Near-Field Microwave Sensing for Chip-Level Tamper Detection
Abstract
1. Introduction
2. Background
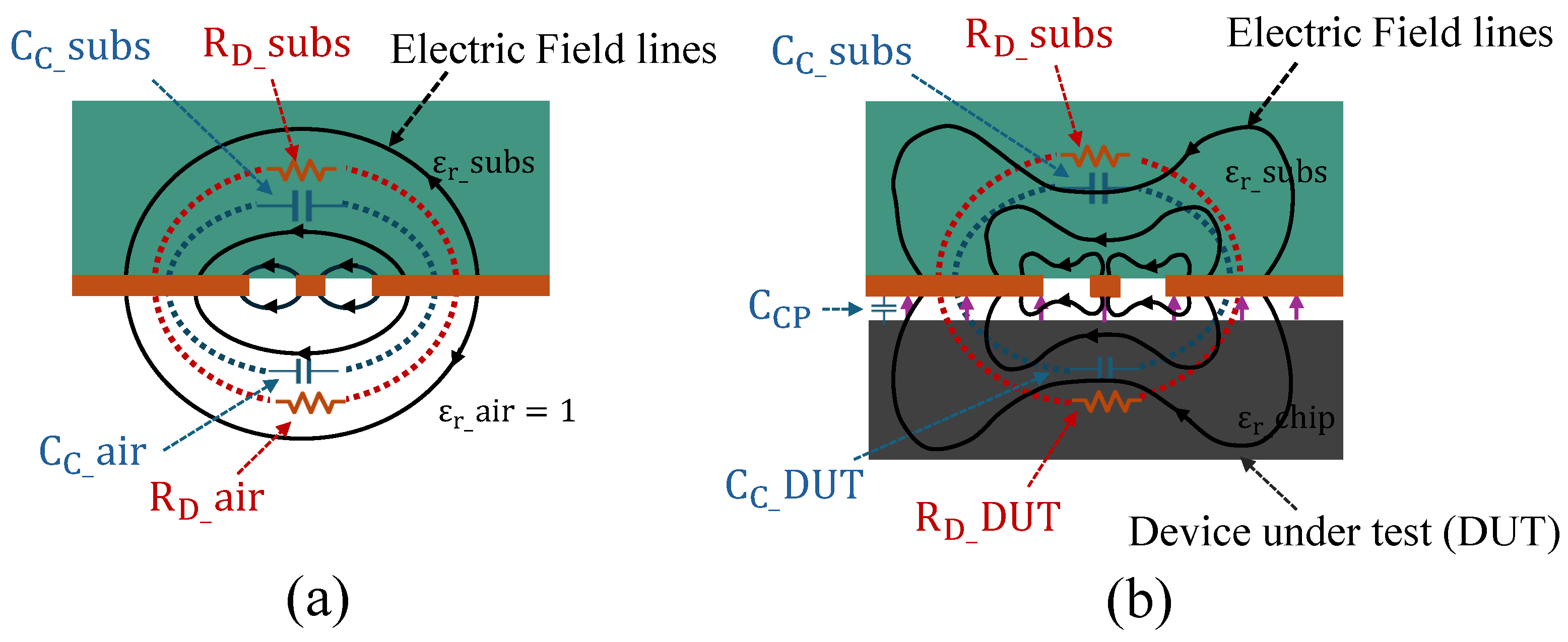
2.1. CSRR-Based Sensor
2.2. Electromagnetic Behavior of CSRR Structures
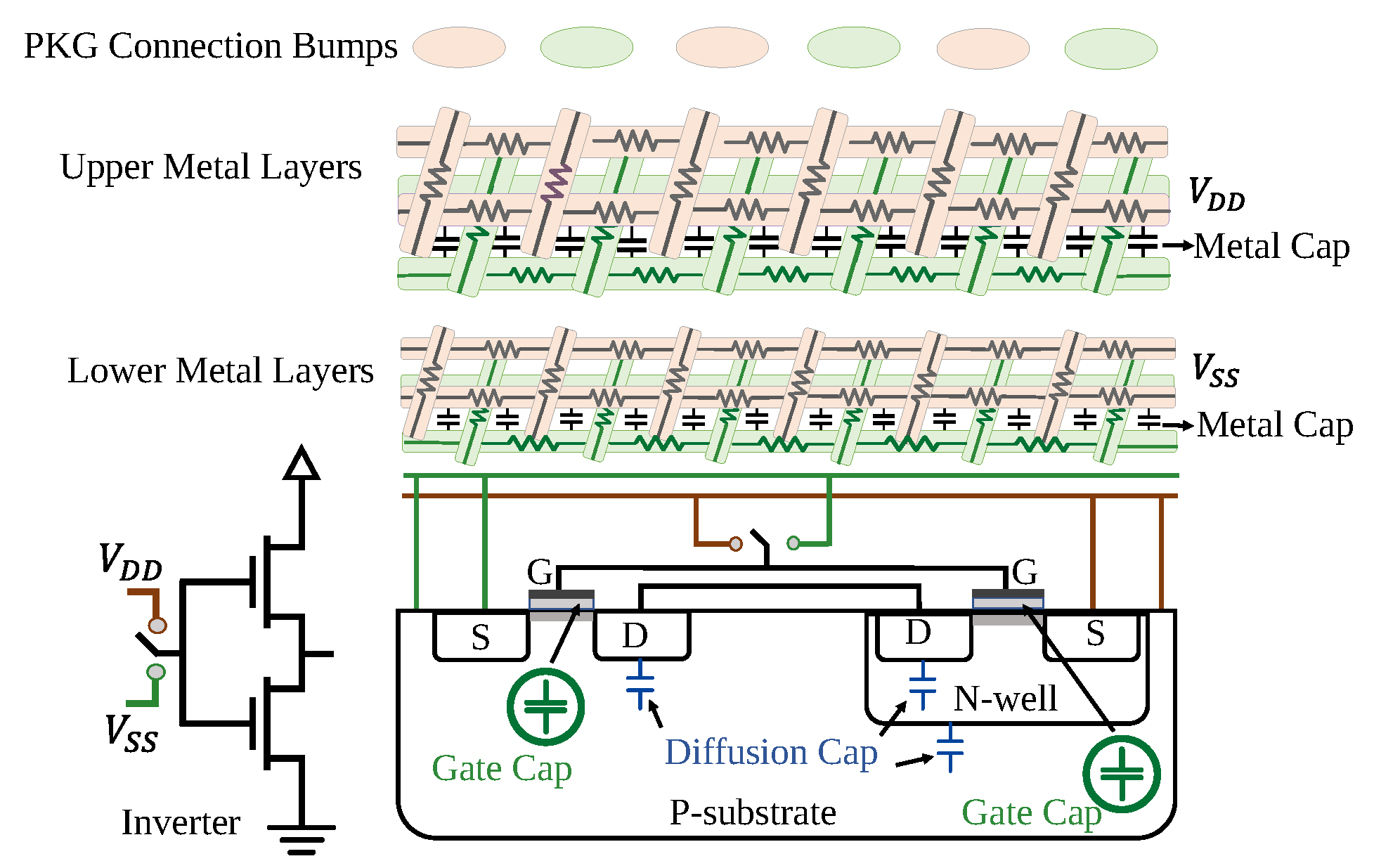
2.3. Sources and Mechanisms of Chip PDN Impedance Variation
2.4. Electrostatic Behavior in Clock-Halted FPGAs
3. Methodology
3.1. Threat Model
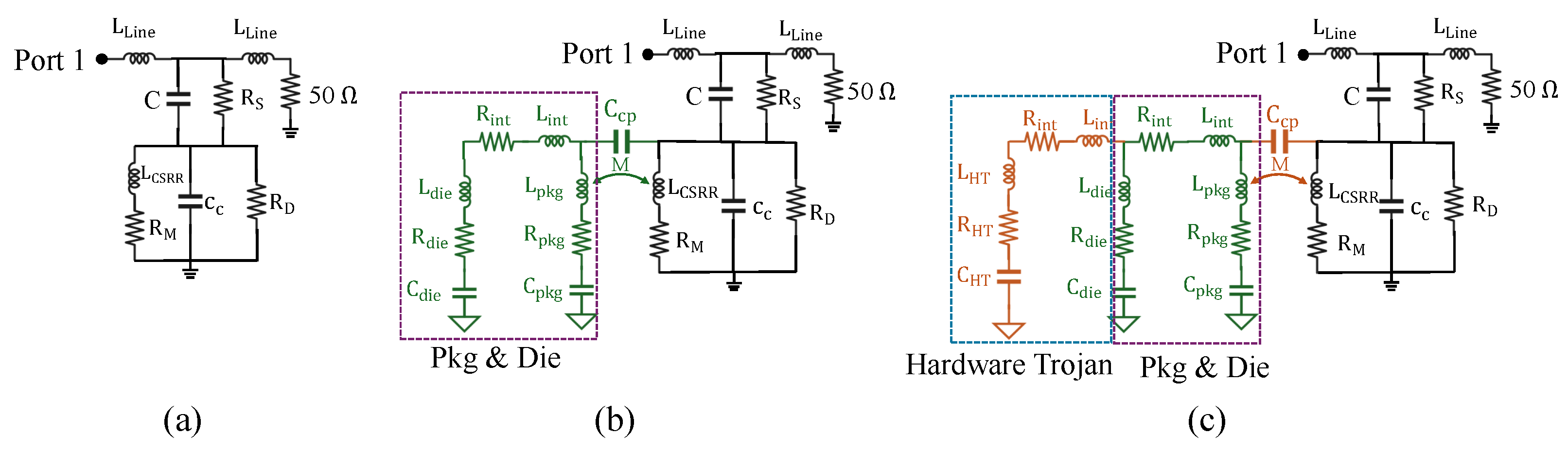
3.2. Tamper Detection Using CSRR Sensors
3.3. Tamper Detection Metric
4. Experimental Setup
4.1. Simulation Setup
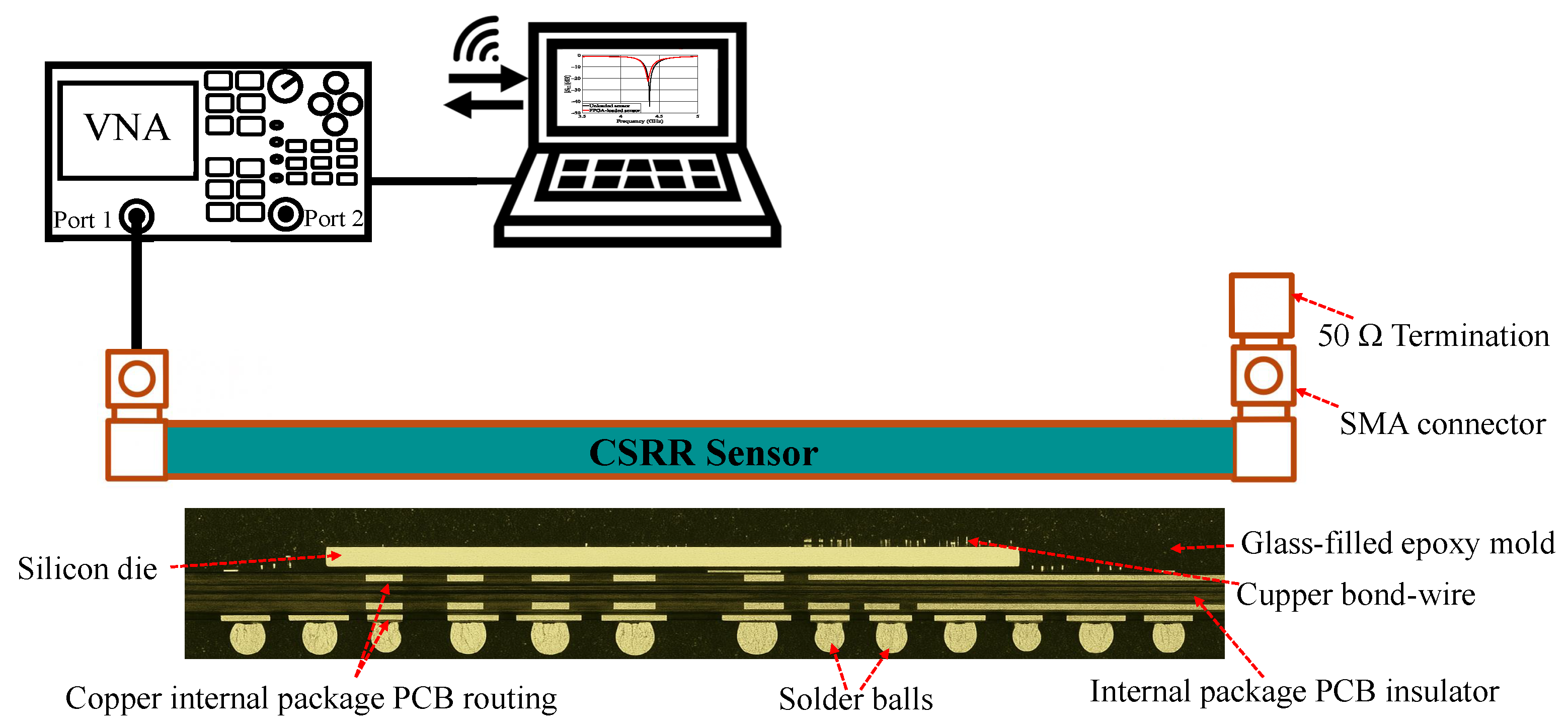
4.2. Device Under Test (DUT)
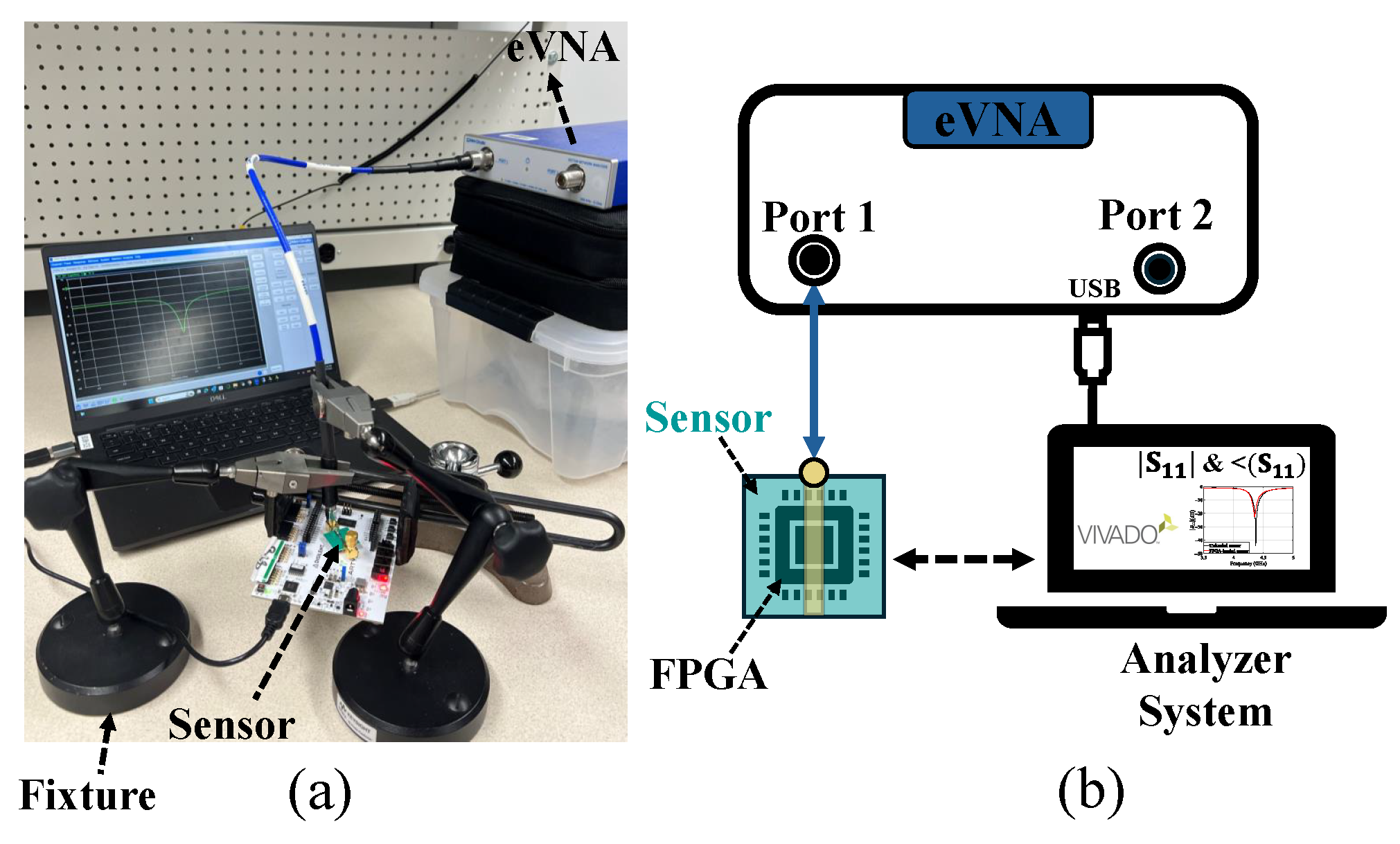
4.3. Measurement Setup
5. Results
5.1. Case Studies of Tampering Detection Using CSRR Sensor
5.1.1. Baseline Experiment: Effect of Passive DUT on the Sensor’s Behavior
5.1.2. Case Study 1: Influence of FPGA State on Sensor Impedance Characteristics
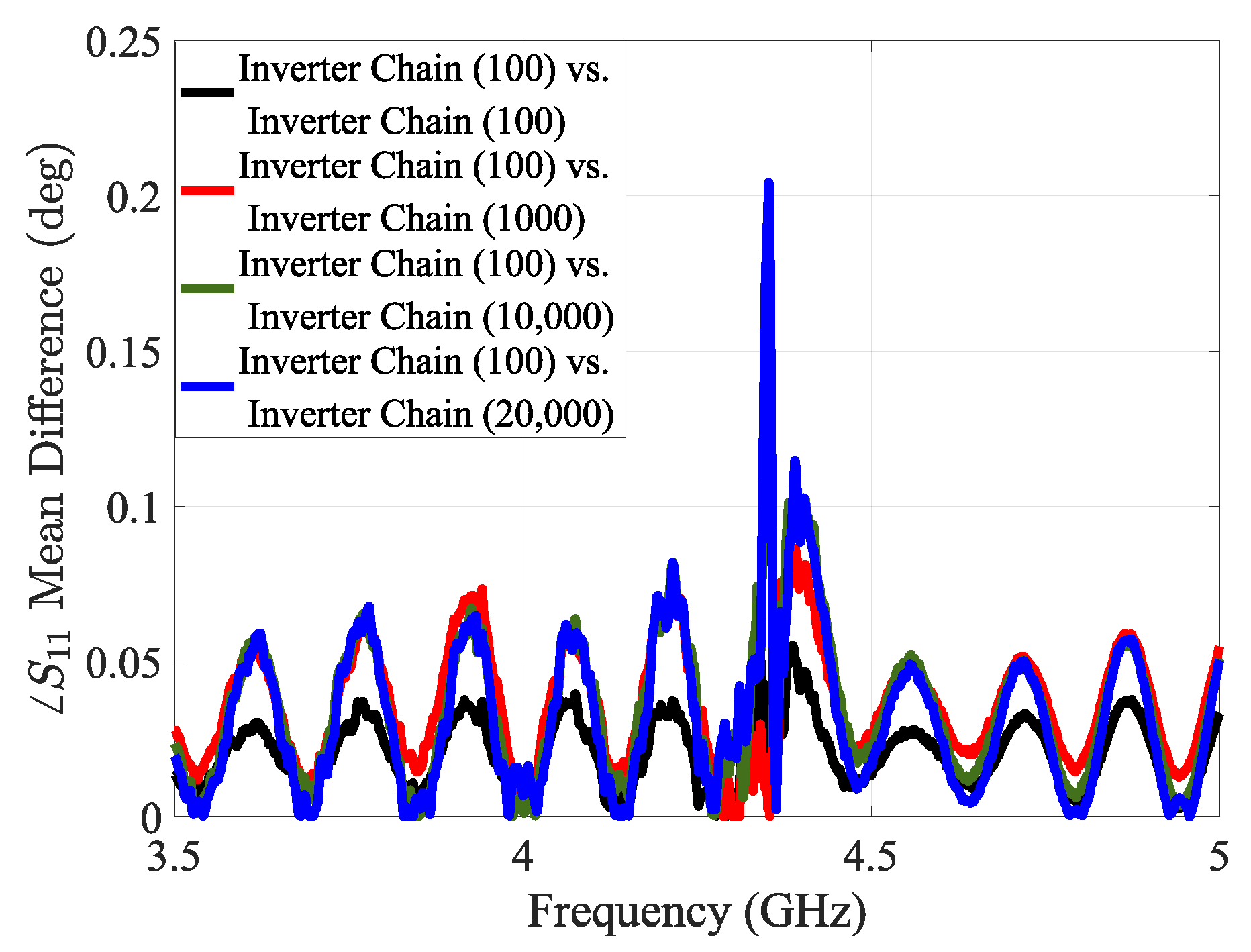
5.1.3. Case Study 2: Influence of Circuit Size on Sensor Impedance Characteristics
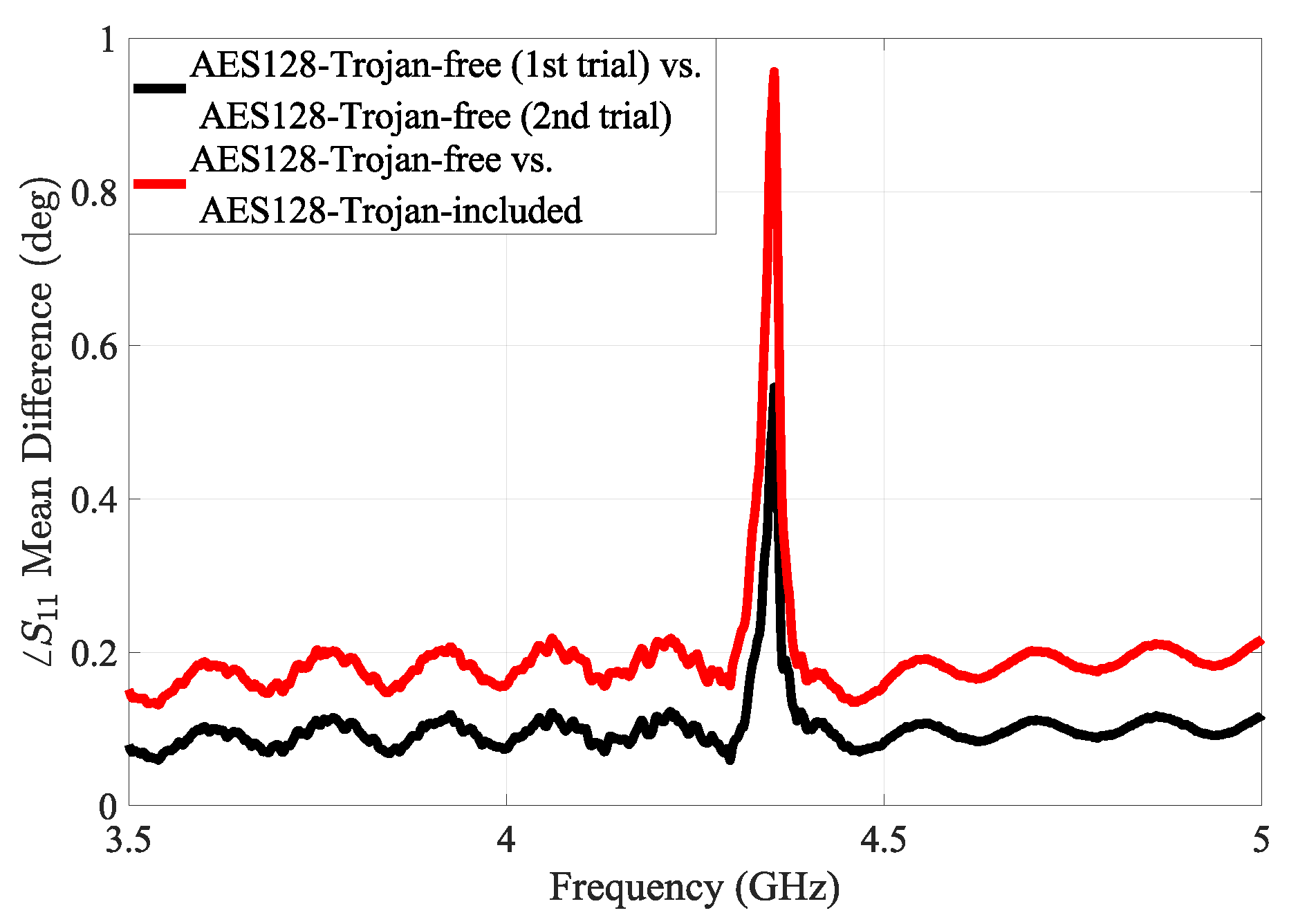
5.1.4. Case Study 3: Hardware Trojan Detection
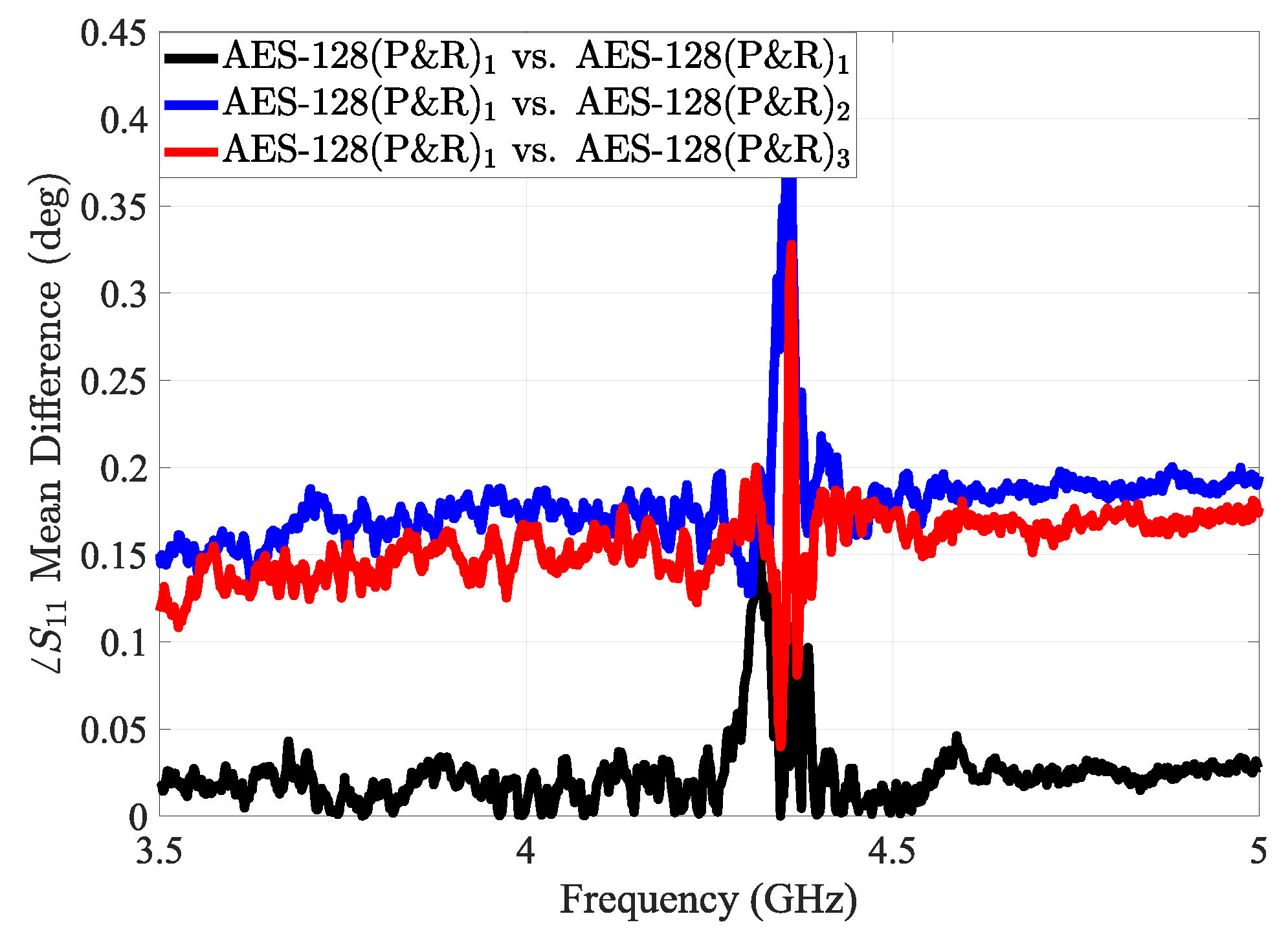
5.1.5. Case Study 4: Effect of Changing the Placement and Routing
6. Discussion and Future Work
6.1. Performance Comparison with a Commercial Probe
6.2. Accuracy and Sensitivity Considerations of the CSRR Sensor
6.3. Future Works
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Nguyen, L.N.; Cheng, C.L.; Prvulovic, M.; Zajić, A. Creating a backscattering side channel to enable detection of dormant hardware trojans. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 1561–1574. [Google Scholar] [CrossRef]
- Adibelli, S.; Juyal, P.; Nguyen, L.N.; Prvulovic, M.; Zajic, A. Near-field backscattering-based sensing for hardware trojan detection. IEEE Trans. Antennas Propag. 2020, 68, 8082–8090. [Google Scholar] [CrossRef]
- Werner, F.T.; Yilmaz, B.B.; Prvulovic, M.; Zajić, A. Leveraging EM side-channels for recognizing components on a motherboard. IEEE Trans. Electromagn. Compat. 2020, 63, 502–515. [Google Scholar] [CrossRef]
- Werner, F.T.; Prvulovic, M.; Zajić, A. Detection of recycled ICs using backscattering side-channel analysis. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2022, 30, 1244–1255. [Google Scholar] [CrossRef]
- Mosavirik, T.; Ganji, F.; Schaumont, P.; Tajik, S. Scatterverif: Verification of electronic boards using reflection response of power distribution network. ACM J. Emerg. Technol. Comput. Syst. (JETC) 2022, 18, 1–24. [Google Scholar] [CrossRef]
- Zhu, H.; Shan, H.; Sullivan, D.; Guo, X.; Jin, Y.; Zhang, X. PDNPulse: Sensing PCB anomaly with the intrinsic power delivery network. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3590–3605. [Google Scholar] [CrossRef]
- Safa, M.S.; Mosavirik, T.; Tajik, S. Counterfeit Chip Detection using Scattering Parameter Analysis. In Proceedings of the 2023 26th International Symposium on Design and Diagnostics of Electronic Circuits and Systems (DDECS), Tallinn, Estonia, 3–5 May 2023; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar]
- Mosavirik, T.; Schaumont, P.; Tajik, S. Impedanceverif: On-chip impedance sensing for system-level tampering detection. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2022, 2023, 301–325. [Google Scholar] [CrossRef]
- Vashistha, N.; Lu, H.; Shi, Q.; Rahman, M.T.; Shen, H.; Woodard, D.L.; Asadizanjani, N.; Tehranipoor, M. Trojan scanner: Detecting hardware trojans with rapid SEM imaging combined with image processing and machine learning. In Proceedings of the International Symposium for Testing and Failure Analysis, Phoenix, AZ, USA, 28 October–1 November 2018; ASM International: Detroit, MI, USA, 2018; Volume 81009, pp. 256–265. [Google Scholar]
- Krachenfels, T.; Seifert, J.P.; Tajik, S. Trojan awakener: Detecting dormant malicious hardware using laser logic state imaging (extended version). J. Cryptogr. Eng. 2023, 13, 485–499. [Google Scholar] [CrossRef]
- Courbon, F.; Loubet-Moundi, P.; Fournier, J.J.; Tria, A. A high efficiency hardware trojan detection technique based on fast SEM imaging. In Proceedings of the 2015 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 788–793. [Google Scholar]
- Agrawal, D.; Baktir, S.; Karakoyunlu, D.; Rohatgi, P.; Sunar, B. Trojan detection using IC fingerprinting. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 296–310. [Google Scholar]
- Li, J.; Lach, J. At-speed delay characterization for IC authentication and Trojan horse detection. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, CA, USA, 9 June 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 8–14. [Google Scholar]
- He, J.; Ma, H.; Liu, Y.; Zhao, Y. Golden chip-free trojan detection leveraging trojan trigger’s side-channel fingerprinting. ACM Trans. Embed. Comput. Syst. (TECS) 2020, 20, 1–18. [Google Scholar] [CrossRef]
- Cha, B.; Gupta, S.K. Trojan detection via delay measurements: A new approach to select paths and vectors to maximize effectiveness and minimize cost. In Proceedings of the 2013 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 19–22 March 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1265–1270. [Google Scholar]
- IOActive. Field-Programmable Chips (FPGAs) in Critical Applications: What Are the Risks? 2020. Available online: https://ioactive.com/field-programmable-chips-fpgas-in-critical-applications-what-are-the-risks/ (accessed on 22 May 2025).
- Saadat-Safa, M.; Nayyeri, V.; Khanjarian, M.; Soleimani, M.; Ramahi, O.M. A CSRR-based sensor for full characterization of magneto-dielectric materials. IEEE Trans. Microw. Theory Tech. 2019, 67, 806–814. [Google Scholar] [CrossRef]
- Liu, Z.; Xiao, G.; Zhu, L. Triple-mode bandpass filters on CSRR-loaded substrate integrated waveguide cavities. IEEE Trans. Compon. Packag. Manuf. Technol. 2016, 6, 1099–1105. [Google Scholar] [CrossRef]
- Bahrami, H.; Hakkak, M.; Pirhadi, A. Analysis and design of highly compact bandpass waveguide filter using complementary split ring resonators (CSRR). Prog. Electromagn. Res. 2008, 80, 107–122. [Google Scholar] [CrossRef]
- Omer, A.E.; Shaker, G.; Safavi-Naeini, S.; Kokabi, H.; Alquié, G.; Deshours, F.; Shubair, R.M. Low-cost portable microwave sensor for non-invasive monitoring of blood glucose level: Novel design utilizing a four-cell CSRR hexagonal configuration. Sci. Rep. 2020, 10, 15200. [Google Scholar] [CrossRef] [PubMed]
- Omer, A.E.; Shaker, G.; Safavi-Naeini, S.; Alquié, G.; Deshours, F.; Kokabi, H.; Shubair, R.M. Non-invasive real-time monitoring of glucose level using novel microwave biosensor based on triple-pole CSRR. IEEE Trans. Biomed. Circuits Syst. 2020, 14, 1407–1420. [Google Scholar] [CrossRef] [PubMed]
- Hannachi, C.; Deshours, F.; Alquie, G.; Kokabi, H. Assessment of finger fat pad effect on CSRR-based sensor scattering parameters for non-invasive blood glucose level detection. Sensors 2023, 23, 473. [Google Scholar] [CrossRef]
- Verma, A.; Tiwari, N.K.; Akhtar, M. Soil moisture detection using CSRR based submersible RF sensor. In Proceedings of the 2018 3rd International Conference on Microwave and Photonics (ICMAP), Dhanbad, India, 9–11 February 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–2. [Google Scholar]
- Gan, H.Y.; Zhao, W.S.; Liu, Q.; Wang, D.W.; Dong, L.; Wang, G.; Yin, W.Y. Differential microwave microfluidic sensor based on microstrip complementary split-ring resonator (MCSRR) structure. IEEE Sens. J. 2020, 20, 5876–5884. [Google Scholar] [CrossRef]
- Shaterian, Z.; Horestani, A.K.; Martín, F.; Mrozowski, M. Design of novel highly sensitive sensors for crack detection in metal surfaces: Theoretical foundation and experimental validation. Sci. Rep. 2023, 13, 18540. [Google Scholar] [CrossRef]
- Fan, L.C.; Zhao, W.S.; Wang, D.W.; Liu, Q.; Chen, S.; Wang, G. An ultrahigh sensitivity microwave sensor for microfluidic applications. IEEE Microw. Wirel. Compon. Lett. 2020, 30, 1201–1204. [Google Scholar] [CrossRef]
- Martín, F.; Vélez, P.; Gil, M. Microwave sensors based on resonant elements. Sensors 2020, 20, 3375. [Google Scholar] [CrossRef]
- Han, X.; Liu, K.; Zhang, S.; Peng, P.; Fu, C.; Qiao, L.; Ma, Z. CSRR metamaterial microwave sensor for measuring dielectric constants of solids and liquids. IEEE Sens. J. 2024, 24, 14167–14176. [Google Scholar] [CrossRef]
- Pozar, D.M. Microwave Engineering: Theory and Techniques; John Wiley & Sons: Hoboken, NJ, USA, 2021. [Google Scholar]
- Su, L.; Mata-Contreras, J.; Vélez, P.; Fernández-Prieto, A.; Martín, F. Analytical method to estimate the complex permittivity of oil samples. Sensors 2018, 18, 984. [Google Scholar] [CrossRef]
- Mosavirik, T.; Monfared, S.K.; Safa, M.S.; Tajik, S. Silicon echoes: Non-invasive trojan and tamper detection using frequency-selective impedance analysis. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2023, 2023, 238–261. [Google Scholar] [CrossRef]
- Monfared, S.K.; Mosavirik, T.; Tajik, S. Leakyohm: Secret bits extraction using impedance analysis. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; pp. 1675–1689. [Google Scholar]
- Sarkar, D.; Antar, Y.M. Antenna Mutual Coupling in Near-Field: Insights Using EM Lagrangian Density and Complex Helicity. IEEE Antennas Wirel. Propag. Lett. 2023, 22, 2670–2674. [Google Scholar] [CrossRef]
- Islam, Z.U.; Bermak, A.; Wang, B. A Review of Microstrip Patch Antenna-Based Passive Sensors. Sensors 2024, 24, 6355. [Google Scholar] [CrossRef]
- Ghosh, S.; Basu, B.; Nandi, A.; Das, M. Hand activity classification based on perturbed nearfield radiation and augmented impedance of a wearable textile antenna. Expert Syst. Appl. 2024, 238, 121830. [Google Scholar] [CrossRef]
- Albishi, A.M.; El Badawe, M.K.; Nayyeri, V.; Ramahi, O.M. Enhancing the sensitivity of dielectric sensors with multiple coupled complementary split-ring resonators. IEEE Trans. Microw. Theory Tech. 2020, 68, 4340–4347. [Google Scholar] [CrossRef]
- Albishi, A.M. A novel coupling mechanism for CSRRs as near-field dielectric sensors. Sensors 2022, 22, 3313. [Google Scholar] [CrossRef] [PubMed]
- Keller, R.B. Design for Electromagnetic Compatibility–In a Nutshell; Springer: Berlin/Heidelberg, Germany, 2023. [Google Scholar]
- Mini-Circuits. EVNA-63+ Wideband Amplifier Datasheet. Available online: https://www.minicircuits.com/pdfs/EVNA-63+.pdf (accessed on 24 June 2025).
- Trust-Hub. Hardware Trojan Benchmarks. Available online: https://trust-hub.org/#/home (accessed on 15 January 2025).
- Zhang, F.; Zhang, D.; Peng, Z.; Ren, Q.; Chen, A.; Su, D. Hardware Trojan Recognition based on Radiated Emission Characteristics. In Proceedings of the 2022 Asia-Pacific International Symposium on Electromagnetic Compatibility (APEMC), Beijing, China, 1–4 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 82–84. [Google Scholar]
- Balasch, J.; Gierlichs, B.; Verbauwhede, I. Electromagnetic circuit fingerprints for hardware trojan detection. In Proceedings of the 2015 IEEE International Symposium on Electromagnetic Compatibility (EMC), Dresden, Germany, 16–22 August 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 246–251. [Google Scholar]
- Söll, O.; Korak, T.; Muehlberghuber, M.; Hutter, M. EM-based detection of hardware trojans on FPGAs. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 84–87. [Google Scholar]
- He, J.; Zhao, Y.; Guo, X.; Jin, Y. Hardware trojan detection through chip-free electromagnetic side-channel statistical analysis. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 2939–2948. [Google Scholar] [CrossRef]
- Vutukuru, M.Y.; Muha, A.; Jha, R. On-chip EM sensor arrays for reliability monitoring of integrated circuits. In Proceedings of the NAECON 2023-IEEE National Aerospace and Electronics Conference, Dayton, OH, USA, 28–31 August 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 157–162. [Google Scholar]
- Chen, E.; Kan, J.; Yang, B.Y.; Zhu, J.; Chen, V. Intelligent electromagnetic sensors for non-invasive trojan detection. Sensors 2021, 21, 8288. [Google Scholar] [CrossRef]
- Wang, H.; Panoff, M.; Zhan, Z.; Wang, S.; Bobda, C.; Forte, D. Programmable EM Sensor Array for Golden-Model Free Run-Time Trojan Detection and Localization. In Proceedings of the 2024 Design, Automation & Test in Europe Conference & Exhibition (DATE), Lyon, France, 31 March–2 April 2025; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar]





| Detection Technique (Ref.) | Legacy Compatible | Chip Access/Connection | Complexity and Cost | Trojan Activation |
|---|---|---|---|---|
| [External probe [41]] | Yes | No | Moderate | Yes |
| [External probe [42]] | Yes | No | Moderate | No |
| [External probe [43]] | Yes | No | Moderate | No |
| [External probe [44]] | Yes | No | Moderate | Yes |
| [External Probe [2]] | Yes | No | High | No |
| [On-Chip sensor [45]] | No | Yes | High | Yes |
| [[On-Chip sensor [46]] | No | Yes | High | Yes |
| [[On-Chip sensor [47]] | No | Yes | High | Yes |
| [External sensor [31]] | Yes | Yes | Low | No |
| [This Work] | Yes | No | Low | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saadat Safa, M.; Tajik, S. Near-Field Microwave Sensing for Chip-Level Tamper Detection. Sensors 2025, 25, 4188. https://doi.org/10.3390/s25134188
Saadat Safa M, Tajik S. Near-Field Microwave Sensing for Chip-Level Tamper Detection. Sensors. 2025; 25(13):4188. https://doi.org/10.3390/s25134188
Chicago/Turabian StyleSaadat Safa, Maryam, and Shahin Tajik. 2025. "Near-Field Microwave Sensing for Chip-Level Tamper Detection" Sensors 25, no. 13: 4188. https://doi.org/10.3390/s25134188
APA StyleSaadat Safa, M., & Tajik, S. (2025). Near-Field Microwave Sensing for Chip-Level Tamper Detection. Sensors, 25(13), 4188. https://doi.org/10.3390/s25134188






