An Analysis and Simulation of Security Risks in Radar Networks from the Perspective of Cybersecurity
Abstract
1. Introduction
2. Cybersecurity Threats Faced by Radar Networks
3. Threat Models and Defense Measures
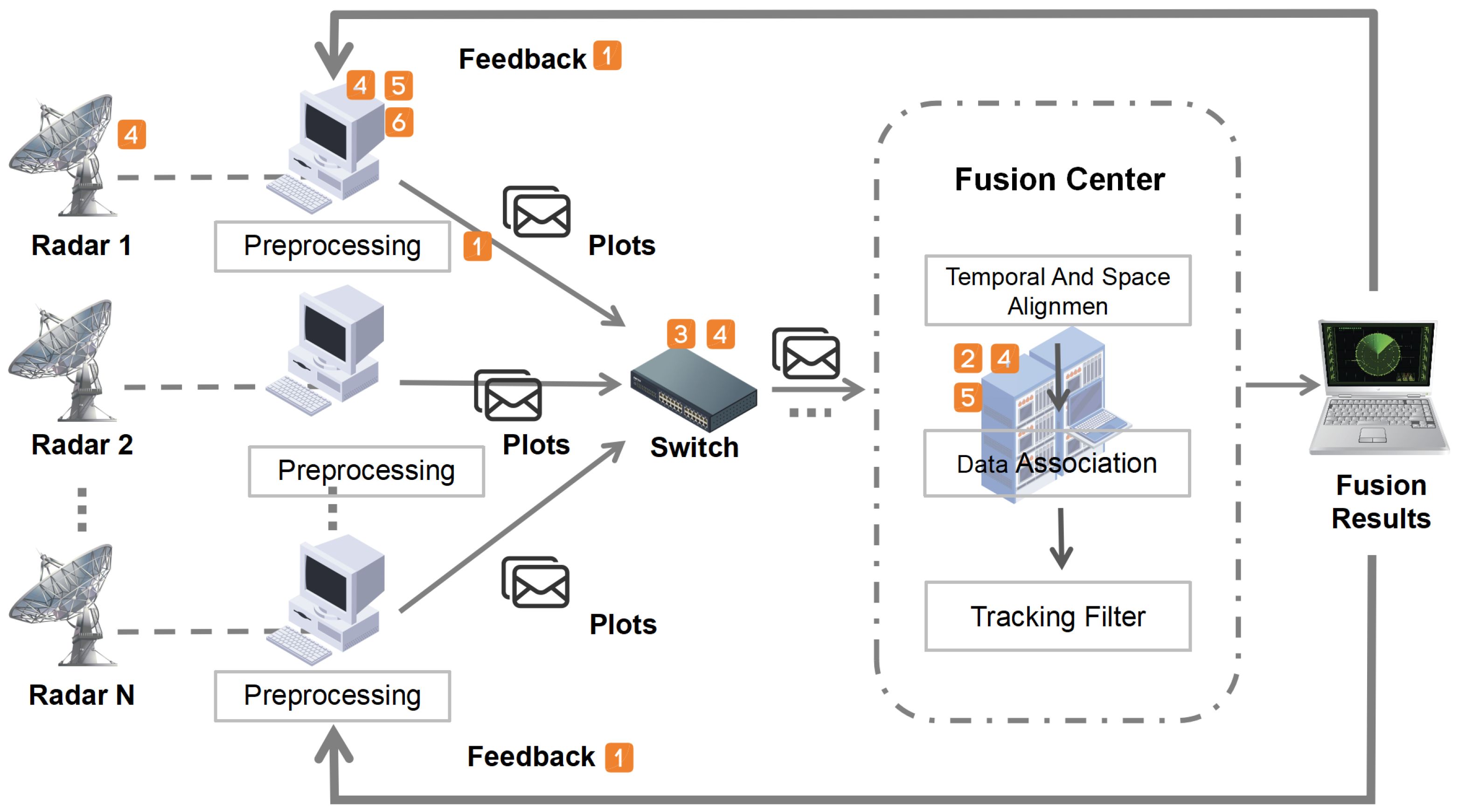
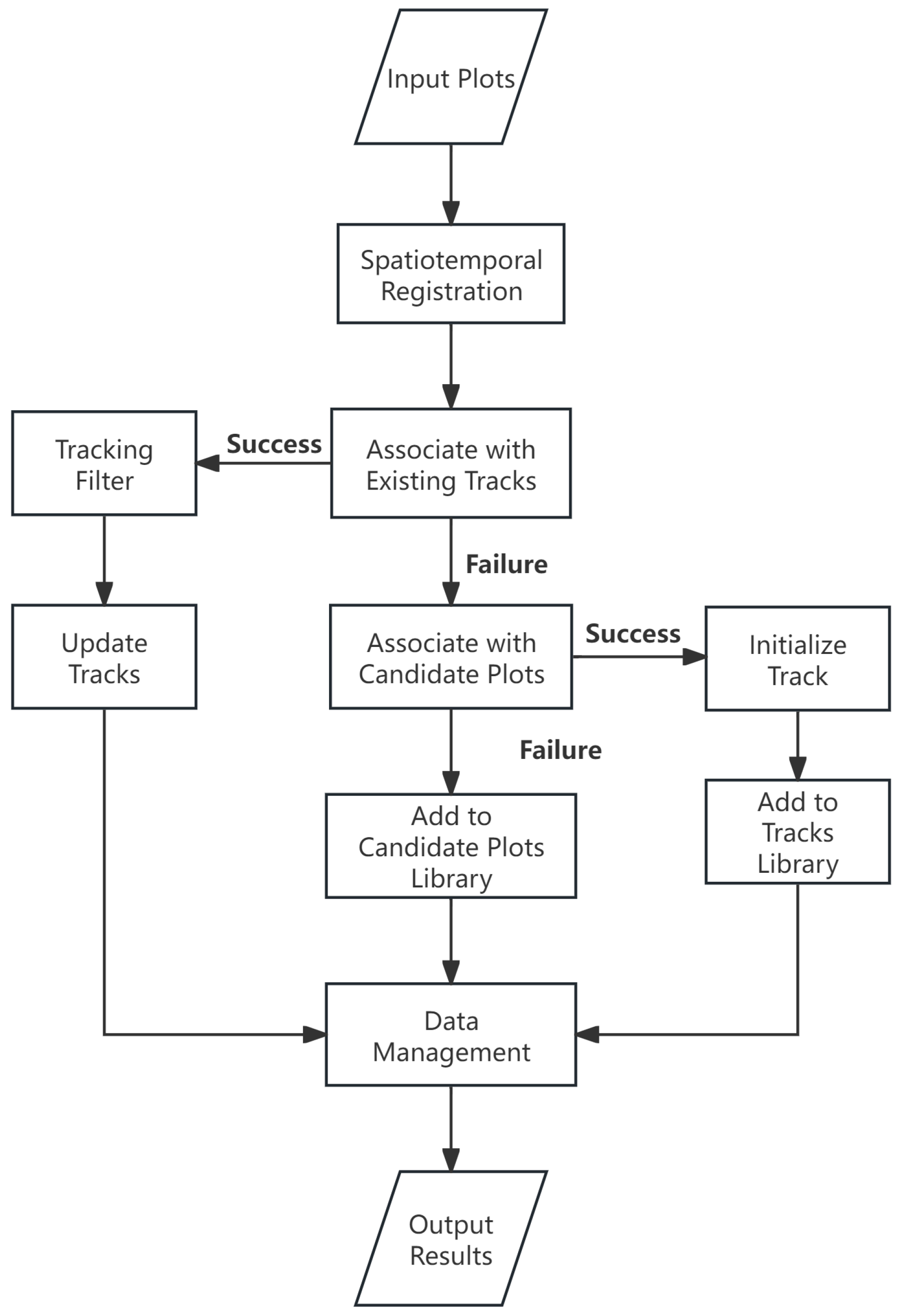
3.1. Connect Radar Network
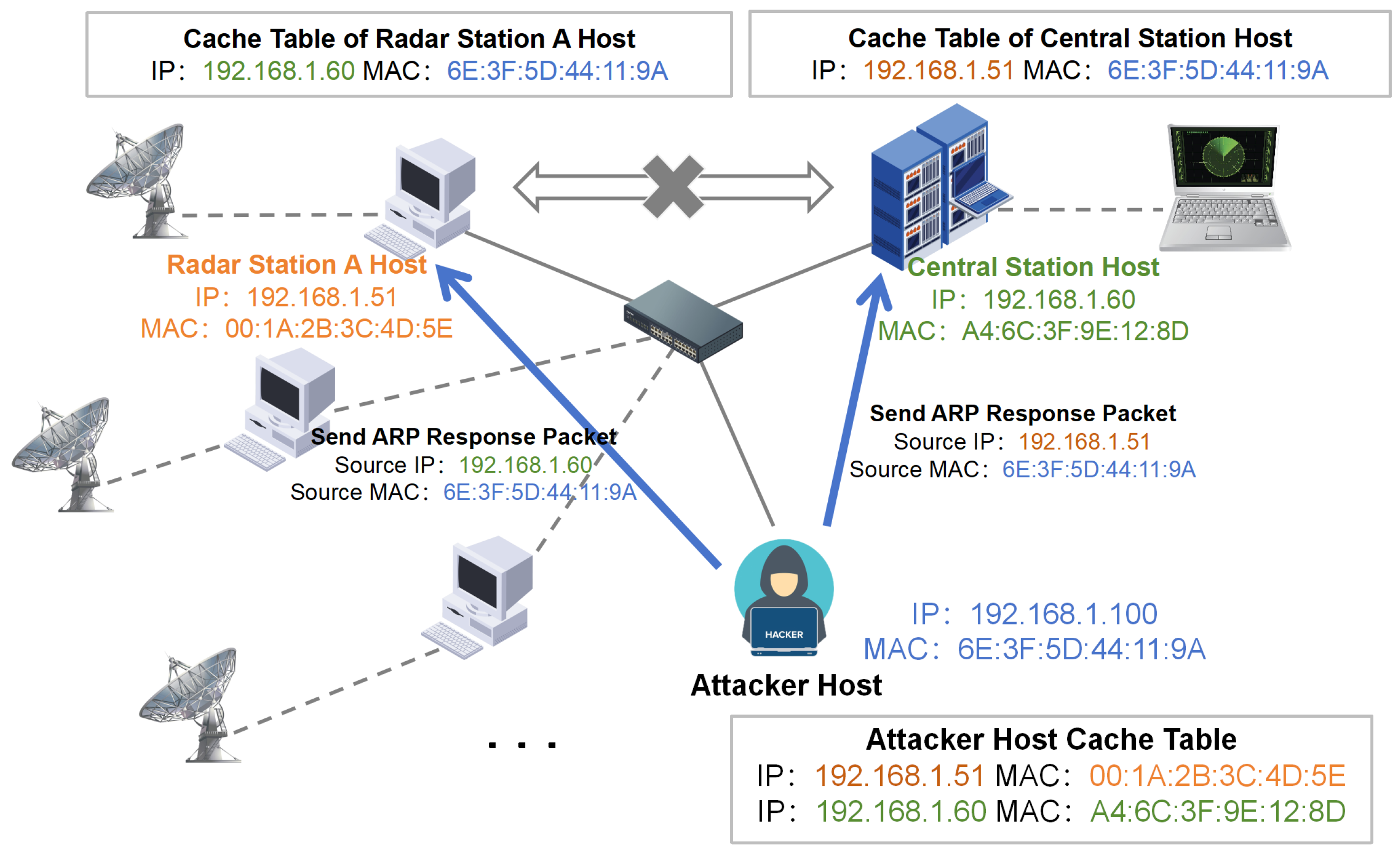
3.2. Man-in-the-Middle Attack via ARP Spoofing
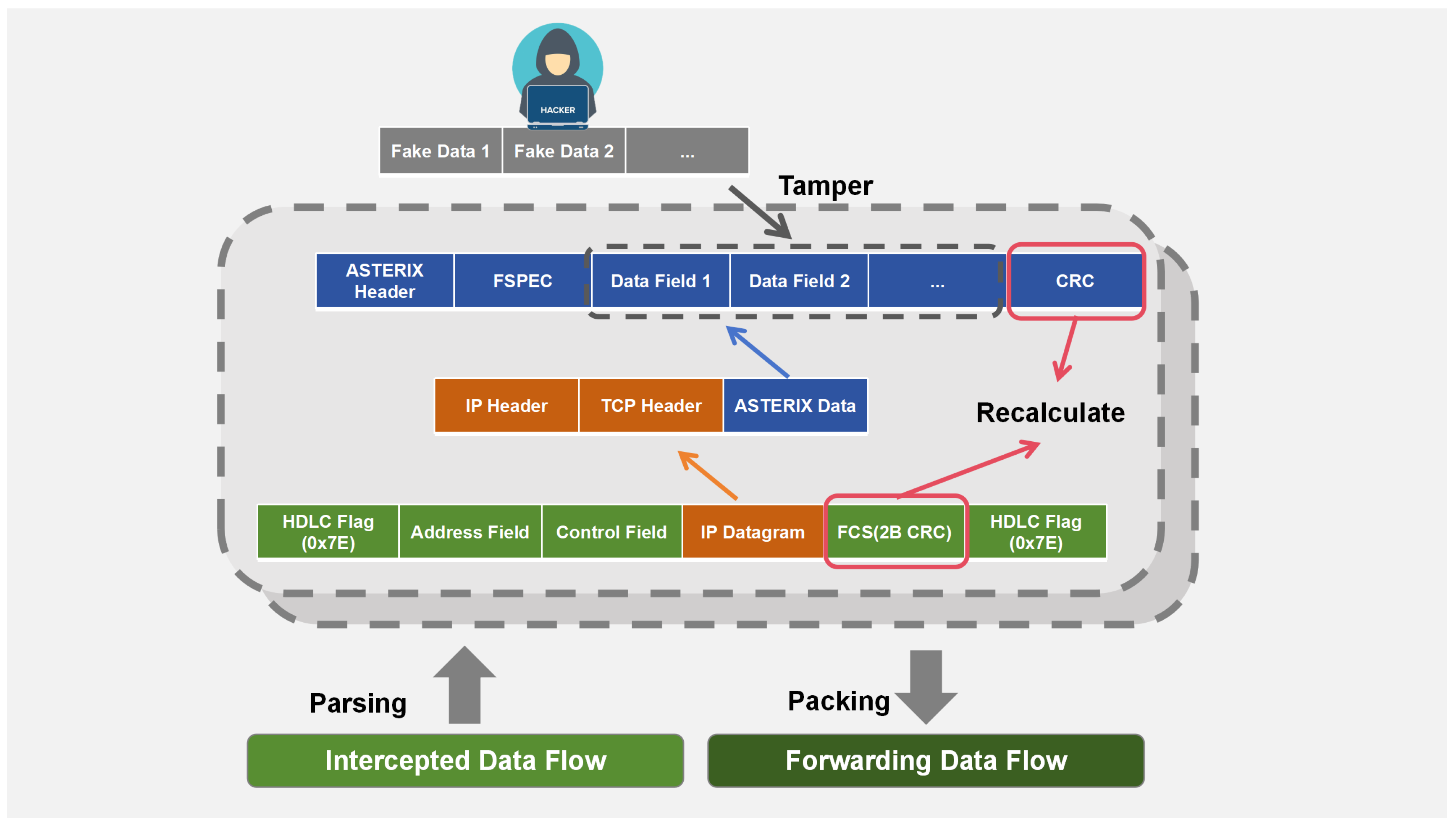
3.3. False Data Injection
3.4. Attack Effect Evaluation
3.5. Realistic Feasibility Analysis
4. Classification and Hazards of False Data Construction Methods
4.1. Single Link Control Scenario
- Set the goal: The attacker aims to pollute the state estimation of target M’s track by associating false plots with the real target, causing position deviation or track jitter.
- Select the tampering method: The attacker chooses offset as the data tampering method.
- Design the attack method: The attacker adopts a method of p times of inactivity and q times of attack. Inject offsets periodically to avoid track splitting due to long-term offsets. Let the start time of the i-th action cycle be ; then, we havewhere is the set of inactivity moments, is the set of attack moments, and T is the interval time, which is determined by the data upload period of the radar station.If the current moment , let and jump to step 8. If , then continue to execute this process.
- Obtain the target state: The attacker intercepts the state measurement value of the target M uploaded by the radar station at the current time t and combines with the intercepted at time to predict the velocity vector of the target M’s track at the current time t. Assuming that the target M moves in a uniform linear motion, we have
- Determine the direction: The attacker selects the offset direction (unit vector) according to the tactical intention. If manufacturing lateral error, the direction perpendicular to the predicted velocity is selected. At this time, we have
- Generate the offset amount : Is is assumed that the radar network uses a correlation threshold G to determine whether two plots belong to the same target. Then, the basic offset amount is set aswhere is used to periodically change the offset direction. is used to control the offset ratio and is a time-varying function; specifically,where is the initial coefficient and k is the modulation slope. Threshold G can be obtained from the following equation:where s represents the Euclidean distance between the predicted position and the measured position, represents the residual covariance matrix in the Kalman filter, and represents the false alarm probability of the correlation process. If is a diagonal matrix and isotropic, the above formula can be simplified asthen
- Increase stealthiness: The attacker adds a random noise that conforms to the radar accuracy model on ; then, we haveAt this time,
- Data tampering: The attacker replaces the state measurement value P of the target M uploaded by the radar station at time t with , where
- Enter the next action cycle: The attacker repeats the above process until the operation is completed.
4.2. Multi-Link Control Scenario
5. Simulation Experiment
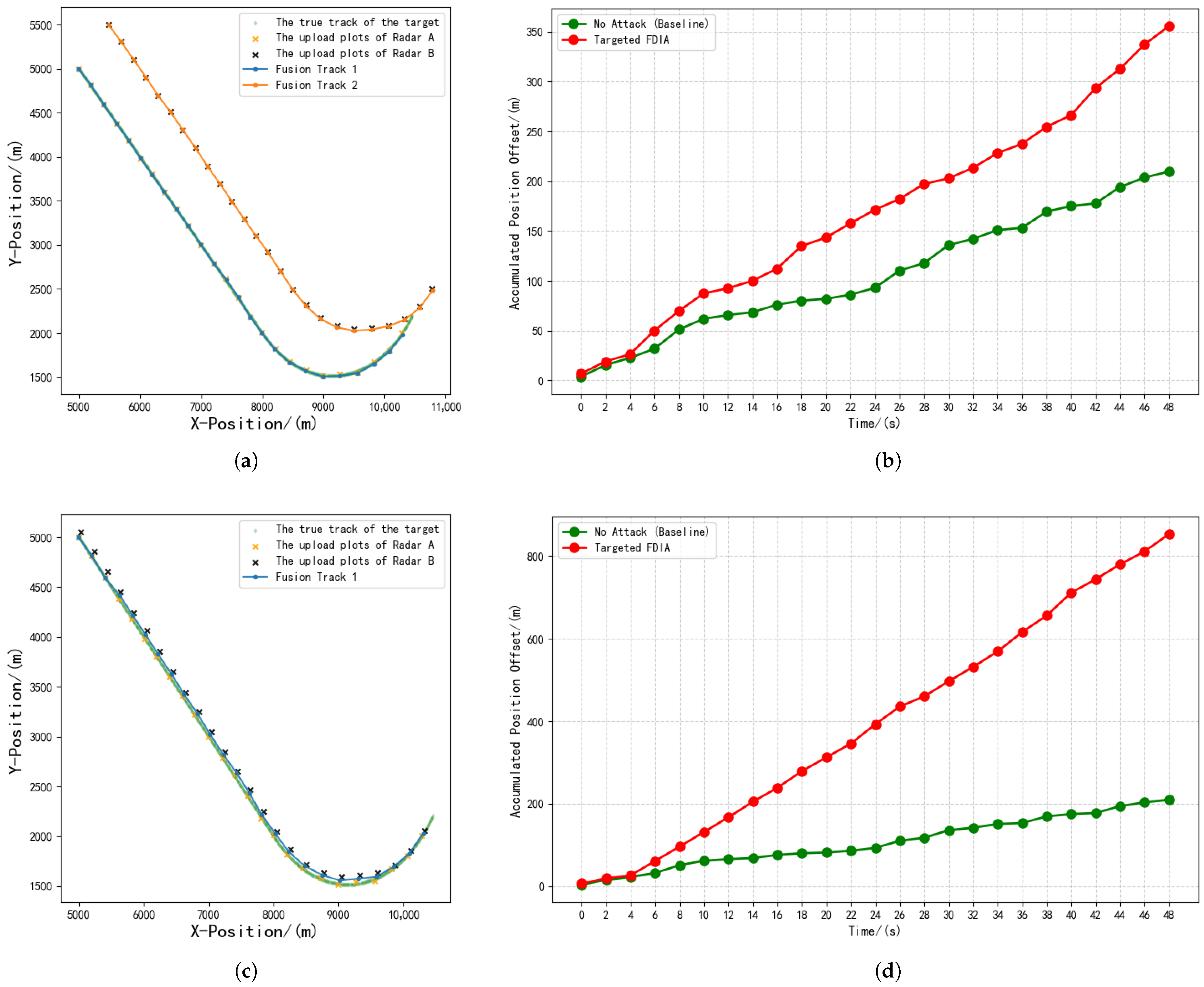
5.1. Single-Link Control Scenario
5.1.1. Experimental Background
5.1.2. Experimental Result
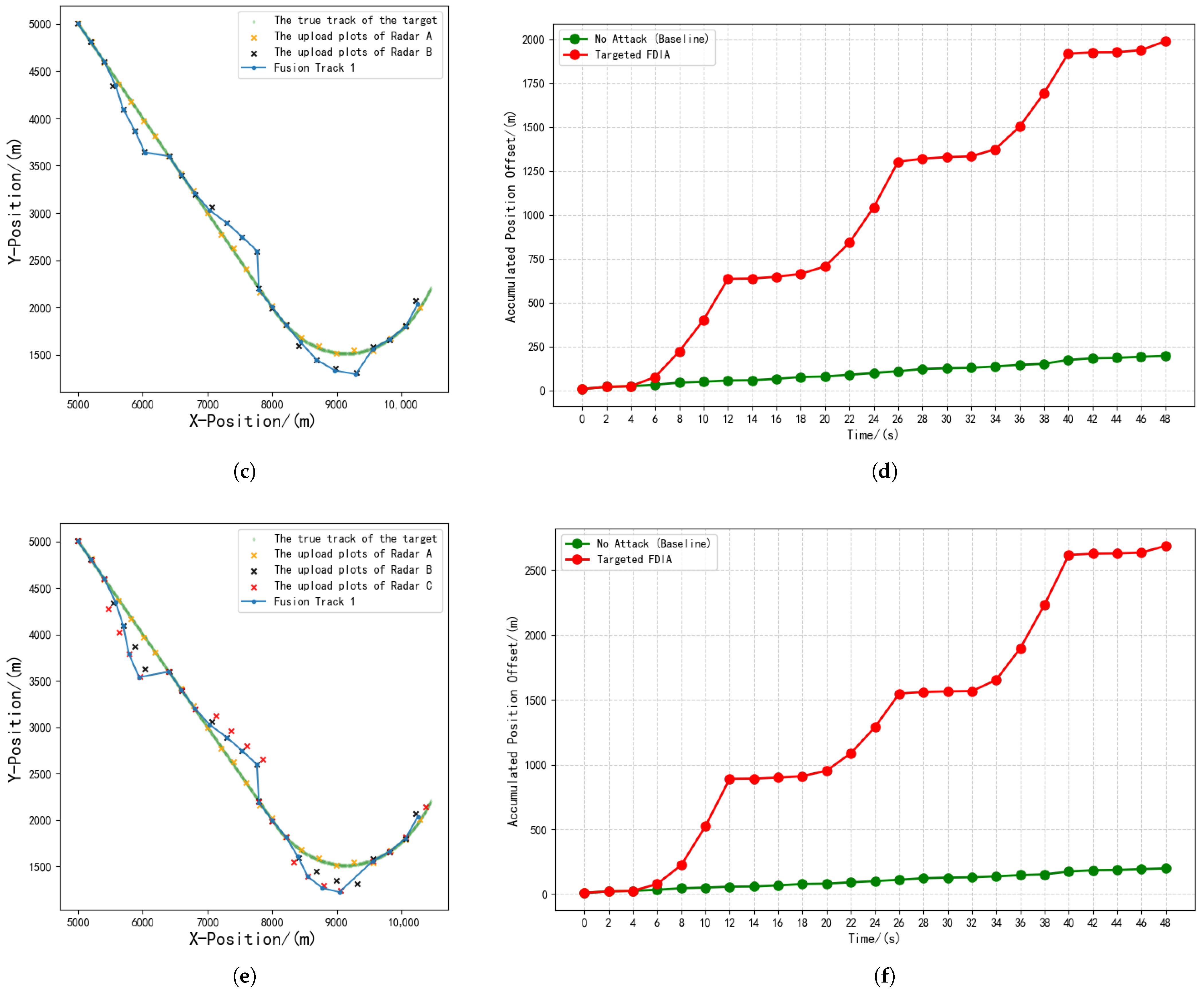
5.2. Multi-Link Control Scenario
5.2.1. Experimental Background
5.2.2. Experimental Results
6. Discussion
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| MITM | Man-in-the-Middle |
| FDIA | False Data Injection Attack |
| ATC | Air Traffic Control |
| CPS | Cyber–Physical System |
References
- Javadi, S.H.; Farina, A. Radar networks: A review of features and challenges. Inf. Fusion 2020, 61, 48–55. [Google Scholar] [CrossRef]
- Yang, C.; Feng, L.; Zhang, H.; He, S.; Shi, Z. A Novel Data Fusion Algorithm to Combat False Data Injection Attacks in Networked Radar Systems. IEEE Trans. Signal Inf. Process. Netw. 2018, 4, 125–136. [Google Scholar] [CrossRef]
- Collins, S.; McCombie, S. Stuxnet: The emergence of a new cyber weapon and its implications. J. Polic. Intell. Count. Terror. 2012, 7, 80–91. [Google Scholar] [CrossRef]
- Whitehead, D.E.; Owens, K.; Gammel, D.; Smith, J. Ukraine cyber-induced power outage: Analysis and practical mitigation strategies. In Proceedings of the 2017 70th Annual Conference for Protective Relay Engineers (CPRE), College Station, TX, USA, 3–6 April 2017; pp. 1–8. [Google Scholar]
- Svilicic, B.; Rudan, I.; Frančić, V.; Mohović, D. Towards a Cyber Secure Shipboard Radar. J. Navig. 2020, 73, 547–558. [Google Scholar] [CrossRef]
- Casanovas, E.E.; Buchaillot, T.E.; Baigorria, F. Vulnerability of radar protocol and proposed mitigation. In Proceedings of the 2015 ITU Kaleidoscope: Trust in the Information Society (K-2015), Barcelona, Spain, 9–11 December 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Wolsing, K.; Saillard, A.; Bauer, J.; Wagner, E.; van Sloun, C.; Fink, I.B.; Schmidt, M.; Wehrle, K.; Henze, M. Network Attacks Against Marine Radar Systems: A Taxonomy, Simulation Environment, and Dataset. In Proceedings of the 2022 IEEE 47th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 26–29 September 2022; pp. 114–122. [Google Scholar] [CrossRef]
- Hossain, M.A.; Hossain, M.S.; Hossain, M.D.; Islam, M.S.; Mustafa, H.A.; Rahman, M.M. Enhancing Marine Radar Security Through Semi-Supervised Learning: A Self-Training Approach. In Proceedings of the 2024 2nd International Conference on Information and Communication Technology (ICICT), Dhaka, Bangladesh, 21–22 October 2024; pp. 279–283. [Google Scholar] [CrossRef]
- Longo, G.; Russo, E.; Armando, A.; Merlo, A. Attacking (and Defending) the Maritime Radar System. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3575–3589. [Google Scholar] [CrossRef]
- Saillard, A.; Wolsing, K.; Wehrle, K.; Bauer, J. Exploring anomaly detection for marine RADAR systems. In Proceedings of the European Symposium on Research in Computer Security, Bydgoszcz, Poland, 16–20 September 2024; pp. 361–381. [Google Scholar]
- Visky, G.; Šiganov, A.; ur Rehman, M.; Vaarandi, R.; Bahşi, H.; Bahsi, H.; Tsiopoulos, L. Hybrid Cybersecurity Research and Education Environment for Maritime Sector. In Proceedings of the 2024 IEEE International Conference on Cyber Security and Resilience (CSR), London, UK, 2–4 September 2024; pp. 644–651. [Google Scholar]
- Leite Junior, W.C.; de Moraes, C.C.; de Albuquerque, C.E.P.; Machado, R.C.S.; de Sá, A.O. A Triggering Mechanism for Cyber-Attacks in Naval Sensors and Systems. Sensors 2021, 21, 3195. [Google Scholar] [CrossRef] [PubMed]
- Cohen, S.; Gluck, T.; Elovici, Y.; Shabtai, A. Security analysis of radar systems. In Proceedings of the ACM Workshop on Cyber-Physical Systems Security & Privacy, London, UK, 11 November 2019; pp. 3–14. [Google Scholar]
- Cohen, S.; Levy, E.; Shaked, A.; Cohen, T.; Elovici, Y.; Shabtai, A. RadArnomaly: Protecting Radar Systems from Data Manipulation Attacks. Sensors 2022, 22, 4259. [Google Scholar] [CrossRef] [PubMed]
- Basels, F.; Wolsing, K.; Padilla, E.; Bauer, J. Demo: Maritime Radar Systems under Attack. Help is on the Way! In Proceedings of the 2024 IEEE 49th Conference on Local Computer Networks (LCN), Normandy, France, 8–10 October 2024; pp. 1–4. [Google Scholar] [CrossRef]
- Longo, G.; Merlo, A.; Armando, A.; Russo, E. Electronic Attacks as a Cyber False Flag against Maritime Radars Systems. In Proceedings of the 2023 IEEE 48th Conference on Local Computer Networks (LCN), Daytona Beach, FL, USA, 2–5 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Lestriandoko, N.H.; Juhana, T.; Munir, R. Security system for surveillance radar network communication using chaos algorithm. In Proceedings of the 2014 8th International Conference on Telecommunication Systems Services and Applications (TSSA), Kuta, Indonesia, 23–24 October 2014. [Google Scholar] [CrossRef]
- Conti, M.; Dragoni, N.; Lesyk, V. A Survey of Man In The Middle Attacks. IEEE Commun. Surv. Tutorials 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Prasad, A.; Chandra, S. Defending ARP Spoofing-based MitM Attack using Machine Learning and Device Profiling. In Proceedings of the 2022 International Conference on Computing, Communication, and Intelligent Systems (ICCCIS), Greater Noida, India, 4–5 November 2022; pp. 978–982. [Google Scholar] [CrossRef]
- Cai, M.; Wu, Z.; Zhang, J. Research and Prevention of Rogue AP Based MitM in Wireless Network. In Proceedings of the 2014 Ninth International Conference on P2P, Parallel, Grid, Cloud and Internet Computing, Guangdong, China, 8–10 November 2014; pp. 538–542. [Google Scholar] [CrossRef]
- Liang, G.; Zhao, J.; Luo, F.; Weller, S.R.; Dong, Z.Y. A Review of False Data Injection Attacks Against Modern Power Systems. IEEE Trans. Smart Grid 2017, 8, 1630–1638. [Google Scholar] [CrossRef]
- Pang, Z.H.; Fan, L.Z.; Dong, Z.; Han, Q.L.; Liu, G.P. False Data Injection Attacks Against Partial Sensor Measurements of Networked Control Systems. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 149–153. [Google Scholar] [CrossRef]
- Serpanos, D. False Data Injection Attacks on Sensor Systems. In Proceedings of the 2022 IEEE/ACM International Conference On Computer Aided Design (ICCAD), San Diego, CA, USA, 30 October–3 November 2022; pp. 1–5. [Google Scholar]
- Reza, F. DDoS-Net: Classifying DDoS Attacks in Wireless Sensor Networks with Hybrid Deep Learning. In Proceedings of the 2024 6th International Conference on Electrical Engineering and Information & Communication Technology (ICEEICT), Dhaka, Bangladesh, 2–4 May 2024; pp. 487–492. [Google Scholar] [CrossRef]
- Shaneman, K.; Gray, S. Optical network security: Technical analysis of fiber tapping mechanisms and methods for detection & prevention. In Proceedings of the IEEE MILCOM 2004. Military Communications Conference, Monterey, CA, USA, 31 October–3 November 2004; Volume 2, pp. 711–716. [Google Scholar] [CrossRef]
- de Riberolles, T.; Zou, Y.; Silvestre, G.; Lochin, E.; Song, J. Anomaly detection for ICS based on deep learning: A use case for aeronautical radar data. Ann. Telecommun. 2022, 77, 749–761. [Google Scholar] [CrossRef]
- Petrović, R.; Simić, D.; Stanković, S.; Perić, M. Man-In-The-Middle Attack Based on ARP Spoofing in IoT Educational Platform. In Proceedings of the 2021 15th International Conference on Advanced Technologies, Systems and Services in Telecommunications (TELSIKS), Nis, Serbia, 20–22 October 2021; pp. 307–310. [Google Scholar] [CrossRef]
- Nam, S.Y.; Kim, D.; Kim, J. Enhanced ARP: Preventing ARP poisoning-based man-in-the-middle attacks. IEEE Commun. Lett. 2010, 14, 187–189. [Google Scholar] [CrossRef]
- Chandru, J.; Bagyalakshmi, C. MITM Attack Based Detection and Prevention for ARP Poisoning in Wireless Network Environment. In Proceedings of the 2025 International Conference on Computing and Communication Technologies (ICCCT), Chennai, India, 16–17 April 2025; pp. 1–6. [Google Scholar] [CrossRef]
- de Riberolles, T.; Song, J.; Zou, Y.; Silvestre, G.; Larrieu, N. Characterizing Radar Network Traffic: A first step towards spoofing attack detection. In Proceedings of the 2020 IEEE Aerospace Conference, Big Sky, MT, USA, 7–14 March 2020. [Google Scholar]

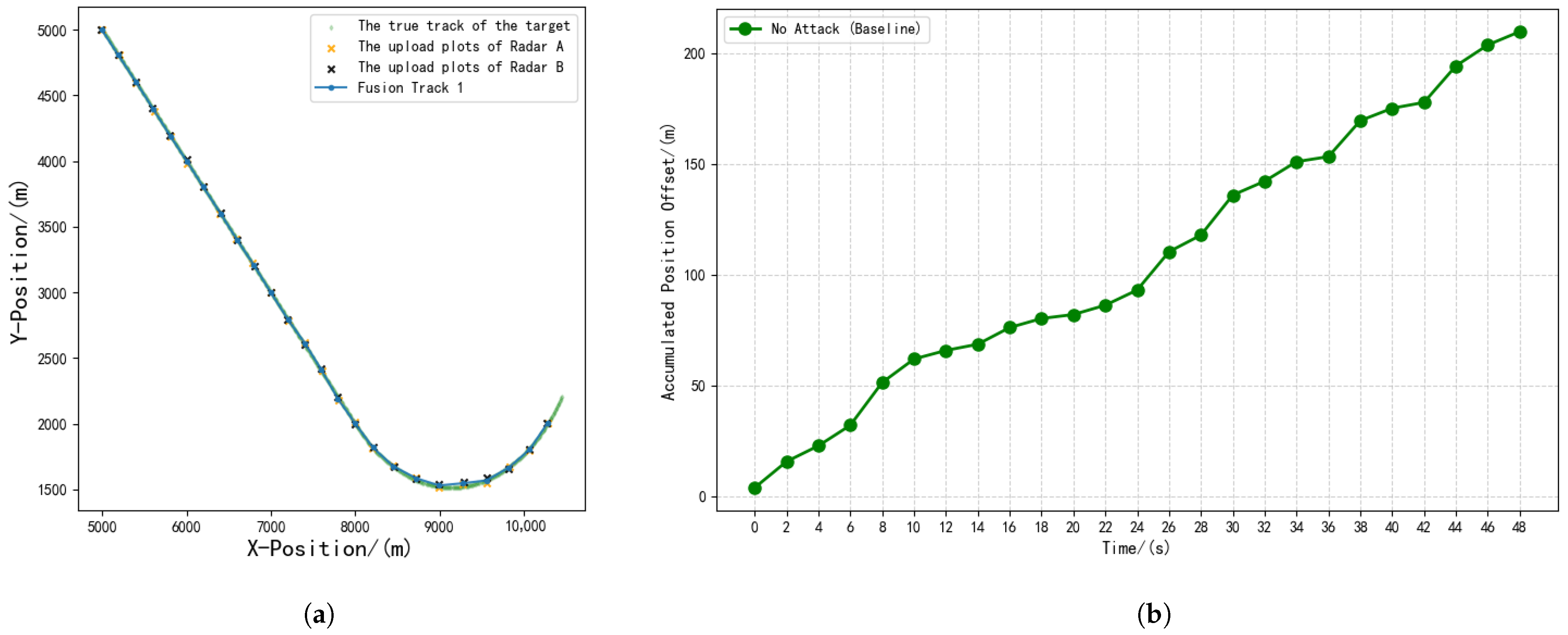
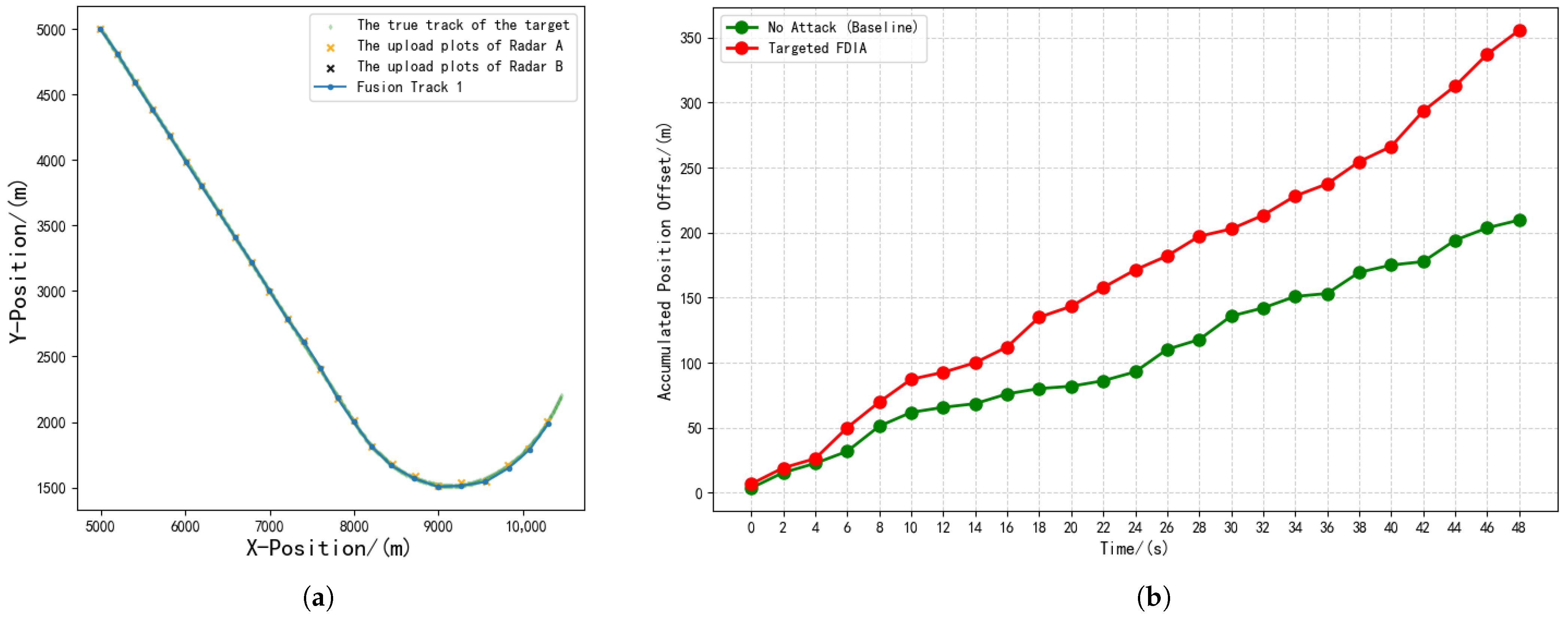
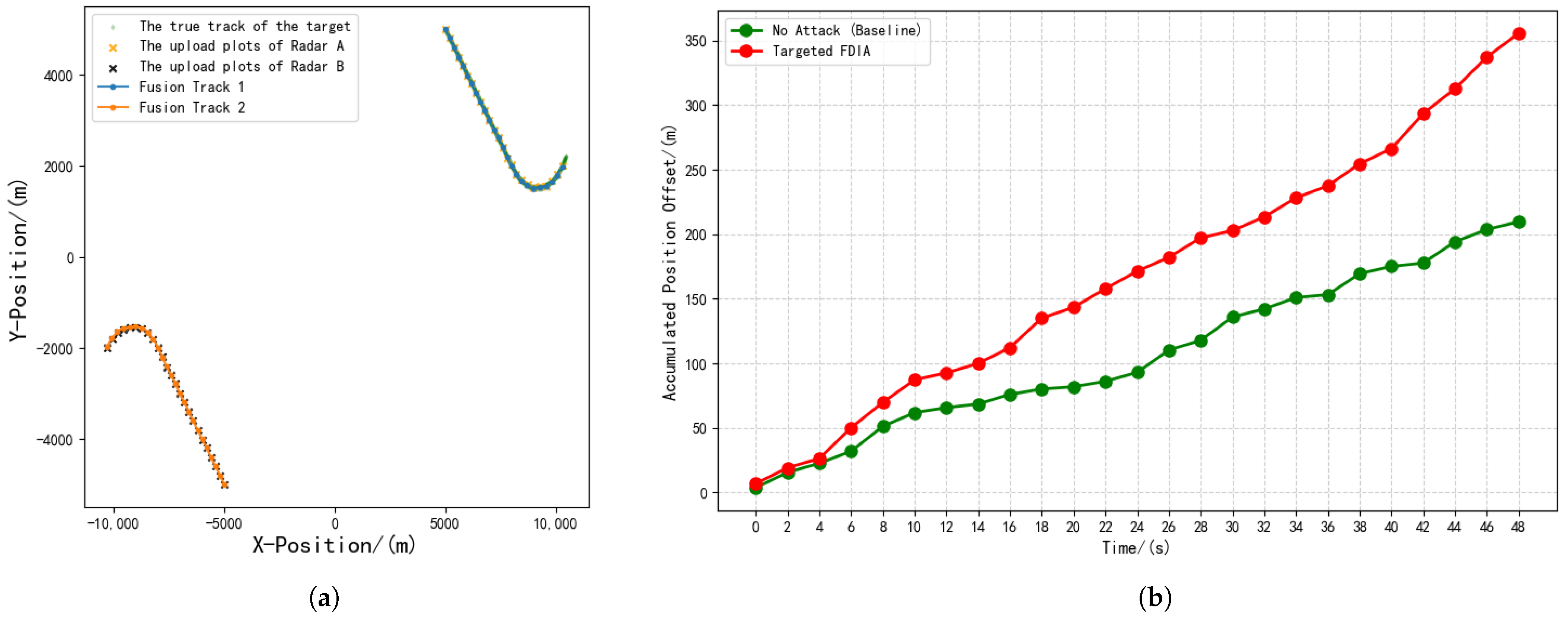
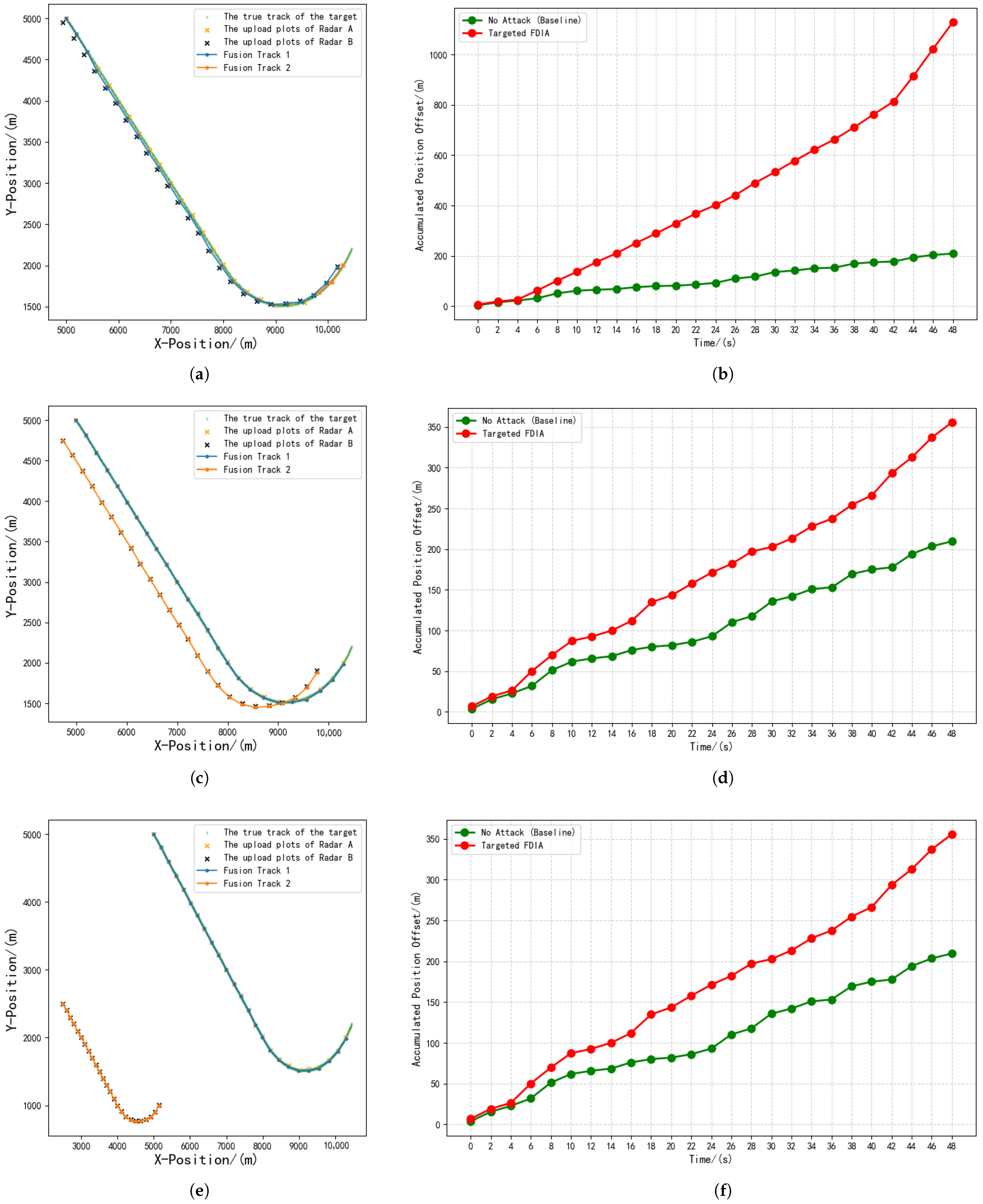

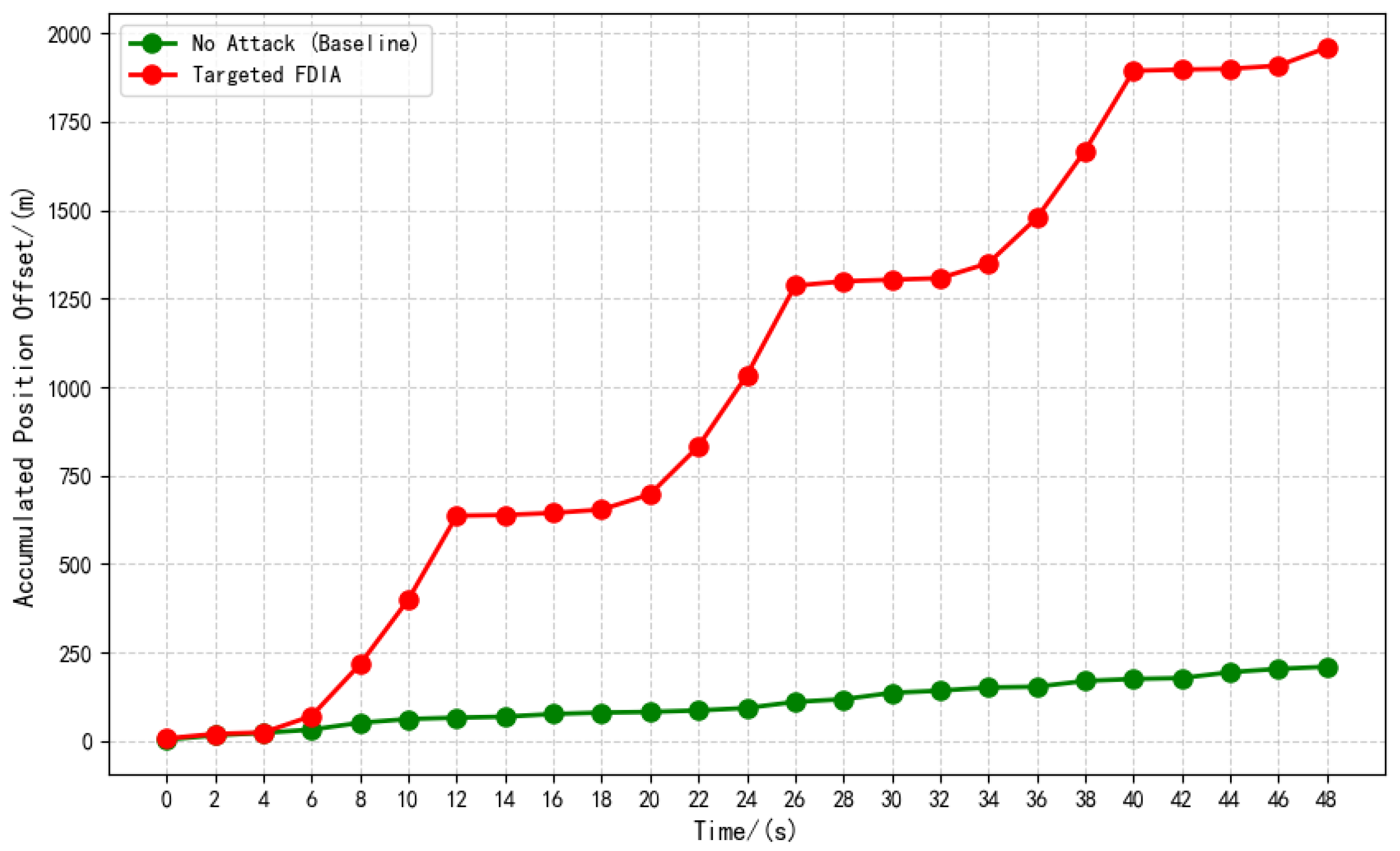

| Experiment | Type | ACPO | AVPO |
|---|---|---|---|
| 1 | No attack | 209.57 | 8.38 |
| 2 | Null value attack | 355.47 | 14.22 |
| 3 | Flip attack | 355.47 | 14.22 |
| Scaling attack (1%) | 1128.72 | 45.15 | |
| 4 | Scaling attack (5%) | 355.47 | 14.22 |
| Scaling attack (50%) | 355.47 | 14.22 | |
| 5 | Offset attack (500 m) | 355.47 | 14.22 |
| Offset attack (50 m) | 852.84 | 34.11 | |
| 6 | The method proposed in this paper | 1958.84 | 78.35 |
| Experiment | Type | ACPO | AVPO |
|---|---|---|---|
| 1 | No attack | 196.75 | 7.87 |
| 2 | Coordinated Strategy 1 | 1989.06 | 79.56 |
| 3 | Coordinated Strategy 2 | 2687.93 | 107.52 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, R.; Zhang, Y.; Li, X.; Ran, J. An Analysis and Simulation of Security Risks in Radar Networks from the Perspective of Cybersecurity. Sensors 2025, 25, 5239. https://doi.org/10.3390/s25175239
Chen R, Zhang Y, Li X, Ran J. An Analysis and Simulation of Security Risks in Radar Networks from the Perspective of Cybersecurity. Sensors. 2025; 25(17):5239. https://doi.org/10.3390/s25175239
Chicago/Turabian StyleChen, Runyang, Yi Zhang, Xiuhe Li, and Jinhe Ran. 2025. "An Analysis and Simulation of Security Risks in Radar Networks from the Perspective of Cybersecurity" Sensors 25, no. 17: 5239. https://doi.org/10.3390/s25175239
APA StyleChen, R., Zhang, Y., Li, X., & Ran, J. (2025). An Analysis and Simulation of Security Risks in Radar Networks from the Perspective of Cybersecurity. Sensors, 25(17), 5239. https://doi.org/10.3390/s25175239





