UAV-Enabled Maritime IoT D2D Task Offloading: A Potential Game-Accelerated Framework
Abstract
1. Introduction
- This paper introduces a novel edge computing architecture in maritime IoT systems to fully utilize the advantage of UAV-assisted edge computing (with UAVs serving as dynamic CHs) and D2D-assisted edge networks (with USVs cooperating in clusters), aiming to provide USVs with low-latency and reliable computing services.
- A global task offloading latency minimization model is constructed by jointly optimizing D2D link selection, UAV arrival time, and hovering coordinates. To reduce computational complexity, a heuristic solution is proposed to decompose the proposed problem into multiple subproblems and design suboptimal solutions, thereby reducing the optimization cost associated with long-term repeated optimization.
- The simulation results under simulated realistic scenarios and various system settings demonstrate that our proposed framework can effectively reduce the overall system delay while making full use of the available communication and computing resources.
2. System Overview and Problem Formulation
2.1. System Model
2.2. Problem Formulation
- Intra-Cluster Task Distribution: Within the cluster, the designated UAV serving as the CH acts as the communication relay. USVs access the CH via a wireless cellular link. Consequently, the intra-cluster task distribution latency from the CH to USV i can be expressed aswhere represents the data transmission rate between the CH and USV i, measured in bits per second, and denotes the size of the task processed by USV i.
- The Task Execution Process: Once intra-cluster task allocation is completed, USV i immediately executes its assigned subtask. Therefore, the task execution delay of USV i can be expressed aswhere represents the number of CPU cycles required to process a data sample, and denotes the CPU computation frequency of USV i.Let denote the intermediate data forwarded from USV i to USV j after local computation. The corresponding communication delay iswhere denotes the D2D data transmission rate between USV i and USV j.
- Task Collection by the CH: Upon the completion of execution, the CH instructs the USVs within the cluster to return their processed segments for aggregation. Since the task collection process is almost identical to the intra-cluster task distribution process, the delay of model collection is equal to .Finally, the total intra-cluster processing delay can be calculated aswhere .
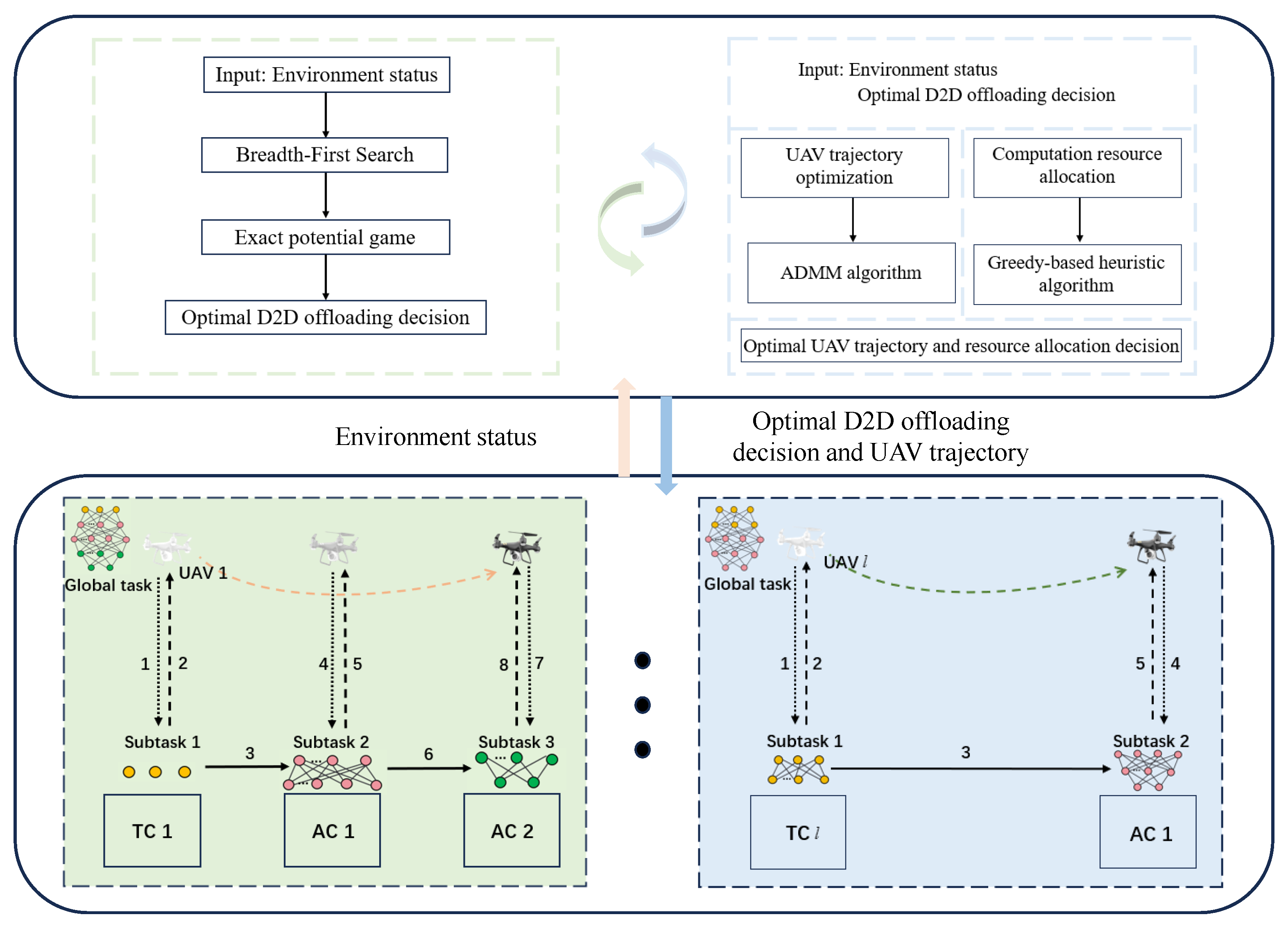
3. Problem Decomposition and Proposed Method
3.1. BFS-Based Distributed Game Clustering
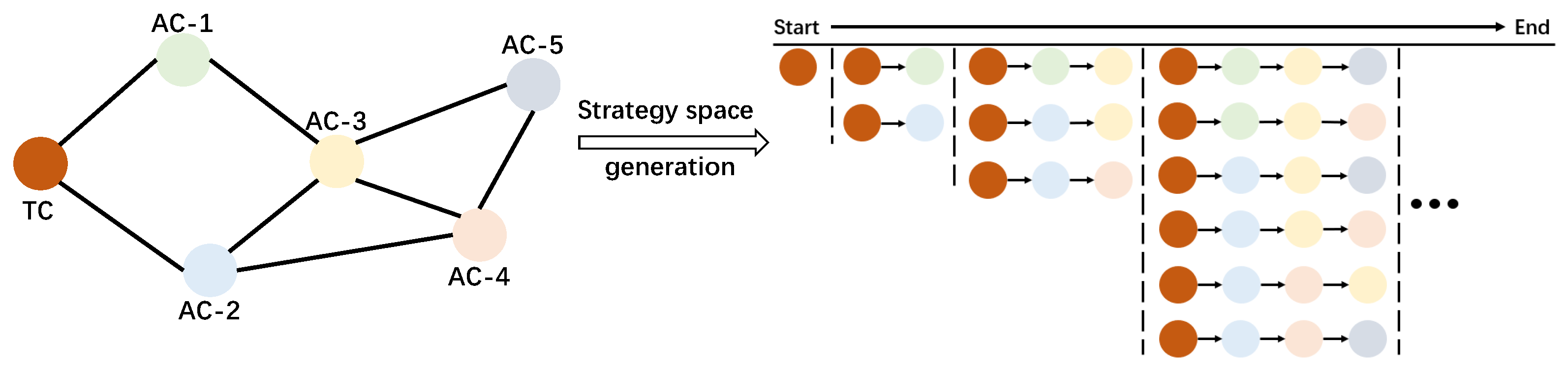
3.2. Optimizing the Task Allocation for a Given Clustering Strategy
| Algorithm 1 Task offloading algorithm for given clustering strategy. |
| Input: Clustering strategy: ; computing capability of each USV: ; transmission rates between nodes: ; computational workload of all D layers: ; transmitted intermediate data size between corresponding M layers: . Output: Task splitting and allocation strategy: ;
|
3.3. Optimizing UAV Arrival Times and Hoverings Coordinate for a Given Clustering Strategy
- Update: Based on the aforementioned definitions of the variables , their optimization can be processed separately and independently. The optimization procedure for each parameter can be formulated aswhere , , represent the solutions obtained after the n-th iteration. Due to the influence of constraints, (31) constitutes a non-convex problem. To resolve this issue, we introduce auxiliary variables , , and , corresponding to the transmission rates , , and , respectively. Thus, (31) can be reformulated aswhere , , and represent the transmission rates after substituting . However, since , , and remain non-convex with respect to , (33) is still intractable for direct solution. Notably, and exhibit convexity with respect to , while is convex with respect to . To address this, we seek convex lower bounds for , , and to replace the original non-convex functions, thereby transforming the optimization problem into a convex problem. Assuming the current iteration point is , the convex lower bounds for , , and obtained via first-order Taylor expansion at can be expressed asSubstituting (34)–(36) into (33) transforms the latter into a convex optimization problem, which can be efficiently solved using conventional convex optimization methods. Similarly, (32) can be solved following an analogous procedure, the details of which are omitted here for brevity.
- Update : The optimization procedure for can be formulated asFollowing the same solution approach applied to (31), we introduce auxiliary variables , , and corresponding to the transmission rates , , and , respectively. Thus, (37) can be reformulated asThe analytical approach for , , and follows the same methodology applied to , , and and thus will not be reiterated here. After this reformulation, (38) becomes a convex optimization problem that can be efficiently solved using standard convex optimization techniques.
- Updating the Lagrange multiplier: The optimization procedure for the Lagrange multiplier can be formulated asThe detailed procedure of addressing the problem of optimizing the UAV arrival times and hovering coordinates given fixed client clustering and task allocation strategies is presented in Algorithm 2.
| Algorithm 2 ADMM-based UAV optimization algorithm for a given clustering strategy. |
| Input: The joint strategy of the L clusters: ; B, ; Output: Optimal UAV arrival time t and hovering coordinates ;
|
3.4. Overview of Clustering-Based Distributed Task Offloading Algorithms
| Algorithm 3 Overview of clustering-based distributed task offloading algorithms. |
| Input: Clustering strategy: ; Output: Optimal global latency T;
|
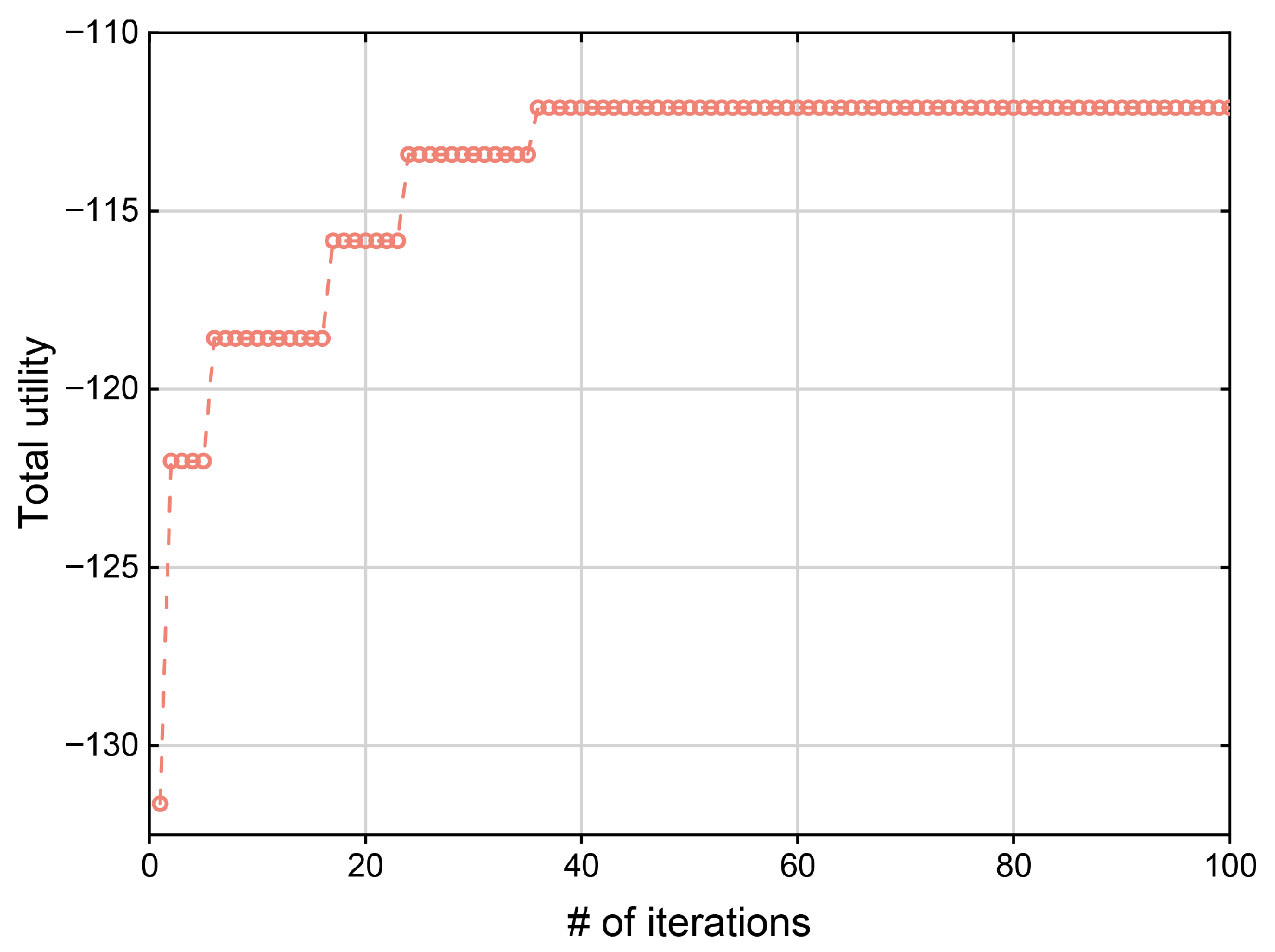
3.5. Convergence and Complexity Analysis
4. Experimental Results and Analysis
4.1. Parameter Settings
4.2. Convergence Behavior
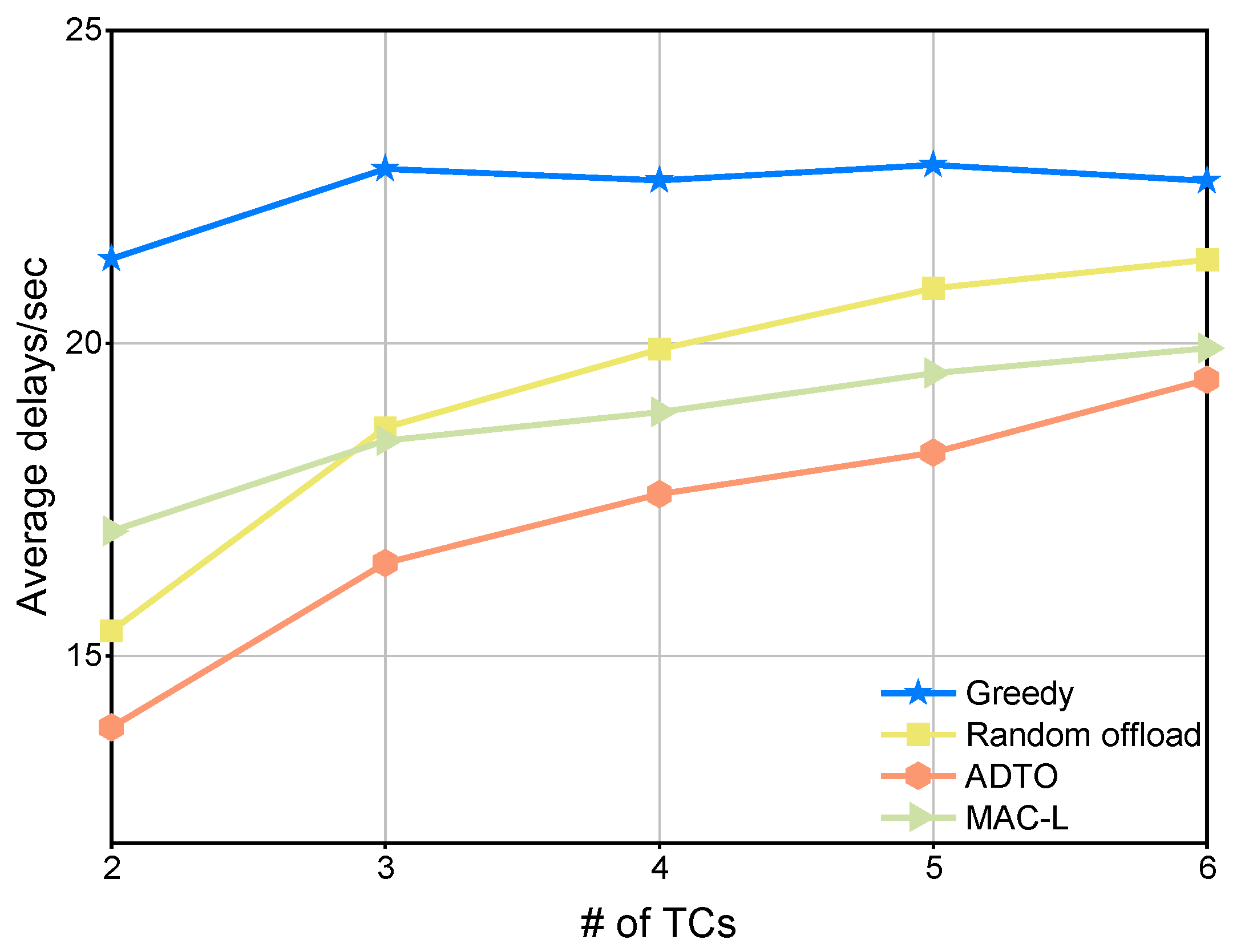
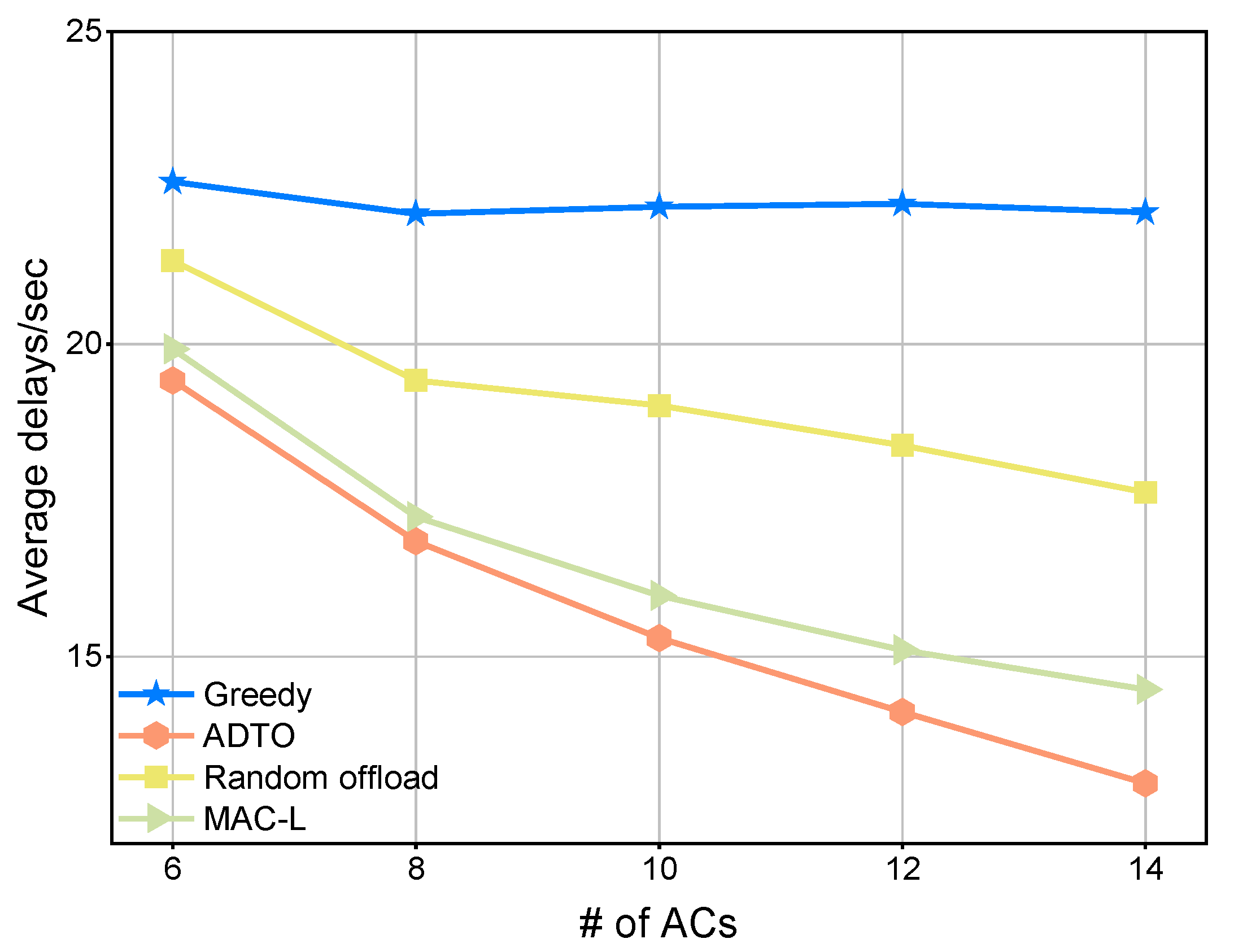
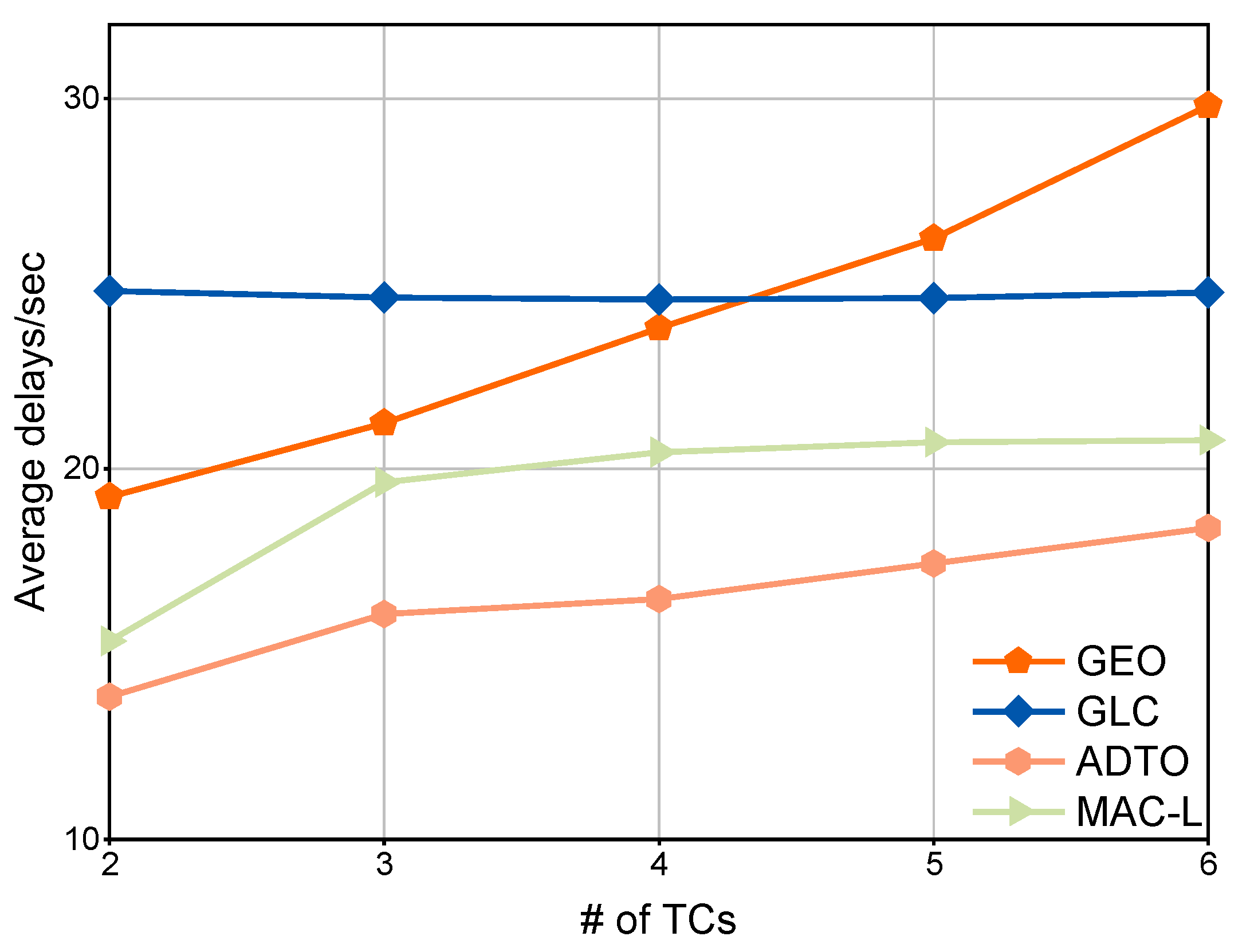
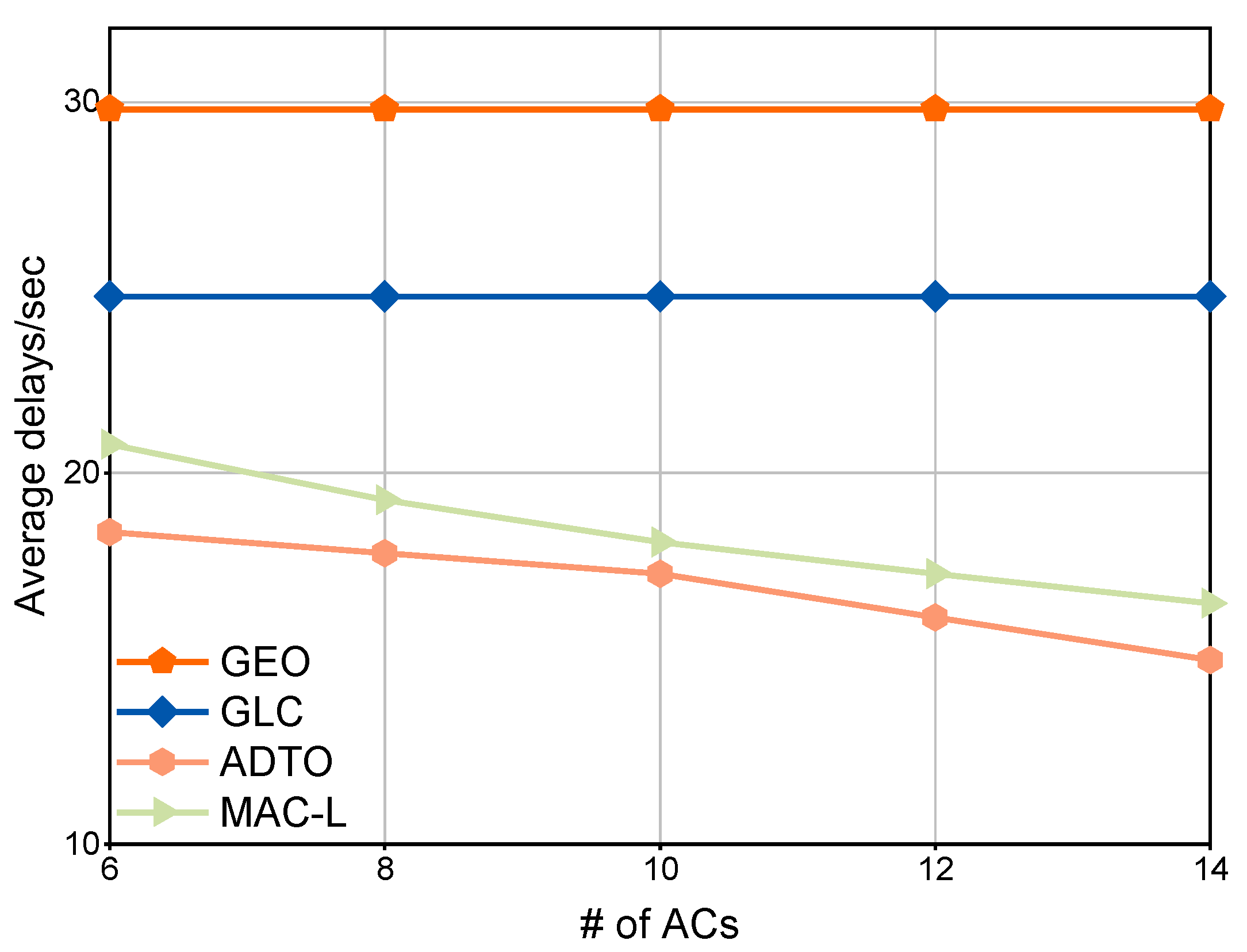
4.3. Task Execution Latency Comparison
4.3.1. Local Offloading Mechanisms
4.3.2. Global Offloading Mechanisms
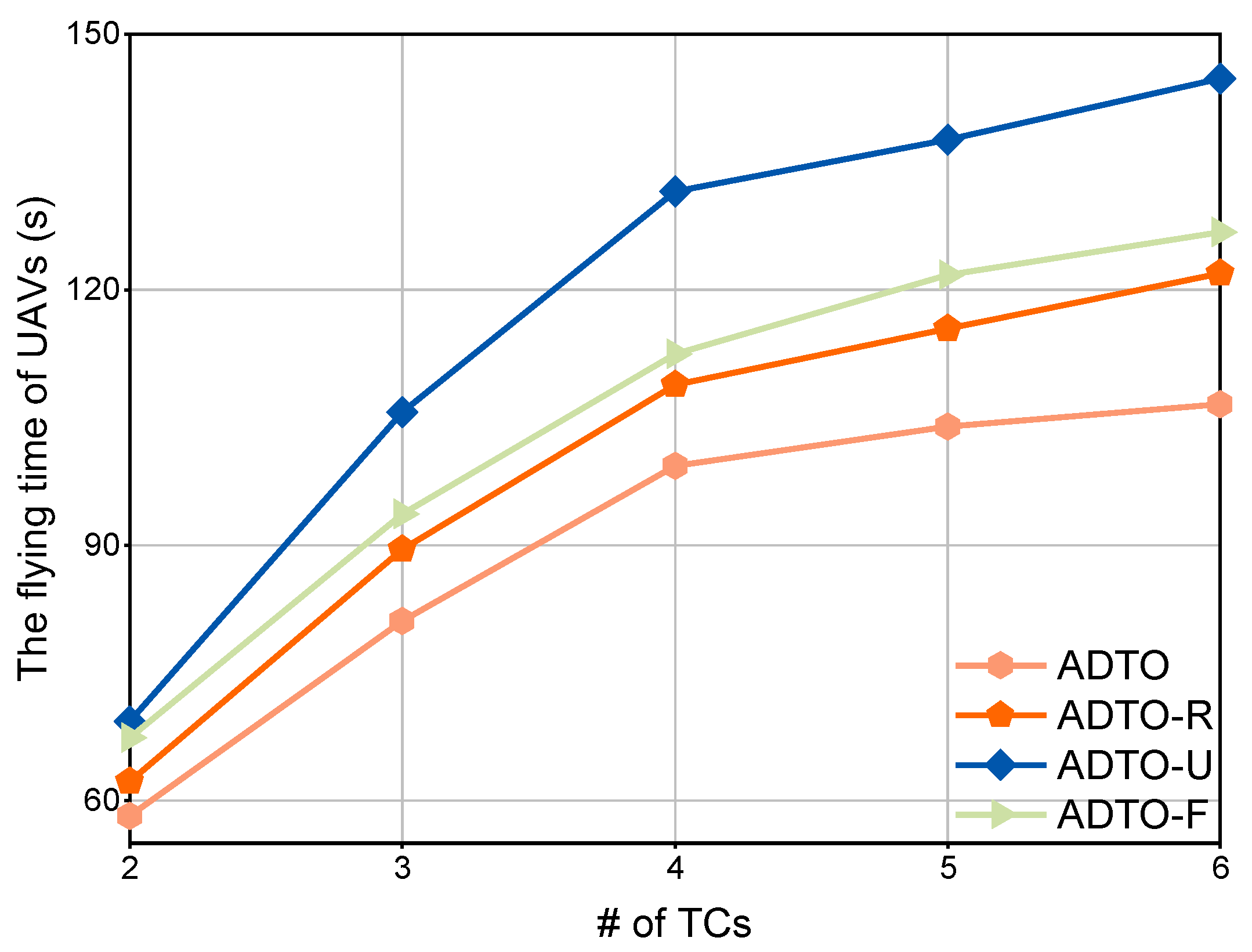
4.4. UAV Time Cost Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| UAV | unmanned aerial vehicle |
| USV | unmanned surface vessel |
| D2D | device-to-device |
| BFS | breadth-first search |
| ADMM | Alternating Direction Method of Multipliers |
| MEC | mobile edge computing |
| SCA | Successive Convex Approximation |
| IoT | Internet of Things |
| CH | cluster head |
| CSI | Channel State Information |
| LoS | Line of Sight |
| TC | task client |
| AC | assisting client |
| EPG | exact potential game |
| NE | Nash Equilibrium |
| RSS | Received Signal Strength |
| MARL | multi-agent reinforcement learning |
| FCTE | Fuzzy Comprehensive Trust Evaluation |
| DT | Digital Twin |
| TBS | terrestrial base station |
References
- Wang, J.B.; Zeng, C.; Ding, C.; Zhang, H.; Lin, M.; Wang, J. Unmanned Surface Vessel Assisted Maritime Wireless Communication Toward 6G: Opportunities and Challenges. IEEE Wirel. Commun. 2022, 29, 72–79. [Google Scholar] [CrossRef]
- Malik, U.M.; Javed, M.A.; Zeadally, S.; Islam, S.U. Energy-Efficient Fog Computing for 6G-Enabled Massive IoT: Recent Trends and Future Opportunities. IEEE Internet Things J. 2022, 9, 14572–14594. [Google Scholar] [CrossRef]
- Hesselbarth, A.; Medina, D.; Ziebold, R.; Sandler, M.; Hoppe, M.; Uhlemann, M. Enabling Assistance Functions for the Safe Navigation of Inland Waterways. IEEE Intell. Transp. Syst. Mag. 2020, 12, 123–135. [Google Scholar] [CrossRef]
- Alqurashi, F.S.; Trichili, A.; Saeed, N.; Ooi, B.S.; Alouini, M.S. Maritime Communications: A Survey on Enabling Technologies, Opportunities, and Challenges. IEEE Internet Things J. 2023, 10, 3525–3547. [Google Scholar] [CrossRef]
- Zhang, G.; Yin, S.; Li, J.; Zhang, W.; Zhang, W. Game-Based Event-Triggered Control for Unmanned Surface Vehicle: Algorithm Design and Harbor Experiment. IEEE Trans. Cybern. 2025, 55, 2729–2741. [Google Scholar] [CrossRef]
- Zhang, G.; Xing, Y.; Zhang, W.; Li, J. Prescribed Performance Control for USV-UAV via a Robust Bounded Compensating Technique. IEEE Trans. Control Netw. Syst. 2025, 1–11. [Google Scholar] [CrossRef]
- Liao, Y.; Chen, X.; Xia, S.; Ai, Q.; Liu, Q. Energy Minimization for UAV Swarm-Enabled Wireless Inland Ship MEC Network with Time Windows. IEEE Trans. Green Commun. Netw. 2023, 7, 594–608. [Google Scholar] [CrossRef]
- Liu, X.; Chen, A.; Zheng, K.; Chi, K.; Yang, B.; Taleb, T. Distributed Computation Offloading for Energy Provision Minimization in WP-MEC Networks with Multiple HAPs. IEEE Trans. Mob. Comput. 2025, 24, 2673–2689. [Google Scholar] [CrossRef]
- Wu, Q.; Cui, M.; Zhang, G.; Wang, F.; Wu, Q.; Chu, X. Latency Minimization for UAV-Enabled URLLC-Based Mobile Edge Computing Systems. IEEE Trans. Wirel. Commun. 2024, 23, 3298–3311. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, J.; Wang, B.; Jiang, F. Offloading strategy for UAV-assisted mobile edge computing based on reinforcement learning. In Proceedings of the IEEE/CIC International Conference on Communications in China (ICCC), Foshan, China, 11–13 August 2022; pp. 702–707. [Google Scholar]
- Liao, Y.; Chen, X.; Liu, J.; Han, Y.; Xu, N.; Yuan, Z. Cooperative UAV-USV MEC Platform for Wireless Inland Waterway Communications. IEEE Trans. Consum. Electron. 2024, 70, 3064–3076. [Google Scholar] [CrossRef]
- Lyu, L.; Chu, Z.; Lin, B.; Dai, Y.; Cheng, N. Fast Trajectory Planning for UAV-Enabled Maritime IoT Systems: A Fermat-Point Based Approach. IEEE Wirel. Commun. Lett. 2022, 11, 328–332. [Google Scholar] [CrossRef]
- Qian, L.P.; Zhang, H.; Wang, Q.; Wu, Y.; Lin, B. Joint Multi-Domain Resource Allocation and Trajectory Optimization in UAV-Assisted Maritime IoT Networks. IEEE Internet Things J. 2023, 10, 539–552. [Google Scholar] [CrossRef]
- He, Y.; Ren, J.; Yu, G.; Cai, Y. D2D Communications Meet Mobile Edge Computing for Enhanced Computation Capacity in Cellular Networks. IEEE Trans. Wirel. Commun. 2019, 18, 1750–1763. [Google Scholar] [CrossRef]
- Chen, X.; Jiao, L.; Li, W.; Fu, X. Efficient Multi-User Computation Offloading for Mobile-Edge Cloud Computing. IEEE/ACM Trans. Netw. 2016, 24, 2795–2808. [Google Scholar] [CrossRef]
- Jiang, Q.; Xu, X.; Bilal, M.; Crowcroft, J.; Liu, Q.; Dou, W.; Jiang, J. Potential Game Based Distributed IoV Service Offloading with Graph Attention Networks in Mobile Edge Computing. IEEE Trans. Intell. Transp. Syst. 2024, 25, 10912–10925. [Google Scholar] [CrossRef]
- Zhang, F.; Wang, M.M. Stochastic Congestion Game for Load Balancing in Mobile-Edge Computing. IEEE Internet Things J. 2021, 8, 778–790. [Google Scholar] [CrossRef]
- Cheng, Z.; Xia, X.; Liwang, M.; Fan, X.; Sun, Y.; Wang, X.; Huang, L. CHEESE: Distributed Clustering-Based Hybrid Federated Split Learning Over Edge Networks. IEEE Trans. Parallel Distrib. Syst. 2023, 34, 3174–3191. [Google Scholar] [CrossRef]
- He, H.; Yang, X.; Huang, F.; Shen, H.; Tian, H. Enhancing QoE in Large-Scale U-MEC Networks via Joint Optimization of Task Offloading and UAV Trajectories. IEEE Internet Things J. 2024, 11, 35710–35723. [Google Scholar] [CrossRef]
- Wang, J.; Zhu, K.; Chen, B.; Han, Z. Distributed Clustering-Based Cooperative Vehicular Edge Computing for Real-Time Offloading Requests. IEEE Trans. Veh. Technol. 2022, 71, 653–669. [Google Scholar]
- Rohoden, K.; Estrada, R.; Otrok, H.; Dziong, Z. Stable femtocells cluster formation and resource allocation based on cooperative game theory. Comput. Commun. 2019, 134, 30–41. [Google Scholar] [CrossRef]
- Wu, D.; Wang, J.; Hu, R.Q.; Cai, Y.; Zhou, L. Energy-Efficient Resource Sharing for Mobile Device-to-Device Multimedia Communications. IEEE Trans. Veh. Technol. 2014, 63, 2093–2103. [Google Scholar] [CrossRef]
- Fang, T.; Yuan, F.; Ao, L.; Chen, J. Joint Task Offloading, D2D Pairing, and Resource Allocation in Device-Enhanced MEC: A Potential Game Approach. IEEE Internet Things J. 2022, 9, 3226–3237. [Google Scholar] [CrossRef]
- Wu, Q.; Wu, D.; Xu, Y.; Wang, J. Demand-Aware Multichannel Opportunistic Spectrum Access: A Local Interaction Game Approach with Reduced Information Exchange. IEEE Trans. Veh. Technol. 2015, 64, 4899–4904. [Google Scholar] [CrossRef]
- Osborne, M.J.; Rubinstein, A. A Course in Game Theory; MIT Press: Cambridge, MA, USA, 1994. [Google Scholar]
- Monderer, D.; Shapley, L.S. Potential games. Games Econ. Behav. 1996, 14, 124–143. [Google Scholar] [CrossRef]
- Lã, Q.D.; Chew, Y.H.; Soong, B.H. Potential Game Theory: Applications in Radio Resource Allocation, 1st ed.; Springer: New York, NY, USA, 1994. [Google Scholar]
- Guo, H.; Zhou, X.; Wang, J.; Liu, J.; Benslimane, A. Intelligent Task Offloading and Resource Allocation in Digital Twin Based Aerial Computing Networks. IEEE J. Sel. Areas Commun. 2023, 41, 3095–3110. [Google Scholar] [CrossRef]
- Soleymani, S.A.; Goudarzi, S.; Xiao, P.; Mihaylova, L.; Shojafar, M.; Wang, W. Multi-agent Q-learning with Particle Filtering for UAV Tracking in Open-RAN Environment. IEEE Trans. Aerosp. Electron. Syst. 2025, 61, 1–21. [Google Scholar] [CrossRef]
- Zhu, S.; Gui, L.; Zhao, D.; Cheng, N.; Zhang, Q.; Lang, X. Learning-Based Computation Offloading Approaches in UAVs-Assisted Edge Computing. IEEE Trans. Veh. Technol. 2021, 70, 928–944. [Google Scholar] [CrossRef]
- Guo, H.; Chen, X.; Zhou, X.; Liu, J. Trusted and Efficient Task Offloading in Vehicular Edge Computing Networks. IEEE Trans. Cogn. Commun. Netw. 2024, 10, 2370–2382. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, B.; Zhao, J.; Yang, T. UAV-Enabled Maritime IoT D2D Task Offloading: A Potential Game-Accelerated Framework. Sensors 2025, 25, 5820. https://doi.org/10.3390/s25185820
Li B, Zhao J, Yang T. UAV-Enabled Maritime IoT D2D Task Offloading: A Potential Game-Accelerated Framework. Sensors. 2025; 25(18):5820. https://doi.org/10.3390/s25185820
Chicago/Turabian StyleLi, Baiyi, Jian Zhao, and Tingting Yang. 2025. "UAV-Enabled Maritime IoT D2D Task Offloading: A Potential Game-Accelerated Framework" Sensors 25, no. 18: 5820. https://doi.org/10.3390/s25185820
APA StyleLi, B., Zhao, J., & Yang, T. (2025). UAV-Enabled Maritime IoT D2D Task Offloading: A Potential Game-Accelerated Framework. Sensors, 25(18), 5820. https://doi.org/10.3390/s25185820





