TSN-Interworked Deterministic Transmission over WLAN
Abstract
1. Introduction
2. The Proposed Scheme
2.1. Background: The Time-Aware Shaper (TAS) in TSN
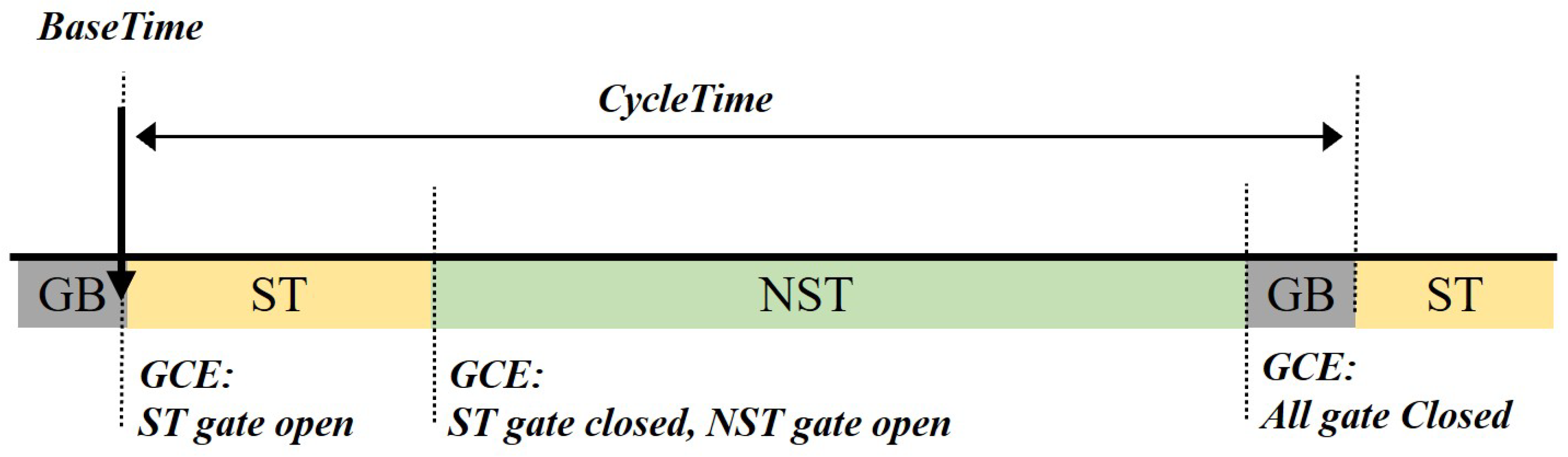
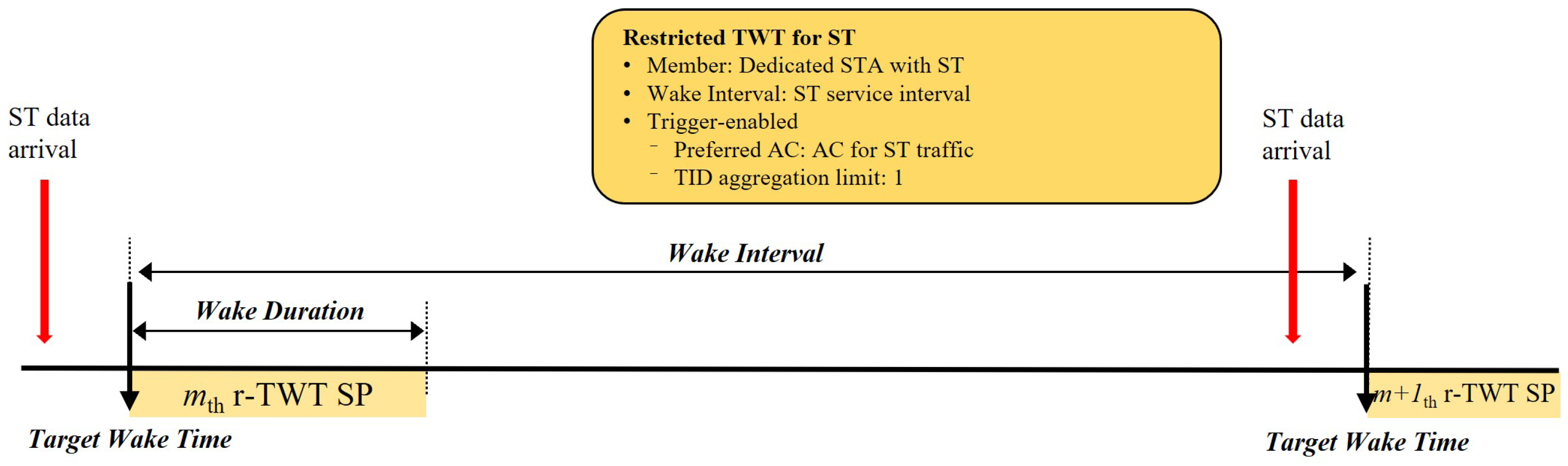
- Schedule Anchor and Synchronization (BaseTime): All TAS scheduling operates on an absolute time base that is synchronized across the entire network. The BaseTime parameter specifies the absolute, nanosecond-precision time at which the schedule begins its first cycle. All switches in the network, synchronized via the IEEE 802.1AS (generalized precision time protocol (gPTP)) protocol, start their Gate Control List (GCL) operations at this identical BaseTime [18]. This is a core concept that directly corresponds to the Target Wake Time parameter in our proposed wireless scheme, which likewise defines the absolute start time of each service period (SP).
- Periodic Scheduling (CycleTime): The schedule initiated at BaseTime repeats indefinitely based on a fixed period known as the CycleTime. This periodic nature allows for the continuous and stable handling of ST streams that require data transmission at regular intervals.
- Gate Control (GateControlEntry): Each cycle is divided into multiple ‘time slots’, and the behavior of each slot is determined by a gate control entry (GCE). A GCE specifies two key pieces of information:
- TimeInterval: Defines the duration of the time slot.
- GateState: An 8-bit mask that defines the ‘Open’ or ‘Closed’ state of the gates for each of the eight traffic queues.
To support ST traffic, the GateState for a specific TimeInterval is configured to open the gate only for the ST-designated queue, while closing the gates for all other lower-priority queues. This creates an exclusive transmission opportunity, where contention is completely eliminated. - Guard Band for Interference Prevention: A critical challenge arises when a long, low-priority frame, which started transmission in the preceding time slot, overruns into the ST slot, thereby delaying the time-sensitive frame. To solve this, TAS inserts a guard band before the ST slot. The guard band is a special time slot where the GateState is set to close all gates, ensuring the medium is idle and available right before the ST frame is scheduled for transmission.
2.2. Limitations of Existing WLAN Mechanisms
- Traffic Isolation: How can Scheduled Traffic (ST) be isolated from Non-Scheduled Traffic (NST) during medium access contention?
- Guaranteeing Timeliness: How can a designated ST frame be guaranteed to transmit at its precise scheduled time, without delays caused by other traffic?
- Network Efficiency: How can the negative performance impact of resource reservation for ST traffic on the overall network be minimized?
2.2.1. The Non-Deterministic Nature of Standard EDCA
2.2.2. Limitations of IEEE 802.11ax TWT
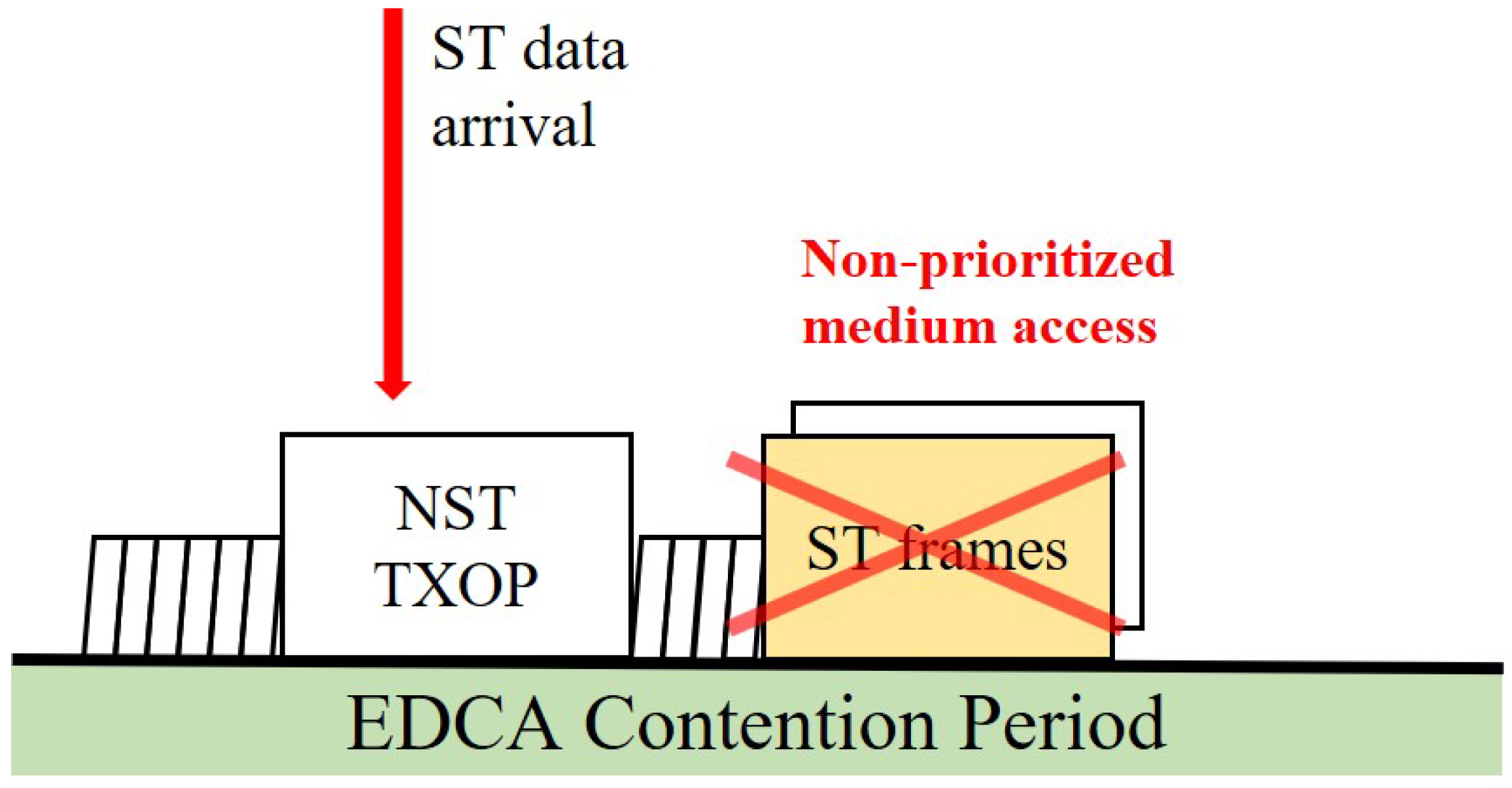
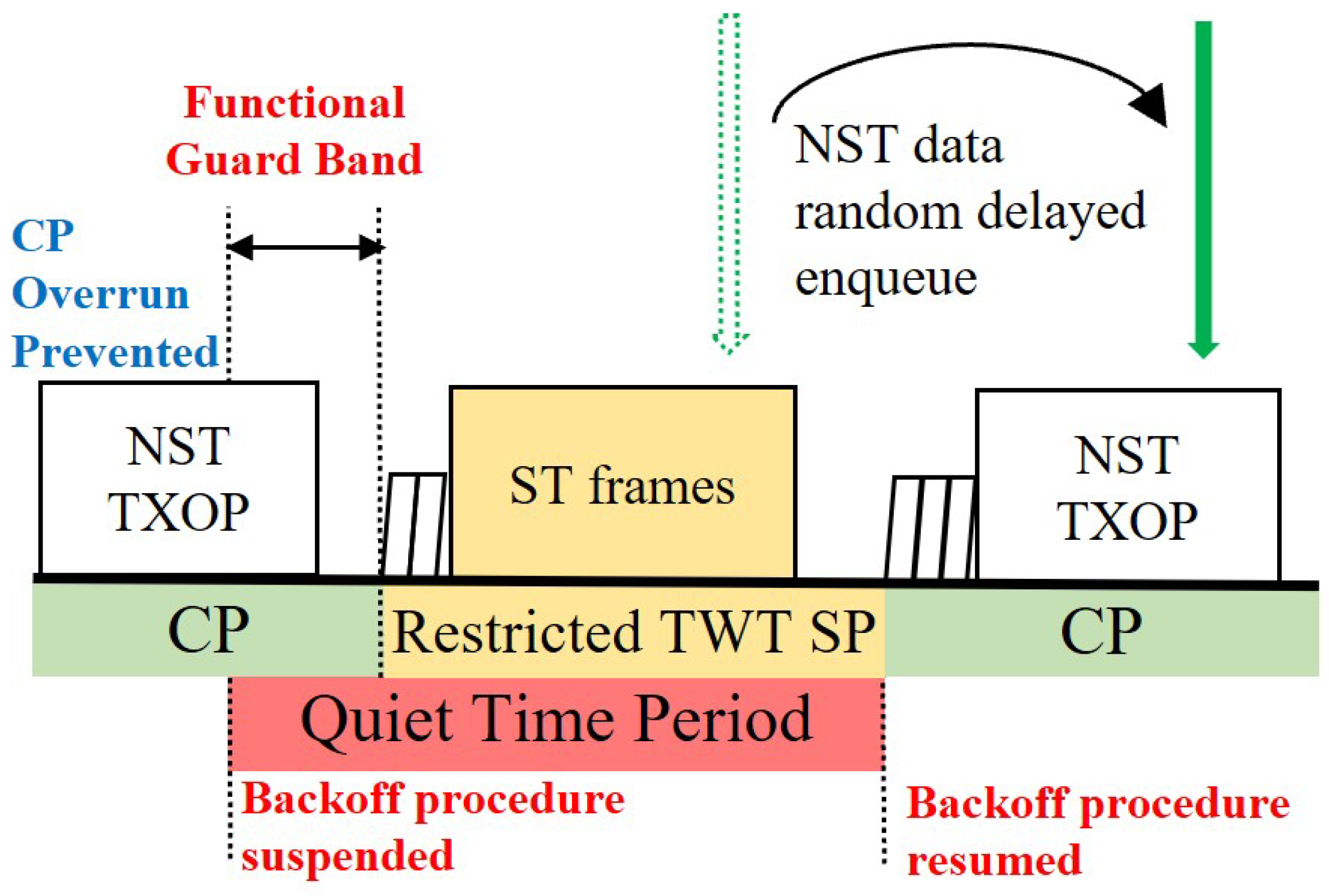
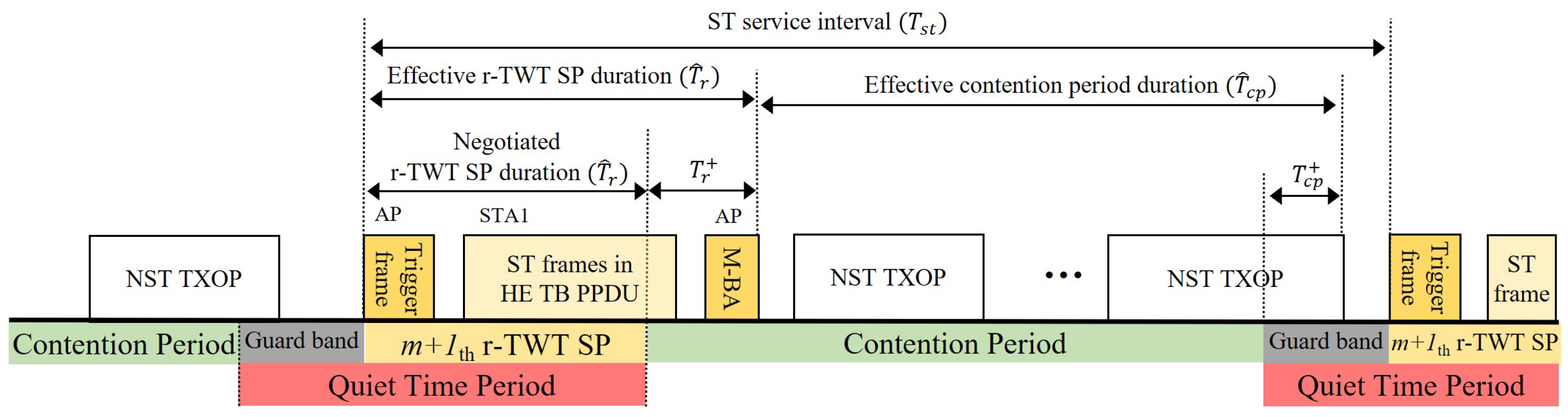
- Contention Period (CP) Overrun: A station that starts a NST frame transmission in the contention period (CP) just before the TWT SP can extend its transmission opportunity (TXOP) into the TWT SP. This ‘CP Overrun’ delays the start of the ST transmission, causing significant jitter that undermines timeliness.
- Backoff Counter Drain and Synchronized Collision: During the TWT SP, other stations are forbidden from transmitting, but their backoff counters continue to decrement whenever the channel is sensed idle. This ‘Backoff Counter drain’ phenomenon causes the backoff counters of multiple stations to converge to zero simultaneously, leading to a massive ‘Synchronized collision’ at the exact moment the next CP begins.
2.3. A Novel Transmission Scheme for Deterministic WLAN
2.3.1. r-TWT as a Functional Guard Band (GB)
2.3.2. QTP for Breaking Synchronized Collisions
2.3.3. Randomized Enqueue for Smoothing CP Load Spikes
3. Numerical Analysis
3.1. Analytical Model Overview
3.2. Scheduled Traffic (ST) Throughput Analysis
3.3. Non-Scheduled Traffic (NST) Throughput Analysis
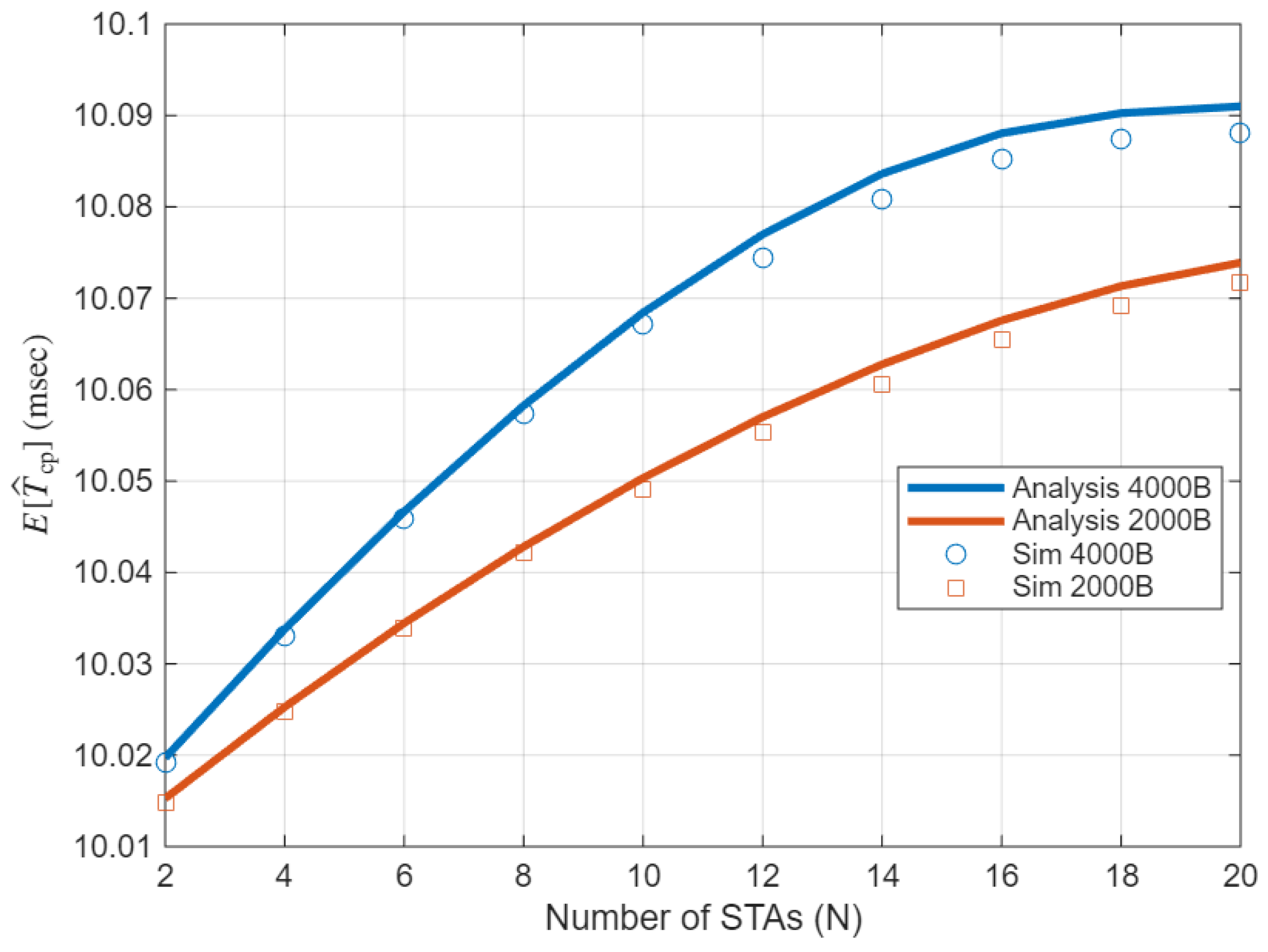
3.3.1. Modeling the Effective Contention Period Duration ()
- (i)
- r-TWT SP Overrun and Underrun and
- (ii)
- Contention Period Overrun
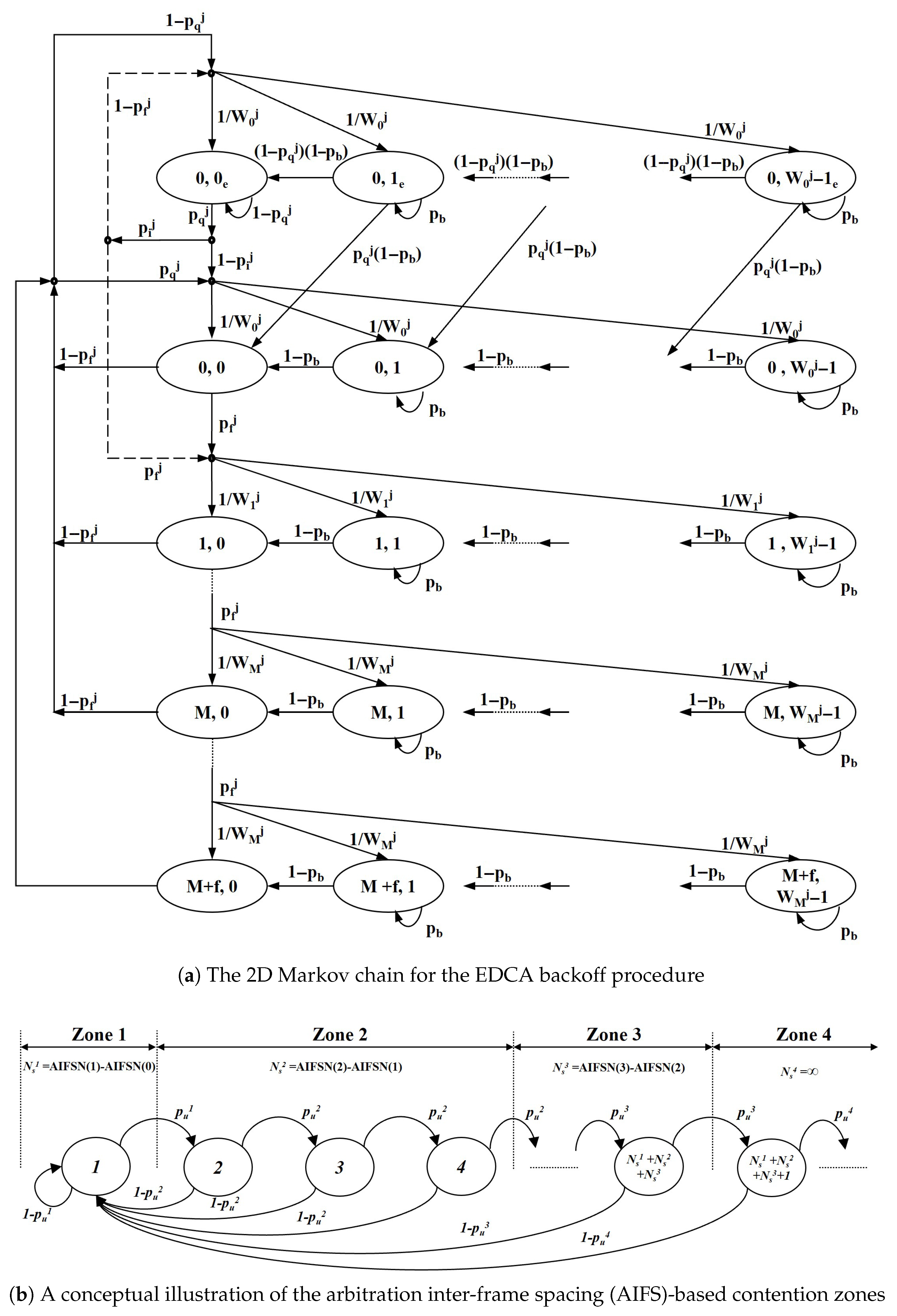
3.3.2. Markov Chain Analysis for NST Throughput
3.3.3. NST Throughput Aggregation
3.3.4. Calculation of Key System Probabilities
3.4. Dimensioning the r-TWT Service Period Under Collisions and Packet Errors
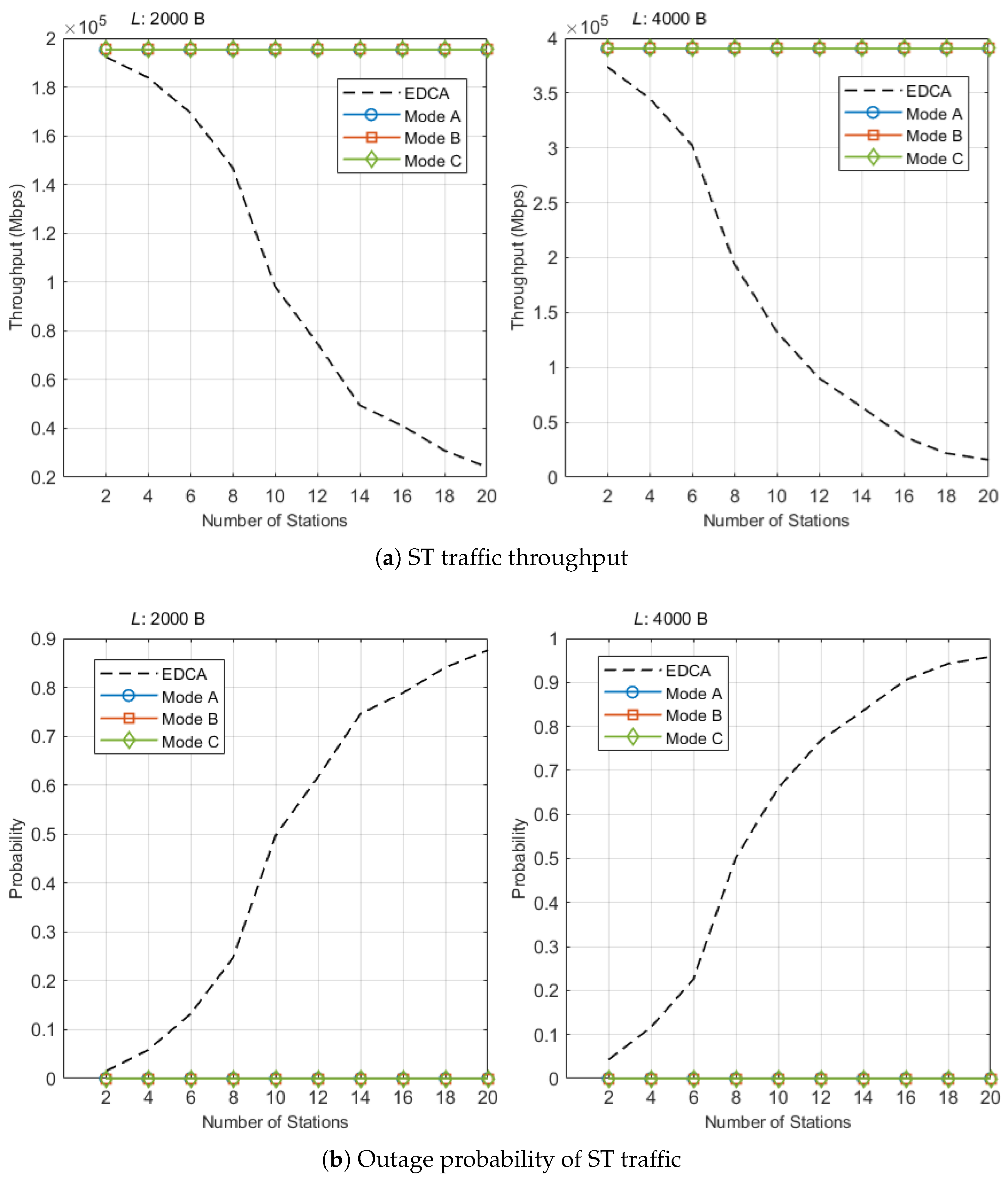
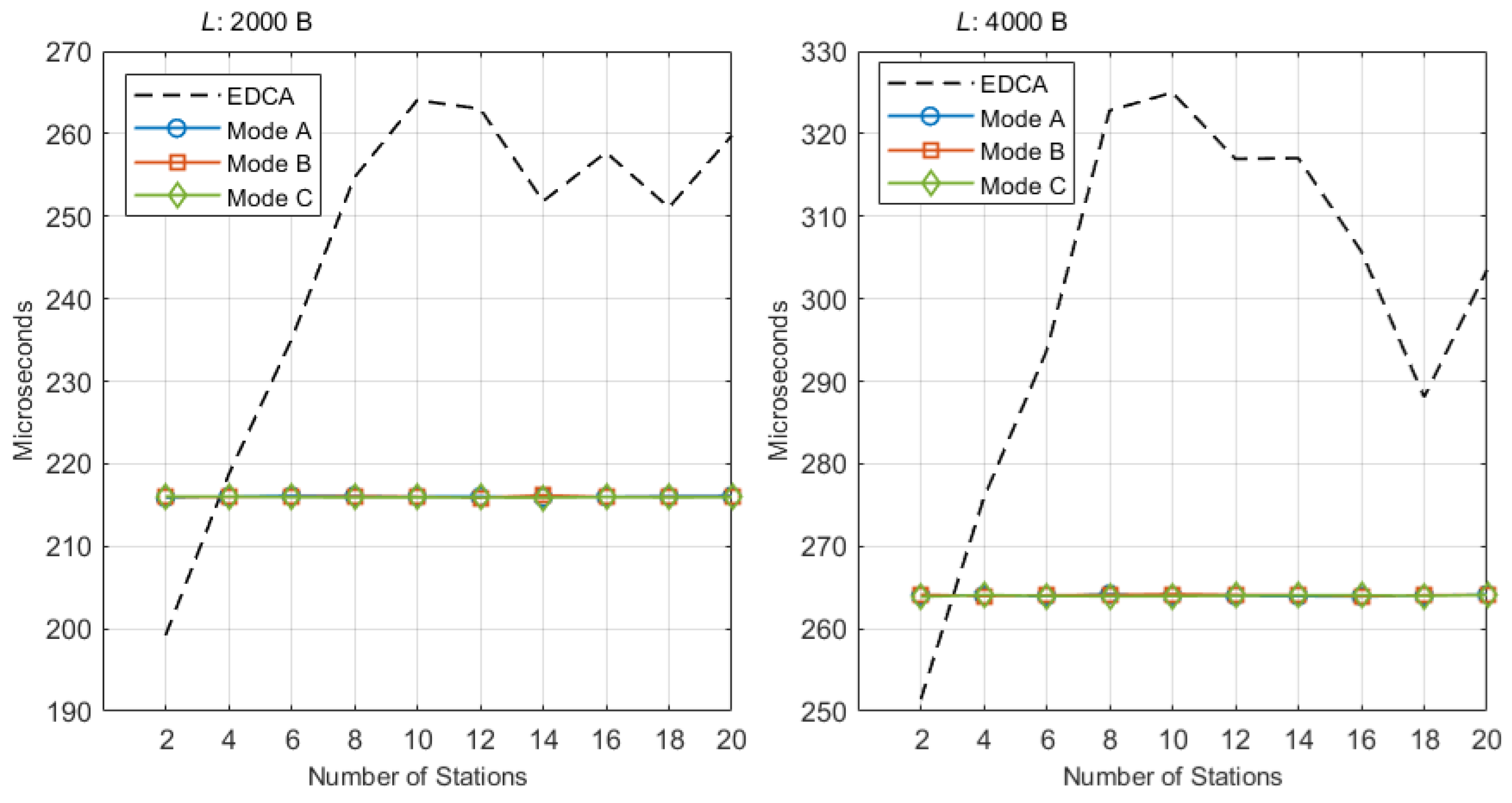
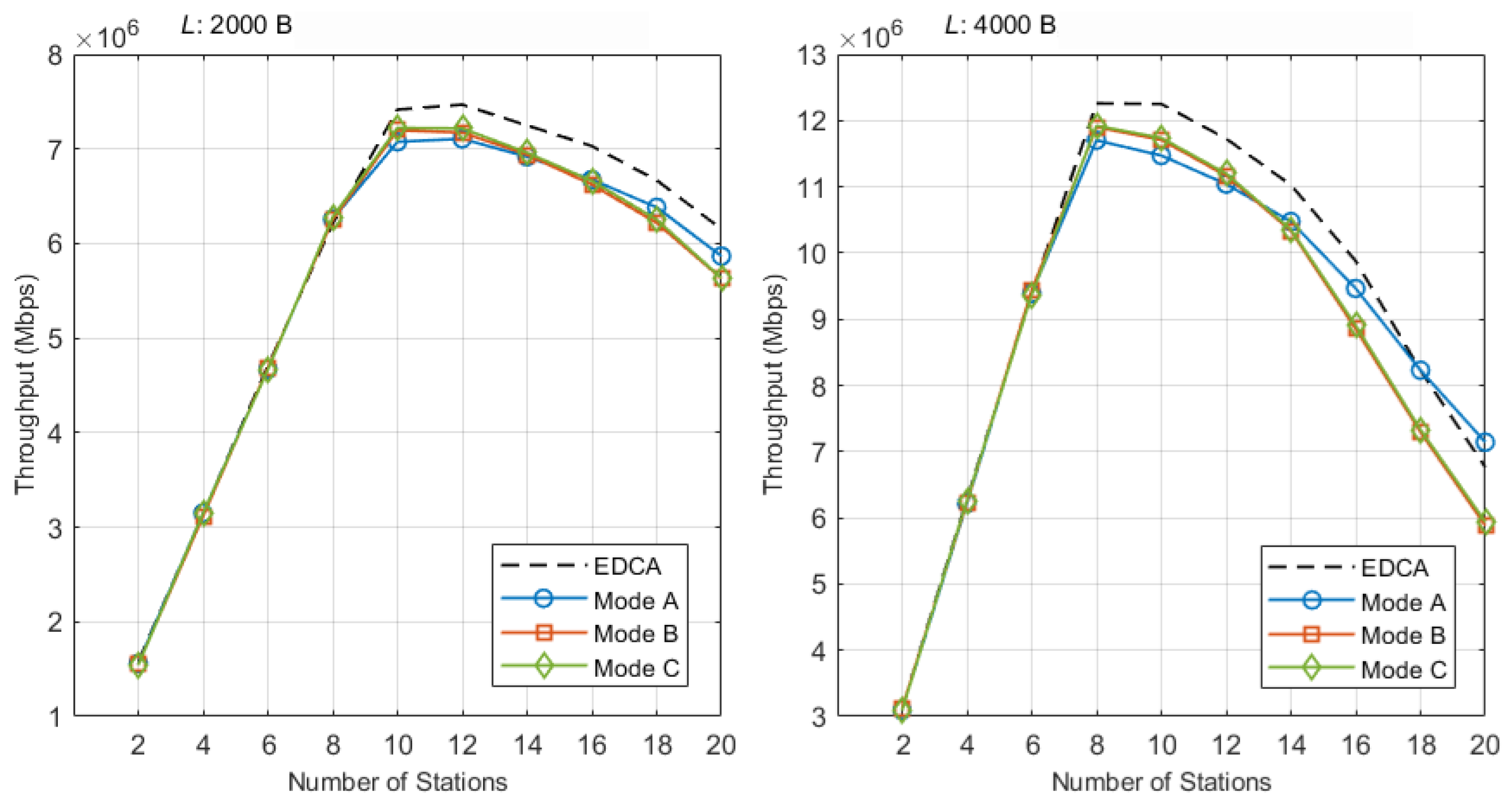
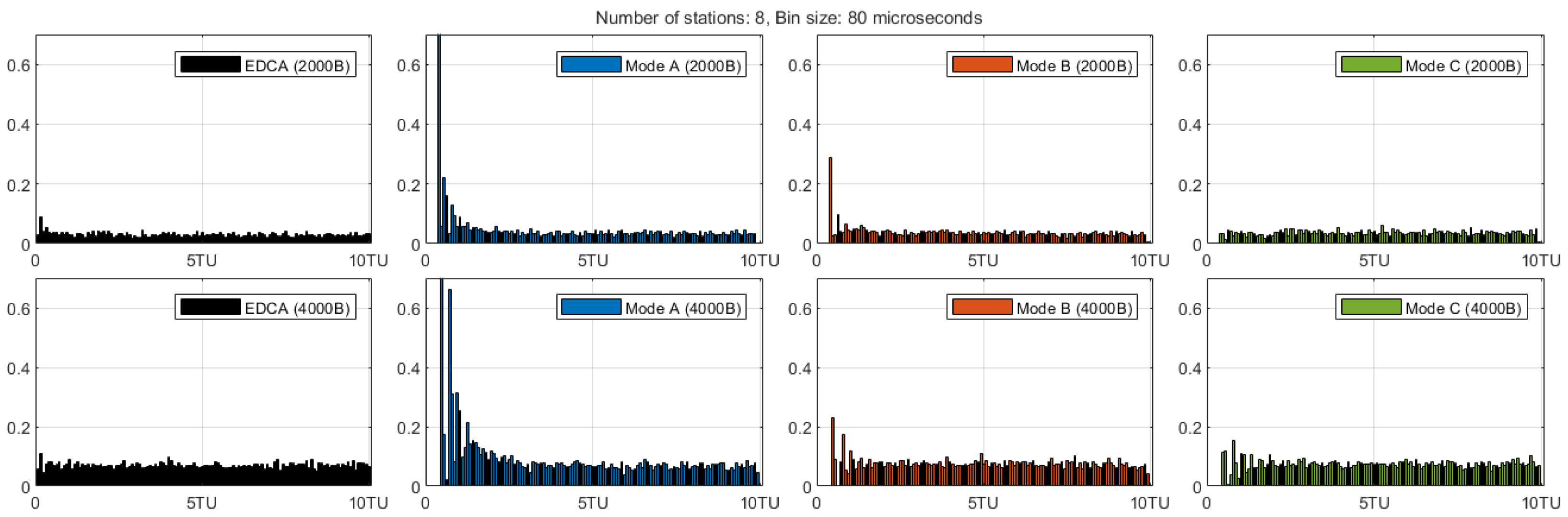
4. Performance Evaluation
5. Discussion
5.1. Overview and Alignment with Objectives
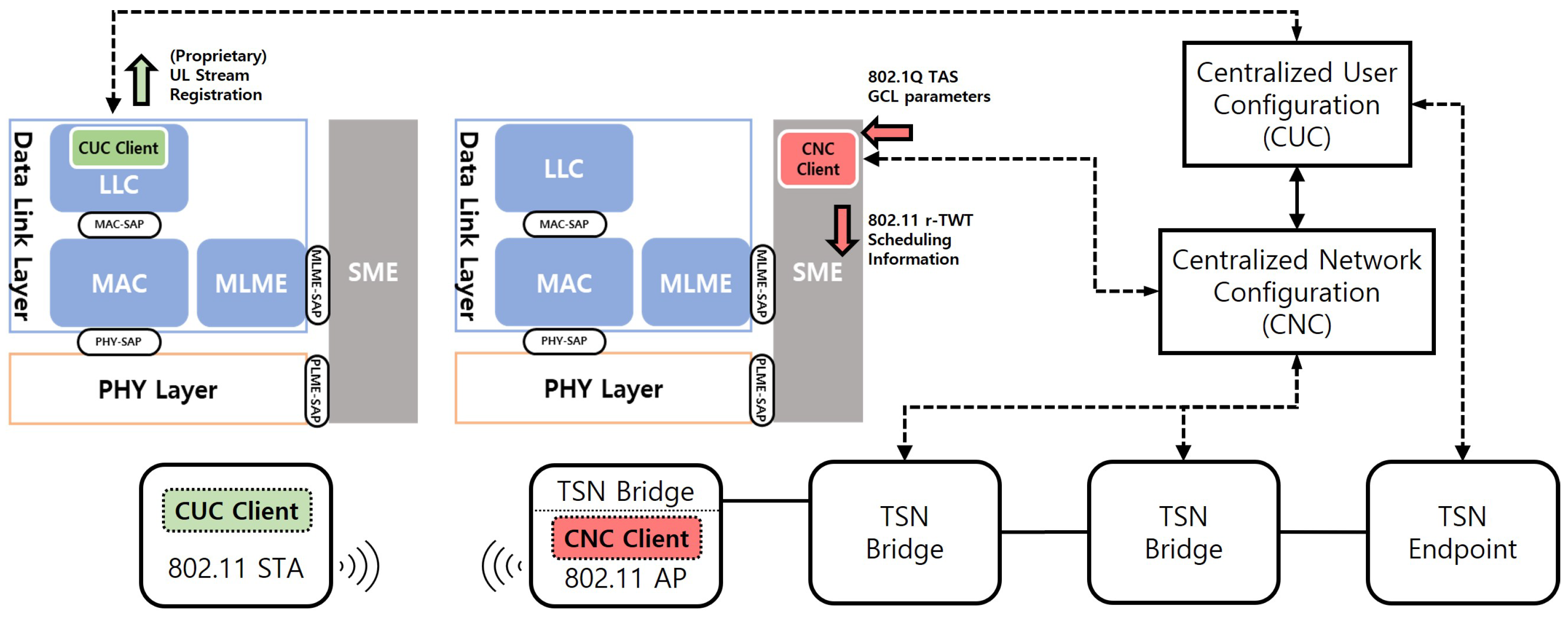
5.2. Interfacing with the TSN Control Plane
- CUC Client @ STA: An application generating ST traffic interfaces with a CUC (Centralized User Configuration) Client located at the Logical Link Control (LLC) layer of the station (STA). When a new ST stream is created, the CUC Client gathers its requirements—such as period, latency, and data size—and sends a Stream Registration Request to the central CUC server.
- CNC Client @ AP: Once the CUC registers the stream, it instructs the CNC (Centralized Network Configuration), which manages the overall network schedule, to configure the necessary paths and schedules. To schedule the WLAN segment, the CNC communicates with a CNC Client residing within the Station Management Entity (SME) of the access point (AP).
- Parameter Translation: The core function of the CNC Client is to translate the TAS parameters received from the CNC into equivalent TWT parameters suitable for the wireless environment. This translation process acts as the essential bridge between the two heterogeneous network technologies. In IEEE 802.1Qbv, each gate control entry (GCE) specifies a time interval and gate state; the mapping rules are summarized in Table 6.
- Schedule Configuration: The TWT parameters, now translated by the CNC Client, are passed to the AP’s MLME (MAC Sublayer Management Entity). The MLME then uses these parameters to configure the final r-TWT schedule and disseminates it through Beacon frames or other management frames.
5.3. Implementation Considerations
- AP side: The SME–MLME pipeline exposes r-TWT/QTP schedule attributes (for example, via MLME-SAP), allowing firmware to advertise SP/GB timing in Beacons/Action frames and to issue trigger frames during the SP for the intended AC/TID.
- STA side (RE): While RE for NST is not yet standardized, SP/GB timing is visible to the host via SAP attributes, so a proprietary driver-level policy can pace NST dequeues around the CP restart. When the MLME indicates an imminent SP end (or CP start), the driver perturbs dequeue times (through LLC–MAC SAP interaction) to spread early-CP transmissions over a short window, implementing RE without modifying chipset firmware.
5.4. Limitations and Threats to Validity
5.5. Cross-Technology Comparison and Implications for Our Design
6. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Finn, N.; Thubert, P.; Varga, B.; Farkas, J. Deterministic Networking (DetNet) Architecture; RFC RFC 8655; Internet Engineering Task Force (IETF): Wilmington, DE, USA, 2019. [Google Scholar] [CrossRef]
- IEEE 802.1 Time-Sensitive Networking (TSN) Task Group. Charter: Deterministic Connectivity with Bounded Latency, Low Jitter, Low Loss. 2025. Available online: https://1.ieee802.org/tsn/ (accessed on 8 September 2025).
- Zhang, T.; Wang, G.; Xue, C.; Wang, J.; Nixon, M.; Han, S. Time-Sensitive Networking (TSN) for Industrial Automation. ACM Comput. Surv. 2024, 57, 1–38. [Google Scholar] [CrossRef]
- John, J.; Noor-A-Rahim, M.; Vijayan, A.; Poor, H.V.; Pesch, D. Industry 4.0 and Beyond: The Role of 5G, WiFi 7, and Time-Sensitive Networking (TSN) in Enabling Smart Manufacturing. Future Internet 2024, 16, 345. [Google Scholar] [CrossRef]
- Fedullo, T.; Morato, A.; Tramarin, F.; Rovati, L.; Vitturi, S. A Comprehensive Review on Time Sensitive Networks with a Special Focus on Their Applicability to Distributed Measurement Systems. Sensors 2022, 22, 1638. [Google Scholar] [CrossRef] [PubMed]
- Xu, Y.; Huang, J. A Survey on Time-Sensitive Networking Standards and Practices. Processes 2023, 11, 2211. [Google Scholar] [CrossRef]
- Cavalcanti, D.; Cordeiro, C.; Smith, M.; Regev, A. WiFi TSN: Enabling Deterministic Wireless Connectivity over 802.11. IEEE Commun. Stand. Mag. 2022, 6, 22–29. [Google Scholar] [CrossRef]
- Adame, T.; Carrascosa-Zamacois, M.; Bellalta, B. Time-Sensitive Networking in IEEE 802.11be: On the Way to Low-Latency WiFi 7. Sensors 2021, 21, 4954. [Google Scholar] [CrossRef] [PubMed]
- Atiq, M.S.A.; Savazzi, S.; Galati-Giordano, L.; Dixit, S. When IEEE 802.11 and 5G Meet Time-Sensitive Networking. IEEE Open J. Ind. Electron. Soc. 2022, 3, 65–76. [Google Scholar] [CrossRef]
- Venkateswaran, S.K.; Tai, C.L.; Ahmed, A.; Sivakumar, R. Target Wake Time in IEEE 802.11 WLANs: Survey, Challenges, and Opportunities. Comput. Commun. 2025, 236, 108127. [Google Scholar] [CrossRef]
- Nurchis, M.; Bellalta, B. Target Wake Time: Scheduled Access in IEEE 802.11ax WLANs. IEEE Wirel. Commun. 2019, 26, 142–150. [Google Scholar] [CrossRef]
- Qiu, W.; Chen, G.; Nguyen, K.N.; Sehgal, A.; Nayak, P.; Choi, J. Category-Based 802.11ax Target Wake Time Solution. IEEE Access 2021, 9, 100154–100172. [Google Scholar] [CrossRef]
- Venkateswaran, S.K.; Tai, C.L.; Garnayak, R.; Ben-Yehezkel, Y.; Alpert, Y.; Sivakumar, R. IEEE 802.11ax Target Wake Time: Design and Performance Analysis in ns-3. In Proceedings of the 2024 Workshop on ns-3 (WNS3 ’24), ACM, Barcelona, Spain, 5–6 June 2024; pp. 10–18. [Google Scholar] [CrossRef]
- IEEE 802.11 Working Group. Liaison Communication to the IEEE 802.1 Working Group; Technical Report, IEEE 802.11; IEEE: Piscataway, NJ, USA, 2022; Doc. No. IEEE 802.11-22/1987r0. [Google Scholar]
- Belogaev, A.; Shen, X.; Pan, C.; Jiang, X.; Blondia, C.; Famaey, J. Dedicated Restricted Target Wake Time for Real-Time Applications in Wi-Fi 7. In Proceedings of the 2024 IEEE Wireless Communications and Networking Conference (WCNC), Dubai, United Arab Emirates, 21–24 April 2024. [Google Scholar] [CrossRef]
- Haxhibeqiri, J.; Jiao, X.; Aslam, M.; Moerman, I.; Hoebeke, J. Enabling TSN over IEEE 802.11: Low-overhead Time Synchronization for Wi-Fi Clients. In Proceedings of the 2021 22nd IEEE International Conference on Industrial Technology (ICIT), Valencia, Spain, 10–12 March 2021; pp. 1068–1073. [Google Scholar] [CrossRef]
- IEEE Std 802.1Qbv-2015: Bridges and Bridged Networks—Amendment 25: Enhancements for Scheduled Traffic, 2015. Time-Aware Shaper (TAS), Gate Control List (GCL), Guard Band. Available online: https://standards.ieee.org/ieee/802.1Qbv/6068/ (accessed on 8 September 2025).
- IEEE Std 802.1AS-2020: Timing and Synchronization for Time-Sensitive Applications. 2020. gPTP Time Synchronization for TSN. Available online: https://standards.ieee.org/ieee/802.1AS/7121/ (accessed on 8 September 2025).
- IEEE Std 802.11-2020: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications, 2020. EDCA Operation; Quiet Element/Period Defined. Available online: https://standards.ieee.org/ieee/802.11/7028/ (accessed on 8 September 2025).
- IEEE Draft Std 802.11be/D7.0: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications—Amendment 2: Enhancements for Extremely High Throughput (EHT). 2024. Available online: https://ieeexplore.ieee.org/document/10622056/amendments?signout=success#amendments (accessed on 8 September 2025).
- Barannikov, A.; Levitsky, I.; Khorov, E. False Protection of Real-Time Traffic with Quieting in Heterogeneous Wi-Fi 7 Networks: An Experimental Study. Sensors 2023, 23, 8927. [Google Scholar] [CrossRef] [PubMed]
- Zheng, J.; Wu, Q. Performance modeling and analysis of the IEEE 802.11p EDCA mechanism for VANET. IEEE Trans. Veh. Technol. 2016, 65, 2673–2687. [Google Scholar] [CrossRef]
- Ahn, W.; Kim, R.Y. Distributed Triggered Access for BSM Dissemination in 802.11bd V2V Networks. Appl. Sci. 2019, 10, 311. [Google Scholar] [CrossRef]
- Ahn, W. Novel multi-AP coordinated transmission scheme for 7th generation WLAN 802.11 be. Entropy 2020, 22, 1426. [Google Scholar] [CrossRef] [PubMed]
- Maldonado, R.; Karstensen, A.; Pocovi, G.; Esswie, A.; Rosa, C.; Alanen, O.; Kasslin, M.; Kolding, T. Comparing Wi-Fi 6 and 5G Downlink Performance for Industrial IoT. IEEE Access 2021, 9, 86928–86937. [Google Scholar] [CrossRef]
- Segura, D.; Damsgaard, S.B.; Kabaci, A.; Mogensen, P.; Khatib, E.J.; Barco, R. An Empirical Study of 5G, Wi-Fi 6, and Multi-Connectivity Scalability in an Indoor Industrial Scenario. IEEE Access 2024, 12, 74406–74416. [Google Scholar] [CrossRef]

| Parameter | Value |
|---|---|
| Evaluated modes | EDCA, Mode A (r-TWT), Mode B (r-TWT + QTP), |
| Mode C (r-TWT + QTP + RE) | |
| Number of STAs | 2, 4, 6, 8, 10, 12, 14, 16, 18, 20 |
| Transmission bandwidth | 20 MHz |
| OFDM symbol duration (11be) | 16 μs |
| Preamble duration (Legacy) | 40 μs |
| Preamble duration (11be SU/TB) | 48 μs |
| Modulation and coding scheme (MCS) index (Control/data frame) | 4/2 |
| Trigger frame MAC payload | 38 Bytes |
| Payload size ( = = L) | 2000/4000 Bytes |
| ST transmission sequence | [Legacy]Trigger Frame ++ [11be trigger-based (TB) PPDU]Data ++ [11be SU]ACK |
| NST transmission sequence | [11be single user (SU) PPDU]Data ++ [11be SU]ACK |
| Packet Error Rate () | |
| Slot Time | 9 μs |
| Short inter-frame spacing (SIFS) | 16 μs |
| AIFS number (AIFSN) (for AC_VO, VI, BE, BK) | [2, 2, 3, 7] |
| (for AC_VO, VI, BE, BK) | [7, 15, 31, 31] |
| (for AC_VO, VI, BE, BK) | [15, 31, 1023, 1023] |
| Retry Limit (for AC_VO, VI, BE, BK) | [7, 7, 7, 7] |
| ST service interval () | 10,240 μs (10 time unit (TU)) |
| r-TWT SP duration () | 0.25 TU |
| Guard band duration | Maximum NST transmission sequence duration |
| RE policy | Uniform randomization over the next CP interval |
| Simulation duration | 40,000 ms |
| Payload | PER | EDCA N = 2 | EDCA N = 10 | EDCA N = 20 | Mode A | Mode B | Mode C |
|---|---|---|---|---|---|---|---|
| 2000 B | 2740.0 | 6370.0 | 6330.0 | 6.6416 | 10.53903 | 10.60567 | |
| 2000 B | 3230.0 | 5980.0 | 6180.0 | 400.18468 | 350.14171 | 374.30620 | |
| 4000 B | 3570.0 | 6910.0 | 7210.0 | 12.73763 | 9.85574 | 12.68245 | |
| 4000 B | 3660.0 | 6890.0 | 4970.0 | 532.89593 | 576.43240 | 600.65931 |
| (a) L = 2 kB | |||||||
|---|---|---|---|---|---|---|---|
| N | EDCA (Mbps) | A (Mbps) | ΔA[%] | B (Mbps) | ΔB[%] | C (Mbps) | ΔC[%] |
| 8 | 49.66 | 50.06 | 0.8 | 49.99 | 0.7 | 50.23 | 1.1 |
| 10 | 59.33 | 56.60 | −4.6 | 57.57 | −3.0 | 57.77 | −2.6 |
| 12 | 59.75 | 56.86 | −4.8 | 57.39 | −3.9 | 57.74 | −3.4 |
| (b) L = 4 kB | |||||||
| N | EDCA (Mbps) | A (Mbps) | ΔA[%] | B (Mbps) | ΔB[%] | C (Mbps) | ΔC[%] |
| 8 | 98.08 | 93.61 | −4.5 | 95.20 | −2.9 | 95.37 | −2.8 |
| 10 | 98.00 | 91.78 | −6.4 | 93.67 | −4.4 | 93.90 | −4.2 |
| 12 | 93.81 | 88.33 | −5.8 | 89.34 | −4.8 | 89.60 | −4.5 |
| L (B) | STA Band | Best Mode | Δ[%] (Avg) |
|---|---|---|---|
| 2 K | Low (N = 2–6) | A | −0.6 |
| 2 K | System-peak (N = 8–12) | C | −1.6 |
| 2 K | High (N = 14–20) | A | −4.6 |
| 4 K | Low (N = 2–6) | B | 0.0 |
| 4 K | System-peak (N = 8–12) | C | −3.8 |
| 4 K | High (N = 14–20) | A | −0.9 |
| (a) Payload kB | |||||
|---|---|---|---|---|---|
| Scheme | |||||
| Mode A (r-TWT) | 1.06 | 1.70 | 2.40 | 3.10 | 4.00 |
| Mode B (r-TWT + QTP) | 0.80 | 1.30 | 2.20 | 3.00 | 3.90 |
| Mode C (r-TWT + QTP + RE) | 0.55 | 0.95 | 1.80 | 2.70 | 3.60 |
| (b) Payload kB | |||||
| Scheme | |||||
| Mode A (r-TWT) | 0.97 | 1.50 | 2.10 | 2.80 | 3.70 |
| Mode B (r-TWT + QTP) | 0.90 | 1.50 | 2.40 | 3.20 | 4.10 |
| Mode C (r-TWT + QTP + RE) | 0.78 | 1.25 | 2.20 | 3.10 | 4.00 |
| TAS Parameter (from CNC) | WLAN Parameter (AP MLME) | Description |
|---|---|---|
| BaseTime | Target Wake Time (TWT) | Absolute schedule anchor; start of the first r-TWT SP. |
| CycleTime | Wake Interval | Period; equals the ST service interval. |
| GCE TimeInterval (ST slot) | Wake Duration (r-TWT) | ST slot length → r-TWT SP duration. |
| GCE GateState (ST queue open) | TWT Member & Trigger-enabled | Single STA as r-TWT member; AP triggers intended AC/TID at SP start. |
| Guard Band (length) | Restricted TWT & QTP alignment (boundary protection) | GB is dimensioned by the longest NST transmission time on the link so that no NST TXOP can spill into the SP. QTP starts one such NST transmission time before each SP and remains active until the end of SP. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahn, W. TSN-Interworked Deterministic Transmission over WLAN. Sensors 2025, 25, 5660. https://doi.org/10.3390/s25185660
Ahn W. TSN-Interworked Deterministic Transmission over WLAN. Sensors. 2025; 25(18):5660. https://doi.org/10.3390/s25185660
Chicago/Turabian StyleAhn, Woojin. 2025. "TSN-Interworked Deterministic Transmission over WLAN" Sensors 25, no. 18: 5660. https://doi.org/10.3390/s25185660
APA StyleAhn, W. (2025). TSN-Interworked Deterministic Transmission over WLAN. Sensors, 25(18), 5660. https://doi.org/10.3390/s25185660





