Future of Telepresence Services in the Evolving Fog Computing Environment: A Survey on Research and Use Cases
Abstract
1. Introduction
Methodology and Work Structure
- Database selection: The literature was gathered from major digital libraries, including IEEE Xplore, ACM Digital Library, Springer, Elsevier (ScienceDirect), and Google Scholar. These sources were chosen because they cover computer networks, fog computing, and telepresence technologies extensively.
- Search strategy: A set of predefined keywords was used to retrieve relevant studies. The primary keywords included “telepresence services”, “fog computing”, “edge computing”, “remote presence”, “5G and 6G networks”, and “distributed computing models”. Boolean operators (AND, OR) were used to refine the search results.
- Inclusion and exclusion criteria: we considered the following inclusion and exclusion criteria:
- Inclusion criteria: peer-reviewed journal and conference papers published within the last 4 years, articles focusing on fog computing applications in communication networks, and studies discussing telepresence architecture.
- Exclusion criteria: papers lacking technical depth, works unrelated to telepresence and fog computing, and studies focused solely on cloud computing without fog or edge-based considerations.
- Screening and selection: After retrieving the initial results, duplicate papers were removed and abstracts were reviewed for relevance. Selected studies were then analyzed based on their contributions to telepresence and fog computing integration.We considered the following approaches:
- Thematic analysis: the literature was categorized into key themes, including fog computing architectures, Cisco’s fog model, security challenges in telepresence-fog integration, and potential improvements for next-generation networks.
- Comparative evaluation: Cisco’s fog computing model was assessed based on identified weaknesses and an alternative model was proposed to address these limitations.
- Emerging trends and future directions: the survey examines technological trends that influence the development of telepresence services in 6G networks, highlighting promising research directions.
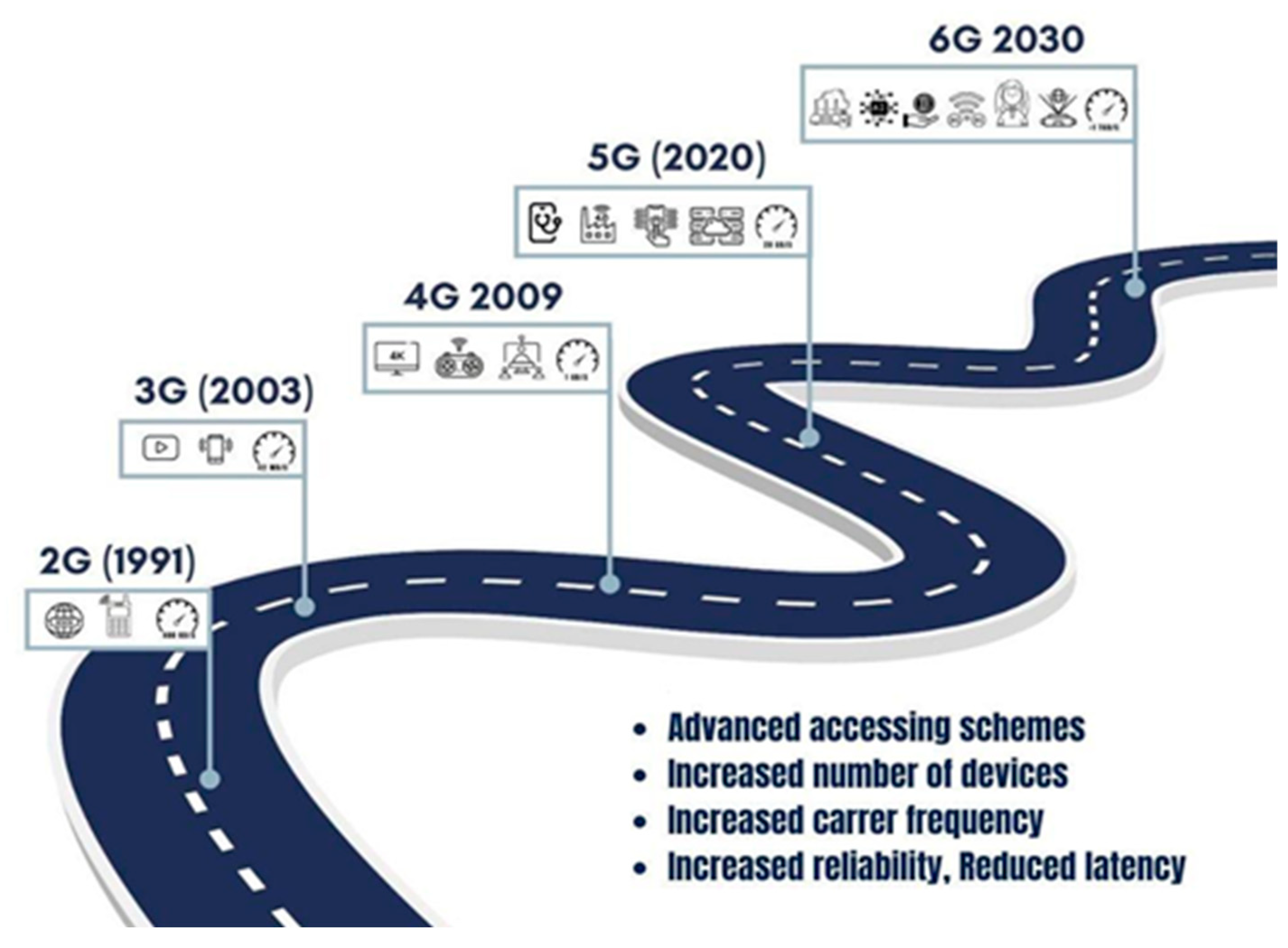
2. 6G Network Development and Key Service Areas for the Future
2.1. Fundamental Changes in the Development of 6G Communication Networks
- Ultralow latency communication networks. New technologies have led to even more significant changes in communication network construction, as it required data transmission with a delay of 1 ms, which is currently 100 times less than in existing communication networks. At the same time, it is worth noting that the concept of a 6G network leads to such a process as the decentralization of communication networks, as the fundamental limitations on the speed of light transmission are insurmountable [12,16].
- Ultradense networks. Ultradense networks are one of the key characteristics of 6G networks and will only become more important as the technology evolves. It is already predicted that by 2030, there will be around 1 million Internet of Things and other devices per square meter of floor space [17]. This means that communication networks must be able to support a huge number of low-latency, high-bandwidth connections. There are several ways to achieve ultradense networks. One is to use new frequency bands. A millimeter-wave communication network using 30 to 300 GHz frequencies is a better alternative. As the frequency increases, the millimeter-wave channel becomes more susceptible to shadowing and tropopause effects of millimeter-wave propagation [18]. However, due to the extremely short wavelength, high beam gain can be achieved by using a large number of antennas. This will solve the problem of loss and shadowing by tuning the signal power in the desired direction using multidirectional antennas [19]. Another way to achieve ultradense networks is by using new technologies such as AI and ML. These technologies can help optimize the use of spectrum and network resources, allowing more devices to be connected without compromising performance [20].
- Internet of skills. The Internet of Skills is a concept that emerged in 2017. It involves the use of ultralow latency networks to provide new services that will allow people and robotic devices to learn new skills. The basic idea behind the Internet of Skills is that ultralow latency networks will enable the real-time transfer of skill model data. This will allow new skills to be taught to humans and robots without the need to be physically present in one place. For example, the Internet of Skills could be used to teach people new languages, equipment skills, or creativity. The Internet of Skills can also be used to teach robots new tasks, such as car repair or surgery [21,22].
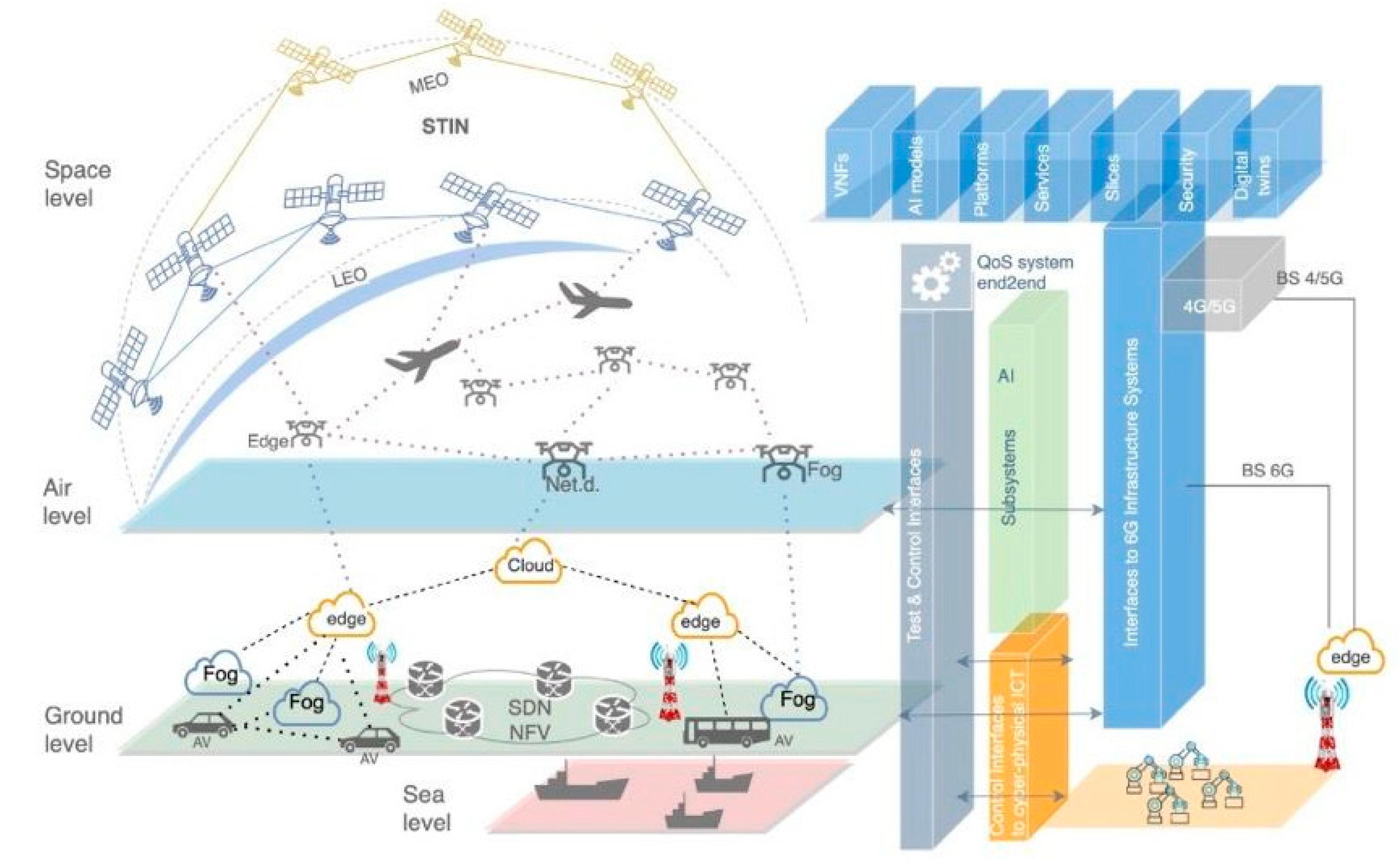
- Flying networks. Flying networks are another fundamental change in the development of communication networks. They combine flying and terrestrial segments of networks into a single communication network. Flying networks have several advantages over traditional networks. They allow for coverage even in hard-to-reach areas and higher data transmission speeds. One of the key features of flying networks is ultralow latency. This is because the distance between the flying device and the subscriber can be relatively short [23]. Flying networks have great potential for the development of new applications and services. They can be used to provide emergency communications, to monitor and manage infrastructure, and to create new entertainment. Flying networks have become one of the main segments of the 6G integrated networks of the 6G concept or space–terrestrial integrated network (STIN), which was approved by ITU-T [24,25].
- Unmanned transport. One of the key areas of development of unmanned transport is networking with roadside computing facilities. This will allow unmanned transport to access information about road and environmental conditions over long distances. This will contribute to the safety and efficiency of unmanned transport. Here are some specific examples of how networking unmanned vehicles can be utilized.
- Warning of potential hazards: Unmanned vehicles can receive information about roadworks, accidents, and other hazards that are out of sight. This will allow them to take action to prevent collisions or other incidents [26].
- Traffic optimization: unmanned vehicles can coordinate their movements with each other to avoid congestion and increase the efficiency of road use [27].
- Improved customer service: unmanned vehicles can provide personalized services to customers, such as offering routes tailored to their preferences or needs [28].
2.2. Main Trends in the Development of 6G Networks
2.2.1. Telepresence Personalization of the Network
2.2.2. Flying Networks
2.2.3. Nanonetworks
3. Fog Computing—A Promising Technological Solution for the 2030 Networks
3.1. A General Overview of Fog Computing
3.2. Defining Fog Computing
3.3. Characteristics of Fog Computing
- Flexibility: Fog computing provides distributed storage and computation resources that can work with various end devices, such as networked sensors, industrial machines, and wearable devices. This makes the fog cloud suitable for various IoT applications, from environmental monitoring to manufacturing management.
- Real-time communication: Fog computing enables simultaneous communication between cloud nodes. This is essential for IoT applications that require a proactive response, such as security monitoring and traffic management.
- Physical distribution: Fog computing distributes applications and services, unlike cloud computing. This means they can be stored anywhere. This reduces latency and improves performance for IoT applications.
- Low latency and location: Fog computing is located near end devices, providing shorter latency when processing information. Additionally, it supports location responsiveness by storing fog computing nodes in multiple locations.
- Compatibility: Fog computing modules can interact with various platforms through different service providers, ensuring compatibility.
- Providing web analysis and cloud integration: Fog computing sits between the end devices and the cloud to play an important role in the ability to process and compute information near the end devices.
- Heterogeneity: Fog computing endpoints or nodes are designed by various companies, each with their provenance schemes, and must be stored according to their location requirements. This allows fog computing to be adaptable to different platforms.
- Ensuring flexibility: Fog computing requirements include connecting directly to devices, such as mobile devices. This allows the use of flexible technologies such as the Location and Identifier Sharing Protocol (LISP), which requires a distributed indexing system.
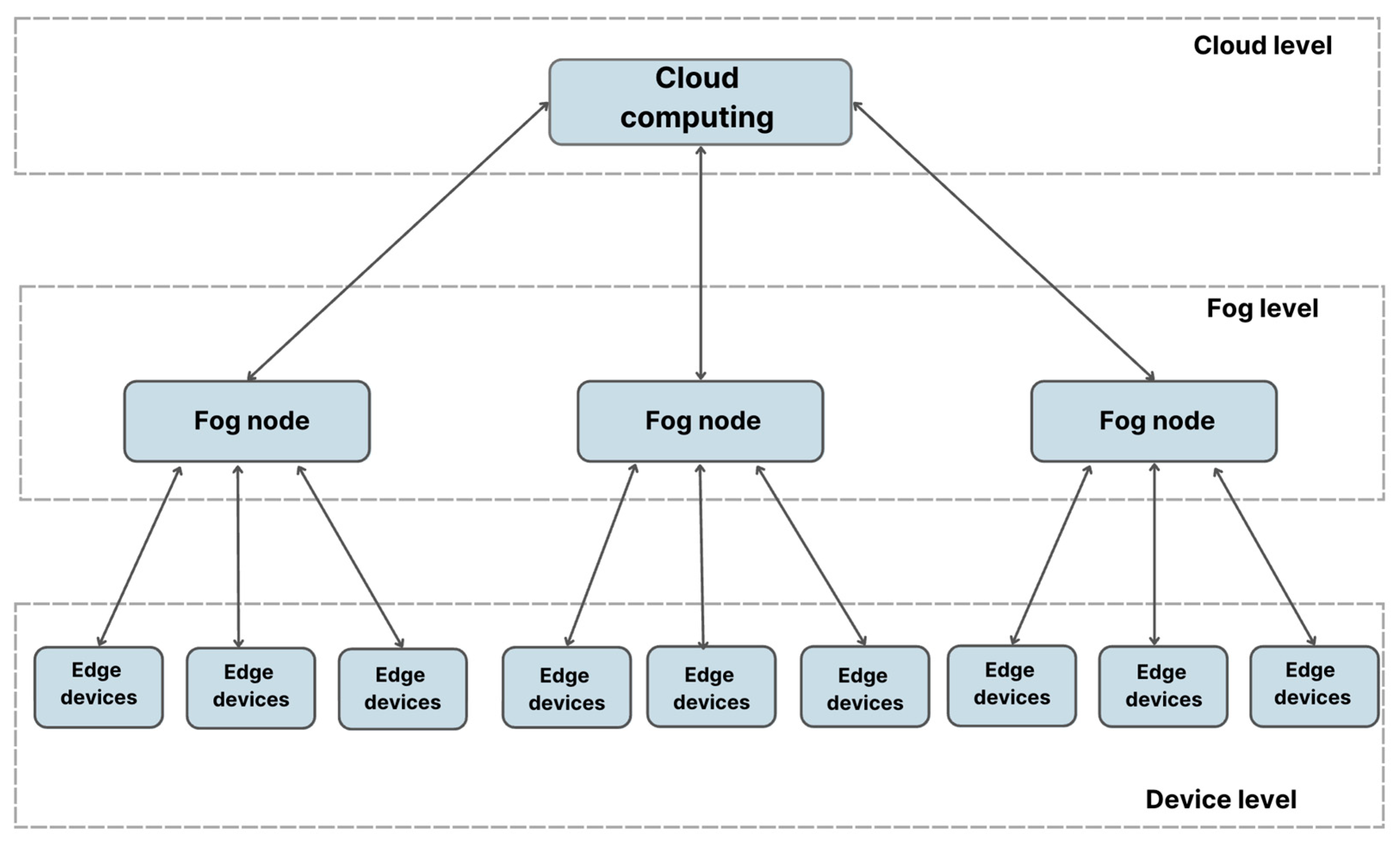
3.4. Structure of Fog Computing
3.4.1. Hierarchical Model of the Architecture
- (a)
- Terminal layer (Terminal)
- (b)
- Fog layer
- (c)
- Cloud layer
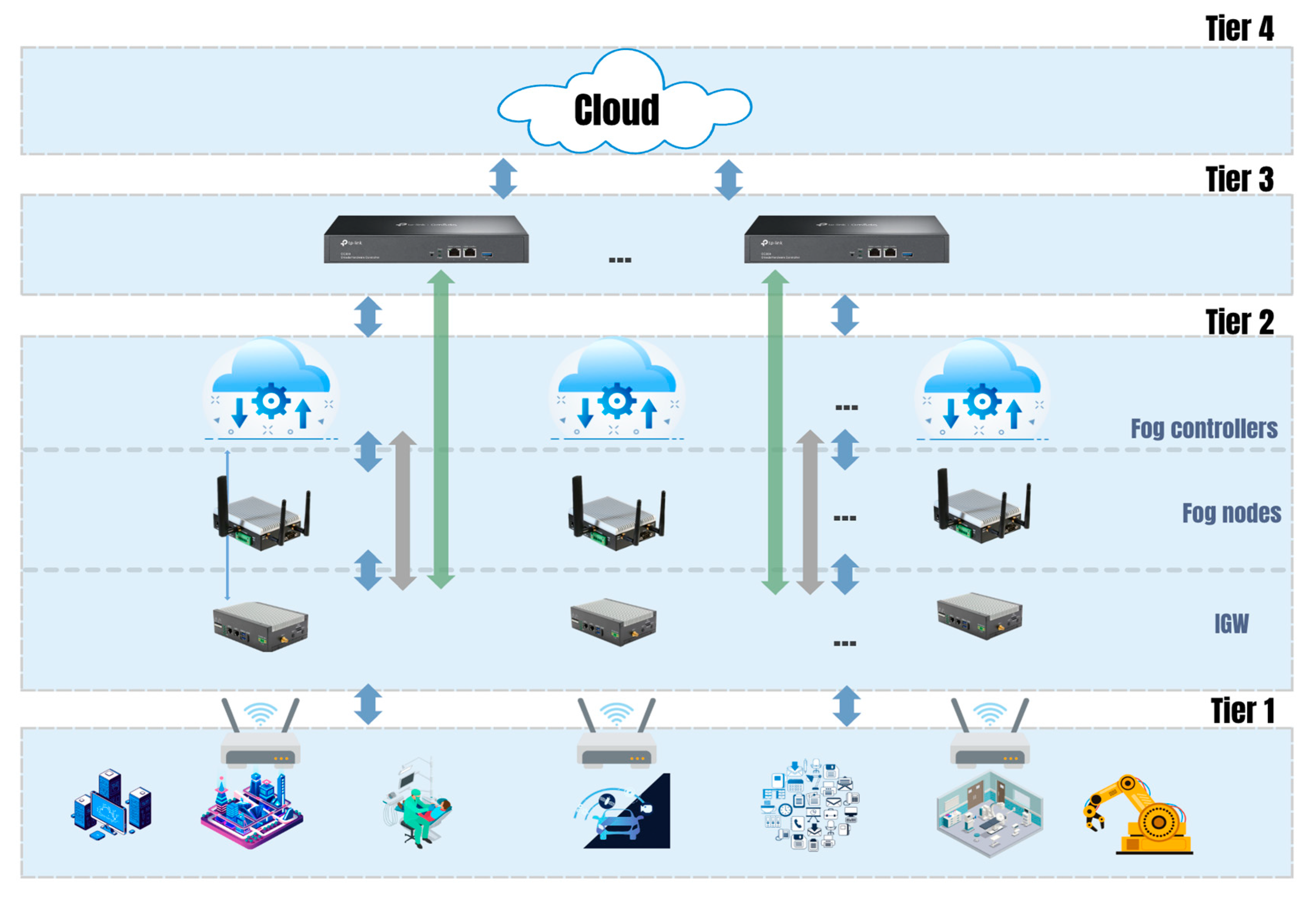
3.4.2. Proposed Multitier Fog Computing Model
- Processing video streams, spatial audio, and sensor data closer to users to minimize round-trip delays.
- Preventing network congestion through local data filtering, compression, and adaptive streaming.
- Improving reliability, which is vital for uninterrupted telepresence experiences.
- AI-driven predictive caching and adaptive resource management boost responsiveness in ever-changing network conditions.
- (a)
- Compression algorithms for efficient data transmission
- (b)
- Latency-aware transport protocols
- Quick UDP Internet connections (QUIC) can be used to minimize connection latency for real-time communication [77].
- WebRTC enables peer-to-peer holographic streaming for decentralized telepresence [78].
- 6G-integrated network slicing can dynamically assign dedicated bandwidth to telepresence applications [79].
- (c)
- Reinforcement learning-based scheduling can allocate computational resources dynamically based on network congestion and user demand.
- Edge AI inference acceleration can be deployed to reduce dependency on cloud-based processing, improving response times.
- Predictive caching and prefetching can optimize holographic data delivery for a seamless experience.
4. Fog Computing Application for Telepresence Services
4.1. Analysis of the Recent Development of Telepresence Services
4.2. Application of Fog Computing to Telepresence Services
4.3. Security Issues with Fog Computing for Telepresence Services
- (a)
- As telepresence services rely on real-time data streaming, fog nodes become potential targets for man-in-the-middle (MITM) attacks.
- (b)
- Decentralized fog nodes require robust access control to prevent unauthorized data access.
- (c)
- IoT devices and endpoints involved in telepresence sessions may be compromised due to weak authentication mechanisms.
- (d)
- Attackers can exploit vulnerabilities in fog computing infrastructure to overload nodes and disrupt telepresence communications.
- (e)
- Malicious actors may alter real-time communication streams, leading to misinformation and privacy breaches.
- Using federated learning to train user data without centralizing, it reduces data exposure risks.
- Homomorphic encryption can enable computations on encrypted data without decryption, ensuring privacy in fog-based AI processing.
- Differential privacy adds noise to data queries, preventing user identity leakage.
- Decentralized self-sovereign identities (SSI) enhance privacy and control over personal data.
5. Standardization and Interoperability in Fog Computing and Telepresence Services
- (a)
- Although IEEE 1934 promotes open standards, many telepresence and 6G service providers utilize proprietary architectures, creating integration difficulties.
- (b)
- Decentralized fog environments are susceptible to security threats, necessitating continuous updates to authentication mechanisms.
- (c)
- Optimizing energy consumption in fog nodes while maintaining high-performance computing remains a key challenge.
- (d)
- Further research is needed to enhance AI-driven workload allocation across hierarchical fog layers. This includes developing novel intelligent resource allocation and management schemes.
- (e)
- Integrating emerging technologies such as terahertz (THz) communication, intelligent reflecting surfaces (IRS), and quantum-secure networks with IEEE 1934 is an open research area.
- 3GPP Release 16: Introduced MEC offloading, uRLLC, and network slicing.
- 3GPP Release 17: Enhanced AI at the network edge, advanced user plane function (UPF) functionalities, and service discovery mechanisms.
- 3GPP Release 18+ (Toward 6G): This version includes AI-native networks, zero-touch automation, and federated learning at the edge, aligning closely with fog computing principles.
6. The Mind Map for Future Work
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Shen, L.-H.; Feng, K.-T.; Hanzo, L. Five Facets of 6G: Research Challenges and Opportunities. ACM Comput. Surv. 2023, 55, 235. [Google Scholar] [CrossRef]
- Salahdine, F.; Han, T.; Zhang, N. 5G, 6G, and Beyond: Recent Advances and Future Challenges. Ann. Telecommun. 2023, 78, 525–549. [Google Scholar] [CrossRef]
- Aslam, A.M.; Chaudhary, R.; Bhardwaj, A.; Budhiraja, I.; Kumar, N.; Zeadally, S. Metaverse for 6G and beyond: The next Revolution and Deployment Challenges. IEEE Internet Things Mag. 2023, 6, 32–39. [Google Scholar] [CrossRef]
- Qadir, Z.; Le, K.N.; Saeed, N.; Munawar, H.S. Towards 6G Internet of Things: Recent Advances, Use Cases, and Open Challenges. ICT Express 2023, 9, 296–312. [Google Scholar] [CrossRef]
- Zuo, Y.; Guo, J.; Gao, N.; Zhu, Y.; Jin, S.; Li, X. A Survey of Blockchain and Artificial Intelligence for 6G Wireless Communications. IEEE Commun. Surv. Tutor. 2023, 25, 2494–2528. [Google Scholar] [CrossRef]
- Singh, R.; Kaushik, A.; Shin, W.; Di Renzo, M.; Sciancalepore, V.; Lee, D.; Sasaki, H.; Shojaeifard, A.; Dobre, O.A. Towards 6G Evolution: Three Enhancements, Three Innovations, and Three Major Challenges. arXiv 2024, arXiv:2402.10781. [Google Scholar]
- Zhang, Z.; Zhou, Y.; Teng, L.; Sun, W.; Li, C.; Min, X.; Zhang, X.P.; Zhai, G. Quality-of-Experience Evaluation for Digital Twins in 6G Network Environments. IEEE Trans. Broadcast. 2024, 70, 995–1007. [Google Scholar] [CrossRef]
- Chafii, M.; Bariah, L.; Muhaidat, S.; Debbah, M. Twelve Scientific Challenges for 6G: Rethinking the Foundations of Communications Theory. IEEE Commun. Surv. Tutor. 2023, 25, 868–904. [Google Scholar] [CrossRef]
- Xue, Q.; Ji, C.; Ma, S.; Guo, J.; Xu, Y.; Chen, Q.; Zhang, W. A Survey of Beam Management for mmWave and THz Communications towards 6G. IEEE Commun. Surv. Tutor. 2024, 26, 1520–1559. [Google Scholar] [CrossRef]
- Yeh, C.; Jo, G.D.; Ko, Y.-J.; Chung, H.K. Perspectives on 6G Wireless Communications. ICT Express 2023, 9, 82–91. [Google Scholar] [CrossRef]
- Wang, X.; Mei, J.; Cui, S.; Wang, C.-X.; Shen, X.S. Realizing 6G: The Operational Goals, Enabling Technologies of Future Networks, and Value-Oriented Intelligent Multi-Dimensional Multiple Access. IEEE Netw. 2023, 37, 10–17. [Google Scholar] [CrossRef]
- Osama, M.; Ateya, A.A.; Ahmed Elsaid, S.; Muthanna, A. Ultra-Reliable Low-Latency Communications: Unmanned Aerial Vehicles Assisted Systems. Information 2022, 13, 430. [Google Scholar] [CrossRef]
- Wang, C.-X.; You, X.; Gao, X.; Zhu, X.; Li, Z.; Zhang, C.; Wang, H.; Huang, Y.; Chen, Y.; Haas, H.; et al. On the Road to 6G: Visions, Requirements, Key Technologies, and Testbeds. IEEE Commun. Surv. Tutor. 2023, 25, 905–974. [Google Scholar] [CrossRef]
- Parra-Ullauri, J.M.; Zhang, X.; Bravalheri, A.; Moazzeni, S.; Wu, Y.; Nejabati, R.; Simeonidou, D. Federated Analytics for 6G Networks: Applications, Challenges, and Opportunities. IEEE Netw. 2024, 38, 9–17. [Google Scholar] [CrossRef]
- Banafaa, M.; Shayea, I.; Din, J.; Hadri Azmi, M.; Alashbi, A.; Ibrahim Daradkeh, Y.; Alhammadi, A. 6G Mobile Communication Technology: Requirements, Targets, Applications, Challenges, Advantages, and Opportunities. Alex. Eng. J. 2023, 64, 245–274. [Google Scholar] [CrossRef]
- Feng, D.; Lai, L.; Luo, J.; Zhong, Y.; Zheng, C.; Ying, K. Ultra-Reliable and Low-Latency Communications: Applications, Opportunities and Challenges. Sci. China Inf. Sci. 2021, 64, 120301. [Google Scholar] [CrossRef]
- Yarrabothu, R.S.; Murthy, G.R. Ultra-Dense Deployments in Next-Generation Networks and Metaverse. In Towards Wireless Heterogeneity in 6G Networks; CRC Press: Boca Raton, FL, USA, 2024; pp. 33–69. [Google Scholar]
- Singh, C.; Sharma, C.; Tripathi, S.; Sharma, M.; Agrawal, A. A Comprehensive Survey on Millimeter Wave Antennas at 30/60/120 GHz: Design, Challenges and Applications. Wirel. Pers. Commun. 2023, 133, 1547–1584. [Google Scholar] [CrossRef]
- Oladimeji, T.T.; Kumar, P.; Elmezughi, M.K. Performance Analysis of Improved Path Loss Models for Millimeter-Wave Wireless Network Channels at 28 GHz and 38 GHz. PLoS ONE 2023, 18, e0283005. [Google Scholar] [CrossRef]
- Celik, A.; Eltawil, A.M. At the Dawn of Generative AI Era: A Tutorial-Cum-Survey on New Frontiers in 6G Wireless Intelligence. IEEE Open J. Commun. Soc. 2024, 5, 2433–2489. [Google Scholar] [CrossRef]
- Oppici, L.; Bobbe, T.; Lüneburg, L.-M.; Nocke, A.; Schwendicke, A.; Winger, H.; Krzywinski, J.; Cherif, C.; Strufe, T.; Narciss, S. Internet of Skills. In Tactile Internet; Elsevier: Amsterdam, The Netherlands, 2021; pp. 75–99. ISBN 9780128213438. [Google Scholar]
- Dohler, M. The Internet of Skills: How 5G-Synchronized Reality Is Transforming Robotic Surgery. In Robotic Surgery; Springer International Publishing: Cham, Switzerland, 2021; pp. 207–215. ISBN 9783030535933. [Google Scholar]
- Ahmad, R.; Ayyash, M.; Salameh, H.B.; El-Khazali, R.; Eigala, H. Indoor Flying Networks for 6G: Concepts, Challenges, Enabling Technologies, and Opportunities. IEEE Commun. Mag. 2023, 61, 156–162. [Google Scholar] [CrossRef]
- Mozaffari, M.; Lin, X.; Hayes, S. Toward 6G with Connected Sky: UAVs and Beyond. IEEE Commun. Mag. 2021, 59, 74–80. [Google Scholar] [CrossRef]
- Ding, F.; Bao, C.; Zhou, D.; Sheng, M.; Shi, Y.; Li, J. Towards Autonomous Resource Management Architecture for 6G Satellite-Terrestrial Integrated Networks. IEEE Netw. 2024, 38, 113–121. [Google Scholar] [CrossRef]
- Sun, J.; Yuan, G.; Song, L.; Zhang, H. Unmanned Aerial Vehicles (UAVs) in Landslide Investigation and Monitoring: A Review. Drones 2024, 8, 30. [Google Scholar] [CrossRef]
- Wu, K.; Chin, K.W.; Soh, S. Multi-UAVs Network Design Algorithms for Computed Rate Maximization. IEEE Trans. Mob. Comput. 2024, 23, 8965–8980. [Google Scholar] [CrossRef]
- Nawaz, H.; Ali, H.M.; Laghari, A.A. UAV Communication Networks Issues: A Review. Arch. Comput. Methods Eng. 2021, 28, 1349–1369. [Google Scholar] [CrossRef]
- Ali, S.A.; Elsaid, S.A.; Ateya, A.A.; ElAffendi, M.; El-Latif, A.A.A. Enabling Technologies for Next-Generation Smart Cities: A Comprehensive Review and Research Directions. Future Internet 2023, 15, 398. [Google Scholar] [CrossRef]
- Zhang, G.; Hansen, J.P. Telepresence Robots for People with Special Needs: A Systematic Review. Int. J. Hum. Comput. Interact. 2022, 38, 1651–1667. [Google Scholar] [CrossRef]
- Lawrence, J.; Goldman, D.; Achar, S.; Blascovich, G.M.; Desloge, J.G.; Fortes, T.; Gomez, E.M.; Häberling, S.; Hoppe, H.; Huibers, A.; et al. Project Starline: A High-Fidelity Telepresence System. ACM Trans. Graph. 2021, 40, 16. [Google Scholar] [CrossRef]
- Leoste, J.; Strömberg-Järvis, K.; Robal, T.; Marmor, K.; Kangur, K.; Rebane, A.M. Testing Scenarios for Using Telepresence Robots in Healthcare Settings. Comput. Struct. Biotechnol. J. 2024, 24, 105–114. [Google Scholar] [CrossRef]
- Ibuki, S.; Okamoto, T.; Fujihashi, T.; Koike-Akino, T.; Watanabe, T. Rateless Deep Graph Joint Source Channel Coding for Holographic-Type Communication. In Proceedings of the GLOBECOM 2023—2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 3330–3335. [Google Scholar]
- Zhang, H.; Zhang, H.; Di, B.; Song, L. Holographic Integrated Sensing and Communications: Principles, Technology, and Implementation. IEEE Commun. Mag. 2023, 61, 83–89. [Google Scholar] [CrossRef]
- Park, I.; Sah, Y.J.; Lee, S.; Lee, D. Avatar-Mediated Communication in Video Conferencing: Effect of Self-Affirmation on Debating Participation Focusing on Moderation Effect of Avatar. Int. J. Hum. Comput. Interact. 2023, 39, 464–475. [Google Scholar] [CrossRef]
- Baker, S.; Waycott, J.; Carrasco, R.; Kelly, R.M.; Jones, A.J.; Lilley, J.; Dow, B.; Batchelor, F.; Hoang, T.; Vetere, F. Avatar-Mediated Communication in Social VR: An in-Depth Exploration of Older Adult Interaction in an Emerging Communication Platform. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems, Yokohama, Japan, 8–13 May 2021; ACM: New York, NY, USA, 2021. [Google Scholar]
- Sheng, M.; Zhou, D.; Bai, W.; Liu, J.; Li, H.; Shi, Y.; Li, J. Coverage Enhancement for 6G Satellite-Terrestrial Integrated Networks: Performance Metrics, Constellation Configuration and Resource Allocation. Sci. China Inf. Sci. 2023, 66, 130303. [Google Scholar] [CrossRef]
- Al Homssi, B.; Al-Hourani, A.; Wang, K.; Conder, P.; Kandeepan, S.; Choi, J.; Allen, B.; Moores, B. Next Generation Mega Satellite Networks for Access Equality: Opportunities, Challenges, and Performance. IEEE Commun. Mag. 2022, 60, 18–24. [Google Scholar] [CrossRef]
- Fu, I.-K.; Charbit, G.; Medles, A.; Lin, D.; Hung, S.-C.; Chen, C.-C.; Liao, S.; Calin, D. Satellite and Terrestrial Network Convergence on the Way toward 6G. IEEE Wirel. Commun. 2023, 30, 6–8. [Google Scholar] [CrossRef]
- Liang, J.; Chaudhry, A.U.; Chinneck, J.W.; Yanikomeroglu, H.; Kurt, G.K.; Hu, P.; Ahmed, K.; Martel, S. Latency versus Transmission Power Trade-off in Free-Space Optical (FSO) Satellite Networks with Multiple Inter-Continental Connections. IEEE Open J. Commun. Soc. 2023, 4, 3014–3029. [Google Scholar] [CrossRef]
- Bai, Y.; Zhao, H.; Zhang, X.; Chang, Z.; Jäntti, R.; Yang, K. Toward Autonomous Multi-UAV Wireless Network: A Survey of Reinforcement Learning-Based Approaches. IEEE Commun. Surv. Tutor. 2023, 25, 3038–3067. [Google Scholar] [CrossRef]
- Nazar, A.M.; Selim, M.Y.; Kamal, A.E. Mounting RIS Panels on Tethered and Untethered UAVs: A Survey. Arab. J. Sci. Eng. 2024, 49, 2857–2885. [Google Scholar] [CrossRef]
- Khakimov, A.; Elgendy, I.A.; Muthanna, A.; Mokrov, E.; Samouylov, K.; Maleh, Y.; El-Latif, A.A.A. Flexible Architecture for Deployment of Edge Computing Applications. Simul. Model. Pract. Theory 2022, 114, 102402. [Google Scholar] [CrossRef]
- Biswas, P.C.; Rani, S.; Hossain, M.A.; Islam, M.R.; Canning, J. Recent Developments in Smartphone Spectrometer Sample Analysis. IEEE J. Sel. Top. Quantum Electron. 2021, 27, 5500212. [Google Scholar] [CrossRef]
- Salman, M.; Garzón Ramos, D.; Birattari, M. Automatic Design of Stigmergy-Based Behaviours for Robot Swarms. Commun. Eng. 2024, 3, 30. [Google Scholar] [CrossRef]
- Shankar, V.; Shirakawa, N.; Ishihara, D. Novel Computational Design of Polymer Micromachined Insect-Mimetic Wings for Flapping-Wing Nano Air Vehicles. Biomimetics 2024, 9, 133. [Google Scholar] [CrossRef] [PubMed]
- Zhu, C.; Fu, X.; Zhang, J.; Qin, K.; Wu, C. Review of Portable near Infrared Spectrometers: Current Status and New Techniques. J. Near Infrared Spectrosc. 2022, 30, 51–66. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, J.; Poor, H.V. Optimal Resource Allocations for Statistical QoS Provisioning to Support mURLLC over FBC-EH-Based 6G THz Wireless Nano-Networks. IEEE J. Sel. Areas Commun. 2021, 39, 1544–1560. [Google Scholar] [CrossRef]
- Nair, M.M.; Tyagi, A.K. AI, IoT, Blockchain, and Cloud Computing: The Necessity of the Future. In Distributed Computing to Blockchain; Academic Press: Cambridge, MA, USA, 2023; pp. 189–206. [Google Scholar]
- Das, R.; Inuwa, M.M. A Review on Fog Computing: Issues, Characteristics, Challenges, and Potential Applications. Telemat. Inform. Rep. 2023, 10, 100049. [Google Scholar] [CrossRef]
- Hazra, A.; Rana, P.; Adhikari, M.; Amgoth, T. Fog Computing for Next-Generation Internet of Things: Fundamental, State-of-the-Art and Research Challenges. Comput. Sci. Rev. 2023, 48, 100549. [Google Scholar] [CrossRef]
- OpenFog. Available online: https://opcfoundation.org/markets-collaboration/openfog/ (accessed on 1 March 2024).
- Rao, A.R.; Elias-Medina, A. Designing an Internet of Things Laboratory to Improve Student Understanding of Secure IoT Systems. Internet Things Cyber-Phys. Syst. 2024, 4, 154–166. [Google Scholar] [CrossRef]
- Rogdakis, K.; Psaltakis, G.; Fagas, G.; Quinn, A.; Martins, R.; Kymakis, E. Hybrid Chips to Enable a Sustainable Internet of Things Technology: Opportunities and Challenges. Discov. Mater. 2024, 4, 4. [Google Scholar] [CrossRef]
- Pakmehr, A.; Gholipour, M.; Zeinali, E. ETFC: Energy-Efficient and Deadline-Aware Task Scheduling in Fog Computing. Sustain. Comput. Inform. Syst. 2024, 43, 100988. [Google Scholar] [CrossRef]
- Malik, U.M.; Javed, M.A.; Zeadally, S.; Islam, S. ul Energy-Efficient Fog Computing for 6G-Enabled Massive IoT: Recent Trends and Future Opportunities. IEEE Internet Things J. 2022, 9, 14572–14594. [Google Scholar] [CrossRef]
- Bi, Q.; Liang, W.; Dai, M. P-RAN, a Fog Computing Platform for 5G and 6G Services. IEEE Commun. Mag. 2023, 61, 78–84. [Google Scholar] [CrossRef]
- Srirama, S.N. A Decade of Research in Fog Computing: Relevance, Challenges, and Future Directions. Softw. Pract. Exp. 2024, 54, 3–23. [Google Scholar] [CrossRef]
- Arivazhagan, C.; Natarajan, V. A Survey on Fog Computing Paradigms, Challenges and Opportunities in IoT. In Proceedings of the 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 28–30 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 385–0389. [Google Scholar]
- Yi, S.; Hao, Z.; Qin, Z.; Li, Q. Fog Computing: Platform and Applications. In Proceedings of the 2015 Third IEEE Workshop on Hot Topics in Web Systems and Technologies (HotWeb), Washington, DC, USA, 12–13 November 2015; IEEE: Piscataway, NJ, USA, 2015. [Google Scholar]
- Sellami, Y.; Imine, Y.; Gallais, A. A Verifiable Data Integrity Scheme for Distributed Data Sharing in Fog Computing Architecture. Future Gener. Comput. Syst. 2024, 150, 64–77. [Google Scholar] [CrossRef]
- Sabireen, H.; Neelanarayanan, V. A Review on Fog Computing: Architecture, Fog with IoT, Algorithms and Research Challenges. ICT Express 2021, 7, 162–176. [Google Scholar] [CrossRef]
- Pallewatta, S.; Kostakos, V.; Buyya, R. Placement of Microservices-Based IoT Applications in Fog Computing: A Taxonomy and Future Directions. ACM Comput. Surv. 2023, 55, 321. [Google Scholar] [CrossRef]
- Mahmud, R.; Ramamohanarao, K.; Buyya, R. Application Management in Fog Computing Environments: A Taxonomy, Review and Future Directions. ACM Comput. Surv. 2021, 53, 88. [Google Scholar] [CrossRef]
- Premalatha, B.; Prakasam, P. A Review on FoG Computing in 5G Wireless Technologies: Research Challenges, Issues and Solutions. Wirel. Pers. Commun. 2024, 134, 2455–2484. [Google Scholar] [CrossRef]
- Karagiannis, V.; Schulte, S. Comparison of Alternative Architectures in Fog Computing. In Proceedings of the 2020 IEEE 4th International Conference on Fog and Edge Computing (ICFEC), Melbourne, VIC, Australia, 11–14 May 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar]
- Ateya, A.A.; Soliman, N.F.; Alkanhel, R.; Alhussan, A.A.; Muthanna, A.; Koucheryavy, A. Lightweight Deep Learning-Based Model for Traffic Prediction in Fog-Enabled Dense Deployed IoT Networks. J. Electr. Eng. Technol. 2023, 18, 2275–2285. [Google Scholar] [CrossRef]
- Bellavista, P.; Giannelli, C.; Montenero, D.D.P.; Poltronieri, F.; Stefanelli, C.; Tortonesi, M. HOlistic pRocessing and NETworking (HORNET): An Integrated Solution for IoT-Based Fog Computing Services. IEEE Access 2020, 8, 66707–66721. [Google Scholar] [CrossRef]
- Khanagha, S.; Ansari, S.; Paroutis, S.; Oviedo, L. Mutualism and the Dynamics of New Platform Creation: A Study of Cisco and Fog Computing. Strateg. Manag. J. 2022, 43, 476–506. [Google Scholar] [CrossRef]
- Gambhir, S.; Tomar, P.; Jain, P. Fog Computing: The next Generation Computing Paradigm. In Computational Intelligence in Analytics and Information Systems; Apple Academic Press: New York, NY, USA, 2023; pp. 65–77. ISBN 9781003332367. [Google Scholar]
- Muthanna, A.; Ateya, A.A.; Balushi, M.A.; Kirichek, R. D2D Enabled Communication System Structure Based on Software Defined Networking for 5G Network. In Proceedings of the 2018 International Symposium on Consumer Technologies (ISCT), St. Petersburg, Russia, 11–12 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 41–44. [Google Scholar]
- Pathak, Y.; Prashanth, P.V.N.; Tiwari, A. AI Meets SDN: A Survey of Artificial Intelligent Techniques Applied to Software-Defined Networks. In 6G Enabled Fog Computing in IoT: Applications and Opportunities; Springer: Cham, Switzerland, 2023; pp. 395–412. [Google Scholar]
- Nawaz, O.; Fiedler, M.; Khatibi, S. QoE-Based Performance Comparison of AVC, HEVC, and VP9 on Mobile Devices with Additional Influencing Factors. Electronics 2024, 13, 329. [Google Scholar] [CrossRef]
- Moina-Rivera, W.; Garcia-Pineda, M.; Gutiérrez-Aguado, J.; Alcaraz-Calero, J.M. Cloud Media Video Encoding: Review and Challenges. Multimed. Tools Appl. 2024, 83, 81231–81278. [Google Scholar] [CrossRef]
- Dumic, E.; da Silva Cruz, L.A. Three-Dimensional Point Cloud Applications, Datasets, and Compression Methodologies for Remote Sensing: A Meta-Survey. Sensors 2025, 25, 1660. [Google Scholar] [CrossRef] [PubMed]
- Golpayegani, F.; Chen, N.; Afraz, N.; Gyamfi, E.; Malekjafarian, A.; Schäfer, D.; Krupitzer, C. Adaptation in Edge Computing: A Review on Design Principles and Research Challenges. ACM Trans. Auton. Adapt. Syst. 2024, 19, 19. [Google Scholar] [CrossRef]
- Simpson, A.; Alshaali, M.; Tu, W.; Asghar, M.R. Quick UDP Internet Connections and Transmission Control Protocol in Unsafe Networks: A Comparative Analysis. IET Smart Cities 2024, 6, 351–360. [Google Scholar] [CrossRef]
- Mahmoud, H.; Abozariba, R. A Systematic Review on WebRTC for Potential Applications and Challenges beyond Audio Video Streaming. Multimed. Tools Appl. 2024, 84, 2909–2946. [Google Scholar] [CrossRef]
- Hamdi, W.; Ksouri, C.; Bulut, H.; Mosbah, M. Network Slicing-Based Learning Techniques for IoV in 5G and beyond Networks. IEEE Commun. Surv. Tutor. 2024, 26, 1989–2047. [Google Scholar] [CrossRef]
- Alsadie, D. A Comprehensive Review of AI Techniques for Resource Management in Fog Computing: Trends, Challenges, and Future Directions. IEEE Access 2024, 12, 118007–118059. [Google Scholar] [CrossRef]
- Alsadie, D. Artificial Intelligence Techniques for Securing Fog Computing Environments: Trends, Challenges, and Future Directions. IEEE Access 2024, 12, 151598–151648. [Google Scholar] [CrossRef]
- Smida, K.; Tounsi, H.; Frikha, M.; Song, Y.-Q. FENS: Fog-Enabled Network Slicing in SDN/NFV-Based IoV. Wirel. Pers. Commun. 2023, 128, 2175–2202. [Google Scholar] [CrossRef]
- Ansar, S.A.; Samriya, J.K.; Kumar, M.; Gill, S.S.; Khan, R.A. Intelligent Fog-IoT Networks with 6G Endorsement: Foundations, Applications, Trends and Challenges. In 6G Enabled Fog Computing in IoT; Springer Nature: Cham, Switzerland, 2023; pp. 287–307. ISBN 9783031301001. [Google Scholar]
- Wang, X.; Shen, T.; Zhang, Y.; Chen, X. An Efficient Topology Emulation Technology for the Space-Air-Ground Integrated Network. In Proceedings of the IEEE INFOCOM 2023—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), New York, NY, USA, 17–20 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–8. [Google Scholar]
- Mahboob, S.; Liu, L. Revolutionizing Future Connectivity: A Contemporary Survey on AI-Empowered Satellite-Based Non-Terrestrial Networks in 6G. IEEE Commun. Surv. Tutor. 2024, 26, 1279–1321. [Google Scholar] [CrossRef]
- Wang, R.; Liu, K.; Dang, Z.; Wang, X.; Dang, F.; Sun, Y.; Tong, Y.; Zhao, H.; Liu, Y. Understanding the Quality of User Experience in Telepresence Systems from an Information Theory Perspective. IEEE Trans. Consum. Electron. 2024, 1. [Google Scholar] [CrossRef]
- Shin, H.; Park, S.; Kim, L.; Kim, J.; Kim, T.; Song, Y.; Lee, S. The Future Service Scenarios of 6G Telecommunications Technology. Telecomm. Policy 2023, 48, 102678. [Google Scholar] [CrossRef]
- Zhang, X.; Xu, M.; Tan, R.; Niyato, D. Learning-Based Auction for Matching Demand and Supply of Holographic Digital Twin over Immersive Communications. IEEE Trans. Multimed. 2023, 26, 5884–5896. [Google Scholar] [CrossRef]
- Zawish, M.; Dharejo, F.A.; Khowaja, S.A.; Raza, S.; Davy, S.; Dev, K.; Bellavista, P. AI and 6G into the Metaverse: Fundamentals, Challenges and Future Research Trends. IEEE Open J. Commun. Soc. 2024, 5, 730–778. [Google Scholar] [CrossRef]
- Arthanat, S.; Rossignol, H.; Preble, E.; Grimm, K.; Corvini, M.; Wilcox, J.; Aytur, S.; Doyle, M. Perspectives on a Telepresence Robot at an Independent Living Facility: Lessons Learned and Implications. J. Enabling Technol. 2023, 18, 107–119. [Google Scholar] [CrossRef]
- Ali, A.; Hussain, S.M.; Begh, G.R. 6G and IOT Use Cases. In 6G Wireless; CRC Press: Boca Raton, FL, USA, 2023; pp. 315–340. [Google Scholar]
- Ometov, A.; Molua, O.L.; Komarov, M.; Nurmi, J. A Survey of Security in Cloud, Edge, and Fog Computing. Sensors 2022, 22, 927. [Google Scholar] [CrossRef]
- Burhan, M.; Alam, H.; Arsalan, A.; Rehman, R.A.; Anwar, M.; Faheem, M.; Ashraf, M.W. A Comprehensive Survey on the Cooperation of Fog Computing Paradigm-Based IoT Applications: Layered Architecture, Real-Time Security Issues, and Solutions. IEEE Access 2023, 11, 73303–73329. [Google Scholar] [CrossRef]
- IEEE 1934-2018; IEEE Standard for Adoption of OpenFog Reference Architecture for Fog Computing. IEEE Standards Association: Piscataway, NJ, USA, 2018. Available online: https://standards.ieee.org/ieee/1934/7137/ (accessed on 16 March 2025).
- Dahmen-Lhuissier, S. Multi-Access Edge Computing (MEC). Available online: https://www.etsi.org/technologies/multi-access-edge-computing (accessed on 16 March 2025).
- Flynn, K. Edge Computing. Available online: https://www.3gpp.org/technologies/edge-computing (accessed on 16 March 2025).
- System Architecture for the 5G System (5GS). Technical Specification (TS) 23.501. Release 15. 3GPP. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3144 (accessed on 10 March 2025).
- ETSI GS MEC 021 V2.2.1. Available online: https://www.etsi.org/deliver/etsi_gs/MEC/001_099/021/02.02.01_60/gs_mec021v020201p.pdf (accessed on 10 March 2025).
- Kaur, K.; Singh, A.; Sharma, A. A Systematic Review on Resource Provisioning in Fog Computing. Trans. Emerg. Telecommun. Technol. 2023, 34, e4731. [Google Scholar] [CrossRef]
| KPIs | 5G | 6G |
|---|---|---|
| Peak data rate | 10 GHz | 1 THz |
| User experience data rate | 1 GHz | >10 GHz |
| Bandwidth | 1 GHz | 100 GHz |
| Carrier bandwidth | 400 MHz | Not defined |
| Channel | Random | Controlled |
| Operating bandwidth | Up to 400 MHz for sub-6 GHz bands Up to 3.25 GHz for mmWave bands | Up to 400 MHz for sub-6 GHz bands Up to 3.25 GHz for mmWave bands |
| Latency | 1ms | 0.1ms |
| Peak spectral efficiency | 30 bps/Hz | 60 bps/Hz |
| Artificial intelligence | Partial | Fully |
| Service level | Limited (VR/AR) | Widely (Tactile) |
| Max. frequency | 90 GHz | 10 THz |
| Mobility | 500 km/h | >1000 km/h |
| Coverage | About 70% | >99% |
| Reliability | About 99.9% | >99.999% |
| Feature | Cisco Fog Model | Edge-Cloud Hybrid | Proposed Multi-Tier Fog Model |
|---|---|---|---|
| Latency | Moderate (Higher than cloud but lacks defined aggregation nodes) | Low (Offloads computation to the cloud dynamically) | Very low (Optimized with hierarchical processing) |
| Energy efficiency | Moderate (Fog nodes process locally but lack power optimization strategies) | High (Cloud resources are used efficiently, reducing edge power consumption) | Very high (Efficient workload distribution across tiers) |
| Scalability | Low (Ambiguous fog node management) | High (Scalability depends on cloud resources) | Very high (Hierarchical fog architecture allows elastic scaling) |
| Security | Moderate (Decentralized data storage increases attack surface) | High (Cloud security mechanisms protect data) | Very high (Multitier security with edge encryption and access control) |
| Deployment complexity | High (Unclear management strategy) | Moderate (Requires cloud integration) | Low (Simplified due to multitier automation and orchestration) |
| Best use case | Basic IoT applications | AI-driven real-time processing | Ultra-low latency 6G applications (e.g., telepresence, industrial IoT) |
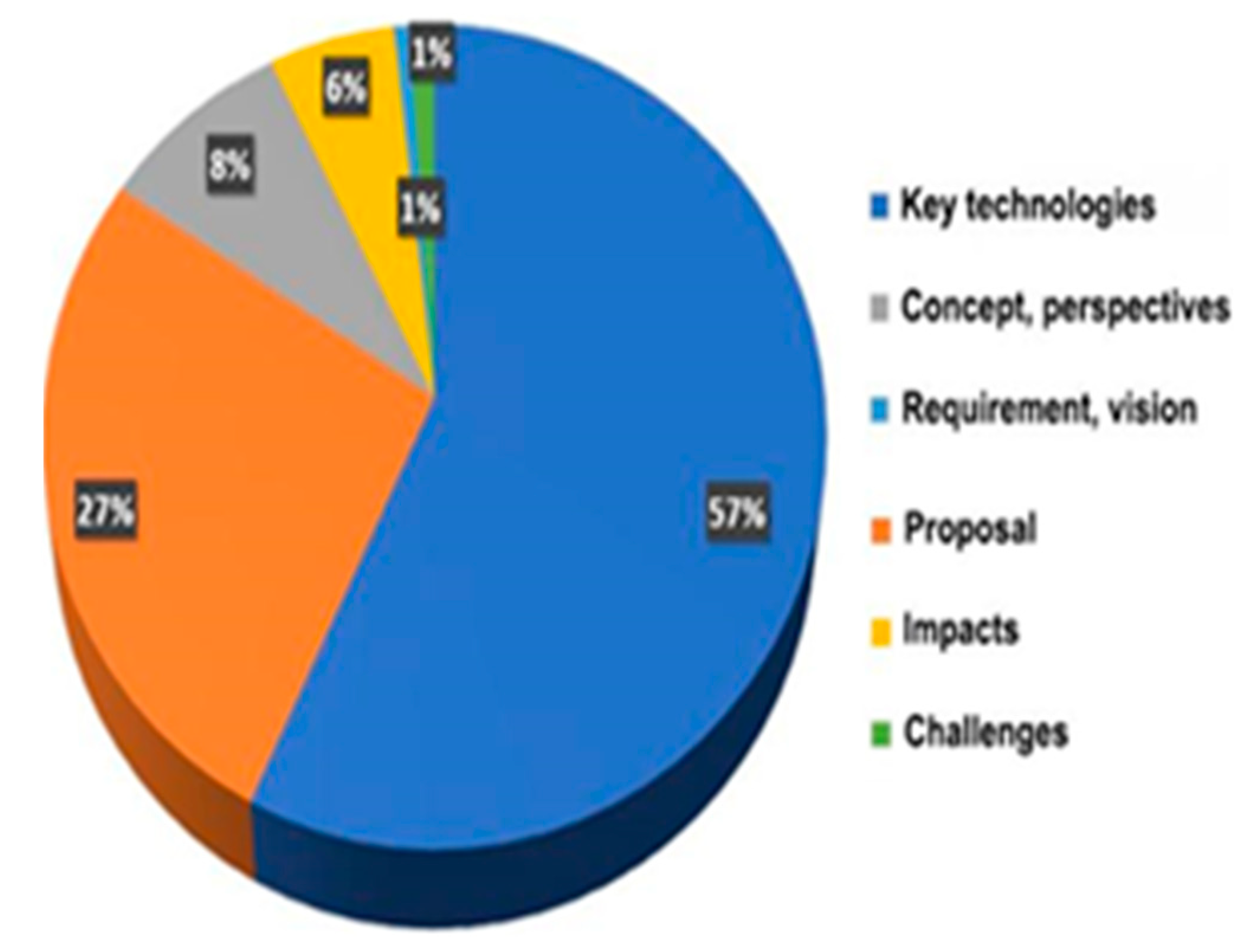
| Topic of Research | Number of Studies |
|---|---|
| Key technologies | 403 |
| Proposal | 190 |
| Concept and perspectives | 60 |
| Impacts | 40 |
| Requirement and vision | 6 |
| Challenges | 7 |
| Security Concern | Mitigation Strategy |
|---|---|
| Data encryption | Implement end-to-end encryption (E2EE) using AES-256 or homomorphic encryption. |
| Access control and authentication | Utilize zero trust architecture (ZTA), biometric authentication, and blockchain-based identity verification. |
| Secure communication | Deploy TLS 1.3 with mutual authentication and software-defined security (SDS) for dynamic policy enforcement. |
| Intrusion detection and anomaly detection | Incorporate AI-driven intrusion detection systems (IDS) and behavioral analytics for real-time anomaly detection. |
| Data integrity and secure storage | Use distributed ledger technology (DLT) to ensure integrity across fog nodes. |
| Privacy-preserving computing | Implement differential privacy, federated learning, and secure multiparty computation (SMPC) to prevent unauthorized data exposure. |
| Pillar | Description |
|---|---|
| Security | Ensures secure data transmission, storage, and processing across fog nodes using encryption, authentication, and blockchain-based security mechanisms. |
| Scalability | Supports the dynamic expansion of fog nodes, enabling the real-time provisioning of computational resources based on demand. |
| Openness | Provides open, standardized APIs and protocols for vendor-neutral integration across heterogeneous devices and platforms. |
| Autonomy | Supports decentralized decision-making, allowing fog nodes to process and act on data without requiring continuous cloud interaction. |
| Programmability | Enables software-defined control mechanisms, allowing flexible deployment and management of fog applications. |
| Ruggedization | Ensures the ability of fog systems to operate in harsh environments, including industrial IoT and mission-critical systems. |
| Hierarchy | Defines multitier fog node structures that optimize workload distribution between the cloud, fog, and edge layers. |
| Latency | Minimizes data transmission delays by processing data closer to the source, which is critical for real-time applications such as telepresence and autonomous vehicles. |
| Layer | Functionality | Example Technologies |
|---|---|---|
| Application layer | Provides interfaces for users and services to interact with fog-based applications. | WebRTC, MQTT, Telepresence APIs |
| Orchestration layer | Manages distributed fog nodes, schedules tasks, and allocates resources dynamically. | AI-based resource schedulers, NFV, SDN Controllers |
| Data management layer | Handles data aggregation, filtering, and processing at different fog nodes. | Apache Kafka, TensorFlow Federated |
| Network layer | Ensures efficient data routing between fog, cloud, and edge devices. | 5G/6G NR, time-sensitive networking (TSN) |
| Security layer | Implements identity authentication, access control, and encryption for secure communication. | Blockchain-based identity management, TLS, zero trust security |
| Infrastructure layer | Consists of fog nodes, edge devices, and cloud servers that execute computations. | GPUs, TPUs, MEC Servers, IoT Gateways |
| Aspect | IEEE 1934 Contributions |
|---|---|
| Low latency | Reduces latency in real-time telepresence applications by enabling localized processing at fog nodes. |
| Interoperability | Provides standardized APIs and protocols, ensuring seamless integration of different telepresence platforms. |
| Security and privacy | Implements secure access control and end-to-end encryption for telepresence data. |
| Scalability | Allows dynamic provisioning of computational resources for high-bandwidth holographic communication. |
| AI and edge intelligence | Supports federated learning and AI-driven decision-making at the edge for autonomous operations. |
| Component | 3GPP Terminology (Rel. 16–18) | Fog Computing Equivalent |
|---|---|---|
| Edge processing | Multiaccess edge computing | Fog nodes |
| Local data routing | Local breakout via UPF | Fog layer for traffic offloading |
| Low-latency services | uRLLC | Fog-enabled real-time applications |
| Distributed AI | Edge AI in 6G RAN | AI-driven fog processing |
| Interoperability | Network slicing and APIs for verticals | OpenFog standard (IEEE 1934) |
| Aspect | 3GPP (5G/6G Fog-Enabled Features) | ETSI MEC | IEEE 1934 (OpenFog Standard) |
|---|---|---|---|
| Standardization | 3GPP TS 23.501, 23.548 (Edge processing) [97] | ETSI MEC specifications (e.g., MEC 021) [98] | IEEE 1934: OpenFog reference model [94] |
| Scope | Focused on telecom networks | Edge computing within telecom networks | Distributed computing across various layers. It represents a generalized fog computing framework |
| Interoperability | Works within mobile networks | Works with 5G core, integrates NFV and SDN | Works across cloud-edge and provides general API-based interoperability |
| Use cases | 5G/6G, IoT, C-V2X, XR | Low-latency applications (e.g., video analytics, V2X) | Ultrareliable low-latency applications, Industrial IoT, and smart cities |
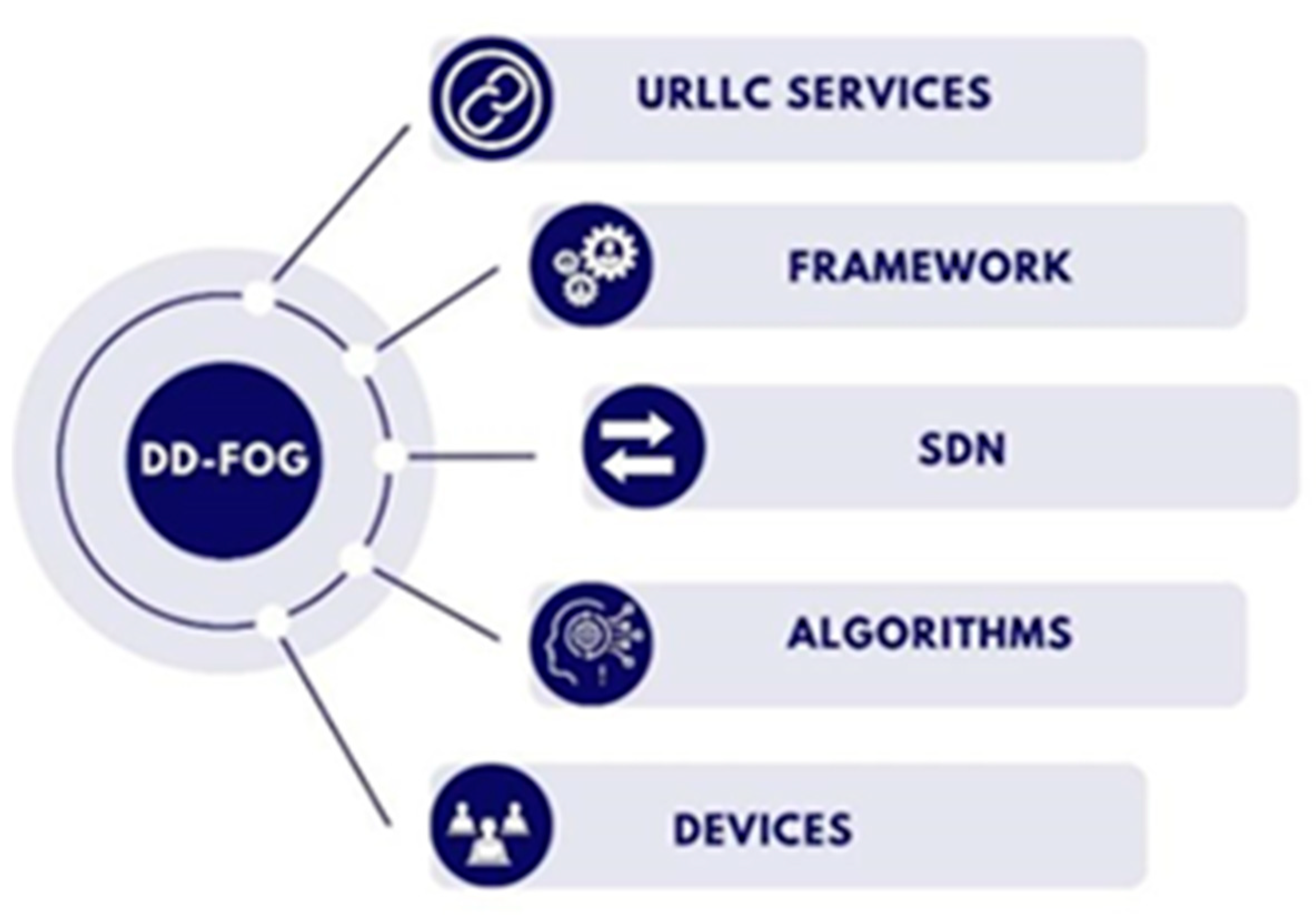
| Research Direction | Discussion |
|---|---|
| URLLC service | The research in this direction aims to develop methods that provide high reliability and low latency communications based on fog and mobile fog nodes. |
| SDN network | The research in this direction aims to manage and coordinate fog computing devices flexibly and efficiently. |
| Framework | The research in this direction aims to develop software frameworks that facilitate the easy and efficient deployment and management of fog computing applications. This also includes developing reliable platforms for fog nodes. |
| Algorithms | The research in this direction aims to develop algorithms to optimize resource utilization, data processing, and application allocation in a fog computing environment. |
| Devices | The research in this direction aims to develop energy-efficient fog computing devices that are high-performing and adaptable to various environments. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Thang, D.V.; Volkov, A.; Muthanna, A.; Koucheryavy, A.; Ateya, A.A.; Jayakody, D.N.K. Future of Telepresence Services in the Evolving Fog Computing Environment: A Survey on Research and Use Cases. Sensors 2025, 25, 3488. https://doi.org/10.3390/s25113488
Thang DV, Volkov A, Muthanna A, Koucheryavy A, Ateya AA, Jayakody DNK. Future of Telepresence Services in the Evolving Fog Computing Environment: A Survey on Research and Use Cases. Sensors. 2025; 25(11):3488. https://doi.org/10.3390/s25113488
Chicago/Turabian StyleThang, Dang Van, Artem Volkov, Ammar Muthanna, Andrey Koucheryavy, Abdelhamied A. Ateya, and Dushantha Nalin K. Jayakody. 2025. "Future of Telepresence Services in the Evolving Fog Computing Environment: A Survey on Research and Use Cases" Sensors 25, no. 11: 3488. https://doi.org/10.3390/s25113488
APA StyleThang, D. V., Volkov, A., Muthanna, A., Koucheryavy, A., Ateya, A. A., & Jayakody, D. N. K. (2025). Future of Telepresence Services in the Evolving Fog Computing Environment: A Survey on Research and Use Cases. Sensors, 25(11), 3488. https://doi.org/10.3390/s25113488











