EMBRAVE: EMBedded Remote Attestation and Verification framEwork
Abstract
1. Introduction
- Contribution
- Paper Structure
2. Background
2.1. Trusted Computing
- Root of Trust for Measurement (RTM): This is responsible for measuring the platform components and storing the measurements securely. This component, also known as the Core Root of Trust for Measurement (CRTM), is often a piece of firmware stored in a one-time programmable ROM, and its purpose is to measure and store the measurement of the first mutable code that takes control of the platform.
- Root of Trust for Storage (RTS): This is responsible for storing the measurements produced by the RTM.
- Root of Trust for Reporting (RTR): This is responsible for the external reporting of the measurements stored in the RTS.
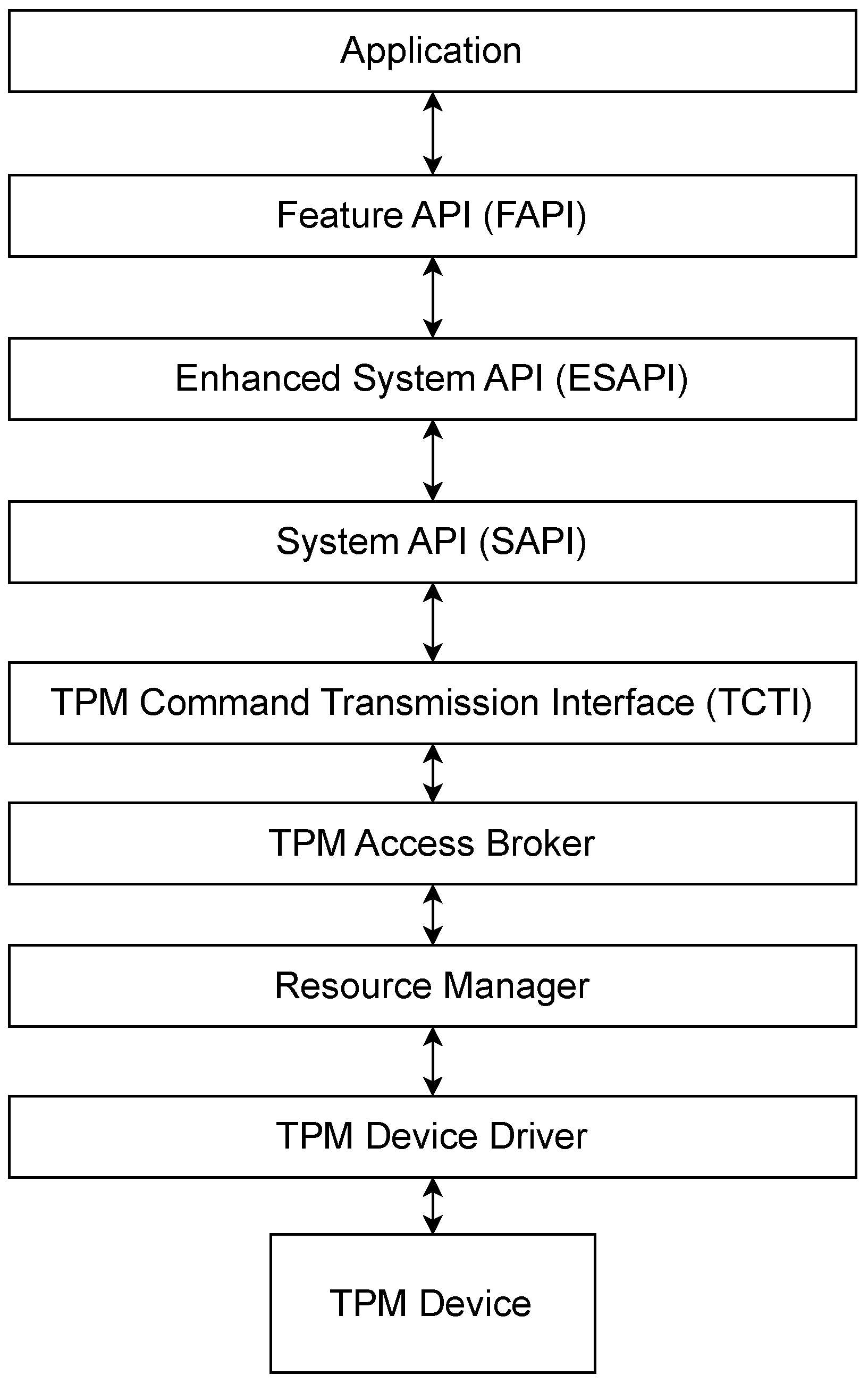
2.2. TPM Software Stack (TSS)
- TPM Command Transmission Interface (TCTI): This handles the communication with lower levels of the stack. This is necessary because there can be different TPM implementations (e.g., hardware TPM, firmware TPM) and each type has different interfaces.
- TPM Access Broker: This manages concurrent accesses to the TPM, ensuring that a process accessing the TPM can complete its task without interference from other processes.
- Resource Manager: This manages the TPM memory similar to a virtual memory manager. This is necessary due to the limited TPM resources.
- TPM Device Driver: This is the operating system-specific driver that manages the direct communication with the TPM chip.
- System API (SAPI) is the lowest-layer API designed to be called from any level in a platform software stack (e.g., firmware, BIOS, OS, application);
- Enhanced System API (ESAPI) is placed on top of the SAPI, offering cryptographically protected communication with the TPM;
- Feature API (FAPI) is the higher-level API that hides all the low-level details and is intended to make it easier to perform operations on the TPM (e.g., key generation).
2.3. Secure and Measured Boot
2.4. Linux Integrity Measurement Architecture
- PCR: The register that stores the measurement. The default is PCR 10.
- template-hash: The hash calculated on the concatenation of the template fields that compose the entry. The PCR field is excluded from the calculation. This is the actual value extended in the PCR 10 to cover the integrity of all the information stored in the template entry.
- template-name: The name of the template used to compose the entry.
- filedata-hash: The hash of the file data that produced the measurement. In this case, the hash is prefixed with the name of the hash algorithm used to calculate it.
- filepath: The absolute path of the measured file.
2.5. Remote Attestation
2.5.1. Single-Device RA
Hardware-Based Attestation
Software-Based Attestation
Hybrid Attestation
2.5.2. Collective RA
3. Related Work
4. EMBRAVE Design
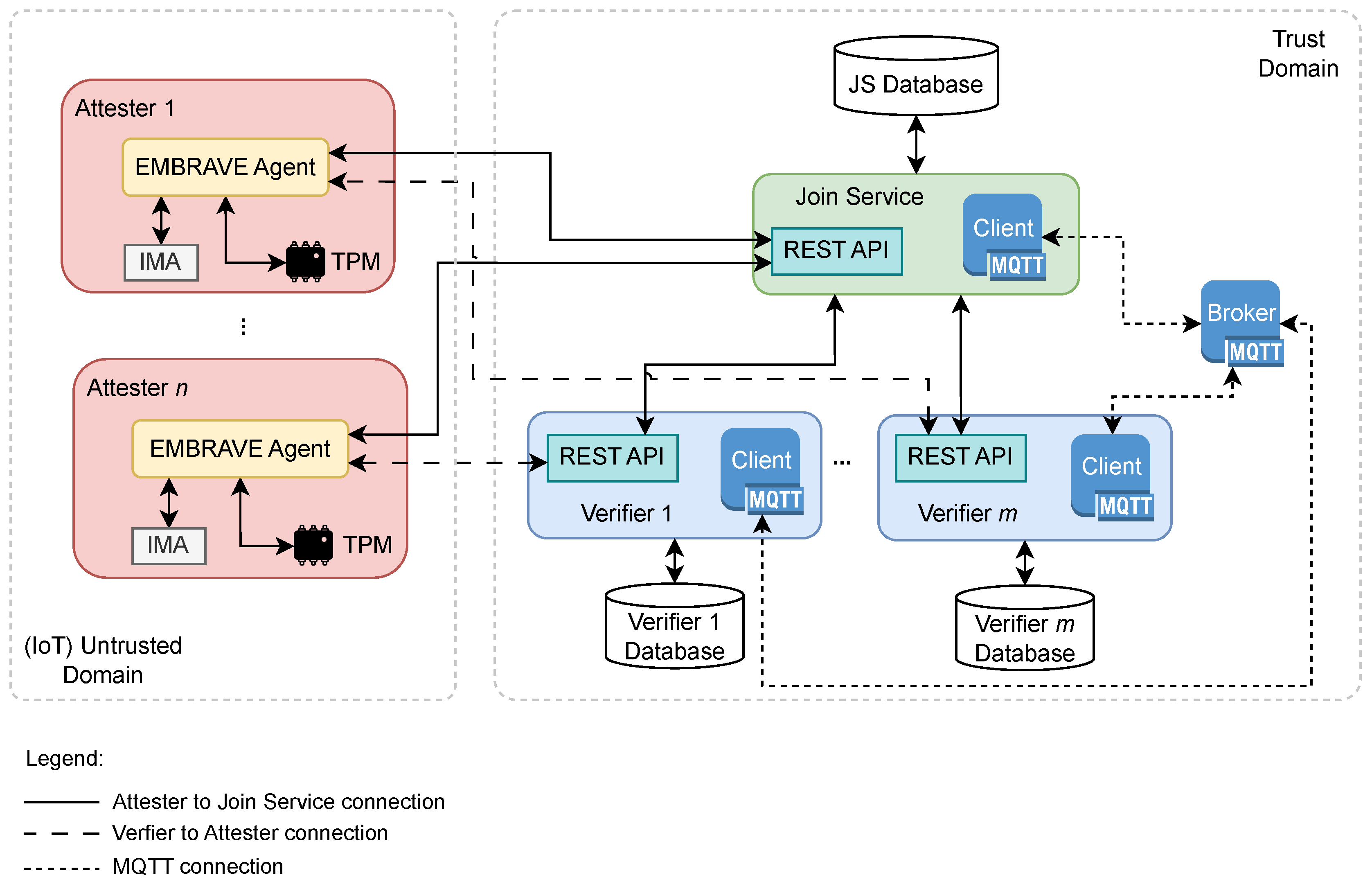
4.1. General Architecture
4.1.1. Join Service
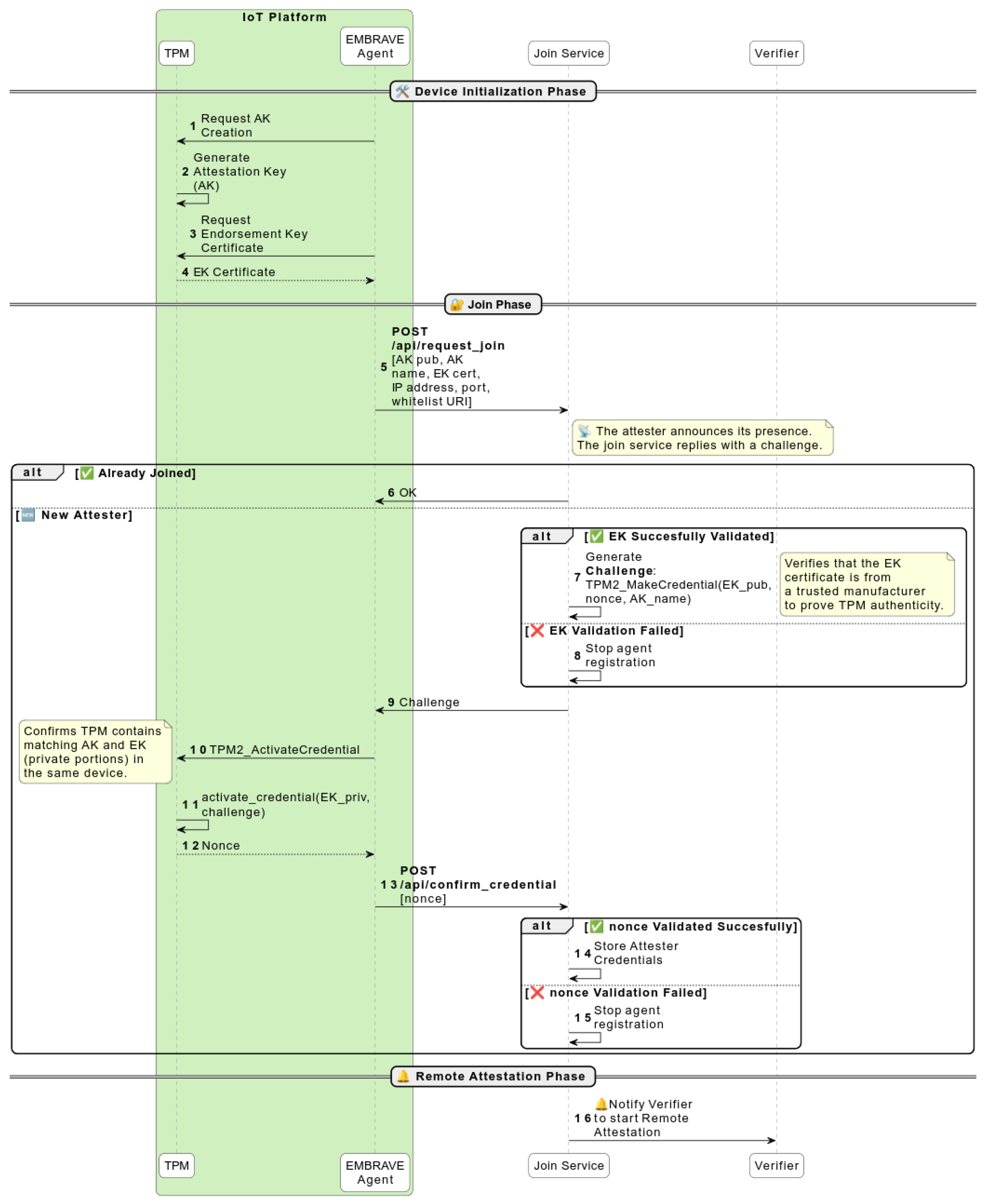
- POST /api/request_join allows a new Attester to join the network. When receiving a request on this API, the Join Service generates a challenge and sends it back to the Attester.
- POST /api/confirm_credential allows a new Attester, after having called/api/request_join, to resolve the challenge received and to send the result back to the Join Service.
- POST /api/request_join_verifier allows a newly deployed Verifier to join the network in the Trust Domain.
4.1.2. EMBRAVE Agent
4.1.3. Verifier
4.1.4. MQTT Broker
- attest/<verifier-id>: The Join Service publishes on this topic to notify a Verifier that a new Attester successfully joined the network and must be attested. A Verifier subscribes to the topic constructed with its identifier. Upon the successful joining of a new Attester, the Join Service publishes on the MQTT topic verfier-id of the Verifier selected for starting the periodic attestation of the Attester.
- status/<verifier-id>: All registered and active Verifiers publish on this topic to share the integrity report with the Join Service after each remote attestation of an Attester. The integrity report contains all the information related to the integrity status of an Attester with its trustworthiness evaluation.
4.1.5. EMBRAVE Scalability
4.2. Join Protocol
- The IP address and port to which the Verifier must send requests during the RA protocol;
- The EK certificate;
- The AK public part;
- The AK name provided as the output of the AK generation command. It is calculated by hashing the AK public part with the hash algorithm associated with it:The derivation of the name is defined in the TPM 2.0 structure specification [51].
- The whitelist URI. The whitelist is the list of trusted files and their measures on the IoT platform. They are measured in a protected environment. It is provided as a URI representing a local or remote location. For example, it may be the name of the database stored in the Verifier (pre-shared) or a secure URL where the Verifier can retrieve the list (e.g., certified by the manufacturer).
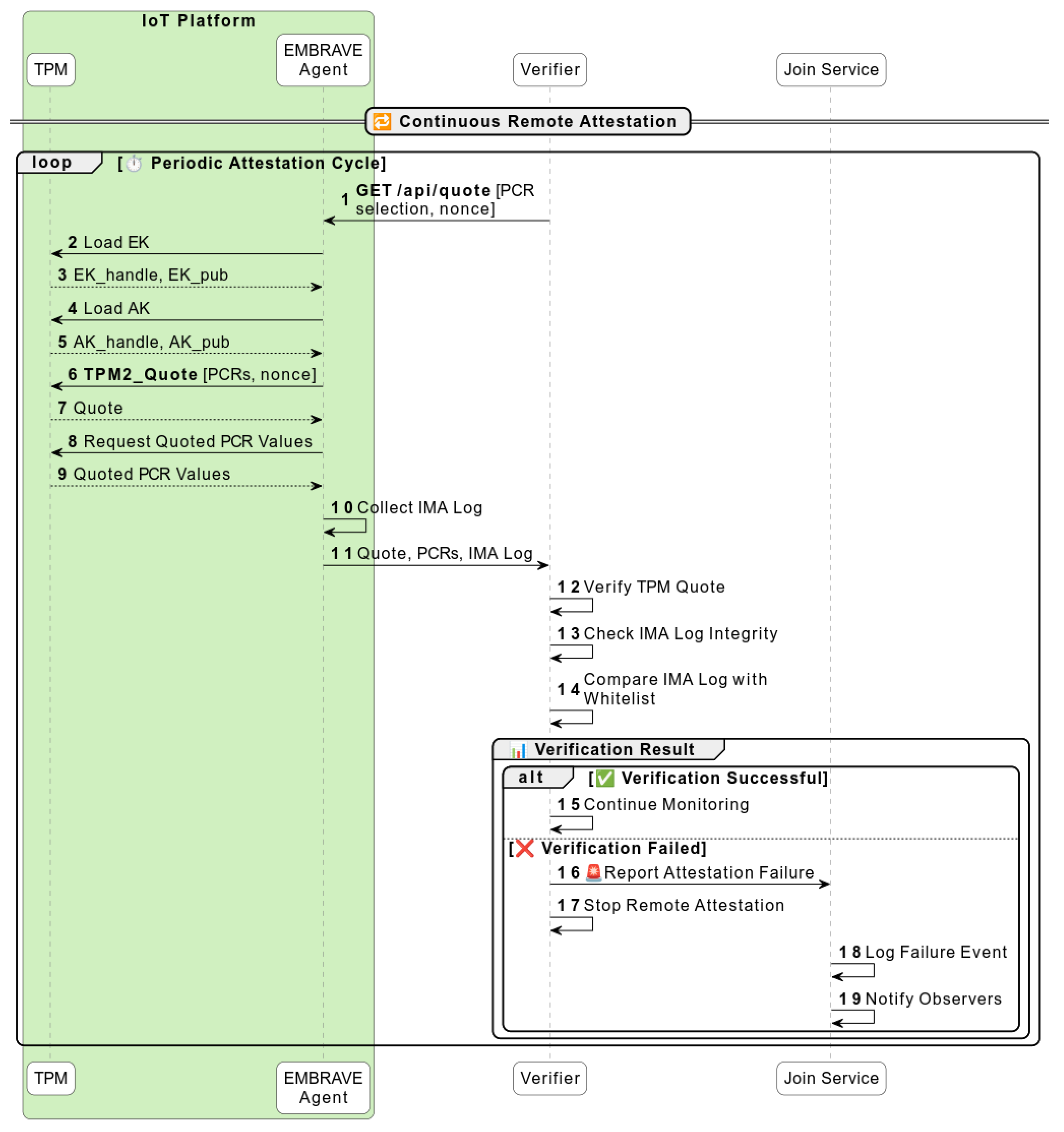
4.3. Remote Attestation Protocol
- Generates a quote with the TPM2_Quote command (6), (7). The output of this command is the signature of the values of the selected PCRs with the AK private part.
- Reads the quoted PCR (8), (9) values with the TPM2_PCR_Read command.
- Reads the IMA log (10) containing all the runtime measurements.
- Sends the quote, the values of the quoted PCRs, and the IMA log back to the Verifier (11).
4.4. Leave Protocol
5. Security Analysis
5.1. System Scope
5.2. Threat Model
5.3. Security Considerations
- AK Unforgeability: No adversary can produce a valid signature using without access to the associated physical TPM.
- Freshness and replay protection: The TPM quote is guaranteed to produce always fresh values and not reusable ones thanks to a nonce.
- Measurement soundness: PCR values correctly reflect the current platform integrity state at the time of attestation request, also thanks to the freshness of the quote.
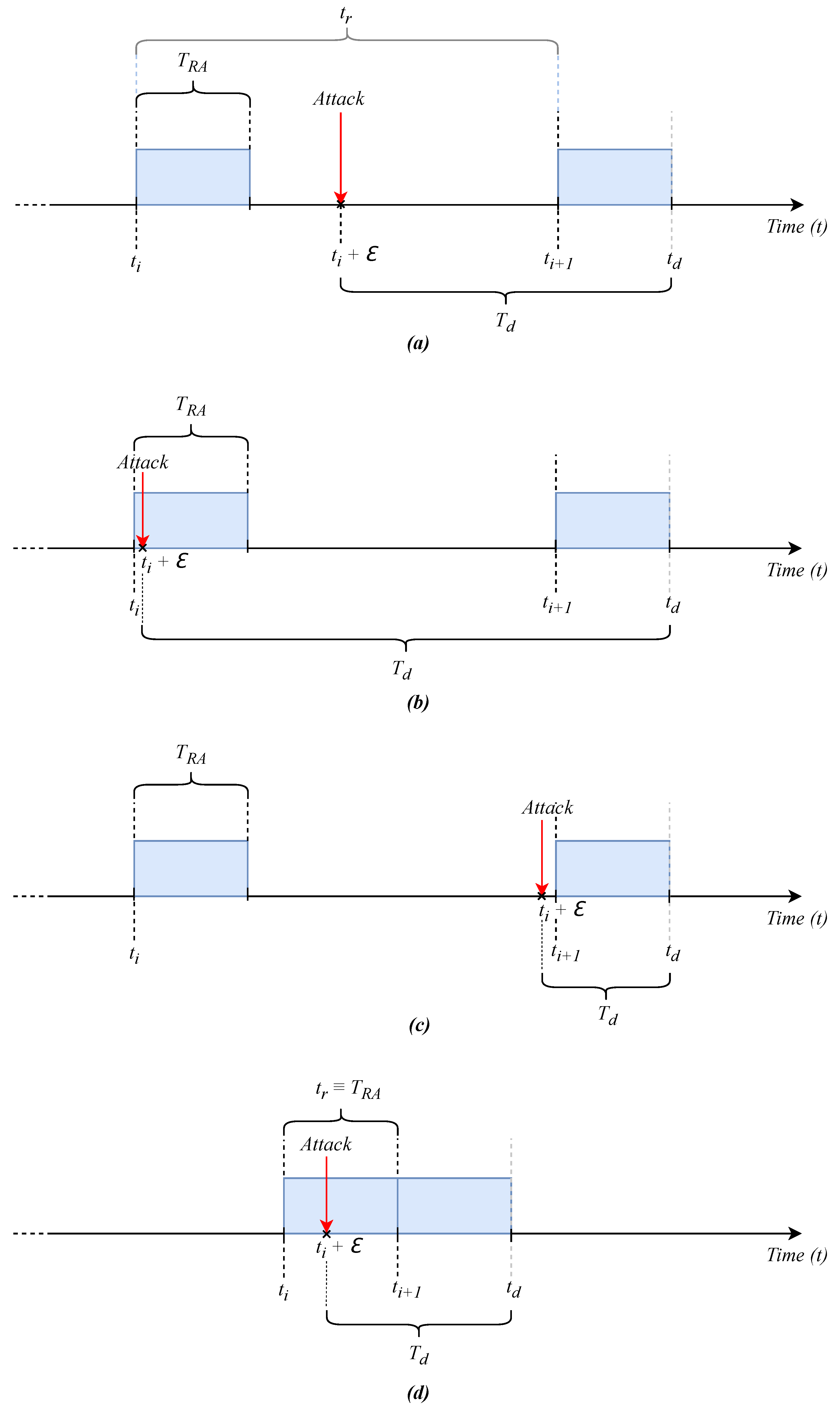
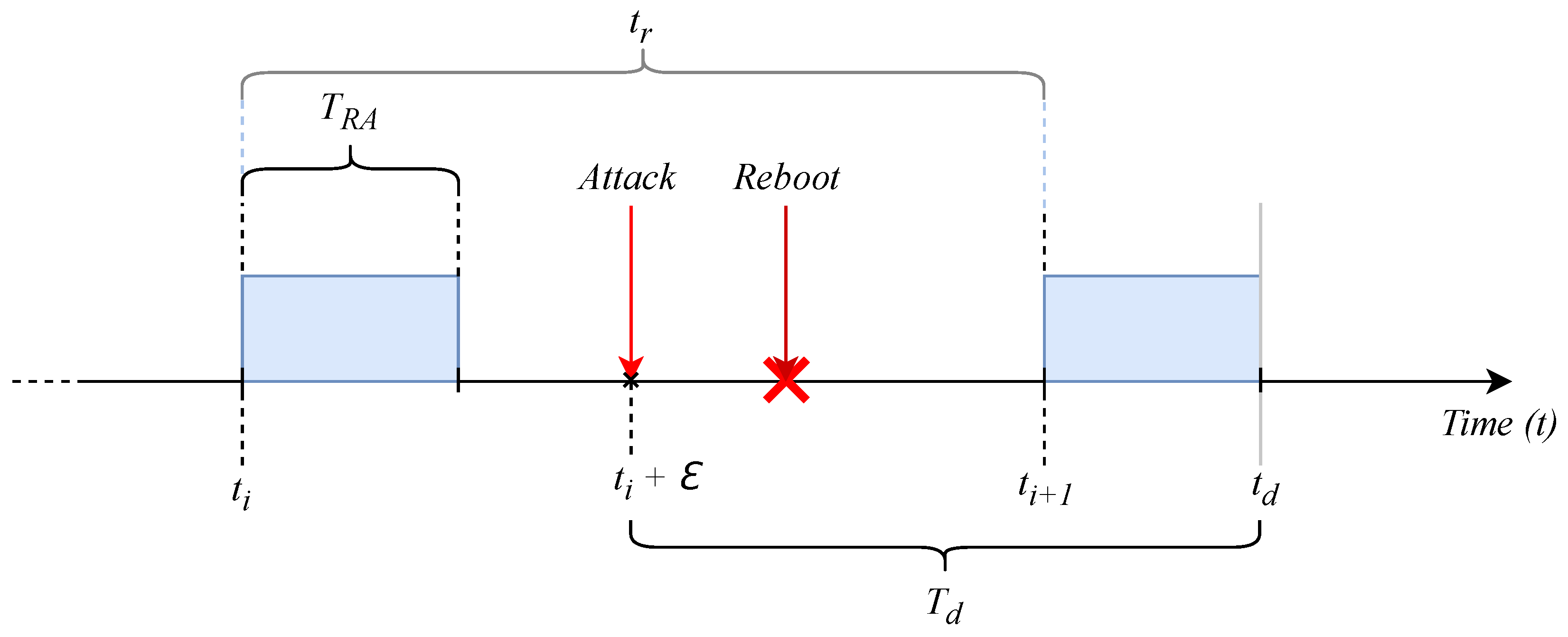
5.4. Attack Simulation
| Algorithm 1 IMA Log example showing expected kernel module measurement (in italic). |
|
| Algorithm 2 IMA Log example showing expected kernel module measurement (in italic) and the compromised kernel module (in bold). |
|
6. Implementation
| Algorithm 3 Listing of the IMA directory in the securityfs virtual filesystem. |
|
7. Experimental Evaluation
7.1. Testbed Description
- A Raspberry Pi 4 Model B [67] (Raspberry Pi, Cambridge, UK) with the processor running at and 4 RAM, using Raspbian GNU/Linux 11 (bullseye) with Linux kernel version 5.15.79.
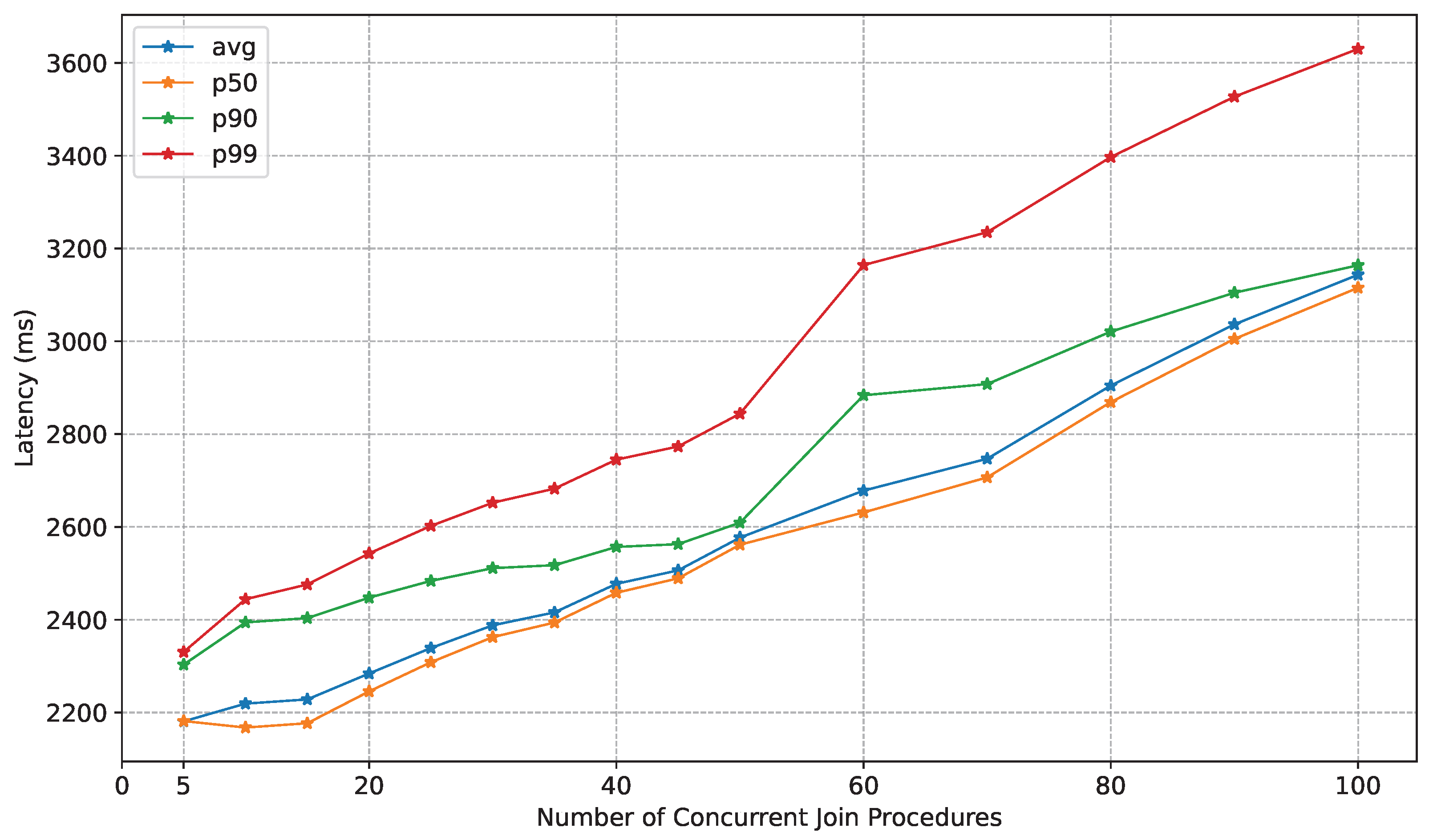
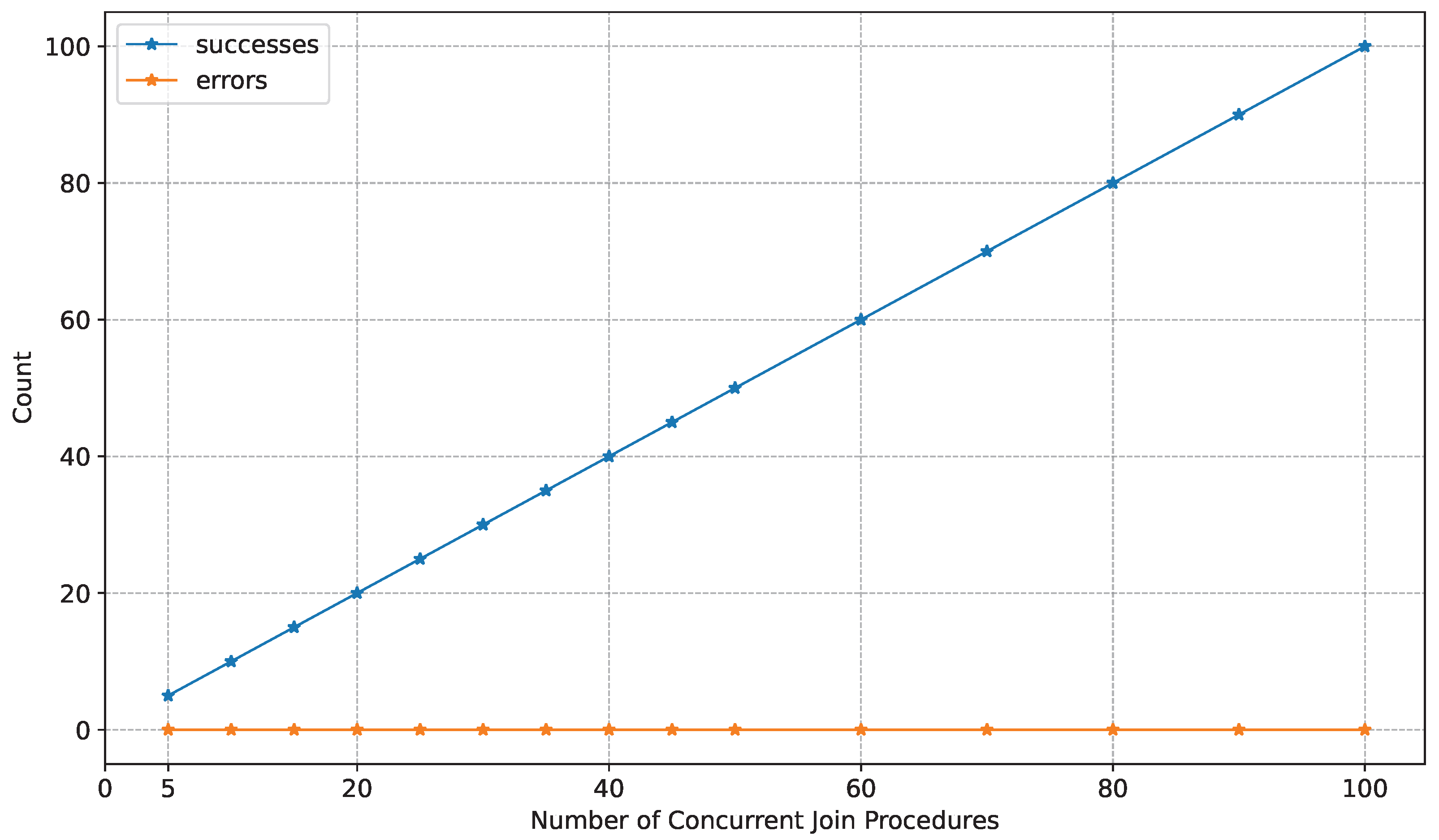
7.2. Experimental Results
- CPU: Intel® Core™ i9-13900H ;
- RAM: 32 ;
- OS: Ubuntu 22.04.5 LTS (Linux v6.8.0).
8. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Wu, H.-T.; Zheng, Y.; Zhao, B.; Hu, J. An Anonymous Reputation Management System for Mobile Crowdsensing Based on Dual Blockchain. IEEE Internet Things J. 2021, 9, 6956–6968. [Google Scholar] [CrossRef]
- Hazra, A. Promising Role of Visual IoT: Challenges and Future Research Directions. IEEE Eng. Manag. Rev. 2023, 51, 169–178. [Google Scholar] [CrossRef]
- Choudhary, V.; Guha, P.; Pau, G.; Mishra, S. An overview of smart agriculture using internet of things (IoT) and web services. Environ. Sustain. Indic. 2025, 26, 100607. [Google Scholar] [CrossRef]
- Kashani, M.H.; Madanipour, M.; Nikravan, M.; Asghari, P.; Mahdipour, E. A systematic review of IoT in healthcare: Applications, techniques, and trends. J. Netw. Comput. Appl. 2021, 192, 103164. [Google Scholar] [CrossRef]
- Katiyar, A.; Kumar, P. A Review of Internet of Things (IoT) in Construction Industry: Building a Better Future. Int. J. Adv. Sci. Comput. Eng. 2021, 3, 65–72. [Google Scholar] [CrossRef]
- Rabby, M.K.; Islam, M.M.; Imon, S.M. A Review of IoT Application in a Smart Traffic Management System. In Proceedings of the 2019 5th International Conference on Advances in Electrical Engineering (ICAEE), Dhaka, Bangladesh, 26–28 September 2019; pp. 280–285. [Google Scholar] [CrossRef]
- Coker, G.; Guttman, J.; Loscocco, P.; Herzog, A.; Millen, J.; O’Hanlon, B.; Ramsdell, J.; Segall, A.; Sheehy, J.; Sniffen, B. Principles of remote attestation. Int. J. Inf. Secur. 2011, 10, 63–81. [Google Scholar] [CrossRef]
- Tomlinson, A. Introduction to the TPM. In Smart Cards, Tokens, Security and Applications; Springer International Publishing: Cham, Switzerland, 2017; pp. 173–191. ISBN 978-3-319-50500-8. [Google Scholar]
- Trusted Computing Group. 2025. Available online: https://trustedcomputinggroup.org/ (accessed on 12 July 2025).
- TCG. Hardware Requirements for a Device Identifier Composition Engine. 2018. Available online: https://trustedcomputinggroup.org/wp-content/uploads/Hardware-Requirements-for-Device-Identifier-Composition-Engine-r78_For-Publication.pdf (accessed on 12 July 2025).
- TCG. Measurement and Attestation RootS (MARS) Library Specification. 2023. Available online: https://trustedcomputinggroup.org/wp-content/uploads/TCG_MARS_Library_Spec_v1r14_pub.pdf (accessed on 12 July 2025).
- Integrity Measurement Architecture (IMA) Documentation. 2023. Available online: https://ima-doc.readthedocs.io/en/latest/index.html (accessed on 12 July 2025).
- Integrity Measurement Architecture (IMA) Wiki. 2025. Available online: https://sourceforge.net/p/linux-ima/wiki/Home/ (accessed on 12 July 2025).
- Schear, N.; Cable, P.T.; Moyer, T.M.; Richard, B.; Rudd, R. Bootstrapping and Maintaining Trust in the Cloud. In Proceedings of the ACSAC ’16: 2016 Annual Computer Security Applications Conference, Los Angeles, CA, USA, 5–8 December 2016; pp. 65–77. [Google Scholar] [CrossRef]
- Moreau, L.; Conchon, E.; Sauveron, D. CRAFT: A Continuous Remote Attestation Framework for IoT. IEEE Access 2021, 9, 46430–46447. [Google Scholar] [CrossRef]
- Xu, W.; Ahn, G.-J.; Hu, H.; Zhang, X.; Seifert, J.-P. DR@FT: Efficient Remote Attestation Framework for Dynamic Systems. In Proceedings of the 15th European Symposium on Research in Computer Security, Athens, Greece, 20–22 September 2010; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6345, pp. 182–198. [Google Scholar] [CrossRef]
- Hardware-Enabled Security: Enabling a Layered Approach to Platform Security for Cloud and Edge Computing Use Cases. 2022. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2022/NIST.IR.8320.pdf (accessed on 12 July 2025).
- TCG. Trusted Platform Module Library Part 1: Architecture. 2024. Available online: https://trustedcomputinggroup.org/wp-content/uploads/TPM-2.0-1.83-Part-1-Architecture.pdf (accessed on 12 July 2025).
- TCG. TCG TSS 2.0 Overview and Common Structures Specification. 2021. Available online: https://trustedcomputinggroup.org/wp-content/uploads/TSS_Overview_Common_v1_r10_pub09232021.pdf (accessed on 12 July 2025).
- Rashmi, R.V.; Karthikeyan, A. Secure boot of Embedded Applications—A Review. In Proceedings of the 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018; pp. 291–298. [Google Scholar] [CrossRef]
- UEFI Secure Boot in Modern Computer Security Solutions. Available online: https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2014/06/20082511/UEFI_Secure_Boot_in_Modern_Computer_Security_Solutions_2013-1.pdf (accessed on 12 July 2025).
- Sailer, R.; Zhang, X.; Jaeger, T.; Van Doorn, L. Design and implementation of a TCG-based integrity measurement architecture. In Proceedings of the 13th USENIX Security Symposium, San Diego, CA, USA, 9–13 August 2004; pp. 223–238. Available online: https://www.usenix.org/legacy/events/sec04/tech/full_papers/sailer/sailer.pdf (accessed on 12 July 2025).
- IMA Template Management Mechanism. Available online: https://www.kernel.org/doc/html/latest/security/IMA-templates.html (accessed on 12 July 2025).
- Kuang, B.; Fu, A.; Susilo, W.; Yu, S.; Gao, Y. A survey of remote attestation in Internet of Things: Attacks, countermeasures, and prospects. Comput. Secur. 2022, 112, 102498. [Google Scholar] [CrossRef]
- Sabt, M.; Achemlal, M.; Bouabdallah, A. Trusted Execution Environment: What It is, and What It is Not. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; pp. 57–64. [Google Scholar] [CrossRef]
- Costan, V.; Devadas, S. Intel SGX Explained. 2016. Available online: https://eprint.iacr.org/2016/086.pdf (accessed on 12 July 2025).
- Cheng, P.-C.; Ozga, W.; Valdez, E.; Ahmed, S.; Gu, Z.; Jamjoom, H.; Franke, H.; Bottomley, J. Intel TDX Demystified: A Top-Down Approach. ACM Comput. Surv. 2024, 56, 1–33. [Google Scholar] [CrossRef]
- Pinto, S.; Santos, N. Demystifying ARM TrustZone: A Comprehensive Survey. ACM Comput. Surv. 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Ankergård, S.F.J.J.; Dushku, E.; Dragoni, N. State-of-the-Art Software-Based Remote Attestation: Opportunities and Open Issues for Internet of Things. Sensors 2021, 21, 1598. [Google Scholar] [CrossRef] [PubMed]
- Seshadri, A.; Luk, M.; Shi, E.; Perrig, A.; van Doorn, L.; Khosla, P. Pioneer: Verifying Code Integrity and Enforcing Untampered Code Execution on Legacy Systems. In Proceedings of the Twentieth ACM Symposium on Operating Systems Principles, Brighton, UK, 23–26 December 2005; pp. 1–16. [Google Scholar] [CrossRef]
- Seshadri, A.; Perrig, A.; van Doorn, L.; Khosla, P. SWATT: SoftWare-based attestation for embedded devices. In Proceedings of the IEEE Symposium on Security and Privacy, 2004. Proceedings. 2004, Berkeley, CA, USA, 12 May 2004; pp. 272–282. [Google Scholar] [CrossRef]
- Cao, J.; Zhu, T.; Ma, R.; Guo, Z.; Zhang, Y.; Li, H. A Software-Based Remote Attestation Scheme for Internet of Things Devices. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1422–1434. [Google Scholar] [CrossRef]
- Eldefrawy, K.; Rattanavipanon, N.; Tsudik, G. HYDRA: Hybrid Design for Remote Attestation (Using a Formally Verified Microkernel). In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Boston, MA, USA, 18–20 July 2017; pp. 99–110. [Google Scholar] [CrossRef]
- Eldefrawy, K.; Tsudik, G.; Francillon, A.; Perito, D. Smart: Secure and minimal architecture for (establishing dynamic) root of trust. In Proceedings of the 19th Annual Network and Distributed System Security Symposium, San Diego, CA, USA, 5–8 February 2012; pp. 99–110. [Google Scholar]
- Aman, M.N.; Basheer, M.H.; Dash, S.; Wong, J.W.; Xu, J.; Lim, H.W.; Sikdar, B. HAtt: Hybrid Remote Attestation for the Internet of Things with High Availability. IEEE Internet Things J. 2020, 7, 7220–7233. [Google Scholar] [CrossRef]
- Ibrahim, A.; Sadeghi, A.-R.; Zeitouni, S. SeED: Secure Non-Interactive Attestation for Embedded Devices. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Boston, MA, USA, 18–20 July 2017; pp. 64–74. [Google Scholar] [CrossRef]
- Carpent, X.; ElDefrawy, K.; Rattanavipanon, N.; Tsudik, G. Lightweight Swarm Attestation: A Tale of Two LISA-s. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, Abu Dhabi, United Arab Emirates, 2–6 April 2017; pp. 86–100. [Google Scholar] [CrossRef]
- Ammar, M.; Washha, M.; Crispo, B. WISE: Lightweight Intelligent Swarm Attestation Scheme for IoT (The Verifier’s Perspective). In Proceedings of the 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Limassol, Cyprus, 15–17 October 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Ambrosin, M.; Conti, M.; Lazzeretti, R.; Rabbani, M.M.; Ranise, S. Toward secure and efficient attestation for highly dynamic swarms: Poster. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Boston, MA, USA, 18–20 July 2017; pp. 281–282. [Google Scholar] [CrossRef]
- Kohnhäuser, F.; Büscher, N.; Katzenbeisser, S. SALAD: Secure and Lightweight Attestation of Highly Dynamic and Disruptive Networks. In Proceedings of the 2018 Asia Conference on Computer and Communications Security, Incheon, Republic of Korea, 4 June 2018; pp. 329–342. [Google Scholar] [CrossRef]
- Ambrosin, M.; Conti, M.; Lazzeretti, R.; Rabbani, M.M.; Ranise, S. PADS: Practical Attestation for Highly Dynamic Swarm Topologies. In Proceedings of the 2018 International Workshop on Secure Internet of Things (SIoT), Barcelona, Spain, 6 September 2018; pp. 18–27. [Google Scholar] [CrossRef]
- Ferro, L.; Bravi, E.; Sisinni, S.; Lioy, A. SAFEHIVE: Secure Attestation Framework for Embedded and Heterogeneous IoT Devices in Variable Environments. In Proceedings of the 2024 ACM Workshop on Secure and Trustworthy Cyber-Physical Systems (SaT-CPS), Porto, Portugal, 21 June 2024; pp. 41–50. [Google Scholar] [CrossRef]
- Asokan, N.; Brasser, F.; Ibrahim, A.; Sadeghi, A.-R.; Schunter, M.; Tsudik, G.; Wachsmann, C. SEDA: Scalable Embedded Device Attestation. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–15 October 2015; pp. 964–975. [Google Scholar] [CrossRef]
- Ambrosin, M.; Conti, M.; Ibrahim, A.; Neven, G.; Sadeghi, A.R.; Schunter, M. SANA: Secure and Scalable Aggregate Network Attestation. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 731–742. [Google Scholar] [CrossRef]
- Berger, S.; Cáceres, R.; Goldman, K.A.; Perez, R.; Sailer, R.; van Doorn, L. vTPM: Virtualizing the trusted platform module. In Proceedings of the 15th USENIX Security Symposium, Vancouver, BC, Canada, 31 July–4 August 2006; pp. 305–320. [Google Scholar]
- Kim, K.T.; Lim, J.D.; Kim, J.N. An IoT Device-trusted Remote Attestation Framework. In Proceedings of the 24th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Republic of Korea, 13–16 February 2022; pp. 218–223. [Google Scholar] [CrossRef]
- Klein, G.; Elphinstone, K.; Heiser, G.; Andronick, J.; Cock, D.A.; Derrin, P.; Elkaduwe, D.; Engelhardt, K.; Kolanski, R.; Norrish, M.; et al. seL4: Formal verification of an OS kernel. In Proceedings of the ACM SIGOPS 22nd Symposium on Operating Systems Principles, Big Sky, MT, USA, 11–14 October 2009; pp. 207–220. [Google Scholar] [CrossRef]
- TCG. TCG Trusted Attestation Protocol (TAP) Information Model for TPM Families 1.2 and 2.0 and DICE Family 1.0. 2019. Available online: https://trustedcomputinggroup.org/wp-content/uploads/TNC_TAP_Information_Model_v1.00_r0.36-FINAL.pdf (accessed on 12 July 2025).
- MQTT: The Standard for IoT Messaging. 2024. Available online: https://mqtt.org/ (accessed on 12 July 2025).
- TCG. Trusted Platform Module Library Part 2: Structures. 2024. Available online: https://trustedcomputinggroup.org/wp-content/uploads/TPM-2.0-1.83-Part-2-Structures.pdf (accessed on 12 July 2025).
- Raj, H.; Saroiu, S.; Wolman, A.; Aigner, R.; Cox, J.; England, P.; Fenner, C.; Kinshumann, K.; Loeser, J.; Mattoon, D.; et al. fTPM: A Software-Only Implementation of a TPM Chip. In Proceedings of the 25th USENIX Security Symposium, Austin, TX, USA, 10–12 August 2016; pp. 841–856. [Google Scholar]
- Boubakri, M.; Chiatante, F.; Zouari, B. Towards a firmware TPM on RISC-V. In Proceedings of the 2021 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 1–5 February 2021; pp. 647–650. [Google Scholar] [CrossRef]
- Linux Keyrings. Available online: https://www.man7.org/linux/man-pages/man7/keyrings.7.html (accessed on 12 July 2025).
- Bellare, M.; Ristenpart, T.; Rogaway, P.; Stegers, T. Format-Preserving Encryption. In Proceedings of the Selected Areas in Cryptography, Calgary, AB, Canada, 13–14 August 2009; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5867, pp. 295–312. [Google Scholar] [CrossRef]
- Loscocco, P.; Smalley, S. Integrating Flexible Support for Security Policies into the Linux Operating System. In Proceedings of the USENIX Annual Technical Conference, Boston, MA, USA, 25–30 June 2001; pp. 29–42. [Google Scholar]
- IMA Policy-IMA 1.0 Documentation. 2023. Available online: https://ima-doc.readthedocs.io/en/latest/ima-policy.html (accessed on 12 July 2025).
- EMBRAVE Source Code. Available online: https://github.com/Cybersecurity-LINKS/embrave (accessed on 12 July 2025).
- OSS Implementation of the TCG TPM2 Software Stack (TSS2). Available online: https://github.com/tpm2-software/tpm2-tss (accessed on 12 July 2025).
- The securityfs Virtual Filesystem. Available online: https://elixir.bootlin.com/linux/v6.16.3/source/security/inode.c (accessed on 12 July 2025).
- The OpenSSL Project. Available online: https://github.com/openssl/openssl (accessed on 12 July 2025).
- The Mongoose Project. Available online: https://mongoose.ws/ (accessed on 12 July 2025).
- The Mosquitto Project. Available online: https://mosquitto.org/ (accessed on 12 July 2025).
- Variscite Ltd. VAR-DT8MCustomBoard V2.x Datasheet. 2021. Available online: https://device.report/m/ac29b129e8d8ac98c41835dc5098049510202bb2aac722b71ae93ea6f0f1733c_pdf (accessed on 12 July 2025).
- Variscite Ltd. DART-MX8M-PLUS V1.x Datasheet. 2023. Available online: https://www.variscite.it/wp-content/uploads/2020/10/DART-MX8M-PLUS_Datasheet.pdf (accessed on 12 July 2025).
- The Yocto Project. Release Notes for 4.0 (Kirkstone). Available online: https://docs.yoctoproject.org/migration-guides/release-notes-4.0.html (accessed on 12 July 2025).
- Raspberry Pi Ltd. Raspberry Pi 4 Model B Datasheet. 2024. Available online: https://datasheets.raspberrypi.com/rpi4/raspberry-pi-4-datasheet.pdf (accessed on 12 July 2025).
- Infineon. OPTIGA™ TPM SLM 9670 TPM2.0 Data Sheet. 2019. Available online: https://www.infineon.com/assets/row/public/documents/30/49/infineon-slm-9670-datasheet-en.pdf (accessed on 12 July 2025).
- Infineon. Iridium-SPI TPM Board Description. 2020. Available online: https://www.infineon.com/dgdl/Infineon-Iridium_1-0_9670_HD-AdditionalTechnicalInformation-v01_01-EN.pdf?fileId=5546d46271bf4f920171ef70667e51b4 (accessed on 12 July 2025).
- Google. Open Profile for DICE. 2021. Available online: https://github.com/google/open-dice/blob/main/docs/specification.md (accessed on 12 July 2025).



| PCR | Template-Hash | Template-Name | Filedata-Hash | Filepath |
|---|---|---|---|---|
| 10 | b9[..]6a | ima-ng | sha256:99[..]17 | boot_aggregate |
| 10 | 10[..]e0 | ima-ng | sha256:91[..]34 | /init |
| 10 | 60[..]cd | ima-ng | sha256:12[..]48 | /usr/bin/sh |
| 10 | 51[..]b6 | ima-ng | sha256:d8[..]43 | /usr/../libc.so |
| … | … | … | … | … |
| Framework | Framework Capabilities | ||
|---|---|---|---|
|
Hardware
RoT-Based |
IoT- and Embedded
Systems-Oriented |
Dynamic Join
and Leave for Devices | |
| Keylime [15] | Yes (TPM 2.0) | No (cloud-oriented) | No (manual RA initialization) |
| CRAFT [16] | Not guaranteed (heterogeneous devices) | Yes | Flexible (heterogeneous RA protocols) |
| DR@FT [17] | Yes (TPM 1.2) | No (generic-purpose- systems-oriented) | No (manual registration) |
| Kim et al. [47] | Not guaranteed (heterogeneous devices) | Yes | No (manual registration) |
| HYDRA [34] | No (seL4 micro- kernel) | Yes | No (manual registration) |
| HAtt [36] | Partial (PUF-based) | Yes | No (manual registration) |
| WISE [39] | Not guaranteed (heterogeneous devices) | Yes | No (static network topology) |
| EMBRAVE | Yes (TPM 2.0) | Yes | Yes (Join Protocol defined) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bravi, E.; Claudio, A.; Lioy, A.; Vesco, A. EMBRAVE: EMBedded Remote Attestation and Verification framEwork. Sensors 2025, 25, 5514. https://doi.org/10.3390/s25175514
Bravi E, Claudio A, Lioy A, Vesco A. EMBRAVE: EMBedded Remote Attestation and Verification framEwork. Sensors. 2025; 25(17):5514. https://doi.org/10.3390/s25175514
Chicago/Turabian StyleBravi, Enrico, Alessio Claudio, Antonio Lioy, and Andrea Vesco. 2025. "EMBRAVE: EMBedded Remote Attestation and Verification framEwork" Sensors 25, no. 17: 5514. https://doi.org/10.3390/s25175514
APA StyleBravi, E., Claudio, A., Lioy, A., & Vesco, A. (2025). EMBRAVE: EMBedded Remote Attestation and Verification framEwork. Sensors, 25(17), 5514. https://doi.org/10.3390/s25175514






