Lightweight Anonymous Authentication for IoT: A Taxonomy and Survey of Security Frameworks
Abstract
1. Introduction
1.1. Our Contributions
- We propose a novel taxonomy by deconstructing existing schemes into nine fundamental sub-frameworks. We analyze six sub-frameworks designed for user anonymity and three for forward secrecy, elucidating their core mechanisms and design principles.
- We synthesize these components into two general frameworks that concurrently provide both user anonymity and forward secrecy. These overarching models offer robust, reusable blueprints for developing new, secure authentication protocols.
- We conduct a comprehensive comparative analysis of all proposed frameworks. This includes an evaluation of their strengths and limitations, as well as their resilience to key security threats such as desynchronization attacks while also considering performance and multi-factor security capabilities.
1.2. Organization of the Paper
2. Overview of Related Work
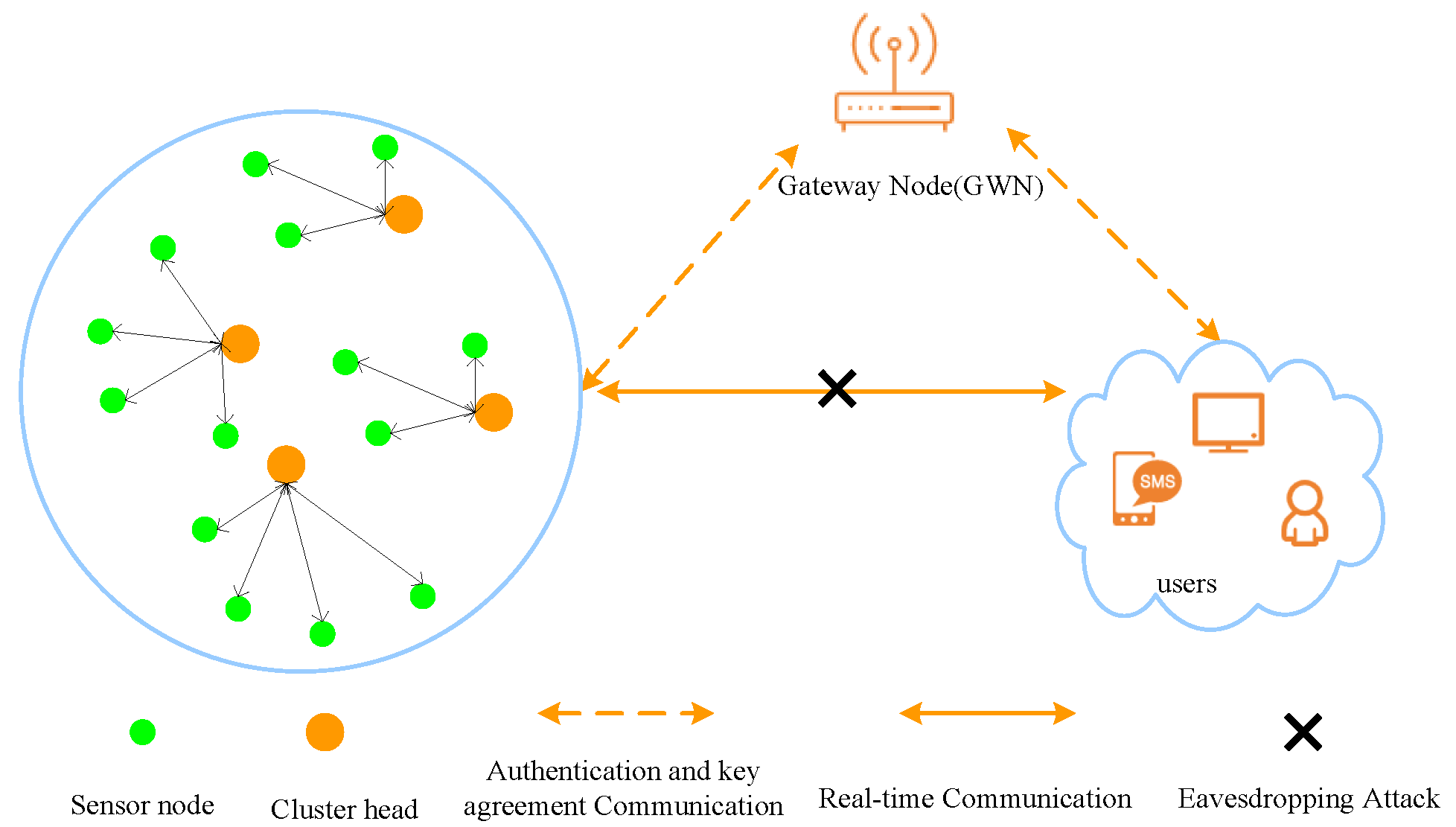
3. System Model and Definitions
3.1. System Model
3.2. Adversary Model
- A can intercept, modify, and replay messages transmitted between users, sensor nodes, and the GWN.
- A can compromise a user’s smart device to extract confidential parameters from their smart card, such as the password validation value. This enables A to perform an offline password guessing attack.
- A can compromise a sensor node and extract its stored confidential parameters.
- A can obtain previously established session keys.
- A can masquerade as a legitimate user.
- A can impersonate a legitimate sensor node.
3.3. Adversary Model
- A can fully control the two communication channels amongthe user, the sensor and the GWN, which means that A isable to intercept, modify, or block messages transmitted in the public channel.
- A is capable of compromising another legitimate external user in the system.
- A is capable of compromising another legitimate sensornode in the system.
3.4. Security Requirements
- Mutual Authentication: A protocol provides mutual authentication if it ensures that a probabilistic polynomial-time (PPT) adversary cannot successfully impersonate a legitimate user, sensor node, or the GWN.
- -
- Untraceability ensures that a PPT adversary cannot determine a user’s real identity from intercepted messages.
- -
- Unlinkability ensures that a PPT adversary cannot link multiple sessions or messages to the same user. A secure protocol must protect against both, as even protocols with dynamic pseudonyms can be vulnerable if other static identifiers are transmitted.
- Forward Secrecy: This property ensures that the compromise of long-term secrets (e.g., a user’s password or a sensor’s private key) does not compromise the confidentiality of past session keys. Even if an adversary A obtains these long-term secrets, they cannot use them to decrypt previously captured communication.
- Multi-factor Security: A scheme is considered multi-factor secure if it remains secure even when an adversary compromises some, but not all, of its authentication factors (e.g., out of n factors) [6,63,64]. For a typical three-factor scheme (password, smart card, and biometrics), this means an adversary still cannot impersonate a user after compromising any two of the three factors [8,65].
- Efficient Identity Lookup: Since users’ real identities are concealed to ensure anonymity, the GWN must have an efficient mechanism to look up a user’s or sensor’s credentials from the temporary identifiers they present during authentication. This lookup operation must not become a performance bottleneck for the system.
- Resistance to Desynchronization Attacks: A desynchronization attack occurs when an adversary blocks messages, causing a mismatch in state variables (e.g., counters or one-time nonces) between communicating parties. A resistant protocol must be self-synchronizing, ensuring that such a temporary mismatch does not prevent the parties from successfully authenticating in a subsequent session.
3.5. System Building
- Symmetric Cipher-Based Encryption: This is the most common approach, using standard block ciphers like AES, 3DES, or DES to implement . As these algorithms are well documented in the literature, their technical specifications are not detailed here.
- Hash Function-Based Encryption: This method achieves encryption by XORing the message M with a key stream derived from a cryptographic hash function (e.g., SHA-256). For instance, in the scheme by Yang et al. [25], the sensor’s identity is encrypted asHere, the key stream is generated by hashing the shared secret with a fresh nonce and a constant r. This approach is well suited for IoT environments where plaintexts are often short (e.g., identities or nonces). Furthermore, since a hash operation is significantly faster than a symmetric cipher operation (e.g., at least 10 times faster in software [66]), protocols using this hash-based approach are generally more lightweight.
- The message has not been tampered with, as any modification would result in a mismatched tag;
- The message originated from a party possessing the secret key, since an adversary without the key cannot forge a valid tag.
4. The Taxonomy of Nine Sub-Frameworks
4.1. SF1-UA
4.1.1. Review SF1-UA
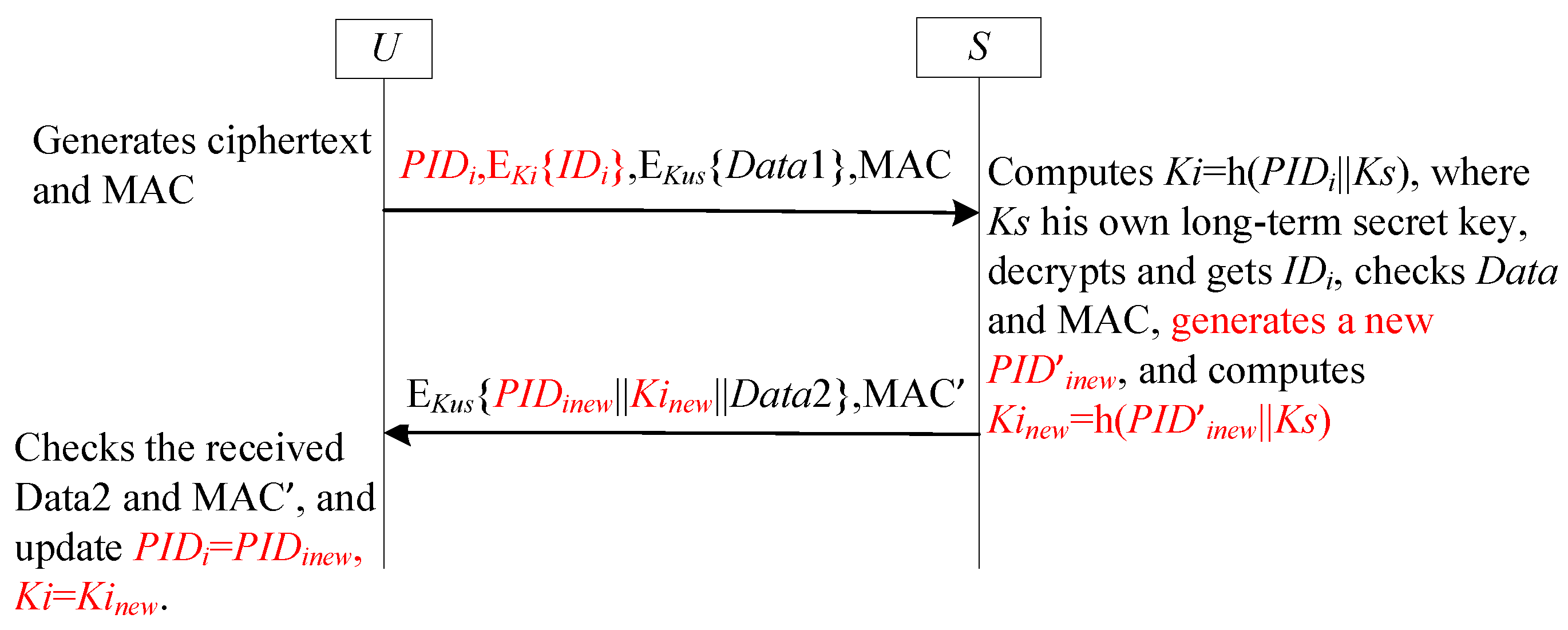
- The secret key used for protecting the real identity is a shared key of the sender and the receiver (see [19,21,22,23,24]). Takeing Wazid et al.’s scheme [21] as an example, the shared secret key is known only to the user and GWN. Using this key stored in its database, the GWN can retrieve the user’s real identity.
- The secret key used for protecting the real identity is shared by all numbers in the system (see [14,15,16,17,18]. For example, in Tai et al.’s scheme [15], each user’s smart card stores the shared secret key with the GWN. When the GWN receives the ciphertext of identity, it can decrypt and get the real Identity.
4.1.2. Analysis SF1-UA
4.2. SF2-UA for User Anonymity
4.2.1. Review SF2-UA
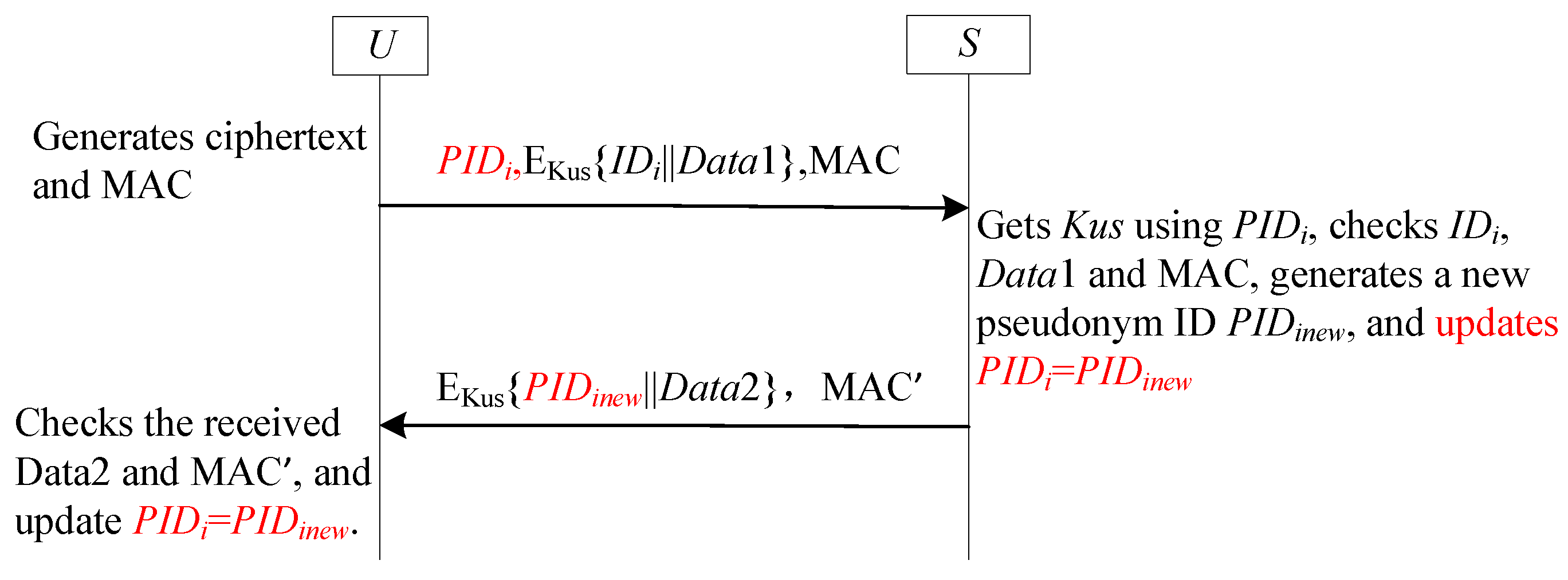
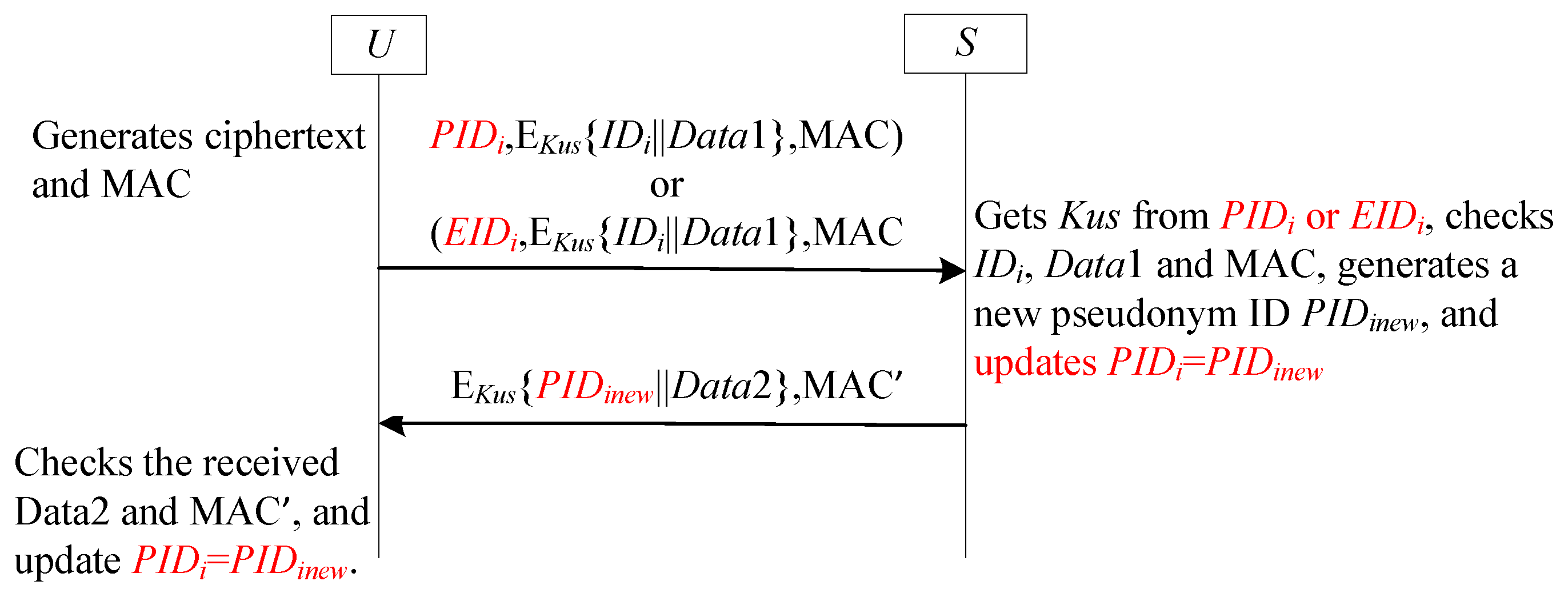
- Static pseudonym identifiers stored in the receiver’s information table provide a mapping to the sender’s real identity (see [25,26,27,28,29]). For instance, in Yang et al.’s scheme [25], a shared static pseudonym serves as the reference identifier between and the GWN. The gateway uses this pseudonym to retrieve the corresponding user’s real identity and secret key.
- Retrieving the real identity requires decrypting transmitted data using both the static pseudonym identifier and the receiver’s long-term secret key (see [30,31,32,34,35,36,37]). Ostadsharif et al.’s scheme [30] exemplifies this approach: upon receiving a user message, the gateway decrypts the embedded identity using its stored pseudonym identifier.
4.2.2. Analysis SF2-UA
4.3. SF3-UA for User Anonymity
4.3.1. Review SF3-UA
4.3.2. Analysis SF3-UA
4.4. SF4-UA for User Anonymity
4.4.1. Review SF4-UA
4.4.2. Analysis SF4-UA
4.5. SF5-UA for User Anonymity
4.5.1. Review SF5-UA
4.5.2. Analysis SF5-UA
4.6. SF6-UA for User Anonymity
4.6.1. Review SF6-UA
4.6.2. Analysis SF6-UA
4.7. SF7-FS for Forward Secrecy
4.7.1. Review SF7-FS
4.7.2. Analysis SF7-FS
4.8. SF8-FS for Forward Secrecy
4.8.1. Review SF8-FS
4.8.2. Analysis SF8-FS
4.9. SF9-FS for Forward Secrecy
4.9.1. Review SF9-FS
4.9.2. Analysis SF9-FS
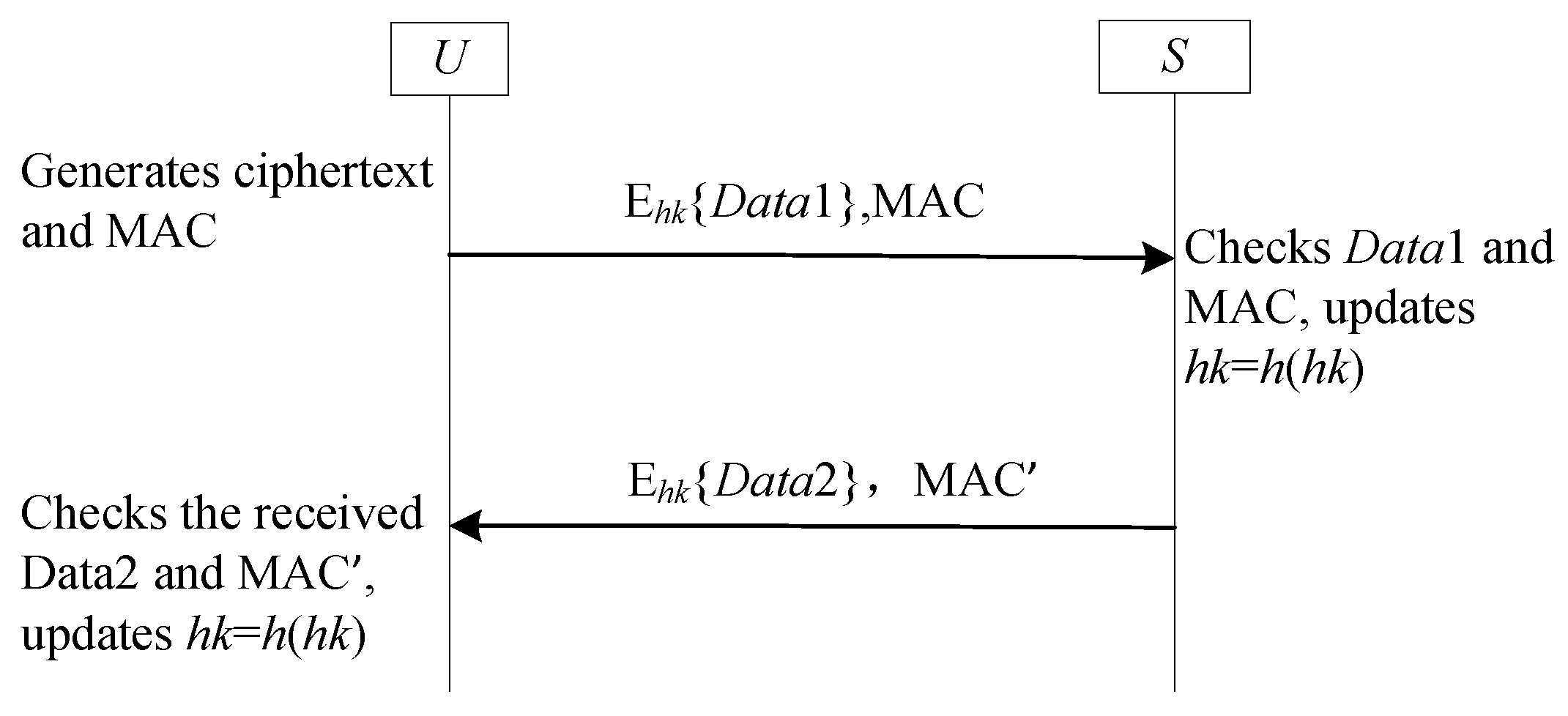
- Combination 1: and . In this scenario, the hash chain values of both sides are not updated. So, this combination is omitted.
- Combination 2: and . In this case, the hash chain values of and GWN are updated. So, this combination is omitted.
- Combination 3: and . This scenario is impossible because the hash chain values of A update first. If , the value of must be 1. Therefore, this combination is omitted.
- Combination 4: and . In this scenario, U updates its hash chain value while S does not. Thus, the hash chain values of U and S do match each other. This scenario does not cause SF9-FS to be completely unusable because we use and to record whether the hash chain value has been updated. When S finds the asynchronous by checking the value of , it can update the hash chain value. Accordingly, this scenario may cause asynchronous between U and S, but it does not have any impact on the future session.
5. Two General Frameworks
5.1. GF1
5.1.1. Review GF1
5.1.2. Analysis GF1
5.2. GF2
5.2.1. Review GF2
5.2.2. Analysis GF2
6. A Comparative Assessment of Existing Frameworks
6.1. Security Analysis of Existing Frameworks
6.2. Security and Performance Comparisons
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Liu, X.; Zhao, S.; Liu, A.; Xiong, N.; Vasilakos, A.V. Knowledge-aware Proactive Nodes Selection approach for energy management in Internet of Things. Future Gener. Comp. Syst. 2019, 92, 1142–1156. [Google Scholar] [CrossRef]
- Zheng, H.; Guo, W.; Xiong, N. A Kernel-Based Compressive Sensing Approach for Mobile Data Gathering in Wireless Sensor Network Systems. IEEE Trans. Syst. Man Cybern. Syst. 2018, 48, 2315–2327. [Google Scholar] [CrossRef]
- Li, F.; Han, Y.; Jin, C. Cost-effective and anonymous access control for wireless body area networks. IEEE Syst. J. 2018, 12, 747–758. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Comput. Netw. 2014, 73, 41–57. [Google Scholar] [CrossRef]
- Yao, Y.; Yang, L.T.; Xiong, N.N. Anonymity-Based Privacy-Preserving Data Reporting for Participatory Sensing. IEEE Internet Things J. 2015, 2, 381–390. [Google Scholar] [CrossRef]
- Wang, C.; Wang, D.; Tu, Y.; Xu, G.; Wang, H. Understanding Node Capture Attacks in User Authentication Schemes for Wireless Sensor Networks. IEEE Trans. Dependable Secur. Comput. 2020, 19, 507–523. [Google Scholar] [CrossRef]
- Ma, C.G.; Wang, D.; Zhao, S.D. Security flaws in two improved remote user authentication schemes using smart cards. Int. J. Commun. Syst. 2014, 27, 2215–2227. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Wang, D.; Zhang, X.; Zhang, Z.; Wang, P. Understanding security failures of multi-factor authentication schemes for multi-server environments. Comput. Secur. 2020, 88, 101619. [Google Scholar] [CrossRef]
- Perrig, A.; Stankovic, J.; Wagner, D. Security in wireless sensor networks. Commun. ACM 2004, 47, 53–57. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. An Efficient Data Aggregation Scheme for Privacy-Friendly Dynamic Pricing-based Billing and Demand-Response Management in Smart Grids. IEEE Internet Things J. 2018, 5, 3126–3135. [Google Scholar] [CrossRef]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; Volume 1. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Tai, W.; Chang, Y.; Li, W. An IoT notion–based authentication and key agreement scheme ensuring user anonymity for heterogeneous ad hoc wireless sensor networks. J. Inf. Secur. Appl. 2017, 34, 133–141. [Google Scholar] [CrossRef]
- Vaidya, B.; Makrakis, D.; Mouftah, H.T. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2016, 9, 171–183. [Google Scholar] [CrossRef]
- Kumar, P.; Lee, S.; Lee, H. E-SAP: Efficient-Strong Authentication Protocol for Healthcare Applications Using Wireless Medical Sensor Networks. Sensors 2012, 12, 1625–1647. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Biswas, G.P. Design of authentication protocol for wireless sensor network-based smart vehicular system. Veh. Commun. 2017, 9, 64–71. [Google Scholar] [CrossRef]
- Fakroon, M.; Alshahrani, M.; Gebali, F.; Traore, I. Secure remote anonymous user authentication scheme for smart home environment. Internet Things 2020, 9, 100158. [Google Scholar] [CrossRef]
- Fan, K.; Zhu, S.; Zhang, K.; Li, H.; Yang, Y. A Lightweight Authentication Scheme for Cloud-Based RFID Healthcare Systems. IEEE Netw. 2019, 33, 44–49. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of Secure User Authenticated Key Management Protocol for Generic IoT Networks. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Chen, Y.; Ge, Y.; Wang, W.; Yang, F. A Biometric-based User Authentication and Key Agreement Scheme for Heterogeneous Wireless Sensor Networks. Ksii Trans. Internet Inf. Syst. 2018, 12, 1779–1798. [Google Scholar]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. An energy efficient mutual authentication and key agreement scheme preserving anonymity for wireless sensor networks. Sensors 2016, 16, 837. [Google Scholar] [CrossRef] [PubMed]
- Jung, J.; Kim, J.; Choi, Y.; Won, D. An Anonymous User Authentication and Key Agreement Scheme Based on a Symmetric Cryptosystem in Wireless Sensor Networks. Sensors 2016, 16, 1299. [Google Scholar] [CrossRef] [PubMed]
- Yang, Z.; He, J.; Tian, Y.; Zhou, J. Faster Authenticated Key Agreement with Perfect Forward Secrecy for Industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2020, 16, 6584–6596. [Google Scholar] [CrossRef]
- Srinivas, J.; Mukhopadhyay, S.; Mishra, D. Secure and efficient user authentication scheme for multi-gateway wireless sensor networks. Ad Hoc Netw. 2017, 54, 147–169. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G.P. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Chang, C.; Le, H. A Provably Secure, Efficient, and Flexible Authentication Scheme for Ad hoc Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2016, 15, 357–366. [Google Scholar] [CrossRef]
- Kumari, S.; Om, H. Authentication protocol for wireless sensor networks applications like safety monitoring in coal mines. Comput. Netw. 2016, 104, 137–154. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Arshad, H.; Nikooghadam, M.; Abbasinezhad-Mood, D. Three party secure data transmission in IoT networks through design of a lightweight authenticated key agreement scheme. Future Gener. Comput. Syst. 2019, 100, 882–892. [Google Scholar] [CrossRef]
- Dhillon, P.K.; Kalra, S. Secure multi-factor remote user authentication scheme for Internet of Things environments. Int. J. Commun. Syst. 2017, 30. [Google Scholar] [CrossRef]
- Li, J.; Ding, Y.; Xiong, Z.; Liu, S. An Improved Two-Factor Mutual Authentication Scheme with Key Agreement in Wireless Sensor Networks. Ksii Trans. Internet Inf. Syst. 2017, 11, 5556–5573. [Google Scholar][Green Version]
- Kumar, P.; Choudhury, A.J.; Sain, M.; Lee, S.; Lee, H. RUASN: A Robust User Authentication Framework for Wireless Sensor Networks. Sensors 2011, 11, 5020–5046. [Google Scholar] [CrossRef] [PubMed]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Kim, J.; Lee, D.; Jeon, W.; Lee, Y.; Won, D. Security Analysis and Improvements of Two-Factor Mutual Authentication with Key Agreement in Wireless Sensor Networks. Sensors 2014, 14, 6443–6462. [Google Scholar] [CrossRef]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Luo, H.; Wen, G.; Su, J. Lightweight three factor scheme for real-time data access in wireless sensor networks. Wirel. Netw. 2020, 26, 955–970. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure Remote User Authenticated Key Establishment Protocol for Smart Home Environment. IEEE Trans. Dependable Secur. Comput. 2020, 17, 391–406. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C. Lightweight and Privacy-Preserving Authentication Scheme with Resilience of De-Synchronization Attacks for Wireless Body Area Networks. IET Inf. Secur. 2020, 14, 380–390. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Sangaiah, A.K.; Li, X.; Wu, F. An enhanced three factor based authentication protocol using wireless medical sensor networks for healthcare monitoring. J. Ambient. Intell. Humaniz. Comput. 2024, 15, 1165–1186. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A robust and anonymous patient monitoring system using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-Netw. Appl. 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Wang, D.; Wang, N.; Wang, P.; Qing, S. Preserving privacy for free: Efficient and provably secure two-factor authentication scheme with user anonymity. Inf. Sci. 2015, 321, 162–178. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Kumar, N.; Choo, K.R. An untraceable and anonymous password authentication protocol for heterogeneous wireless sensor networks. J. Netw. Comput. Appl. 2017, 104, 133–144. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Sangaiah, A.K.; Xu, L.; Kumari, S.; Wu, L.; Shen, J. A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Gener. Comput. Syst. 2017, 82, 727–737. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Gope, P.; Das, A.K.; Kumar, N.; Cheng, Y. Lightweight and Physically Secure Anonymous Mutual Authentication Protocol for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2019, 15, 4957–4968. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. Lightweight and Energy-Efficient Mutual Authentication and Key Agreement Scheme With User Anonymity for Secure Communication in Global Mobility Networks. IEEE Syst. J. 2016, 10, 1370–1379. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q. Resilience of DoS attacks in designing anonymous user authentication protocol for wireless sensor networks. IEEE Sens. J. 2017, 17, 498–503. [Google Scholar] [CrossRef]
- Chang, I.; Lee, T.; Lin, T.; Liu, C. Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks. Sensors 2015, 15, 29841–29854. [Google Scholar] [CrossRef]
- Xiong, L.; Peng, D.; Peng, T.; Liang, H.; Liu, Z. A Lightweight Anonymous Authentication Protocol with Perfect Forward Secrecy for Wireless Sensor Networks. Sensors 2017, 17, 2681. [Google Scholar] [CrossRef] [PubMed]
- Xiong, L.; Xiong, N.; Wang, C.; Yu, X.; Shuai, M. An Efficient Lightweight Authentication Scheme With Adaptive Resilience of Asynchronization Attacks for Wireless Sensor Networks. IEEE Trans. Syst. Man, Cybern. 2019, 51, 5626–5638. [Google Scholar] [CrossRef]
- Nashwan, S. AAA-WSN: Anonymous access authentication scheme for wireless sensor networks in big data environment. Egypt. Inform. J. 2020, 22, 15–26. [Google Scholar] [CrossRef]
- Shuai, M.; Liu, B.; Yu, N.; Xiong, L. Lightweight and Secure Three-Factor Authentication Scheme for Remote Patient Monitoring Using On-Body Wireless Networks. Secur. Commun. Netw. 2019, 2019, 8145087. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.R. A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Wei, F.; Tian, Y.; Shen, J.; Yang, Y. An untraceable temporal-credential-based two-factor authentication scheme using ECC for wireless sensor networks. J. Netw. Comput. Appl. 2016, 76, 37–48. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring two-factor authentication schemes for real-time data access in industrial wireless sensor networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Kumari, S.; Khan, M.K.; Atiquzzaman, M. User authentication schemes for wireless sensor networks: A review. Ad Hoc Netw. 2015, 27, 159–194. [Google Scholar] [CrossRef]
- Huang, X.; Xiang, Y.; Chonka, A.; Zhou, J.; Deng, R.H. A Generic Framework for Three-Factor Authentication: Preserving Security and Privacy in Distributed Systems. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 1390–1397. [Google Scholar] [CrossRef]
- Yu, J.; Wang, G.; Mu, Y.; Gao, W. An efficient generic framework for three-factor authentication with provably secure instantiation. IEEE Trans. Inf. Forensics Secur. 2014, 9, 2302–2313. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Wei, F. On the security of a privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst. J. 2018, 12, 2039–2042. [Google Scholar] [CrossRef]
- Lee, C.; Chen, C.; Wu, P.; Chen, T. Three-factor control protocol based on elliptic curve cryptosystem for universal serial bus mass storage devices. IET Comput. Digit. Tech. 2013, 7, 48–56. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Srinivas, J.; Kumar, N.; Chattopadhyay, S.; Choo, K.R. A Provably Secure and Lightweight Anonymous User Authenticated Session Key Exchange Scheme for Internet of Things Deployment. IEEE Internet Things J. 2019, 6, 8739–8752. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. An improved and anonymous two-factor authentication protocol for health-care applications with wireless medical sensor networks. Multimed. Syst. 2017, 23, 195–205. [Google Scholar] [CrossRef]
- Nali, D.; van Oorschot, P.C. CROO: A universal infrastructure and protocol to detect identity fraud. In Proceedings of the Computer Security-ESORICS 2008: 13th European Symposium on Research in Computer Security, Málaga, Spain, 6–8 October 2008; Proceedings 13. Springer: Berlin/Heidelberg, Germany, 2008; pp. 130–145. [Google Scholar]
- Zhong, J.; He, S.; Liu, Z.; Xiong, L. ProVerif_GF. 2025. Available online: https://github.com/huol20/ProVerif_GF (accessed on 14 August 2025).
- Liu, X.; Wang, M.; Jing, H.; Zhang, R.; Guo, Z. A Lightweight Authentication Scheme for VANETs Based on Secgear. IEEE Trans. Veh. Technol. 2025, 74, 10789–10801. [Google Scholar] [CrossRef]
- Xie, D.; Yang, J.; Wu, B.; Bian, W.; Chen, F.; Wang, T. An effectively applicable to resource constrained devices and semi-trusted servers authenticated key agreement scheme. IEEE Trans. Inf. Forensics Secur. 2024, 19, 3451–3464. [Google Scholar] [CrossRef]

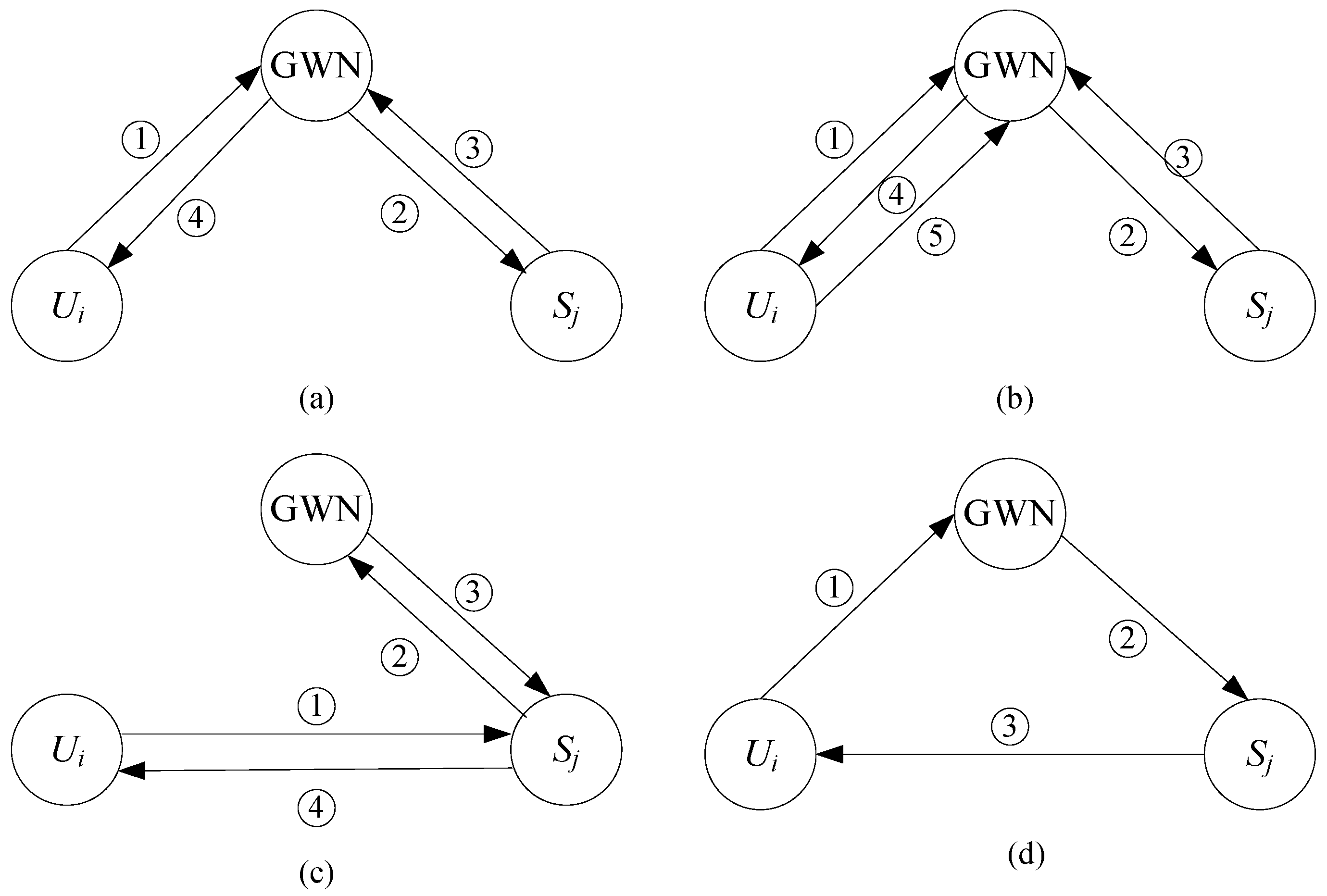
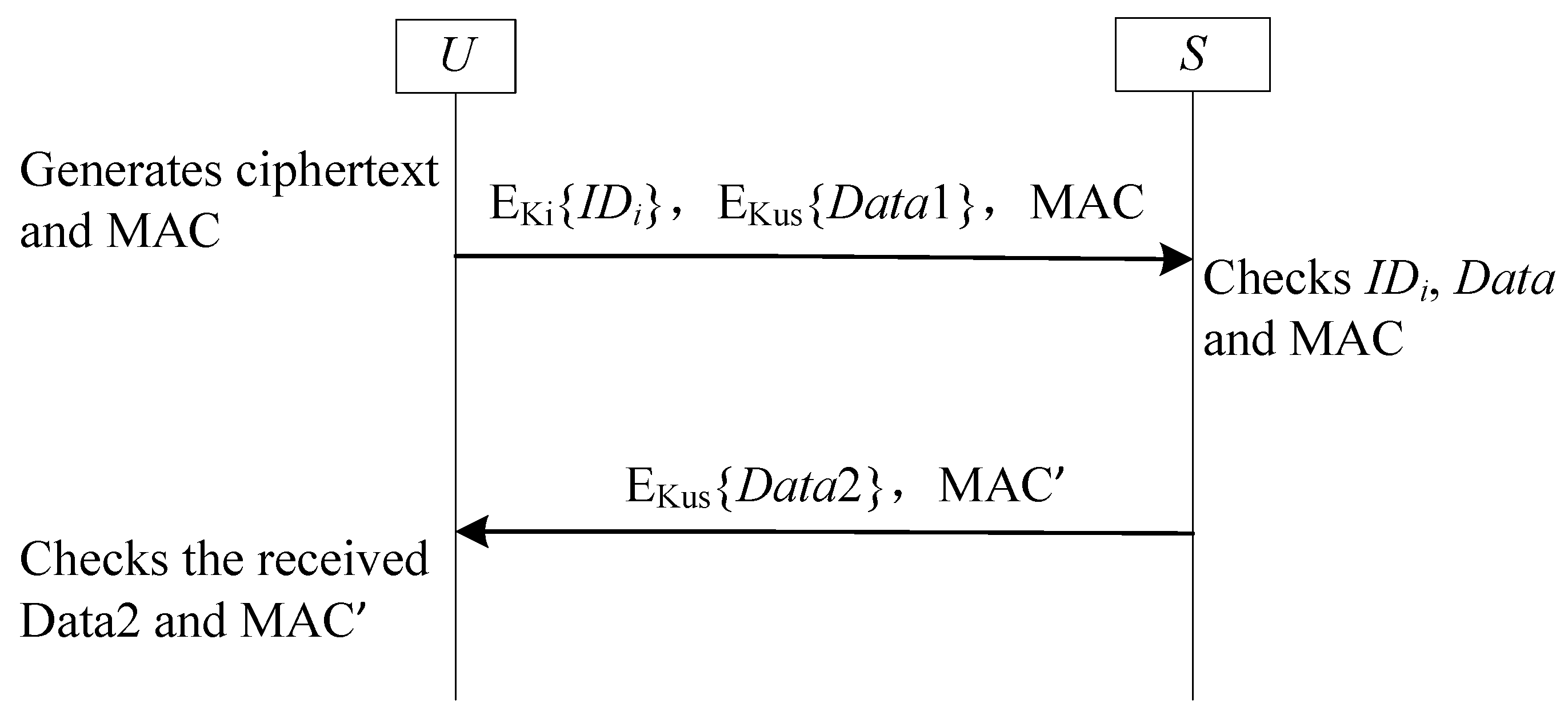
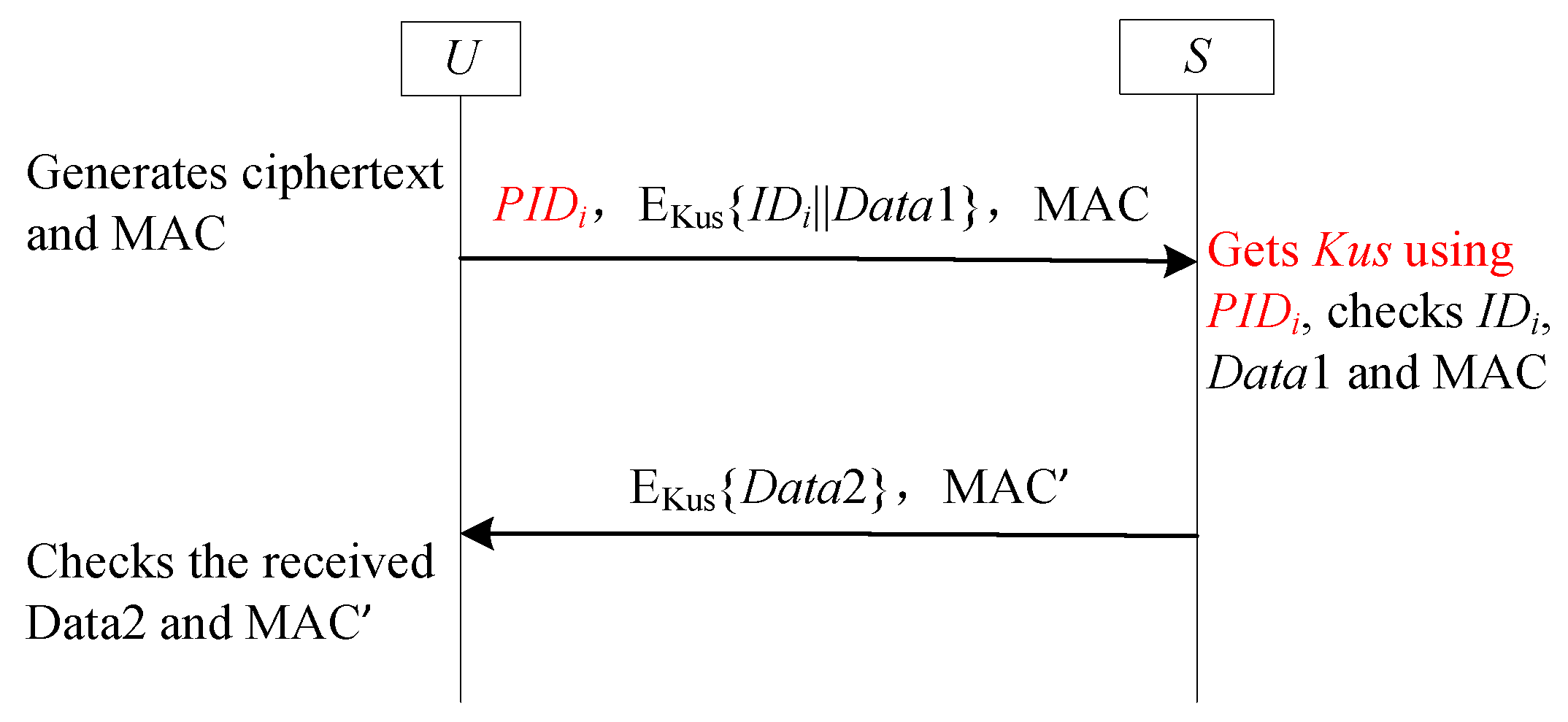


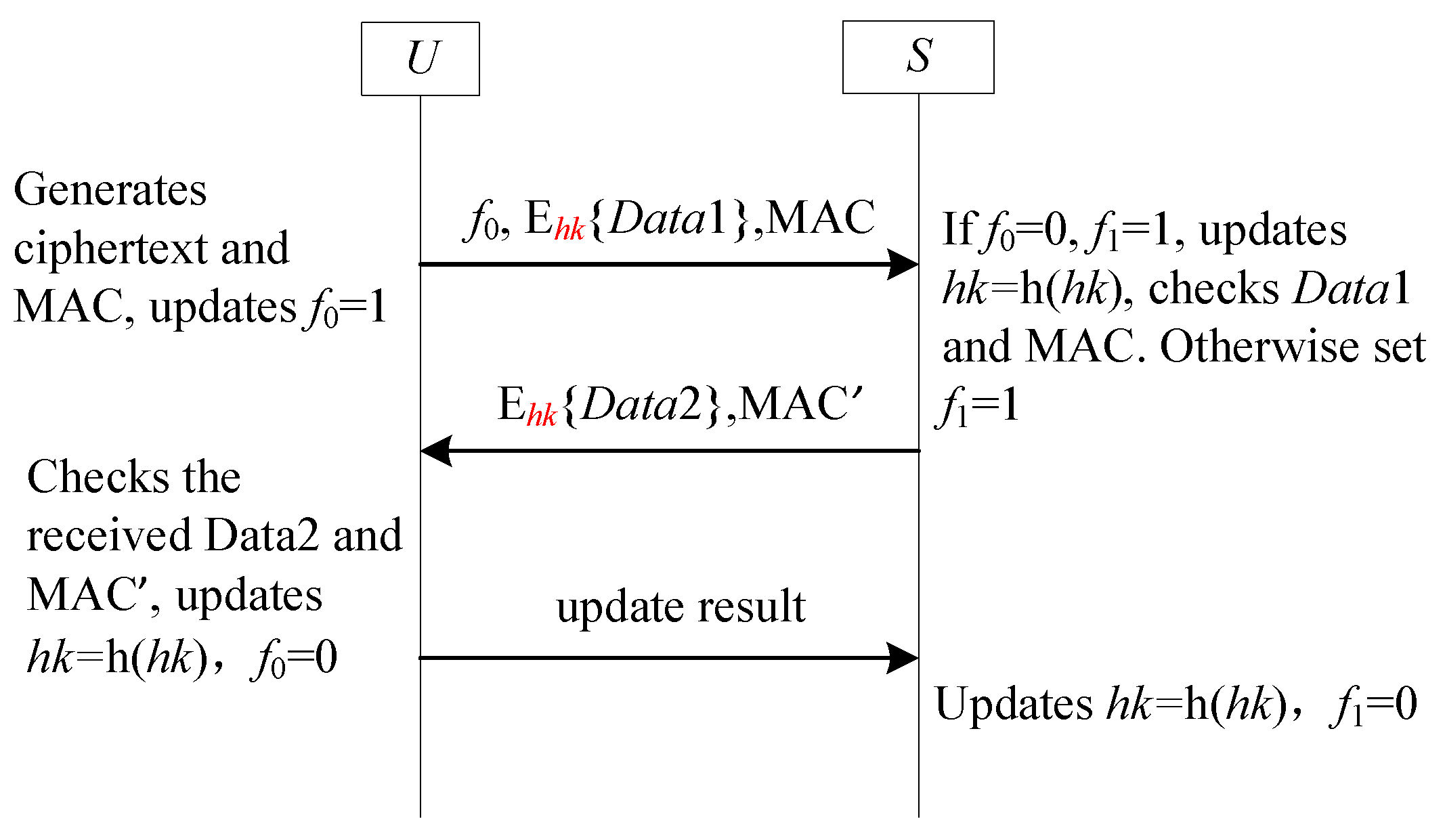
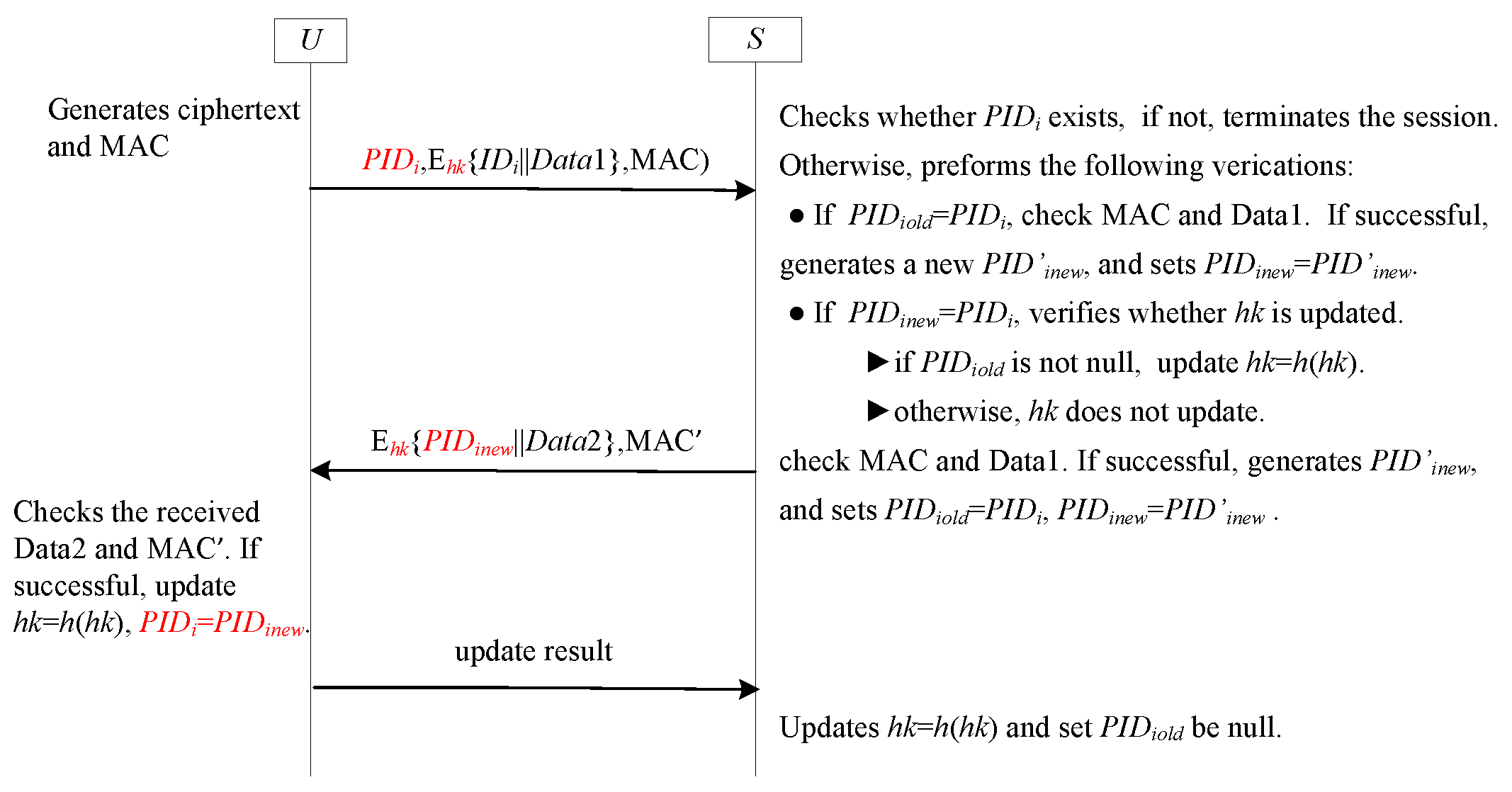
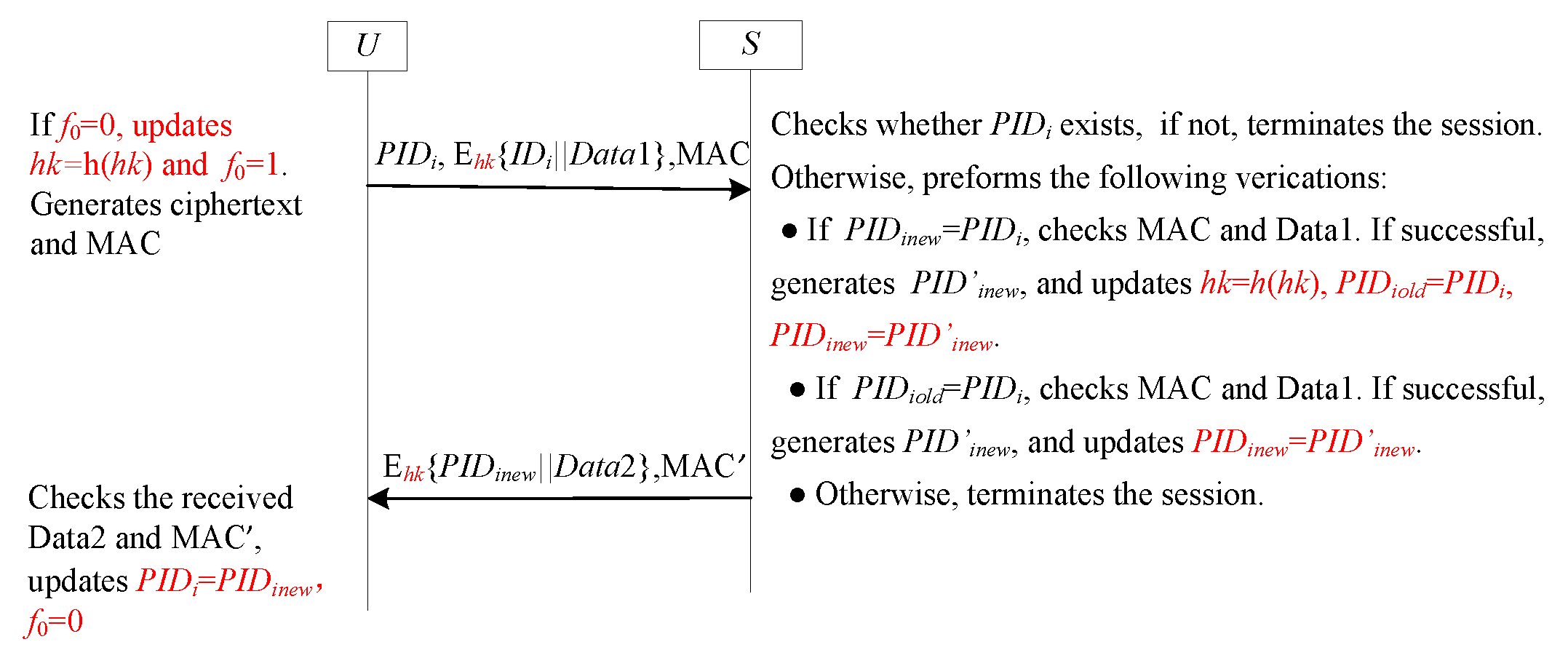
| Notation | Descriptions |
|---|---|
| U | The sender refers to or GWN in Figure 3 |
| S | The receiver refers to GWN or in Figure 3 |
| The real identity of U | |
| The pseudonym identity of U | |
| The secret key to protect , which is the shared key between U and S or group shared key | |
| The secret key shared by U and S | |
| The messages which U intended to send to S | |
| The messages authentication value, which is generated accord to Section 3.5 | |
| The messages which U intended to transmit to S | |
| The returned message authentication value, which is generated according to Section 3.5 | |
| , | Two pseudonym IDs of S |
| h | The general one-way hash function |
| The one-time secret key shared by U and S, which is updated by hash function | |
| , | The serial number of U and S, respectively, which represents the number of times of performing one-time hash chain value |
| , | The tag of U and S, respectively |
| String concatenation operation | |
| ⊕ | XOR operation |
| SF1 | SF2 | SF3 | SF4 | SF5 | SF6 | SF7 | SF8 | SF9 | GF1 | GF2 | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | |||||||||||
| R1 | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| R2 | √ | × | × | √ | √ | √ | √ | − | − | − | √ | √ |
| R3 | − | − | − | − | − | − | − | √ | √ | √ | √ | √ |
| R4 | × | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| R5 | − | − | − | × | √ | √ | √ | × | √ | √ | √ | √ |
| Scheme | Year | Framework | Security Features | Performance | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| R1 | R2 | R3 | R4 | R5 | User | GWN | Sensor | |||
| Liu [71] | 2025 | SF4-UA | √ | √ | √ | √ | × | − | ||
| Xie [72] | 2024 | SF4-UA | √ | √ | − | √ | √ | |||
| Luo [38] | 2020 | SF3-UA + SF7-FS | √ | √ | √ | √ | × | |||
| Wazid [39] | 2020 | SF3-UA | √ | √ | − | √ | × | |||
| Nashwan [57] | 2020 | GF1 | √ | √ | √ | √ | √ | |||
| Shuai [40] | 2020 | SF3-UA + SF8-FS | √ | √ | √ | √ | × | |||
| Yang [25] | 2020 | SF2-UA + SF9-FS | − | √ | √ | √ | √ | |||
| Banerjee [41] | 2020 | SF3-UA | √ | √ | − | √ | × | |||
| Fakroon [19] | 2020 | SF1-UA | √ | √ | − | × | √ | |||
| Banerjee [67] | 2019 | SF4-UA | √ | √ | − | √ | √ | |||
| Xiong [56] | 2019 | GF2 | √ | √ | √ | √ | √ | |||
| Shuai [58] | 2019 | SF1-UA + SF8-FS | √ | √ | √ | × | √ | |||
| Gope [50] | 2019 | SF5-UA | √ | √ | √ | √ | √ | |||
| Ostadsharif [30] | 2019 | SF2-UA | √ | × | − | × | √ | |||
| Wazid [21] | 2018 | SF1-UA | √ | √ | − | × | √ | |||
| Ali [42] | 2018 | SF3-UA | √ | √ | − | √ | × | |||
| Chen [22] | 2018 | SF1-UA | √ | × | − | √ | √ | |||
| Amin [43] | 2018 | SF3-UA | √ | √ | − | √ | × | |||
| Amin [47] | 2017 | SF4-UA | √ | √ | − | √ | √ | |||
| Xiong [55] | 2017 | GF1 | √ | √ | √ | √ | √ | |||
| Mohit [18] | 2017 | SF1-UA | √ | × | − | √ | √ | |||
| Wu [48] | 2017 | SF4-UA | √ | √ | − | √ | √ | |||
| Dhillon [31] | 2017 | SF2-UA | √ | × | − | √ | √ | |||
| Tai [15] | 2017 | SF1-UA | √ | × | − | √ | √ | |||
| Srinivas [26] | 2017 | SF2-UA | √ | × | − | √ | √ | |||
| Li [32] | 2017 | SF2-UA | √ | × | − | √ | √ | |||
| Wu [49] | 2017 | SF4-UA | √ | √ | − | √ | √ | |||
| Wu [68] | 2017 | SF4-UA | √ | √ | − | √ | √ | |||
| Lu [23] | 2016 | SF1-UA | √ | √ | − | × | √ | |||
| Jung [24] | 2016 | SF1-UA | √ | √ | − | × | √ | |||
| Gope [11] | 2016 | SF5-UA + SF7-FS | √ | √ | √ | √ | × | |||
| Das [45] | 2016 | SF3-UA | √ | √ | − | √ | × | |||
| Amin [27] | 2016 | SF2-UA | √ | × | − | √ | √ | |||
| Chang [28] | 2016 | SF2-UA | √ | × | − | √ | √ | |||
| Kumari [29] | 2016 | SF2-UA | √ | × | − | √ | √ | |||
| Vaidya [16] | 2016 | SF1-UA | − | × | − | √ | √ | |||
| Jiang [44] | 2015 | SF3-UA | √ | √ | − | × | × | |||
| Chang [54] | 2015 | SF6-UA | √ | √ | − | √ | × | |||
| He [34] | 2015 | SF2-UA | √ | × | − | √ | √ | |||
| Turkanovic [35] | 2014 | SF2-UA | √ | × | − | √ | √ | |||
| Kim [36] | 2014 | SF2-UA | √ | × | − | √ | √ | |||
| Xue [37] | 2013 | SF2-UA | √ | × | − | √ | √ | |||
| Kumar [17] | 2012 | SF1-UA | − | × | − | √ | √ | |||
| Kumar [33] | 2011 | SF2-UA | √ | × | − | √ | √ | |||
| Das [14] | 2009 | SF1-UA | − | × | − | √ | √ | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhong, J.; He, S.; Liu, Z.; Xiong, L. Lightweight Anonymous Authentication for IoT: A Taxonomy and Survey of Security Frameworks. Sensors 2025, 25, 5594. https://doi.org/10.3390/s25175594
Zhong J, He S, Liu Z, Xiong L. Lightweight Anonymous Authentication for IoT: A Taxonomy and Survey of Security Frameworks. Sensors. 2025; 25(17):5594. https://doi.org/10.3390/s25175594
Chicago/Turabian StyleZhong, Jian, Sheng He, Zhicai Liu, and Ling Xiong. 2025. "Lightweight Anonymous Authentication for IoT: A Taxonomy and Survey of Security Frameworks" Sensors 25, no. 17: 5594. https://doi.org/10.3390/s25175594
APA StyleZhong, J., He, S., Liu, Z., & Xiong, L. (2025). Lightweight Anonymous Authentication for IoT: A Taxonomy and Survey of Security Frameworks. Sensors, 25(17), 5594. https://doi.org/10.3390/s25175594






