A Scalable Approach to IoT Interoperability: The Share Pattern
Abstract
1. Introduction
Related Work
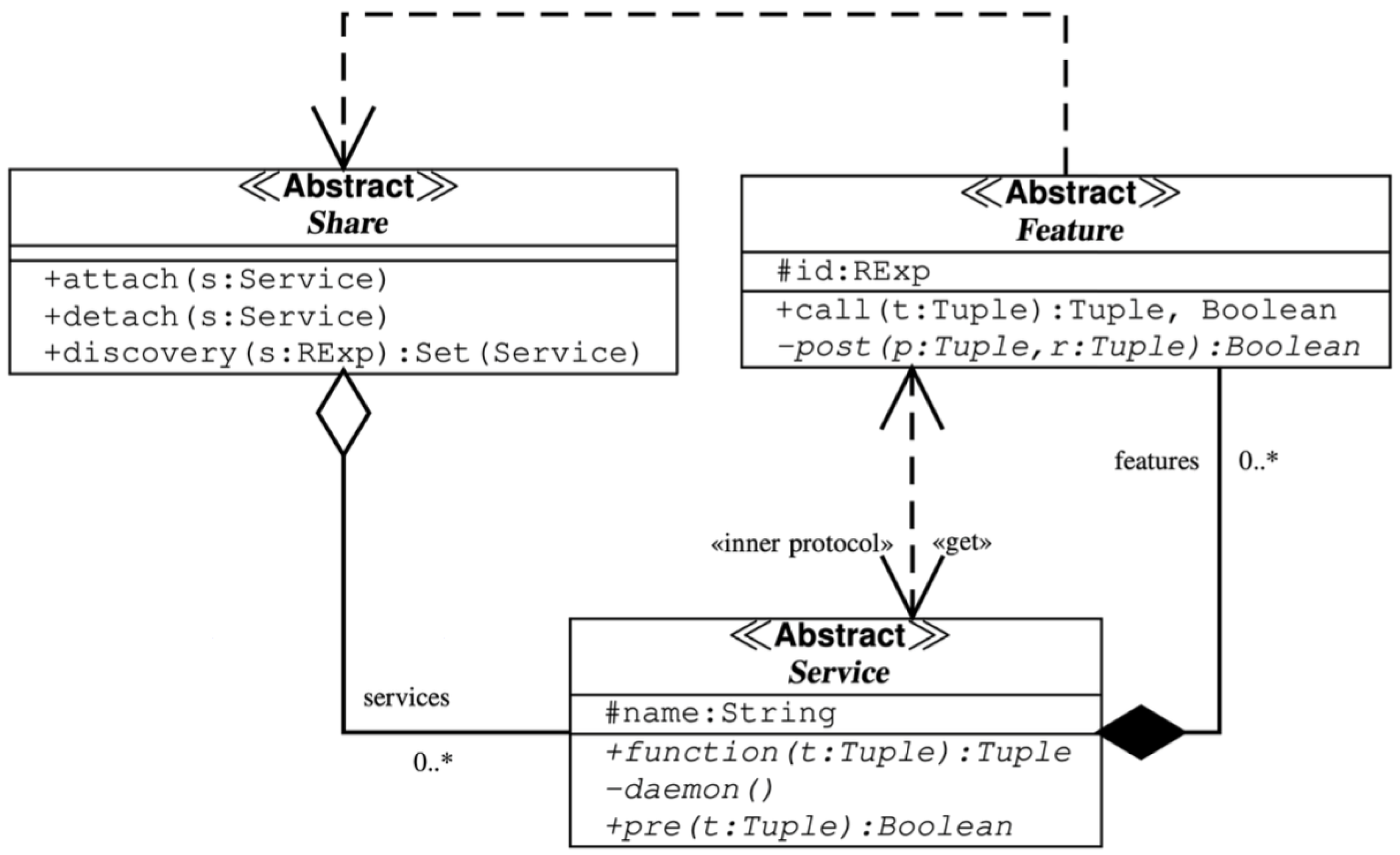
2. Background
- Share;
- Service;
- Feature.
| Listing 1. Share: OCL rules. |
| context Share::attach(s:Service) pre: services->excludes(s) post: services->includes(s) context Share::detach(s:Service) pre: services->includes(s) post: services->excludes(s) context Share::discovery(s:String):Set(Service) post: result = Set(services->select(name.matches(s))) context Share inv: services->asSet() |
| Listing 2. Share: feature OCL rules. |
| context Feature::call(t:Tuple):Boolean, Tuple def: found : Sequence(Service) = select(s : Share.discovery(id) | let s.pre(k:Tuple):Boolean, self.post(v,q):Boolean, s. function(w):r in t.isOclType() = k.isOclType() and t.isOclType() = v.isOclType() and r.isOclType() = q.isOclType() and s.pre(t) and self.post(t,s.function(t))) post: if found->notEmpty() then result = {true, found->first().function(t)} else result = {false, Sequence{}} endif |
- the unique identifier of the Service (i.e., its MIB);
- a LUA function, i.e., the Service function implementation of the client stub;
- a LUA function that implements the daemon, which declares different parts:
- 1.
- a feature with RExp 2.5.8.4.*;
- 2.
- a post condition that specifies the comparison of the temperature and the threshold with precision;
- 3.
- the reception of the parameters and the call of the temp_check function.
- the pre condition of the temperature_alert service, specifying that the temperature must be within the range of −50 to 150, inclusive.
- the unique identifier of the Service (i.e., its MIB);
- a LUA function, i.e., the Service function implementation of the client stub, to enable a connection to the service;
- a LUA function which implements the daemon; here, it is possible to observe the validation of the comparison from the temperature and threshold;
- the pre condition of the temperature_check service, specifying that the temperature must be in the range −50 to 150 with edges included.
| Listing 3. Share: service temperature_alert. |
| temperature_alert = Service.new("2.5.8.3.1", -- declaration service function(temp, threshold) -- function --send temp and threshold to daemon and receive result value end, function() -- daemon local temp_check = Feature.new( "2.5.8.4.*", --RExp function(temp, threshold) return temp >= threshold end --postcondition ) --receive parameters from function using inner protocol local alert, ok = temp_check.call(temp, threshold) --send result value alert to function using inner protocol end, function(temp, threshold) return temp >= -50 and temp <= 150 and threshold > 0 end ) --precondition deviceA = Share.new(myIp) deviceA.attach(temperature_alert) |
| Listing 4. Share: service temperature_check. |
| temperature_check = Service.new("2.5.8.4.1", -- declaration service function() return function(temp, threshold, ip) local tcp = socket.tcp() -- Initialize tcp socket local host, port = ip, 8888 tcp:connect(host, port) tcp:send(temp .. ’,’ .. threshold) local result, status = tcp:receive() -- Get response once tcp:close() -- Close connection return result end end, function() local server = socket.bind("*", 8888) while true do local client = server:accept() local data, err = client:receive() if not err then local temp, threshold = data:match("([^,]+),([^,]+)") temp, threshold = tonumber(temp), tonumber(threshold) if temp and threshold and temp >= threshold then client:send("ALERT: Temperature exceeded threshold!") else client:send("Temperature is within normal range.") end end client:close() -- Close client connection -- No break here to allow continuous operation end end, function(temp, threshold) return temp >= -50 and temp <= 150 and threshold > 0 end ) deviceB = Share.new(Myip) deviceB.attach(temperature_check) |
Sequence Diagram
3. Materials and Methods
3.1. Emulator Implementation
3.2. Structure and Functionalities
| Listing 5. Share: temperature sensor service. |
| -- This Service returns a temperature value with 2 decimal digit precision coTemperatureP2 = coroutine.create( function() local t while true do t = intT + math.random(-100, 100)/100 t = t - t%0.01 --P2 precision local tuple = {} table.insert(tuple, t) coroutine.yield(tuple) end end ) temperatureP2 = Service:new( "temperatureP2", "1.1.2", [[ return function() status, values = coroutine.resume(coTemperatureP2) end ]] , coTemperatureP2, function() return true --Pre-Conditions always satisfied end ) |
| Listing 6. Share: definition of Service class. |
| -- Definition of the Service~class Service = {} Service.__index = Service -- This function implements the constructor of a Service object function Service:new(pMName, pName, pFunction, pDaemon, pPre) return setmetatable({ mName = pMName, -- Mnemonic name name = pName, -- MIB sFunction = pFunction -- Service function daemon = pDaemon -- Service daemon pre = pPre -- Pre-conditions }, Service) end |
| Listing 7. Share: MIB table of emulator. |
| 2.* : Actuators 2.1.* : Temperature 2.1.1.* : Increasing temperature 2.1.1.1.* : Increasing temperature On 2.1.1.1.1 : Increasing temperature On service (Energy Label A) 2.1.1.1.2 : Increasing temperature On service (Energy Label B) 2.1.1.1.3 : Increasing temperature On service (Energy Label C) 2.1.1.2.* : Increasing temperature Off 2.1.1.2.1 : Increasing temperature Off service (Energy Label A) 2.1.1.2.2 : Increasing temperature Off service (Energy Label B) 2.1.1.2.3 : Increasing temperature Off service (Energy Label C) 2.1.2.* : Decreasing temperature 2.1.2.1.* : Decreasing temperature On service 2.1.2.1.1 : Decreasing temperature On service (Energy Label A) 2.1.2.1.2 : Decreasing temperature On service (Energy Label B) 2.1.2.1.3 : Decreasing temperature On service (Energy Label C) 2.1.2.2.* : Decreasing temperature Off service 2.1.2.2.1 : Decreasing temperature Off service (Energy Label A) 2.1.2.2.2 : Decreasing temperature Off service (Energy Label B) 2.1.2.2.3 : Decreasing temperature Off service (Energy Label C) 2.2.* : Humidity 2.2.1.* : Increasing humidity 2.2.1.1.* : Increasing humidity On 2.2.1.1.1 : Increasing humidity On service (Energy Label A) 2.2.1.2.* : Increasing humidity Off 2.2.1.2.1 : Increasing humidity Off service (Energy Label A) 2.2.2.* : Decreasing humidity 2.2.2.1.* : Decreasing humidity On 2.2.2.1.1 : Decreasing humidity On service (Energy Label A) 2.2.2.1.2 : Decreasing humidity On service (Energy Label B) 2.2.2.1.3 : Decreasing humidity On service (Energy Label C) 2.2.2.2.* : Decreasing humidity Off 2.2.2.2.1 : Decreasing humidity Off service (Energy Label A) 2.2.2.2.2 : Decreasing humidity Off service (Energy Label B) 2.2.2.2.3 : Decreasing humidity Off service (Energy Label C) |
| Listing 8. Share: emulator Givoni. |
| 4.* : Givoni 4.1.* : Generic 4.1.1 : Generic On service 4.1.2 : Generic Off service 4.2.* : Efficient 4.2.1 : Efficient On service 4.2.2 : Efficient Off service |
| Listing 9. Share: mathematics services. |
| 3.* : Mathematics 3.1.* : Average 3.1.0 : Average service with an accuracy of zero decimal digit 3.1.1 : Average service with an accuracy of one decimal digit 3.1.2 : Average service with an accuracy of two decimal digits 3.2 : Minimum service 3.3 : Maximum service |
| Listing 10. Share: zones. |
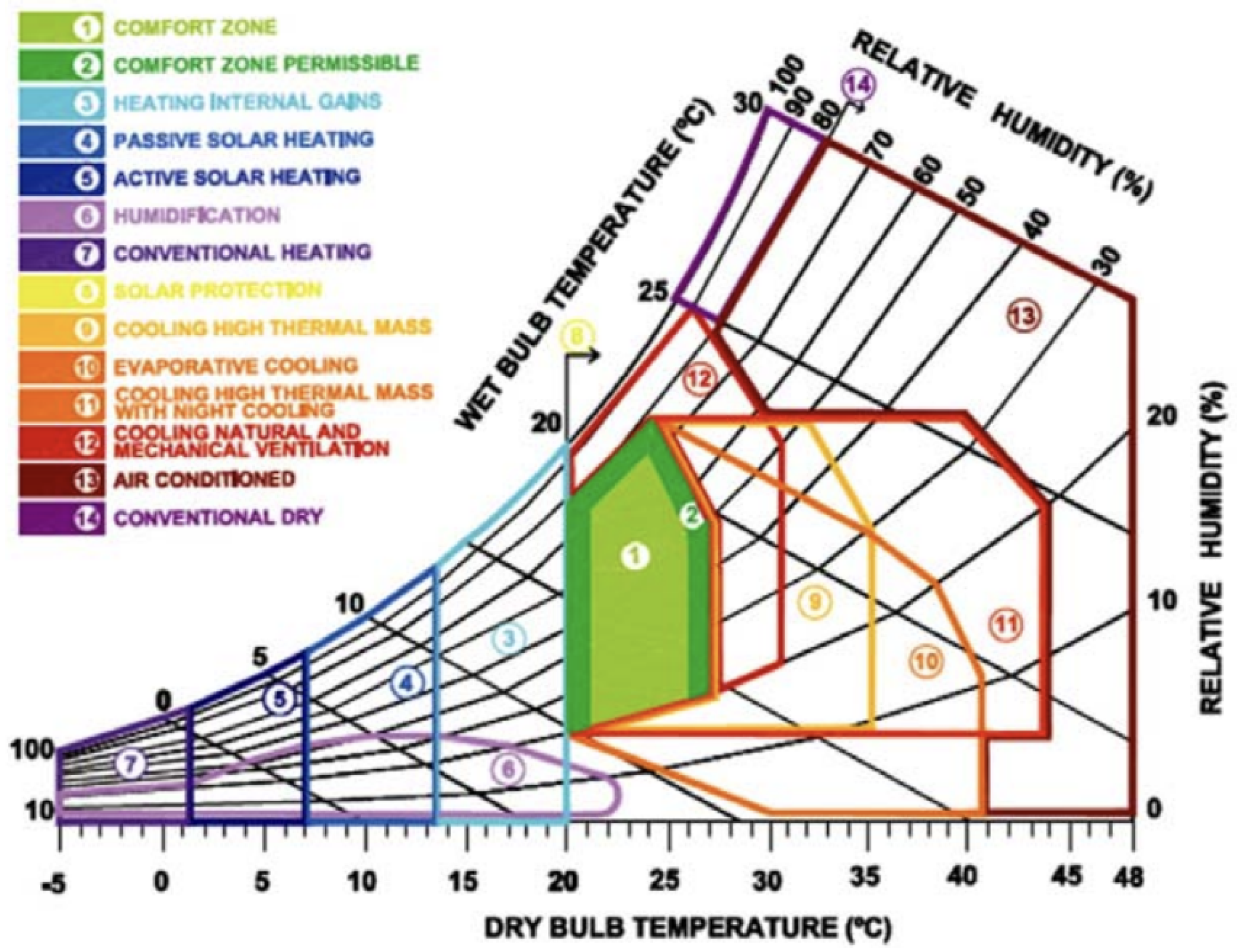
| function aZone (t, h) return (t <= 26 and h <= 20 and h > -10/3*t + 260/3) or (t > 26 and t <= 41 and h <= -2/3*t + 112/3) or (h > -2/3*t + 112/3 and t > 26 and h <= -t + 76 and h <= -35/8*t + 185) end function bZone (t,h) return (t > 41 and h <= 10) or (h > 10 and h > -35/8*t + 185 and h <= -28/17*t + 1774/17 and h <= 80 and t > 33) or (t <= 33 and h > - 35/8*t + 185 and h <= - 10/3*t + 160) or (h > -t + 76 and h <= -35/8*t + 185 and h > -15*t +440 and h<= -5*t + 200) end function cZone (t,h) return (h > 22 and t > 20 and t <= 33 and h > -10/3*t + 160) or (h > 22 and t > 33 and h > -28/17*t + 1774/17) or (t > 25.8 and t < 26 and h> 71 and h < 72.1) end function dZone (t,h) return h > 80 and h > -5*t + 180 and h <= -5*t + 200 and t > 16 and t < 24 end function eZone (t, h) return t <= 20 and h <= -5*t + 180 and h > -2*t +60 |
3.3. Formal Specification with OCL
| Listing 11. Share OCL constraints: attach(s:Service). |
| context Share::attach(s:Service) pre: services->excludes(s) pre liveness:s.features->forAll(f | discovery([f.id](http://f.id/)).notEmpty()) pre safeness: s.fratures->closure(collect(discovery(id).fratures)->excludes(s) post: services->includes(s) |
| Listing 12. Share OCL constraints: detach(s:Service). |
| context Share::detach(s:Service) pre consistency: Share::allInstances().services.features-> forAll(f | discovery([f.id](http://f.id/)) .notEmpty()) post: services->excludes(s) |
4. Results
5. Discussion
6. Conclusions and Future Work
- verify the workload of the individual nodes and the entire system;
- determine the functioning of the system in the presence of failures or the unavailability of devices;
- help in the design of fault-tolerance systems with safeguard causes.
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Internet of Things Forecast. Available online: https://www.ericsson.com/en/mobility-report/internet-of-things-forecast (accessed on 3 March 2025).
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2020, 54, 2787–2805. [Google Scholar] [CrossRef]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L.; Gagliardi, R. Applications of Artificial Intelligence and Machine learning in smart cities. Comput. Commun. 2020, 154, 313–323. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Zahmatkesh, H.; Mostarda, L. Quantifying uncertainty in internet of medical things and big-data services using intelligence and deep learning. IEEE Access 2019, 7, 115749–115759. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing (MCC ’12), Helsinki, Finland, 17 August 2012; Association for Computing Machinery: New York, NY, USA, 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Pourreza, H.; Graham, P. On the Fly Service Composition for Local Interaction Environments. In Proceedings of the Fourth Annual IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOMW’06), Pisa, Italy, 13–17 March 2006; IEEE: Piscataway, NJ, USA, 2006; pp. 6–399. [Google Scholar] [CrossRef]
- Zhao, Q.; Huang, G.; Huang, J.; Liu, X.; Mei, H. A Web-Based Mashup Environment for On-the-Fly Service Composition. In Proceedings of the 2008 IEEE International Symposium on Service-Oriented System Engineering, Jhongli, Taiwan, 18–19 December 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 32–37. [Google Scholar] [CrossRef]
- Baldoni, R.; Di Ciccio, C.; Mecella, M.; Patrizi, F.; Querzoni, L.; Santucci, G.; Dustdar, S.; Li, F.; Truong, H.-L.; Albornos, L.; et al. An Embedded Middleware Platform for Pervasive and Immersive Environments for-All. In Proceedings of the 2009 6th IEEE Annual Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks Workshops, Rome, Italy, 22–26 June 2009; University of Groningen, Johann Bernoulli Institute for Mathematics and Computer Science: Groningen, The Netherlands, 2009. ISBN 9781424439386. [Google Scholar] [CrossRef]
- Booth, D.; Liu, C.K. Web Services Description Language (WSDL) Version 2.0 Part 0: Primer. 2007. Available online: http://www.w3.org/TR/wsdl20-primer (accessed on 26 June 2007).
- Chinnici, R.; Moreau, J.-J.; Ryman, A.; Weerawarana, S. Web Services Description Language (WSDL) Version 2.0 Part 1: Core Language. 2007. Available online: http://www.w3.org/TR/wsdl20 (accessed on 26 June 2007).
- Chinnici, R.; Haas, H.; Lewis, A.A.; Moreau, J.-J.; Orchard, D.; Weerawarana, S. Web Services Description Language (WSDL) Version 2.0 Part 2: Adjuncts. 2007. Available online: http://www.w3.org/TR/wsdl20-adjuncts (accessed on 26 June 2007).
- Culmone, R.; Cacciagrano, D.; Al-Turjman, F.; Mostarda, L. Share: A Design Pattern for Dynamic Composition of IoT Services. In Forthcoming Networks and Sustainability in the IoT Era; Ever, E., Al-Turjman, F., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 144–156. [Google Scholar] [CrossRef]
- Meyer, B. Applying ‘design by contract’. Computer 1992, 25, 40–51. [Google Scholar] [CrossRef]
- Porting Lua Interpreter on Microcontrollers. Available online: https://github.com/elua/elua?tab=readme-ov-file (accessed on 10 May 2025).
- Marchetti, E.; Bartolini, C.; Bertolino, A.; Polini, A. WS-TAXI: A WSDL-Based Testing Tool for Web Services. In Proceedings of the 2009 International Conference on Software Testing Verification and Validation (ICST), Denver, CO, USA, 1–4 April 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 326–335. [Google Scholar] [CrossRef]
- Cacciagrano, D.; Corradini, F.; Culmone, R.; Vito, L. Dynamic Constraint-Based Invocation of Web Services. In Web Services and Formal Methods, Proceedings of the Third International Workshop, WS-FM 2006, Vienna, Austria, 8–9 September 2006; Proceedings; Springer: Berlin/Heidelberg, Germany, 2006; pp. 138–147. [Google Scholar] [CrossRef]
- Cacciagrano, D.; Corradini, F.; Culmone, R.; Tesei, L.; Vito, L. A Model-Prover for Constrained Dynamic Conversations. In Proceedings of the iiWAS’2008—The Tenth International Conference on Information Integration and Web-Based Applications Services, Linz, Austria, 24–26 November 2008; ACM: New York, NY, USA, 2008; pp. 630–633. [Google Scholar] [CrossRef]
- Cacciagrano, D.; Corradini, F.; Culmone, R.; Vito, L. Constraint-Based Dynamic Conversations. In Proceedings of the The Fifth International Conference on Networking and Services (ICNS 2009), Valencia, Spain, 20–25 April 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 7–12. [Google Scholar] [CrossRef]
- Barnett, M.; Leino, R. Weakest-Precondition of Unstructured Programs. In Proceedings of the 6th ACM SIGPLAN-SIGSOFT Workshop on Program Analysis for Software Tools and Engineering (PASTE ’05), Lisbon, Portugal, 5–6 September 2005; ACM Press: New York, NY, USA, 2005; pp. 82–87, ISBN 1-59593-239-9. [Google Scholar]
- de Moura, L.; Bjørner, N. Z3: An Efficient SMT Solver. In Tools and Algorithms for the Construction and Analysis of Systems; Ramakrishnan, C.R., Rehof, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 337–340. ISBN 978-3-540-78800-3. [Google Scholar]
- Tavares, A.L.C.; Valente, M.T. A Gentle Introduction to OSGi. ACM SIGSOFT Softw. Eng. Notes 2008, 33, 1–5. [Google Scholar] [CrossRef]
- Whitecat ESP32 N1 Board. 2019. Available online: https://whitecatboard.org/lorawan-deployment-in-cornella/ (accessed on 15 April 2025).
- Washizaki, H.; Ogata, S.; Hazeyama, A.; Okubo, T.; Fernandez, E.B.; Yoshioka, N. Landscape of Architecture and Design Patterns for IoT Systems. IEEE Internet Things J. 2020, 7, 10091–10101. [Google Scholar] [CrossRef]
- Gamma, E.; Helm, R.; Johnson, R.; Vlissides, J. Design Patterns: Elements of Reusable Object-Oriented Software. Gang of Four; Addison-Wesley Professional: Boston, MA, USA, 1994; ISBN 10 0201633612/13 978-0201633610. [Google Scholar]
- Konrad, S.; Cheng, B. Requirements Patterns for Embedded Systems. In Proceedings of the IEEE International Conference on Requirements Engineering, Essen, Germany, 9–13 September 2002; pp. 127–136. [Google Scholar] [CrossRef]
- Tampouratzis, N.; Papaefstathiou, I.; Nikitakis, A.; Brokalakis, A.; Andrianakis, S.; Dollas, A.; Marcon, M.; Plebani, E. A Novel, Highly Integrated Simulator for Parallel and Distributed Systems. ACM Trans. Archit. Code Optim. 2020, 17, 1–28. [Google Scholar] [CrossRef]
- Xu, C.; Du, X.; Li, X.; Tu, Y.; Li, L.; Jin, X.; Xia, C. 5G-Based Industrial Wireless Controller: Protocol Adaptation, Prototype Development, and Experimental Evaluation. Actuators 2023, 12, 49. [Google Scholar] [CrossRef]
- Xu, C.; Yu, H.; Jin, X.; Xia, C.; Li, D.; Zeng, P. Industrial Internet for intelligent manufacturing: Past, present, and future. Front. Inf. Technol. Electron. Eng. 2024, 25, 1173–1192. [Google Scholar] [CrossRef]
- Structure of Management Information (SMI) Numbers (MIB Module Registrations). 2020. Available online: https://www.iana.org/ (accessed on 15 April 2025).
- Pop, P.; Eles, P.; Peng, Z. Analysis and Synthesis of Distributed Real-Time Embedded Systems; Springer Science & Business Media: New York, NY, USA, 2004. [Google Scholar]
- Dwivedi, A.K.; Vyas, O.P. An Exploratory Study of Experimental Tools for Wireless Sensor Networks. Wirel. Sens. Netw. 2011, 3, 215–240. [Google Scholar] [CrossRef]
- Programming in Lua. Roberto Ierusalimschy. 2003. Available online: https://www.lua.org/pil/contents.html (accessed on 15 April 2025).
- Givoni, B. Climate Considerations in Building and Urban Design; Van Nostrand Reinhold: New York, NY, USA, 1998. [Google Scholar]
- Ierusalimschy, R.; Figueiredo, L.H.; Celes, W. The implementation of Lua 5.0. J. Univers. Comput. Sci. 2005, 11, 1159–1176. [Google Scholar]
- European Union. Regulation (EU) 2017/1369 of the European Parliament and of the Council of 4 July 2017 Setting a Framework for Energy Labelling and Repealing Directive 2010/30/EU. 2017. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:32017R1369 (accessed on 15 April 2025).
- European Union. Consolidated Text: Regulation (EU) 2017/1369 of the European Parliament and of the Council of 4 July 2017 setting a framework for energy labelling and repealing Directive 2010/30/EU. 2021. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=LEGISSUM:regulation (accessed on 27 July 2025).
- Warmer, J.; Kleppe, A. The Object Constraint Language: Precise Modeling with UML; Addison-Wesley: Boston, MA, USA, 1999. [Google Scholar]
- Object Management Group. Object Constraint Language (OCL), Version 2.3.1; OMG Document Formal/2012-01-01. 2012. Available online: https://www.omg.org/spec/OCL/2.3.1/ (accessed on 30 April 2025).
- ISO/IEC 19507:2012; Information Technology—Object Management Group Object Constraint Language (OCL). ISO/IEC: Geneva, Switzerland, 2012.
- OpenWrt. Available online: https://openwrt.org/ (accessed on 27 July 2025).


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Petracci, R.; Culmone, R. A Scalable Approach to IoT Interoperability: The Share Pattern. Sensors 2025, 25, 4701. https://doi.org/10.3390/s25154701
Petracci R, Culmone R. A Scalable Approach to IoT Interoperability: The Share Pattern. Sensors. 2025; 25(15):4701. https://doi.org/10.3390/s25154701
Chicago/Turabian StylePetracci, Riccardo, and Rosario Culmone. 2025. "A Scalable Approach to IoT Interoperability: The Share Pattern" Sensors 25, no. 15: 4701. https://doi.org/10.3390/s25154701
APA StylePetracci, R., & Culmone, R. (2025). A Scalable Approach to IoT Interoperability: The Share Pattern. Sensors, 25(15), 4701. https://doi.org/10.3390/s25154701






