Among the DLTs: Holochain for the Security of IoT Distributed Networks—A Review and Conceptual Framework
Abstract
1. Introduction
- A comprehensive review of DLTs in the context of resource-constrained IoT environments, highlighting the motivation for adopting Holochain over traditional blockchain.
- Introduction of the HoloSec framework, a conceptual security solution that integrates Holochain’s agent-centric architecture with advanced cryptographic mechanisms and machine learning for enhanced IoT network protection.
- Implementation of a Holochain-based IoT network tailored to a healthcare scenario, providing practical insights into real-world deployment.
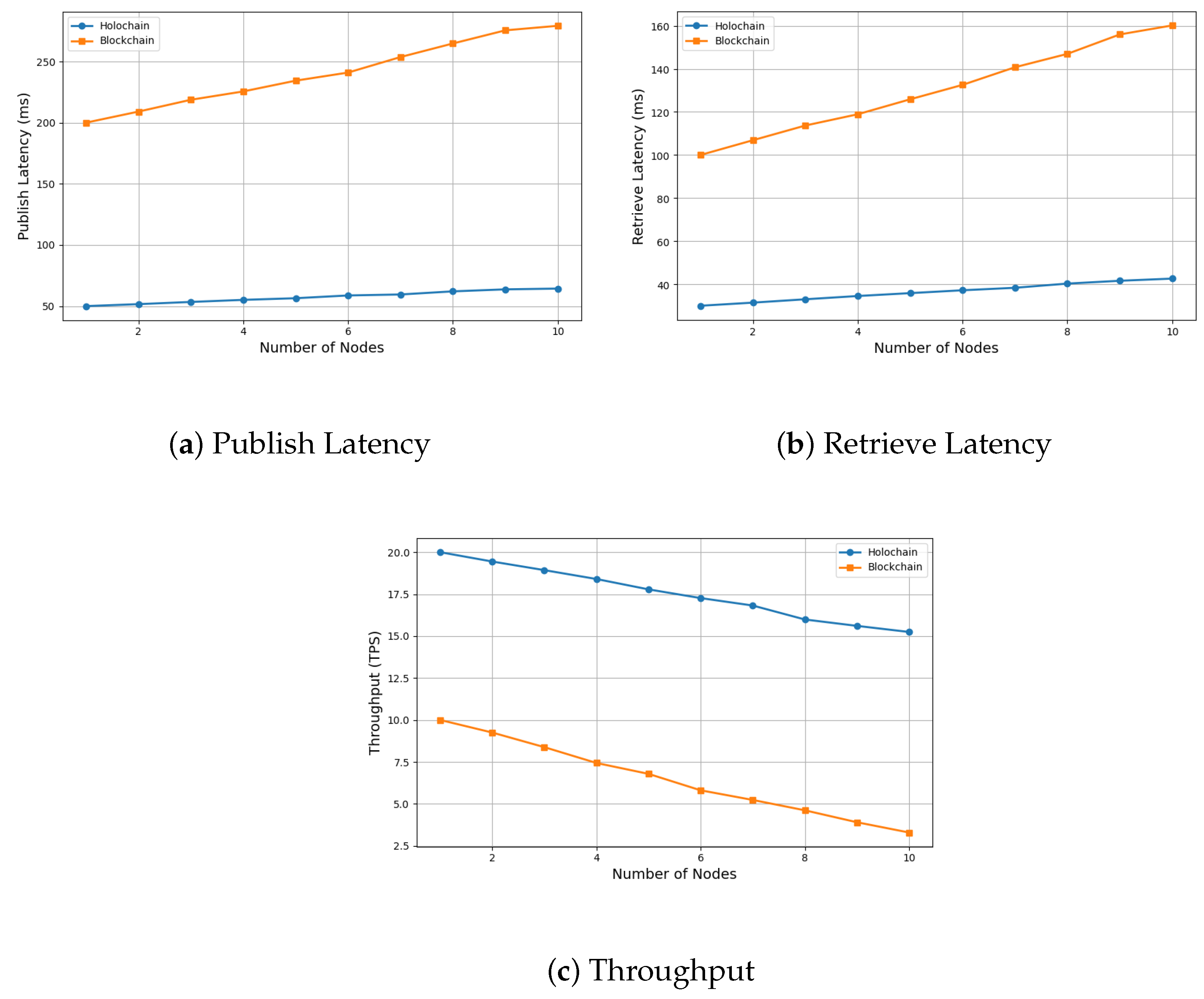
- Empirical performance comparison between Holochain and traditional blockchain, demonstrating Holochain’s superior latency (50 ms publish, 30 ms retrieve) and throughput (20 TPS vs. blockchain’s 10 TPS) in a single-node setup.
- Identification of key research challenges and future directions related to the integration of Holochain in IoT, including scalability, interoperability, security, and regulatory compliance.
2. Literature Review
2.1. Comparison of Holochain with Other DLTs in IoT Networks
2.2. Applications of Holochain in IoT Networks
2.3. Supply Chain Management (SCM)
2.4. Smart Energy and Decentralized Power Grids
2.5. Wireless Sensor Networks (WSNs)
2.6. Social Internet of Vehicles (SIoV)
2.7. Healthcare 4.0
2.8. Smart Cities
2.9. Agriculture
2.10. Industrial IoT (IIoT) Networks
3. HoloSec: Proposed Conceptual Holochain Security Framework for IoT Distributed Networks
3.1. Agent Initialization and Trust Establishment
- Positive behaviors (e.g., timely data sharing, valid transactions) increase the TS.
- Negative behaviors (e.g., delayed responses, invalid data) decrease the TS.
3.2. Data Integrity Verification
- The data hash.
- Metadata (e.g., timestamp, origin ID).
- Signatures from a select group of trusted peer agents based on their TS.
- Retrieves the CoC record from the DHT.
- Validates the signatures using the public keys of the originating and peer agents.
- Recomputes the hash of the received data and compares it with the hash in the CoC record.
3.3. Secure Communication and Authentication
- The sender encrypts the data using the recipient’s public key (e.g., RSA or ECC).
- The sender signs the encrypted data using its private key.
- The recipient decrypts the data using its private key and verifies the sender’s signature using the sender’s public key.
3.4. Anomaly Detection and Response
- Logs the incident immutably on the global DHT to ensure transparency and traceability.
- Adjusts the agent’s TS in an adaptive manner, proportional to the severity of anomalous behavior.
- Initiates predefined security actions, including isolating affected agents, notifying stakeholders, and activating automated recovery workflows.
- Employs key rotation to revoke potentially compromised keys and replace them with new cryptographic pairs. This process not only re-establishes secure communication but also enforces access control by preventing further use of the invalidated credentials.
3.5. Continuous Monitoring and Adaptation
- Agents with consistently high TS values are granted additional privileges (e.g., access to sensitive data).
- Agents with low TS values are subjected to stricter security protocols (e.g., additional authentication steps).
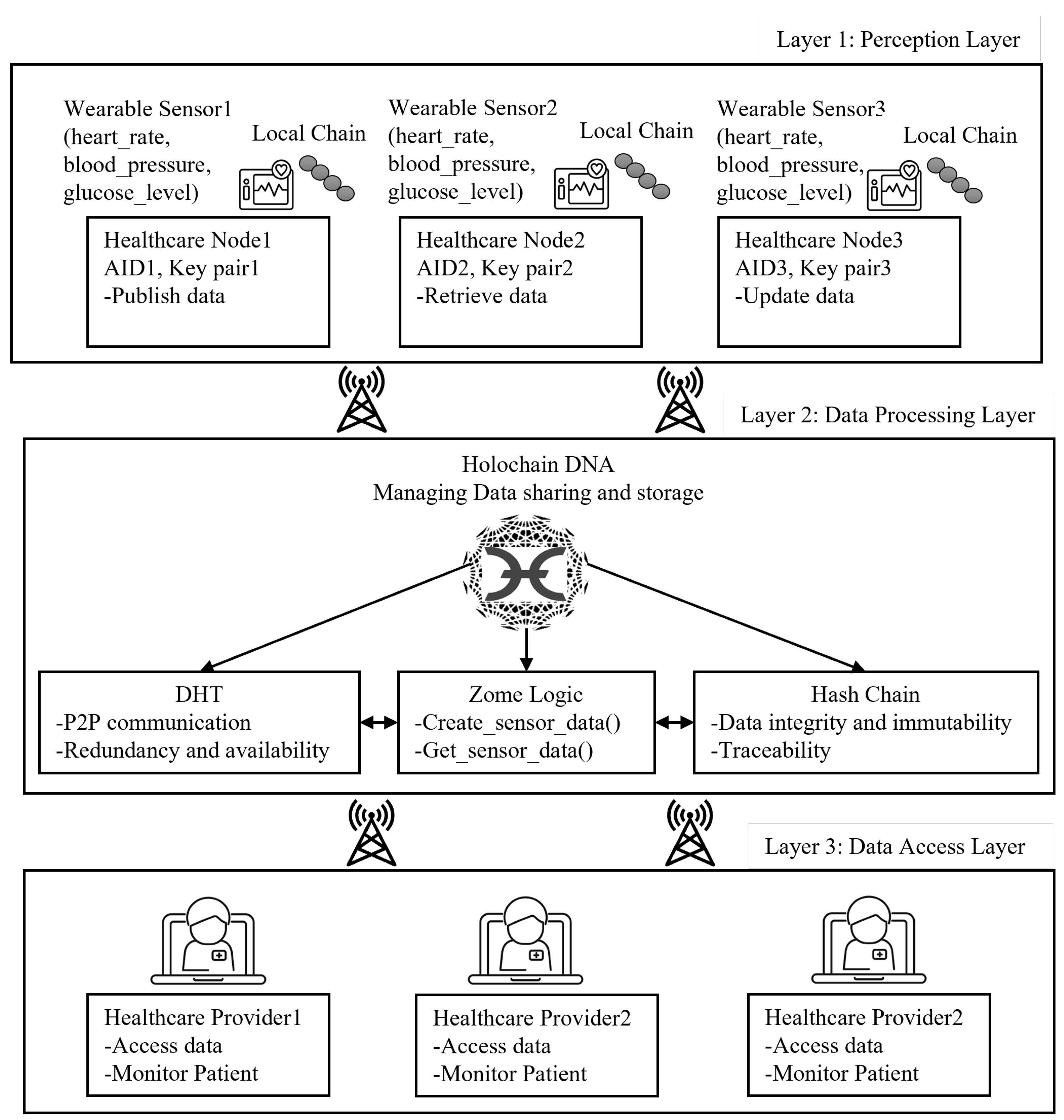
4. Holochain Experiment for Healthcare IoT Network
4.1. Experimental Setup and Configuration
| Listing 1. DNA Structure. |
 |
| Listing 2. Zome Logic for Healthcare IoT Network. |
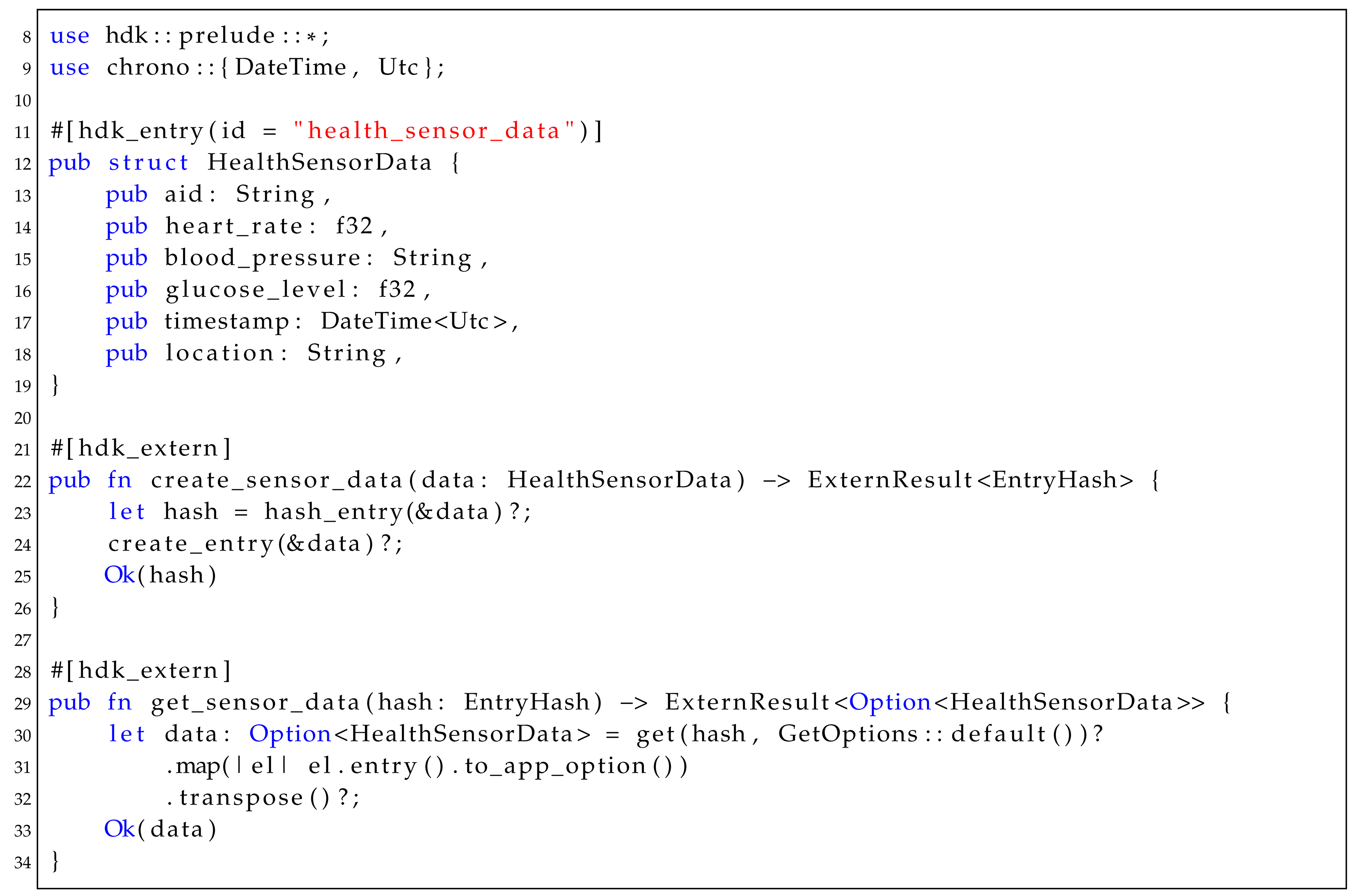 |
- Node 1: Monitored heart rate and blood pressure during a patient check-up. Data was published using the command:
holochain-cli call --fn=create_sensor_data --args='{ "aid": "W-sensor-1", "heart_rate": 75.0, "blood_pressure": "120/80", "glucose_level": 95.0, "timestamp": "2025-04-16T14:23:00Z", "location": "Room 101, Clinic A" }' --id=node1 - Node 2: Retrieved the data shared by Node 1 to verify the patient’s condition. The hash of the entry created by Node 1 was used as input for the retrieval command:
holochain-cli call --fn=get_sensor_data --args='{"hash": "<entry_hash>"}' --id=node2 - Node 3: Published glucose data to update the patient’s monitoring status. This node also verified the integrity of the data by retrieving and validating the timestamp and physiological parameters.
4.2. Results and Comparison
5. Challenges and Open Research Directions
5.1. Interoperability
- Protocol adapters that translate MQTT/CoAP messages into a format that Holochain can process.
- Edge computing integration, where edge devices serve as intermediaries, preprocessing data before DHT storage.
- Decentralized identity and access management, ensuring secure device authentication within an agent-centric network.
5.2. Tooling Maturity and Ecosystem Development
- Development of comprehensive SDKs, middleware, and standardized protocols to simplify integration with IoT systems and improve interoperability with other DLTs.
- Creation of advanced developer tools and resources, including debugging, testing, simulation environments, and detailed documentation.
- Fostering an active and supportive developer community by encouraging reusable components, plugin architectures, and feedback-driven iterative improvements in tooling and deployment practices.
5.3. Scalability in Large-Scale Networks
- Optimizing DHT performance to efficiently manage high-throughput environments and reduce lookup latency.
- Implementing adaptive sharding mechanisms to distribute workload dynamically and improve query efficiency, for instance, by dynamically partitioning the DHT by location or device type.
- Edge computing integration to process data locally, reducing latency and bandwidth consumption before storing data in the DHT.
- Developing load-balancing techniques to prevent hotspot nodes and ensure uniform data distribution across the network.
- Exploring hybrid approaches that combine Holochain with edge and cloud computing for efficient large-scale deployment.
5.4. Security Threats
- Developing secure authority selection mechanisms for transaction approval, incorporating trust metrics, stake-based incentives, and decentralized reputation models to minimize adversarial influence.
- Implementing decentralized authentication through strong identity verification techniques to prevent identity spoofing and unauthorized access, leveraging cryptographic signatures and decentralized identity frameworks.
- Introducing trust-based or stake-weighted models to restrict the influence of malicious nodes and enhance network resilience.
- Utilizing advanced cryptographic methods such as zero-knowledge proofs and homomorphic encryption to ensure data privacy, integrity, and secure computation within the network.
- Employing real-time ML anomaly detection by training models on Holochain’s source chain history to identify suspicious patterns such as Sybil attacks, collusion, and data injection threats.
5.5. Data Management and Storage
- Developing hybrid architectures that combine DHTs with centralized caching and adaptive data replication strategies to improve data retrieval speeds and balance consistency and availability in decentralized environments.
- Investigating efficient indexing techniques and consensus-free synchronization mechanisms to enhance query performance and ensure data consistency in large-scale distributed networks and agent-centric architectures.
- Strengthening DHT integrity by implementing verifiable storage mechanisms, cryptographic commitments, and tamper-proof logging to ensure data authenticity and resist manipulation, including hierarchical and off-chain storage, time-series compression, and GDPR-compliant data deletion.
5.6. Regulatory and Privacy Considerations
- Developing mechanisms to support the right to be forgotten while preserving decentralization principles.
- Implementing privacy-preserving techniques such as zero-knowledge proofs, differential privacy, and secure multi-party computation.
- Designing regulatory-compliant data governance models for decentralized IoT ecosystems.
- Creating auditing and compliance monitoring frameworks tailored for decentralized architectures.
- Investigating policy-driven access control mechanisms to ensure legal and ethical data usage.
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ismail, S.; Reza, H. Security Challenges of Blockchain-Based Supply Chain Systems. In Proceedings of the 2022 IEEE 13th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 26–29 October 2022; pp. 1–6. [Google Scholar]
- Jia, S.; Zhao, Y.; Zhang, Y.; Jia, B.; Lian, W. CAA-RF: An Anomaly Detection Algorithm for Computing Power Blockchain Networks. Appl. Sci. 2025, 15, 5804. [Google Scholar] [CrossRef]
- Kamran, M.; Rehan, M.M.; Nisar, W.; Rehan, M.W. AHEAD: A Novel Technique Combining Anti-Adversarial Hierarchical Ensemble Learning with Multi-Layer Multi-Anomaly Detection for Blockchain Systems. Big Data Cogn. Comput. 2024, 8, 103. [Google Scholar] [CrossRef]
- Almasabi, A.M.; Alkhodre, A.B.; Khemakhem, M.; Eassa, F.; Abi Sen, A.A.; Harbaoui, A. Internet of Things-Based Anomaly Detection Hybrid Framework Simulation Integration of Deep Learning and Blockchain. Information 2025, 16, 406. [Google Scholar] [CrossRef]
- Valencia-Arias, A.; González-Ruiz, J.D.; Verde Flores, L.; Vega-Mori, L.; Rodríguez-Correa, P.; Sánchez Santos, G. Machine Learning and Blockchain: A Bibliometric Study on Security and Privacy. Information 2024, 15, 65. [Google Scholar] [CrossRef]
- Villegas-Ch, W.; Govea, J.; Gutierrez, R.; Mera-Navarrete, A. Optimizing Security in IoT Ecosystems Using Hybrid Artificial Intelligence and Blockchain Models: A Scalable and Efficient Approach for Threat Detection. IEEE Access 2025, 13, 16933–16958. [Google Scholar] [CrossRef]
- Fernando, P.; Braeken, A.; Liyanage, M. Breaking Chains, Empowering IoT: A Comparative Study of Holochain and Blockchain. In Proceedings of the 2023 IEEE Latin-American Conference on Communications (LATINCOM), Panama City, Panama, 15–17 November 2023; pp. 1–6. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; MIT: Cambridge, MA, USA, 2008. [Google Scholar]
- Sealey, N.; Aijaz, A.; Holden, B. IOTA Tangle 2.0: Toward a Scalable, Decentralized, Smart, and Autonomous IoT Ecosystem. In Proceedings of the 2022 International Conference on Smart Applications, Communications and Networking (SmartNets), Palapye, Botswana, 29 November–1 December 2022; pp. 1–8. [Google Scholar]
- Baird, L. The Swirlds Hashgraph Consensus Algorithm: Fair, Fast, Byzantine Fault Tolerance. Swirlds Tech Reports, SWIRLDS-TR-2016-01. Tech. Rep. 2016, 34, 9–11. [Google Scholar]
- Singh, A.; Click, K.; Parizi, R.M.; Zhang, Q.; Dehghantanha, A.; Choo, K.-K.R. Sidechain technologies in blockchain networks: An examination and state-of-the-art review. J. Netw. Comput. Appl. 2020, 149, 102471. [Google Scholar] [CrossRef]
- Harris-Braun, E.; Luck, N.; Brock, A. Holochain: Scalable Agent-Centric Distributed Computing. DRAFT (ALPHA 1). 2018. Available online: https://whitepaperdatabase.com/wpcontent/uploads/2018/08/holochain-HOT-whitepaper.pdf (accessed on 18 November 2024).
- Zhang, H.; Zaman, M.; Stacey, B.; Sampalli, S. A Novel Distributed Ledger Technology Structure for Wireless Sensor Networks Based on IOTA Tangle. Electronics 2022, 11, 2403. [Google Scholar] [CrossRef]
- Khan, M.; Schaefer, D.; Milisavljevic-Syed, J. A Review of Distributed Ledger Technologies in the Machine Economy: Challenges and Opportunities in Industry and Research. Procedia CIRP 2022, 107, 1168–1173. [Google Scholar] [CrossRef]
- Ismail, S.; Nouman, M.; Dawoud, D.W.; Reza, H. Towards a lightweight security framework using blockchain and machine learning. Blockchain Res. Appl. 2024, 5, 100174. [Google Scholar] [CrossRef]
- Akhtar, Z. From Blockchain to Hashgraph: Distributed Ledger Technologies in the Wild. In Proceedings of the 2019 International Conference on Electrical, Electronics and Computer Engineering (UPCON), Aligarh, India, 8–10 November 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Ismail, S.; Dawoud, D.W.; Reza, H. Securing Wireless Sensor Networks Using Machine Learning and Blockchain: A Review. Future Internet 2023, 15, 200. [Google Scholar] [CrossRef]
- Popov, S. The tangle. White Pap. 2018, 1, 30. [Google Scholar]
- Peelam, M.S.; Chaurasia, B.K.; Sharma, A.K.; Chamola, V.; Sikdar, B. Unlocking the Potential of Interconnected Blockchains: A Comprehensive Study of Cosmos Blockchain Interoperability. IEEE Access 2024, 12, 171753–171776. [Google Scholar] [CrossRef]
- Holochain. Holochain—Think Outside the Blocks. Available online: https://www.holochain.org/ (accessed on 18 November 2024).
- Pancari, S.; Rashid, A.; Zheng, J.; Patel, S.; Wang, Y.; Fu, J. A Systematic Comparison between the Ethereum and Hyperledger Fabric Blockchain Platforms for Attribute-Based Access Control in Smart Home IoT Environments. Sensors 2023, 23, 7046. [Google Scholar] [CrossRef]
- Eghmazi, A.; Ataei, M.; Landry, R.J.; Chevrette, G. Enhancing IoT Data Security: Using the Blockchain to Boost Data Integrity and Privacy. IoT 2024, 5, 20–34. [Google Scholar] [CrossRef]
- Carelli, A.; Palmieri, A.; Vilei, A.; Castanier, F.; Vesco, A. Enabling Secure Data Exchange through the IOTA Tangle for IoT Constrained Devices. Sensors 2022, 22, 1384. [Google Scholar] [CrossRef]
- Gaba, S.; Khan, H.; Almalki, K.J.; Jabbari, A.; Budhiraja, I.; Kumar, V.; Singh, A.; Singh, K.K.; Askar, S.S.; Abouhawwash, M. Holochain: An Agent-Centric Distributed Hash Table Security in Smart IoT Applications. IEEE Access 2023, 11, 81205–81223. [Google Scholar] [CrossRef]
- Wannenwetsch, K.; Ostermann, I.; Priel, R.; Gerschner, F.; Theissler, A. Blockchain for Supply Chain Management: A Literature Review and Open Challenges. Procedia Comput. Sci. 2023, 225, 1312–1321. [Google Scholar] [CrossRef]
- Ismail, S.; Dandan, S.; Dawoud, D.W.; Reza, H. A Comparative Study of Lightweight Machine Learning Techniques for Cyber-attacks Detection in Blockchain-Enabled Industrial Supply Chain. IEEE Access 2024, 12, 102481–102491. [Google Scholar] [CrossRef]
- Anwar, U.A.A.; Rahayu, A.; Wibowo, L.A.; Sultan, M.A.; Aspiranti, T.; Furqon, C.; Rani, A.M. Supply chain integration as the implementation of strategic management in improving business performance. Discov. Sustain. 2025, 6, 101. [Google Scholar] [CrossRef]
- Jafari, H.; Ghaderi, H.; Malik, M.; Bernardes, E. The effects of supply chain flexibility on customer responsiveness: The moderating role of innovation orientation. Prod. Plan. Control 2023, 34, 1543–1561. [Google Scholar] [CrossRef]
- Asante, M.; Epiphaniou, G.; Maple, C.; Al-Khateeb, H.; Bottarelli, M.; Ghafoor, K.Z. Distributed Ledger Technologies in Supply Chain Security Management: A Comprehensive Survey. IEEE Trans. Eng. Manag. 2023, 70, 713–739. [Google Scholar] [CrossRef]
- Mehannaoui, R.; Mouss, K.N.; Aksa, K.; Benchine, H.; Ismail, S. A holochain-based IoT-enabled agri-food traceability system: Application in the recombined milk supply chain. Int. J. Inf. Technol. 2025, 17, 1–17. [Google Scholar] [CrossRef]
- Sakthi, U.; DafniRose, J. Blockchain-Enabled Smart Agricultural Knowledge Discovery System using Edge Computing. Procedia Comput. Sci. 2022, 202, 73–82. [Google Scholar] [CrossRef]
- Maull, R.; Godsiff, P.; Mulligan, C.; Brown, A.; Kewell, B. Distributed ledger technology: Applications and implications. Strateg. Change 2017, 26, 481–489. [Google Scholar] [CrossRef]
- Raza, A.; Badidi, E.; Hayajneh, M.; Barka, E.; Harrouss, O.E. Blockchain-Based Reputation and Trust Management for Smart Grids, Healthcare, and Transportation: A Review. IEEE Access 2024, 12, 196887–196913. [Google Scholar] [CrossRef]
- Zia, M.F.; Benbouzid, M.; Elbouchikhi, E.; Muyeen, S.M.; Techato, K.; Guerrero, J.M. Microgrid Transactive Energy: Review, Architectures, Distributed Ledger Technologies, and Market Analysis. IEEE Access 2020, 8, 19410–19432. [Google Scholar] [CrossRef]
- Krawiec, K.; Kraft, O.; Jahn, R. A comparative analysis of using Distributed Ledger Technologies for Transactive Energy Systems. In Proceedings of the 2022 8th International Youth Conference on Energy (IYCE), Eger, Hungary, 6–9 July 2022; pp. 1–6. [Google Scholar]
- Ramasamy, L.K.; Khan K. P., F.; Imoize, A.L.; Ogbebor, J.O.; Kadry, S.; Rho, S. Blockchain-Based Wireless Sensor Networks for Malicious Node Detection: A Survey. IEEE Access 2021, 9, 128765–128785. [Google Scholar] [CrossRef]
- Elsadig, M.A. Detection of Denial-of-Service Attack in Wireless Sensor Networks: A Lightweight Machine Learning Approach. IEEE Access 2023, 11, 83537–83552. [Google Scholar] [CrossRef]
- Al-Quayed, F.; Ahmad, Z.; Humayun, M. A Situation Based Predictive Approach for Cybersecurity Intrusion Detection and Prevention Using Machine Learning and Deep Learning Algorithms in Wireless Sensor Networks of Industry 4.0. IEEE Access 2024, 12, 34800–34819. [Google Scholar] [CrossRef]
- Tuteja, G.; Rani, S.; Sharma, A.; Singla, S. Blockchain-Enabled Security and Integrity Mechanisms for Wireless Sensor Networks in IoT Systems*. In Proceedings of the 2024 Global Conference on Communications and Information Technologies (GCCIT), Bangalore, India, 25–26 October 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Soltani, R.; Zaman, M.; Upadhyay, D.; Jain, A.; Sampalli, S. Using IOTA Tangle and Machine Learning for a Defensive Model-Based Approach Against Replication Attacks on Wireless Sensor Networks. IEEE Access 2024, 12, 148605–148624. [Google Scholar] [CrossRef]
- Chen, C.M.; Li, Z.; Das, A.K.; Chaudhry, S.A.; Lorenz, P. Provably Secure Authentication Scheme for Fog Computing-Enabled Intelligent Social Internet of Vehicles. IEEE Trans. Veh. Technol. 2024, 73, 13600–13610. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, Z.; Wu, Q.; Zhao, H.; Xu, H.; Wu, X. Energy-Aware Dynamic Resource Allocation in UAV Assisted Mobile Edge Computing Over Social Internet of Vehicles. IEEE Access 2018, 6, 56700–56715. [Google Scholar] [CrossRef]
- Mittal, S.; Dudeja, R.K.; Bali, R.S.; Aujla, G.S. A distributed task orchestration scheme in collaborative vehicular cloud edge networks. Computing 2024, 106, 1151–1175. [Google Scholar] [CrossRef]
- Ismail, S.; Hammad, E.; Iqbal, R. Towards Holochain-Based Adaptive Trust Management in Social Internet of Vehicles. In Proceedings of the 2025 IEEE 15th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2025; pp. 878–884. [Google Scholar] [CrossRef]
- Al-Jaroodi, J.; Mohamed, N.; Abukhousa, E. Health 4.0: On the Way to Realizing the Healthcare of the Future. IEEE Access 2020, 8, 211189–211210. [Google Scholar] [CrossRef]
- Ciasullo, M.V.; Orciuoli, F.; Douglas, A.; Palumbo, R. Putting Health 4.0 at the service of Society 5.0: Exploratory insights from a pilot study. Socio-Econ. Plan. Sci. 2022, 80, 101163. [Google Scholar] [CrossRef]
- Aftab, A.; Chrysostomou, C.; Qureshi, H.K.; Rehman, S. Holo-Block Chain: A Hybrid Approach for Secured IoT Healthcare Ecosystem. In Proceedings of the 2022 18th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Thessaloniki, Greece, 10–12 October 2022; pp. 243–250. [Google Scholar]
- Zaman, S.; Khandaker, M.R.A.; Khan, R.T.; Tariq, F.; Wong, K.K. Thinking Out of the Blocks: Holochain for Distributed Security in IoT Healthcare. IEEE Access 2022, 10, 37064–37081. [Google Scholar] [CrossRef]
- Bekkali, A.E.; Essaaidi, M.; Boulmalf, M. A Blockchain-Based Architecture and Framework for Cybersecure Smart Cities. IEEE Access 2023, 11, 76359–76370. [Google Scholar] [CrossRef]
- Silva, N.S.e.; Castro, R.; Ferrão, P. Smart Grids in the Context of Smart Cities: A Literature Review and Gap Analysis. Energies 2025, 18, 1186. [Google Scholar] [CrossRef]
- Alotaibi, A.; Aldawghan, H.; Aljughaiman, A. A Review of the Authentication Techniques for Internet of Things Devices in Smart Cities: Opportunities, Challenges, and Future Directions. Sensors 2025, 25, 1649. [Google Scholar] [CrossRef]
- Padma, A.; Ramaiah, M. Blockchain Based an Efficient and Secure Privacy Preserved Framework for Smart Cities. IEEE Access 2024, 12, 21985–22002. [Google Scholar] [CrossRef]
- Omar, A.A.; Jamil, A.K.; Khandakar, A.; Uzzal, A.R.; Bosri, R.; Mansoor, N.; Rahman, M.S. A Transparent and Privacy-Preserving Healthcare Platform With Novel Smart Contract for Smart Cities. IEEE Access 2021, 9, 90738–90749. [Google Scholar] [CrossRef]
- Ahmed, A.; Parveen, I.; Abdullah, S.; Ahmad, I.; Alturki, N.; Jamel, L. Optimized Data Fusion With Scheduled Rest Periods for Enhanced Smart Agriculture via Blockchain Integration. IEEE Access 2024, 12, 15171–15193. [Google Scholar] [CrossRef]
- Thilakarathne, N.N.; Abu Bakar, M.S.; Abas, P.E.; Yassin, H. Internet of things enabled smart agriculture: Current status, latest advancements, challenges and countermeasures. Heliyon 2025, 11, e42136. [Google Scholar] [CrossRef] [PubMed]
- Hasan, H.R.; Musamih, A.; Salah, K.; Jayaraman, R.; Omar, M.; Arshad, J.; Boscovic, D. Smart agriculture assurance: IoT and blockchain for trusted sustainable produce. Comput. Electron. Agric. 2024, 224, 109184. [Google Scholar] [CrossRef]
- Zheng, C.; Peng, X.; Wang, Z.; Ma, T.; Lu, J.; Chen, L.; Dong, L.; Wang, L.; Cui, X.; Shen, Z. A Review on Blockchain Applications in Operational Technology for Food and Agriculture Critical Infrastructure. Foods 2025, 14, 251. [Google Scholar] [CrossRef]
- Chiu, W.Y.; Meng, W.; Ge, C. Nosneaky: A blockchain-based execution integrity protection scheme in industry 4.0. IEEE Trans. Ind. Inform. 2022, 19, 7957–7965. [Google Scholar] [CrossRef]
- Soori, M.; Jough, F.K.G.; Dastres, R.; Arezoo, B. Blockchains for industrial Internet of Things in sustainable supply chain management of industry 4.0, a review. Sustain. Manuf. Serv. Econ. 2024, 3, 100026. [Google Scholar] [CrossRef]
- Kple, A.M.; Deepak, G.; Rimal, B.P. Holochain-Based Secure and Energy Efficient IoT Network. In Proceedings of the 2024 International Wireless Communications and Mobile Computing (IWCMC), Ayia Napa, Cyprus, 27–31 May 2024; pp. 999–1004. [Google Scholar] [CrossRef]
- Everspaugh, A.; Paterson, K.; Ristenpart, T.; Scott, S. Key rotation for authenticated encryption. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Cham, Switzerland, 2017; pp. 98–129. [Google Scholar]
- Ktari, J.; Frikha, T.; Hamdi, M.; Hamam, H. Enhancing Blockchain Consensus With FPGA: Accelerating Implementation for Efficiency. IEEE Access 2024, 12, 44773–44785. [Google Scholar] [CrossRef]
- Wu, X.; Chang, J.; Wang, Z.; Cheng, J. DyPoA: Enhanced PoA protocol with a dynamic set of validators for IoT. Clust. Comput. 2024, 27, 12527–12545. [Google Scholar] [CrossRef]


| DLT Technology | Blockchain | Tangle (IOTA) | Hashgraph | Sidechains | Holochain |
|---|---|---|---|---|---|
| Consensus Mechanism | PoW, PoS, or Delegated PoS [8] | DAG where transactions validate each other [9] | Gossip protocol and Virtual Voting for BFT [10] | Independent consensus; varies by implementation (e.g., PoW, PoS) [11] | Agent-centric with local validation, no global consensus [12] |
| Scalability | Limited by block size and mining bandwidth | High; scales with more participants [9,13] | High; efficient communication | Depends on parent chain’s scalability | Very high; nodes operate independently [14] |
| Latency | High; delayed by mining/validation [15] | Low; transactions validate directly | Very low; near-instantaneous finality [16] | Variable; depends on implementation | Very low; local transactions are processed instantly |
| Resource Efficiency | High energy consumption (e.g., PoW) [8] | Low; no mining overhead | Low; avoids mining requirements | Dependent on parent chain | Very low; lightweight operations |
| Security | Vulnerable to 51% attacks [17] | Resilient; majority network control required | BFT | Independent security; separate trust model | Local integrity |
| Decentralization | High but centralized mining pools exist | High; designed for IoT | High; all nodes contribute equally | Variable; dependent on parent chain | High; agents independently own data |
| Data Ownership | Shared across nodes [8] | Shared ownership | Shared ownership | Inherited from parent chain | Agent-centric; users own their data |
| Throughput | Moderate (7–20 TPS for Bitcoin, 1000+ TPS for modern blockchains) | High; parallel processing of transactions | Very high; thousands of TPS | Variable; depends on design | Very high; no bottlenecks from global consensus |
| IoT Suitability | Limited by scalability and latency | Excellent; tailored for lightweight IoT devices | Suitable but resource-intensive | Moderate; specific to use case | Excellent; lightweight, agent-centric design |
| Key Challenges | Scalability, energy consumption | Immaturity; orphaned transactions | Complexity; proprietary licensing | Interoperability with main chain | Adoption and interoperability |
| Platforms/Languages | Bitcoin, Ethereum, C++, Go, Solidity | IOTA Rust, Go, C [18] | Hedera Java, JS | Polkadot, Cosmos Rust, Go [19] | Holo Rust [20] |
| Performance Metric | Holochain | Blockchain |
|---|---|---|
| Latency | 50 ms (publish), 30 ms (retrieve) | 200 ms (publish), 100 ms (retrieve) |
| Throughput | 20 TPS (stable) | 10 TPS (decrease with more nodes) |
| Network Overhead | Low (P2P/DHT) | High (Global broadcast) |
| Storage Growth | Linear per agent (Local + shared DHT) | Exponential (full ledger replication) |
| Consensus Mechanism | Agent-centric validation | Global PoA consensus |
| 10-Node Test | 15 TPS (+20% latency) | <5 TPS (2× latency) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ismail, S.; Mehannaoui, R.; Hunde, E.T.; Reza, H. Among the DLTs: Holochain for the Security of IoT Distributed Networks—A Review and Conceptual Framework. Sensors 2025, 25, 3864. https://doi.org/10.3390/s25133864
Ismail S, Mehannaoui R, Hunde ET, Reza H. Among the DLTs: Holochain for the Security of IoT Distributed Networks—A Review and Conceptual Framework. Sensors. 2025; 25(13):3864. https://doi.org/10.3390/s25133864
Chicago/Turabian StyleIsmail, Shereen, Raouf Mehannaoui, Eden Teshome Hunde, and Hassan Reza. 2025. "Among the DLTs: Holochain for the Security of IoT Distributed Networks—A Review and Conceptual Framework" Sensors 25, no. 13: 3864. https://doi.org/10.3390/s25133864
APA StyleIsmail, S., Mehannaoui, R., Hunde, E. T., & Reza, H. (2025). Among the DLTs: Holochain for the Security of IoT Distributed Networks—A Review and Conceptual Framework. Sensors, 25(13), 3864. https://doi.org/10.3390/s25133864






