Wireless Sensor Network Deployment: Architecture, Objectives, and Methodologies
Abstract
1. Introduction
- 1.
- Reviews the general architecture of sensor nodes, identifying how hardware and software characteristics affect deployment strategies.
- 2.
- Categorizes deployment objectives and aligns them with practical application scenarios.
- 3.
- Compares sensing models and explains their role in defining coverage constraints.
- 4.
- Classifies deployment methodologies (deterministic, random, hybrid), highlighting their trade-offs, constraints, and suitability.
- 5.
- Critically analyzes the strengths and limitations of current techniques.
- 6.
- Identifies open research challenges and proposes future research directions for more intelligent, adaptive, and resilient deployments.
2. Sensor Nodes
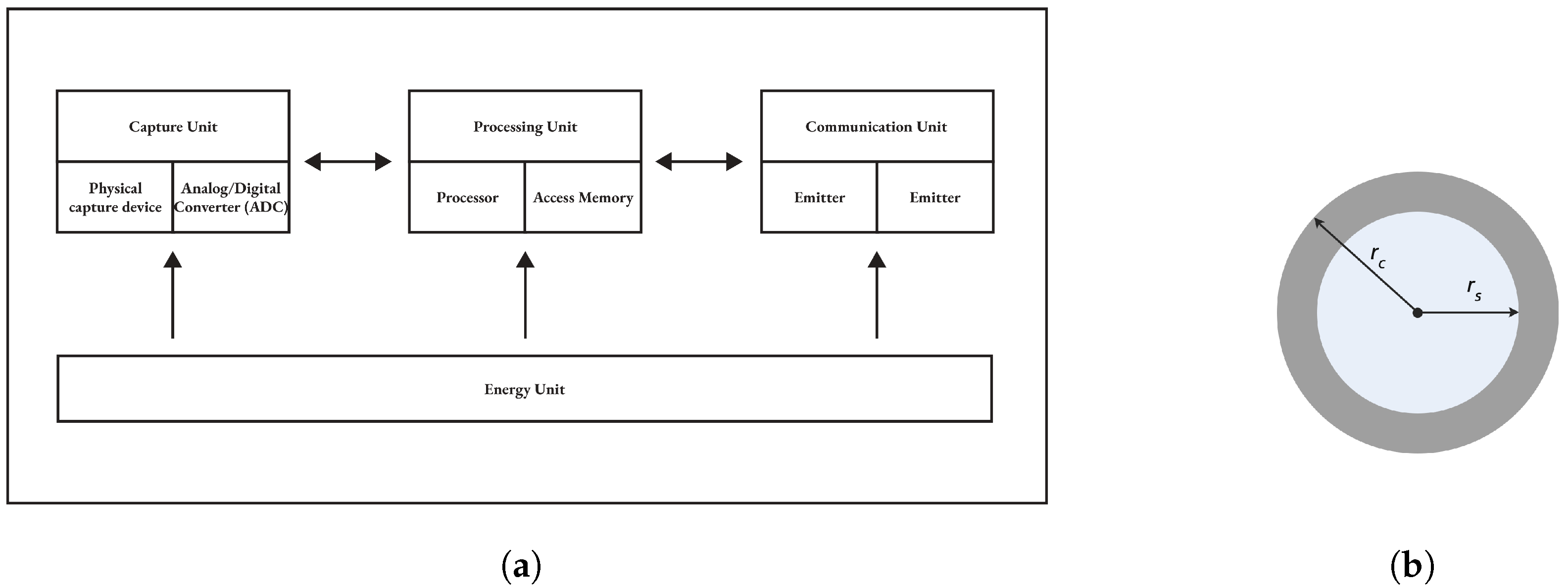
2.1. Components of a Sensor Node
- The capture unit is composed of two sub-units, including a physical capture device that takes information from the local environment and an analog/digital converter called ADC (Analog to Digital Converter). The sensor is responsible for providing analog signals that the ADC transforms into a digital signal understandable by the processing unit.
- The processing unit is generally a processor coupled to a random access memory. Its role is to control the proper functioning of the other units. On some sensors, it can embed an operating system to operate the sensor. It can also be coupled to a storage unit, which will be used to record the information transmitted by the capture unit. This unit can also be equipped with an intelligence enabling it to analyze/process the data acquired by the capture unit.
- The communication unit performs all transmissions and receptions of data on a wireless medium. It can be of the optical type or of the radio-frequency type.
- The unit of energy, usually a battery of small size and limited capacity. This often makes energy a sensor’s most valuable resource, as it directly affects its lifespan.
2.2. Types of Sensor Nodes
- The regular node (RN) which has a transmission unit and a data processing unit;
- The sensor node or source node, which is a regular node, equipped with an acquisition or detection unit;
- The actuator node also called robot which is a regular node which has a unit thanks to which it performs specific tasks (mechanical tasks);
- The gateway node which is a regular node that broadcasts traffic into the network;
- The sink node, which is a regular node with a serial converter connected to a second communication unit. The second communication unit provides a rebroadcast of the data coming from the sensor nodes to a user or to other networks (Internet, for example). It is sometimes called a base station. Table 1 summarizes the types of nodes in a WSN.
- Source Node (SN): Detects phenomena occurring in its immediate environment and broadcasts them either directly or by multiple hops.
- Relay Node (RN): Gathers and relays the measurements coming from the SN. In a flat architecture, an SN can be considered an RN potential. In a 2-level architecture, an RN plays its role for one or more SN. In a 2-tier architecture, the transmission capacity of the RN is assumed to be higher than that of the SN.
- Data Collector Node (DC): In addition to being an RN, it collects measurements from SNs and, potentially, aggregates them. In general, SNs are grouped into several clusters, and one DC is used as the cluster leader for each cluster.
3. Types of Deployment in Wireless Sensor Network
3.1. Deterministic Deployment and Stochastic Deployment
3.2. Single-Objective Deployment and Multi-Objective Deployment
3.3. Homogeneous Deployment and Heterogeneous Deployment
3.4. Static Deployment and Dynamic Deployment
4. Objectives to Be Met During Deployment
4.1. Coverage
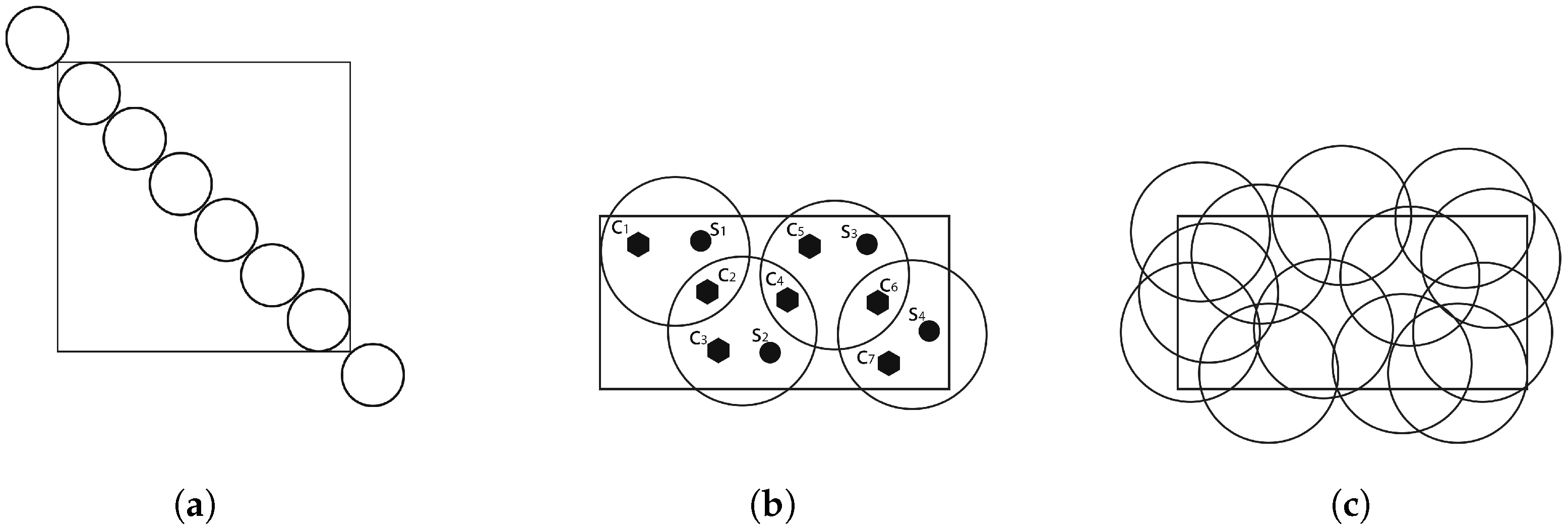
- Barrier coverage: The objective is to obtain an arrangement of sensors with the task of maximizing the probability of detecting the penetration of a specific target through the barrier. Here, sensors are usually deployed not to detect/track events in an area of interest, but to detect intruders attempting to enter that area. As shown in Figure 2a, the protective barrier formed by the sensors ensures that any movement through it is detected. This type of coverage is suitable for motion or intrusion detection applications.
- Target coverage: The objective is to cover a set of targets whose position is known and which must be monitored. As illustrated by Figure 2b, this coverage scheme focuses on determining the positions of the sensor nodes, guaranteeing effective coverage for a limited number of stationary targets. Each target must be covered by at least one sensor node. The coverage of a target is defined as the number of sensor nodes covering it. As a result, deployment costs are lower because fewer sensors are used compared to the number required to cover the entire area.
- Area coverage: The main purpose is to cover (monitor) a region and maximize the detection rate of a specific area. Depending on the required deployment requirements, full or partial coverage may be requested. However, if the number of sensors is insufficient, complete coverage cannot be achieved, and the objective will therefore be to maximize the coverage rate as shown in Figure 2c.
4.2. Connectivity
4.3. Overlap
4.4. Energy Efficiency
4.5. Node Synchronization
4.6. Localization Techniques
4.7. Fault Tolerance
4.8. Number of Nodes
5. Detection Models
5.1. Binary Model
5.2. Probabilistic Model
5.2.1. The Elves Model
5.2.2. The Shadow Fading Model
- x is the random variable representing the signal strength;
- is the mean of the logarithm of the signal strength (in decibels),
- is the standard deviation of the logarithm of the signal strength (in decibels);
- is a mathematical constant approximately equal to 3.14159.
5.2.3. The Rayleigh Fading Model
- x is the random variable representing the amplitude of the signal;
- is a scale parameter that determines the spread of the distribution.
5.2.4. The Nakagami-m Fading Model
- x is the random variable representing the amplitude of the signal;
- m is the fading parameter that determines the severity of fading ();
- is the gamma function;
- is the average power of the received signal.
6. Methodologies for Deploying
6.1. Grid-Based Techniques
6.2. Techniques Based on Virtual Force
6.3. Techniques Based on Computational Geometry
6.4. Heuristic Optimization
- The simulated annealing, which will traverse the search space while allowing itself to deteriorate its solution to leave the local optima. During the process, the annealing will accept less and less of these deteriorations, which will make it converge towards an optimum, which is hoped to be global [60].
- Search with taboos, unlike simulated annealing, is deterministic and has a notion of memory. The selection of the best neighbor of a solution leads the algorithm to detect the local optima, and since the examination of the search space is conducted by limiting the neighborhood of the solution by making certain moves “taboo”, the algorithm must theoretically examine the global optimum [60]. In [61], the authors proposed a low-power multi-hop adaptive clustering hierarchy protocol. In their work, they propose an optimization of the head of a cluster in the RCSFs by working on the selection of the optimal path in the routing so as to improve the lifetime as well as the energy efficiency of the network. To obtain better results, they used, in addition to the method of optimization by swarms of particles, the research with taboos. This allowed them to avoid the problems of poor local optima that can be encountered using only certain metaheuristic techniques, in particular, optimization by particle swarms. By doing so, they manage to improve the number of clusters formed, the percentage of alive nodes and the reduction in the average packet loss rate and the average end-to-end delay in the RCSF.
- Evolutionary algorithms, resulting from Darwin’s theory of evolution, manipulate several solutions at the same time by combining them to form new solutions. Having a population of solutions simplifies the examination of the search space. The best solutions will be chosen to participate in the creation of new solutions, which will favor the combinations of “good characteristics”, and will make it possible to find a global optimum [60]. Several works [24,25,26,27,28,29,31,62] use, for example, genetic algorithms in the deployment of RCSFs to achieve different objectives. In these works, the authors generally propose an optimal compromise between the coverage, the connectivity, and the lifetime of the network. While the authors of [24,25] worked on how to maximize area coverage in the deployment of homogeneous wireless sensor networks based on an efficient genetic algorithm, the authors of [27], on the other hand, focused on a deployment seeking to maximize target coverage. In [31], the main objective of the authors was to present a dynamic deployment technique based on a genetic algorithm in order to maximize the area coverage with the smallest number of nodes while minimizing overlaps between neighboring nodes. In [35], the authors proposed a genetic algorithm approach for placement of k-coverage and m-connected nodes in target-based wireless sensor networks. Given a set of target points, they found the minimum number of potential positions to place the sensor nodes respecting both coverage and connectivity by proposing a scheme based on a genetic algorithm.
7. Open Issues and Future Research Directions in WSNs
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Heydarishahreza, N.; Ebadollahi, S.; Vahidnia, R.; Dian, F.J. Wireless Sensor Networks Fundamentals: A Review. In Proceedings of the 2020 11th IEEE Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Virtual, 4–7 November 2020; pp. 0001–0007. [Google Scholar] [CrossRef]
- TASS. Russian Military Deploying SOSUS-like Global Maritime Surveillance System Named Garmoniya. 2017. Available online: https://armyrecognition.com/focus-analysis-conflicts/navy/naval-technology/russian-military-deploying-sosus-like-global-maritime-surveillance-system-named-garmoniya (accessed on 19 July 2022).
- Deif, D.; Gadallah, Y. Classification of Wireless Sensor Networks Deployment Techniques. IEEE Commun. Surv. Tutor. 2014, 16, 834–855. [Google Scholar] [CrossRef]
- Bojkovic, Z.; Bakmaz, B. A survey on wireless sensor networks deployment. Wseas Trans. Commun. 2008, 7, 1172–1181. [Google Scholar]
- Abdollahzadeh, S.; Navimipour, N.J. Deployment strategies in the wireless sensor network: A comprehensive review. Comput. Commun. 2016, 91–92, 1–16. [Google Scholar] [CrossRef]
- Barrenetxea, G.; Ingelrest, F.; Schaefer, G.; Vetterli, M. The hitchhiker’s guide to successful wireless sensor network deployments. In Proceedings of the 6th ACM Conference on Embedded Network Sensor Systems, Raleigh, NC, USA, 5–7 November 2008; Association for Computing Machinery: New York, NY, USA, 2008. SenSys ’08. pp. 43–56. [Google Scholar] [CrossRef]
- Larbi, R. Déploiement Optimal des Nœuds de Capteurs Employant le Clustering K-Means et un Algorithme Génétique. Master’s Thesis, École de Technologie Supérieure, Montréal, QC, Canada, 2021. [Google Scholar]
- Zhang, M. Optimisation de la Couverture de Communication et de Mesure dans les Réseaux de Capteurs. Ph.D. Thesis, Université de Reims Champagne-Ardenne, Reims, France, 2015. [Google Scholar]
- Priyadarshi, R.; Gupta, B.; Anurag, A. Deployment techniques in wireless sensor networks: A survey, classification, challenges, and future research issues. J. Supercomput. 2020, 76, 7333–7373. [Google Scholar] [CrossRef]
- Kone, C.T. Conception de l’architecture d’un réseau de capteurs sans fil de grande dimension. Ph.D. Thesis, Université Henri Poincaré-Nancy I, Nancy, France, 2011. [Google Scholar]
- Priyadarshi, R.; Gupta, B.; Anurag, A. Wireless Sensor Networks Deployment: A Result Oriented Analysis. Wirel. Pers. Commun. 2020, 113, 843–866. [Google Scholar] [CrossRef]
- Zheng, K.; Fu, J.; Liu, X. Relay Selection and Deployment for NOMA Enabled Multi-UAV-assisted WSN. IEEE Sens. J. 2025, 25, 16235–16249. [Google Scholar] [CrossRef]
- Mnasri, S. Contributions to the Optimized Deployment of Connected Sensors on the Internet of Things Collection Networks. Ph.D. Thesis, Université Toulouse Jean Jaurès, Toulouse, France, 2018. [Google Scholar]
- He, Y.; Huang, F.; Wang, D.; Chen, B.; Li, T.; Zhang, R. Performance Analysis and Optimization Design of AAV-Assisted Vehicle Platooning in NOMA-Enhanced Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2025, 1–10. [Google Scholar] [CrossRef]
- Amutha, J.; Sharma Sandeep, N.J. WSN Strategies Based on Sensors, Deployment, Sensing Models, Coverage and Energy Efficiency: Review, Approaches and Open Issues. Wirel. Pers. Commun. 2020, 111, 1089–1115. [Google Scholar] [CrossRef]
- Deng, X.; Yu, Z.; Tang, R.; Qian, X.; Yuan, K.; Liu, S. An Optimized Node Deployment Solution Based on a Virtual Spring Force Algorithm for Wireless Sensor Network Applications. Sensors 2019, 19, 1817. [Google Scholar] [CrossRef]
- Kim, Y.h.; Kim, C.M.; Yang, D.S.; Oh, Y.j.; Han, Y.H. Regular sensor deployment patterns for p-coverage and q-connectivity in wireless sensor networks. In Proceedings of the International Conference on Information Network, Bali, Indonesia, 1–3 February 2012; pp. 290–295. [Google Scholar] [CrossRef]
- Liu, Y.; Suo, L.; Sun, D.; Wang, A. A virtual square grid-based coverage algorithm of redundant node for wireless sensor network. J. Netw. Comput. Appl. 2013, 36, 811–817. [Google Scholar] [CrossRef]
- Khoufi, I.; Minet, P.; Laouiti, A.; Mahfoudh, S. Survey of Deployment Algorithms in Wireless Sensor Networks: Coverage and Connectivity Issues and Challenges. Int. J. Auton. Adapt. Commun. Syst. 2017, 10, 341–390. [Google Scholar] [CrossRef]
- Wang, B. Coverage Problems in Sensor Networks: A Survey. ACM Comput. Surv. 2011, 43, 1–53. [Google Scholar] [CrossRef]
- Fariba, A.; Jafari, N.N. Deployment Strategies in the Wireless Sensor Networks: Systematic Literature Review, Classification, and Current Trends. Wirel. Pers. Commun. 2017, 95, 819–846. [Google Scholar] [CrossRef]
- Devi, G.; Bal, R.S. Node Deployment Coverage in Large Wireless Sensor Networks. J. Netw. Commun. Emerg. Technol. 2016, 6, 19–25. [Google Scholar]
- Anju, S.; Pal, S.R. Survey on Coverage Problems in Wireless Sensor Networks. Wirel. Pers. Commun. 2015, 80, 1475–1500. [Google Scholar] [CrossRef]
- Yoon, Y.; Kim, Y. An Efficient Genetic Algorithm for Maximum Coverage Deployment in Wireless Sensor Networks. IEEE Trans. Cybern. 2013, 43, 1473–1483. [Google Scholar] [CrossRef] [PubMed]
- Zorlu, O.; Sahingoz, O.K. Increasing the coverage of homogeneous wireless sensor network by genetic algorithm based deployment. In Proceedings of the 2016 Sixth International Conference on Digital Information and Communication Technology and its Applications (DICTAP), Konya, Turkey, 21–23 July 2016; pp. 109–114. [Google Scholar] [CrossRef]
- Hanh, N.T.; Binh, H.T.T.; Hoai, N.X.; Palaniswami, M.S. An efficient genetic algorithm for maximizing area coverage in wireless sensor networks. Inf. Sci. 2019, 488, 58–75. [Google Scholar] [CrossRef]
- Njoya, A.N.; Abdou, W.; Dipanda, A.; Tonye, E. Evolutionary-Based Wireless Sensor Deployment for Target Coverage. In Proceedings of the 2015 11th International Conference on Signal-Image Technology Internet-Based Systems (SITIS), Bangkok, Thailand, 23–27 November 2015; pp. 739–745. [Google Scholar] [CrossRef]
- Mnasri, S.; Thaljaoui, A.; Nasri, N.; Val, T. A genetic algorithm-based approach to optimize the coverage and the localization in the wireless audio-sensors networks. In Proceedings of the 2015 International Symposium on Networks, Computers and Communications (ISNCC), Yasmine Hammamet, Tunisia, 13–15 May 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Tossa, F.; Abdou, W.; Ezin, E.C.; Gouton, P. Improving Coverage Area in Sensor Deployment Using Genetic Algorithm. In Proceedings of the Computational Science—ICCS 2020, Amsterdam, The Netherlands, 3–5 June 2020; Krzhizhanovskaya, V.V., Závodszky, G., Lees, M.H., Dongarra, J.J., Sloot, P.M.A., Brissos, S., Teixeira, J., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 398–408. [Google Scholar]
- Tossa, F.; Abdou, W.; Ansari, K.; Ezin, E.C.; Gouton, P. Area Coverage Maximization under Connectivity Constraint in Wireless Sensor Networks. Sensors 2022, 22, 1712. [Google Scholar] [CrossRef]
- Hanaa, Z.; Mahmoud, B.; Mostafa, E.; Hesham, A.; Ajith, A. An improved dynamic deployment technique based-on genetic algorithm (IDDT-GA) for maximizing coverage in wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 4177–4194. [Google Scholar]
- Ha, L.D.T.; Binh, N.T.; Nghia, H.T.T.; Duc, N. An Improved Genetic Algorithm for Maximizing Area Coverage in Wireless Sensor Networks. In Proceedings of the Sixth International Symposium on Information and Communication Technology, Hue, Vietnam, 3–4 December 2015; Association for Computing Machinery: New York, NY, USA, 2015. SoICT 2015. pp. 61–66. [Google Scholar] [CrossRef]
- Farsi, M.; Elhosseini, M.A.; Badawy, M.; Arafat Ali, H.; Zain Eldin, H. Deployment Techniques in Wireless Sensor Networks, Coverage and Connectivity: A Survey. IEEE Access 2019, 7, 28940–28954. [Google Scholar] [CrossRef]
- Subash, H.; Pratyay, K. Coverage and connectivity aware energy efficient scheduling in target based wireless sensor networks: An improved genetic algorithm based approach. Wirel. Netw. 2019, 15, 1995–2011. [Google Scholar] [CrossRef]
- Gupta, S.K.; Kuila, P.; Jana, P.K. Genetic algorithm approach for k-coverage and m-connected node placement in target based wireless sensor networks. Comput. Electr. Eng. 2016, 56, 544–556. [Google Scholar] [CrossRef]
- Njoya, A.N.; Ari, A.A.A.; Awa, M.N.; Titouna, C.; Labraoui, N.; Effa, J.Y.; Abdou, W.; Gueroui, A. Hybrid Wireless Sensors Deployment Scheme with Connectivity and Coverage Maintaining in Wireless Sensor Networks. Wirel. Pers. Commun. 2020, 56, 544–556. [Google Scholar] [CrossRef]
- Amin, B.M.; M’hammed, S.; David, B.; Louis, A.; El-Hami, A.; Belahcene, M. Multi-Objective WSN Deployment Using Genetic Algorithms Under Cost, Coverage, and Connectivity Constraints. Wirel. Pers. Commun. 2017, 94, 2739–2768. [Google Scholar] [CrossRef]
- Sheikh-Hosseini, M.; Samareh Hashemi, S.R. Connectivity and coverage constrained wireless sensor nodes deployment using steepest descent and genetic algorithms. Expert Syst. Appl. 2022, 190, 116164. [Google Scholar] [CrossRef]
- Cardei, I.; Cardei, M. Energy-efficient connected-coverage in wireless sensor networks. Int. J. Sens. Netw. 2008, 3, 201–210. [Google Scholar] [CrossRef]
- Vidhya, J.; Prasanna, P.; Margarat, M.; Jayalakshmy, S. Enhancing Network Coverage using sensing models in wireless sensor network. J. Phys. Conf. Ser. 2021, 1717, 012062. [Google Scholar] [CrossRef]
- Haseeb, K.; Ud Din, I.; Al-Mogren, A.; Islam, N. An Energy Efficient and Secure IoT-based WSN Framework: An application to Smart Agriculture. Sensors 2020, 20, 2081. [Google Scholar] [CrossRef]
- Ghani, A.; Naqvi, S.H.A.; Ilyas, M.U.; Khan, M.K.; Hassan, A. Energy efficiency in multipath Rayleigh faded wireless sensor networks using collaborative communication. IEEE Access 2019, 7, 26558–26570. [Google Scholar] [CrossRef]
- Williams, A.J.; Torquato, M.F.; Cameron, I.M.; Fahmy, A.A.; Sienz, J. Survey of energy harvesting technologies for wireless sensor networks. IEEE Access 2021, 9, 77493–77510. [Google Scholar] [CrossRef]
- Khernane, S.; Bouam, S.; Arar, C. Renewable energy harvesting for wireless sensor networks in precision agriculture. Int. J. Networked Distrib. Comput. 2024, 12, 8–16. [Google Scholar] [CrossRef]
- Sah, D.K.; Hazra, A.; Mazumdar, N.; Amgoth, T. An efficient routing awareness based scheduling approach in energy harvesting wireless sensor networks. IEEE Sens. J. 2023, 23, 17638–17647. [Google Scholar] [CrossRef]
- Sharma, P.; Singh, A.K. A survey on RF energy harvesting techniques for lifetime enhancement of wireless sensor networks. Sustain. Comput. Inform. Syst. 2023, 37, 100836. [Google Scholar] [CrossRef]
- Van Leemput, D.; Hoebeke, J.; De Poorter, E. Integrating battery-less energy harvesting devices in multi-hop industrial wireless sensor networks. IEEE Commun. Mag. 2024, 62, 66–73. [Google Scholar] [CrossRef]
- Wang, Z.; Yong, T.; Song, X. Fast and Low-Overhead Time Synchronization for Industrial Wireless Sensor Networks with Mesh-Star Architecture. Sensors 2023, 23, 3792. [Google Scholar] [CrossRef]
- Liu, W.; Fan, R.; Mai, Y.; Wan, Z. Clock synchronization based on pulse with propagation delay eliminated in wireless sensor networks. IET Commun. 2023, 17, 1955–1961. [Google Scholar] [CrossRef]
- Shi, F.; Yang, S.X.; Tuo, X.; Ran, L.; Huang, Y. A novel rapid-flooding approach with real-time delay compensation for wireless-sensor network time synchronization. IEEE Trans. Cybern. 2020, 52, 1415–1428. [Google Scholar] [CrossRef]
- Hababeh, I.; Khalil, I.; Al-Sayyed, R.; Moshref, M.; Nofal, S.; Rodan, A. Competent Time Synchronization Mac Protocols to Attain High Performance of Wireless Sensor Networks for Secure Communication. Cybern. Inf. Technol. 2023, 23, 75–93. [Google Scholar] [CrossRef]
- Wang, Z.; Sun, D.; Yu, C. Reference broadcast-based secure time synchronization for industrial wireless sensor networks. Appl. Sci. 2023, 13, 9223. [Google Scholar] [CrossRef]
- Fawad, M.; Khan, M.Z.; Ullah, K.; Alasmary, H.; Shehzad, D.; Khan, B. Enhancing localization efficiency and accuracy in wireless sensor networks. Sensors 2023, 23, 2796. [Google Scholar] [CrossRef]
- Wang, H.; Zhang, L.; Liu, B. Research and Design of a Hybrid DV-Hop Algorithm Based on the Chaotic Crested Porcupine Optimizer for Wireless Sensor Localization in Smart Farms. Agriculture 2024, 14, 1226. [Google Scholar] [CrossRef]
- Mohapatra, H.; Rath, A.K. Survey on fault tolerance-based clustering evolution in WSN. IET Netw. 2020, 9, 145–155. [Google Scholar] [CrossRef]
- Yang, X.; Han, G.; Liu, L.; Qian, A.; Zhang, W. IGRC: An improved grid-based joint routing and charging algorithm for wireless rechargeable sensor networks. Future Gener. Comput. Syst. 2019, 92, 837–845. [Google Scholar] [CrossRef]
- Das, I.; Shaw, R.N.; Das, S. Analysis of effect of fading models in wireless sensor networks. In Proceedings of the 2020 IEEE International Conference on Computing, Power and Communication Technologies (GUCON), Greater Noida, India, 2–4 October 2020; pp. 858–860. [Google Scholar]
- Ha, D.H.; Ha, D.B.; Vo, V.A.; Voznak, M. Performance Analysis on Wireless Power Transfer Wireless Sensor Network with Best AF Relay Selection over Nakagami-m Fading. In Proceedings of the Industrial Networks and Intelligent Systems, Ho Chi Minh City, Vietnam, 19 August 2019; Duong, T.Q., Vo, N.S., Nguyen, L.K., Vien, Q.T., Nguyen, V.D., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 193–204. [Google Scholar]
- Fouilhoux, P. Méthodes Heuristiques en Optimisation Combinatoire. Available online: http://www-poleia.lip6.fr/~fouilhoux/documents/synthese-heuristique (accessed on 19 July 2022).
- Business, E.A.F. Algorithmes: Heuristiques et Méta-Heuristiques. Available online: https://www.eurodecision.com/algorithmes/recherche-operationnelle-optimisation/heuristiques-meta-heuristiques (accessed on 19 July 2022).
- Vijayalakshmi, K.; Anandan, P. A multi objective Tabu particle swarm optimization for effective cluster head selection in WSN. Clust. Comput. 2019, 22, 12275–12282. [Google Scholar] [CrossRef]
- Eshelman, L.J.; Schaffer, J.D. Real-Coded Genetic Algorithms and Interval-Schemata. In Foundations of Genetic Algorithms; Whitley, L.D., Ed.; Elsevier: Amsterdam, The Netherlands, 1993; Volume 2, pp. 187–202. [Google Scholar] [CrossRef]
- Lu, Z.; Wang, C.; Wang, P.; Xu, W. 3D Deployment Optimization of Wireless Sensor Networks for Heterogeneous Functional Nodes. Sensors 2025, 25, 1366. [Google Scholar] [CrossRef]
- Iqbal, M.; Naeem, M.; Anpalagan, A.; Ahmed, A.; Azam, M. Wireless sensor network optimization: Multi-objective paradigm. Sensors 2015, 15, 17572–17620. [Google Scholar] [CrossRef]
- Feng, H.; Xu, C.; Jin, B.; Zhang, M. A Deployment Optimization for Wireless Sensor Networks Based on Stacked Auto Encoder and Probabilistic Neural Network. Digit. Commun. Netw. 2024. [CrossRef]
- Karimi-Bidhendi, S.; Guo, J.; Jafarkhani, H. Energy-efficient deployment in static and mobile heterogeneous multi-hop wireless sensor networks. IEEE Trans. Wirel. Commun. 2021, 21, 4973–4988. [Google Scholar] [CrossRef]
- Elfouly, F.H.; Ramadan, R.A.; Khedr, A.Y.; Yadav, K.; Azar, A.T.; Abdelhamed, M.A. Efficient node deployment of large-scale heterogeneous wireless sensor networks. Appl. Sci. 2021, 11, 10924. [Google Scholar] [CrossRef]
- Sarkar, N.I.; Gul, S. Deploying Wireless Sensor Networks in Multi-Story Buildings toward Internet of Things-Based Intelligent Environments: An Empirical Study. Sensors 2024, 24, 3415. [Google Scholar] [CrossRef]
- Sukhadeo, B.S.; Dhurgude, S.D.; Sinkar, Y.D.; Athawale, S.V. A framework of survivability model virtualized wireless sensor networks for IOT-assisted wireless sensor network. Internet Technol. Lett. 2025, 8, e552. [Google Scholar] [CrossRef]
- Islam, M.M.; Hassan, M.M.; Lee, G.W.; Huh, E.N. A survey on virtualization of wireless sensor networks. Sensors 2012, 12, 2175–2207. [Google Scholar] [CrossRef]
- Silva, M.; Santos, J.; Curado, M. The path towards virtualized wireless communications: A survey and research challenges. J. Netw. Syst. Manag. 2024, 32, 12. [Google Scholar] [CrossRef]

| Node Type | Core Components | Roles and Responsibilities | Communication Interface and Range | Energy Source | Processing Capacity |
|---|---|---|---|---|---|
| Regular Node | Radio transceiver, microcontroller, memory, power unit | Packet forwarding, basic routing, neighbor discovery | Low-power radio (e.g., IEEE 802.15.4), 10–100 m | Battery (Li-ion, alkaline) or ambient energy harvesting | MCU 8–32 MHz, 16–256 KB RAM |
| Sensor Node | Regular node components + sensing unit(s), A/D converter | Periodic or event-driven data acquisition, local filtering/aggregation | Same radio + I²C/SPI interfaces for external sensors | As Regular Node | MCU with sensor driver support, moderate on-board storage |
| Actuator Node | Regular node + D/A drivers, relays, motor drivers | Executes physical commands (motions, switching) | Same radio interface as Sensor Node | Higher-capacity battery, supercapacitors | MCU with real-time OS (TinyOS/Contiki) |
| Gateway Node | High-power radio (Wi-Fi, cellular), Ethernet/Wi-Fi module, powerful CPU, extended memory | Data aggregation, protocol translation, network management, remote updates | Multi-interface: IEEE 802.15.4 (WSN) + Ethernet/Wi-Fi/LTE (backhaul) | Mains power (redundant supply) | CPU > 100 MHz, > 1 MB RAM |
| Sink Node | High-power transceiver, high-performance CPU, large storage, serial converter | Final data collection, data fusion/analysis, cloud/server interface | Same as Gateway + optional satellite/mesh backhaul | Mains or UPS backup | Multi-core CPU, gigabytes of RAM/storage |
| Strategy | Key Metrics | Ideal Scenarios |
|---|---|---|
| Static/Deterministic | Coverage ↑, Connectivity ↑, Mobility energy ↓ | Fixed-infrastructure sites; factory floors; smart buildings where nodes can be placed precisely. |
| Stochastic/Random | Coverage variance moderate, Connectivity probabilistic, Low planning cost | Disaster zones, battlefields, environmental drops (aircraft); rough terrain where manual placement is infeasible. |
| Grid-based (Triangular/Square/Hexagonal) | Uniform coverage, Predictable connectivity, Node count optimal | Agricultural monitoring, large-scale environmental surveys, perimeter surveillance requiring regular spacing. |
| Single-Objective Optimization | Maximizes one metric (e.g., coverage or lifetime), Simpler computation | Applications with a hard primary goal (e.g., gas leak detection demands maximal sensing). |
| Multi-Objective Optimization | Balanced coverage/energy/latency, Compromise solutions | Quality-critical WSNs (e.g., structural health monitoring) requiring trade-offs between lifetime and QoS. |
| Homogeneous | Uniformity, Easier management, Lower deployment cost | Low-cost mass deployments (e.g., temperature logging) where identical nodes suffice. |
| Heterogeneous | Specialized roles (sensors, actuators, relays), Enhanced functionality | Industrial automation, smart grids, or precision agriculture needing both sensing and actuation. |
| Dynamic/Mobile | Adaptivity, Fault tolerance, Coverage healing | Vehicular networks, emergency response, mobile target tracking requiring repositioning. |
| Source | Power Density | Advantages | Challenges | Ref. |
|---|---|---|---|---|
| Solar | High (mW–W/cm2) | High yield, mature technology | Weather-dependent, storage overhead | [43] |
| Thermal (TEG) | Moderate (µW–mW/cm2) | Continuous in gradients | Low voltage, efficiency drops at small | [44] |
| Piezoelectric | Variable (µW–mW) | Suitable for structural/vibration contexts | Resonance tuning, narrow bandwidth | [45] |
| RF | Low (µW–µW/cm2) | Ubiquitous indoor sources | Low energy density, rectenna design | [46] |
| Hybrid Systems | Combined | Enhanced reliability, seamless switching | Increased complexity, cost | [47] |
| Model | Description | Consideration | Mathematical Expression |
|---|---|---|---|
| Binary | Simplest model based on circular detection range. | Assumes all points within the sensor’s range are covered. | |
| Elves | Probabilistic model considering uncertain detection distances. | Accounts for node distance and characteristics. | |
| Shadow Fading | Accounts for signal strength variations due to obstacles. | Models signal strength variations using log-normal distribution. | |
| Rayleigh Fading | Models signal strength variations due to multi-path propagation. | Follows Rayleigh distribution for random amplitude variations. | |
| Nakagami-m Fading | Generalized fading model for LOS and NLOS scenarios. | Characterized by Nakagami distribution with fading parameter m. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tossa, F.; Faga, Y.; Abdou, W.; Ezin, E.C.; Gouton, P. Wireless Sensor Network Deployment: Architecture, Objectives, and Methodologies. Sensors 2025, 25, 3442. https://doi.org/10.3390/s25113442
Tossa F, Faga Y, Abdou W, Ezin EC, Gouton P. Wireless Sensor Network Deployment: Architecture, Objectives, and Methodologies. Sensors. 2025; 25(11):3442. https://doi.org/10.3390/s25113442
Chicago/Turabian StyleTossa, Frantz, Yves Faga, Wahabou Abdou, Eugène C. Ezin, and Pierre Gouton. 2025. "Wireless Sensor Network Deployment: Architecture, Objectives, and Methodologies" Sensors 25, no. 11: 3442. https://doi.org/10.3390/s25113442
APA StyleTossa, F., Faga, Y., Abdou, W., Ezin, E. C., & Gouton, P. (2025). Wireless Sensor Network Deployment: Architecture, Objectives, and Methodologies. Sensors, 25(11), 3442. https://doi.org/10.3390/s25113442









