accessed on 5 October 2025).
- Castro-Valdivia, R.; López-Álvarez, F.J.; Zarate-Nava, M.R.; Castillo-Tapia, R.; Pacheco-Sánchez, C.A.; Landa-Huerta, E.M. Sistema de Seguridad para Dispositivos IoT Mediante Raspberry-Pi. Congreso Estudiantil de Inteligencia Artificial Aplicada a la Ingeniería y Tecnología. 2024, pp. 186–191. Available online: https://virtual.cuautitlan.unam.mx/intar/memoriasceiaait/wp-content/uploads/sites/19/2024/12/186-Sistema-de-seguridad-para-dispositivos-IoT-__mediante-raspberry-Pi-EDITADO.pdf (accessed on 5 October 2025).
- Sforzin, A.; Mármol, F.G.; Conti, M.; Bohli, J.M. RPiDS: Raspberry-Pi IDS—A Fruitful Intrusion Detection System for IoT. In Proceedings of the Intl IEEE Conferences on Ubiquitous Intelligence & Computing, Advanced and Trusted Computing, Scalable Computing and Communications, Cloud and Big Data Computing, Internet of People, and Smart World Congress (UIC/ATC/ScalCom/CBDCom/IoP/SmartWorld), Toulouse, France, 18–21 July 2016; pp. 440–448. Available online: https://ieeexplore.ieee.org/document/7816876 (accessed on 5 October 2025).
- Syamsuddin, I.; Barukab, O.M. SUKRY: Suricata IDS with Enhanced kNN Algorithm on Raspberry-Pi for Classifying IoT Botnet Attacks. Electronics 2022, 11, 737. [Google Scholar] [CrossRef]
- Dennstädt, F.; Hastings, J.; Putora, P.M.; Schmerder, M.; Cihoric, N. Implementing large language models in healthcare while balancing control, collaboration, costs and security. Digit. Med. 2025, 8, 143. [Google Scholar] [CrossRef] [PubMed]





| Attack: TCP SYN flood | hping3 -S -p 481 –flood 10.0.0.20 |
| Alert | 07/08/2025-09:15:44.440308 [**] [1:200002:2] [DDoS][IOMT] Unusually high traffic [**] TCP 10.0.0.10:3837 → 10.0.0.20:481 |
| Rules | ip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 481 tcp flags syn limit rate 5/second counter packets 22 bytes 1012 acceptip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 481 tcp flags syn counter packets 109,772 bytes 5,049,512 drop |
| Packets blocked/accepted | 109,772 blocked/22 accepted |
| Attack: Nmap NULL scan | nmap -sN 10.0.0.20 -p 21,22,80,443,1720 |
| Alert | 07/08/2025-09:24:32.288151 [**] [1:200006:1] [Intrusion][Nmap] NULL scan detected [**] [Classification: (null)] [Priority: 3] TCP 10.0.0.10:39515 → 10.0.0.20:21-443,1720 |
| Rules | ip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport [21/22,80,443,1720] tcp flags syn limit rate 5/second counter acceptip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport [21/22,80,443,1720] counter drop (Rules separated per port) |
| Packets blocked/accepted | 2 blocked per port (total 10)/0 accepted |
| Attack: Nmap FIN scan | nmap -sF 10.0.0.20 -p 111 |
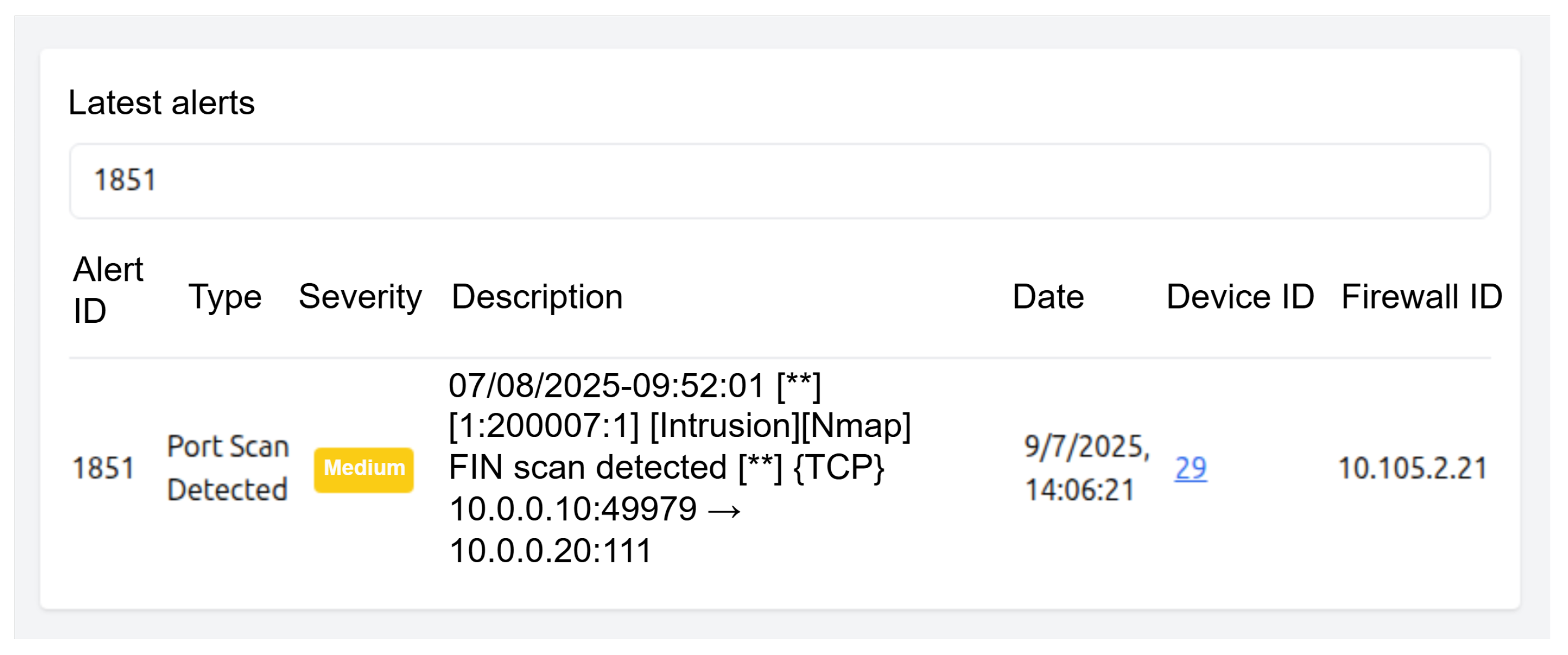
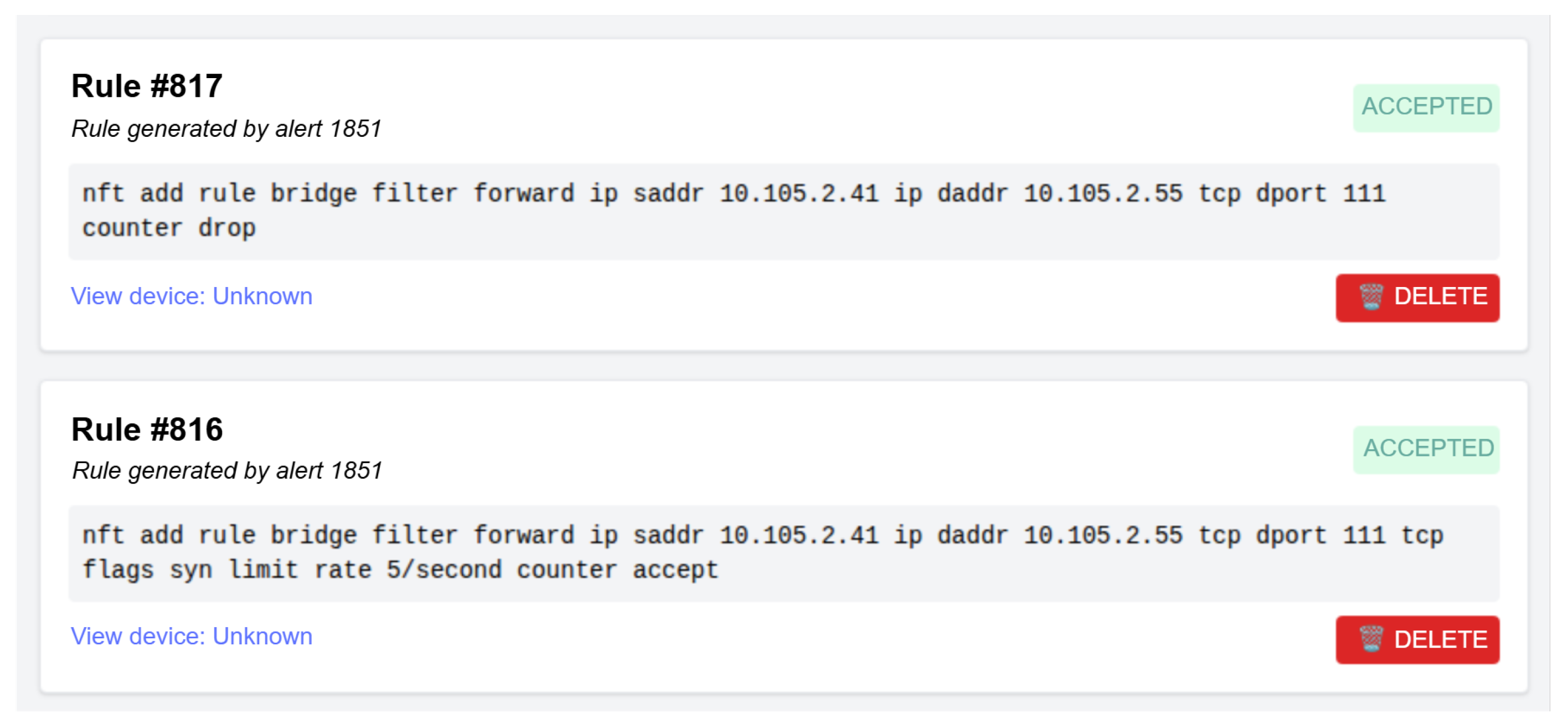
| Alert | 07/08/2025-09:52:01 [**] [1:200007:1] [Intrusion][Nmap] FIN scan detected [**] TCP 10.0.0.10:49979 → 10.0.0.20:111 |
| Rules | ip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 111 tcp flags syn limit rate 5/second counter acceptip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 111 counter drop |
| Packets blocked/accepted | 2 blocked/0 accepted |
| Attack: Nmap OS fingerprinting and high traffic (DDoS) | nmap -O –reason 10.0.0.20 |
| Alert | 07/15/2025-16:42:03 [**] [1:300005:1] [Intrusion][Nmap] Suspicious OS fingerprinting (SYN without payload) [**] TCP 10.0.0.10:45971 → 10.0.0.20:1720 07/15/2025-16:42:04 [**] [1:200002:2] [DDoS][IoMT] Unusually high traffic [**] TCP 10.0.0.10:45973 → 10.0.0.20:3920 |
| Rules | ip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 1720 tcp flags syn limit rate 5/second counter acceptip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 1720 counter dropip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 3920 tcp flags syn limit rate 5/second counter acceptip saddr 10.0.0.10 ip daddr 10.0.0.20 tcp dport 3920 counter dropip saddr 10.0.0.10 ip protocol tcp counter drop |
| Packets blocked/accepted | 2012 blocked/0 accepted |
| Attack: Nmap OS fingerprinting | nmap -O –reason 10.0.1.20 |
| Alert | 07/17/2025-11:09:XX [**] [1:300005:1] [Intrusion][Nmap] Suspicious OS fingerprinting (SYN without payload) [**] TCP 10.0.1.10:XXXXX → 10.0.1.20:1720/5060 |
| Rules | ip saddr 10.0.1.10 ip daddr 10.0.1.20 tcp dport 1720 tcp flags syn limit rate 5/second counter acceptip saddr 10.0.1.10 ip daddr 10.0.1.20 tcp dport 1720 counter dropip saddr 10.0.1.10 ip daddr 10.0.1.20 tcp dport 5060 tcp flags syn limit rate 5/second counter acceptip saddr 10.0.1.10 ip daddr 10.0.1.20 tcp dport 5060 counter drop |
| Packets blocked/accepted | 2030 blocked/0 accepted |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gosálvez-White, I.; Rodríguez-Martín, N.; Barajas-García, N.; Mena-Gallardo, C.; García-Teodoro, P. MEDIotWALL: Securing Smart Healthcare Environments Through IoT Firewalls. Sensors 2025, 25, 6235. https://doi.org/10.3390/s25196235
Gosálvez-White I, Rodríguez-Martín N, Barajas-García N, Mena-Gallardo C, García-Teodoro P. MEDIotWALL: Securing Smart Healthcare Environments Through IoT Firewalls. Sensors. 2025; 25(19):6235. https://doi.org/10.3390/s25196235
Chicago/Turabian StyleGosálvez-White, Irene, Nerea Rodríguez-Martín, Nicolás Barajas-García, Carmen Mena-Gallardo, and Pedro García-Teodoro. 2025. "MEDIotWALL: Securing Smart Healthcare Environments Through IoT Firewalls" Sensors 25, no. 19: 6235. https://doi.org/10.3390/s25196235
APA StyleGosálvez-White, I., Rodríguez-Martín, N., Barajas-García, N., Mena-Gallardo, C., & García-Teodoro, P. (2025). MEDIotWALL: Securing Smart Healthcare Environments Through IoT Firewalls. Sensors, 25(19), 6235. https://doi.org/10.3390/s25196235






